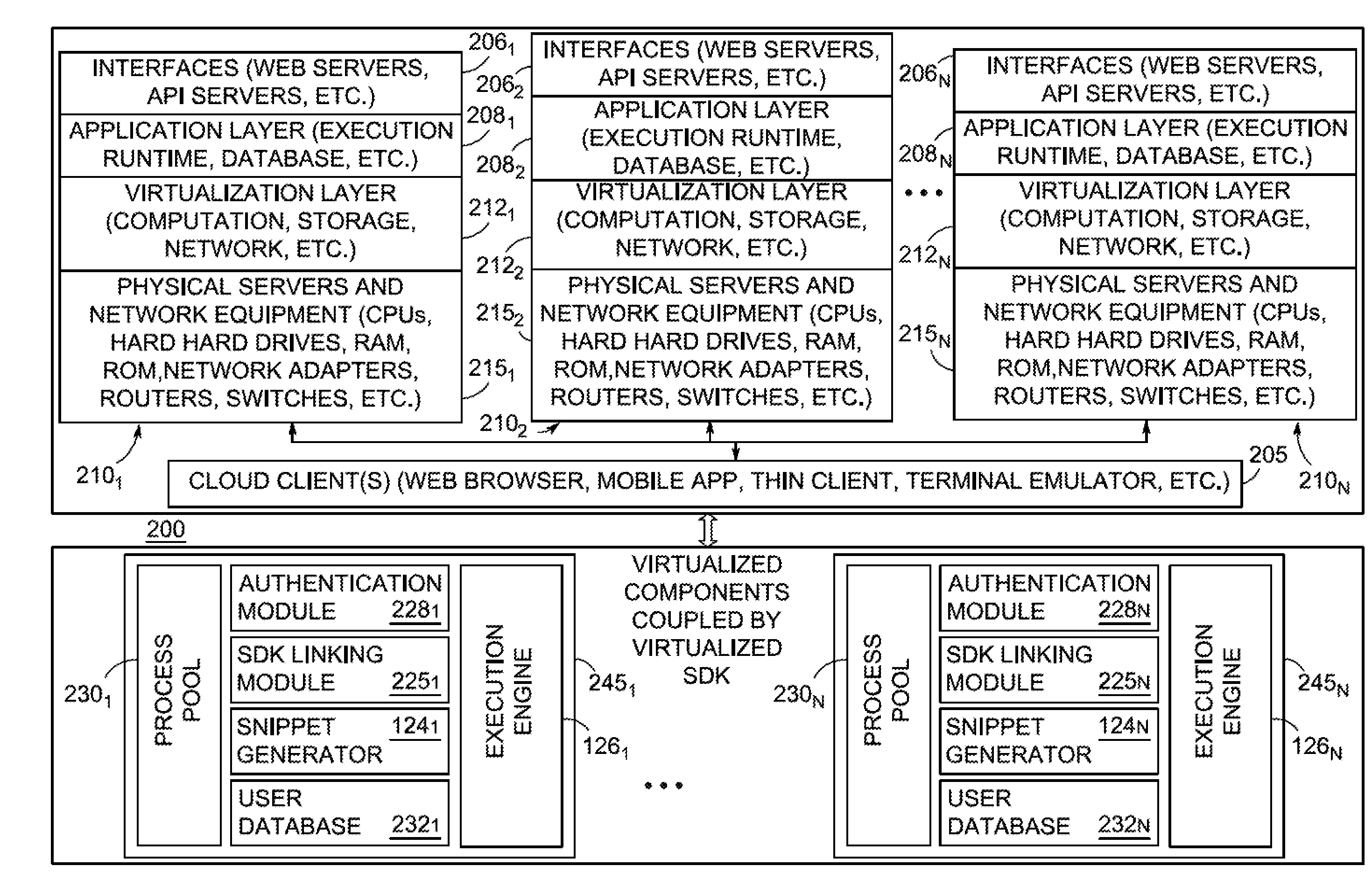
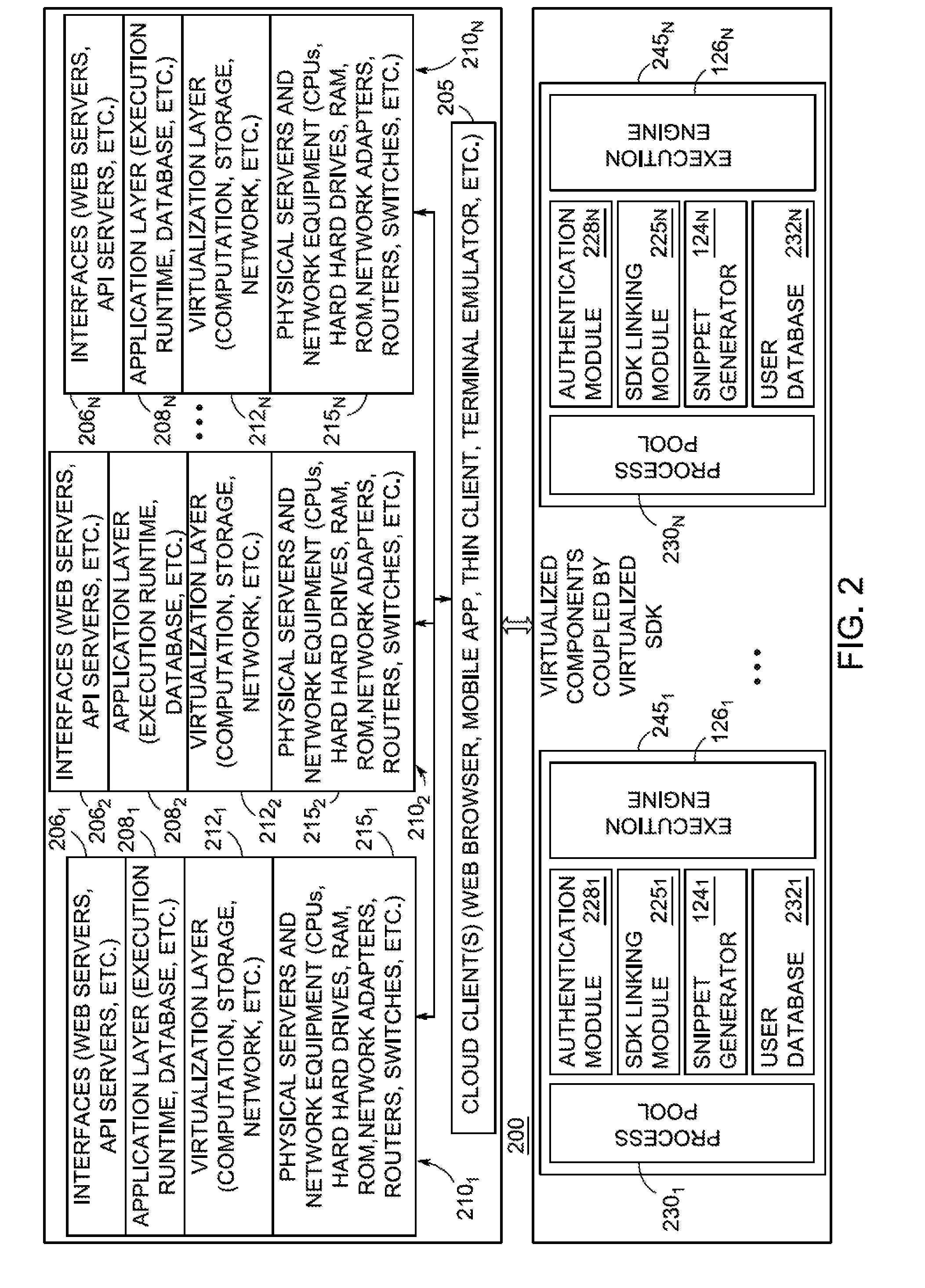
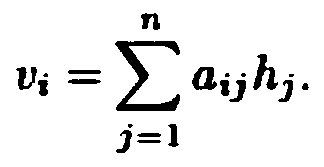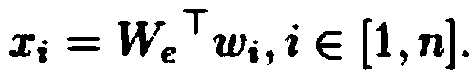Patents
Literature
278 results about "Code snippet" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
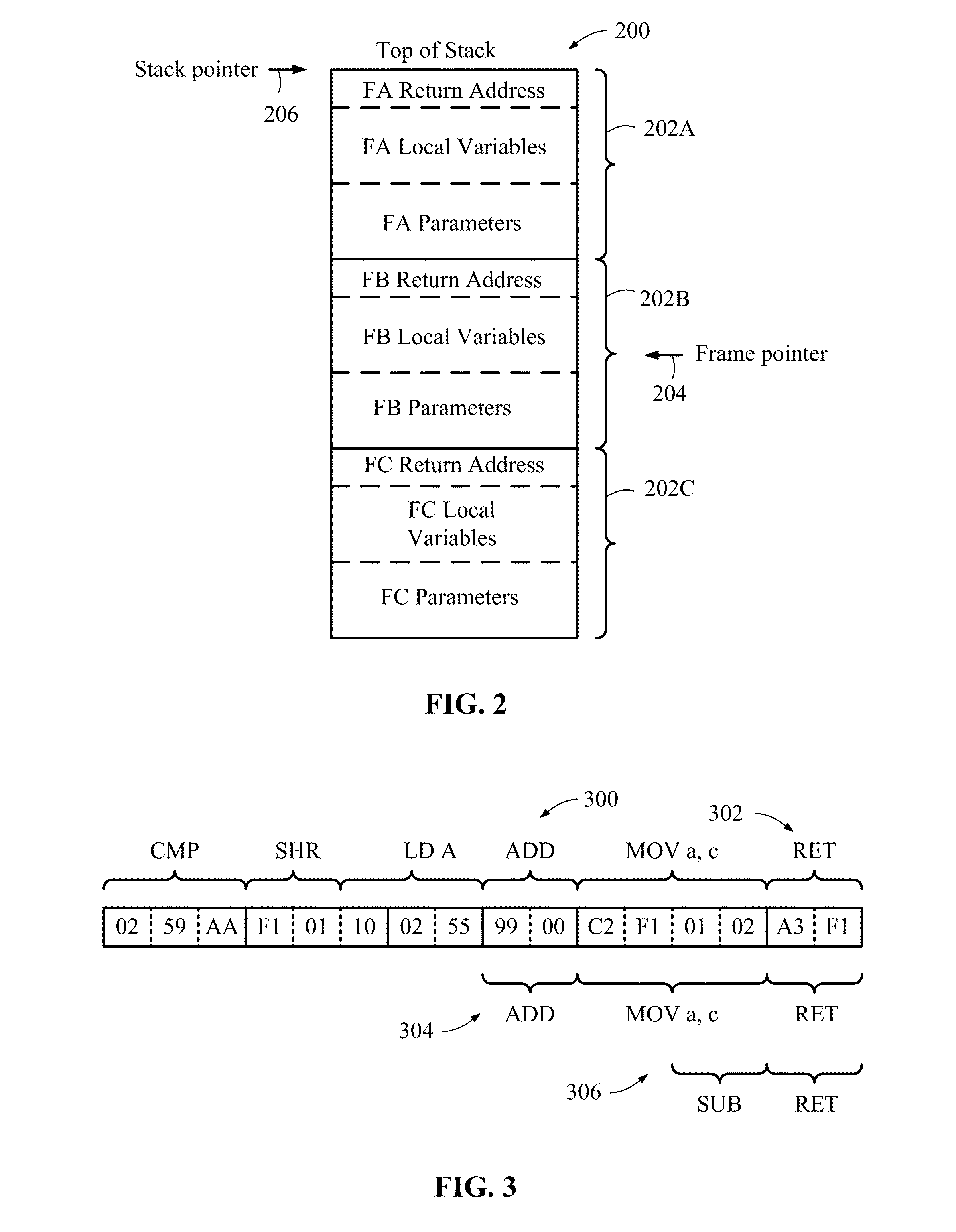
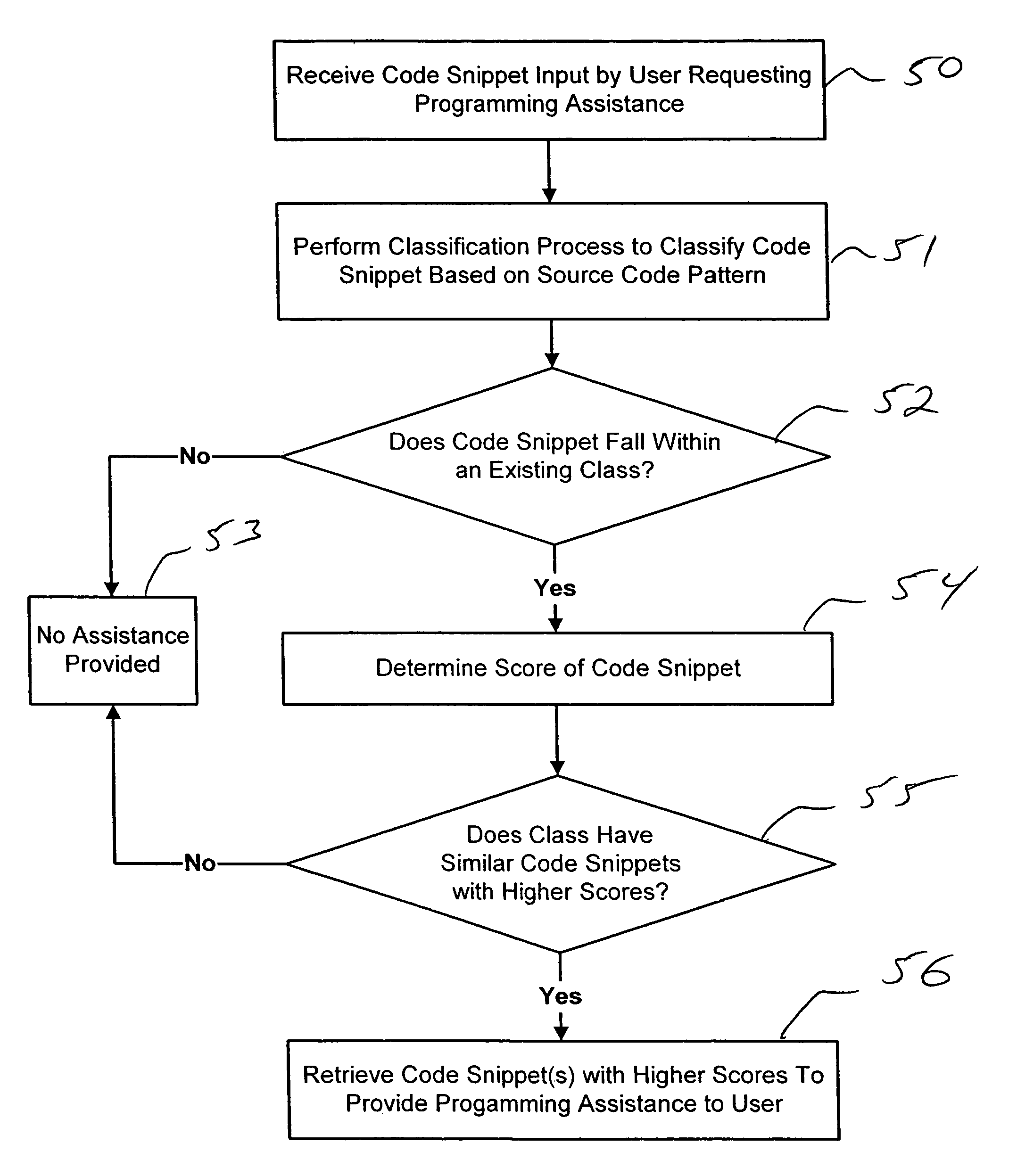
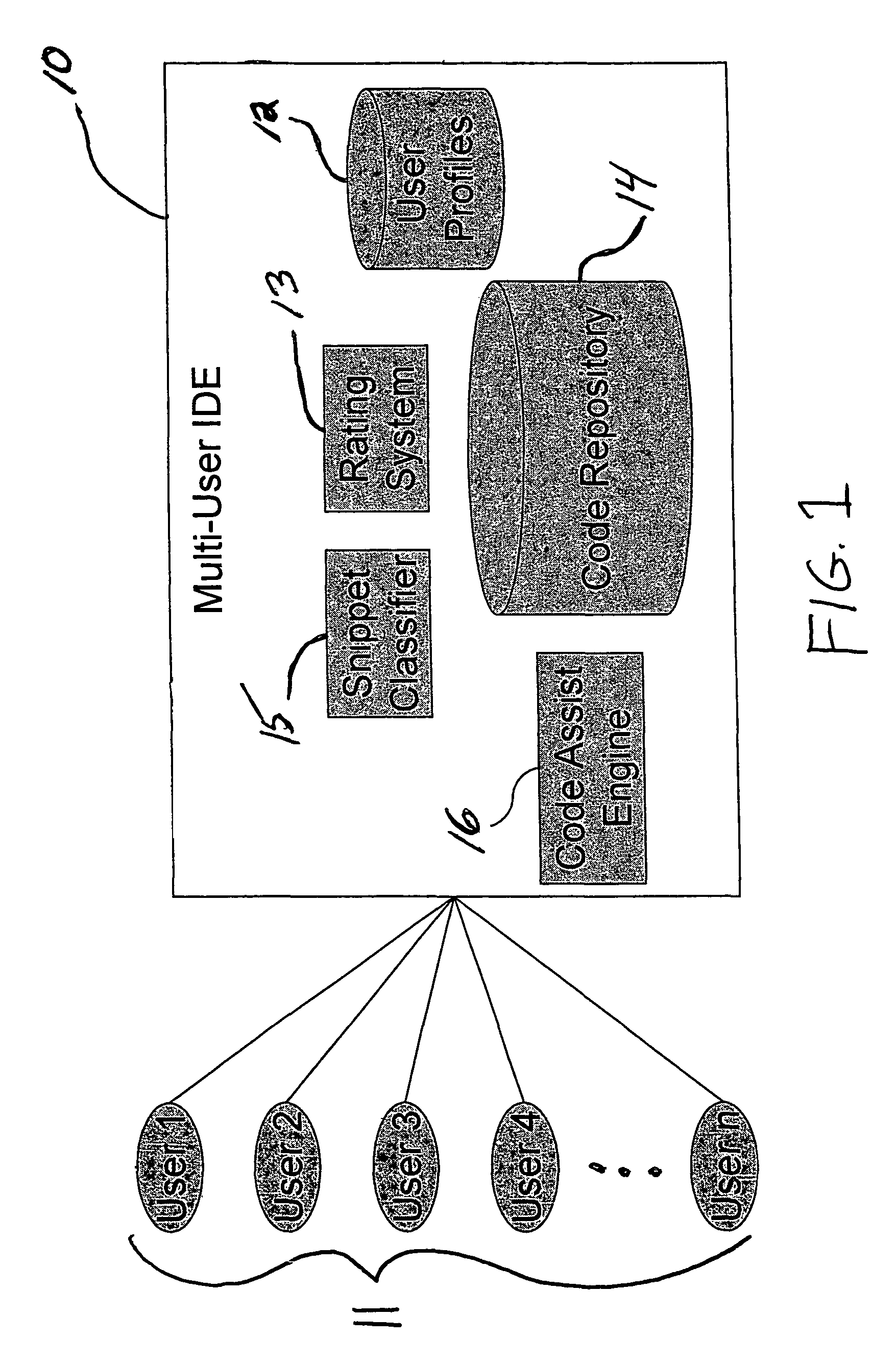
Collaborative software development systems and methods providing automated programming assistance
ActiveUS20070168946A1Increased and decreasedVersion controlSoftware reuseCode snippetSoftware engineering
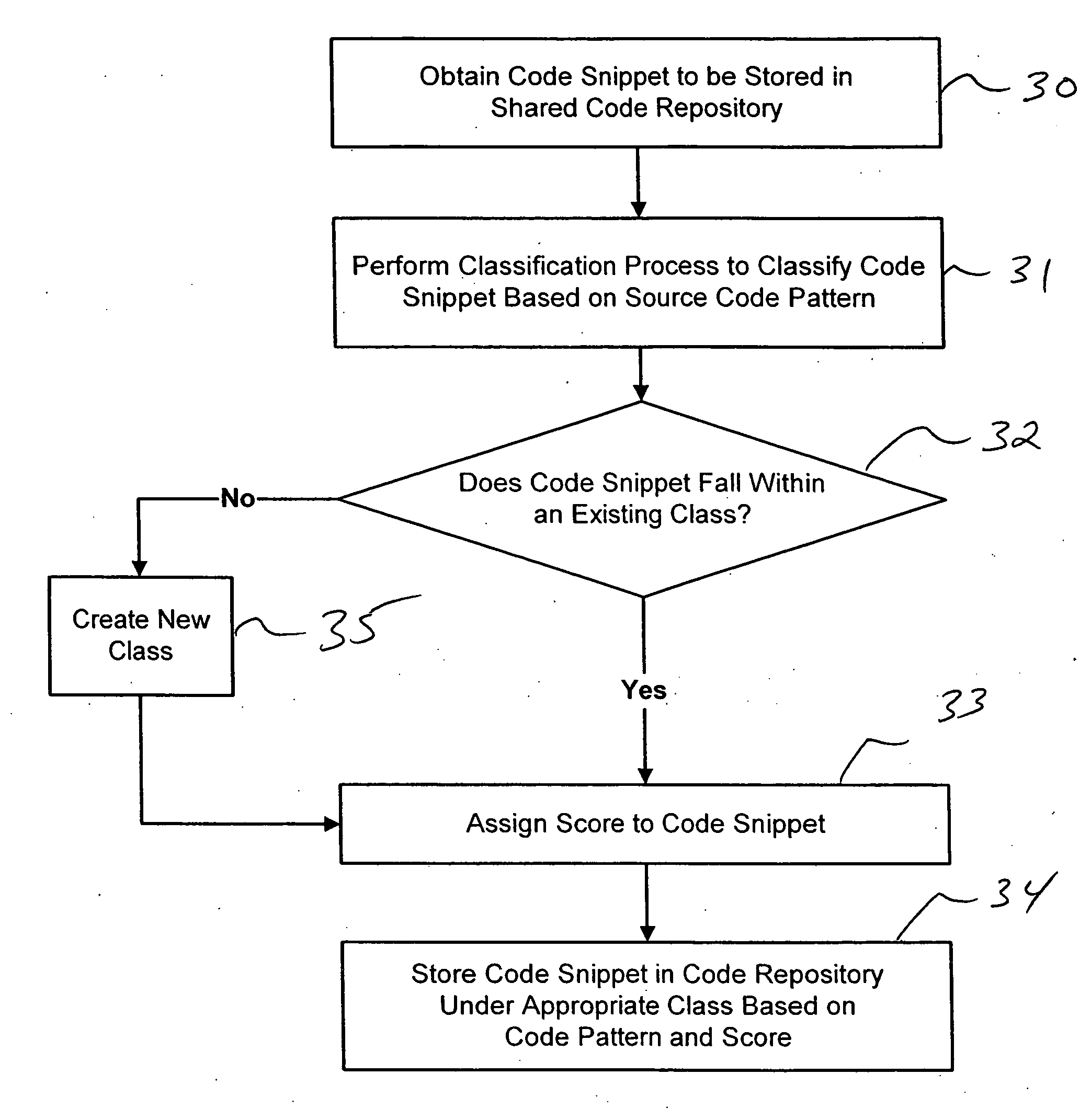
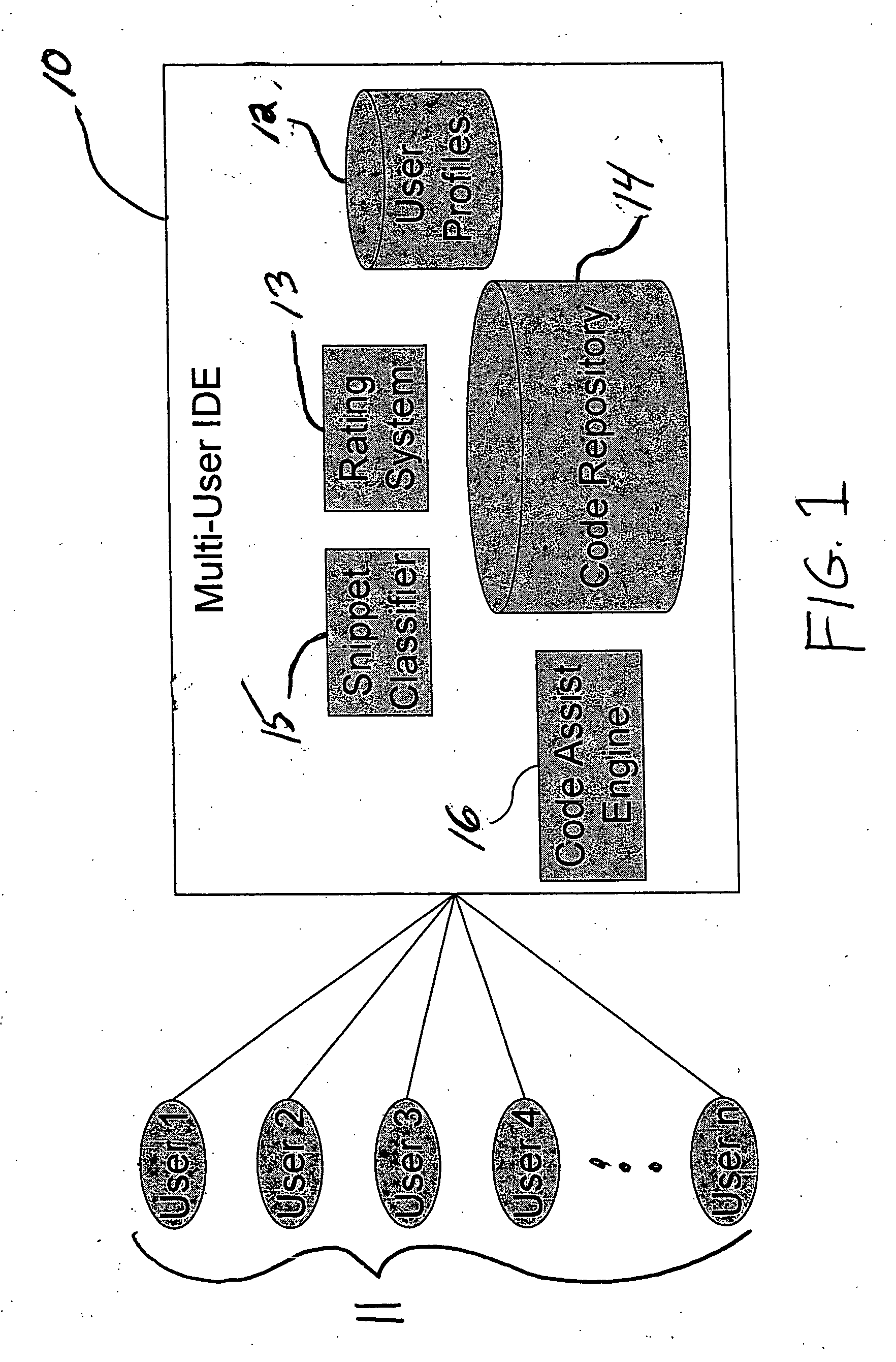
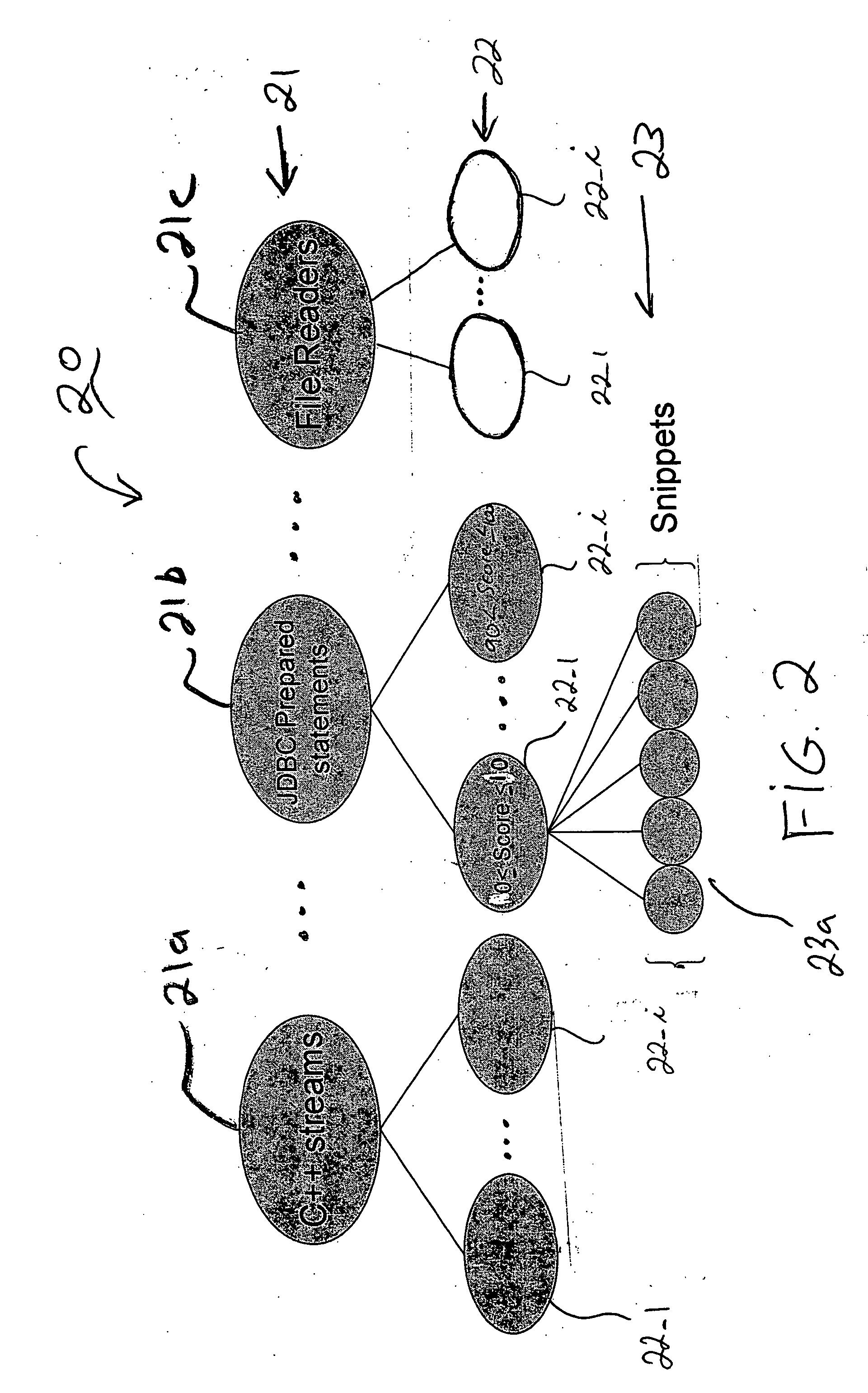
Collaborative program development systems are provided which implement methods for providing automated programming assistance to code developers in a collaborative program development environment. In particular, systems and methods for automated programming assistance are supported by leveraging a database or library of shared code snippets that are classified according to code patterns and rating scores that are derived from feedback and input from various code developers within a collaborative program development environment.
