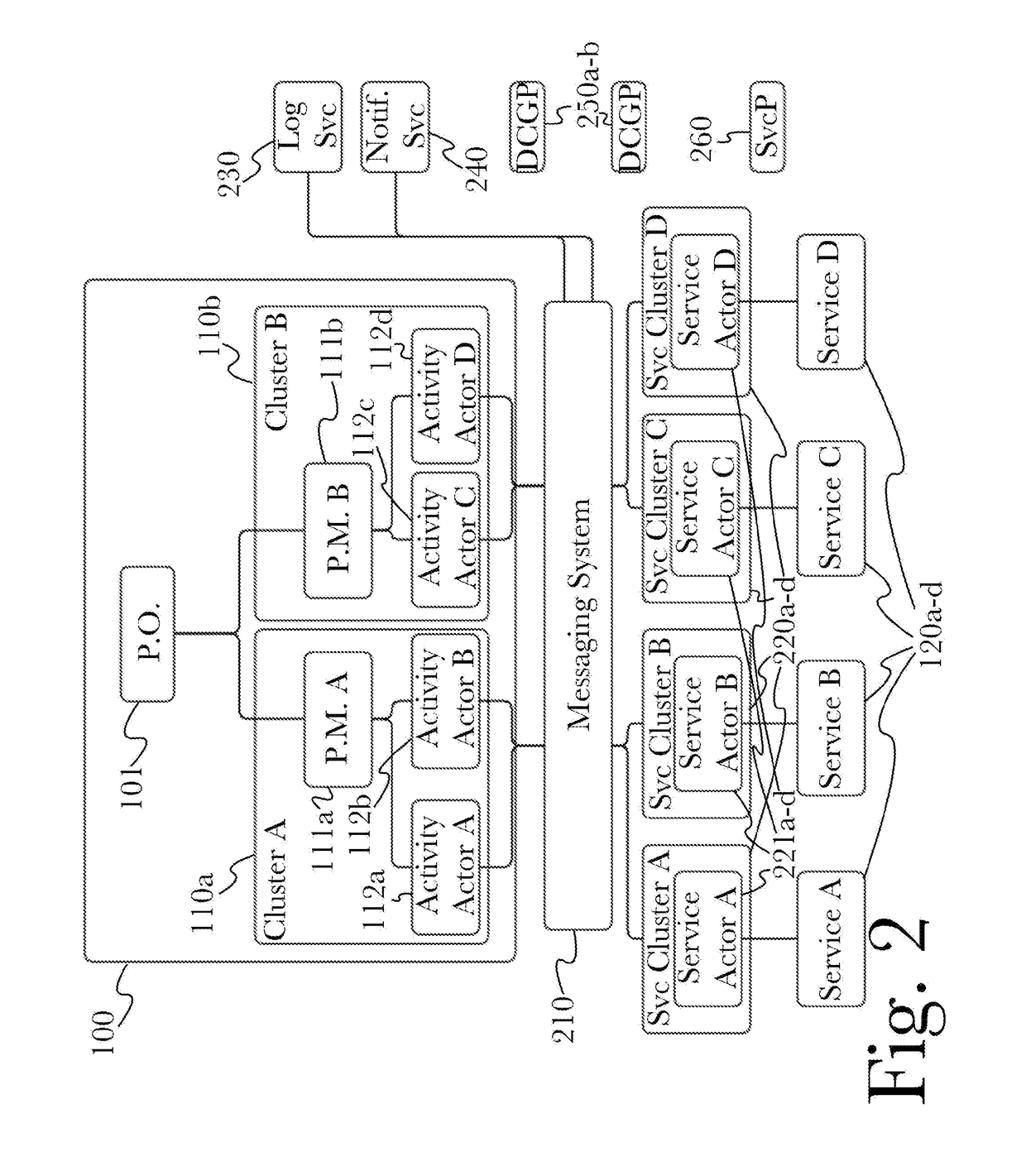
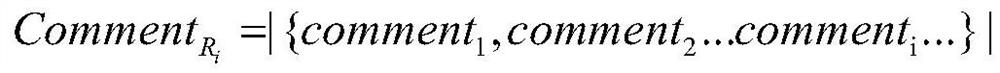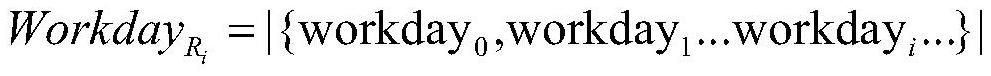Patents
Literature
32 results about "Code audit" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A software code audit is a comprehensive analysis of source code in a programming project with the intent of discovering bugs, security breaches or violations of programming conventions. It is an integral part of the defensive programming paradigm, which attempts to reduce errors before the software is released. C and C++ source code is the most common code to be audited since many higher-level languages, such as Python, have fewer potentially vulnerable functions (e.g., functions that do not check bounds).
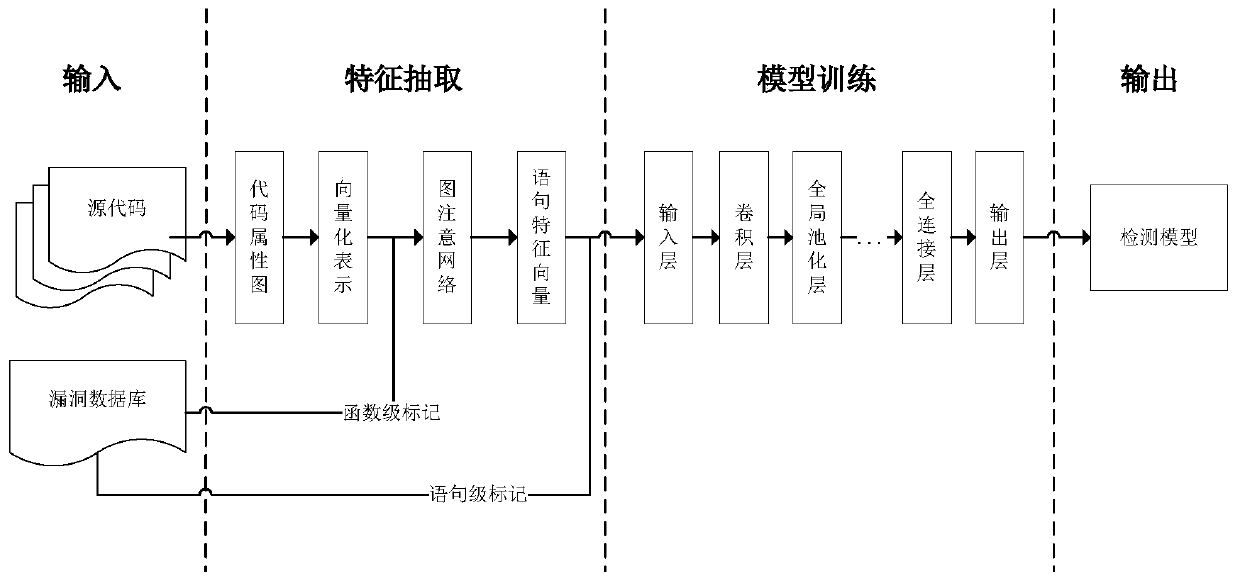
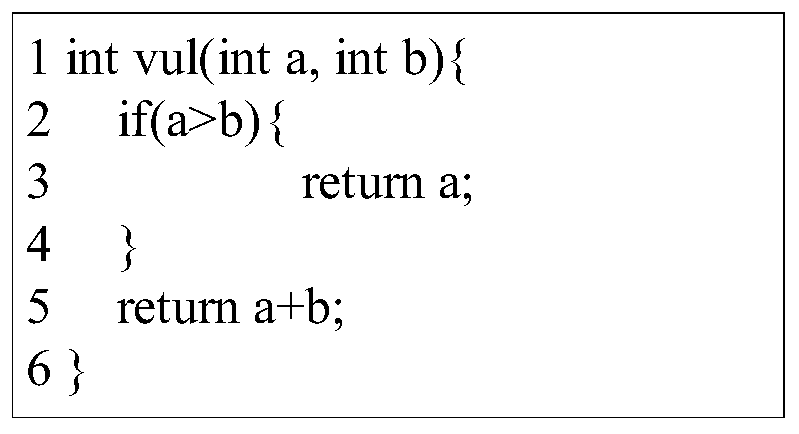
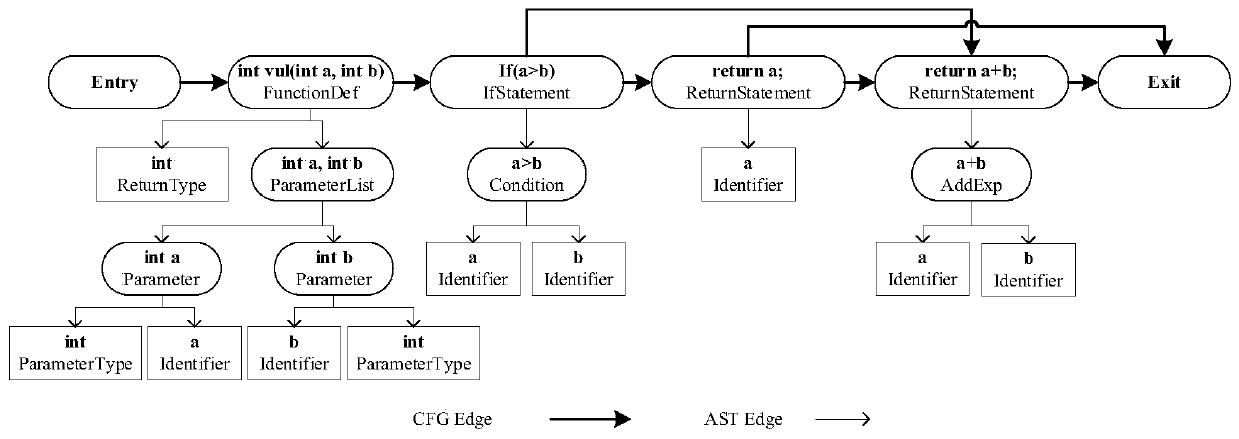
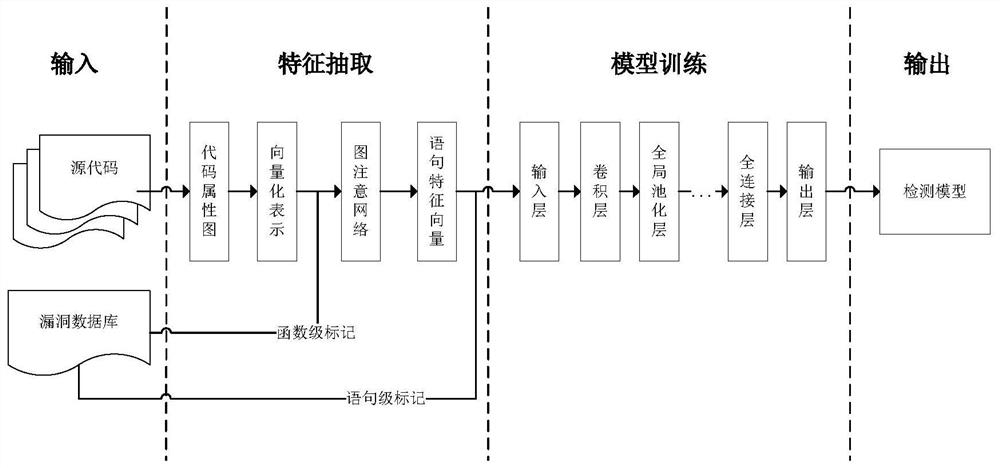
Fine-grained source code vulnerability detection method based on graph neural network
ActiveCN111259394AImprove audit efficiencyHigh degree of automationPlatform integrity maintainanceNeural architecturesData setAlgorithm
The invention discloses a fine-grained source code vulnerability detection method based on a graph neural network, which comprises the following steps: A, for all source codes of software, extractinga code attribute graph of a function in the source codes, and performing vectorization representation on the code attribute graph, the vectorization representation comprising vectorization representation of node attributes and graph structures; B, extracting code features by using a graph attention network, and processing all statements to obtain a final data set; and C, training a vulnerability detection model, and determining a final model through the effect on the test set. The source code vulnerability detection method provided by the invention has the advantages that the automation degreeis higher; dependence on domain expert knowledge is reduced, code auditing cost is greatly saved, code auditing efficiency is improved, grammar and semantic information in source codes are better reserved, meanwhile, vectorized representation of statements can be learned purposefully through a graph attention network, and vulnerability detection of a finer-grained statement level is achieved.
Owner:SUN YAT SEN UNIV
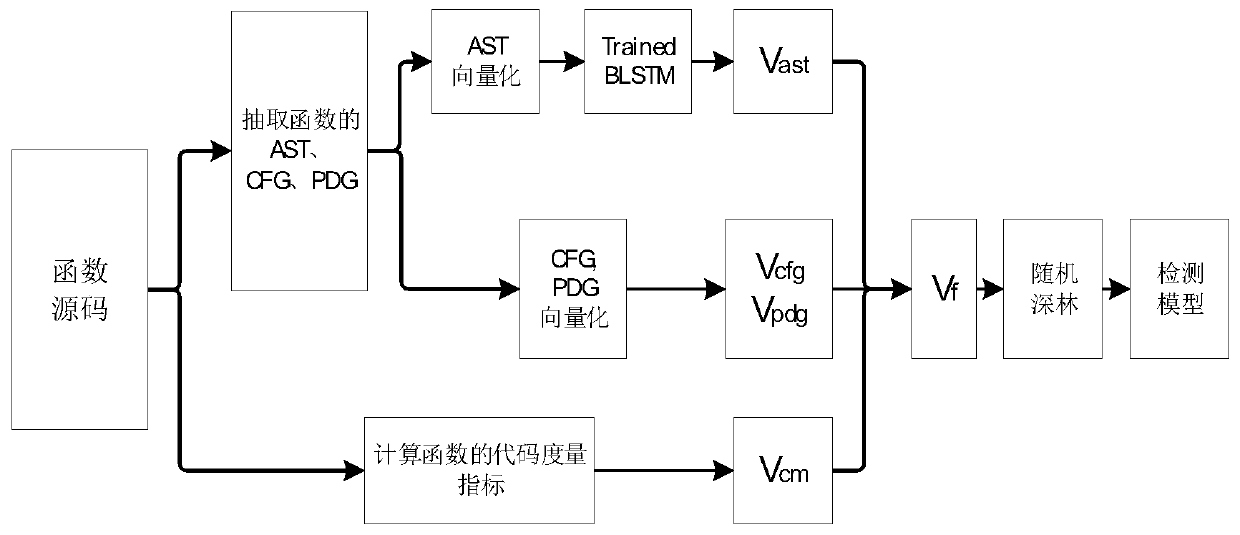
Source code vulnerability detection method based on deep learning
ActiveCN110011986AReduce audit costsImprove audit efficiencyCharacter and pattern recognitionTransmissionFeature extractionAlgorithm
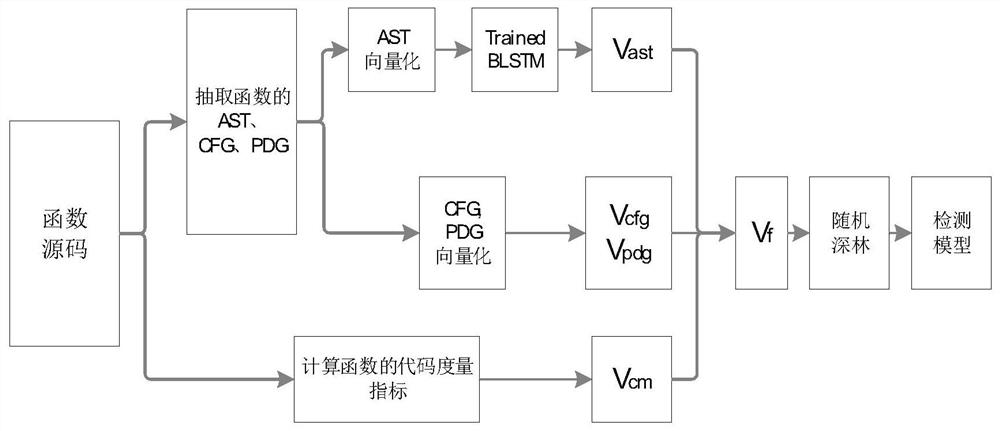
The invention provides a source code vulnerability detection method based on deep learning, and the method comprises the steps: automatically completing the feature extraction of a source code based on deep learning, and constructing a vulnerability detection model by using a random deep forest algorithm in combination with a code measurement index and an automatically extracted source code feature. The source code vulnerability detection method based on deep learning provided by the invention has higher degree of automation, reduces dependence on domain expert knowledge, greatly reduces the code auditing cost and improves the code auditing efficiency. Compared with other methods for vulnerability detection by using deep learning, , grammar and semantic information of the code are reservedto the maximum extent by combining multiple representations of the code, the code can be better depicted by the characteristics automatically extracted by the deep learning algorithm, and meanwhile,the detection effect is further improved by combining common code measurement indexes as detection characteristics.
Owner:SUN YAT SEN UNIV
Meta-indexing, search, compliance, and test framework for software development
A system for meta-indexing, search, compliance, and test framework for software development is provided, comprising an indexing service configured to create a dataset by processing and indexing source code of a project provided by a developer, perform a code audit on the indexed source code, store results from the code audit in the dataset, gather additional information relating to the provided project, store the additional information in the dataset, and store the dataset into memory; and a monitoring service configured to continuously monitor the project for at least source code changes and make changes to the dataset as needed.
