Vulnerability detection method and device, server and storage medium
A vulnerability detection and vulnerability technology, applied in computer security devices, instruments, program code conversion, etc., can solve problems such as economic losses, Trojan horse viruses, and user privacy data theft
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
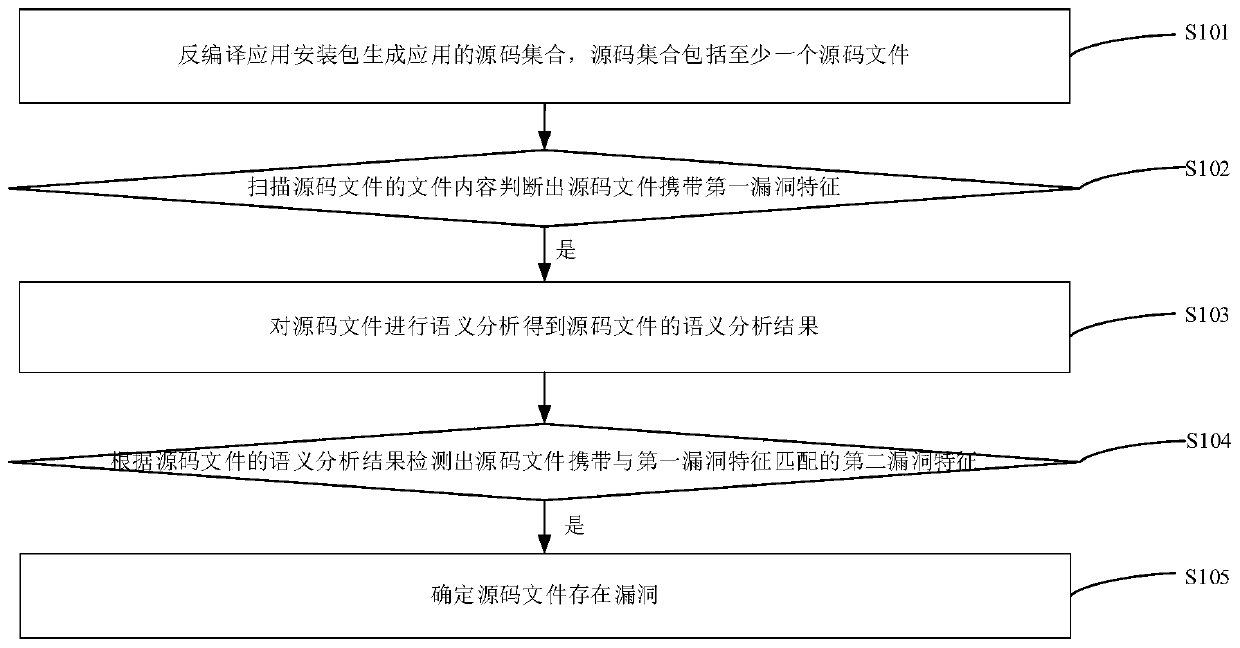
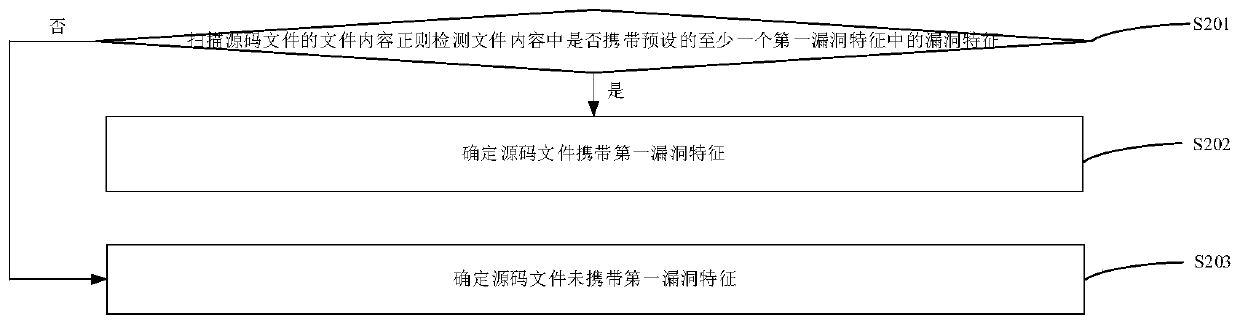
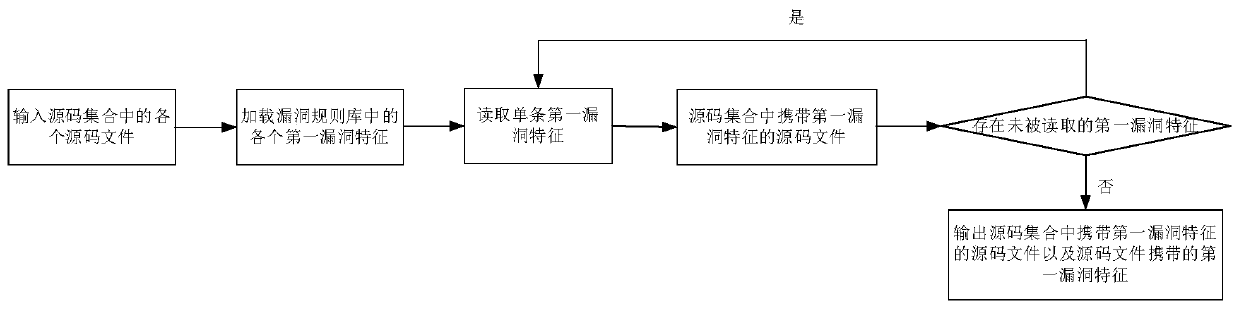
[0032] Based on the above background technology, it can be seen that with the rapid increase of the number of computer applications, the security of computer applications becomes more and more important. If there are loopholes in the computer application and once the vulnerability is invaded by an attacker, the privacy data of the user in the computer application may be stolen, a Trojan horse virus may appear in the terminal where the computer application is installed, and even serious economic losses may occur.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com