Owner:IBM CORP
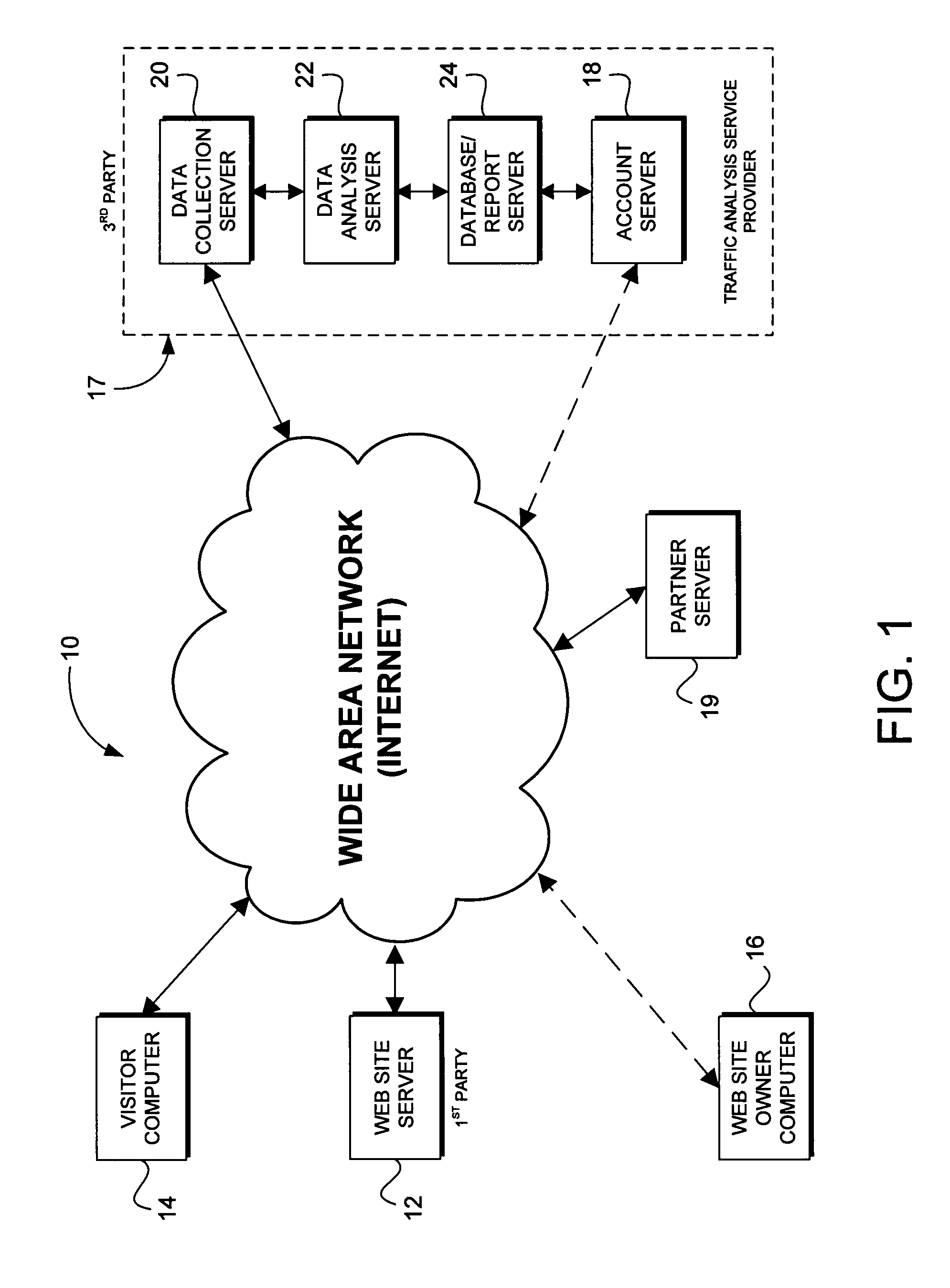
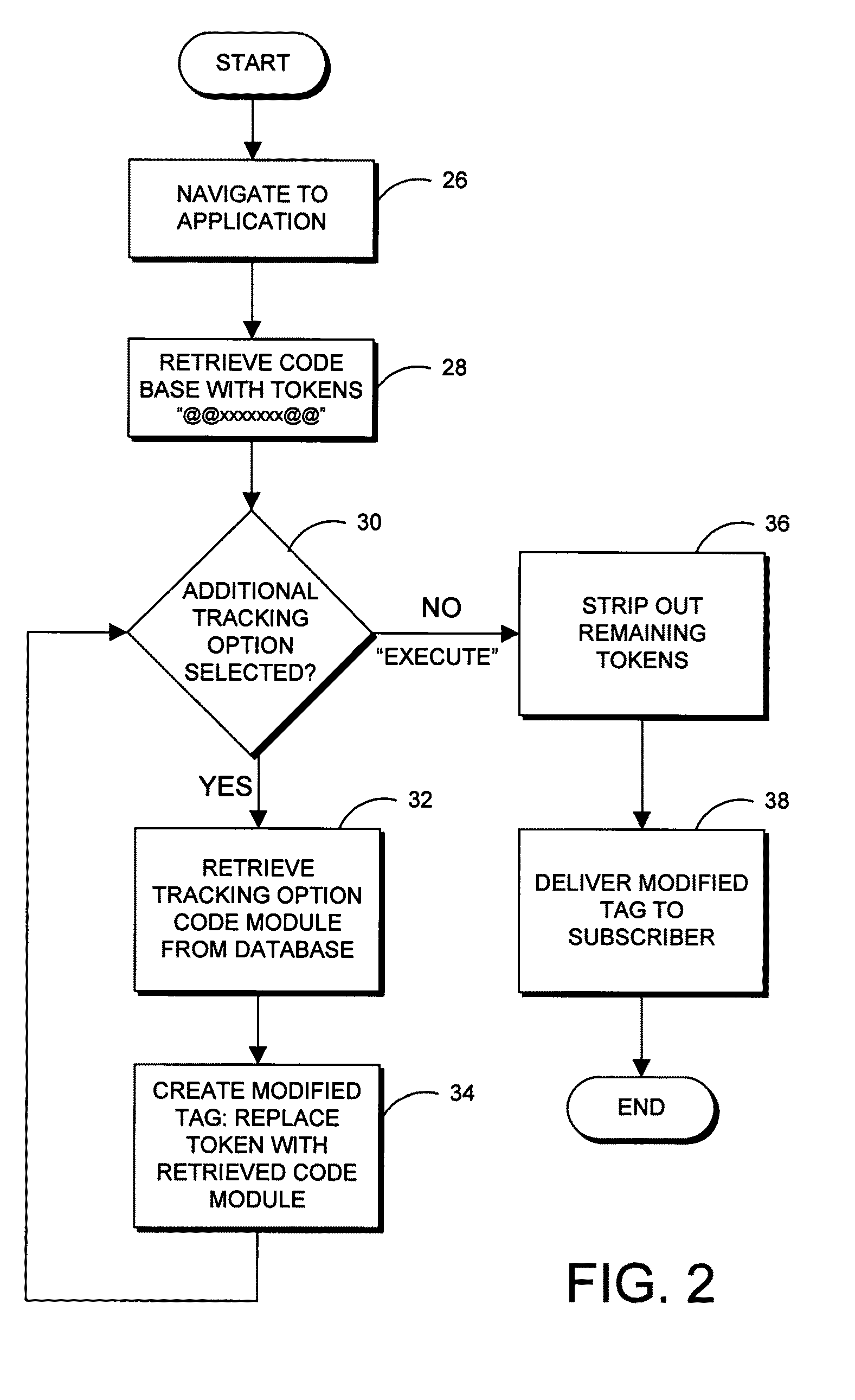
Method and system for constructing a customized web analytics application
ActiveUS20100318976A1Readily apparentWebsite content managementProgram controlCode snippetWeb analytics
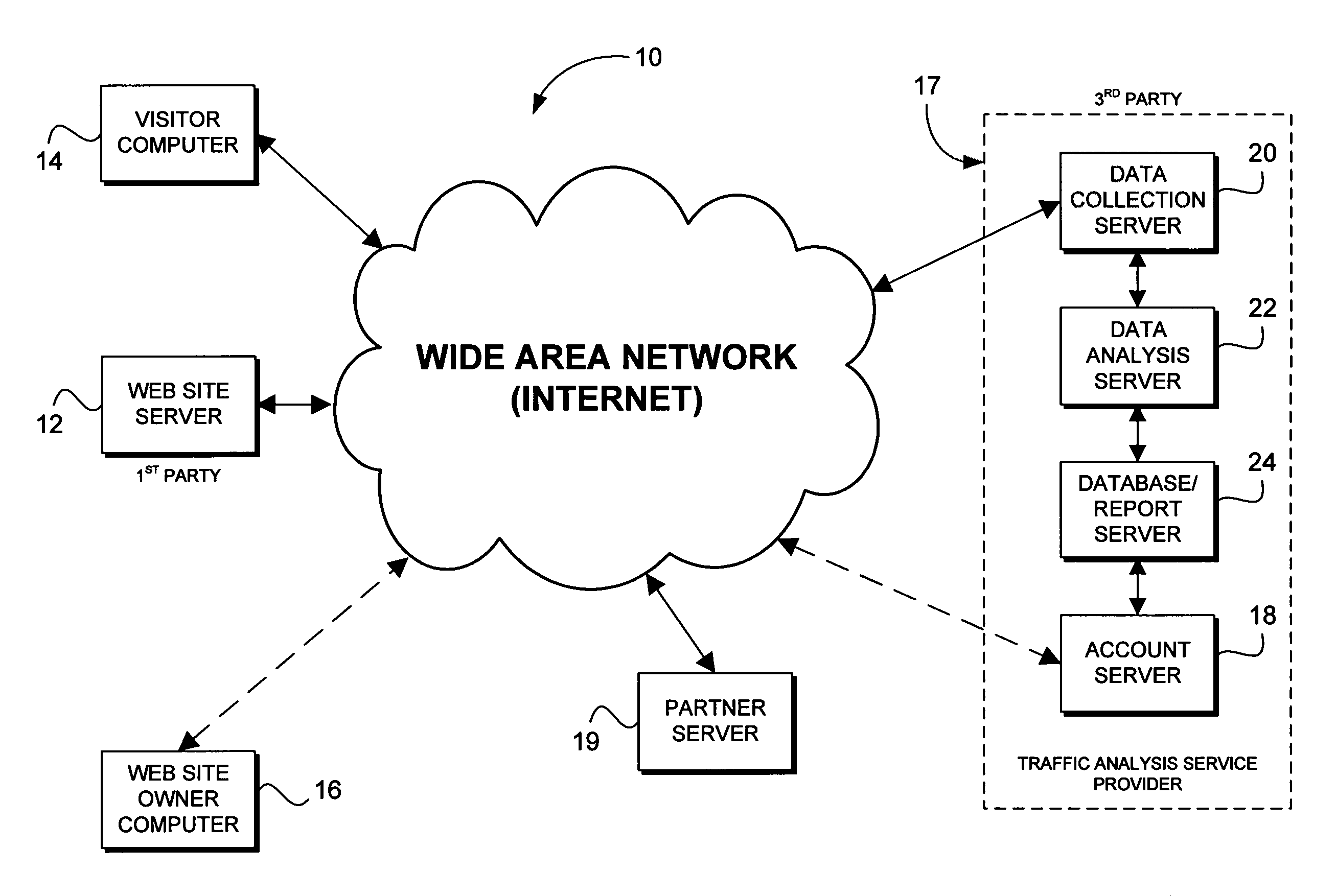
A method for constructing a customized web analytics application comprises providing a base analytics code, including a base data mining code and a plurality of tokens corresponding to unincorporated code snippets, and incorporating code snippets as selected to create the application where each code snippet is configured to track a different custom web analytic. The system displays a selection of at least one web analytic to track and receives user selection of at least one displayed web analytic to track over a wide area network. Once selected, an unincorporated code snippet corresponding to each selected displayed web analytic is retrieved from a library of such code snippets. The code snippet is then substituted in place of its corresponding token within the base analytics code to create a customized analytics code. The customized code is finalized by removing the remaining tokens and the finalized code transmitted to the user for incorporation into their web pages.
Owner:ORACLE INT CORP
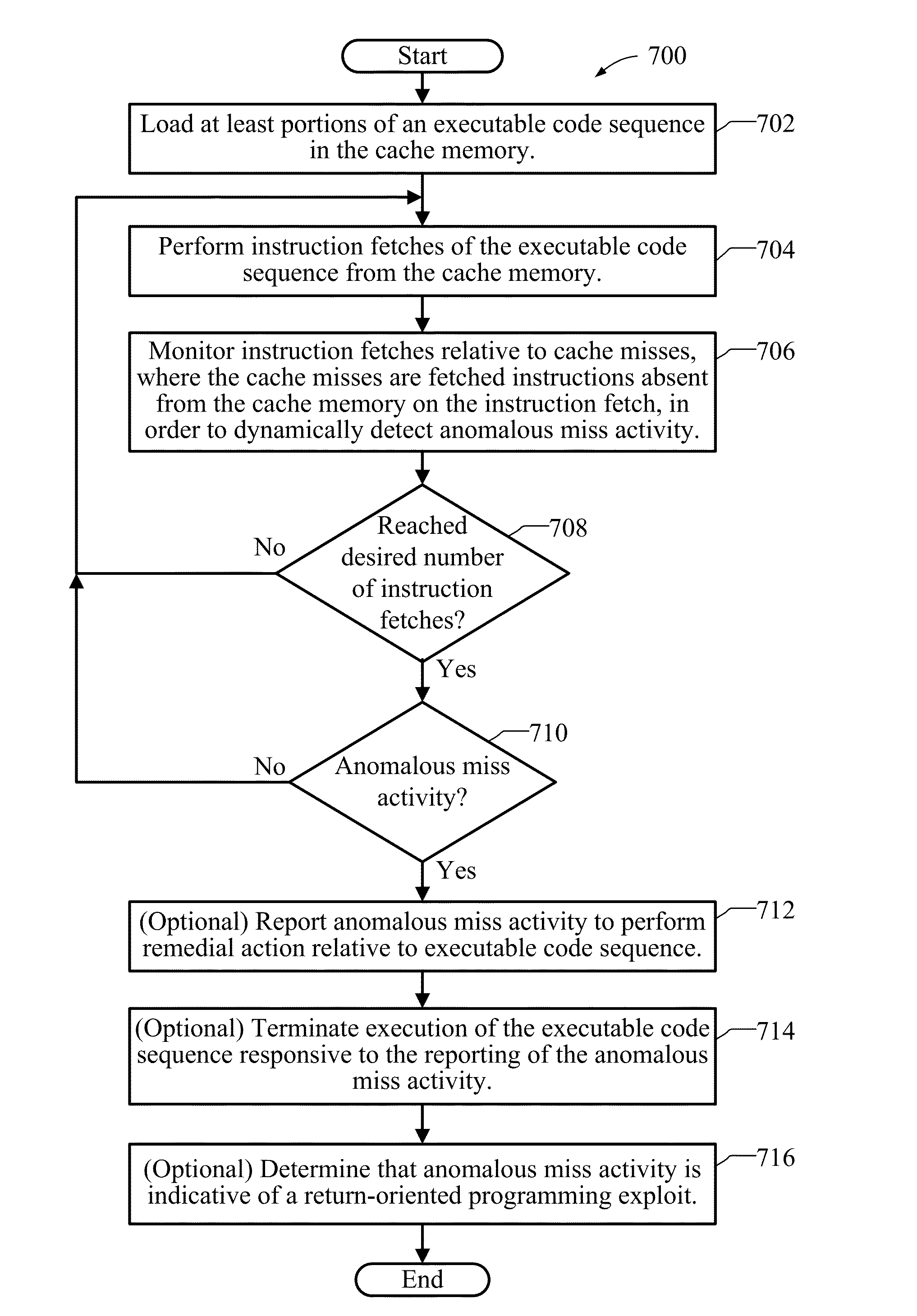
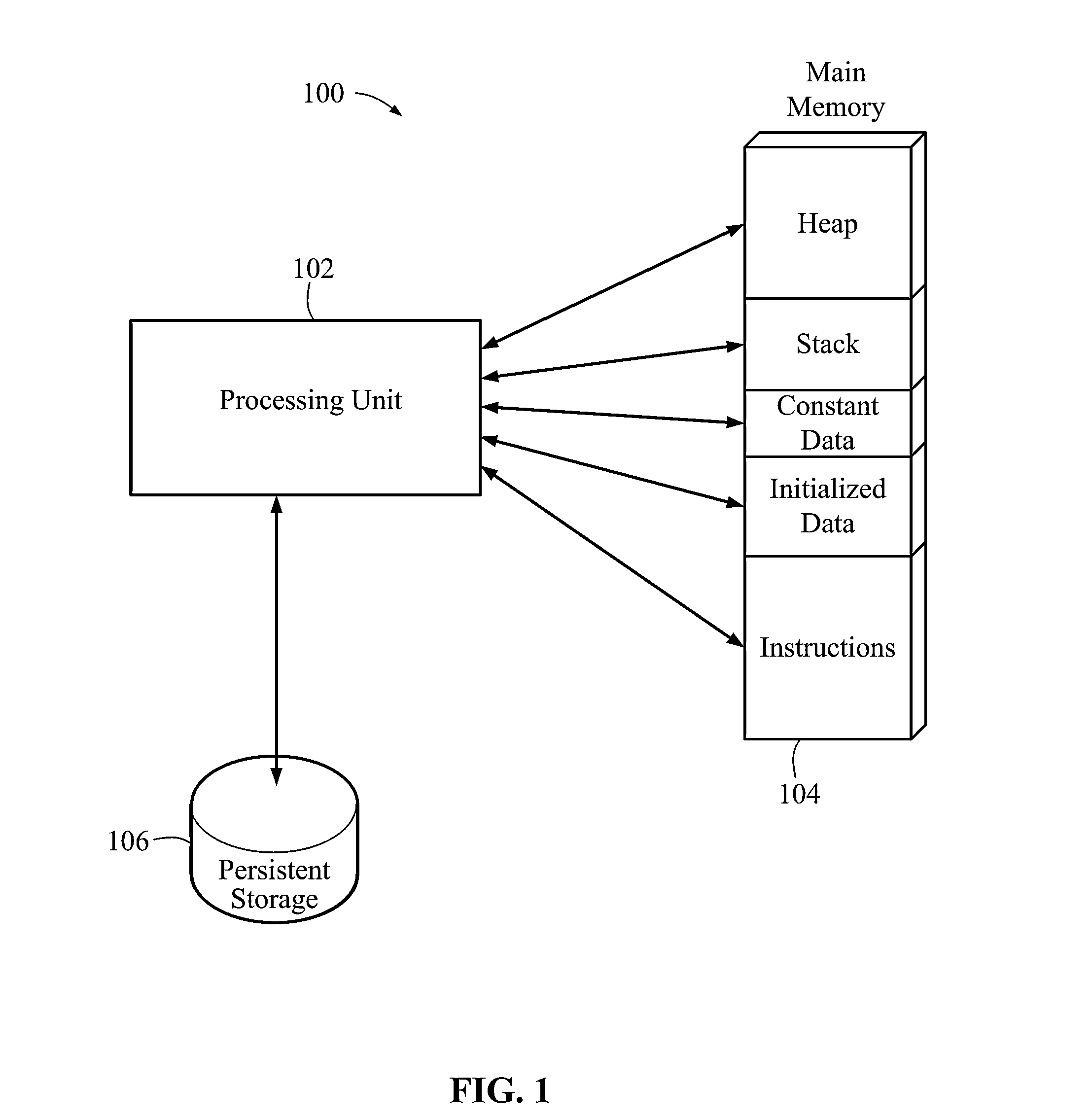
Methods, Devices, And Systems For Detecting Return-Oriented Programming Exploits
InactiveUS20130117843A1Memory architecture accessing/allocationMemory loss protectionCode snippetRemedial action
Methods, devices, and systems for detecting return-oriented programming (ROP) exploits are disclosed. A system includes a processor, a main memory, and a cache memory. A cache monitor develops an instruction loading profile by monitoring accesses to cached instructions found in the cache memory and misses to instructions not currently in the cache memory. A remedial action unit terminates execution of one or more of the valid code sequences if the instruction loading profile is indicative of execution of an ROP exploit involving one or more valid code sequences. The instruction loading profile may be a hit / miss ratio derived from monitoring cache hits relative to cache misses. The ROP exploits may include code snippets that each include an executable instruction and a return instruction from valid code sequences.
Owner:QUALCOMM INC
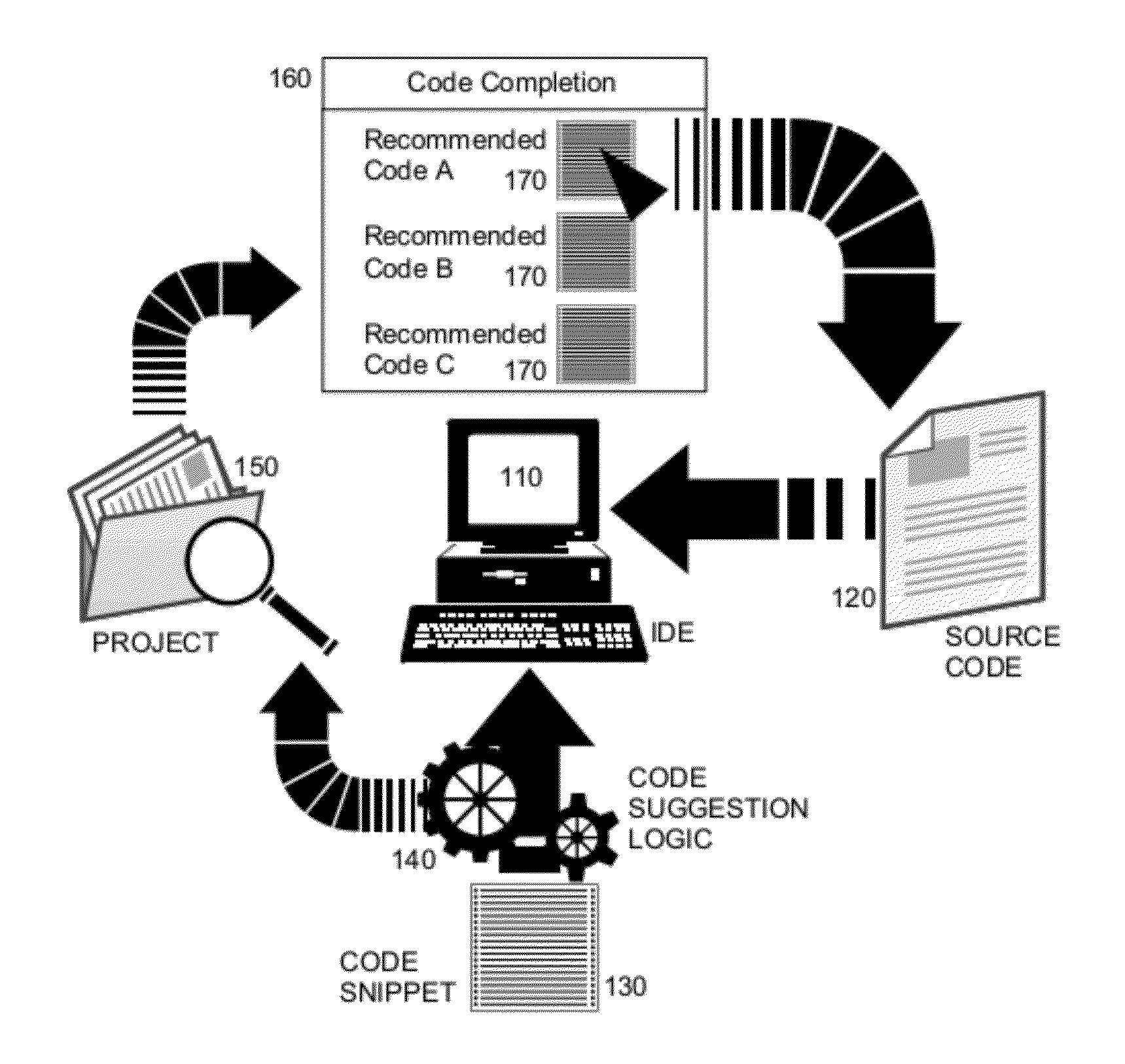
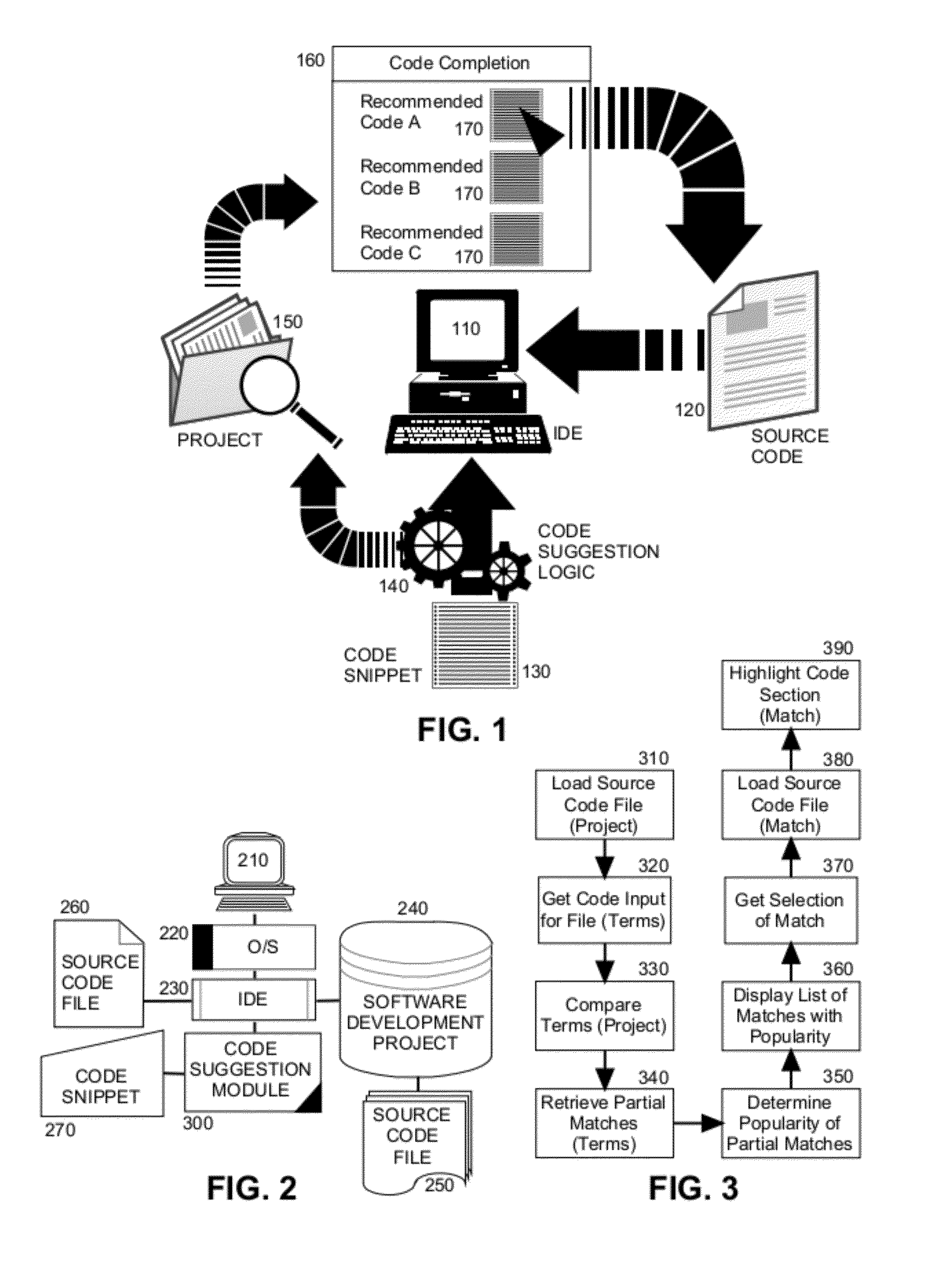
Code suggestion in a software development tool
ActiveUS20120174061A1Intelligent editorsSpecific program execution arrangementsCode snippetSource code file
Embodiments of the present invention provide a method, system and computer program product for the automated suggestion of code usage patterns in an IDE. In an embodiment of the invention, a method for automated suggestion of code usage patterns in an IDE is provided. The method includes receiving input of a code snippet for a source code file of a software development project loaded into memory of a host computer for display through an IDE. The method further includes matching terms of the received input to terms in different blocks of code in different source code files of the software development project. The method yet further includes selecting one of the different blocks of code as a code completion choice for insertion into the source code file in the IDE. Finally, the method includes inserting the selected one of the different blocks of code into the source code file in the IDE.
Owner:IBM CORP
System and method for detecting classes of automated browser agents
ActiveUS20150112892A1Reduce probabilityMathematical modelsDigital data authenticationWeb browserCode snippet
A method for determining if a web browser is being operated by a human or a non-human agent, based on analysis of certain aspects of how a user interacts with a webpage. By placing a code snippet into the code of a webpage prior to a given user accessing that webpage, one is able to evaluate the user's actions in order to predict the type of user. The predictions are made by acquiring information on how the user loads, navigates, and interacts with the webpage and comparing that information with statistics taken from a control group. Performance metrics from all webpages containing similar code elements are compiled by analysis servers and made available to the operator of a webpage through a variety of reporting mediums. By compiling such performance metrics, the method helps combat and prevent malicious automated traffic directed at advertisements and other aspects of a given webpage.