Owner:QPX LLC
Code audit method and device
ActiveCN101551836AImprove accuracyImprove audit efficiencyError detection/correctionPlatform integrity maintainanceComputer networkSecurity properties
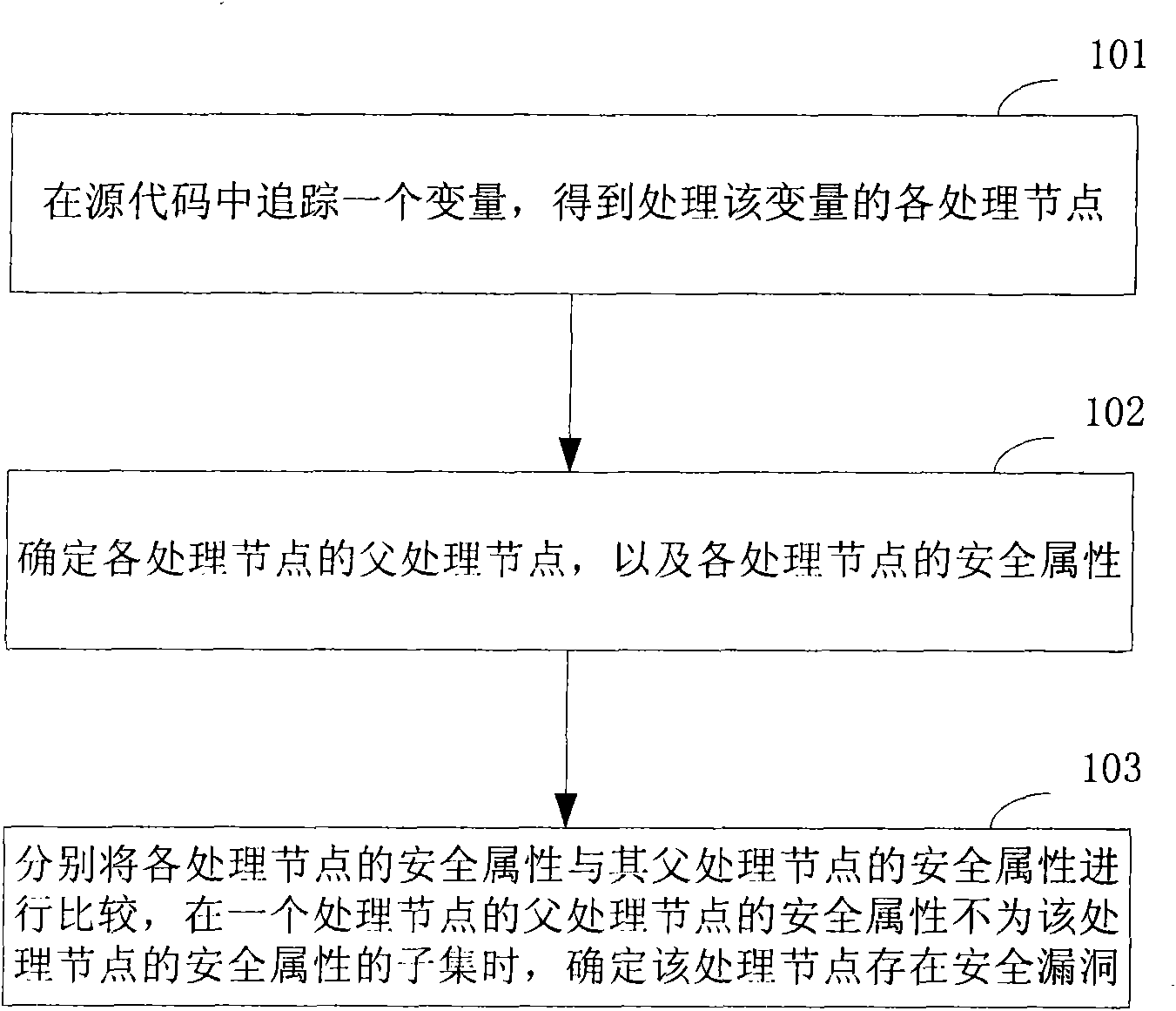
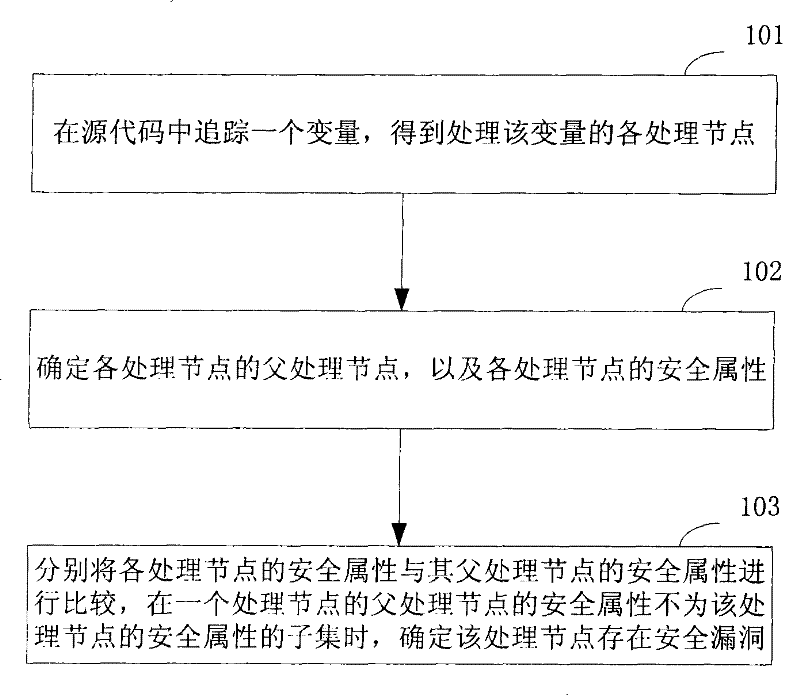
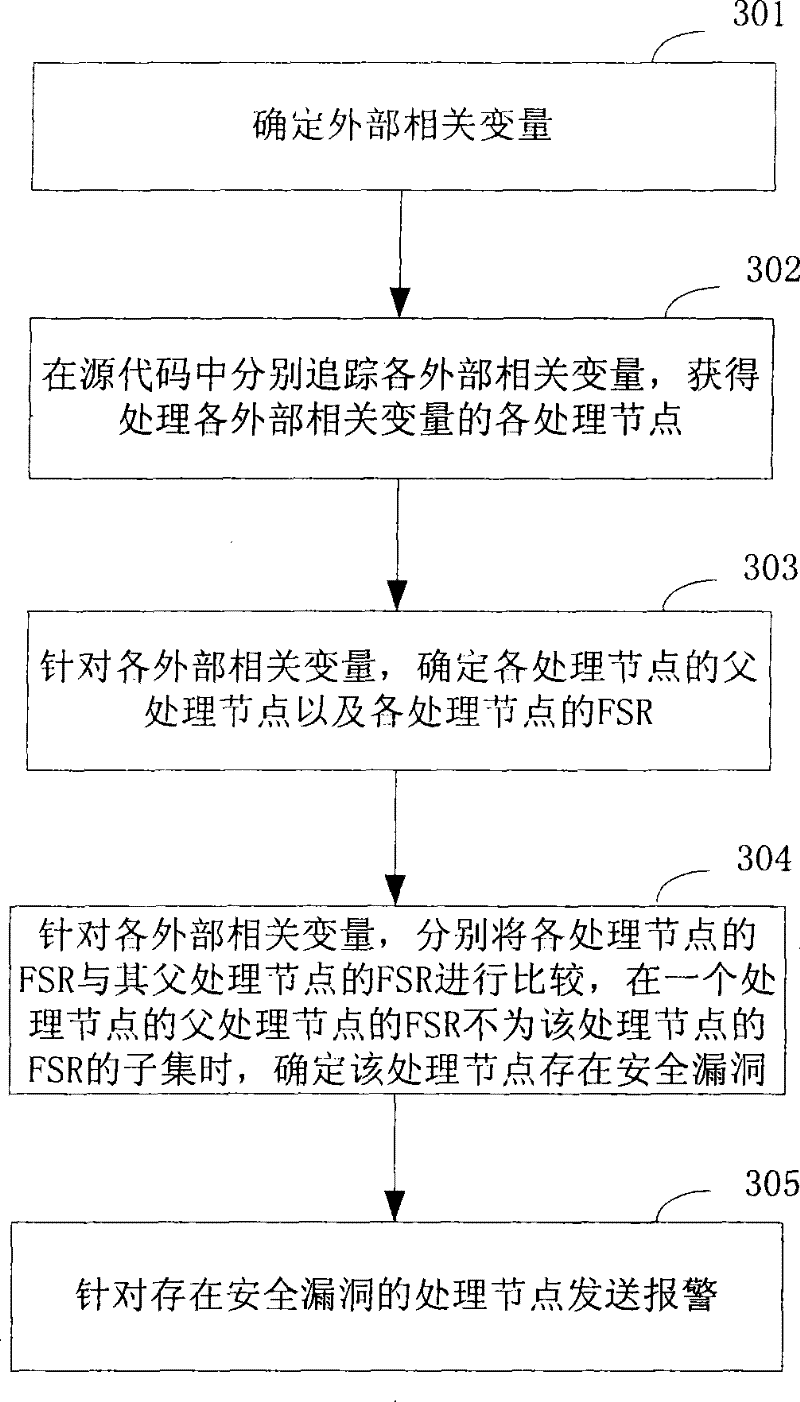
The invention discloses a code audit method comprising the steps: tracking a variable in source codes to obtain all processing nodes of the variable; determining the parent processing node and the security attribute of each processing node; respectively comparing the security attribute of each processing node with the safety attribute of the parent processing node of each processing node and determining a processing node existing security vulnerability if the security attribute of the parent processing node of the processing node is not the subset of the safety attribute of the processing node. In addition, the invention further discloses a code audit device. In the invention, with the technical scheme that the processing logic of the variable is determined if the variable has vulnerability according to the processing nodes, the accuracy of code audit can be improved, so that the safety vulnerability existing in the source codes can be truly and accurately reflected.
Owner:SIEMENS CHINA
Method for performing automated security detection on android application
InactiveCN106446689AImprove the efficiency of security hardeningAvoid safety hazardsPlatform integrity maintainanceCode snippetSecurity analysis
The invention discloses a method for performing automated security detection on an android application. The method comprises the steps of performing dex file interception on the android application through a specific android system; and then performing security detection on a source code of the android application based on a vulnerability rule base by utilizing specific findbugs. The technical scheme has the beneficial effects that code audit and vulnerability mining are fused integrally by the method, and a shelled application can be subjected to security detection; when the Android application is detected, the application does not need to be subjected to decompilation, debugging, code audit and penetration testing manually, and by utilizing the technical scheme, efficient and quick security analysis can be realized; automated security testing of massive applications can be realized; and developers are assisted to locate vulnerability key code snippets, the developers are facilitated to solve potential security hazards, and the security reinforcement efficiency of the developers is improved.
Owner:ZHONGKE INFORMATION SECURITY COMMON TECH NAT ENG RES CENT CO LTD
Meta-indexing, search, compliance, and test framework for software development using smart contracts
A system and method for meta-indexing, search, compliance, and test framework for software development using smart contracts is provided, comprising an indexing service configured to create a dataset by processing and indexing source code of a project provided by a developer, perform a code audit on the indexed source code, store results from the code audit in the dataset, gather additional information relating to the provided project, store the additional information in the dataset, and store the dataset into memory; and a monitoring service configured to continuously monitor the project for at least source code changes and make changes to the dataset as needed. Additionally, a smart contract authority creates and enforces smart contracts for every transaction taking place upon the software essentially mandating and guaranteeing the security and authenticity of the software during the software's development and use.
Owner:QOMPLX LLC
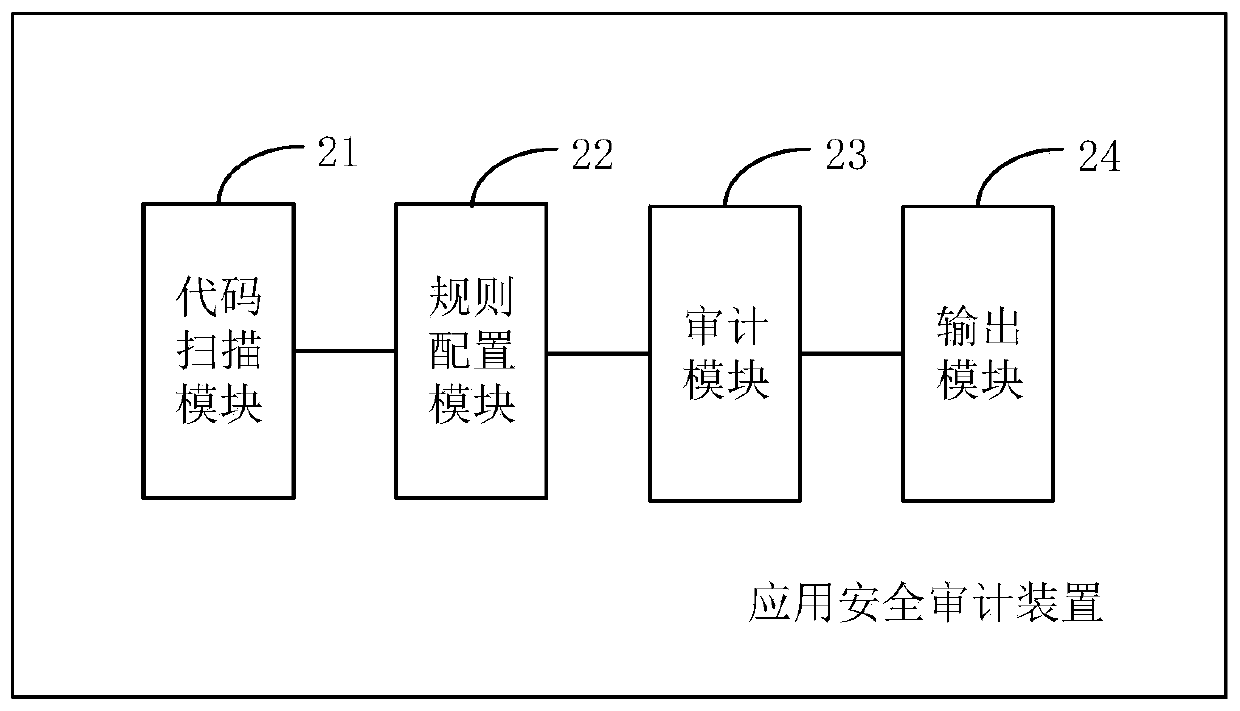
Application security auditing method and device, electronic equipment and storage medium
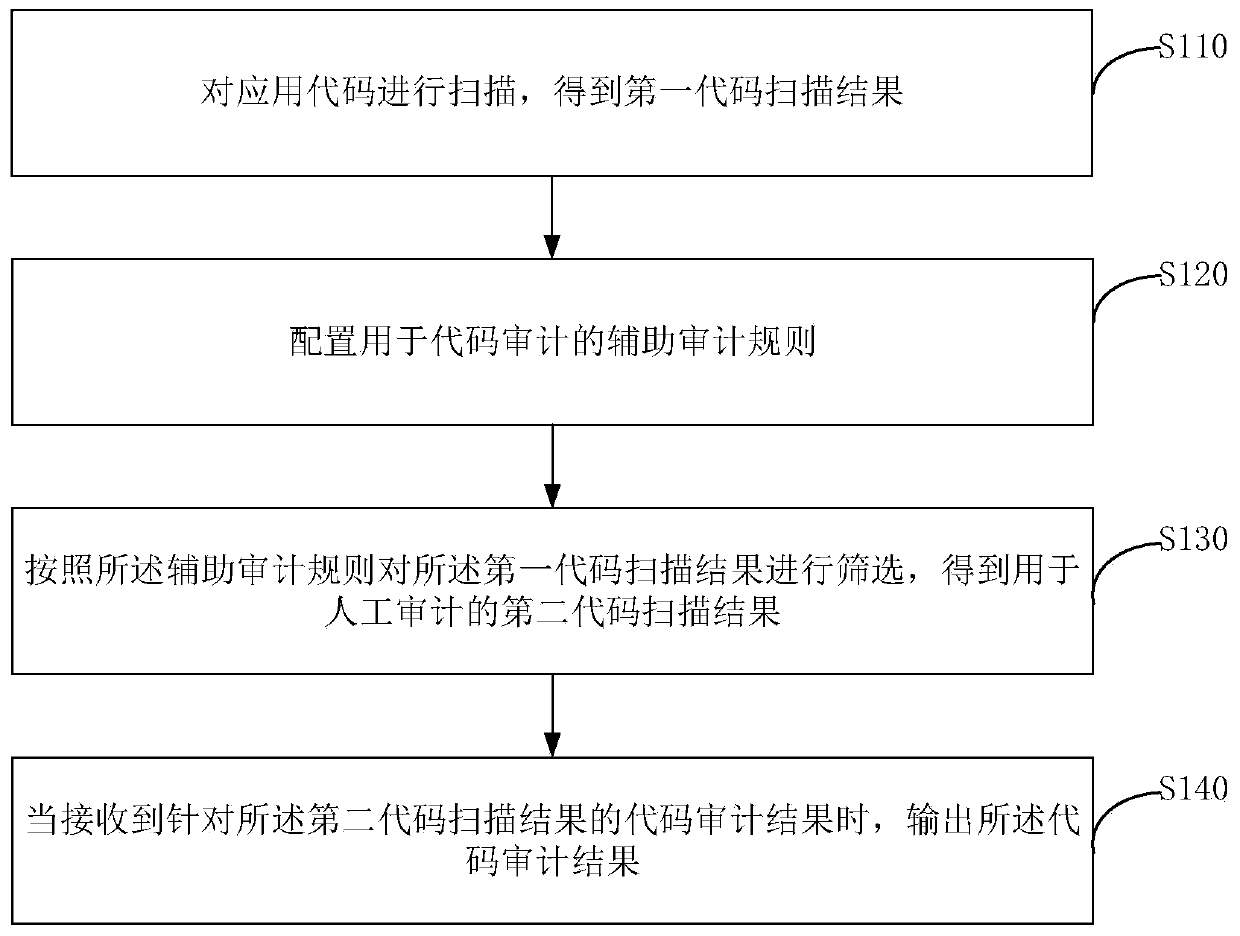
InactiveCN110968868AShorten the timeReduce a large number of false positivesPlatform integrity maintainanceProgramming languageSoftware engineering
The embodiment of the invention discloses an application security auditing method and device, electronic equipment and a storage medium, and the method comprises the steps: scanning an application code, and obtaining a first code scanning result; configuring an auxiliary auditing rule for code auditing; screening the first code scanning result according to the auxiliary auditing rule to obtain a second code scanning result for manual auditing; and when a code auditing result for the second code scanning result is received, outputting the code auditing result. Therefore, the auxiliary auditingof the manual auditing is realized, the manual auditing time and a large amount of false alarms are reduced, and the application security auditing efficiency is improved.
