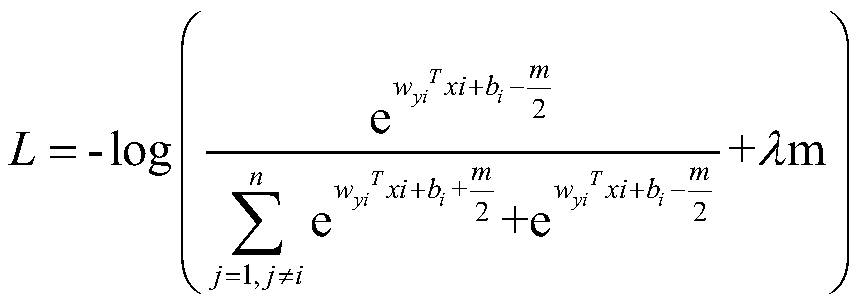Patents
Literature
164results about How to "Improve audit efficiency" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Firewall policy processing method and device
InactiveCN104135461AImprove audit efficiencyGood policy managementTransmissionDistributed computingAccess control list
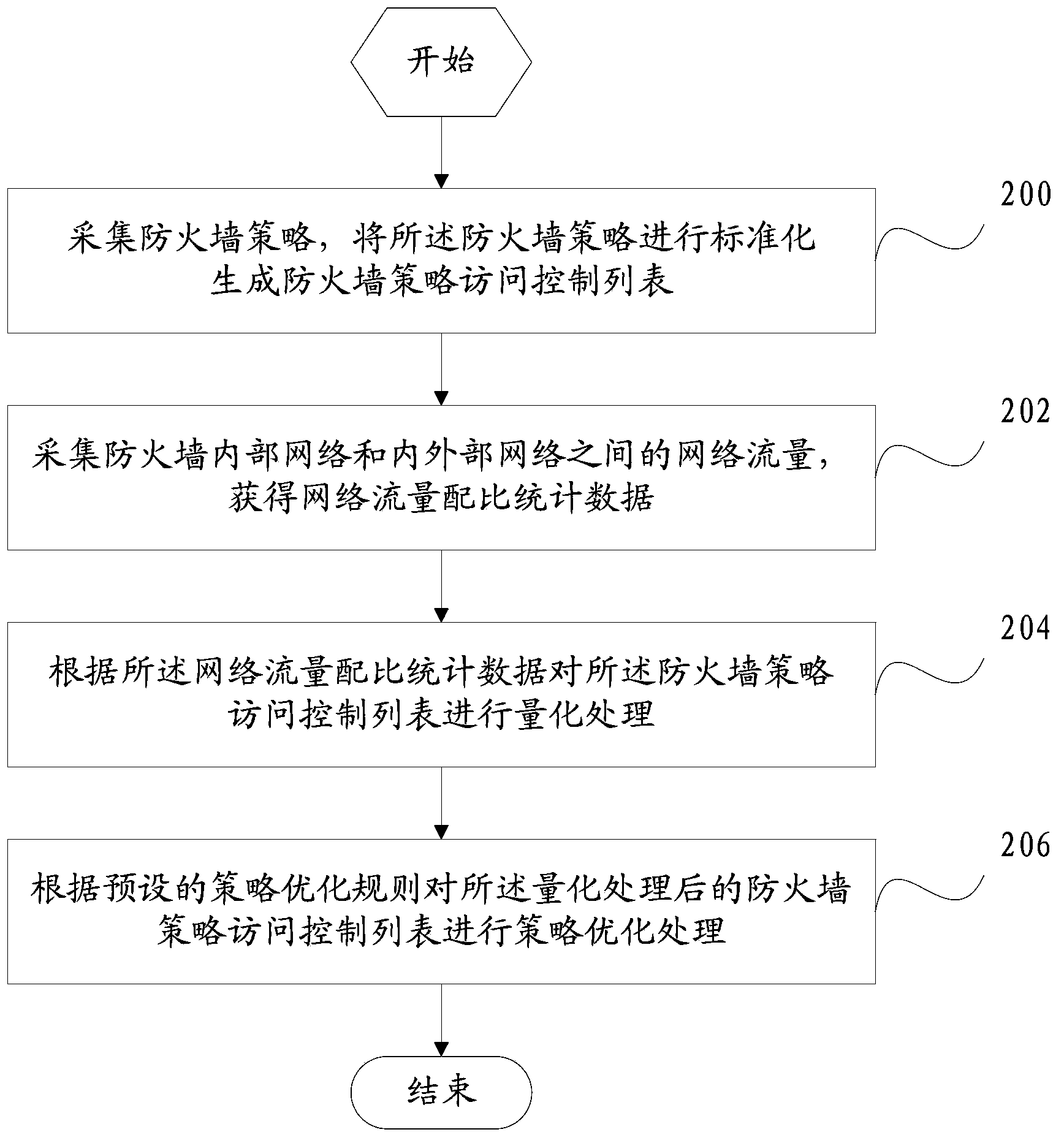
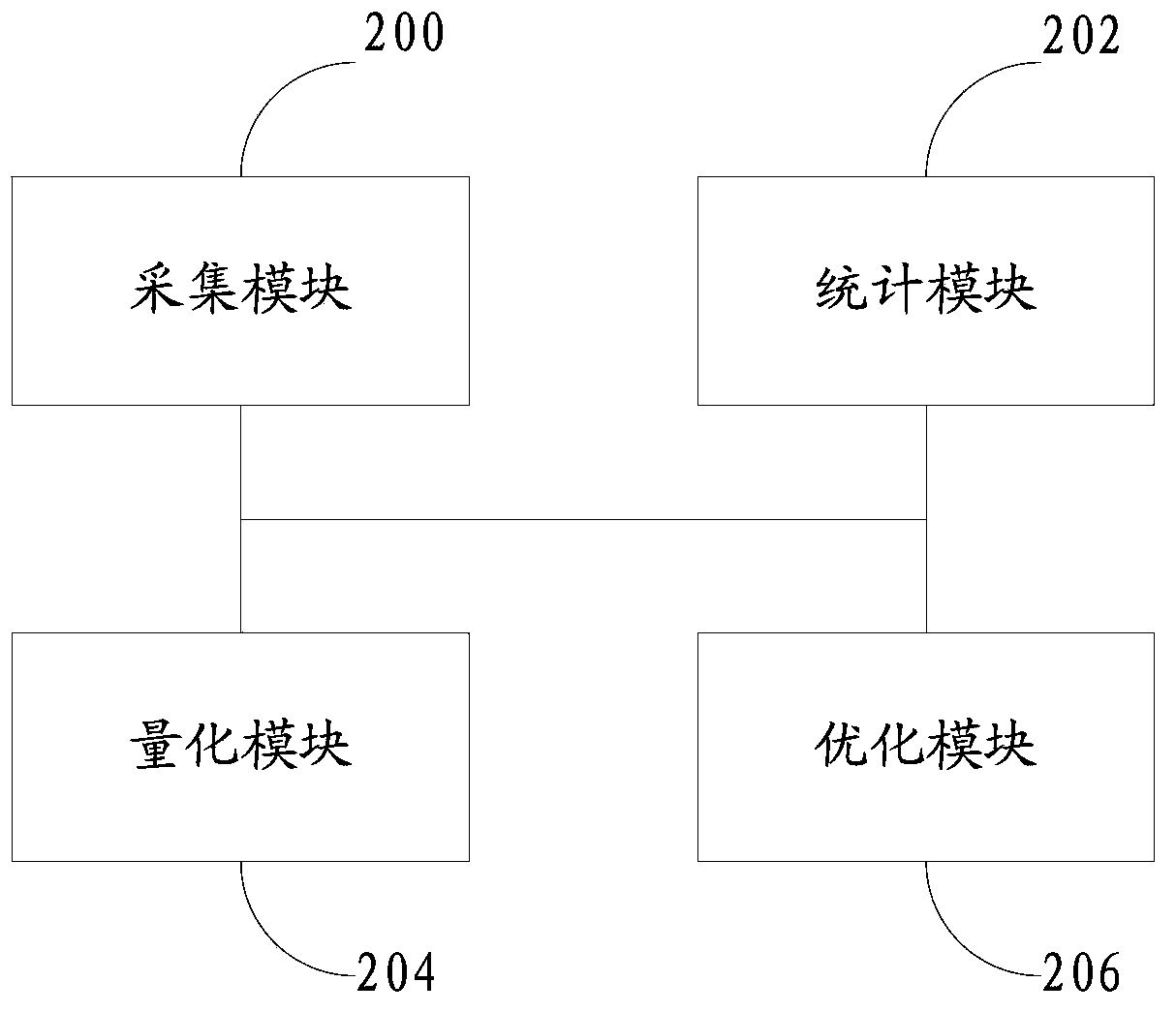
The invention discloses a firewall policy processing method and device. The method comprises the following steps: acquiring firewall policies, and standardizing the firewall policies to generate a firewall policy access control list; acquiring network flow of an internal network as well as between internal and external networks of a firewall to obtain network flow proportion statistics; quantifying the firewall policy access control list according to the network flow proportion statistics; and performing policy optimization processing on the quantified firewall policy access control list according to a preset policy optimizing rule. With the firewall policy processing method and device, the defect of waste of time and labor in manual auditing of firewall policies can be overcome, the management of firewall change policies is reinforced, the establishment of policies with safety risks is avoided, and the security of the firewall is enhanced.
Owner:HANDAN BRANCH OF CHINA MOBILE GRP HEBEI COMPANYLIMITED
Method for completely auditing user behaviors under centralization access mode
InactiveCN101442449AIntegrity guaranteedResolve integrityData switching networksNetwork behaviorApplication software
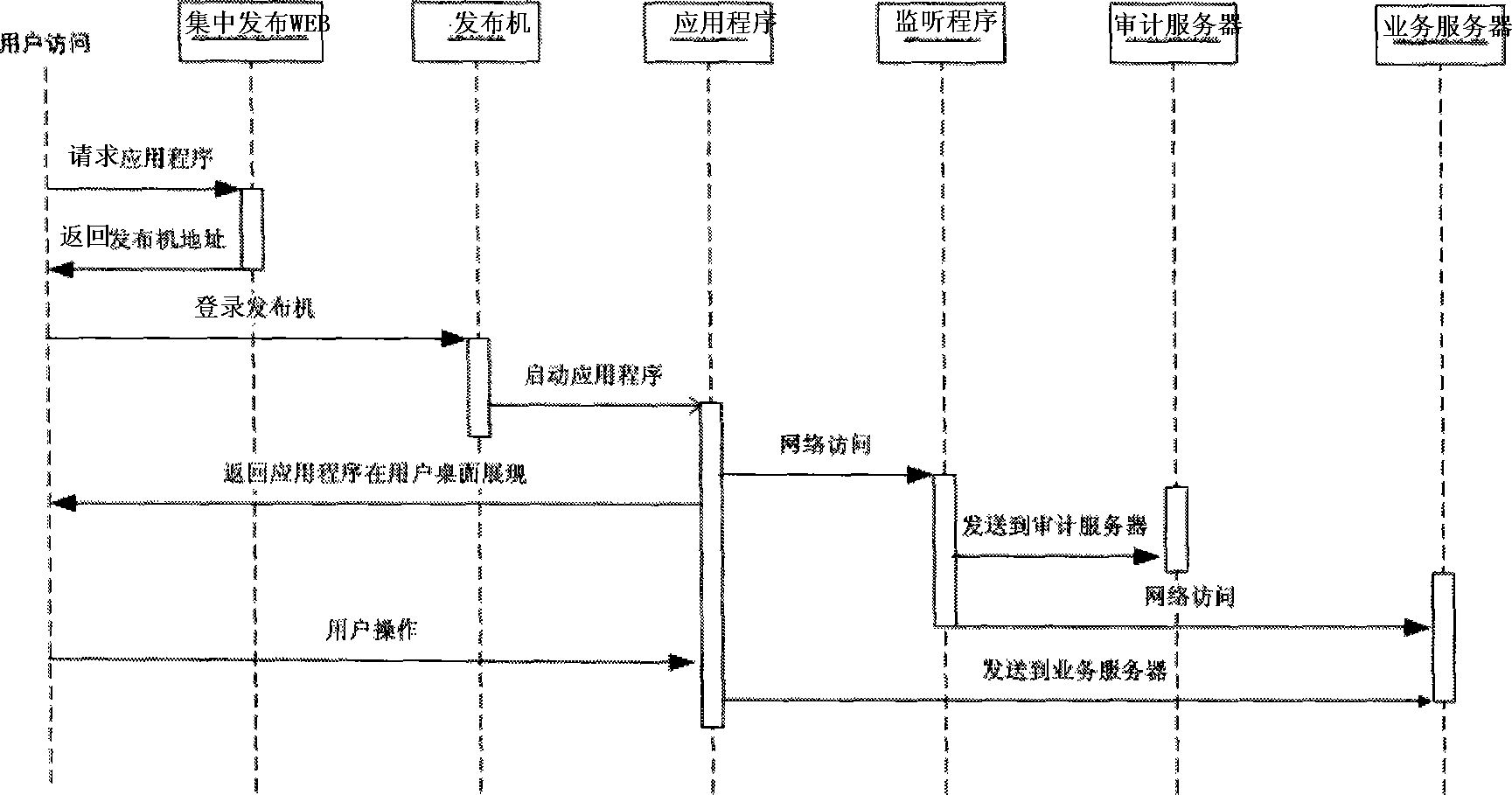
The invention discloses a method for overall auditing behavior of a customer under an integrated access pattern, wherein an integrated issuing platform consisting of a plurality of issuing machines is provided, each issuing machine is provided with application software and a network monitoring program; and an auditing server is linked to the network in a bypass mode, and a network acquisition module of the method acquires a network behavior log operated by a user to an auditing server which matches the network access information of the user transmitted by the monitoring program with the network operation log to form complete auditing information for search and analysis, thereby realizing complete auditing data based on the operator. The invention achieves complementarity of advantages of the monitoring program and network behavior auditing methods through the combination of two technological means, thereby ensuring the completeness of the auditing data and improving the auditing efficiency.
Owner:CHINA MOBILE GROUP ZHEJIANG
Operation and maintenance safety auditing method and system
InactiveCN106330919AAvoid substitutionGuarantee authenticityCharacter and pattern recognitionTransmissionCorrelation analysisComputer science
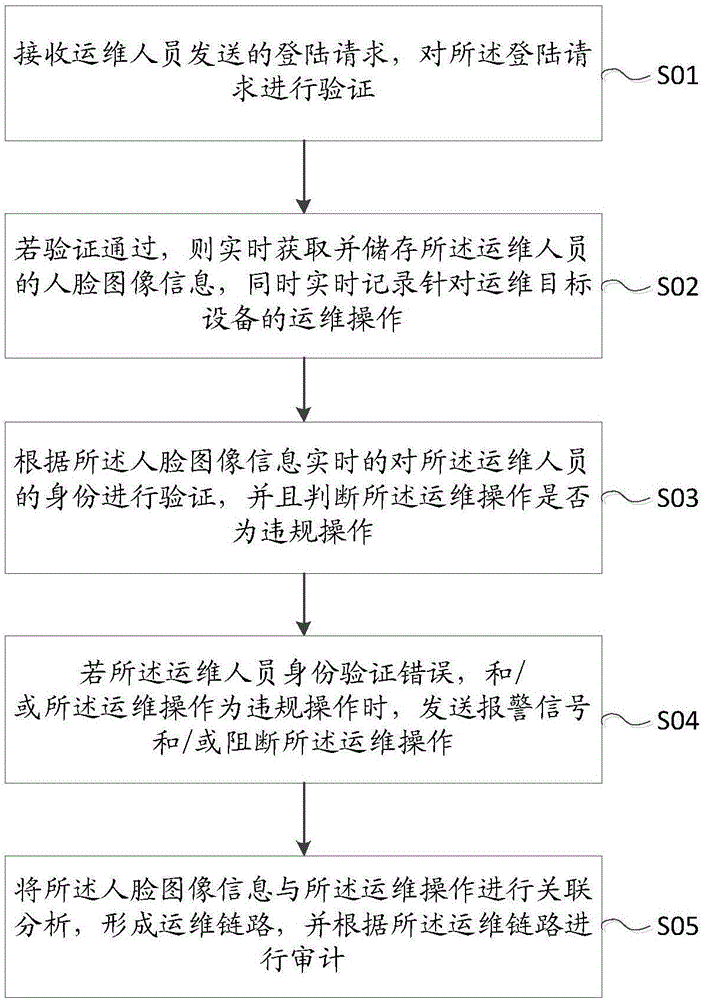
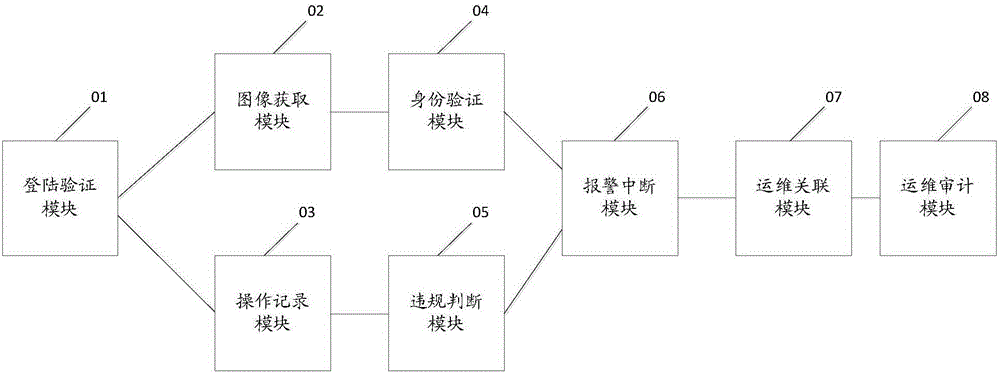
The invention discloses an operation and maintenance safety auditing method. The operation and maintenance safety auditing method comprises the following steps: receiving a login request sent by operation and maintenance personnel, and verifying the login request; if the verification is passed, obtaining and storing face image information of the operation and maintenance personnel in real time, and meanwhile recording an operation and maintenance operation on operation and maintenance target equipment in real time; verifying the identity of the operation and maintenance personnel in real time according to the face image information, and judging whether the operation and maintenance operation is an illegal operation; if the verification of the identity of the operation and maintenance personnel is wrong, and / or the operation and maintenance operation is the illegal operation, sending an alarm signal and / or interrupting the operation and maintenance operation; and carrying out correlation analysis on the face image information and the operation and maintenance operation, forming an operation and maintenance link, and carrying out audit according to the operation and maintenance link. Identity authentication can be carried out on the identity of the IT operation and maintenance personnel in an operation and maintenance personnel process, and the illegal operation and maintenance operation can be found in time. The invention further discloses an operation and maintenance safety auditing system.
Owner:STATE GRID CORP OF CHINA +2
Rule-based automatic auditing method and system
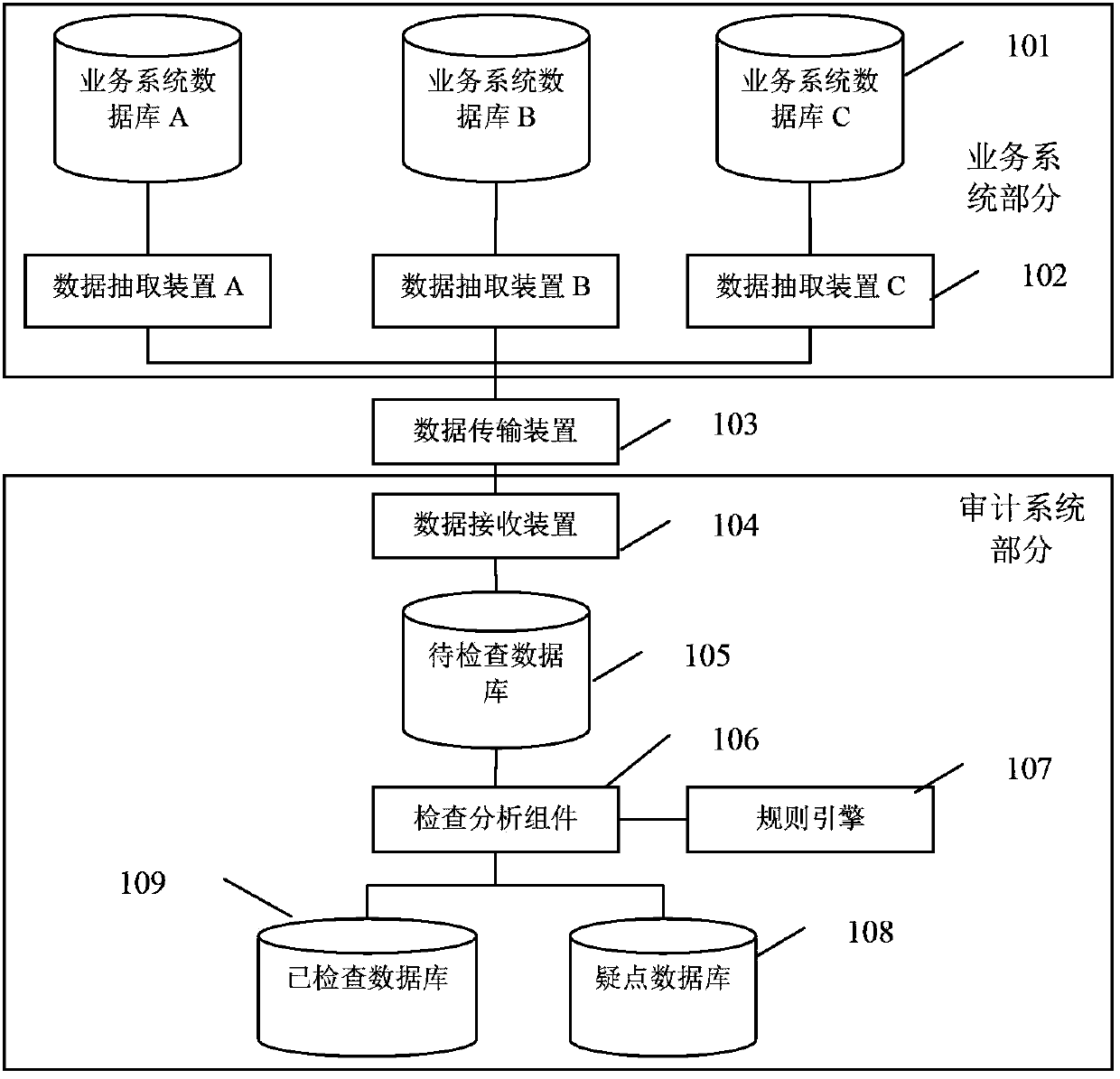
The invention provides a rule-based automatic auditing system. The automatic auditing system comprises a business system part, a data transmission device and an auditing system part, which are sequentially connected, wherein the business system part comprises a plurality of business systems, each business system comprises a business system database and a data extracting device, the business system database is connected with the data transmission device through the data extracting device, the data transmission device is used for transmitting data prepared by all the business systems to a data receiving device of the auditing system part through an internet at regular intervals, and the auditing system part comprises the data receiving device, a database to be checked, a checking analyzing component, a rule engine, a doubtful point database, and a checked database. The rule-based automatic auditing system can continue auditing and monitoring automatically, can find abnormal data in a large number of business data automatically, improves the auditing efficiency, and can customize check rules; furthermore, the rule definition is described with natural language and is simple and easy to understand, so that the application range of the customized check rules is enlarged.
