Data auditing method and device, computer device and storage medium
A data audit and database technology, applied in the database field, can solve the problem of long time-consuming database security audit
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
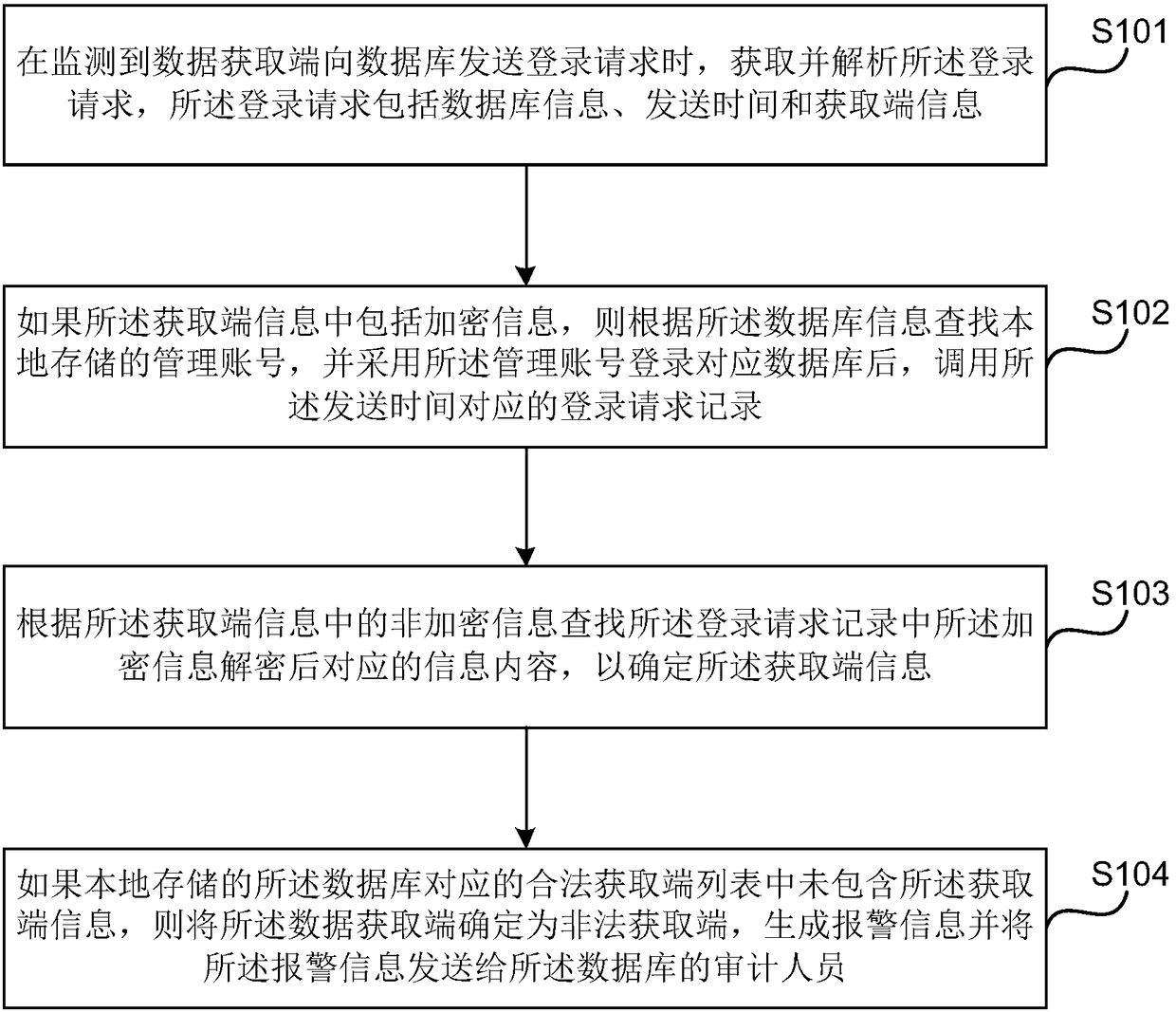
[0028] Embodiment 1 of the present invention provides a data audit method. The method can be executed by a data audit system, wherein the device can be implemented by software and / or hardware, and can generally be integrated in an audit system configured with a database. figure 1 A schematic flow chart of the data audit method provided in Embodiment 1 of the present invention, as shown in figure 1 As shown, the method includes:
[0029] S101. Obtain and parse the login request when it is detected that the data acquisition terminal sends a login request to the database, and the login request includes database information, sending time, and acquisition terminal information.
[0030] Wherein, the login request can be understood as a request sent to the database when the data acquisition terminal logs in to the database. In this embodiment, whether the data acquisition terminal sends a login request to the database can be monitored in real time or according to a set period. The...