Owner:北京国舜科技股份有限公司
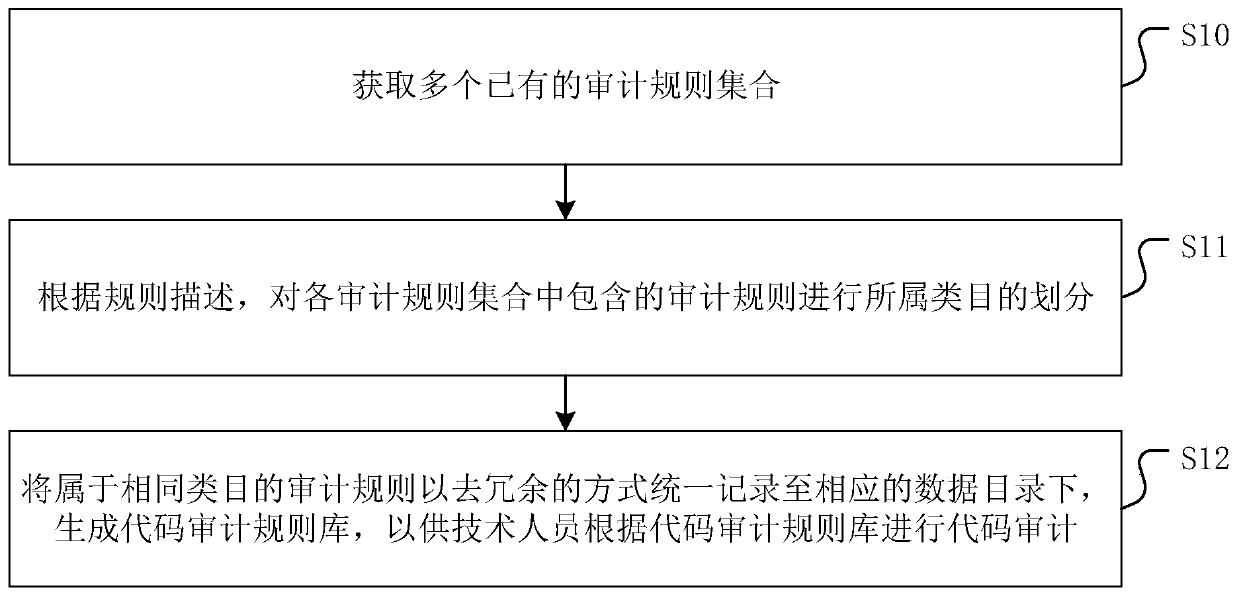
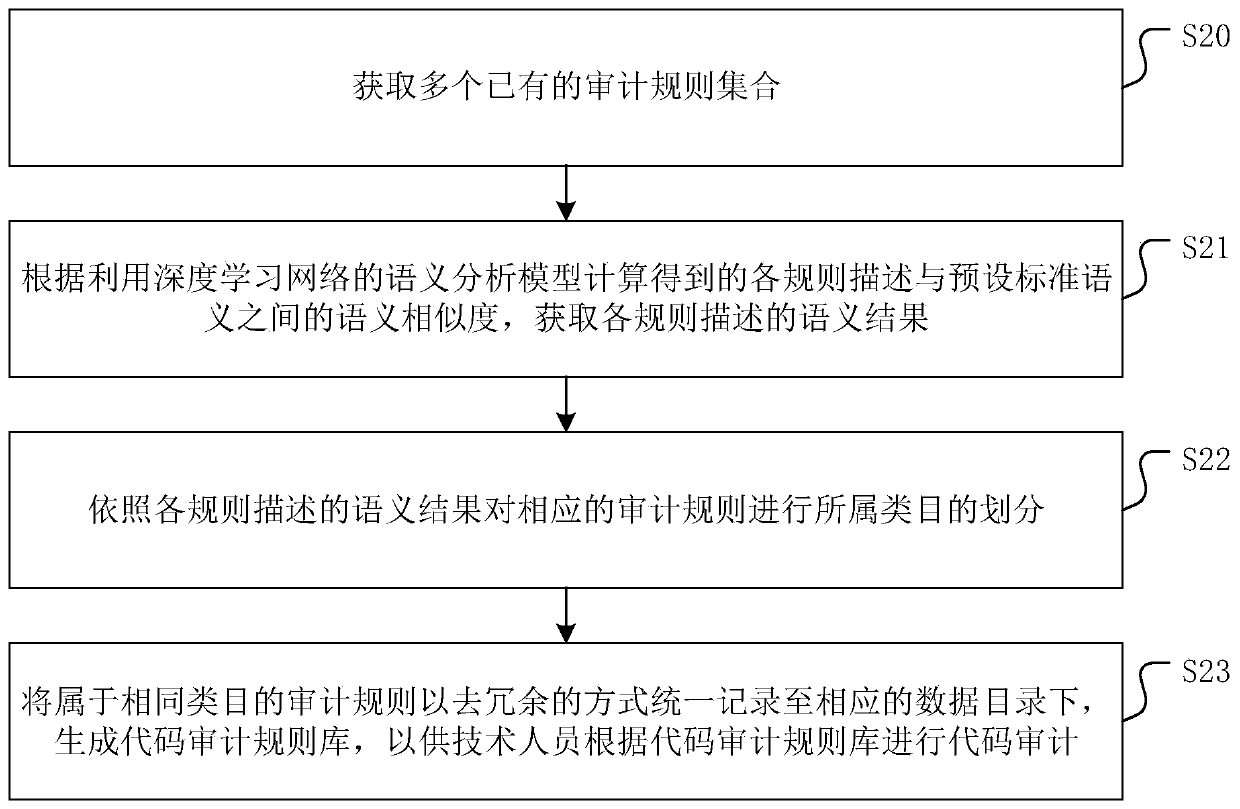
Code auditing rule base generation method and device, equipment and medium
ActiveCN110109678AAudit implementationGood library maintenance abilityEnergy efficient computingCode compilationProgramming languageCode audit
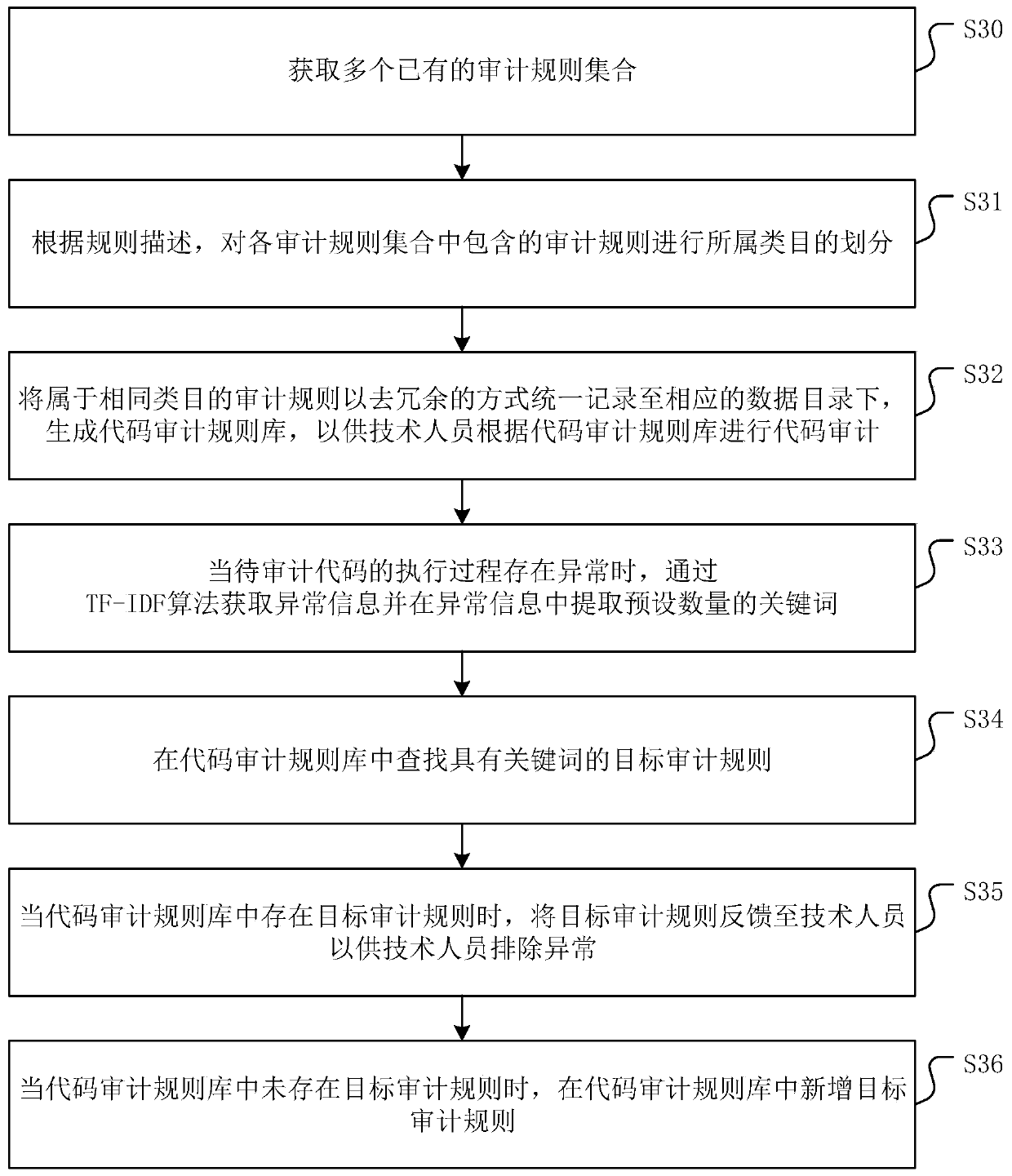
The invention discloses a code auditing rule base generation method and device, equipment and a medium. The method comprises the following steps: obtaining a plurality of existing auditing rule sets;wherein each audit rule set comprises one or more audit rules, and each audit rule has corresponding rule description; according to the rule description, carrying out category division on audit rulescontained in each audit rule set; and uniformly recording the auditing rules belonging to the same category in a corresponding data directory in a redundancy removal manner, and generating a code auditing rule base for technical personnel to perform code auditing according to the code auditing rule base. The code auditing rule base generated by the method has good base maintenance capability, canrelatively reduce the overall manpower cost required by code auditing, and ensures the comprehensiveness and accuracy of code auditing. In addition, the invention further provides a code auditing rulebase generation device and equipment and a medium, and the beneficial effects are the same as those mentioned above.
Owner:GUANGDONG POWER GRID CO LTD +1
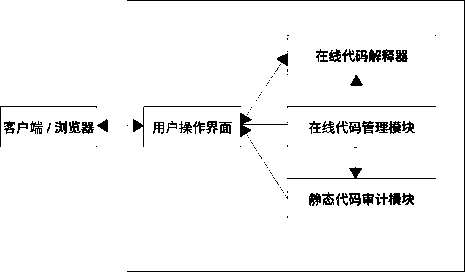
Static code analyzing system and method capable of being debugged online
PendingCN108399133ADiscover security risksAssist in reviewSoftware testing/debuggingCode compilationProgramming languageAnalysis method
The invention discloses a static code analyzing system and method capable of being debugged online. The method comprises four main parts of an online code managing module, a static code auditing module, an online code interpreter and a user operating interface. According to the method, a user is allowed to conduct version control on project codes through the online code managing module, the staticcode auditing module can automatically conduct safety analysis on the project codes, and possible defect codes and defects types are listed. The user can browse and edit codes on the user operating interface, and method tracing and breakpoint setting operations can be conducted on the codes on the user operating interface, so that the project defect and the repairing method can be quickly determined.
Owner:曾鸿坤
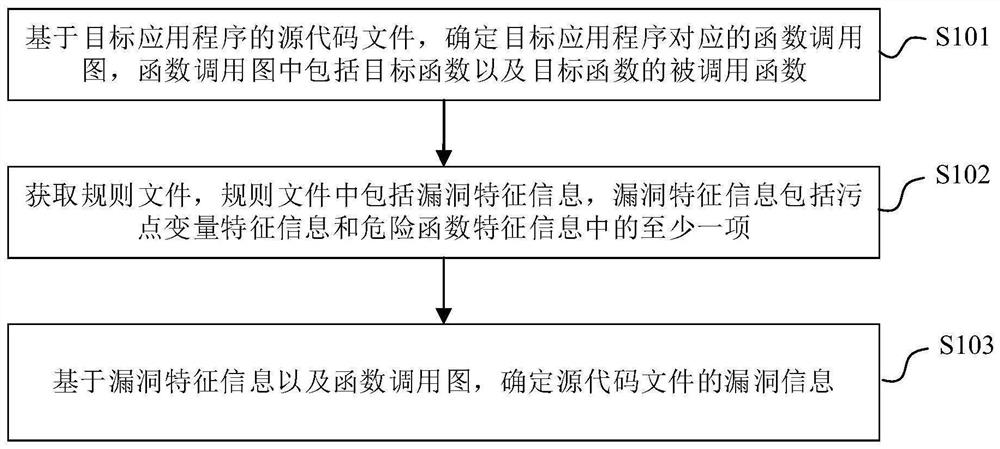
Code auditing method and device, electronic equipment and medium
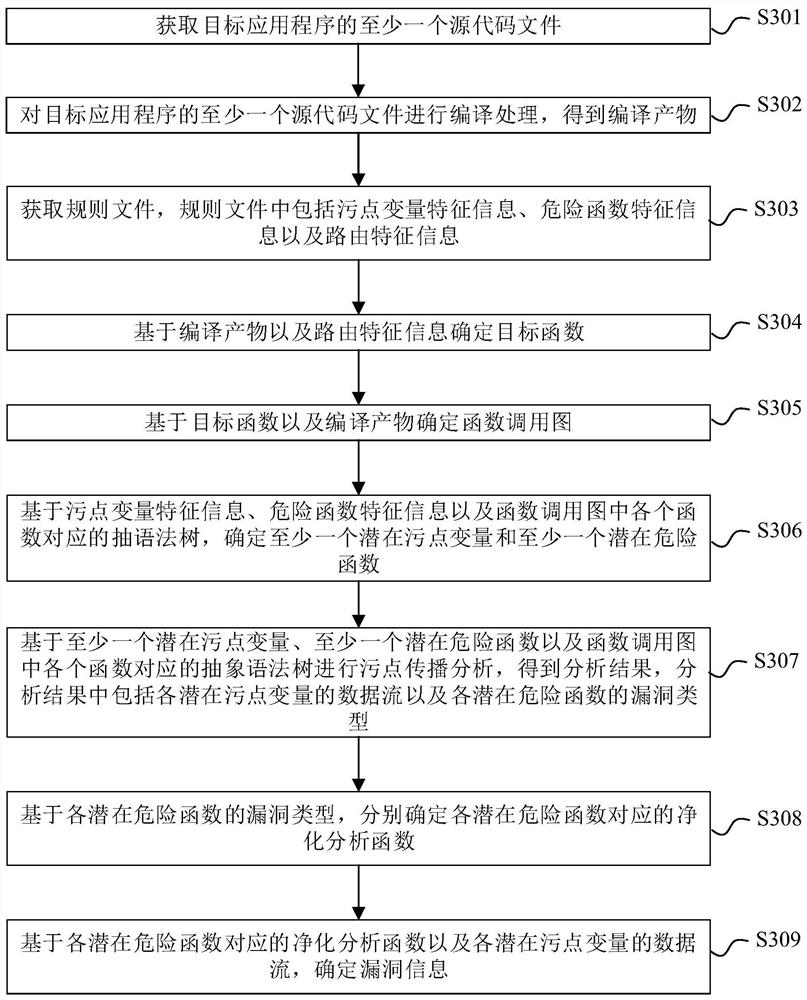
ActiveCN111666218AReduce consumptionReduce dependenceInterprogram communicationSoftware testing/debuggingSource code fileCall graph
The invention provides a code auditing method and device, electronic equipment and a medium. The method comprises the following steps: based on a source code file of a target application, determininga function call graph corresponding to the target application program, wherein the function call graph comprises a target function and a called function of the target function; and obtaining a rule file, the rule file including vulnerability feature information, the vulnerability feature information including at least one of stain variable feature information and danger function feature information, and determining vulnerability information of the source code file based on the vulnerability feature information and the function call graph. The false alarm rate is reduced, and the development efficiency is improved.
Owner:BEIJING BYTEDANCE NETWORK TECH CO LTD
System and method for implementing a code audit tool
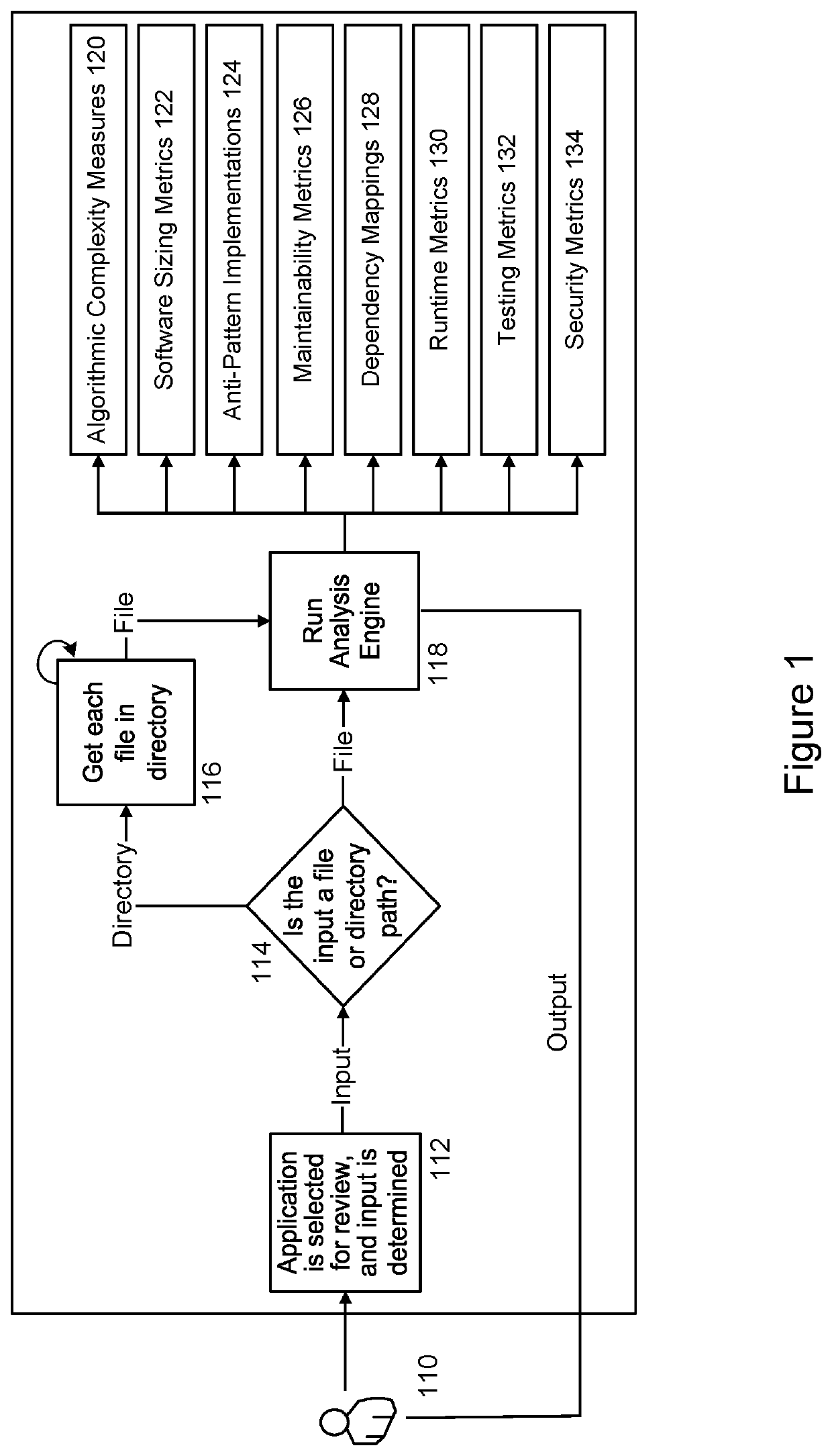
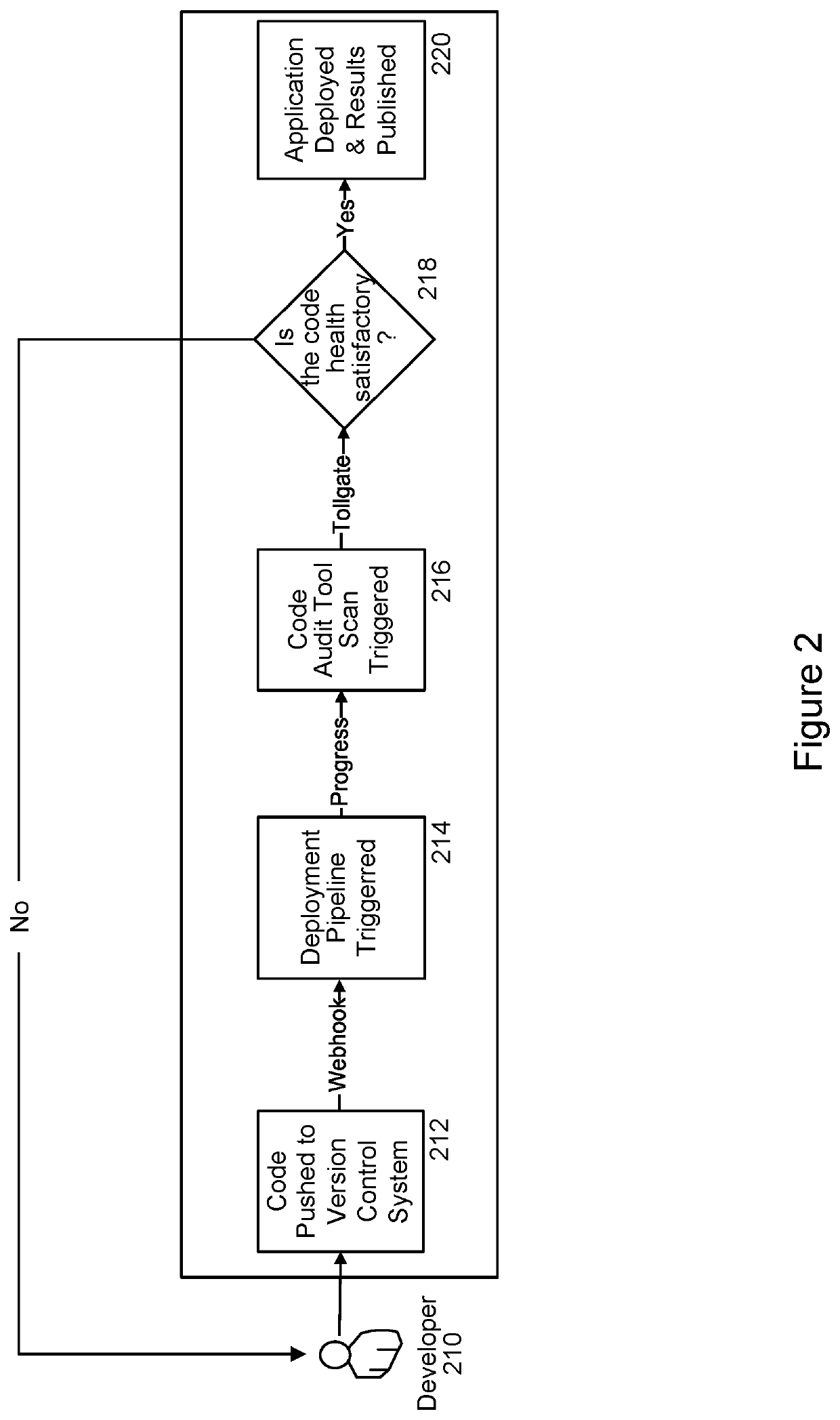
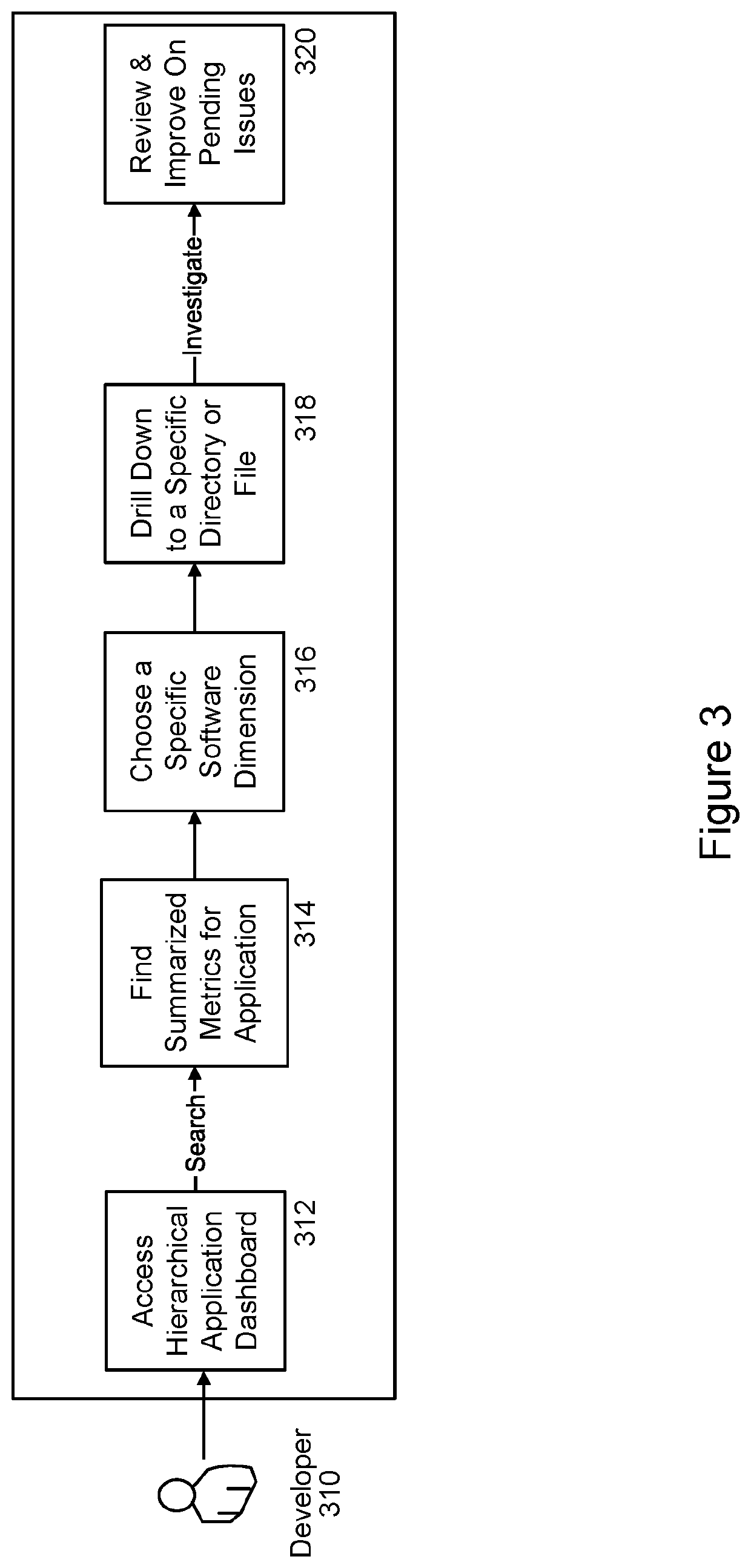
PendingUS20210406004A1Improve code health determinationGood for healthReverse engineeringSoftware metricsSecurity metricMaintainability
An embodiment of the present invention is directed to a code audit tool that intelligently analyzes and profiles code, such as Python code, based on a variety of previously unmeasured factors and metrics including a set of software dimensions, such as Algorithmic Complexities; Software Sizing Metrics; Anti-Pattern Implementations; Maintainability Metrics; Dependency Mappings; Runtime Metrics; Testing Metrics; and Security Metrics. Once this analysis is complete, a standardized report card or other scoring interface may be generated. This may include analytical findings as well as suggestions and recommend steps so that developers can make informed decisions, enhance their code bases and improve the score assigned to their code.
