Vulnerability detection method and device
A vulnerability detection and vulnerability technology, applied in the computer field, can solve the problem of low vulnerability detection efficiency, and achieve the effect of improving vulnerability detection efficiency and saving development costs.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
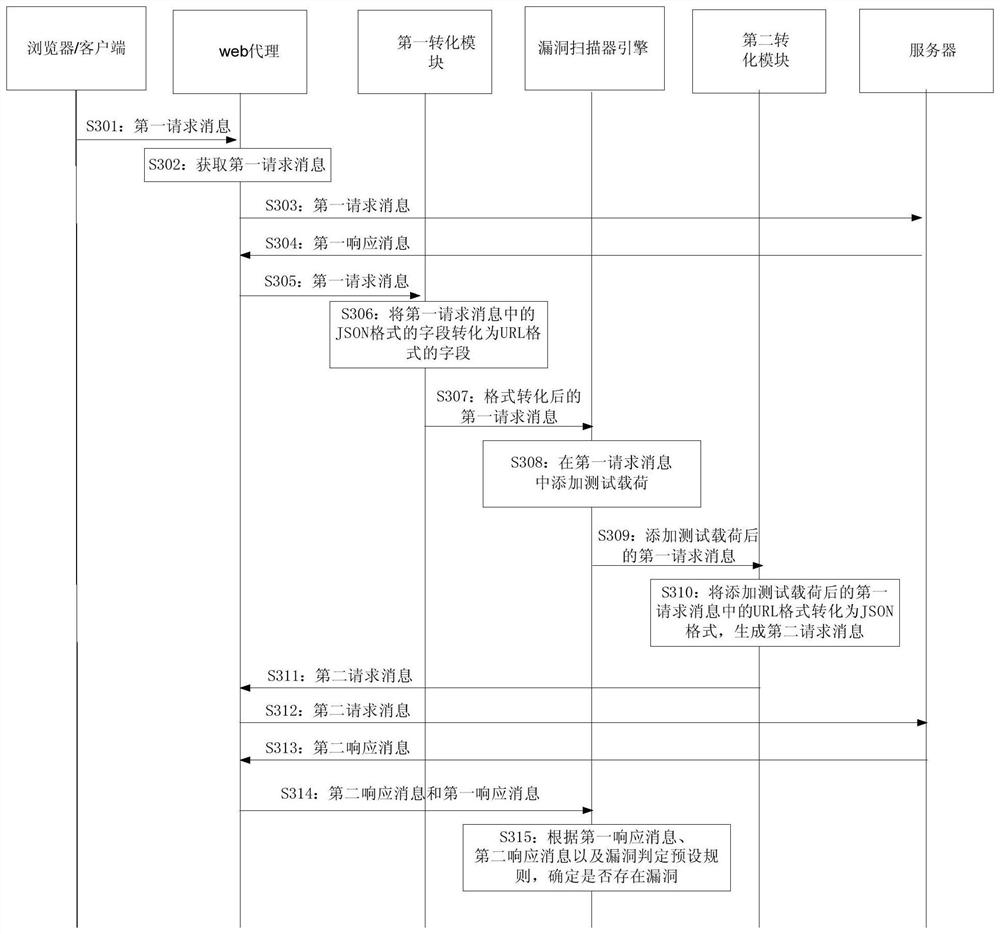
[0088] image 3 It is a schematic flow chart of Embodiment 1 of the vulnerability detection method of this application. The vulnerability detection method of this embodiment is applied to a vulnerability detection system, which includes a browser / client, a web proxy, a first conversion module, and a vulnerability scanner. engine and a second conversion module; wherein, the first conversion module is used to convert JSON to URL format, and the second conversion module is used to convert URL format to JSON format, and the first conversion module and the second conversion module can be deployed on the web agent It can also be deployed independently, and this application does not limit it; wherein, the vulnerability scanner engine is a vulnerability scanner engine based on the URL format, that is, it can only recognize request messages in the URL format, and when adding a test load, based on URL format is added; Browser / client and server communicate based on JSON format, the metho...
Embodiment 2
[0142] Figure 4 It is a schematic flow chart of Embodiment 2 of the vulnerability detection method of this application. The difference between Embodiment 2 and Embodiment 1 is that the way to obtain the first response message is that the vulnerability scanner engine obtains it without adding a load. image 3 The same steps as in , see image 3 A detailed description of the same steps in , Figure 4 will not repeat them, such as Figure 4 Shown:
[0143] S401: The browser / client sends a first request message to the web proxy.
[0144] S402: The web agent acquires the first request message.
[0145] S403: The web proxy sends a first request message to the first transformation module.
[0146] S404: The first converting module converts the fields in the JSON format in the first request message into the fields in the URL format.
[0147] S405: The first converting module sends the format-converted first request message to the vulnerability scanner engine.
[0148] S406: Th...
Embodiment 3
[0165] Embodiment 3 is based on Embodiment 1 or Embodiment 2. Further, after the first conversion module performs format conversion, it also includes adding a format conversion identifier in the first request message; before the second conversion module performs format conversion, it also includes: It includes determining that the first request message contains the format conversion identifier.
[0166] In this embodiment, the format conversion flag is used to identify whether the format conversion has been performed before adding the test load, so as to facilitate another format conversion after adding the test load to ensure normal communication.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com