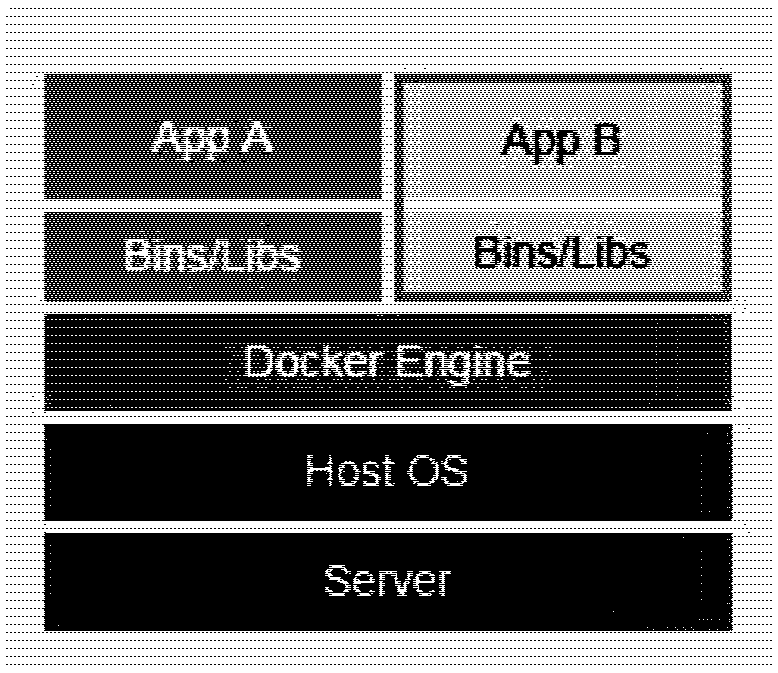
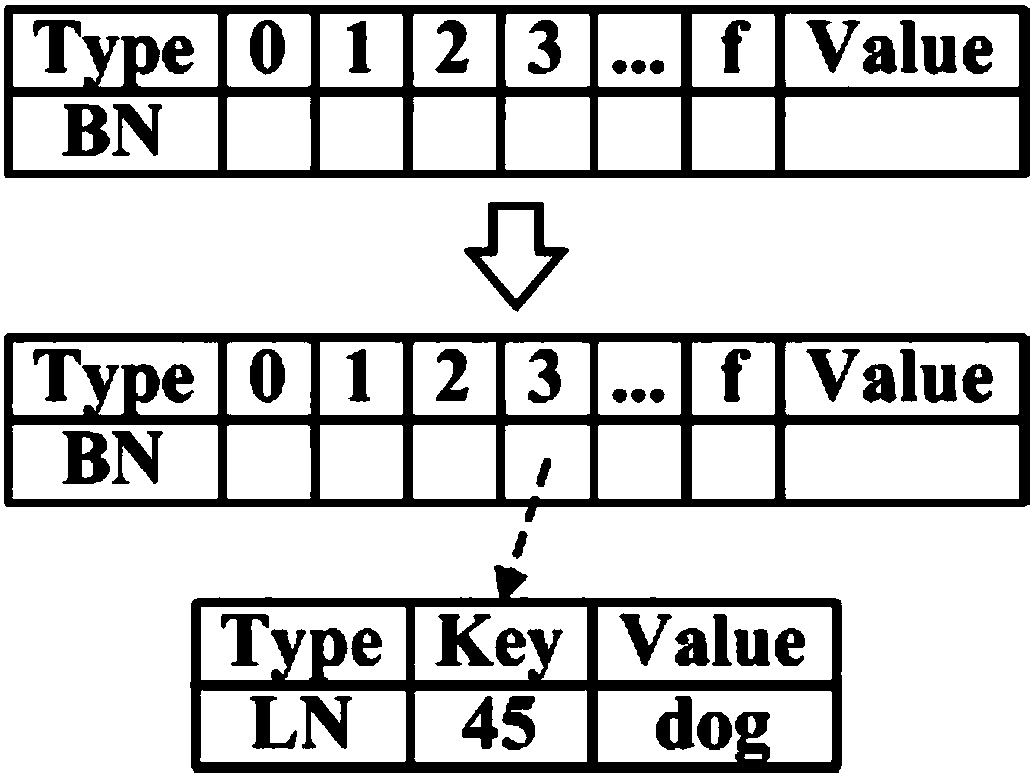
Patents
Literature
274results about How to "Resolve integrity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
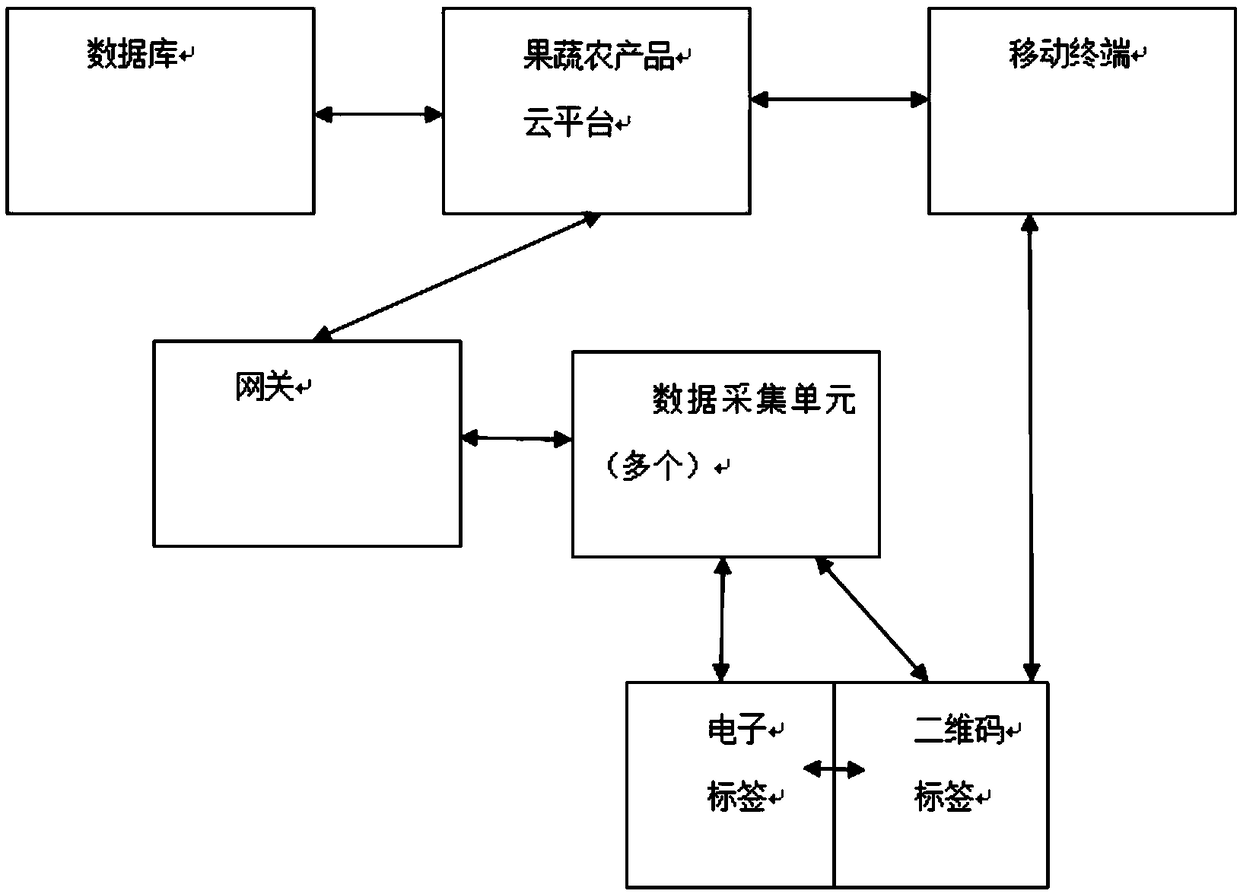
A fruit and vegetable agricultural product quality safety traceability system based on a block chain
InactiveCN109191003AGuaranteed not to be tampered withResolve integrityResourcesCommerceQuality safetyComputer science
The invention provides a fruit and vegetable agricultural product quality safety traceability system based on a block chain, which comprises a fruit and vegetable number generation module, a fruit andvegetable transaction generation recording module, a verification block chain module and a transaction block chain module. The invention utilizes the block chain technology, can ensure that the datain the whole link cannot be tampered with and cannot be replaced, records the whole transaction process through the transaction block chain and verifies the transaction behavior through the verification block chain, thereby solving the integrity and trustworthiness of the quality safety data in the fruit and vegetable agricultural product quality safety traceability system.
Owner:ZHONGKAI UNIV OF AGRI & ENG
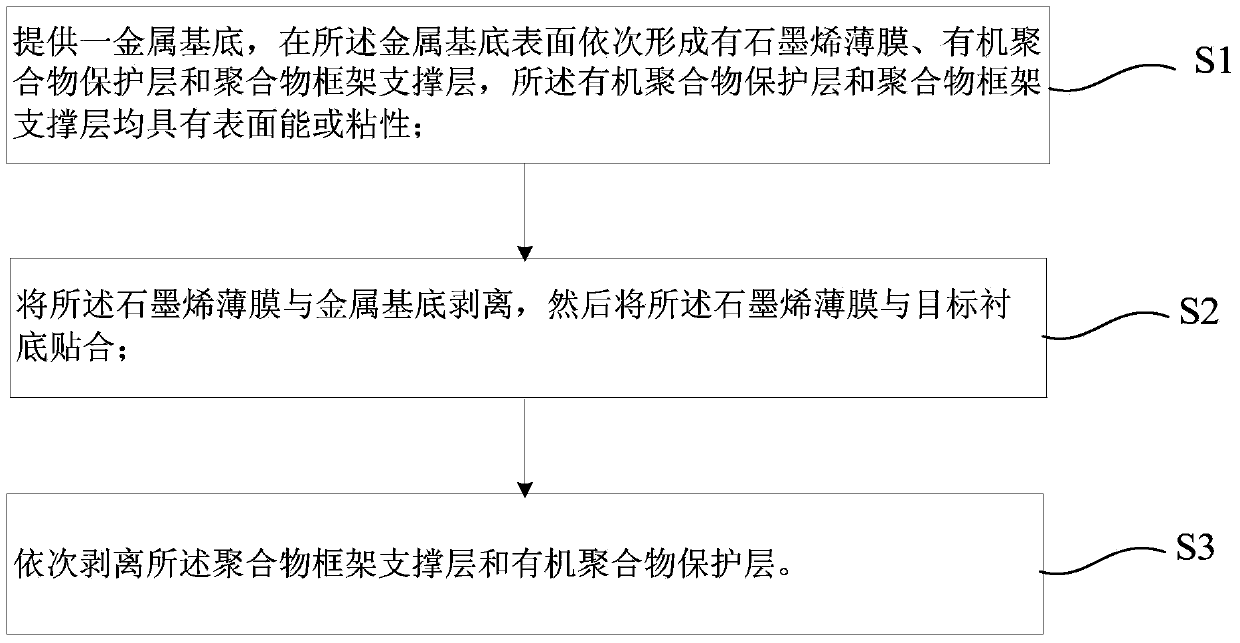
Transfer method of graphene film
The invention provides a transfer method of a graphene film, which at least comprises the following steps: providing a metal substrate, and sequentially forming a graphene film, an organic polymer protective layer and a polymer frame support layer on the metal substrate surface, wherein the organic polymer protective layer and polymer frame support layer respectively have surface energy or viscosity; peeling the graphene film from the metal substrate, and attaching the graphene film to a target substrate; and finally, sequentially peeling the polymer frame support layer and organic polymer protective layer. By utilizing the proper surface energy or proper viscosity of the organic polymer protective layer and polymer frame support layer, the organic polymer protective layer and polymer frame support layer can be directly attached without any adhesive, and can be peeled without damage after transfer, thereby simplifying and stabilizing the technique and ensuring the complete transfer of the graphene film and the reutilization of the metal substrate.
Owner:SHANGHAI ADVANCED RES INST CHINESE ACADEMY OF SCI
Honeycomb concrete
InactiveCN101239837ASolve the problem of "cold bridge"Extended service lifeCeramicwarePortland cementFilling materials
The present invention relates to a honeycomb concrete belong to a building material. The honeycomb concrete comprises the mother material and supplementary material with the following weight proportion: quick hardening sulfaluminous cement or ultrastrength cement: 30-70 parts; filling material: 25-60 parts; ordinary Portland cement: 5-10 parts; waterproofing agent: 1-1.5 parts; bleeding agent: 2.0-3.0 parts; suspension agent: 2.0-5.0 parts; foam stabilizer: 0.1-0.5 parts; and honeycomb agent: 38-60 parts. The invention has the following advantages and beneficial effects: light weight, high strength, long service lifetime, heat preserving with high efficiency, heat insulation, sound insulation, self-water-proofing, non combustibility, impact resistance, small contraction percentage, convenient construction and installation, reducing the weight of the building, increasing the using area, convenient product preparation and construction, the concrete not only can be made in factory but also can be made at the construction site.
Owner:徐东亮 +2
Video monitoring intelligent early-warning system and method on basis of target space relation constraint
ActiveCN103530995AEfficient detectionRapid positioningClosed circuit television systemsAlarmsVideo monitoringEarly warning system
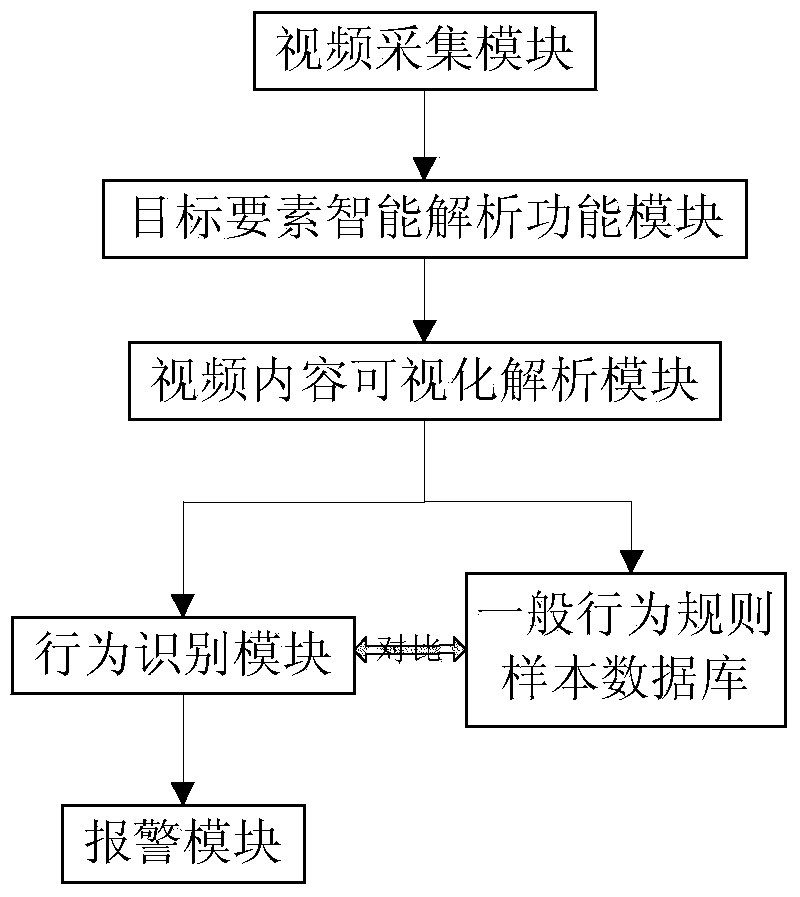
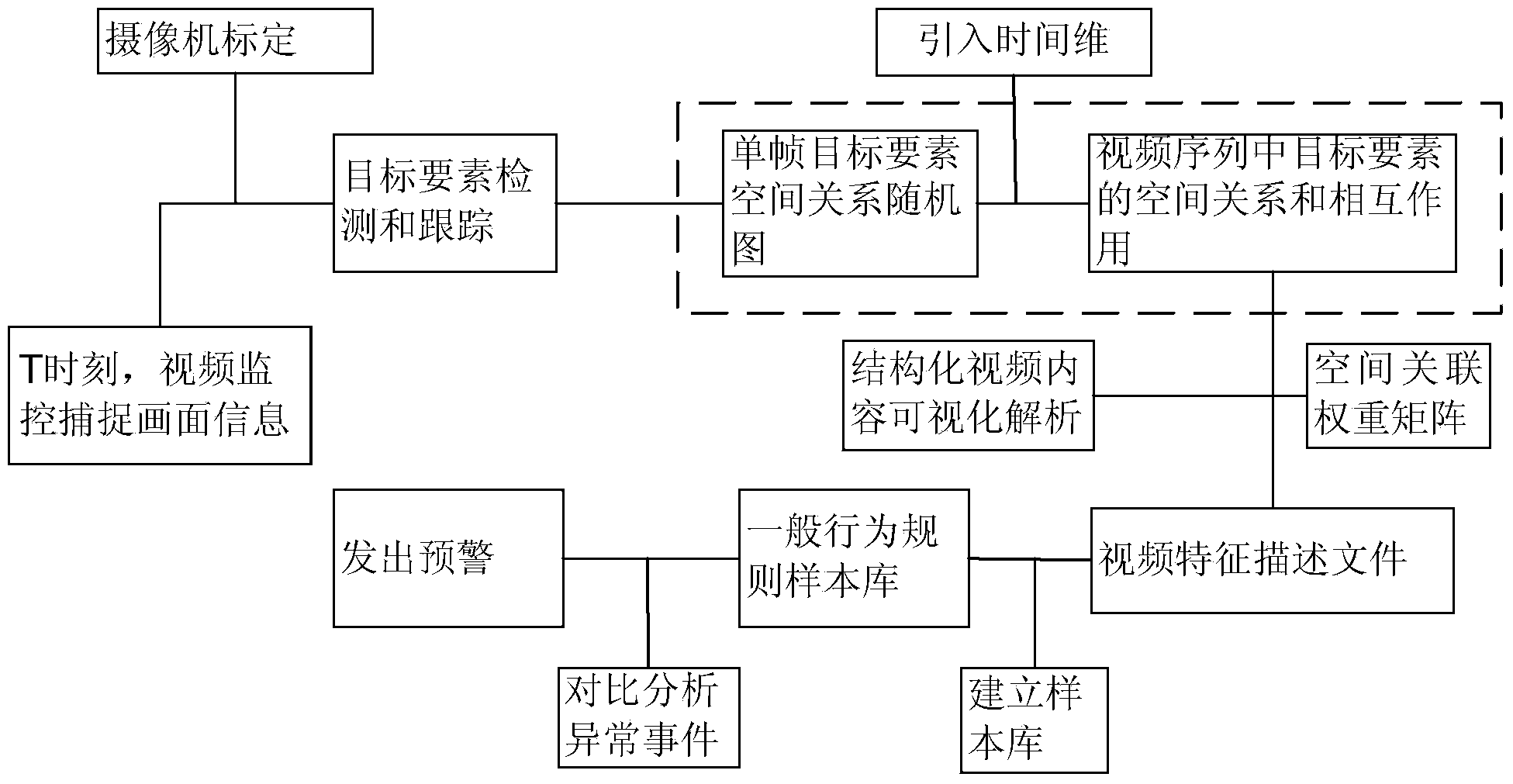
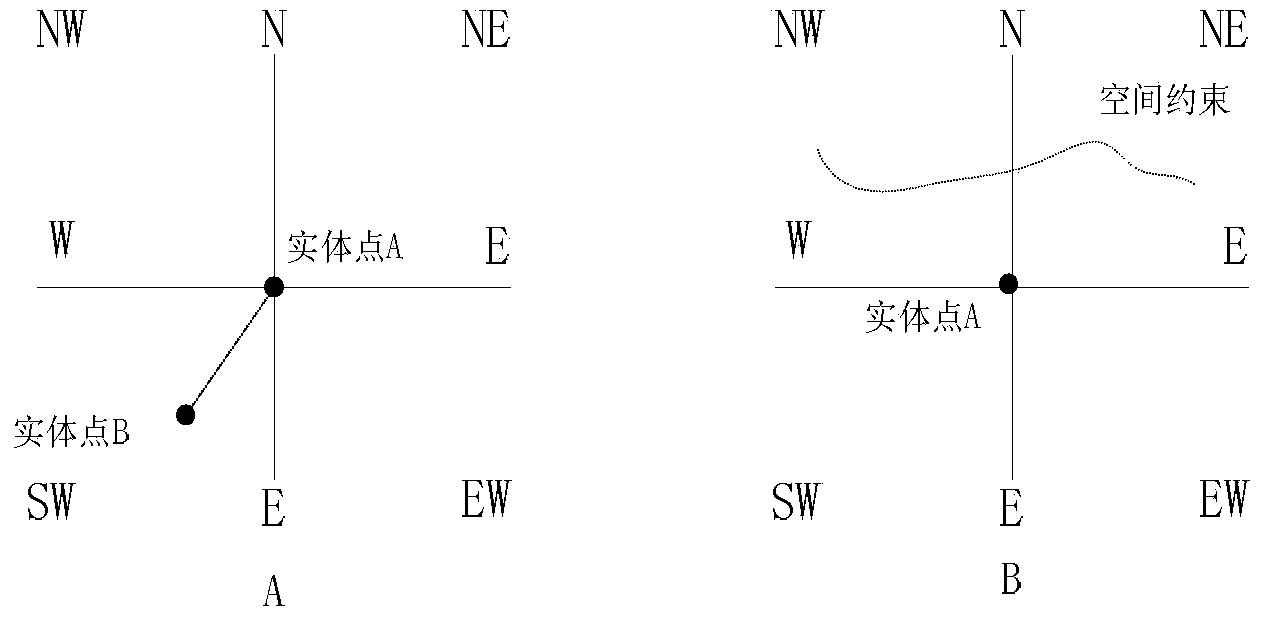
The invention discloses a video monitoring intelligent early-warning system and a video monitoring intelligent early-warning method on the basis of target space relation constraint. The system comprises a video acquisition module, a target component intelligent analysis functional module, a video content visual analysis module, a general behavior rule sample database and an alarm module. On the basis of behavior comprehension on target components, aiming at spatial correlation between targets, the system carries out behavior characteristic analysis, evolution and classification, establishes a spatial correlation mode sample library, implements detection and identification on abnormal behaviors, can more effectively and accurately carry out identification and judgment on emergencies and can lock an abnormity trigger point to provide evidence for post-mordem forensics. The system introduces target space relation constraint, divides a video scene region to complete defining related concepts of the target components of a video, eliminates a certain fuzziness and faults in space semantic information, solves the problems of incompletion and inaccuracy in video content analysis and is more accurate and more efficient to detect abnormal events in a video monitoring range.