Owner:JPMORGAN CHASE BANK NA
Code auditing method and device, electronic equipment and medium
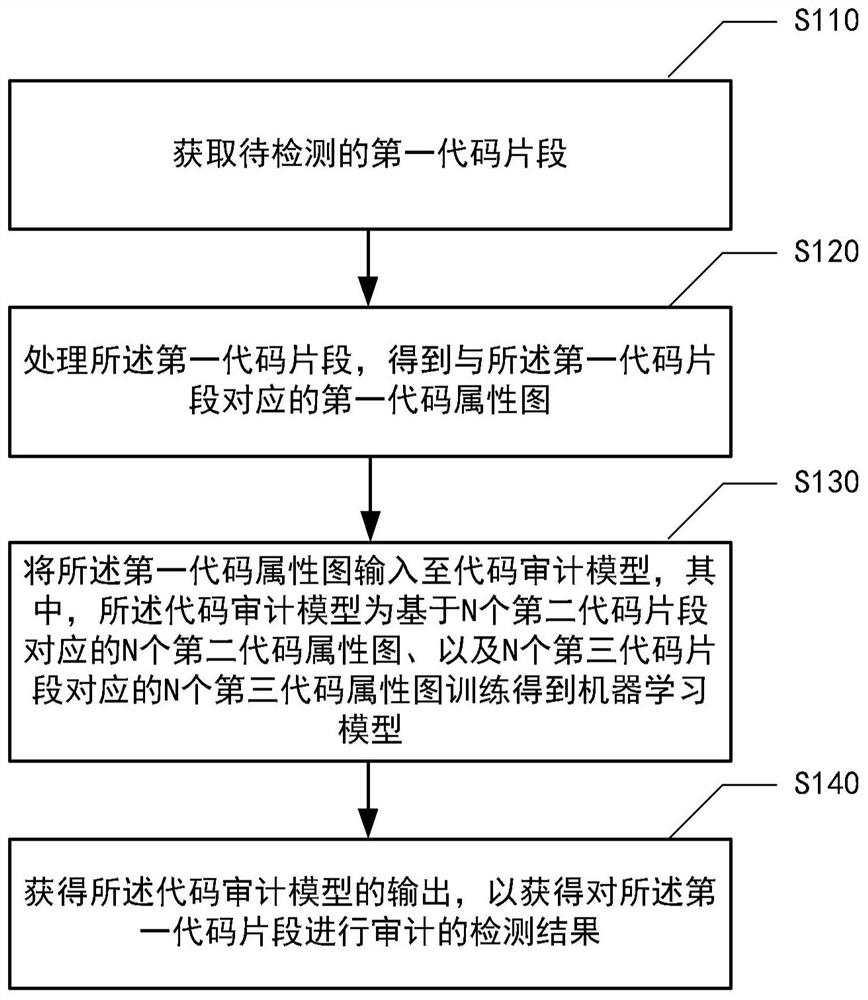
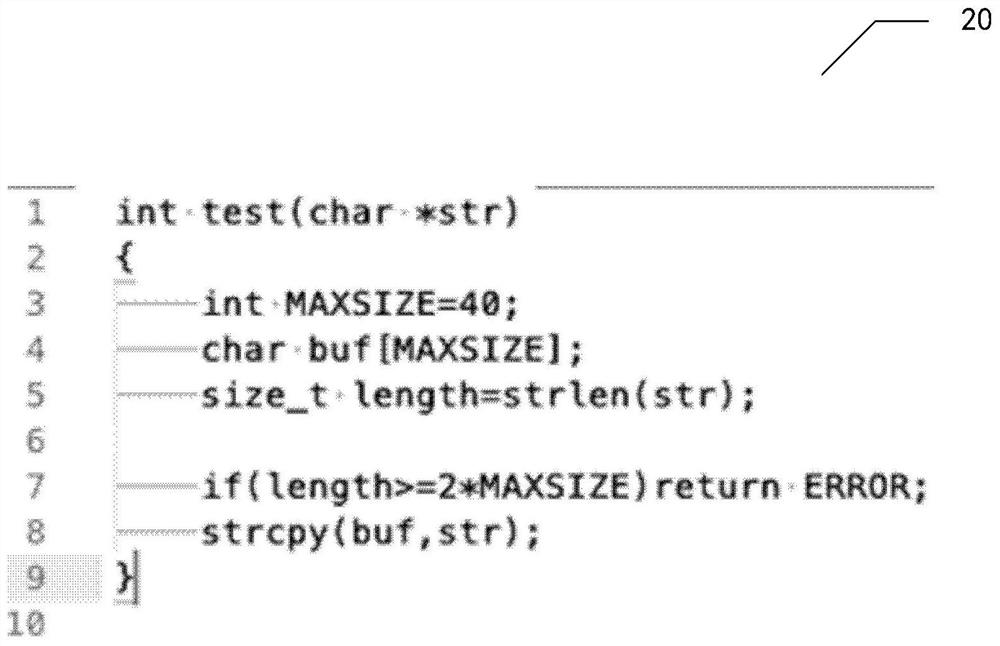
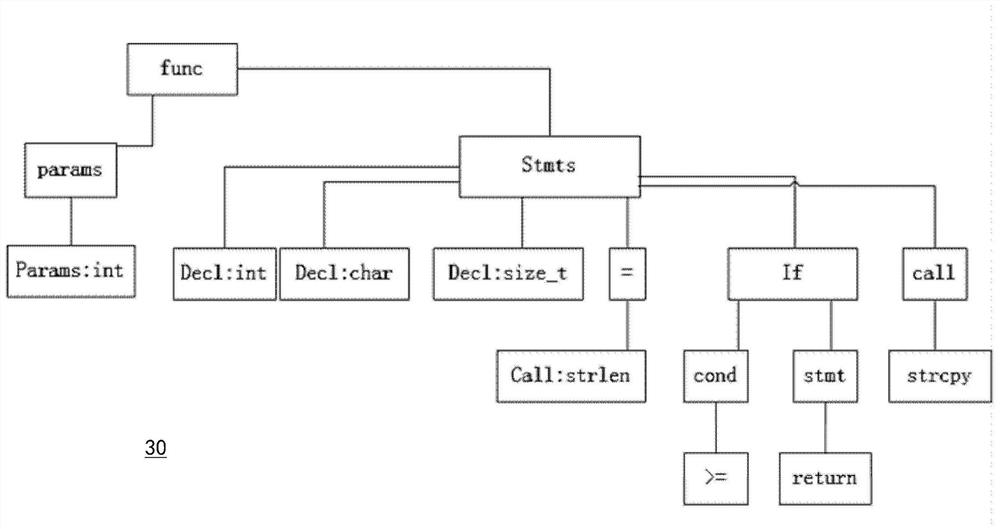
PendingCN111832028AReduce error rateImprove detection accuracyPlatform integrity maintainanceNeural architecturesCode snippetTheoretical computer science
The invention relates to the technical field of artificial intelligence, and provides a code auditing method and device. The code auditing method comprises the following steps: acquiring a to-be-detected first code fragment; processing the first code snippet to obtain a first code attribute graph corresponding to the first code snippet; inputting the first code attribute graph into a code auditingmodel, wherein the code auditing model is a machine learning model obtained by training based on N second code attribute graphs corresponding to N second code snippets and N third code attribute graphs corresponding to N third code snippets; wherein the second code snippets are code snippets with bugs, and the third code snippets are code snippets obtained after bugs in the second code snippets are repaired; and obtaining an output of the code auditing model to obtain a detection result of auditing the first code snippet. The invention further provides a training method and device of the codeauditing module, electronic equipment and a medium.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Meta-indexing, search, compliance, and test framework for software development
A system for meta-indexing, search, compliance, and test framework for software development is provided, comprising an indexing service configured to create a dataset by processing and indexing source code of a project provided by a developer, perform a code audit on the indexed source code, store results from the code audit in the dataset, gather additional information relating to the provided project, store the additional information in the dataset, and store the dataset into memory; and a monitoring service configured to continuously monitor the project for at least source code changes and make changes to the dataset as needed.
Owner:QOMPLX INC
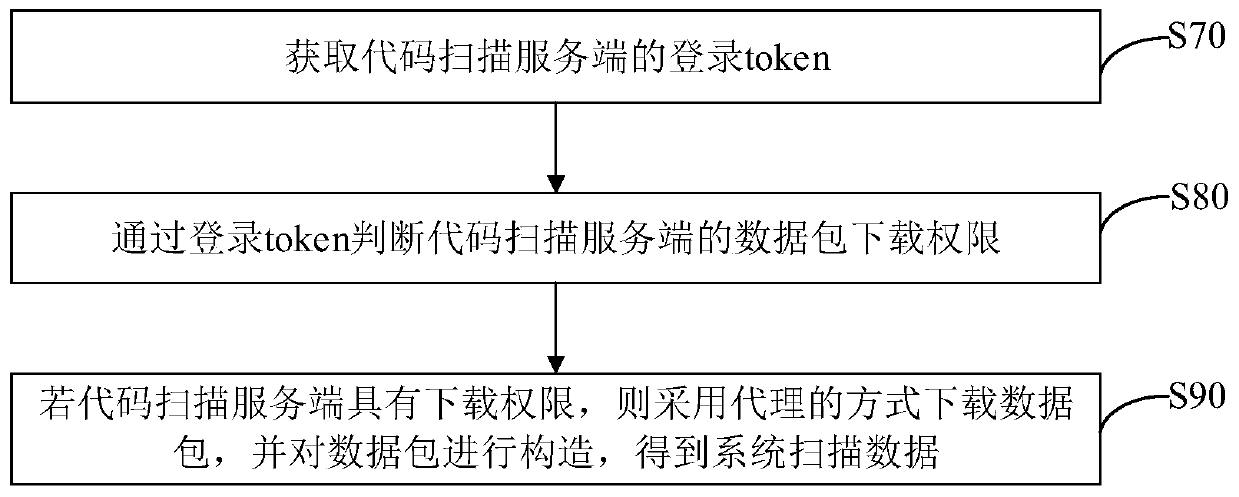
Code scanning result processing method and device, computer equipment and storage medium
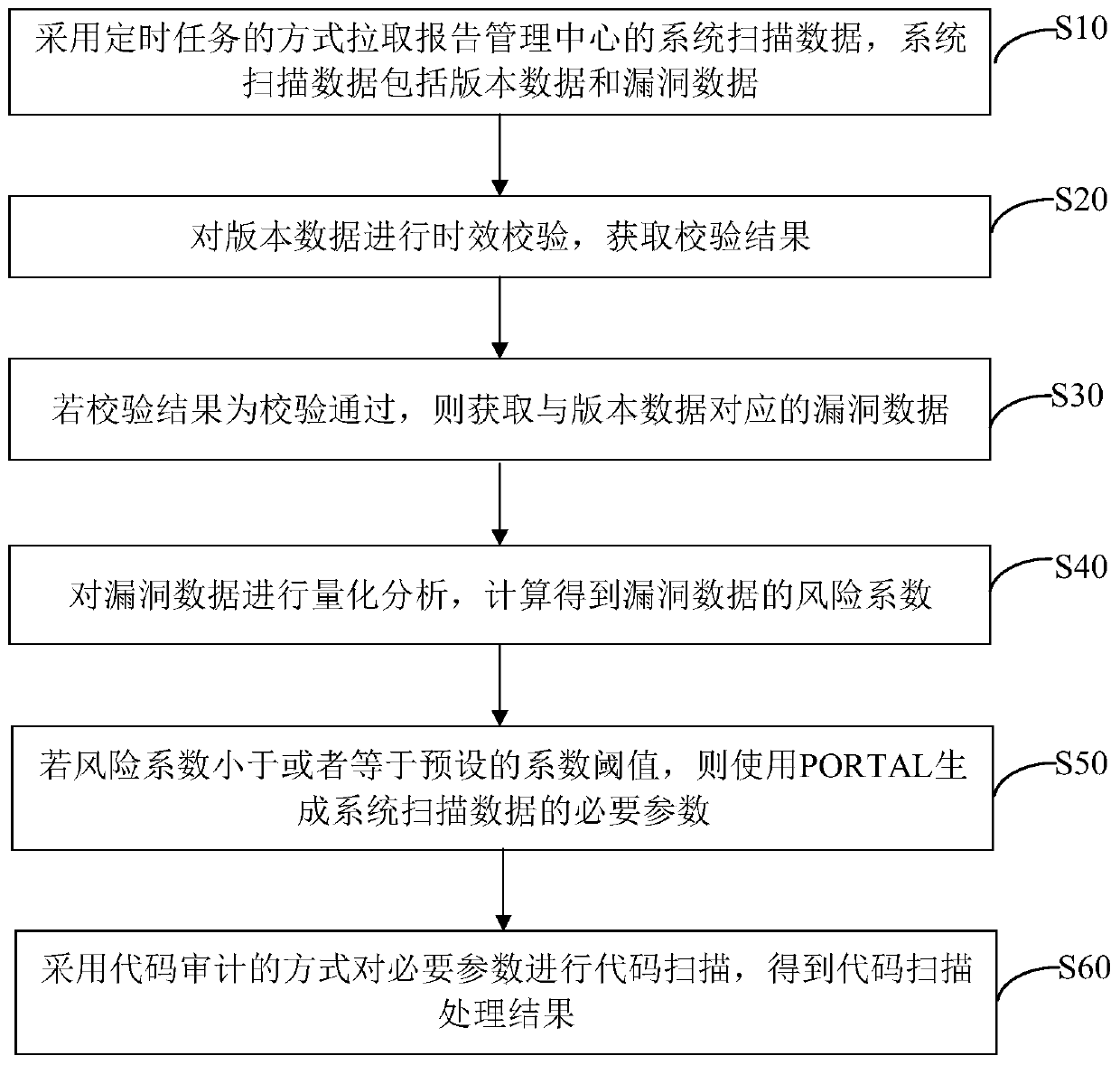
PendingCN110990249AImprove processing efficiencyImprove securitySoftware testing/debuggingData packAlgorithm
The invention discloses a code scanning result processing method and a device, computer equipment and a storage medium. The method comprises the steps of pulling system scanning data of a report management center in a timed task mode, and the system scanning data comprise version data and vulnerability data; performing aging verification on the version data to obtain a verification result; if theverification result is that the verification is passed, obtaining vulnerability data corresponding to the version data; performing quantitative analysis on the vulnerability data, and performing calculation to obtain a risk coefficient of the vulnerability data; if the risk coefficient is smaller than or equal to a preset coefficient threshold, generating necessary parameters of system scanning data by using PORTAL; performing code scanning on the necessary parameters in a code auditing mode, and obtaining a code scanning processing result. According to the code scanning result processing method, the comprehensive integrity of vulnerability repair can be guaranteed, and the efficiency and safety of code scanning processing result processing are improved.
Owner:PING AN TECH (SHENZHEN) CO LTD
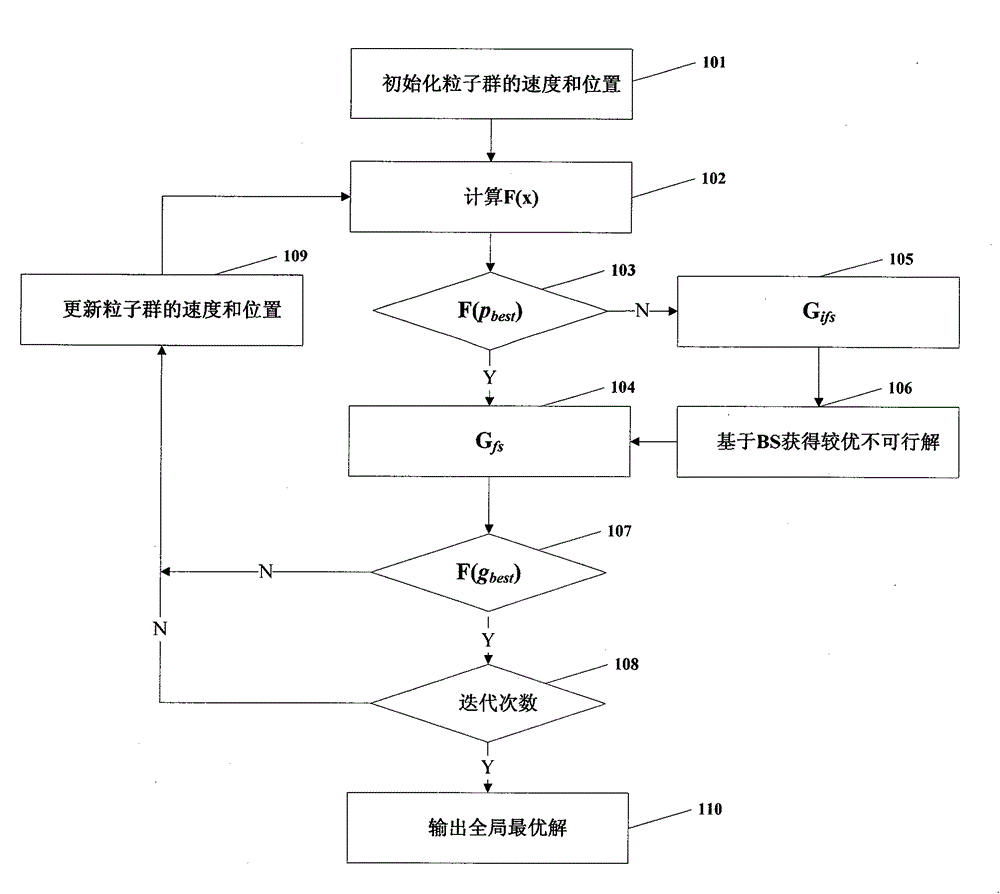
Code auditing method for particle swarm optimization based on bubble sort
InactiveCN103823752AAccurate solutionBiological modelsSoftware testing/debuggingCode auditParticle swarm algorithm
The invention discloses a code auditing method for particle swarm optimization based on bubble sort. The method includes: initializing a particle swarm; testing a path and calculating a fitness function value; on the basis of using a feasible rule for constraint solution, dividing the particle swarm into feasible particles and infeasible particles, and putting the feasible particles and the infeasible particles into two vessels; retaining infeasible particles low in violation degree on the basis of the bubble sort, and putting the retained infeasible particles in the feasible particle swarm to solve the problem that a global optimal point is positioned close to a constrained boundary; finally working out a shortest path of defected codes to avoid the problem of proneness to fall into premature convergence when particle swarm optimization is applicable to code audit aiming at paths.
