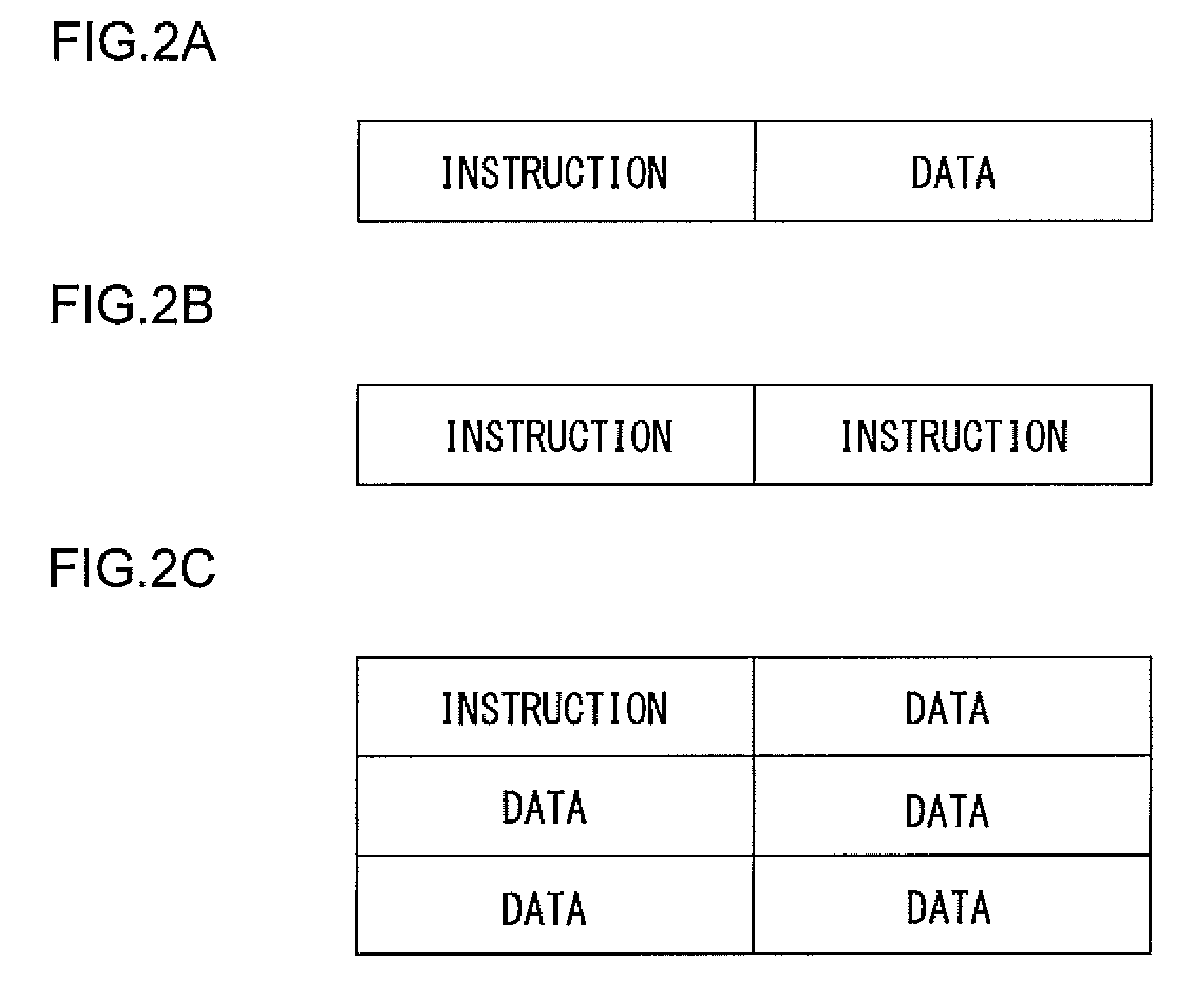
Patents
Literature
356 results about "Library function" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Each public library functions to serve its community in different ways, but its core functions are: To make available all of the information, entertainment (within limits), and resources possible to every patron, regardless of age, financial status, or any other factors. To provide a quiet, safe place for study, research, reading, and learning.
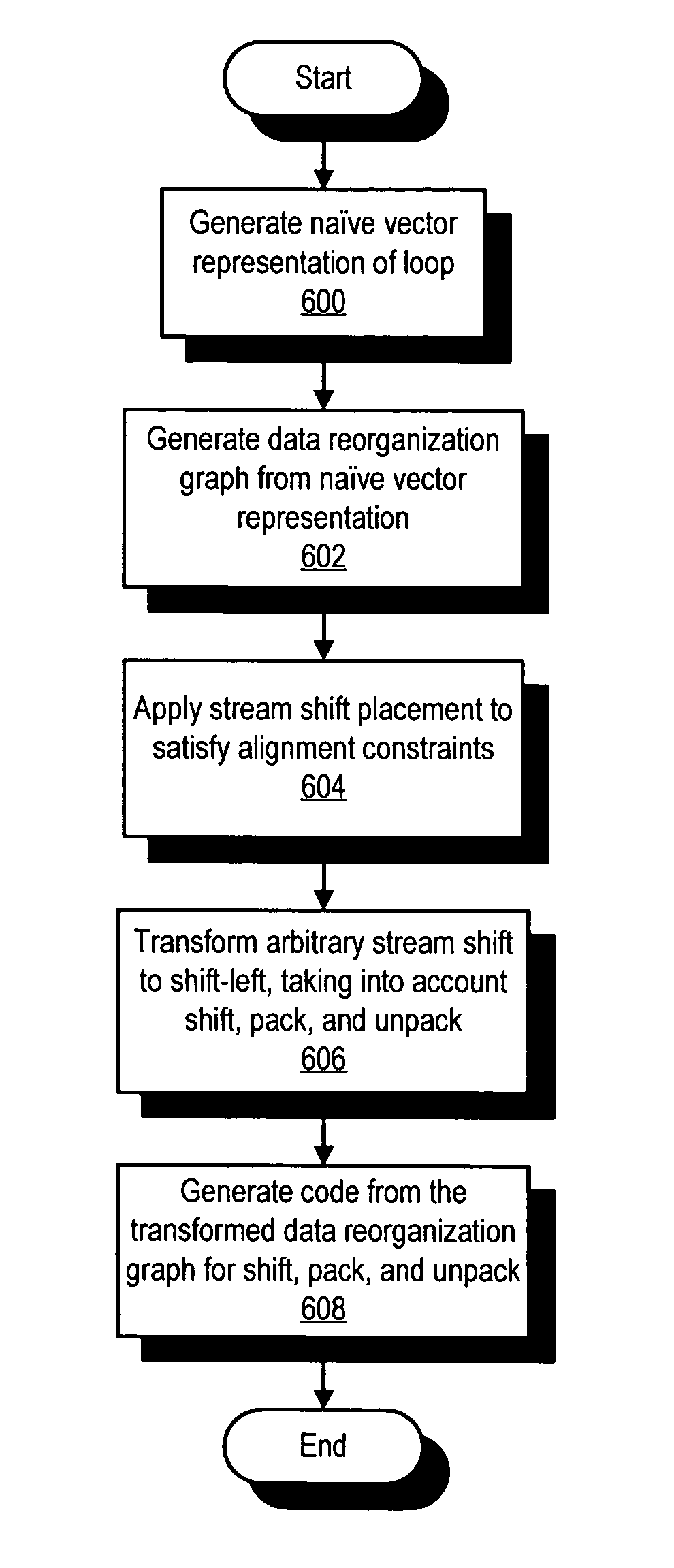
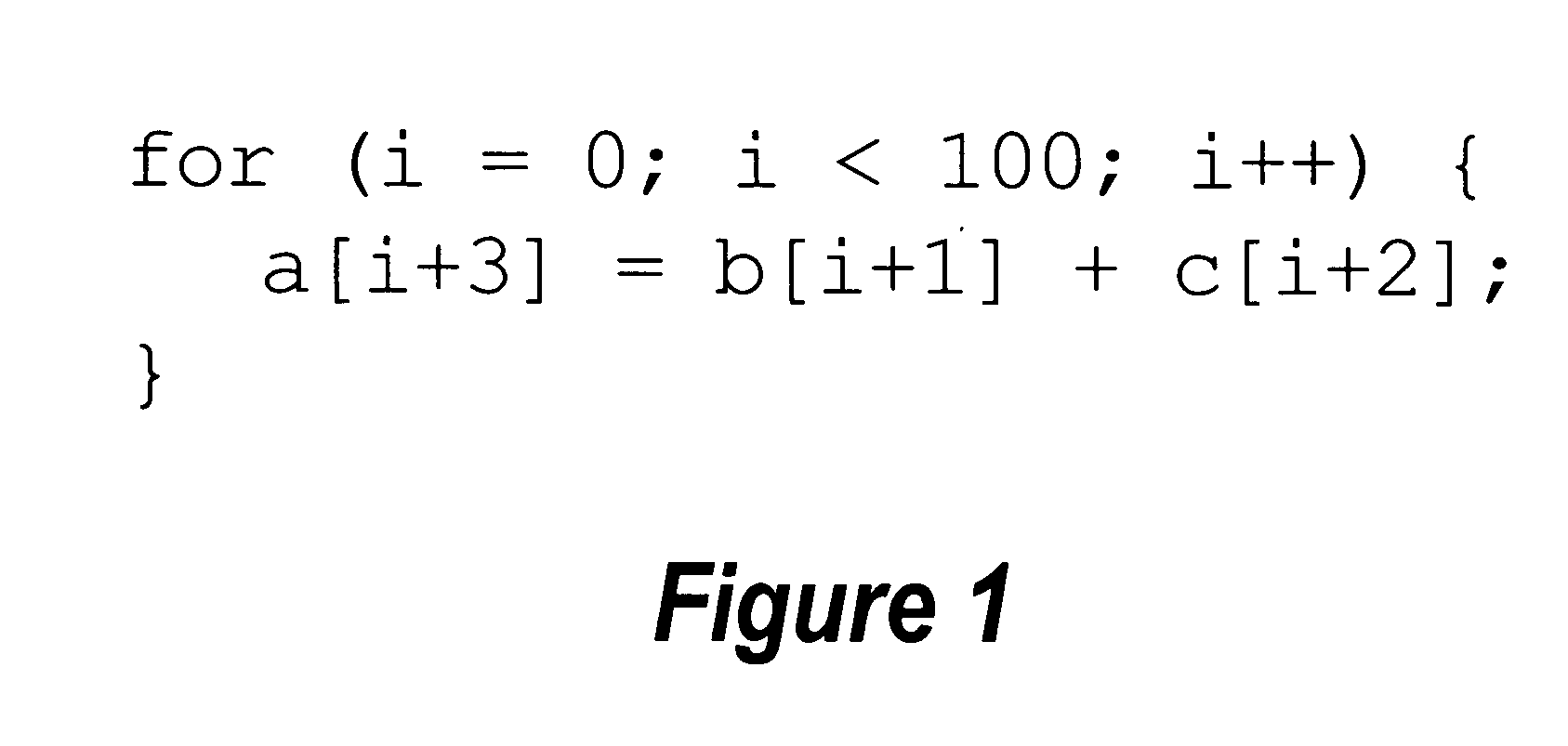
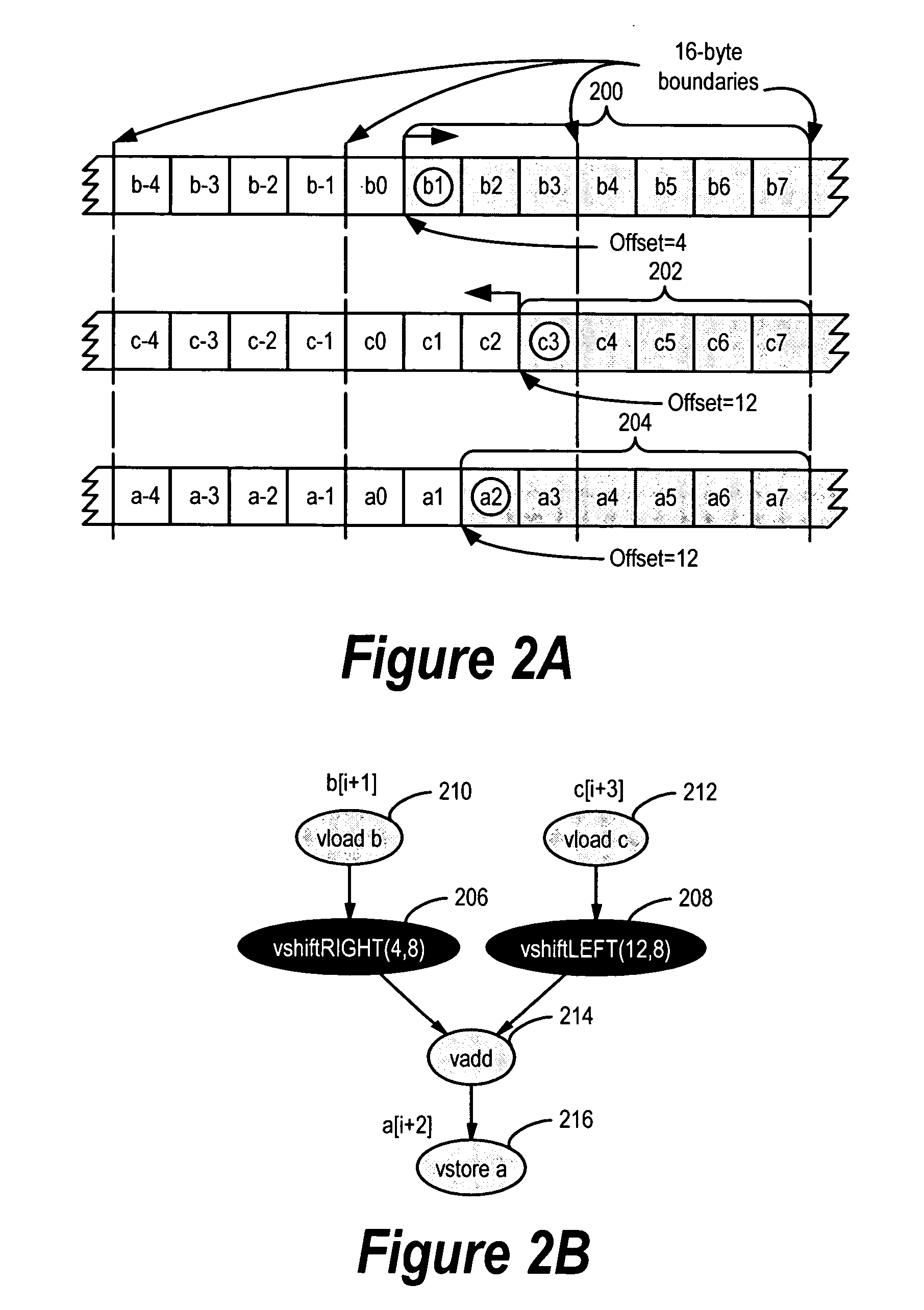
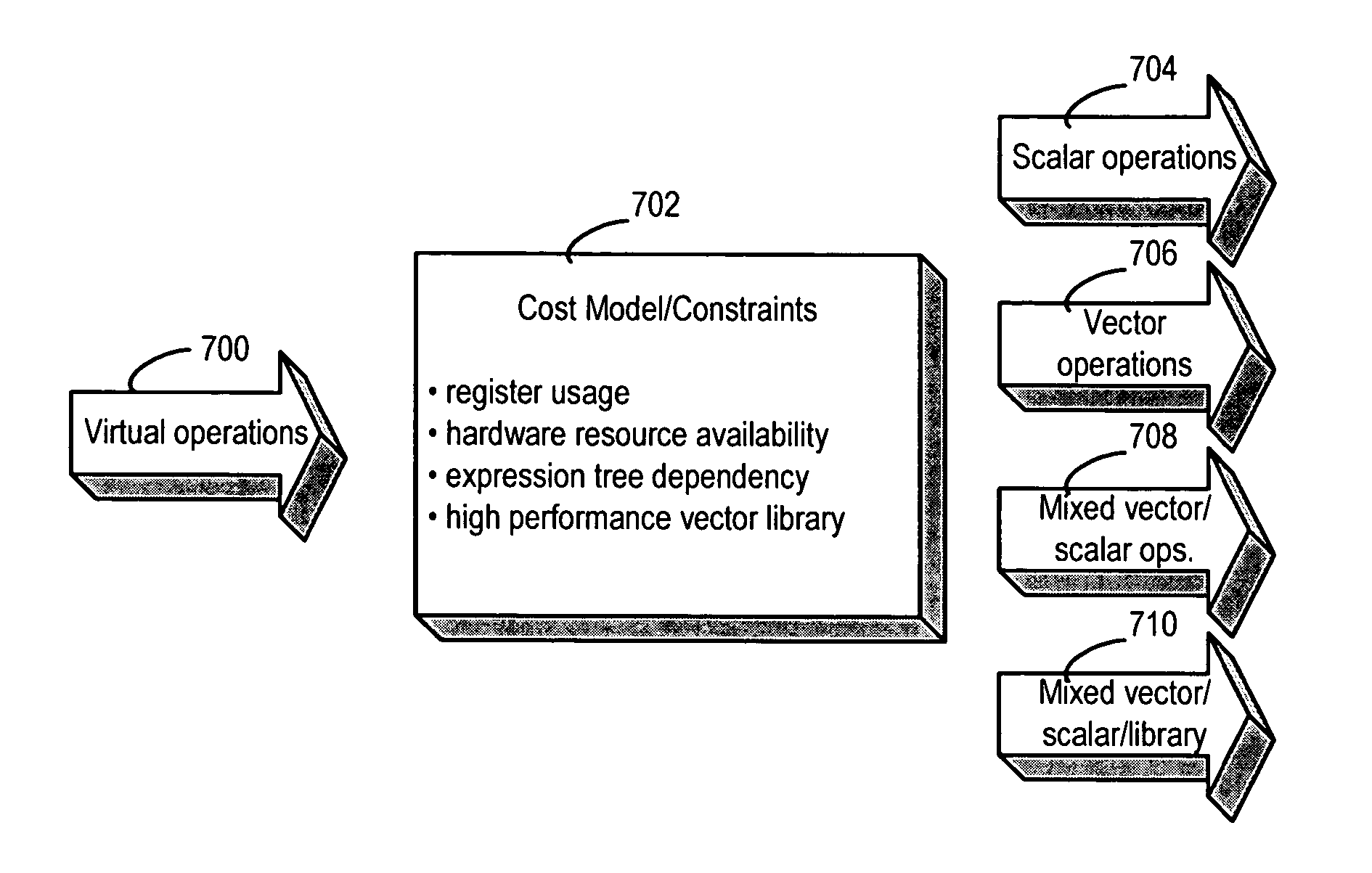
Framework for generating mixed-mode operations in loop-level simdization
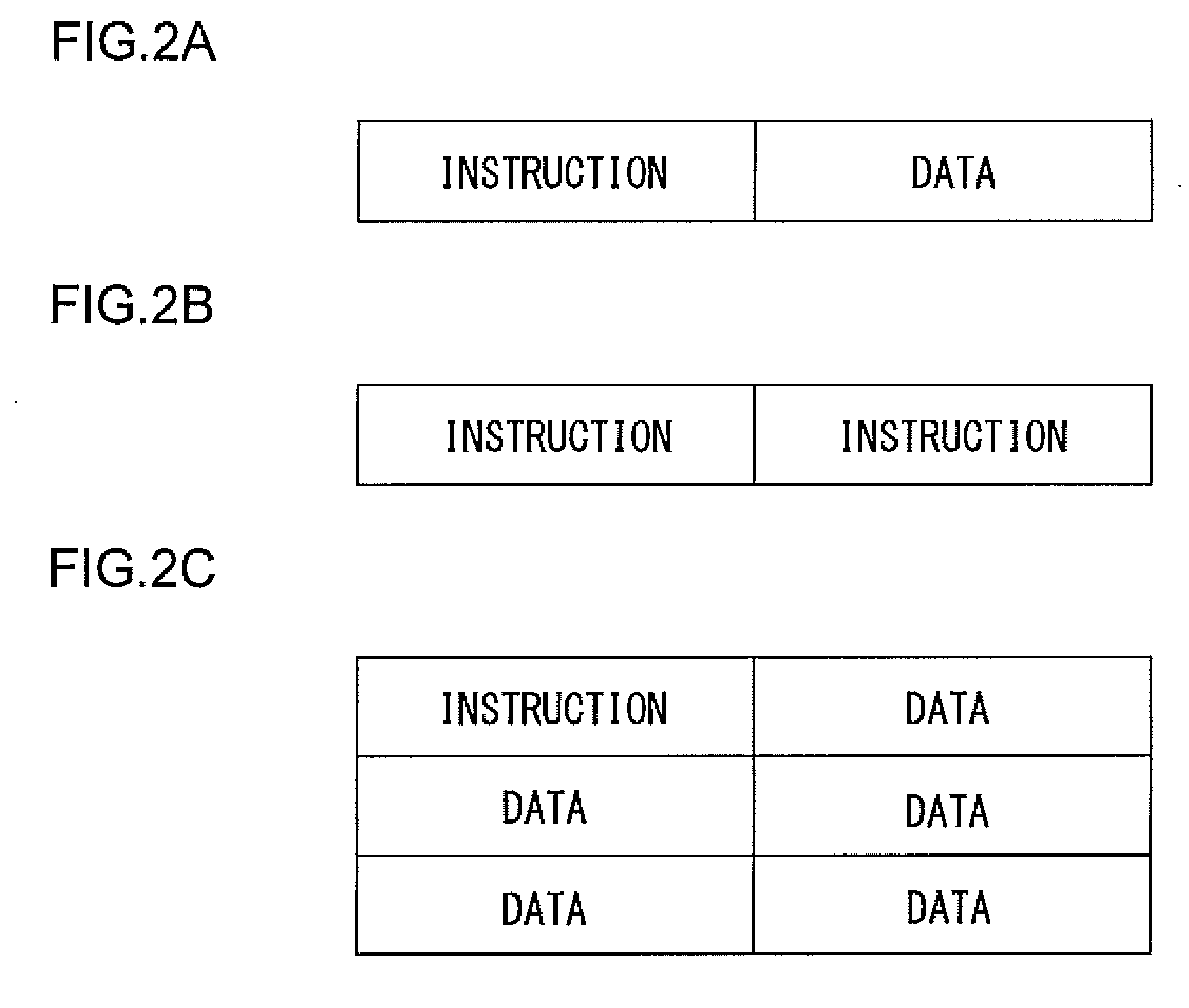
InactiveUS20050273769A1Software engineeringSpecific program execution arrangementsProgram instructionParallel computing
A method, computer program product, and information handling system for generating mixed-mode operations in the compilation of program code for processors having vector or SIMD processing units is disclosed. In a preferred embodiment of the present invention, program instructions making up the body of a loop are abstracted into virtual vector instructions. These virtual vector instructions are treated, for initial code optimization purposes, as vector instructions (i.e., instructions written for the vector unit). The virtual vector instructions are eventually expanded into native code for the target processor, at which time a determination is made for each virtual vector instruction as to whether to expand the virtual vector instruction into native vector instructions, into native scalar instructions, into calls to pre-defined library functions, or into a combination of these. A cost model is used to determine the optimal choice of expansion based on hardware / software constraints, performance costs / benefits, and other criteria.