Owner:博拉网络股份有限公司
Method for completely auditing user behaviors under centralization access mode
InactiveCN101442449AIntegrity guaranteedResolve integrityData switching networksNetwork behaviorApplication software
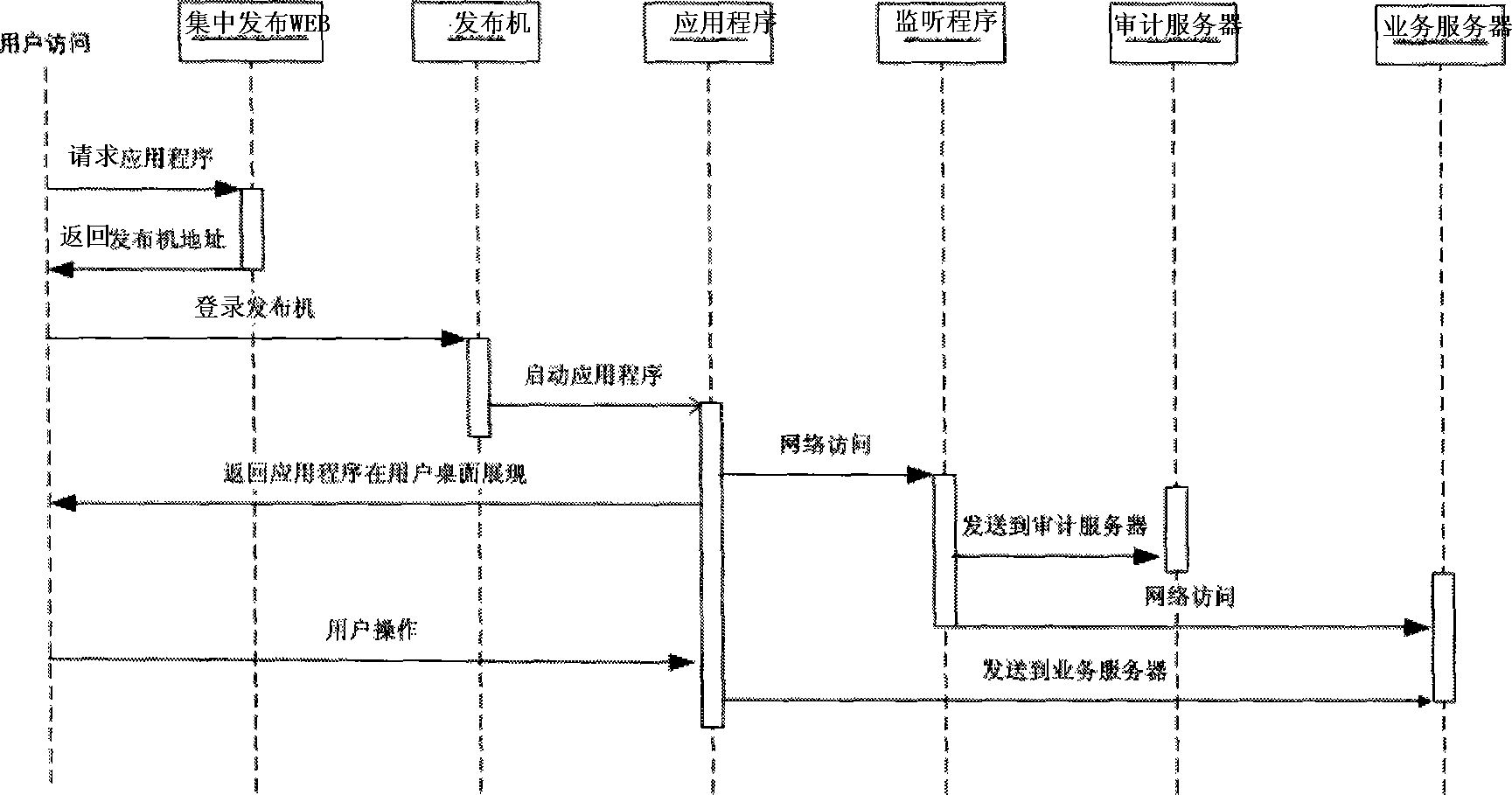
The invention discloses a method for overall auditing behavior of a customer under an integrated access pattern, wherein an integrated issuing platform consisting of a plurality of issuing machines is provided, each issuing machine is provided with application software and a network monitoring program; and an auditing server is linked to the network in a bypass mode, and a network acquisition module of the method acquires a network behavior log operated by a user to an auditing server which matches the network access information of the user transmitted by the monitoring program with the network operation log to form complete auditing information for search and analysis, thereby realizing complete auditing data based on the operator. The invention achieves complementarity of advantages of the monitoring program and network behavior auditing methods through the combination of two technological means, thereby ensuring the completeness of the auditing data and improving the auditing efficiency.
Owner:CHINA MOBILE GROUP ZHEJIANG
Robot manual navigation method based on single-person gestures and voice information
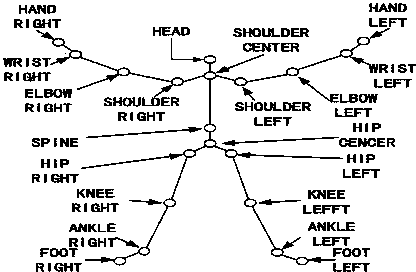
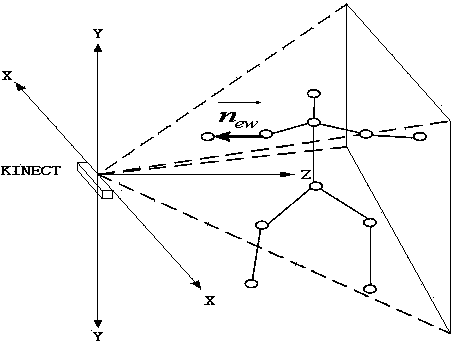
ActiveCN103885585AResolve integrityOvercome limitationsInput/output for user-computer interactionSpeech recognitionSomatosensory systemControl system
The invention discloses a robot manual navigation method based on single-person gestures and voice information. The method includes: collecting human skeleton joint point information and voice information in a current environment through Kinect equipment, and figuring out skeleton information integrity and voice information intelligibility; if the skeleton information integrity is not smaller than a skeleton information integrity threshold, using gesture identification to perform robot manual navigation; if the skeleton information integrity is smaller than the skeleton information integrity threshold and the voice information intelligibility is not smaller than a voice information intelligibility threshold, using voice identification to perform robot manual navigation; if the skeleton information integrity is smaller than the skeleton information integrity threshold and the voice information intelligibility is smaller than the voice information intelligibility threshold, outputting no navigation instructions. The robot manual navigation method has the advantages that gestures and voice are combined to be applied to a robot control system, and accordingly the method is high in practicality, high in accuracy and good in instantaneity.
Owner:深圳市贝特尔机器人有限公司 +1
Method and device for managing testing environment on the basis of container technology
ActiveCN108694117AReduce resource usageOvercome irrecyclable managementSoftware testing/debuggingCurrent timeAccess time
The invention provides a method and device for managing a testing environment on the basis of a container technology, electronic equipment and a readable storage medium, and solves the problem of theresource management of the testing environment through the implementation of the automatic startup and stop of the testing environment. The method comprises the following steps that: maintaining a container monitoring lookup table, wherein the container monitoring lookup table comprises one or a plurality of entries independently corresponding to one or a plurality of created test containers, andeach entry comprises the time-out time, the container state and the last access time of the corresponding test container; responding when an access request for the specific test container is received,inquiring the container monitoring lookup table to determine the state of the specific test container; responding when the state of the specific test container is off: starting the specific test container, updating the state corresponding to the specific test container in the container monitoring lookup table to be active, and in addition, updating the corresponding last access time as current time; and routing the access to the specific test container.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
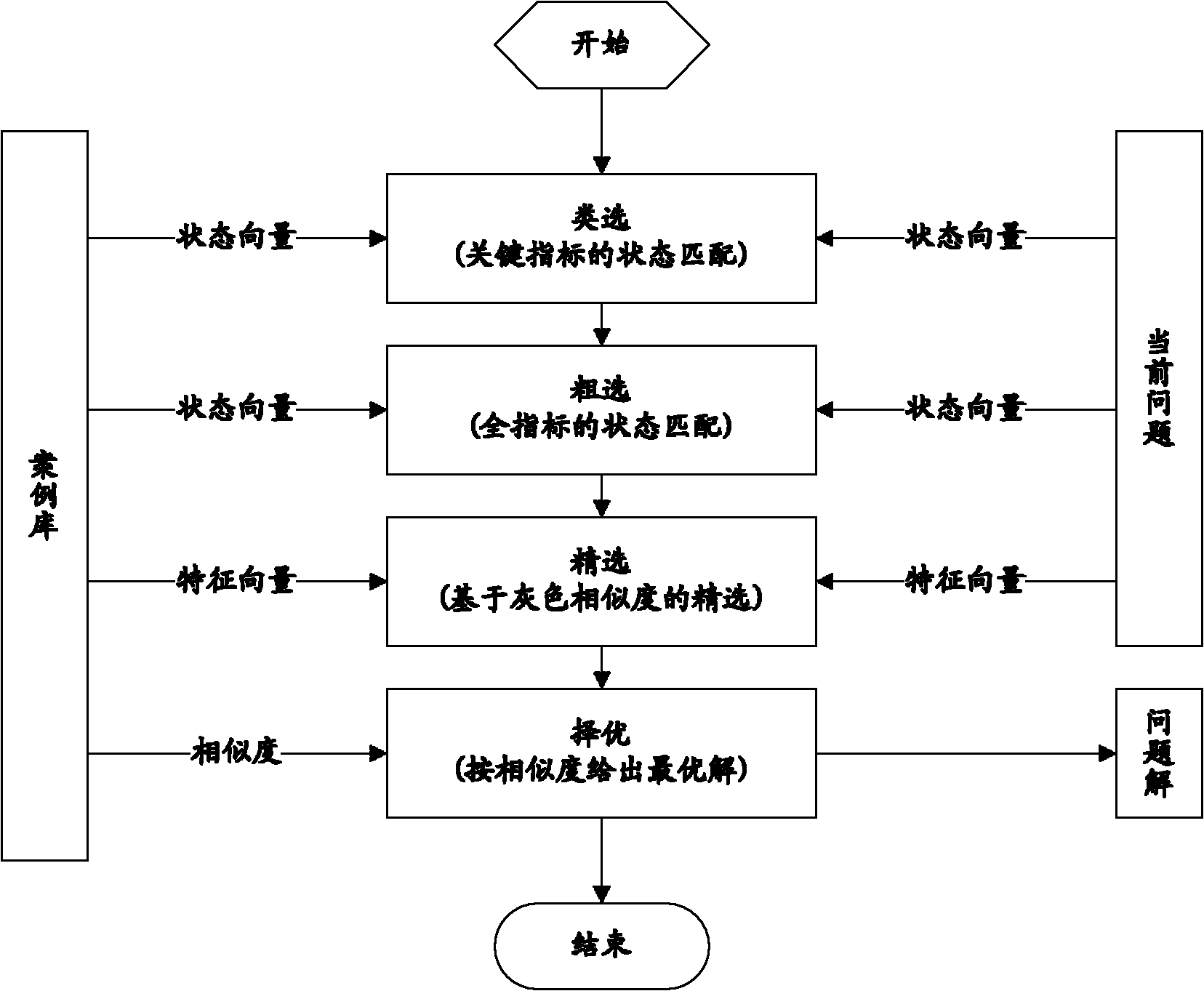
Case-reasoning-based molten steel temperature prediction method
InactiveCN102163261AResolve integrityResolve interferenceSpecial data processing applicationsPredictive methodsMolten steel
The invention discloses a case-reasoning-based molten steel temperature prediction method. The method comprises the following steps of: 1, establishing a case library in which the values of influence factors of molten steel temperatures and the molten steel temperatures are stored; 2, defining a present problem and a problem solution; 3, sorting case sets in the case library according to key state vectors; 4, roughly selecting the sorted case sets according to the discrete values of all the state vectors; 5, finely selecting the roughly-selected case sets according to the gray scale similarity of the present problem to candidate cases; and 6, preferentially calculating matched cases of which the gray scale similarity is greater than a preset similarity threshold value in a weighted mode to acquire the problem solution of the present problem. Based on a multistep retrieving policy case reasoning method, the defects that the traditional neural network method has long training time and is not suitable for on-line application and the like are overcome; and due to a weighted value-contained gray correlation degree method, the problems of incompleteness and interference existence of production data are solved to a certain extent.
Owner:汪红兵
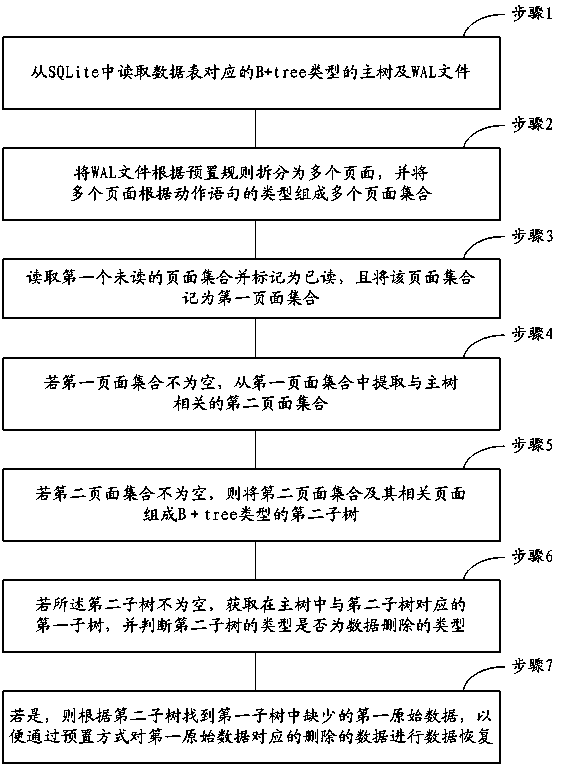
Method and device for recovering deleted data in SQLite
ActiveCN104376091ANon-destructiveGuaranteed non-destructiveSpecial data processing applicationsDatabase design/maintainanceOriginal dataDatabase
The invention provides a method and device for recovering deleted data in the SQLite. The method includes the steps that a B+tree type main tree and a WAL file which correspond to a data sheet are read from the SQLite; the WAL file is divided into a plurality of page sets according to imperative statements; a first unread page set is read and marked as read and is marked as a first page set; if the first page set is not empty, a second page set related to the main tree is extracted from the first page set; if the second page set is not empty, the second page set and related pages form a B+tree type second subtree; if the second subtree is not empty, a first subtree, corresponding to the second subtree, in the main tree is obtained, and whether the second subtree is in a data deleting type or not is judged; if the second subtree is in the data deleting type, first original data deficient in the first subtree are found according to the second subtree, and data recovering can be carried out on the deleted data corresponding to the first original data in a preset mode conveniently. By means of the method, the data recovery accuracy rate and the data recovery comprehensiveness can be improved.