Owner:BEIJING SAFE CODE TECH
A fine-grained source code vulnerability detection method based on graph neural network
ActiveCN111259394BImprove audit efficiencyHigh degree of automationPlatform integrity maintainanceNeural architecturesData setAlgorithm
The invention discloses a fine-grained source code vulnerability detection method based on a graph neural network, including the following: A. For all source codes of a software, extract the code attribute graph of the function in the source code, and perform vectorized representation of the code attribute graph , the vectorized representation includes the vectorized representation of node attributes and graph structure; B, uses the graph attention network to extract code features, and processes all sentences to obtain the final data set; C, trains the vulnerability detection model, and passes the effect on the test set Determine the final model. The source code vulnerability detection method provided by the invention has a higher degree of automation, reduces the dependence on domain expert knowledge, greatly saves the cost of code auditing, improves the efficiency of code auditing, and better retains the syntax and semantic information in the source code. , while using the graph attention network can more purposefully learn the vectorized representation of sentences and achieve more fine-grained sentence-level vulnerability detection.
Owner:SUN YAT SEN UNIV
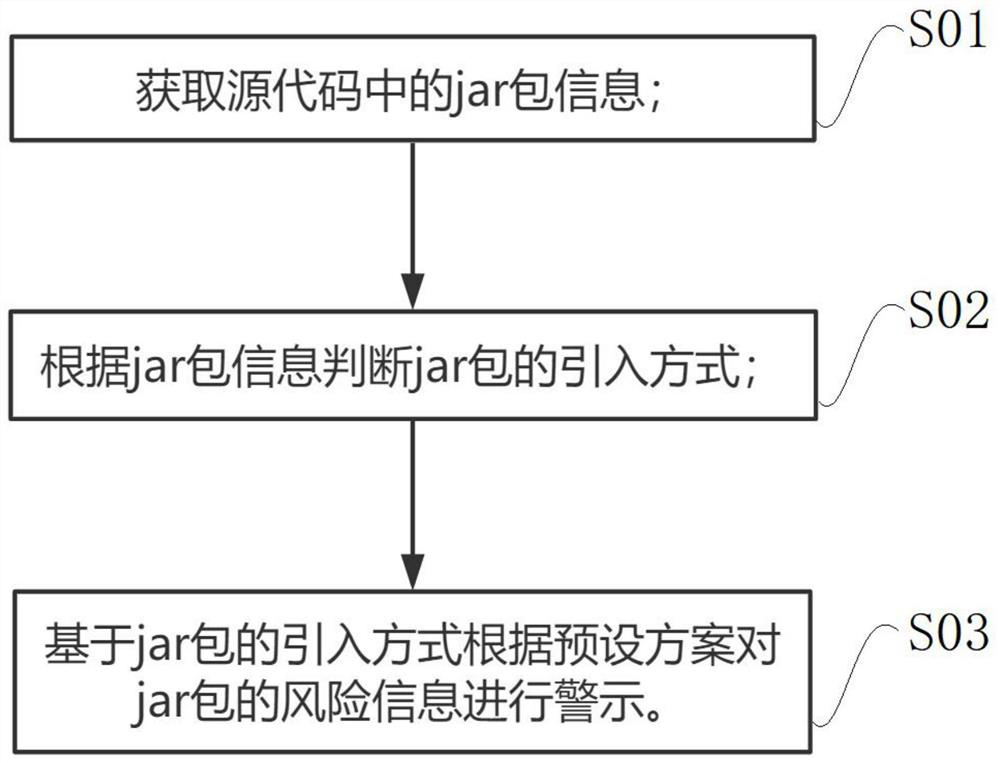
Vulnerability analysis method and device for source code package, terminal and storage medium
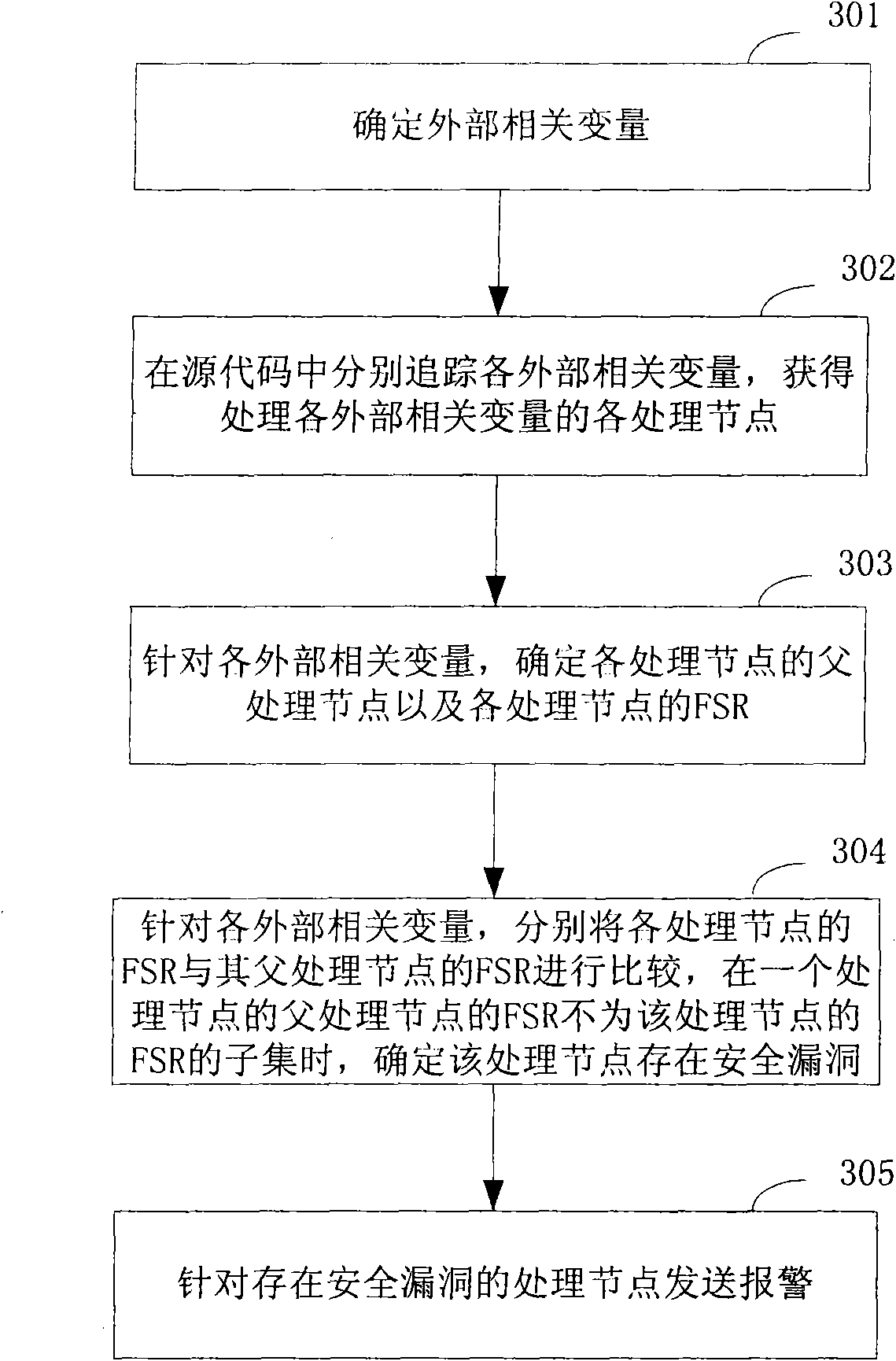
PendingCN113886823AReduce unpredictable risksPlatform integrity maintainanceProgram loading/initiatingJARCode audit
The invention relates to the field of code auditing, in particular to a vulnerability analysis method and device for a source code package, a terminal and a storage medium, and the method comprises the following steps: obtaining jar package information in a source code; judging an introduction mode of the jar packet according to the jar packet information; and warning the risk information of the jar packet according to a preset scheme based on the introduction mode of the jar packet. According to the method and the device, a code auditor can intuitively find the risk information hidden in the jar package of the source code, so that a developer is urged to replace or upgrade by using another jar package, and the unpredictable risk existing in the process of using the source code is reduced.
Owner:SECZONE TECH CO LTD
Code audit method and device
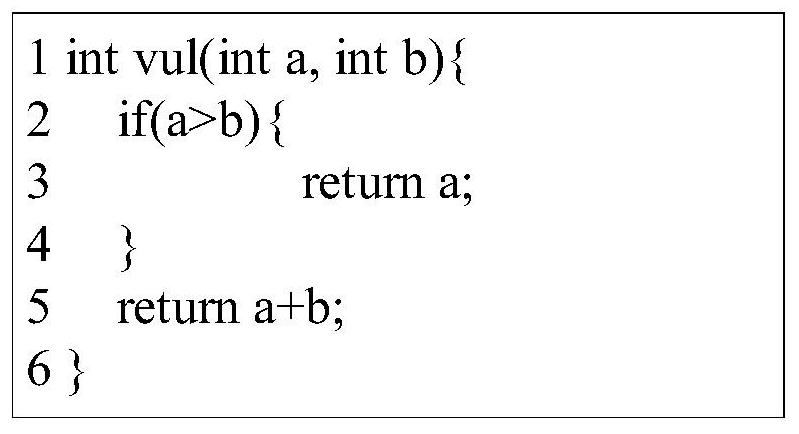
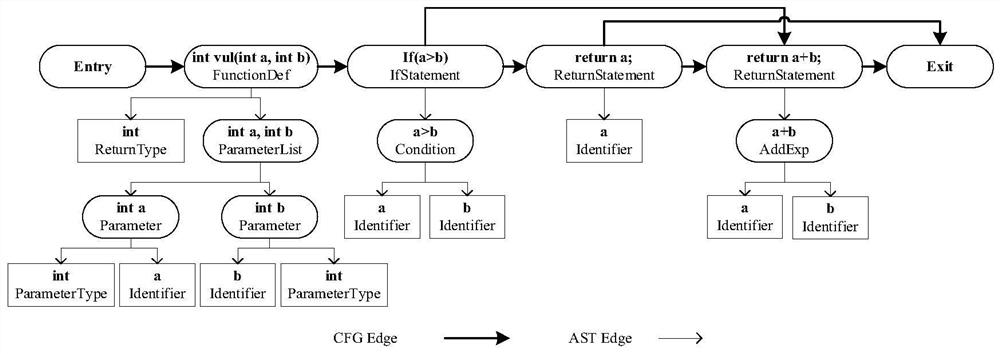
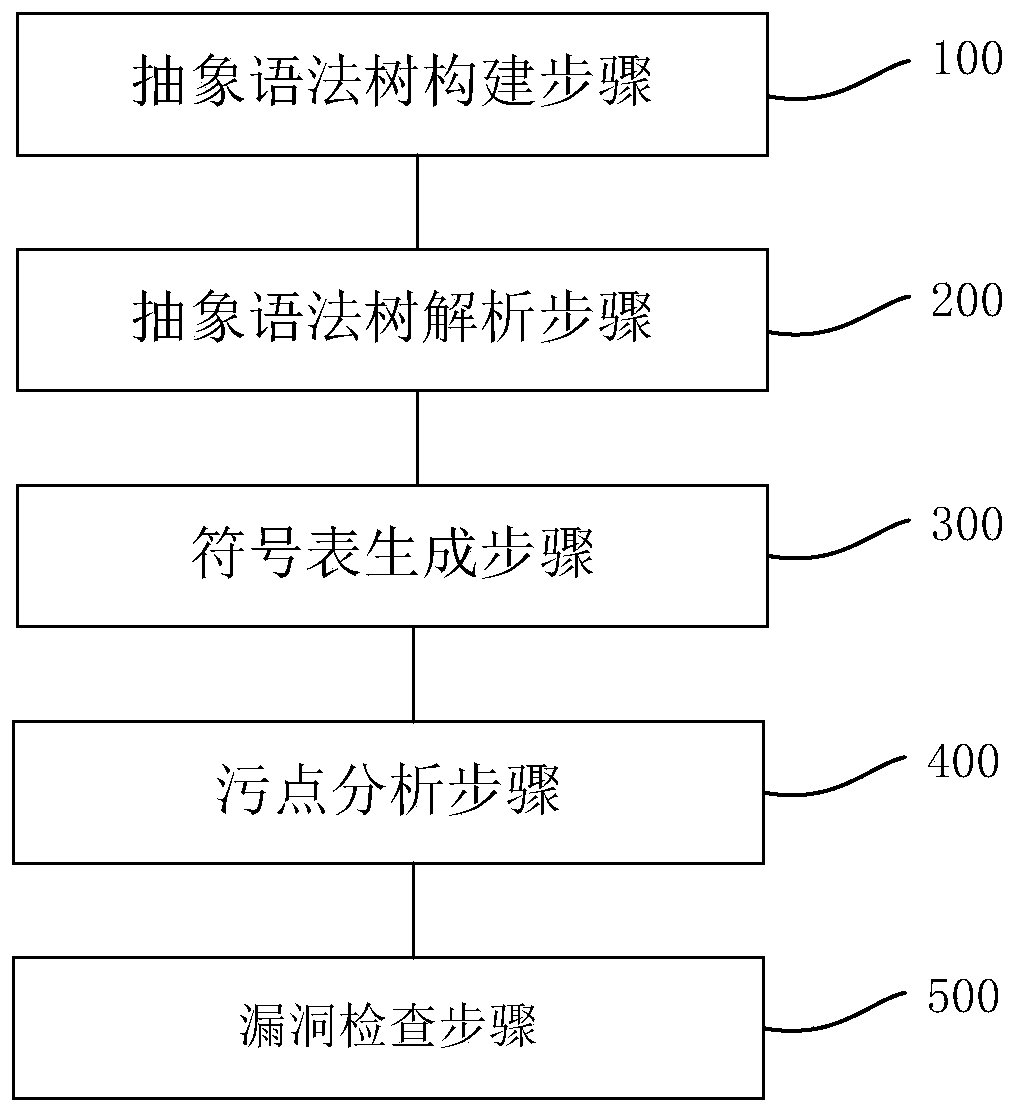
ActiveCN110059006BImprove detection efficiencySoftware testing/debuggingSource code fileStructure analysis
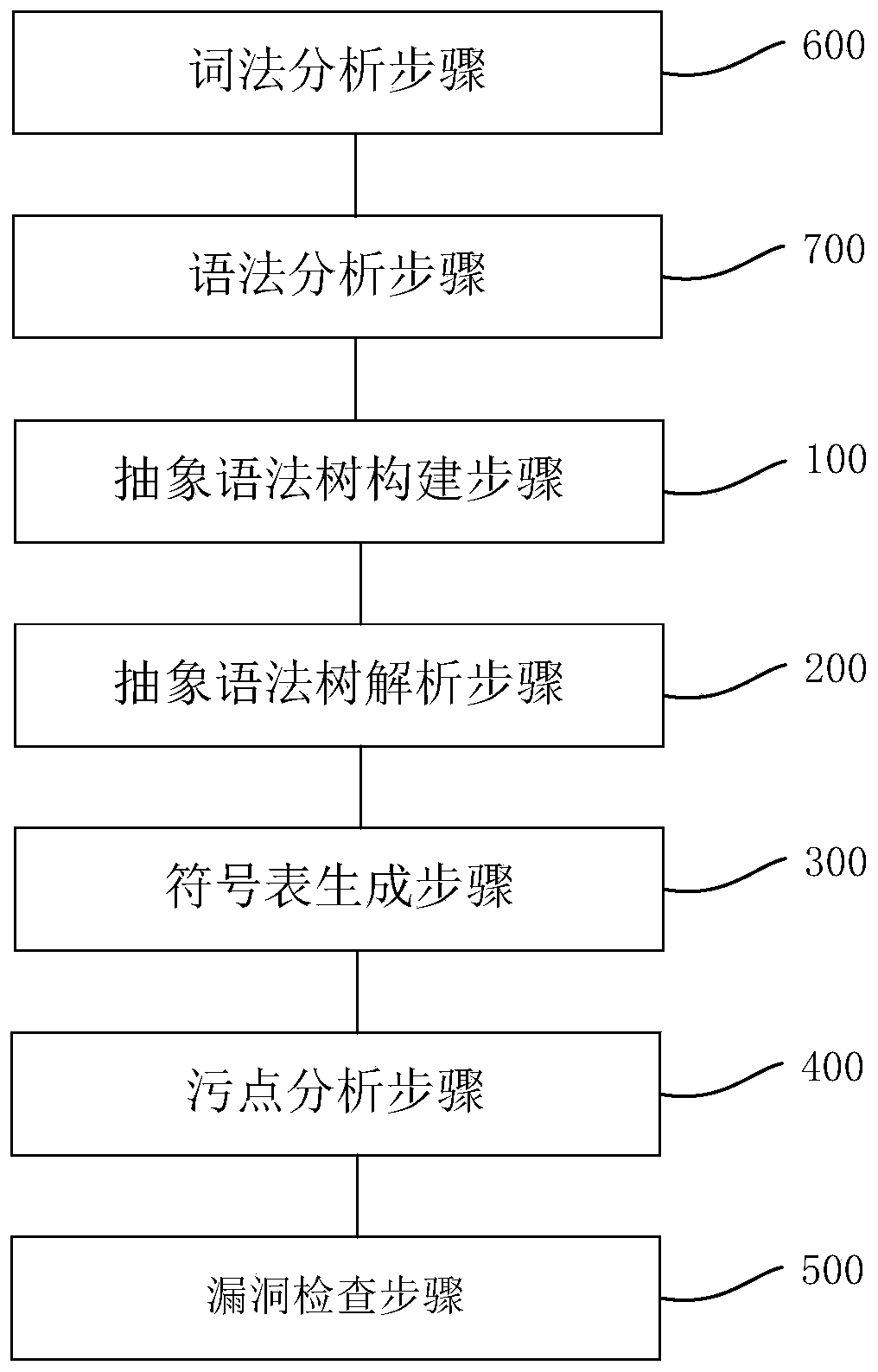
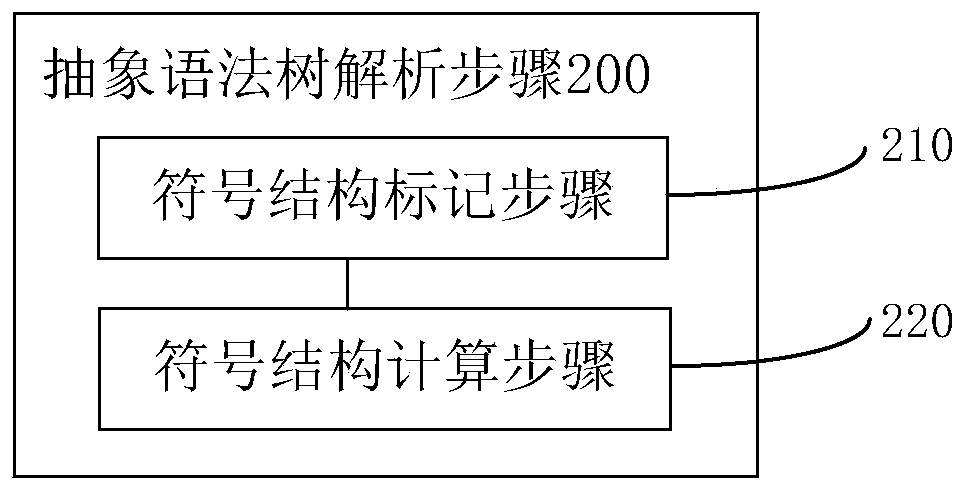
The embodiment of the invention relates to the technical field of information security maintenance, and provides a code auditing method and device, and the method comprises the steps: obtaining an abstract syntax tree based on a program source code file, with the abstract syntax tree comprising nodes for representing a syntax structure of the program source code file; based on a stain database, conducting grammatical structure analysis on the nodes to obtain a symbol structure, wherein the symbol structure comprise the first symbol structure marked by stain symbols and / or the second symbol structure not marked by the stain symbols; generating a symbol table based on the symbol structure calculation, with the symbol table comprising node symbols matched with the program source code; performing stain analysis on the symbol table to obtain a stain symbol table and a stain execution path table; traversing the stain symbol table and the stain execution path table to obtain potential vulnerabilities which comprise stain symbols with stain execution paths. According to the embodiment of the invention, the codes can be audited by combining context semantics, and code auditing efficiency and accuracy are improved.