Owner:IBM CORP
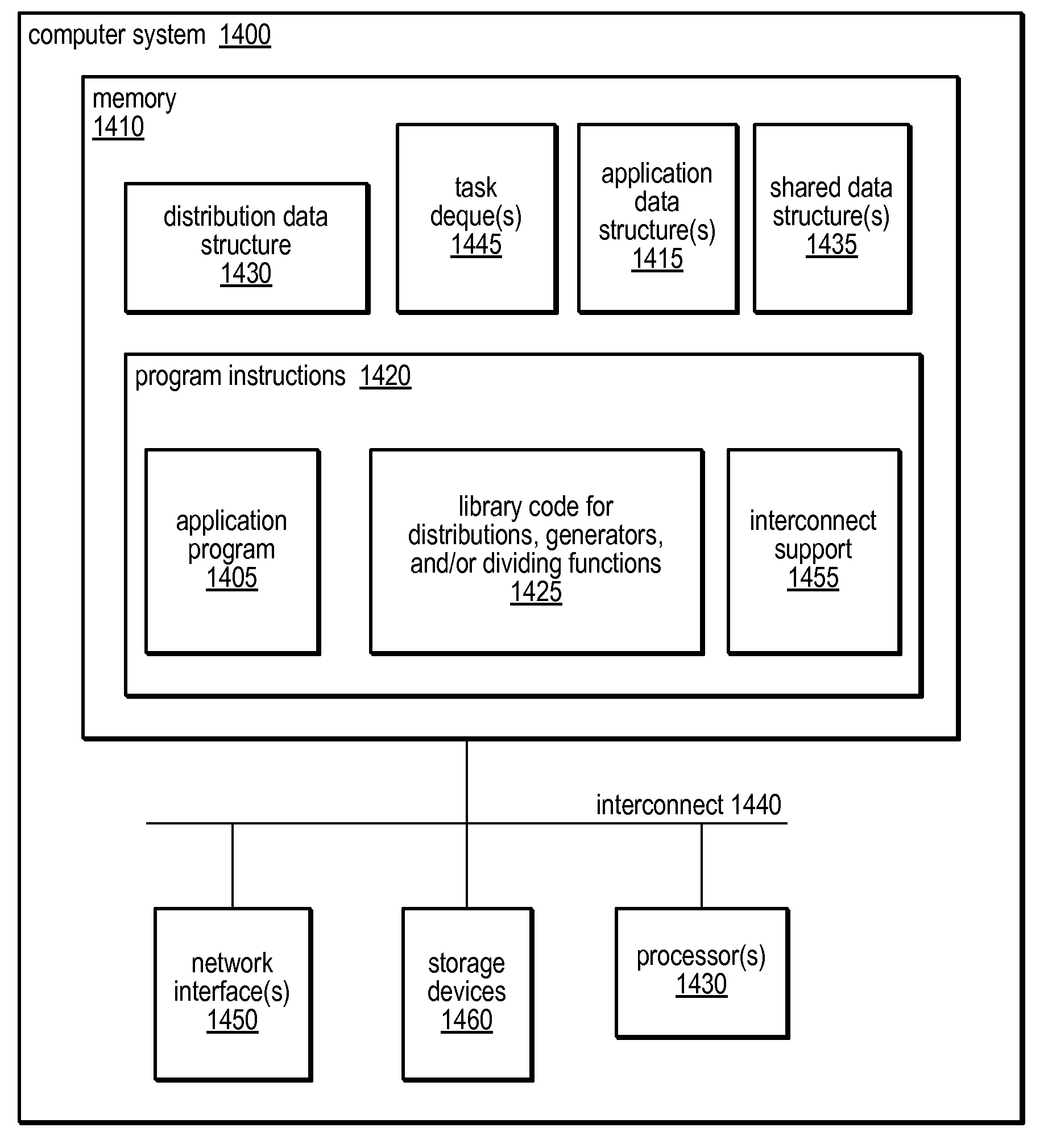
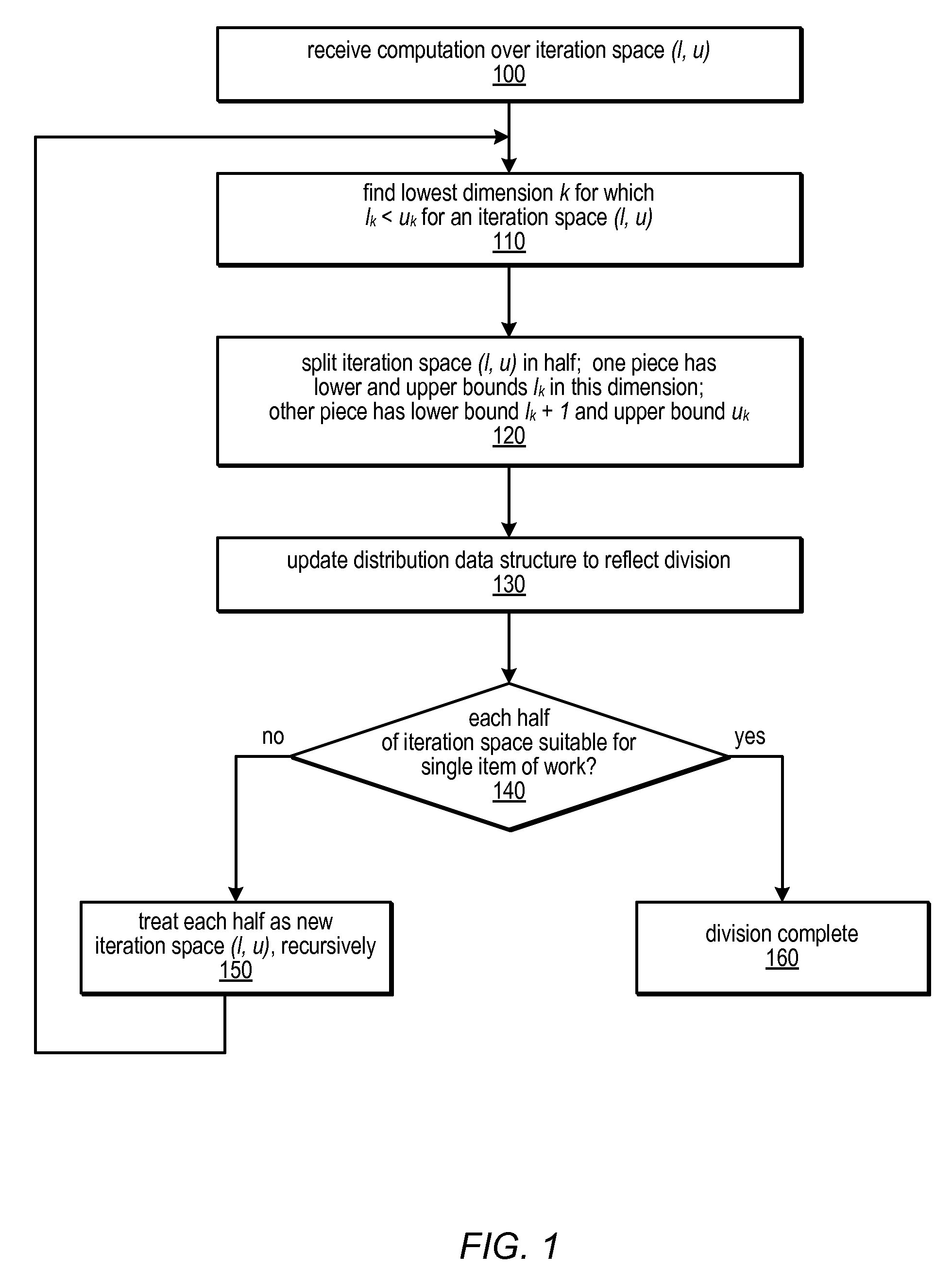
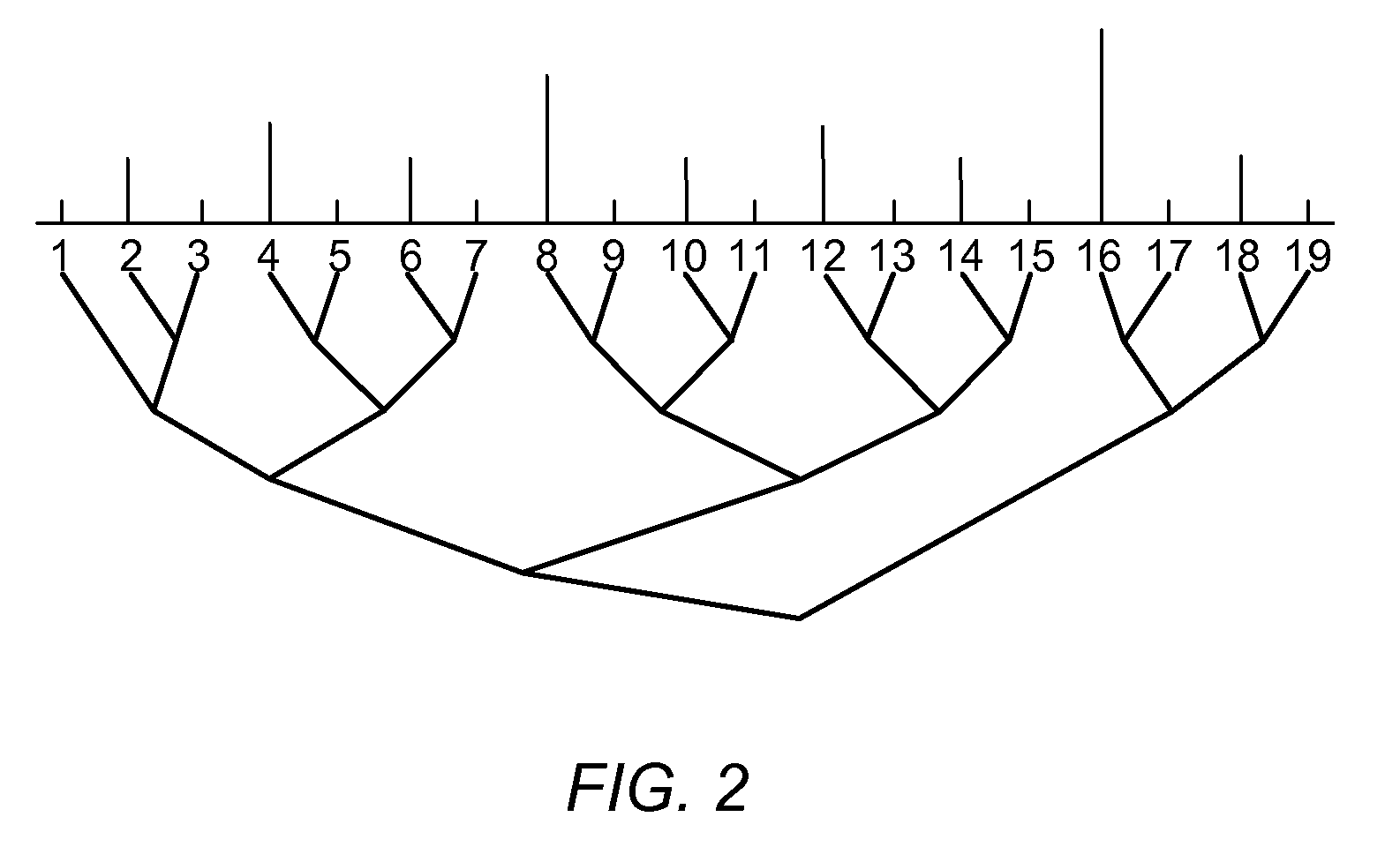
Distribution Data Structures for Locality-Guided Work Stealing
ActiveUS20100031267A1Keep localProvide load balancingResource allocationMemory systemsLocality of referenceLanguage construct
A data structure, the distribution, may be provided to track the desired and / or actual location of computations and data that range over a multidimensional rectangular index space in a parallel computing system. Examples of such iteration spaces include multidimensional arrays and counted loop nests. These distribution data structures may be used in conjunction with locality-guided work stealing and may provide a structured way to track load balancing decisions so they can be reproduced in related computations, thus maintaining locality of reference. They may allow computations to be tied to array layout, and may allow iteration over subspaces of an index space in a manner consistent with the layout of the space itself. Distributions may provide a mechanism to describe computations in a manner that is oblivious to precise machine size or structure. Programming language constructs and / or library functions may support the implementation and use of these distribution data structures.
Owner:SUN MICROSYSTEMS INC
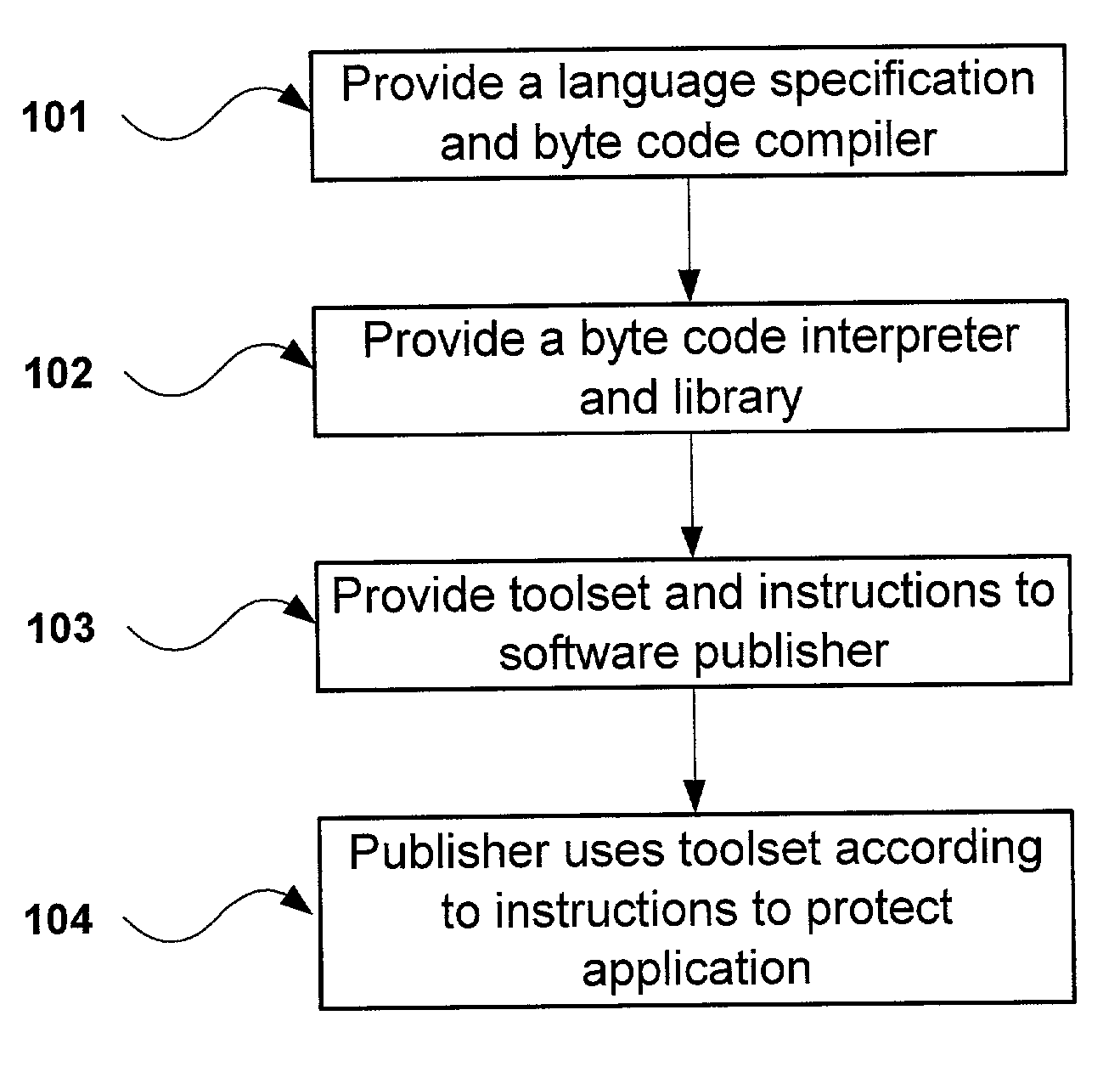
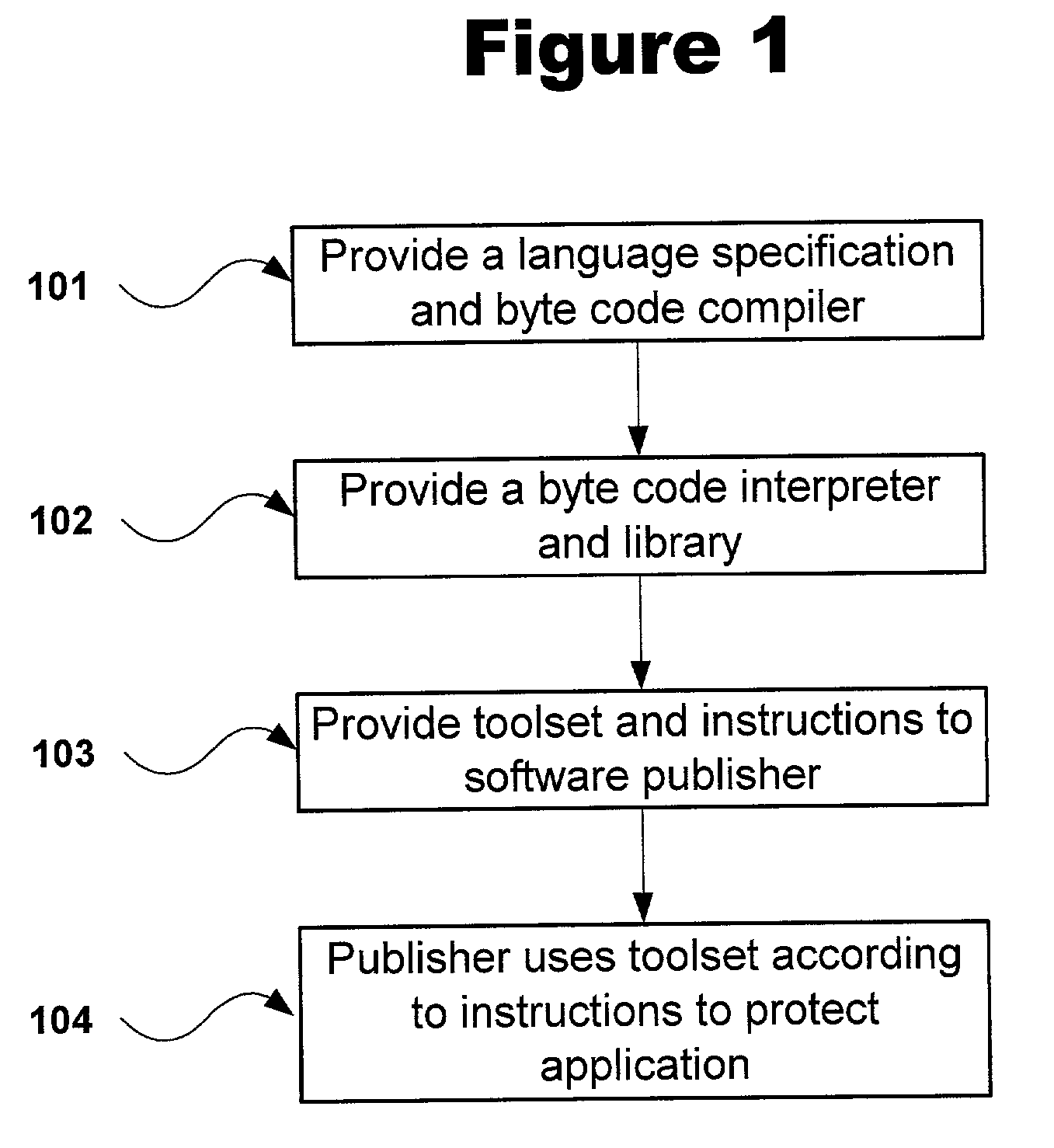
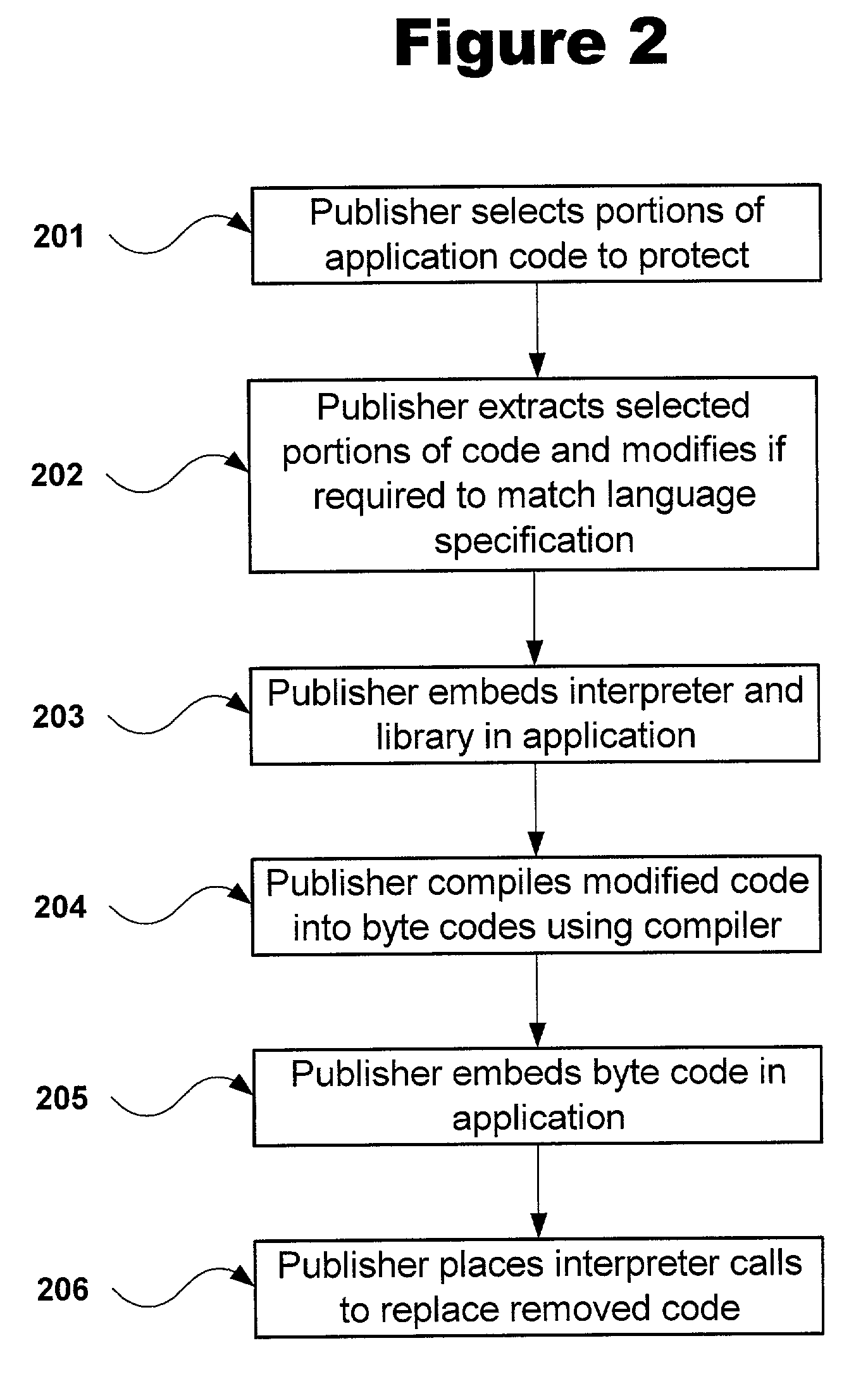
Protecting software from unauthorized use by converting source code modules to byte codes
ActiveUS7124445B2Difficult to operateDifficult to determineDigital data processing detailsUnauthorized memory use protectionObfuscationApplication software
Owner:PACE ANTI PIRACY
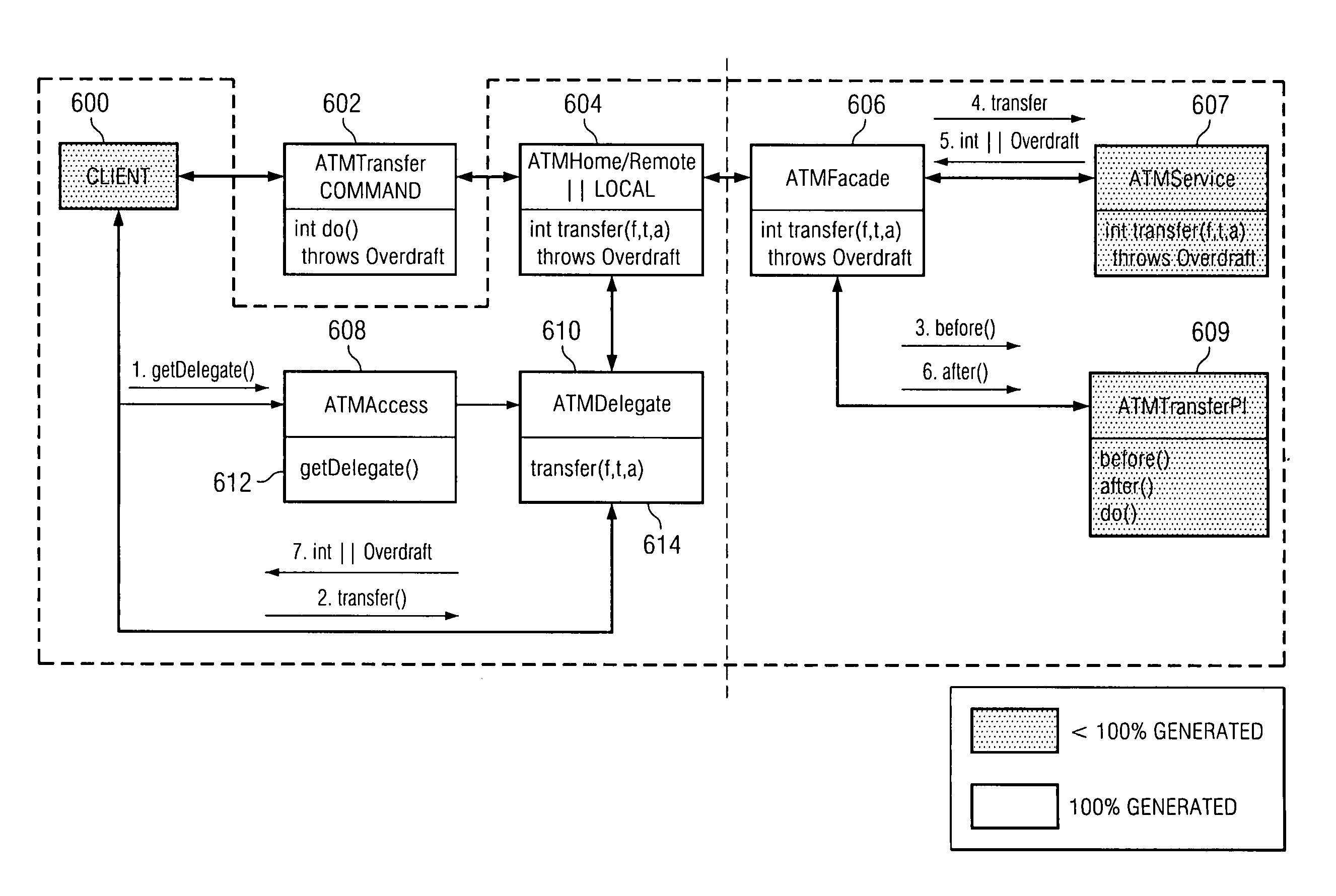
Method and apparatus for generating service frameworks
A method, an apparatus, and computer instructions for generating service frameworks are provided by aspects of the present invention. One aspect of the present invention provides a system library, which includes strongly typed classes that enterprise applications may use in order to obtain code assist and compile time checking from IDE tools typically used by enterprise application developers. Another aspect of the present invention provides the ability to define platform independent models that enable service use cases in order to determine what basic services are needed by the enterprise application. Yet another aspect of the present invention includes an integrated generator that generates the strongly typed components and skeleton code from the platform independent models by applying best practice pattern usage for the target platform currently used with the system library functions.
