Method for completely auditing user behaviors under centralization access mode
A user-behavior technology, applied in the field of information security, can solve problems such as system resource occupation, data loss, and system efficiency reduction, and achieve the effect of solving performance problems of the audit system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
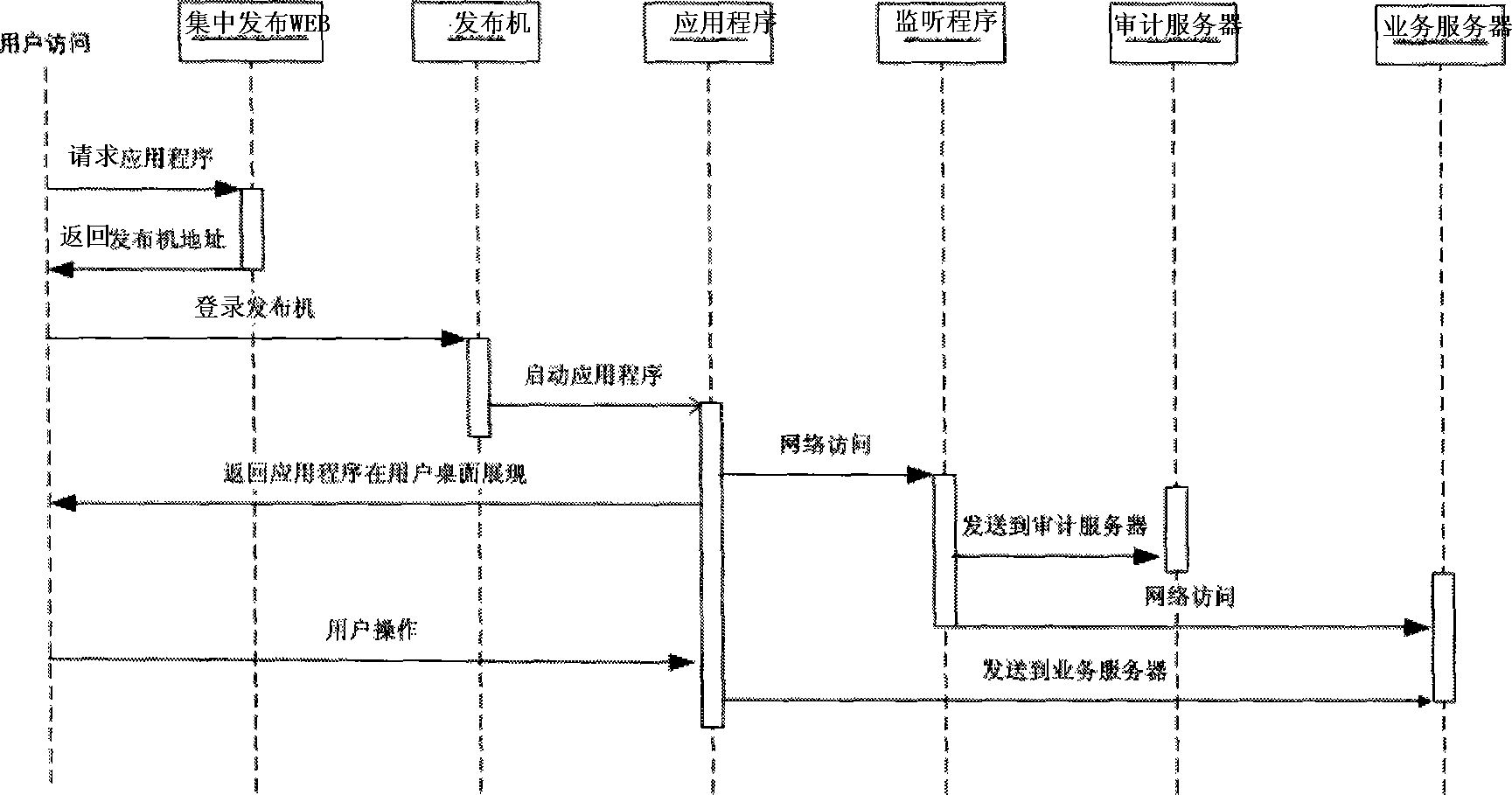
[0027] See attached picture. In the present invention, a centralized publishing platform is arranged between the client end and the background server, which is composed of several publishing machines, and the network monitoring program is installed on the publishing machines.
[0028] Concrete steps of the present invention are as follows:
[0029] Step 1: Set up a centralized publishing platform composed of several publishing machines, and deploy application software and network monitoring programs on the publishing machines;
[0030] Step 2, the user requests access to the application software through the web interface of the centralized publishing platform;
[0031] Step 3: The centralized publishing platform designates users to access the application software on the specific publishing machine according to the load balancing mechanism;
[0032] Step 4, the user uses his own account (main account) to connect to the publishing machine through the client of the centralized ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com