Owner:HUMAN SECURITY INC
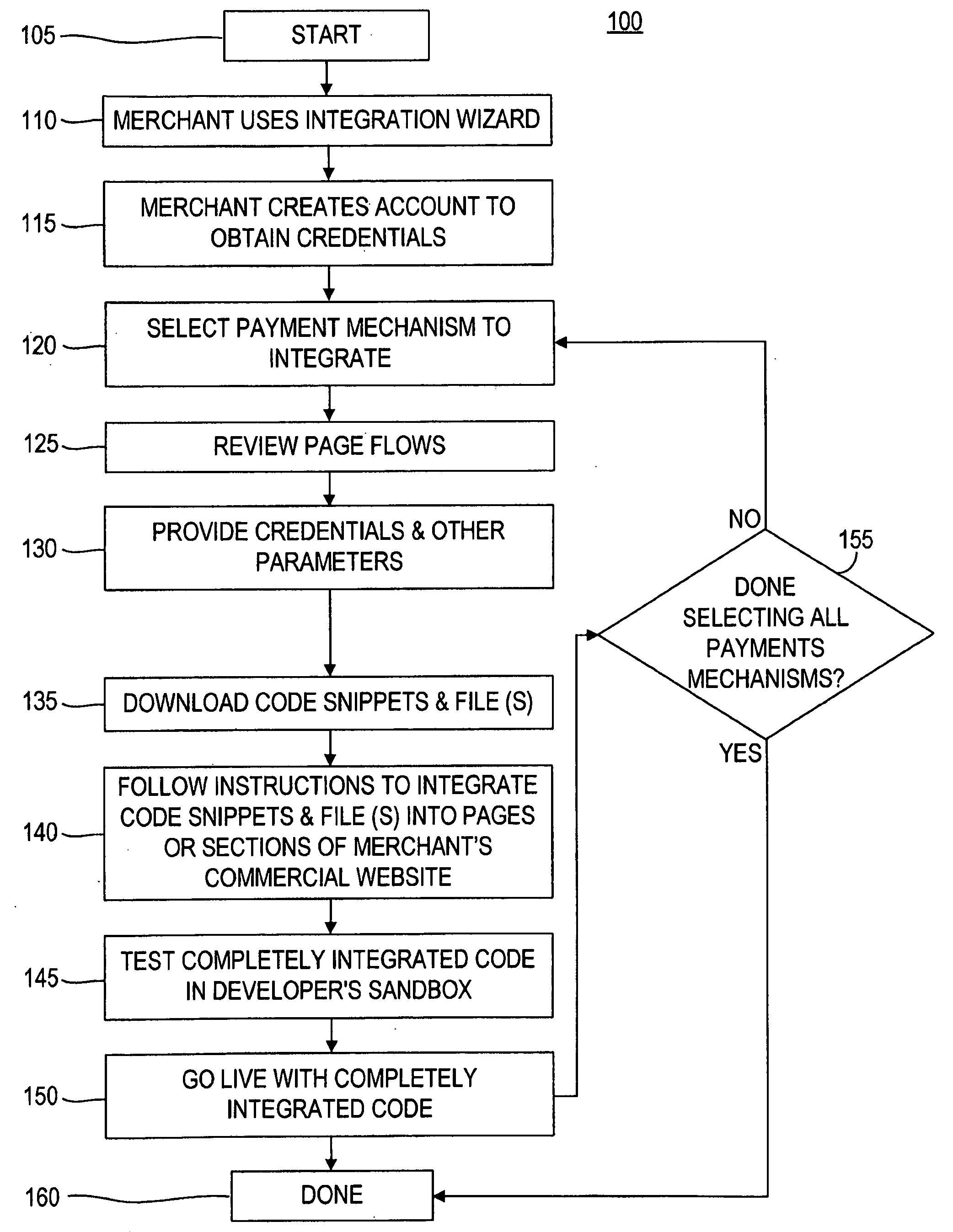
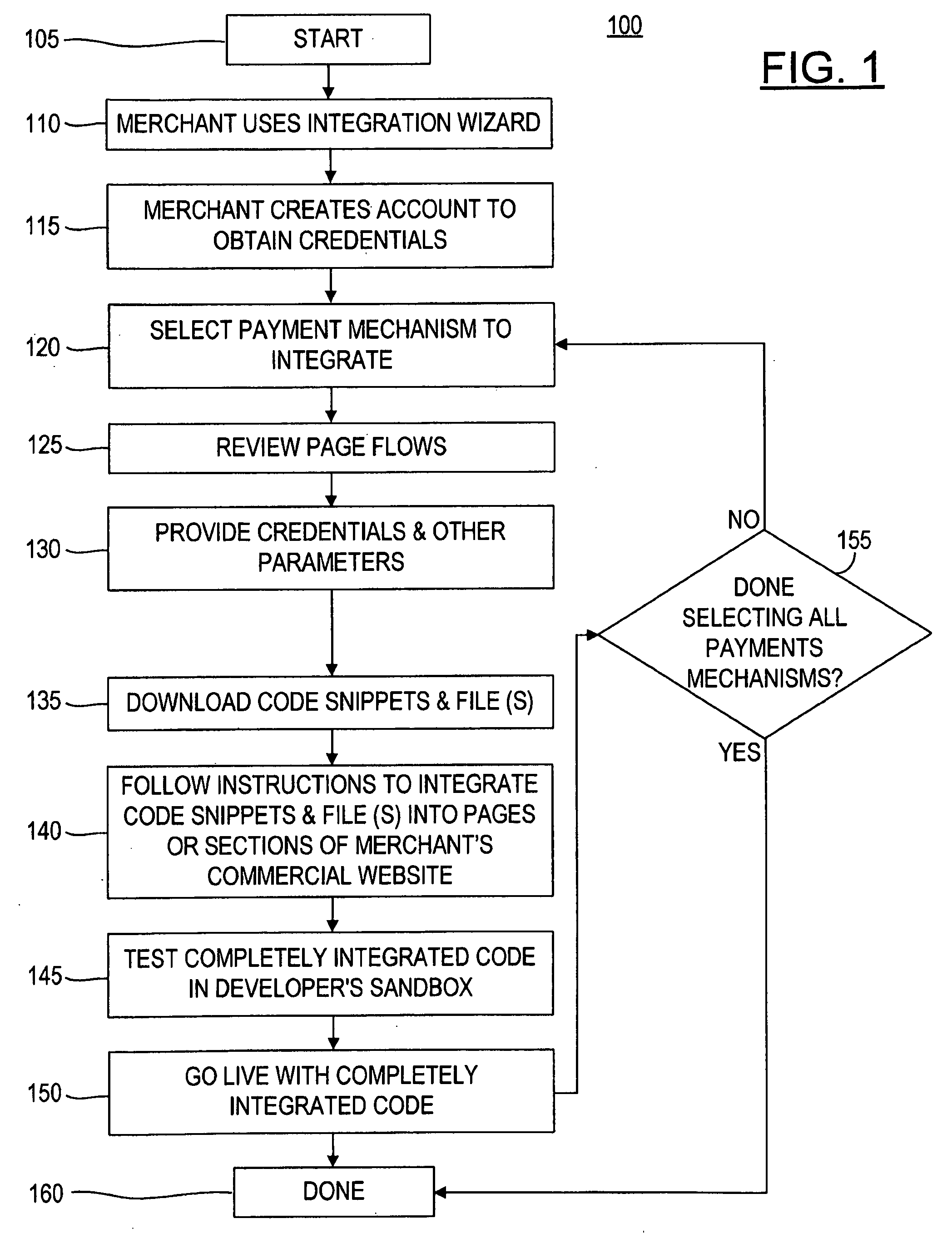
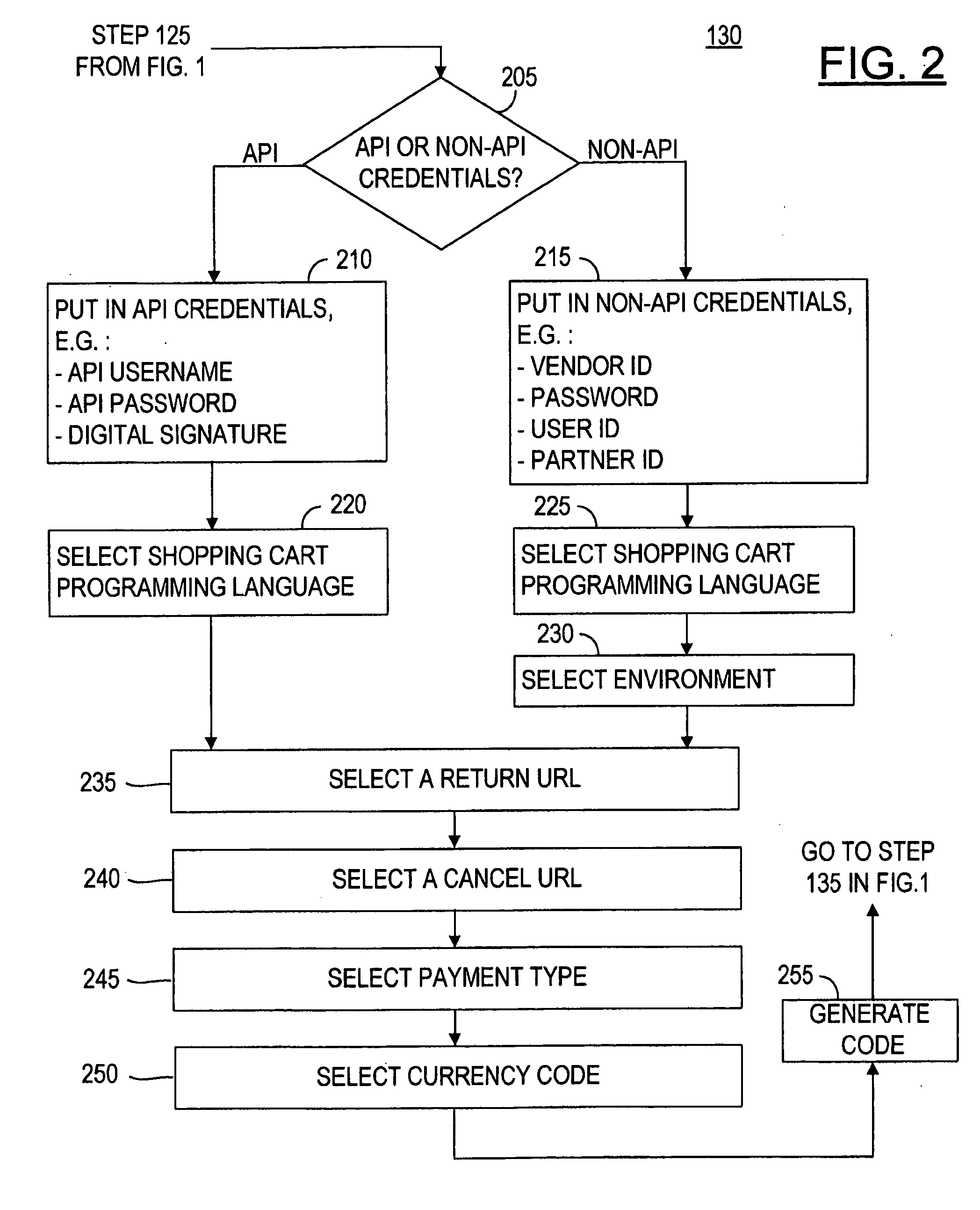
Payment Mechanism Integration Wizard
Provided is a method and a web-site integration system to integrate payment mechanisms into a commercial website that offers online merchants a flexible, user-friendly and customizable wizard to integrate payment mechanisms into their online commercial websites without having to understand the detailed intricacies of an API or other computer code. The wizard steps the merchant through creating an account to obtain credentials and educates the merchant on the page flows of the payment mechanism that the merchant wishes to integrate. Then, the wizard generates code snippets and files to be downloaded by the merchant and to be easily inserted into key pages of the merchant's online commercial website. The merchant can then test the completely integrated code in a developer's sandbox or go live with the completely integrated code.
Owner:PAYPAL INC
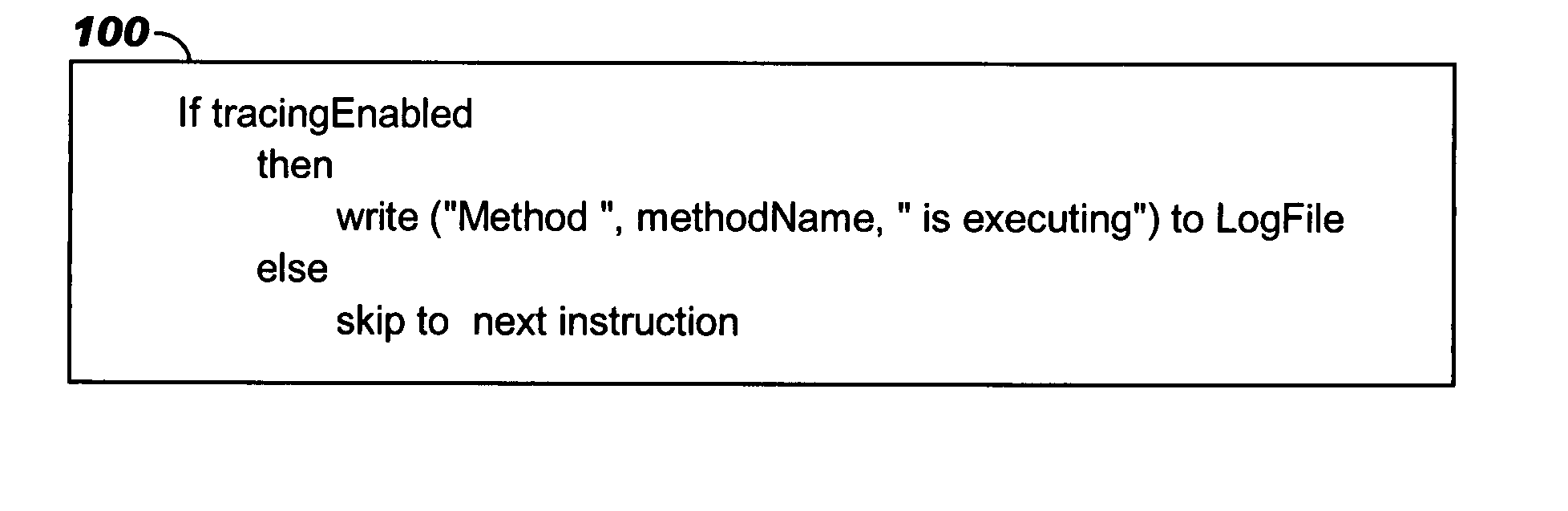
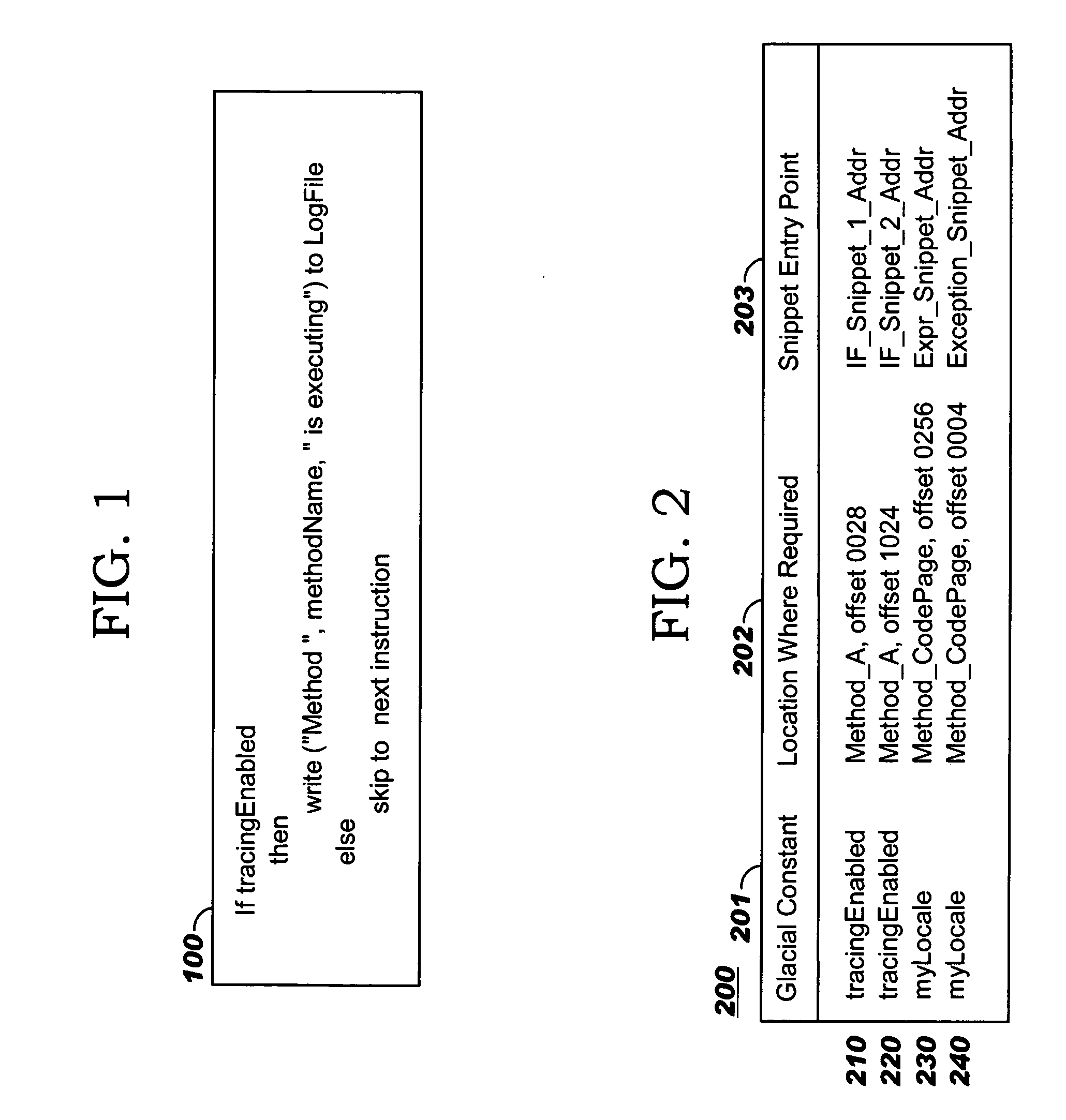
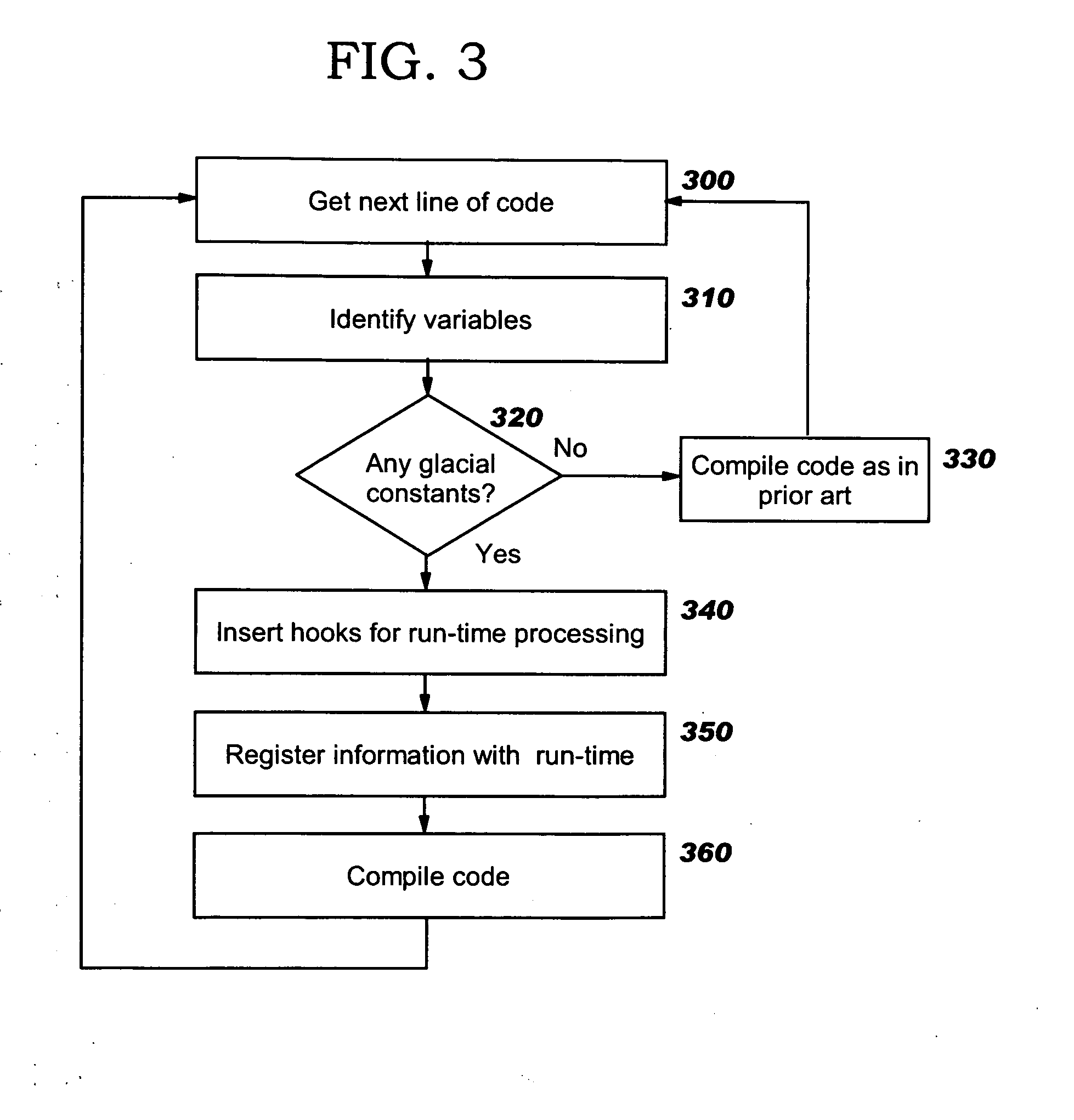
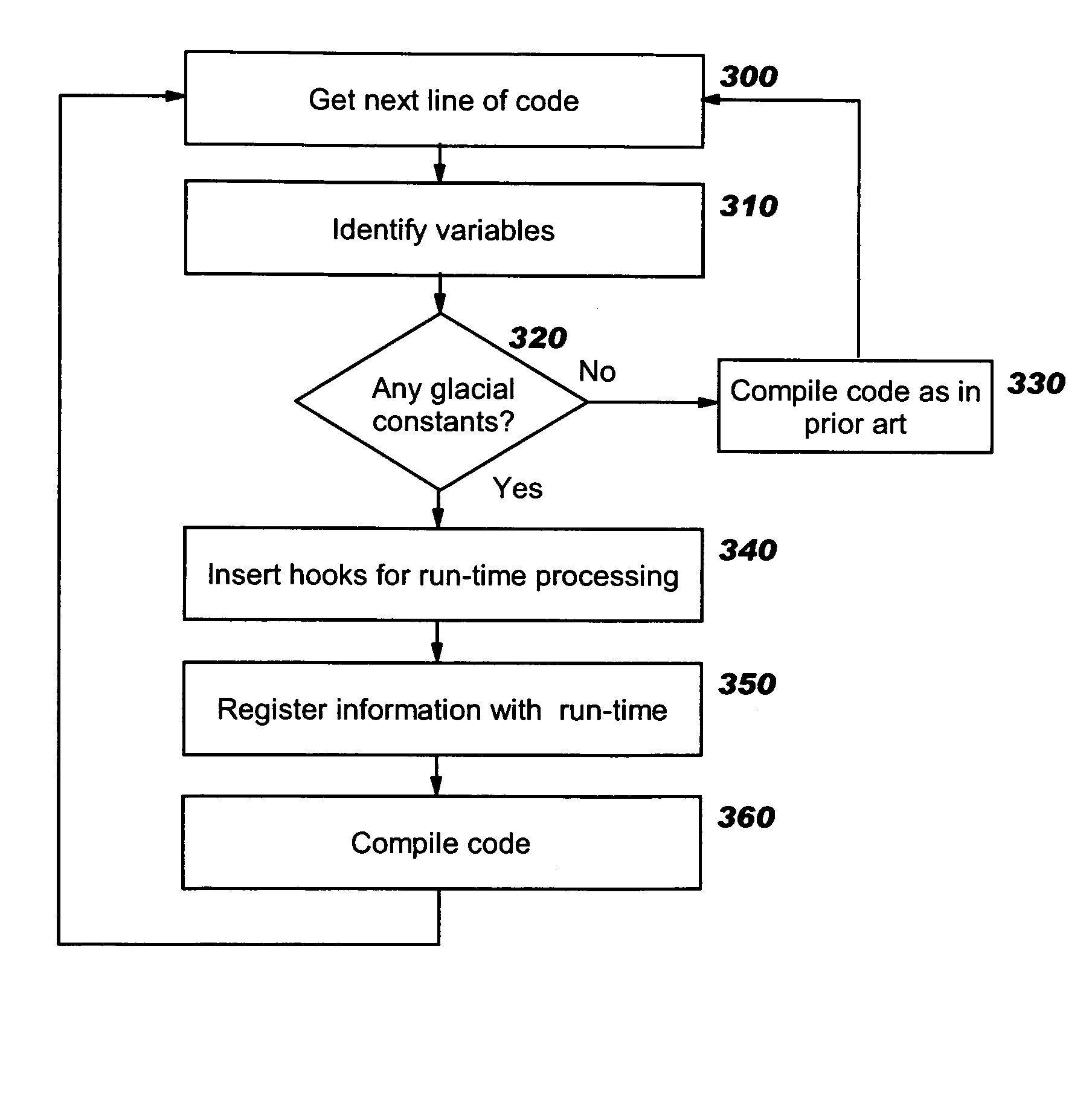
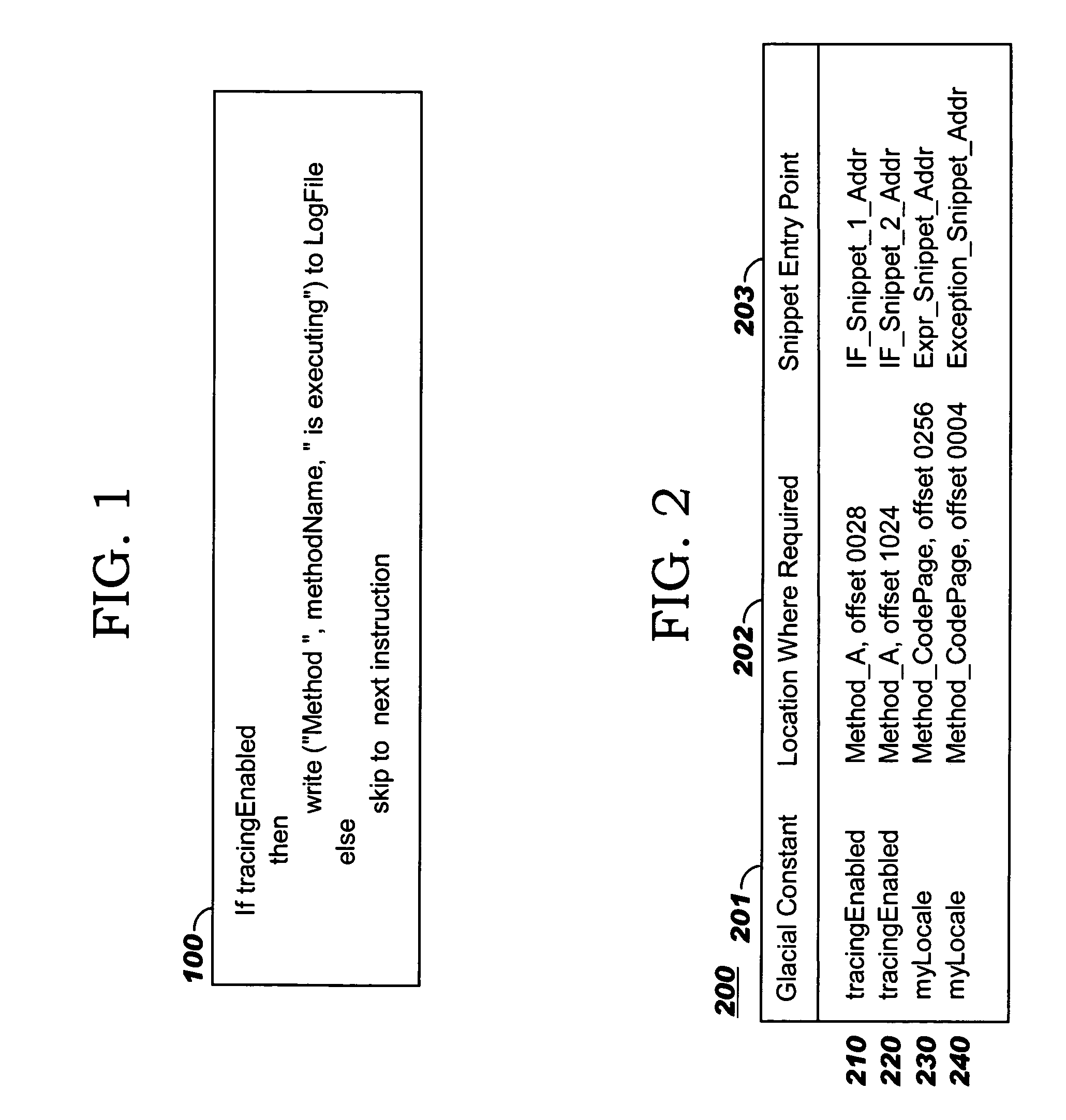
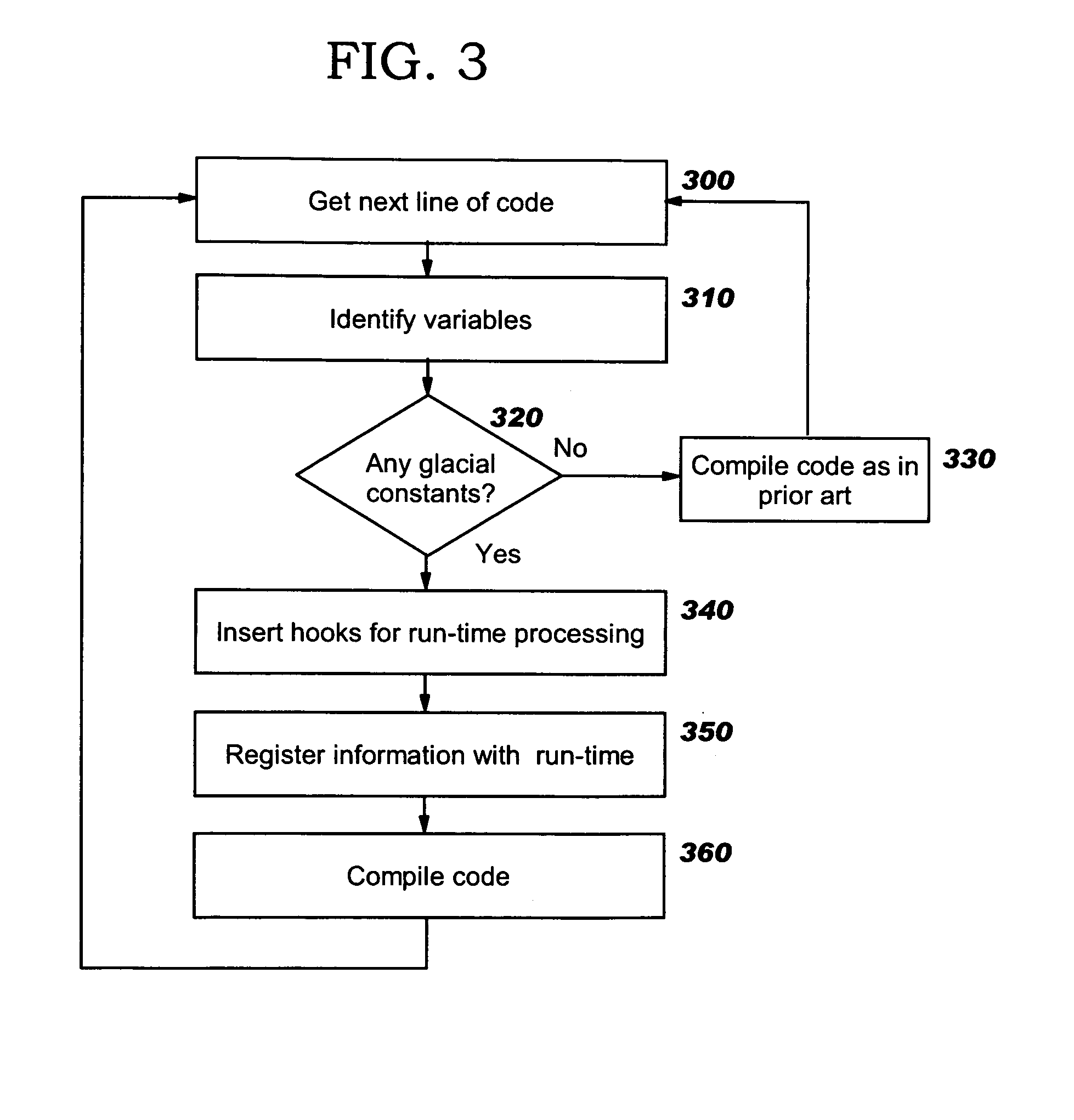
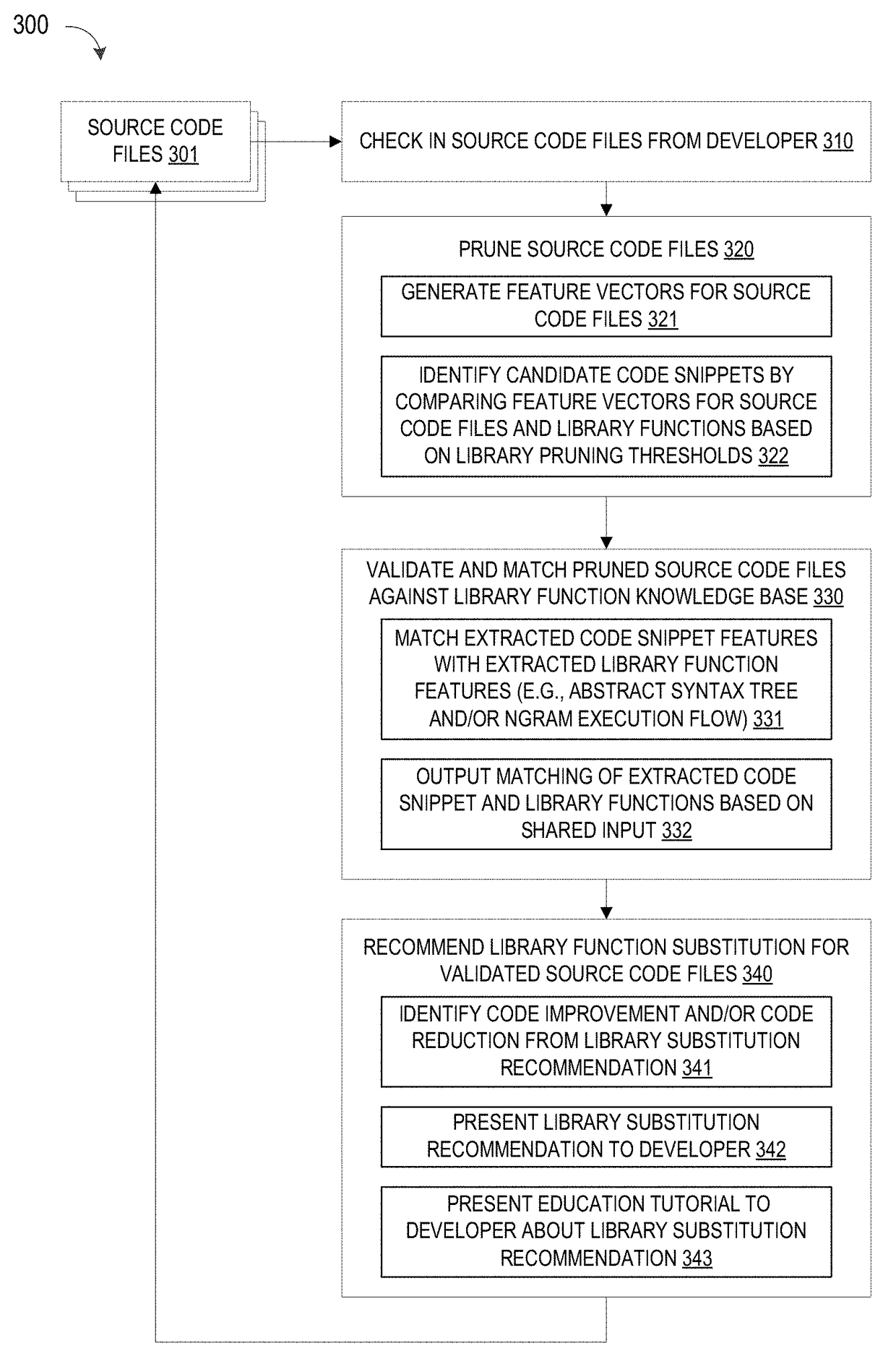
Programmatic compiler optimization of glacial constants
Optimizations are programmatically applied by a compiler (preferably, a just-in-time or “JIT” compiler), and enable achieving improved performance while a variable acts as a global constant, yet also allow code to execute correctly if the global constant's run-time value changes from the value on which the optimization was originally based. Code snippets that dynamically patch executable code are described, where these code snippets take corrective actions to enable correct program execution following a run-time change to the value of a glacial constant. A backup recovery path may also be maintained, where this path provides code that is executed in the event of a change to a glacial constant and that treats the glacial constant as a variable. Recompilation may also be used after a change to a glacial constant, where the originally-compiled code has made an assumption about the glacial constant's value that is no longer accurate. Combinations of these approaches may be used.