Owner:SHANGHAI BAOSIGHT SOFTWARE CO LTD
Cloud storage data auditing method for preventing secret key from being revealed
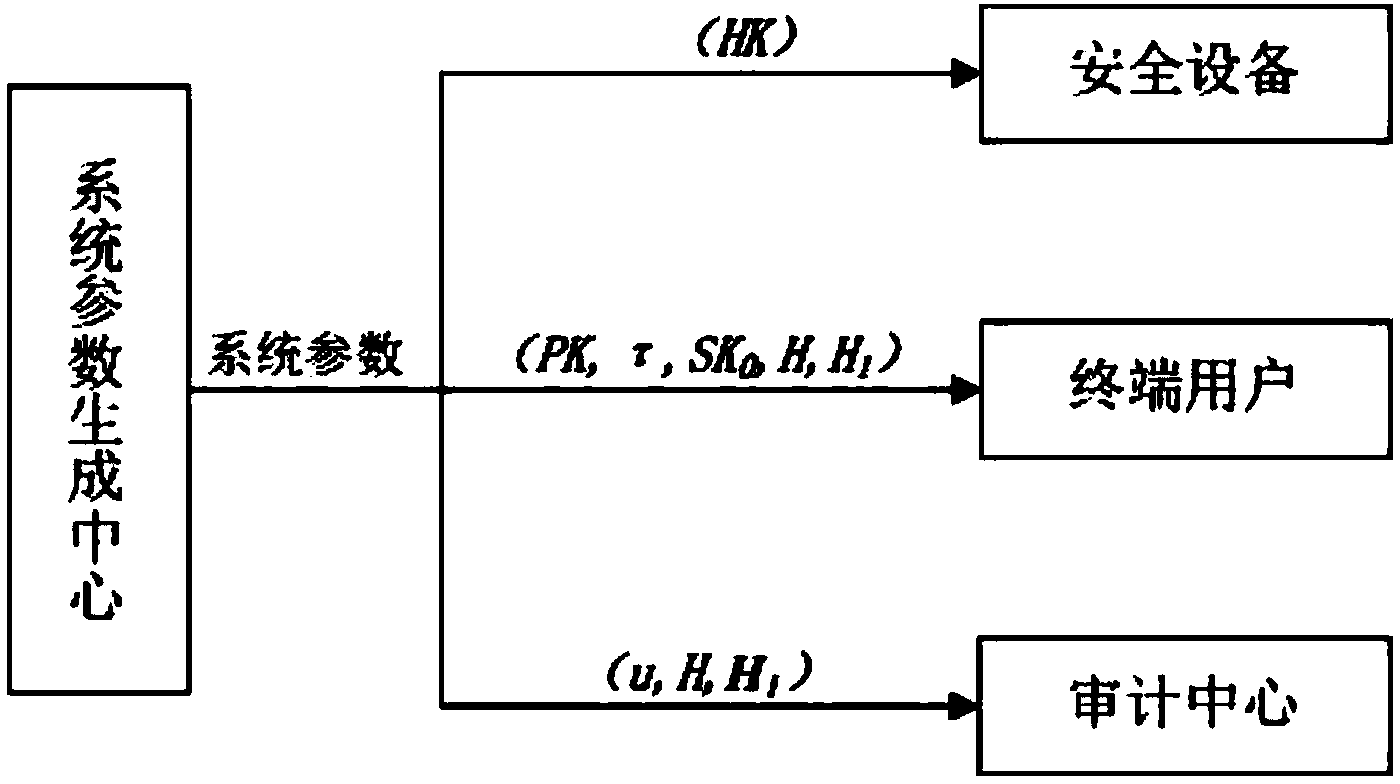
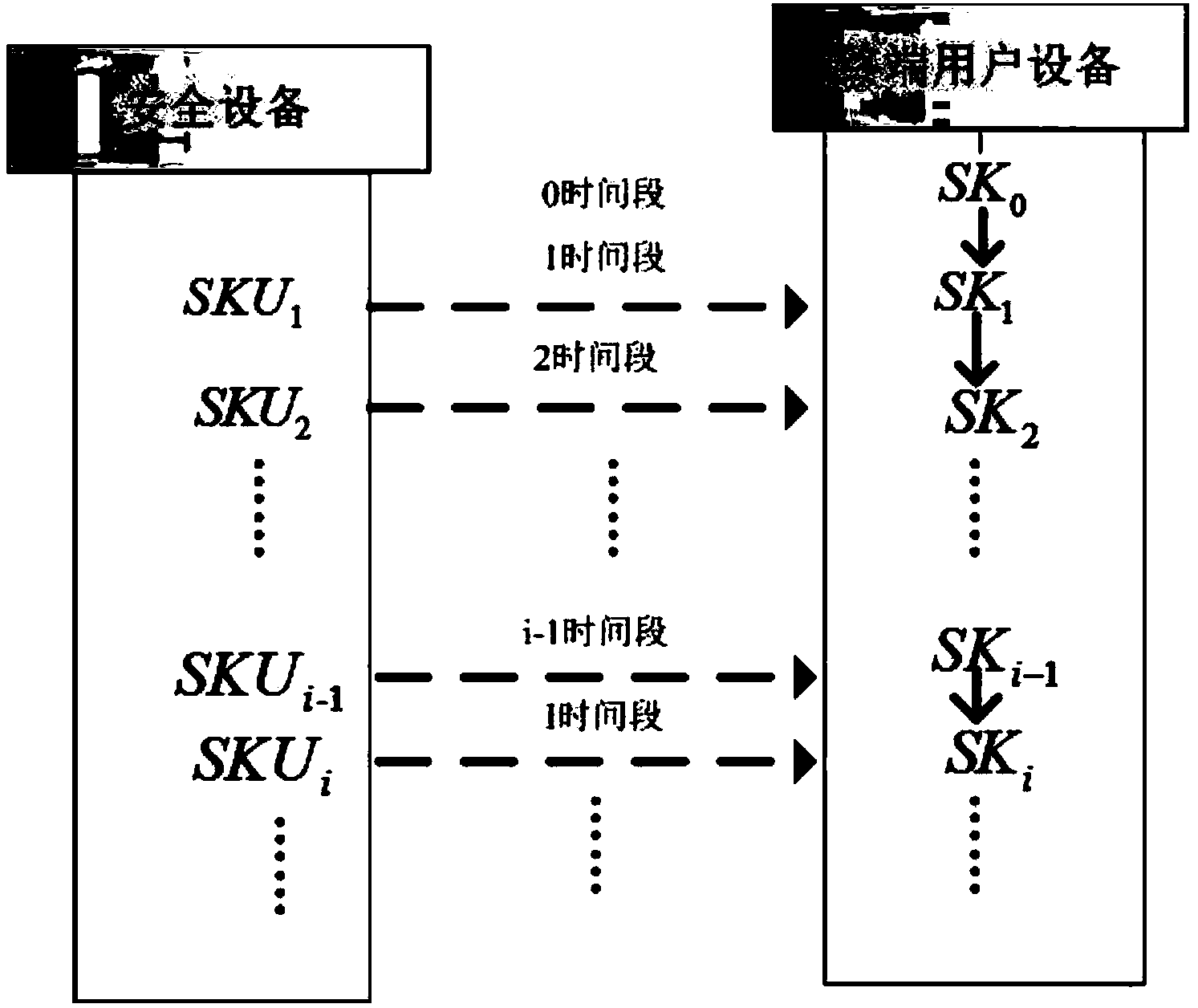
ActiveCN103986732AImprove audit efficiencyImprove efficiencyTransmissionPhysical securityTime segment
The invention provides a cloud storage data auditing method for preventing a secret key from being revealed. The method comprises the first step of system parameter generating, the second step of secret key updating and the third step of file uploading and auditing. According to the method, a physically safe safety device is introduced to help a user to periodically update the secret key, and therefore data auditing in other time periods is still safe even when an attacker attacks the user at one time period and obtains the user secret key at the time period.
Owner:SHANDONG ZHENGZHONG COMP NETWORK TECH CONSULTING
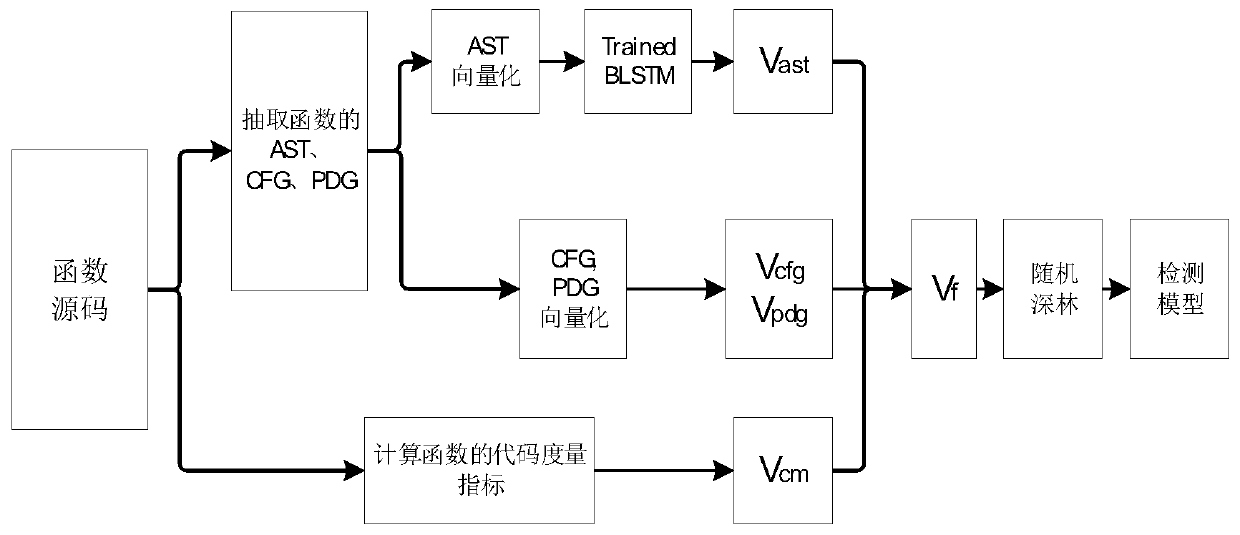
Source code vulnerability detection method based on deep learning
ActiveCN110011986AReduce audit costsImprove audit efficiencyCharacter and pattern recognitionTransmissionFeature extractionAlgorithm
The invention provides a source code vulnerability detection method based on deep learning, and the method comprises the steps: automatically completing the feature extraction of a source code based on deep learning, and constructing a vulnerability detection model by using a random deep forest algorithm in combination with a code measurement index and an automatically extracted source code feature. The source code vulnerability detection method based on deep learning provided by the invention has higher degree of automation, reduces dependence on domain expert knowledge, greatly reduces the code auditing cost and improves the code auditing efficiency. Compared with other methods for vulnerability detection by using deep learning, , grammar and semantic information of the code are reservedto the maximum extent by combining multiple representations of the code, the code can be better depicted by the characteristics automatically extracted by the deep learning algorithm, and meanwhile,the detection effect is further improved by combining common code measurement indexes as detection characteristics.
Owner:SUN YAT SEN UNIV
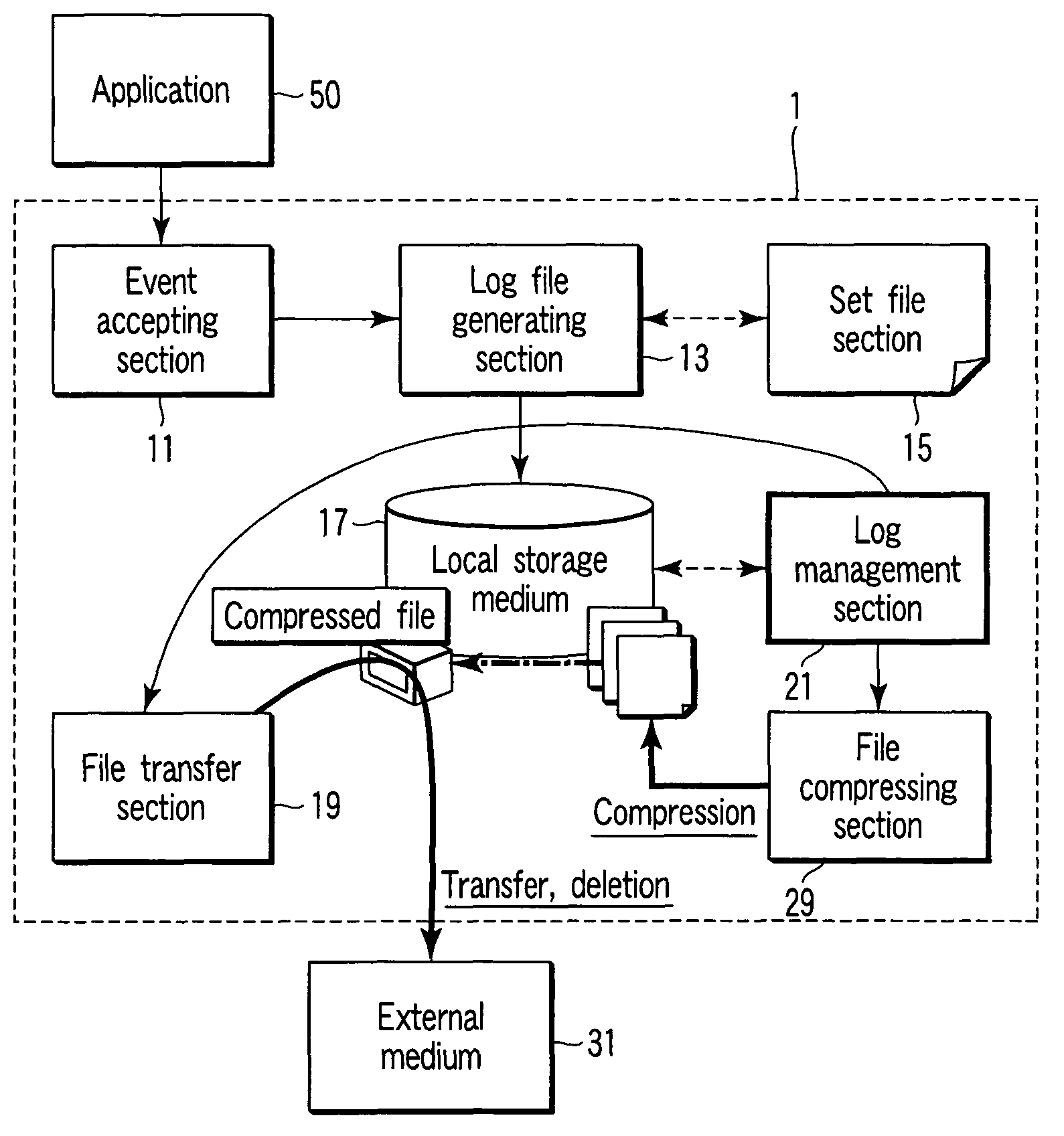
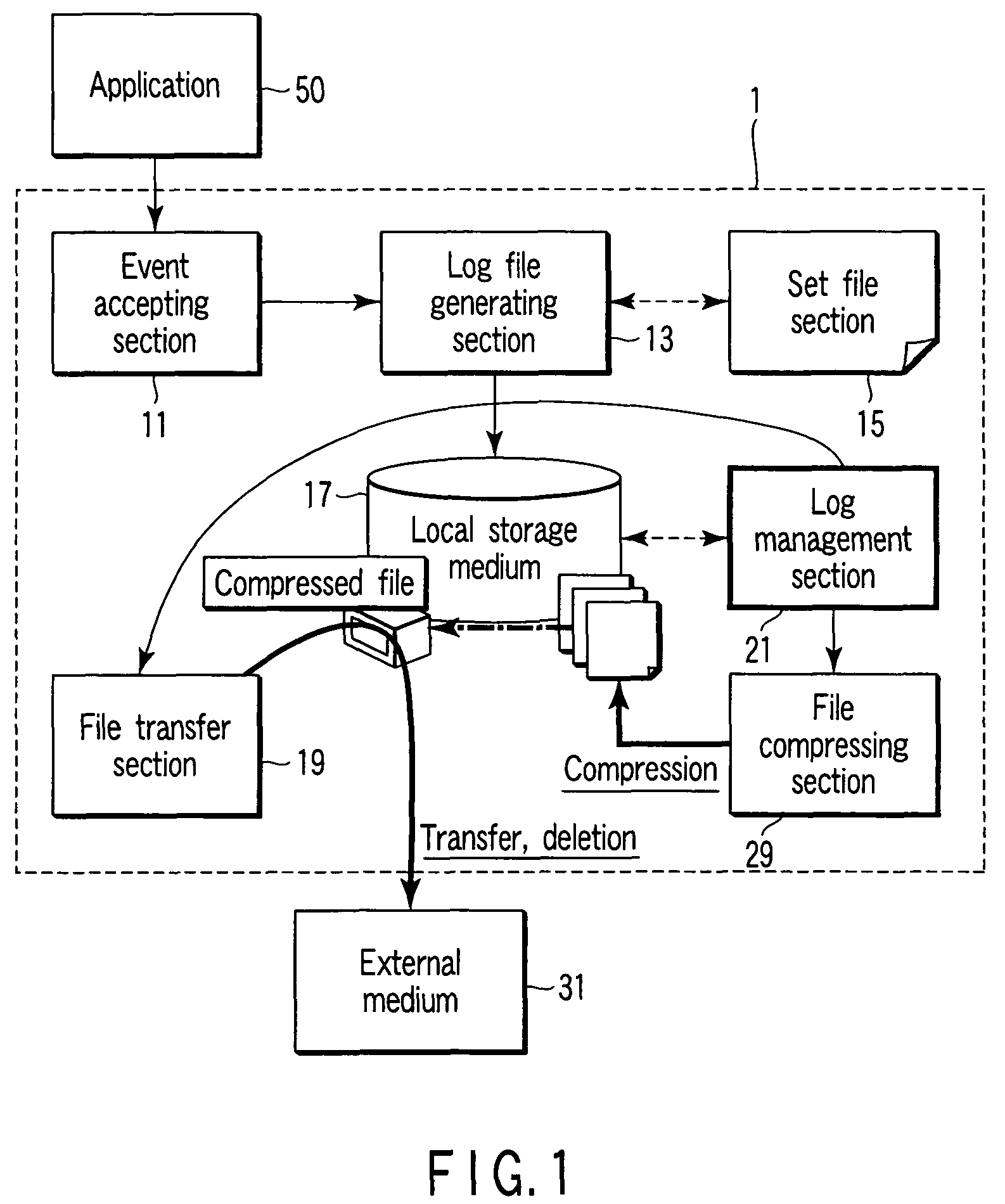
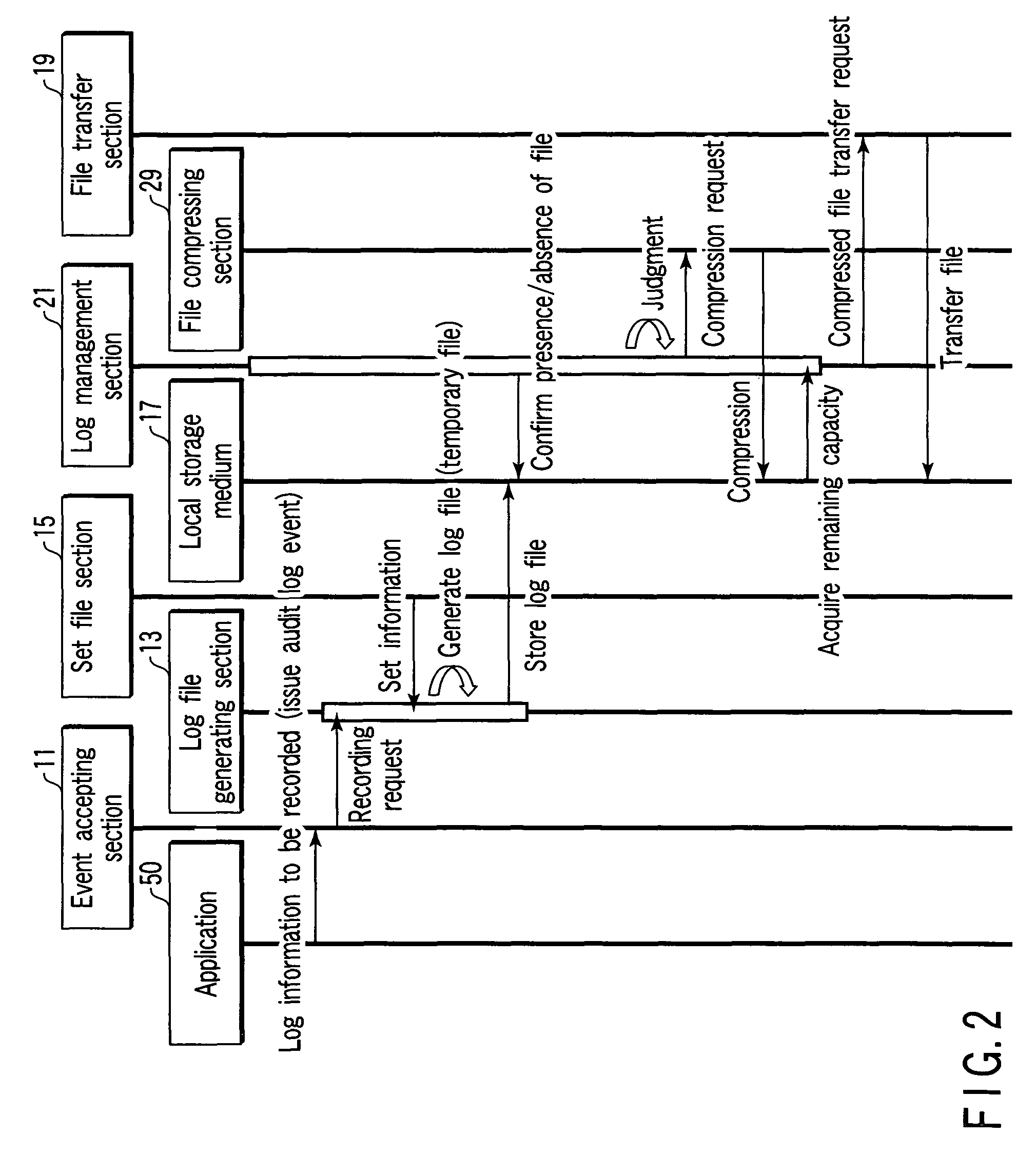
Medical equipment having audit log managing function
ActiveUS7827148B2Reduce testingReduce capacityElectrotherapyLocal control/monitoringExternal storageLog management
Owner:TOSHIBA MEDICAL SYST CORP
Method and device for processing HTTP (hyper text transport protocol) access request and gateway equipment
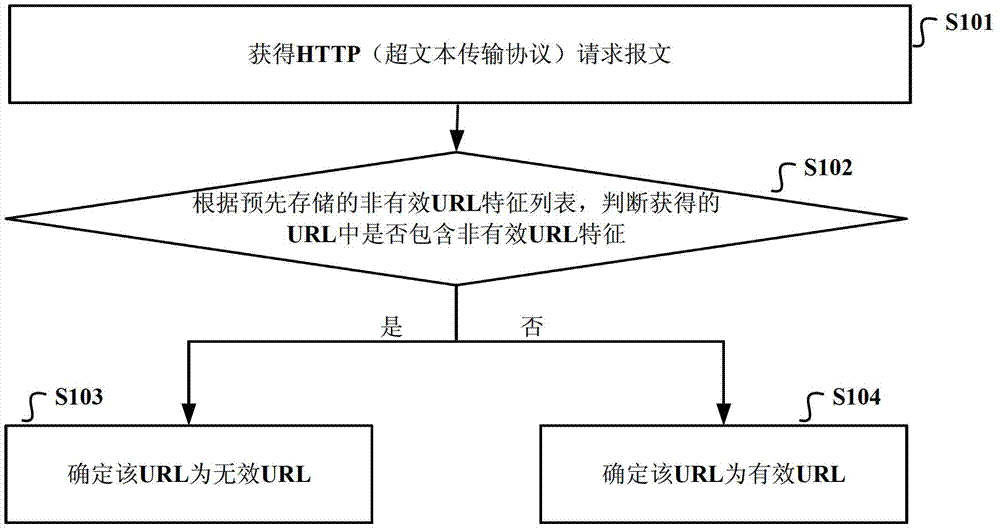
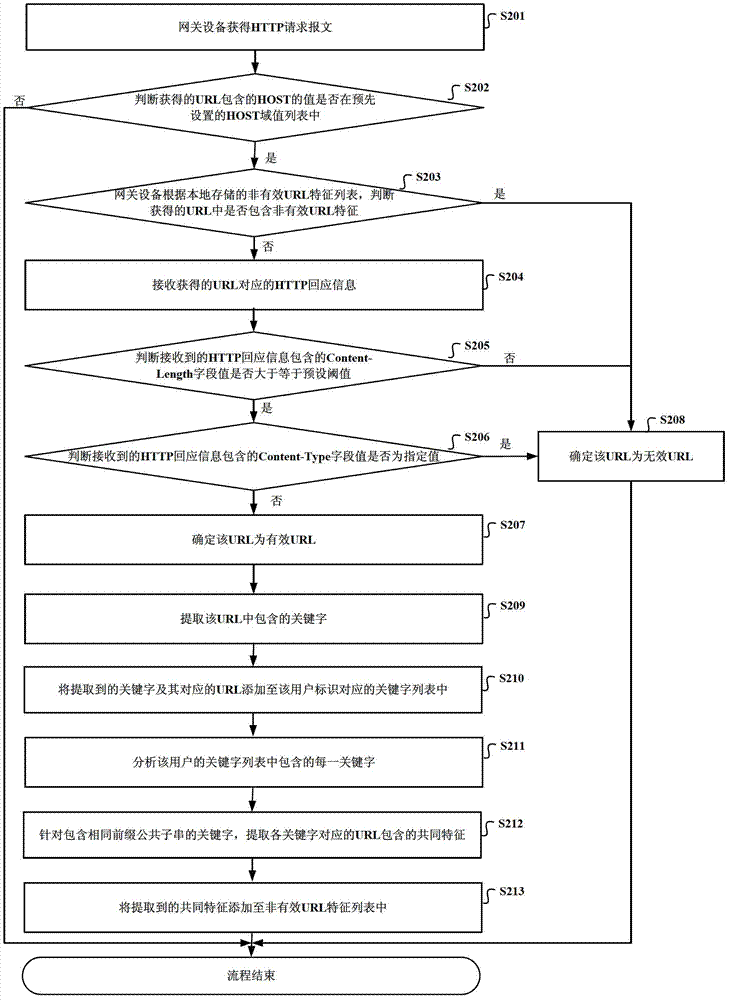
InactiveCN102857572AImprove audit efficiencySave processing resourcesTransmissionUniform resource locatorHyper text transport protocol
The invention discloses a method and a device for processing HTTP (hyper text transport protocol) access request and gateway equipment. The method and the device for processing HTTP access request and the gateway equipment are used for judging effectiveness of a URL(universal resource locator), improving search and audit efficiency of a search engine, and saving equipment processing resources. The method for processing HTTP access request includes acquiring HTTP request message which carries the URL; judging whether the URL contains non-effective URL characteristic or not according to a non-effective URL characteristic list stored in advance; determining that the URL is non-effective if so; and determining the URL is effective if not.
