Method and device for detecting path of service function link
A technology of business functions and paths, applied in the field of communication, can solve the problem of inability to guarantee the integrity and consistency of detection sequences
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
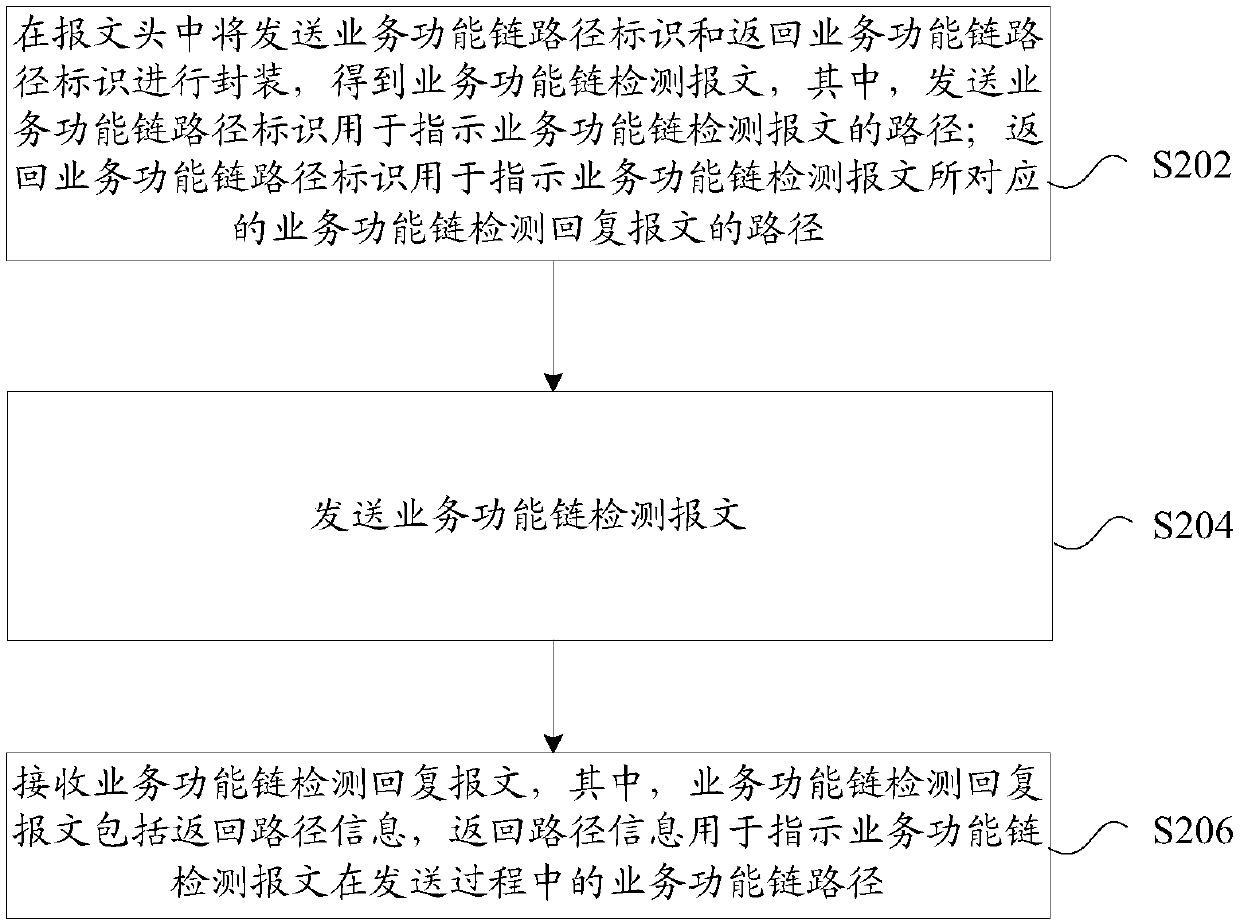
[0059] figure 2 is a flowchart of a method for detecting a path of a service function chain according to an embodiment of the present invention, such as figure 2 As shown, the process includes the following steps:
[0060] Step S202, encapsulating the path identifier of the sending service function chain and the path identifier of the returning service function chain in the message header to obtain a service function chain detection message, wherein the sending service function chain path identifier is used to indicate the service function chain detection message path; the return service function chain path identifier is used to indicate the path of the service function chain detection reply message corresponding to the service function chain detection message;
[0061] Step S204, sending a service function chain detection message;
[0062] Step S206, receiving a service function chain detection reply message, wherein the service function chain detection reply message incl...