Owner:IBM CORP
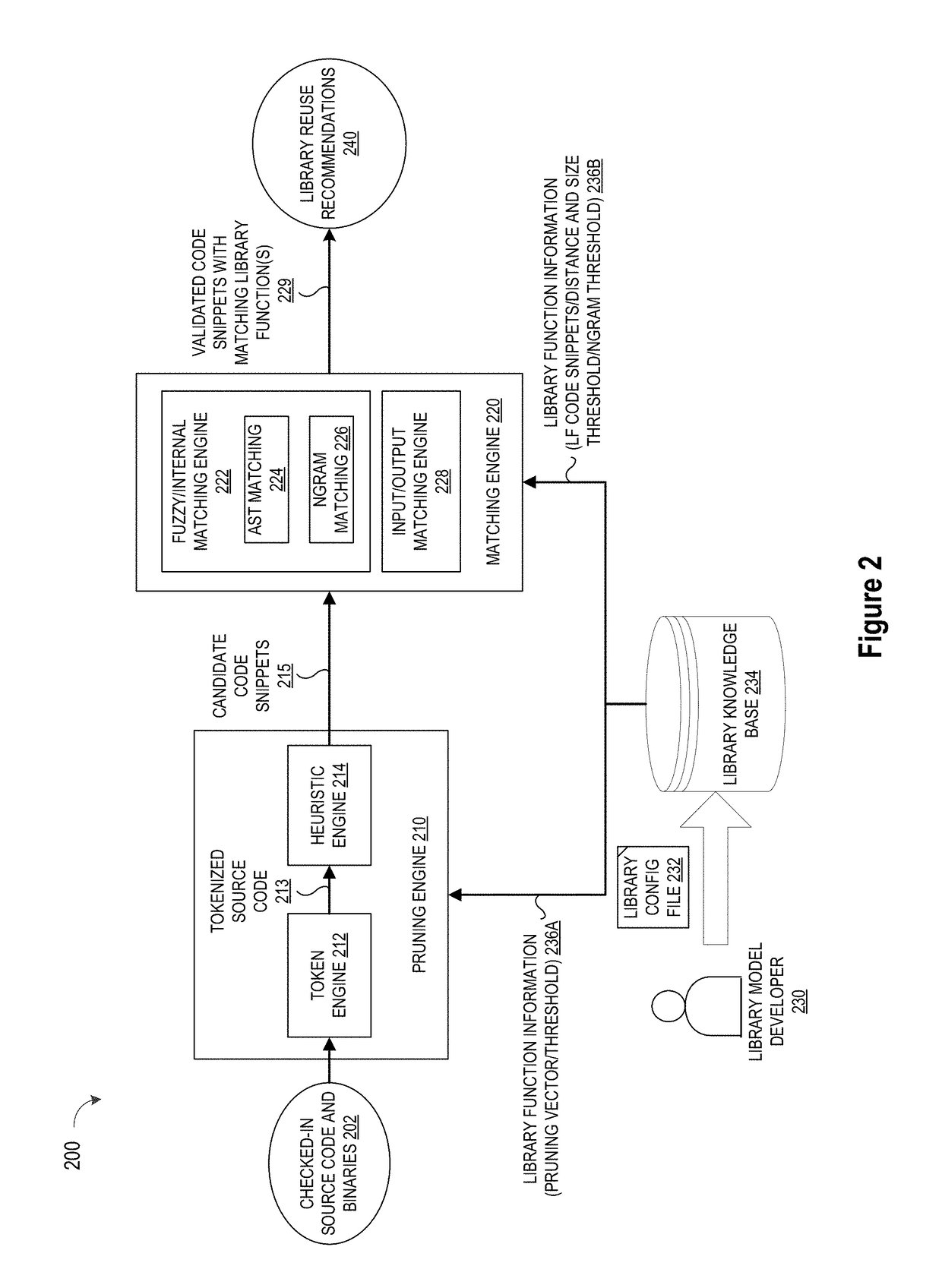
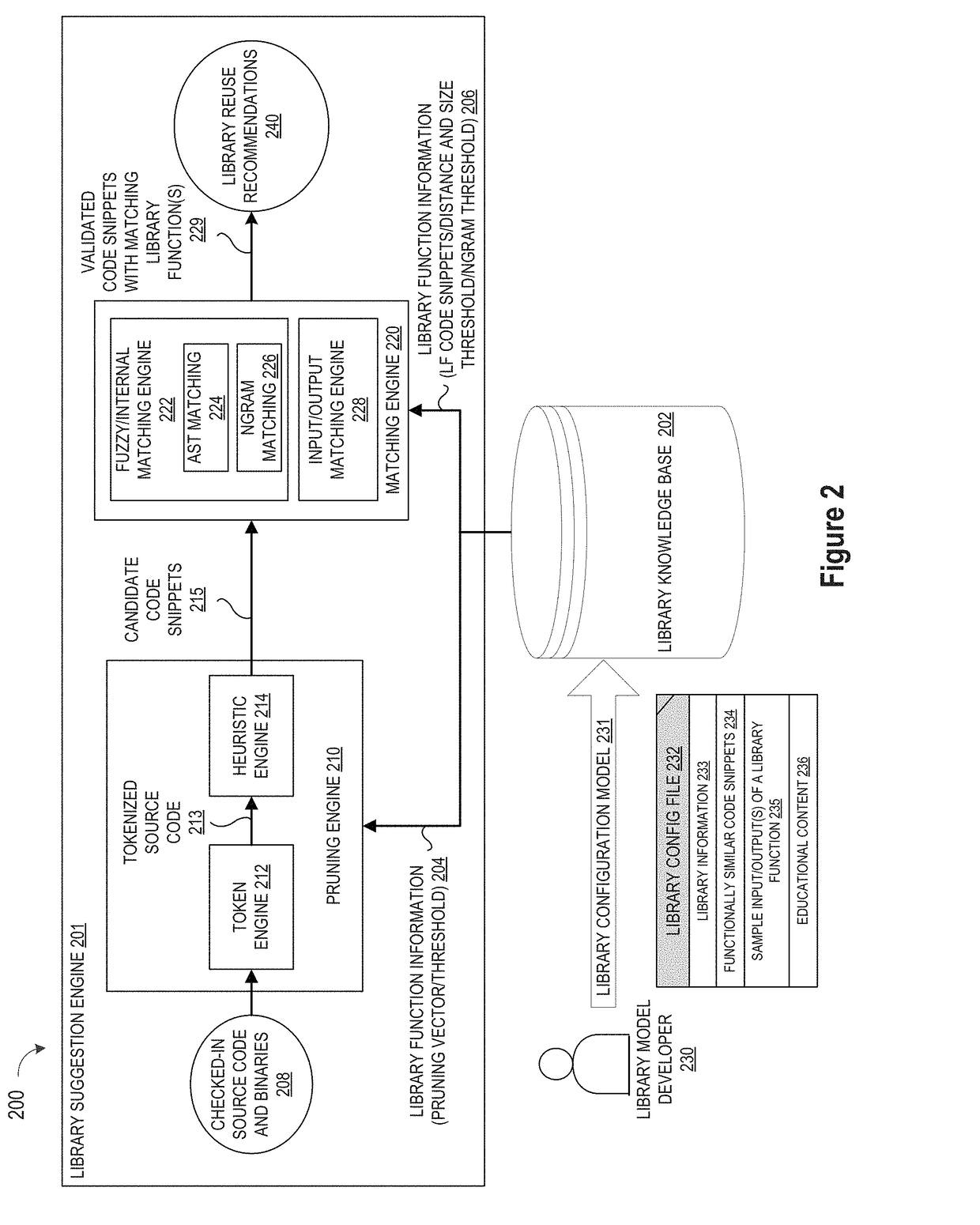
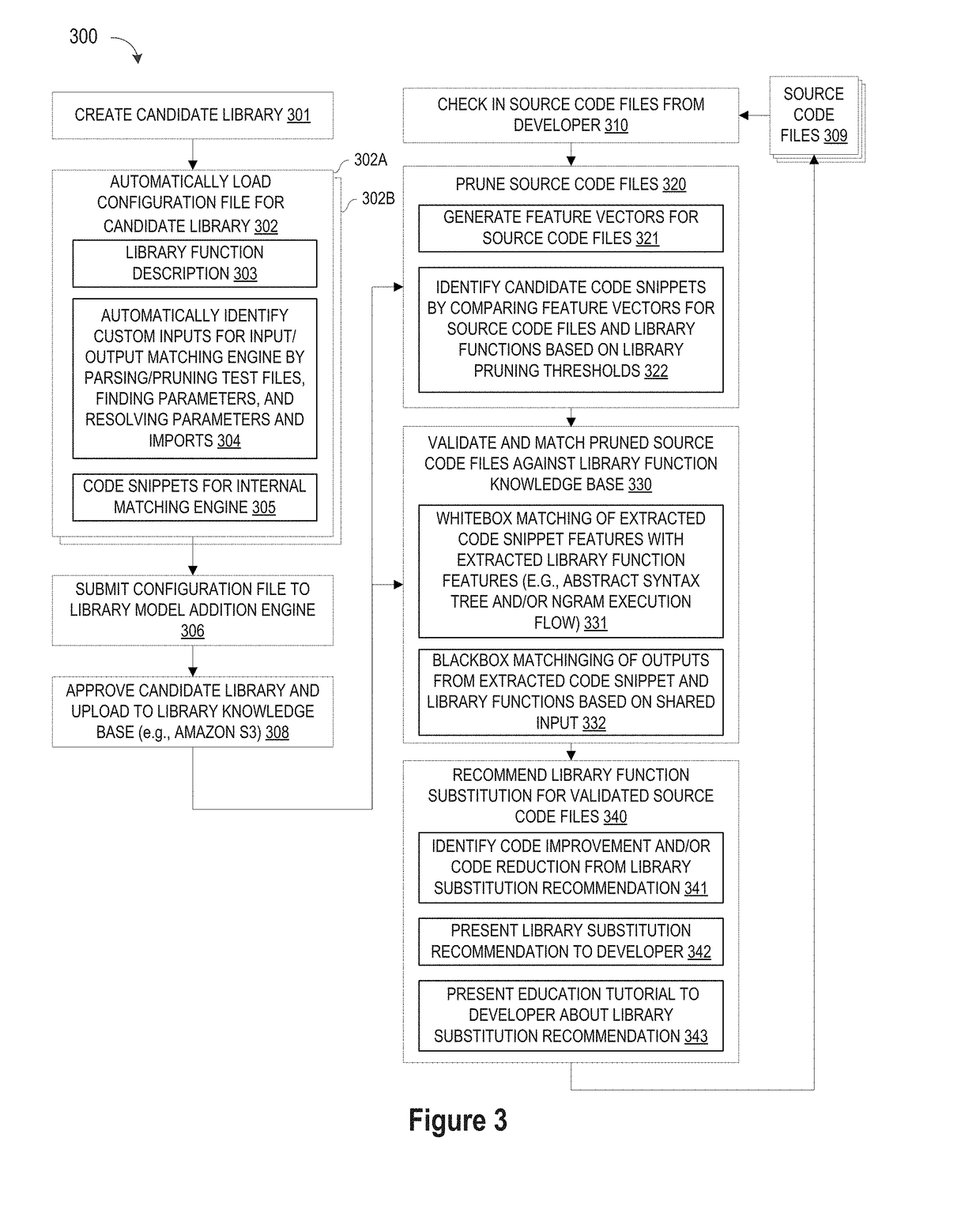
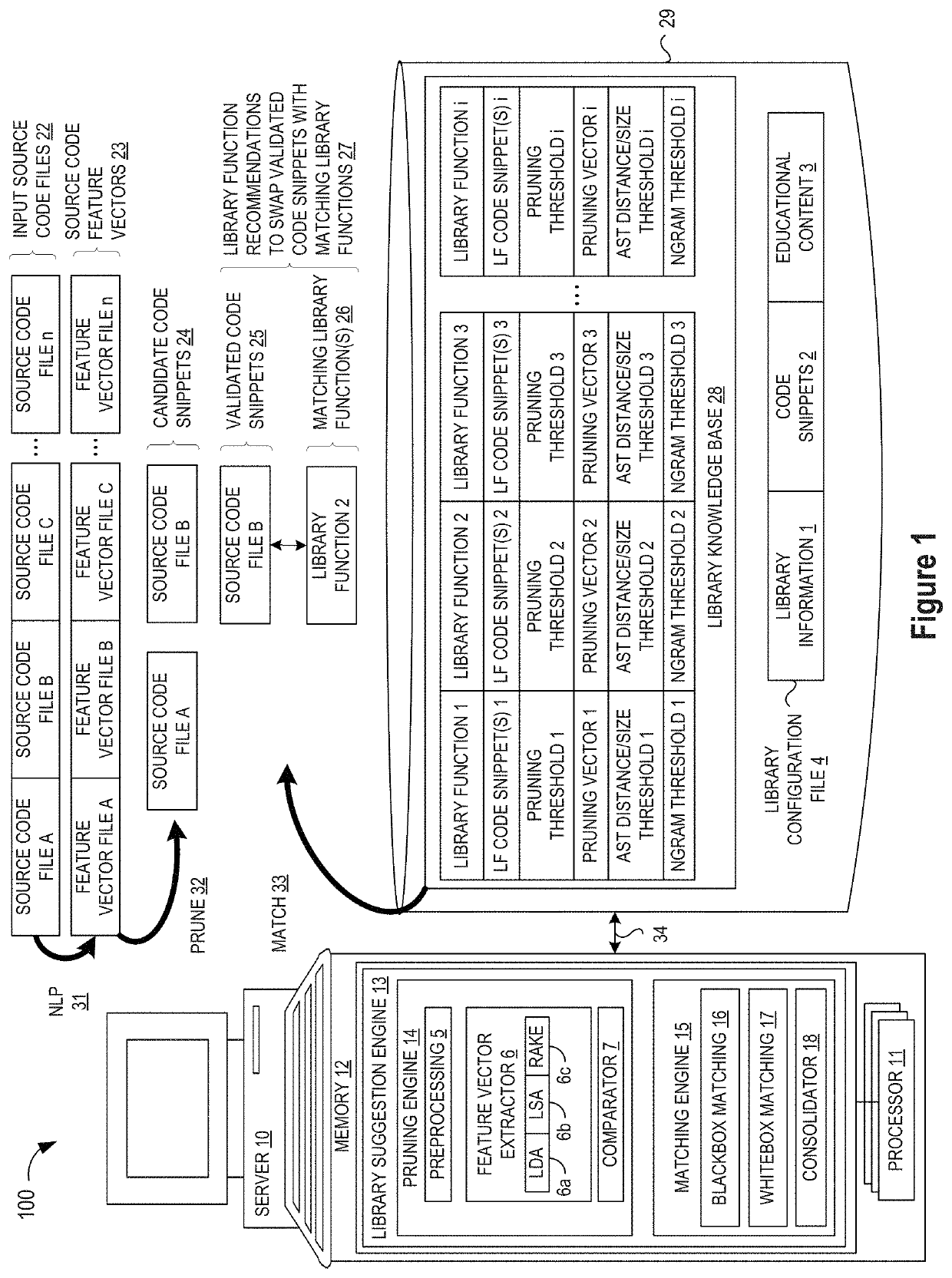
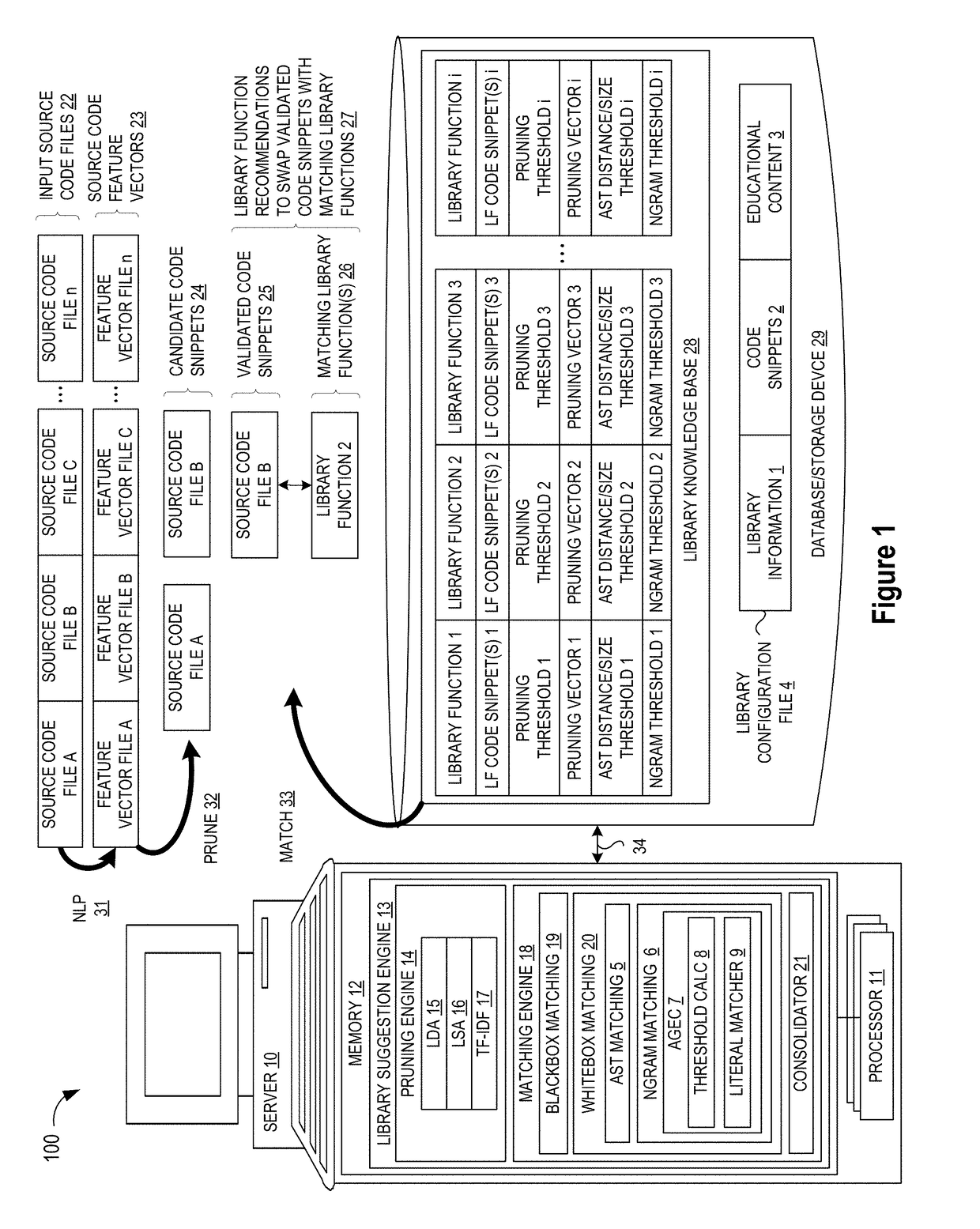
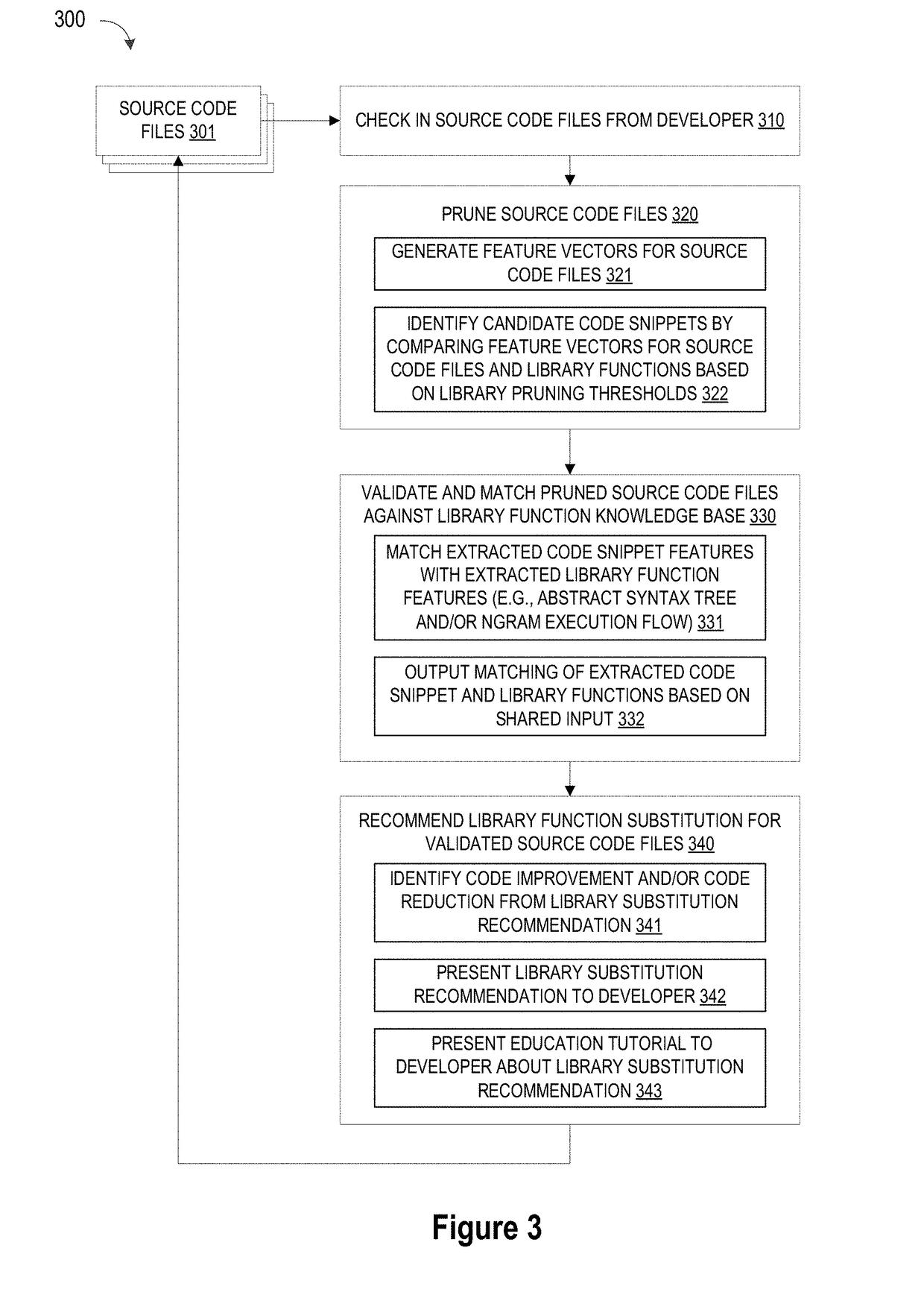
Blackbox matching engine
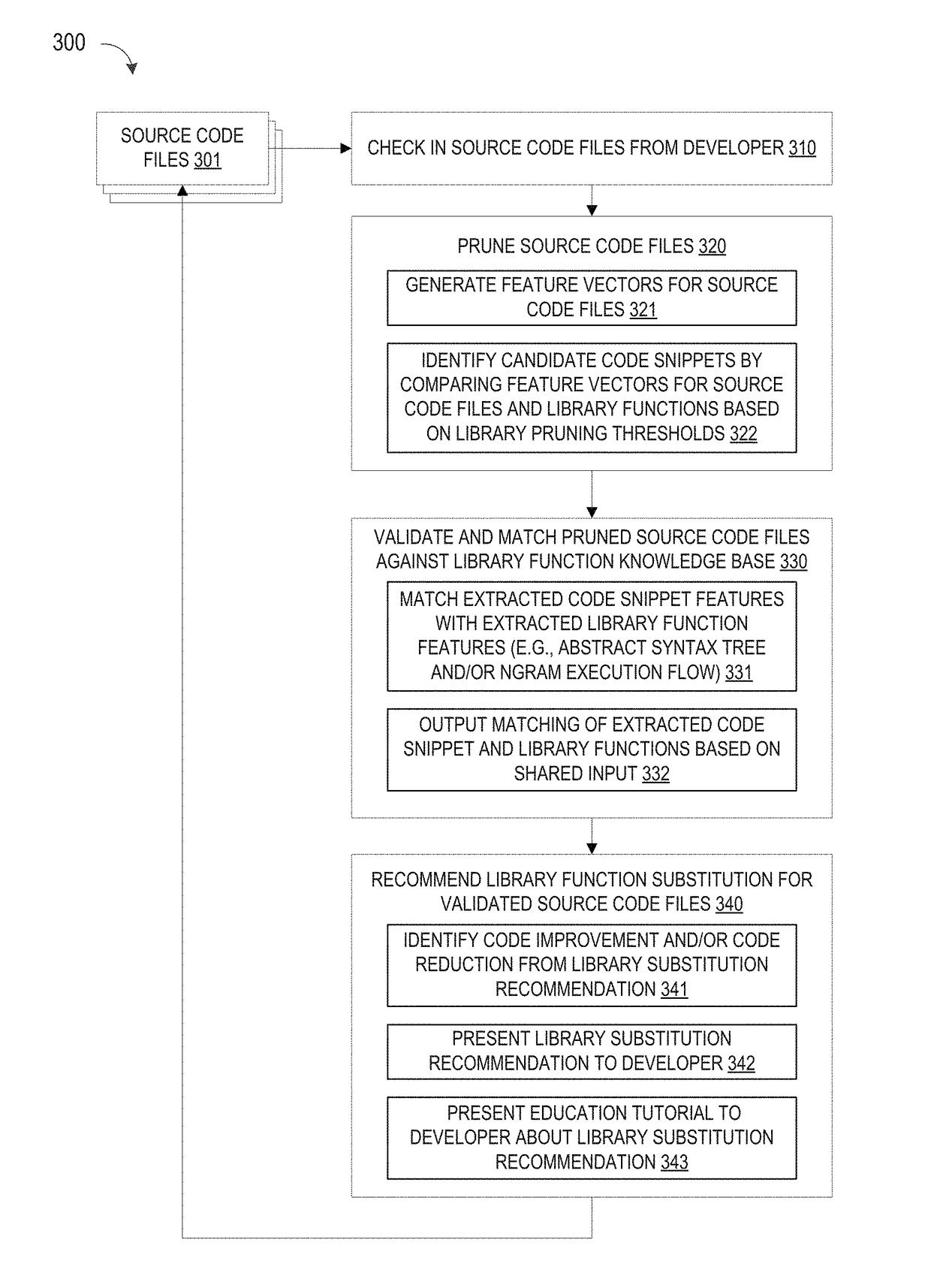
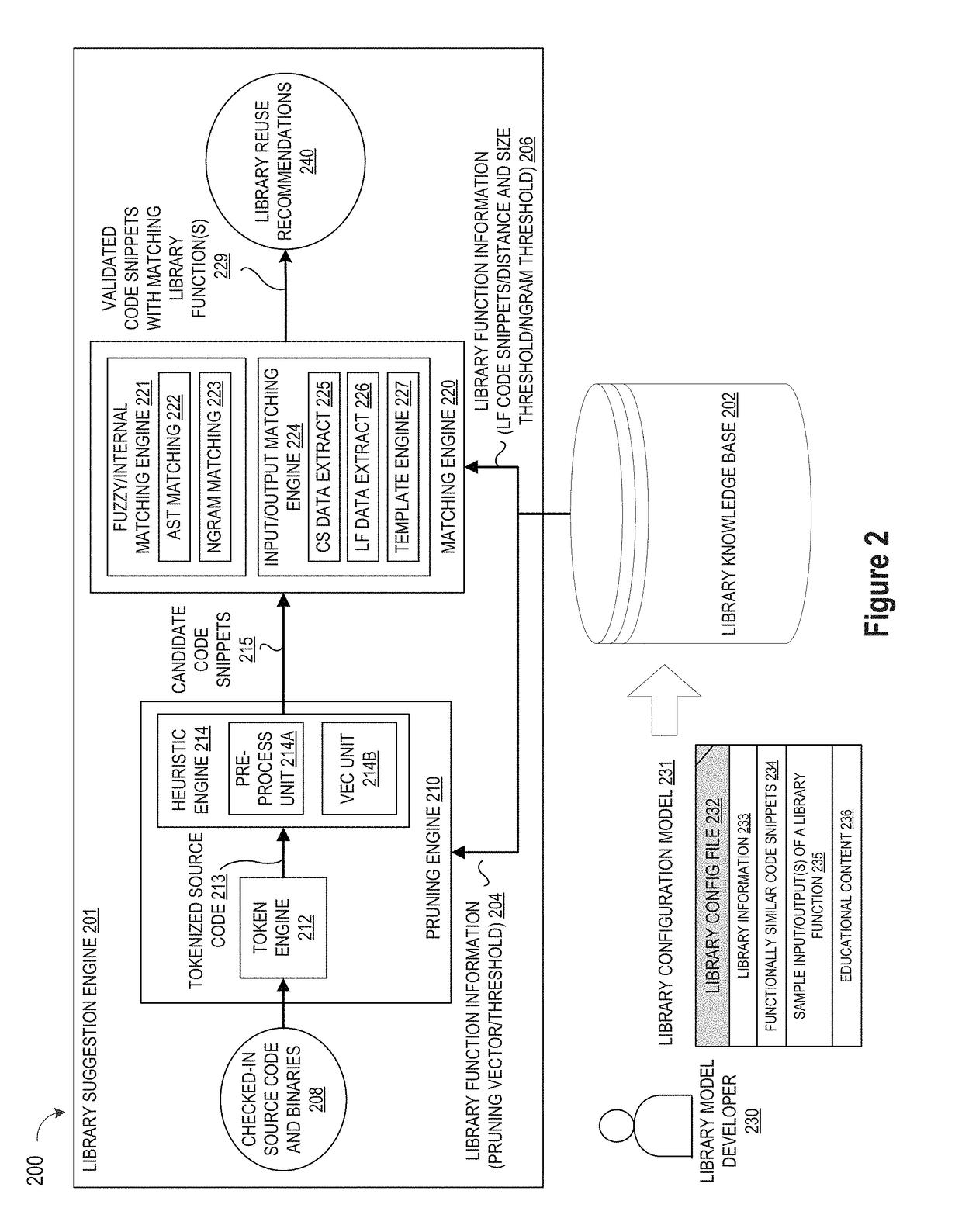
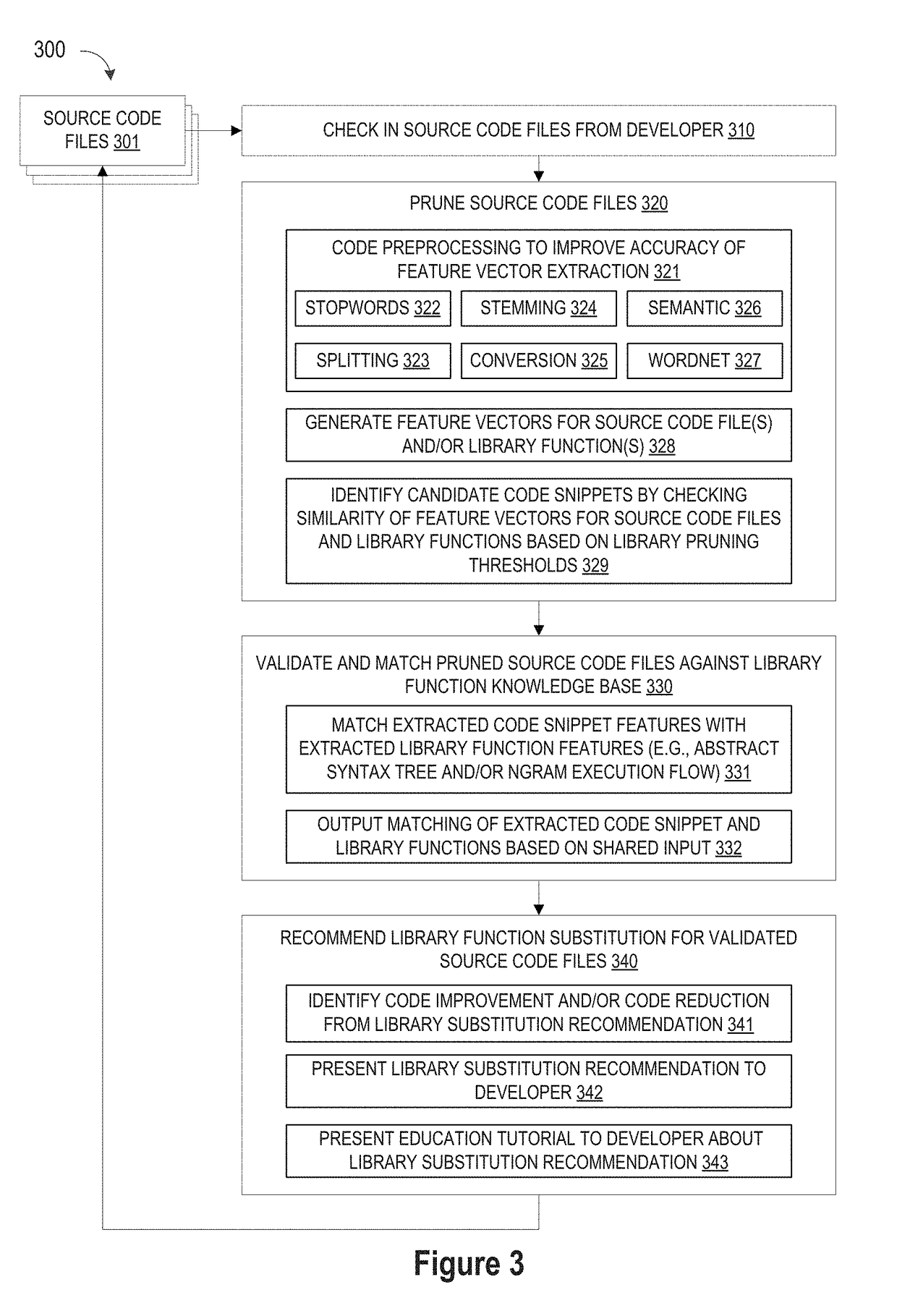
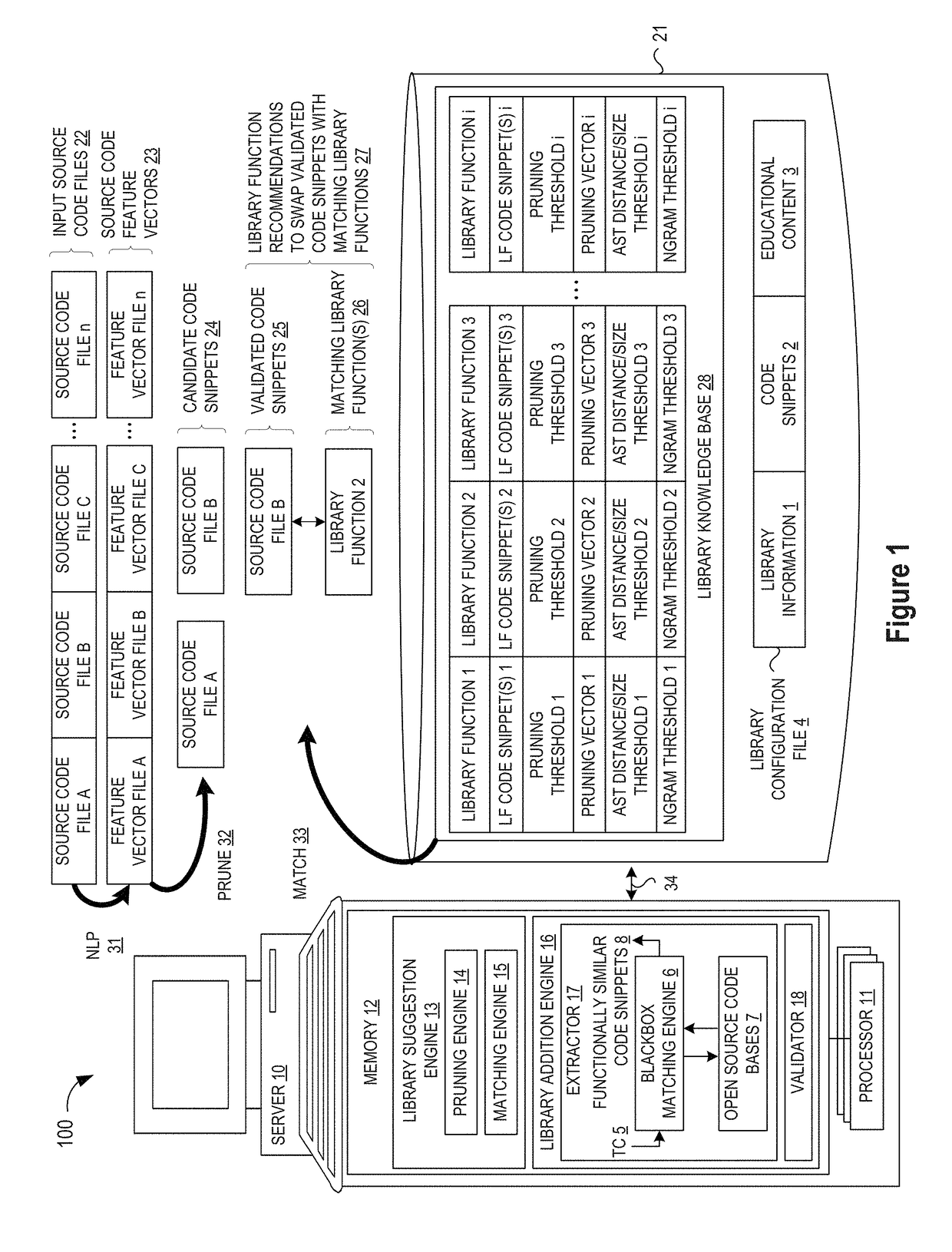
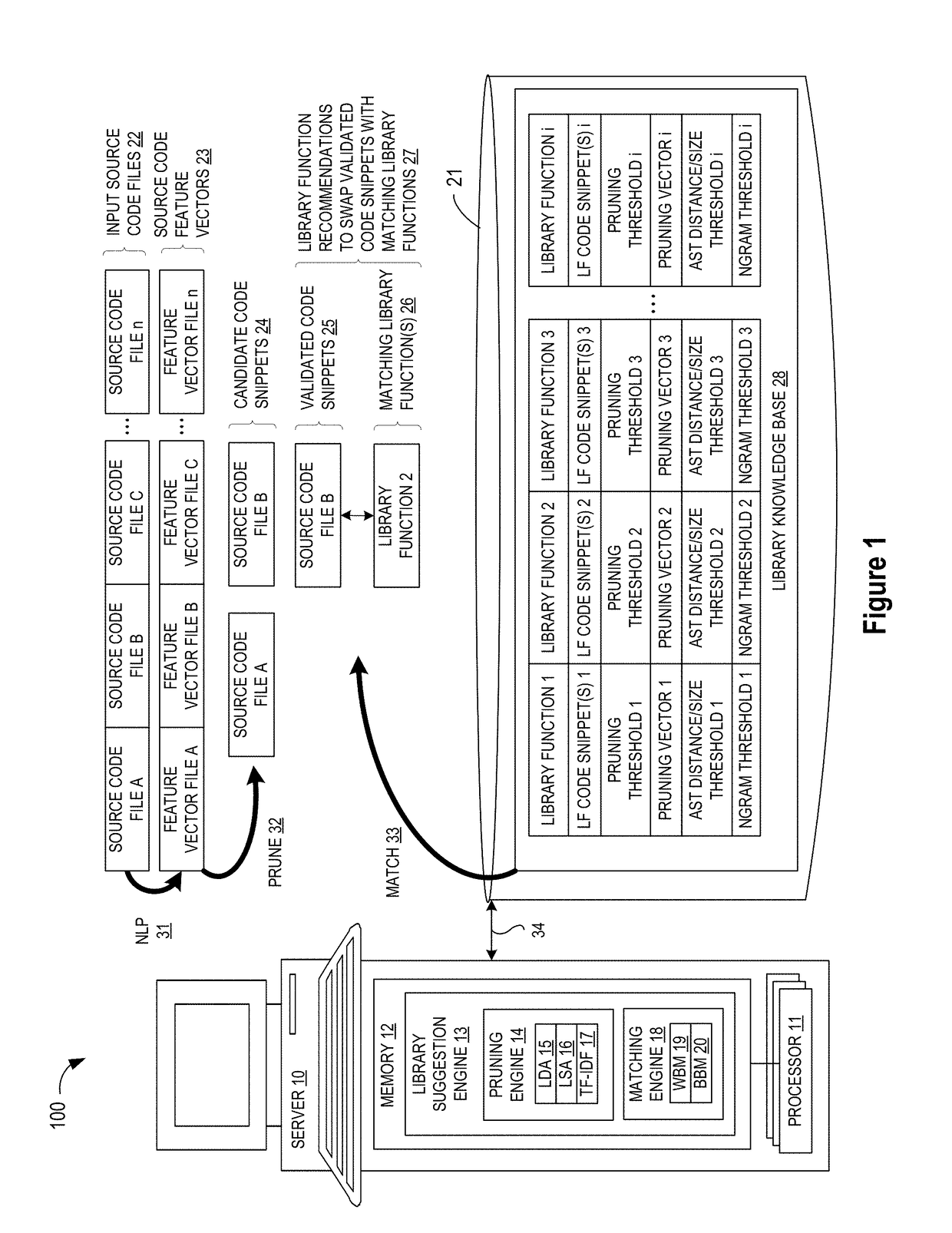
ActiveUS10114624B1Improve code reuseImproving codebase maintainabilityConditional code generationError detection/correctionSource code fileCode snippet
A method and apparatus are disclosed for enhancing operable functionality of input source code files from a software program by identifying a first code snippet and a first library function which generate similar outputs from a shared input by parsing each and every line of code in a candidate code snippet to generate a templatized code snippet data structure for the first code snippet, and then testing the templatized code snippet data structure against extracted library function information to check for similarity of outputs between the first code snippet and the first library function in response to a shared input so that the developer is presented with a library function recommendation which includes the first code snippet, the first library function, and instructions for replacing the first code snippet with the first library function.
Owner:DEVFACTORY INNOVATIONS FZ LLC