Owner:BEIJING XINWANG RUIJIE NETWORK TECH CO LTD
Digital auditing system and method based on process automation technology
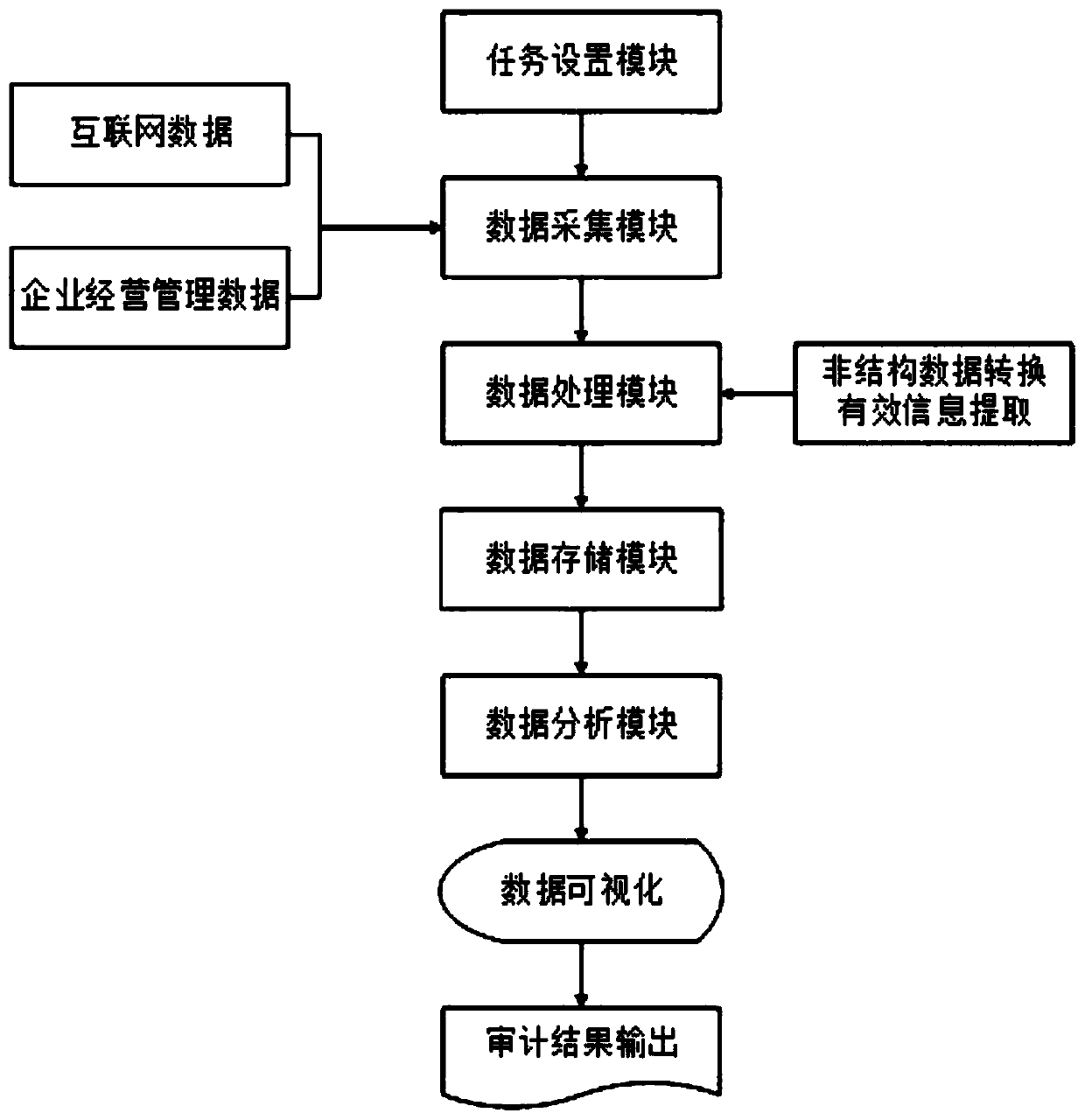
PendingCN111461668ARealize full auditAnalysis is objective and effectiveDatabase management systemsOffice automationData transformationCollection analysis
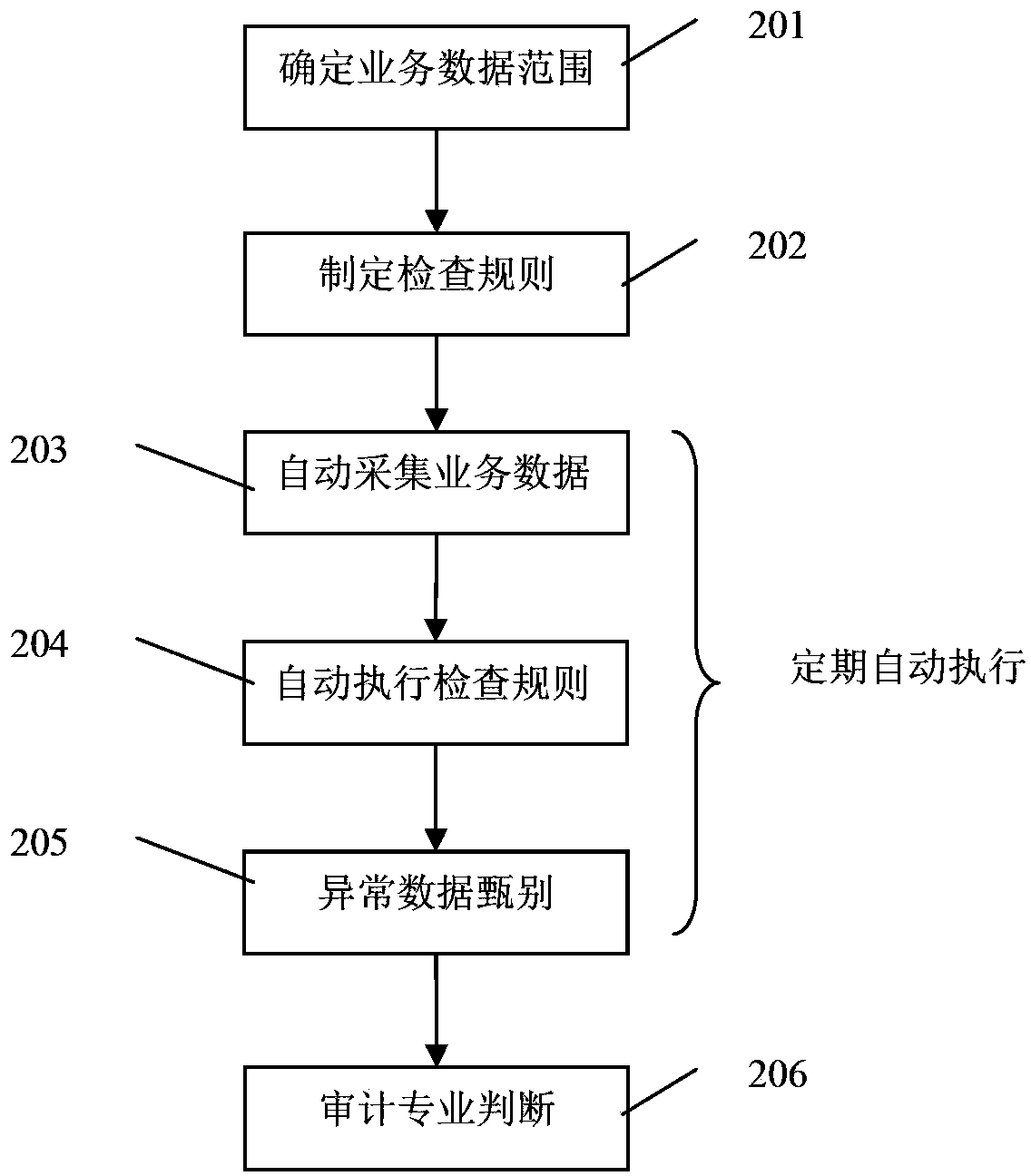
The invention relates to a digital auditing system based on a process automation technology. The digital auditing system includes a task setting module, a data acquisition module, a data processing module, a data storage module, a data analysis module and a data visualization module which are connected in sequence; a data acquisition source of the data acquisition module comprises Internet data and enterprise operation management data, the data processing module can convert unstructured data into effective information for extraction, and the system finally outputs audit results from the data visualization module. According to the invention, through the model constructed for the intelligent auditing system, the occurring business is used as an auditing and monitoring object, data is automatically collected and analyzed, doubtful data is automatically output, the electricity handling procedure, time and cost are accurately positioned, and a valuable auditing system and method are provided for company strategy adjustment and management improvement.
Owner:STATE GRID TIANJIN ELECTRIC POWER +1
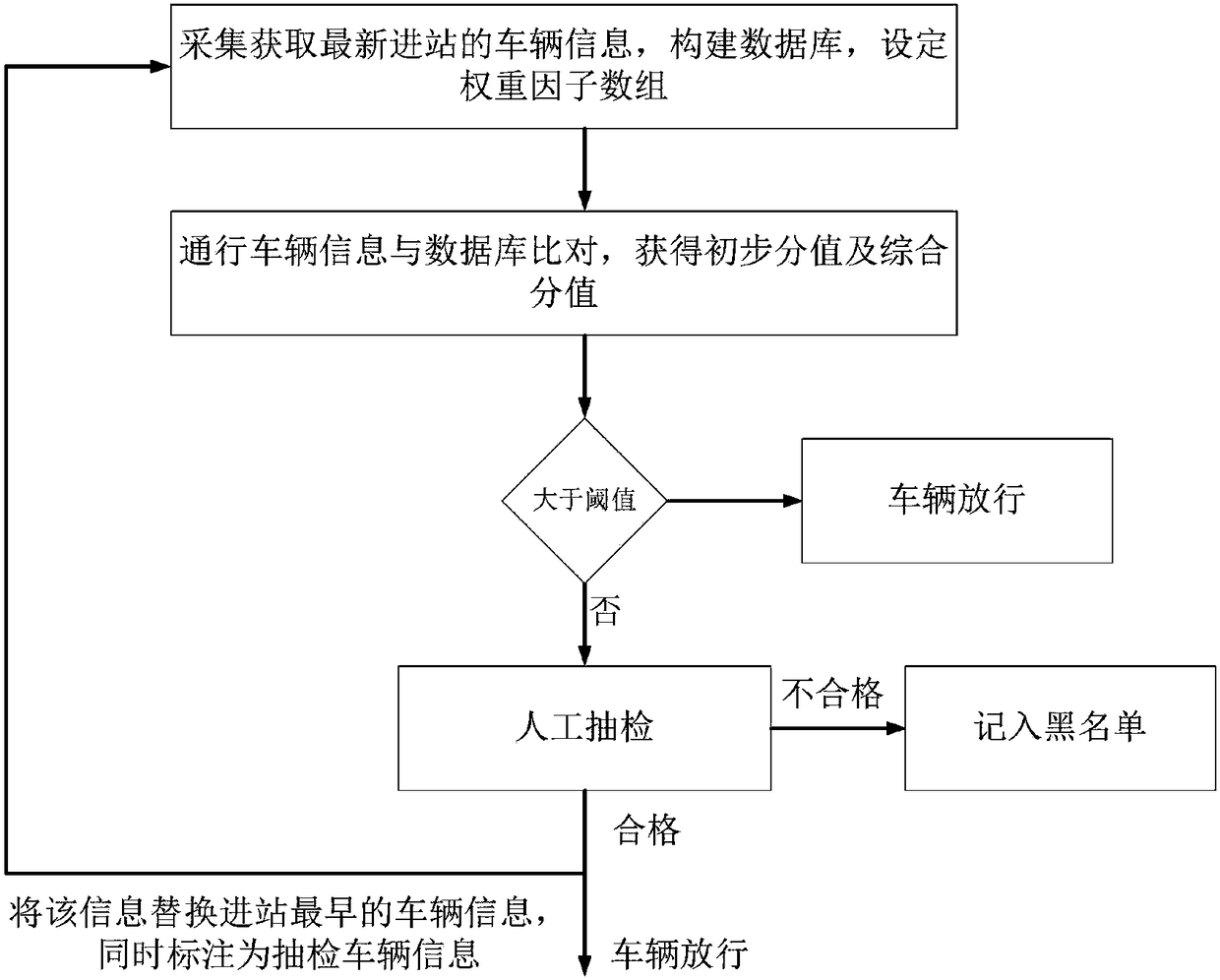
Highway vehicle inspection system and working method thereof
InactiveCN110264734ABlow down cardHigh degree of intelligenceDetection of traffic movementParticular environment based servicesEngineeringManagement efficiency
The invention belongs to the technical field of transportation, and discloses a highway vehicle inspection system and a working method thereof. The highway vehicle inspection system comprises a cloud server and a plurality of vehicle detection modules, wherein the vehicle detection modules are used for acquiring trajectory points of a vehicle, acquiring comprehensive information of the vehicle, and transmitting the trajectory points and the comprehensive information of the vehicle to the cloud server; and the cloud server is used for matching the trajectory points of the vehicle with road information of a highway to obtain a precise trajectory of the vehicle. The highway vehicle inspection system adopts a computer big data processing technology, has the advantages of high intelligence degree and precise detection, can improve the inspection efficiency and improve the passing management efficiency, and can effectively fight against the fee evasion behavior such as the vehicle card exchange, plate faking and fee evasion at a guardrail notch.
Owner:北京梦陀螺科技有限公司
Comprehensive financial auditing system based on big data
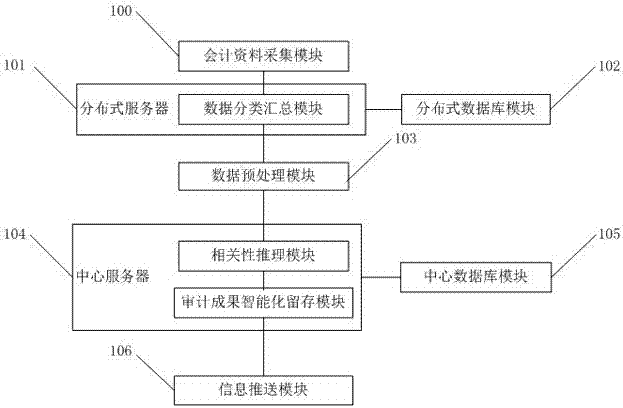
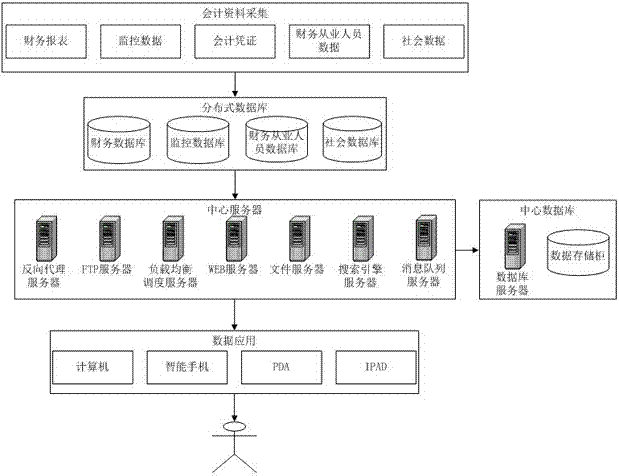
InactiveCN107492030AReduce workloadAccurate audit resultsFinanceData miningData profilingCentral database
The invention discloses a comprehensive financial auditing system based on big data. The system comprises an accounting data collection module, a distributed server, a distributed database module, a data preprocessing module, a central server, a central database module and an information pushing module, wherein the accounting data collection module collects various accounting data and auditing materials of all departments in all regions, the accounting data and the auditing materials are stored in the distributed database module of all the departments in all the regions after being calculated and processed through the distributed server, the accounting data and the auditing materials at all the departments in all the regions are summarized to the central server for processing and calculation after being processed through the data preprocessing module, and various calculation results are saved in the central database module. According to the comprehensive financial auditing system based on big data, relevant data of auditing systems, financial employee systems, report systems, monitoring systems and social systems in financial management is mined through big data analysis and correlation inference, the law and mechanism of financial inference are analyzed, and more accurate and convenient support is provided for auditing.