Owner:XIAMEN MEIYA PICO INFORMATION
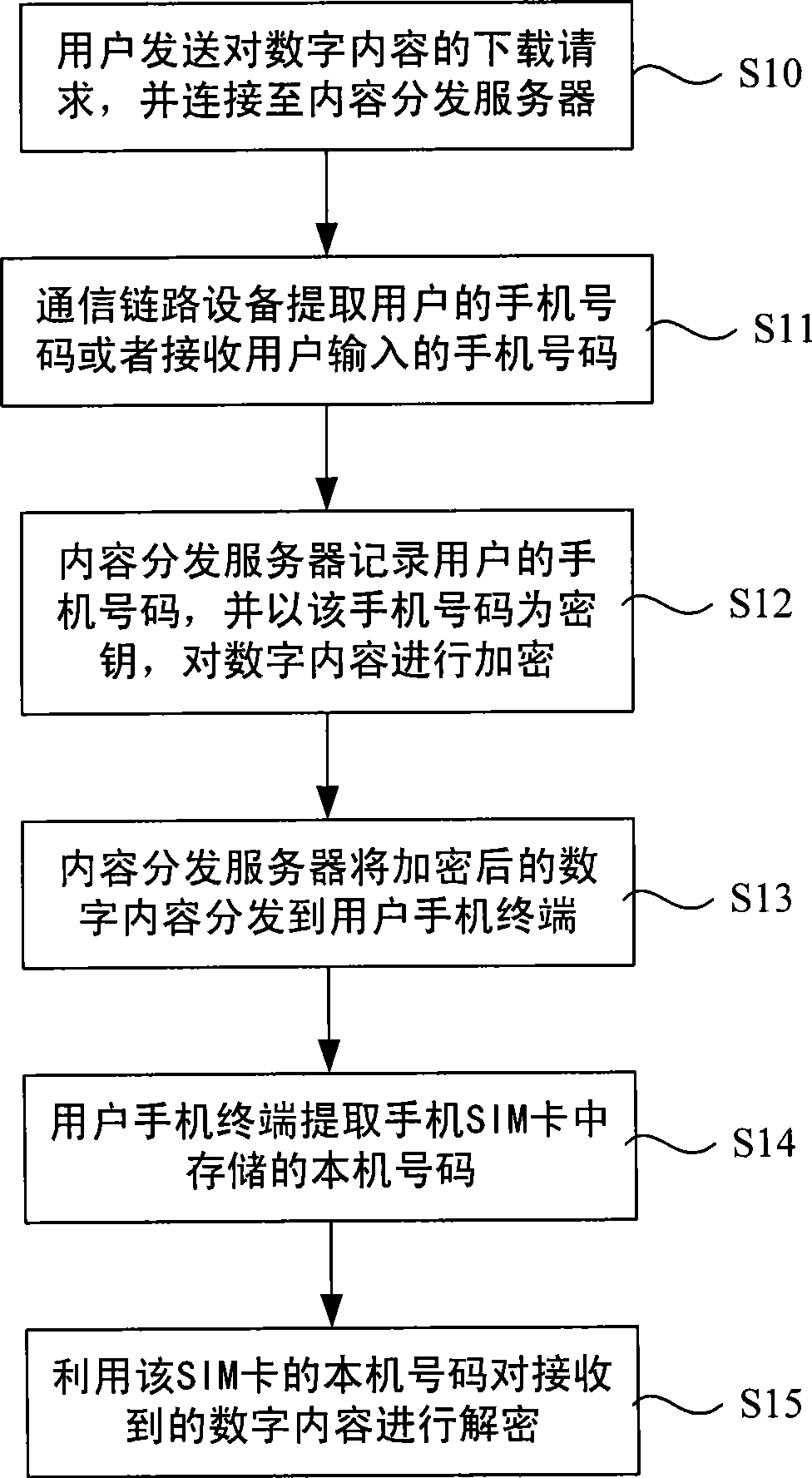
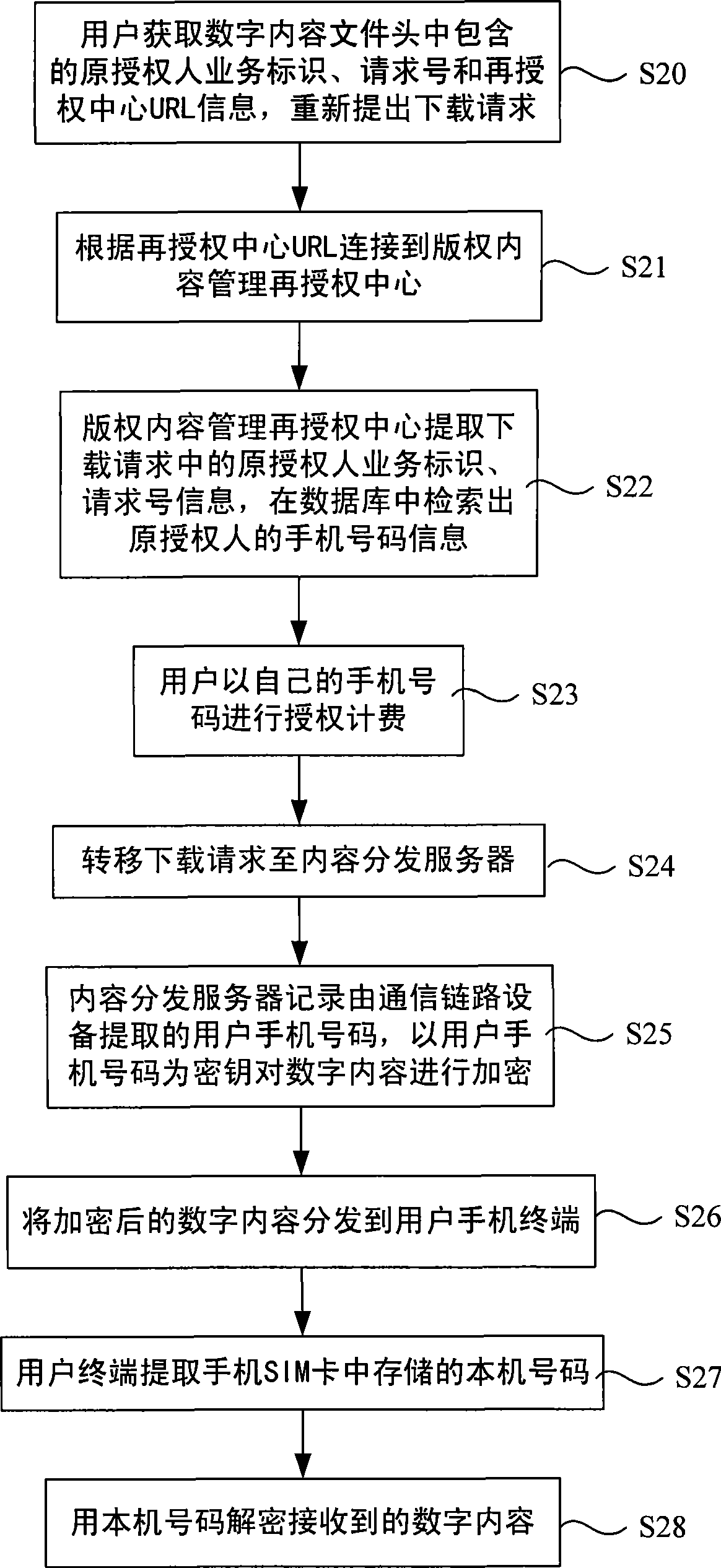
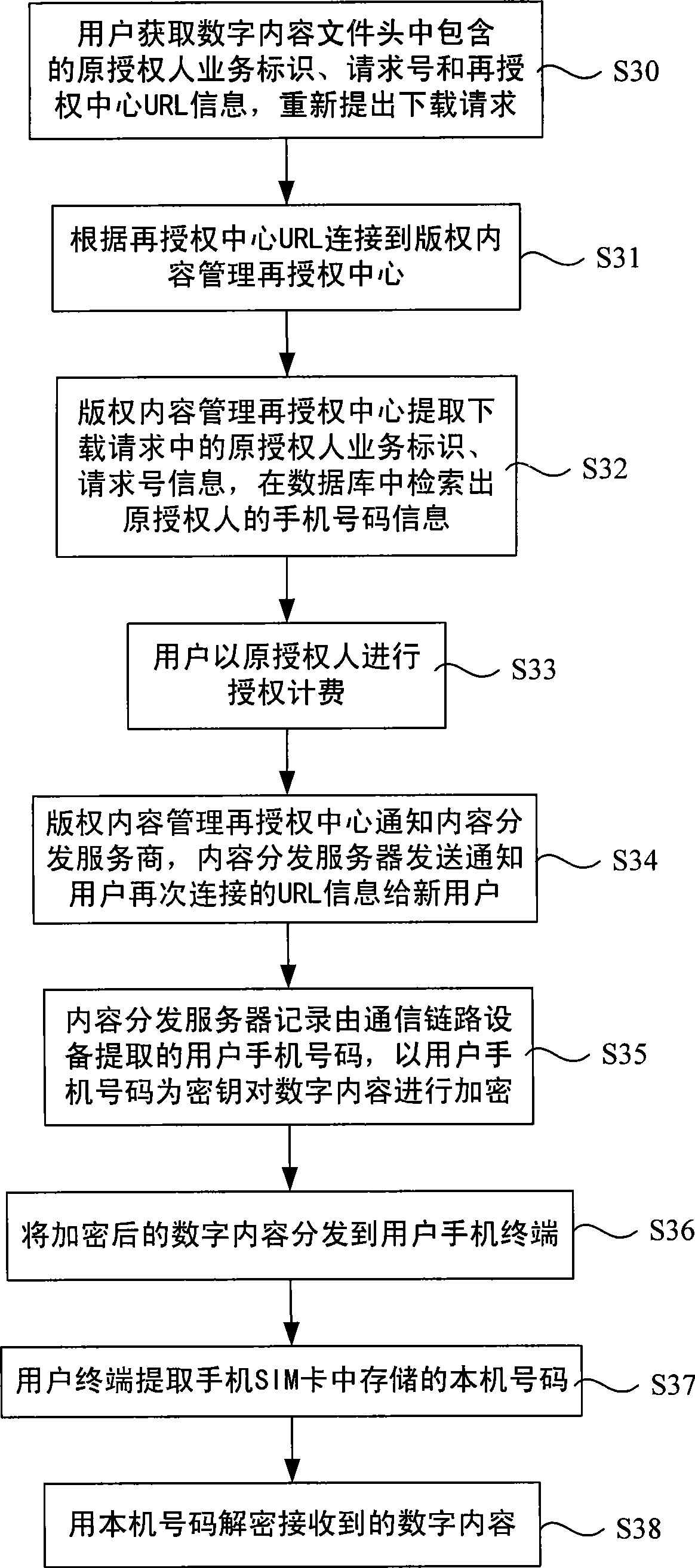
Method, server and deciphering device for protecting digital contents of mobile communication application
InactiveCN101466094AProtect playSettlement feeKey distribution for secure communicationSecurity arrangementContent distributionMobile Telephone Number
The invention discloses a digital content protection method, a content distribution server and a digital content decryption device in the mobile communication application. The technical proposal is as follows: the method comprises that: a. when users send a downloading request and the downloading request is connected with the content distribution server, a communication link device is used for extracting mobile phone numbers of the users or receiving the mobile phone numbers input by the users, and informs the content distribution server; b. the content distribution server takes the recorded mobile phone numbers as the key to encrypt the digital content, and distributes the encrypted digital content to the user mobile phone terminal; c. the user mobile phone terminal extracts the mobile phone number stored into the SIM card of the mobile phone, the mobile phone number is used for decrypting the received digital content, and the decryption can be successful when the mobile phone number is the same as the user mobile phone number at the time of encrypt. The method, the content distribution server and the digital content decryption device can be applied to the mobile communication field.
Owner:郭诺
Method for abstracting document data information appeared in newspaper
InactiveCN1912874AAssurance of Accuracy and CompletenessSimplify manual operationsSpecial data processing applicationsDocument preparationData information
This invention discloses a method for picking up data information of materials appearing in the newspaper including: picking up information of printed sheets and all manuscript regions based on the printed sheet information structure of typeset documents, picking up all manuscripts in the manuscript regions based on the manuscript information of said sheet files, picking up the association relation among manuscripts based on the position relations of these regions and merging the associated manuscripts based on said relation, sequencing them in terms of the importance of them and the region information, modifying and labeling the sheet information content and their information to get the data information of the materials appearing in the newspaper.
Owner:PEKING UNIV +1
Metal mold type gravity casting die for cast of tin bronze, and casting method
InactiveCN1915559ASolve the problem that is not suitable for gravity casting of metal moldResolve integrityMolten metal supplying equipmentsFoundry mouldsMetal moldTin bronze
A gravitationally casting metal mould set for casting the tin-bronze workpiece is composed of a metal mould consisting of upper and lower moulds, external sand core consisting of upper and lower cores and inlaid in the recess of metal mould, and internal sand core. Its casting method includes such steps as assembling the mould set, pouring molten tin-bronze, and cooling.
Owner:SHANGHAI TIANSHEN COPPER GRP CO LTD
Verifiable searchable encryption method
ActiveCN108039943AResolve integrityTroubleshoot result validation issuesKey distribution for secure communicationEncryption apparatus with shift registers/memoriesReverse indexEncryption
The invention discloses a verifiable searchable encryption method. The verifiable searchable encryption method comprises the steps that: U1, a client calculates a reverse index according to a file set, and calculates a set of key value pairs for each keyword in the reverse index; each set of key value pairs is inserted into an MPT tree structure; and the root hash of the MPT tree structure is calculated and stored; U2, the client uploads an initialized MPT tree to a server, and uploads updated key value pairs to the server when the file set is updated; U3, the client sends a challenge token tothe server, and receives a searching result and reference information used for verification returned by the server; U4, the client matches the sent challenge token with the reference information, andreconstructs the root hash of the MPT tree structure according to a matching result; and U5, the reconstructed root hash is compared with the root hash stored by the client. According to the searchable encryption method disclosed by the invention, the freshness attack and the integrity attack due to the fact that the server is dishonest can be verified at the same time; the application range is relatively wide; and the overhead is low.
Owner:SHENZHEN GRADUATE SCHOOL TSINGHUA UNIV
Automatic welding method of flow production line for hydraulic support grid box type structure members
ActiveCN102441720ASolve the deformationResolve integrityWelding accessoriesFlat jointProduction line
The invention relates to the field of welding fabrication of hydraulic support structure members, particularly to an automatic welding method of a flow production line for hydraulic support grid box type structure members, which solves the problem that the traditional manual welding method cannot guarantee the welding forming quality and workpieces cannot be completely and automatically welded due to deformation caused by a unit type automatic robot due to thick plate welding thermal cycle. The automatic welding method comprises the following concrete steps of: cutting and forming the grid box type structure members; automatically counting and assembling bottom plates and main rib plates; preheating the counted and assembled bottom plates and main rib plates; automatically welding the main rib plates; automatically counting and assembling separation plates; preheating the counted and assembled separation plates; automatically welding the flat joints of the separation plates; automatically welding the left vertical joints of the separation plates; automatically welding the right vertical joints of the separation plates; counting and assembling function parts; counting and assembling cover plates; automatically welding the flat joints of the cover plates; automatically welding the arc joints of the cover plates; and circulating the above steps. The method provided by the invention is reasonable and simple in process, strong in operability and high production efficiency, and can guarantee the welding quality.