Owner:IBM CORP +1
Continuous run-time validation of program execution: a practical approach
ActiveUS20140082327A1Easy to modifyGuaranteed CompatibilityError detection/correctionDigital computer detailsControl flowReal time validation
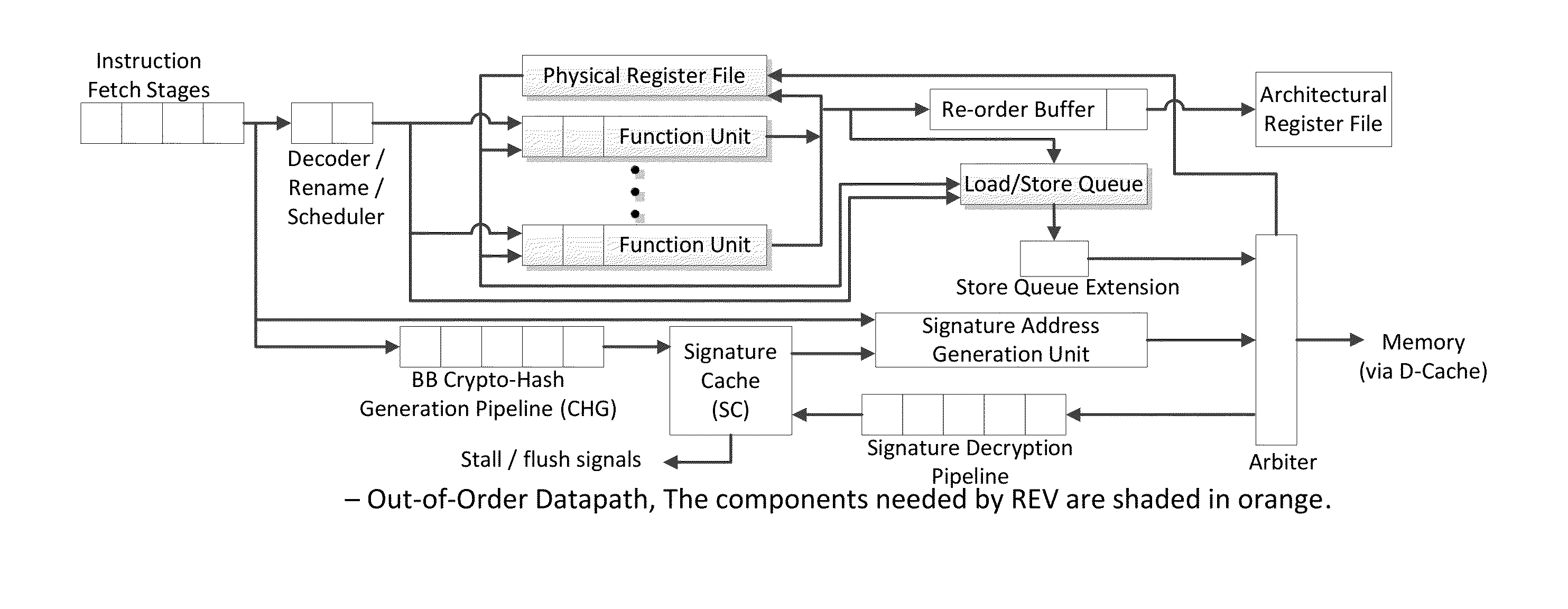
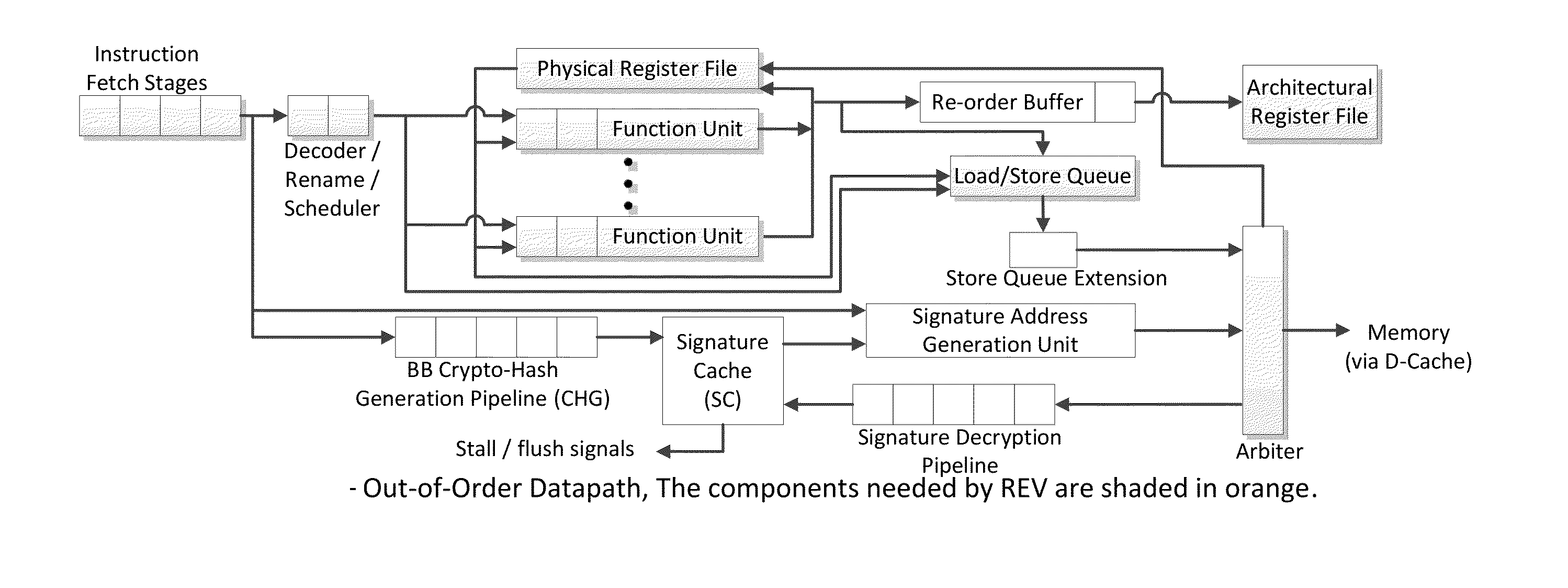
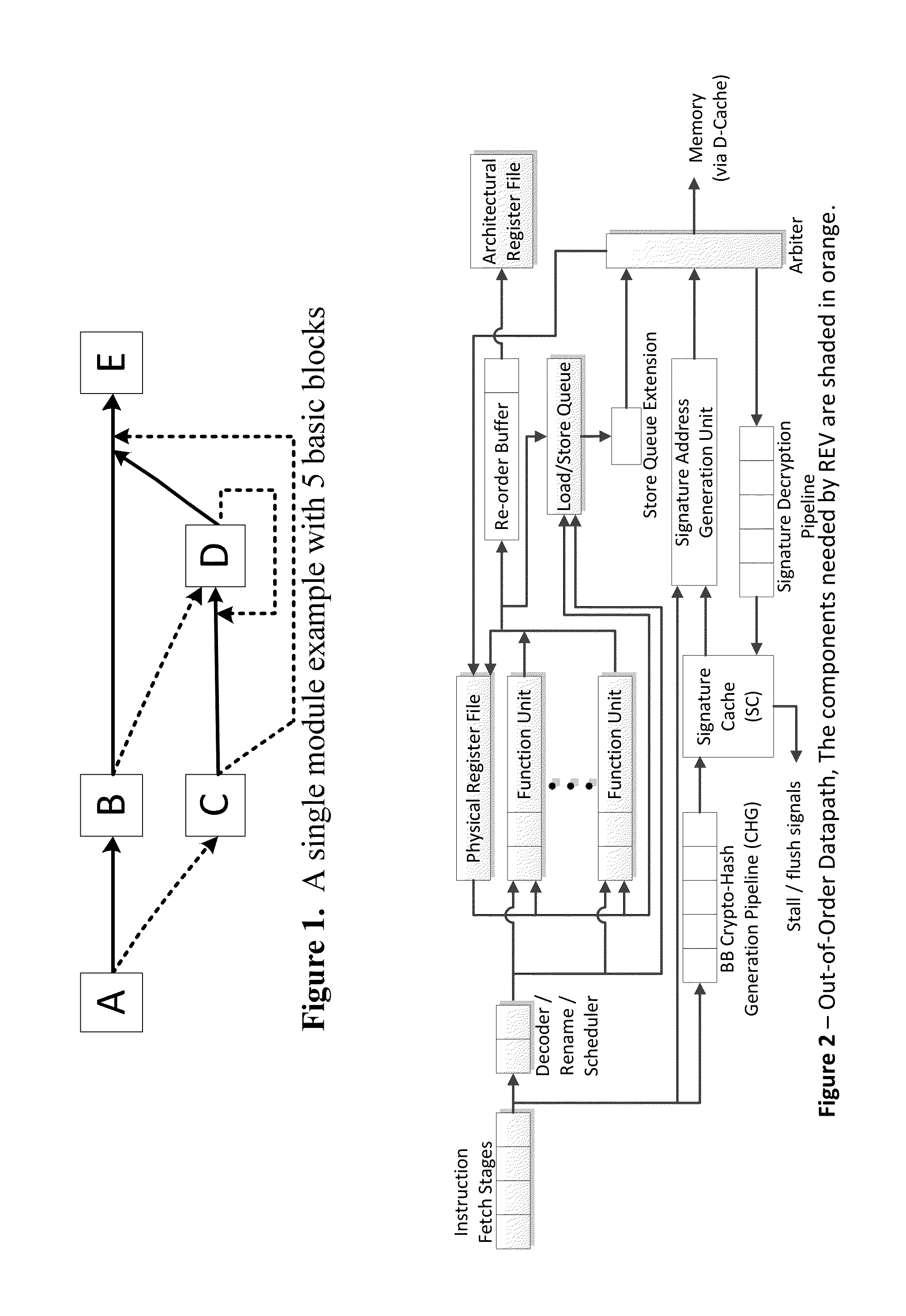
Trustworthy systems require that code be validated as genuine. Most systems implement this requirement prior to execution by matching a cryptographic hash of the binary file against a reference hash value, leaving the code vulnerable to run time compromises, such as code injection, return and jump-oriented programming, and illegal linking of the code to compromised library functions. The Run-time Execution Validator (REV) validates, as the program executes, the control flow path and instructions executed along the control flow path. REV uses a signature cache integrated into the processor pipeline to perform live validation of executions, at basic block boundaries, and ensures that changes to the program state are not made by the instructions within a basic block until the control flow path into the basic block and the instructions within the basic block are both validated.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
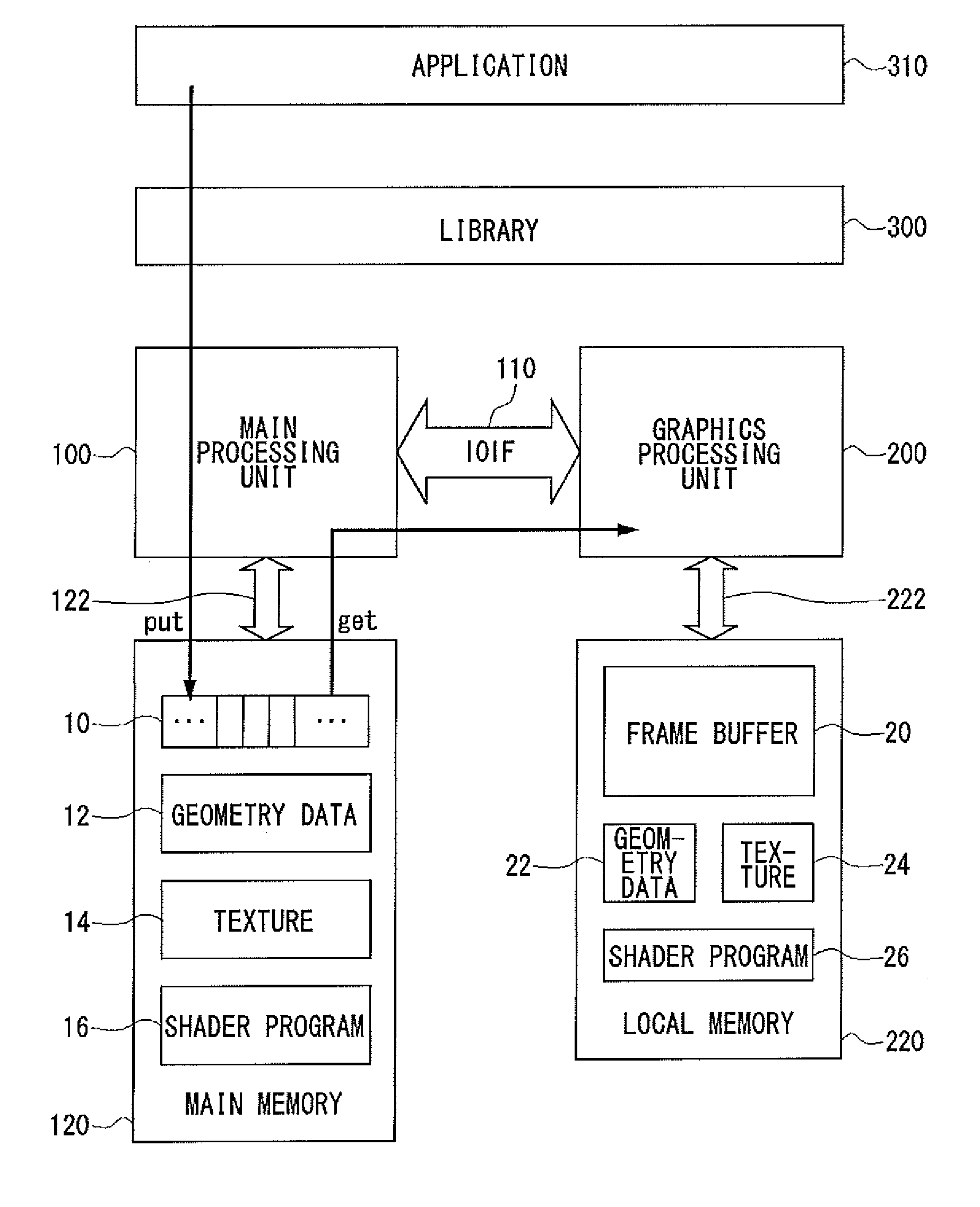
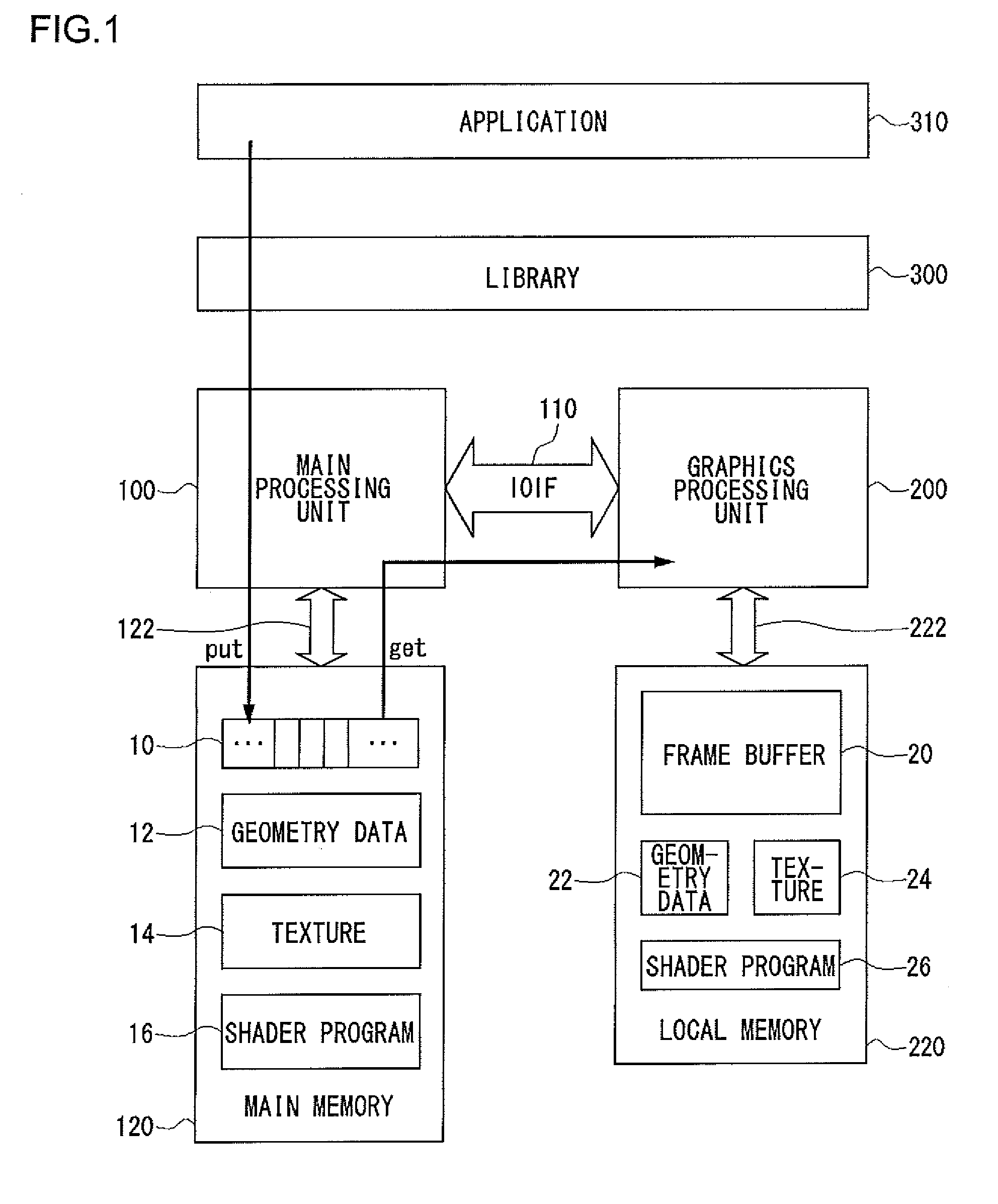
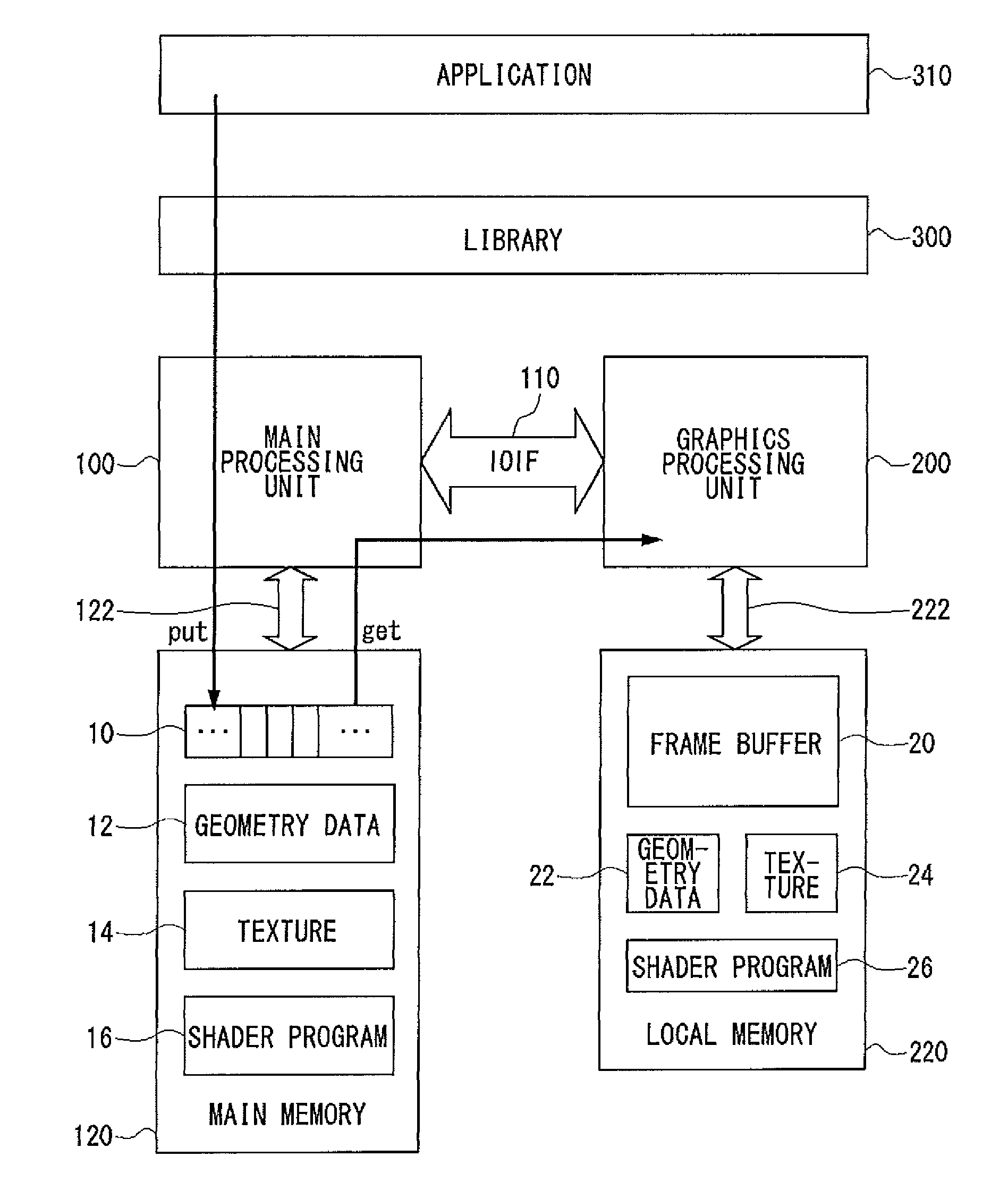
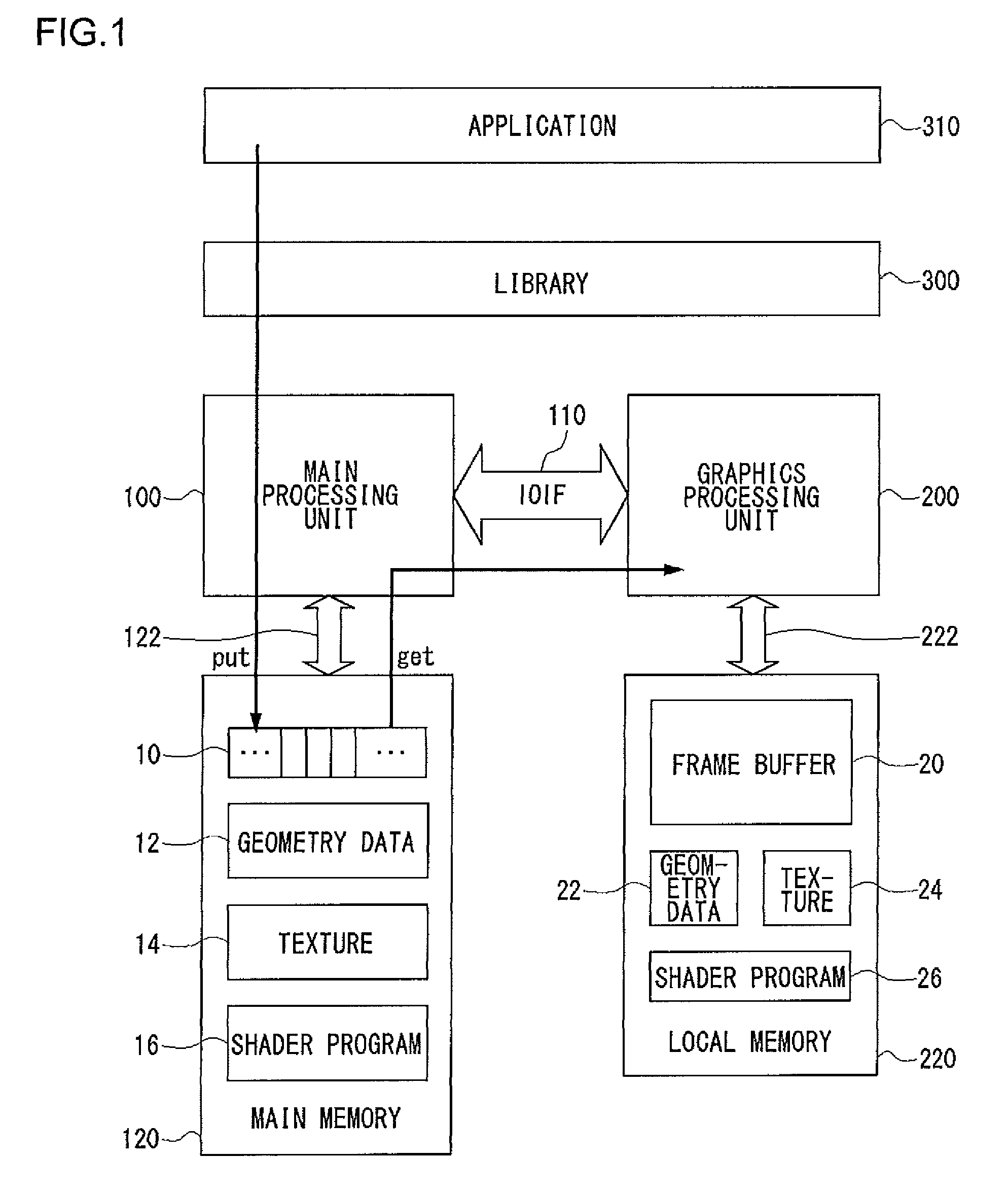
Graphics Processing Apparatus, Graphics Library Module And Graphics Processing Method
ActiveUS20090002380A1Increase flexibilityImprove efficiencyImage memory managementImage generationGraphics libraryLibrary function