Owner:BEIJING CHUANGXIN JOURNEY NETWORK TECH CO LTD
Code audit method and device
ActiveCN101551836BImprove accuracyImprove audit efficiencyError detection/correctionPlatform integrity maintainanceComputer networkCode audit
The invention discloses a code audit method comprising the steps: tracking a variable in source codes to obtain all processing nodes of the variable; determining the parent processing node and the security attribute of each processing node; respectively comparing the security attribute of each processing node with the safety attribute of the parent processing node of each processing node and determining a processing node existing security vulnerability if the security attribute of the parent processing node of the processing node is not the subset of the safety attribute of the processing node. In addition, the invention further discloses a code audit device. In the invention, with the technical scheme that the processing logic of the variable is determined if the variable has vulnerability according to the processing nodes, the accuracy of code audit can be improved, so that the safety vulnerability existing in the source codes can be truly and accurately reflected.
Owner:SIEMENS CHINA
Code auditing method and device, terminal and storage medium
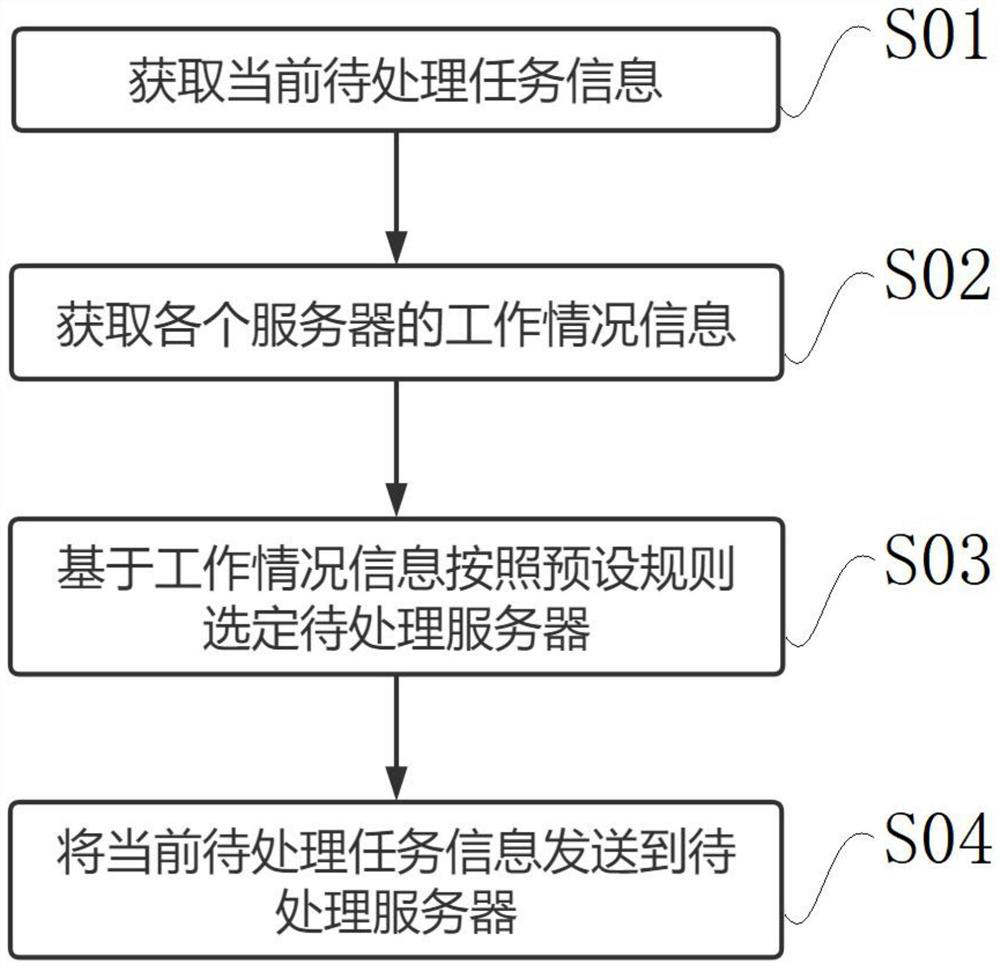
PendingCN113886076AImprove audit efficiencyProgram initiation/switchingResource allocationEngineeringCode audit
The invention relates to the field of source code auditing, in particular to a code auditing method and device, a terminal and a storage medium, a plurality of servers are provided for processing code auditing tasks, and the method comprises the steps of obtaining current to-be-processed task information; obtaining working condition information of each server; selecting a to-be-processed server according to a preset rule based on the working condition information; and sending the current task information to be processed to the server to be processed. According to the method, the multiple servers are set for code auditing at the same time, and if a new code auditing task occurs, which server is allocated to execute code auditing is determined according to the working condition information of each server, so the code auditing efficiency is improved.
Owner:SECZONE TECH CO LTD
A source code vulnerability detection method based on deep learning
ActiveCN110011986BReduce audit costsImprove audit efficiencyCharacter and pattern recognitionTransmissionFeature extractionAlgorithm
Owner:SUN YAT SEN UNIV
Automated compliance and testing framework for software development
ActiveUS20210397447A1Access to such functionalityCryptography processingVersion controlSoftware development processData set
A system for enforcing compliance and testing for software development, comprising an indexing service configured to create a dataset by processing and indexing source code of a project by a developer, perform a code audit on the indexed source code, store results from the code audit in the dataset, gather additional information relating to the provided project, store the additional information in the dataset, and store the dataset into memory; and a monitoring service configured to continuously monitor the project for source code changes and make changes to the dataset as needed. Further comprising an enforcement module to automatically verify code and other media related to the software development process by ensuring obligations from a rules database are met and where not able to automate the compliance check forward to an appropriate authority, receive back the manually reviewed compliance check, then produce and implement automated recommendations for compliance adherence.
Owner:QOMPLX INC
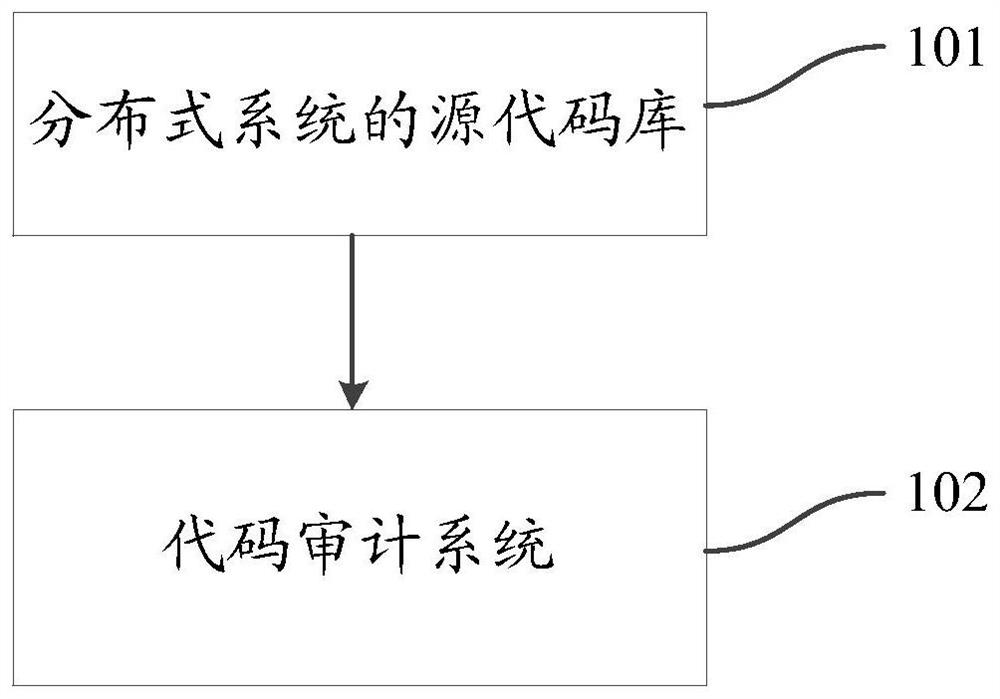
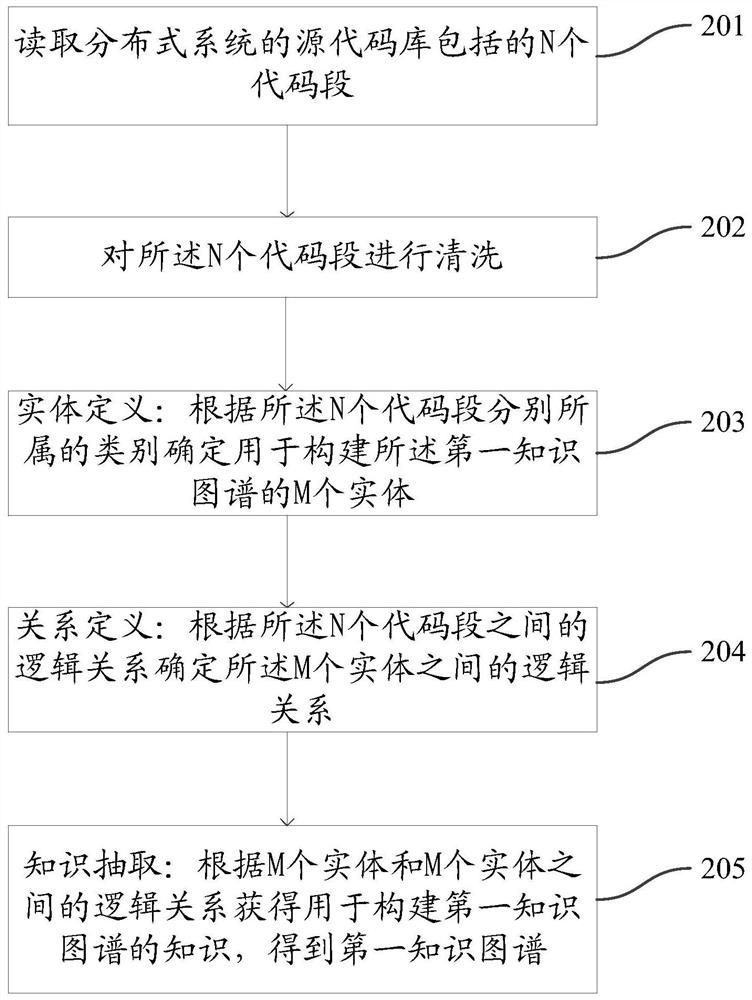
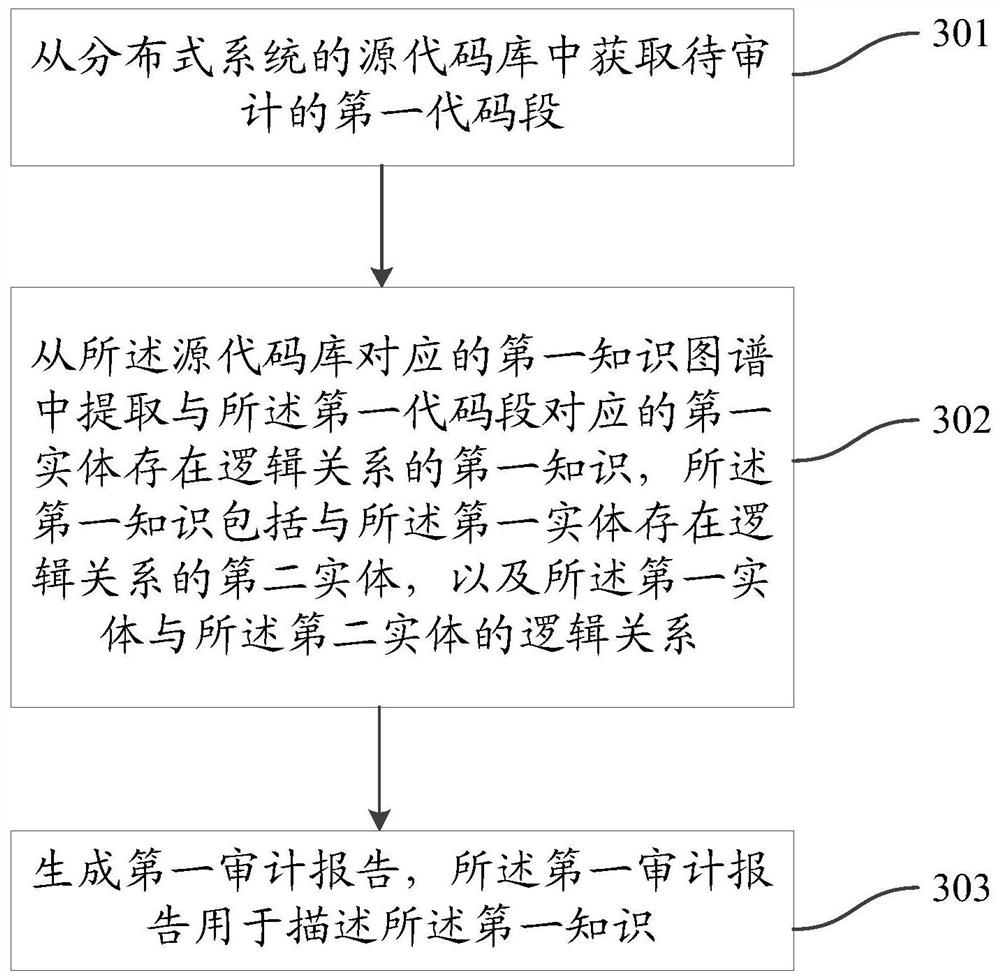
Code auditing method and device based on knowledge graph
ActiveCN112528291AAudit implementationAudit High LevelPlatform integrity maintainanceSpecial data processing applicationsGranularityTheoretical computer science
The invention discloses a code auditing method and device based on a knowledge graph, is used for meeting the code auditing requirement of a distributed system, and is suitable for a multi-level and multi-granularity code auditing scene. The method comprises the steps of obtaining a to-be-audited first code segment from a source code library of a distributed system; extracting first knowledge having a logical relationship with a first entity corresponding to the first code segment from a first knowledge graph corresponding to a source code library, wherein the first knowledge comprises a second entity having a logical relationship with the first entity and a logical relationship between the first entity and the second entity; wherein the first knowledge graph is used for describing a logicrelationship between entities corresponding to different code segments included in a source code library; and generating a first audit report, wherein the first audit report is used for describing the first knowledge.
Owner:QINGDAO HISENSE SMART HOME SYST CO LTD
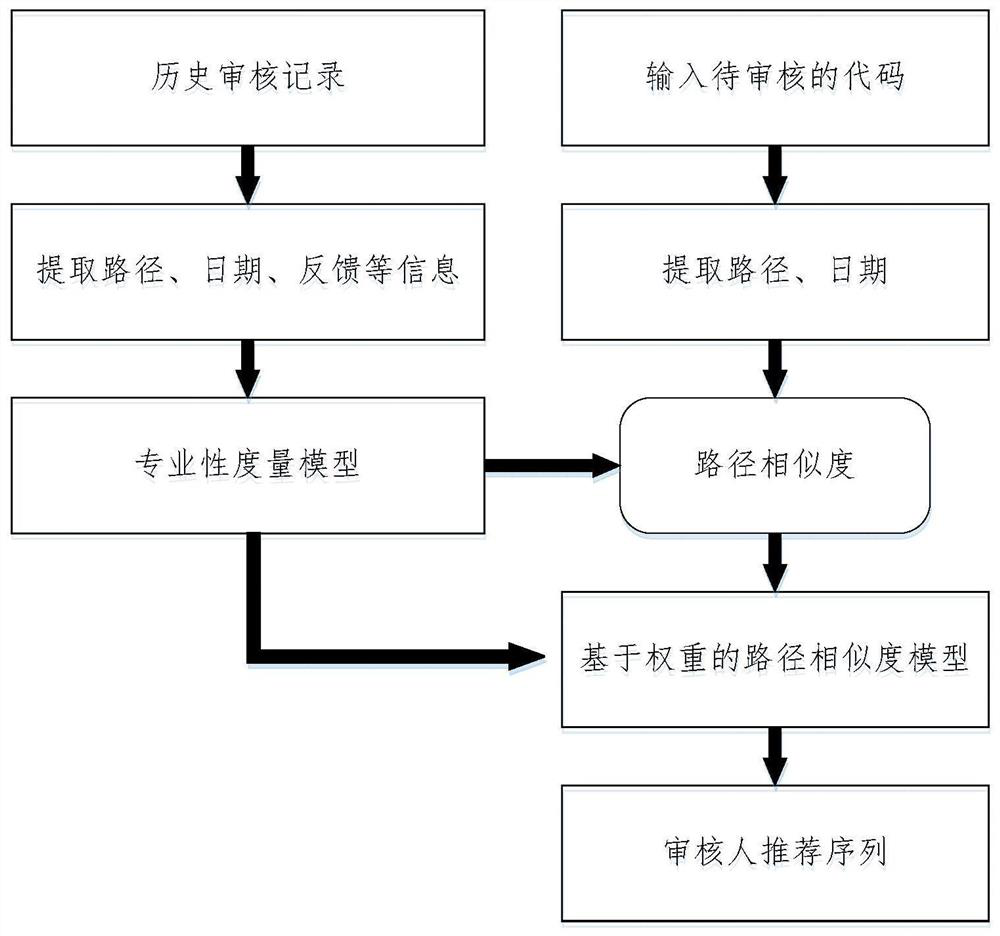
A code reviewer recommendation method based on history
ActiveCN107122391BDigital data information retrievalCharacter and pattern recognitionEngineeringTime factor
The present invention provides a method for recommending code reviewers based on historical records. The method utilizes the feedback information on codes in historical review records and integrates time factors to sequentially determine the professional weights of different reviewers for a piece of code at different times. Path similarity analysis to finally determine the reviewer's recommendation sequence; this method provides a robust and efficient code reviewer recommendation method, it first extracts the feedback from different reviewers in the historical records for a certain piece of code, the number of comprehensive feedback, Date, frequency and other information to determine the professionalism of different reviewers for a piece of code, and then use the string comparison method based on path similarity, combined with time factors, and use the principle of communication to build a path similarity model based on weight, and finally get different The reviewer's priority order for a piece of code.