example 1
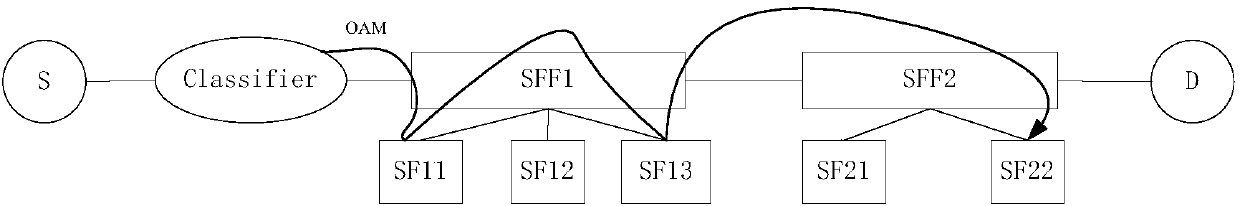
[0101] In this example 1, the traffic sent from S to D needs to be processed by some business functions, and the business function chain that follows: SF11->SF13->SF22, such as image 3 shown. In order to realize the detection of service function chain path failures and ensure the consistency verification of service function chains, this application extends the Loopback message, the flag field in the loopback message, such as Figure 4 shown. The flag here is the length of one byte, and one of the identification bits CS can be used to indicate the consistency detection, and the remaining bits can be indicated by R, indicating that the remaining bits are reserved for future use. CS=1 indicates that the loopback message needs
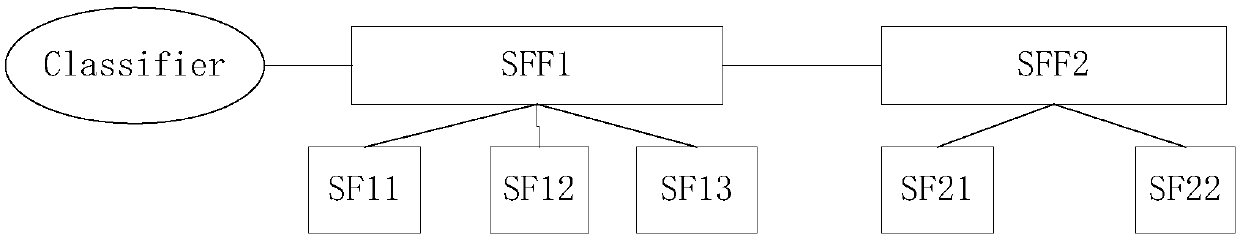
[0102] When such a Loopback message header is encapsulated with an NSH header, the header carries the identifier SFPID of the service function chain to be detected, and the NSH header will indicate that the message is an OAM message. image 3 The SFF / S...
example 2
[0106] In this example 2, for the linktrace message, it is forwarded on an SFC path (still as SF11->SF13->SF22 in embodiment 1) for detection of the path, as in embodiment 1, it needs to have a flag mark (you can Same as in Example 1, such as Figure 5 As shown), it is used to indicate that the linktrace message needs to check the consistency of the path.
[0107] Each SF that receives the detection message will reply with a trace response message. The trace response message also needs to carry an SF plus TLV (metadata). This TLV not only carries the information of the SF, but also needs to carry the service index , which is used to indicate the position of the service function chain where this SF is located, such as Figure 6 shown. Therefore, the consistency of the sequence of these SFs is guaranteed.
[0108] for image 3 The service function chain SF11->SF13->SF22, the NSH header in the Linktrace message not only contains the SFPID identifying this path, but also has a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com