Owner:CHINA THREE GORGES UNIV
Desktop screen auditing method based on user behaviors
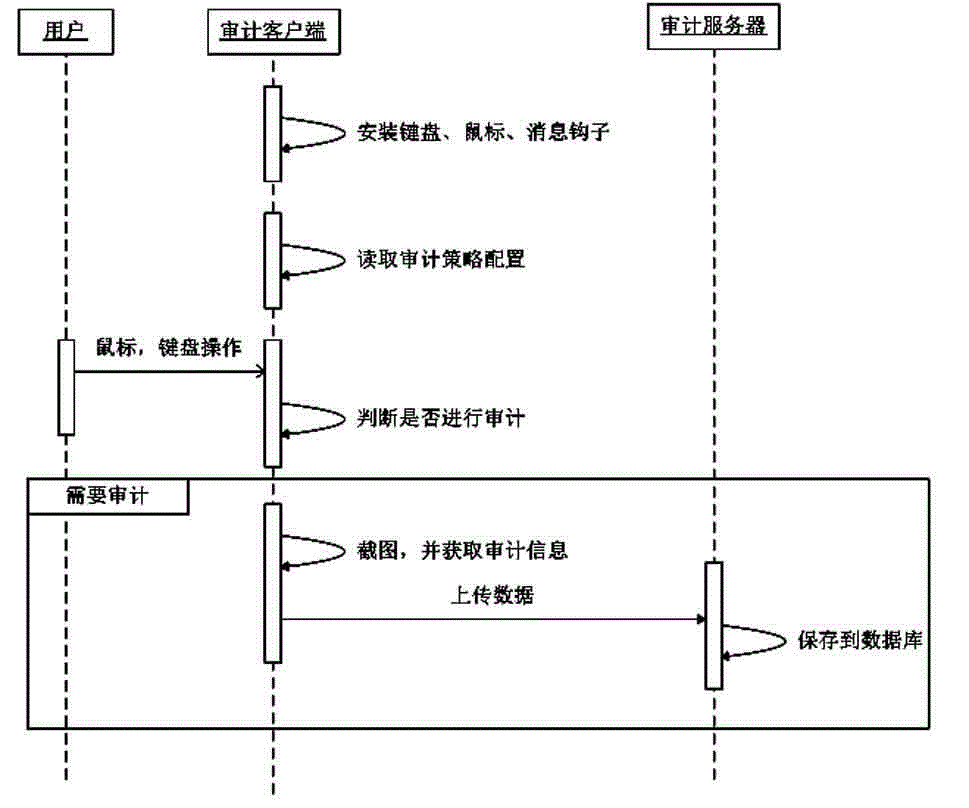
InactiveCN104700231ASave storage and network bandwidth resourcesImprove audit efficiencyHardware monitoringResourcesClient-sideImage compression
The invention relates to the technical field of screens and in particular relates to a desktop screen auditing method based on user behaviors. The desktop screen auditing method based on the user behaviors comprises the steps of 1, installing a hook for capturing the operating behaviors of a user after an auditing client is started up, and reporting data to an auditing server, 2, enabling the auditing client to read the configuration, 3, when the user works normally, triggering screen capturing after the hook captures the effective operation of the user, and performing image compression, next, recording whether mouse clicking or keyboard inputting is performed at present by a screenshot module, and meanwhile, recording the information, 4, uploading the image and the recorded information in the step 3 by the auditing client, and 5, activating an auditing server to receive the data uploaded by the auditing client and save the image and the image information into a database, and ending the steps. The desktop screen auditing method based on the user behaviors is capable of realizing screen capturing on demand, effectively classifying the screenshot data and improving the retrieval efficiency of an administrator.
Owner:FUZHOU UNIVERSITY
Data auditing method and device, computer device and storage medium
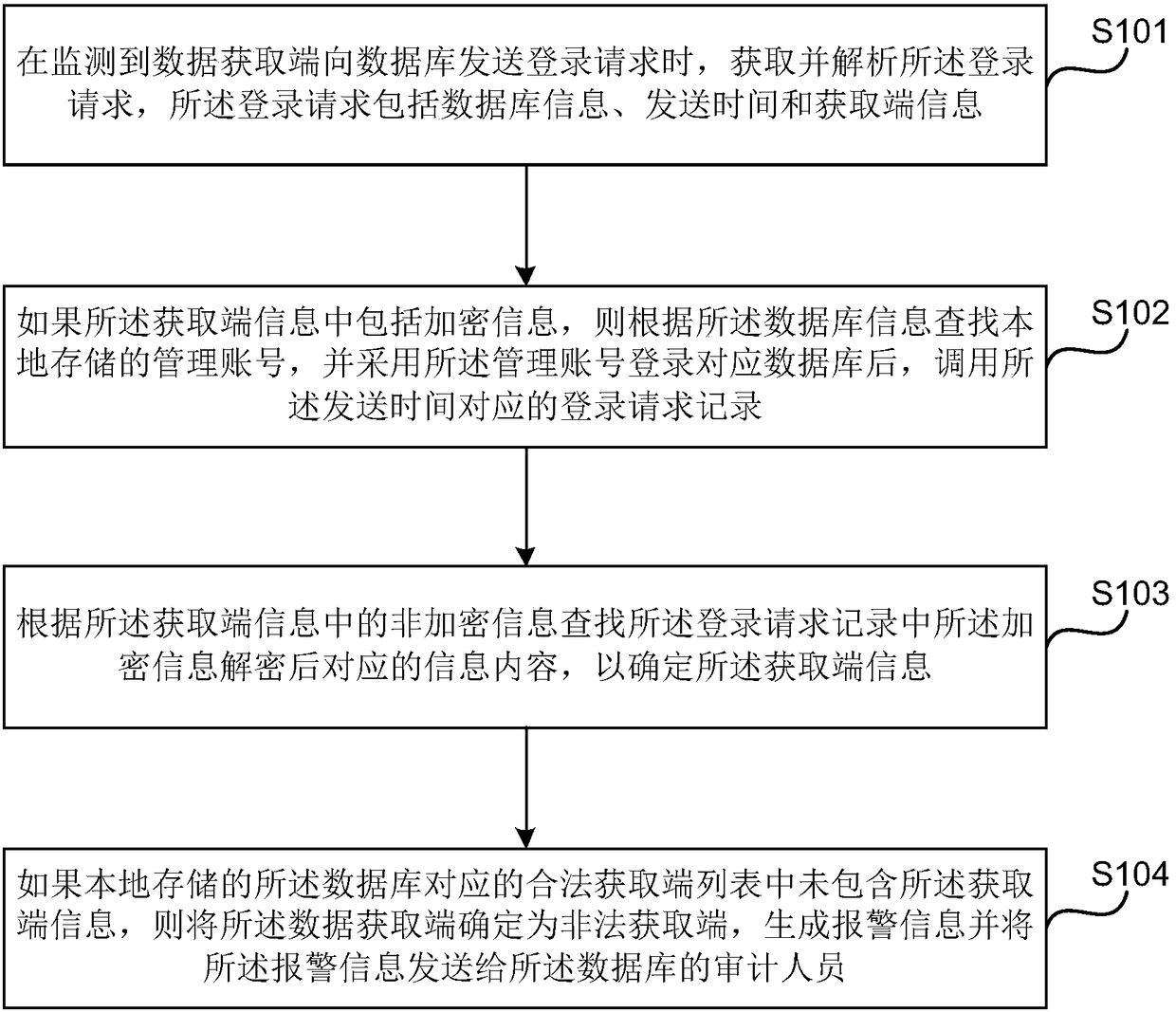
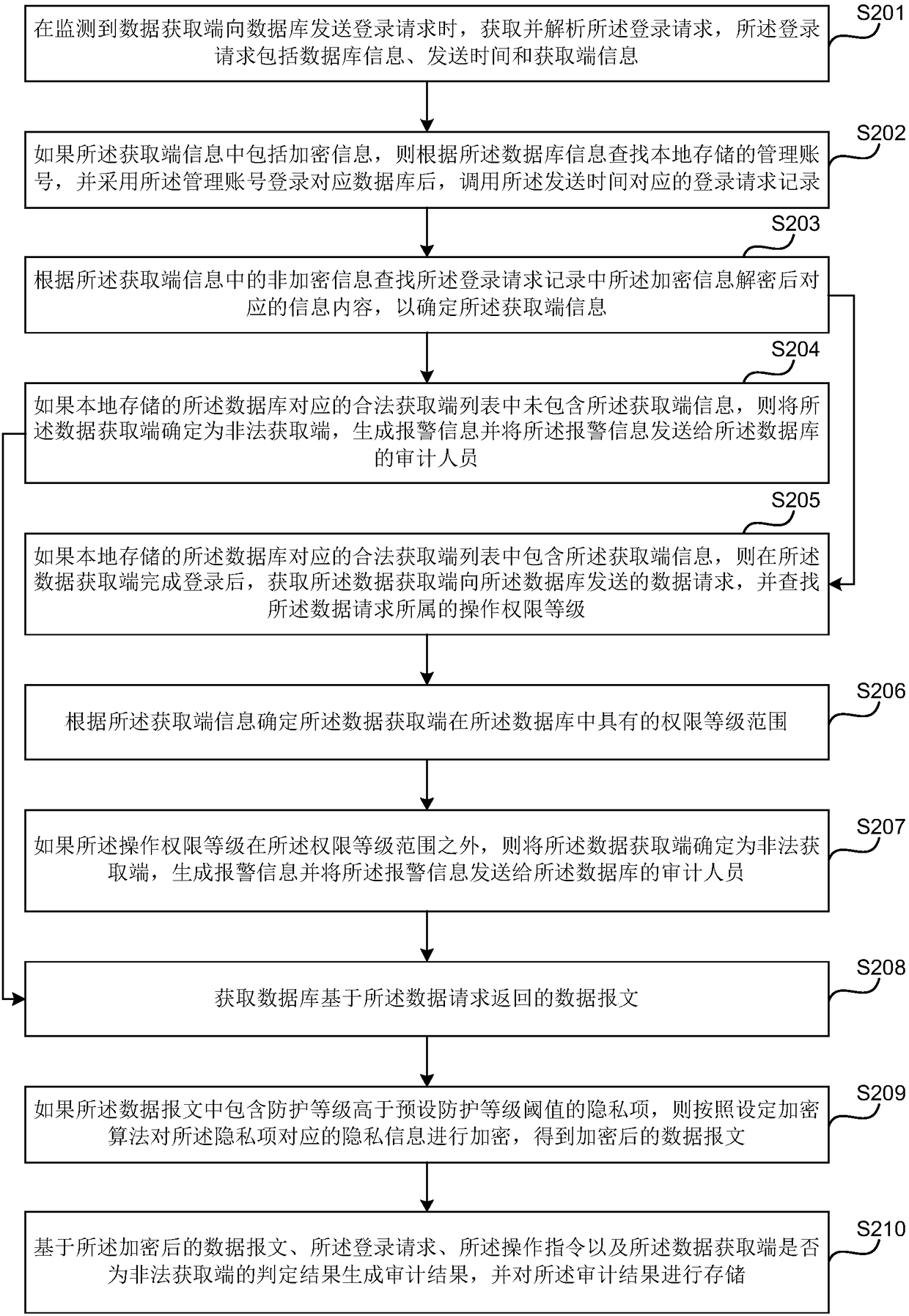
InactiveCN108416225AImprove audit efficiencyPrecise positioningDigital data protectionSide informationData acquisition
The invention discloses a data auditing method and device, a computer device and a storage medium. The method includes the steps of obtaining and parsing a login request sent by a data acquisition side to a database, wherein the login request includes database information, sending time and acquisition side information; if the acquisition side information includes encrypted information, searching for locally stored management accounts according to the database information, and after the management accounts are used for logging into the corresponding database, calling login request records corresponding to the sending time; according to non-encrypted information in the acquisition side information, searching for information content corresponding to the encrypted information in the login request records after decryption to determine the acquisition side information; if the acquisition side information is not included in a legal acquisition side list corresponding to the locally stored database, determining the data acquisition side as an illegal acquisition side, generating alarm information and sending the alarm information to an auditor of the database. According to the embodiment,by adopting the technical scheme above, accurate locating of the data acquisition side can be achieved.
Owner:深圳小蝉文化传媒股份有限公司
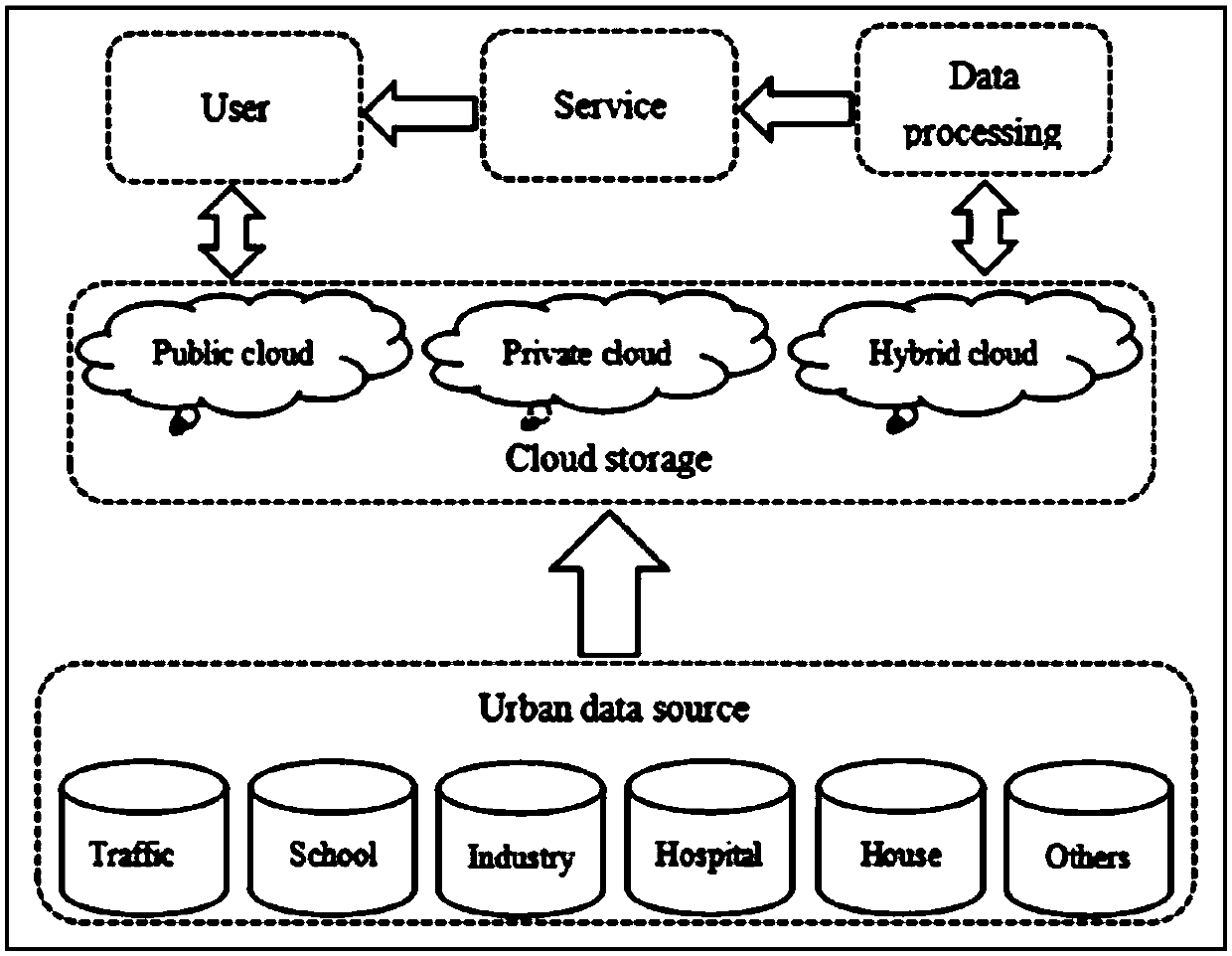
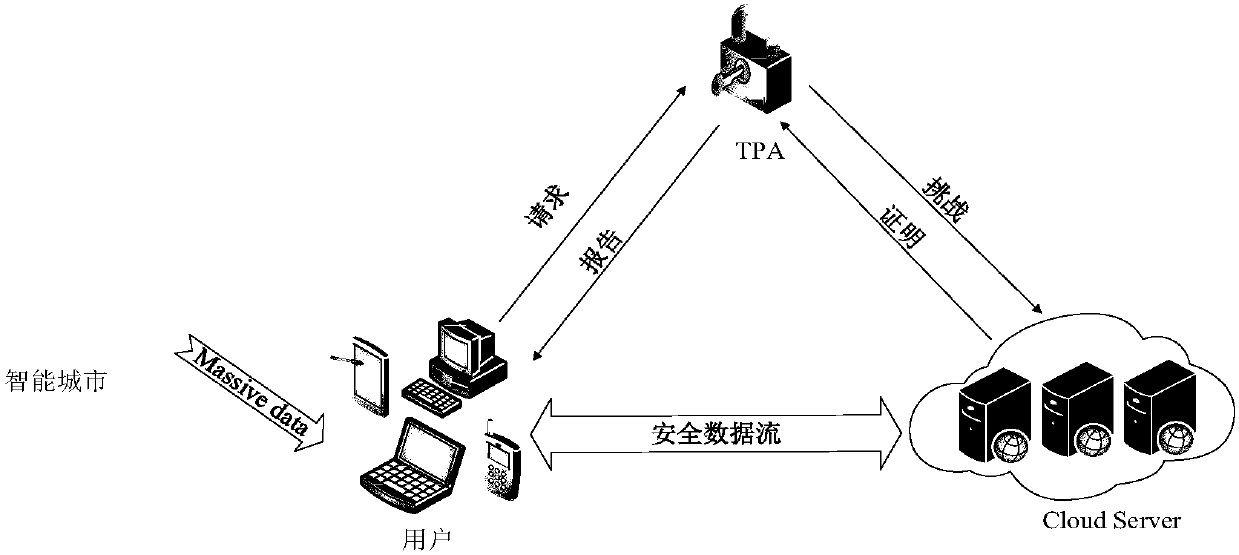
Lightweight and privacy protected public cloud auditing system and method for smart city
ActiveCN108400981ALighten the computational burdenIncrease network loadDigital data protectionOffice automationMetadataAuthentication
The invention discloses a lightweight and privacy protected public cloud auditing system and method for a smart city. The system includes a smart city, a user, a cloud server (CS) and a third party auditor (TPA). According to the scheme of the invention, the third party auditor (TPA) replaces the user to verify the integrity of outsourced data, and the user does not need to restore a data copy, and the network burden between the user and a cloud storage platform (CSP) is not increased. In consideration of most resource-constrained mobile terminal users and sensor nodes in the smart city, the third party auditor (TPA) in the invention replaces the user to generate a data authentication metadata set, which reduces the computation burden of the user. Secondly, according to the scheme of the invention, the most time-consuming pair operation in the current cryptography can be avoided on the whole, and the cloud storage platform (CSP) no longer needs to blind evidences, the computation overhead of the third party auditor (TPA) and the cloud storage platform (CSP) can be greatly reduced, and the computation burden of the entire cloud storage system can be reduced. The data storage side CSP and the auditing third party TPA are always unable to obtain any information about the data, and thus the privacy of the outsourced storage data can be protected.
Owner:江苏谷德运维信息技术有限公司
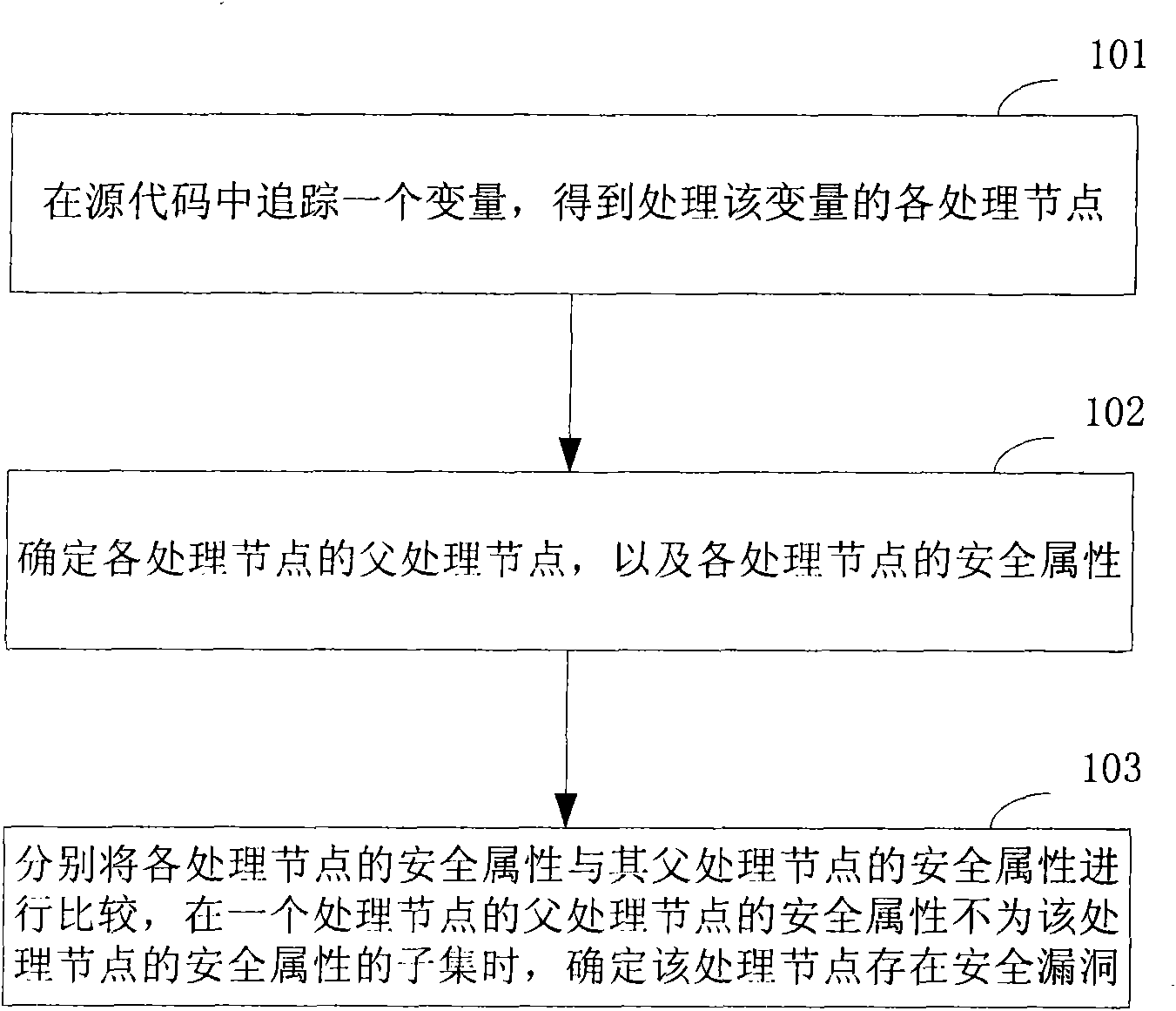
Code audit method and device
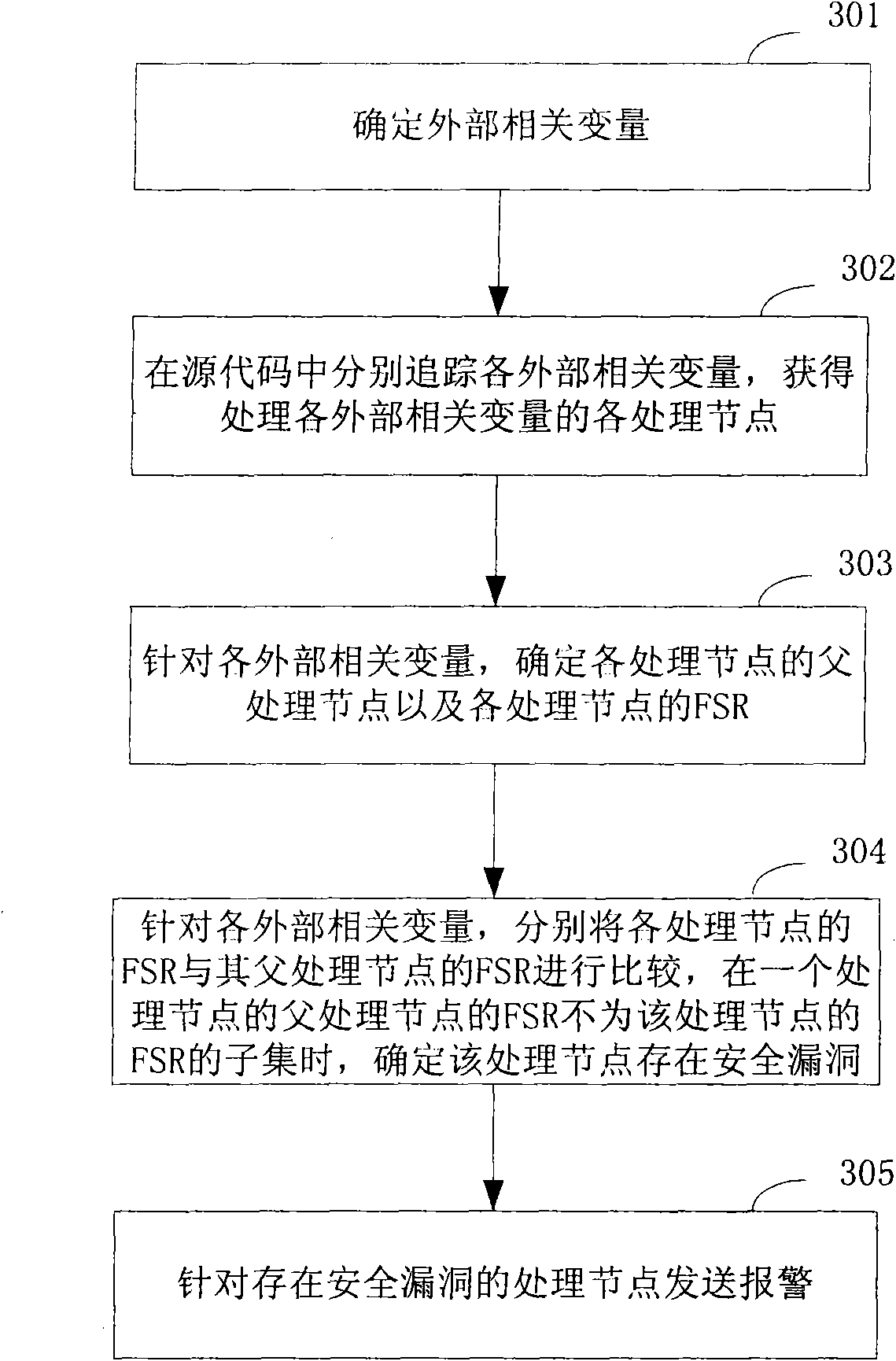
ActiveCN101551836AImprove accuracyImprove audit efficiencyError detection/correctionPlatform integrity maintainanceComputer networkSecurity properties
The invention discloses a code audit method comprising the steps: tracking a variable in source codes to obtain all processing nodes of the variable; determining the parent processing node and the security attribute of each processing node; respectively comparing the security attribute of each processing node with the safety attribute of the parent processing node of each processing node and determining a processing node existing security vulnerability if the security attribute of the parent processing node of the processing node is not the subset of the safety attribute of the processing node. In addition, the invention further discloses a code audit device. In the invention, with the technical scheme that the processing logic of the variable is determined if the variable has vulnerability according to the processing nodes, the accuracy of code audit can be improved, so that the safety vulnerability existing in the source codes can be truly and accurately reflected.