Owner:SHANXI PINGYANG IND MACHINERY
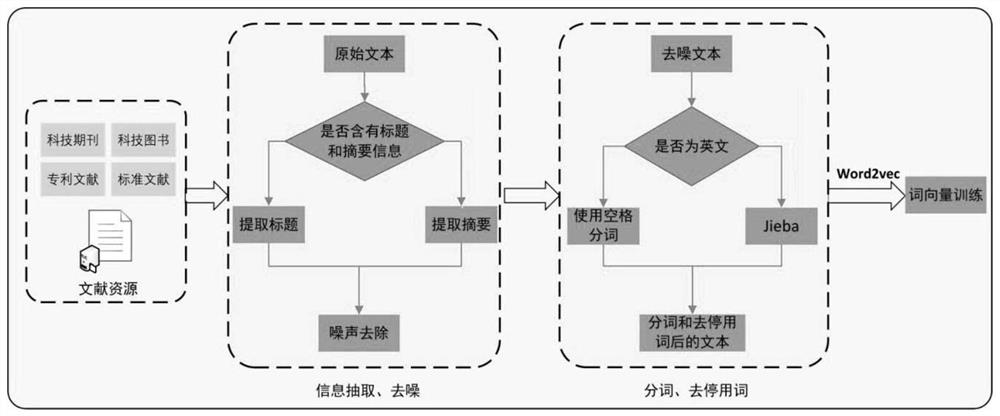
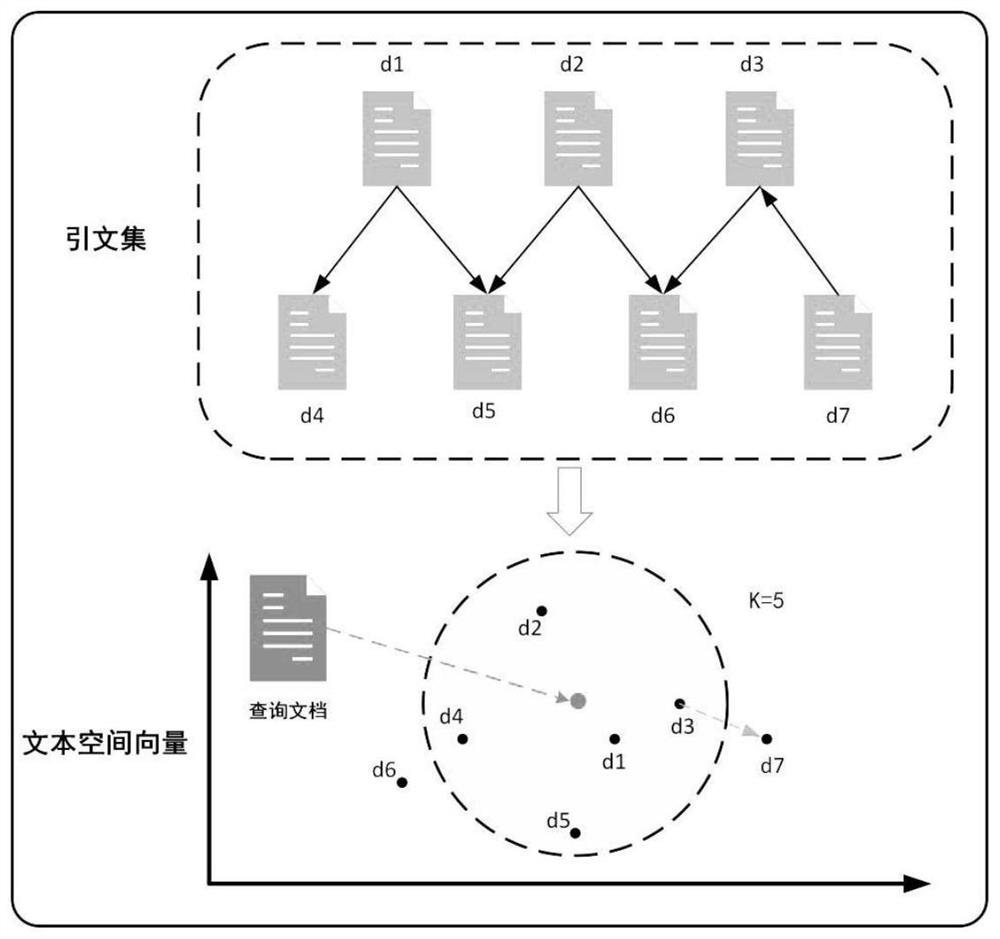
Scientific and technical literature quotation recommendation method based on deep learning
ActiveCN113239181ASolve semantic understandingResolve integrityData processing applicationsSemantic analysisSemantic vectorLanguage understanding
The invention discloses a scientific and technical literature quotation recommendation method based on deep learning. The method comprises the following steps: sequentially performing information extraction, noise removal, word list index construction and vectorization processing on text data; firstly, performing semantic vectorization representation on a to-be-matched text through Bi-LSTM, then performing interactive coding on the text by adopting an Attention mechanism, and performing feature extraction on interactive information of the text through a multilayer CNN network so as to obtain final matching degree information of the text; in the first stage, forming a related quotation recommendation set through vector space similarity of texts, and in the second stage, using a text reasoning matching method for carrying out language understanding on candidate sets so as to obtain an accurate relevancy ranking list. According to the method, the problems of semantic comprehension, content integrity and accuracy in existing text reasoning matching can be solved, high-quality semantic features and a digital text input form are provided, and feature extraction is performed on interactive information of the text, so that final matching degree information of the text is obtained.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
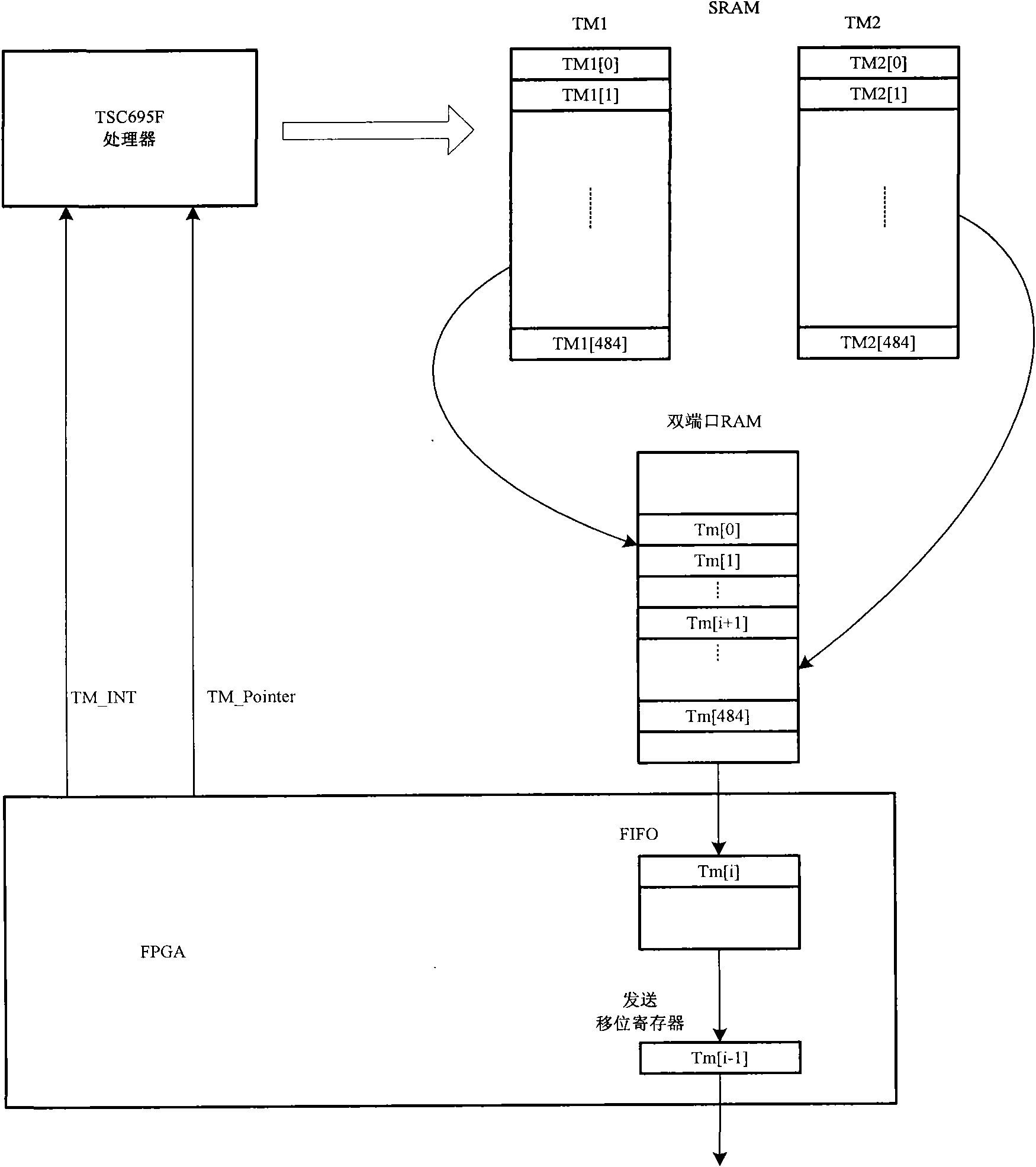
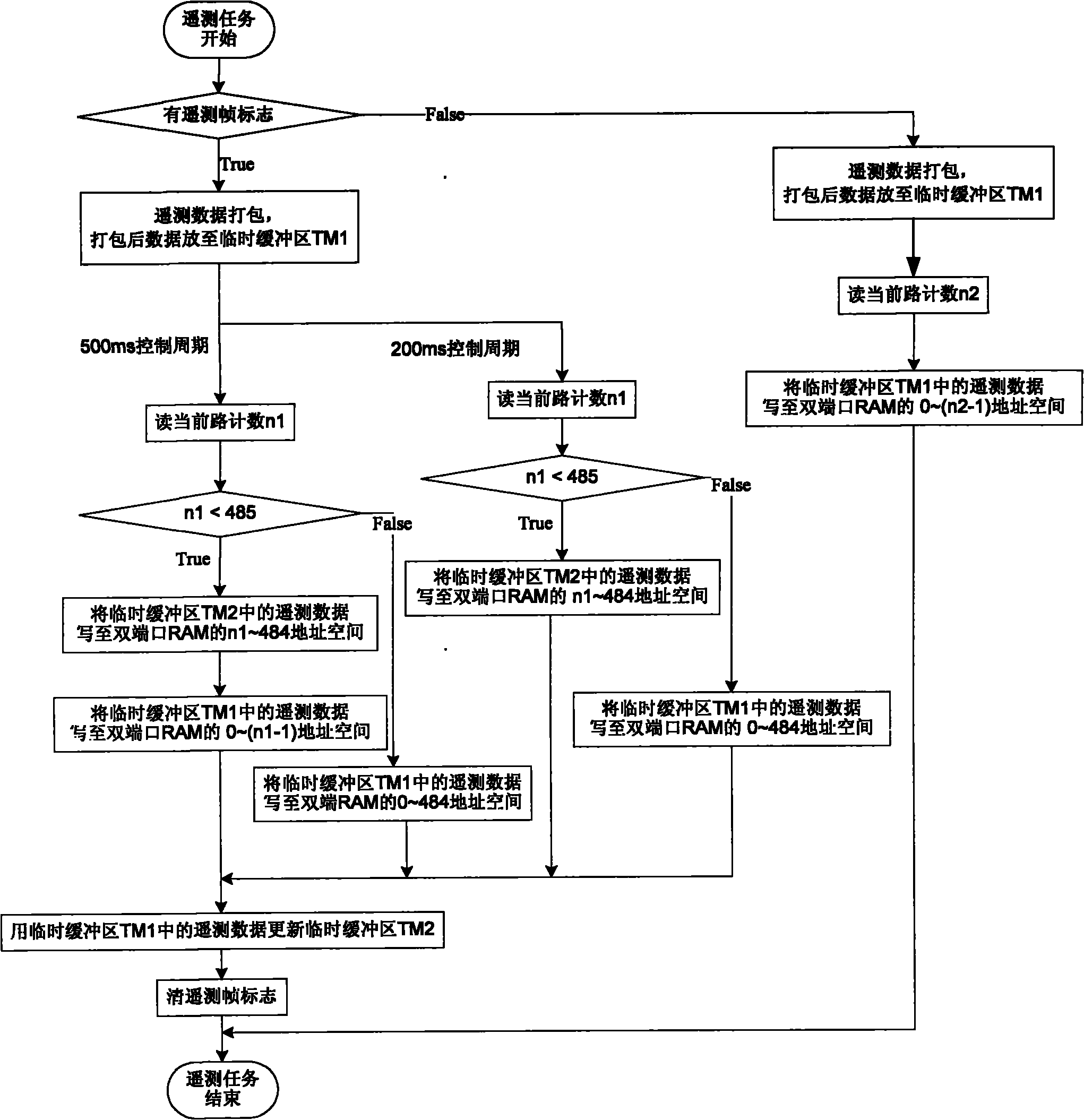
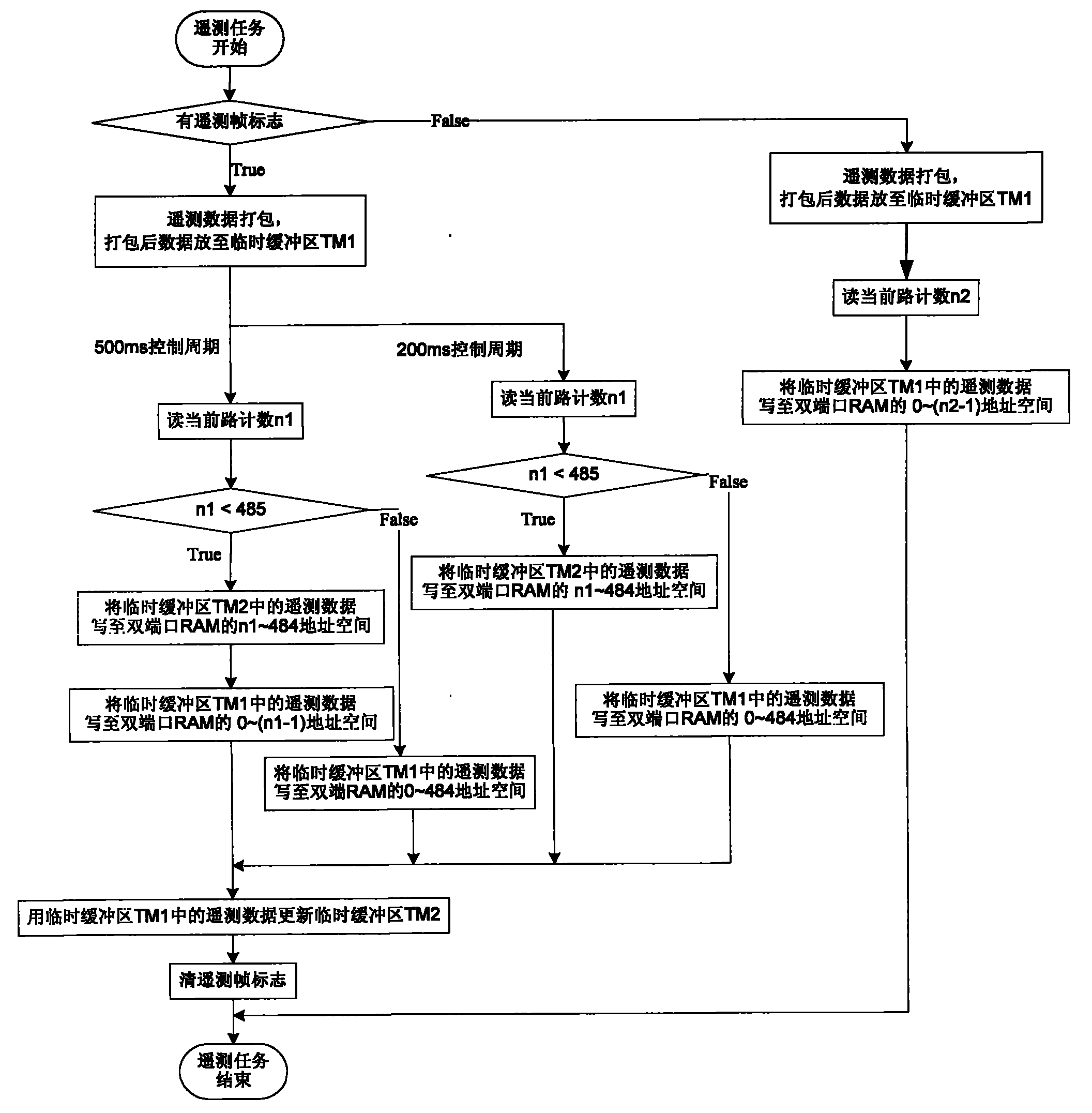
Method for realizing receiving completeness of telemeter data
ActiveCN102075291AIntegrity guaranteedAvoid completenessError preventionData switching networksStatic random-access memoryAsynchronous communication
The invention discloses a method for realizing the receiving completeness of telemeter data, which is characterized in that: a telemeter frame marker bit TM_INT is arranged in a telemeter interrupt service routine, so the interrupt processing time is shorter, the marker TM_INT is inquired in the telemeter interrupt service routine, telemeter data package is proceeded, the telemeter data which is packaged at two adjacent times is stored in two temporary buffering areas which are arranged in Static Random Access Memory (SRAM), then the TM-POINT is counted according to the current telemeter path, the packaged telemeter data stored in the two temporary buffering areas are filled to a double-port random access memory (RAM), so the data completeness is guaranteed, and since the interrupt processing time is very short, the interrupt contradiction problem can be reduced, and the influence on the asynchronous communication of parts can be avoided; and meanwhile, relative to a relevant interrupt protection way, the method avoids the operation for frequently switching on and switching off the interrupt, so the complication of the system and the software time sequence can be reduced, and the completeness problem of the telemeter data can be solved.
Owner:BEIJING INST OF CONTROL ENG
Multi-view three-dimensional measurement system and method
ActiveCN111750806ASolve the problem of low coincidenceSolve problems that cannot be effectively rebuiltImage enhancementImage analysisPoint cloudBeam splitting
The invention discloses a multi-view three-dimensional measurement system and method. The system comprises a projector, a peripheral camera, a beam splitting plate and a color camera; the peripheral camera adopts an inclined image plane structure to meet the depth-of-field requirement; the beam splitting plate is used for imaging of the color camera; and the color camera is used for restoring object color information. The calibration measurement method comprises the steps of establishing an inclined image surface imaging model for surrounding cameras, shooting a calibration plate by using thecameras, extracting coordinates of feature points, and obtaining internal and external parameters of the cameras by using a Zhang Zhengyou calibration method; calibrating internal and external parameters of the projector by adopting a pseudo-camera method principle; calibrating a relationship between each camera coordinate system and a projector coordinate system through a binocular three-dimensional calibration principle to realize system calibration; and realizing multi-view point cloud fusion by establishing a world coordinate system on the projector coordinate system. The system has the advantages of being high in measurement precision, high in speed, easy and convenient to operate and capable of conducting three-dimensional measurement on a high-reflectivity object.
Owner:XI AN JIAOTONG UNIV
PI solution method based on IC package PCB co-design
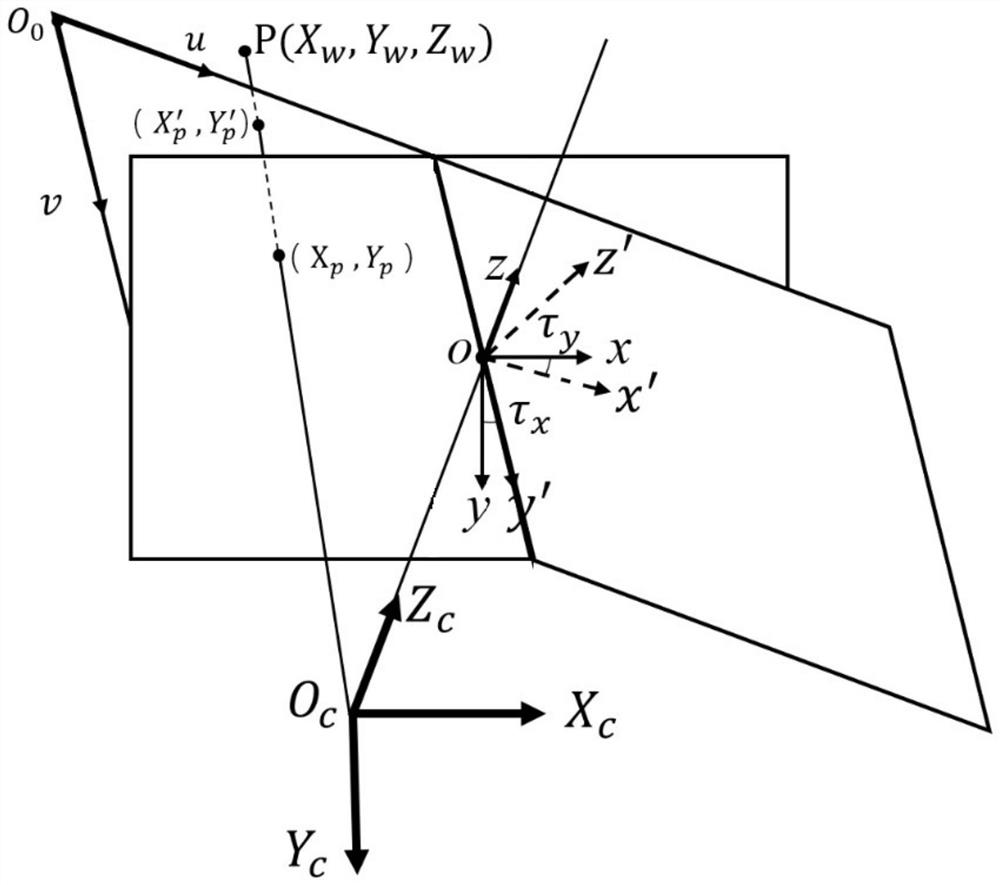
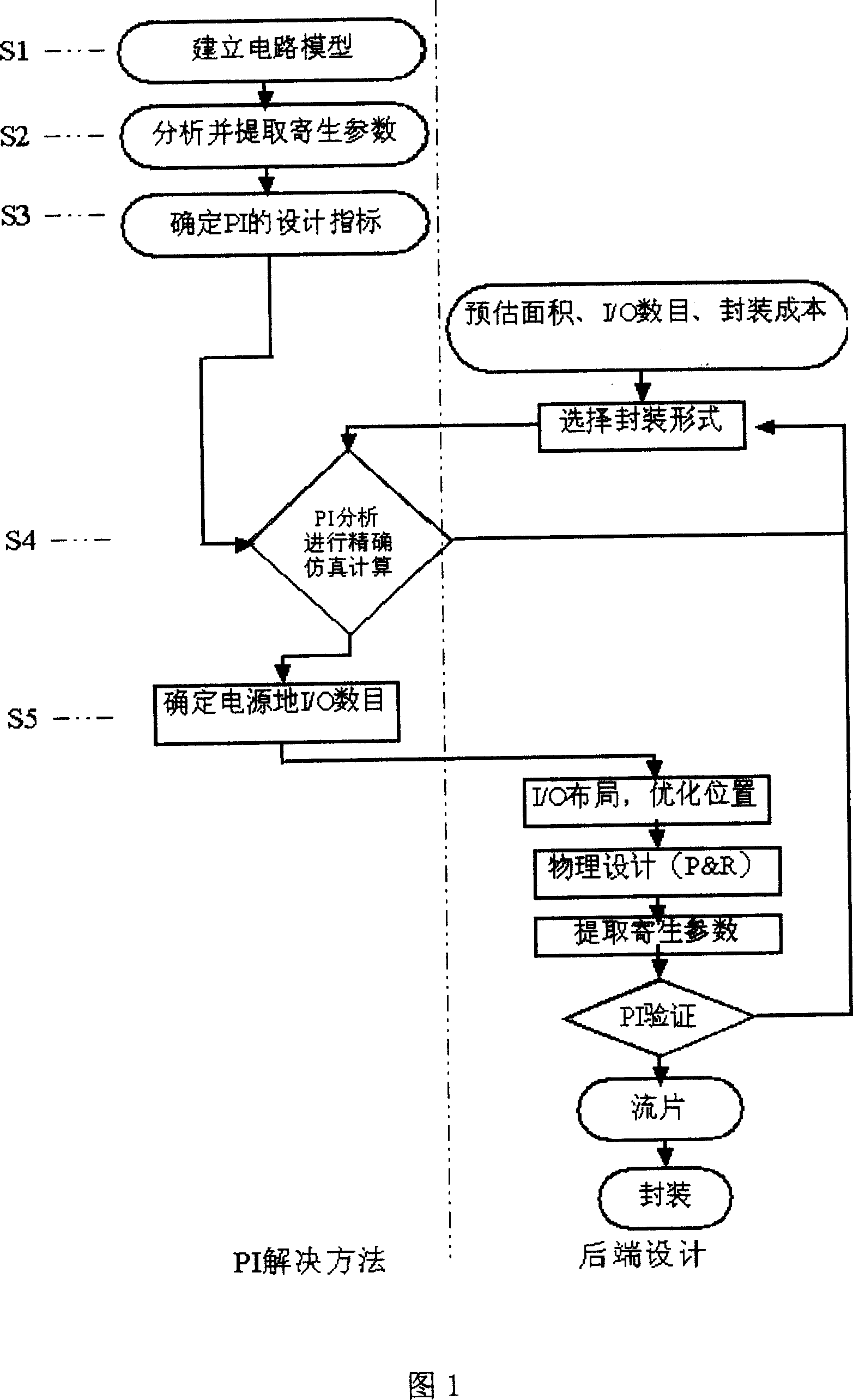
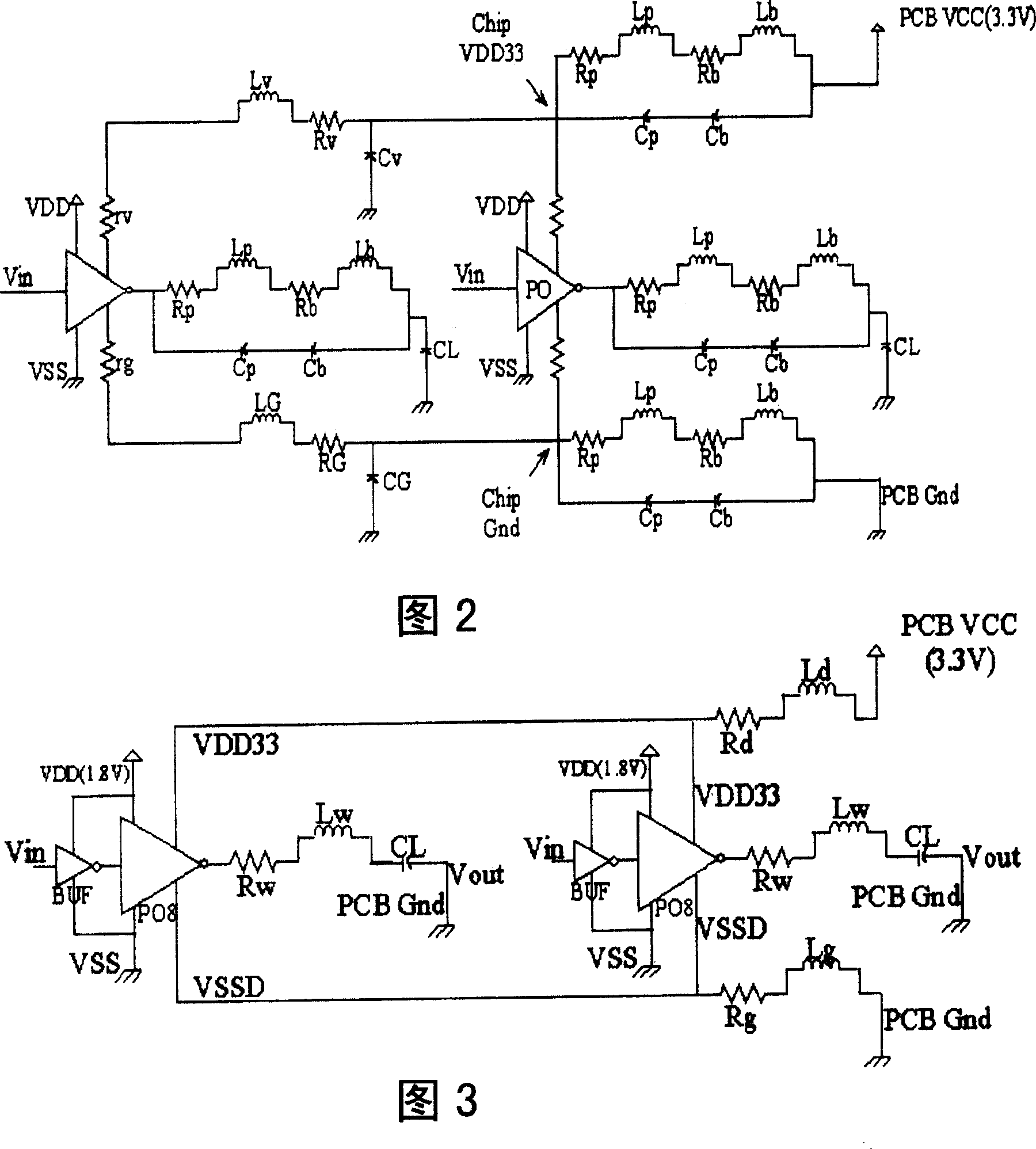
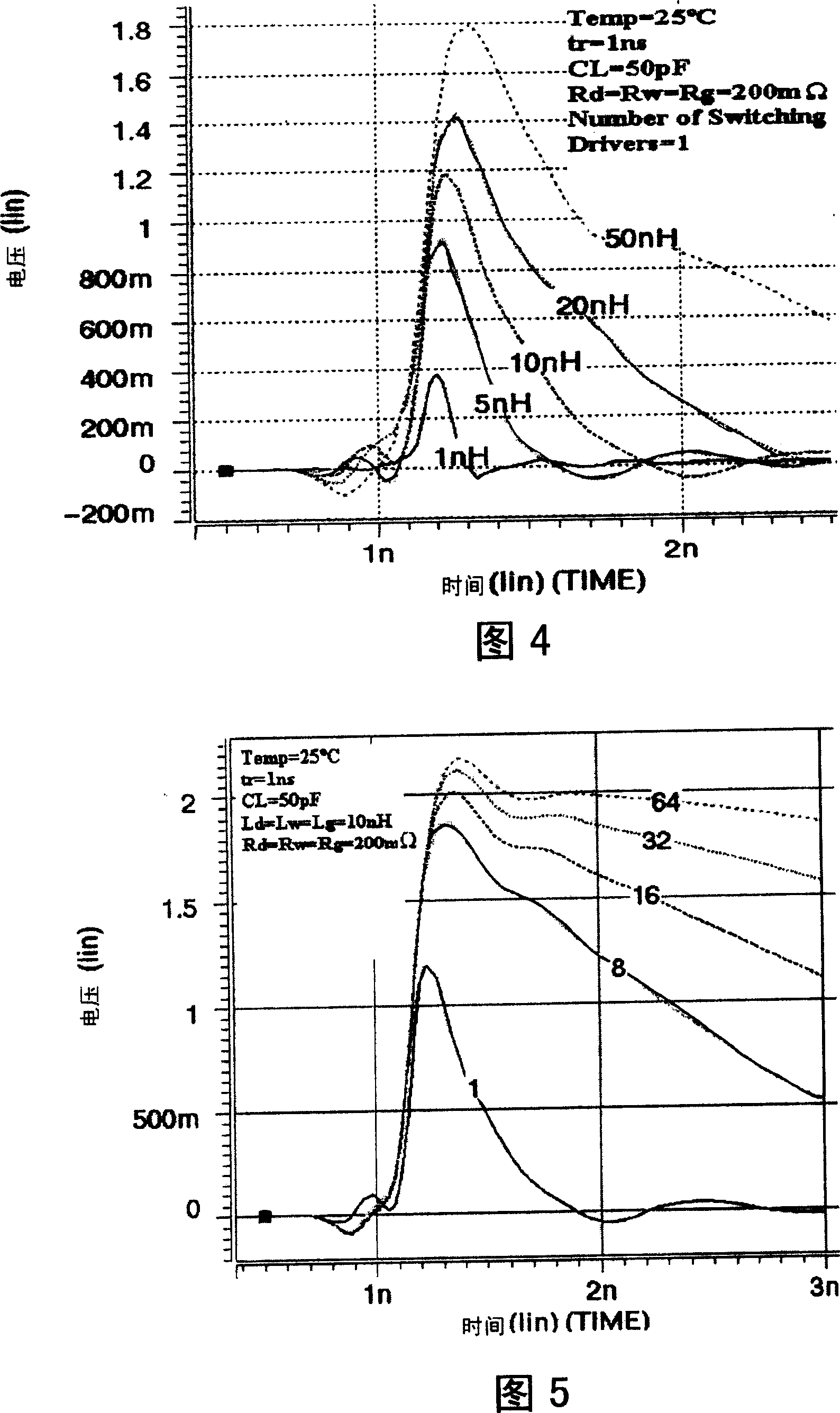
ActiveCN101071449AFit for integrity issuesResolve integritySpecial data processing applicationsPower integrityCircuit models
The invention relates to the field of very large scale integrated (VLSI) circuit technique, especially a PI solving method for IC-package-PCB cooperative design for solving power supply integrity problem in back-end design, comprising: 1) building a circuit model suitable for VLSI PI analysis; 2) analyzing and extracting parasitical parameters corresponding to the circuit mode; 3) determining design indexes in the PI design; 4) utilizing EDA tool and owned algorithm model to make accurate simulation and calculation; 5) on the premise of considering power supply integrity, according to the PI design indexes and simulated results, quickly determining a proper number of I / Os of power supply.