Embodiment 2
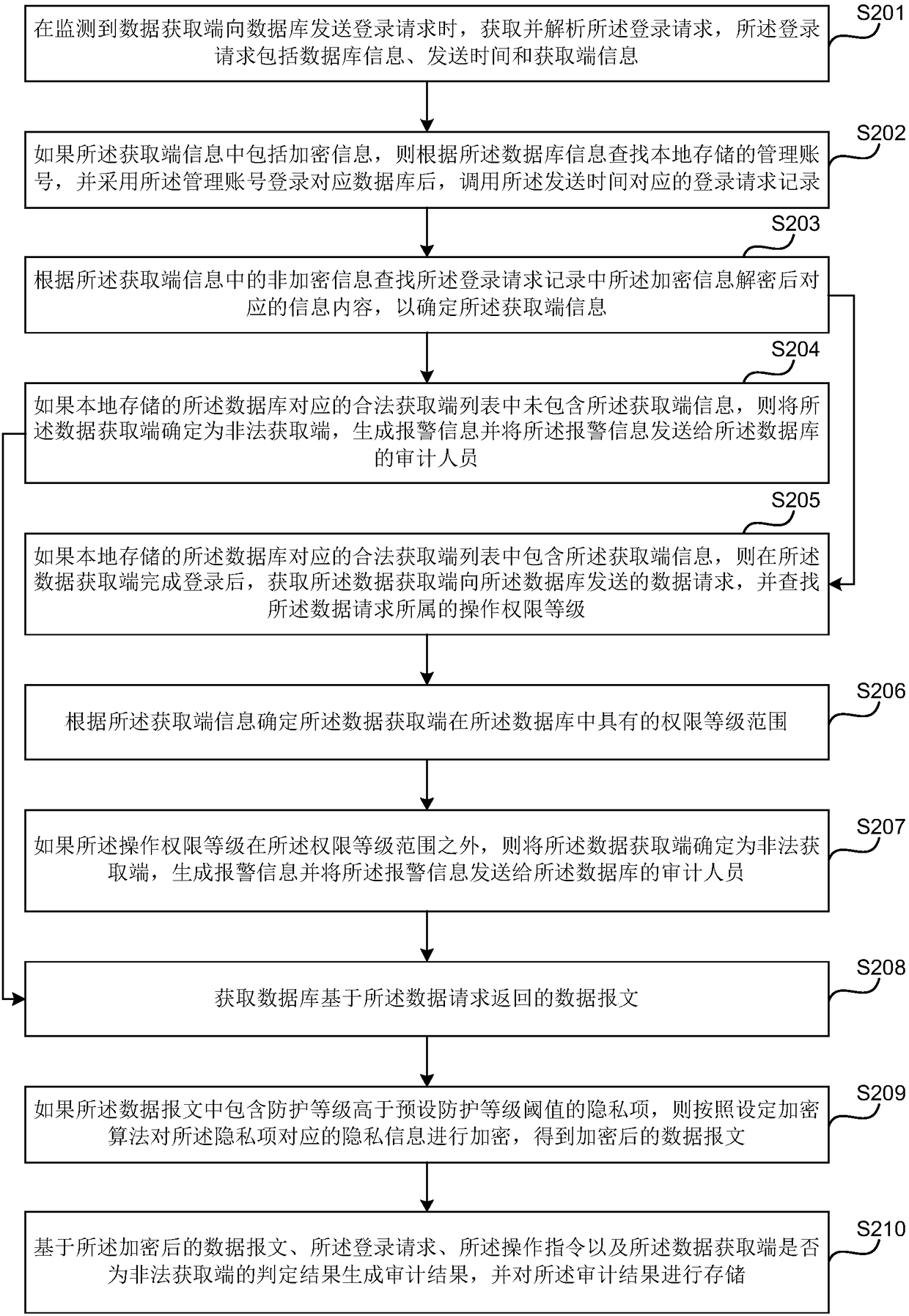
[0049] figure 2It is a schematic flowchart of the data auditing method provided by Embodiment 2 of the present invention. This embodiment is optimized on the basis of the above-mentioned embodiments. Further, the data audit method provided by this embodiment may further include: if the locally stored legal obtainer list corresponding to the database contains the obtainer information, then After the data acquisition terminal completes the login, obtain the data request sent by the data acquisition terminal to the database, and find the operation authority level to which the data request belongs; determine the data acquisition terminal according to the information of the acquisition terminal. The scope of the authority level in the database; if the operation authority level is outside the scope of the authority level, the data acquisition terminal is determined as an illegal acquisition terminal, an alarm message is generated and the alarm information is sent to all auditors o...
Embodiment 3
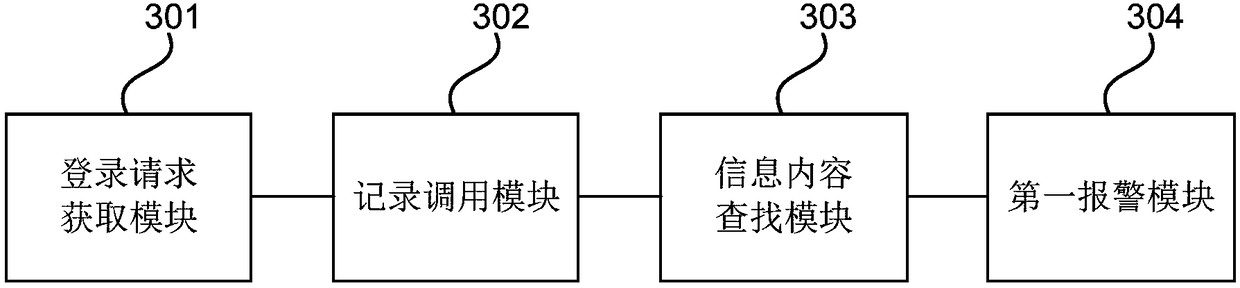
[0082] Embodiment 3 of the present invention provides a data auditing device. The device can be implemented by software and / or hardware, and generally can be integrated in an audit system configured with a database, and audit data can be implemented by implementing a data audit method. image 3 The structural block diagram of the data auditing device provided for the third embodiment of the present invention, such as image 3 As shown, the device includes:
[0083] The login request acquisition module 301 is configured to acquire and parse the login request when it is detected that the data acquisition terminal sends a login request to the database, and the login request includes database information, sending time and acquisition terminal information;
[0084] The record calling module 302 is configured to search for a locally stored management account according to the database information when the information on the acquiring terminal includes encrypted information, and afte...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com