Owner:SIEMENS CHINA
Auditing system and method for shared file operation in local area network
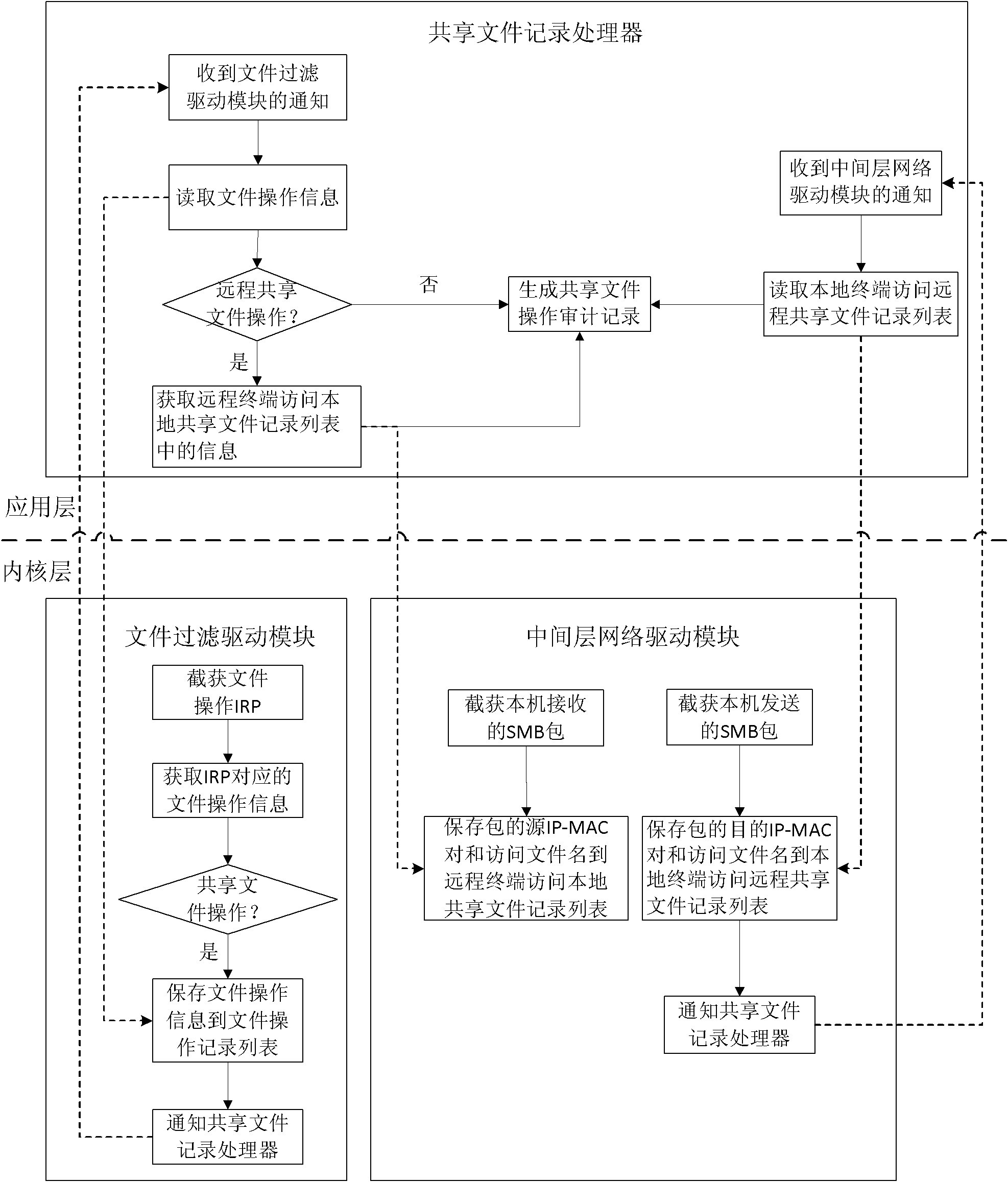
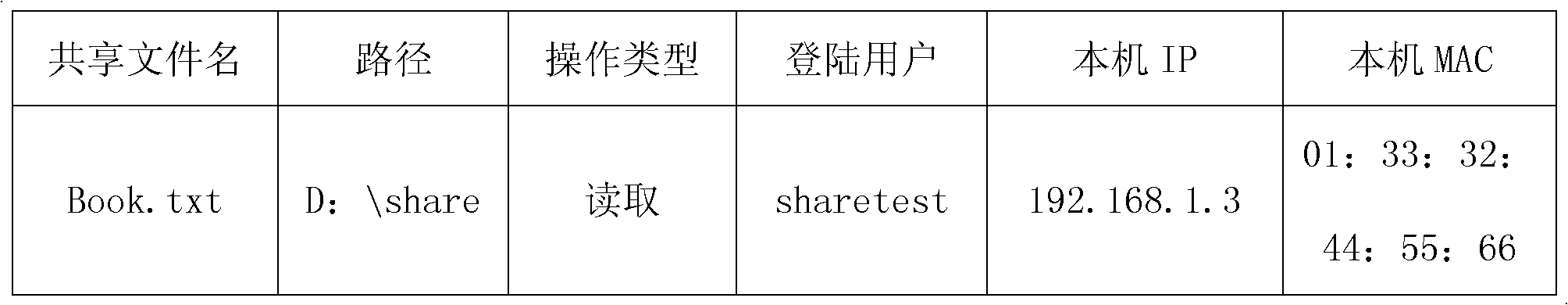
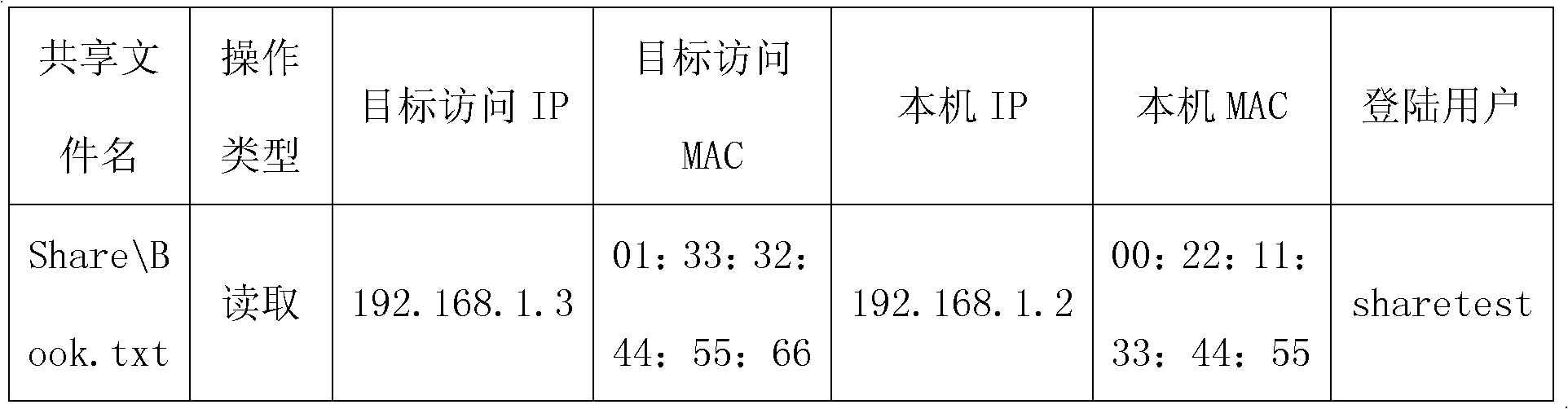
ActiveCN102467618ADoes not affect operating speedDoes not affect network speedDigital data protectionData switching by path configurationServer Message BlockComputer terminal
The invention discloses an auditing system for shared file operation in a local area network. The auditing system comprises a plurality of terminals and a record storage server. Each terminal comprises a middle layer network driver module, a file filter driver module and a shared file record processor. The invention additionally discloses an auditing method by using the system. The auditing system and the auditing method are simple, high-efficiency and easy to integrate. During auditing, the middle layer network driver module and the file filter driver module respectively intercept and capture a shared access server message block (SMB) packet and an I / O request packet (IRP) for file operation, and record the operation information of the shared file; and the shared file record processor generates detailed shared file operation auditing records according to the information and terminal login usernames and reports the records to the record storage server. Therefore, an intranet administrator can easily administrate the shared file operation.
Owner:SHANGHAI BAOSIGHT SOFTWARE CO LTD
Method for improving three-layer correlation accuracy
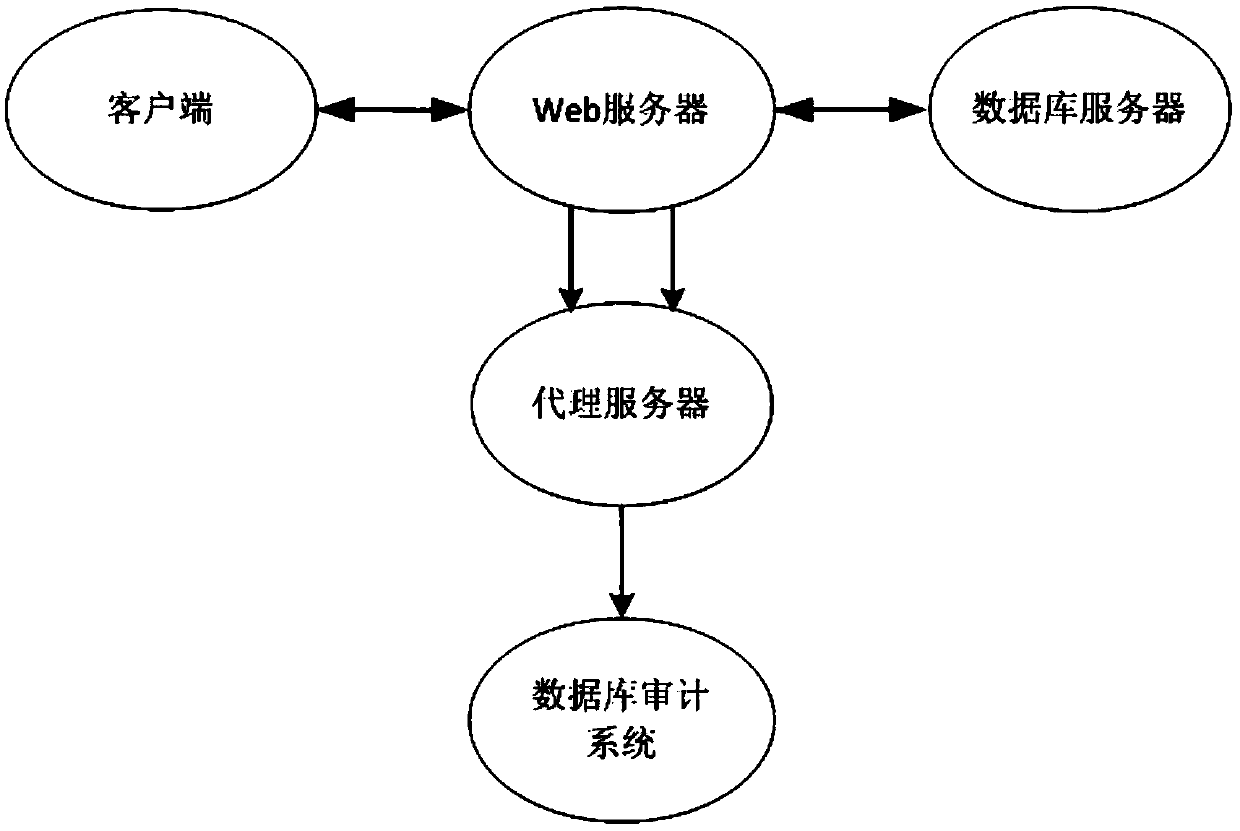
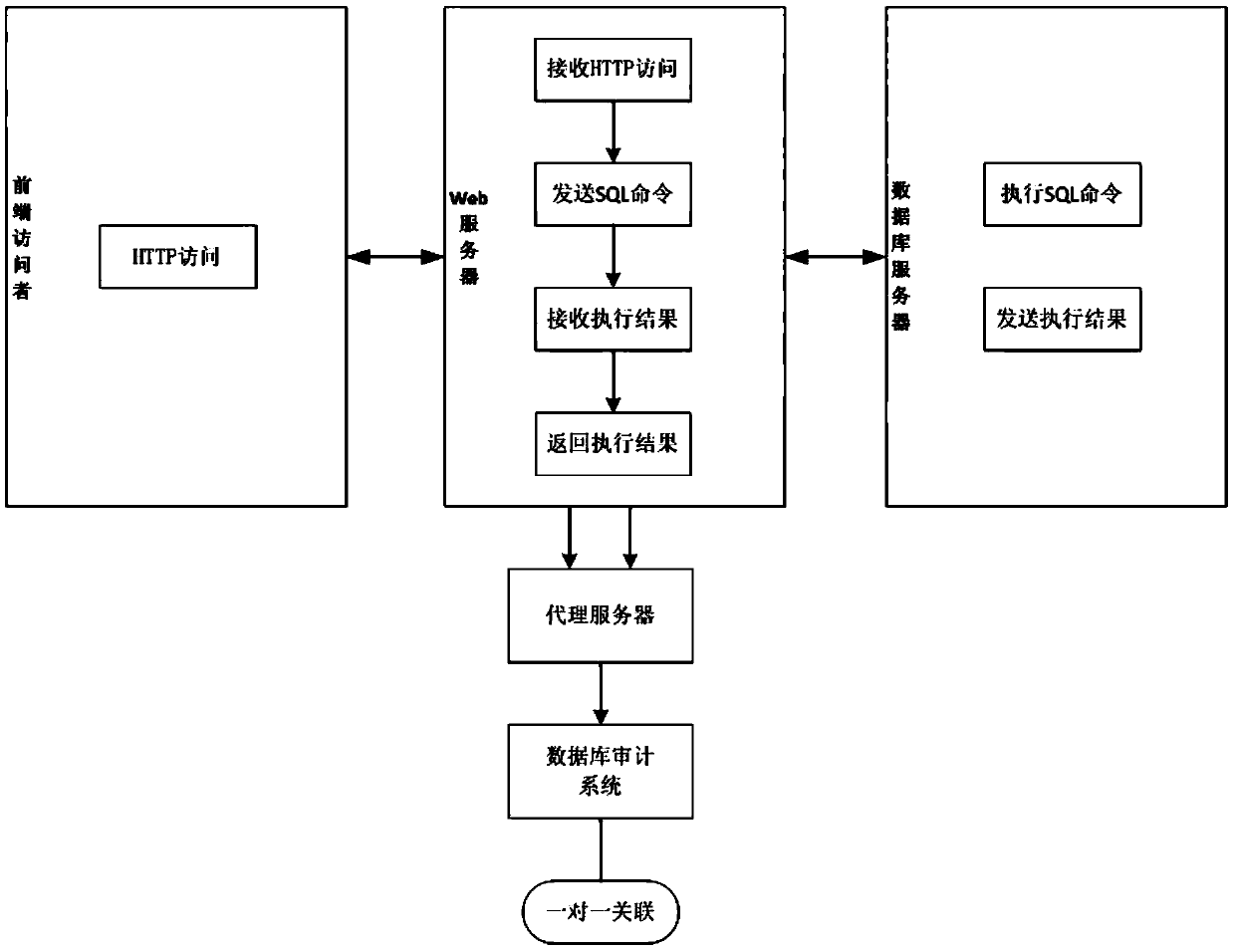
ActiveCN105373603AImprove the efficiency of one-to-one associationImprove association efficiencySpecial data processing applicationsWeb serviceProxy server
The invention relates to the technical field of database audit and safety management, and aims at providing a method for improving three-layer correlation accuracy. The method comprises the following steps: obtaining information generated during interaction between a Web server and a front-end accessor and information generated during interaction between the Web server and a background database through a proxy server, and sending the information to a database audit system; and receiving, by the database audit system, the data sent by the proxy server, and carrying out one-to-one correlation to determine the correlation of front-end HTTP access and background database access. According to the method, the efficiency of the one-to-one correlation between the background database access and the front-end accessor is greatly improved, so that the audit efficiency of the database audit system is improved; and meanwhile, the correctness of the one-to-one correlation between the background database access and the front-end accessor is greatly improved, so that the audit correctness of the database audit system is improved.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Highway green aisle vehicle information management system
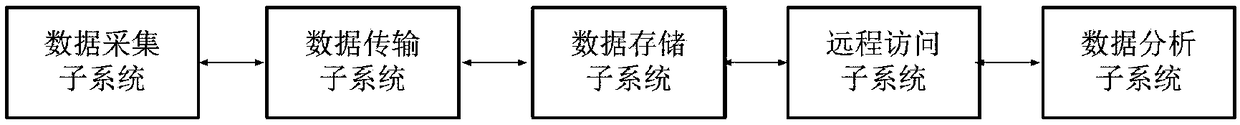
The invention discloses a highway green aisle vehicle information management system. It includes data acquisition subsystem to collect vehicle body image information, license plate image information and cargo image information, and the vehicle body image information, license plate image information and cargo image information is sent to the data storage subsystem through the data transmission subsystem; the data transmission subsystem is used for transmitting the information sent by the data acquisition subsystem to the data storage subsystem and transmitting the data sent by the data storagesubsystem to the remote access subsystem; the data storage subsystem is used for storing vehicle body image information, license plate image information, cargo image information, axle number information, lane information, release mode information, exempt amount information, operator information and conduct analysis; the remote access subsystem is used to provide an interface for the client to access data in the data storage subsystem. The invention realizes the automatic management on the whole green aisle, has high audit efficiency and simple procedure.