Owner:SYSU CMU SHUNDE INT JOINT RES INST +1
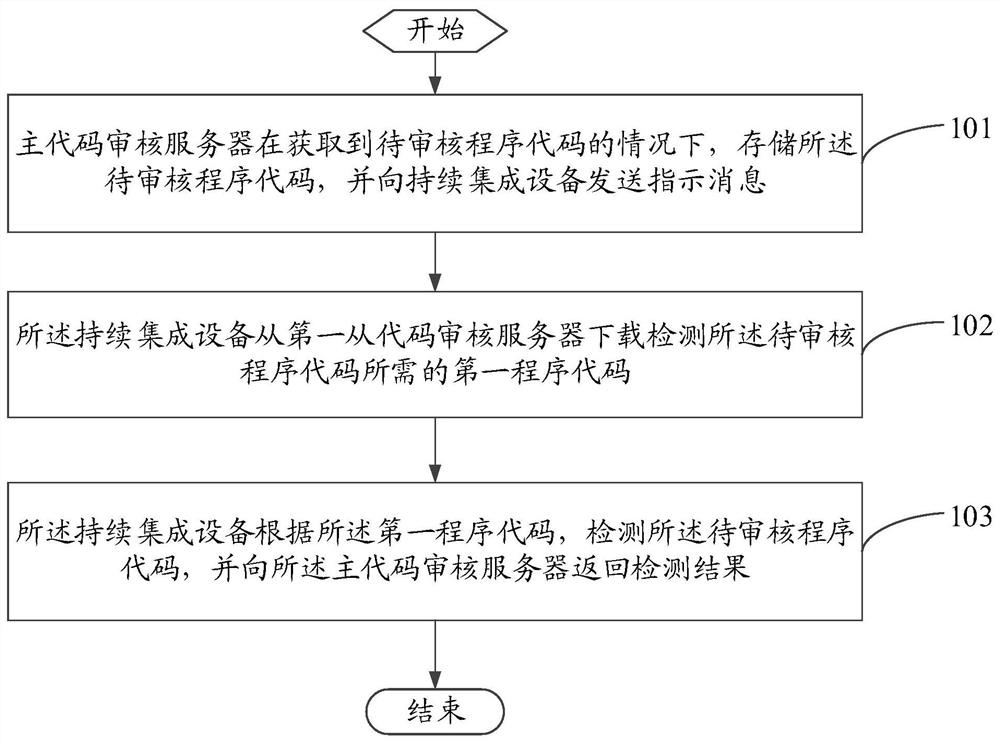
A code management method and code warehouse distributed system
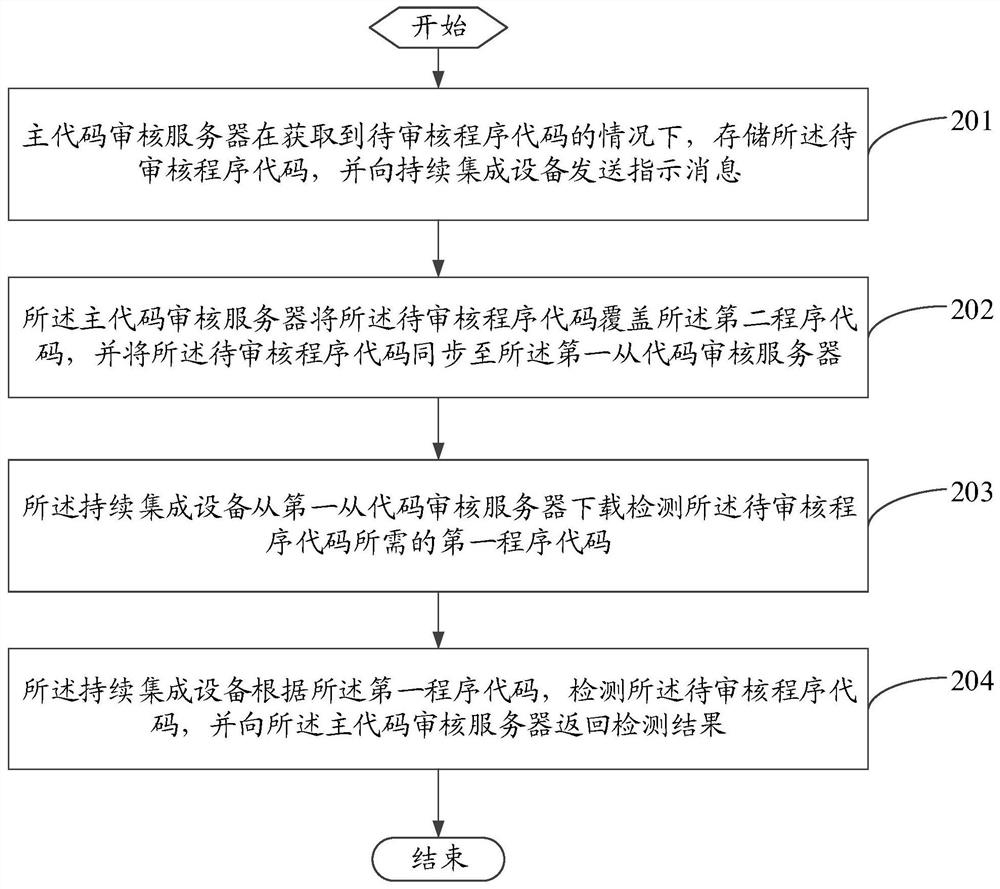
ActiveCN109558318BAvoid getting stainedImprove performanceSoftware testing/debuggingProgramming languageContinuous integration
The invention discloses a code management method and a code warehouse distributed system, wherein the method includes: when the master code audit server obtains the program code to be audited, stores the program code to be audited, and sends the code to the continuous integration device An instruction message, the instruction message includes the program code to be audited; the continuous integration device downloads the first program code required to detect the program code to be audited from the first slave code audit server; the continuous integration device according to the the first program code, detect the program code to be reviewed, and return the detection result to the main code review server. The embodiment of the present invention can improve the performance of the code warehouse.
Owner:BEIJING CHJ AUTOMOTIVE TECH CO LTD
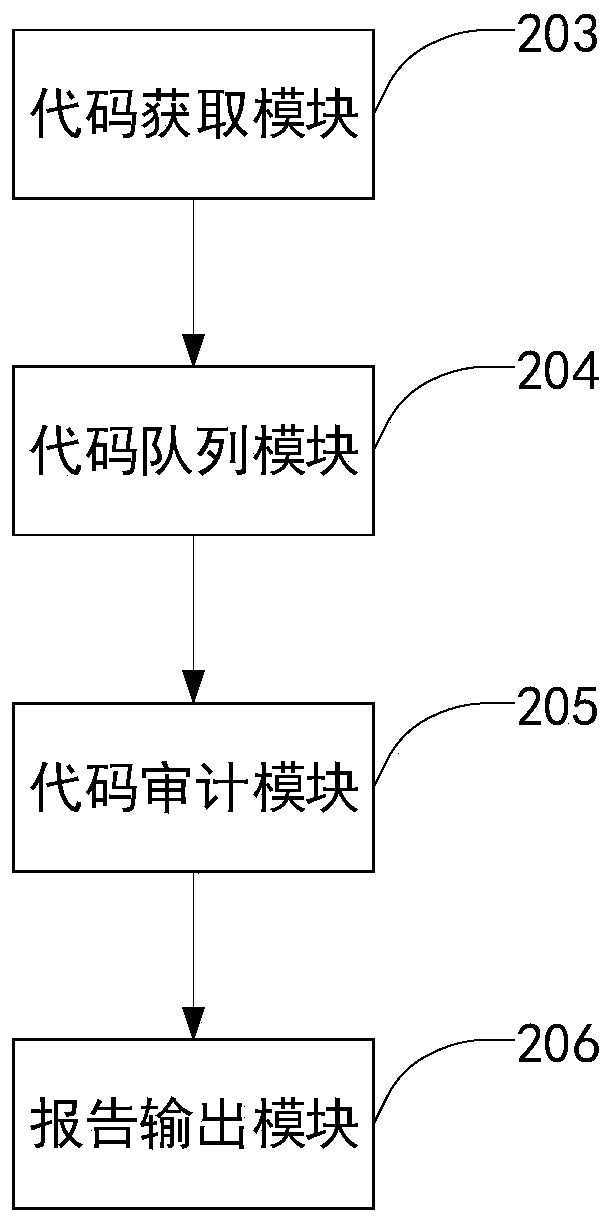
Automatic code auditing method, system and device and storage medium
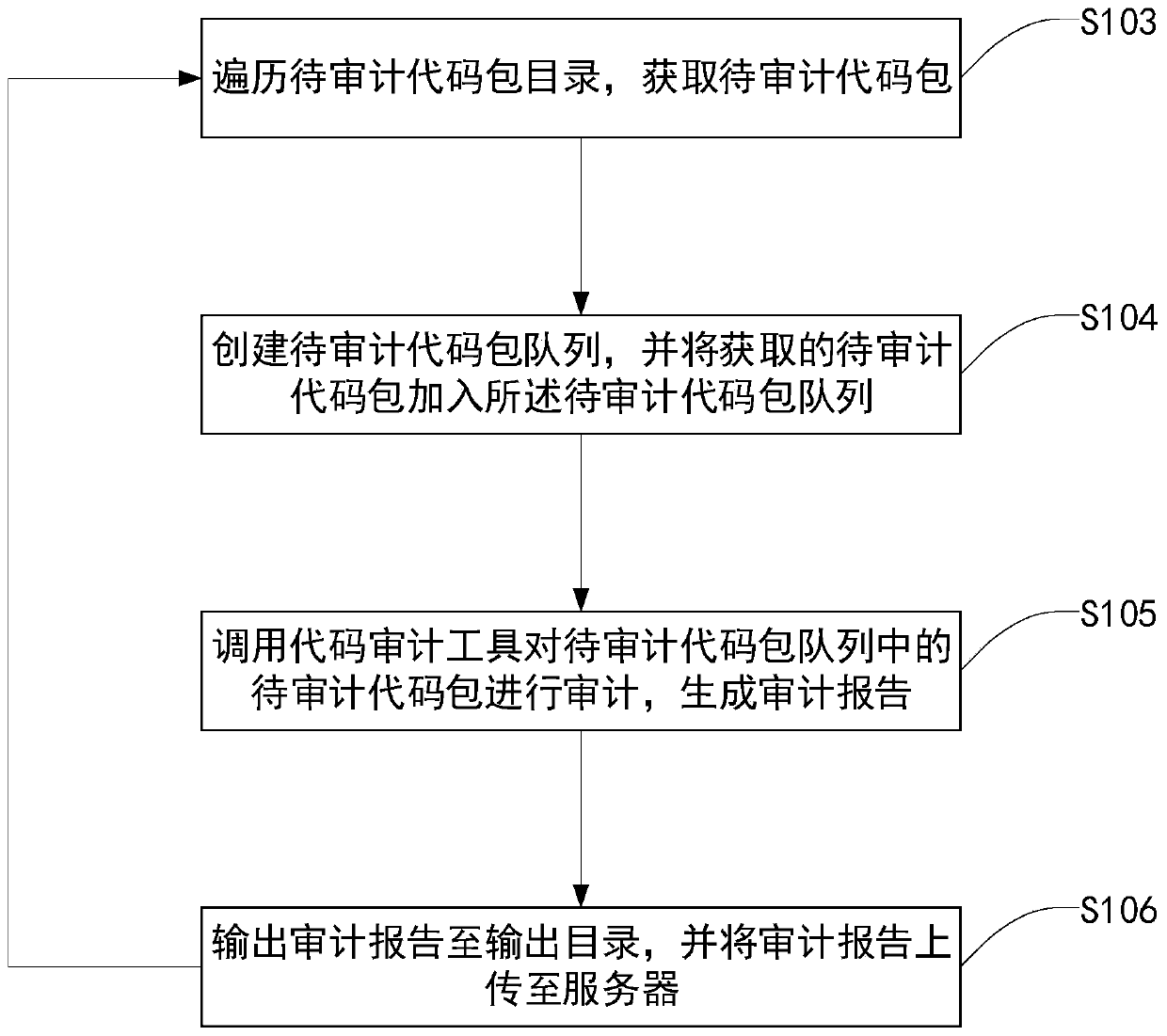
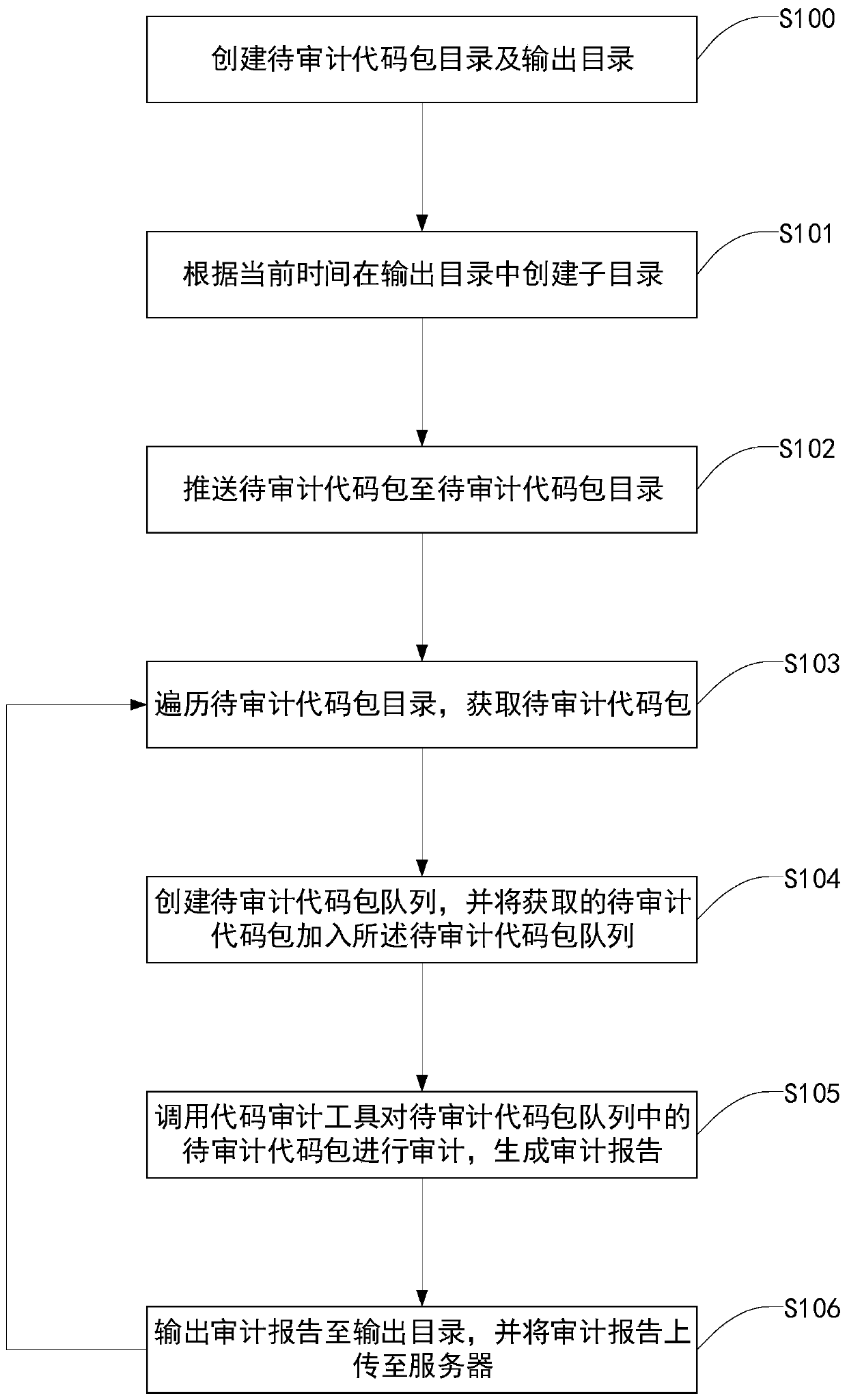
PendingCN111078577AAdapt to the lack of independent research and development capabilitiesAdapt to the situationSoftware testing/debuggingEngineeringInformation security
The invention discloses an automatic code auditing method, system and device and a storage medium, and the method comprises the steps: traversing a to-be-audited code package directory, and obtaininga to-be-audited code package; creating a to-be-audited code packet queue, and adding the obtained to-be-audited code packet into the to-be-audited code packet queue; calling a code auditing tool to audit the to-be-audited code packets in the to-be-audited code packet queue to generate an auditing report; and outputting the auditing report to an output directory, and uploading the auditing report to a server. According to the invention, the to-be-audited code packet is obtained by traversing the to-be-audited code packet directory, and the to-be-audited code packet queue is created, so that mistakes and omissions are avoided; automatic code auditing is achieved by calling a code auditing tool, the achieving method is simple, the cost is low, and the method is suitable for the situations that independent research and development capacity of entrepreneurship companies and small enterprises is insufficient, and budget investment is insufficient. The method can be widely applied to the technical field of information security.
Owner:易票联支付有限公司
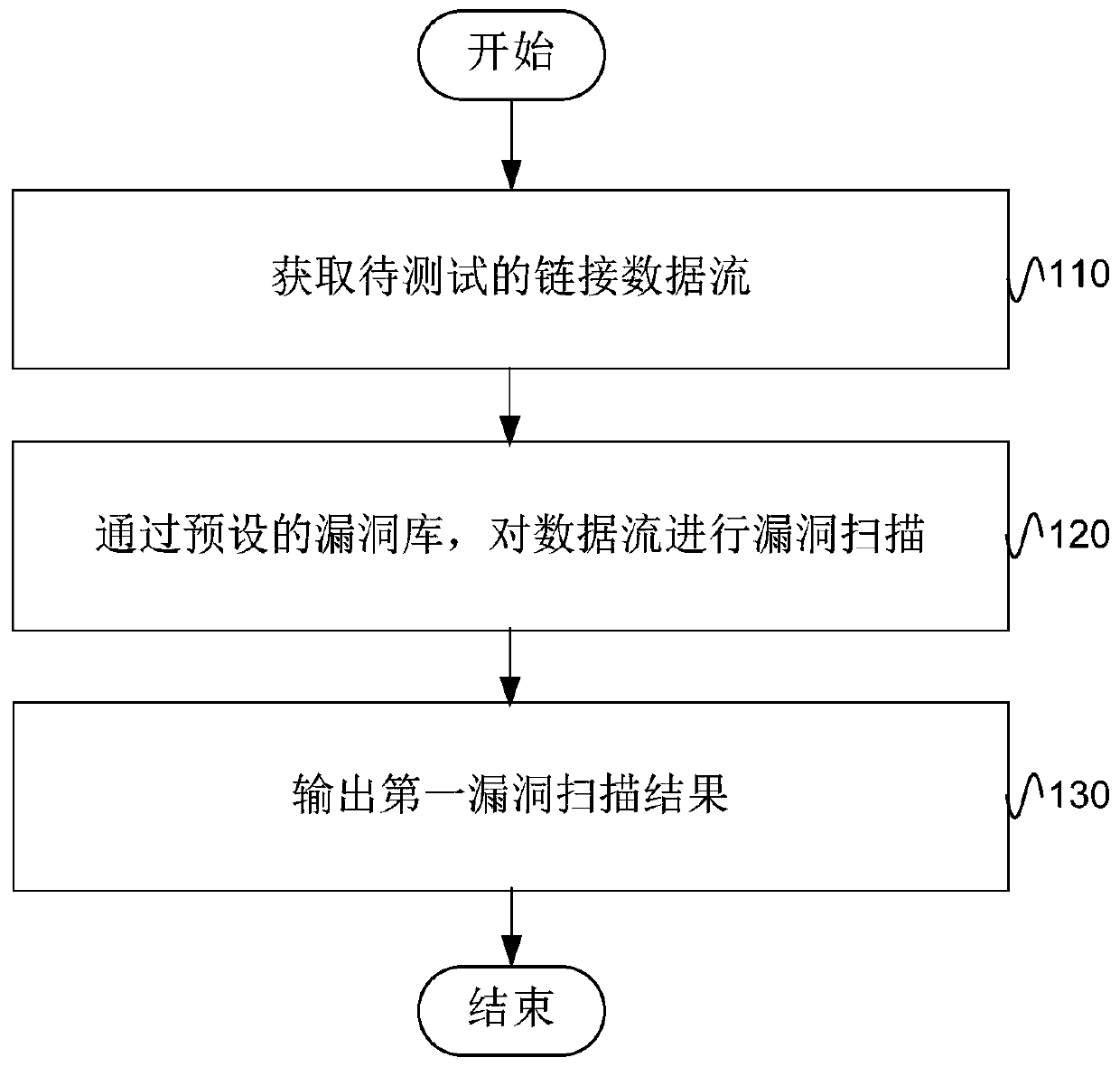
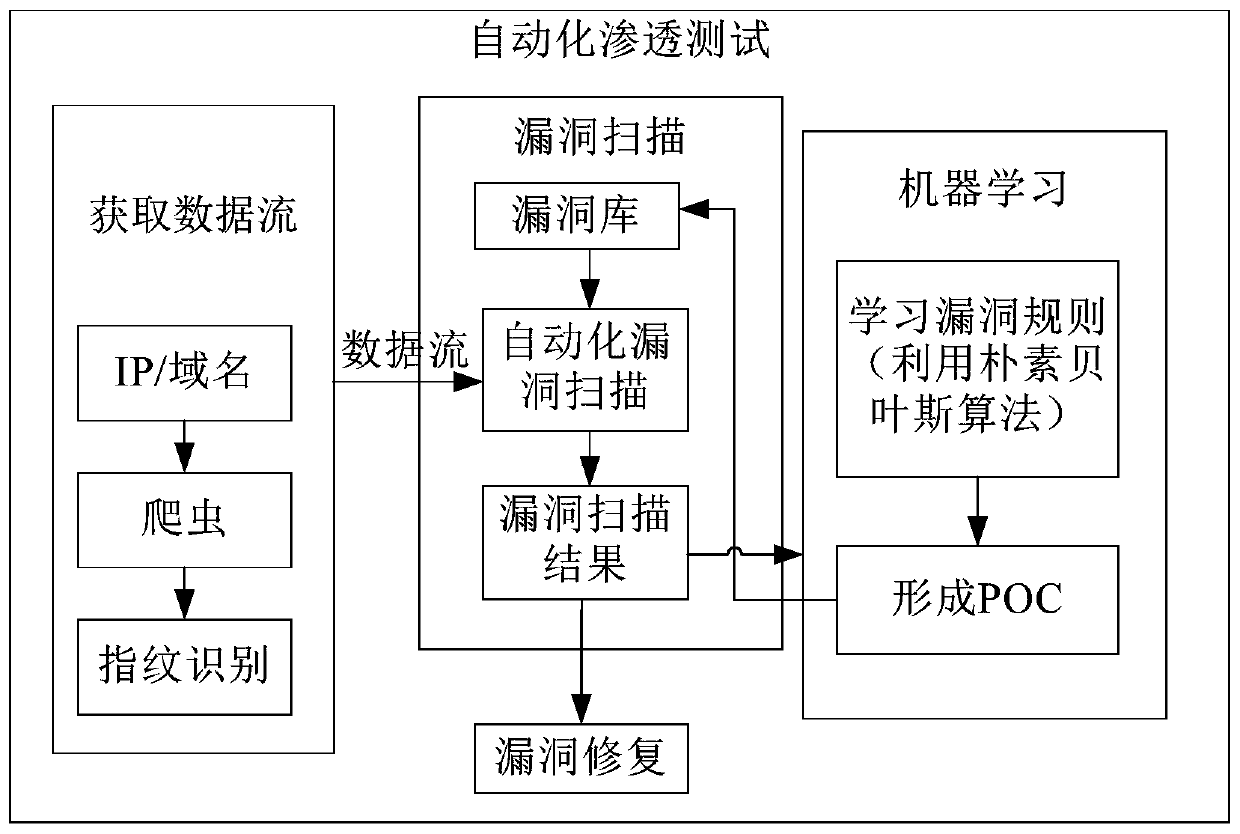
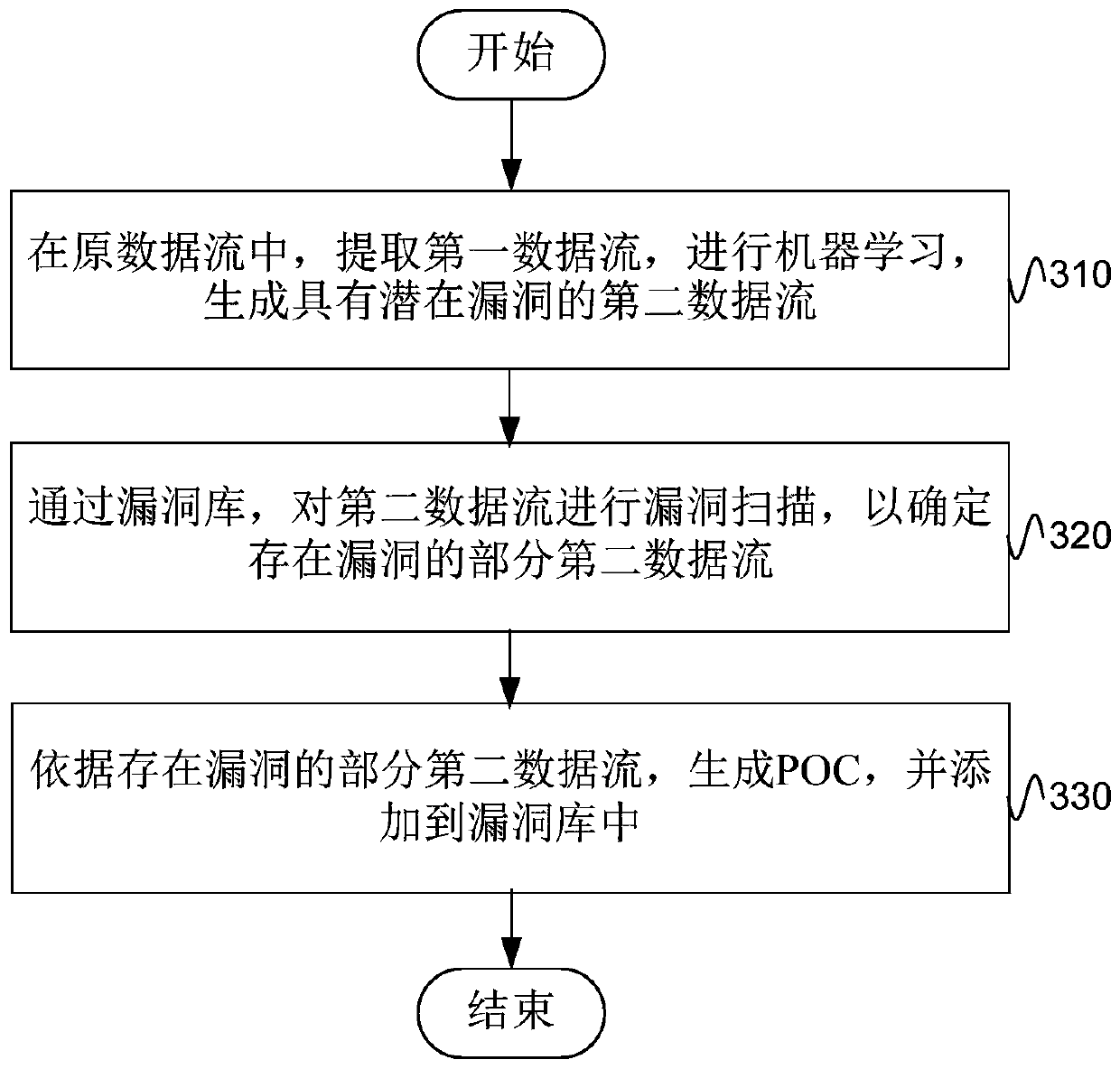