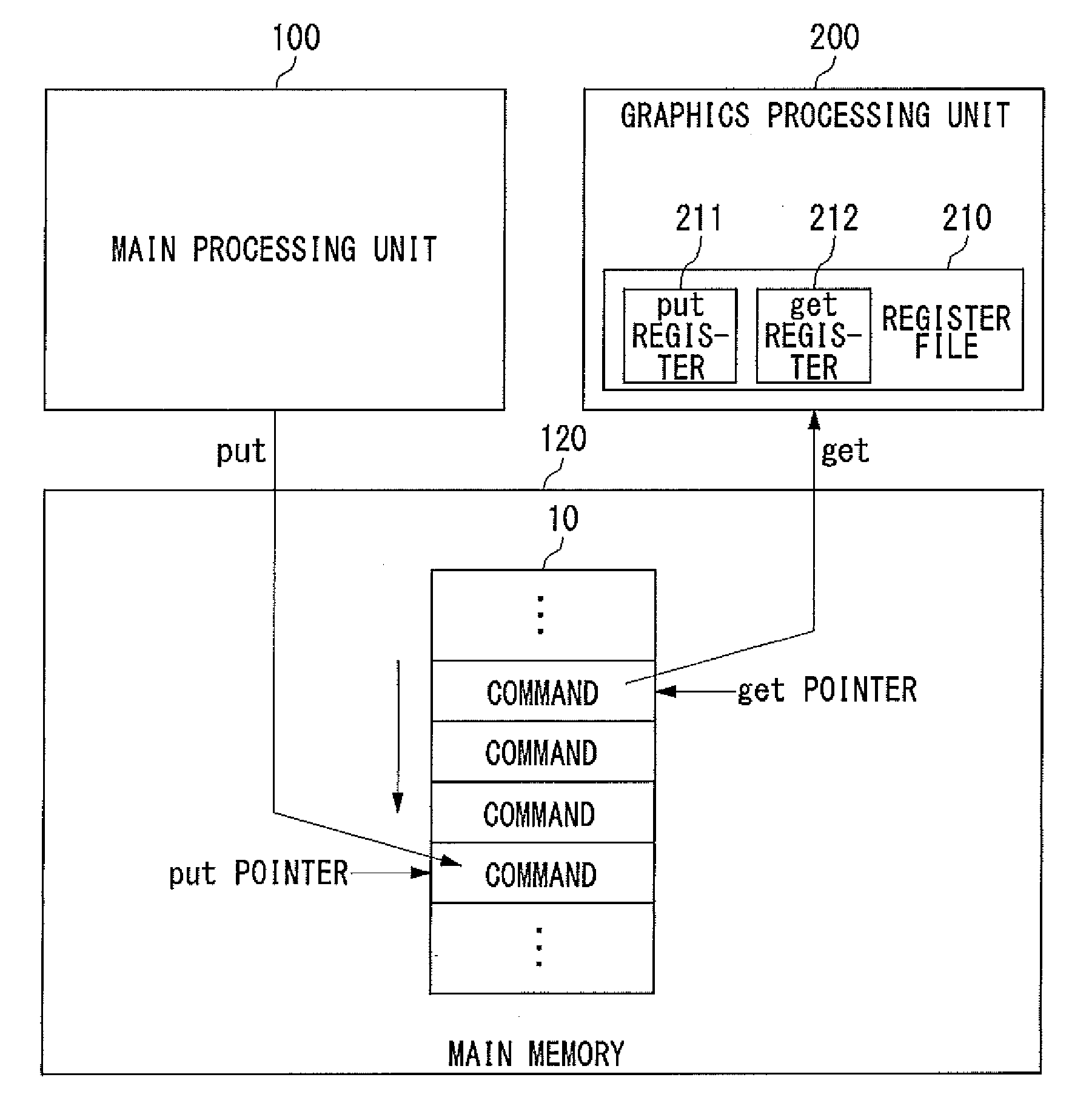
There is provided a graphics processing system that includes a main processing unit and a graphics processing unit (GPU). The main processing unit puts rendering commands generated using a graphics library in the queue of a command buffer in a main memory. In this process, the library function offered by the graphics library is converted into the rendering commands, without any rendering attributes retained in the library. The GPU reads and executes the rendering commands stacked in the command buffer, and generates rendering data in a frame buffer.
Owner:SONY COMPUTER ENTERTAINMENT INC
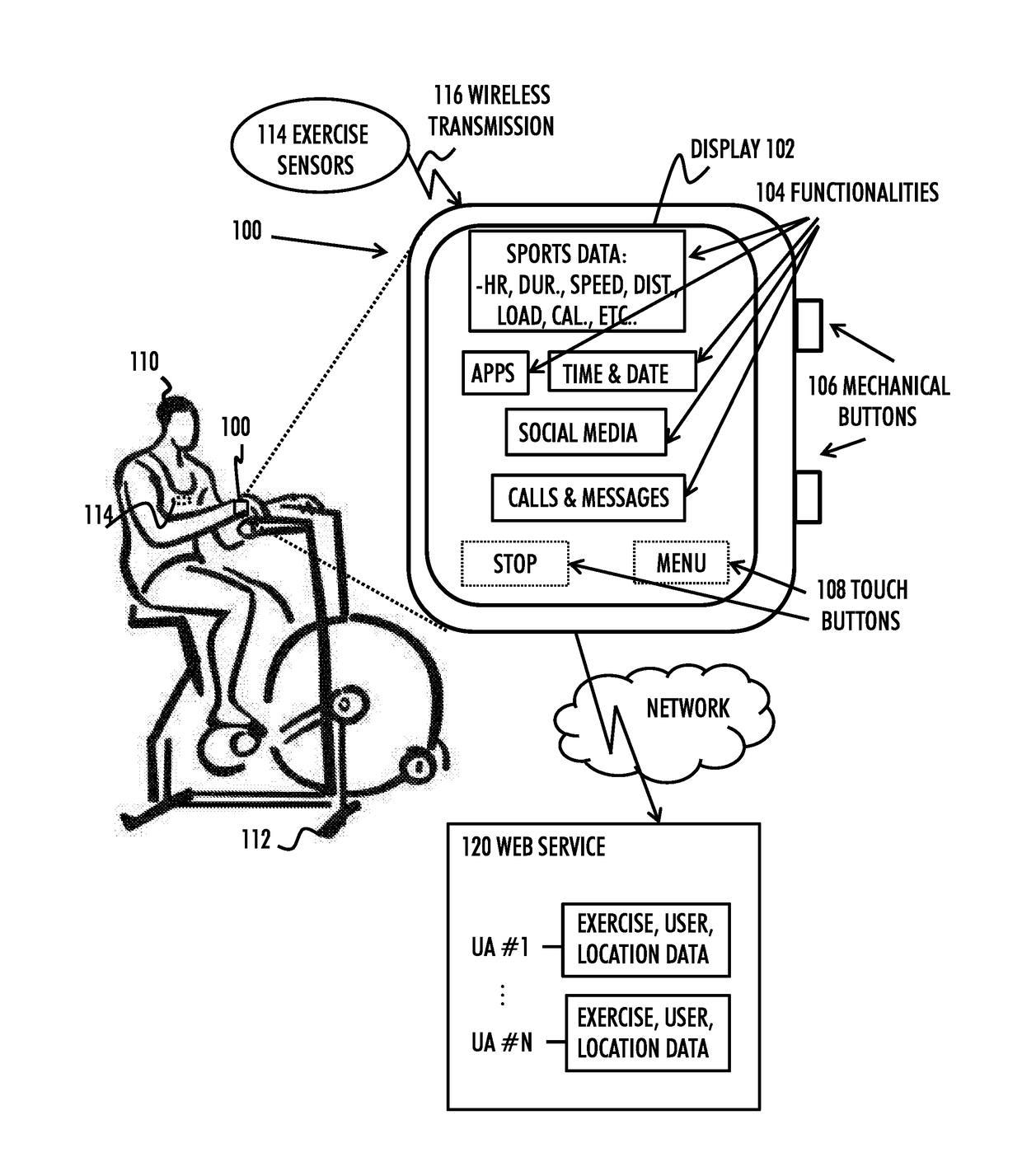
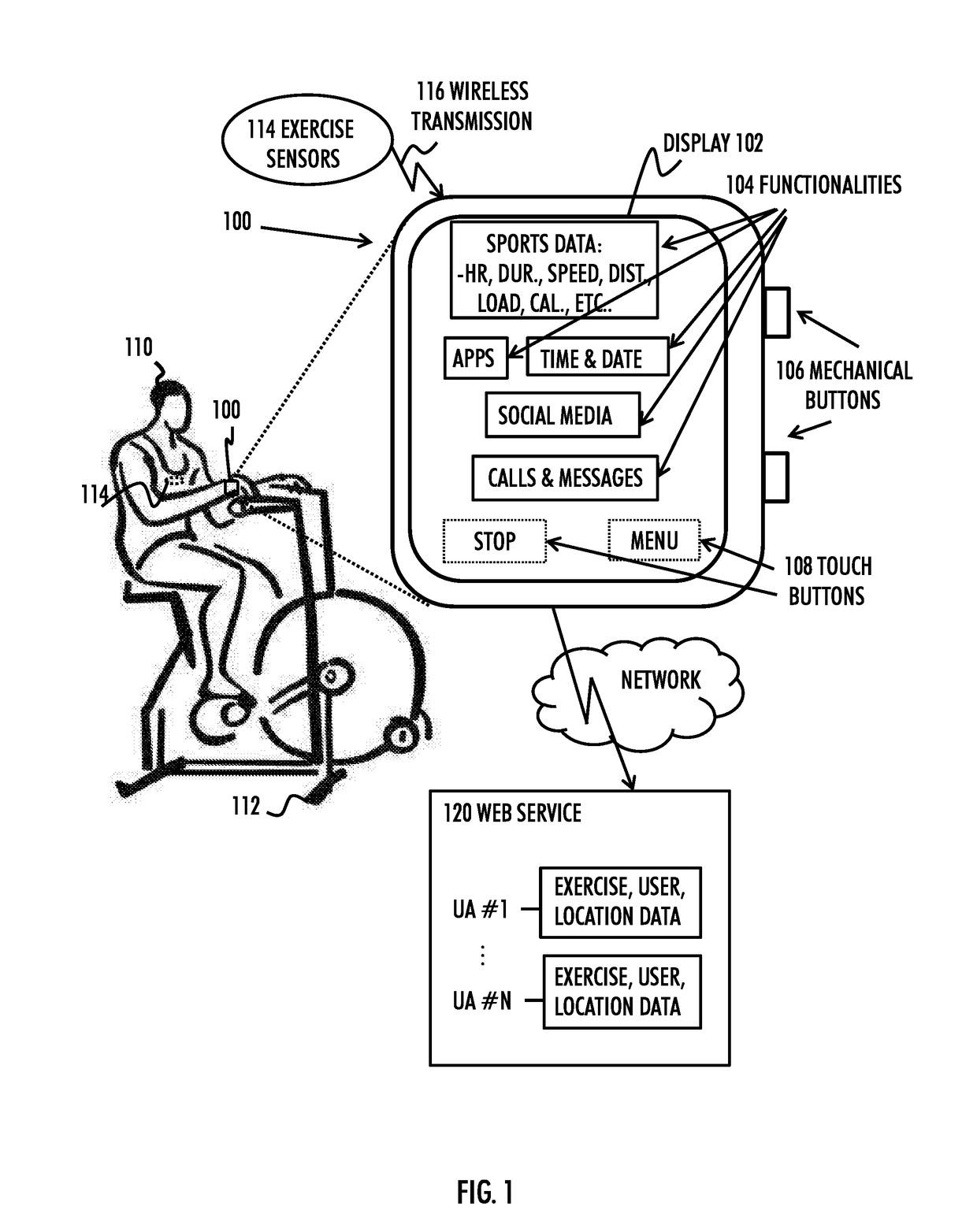
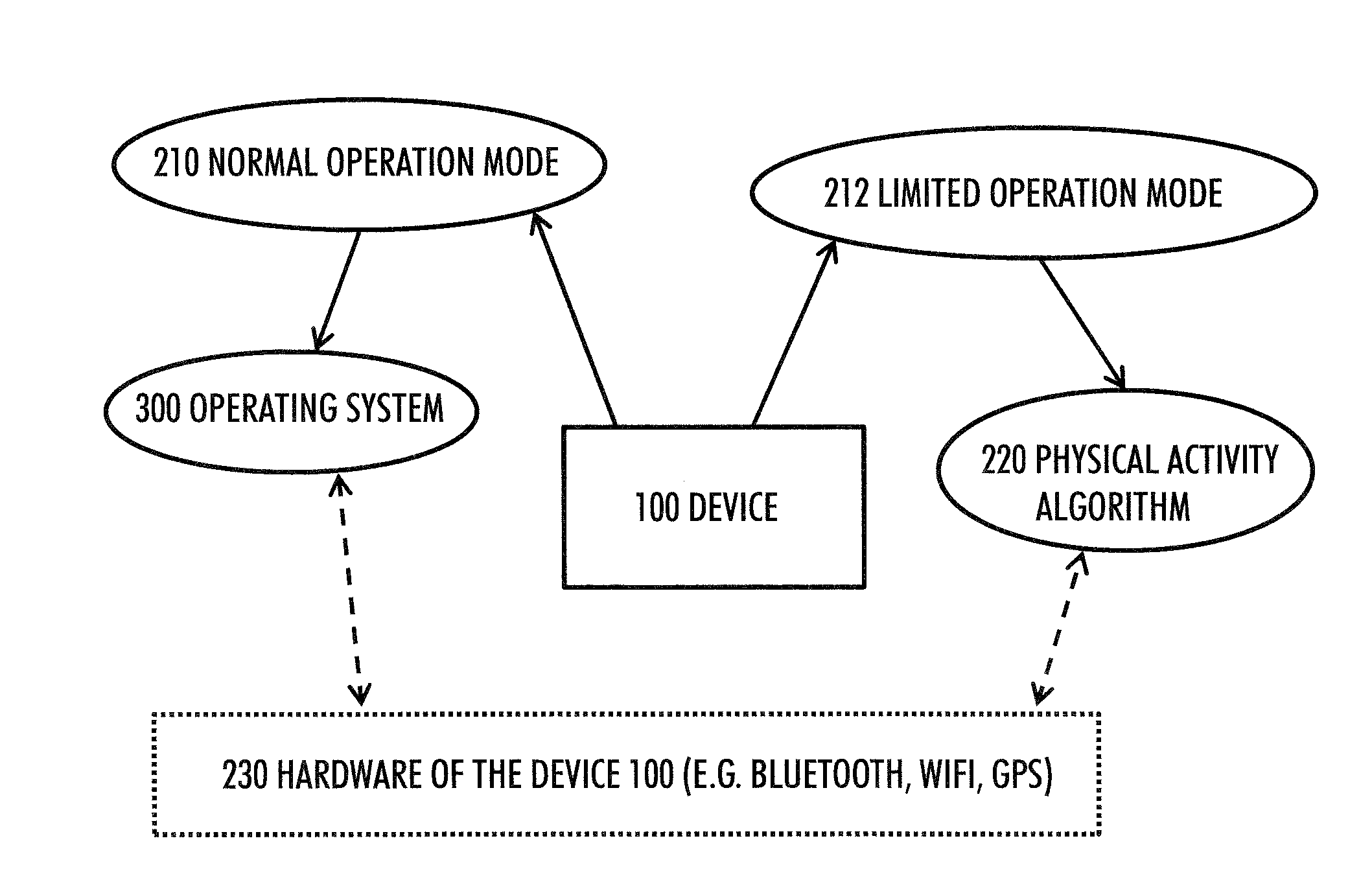
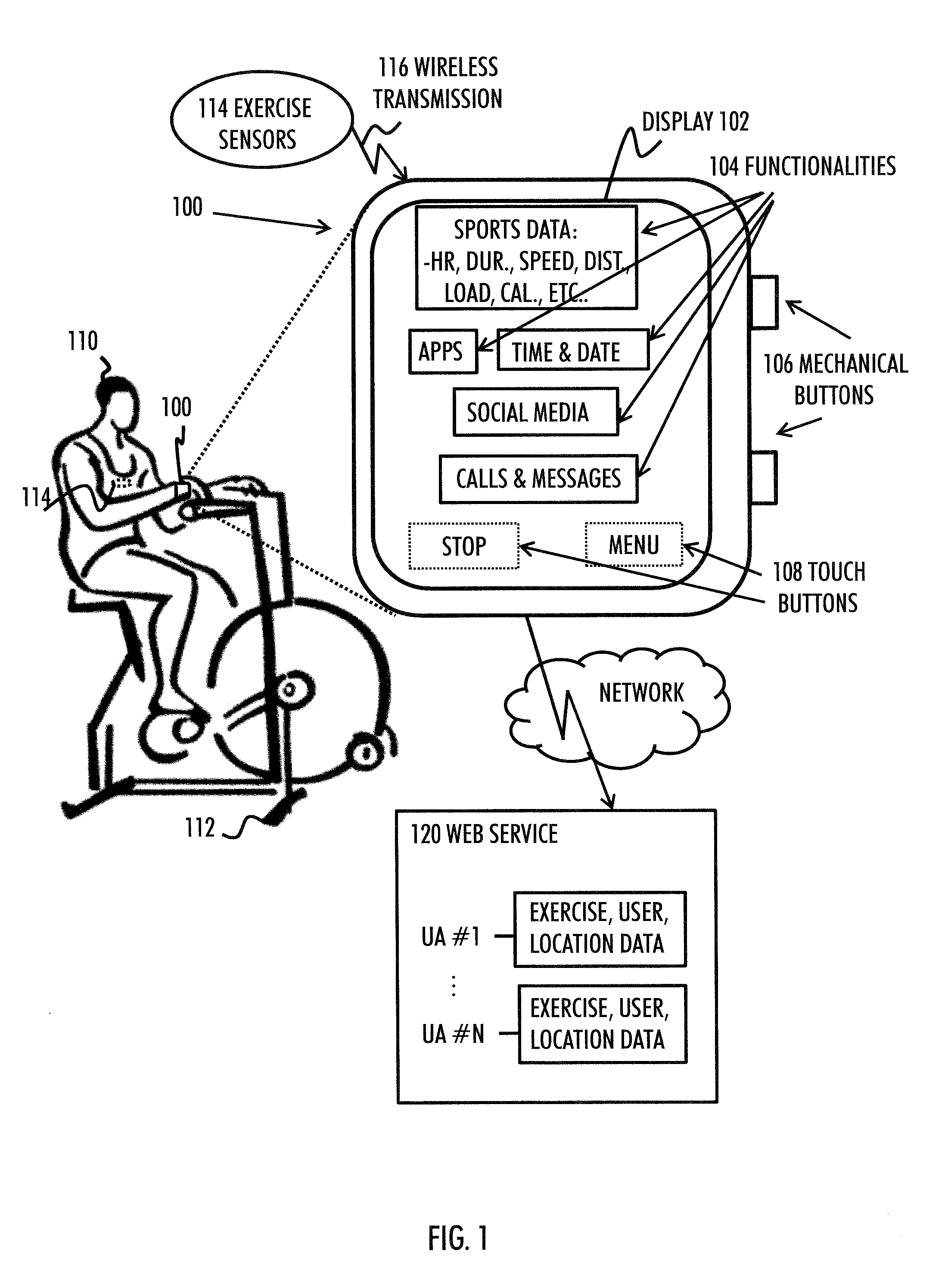
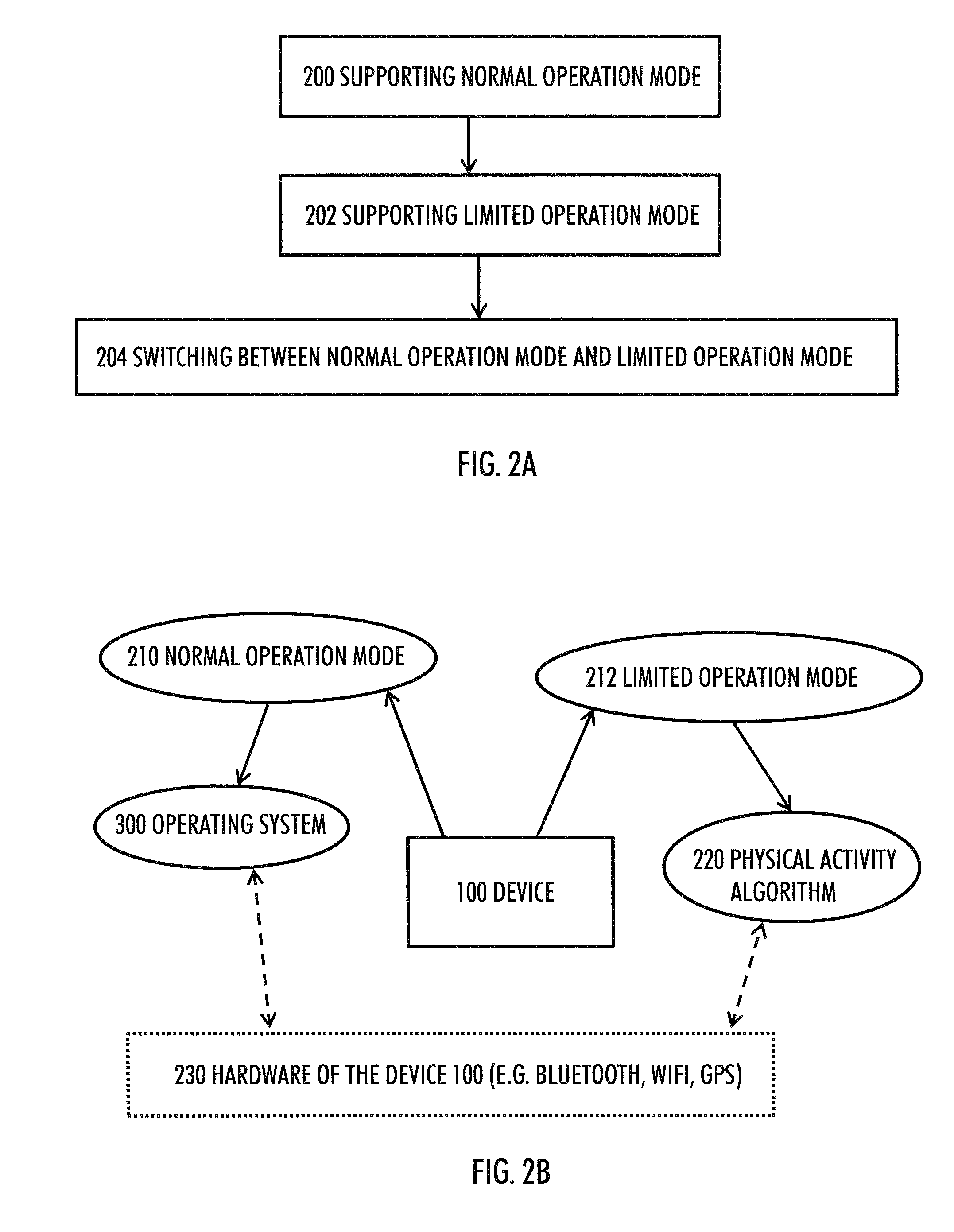
Device power saving during exercise
ActiveUS20170168555A1Operation mode is limitedMedical communicationPower supply for data processingComputer hardwareOperation mode
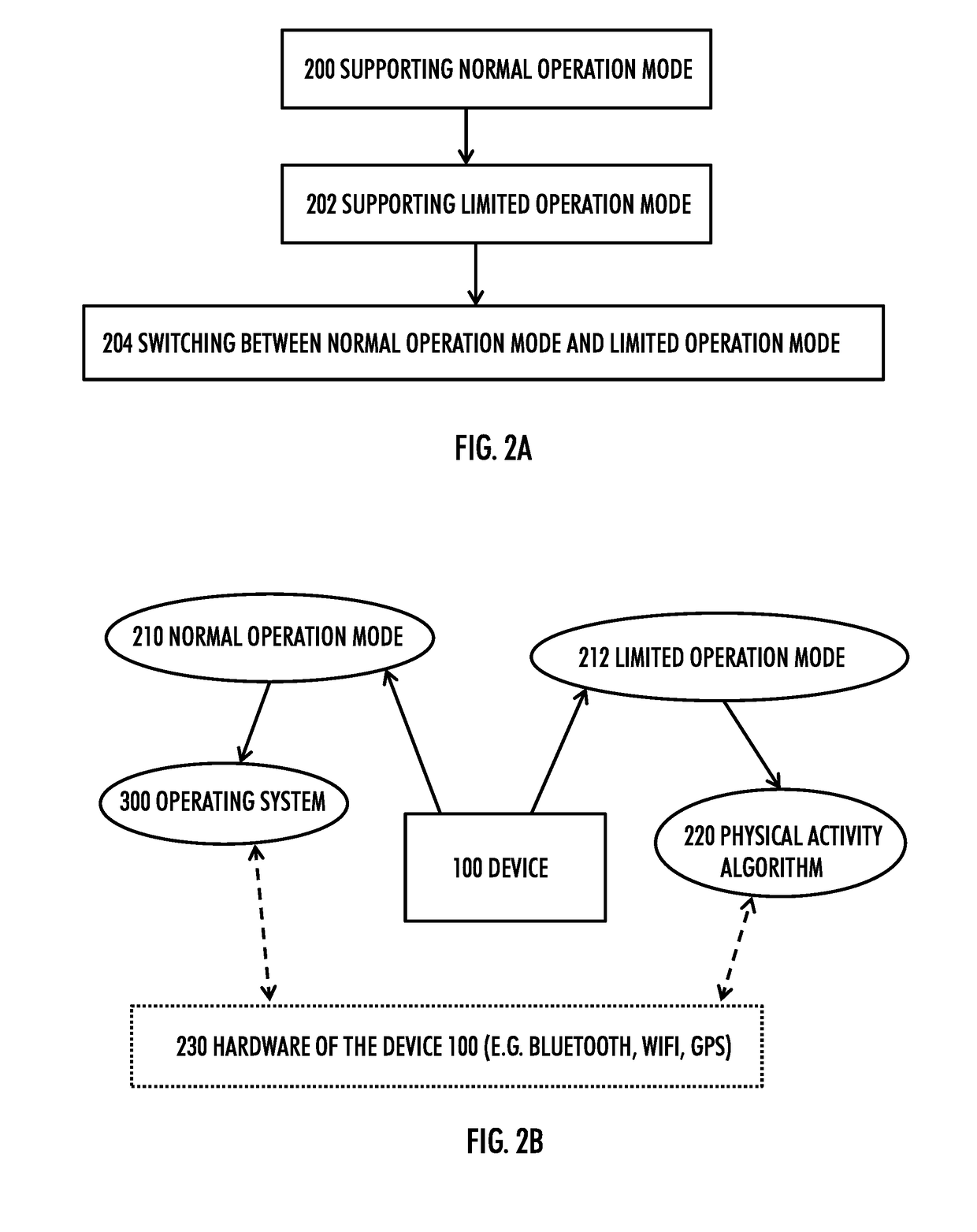
A method includes: supporting a normal operation mode during which functionalities of a portable apparatus are available through an operating system of the apparatus, wherein the operating system includes a plurality of layers including a kernel and library functions-layer; supporting a limited operation mode during which the apparatus is configured to execute a physical activity algorithm based on physical activity data corresponding to a physical activity session performed by a user of the apparatus, wherein the physical activity algorithm applies a direct low-level hardware access bypassing at least the layers above the kernel and the library functions-layer; and switching between the normal operation mode and the limited operation mode
