Verifiable searchable encryption method
A search method and search path technology, applied in the field of verifiable encrypted search, to achieve the effect of low overhead and fewer communication rounds
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The present invention will be further described in detail below in conjunction with specific embodiments and with reference to the drawings.
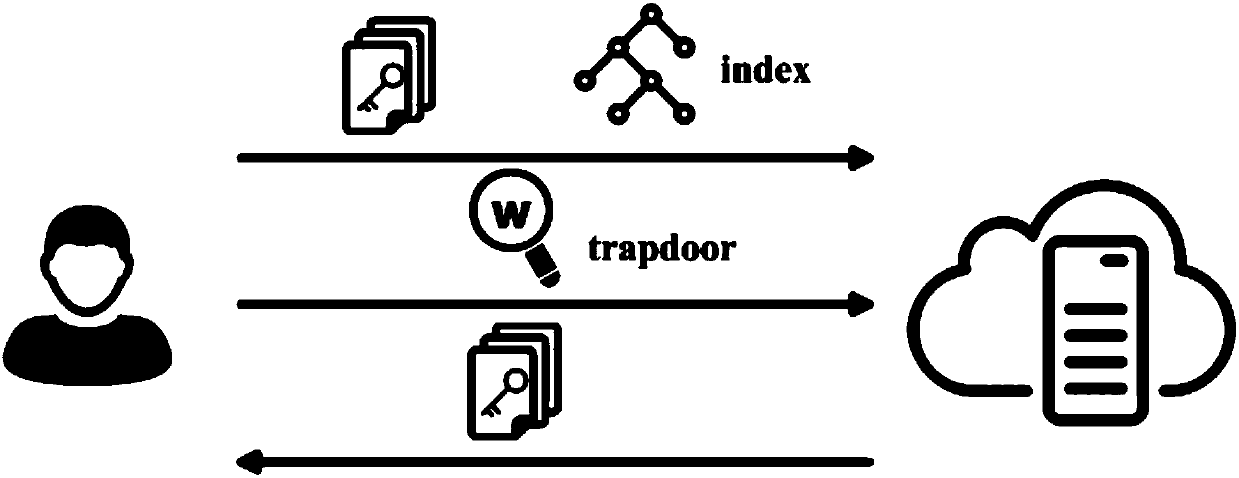
[0030] The system framework of the verifiable encrypted search scheme includes two entities: client and server. The client uploads the verification index (index) corresponding to its data to the cloud; the cloud server (server) provides storage, search and verification services for the client; after the client searches Verify the search results returned by the cloud server. As follows, before describing the working process of the system, the signs and meanings of some concepts that will be used in this specific implementation are given.
[0031]
[0032] The workflow of the system is defined as follows:
[0033] KGen C (1 k )→(K 1 ,K 2 }: is the probability calculation operation performed by the Client. Its input is a security parameter, and its output is a symmetric key set K 1 ,K 2 .
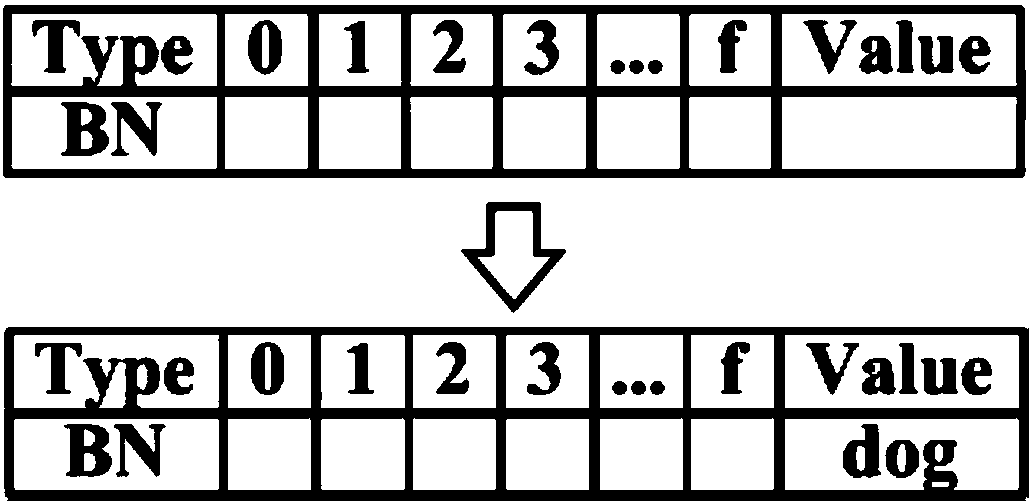
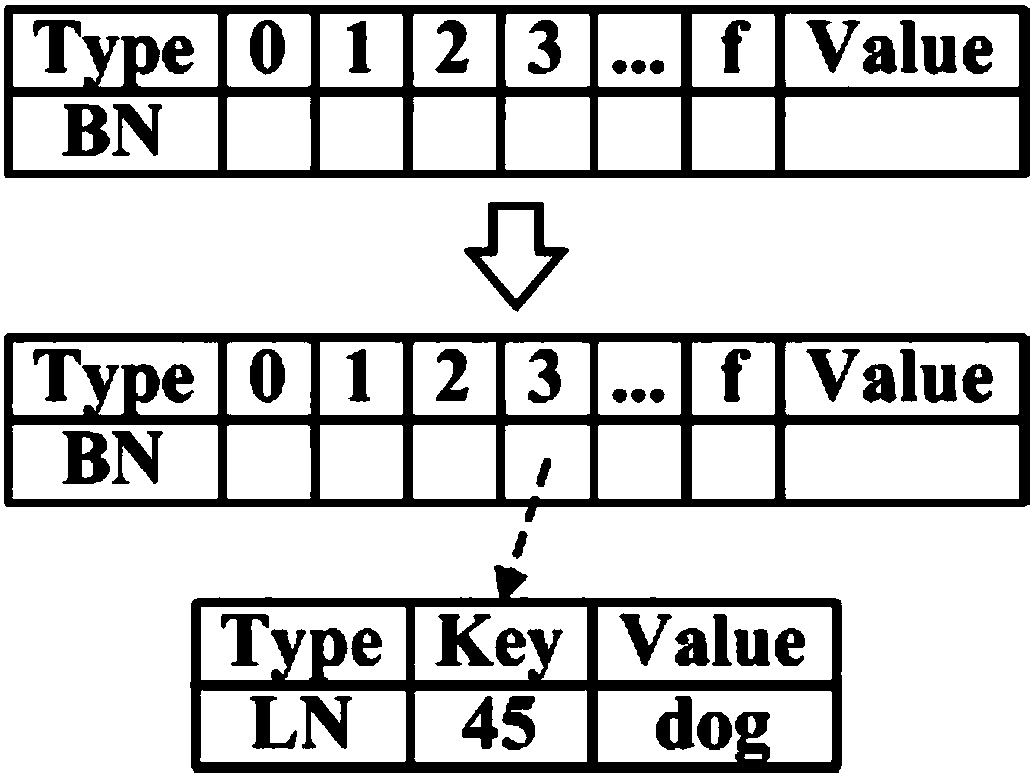
[0034] Init C (K 1 ,K 2 ,D)→{λ}: is the initiali...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com