Owner:西安鲲博电子科技有限公司
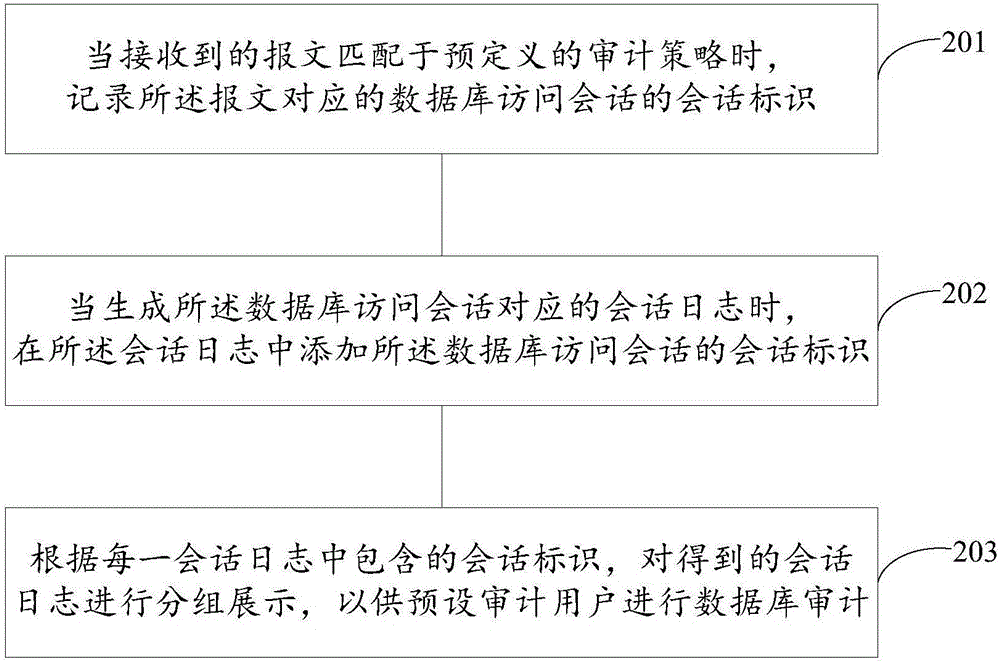
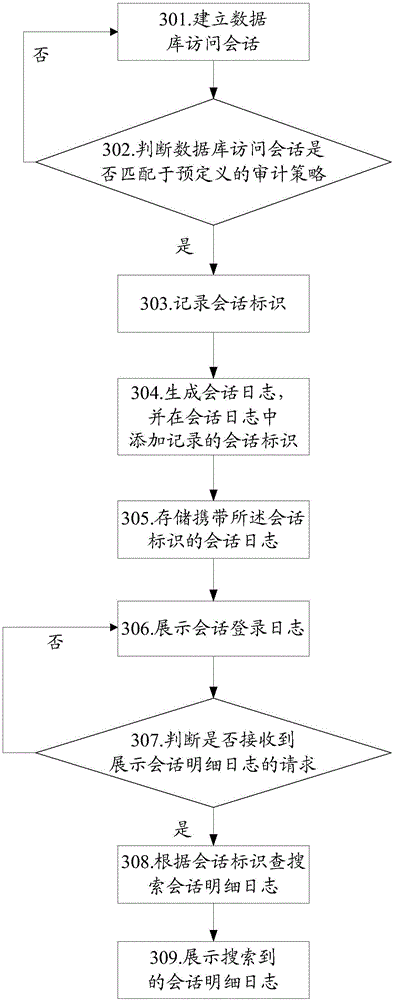
Method and device for realizing database auditing
InactiveCN106202560AImprove audit efficiencyQuick searchSpecial data processing applicationsTraffic volumeDatabase access
The application provides a method and a device for realizing database auditing. The method comprises the following steps: when a received message is matched with a predefined audit strategy, recording session identifiers of a database access session corresponding to the message; when session logs corresponding to the database access session are generated, adding the session identifiers of the database access session in the session logs; according to the session identifier included in each session log, grouping and displaying the obtained session logs. A preset audit user can conveniently and quickly search all focused session logs, especially when the access flow of a database is large, a large number of session logs can be generated, so that the auditing efficiency can be effectively improved according to the technical scheme.
Owner:HANGZHOU DPTECH TECH
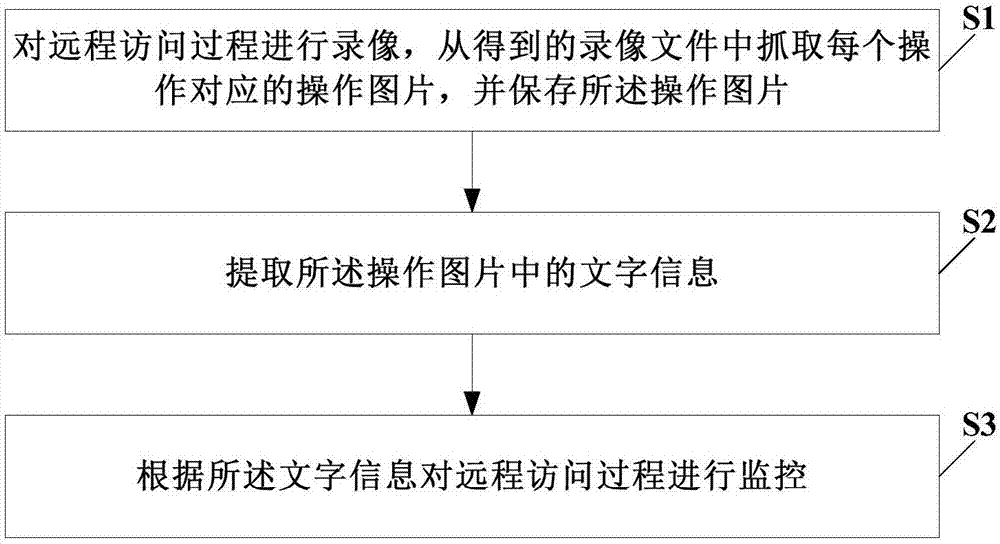
Remote access monitoring method and related device
InactiveCN107194394AReduce storage burdenEasy to find violationsCharacter and pattern recognitionTransmissionVideo recordVideo recording
The invention provides a remote access monitoring method and a related device. Through video recording on a remote access process, an operation picture corresponding to each operation is captured from the obtained video recording file, and the operation picture is saved as original monitoring data. In comparison with direct video recording file storage in the prior art, the embodiment of the invention can greatly lessen the storage burden of a related storage device. In comparison with the method of firstly searching one or more corresponding operation pictures in the video recording file based on a command line character in the prior art and then carrying out auditing and analysis according to the operation picture, the embodiment of the invention extracts text information in the operation picture and carries out auditing and analysis according to the text information, an illegal operation in massive remote operations can be found out, and the auditing efficiency is improved.
Owner:BEIJING SHENZHOU TAIYUE INFORMATION SAFETY TECH CO LTD
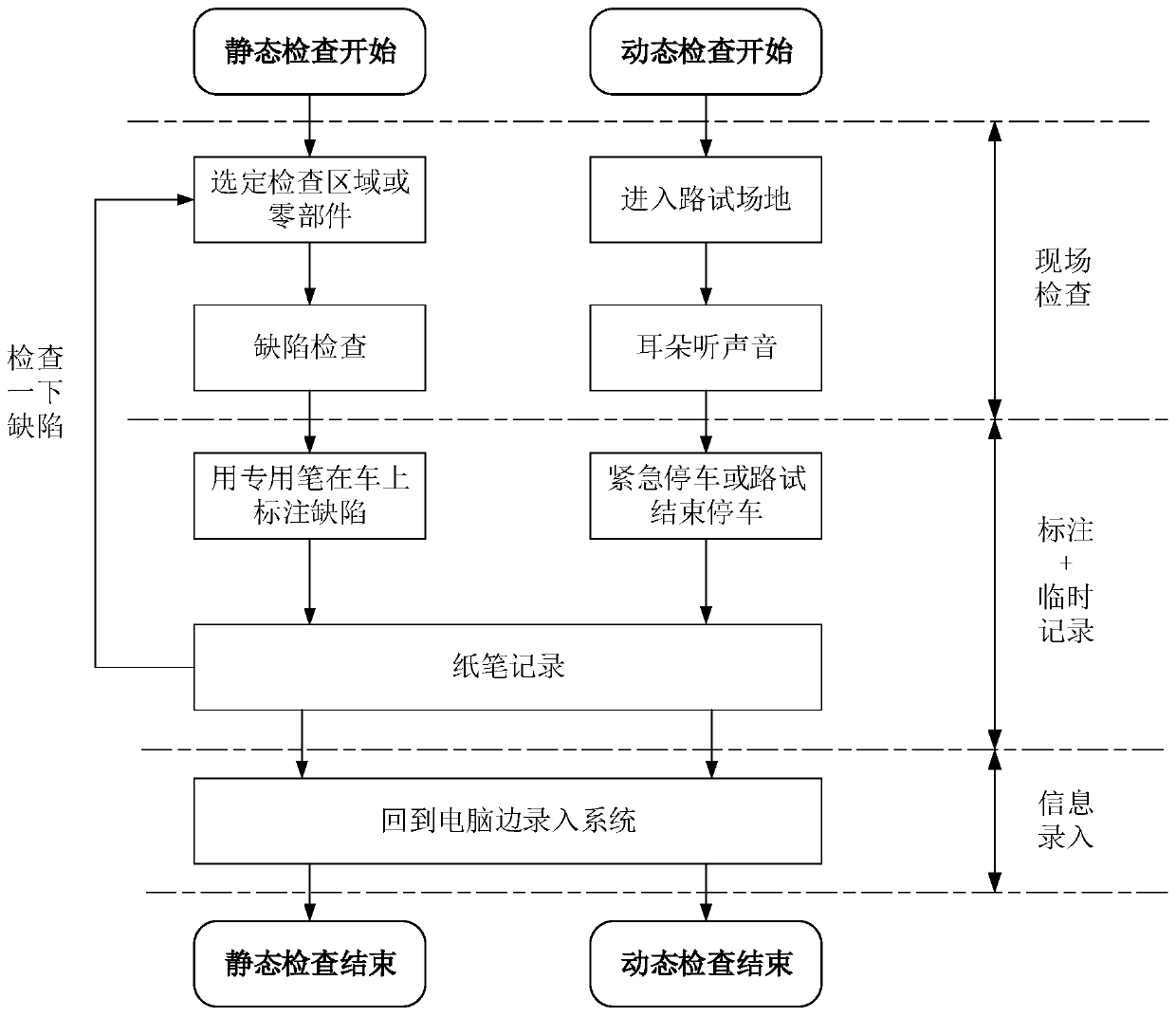
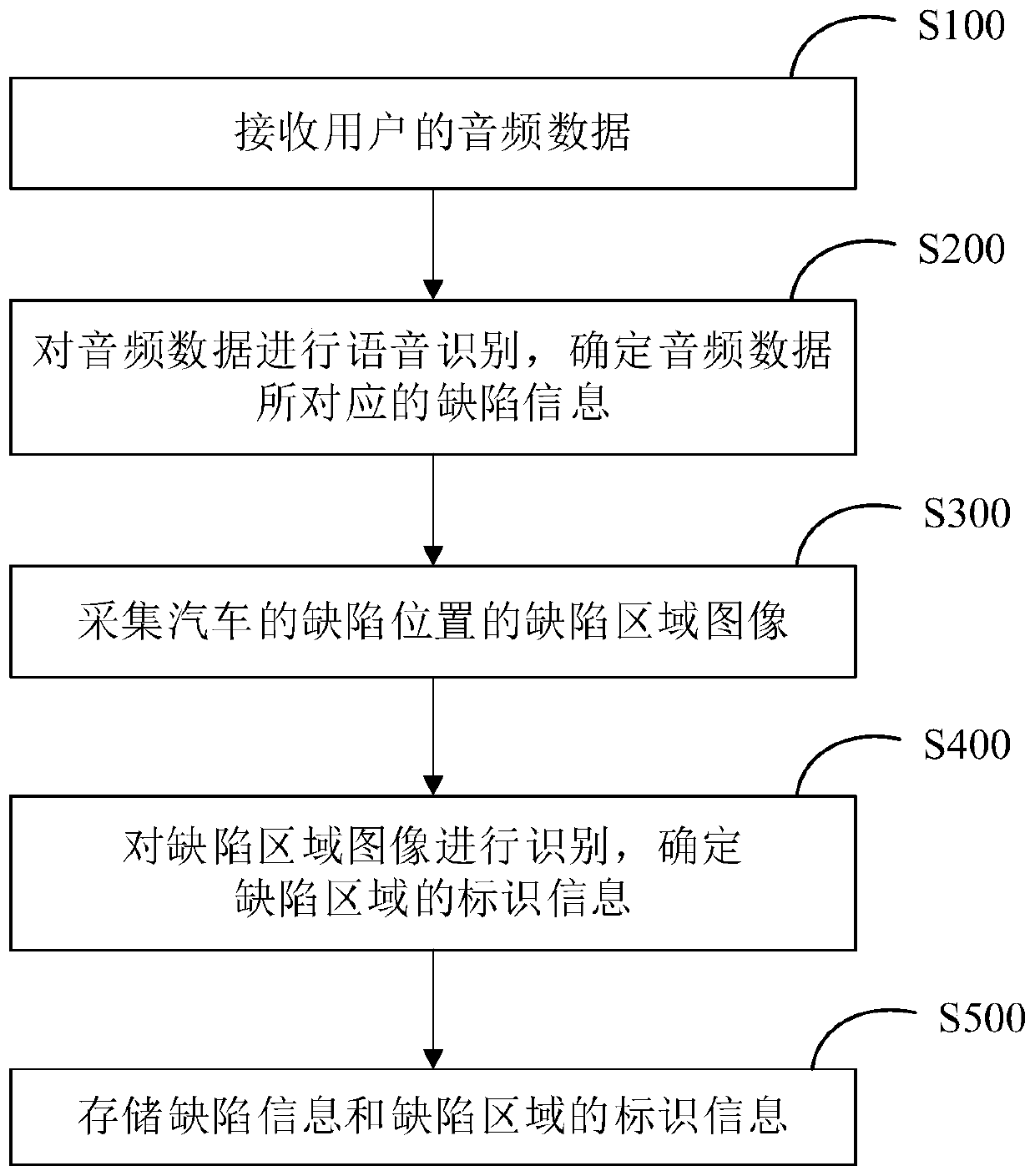
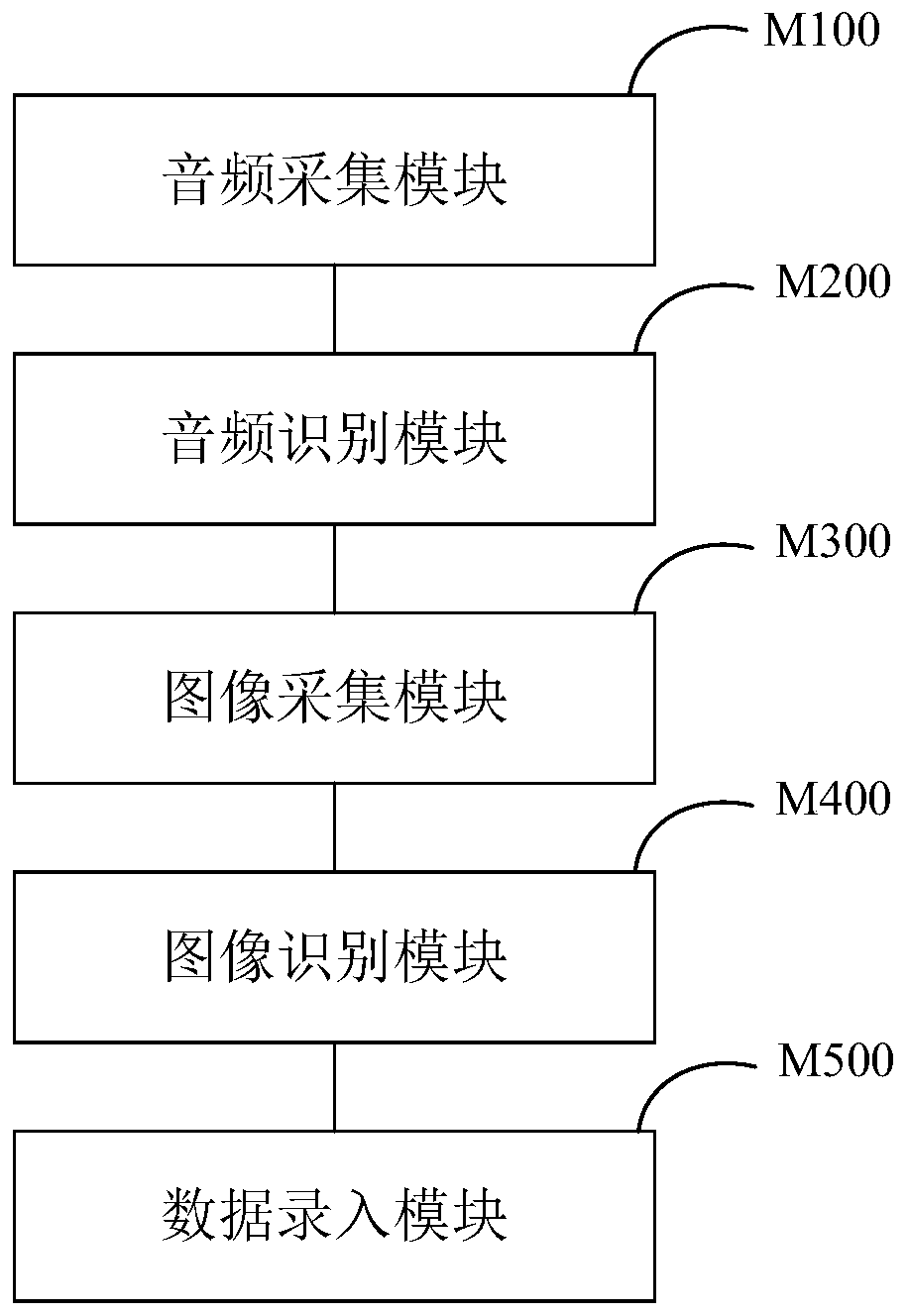
Automobile defect data automatic input method, system and device and medium
InactiveCN111127699ADo not change work habitsSimple working processRegistering/indicating working of vehiclesCharacter and pattern recognitionPattern recognitionEngineering
The invention provides an automobile defect data automatic input method, an automobile defect data automatic input system, an automobile defect data automatic input device and a medium. The automobiledefect data automatic input method comprises the steps of: receiving audio data of a user; performing voice recognition on the audio data, and determining defect information corresponding to the audio data; acquiring a defect region image of a defect position of an automobile; identifying the defect region image, and determining identification information of a defect region; and storing the defect information and the identification information of the defect region. According to the automobile auditing auxiliary scheme provided by the invention, an intelligent auxiliary function is provided for an auditing process by combining voice recognition, image recognition and other technologies, defect information and identification information of the defect region are automatically input, and theauditing efficiency and precision are improved.
Owner:AIWAYS AUTOMOBILE CO LTD
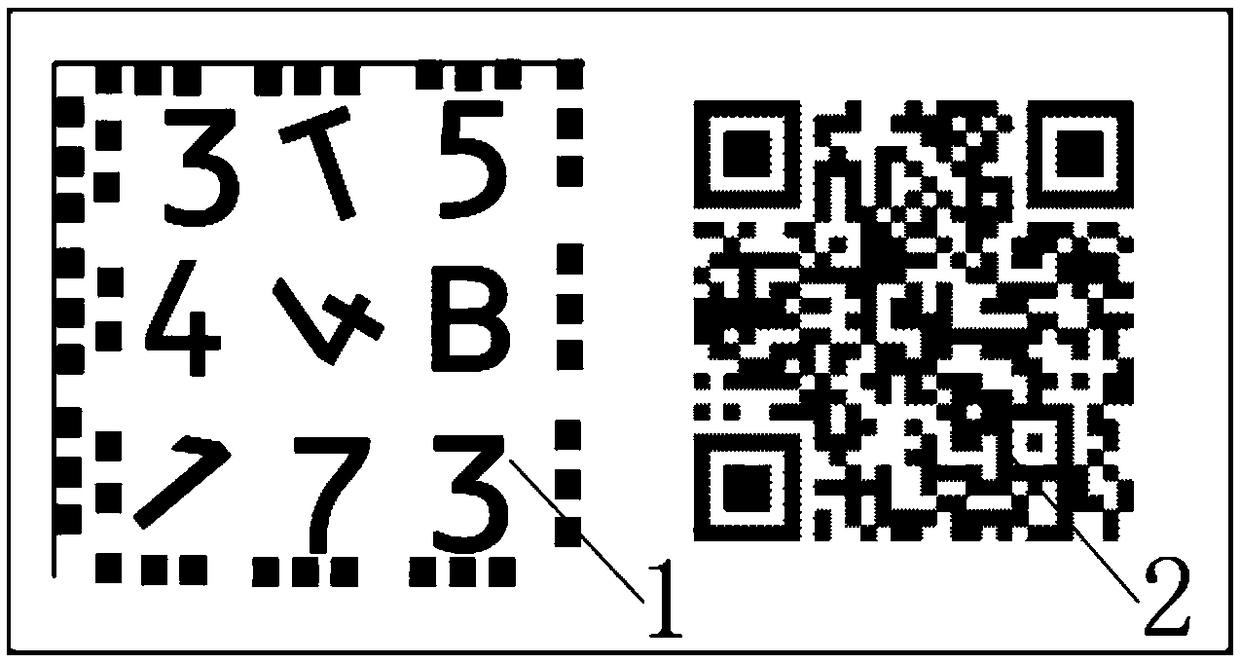
An anti-counterfeit label and an identification system based on a QR code and OCR feature identification
InactiveCN109190734AProtect from crackingConvenient queryCharacter and pattern recognitionCommerceArray data structureComputer science
The invention relates to an anti-counterfeit label and an identification system based on a QR code and OCR feature identification. The anti-counterfeit label comprises an OCR feature recognition areaand a QR two-dimensional code recognition area, the OCR feature identification area adopts a matrix array conversion array to form an OCR feature identification mark, OCR is a character that can be decoded directly by the visual system, and random OCR characters are generated by a special encoding device and distributed on the OCR feature recognition area. The QR two-dimensional code recognition area is used for verifying whether the OCR is correct or not, and the OCR two-dimensional code recognition area is uniquely corresponding to the QR two-dimensional code recognition area by encrypting asequence formed by the OCR characters to form a unique corresponding ciphertext encoding. At that same time, the QR two-dimensional code identification area contains a background network interface access, and can be used for product anti-counterfeit trace. The invention has the advantages that the problem that the anti-counterfeit label is recognized by the human eye based on the QR code and thecharacteristic picture is solved, and the authenticity of the anti-counterfeit label can be automatically recognized at the same time.