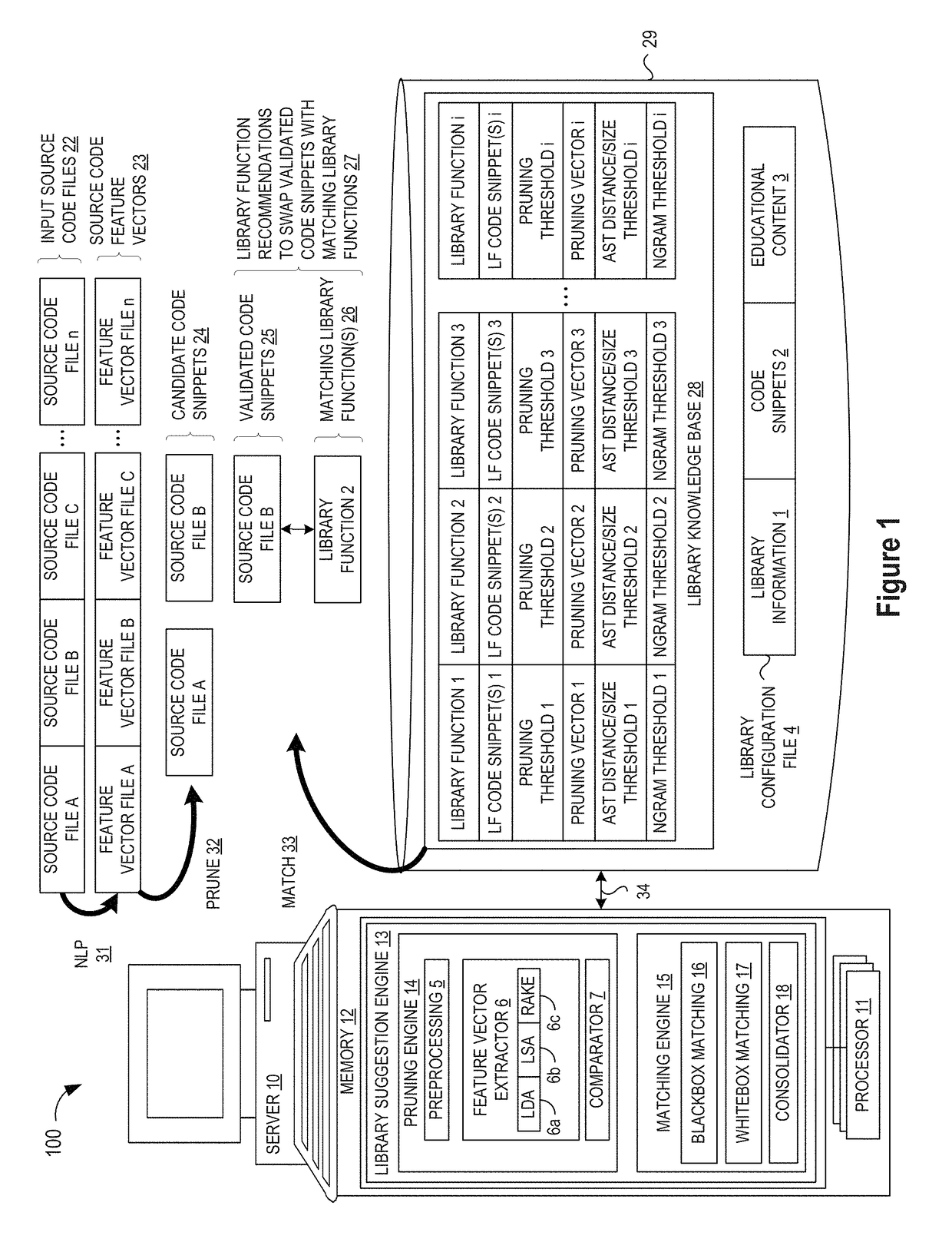
Pruning Engine
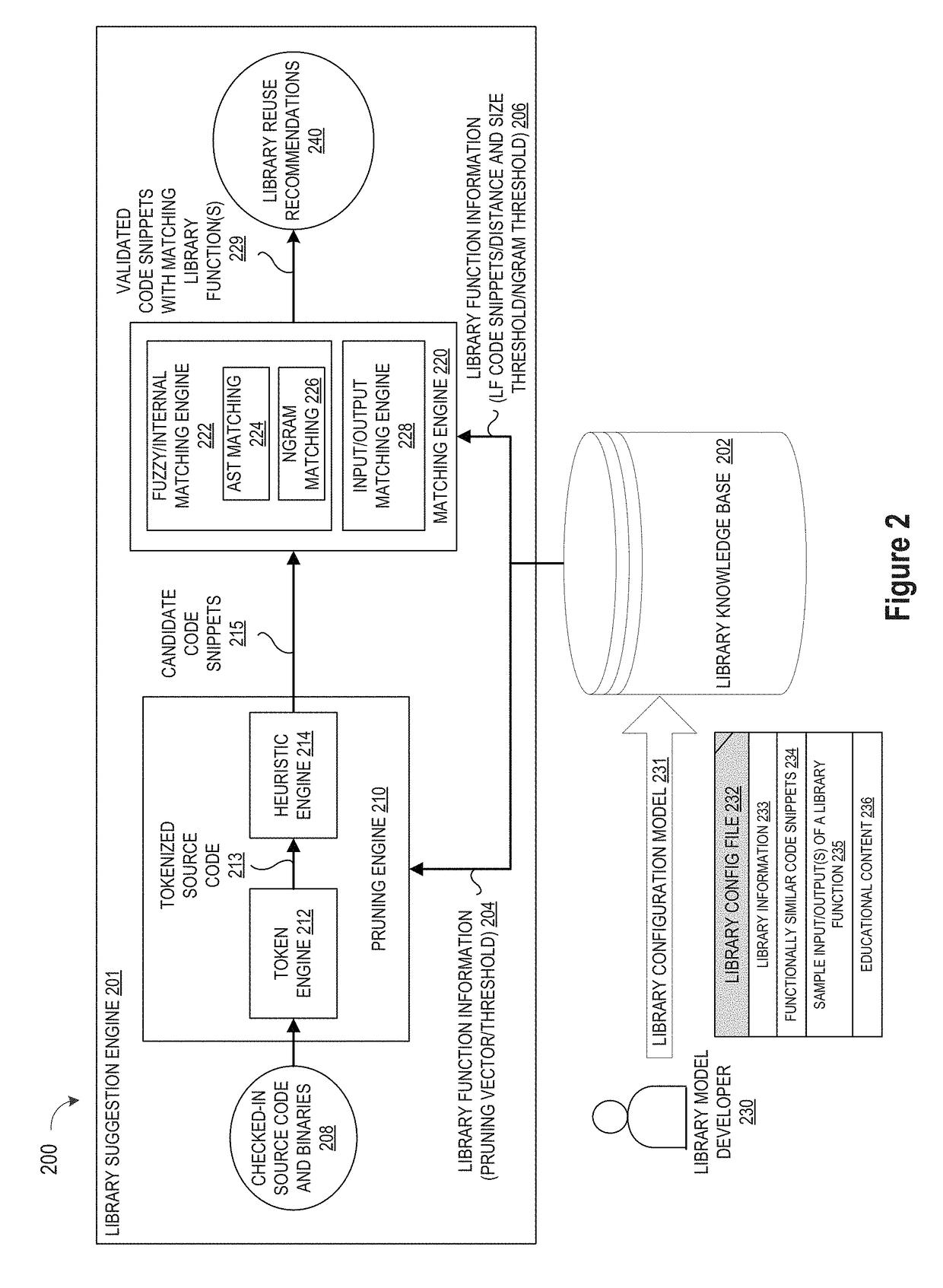
ActiveUS20190079741A1Improve code reuseImprove accuracyVersion controlCode refactoringCode snippetSource code file
A method and apparatus are disclosed for enhancing operable functionality of input source code files from a software program by preprocessing input source code files with codeword processing operations to generate a plurality of preprocessed input source code files, identifying candidate code snippets by pruning one or more preprocessed input source code files that do not meet a similarity threshold measure for library functions stored in the system library, and identifying at least a first validated code snippet from the one or more candidate code snippets that matches a first library function stored in the system memory on the basis of at least first and second matching metrics.
Owner:DEVFACTORY INNOVATIONS FZ LLC
Collaborative software development systems and methods providing automated programming assistance
Collaborative program development systems are provided which implement methods for providing automated programming assistance to code developers in a collaborative program development environment. In particular, systems and methods for automated programming assistance are supported by leveraging a database or library of shared code snippets that are classified according to code patterns and rating scores that are derived from feedback and input from various code developers within a collaborative program development environment.