Owner:POLAR ELECTRO
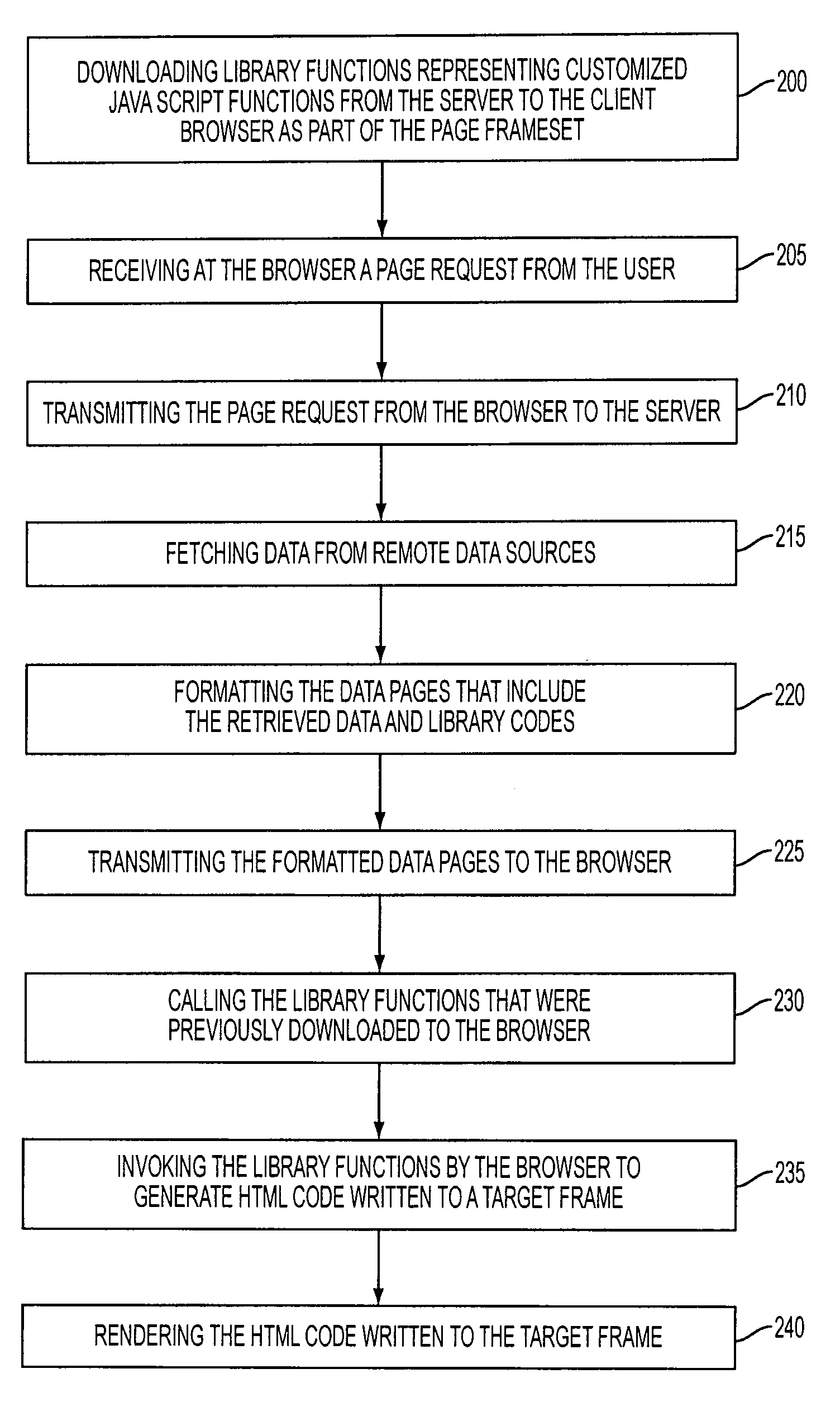
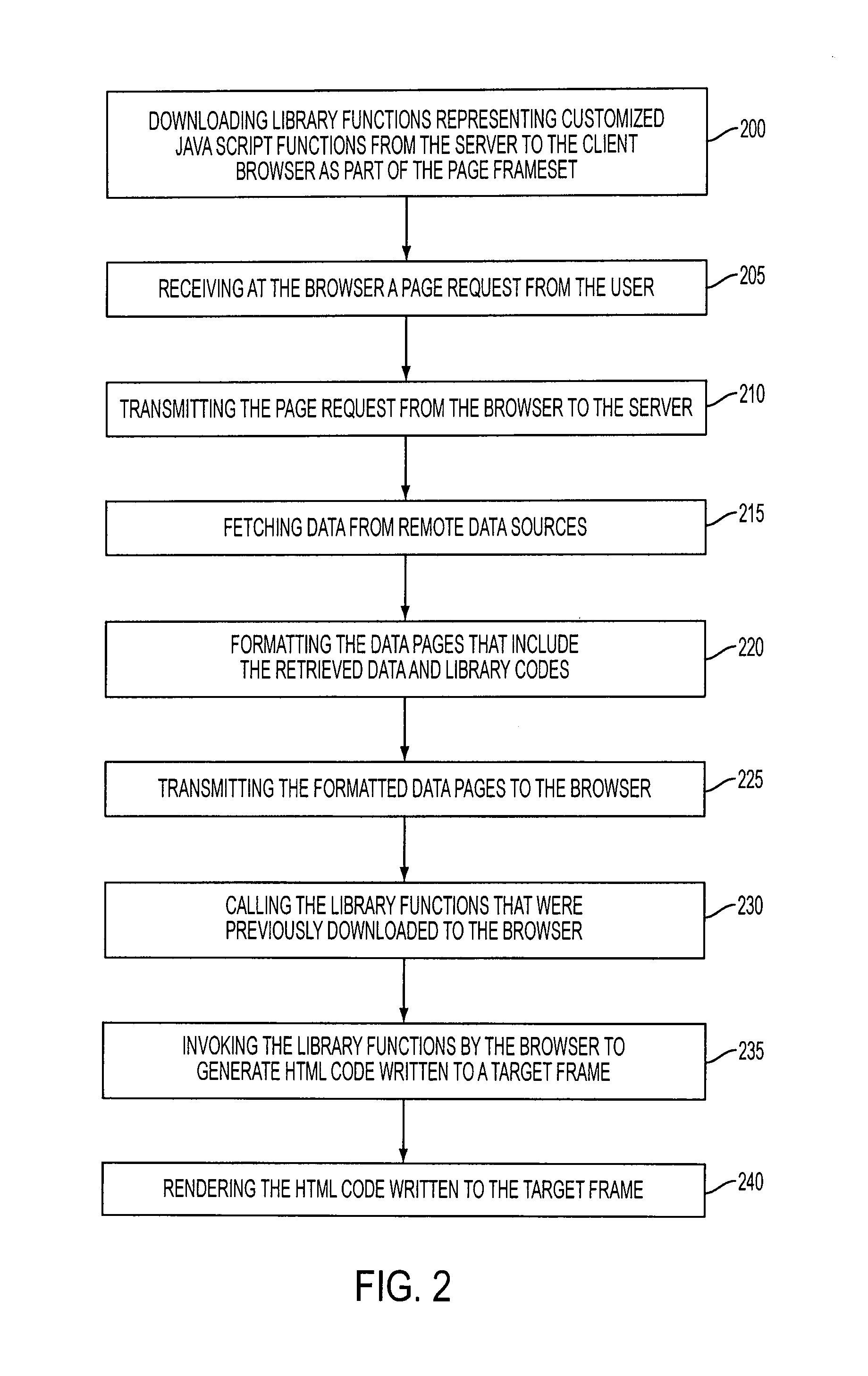
Creating dynamic web pages at a client browser
InactiveUS7376653B2Shorten the timeReduces central processing unit (CPU) utilizationData processing applicationsTransmissionClient-sideLibrary function
A system and method for accelerated downloading of dynamic web pages. Initially, customized script library functions are downloaded from the server to the client browser as part of the page frameset. A page request from a user is received by the client browser and transmitted to the server. In turn, page data is fetched by the server from remote data sources and formatted to include library code for invoking associated library functions written in a script programming language, e.g., JavaScript. The formatted data pages is transmitted from the server to the client browser which calls the library functions that were previously downloaded to the client browser in response to the library code in the data pages. The appropriate library functions are invoked from the client browser to generate Hyper-Text Markup Language code that is written to a target frame. Finally, the Hyper-Text Markup Language code written to the target frame is rendered. The downloaded JavaScript library functions are therefore downloaded to the client side only once but accessed multiple times thereby increasing efficiency of downloading and reducing bandwidth. Faster page draw is achieved because of the limited amount of information or data that is repeatedly transferred to the client browser from the server.