Owner:陕西丝路标准数据有限公司
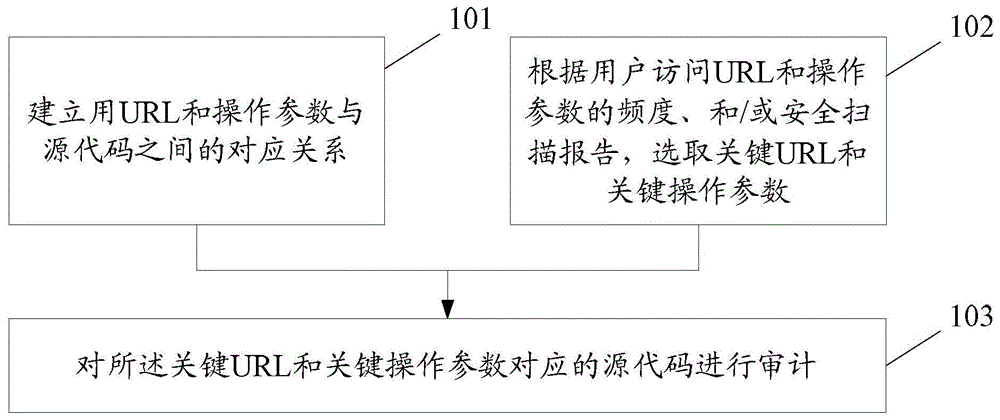
Code auditing method and apparatus
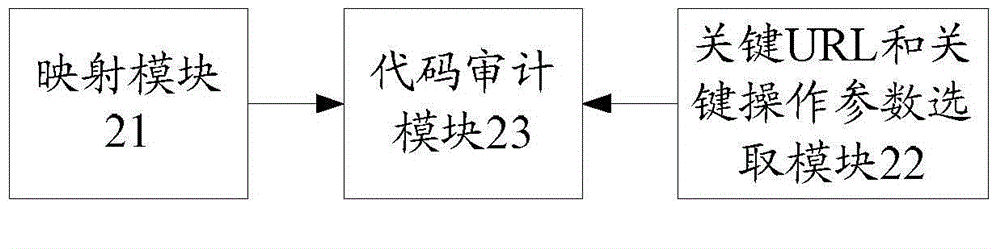
ActiveCN105740135APrecise positioningReduce false positivesSoftware testing/debuggingUniform resource locatorSource code
The present invention discloses a code auditing method. The method comprises: establishing a corresponding relation between a URL and an operating parameter and a source code; according to a frequency at which a user accesses the URL and the operating parameter, and / or a secure scanning report, selecting a key URL and a key operating parameter; and auditing the source code corresponding to the key URL and the key operating parameter.
Owner:SHANXI CHINA MOBILE COMM CORP
Electronic license plate-based intelligent vehicle inspection system and method
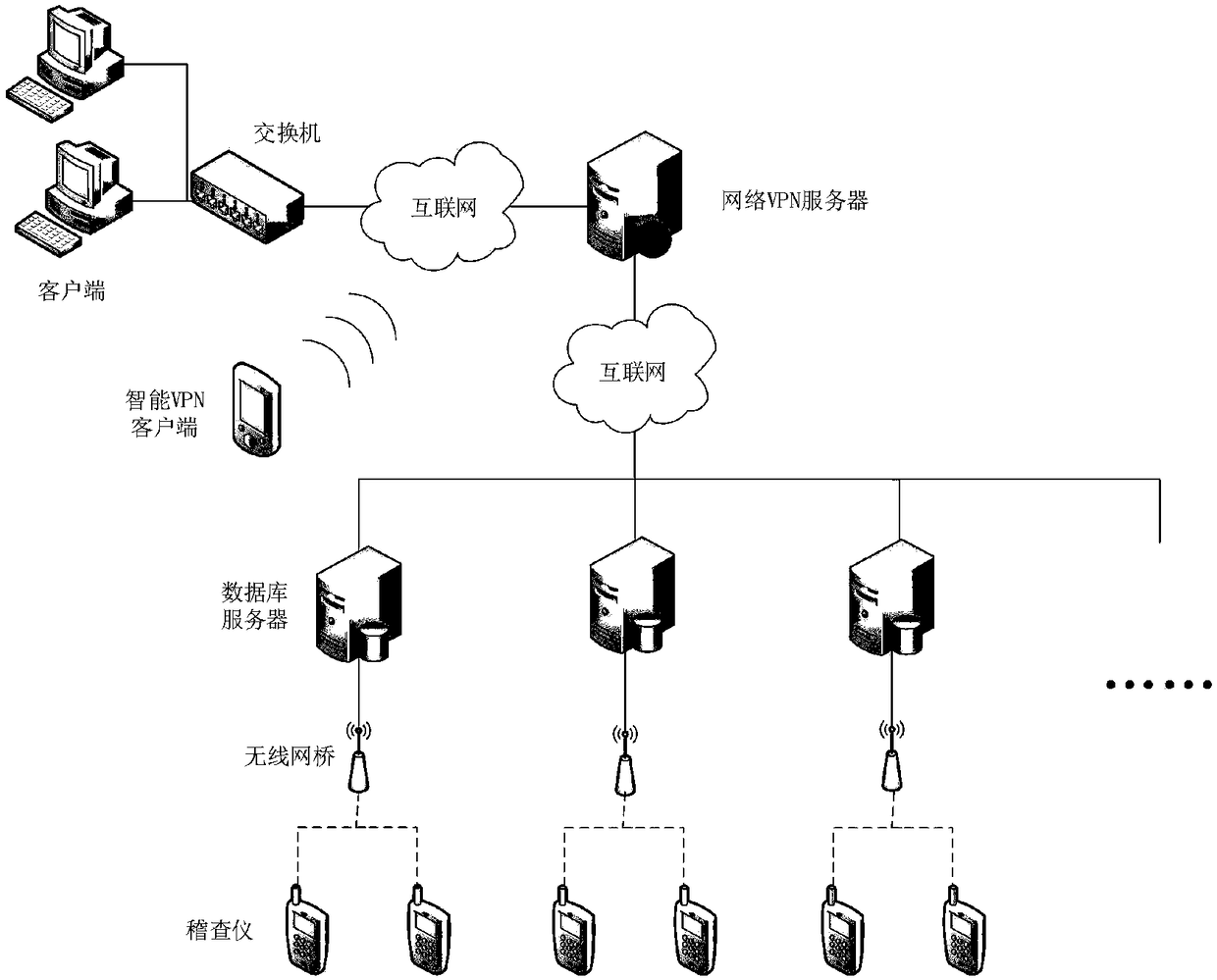
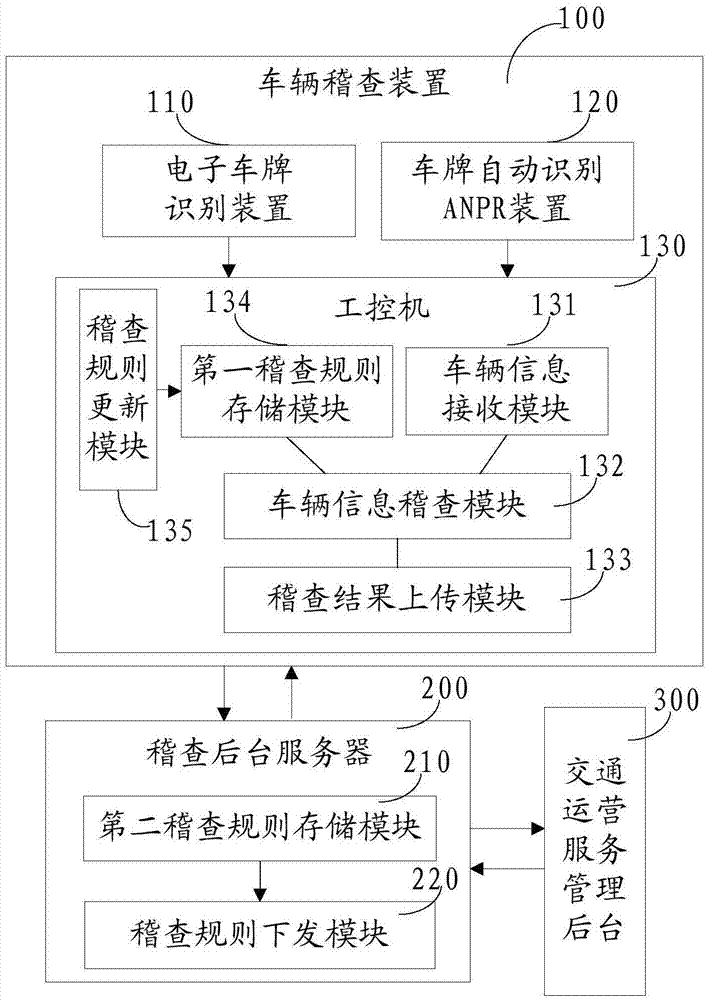
InactiveCN105448102AImprove audit efficiencyFlexible Audit OperationRoad vehicles traffic controlVehicle inspectionIdentification device
The invention discloses an electronic license plate-based intelligent vehicle inspection system and method and belongs to the road inspection technical field. The inspection system includes vehicle inspection equipment and an inspection background server (200); the vehicle inspection equipment includes a vehicle inspection device (100) and an inspection vehicle for carrying the vehicle inspection device (100); the vehicle inspection device (100) includes an electronic license plate recognition device (110) and a license plate automatic recognition ANPR device (120); the electronic license plate recognition device (110) and the license plate automatic recognition ANPR device (120) are respectively connected with an industrial personal computer (130); and the vehicle inspection equipment is connected with the inspection background server (200) through the industrial personal computer (130). With the inspection system and method provided by the invention adopted, intelligent inspection of motor vehicles can be realized, and vehicle inspection efficiency of workers of the public security and traffic management department can be effectively improved. The inspection system and method are suitable for a variety of application occasions such as illegal parking management and non-parking inspection.
Owner:WATCHDATA SYST
Audit method and system based on convolutional neural network model and readable storage medium
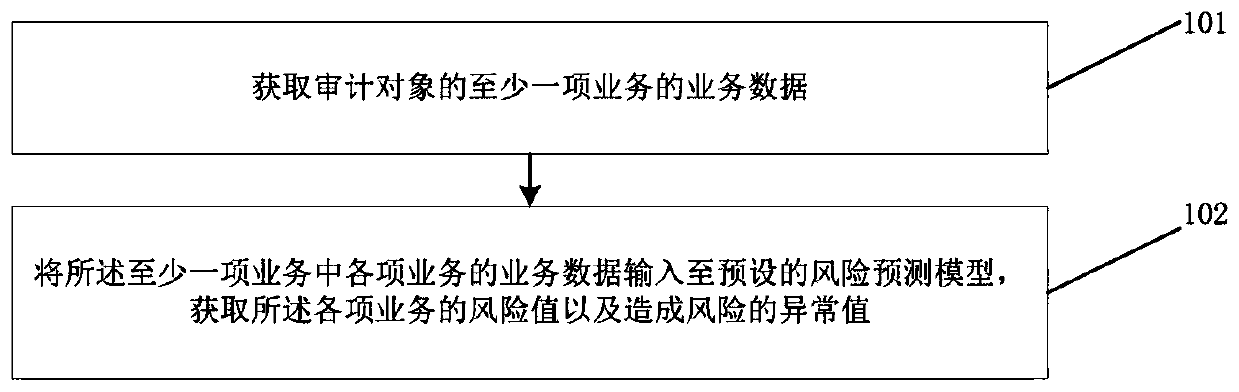
PendingCN110543565AReduce labor costsImprove audit efficiencyFinanceResourcesEngineeringBusiness data
The invention provides an auditing method and system based on a convolutional neural network model, and a readable storage medium. The method comprises the following steps: obtaining service data of at least one service of an auditing object; and inputting the business data of each business in the at least one business into a preset risk prediction model, and obtaining a risk value of each business and an abnormal value causing the risk.
Owner:GUANGXI POWER GRID CO LTD NANNING POWER SUPPLY BUREAU
Data integrity auditing method supporting tag block chain storage and query
PendingCN111898164AImprove storage scalabilitySave storage spaceDigital data protectionData integrityCiphertext
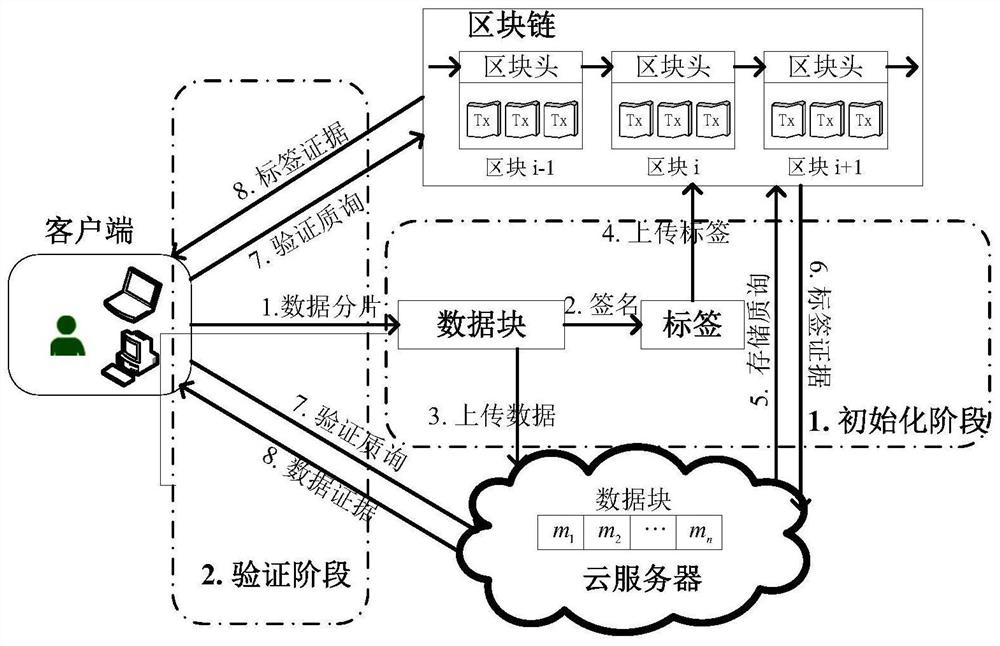
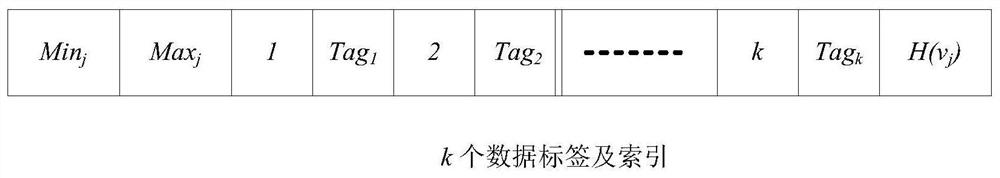
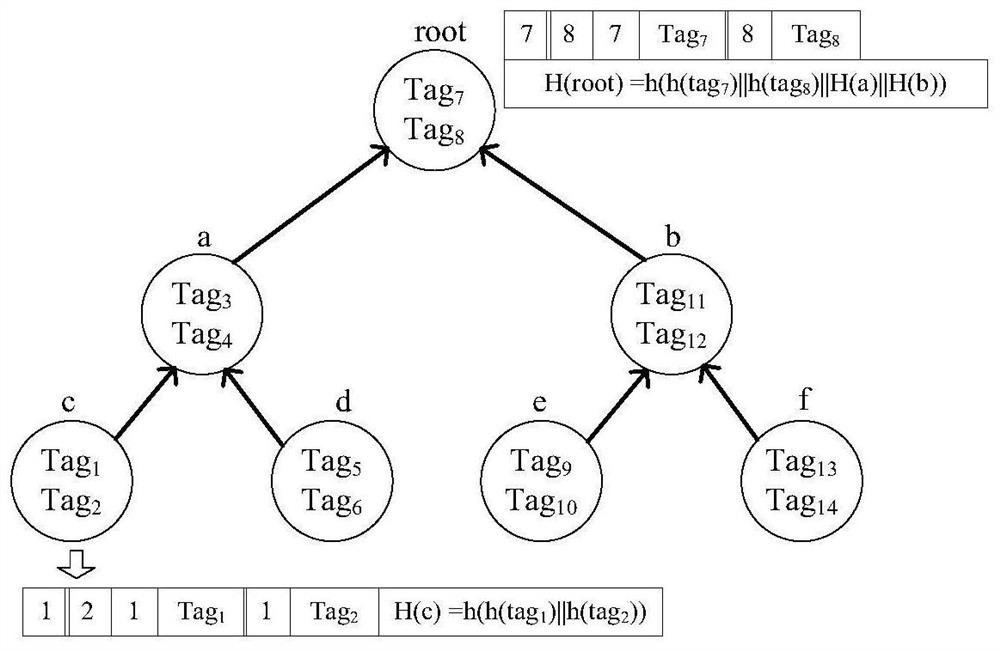
The invention discloses a data integrity auditing method supporting tag block chain storage and query, which comprises the steps that a client blocks a data file and generates a data tag, data is stored on a cloud server, and the data tag is stored on a block chain platform in a T-Merkle tree structure; an auditor sends a sampling auditing inquiry to the cloud server and the block chain platform;the block chain platform executes a query algorithm to obtain the data tag, calculates ciphertext label evidence and returns the ciphertext tag evidence to the auditor, and meanwhile, the cloud servercalculates ciphertext data evidence and returns the ciphertext data evidence to the auditor; and the auditor directly verifies the integrity of the data through the double-line pair property on the premise that decryption is not needed. According to the invention, the block chain platform is used for storing data tags, a corresponding block chain storage structure and a query method are provided,and a bilinear pair verification method based on ZSS short signatures is designed, so that the expandability of the system and the security and high efficiency of data integrity auditing are improved.
Owner:WUHAN TEXTILE UNIV
Intelligent auditing method and system and readable storage medium
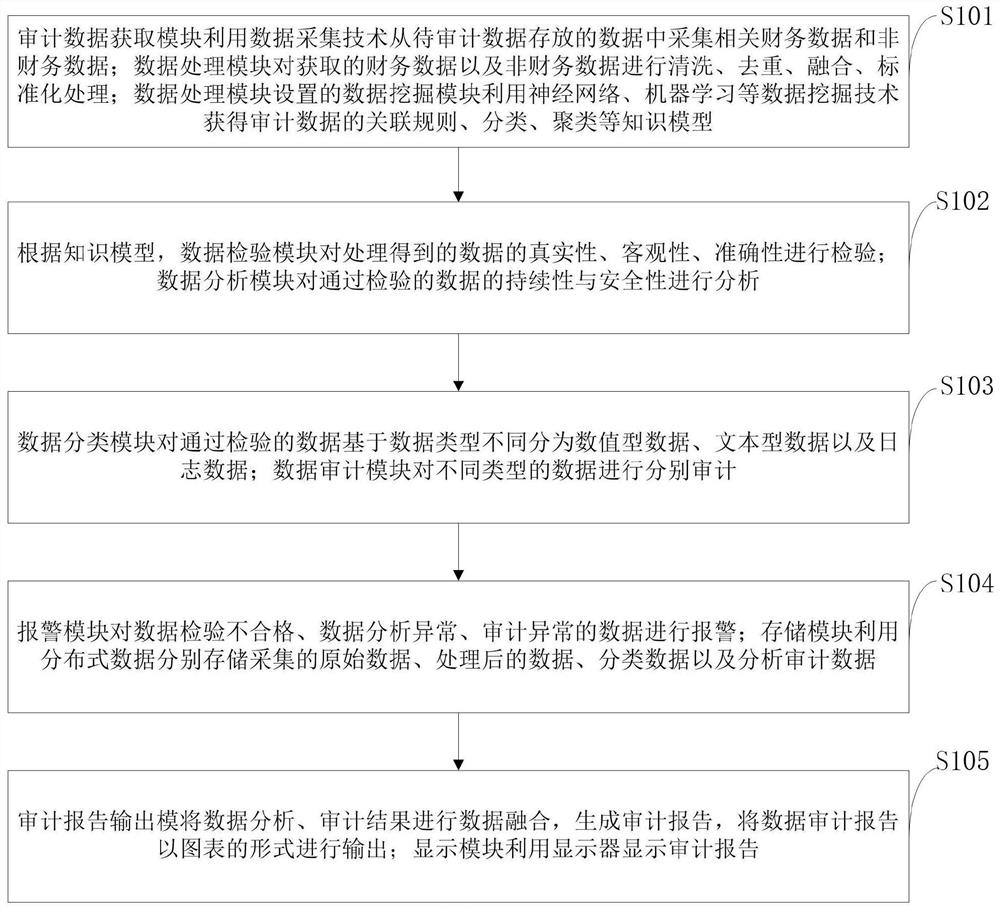
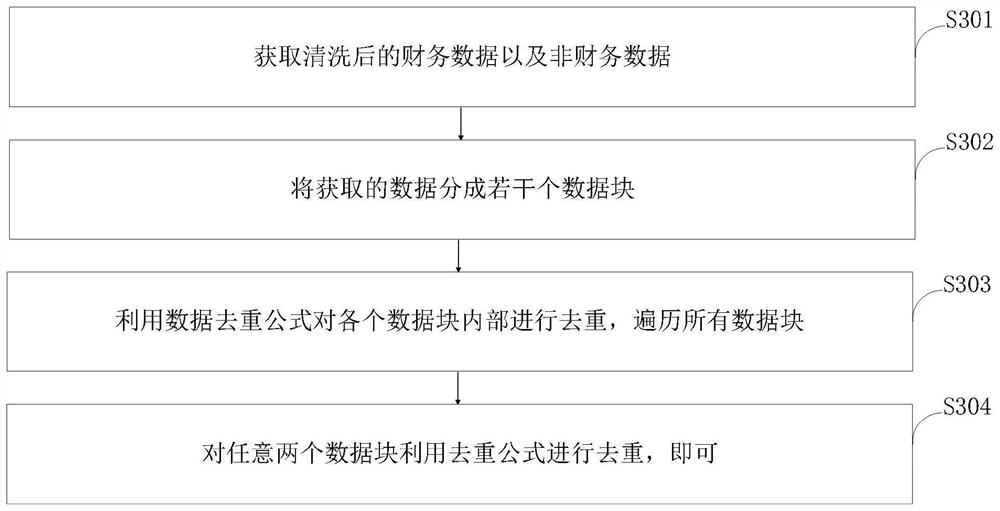
InactiveCN112100164AEasy to collectSimplify the audit processFinanceRelational databasesData classDisplay device
The invention belongs to the technical field of data auditing, and discloses an intelligent auditing method and system and a readable storage medium. The method comprises the steps of: performing processing and data mining on the acquired data; checking the authenticity, objectivity and accuracy of the data; analyzing the continuity and the security of the data; dividing the data passing the inspection into numeric data, text data and log data based on different data types; respectively auditing different types of data; alarming the data which is unqualified in data inspection, abnormal in data analysis and abnormal in auditing; performing data fusion on the data analysis and auditing results to generate an auditing report, and outputting the data auditing report in a chart form; displaying audit reports with a display. According to the method, the data collection, analysis and auditing processes can be simplified, the data can be comprehensively and effectively audited, related problems hidden in mass data can be effectively found, and the auditing efficiency is effectively improved.