Owner:IBM CORP
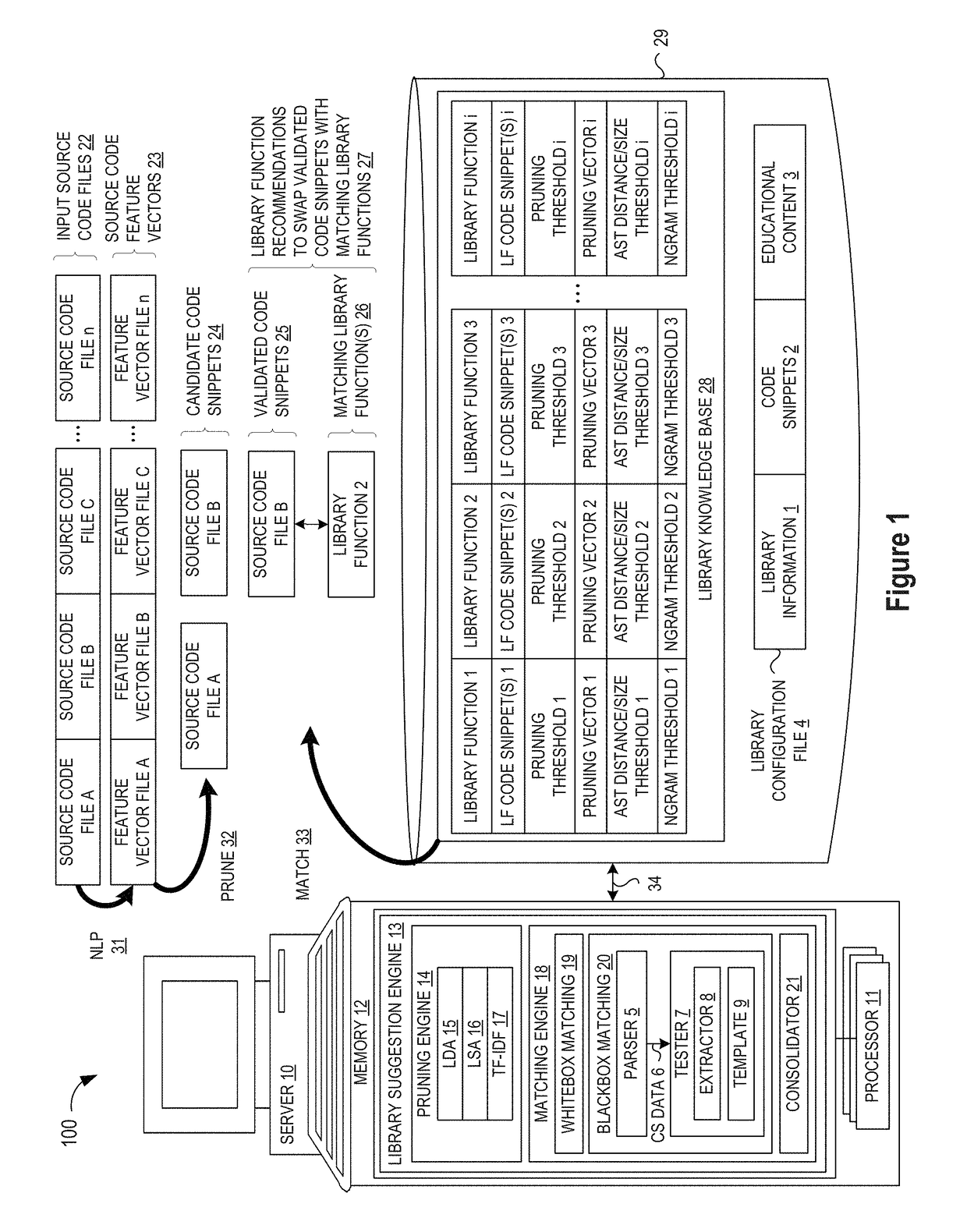
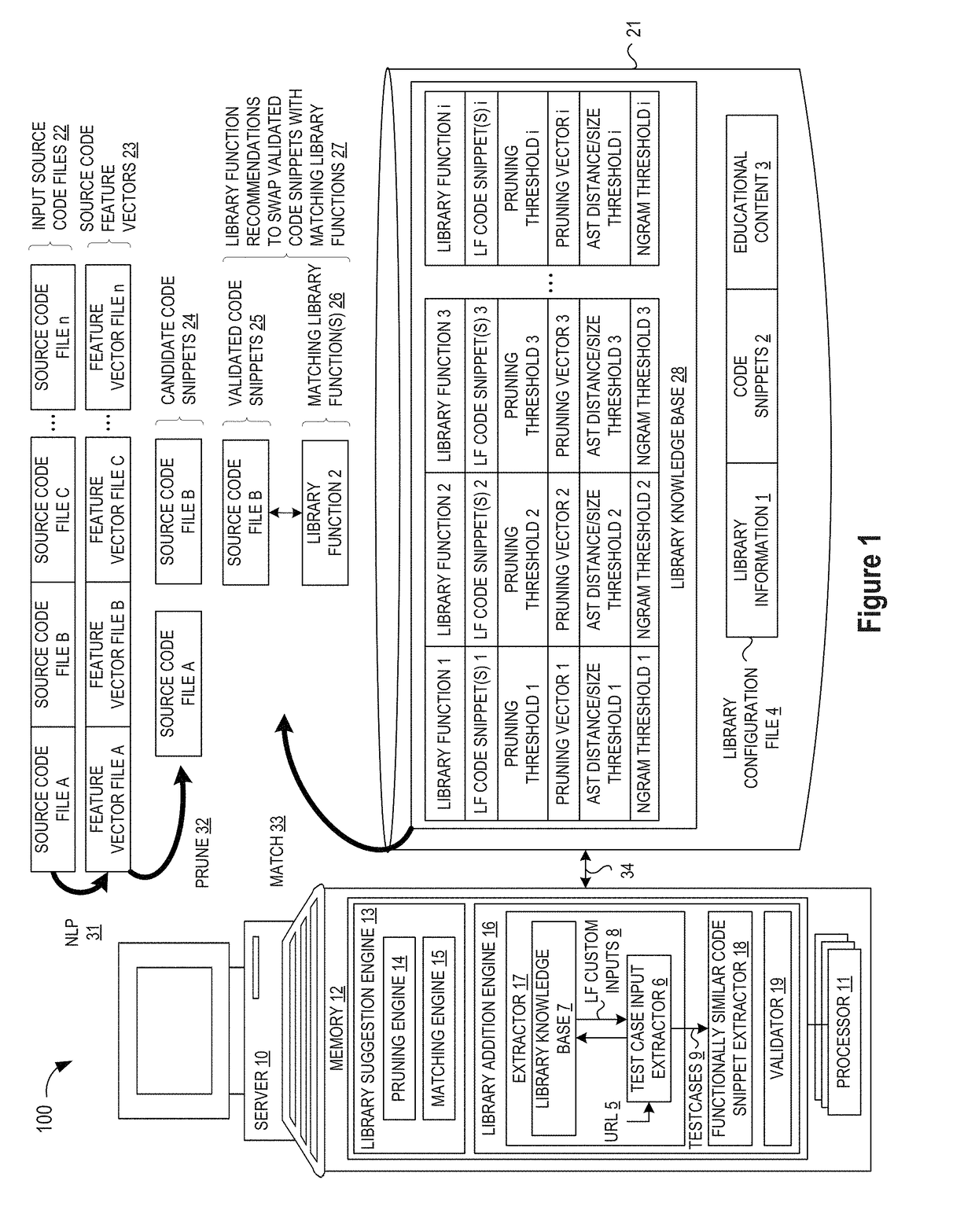
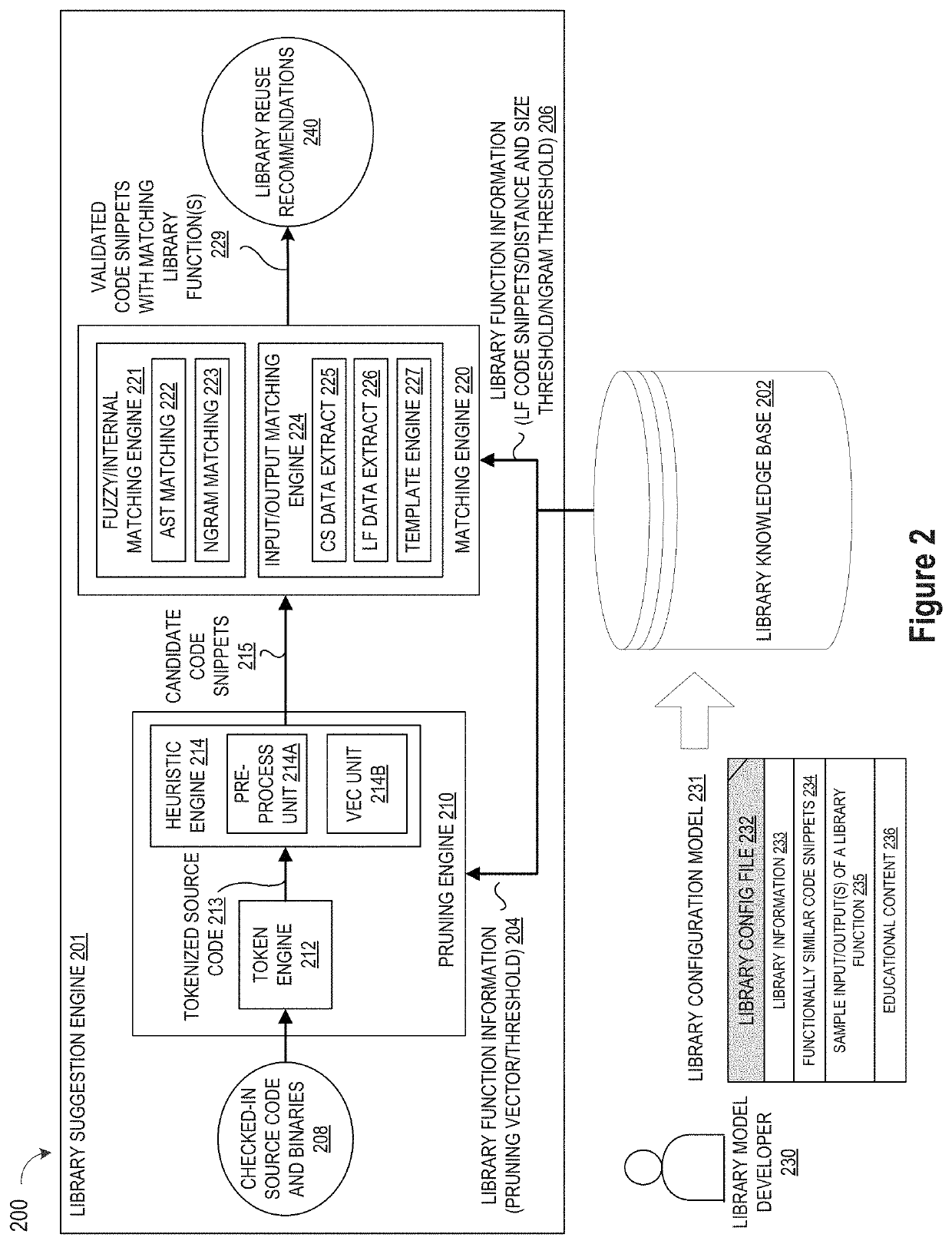
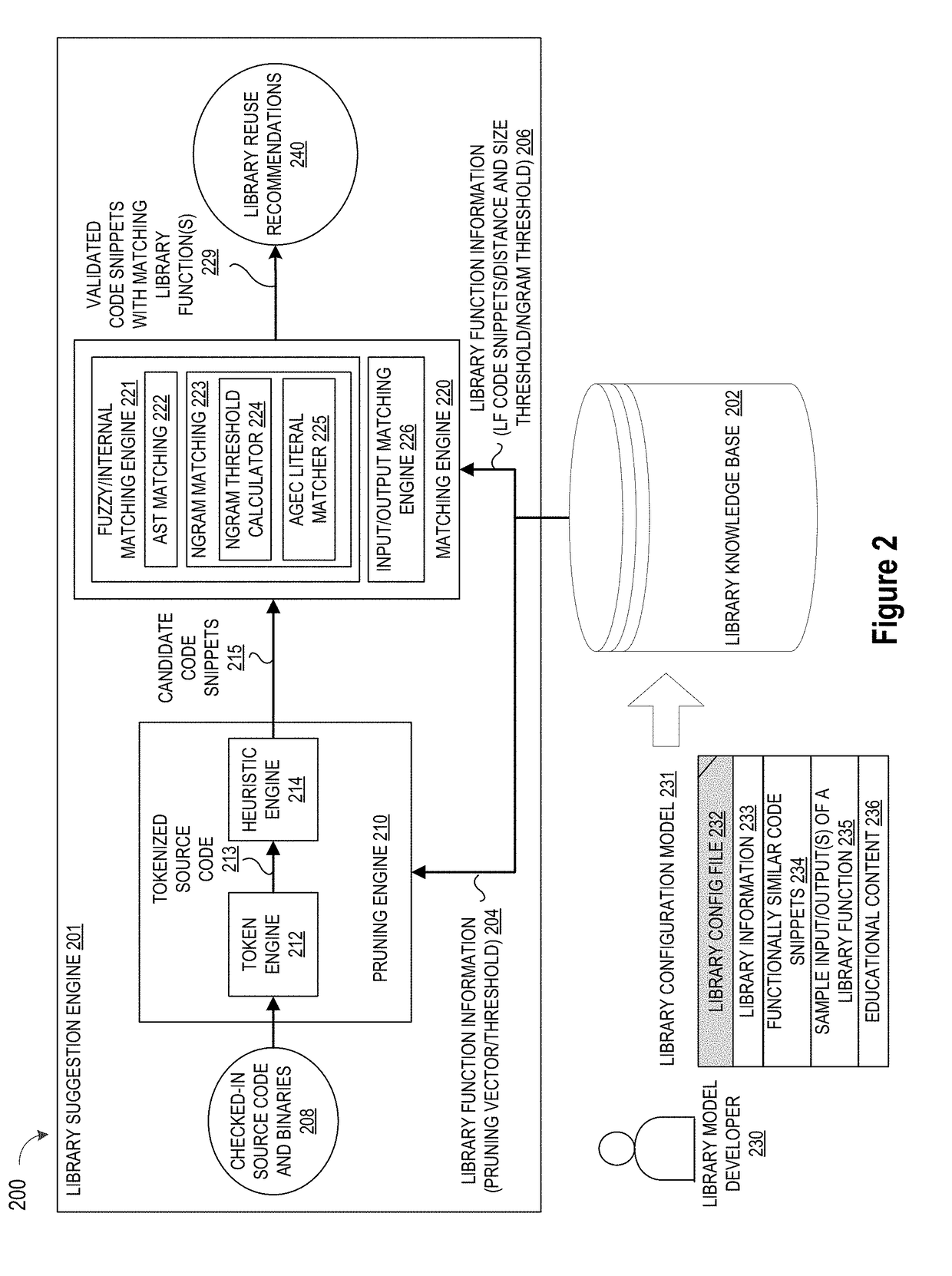
Automating Identification of Code Snippets for Library Suggestion Models
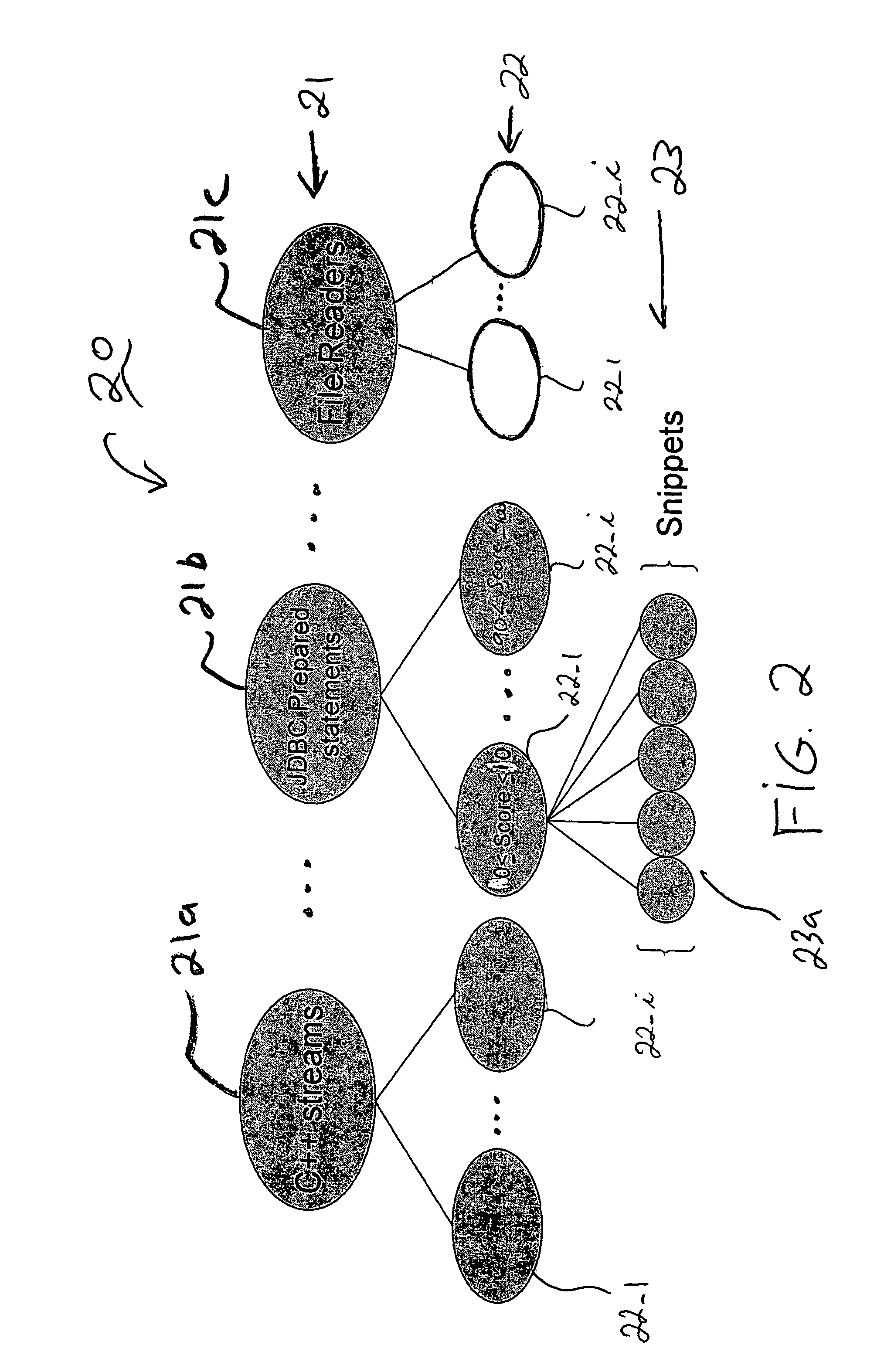
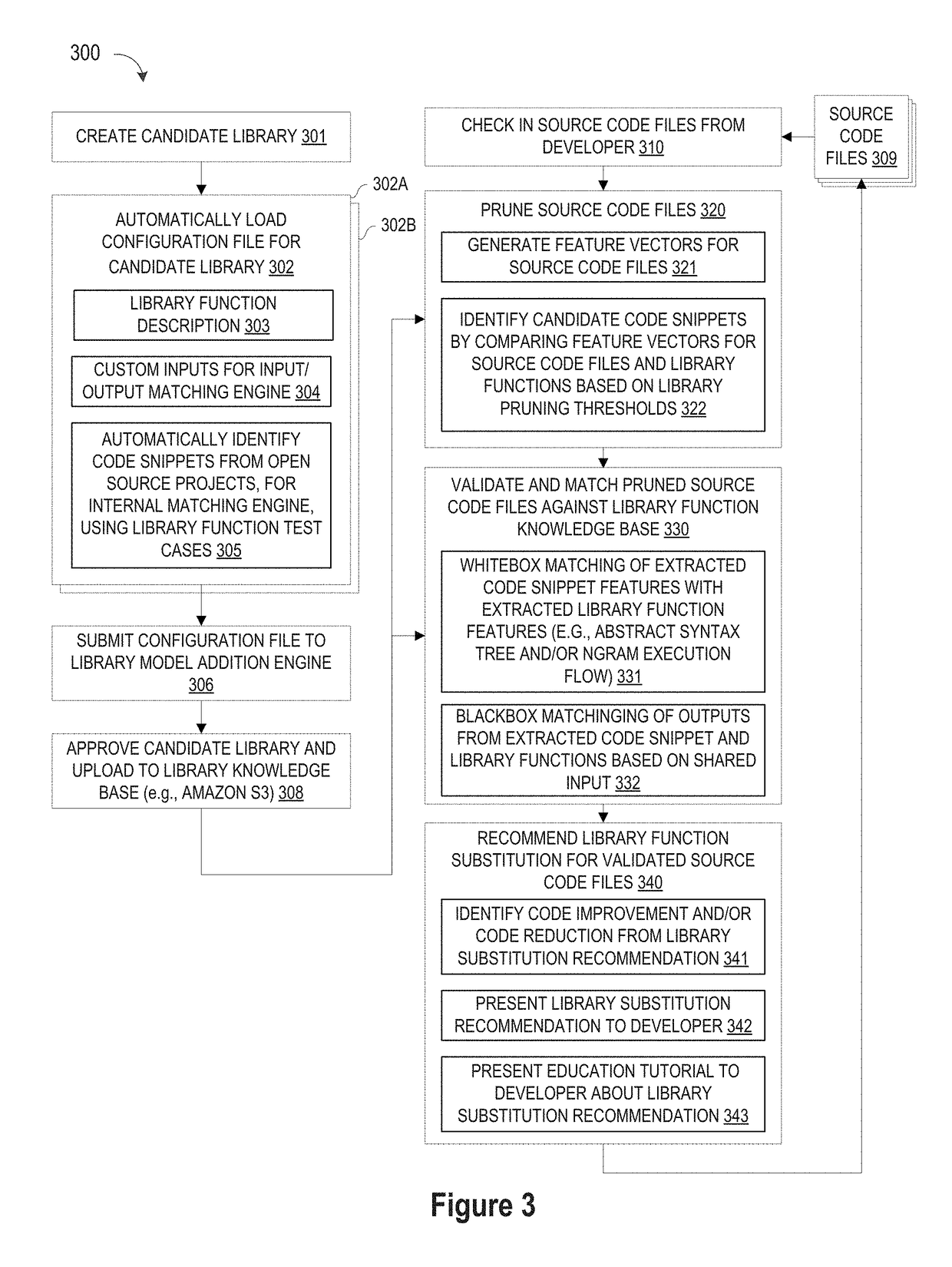
ActiveUS20190079754A1Improve code reuseImproving codebase maintainabilitySemantic analysisVersion controlCode snippetData field
A method, system, and apparatus are disclosed for adding library models to a library knowledge base by defining a template for a library configuration file that conveys information about each library model, custom inputs and code snippets to facilitate library comparison operations, and education content for the library model, where the library configuration file template may be automatically filled by populating selected data fields in the template with information identifying the library model and a set of custom inputs for the library model, and then passing a set of test cases from the set of custom inputs to an input / output matching engine to evaluate a repository of code snippets and identify a set of functionally similar code snippets for inclusion one or more data fields in the template.
Owner:DEVFACTORY INNOVATIONS FZ LLC
Method for detecting, removing and recovering malicious codes of Android repackaging malicious software
A method for detecting, removing and recovering malicious codes of Android repackaging malicious software comprises the steps as follows: a feature library consisting of fuzzy hash codes is established for malicious access point classes of known malicious programs and is used for being matched with access point classes of to-be-detected programs after disassembling; then complete malicious code snippets and malicious code resource files which are added through repackaging are sequentially removed; and finally, code snippets modifying source programs in a repackaging process are found out, and original functions of the code snippets are recovered. According to method, aiming at the main propagation characteristic that malicious code repackaging embedment of the malicious programs is more and more severe in current Android platform, the embedded malicious code parts in the normal programs are detected and removed.
Owner:SHANGHAI JIAO TONG UNIV
Method and apparatus for code virtualization and remote process call generation
ActiveUS20140372975A1Programming languages/paradigmsVisual/graphical programmingCode snippetUser device
A system and method for code virtualization and remote process call code on a user device. The method includes selecting a remote process on a remote server, the remote process correlated to at least one remote service, and receiving from at least one virtual code provider (VCP) on the remote server, a code snippet with parameters from pre-defined fields to call the remote process. The method installs a software development kit (SDK) downloaded from the remote server, onto the user device. The method inserts the code snippet based on the SDK into a local code base on the user device, and inserts parameter values into the code snippet and deploying the code snippet such that the code snippet calls the remote process with the SDK from the user device.
Owner:CIANMBELLA LTD
Programmatic compiler optimization of glacial constants
Optimizations are programmatically applied by a compiler (preferably, a just-in-time or “JIT” compiler), and enable achieving improved performance while a variable acts as a global constant, yet also allow code to execute correctly if the global constant's run-time value changes from the value on which the optimization was originally based. Code snippets that dynamically patch executable code are described, where these code snippets take corrective actions to enable correct program execution following a run-time change to the value of a glacial constant. A backup recovery path may also be maintained, where this path provides code that is executed in the event of a change to a glacial constant and that treats the glacial constant as a variable. Recompilation may also be used after a change to a glacial constant, where the originally-compiled code has made an assumption about the glacial constant's value that is no longer accurate. Combinations of these approaches may be used.
Owner:INT BUSINESS MASCH CORP
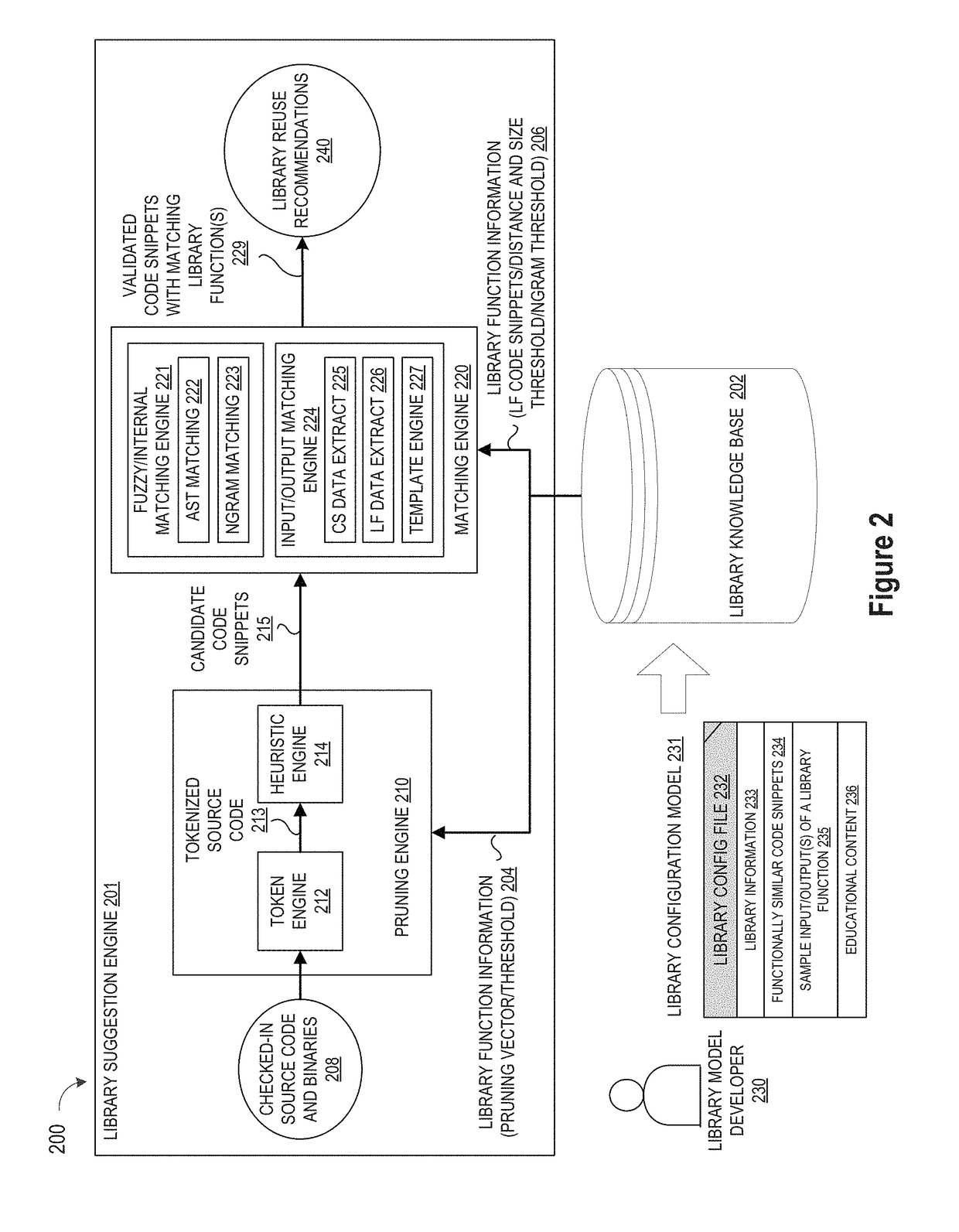
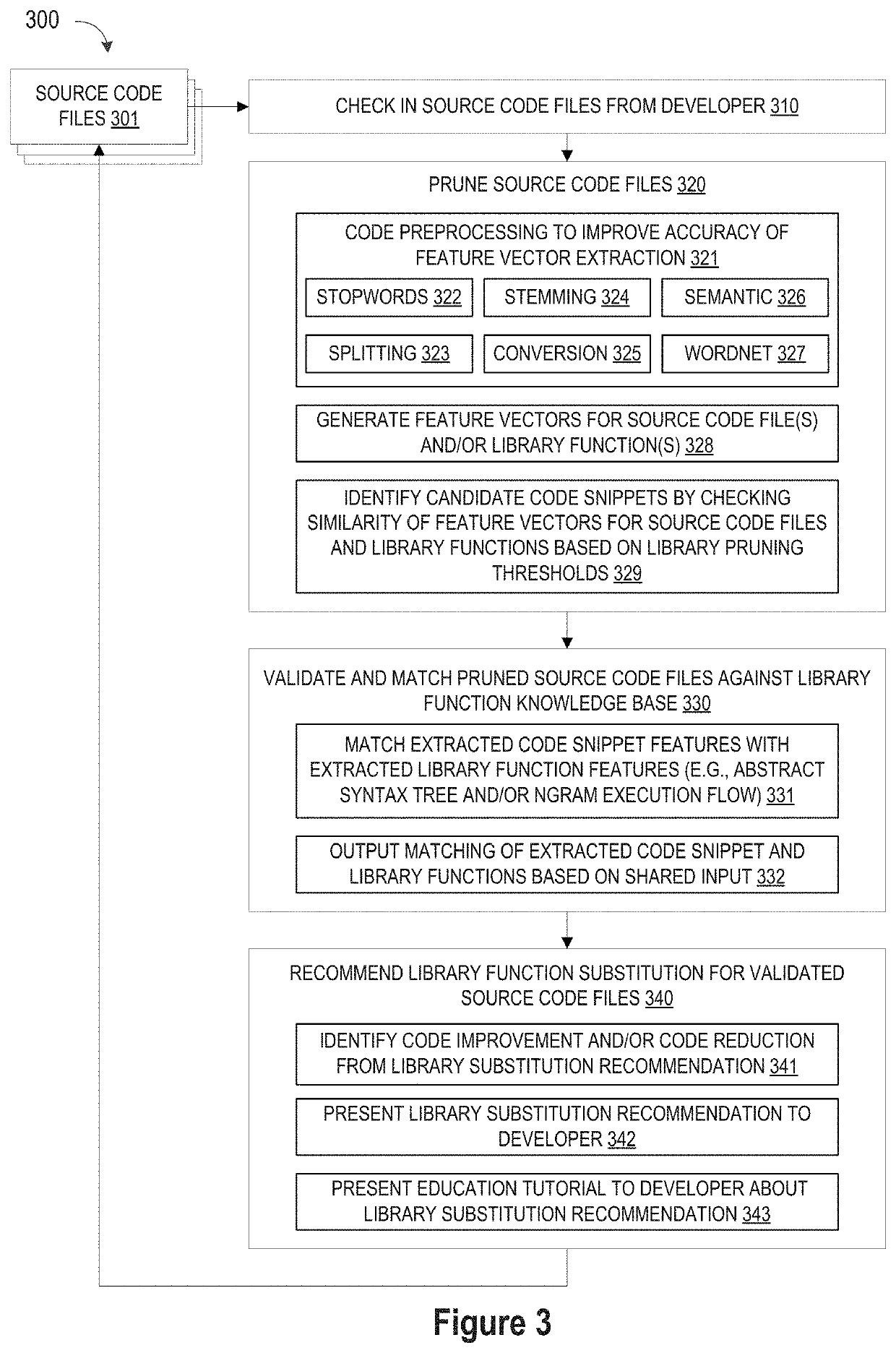
Library suggestion engine
ActiveUS10048945B1Improve code reuseImproving codebase maintainabilityIntelligent editorsSoftware reuseSource code fileCode snippet
A method and apparatus are disclosed for enhancing operable functionality of input source code files from a software program by identifying candidate code snippets from the plurality of input source code files that meet a similarity threshold measure for library functions stored in the system library and then identifying at least a first validated code snippet from the candidate code snippets that matches a first library function stored in the system memory on the basis of at least first and second matching metrics so that the developer is presented with a library function recommendation which includes the first validated code snippet, the first library function, and instructions for replacing the first validated code snippet with the first library function.
Owner:DEVFACTORY INNOVATIONS FZ LLC
Automating Identification of Test Cases for Library Suggestion Models
ActiveUS20190079853A1Improve code reuseImproving codebase maintainabilityVersion controlCode refactoringDocumentation procedureCode snippet
A method, system, and apparatus are disclosed for adding library models to a library knowledge base by defining a template for a library configuration file that conveys information about each library model, custom inputs and code snippets to facilitate library comparison operations, and education content for the library model, where the library configuration file template may be automatically filled by populating selected data fields in the template with information identifying the library model, scraping documentation pages to extract test cases, and then scraping test case code to extract the test case input parameters for input to an input / output matching engine to evaluate a repository of code snippets and identify a set of functionally similar code snippets for inclusion one or more data fields in the template.