Owner:INST OF MICROELECTRONICS CHINESE ACAD OF SCI
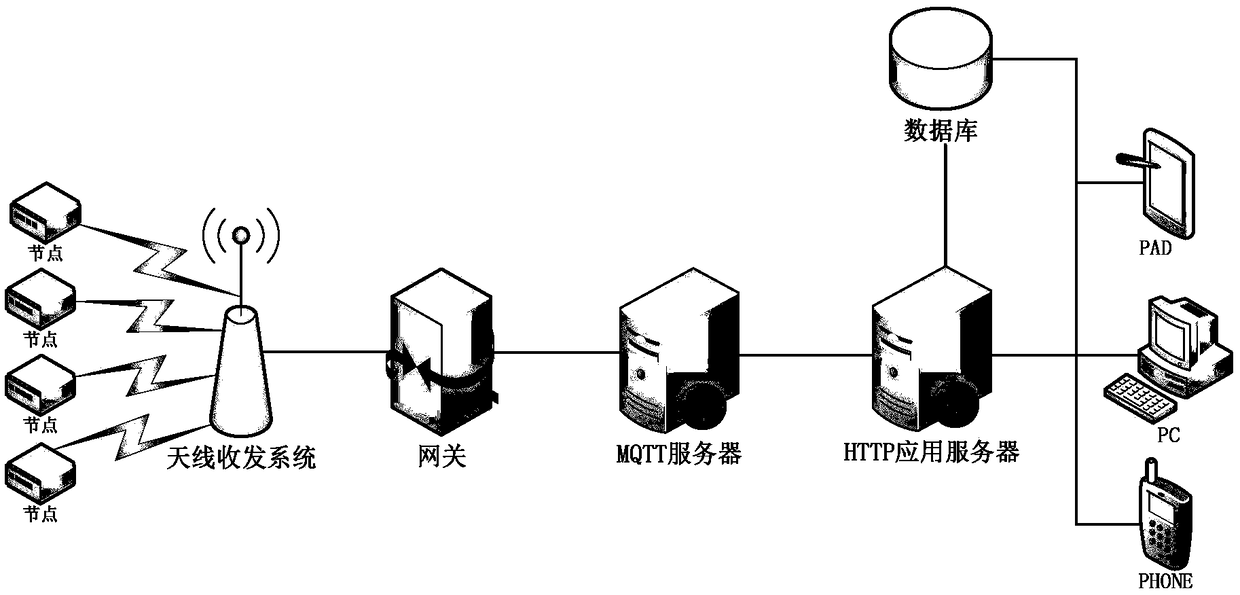
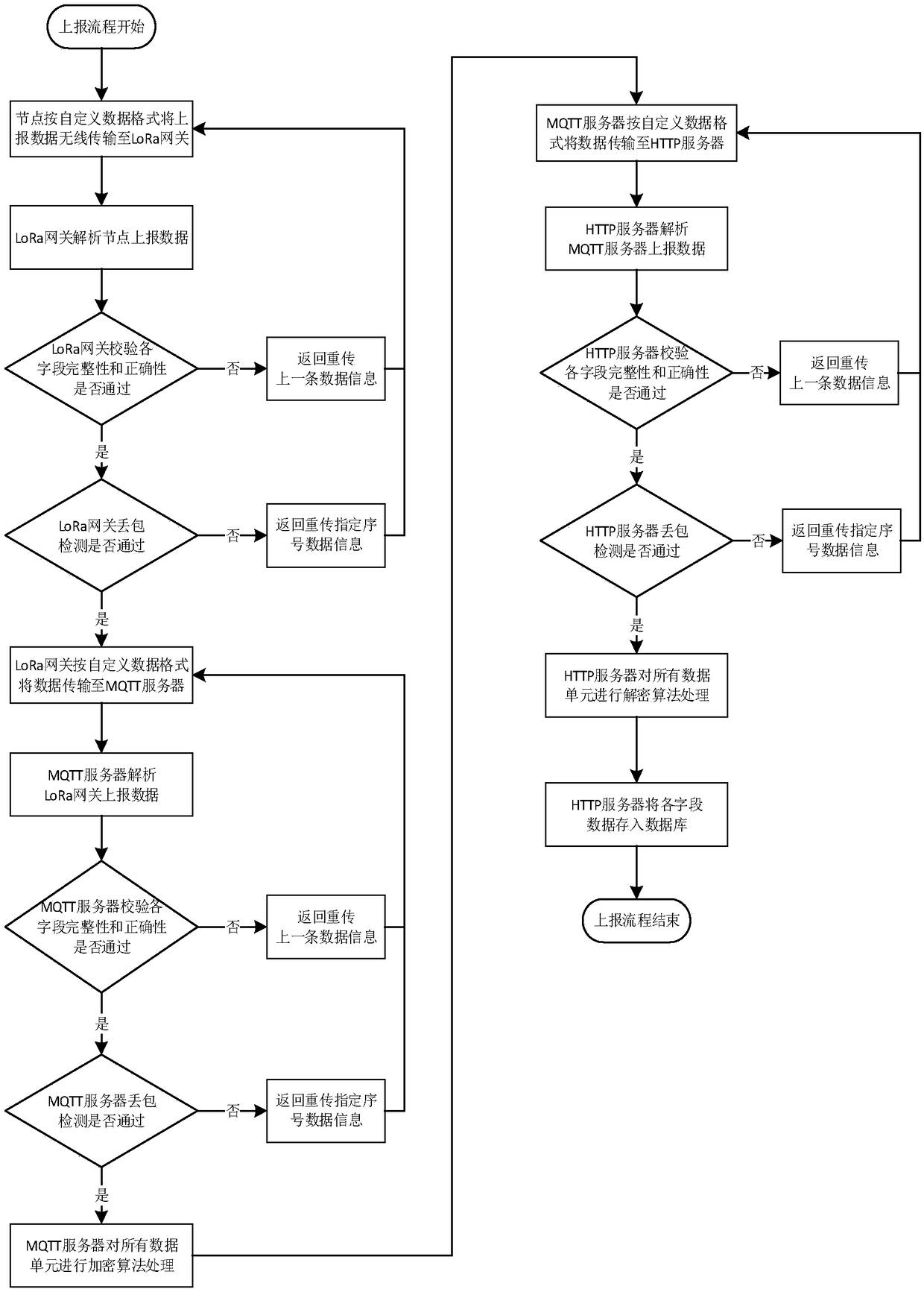
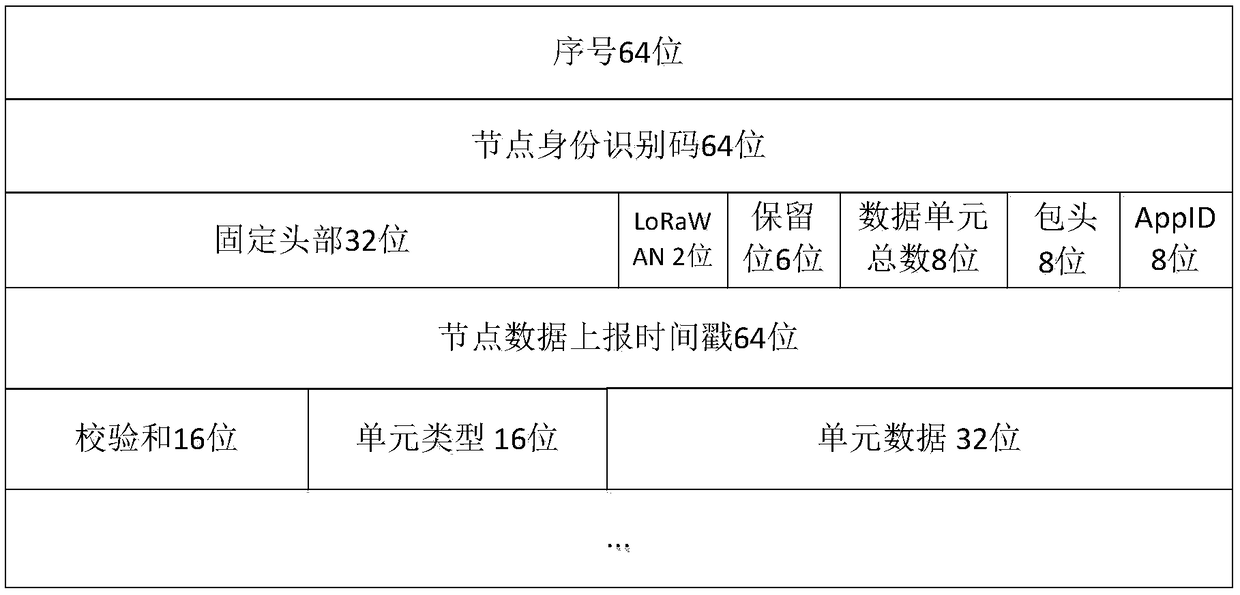
A data reporting and instruction sending method based on LoRa Internet of Things
InactiveCN108989455ASolve the errorResolve integrityTransmission systemsData switching networksPacket lossOriginal data
A method for node data reporting and instruction issuing based on LoRa Internet of Things comprises the following steps: step S1-1) the LoRa network node reports the data packet to the LoRa gateway according to the self-defined data format; Step S1-2) the LoRa gateway analyzes the data packet according to the self-defined data format, carries out integrity and correctness verification of each field and packet loss detection, and after the checksum detection is passed, a 64-bit LoRa gateway identification code is added into the data packet and sent to the MQTT server through the MQTT protocol;Step S1-3) the MQTT serv parses the data packet according to the self-defined data format, after passing the check and packet loss detection, encrypts all data units of the data packets, and then sends the data packets to the HTTP server through the MQTT protocol; Step S1-4) the HTTP server parses the data packet according to the self-defined data format, after the checksum packet loss detection is passed, decrypts all data units of the data packet, obtains the original data units, and then stores the data of each field of the data packet into the database.
Owner:NANHAI RES STATION OF INST OF ACOUSTICS CHINESE ACADEMY OF SCI
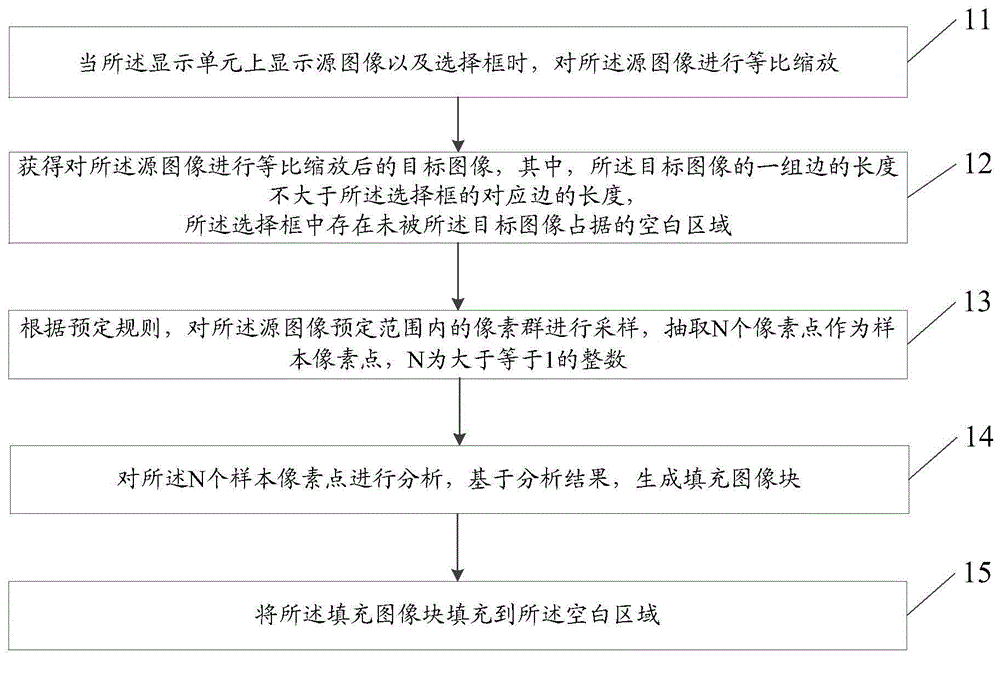
Information processing method and electronic equipment
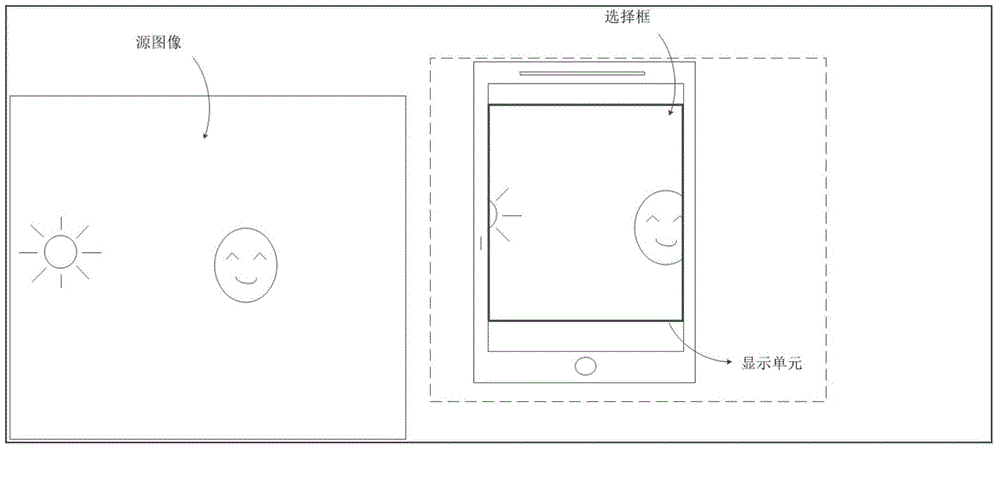
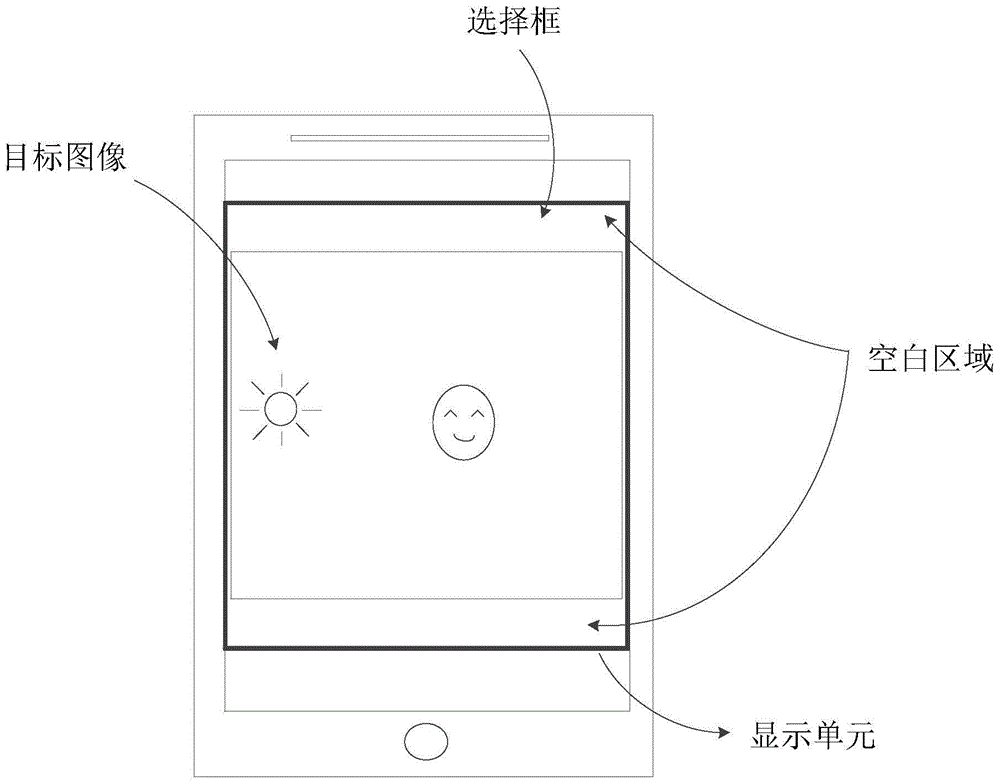
ActiveCN104461439AGuaranteed no distortionUndistortedGeometric image transformationDigital output to display deviceInformation processingComputer vision
The invention provides an information processing method and electronic equipment. The electronic equipment is provided with a display unit. The information processing method comprises the steps that when a source image or a selection frame are displayed on a display unit, the source image is zoomed; a target image is obtained after the source image is zoomed, wherein the length of one set of edges of the target image is not larger than that of the corresponding edge of the selection frame, and the blank area not occupied by the target image exists in the selection frame; according to preset rules, pixel groups in the preset range of the source image are sampled, and N pixel points are extracted as sample pixel points, wherein N is an integer larger than or equal to 1; the N sample pixel points are analyzed, and filling image blocks are formed based on the analysis result; the blank area is filled with the filling image blocks.
Owner:LENOVO (BEIJING) CO LTD
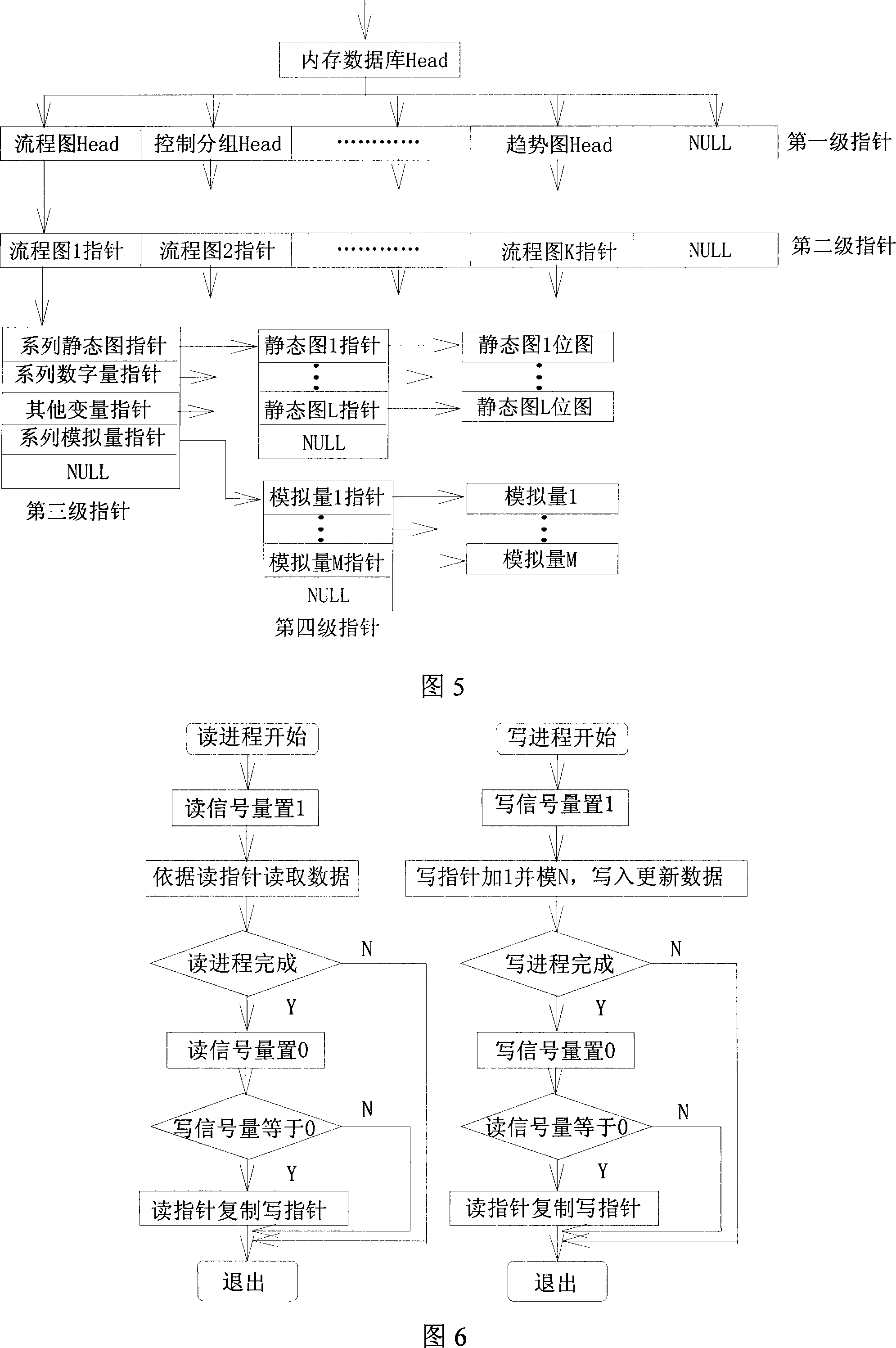
Synchronization process of total distributed control system operator stations EMS memory database structure storage
InactiveCN101158871AResolve integritySolving Consistency IssuesTotal factory controlProgramme total factory controlData integrityConsistency problem
The invention discloses a synchronization method of memory database structure storage of a distributed control system operator station. An operation configuration file is stored inside the operator station built-in Flash memory. The operation configuration file is taken as a data dictionary and establishes a memory database inside the operator station share RAM memory, the memory database structure is stored separately with the data and is monitored on a real-time monitoring software platform. By adopting a multi-level pointer storage structure, the memory database relational tuple is expressed as a pointer set pointing to the actual data. Aiming to the single update feature of the operator station, the invention adopts the read-write double-pointer and combines the read-write signal amount technology to realize the synchronization of the memory database. The invention effectively solves the data integrity and consistency problems caused by the data confliction when reading and writing task of the operator station; the multi-pointer storage structure has the high efficiency of direct address visit, is suitable for operator station memory database variable word length field special requirements and the industrial field data are only needed to be stored once in the memory database.