Owner:REFINITIV US ORG LLC
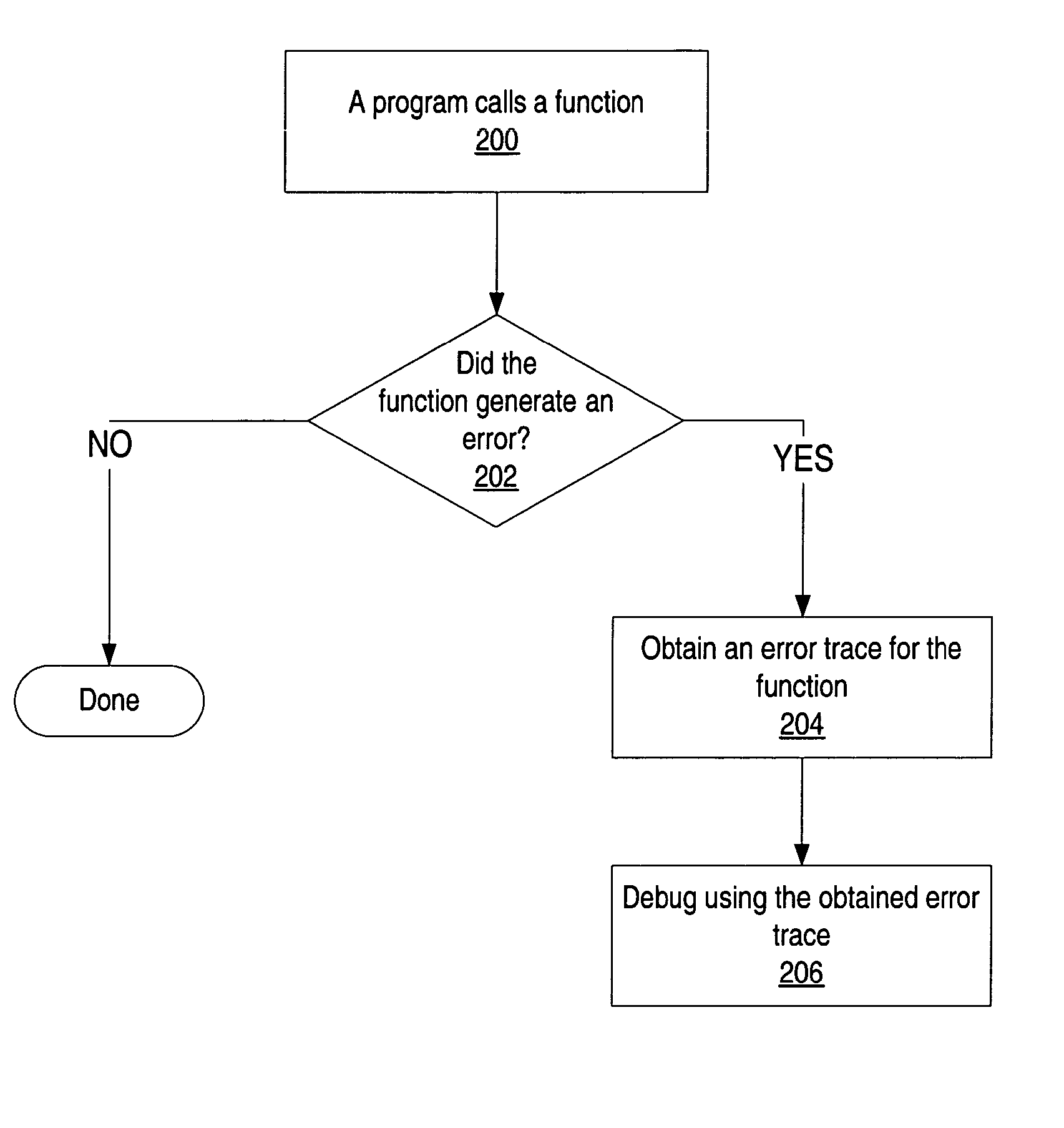
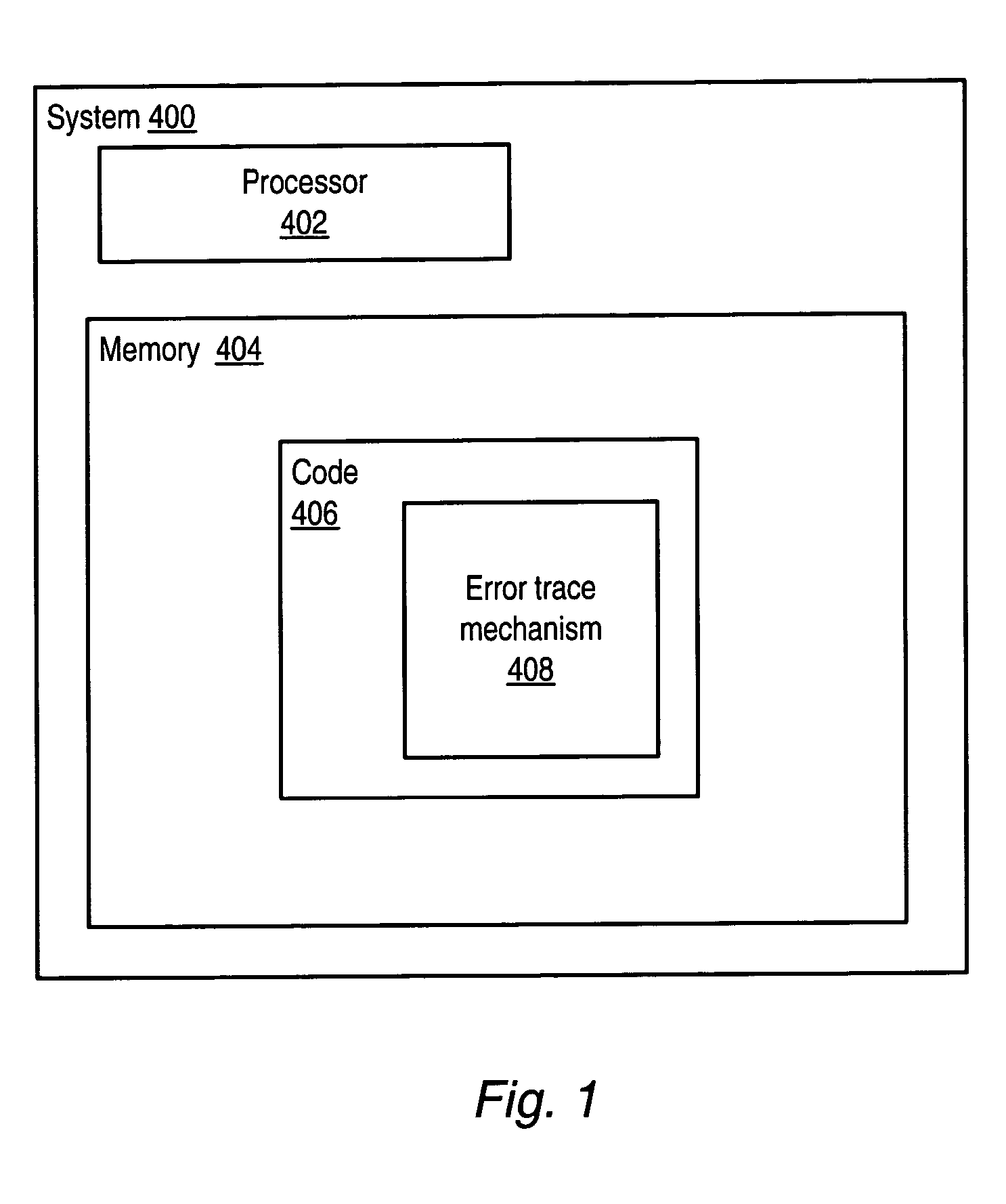
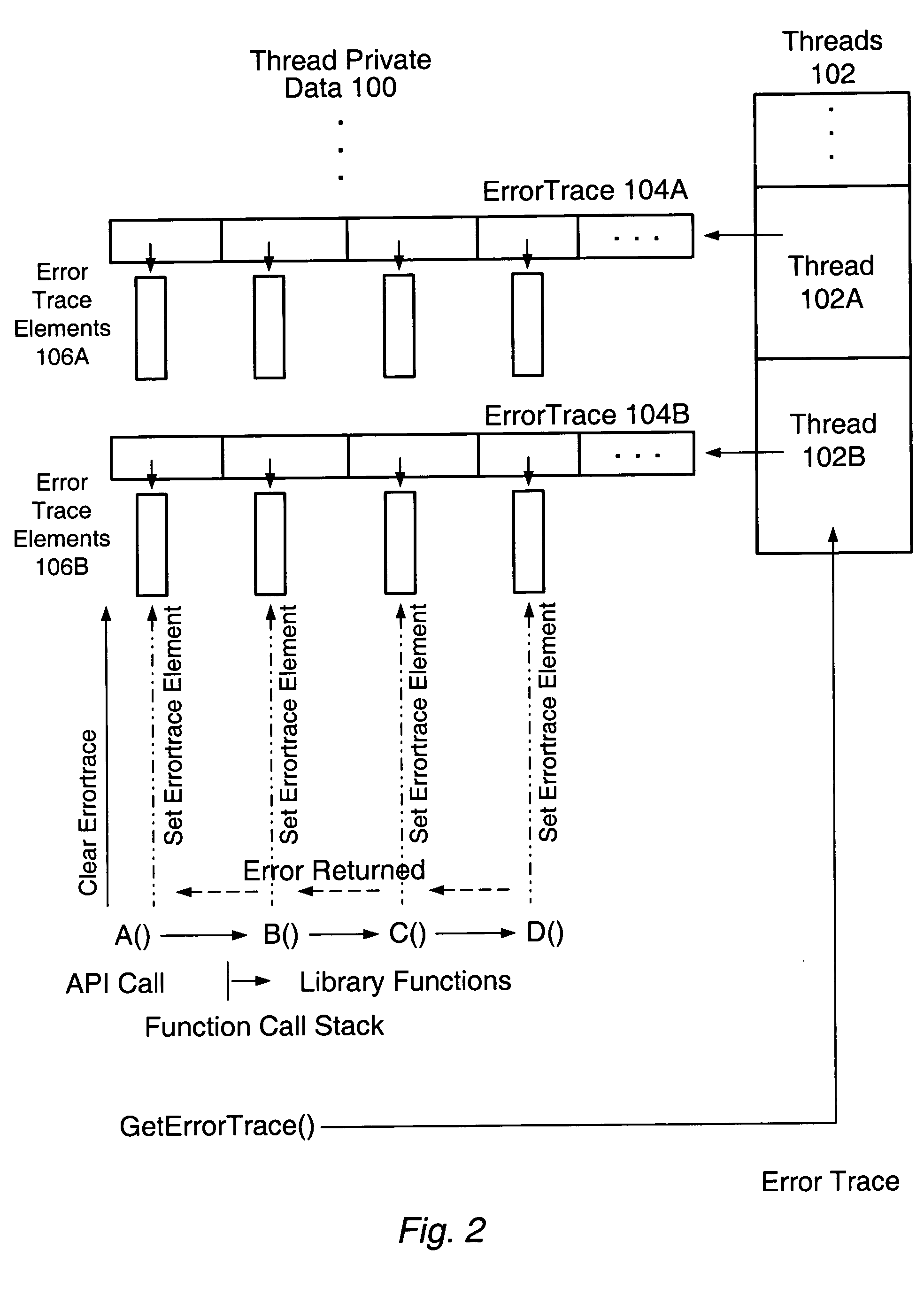
Flexible error trace mechanism
For a flexible error trace mechanism, embodiments may be implemented for C / C++ interface libraries, or in programs written in C / C++ or other programming languages. In one embodiment, when an error occurs in a function call, a trace element may be recorded that may include the source file name, function name, line number and other information that may be used to identify the error. In one embodiment, the library function may call a plurality of library functions in a function call stack. For each of the plurality of library functions, if the library function generates an error, an error trace element may be added to the error trace. After completion of the library function, the program may obtain the error trace for the library function. The error(s), if any, may be debugged using the information in the obtained error trace.
Owner:ORACLE INT CORP +1
Graphics Processing Apparatus
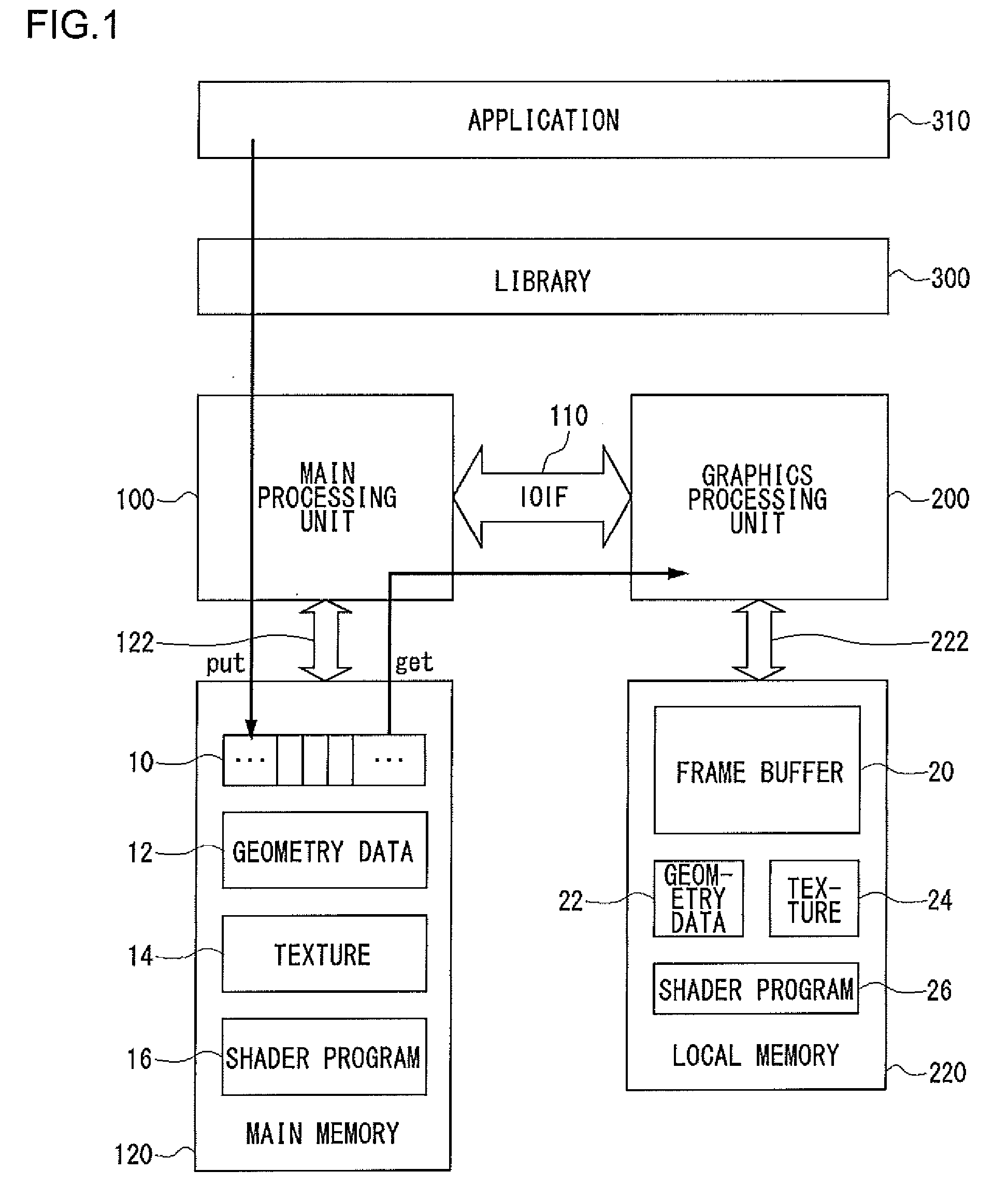
ActiveUS20080278509A1Increase flexibilityImprove efficiencyImage data processing detailsElectric digital data processingGraphics libraryLibrary function
There is provided a graphics processing system that includes a main processing unit and a graphics processing unit (GPU). The main processing unit puts rendering commands generated using a graphics library in the queue of a command buffer in a main memory. In this process, the library function offered by the graphics library is converted into the rendering commands, without any rendering attributes retained in the library. The GPU reads and executes the rendering commands stacked in the command buffer, and generates rendering data in a frame buffer.
Owner:SONY COMPUTER ENTERTAINMENT INC
Character constant weight method
InactiveCN1773413AVersatileGood security propertiesDigital data processing detailsManagement toolOperational system
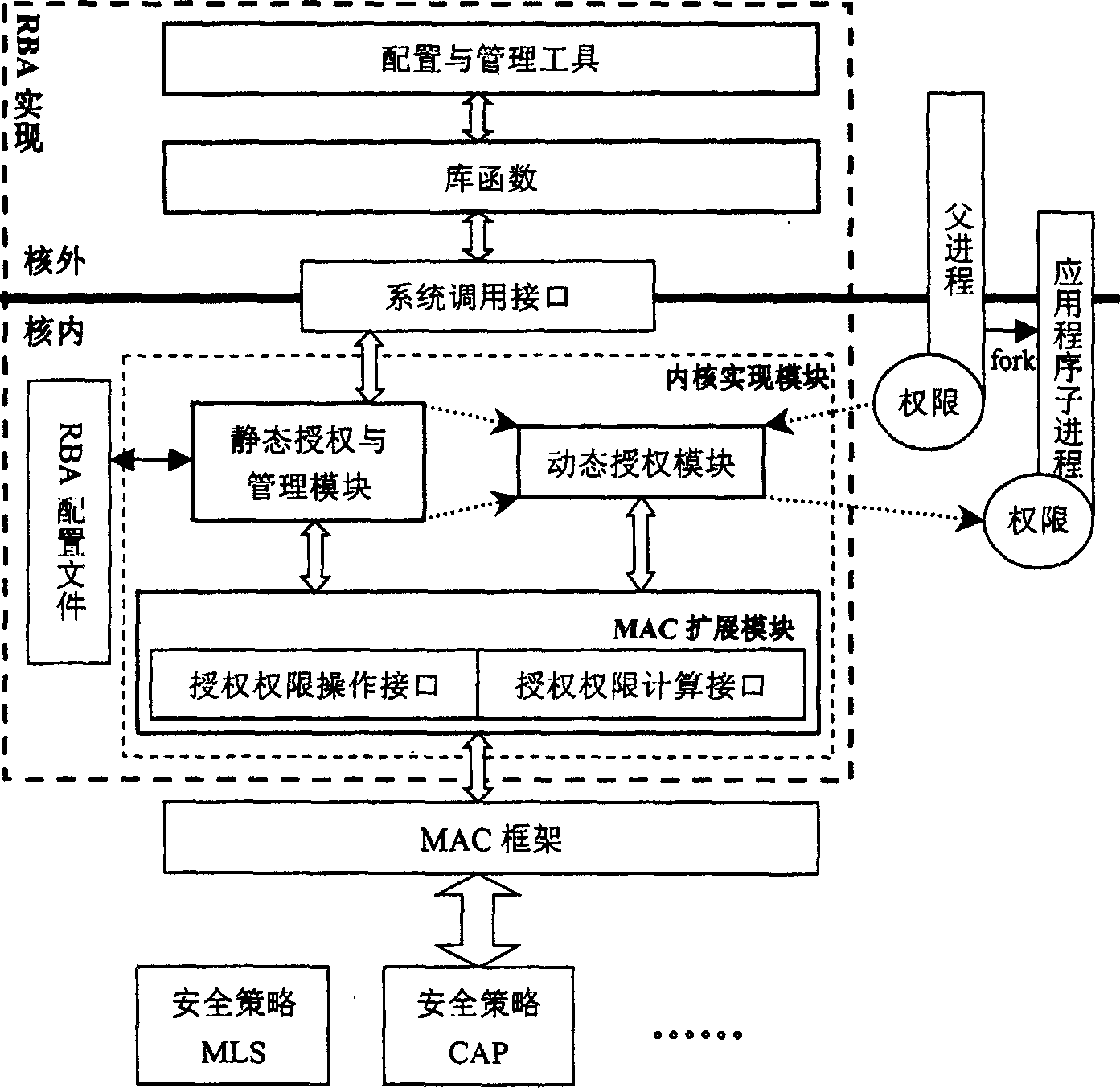
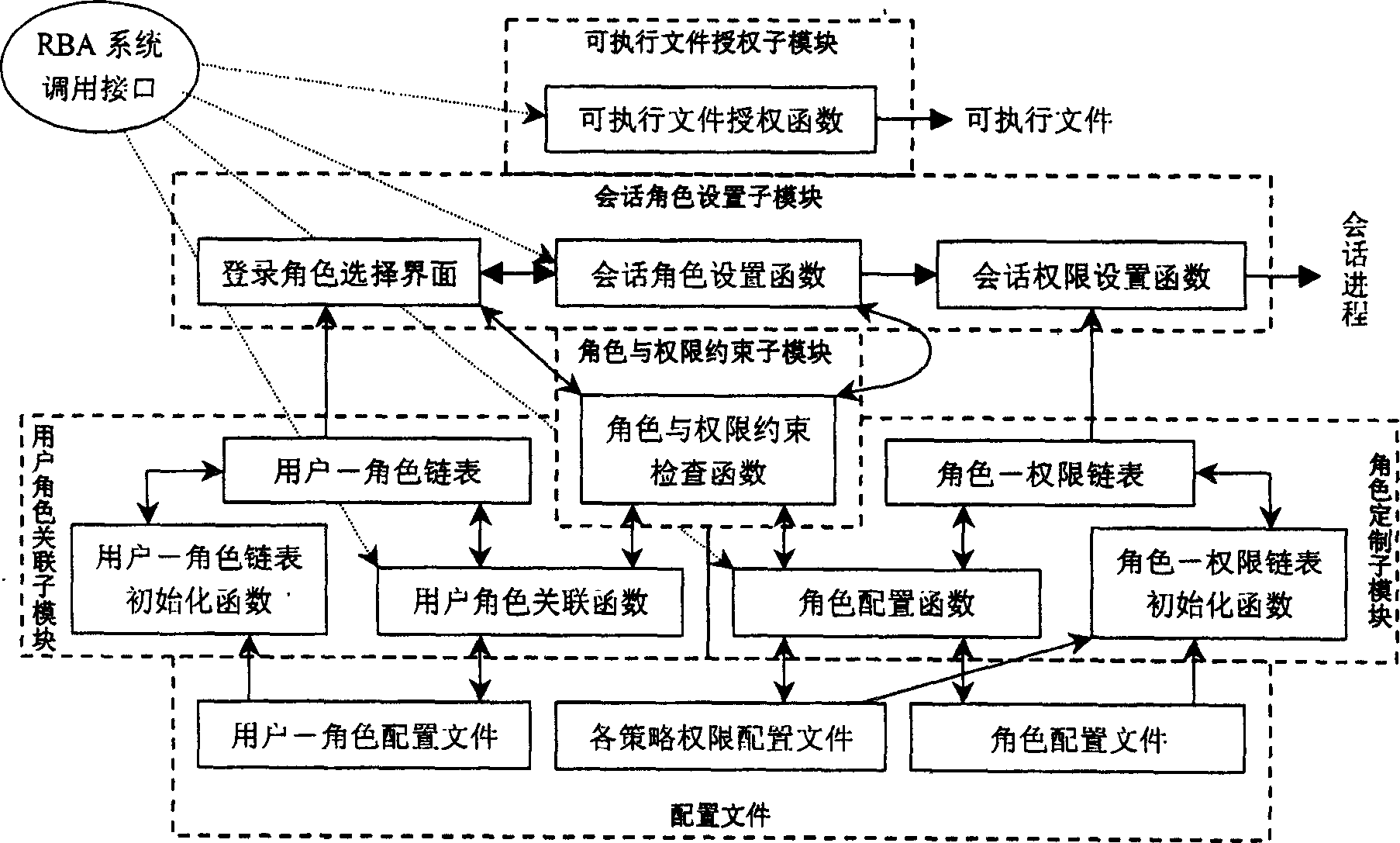
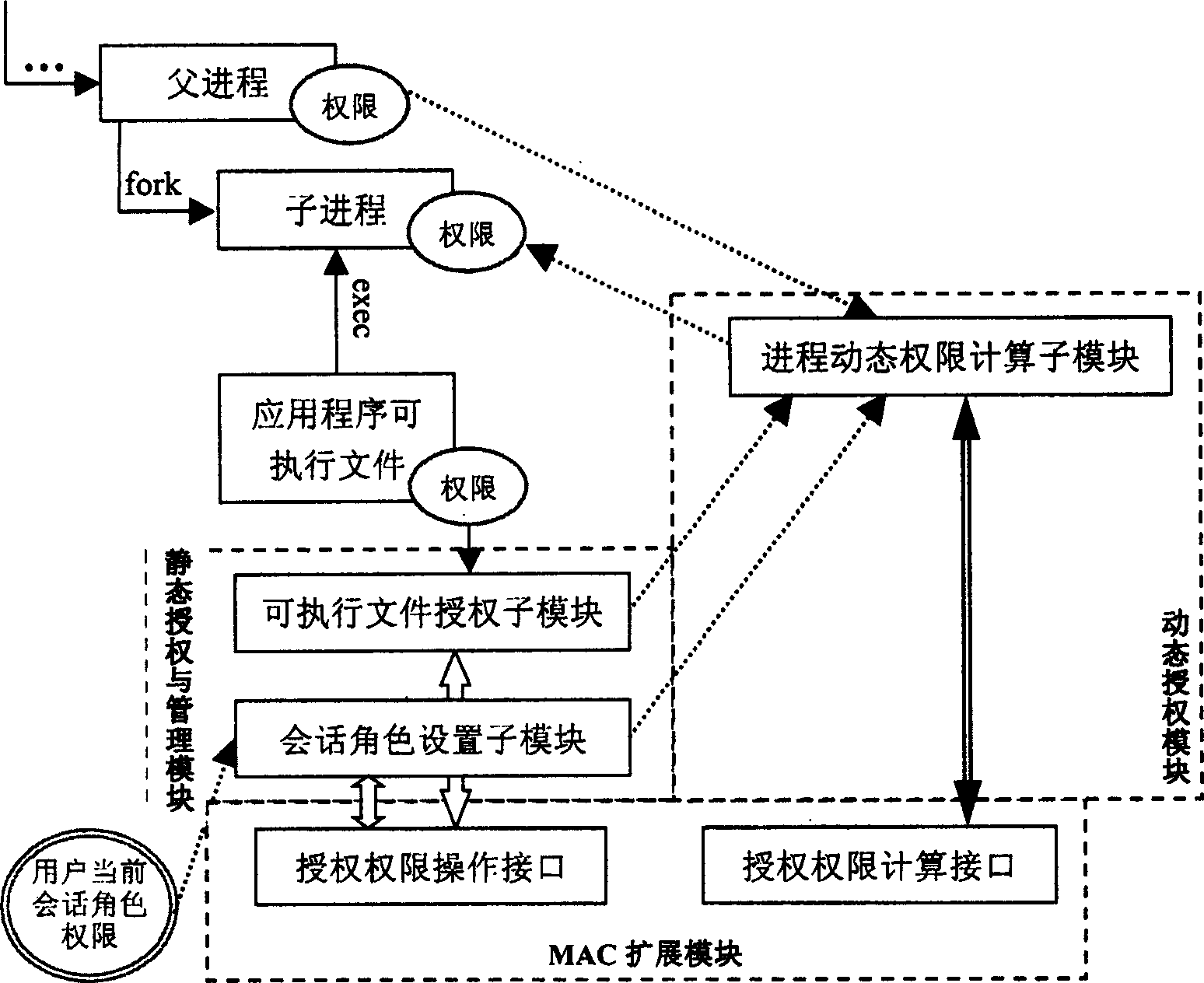
The present invention discloses an actor authority defining method. Its technical scheme includes the following contents: on the forced access frame MAC of operation system constructing a RBA implement system to make authorization for main body in safety operation system adopting forced access control MAC mechanism and configure management. The RBA implement system is formed from internal kernel implement module, RBA configuration file, system calling interface, library function and configuration and management tool. Besides, said invention also provides the concrete implement steps of said method by adopting said RBA implement system.