Penetration testing method and device
ActiveCN106874768BFull searchFind complexPlatform integrity maintainanceMachine learningData streamLink data
Owner:BEIJING RZXT TECH DEV CO LTD
Code auditing method and device, equipment and computer readable storage medium
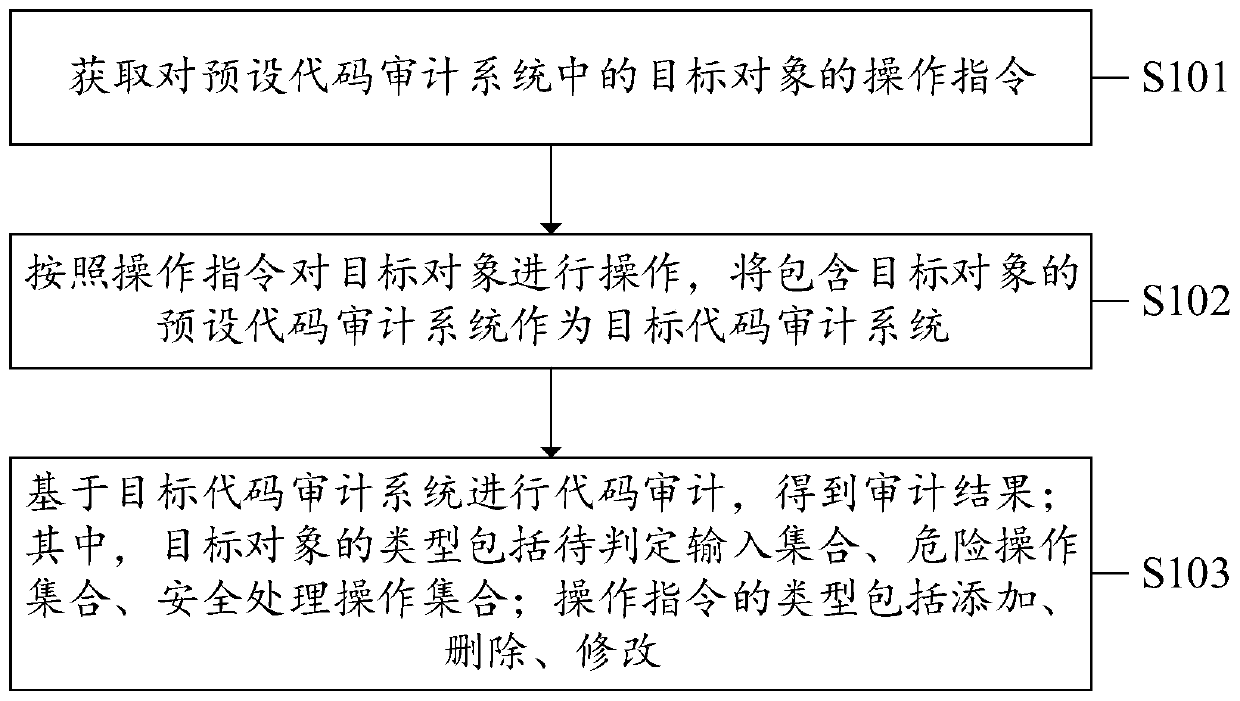
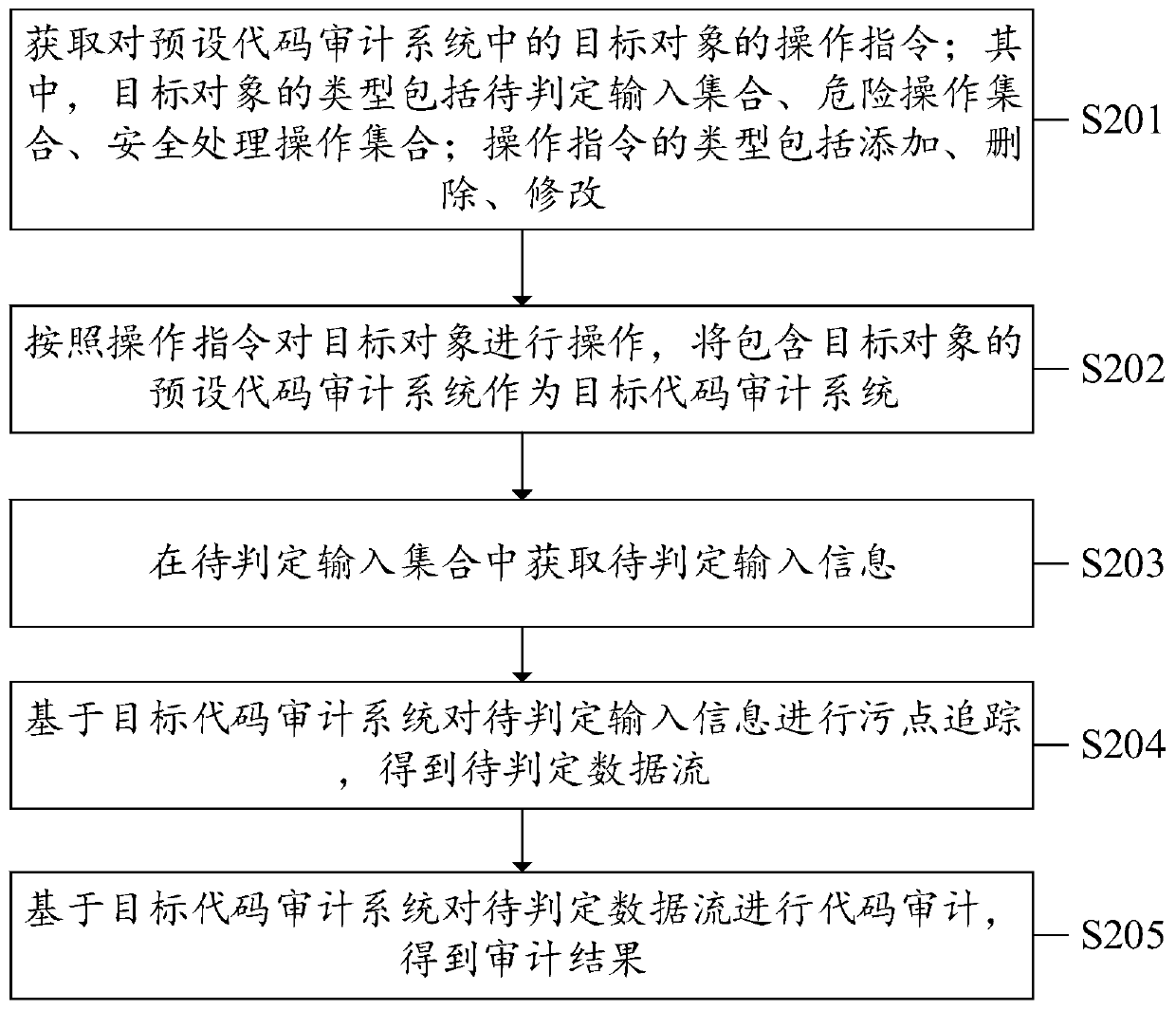
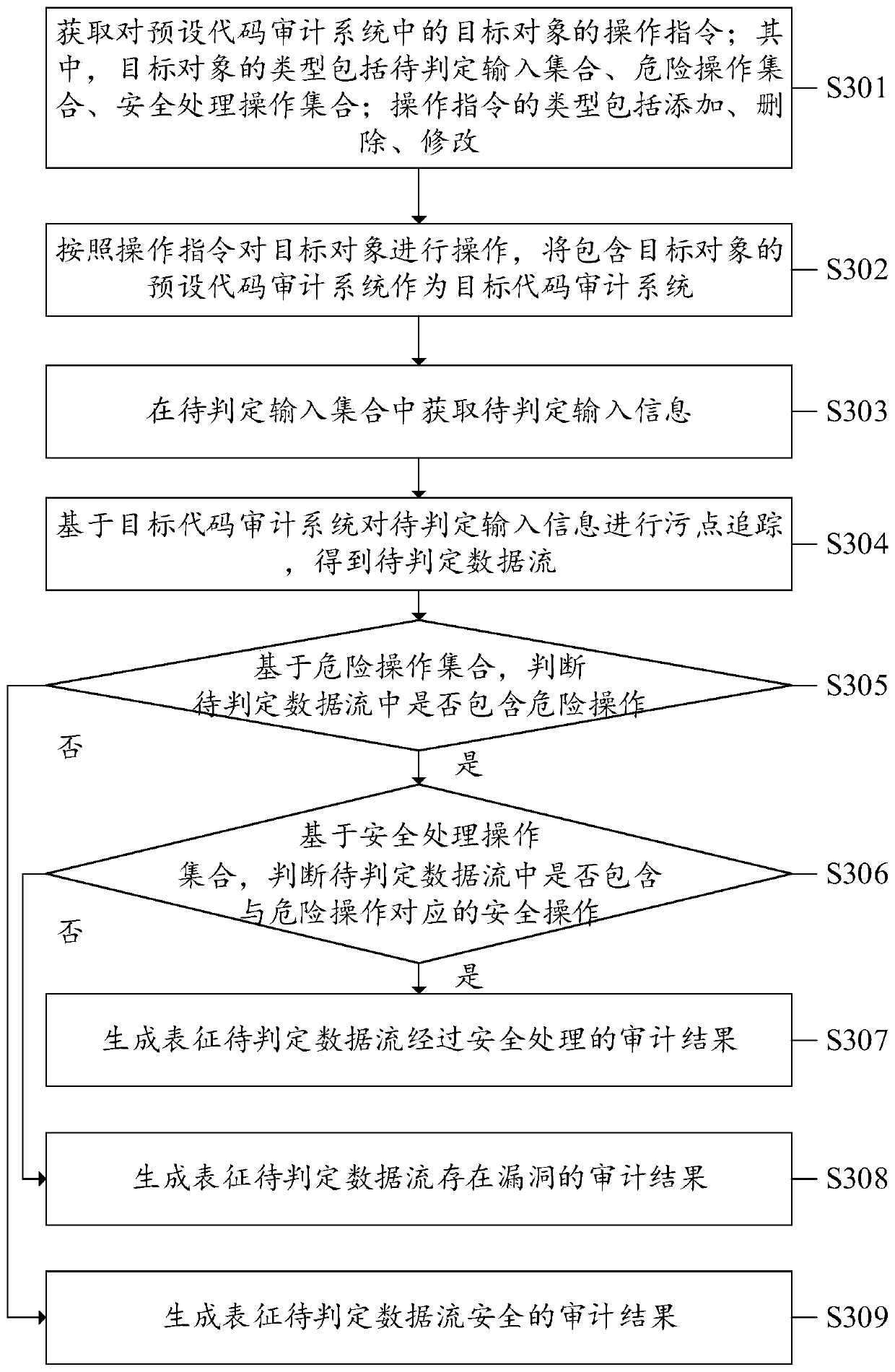
PendingCN111309631AImprove scalabilityFlexible adjustmentSoftware testing/debuggingObject codeSoftware engineering
The invention discloses a code auditing method and device, equipment and a computer readable storage medium. The method comprises the steps of obtaining an operation instruction for a target object ina preset code auditing system; operating the target object according to the operation instruction, and taking a preset code auditing system containing the operated target object as a target code auditing system; performing code auditing based on the target code auditing system to obtain an auditing result; wherein the type of the target object comprises a to-be-judged input set, a dangerous operation set and a safe processing operation set; wherein the types of the operation instructions comprise addition, deletion and modification. In the present application, a target object in a preset codeauditing system can be operated by means of an operation instruction; and the preset code auditing system containing the operated target object is used as the target code auditing system, so that a user can flexibly adjust the preset code auditing system according to needs, the adaptability of the code auditing system is enhanced, and the expandability of code auditing is improved.
Owner:SANGFOR TECH INC
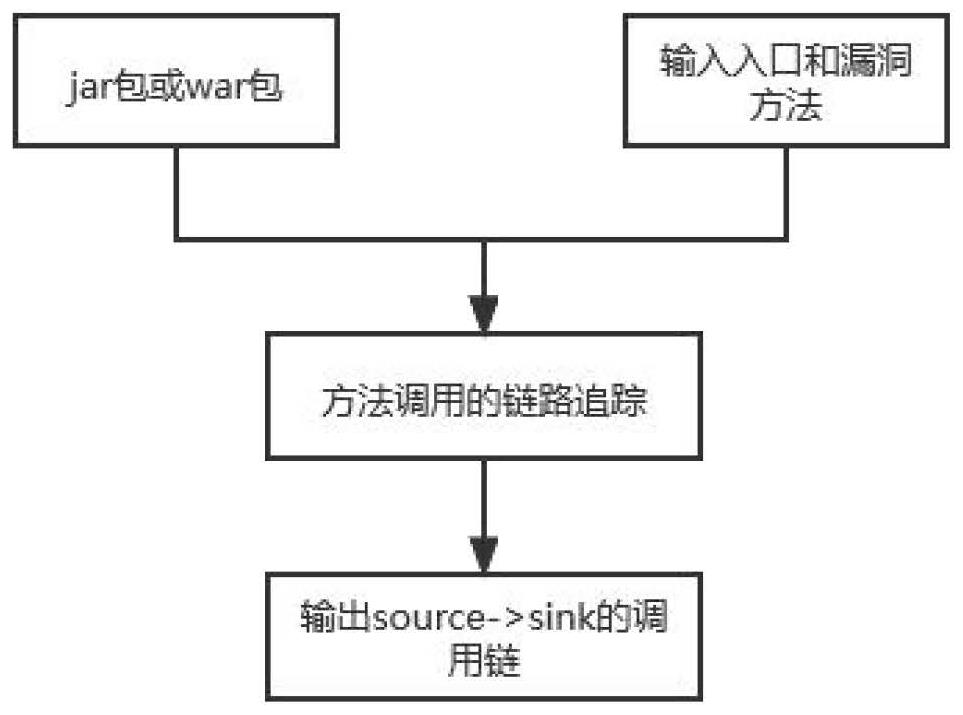
Code auditing scheme based on Java bytecode technology
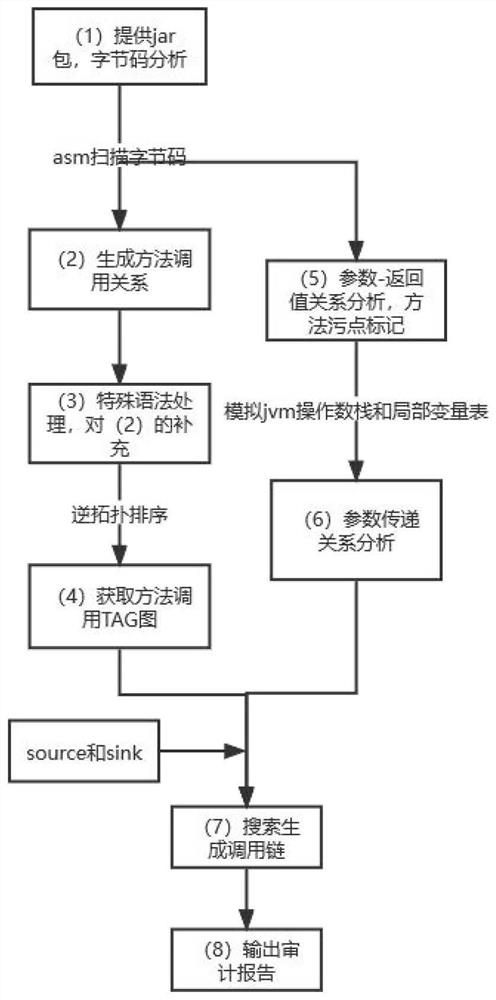
The invention discloses a code auditing scheme based on a Java bytecode technology, which is simple as follows: scanning bytecodes in a Jar packet or a War packet through ASM to obtain a method calling relationship in the packet, and calling a child method by a parent method; performing inverse topological sorting on the method calling relationship to generate a directed acyclic graph (TAG) of the method relationship; analyzing the relationship between the return value of each method and the parameters, and performing stain marking on the parameters; analyzing whether the parameters of the child method are influenced by the parameters of the parent method or not, and obtaining a taint transmission relation; and finally, searching the whole method calling relation graph according to an input entry and a vulnerability method provided by a user, and finding out a method calling chain from the input entry to the vulnerability method.
Owner:TIANYI ELECTRONICS COMMERCE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com