Owner:ZHEJIANG UNIV
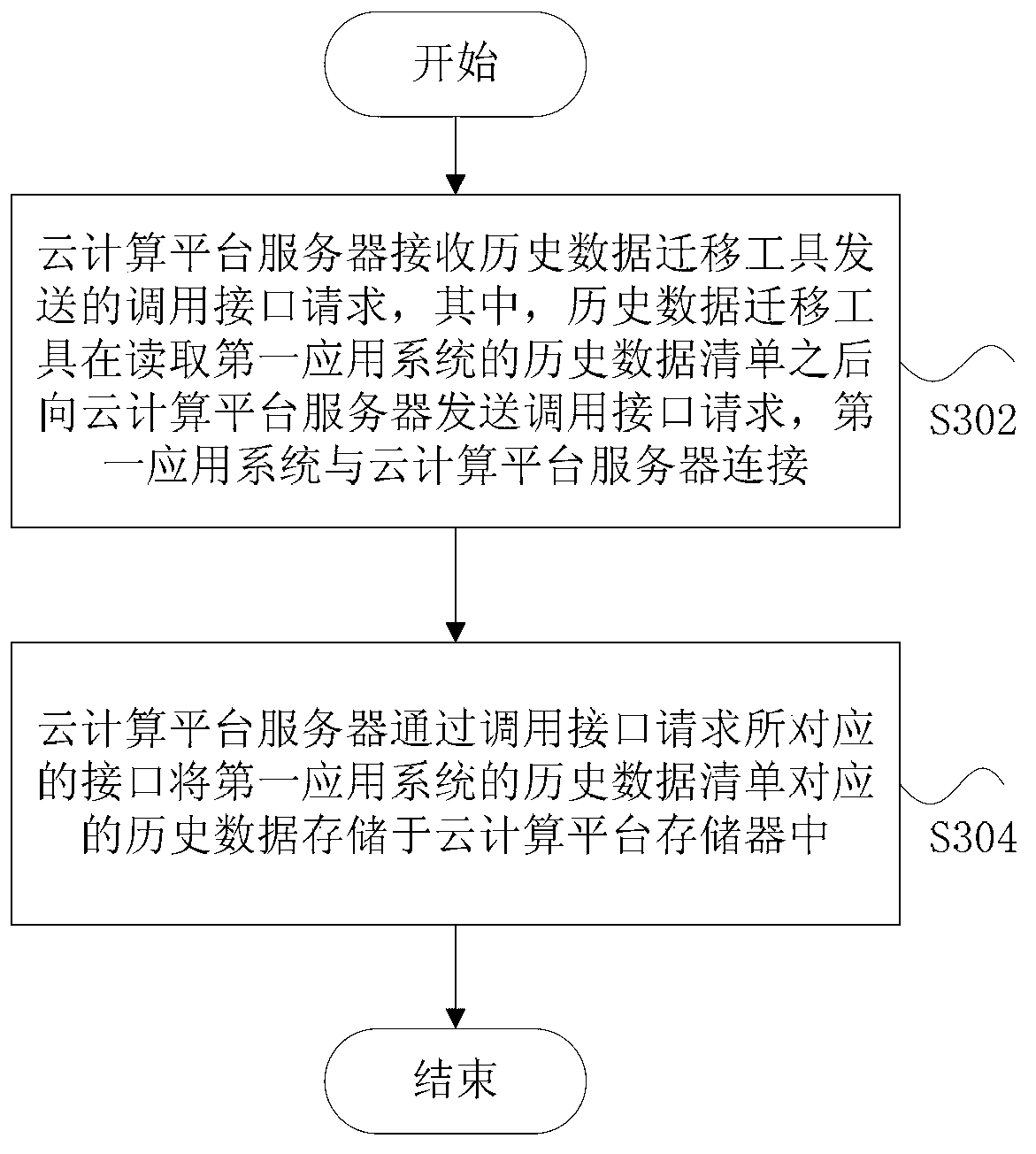
Historical data migration method and device
ActiveCN102799485AIntegrity guaranteedResolve integrityProgram initiation/switchingTransmissionCloud computingData migration
The invention discloses a historical data migration method and a device. The historical data migration method comprises the steps as follows: a cloud computing platform server receives a call interface request sent by a historical data migration tool, wherein the historical data migration tool sends the call interface request to the cloud computing platform server after reading the historical data list of a first application system, and the first application system is connected with the cloud computing platform server; and the cloud computing platform server stores the historical data corresponding to the historical data list of the first application system therein through an interface corresponding to the call interface request. By using the historical data migration method and device provided in the invention, the migration of historical unstructured data can be carried out completely, safety and quickly.
Owner:BEIJING FOREVER TECH
A fusion method and a fusion system of high dynamic range images
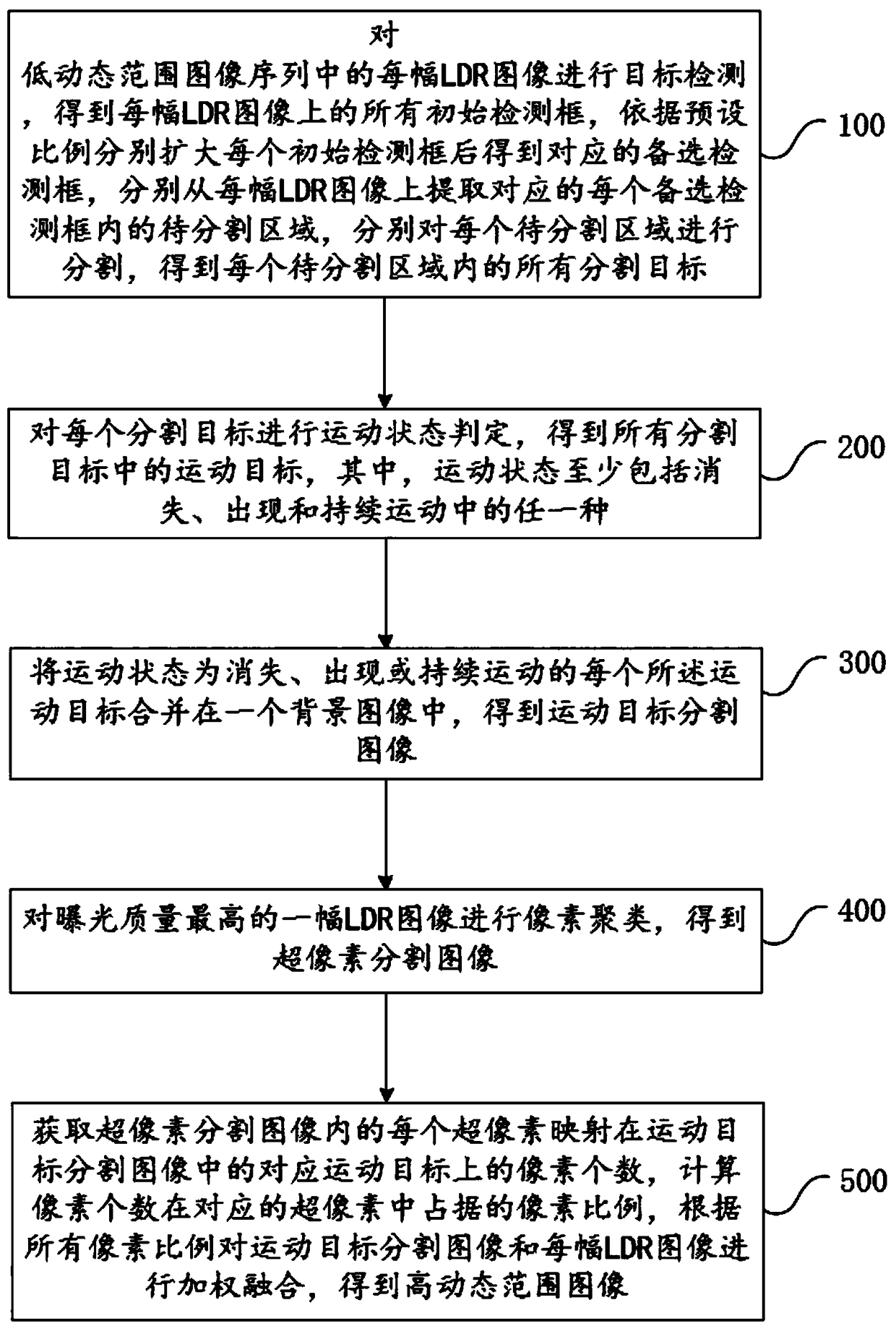
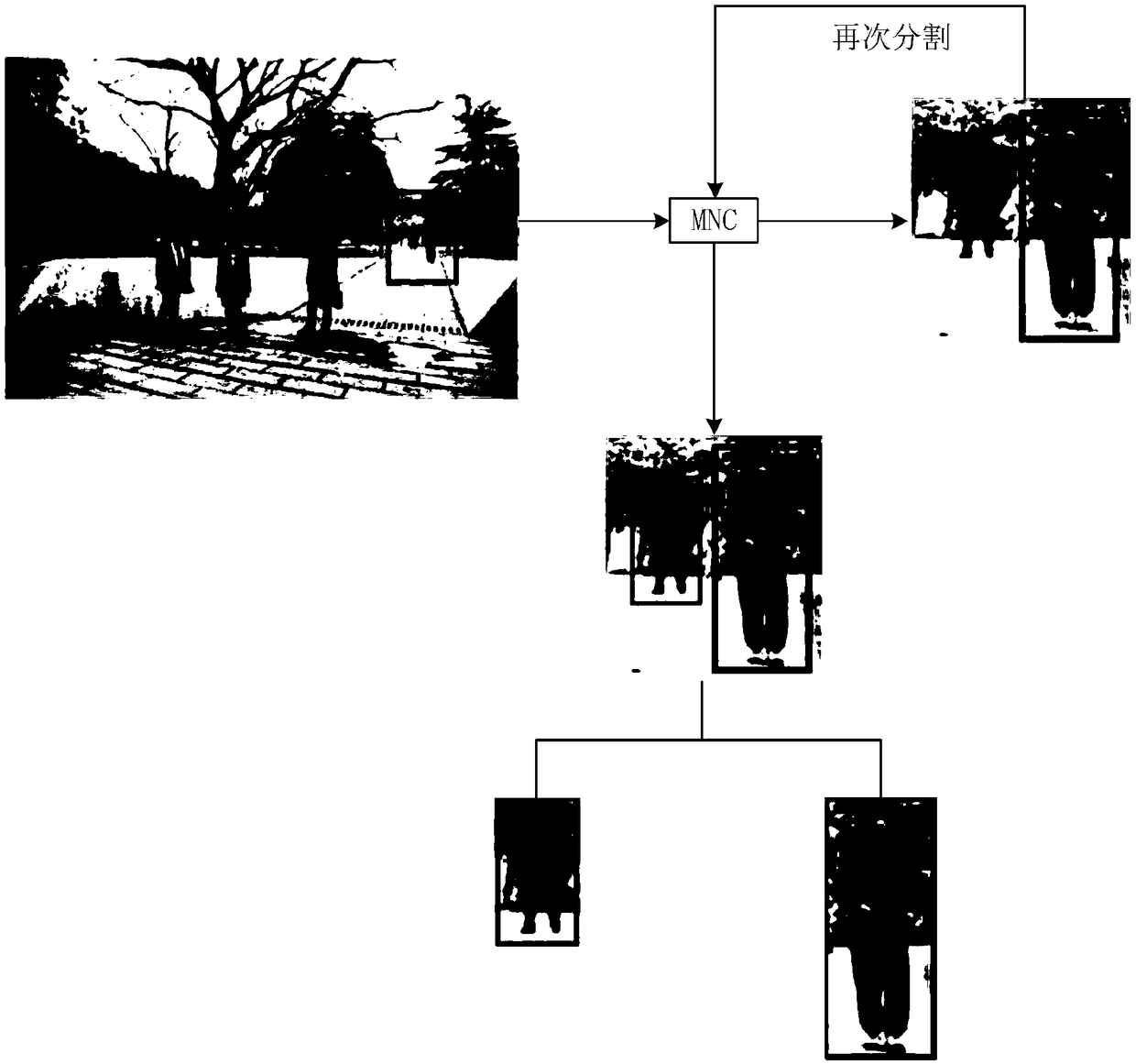
InactiveCN109360163ARaise the ratioTarget details are clearImage enhancementImage analysisSuperpixel segmentationImage sequence
The invention relates to a fusion method and a fusion system of high dynamic range images. The method comprises the following steps of: performing target detection on each LDR image in a low dynamic range image sequence to obtain an initial detection frame, expanding the initial detection frame according to a preset proportion, extracting a region to be segmented in an alternative detection framefrom the LDR image, and segmenting the region to be segmented to obtain a segmented target; The moving state of the segmented object is judged, and the moving object is merged into a background imageto obtain the segmented image of the moving object. Pixel clustering is performed on the LDR image with the highest exposure quality, a super pixel segmentation image is acquired, and the moving object segmentation image and each LDR image are weighted and fused according to the number of pixels of each super pixel mapped on the moving object in the moving object segmentation image to obtain a high dynamic range image. The invention improves the accuracy of moving object detection and judgment, and makes the moving object in the high dynamic range image clearer.
Owner:SHENZHEN JIMUYIDA TECH CO LTD
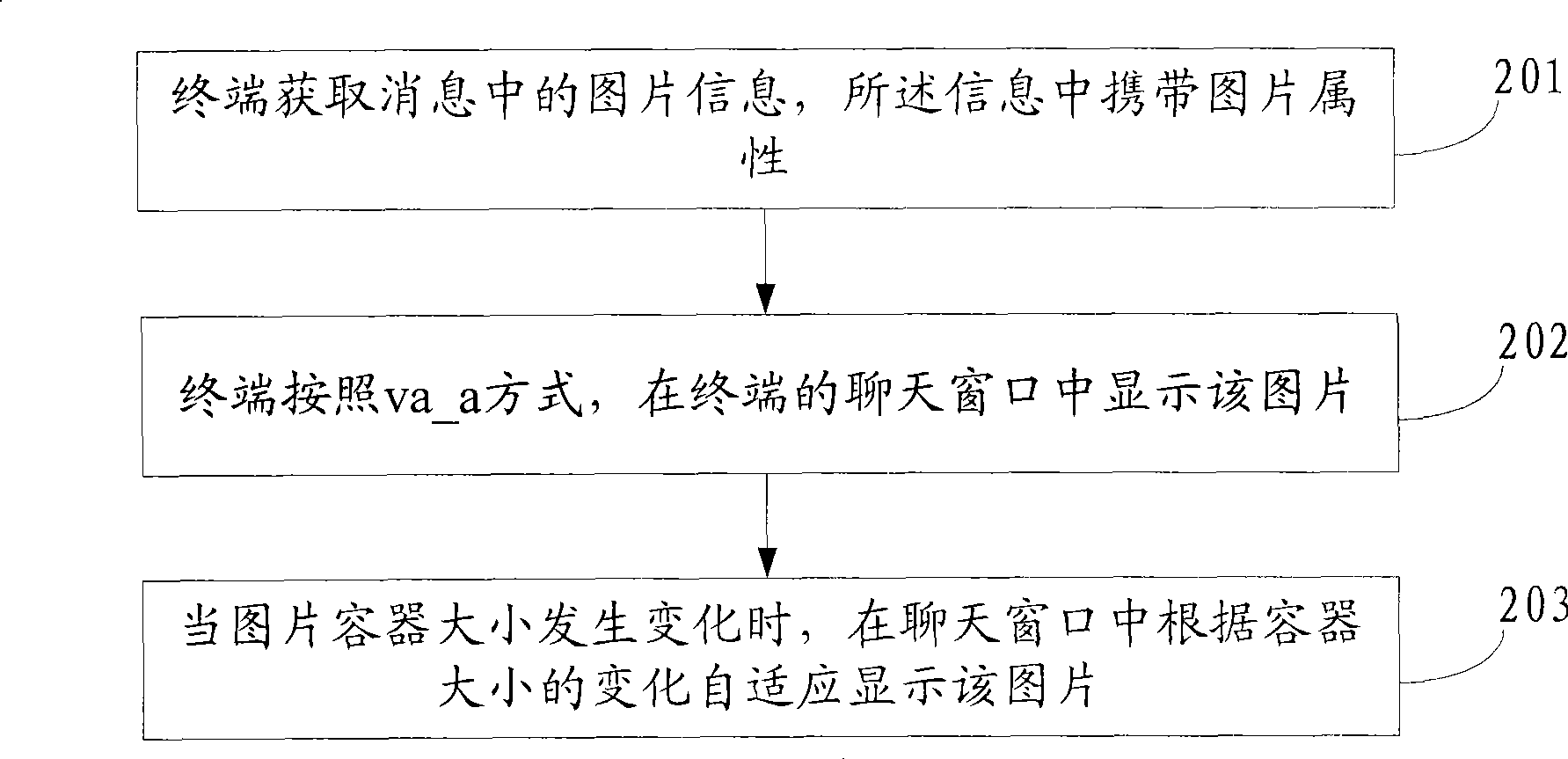
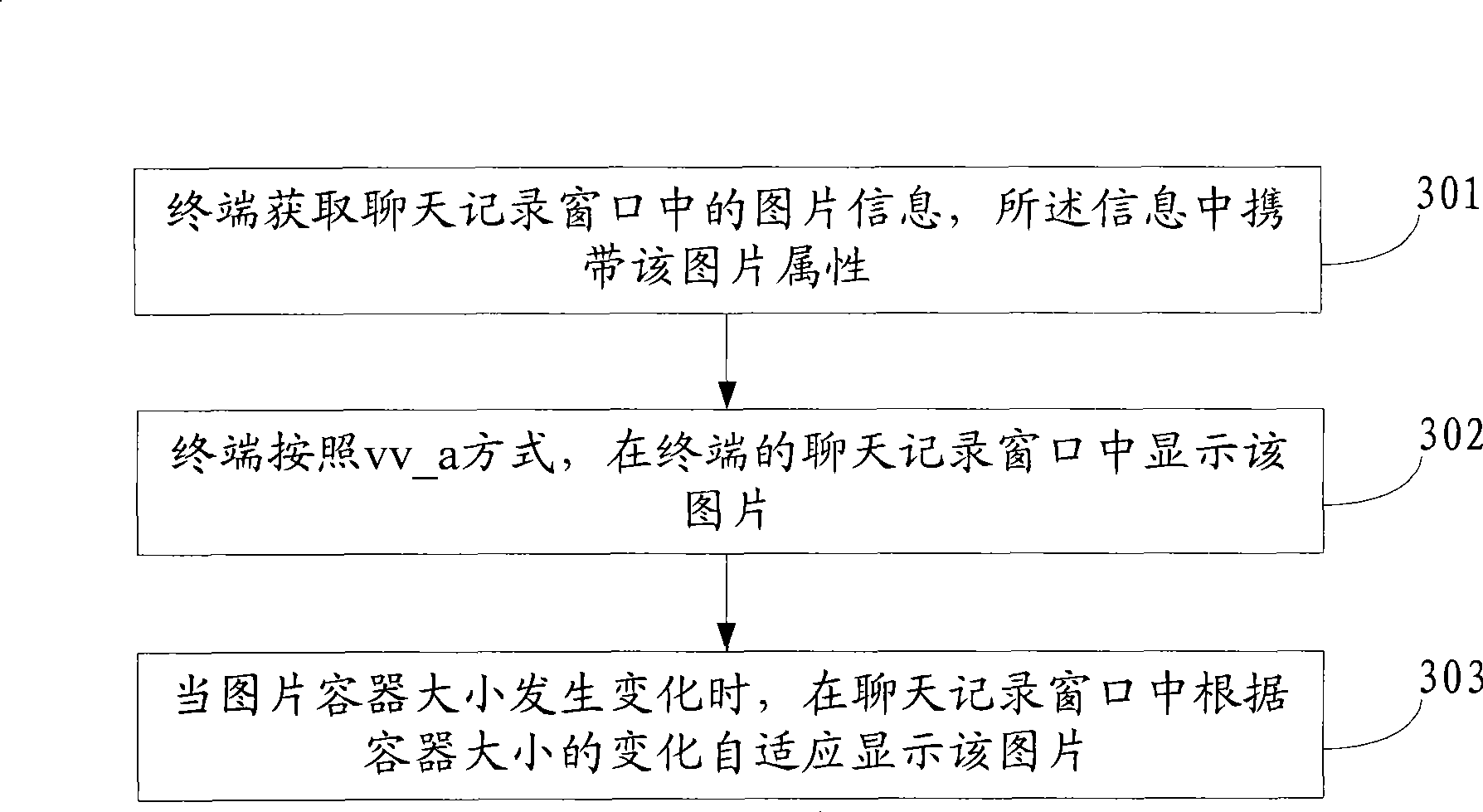
Method and apparatus for image display by instant communication tool
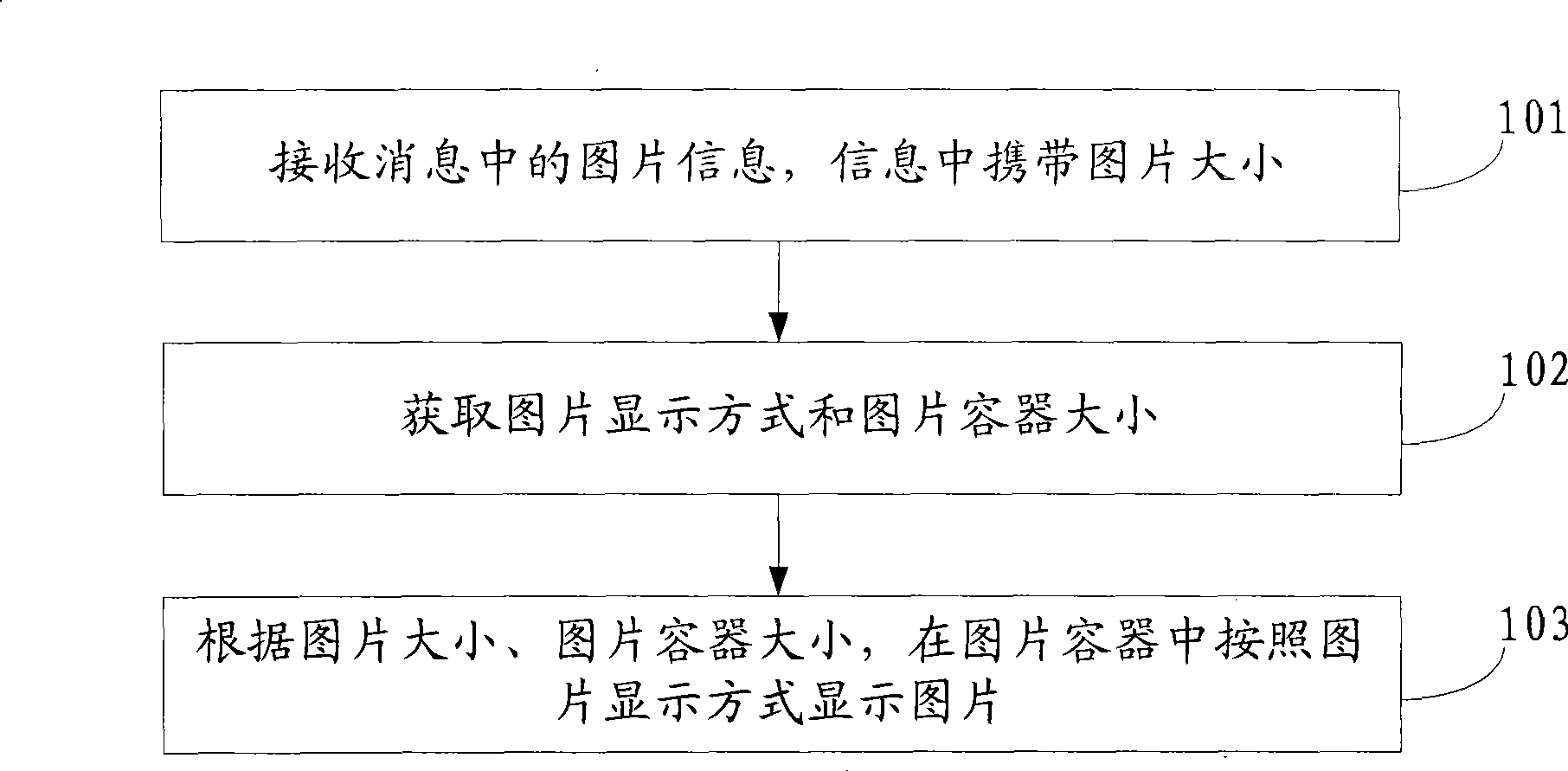
ActiveCN101478732AResolve integrityAddress flexibilitySubstation equipmentMessaging/mailboxes/announcementsComputer graphics (images)Image display
An embodiment of the invention discloses a method for displaying picture of instant communication tool and a device thereof. The invention belongs to the computer field. The method of the invention comprises the following steps: receiving picture information in the information which carries the size of picture; obtaining picture display mode and picture container size; and displaying the picture in the picture container according to the picture size, the picture container size and the picture display mode. The device of the invention comprises a receiving module, an acquiring module and a display module. The method provided by the embodiment of the invention can provide more picture display modes for the picture display area in IM, settles the problem of incomplete picture display in IM, increases the display effect of picture and the use experience of user, and facilitates the user for browsing the picture.