Owner:NANJING AUDIT UNIV
CIT (computer and information technology) intelligent security control system and method
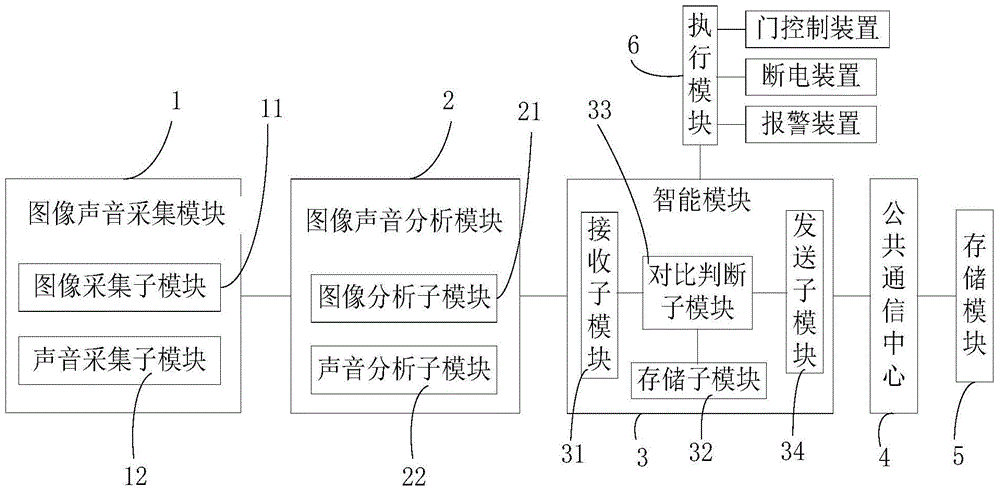
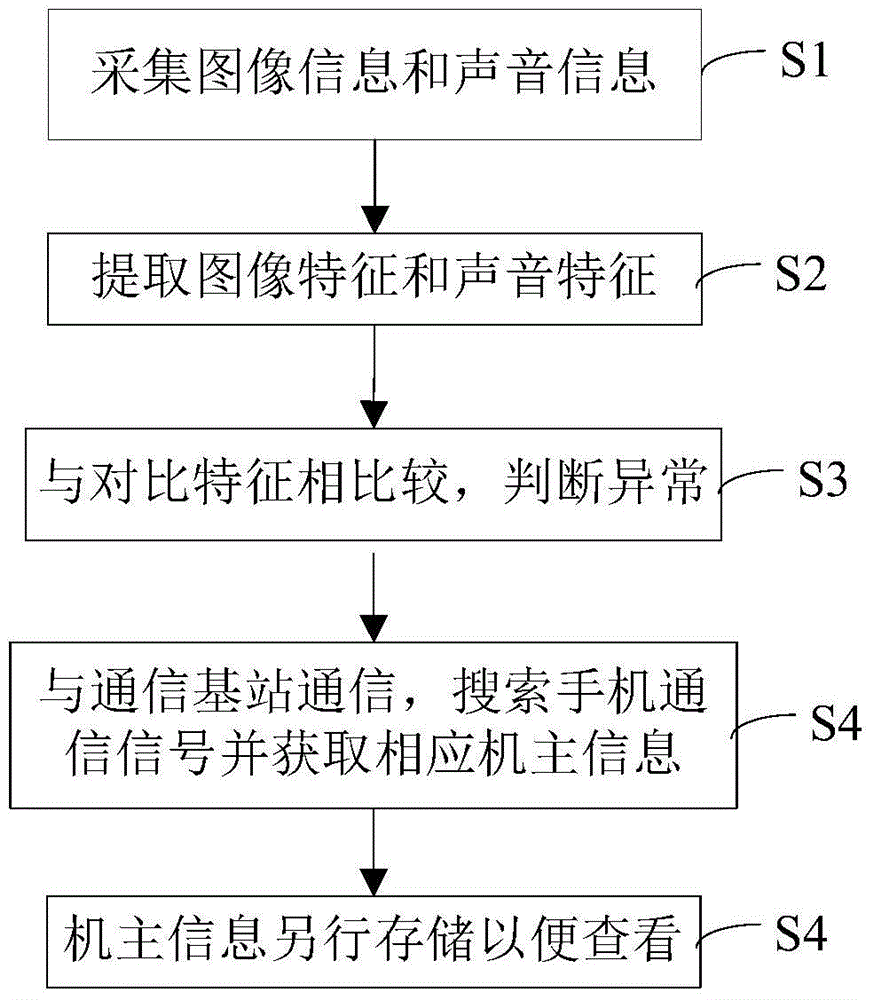
InactiveCN104581045ANarrow down the scope of identity verificationImprove audit efficiencyClosed circuit television systemsSpeech recognitionControl systemComputer module
The invention provides a CIT (computer and information technology) intelligent security control system. The CIT intelligent security control system comprises an image and sound collection module which is used for performing photographing and sound recording on a monitored region, an image and sound analysis module which is connected with the image and sound collection module and is used for analyzing collected image and sound and extracting the characteristics of the image and the characteristics of the sound, an intelligent processing module which is connected with the image and sound analysis module and comprises a receiving sub-module, a storage sub-module, a comparison and judgment sub-module and a sending sub-module, and a public communication center which is connected with the intelligent processing module and is used for searching a mobile phone communication signal in a predetermined range through a communication base station and obtaining owner information corresponding to a mobile phone and storing the owner information in the storage module, wherein the comparison and judgment sub-module is respectively connected with the receiving sub-module, the storage sub-module and the sending sub-module and is used for comparing the characteristics of the image and the characteristics of the sound which are received by the receiving sub-module with comparison characteristics stored in the storage sub-module to judge whether the image and the sound are abnormal or not and sending a command through the sending sub-module;. The CIT intelligent security control system provided by the invention can effectively reduce difficulty in post-checking.
Owner:ANHUI HUASHENG TECH HLDG
Cluster audit control method based on blockchain technology
ActiveCN108900505AAchieve protectionImprove audit efficiencyTransmissionReal time acquisitionBlockchain
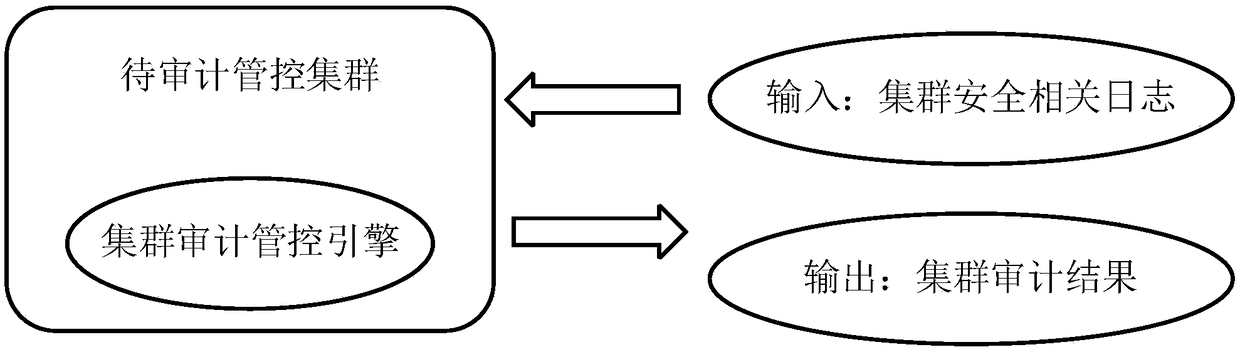
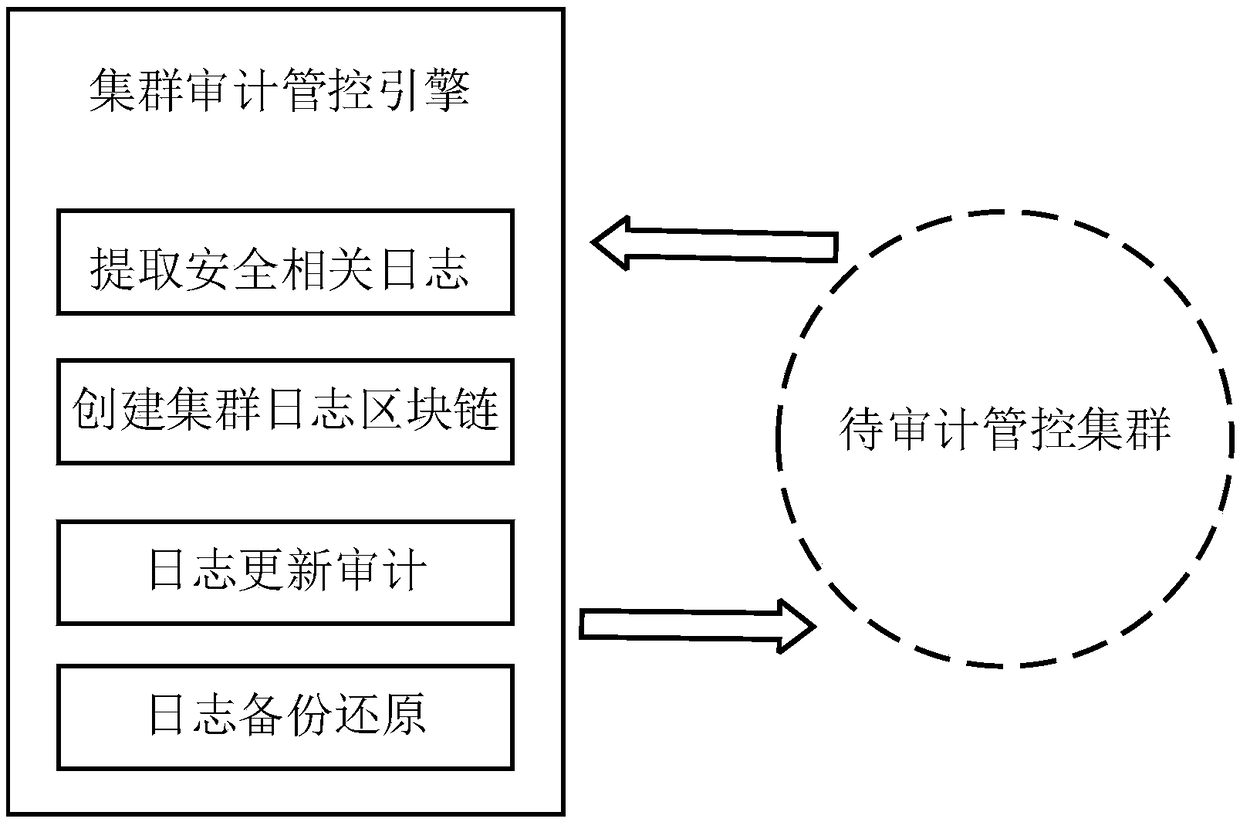
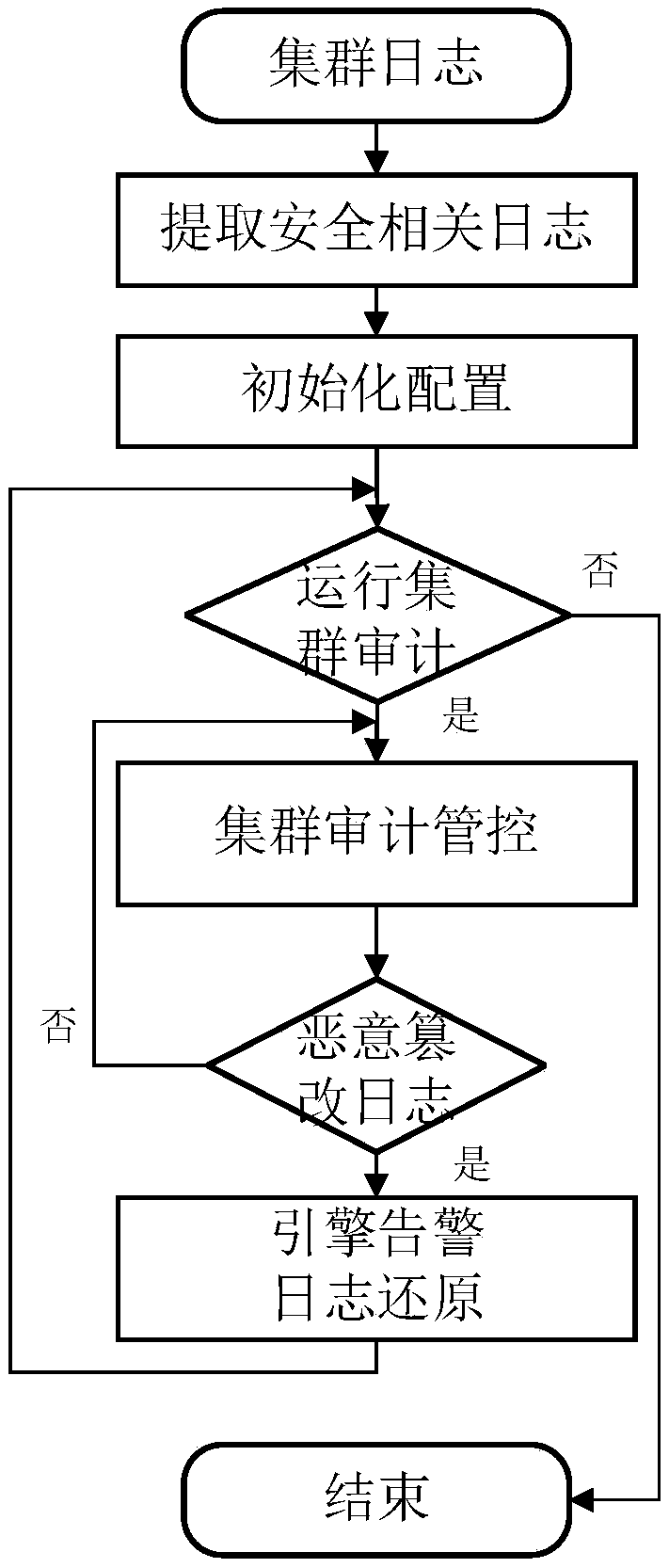
The invention provides a cluster audit control method based on a blockchain technology. The cluster audit control method based on a blockchain technology includes the steps: extracting security related logs in the cluster and collecting information, then establishing a cluster audit control engine, saving the initial state of the logs, collecting logs in real time, and auditing the logs; when thelogs are updated, performing the operation of comparison and adding on the updated logs on the blockchain by the cluster audit control engine, and backing up the updated logs to a server; and when thecluster logs are maliciously tampered, reporting the tampering events and restoring the original logs by the cluster audit control engine. The invention provides a method for security audit of the cluster and management of the cluster. The cluster audit control method based on a blockchain technology can improve the audit efficiency of the cluster and the security of the cluster.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Database auditing method and device, equipment and storage medium
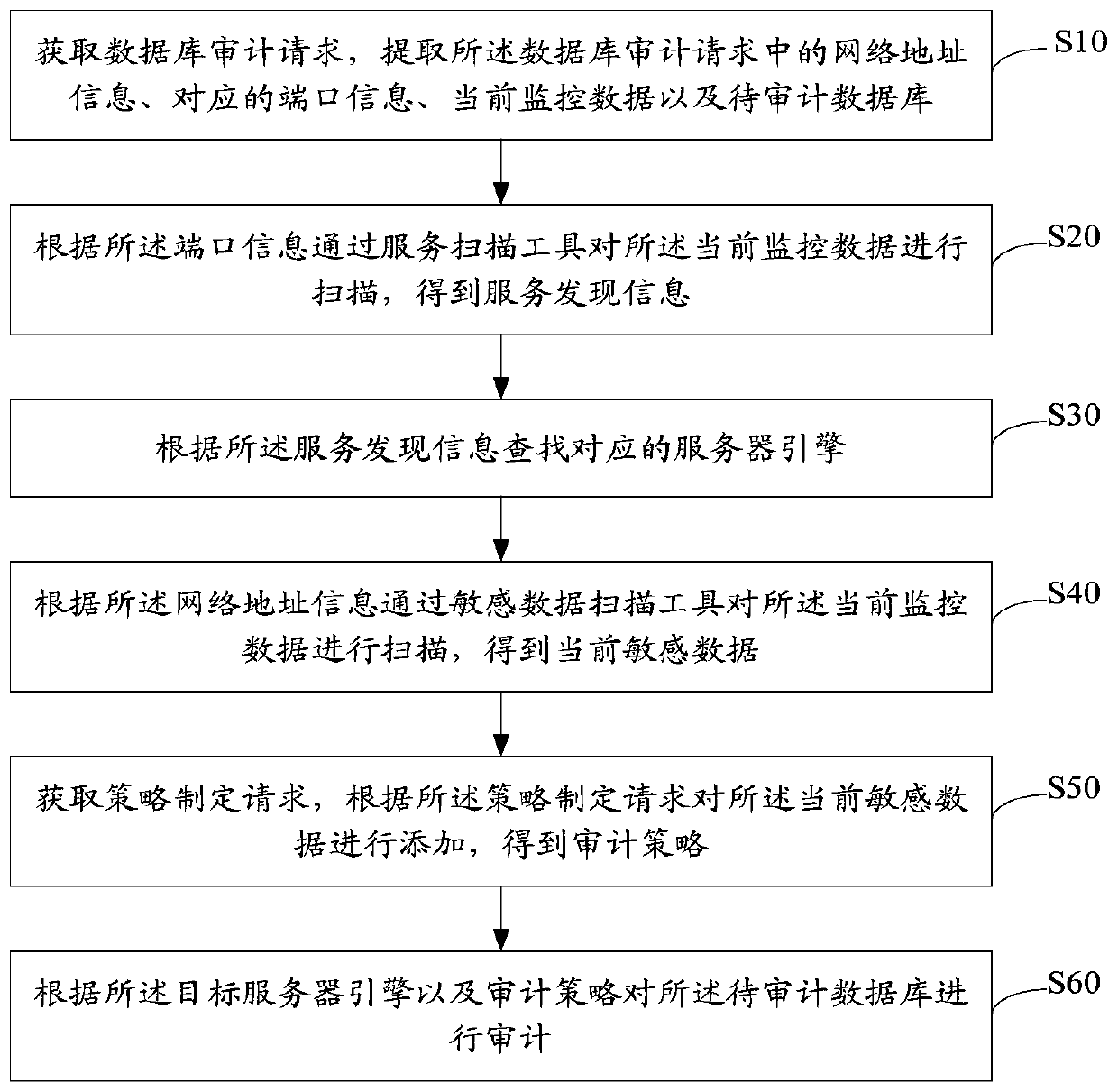
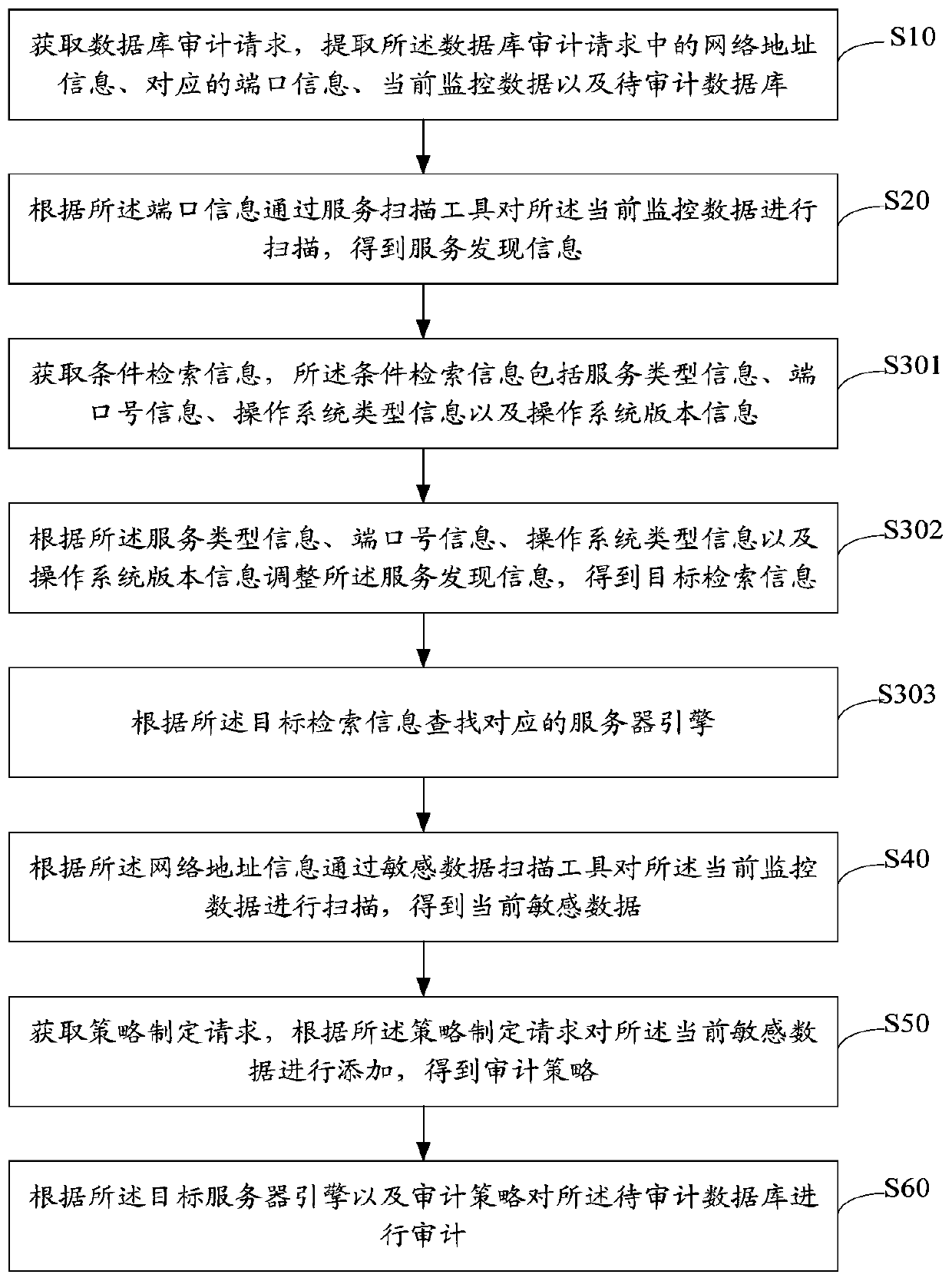
ActiveCN111104395AImprove audit efficiencyDigital data protectionEnergy efficient computingNetwork addressingEngineering
The invention relates to the technical field of database auditing, and discloses a database auditing method and device, equipment, and a storage medium. The method comprises the steps of obtaining a database auditing request, and extracting network address information, corresponding port information, current monitoring data and a to-be-audited database in the database auditing request; scanning the current monitoring data through a service scanning tool according to the port information to obtain service discovery information; searching a corresponding server engine according to the service discovery information; scanning the current monitoring data through a sensitive data scanning tool according to the network address information to obtain current sensitive data; obtaining a strategy making request, and adding the current sensitive data according to the strategy making request to obtain an auditing strategy; and auditing the to-be-audited database according to the server engine and the auditing strategy, thereby achieving the purpose of improving the auditing efficiency of the sensitive data.
Owner:武汉英迈信息科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com