Cloud storage data auditing method for preventing secret key from being revealed
A data auditing and cloud storage technology, applied in the field of cloud computing security, can solve the problems of system audit security loss, low user security awareness, and inability to resist key leakage, etc., to improve storage efficiency and audit performance, and reduce the number of tags , the effect of reducing the burden on oneself
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
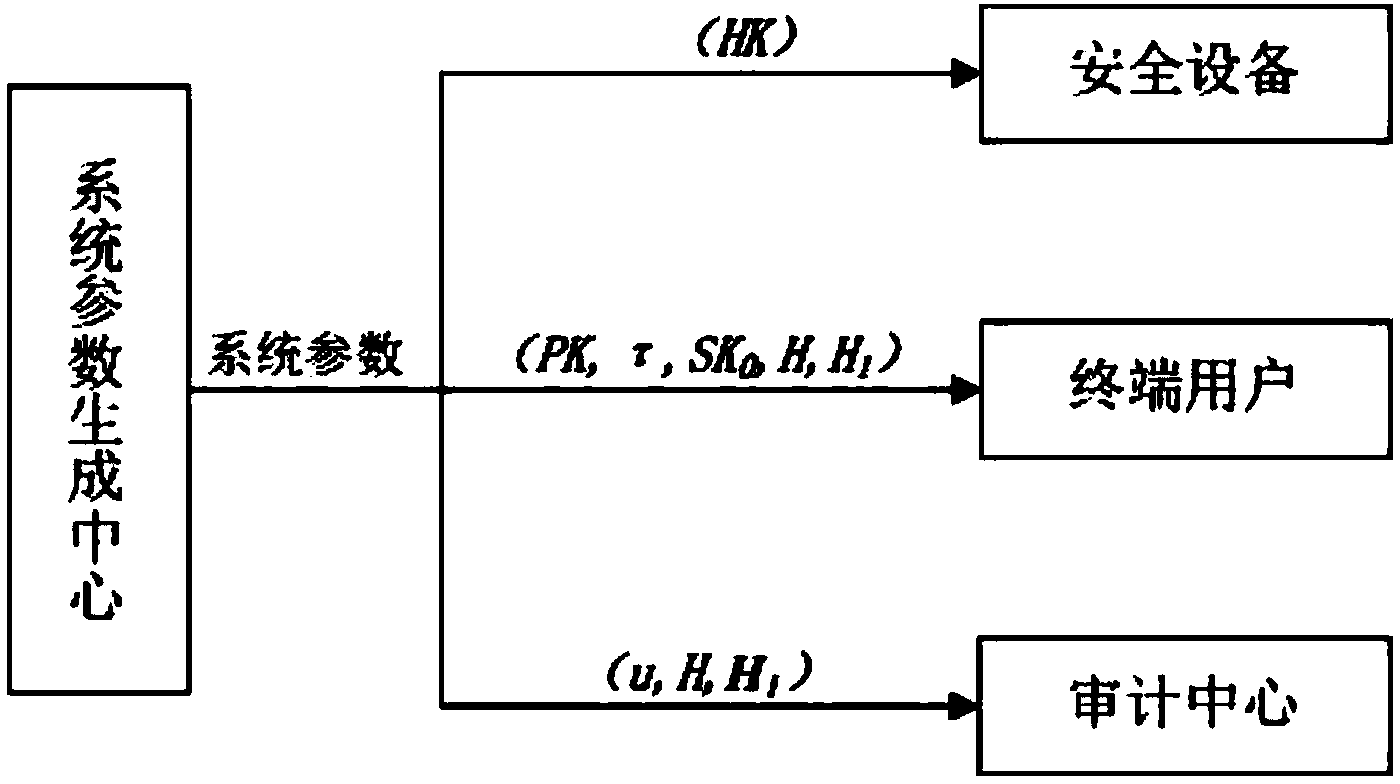
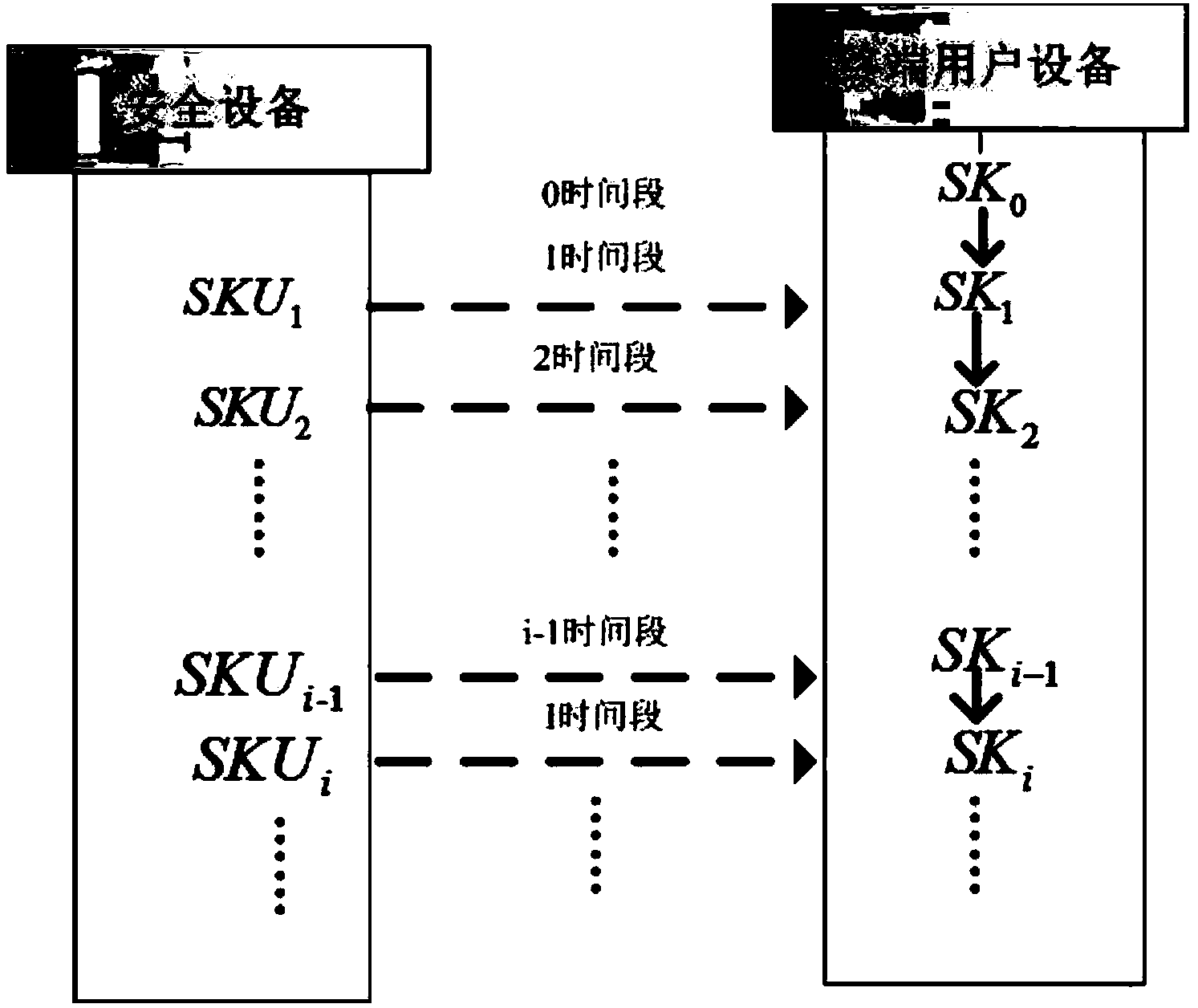
[0030] The members of the system used in the cloud storage data audit method that can resist key leakage provided by this patent include a system parameter generation center, a cloud, end users, security equipment, and an audit center. Among them, the system parameter generation center generates various system parameters, generates public and private keys for users, selects device private keys for security devices, calculates audit parameters, etc.; the cloud provides storage resources for user data; a large amount of data of end users must be outsourced to the cloud; security The device assists the user to periodically update the key; the audit center verifies the data integrity on behalf of the user.
[0031] The following examples are used to describe the implementation of the present invention in detail, so as to fully understand and implement the process of how to apply technical means to solve technical problems and achieve technical effects in the present invention.
[00...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com