Zero false alarm detection method for Android App vulnerabilities
A detection method and vulnerability technology, applied in the fields of instruments, electrical digital data processing, platform integrity maintenance, etc., can solve problems such as slow program execution, verification loopholes, and high false positive rate, so as to solve the problem of high false positive rate and improve accuracy. rate, the effect of reducing the number of
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
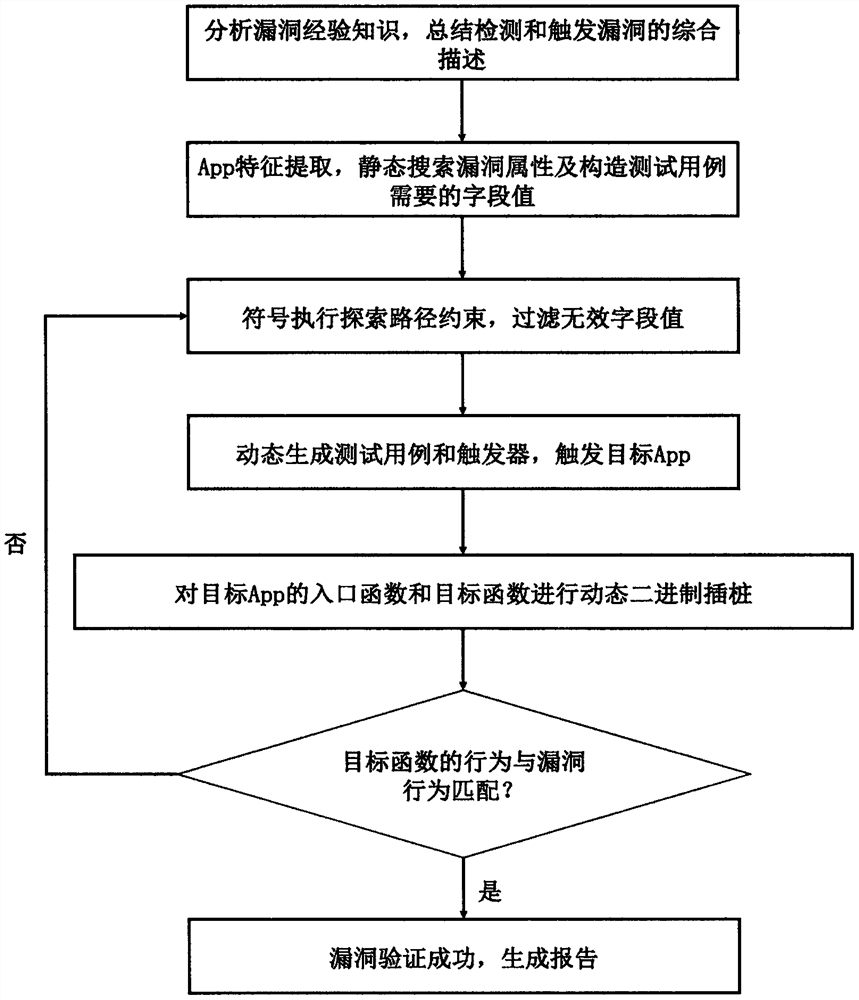
[0019] Such as figure 1 Shown, the realization steps of the present invention are as follows:
[0020] 1. Analyze the experience and knowledge of Android App vulnerabilities, summarize the comprehensive description of detection and trigger vulnerabilities
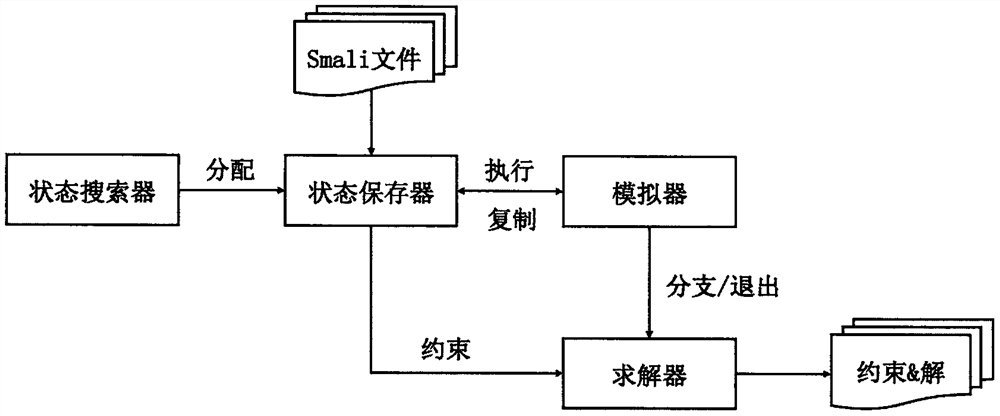
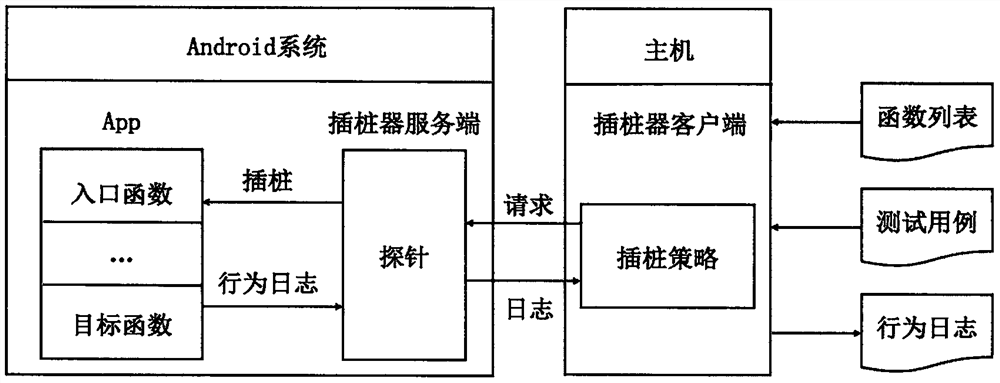
[0021] The present invention summarizes the comprehensive description of detecting and triggering the vulnerability by analyzing the attack path of the vulnerability, the CVE report, the experience knowledge of the vulnerability such as the Android development document, and comprehensively describes the type of the vulnerability. The summarized information includes: (1) components, that is, objects with vulnerabilities in Android App; (2) attributes, that is, the necessary conditions for generating vulnerabilities; (3) entry functions, that can be rewritten by developers and accept external inputs belonging to (1 ) function set; (4) target function, a set of functions that can trigger vulnerabilities. They are usually sys...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com