Owner:DEVFACTORY INNOVATIONS FZ LLC
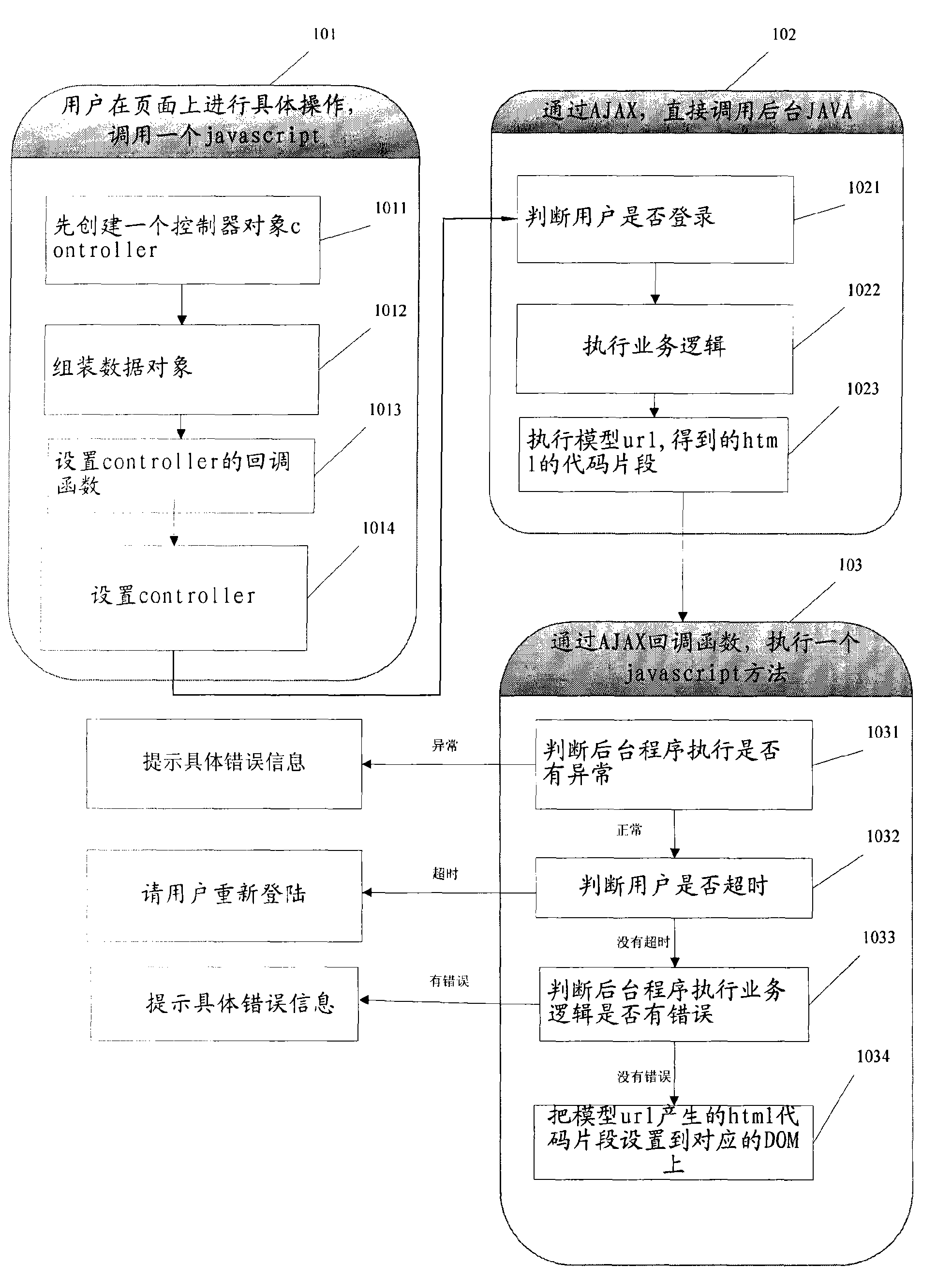
Method for realizing MVC
InactiveCN101587435AEasy to operateImprove development efficiencySpecific program execution arrangementsCode snippetDEVS
The invention provides a method used for realizing MVC by taking JavaScript as a controller. Models and view-interaction with a user are realized by HTML under JavaScript MVC. Models-realization of service logic in a system and generation of HTML code snippets are realized by JSP. The models mainly provide part of code snippets for the view but do not take charge of the arrangement of entire page display and the control of page switching. The controller, which is realized through JavaScript, is a bridge between the models and the view and determines which models are shown on the page. Through JavaScript MVC, the method ensures convenient operation of developers and increases the development efficiency to develop program quickly. Moreover, because JavaScript MVC is based on Ajax, local page refreshing is realized and friendlier interfaces can be provided for users to ensure excellent user experience.
Owner:BEIJING YIQI TELECOMM TECH
Pruning engine
A method and apparatus are disclosed for enhancing operable functionality of input source code files from a software program by preprocessing input source code files with codeword processing operations to generate a plurality of preprocessed input source code files, identifying candidate code snippets by pruning one or more preprocessed input source code files that do not meet a similarity threshold measure for library functions stored in the system library, and identifying at least a first validated code snippet from the one or more candidate code snippets that matches a first library function stored in the system memory on the basis of at least first and second matching metrics.
Owner:DEVFACTORY INNOVATIONS FZ LLC
Method and device for protecting JavaScript codes
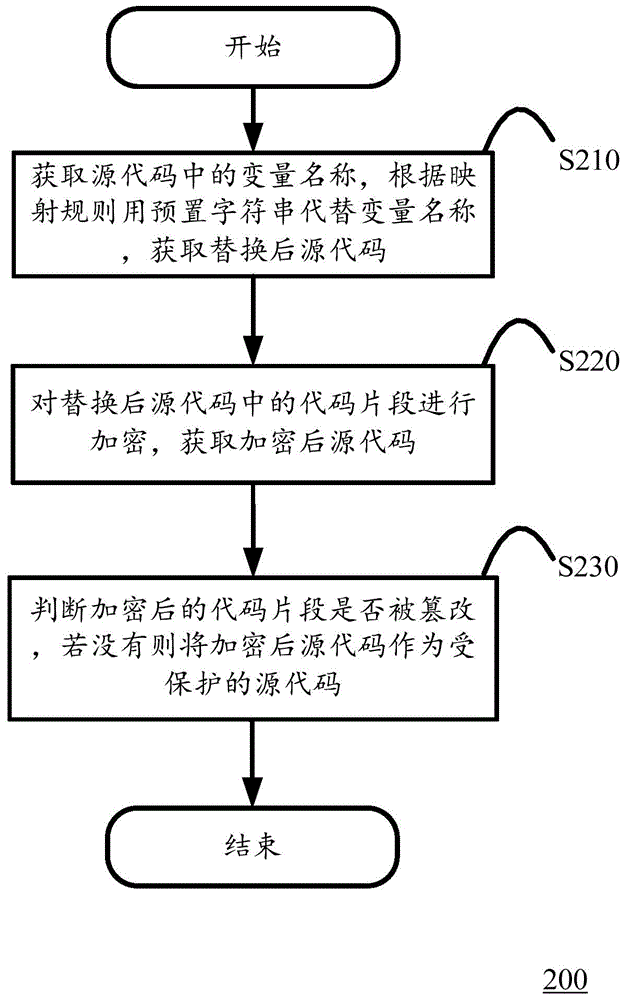
ActiveCN105205359AEffective protectionPrevent theftProgram/content distribution protectionComputer hardwareCode snippet
The invention discloses a method for protecting JavaScript codes. The method includes the steps that variable names in source codes are acquired, the variable names are replaced with preset character strings according to a mapping rule, and then the source codes obtained after replacement are acquired; code snippets in the source codes obtained after replacement are encrypted, and the encrypted source codes are acquired; whether the encrypted code snippets are tampered or not is judged, and if not, the encrypted source codes serve as protected source codes.
Owner:XIAMEN FEIXIN NETWORK TECH CO LTD
Highly accurate code snippet recommendation method
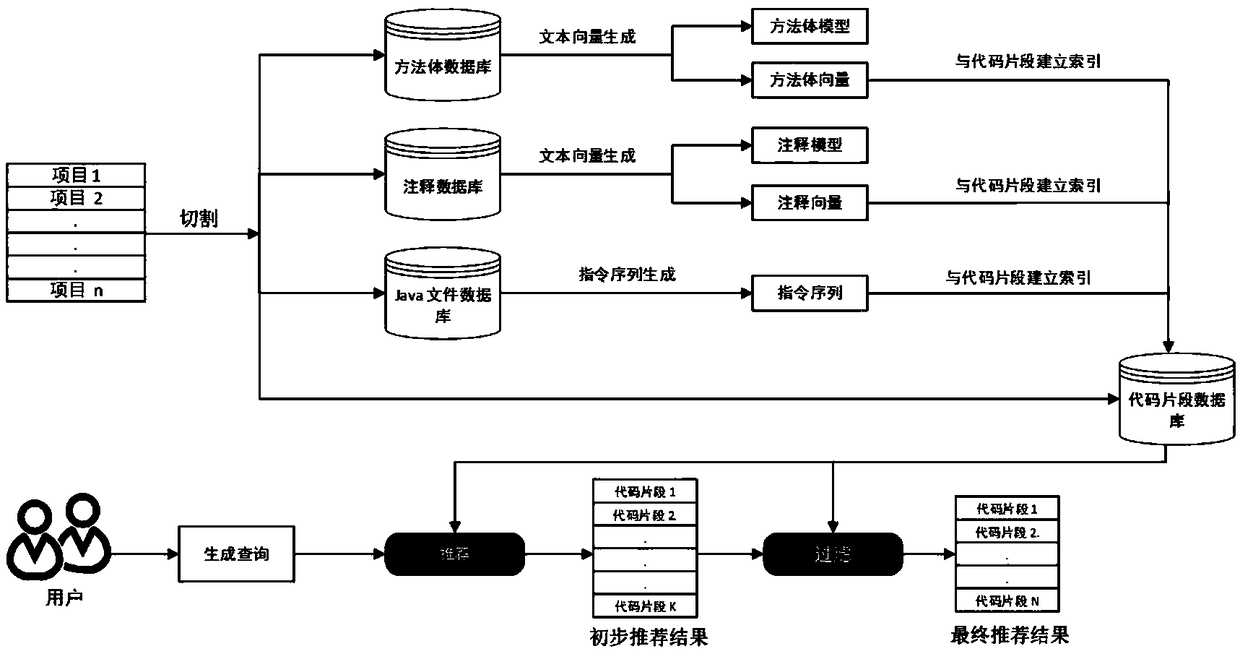
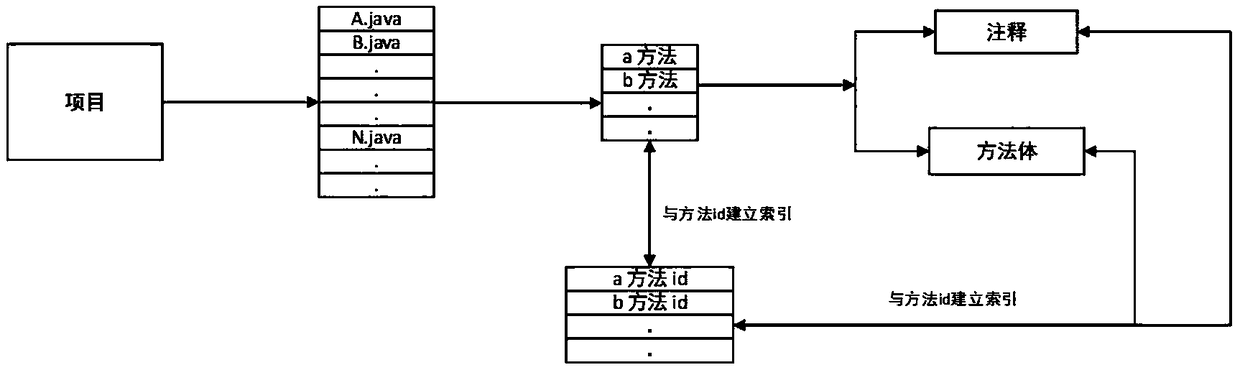
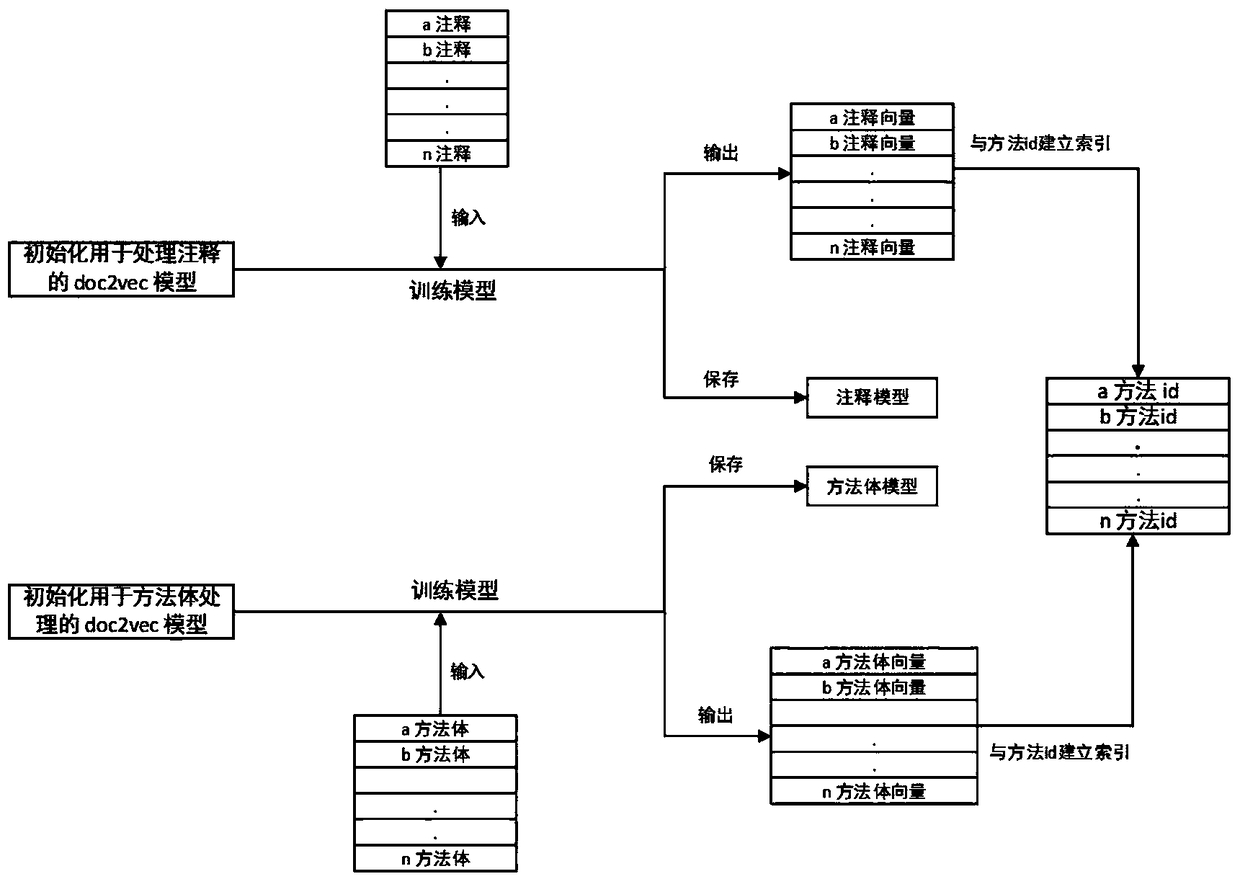
ActiveCN108717470AImprove recommendation accuracyRecommended results are accurateSemantic analysisSpecial data processing applicationsCode snippetUser input
The invention provides a highly accurate code snippet recommendation method. The method comprises the steps of splitting and dividing a project, and generating class files, a code snippet , a code snippet method body and a code snippet note; generating a code snippet method body vector and a code snippet note vector based on the code snippet method body and the code snippet note; compiling and decompiling each class file, and extracting an instruction sequence of the code snippet from the decompiled file; generating an inquiry vector based on an inquiry input by a user, and screening out a group of primary recommendation results with highest text similarity according to a text similarity of the inquiry vector and a code snippet text characteristic; and according to statement similarity ofall code snippet s in the primary recommendation results, screening the primary recommendation results for the second time and then re-ranking so as to form a final recommendation result. The method overcomes the defect that the existing method is low in recommendation accuracy due to unique use characteristic and failure in filtering of recommendation results. The method is applicable to the field of recommendation of open source code snippets.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Code recommendation
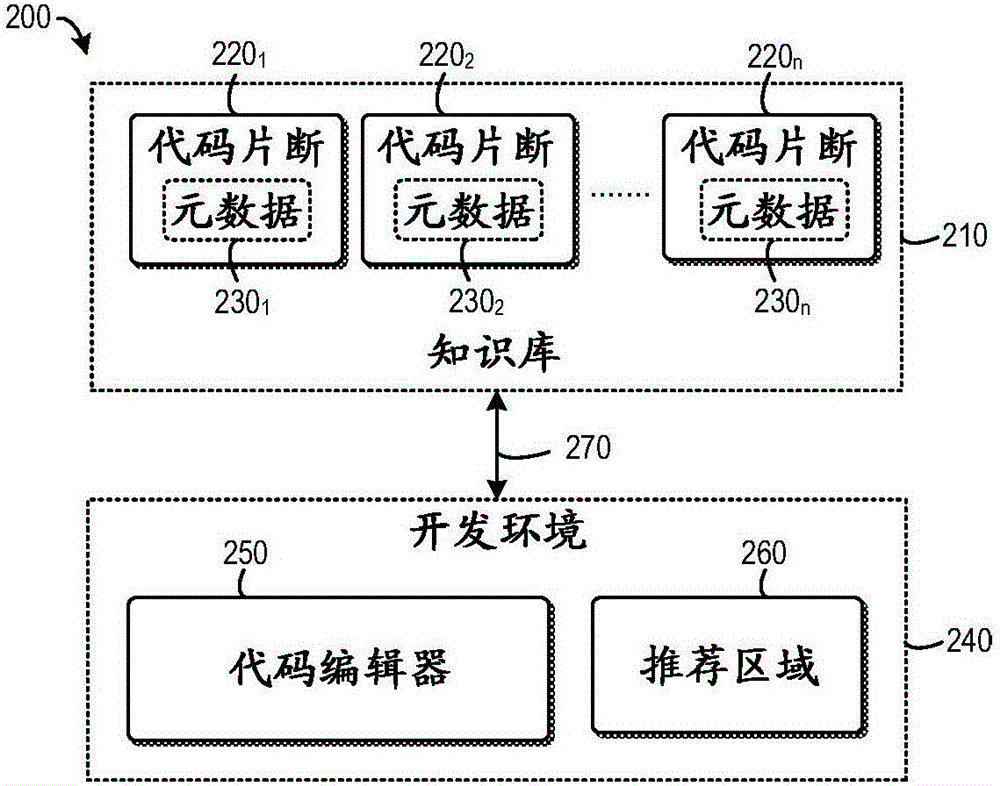
ActiveCN106462399AQuality improvementImprove friendlinessIntelligent editorsSoftware designCode snippetUser friendliness
A method generally relates to code recommendation. In the method, code snippets (220 1, 220 2, ...220 n) may be extracted using an invocation-centered code slicing process and then grouped according to the method usages. For each method usage, a representative code snippet may be selected and stored in the knowledge base (210) in association with metadata (230 1, 230 2, ...230 n). The programming context may be obtained and used to query the knowledge base (210) to retrieve one or more code snippets for recommendation. The recommended code snippets may be ranked to improve the utility and user friendliness, and the metadata (230 1, 230 2,...230 n) may be used to provide variation points and possibly other auxiliary information to improve the operation efficiency and user experience.
Owner:MICROSOFT TECH LICENSING LLC
Identification of concepts in software
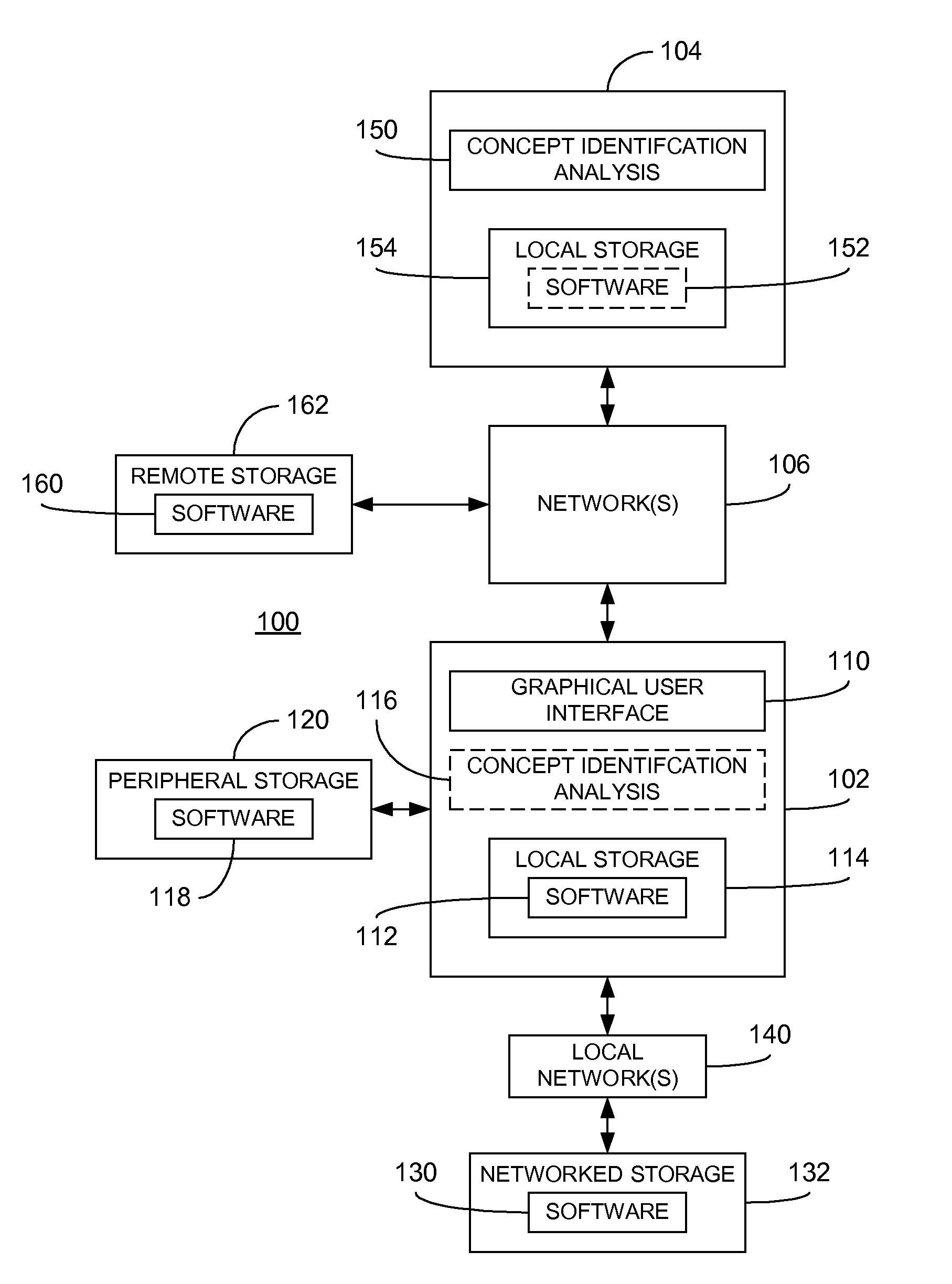
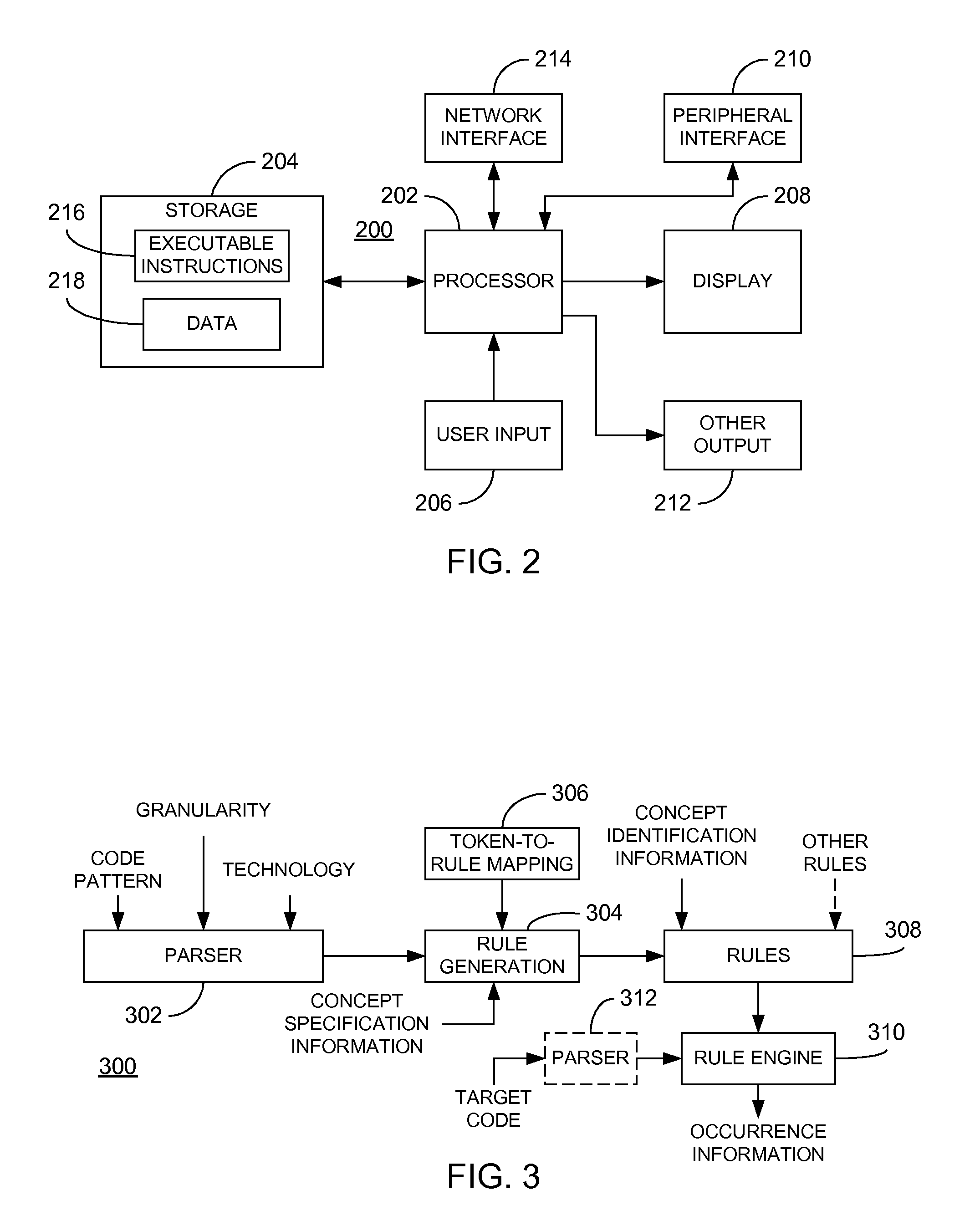
ActiveUS20100077351A1Facilitating great sharingEasy to analyzeError detection/correctionProgram documentationAbstract designSchema for Object-Oriented XML
Techniques enabling an end-user to specify complex concepts consisting of code abstractions, design abstractions and architectural abstractions in rule form are disclosed. In one embodiment, a graphical user interface is provided to guide a user through the process of entering concept specification information in order to define concepts, including the provision of one or more code snippets that are subsequently analyzed to assist the user in specifying the concept. The resulting rules or concept signatures are evaluated by a rule engine to determine the degree to which the underlying concepts are reflected in a given set of code. Recommended measures that need to be taken for transforming code to satisfy a concept may be provided subsequent to the analysis of the code. In this manner, code quality may be improved through systematic analysis of targeted code to demonstrate adherence (or non-adherence, as the case may be) to user-defined concepts.
Owner:ACCENTURE GLOBAL SERVICES LTD
Method and System for Arbitrary-Granularity Execution Clone Detection
ActiveUS20180349105A1Improve code reuseReducing false positiveIntelligent editorsSoftware reuseCode snippetSource code file
A method and apparatus are disclosed for enhancing operable functionality of input source code files from a software program by identifying a first code snippet and a first library function which have similar execution flow similarity measures by evaluating a first contiguous sequence of n items extracted from the first code snippet against a second contiguous sequence of n items extracted from the first library function using an Ngram threshold that is calculated for the first library function and one or more literals from the first code snippet so that the developer is presented with a library function recommendation which includes the first code snippet, the first library function, and instructions for replacing the first code snippet with the first library function.