Owner:TENCENT TECH (SHENZHEN) CO LTD
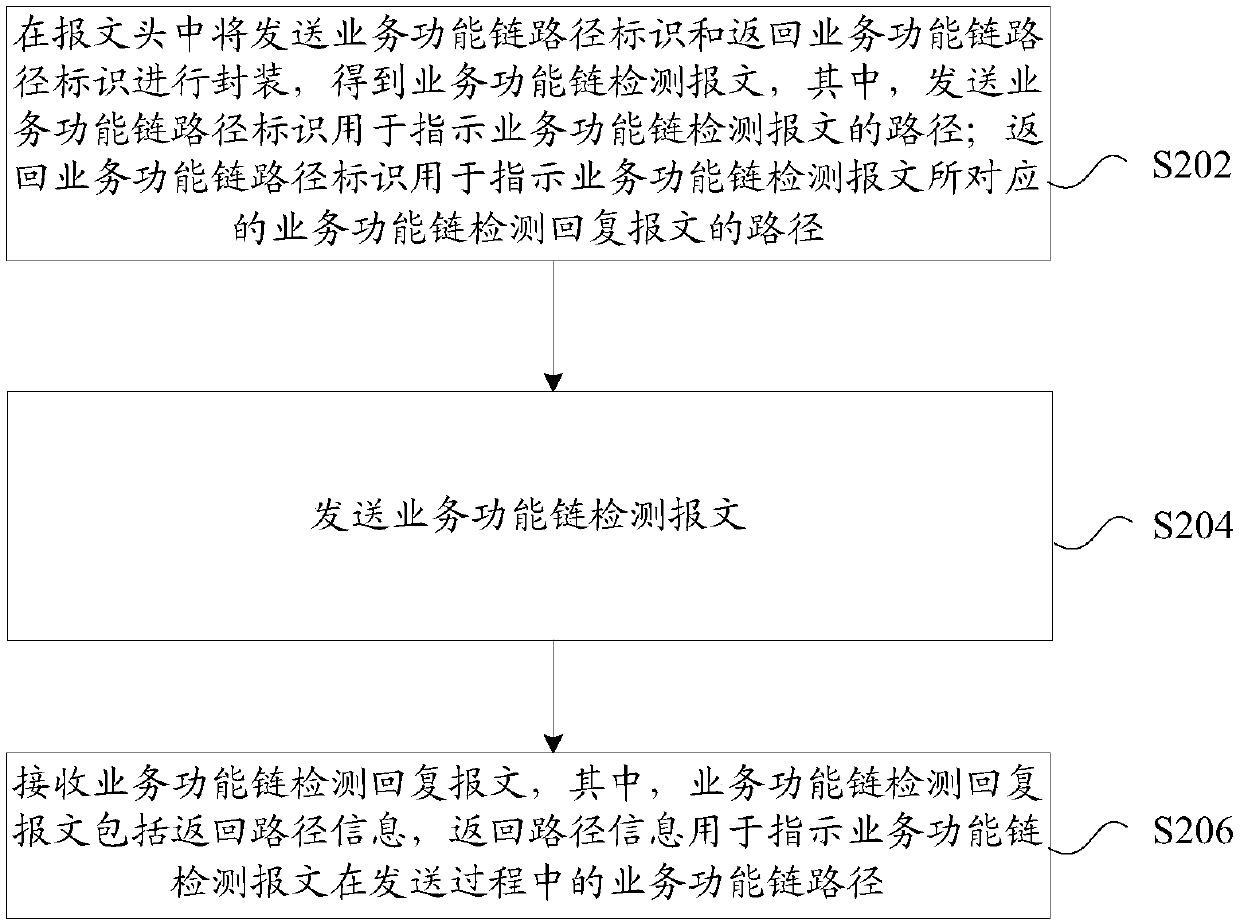
Method and device for detecting path of service function link
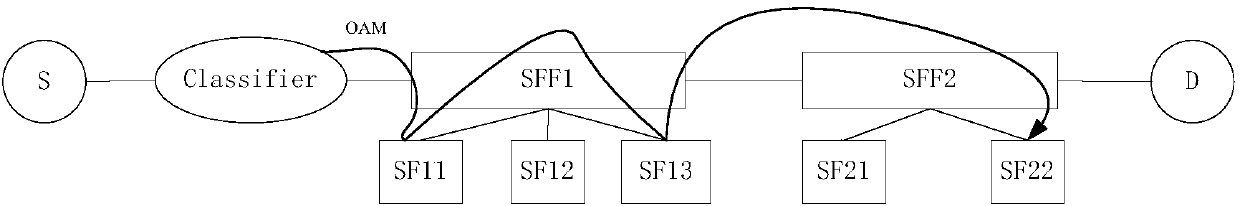
InactiveCN107872356AResolve integritySolving Consistency IssuesData switching networksSecuring communicationDistributed computingBusiness function
Owner:ZTE CORP
Method for secure communication of wireless sensor network based on combined password
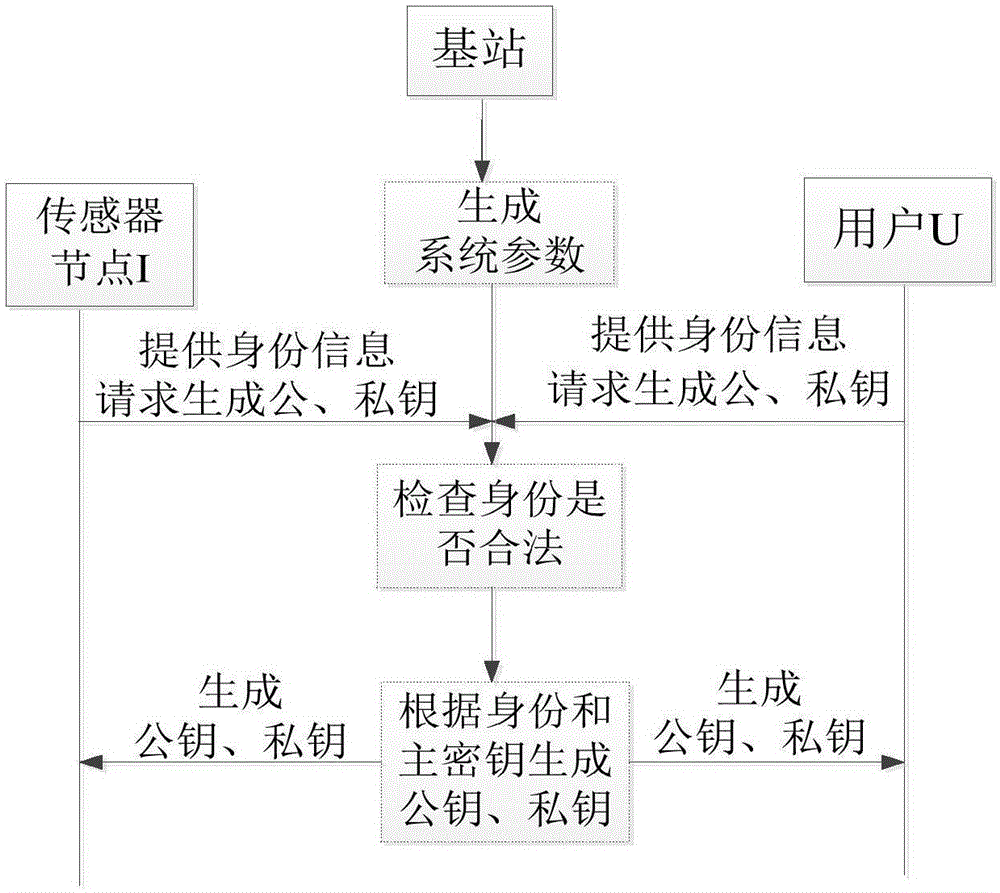
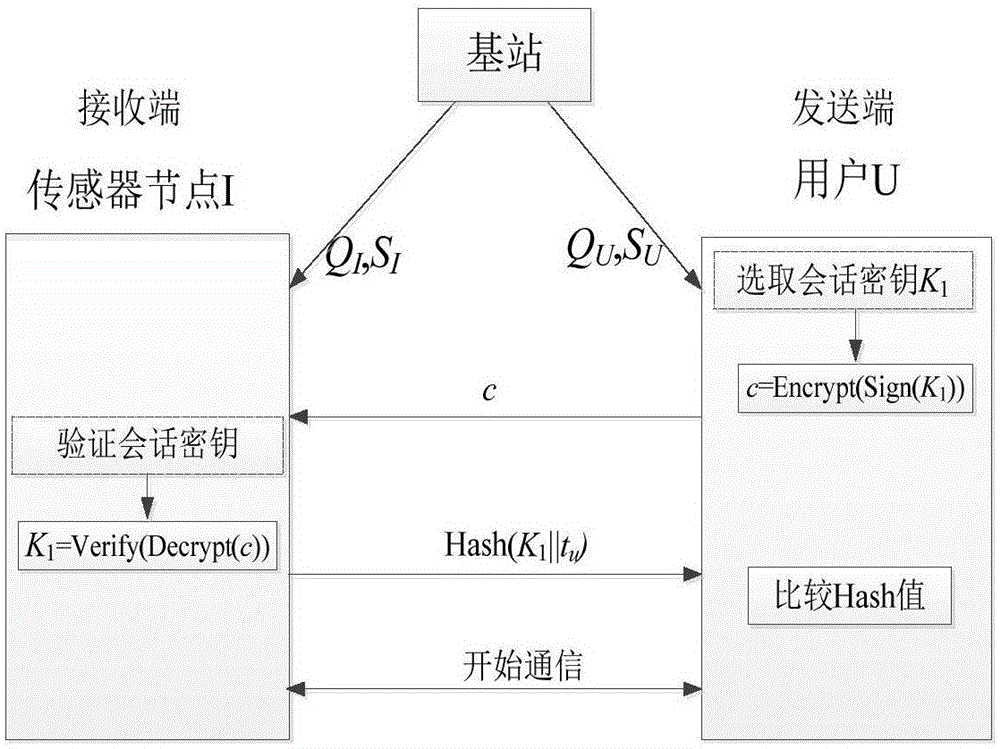
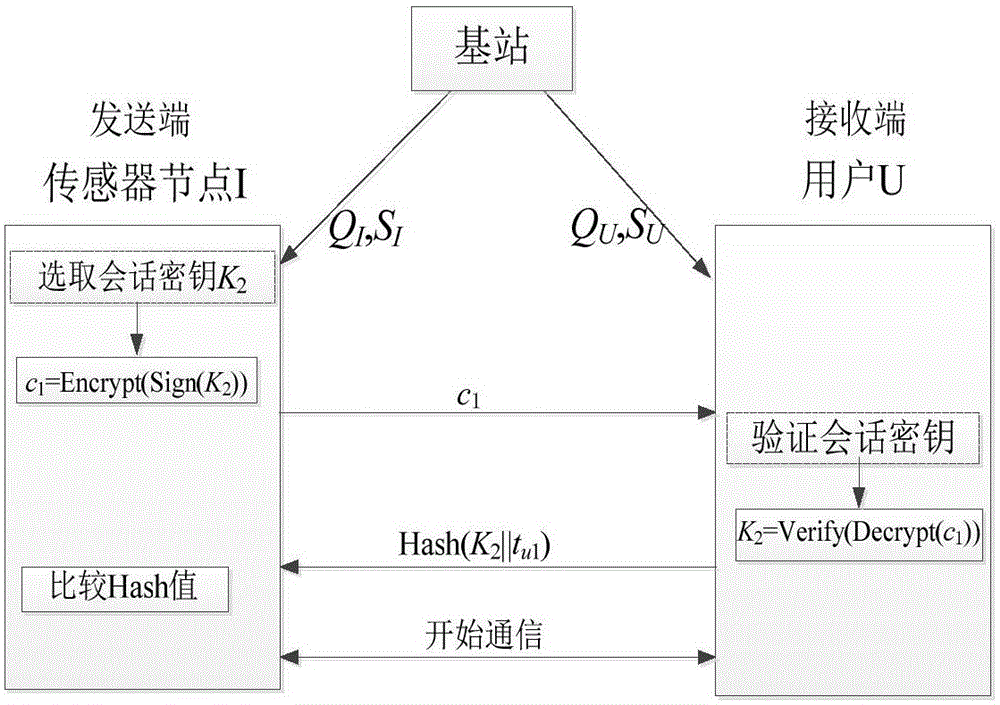
ActiveCN105163309AResolve confidentialitySolve authenticationNetwork topologiesSecurity arrangementSecure communicationWireless mesh network
The invention discloses a method for secure communication of a wireless sensor network based on a combined password, belonging to the field of secret communication. The method comprises the following steps that a base station sets and exposes system parameters and respectively generates public and private key pairs (QU, SU) and (QI, SI) for a user U and a node I; when the user is communicated with the sensor node, the user utilizes SU and QI to carry out signature and encryption on K1 in sequence based on a preset session key K1, and then the user sends a ciphertext to a receiving end, and the receiving end utilizes SI and QU to carry out decryption and verification in sequence; and lastly, the user utilizes the session key K1 to realize secure communication. When the sensor node needs to be communicated with the user, the node still utilizes SI and QU to carry out signature and encryption on a selected session key K2 in sequence, and then the user sends the ciphertext to the receiving end, and the receiving end still utilizes SU and QI to carry out decryption and verification. According to the method, secure communication of the wireless sensor network is realized by utilizing a combined public key password, so that the storage requirements for identity information and the cost for the base station to produce a private key are greatly reduced.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
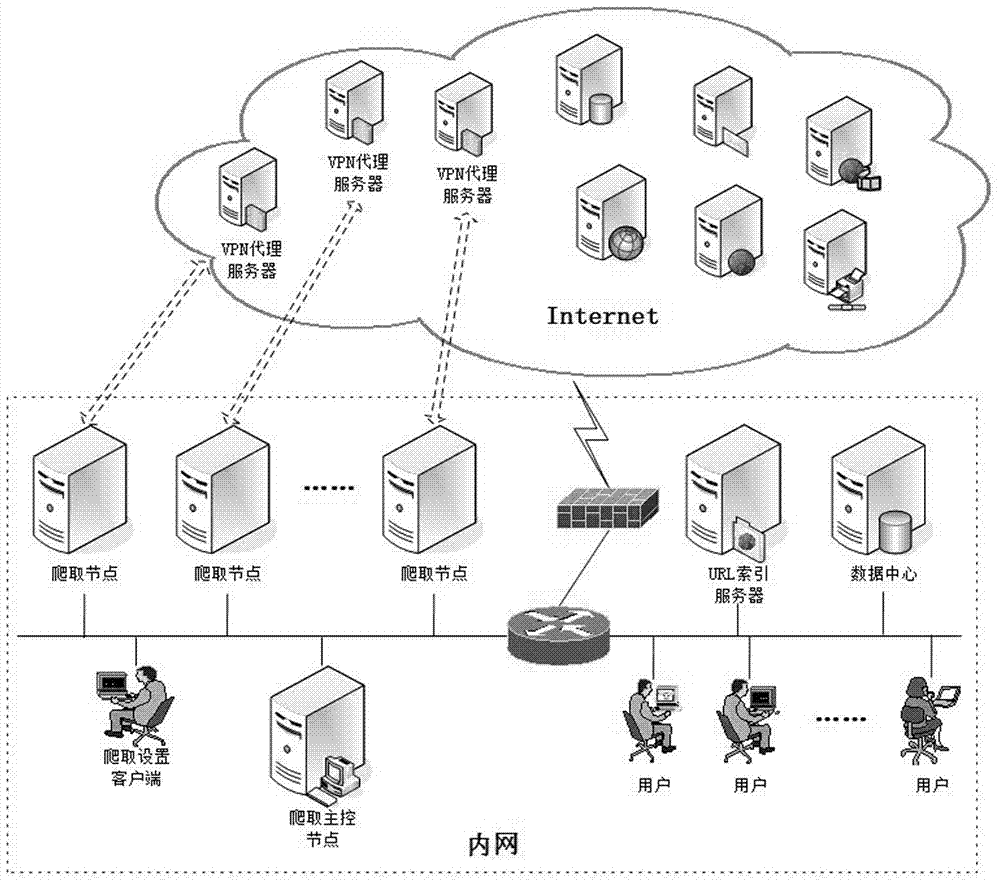
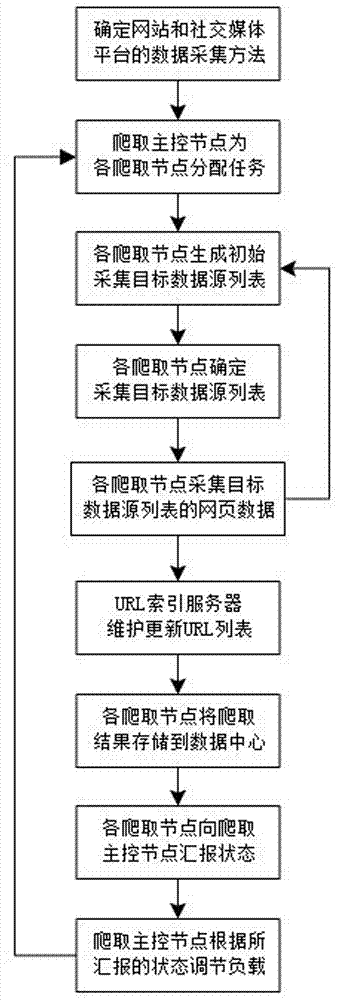
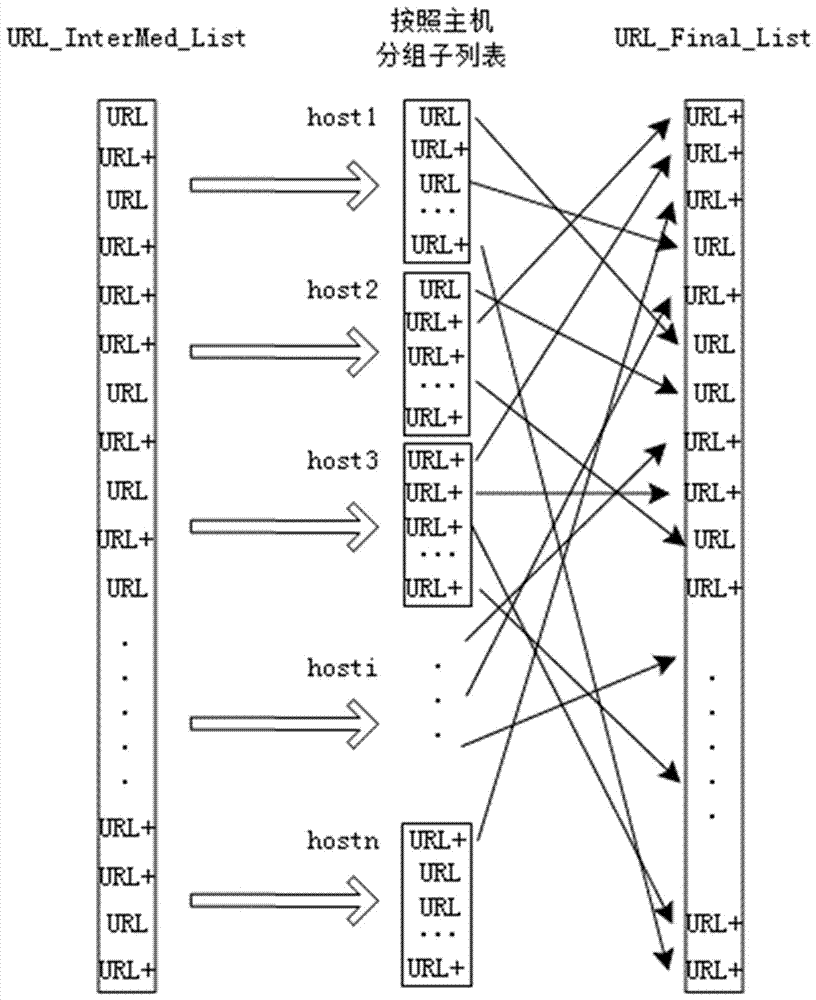
Distributed web crawler system and scheduling method based on VPN
ActiveCN107241319ALoad balancingCause access denied issueData processing applicationsTransmissionSingle serverLocal area network
The invention provides a distributed web crawler system and scheduling method based on VPN. A remote VPN agency server is connected in a VPN dialing mode, and the VPN connection is switched to obtain different public network IPs, and the problem of single local area network IP address is solved; then, although a plurality of public network IPs can be obtained by the manner of accessing the remote VPN agency server, with respect of the updating frequency of social news websites, the IP addresses are still precious scarce resource, and in order to obtain data as much as possible for one IP address, the manner of multi-target data source URL insertion collection is adopted to avoid densely collecting the data in the single server at the same time, resulting in that the server refuses the access, and the data collection coverage and integrity of the social media network platforms are solved; and finally, different from the current network connection allocation manner in load balancing, the loads of the crawler nodes are balanced in a manner of adjusting the keywords.