Owner:NAT UNIV OF DEFENSE TECH
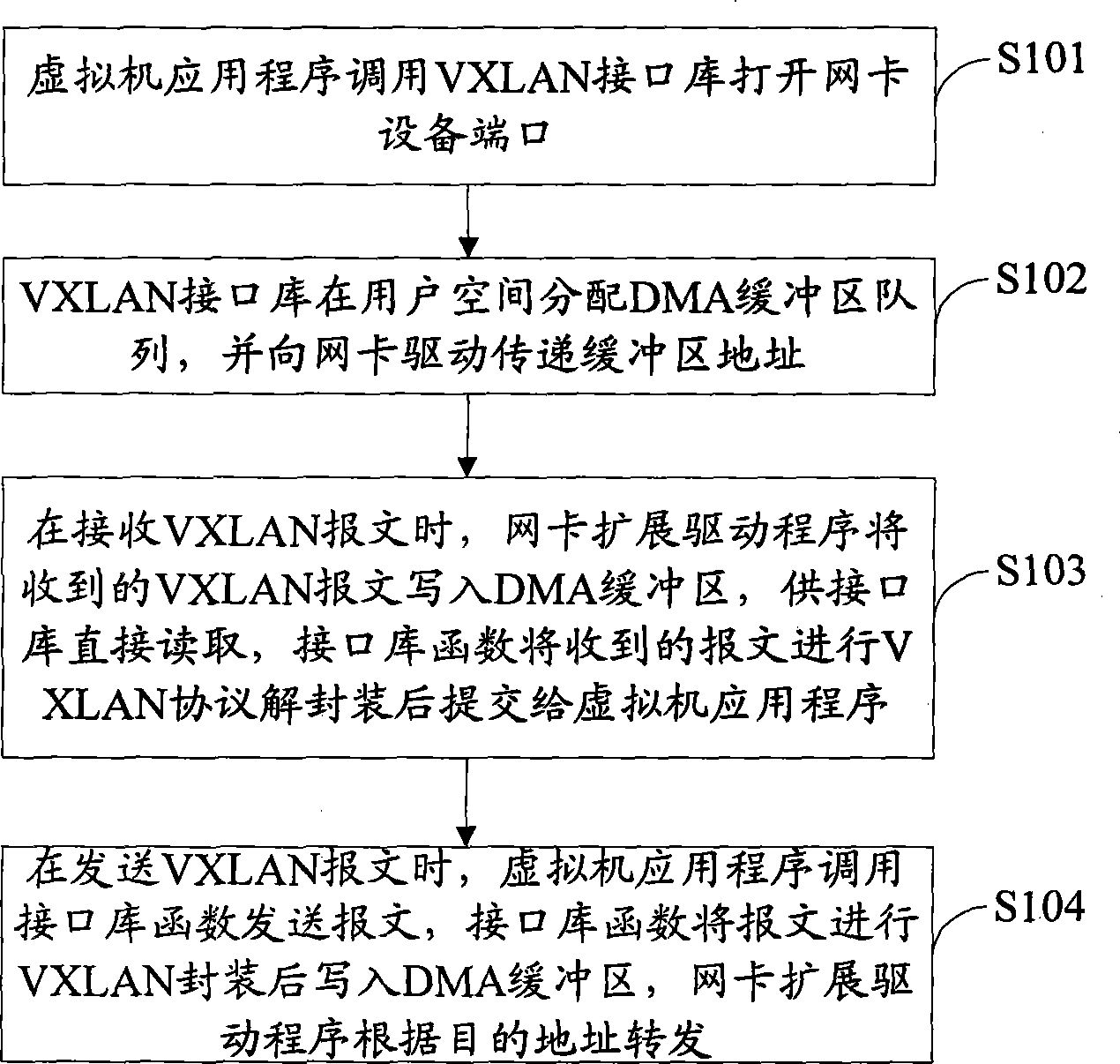
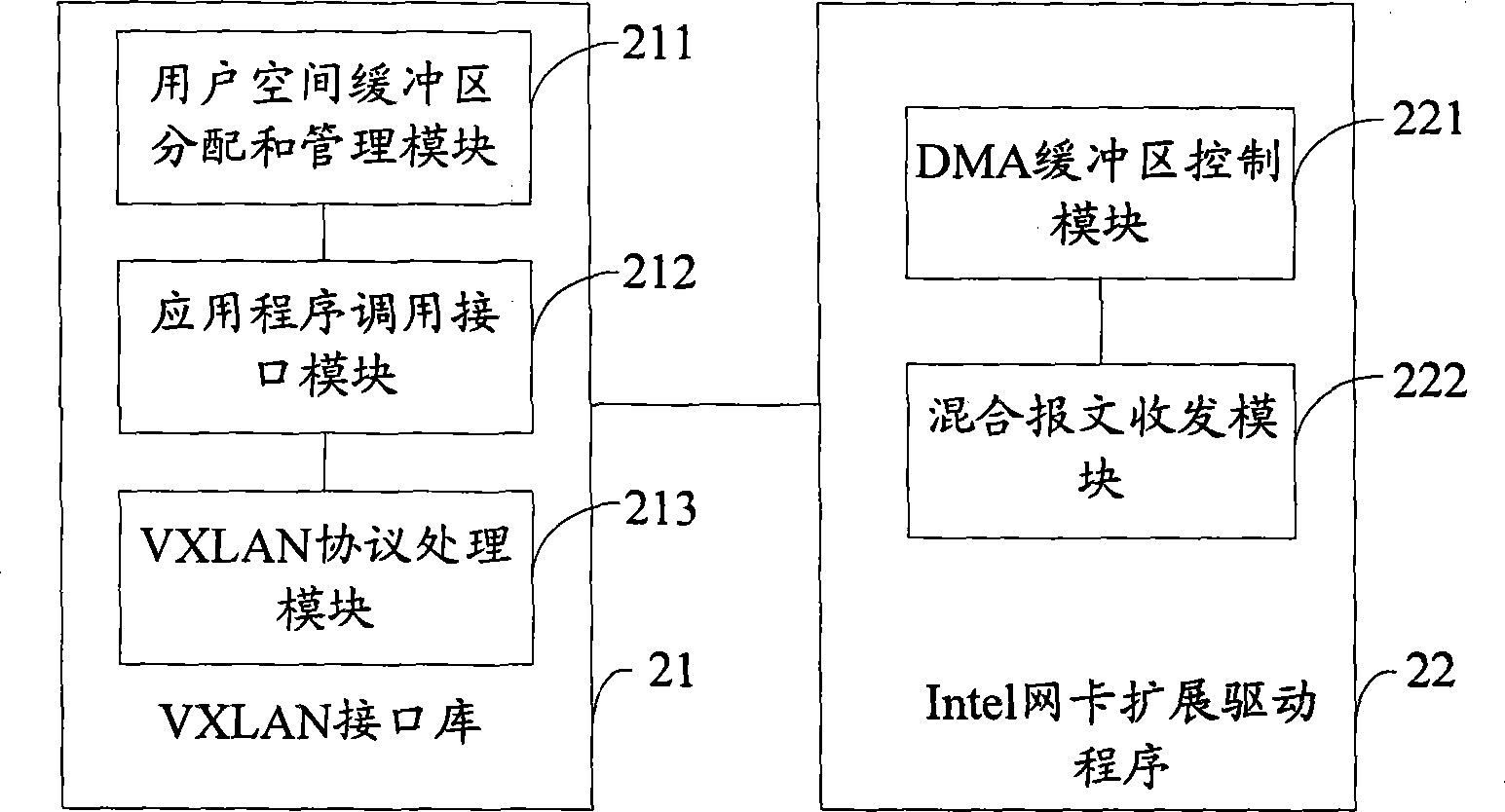
Method and system for achieving transmission and receiving of VXLAN message line speed
The invention belongs to the field of network data processing, and provides a method and a system for achieving transmission and receiving of VXLAN message line speed. The method comprises the steps that a virtual machine application program calls a VXLAN interface library to open a network card device port, the VXLAN interface library distributes direct memory access (DMA) buffer area queues in user space, and transmits an address of a buffer area to a network card driver, a network card extension drive program writes a received VXLAN message in the DMA buffer area, an interface library function conducts VXLAN agreement de-encapsulation to the received message and submits the message to the virtual machine application program, the virtual machine application program calls the interface library function to sent the message, the interface library function conducts VXLAN encapsulation to the message and writes the message in the DMA buffer area, and the network card