Owner:DEVFACTORY INNOVATIONS FZ LLC
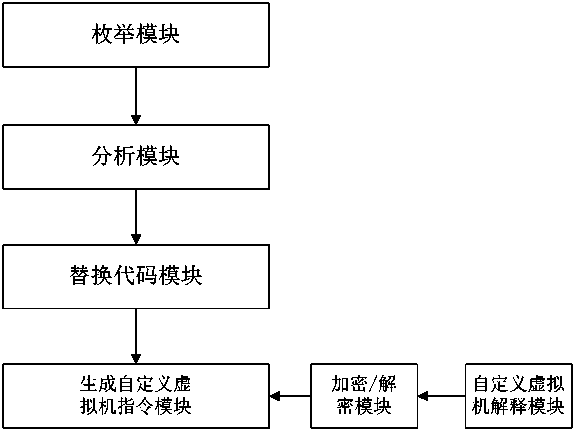
Method and device for protecting JAVA executable program through virtual machine
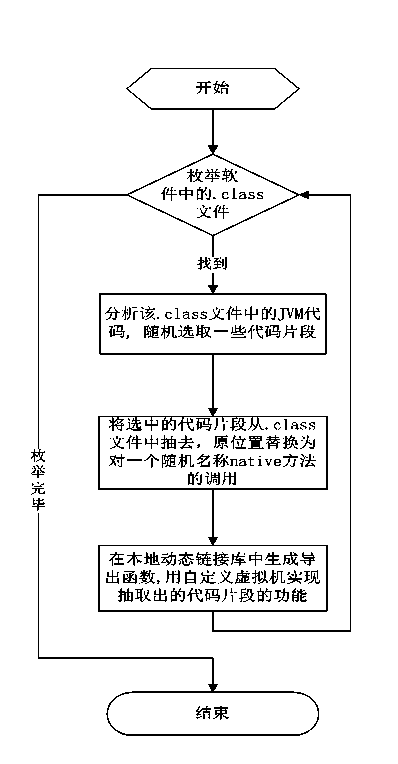
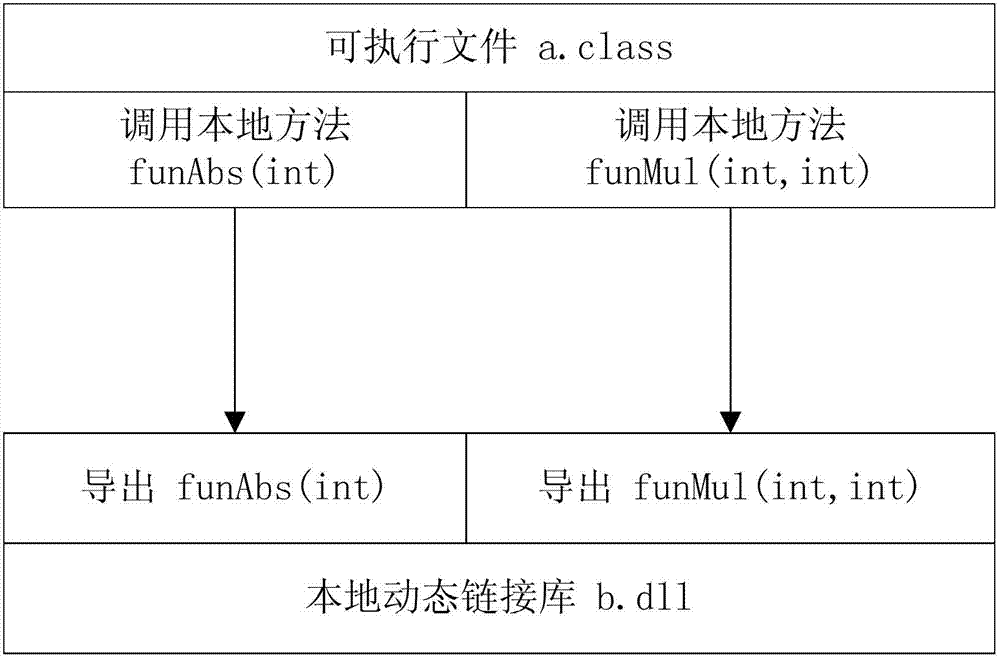
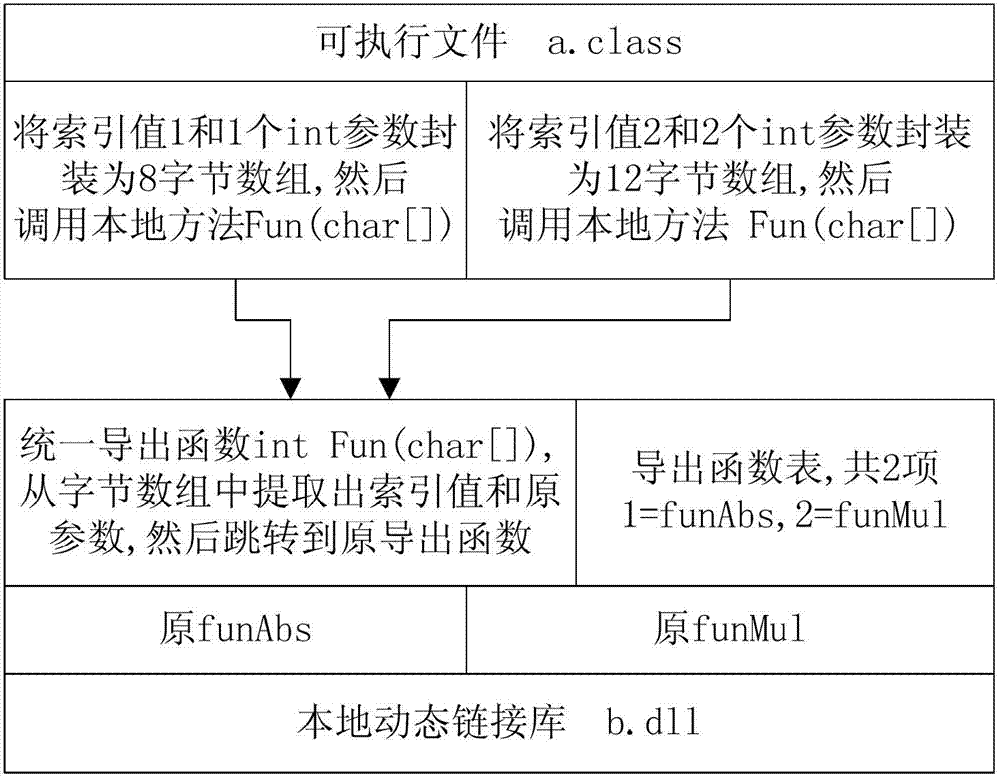
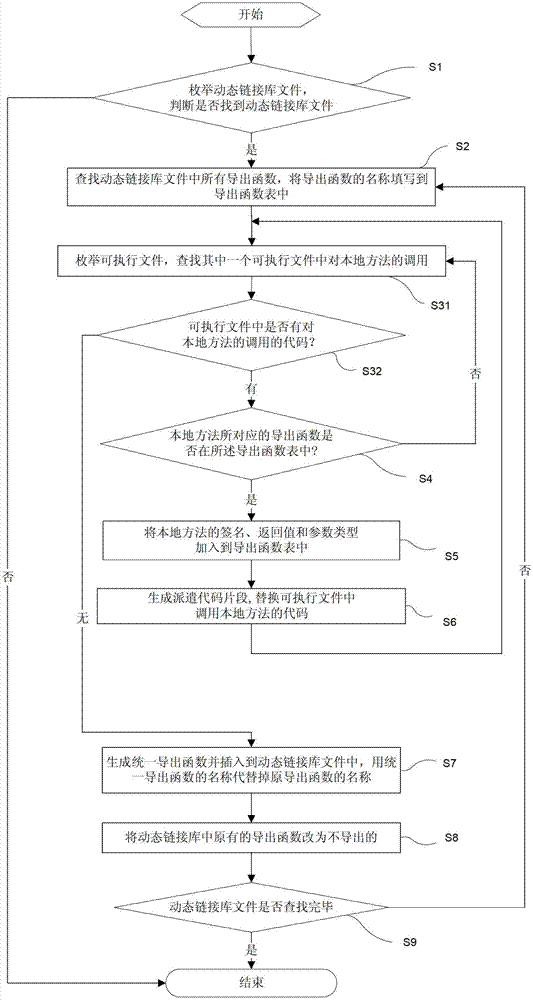
ActiveCN103413075AProtection logicProtection processProgram/content distribution protectionCode snippetContrarian
The invention discloses a method and device for protecting a JAVA executable program through a virtual machine. The method comprises the step of creating a local dynamic link library file, the step of enumerating a .class file in protected JAVA software, the step of analyzing a JVM code in the .class file, the step of drawing a code snippet at random, the step of replacing a home position with the calling to a native method, the step of generating a derived function in the local dynamic link library file, and the step of achieving the function of drawing the code snippet by using the user-defined virtual machine. By means of the method, codes and logic of the JAVA software can be effectively prevented from being reversed and decoded, and the safety intensity of the software is improved.
Owner:BEIJING SENSESHIELD TECH
Detection method and system of Internet information system malicious codes
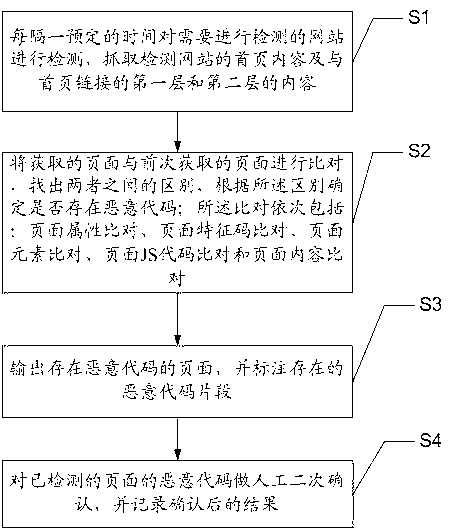
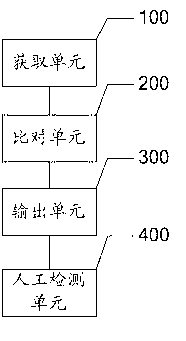
ActiveCN103279710APerfect content detection completenessImprove accuracyPlatform integrity maintainanceWeb siteCode snippet
The invention discloses a detection method and system of Internet information system malicious codes. According to the method, detection is carried out on a website needed to be detected every scheduled time, contents of a home page and contents of a first layer and a second layer which are linked with the home page of the detected website are grasped; an obtained page is compared with a page obtained earlier to find out the difference between the two pages, and whether the malicious codes exist or not is determined according to the difference; then the page where the malicious codes exist is outputted, and existing malicious code snippets are labeled; at last, manual secondary identification is carried out on the malicious codes of the detected page, and a result after identification is recorded. Therefore, multiple detection of the contents of the page is achieved, omnibearing step-by-step multistage content detection is supported, the integrity of the content detection is perfected, and detection accuracy is improved; detection performance, detection efficiency and requirements for software and hardware environments are improved.
Owner:深圳市易聆科网络安全有限公司
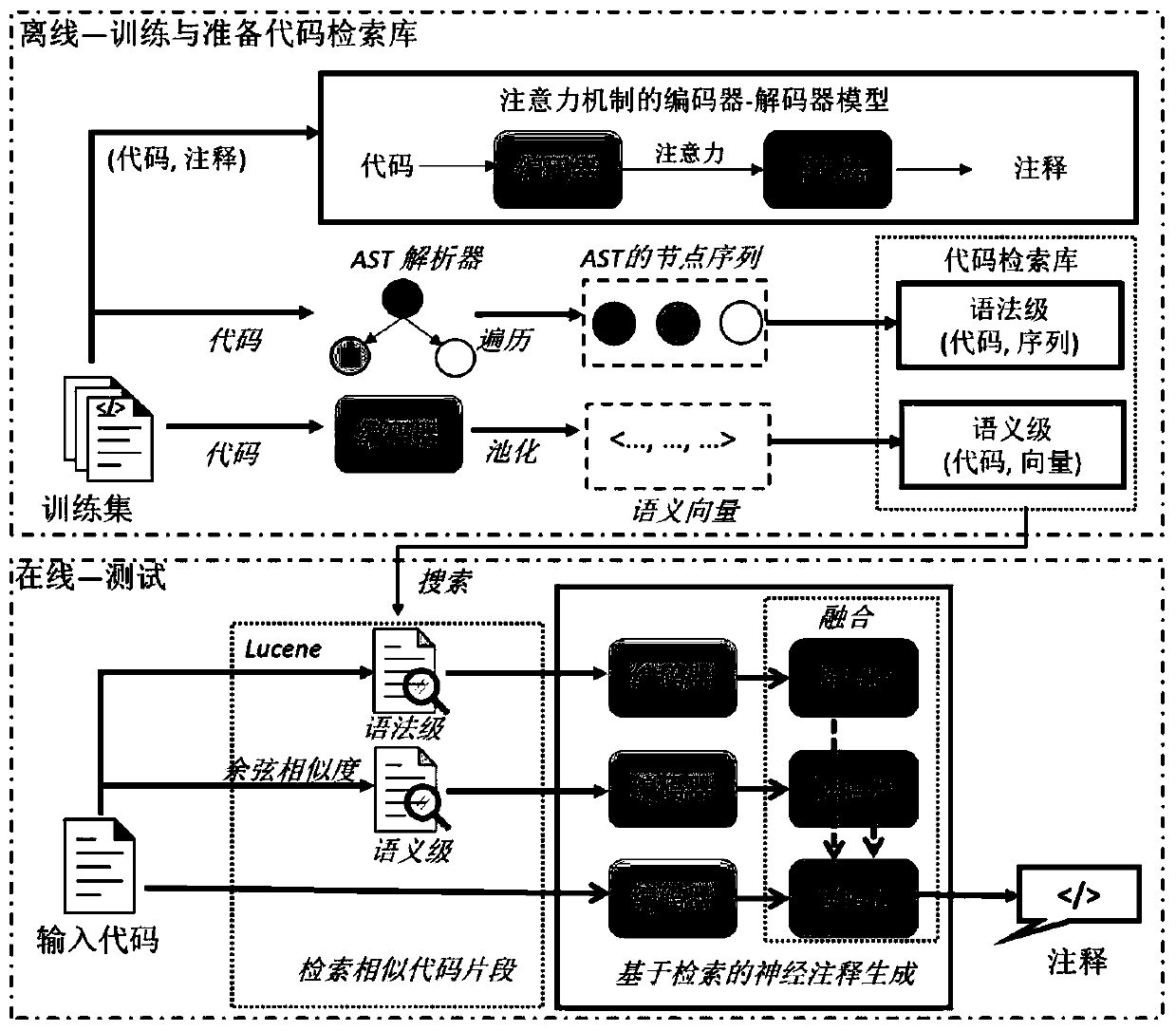
Source code annotation automatic generation method
The invention provides a source code annotation automatic generation method. The method comprises an offline stage and a testing stage. In the offline stage, firstly, training corpora are collected totrain an encoder-decoder model of an attention mechanism. Then, the codes of the training corpora are used for constructing a code retrieval library. The training corpora comprise source code fragments and corresponding annotations. In the line testing stage, for the input code snippets, two existing code snippets are searched with similar grammar levels and semantic levels in the code retrievallibrary, and then annotations corresponding to the input code snippets are generated by taking the two similar existing code snippets and the input code snippets as inputs of a neural annotation generation module based on retrieval.
Owner:BEIHANG UNIV
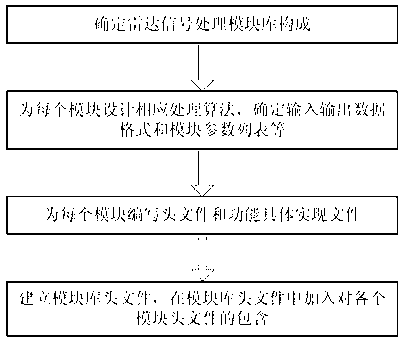
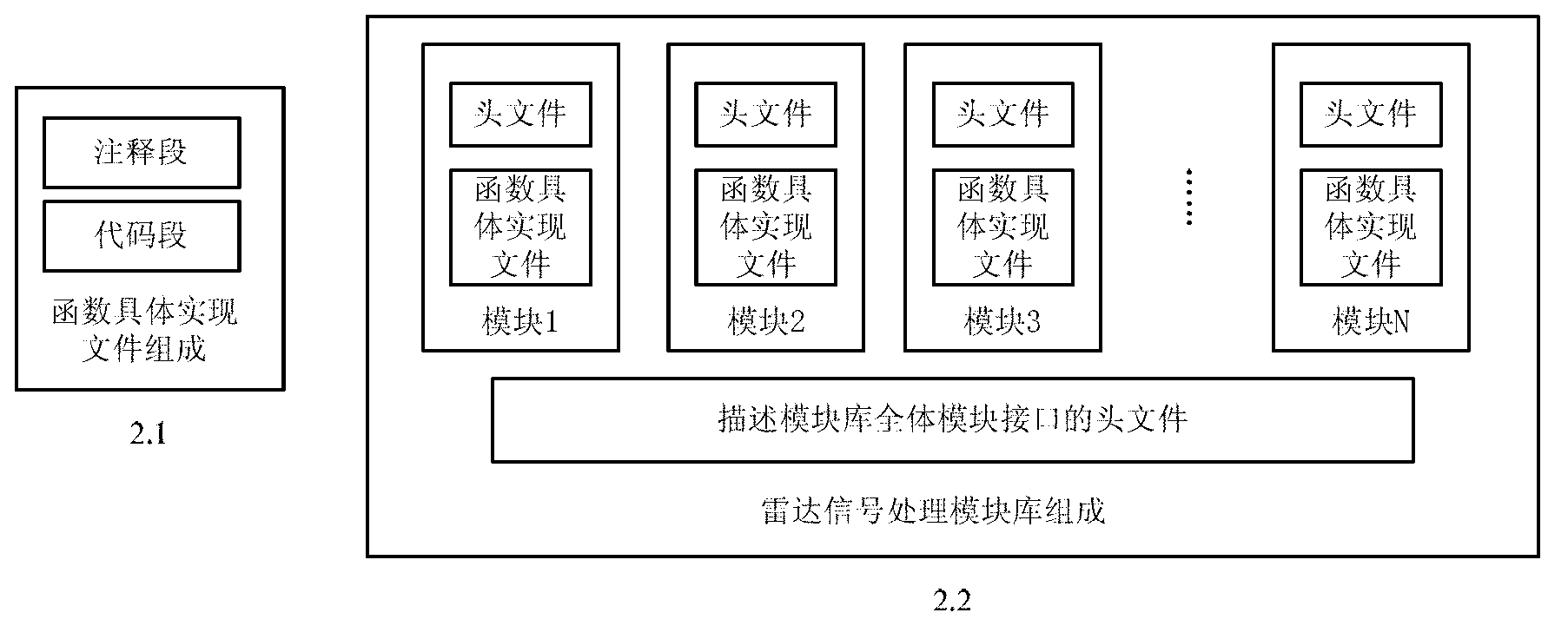
Computing middleware-based radar signal processing module library construction method and application thereof
ActiveCN103019744ACreate a processImprove development efficiencySpecific program execution arrangementsSystems designRadar signal processing
A computing middleware-based radar signal processing module library construction method and application thereof belong to constitution of a software radar signal processing system design. The method is characterized in that the module library comprises a fine-grained basic arithmetic library and a coarse-grained complex radar signal processing algorithm; each module includes a function concrete realization file and a header file corresponding to the file; the entire established module library is described by a separate header file; and the function concrete realization file contains two parts, namely a note segment and a code snippet. According to the invention, modular and universal radar signal processing algorithm can be realized, better compatibility of a third-party module library is taken, radar signal processing task realization modes can be flexibly selected, and the development efficiency of the radar signal processing system is improved at the same time.
Owner:TSINGHUA UNIV
Software security protection method and equipment
ActiveCN103246848AImprove decompilationIncrease the difficulty of debuggingPlatform integrity maintainanceLocal methodCode snippet
The invention discloses a software security protection method. The method includes the steps of searching for all export functions in dynamic link library files in software and establishing a table of export functions; checking whether names of the corresponding called export functions exist in the table of export functions or not; if yes, storing related parameters of a local method into the table of export functions; if not calling the local method, actuating a replacement step; adapting, namely generating dispatch code snippets and replacing codes, which call the local method, in executable files; and replacing, namely generating a unified export function and replacing the names of all export functions with the name of the unified export function, wherein the unified export function is used for jumping to an original export function. By the software security protection method and system, only the unified export function is exposed from an interface of the software, and the software is more difficult to decompile and debug and is safer.
Owner:BEIJING SENSESHIELD TECH
Automated tagging and tracking of defect codes based on customer problem management record
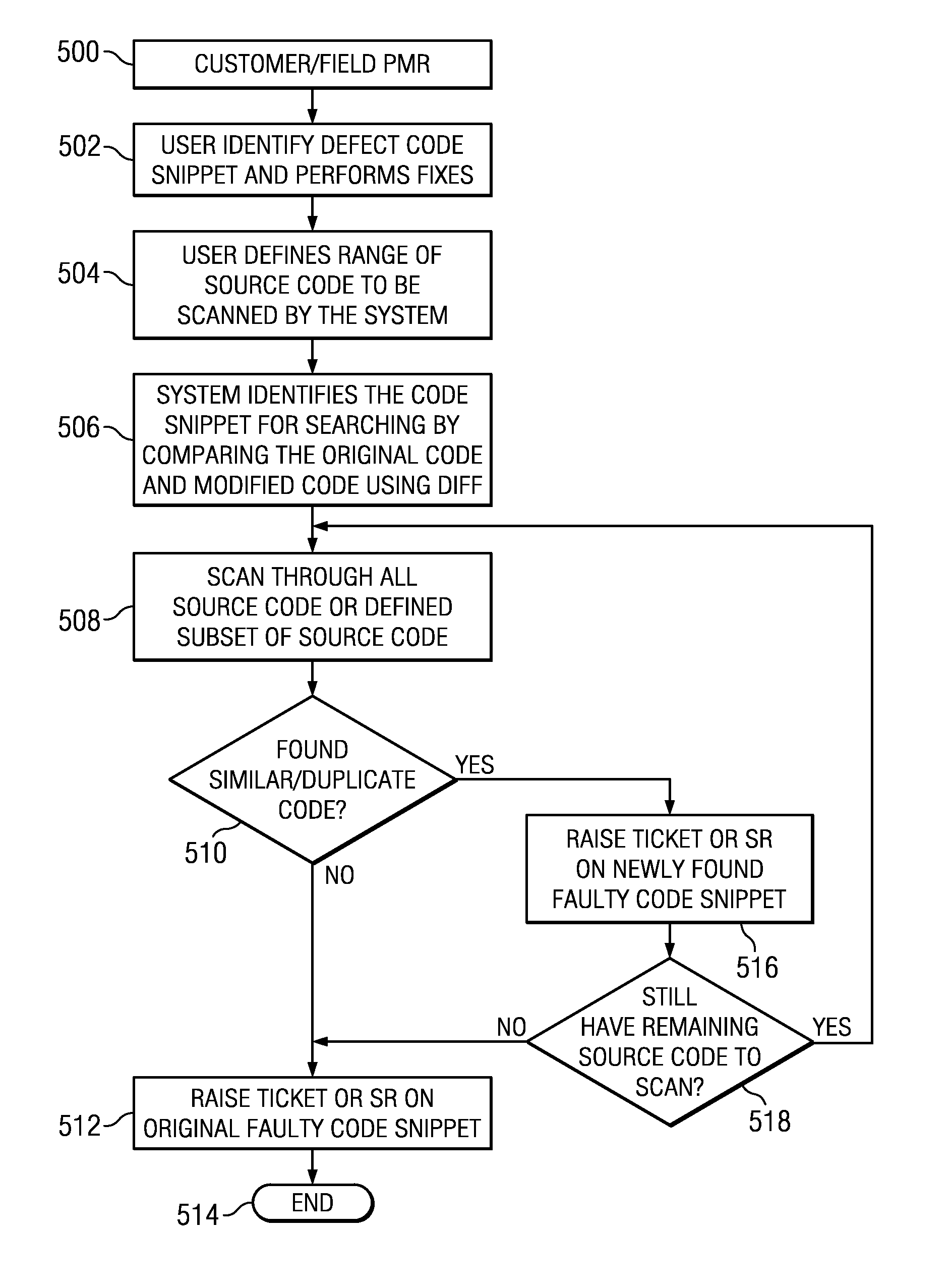
ActiveUS20130311975A1Facilitate software defect trackingEasy to correctVersion controlSoftware testing/debuggingProblem managementCode snippet
A routine for tagging and tracking source code may be implemented in a software development environment. The routine begins upon the identification of a defect in a software product or system. Once the defect has been identified and rectified, a search of other source code (typically located in a source code management system that supports version control) is specified. Using the search specification, the system automatically identifies the code snippet to be searched and begins searching the identified codebase for duplicates. A ticket or service record is then created for every duplicate / similar code snippet found during the search. The ticket / record enables software defect tracking to be carried out on the newly-located instances of the code. The system also automatically manages the code snippets identified by the duplicate detection.
Owner:IBM CORP
Method and apparatus for defining and instrumenting reusable java server page code snippets for website testing and production
InactiveUS7475388B2Error detection/correctionSpecific program execution arrangementsWeb siteCode snippet
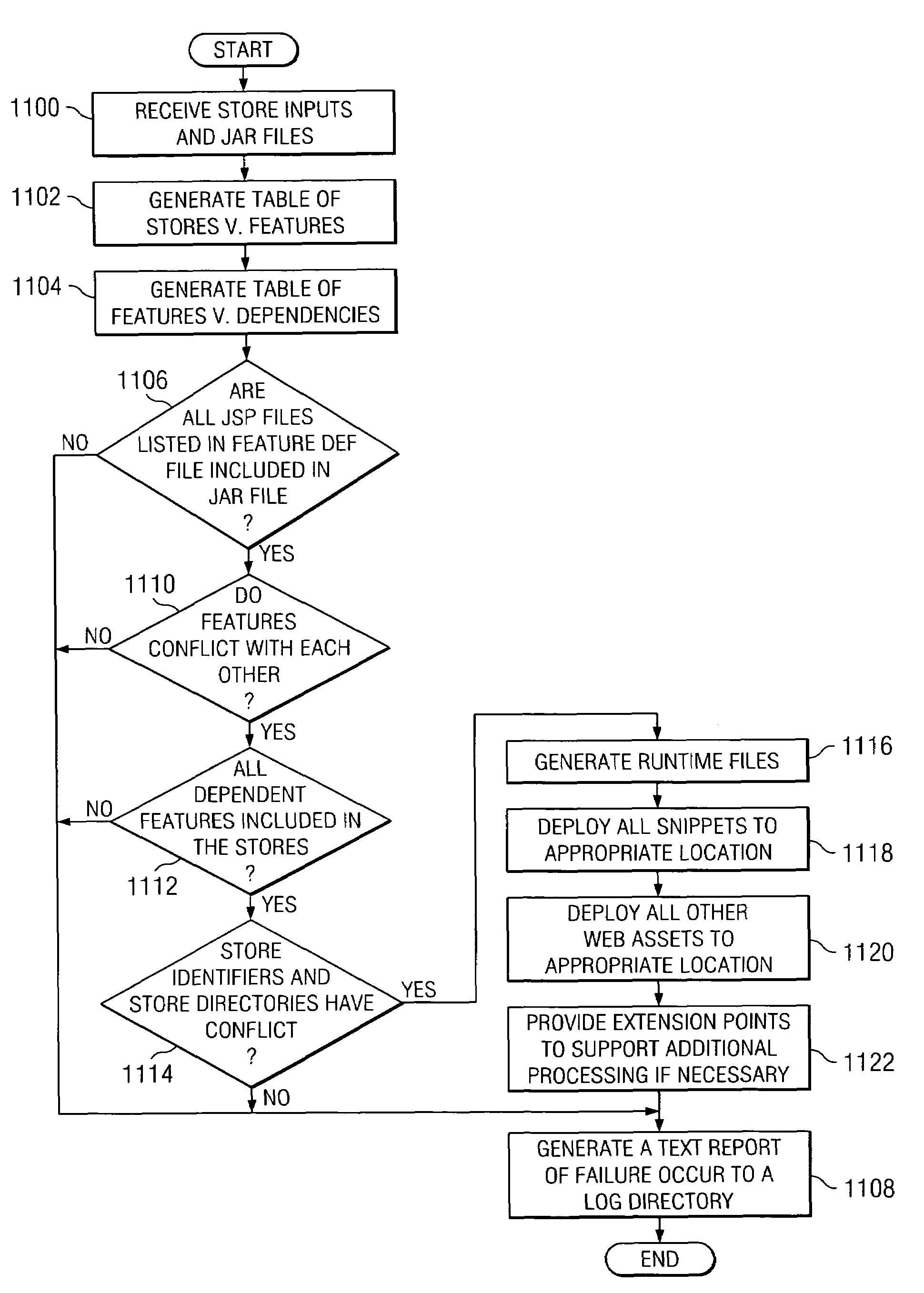
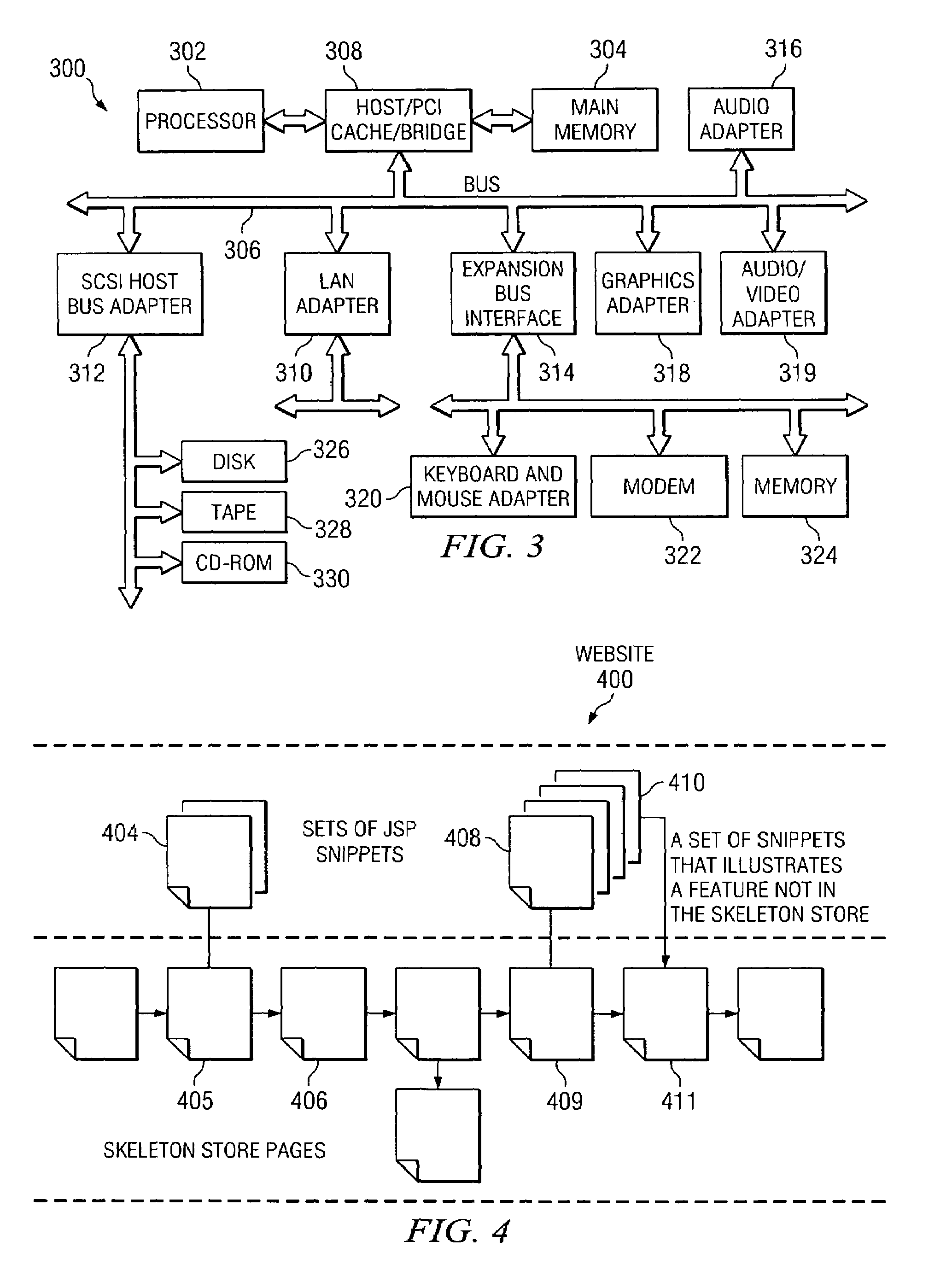
Reusable JSP code snippets are defined and instrumented for Website testing and production. A user may define tile definitions in a markup language file for a number of JSP code snippets to be included in a store page. Upon receiving store inputs comprising tile definitions and jar files for the features, tables may be generated that map features to stores and features dependencies to features. Based on the tables, the store inputs may be validated. If no error occurs, run time files may be generated and JSP code snippets may be instrumented to the appropriate location for Website testing and production.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com