Owner:南方电网互联网服务有限公司
AIS (Automatic Identification System) trajectory big data-based ship traffic environment reconstruction method
ActiveCN108806335ASolve intermittentResolve integrityMarine craft traffic controlSpecial data processing applicationsSocial benefitsTime segment
The invention discloses an AIS (Automatic Identification System) trajectory big data-based ship traffic environment reconstruction method. The method includes the following steps that: step 1-1, a time interval parameter is segmented so as to be divided into various time segments, the trajectory data of all ships in a specified geographical range within a time segment are only requested each time;step 1-2, a web front end temporarily stores the trajectory data in the step 1-1, preprocesses the trajectory data, and calculates and reconstructs the spatial relationship of the trajectory data; step 1-3, the web front end periodically requests new trajectory data from a server and performs dynamic update; and the step 1-1, 1-2, and 1-3 are repeated, so that the continuous reconstruction of a traffic environment can be realized at the web front-end. With the method adopted, an AIS data-based visualization technological means is provided for shipborne equipment and the equipment of a maritime supervision department, and inland navigation can be smoother, more orderly, safer and more efficient, and obvious economic and social benefits can be brought about.
Owner:DALIAN MARITIME UNIVERSITY
Topology identification method and device for power distribution automation
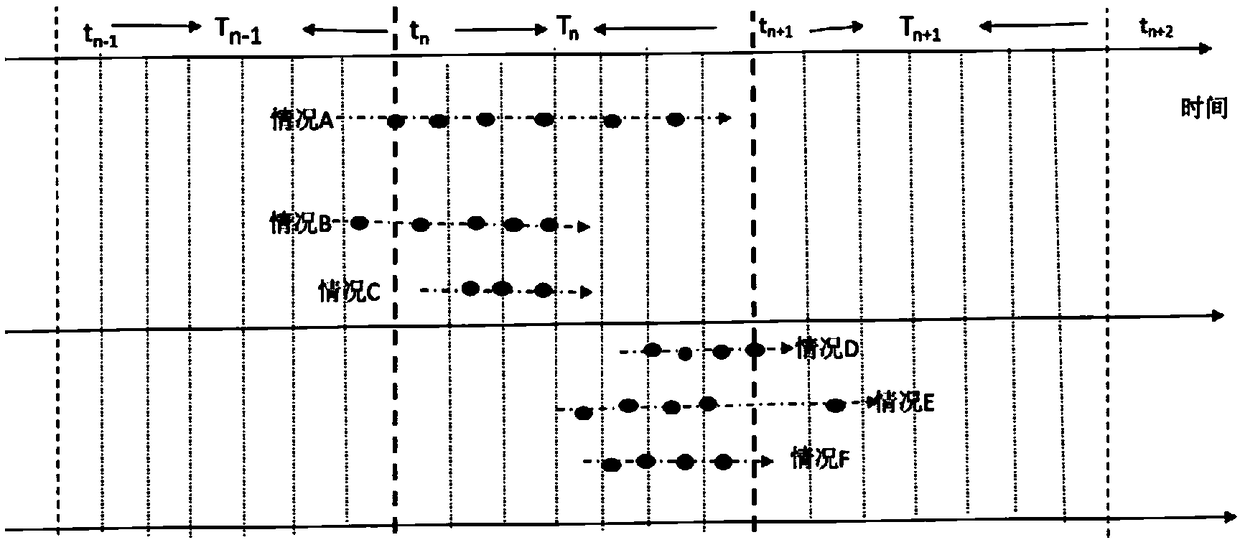
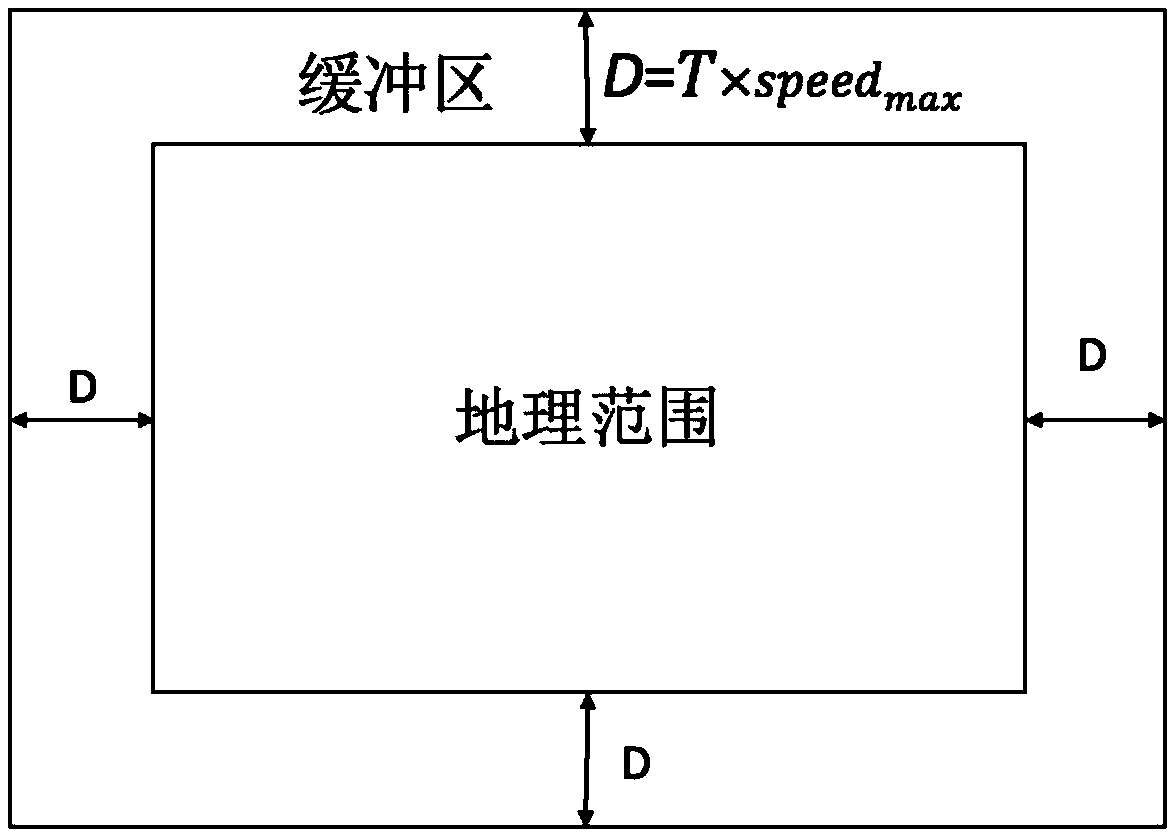
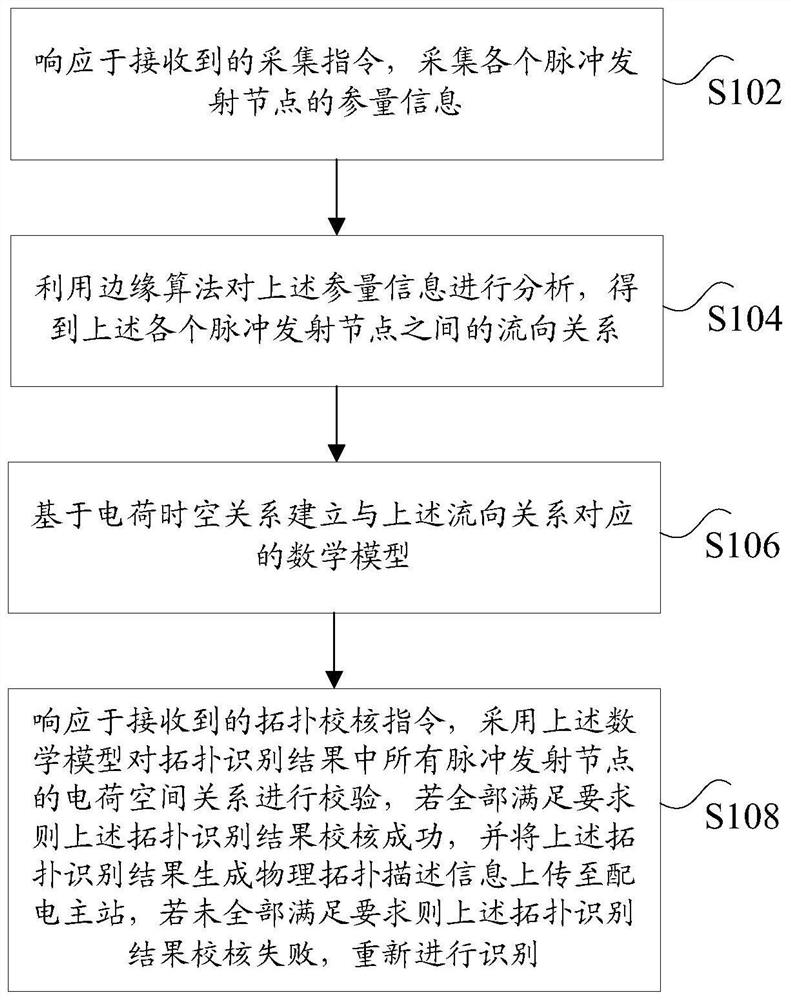
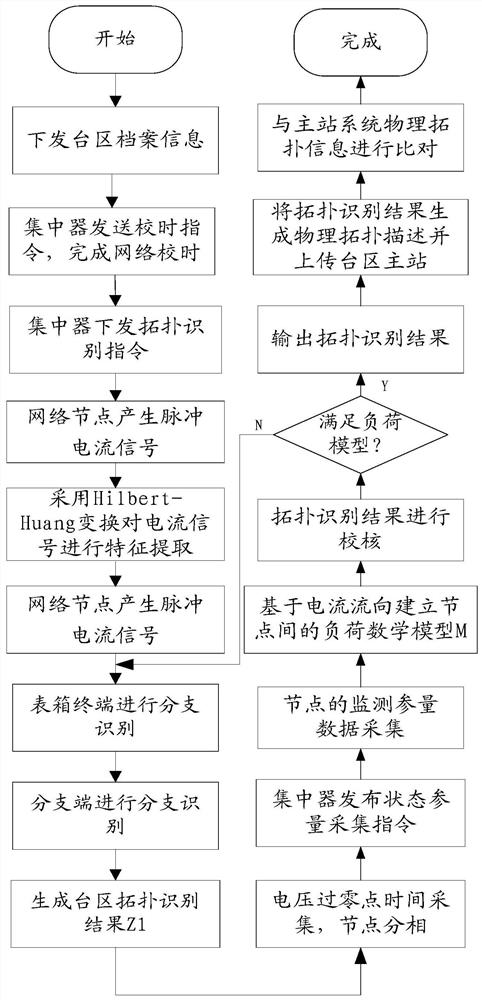
ActiveCN112510841AIncrease the level of automationResolve integrityPower distribution line transmissionData switching networksTopology identificationAlgorithm
The invention discloses a topology identification method and device for power distribution automation. The method comprises the following steps: in response to a received acquisition instruction, acquiring parameter information of each pulse transmitting node; analyzing the parameter information by using an edge algorithm to obtain a flow direction relationship among the pulse transmitting nodes;establishing a mathematical model corresponding to the flow direction relationship based on the charge space-time relationship; in response to a received topology check instruction, adopting the mathematical model to check the charge space relationship of all the pulse transmitting nodes in the topology identification result: if all the pulse transmitting nodes meet the requirements, determining that the topology identification result is successfully checked, and generating physical topology description information from the topology identification result and uploaded to a power distribution main station; if not all the topological recognition results meet the requirements, determining that the topological recognition results fail to be checked, and carrying out recognition again. Accordingto the invention, the technical problems of incomplete topological relation and disordered communication of the low-voltage distribution area in the distribution automation master station system in the prior art are solved.
Owner:STATE GRID BEIJING ELECTRIC POWER +1
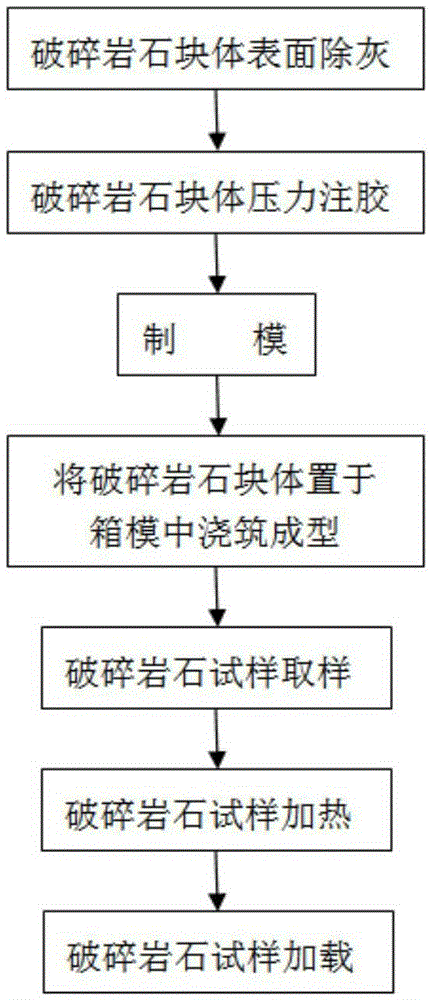
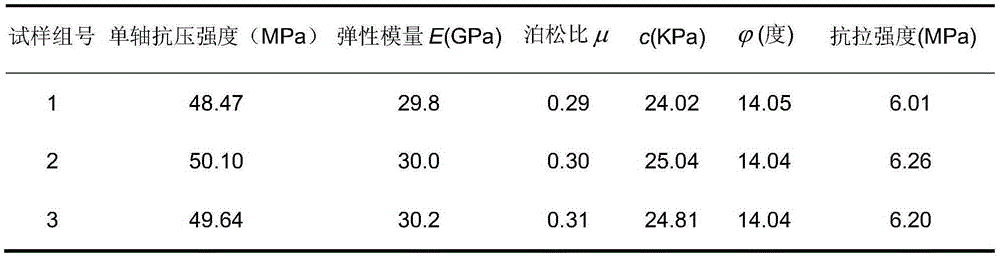
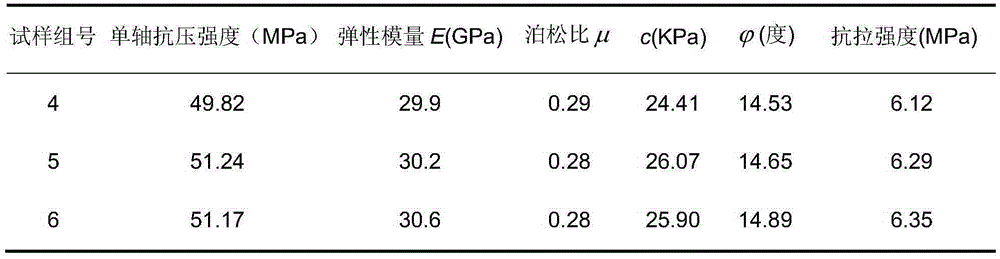
A preparing and loading method of a broken rock test sample
ActiveCN105352786ASolve the fragileResolve integrityPreparing sample for investigationStrength propertiesHeat deflection temperatureTest sample
A preparing and loading method of a broken rock test sample is disclosed and is suitable for test sample preparation of a weak broken rock block. The method includes subjecting the weak broken rock block to surface dedusting, injecting colloid under pressure, putting the rock block after colloid injection into a hollow cuboid or cube box, pouring with cement mortar or low-strength concrete, molding, putting the rock block molded with the mortar or the low-strength concrete to a coring machine, coring, cutting the test sample to obtain a needed standardized rock test sample, heating the obtained rock test sample to allow the temperature of the colloid in the rock to achieve a heat distorsional temperature, and loading to perform mechanical property tests of the rock. The method is simple, convenient and high in applicability, and overcomes the problem that rock samples are easily broken and incomplete in a sampling process of the weak broken rock block. The standardized rock test sample is heated before loading, thus eliminating or reducing influences of the colloid on mechanical properties of the rock test sample as far as possible. Obtained test results are accurate and reliable.
Owner:西安华清科教产业(集团)有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com