extension drive program transmits the message according to a target address. According to the method and the system for achieving the transmission and the receiving of the VXLAN message line speed, real-time processing to the VXLAN message is achieved in a cloud computing environment and cost of VXLAN message processing is effectively lowered on the premise that hardware equipment is not exchanged.
Owner:西安乘祥科技有限公司
Graphics processing apparatus, graphics library module and graphics processing method
ActiveUS8149242B2Increase flexibilityImprove efficiencyImage data processing detailsImage generationGraphicsMain processing unit
Owner:SONY COMPUTER ENTERTAINMENT INC
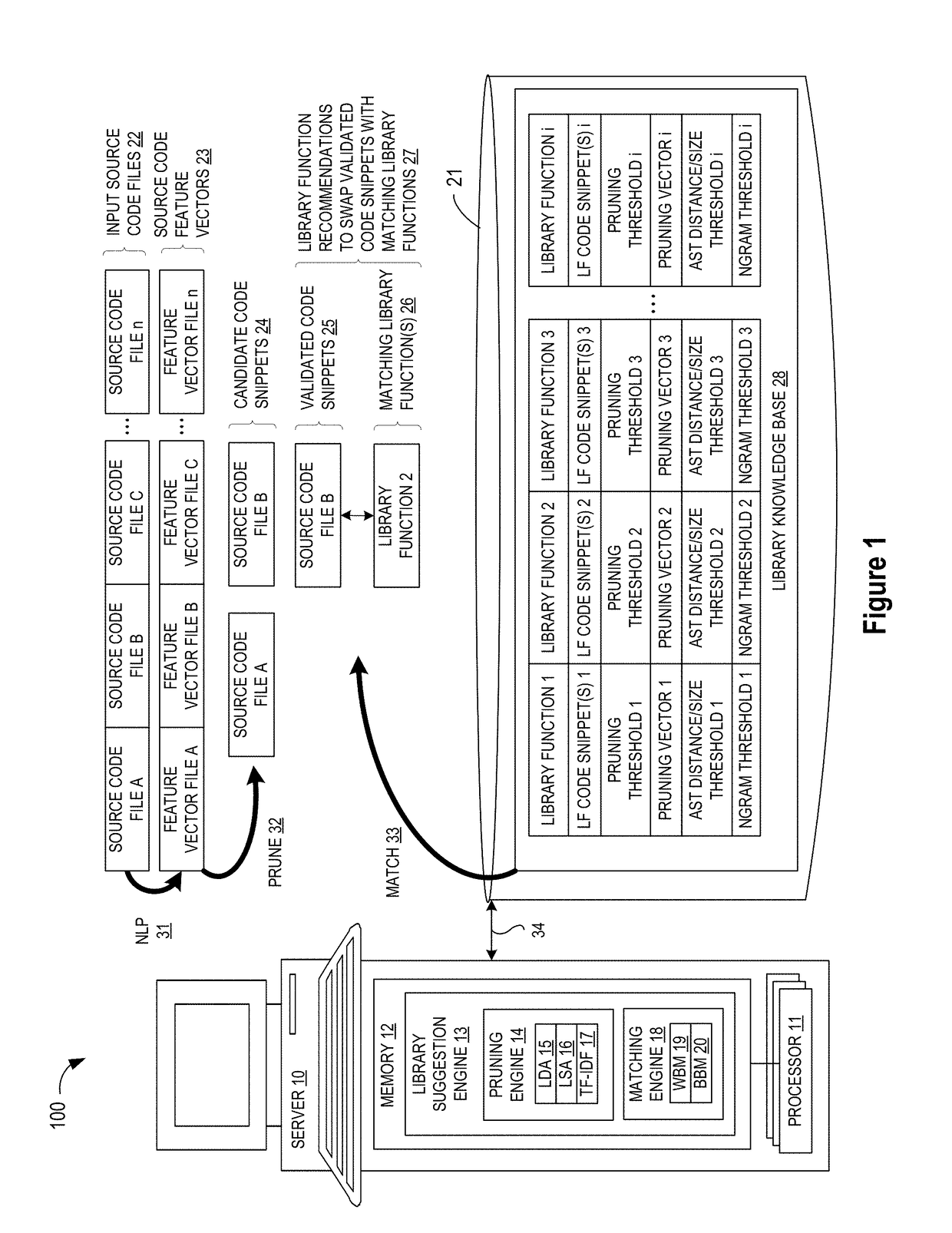
Blackbox matching engine
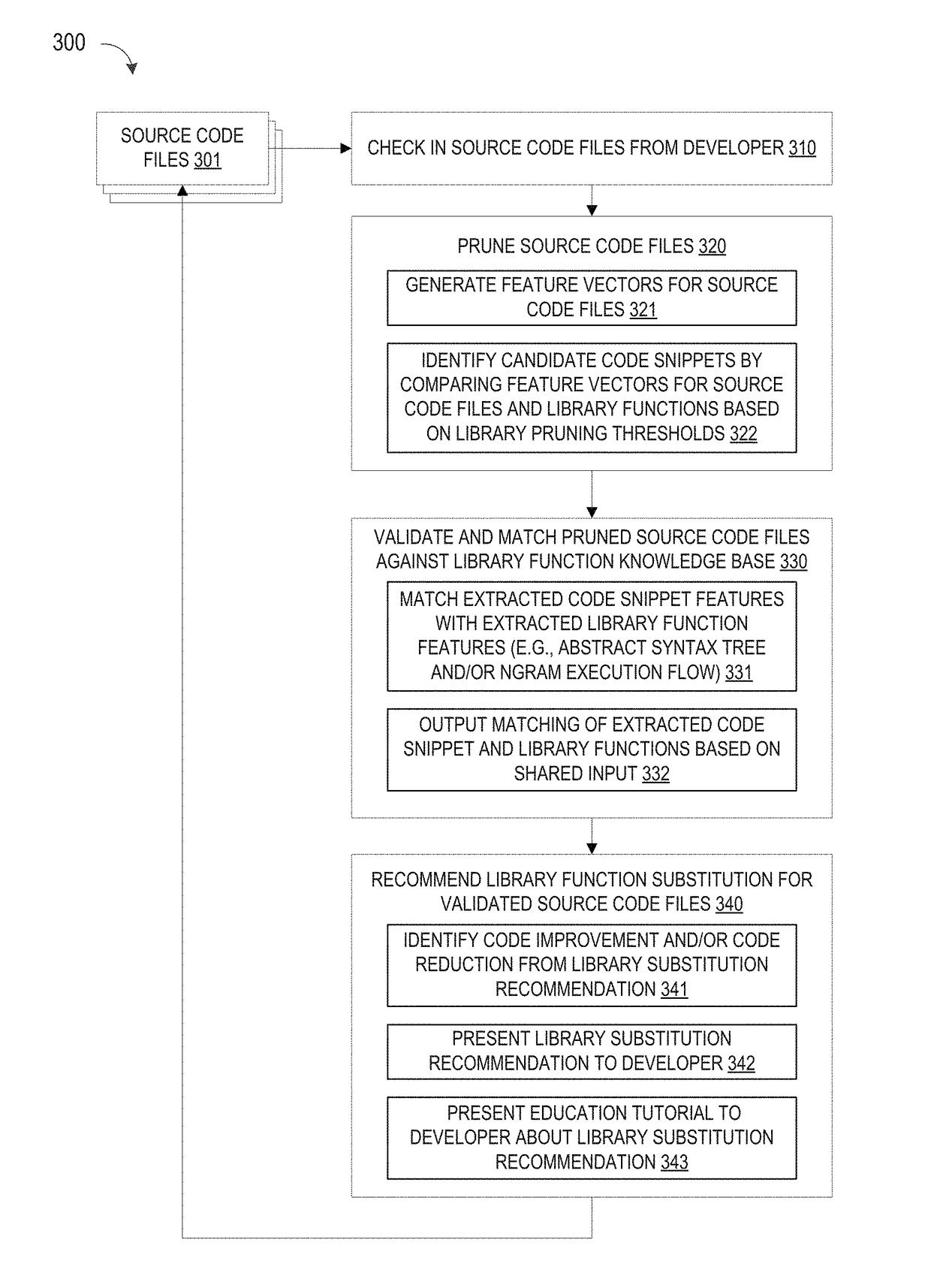
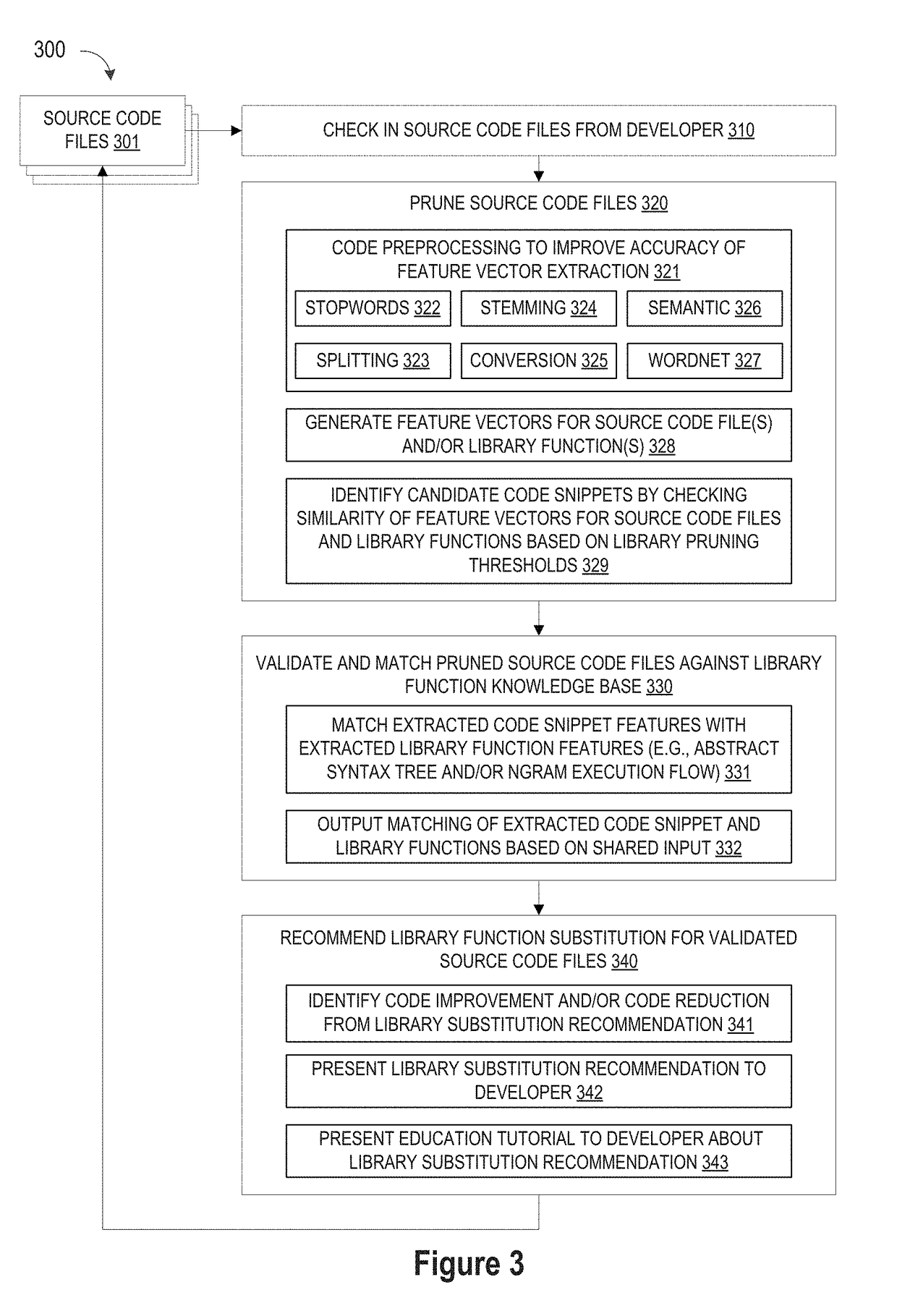
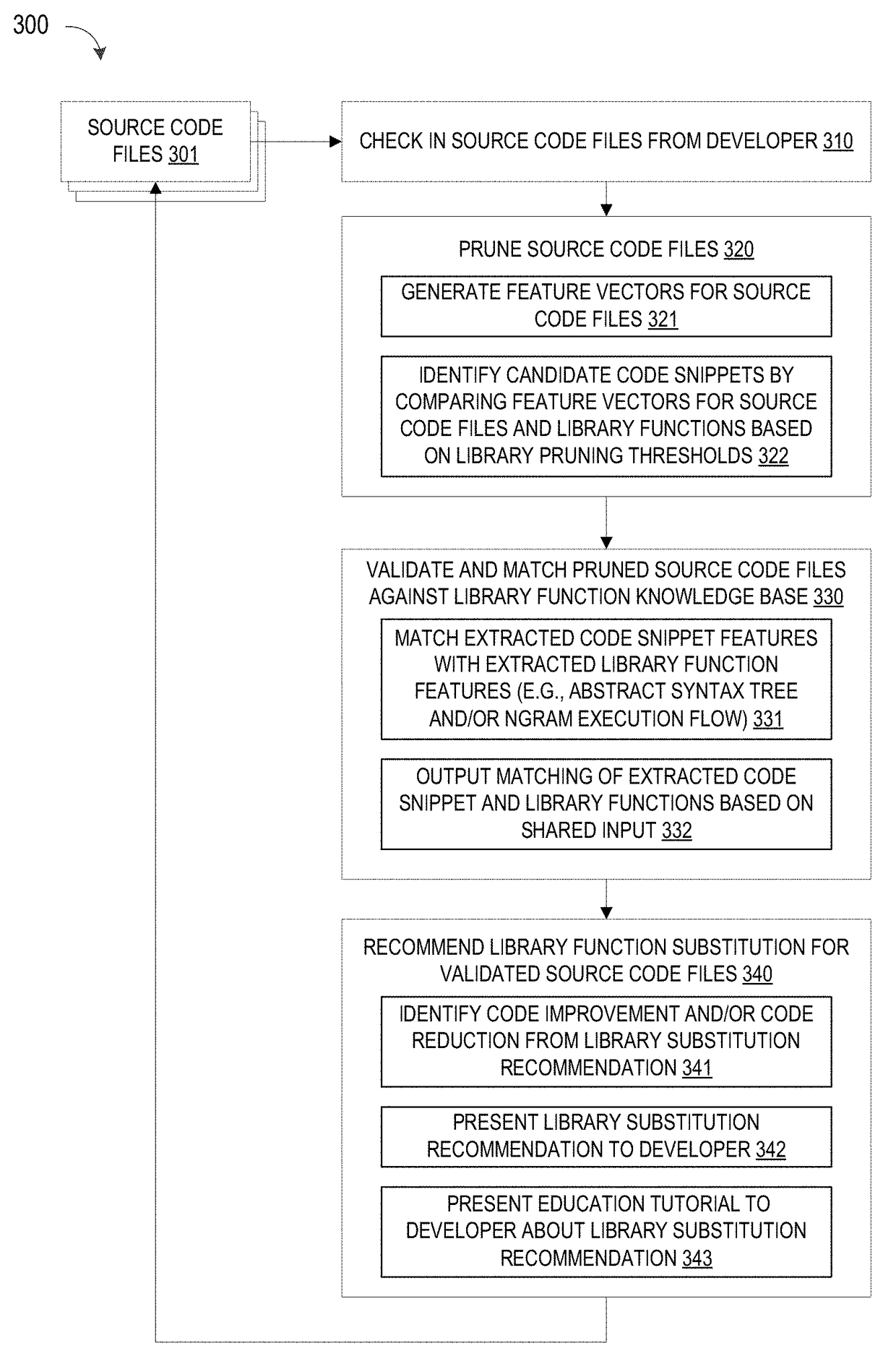
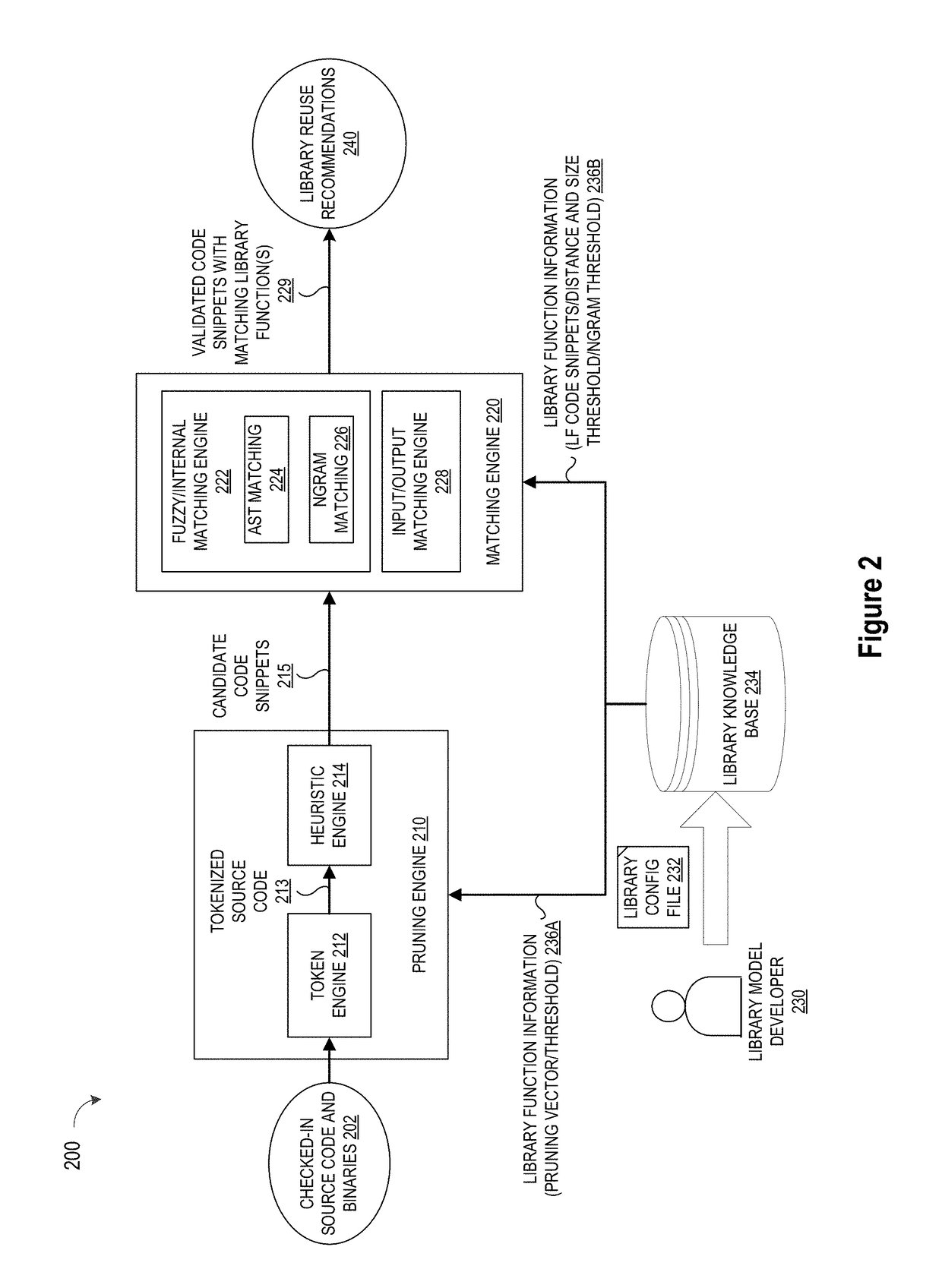
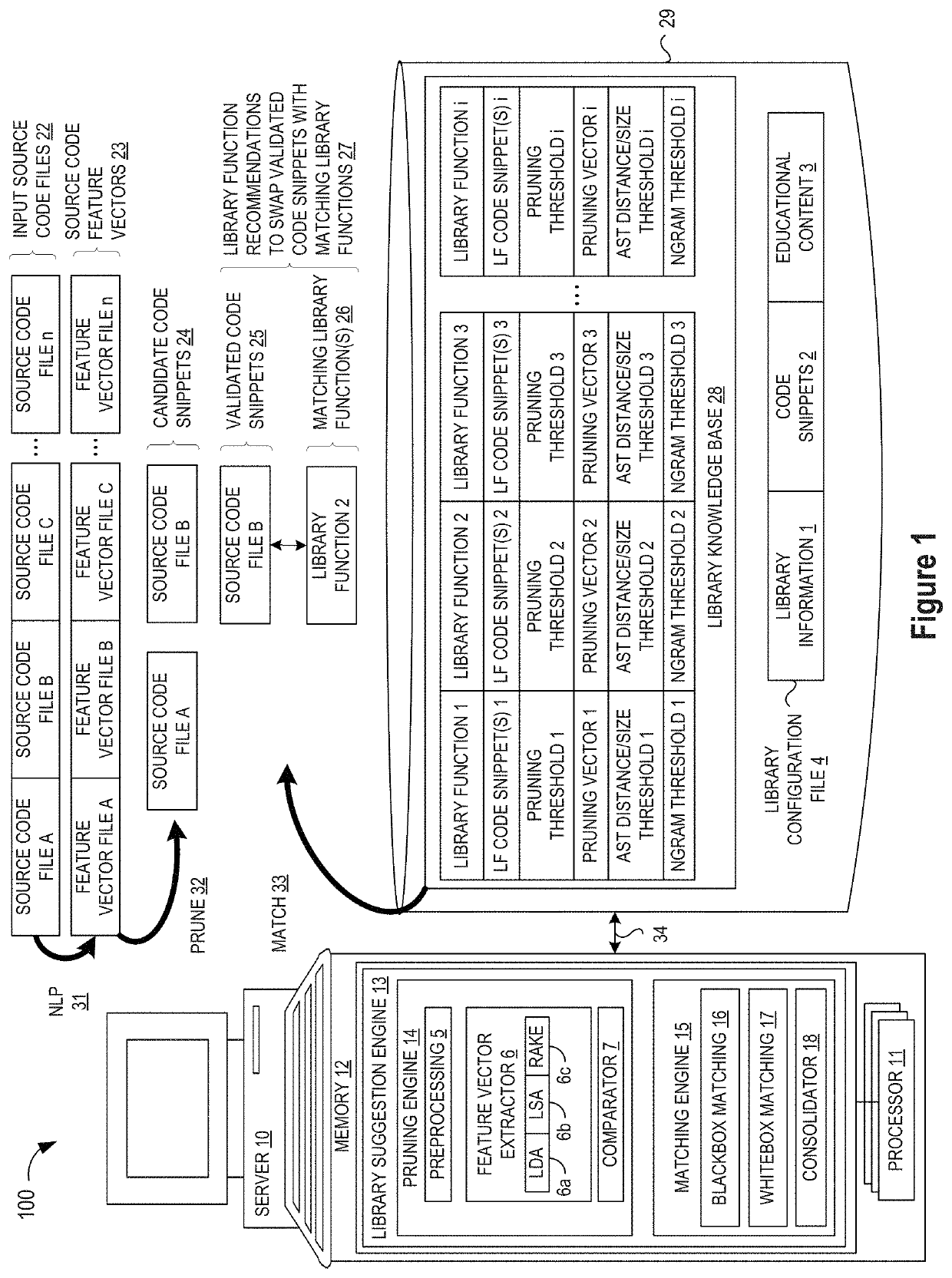
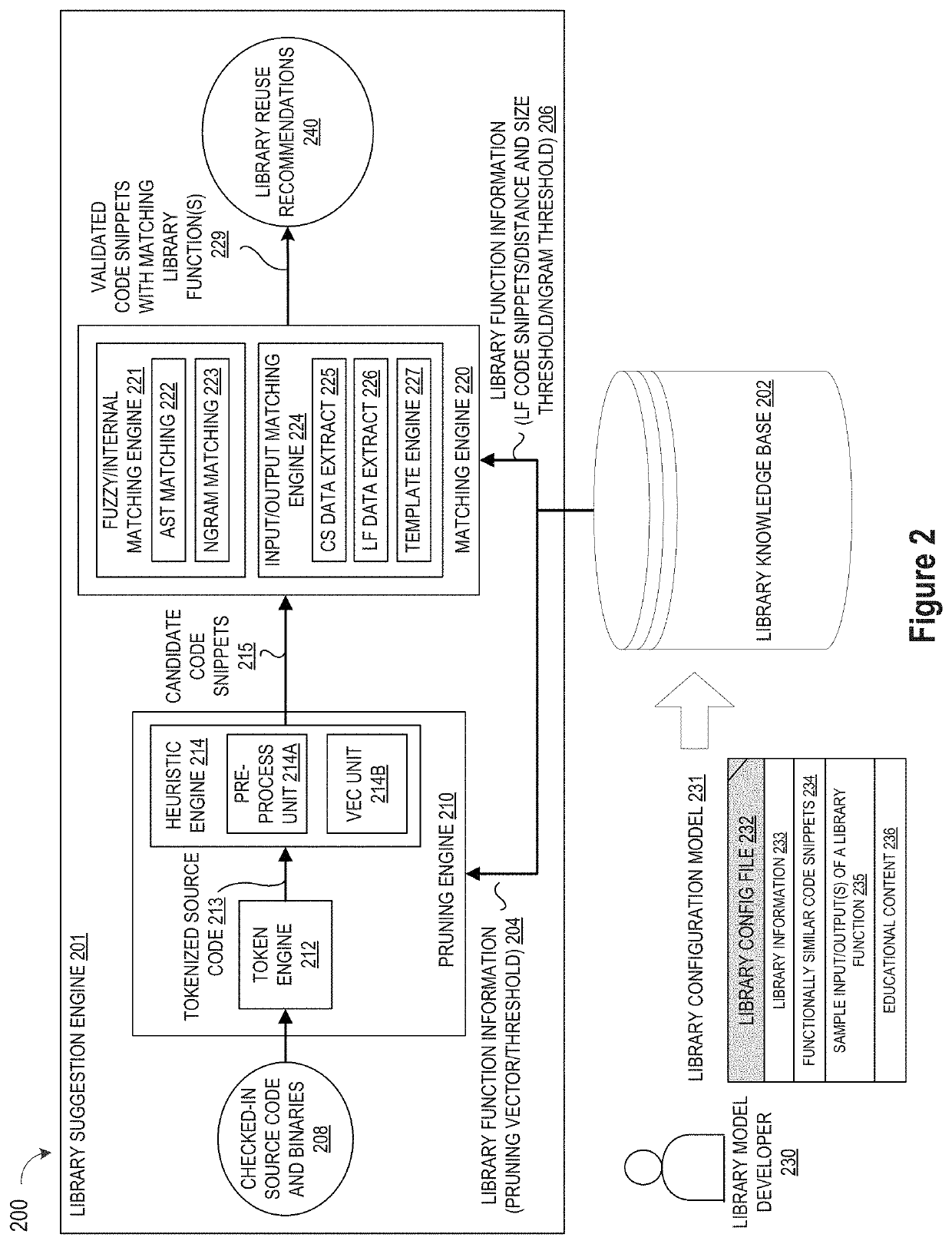
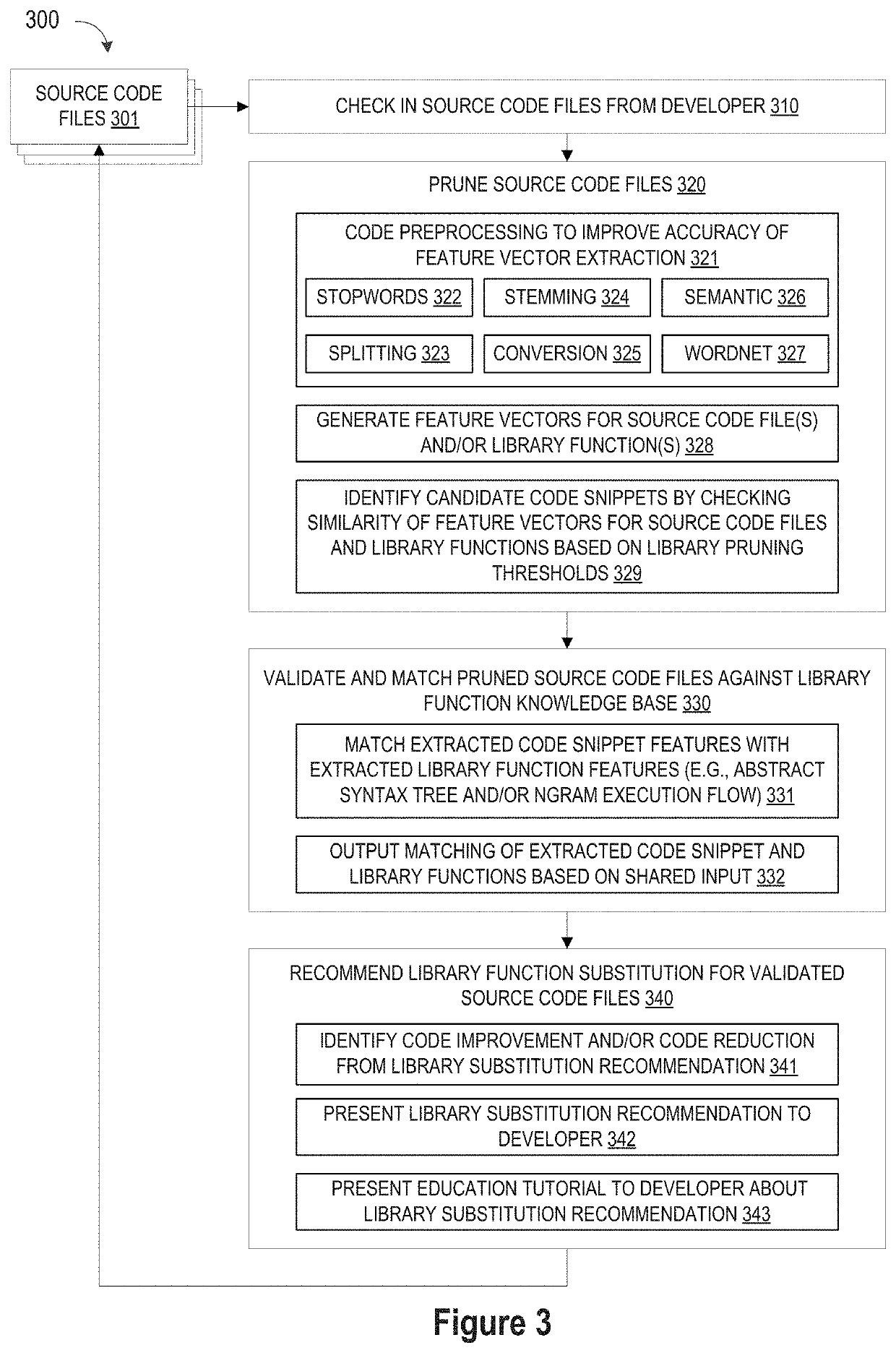
ActiveUS10114624B1Improve code reuseImproving codebase maintainabilityConditional code generationError detection/correctionSource code fileCode snippet
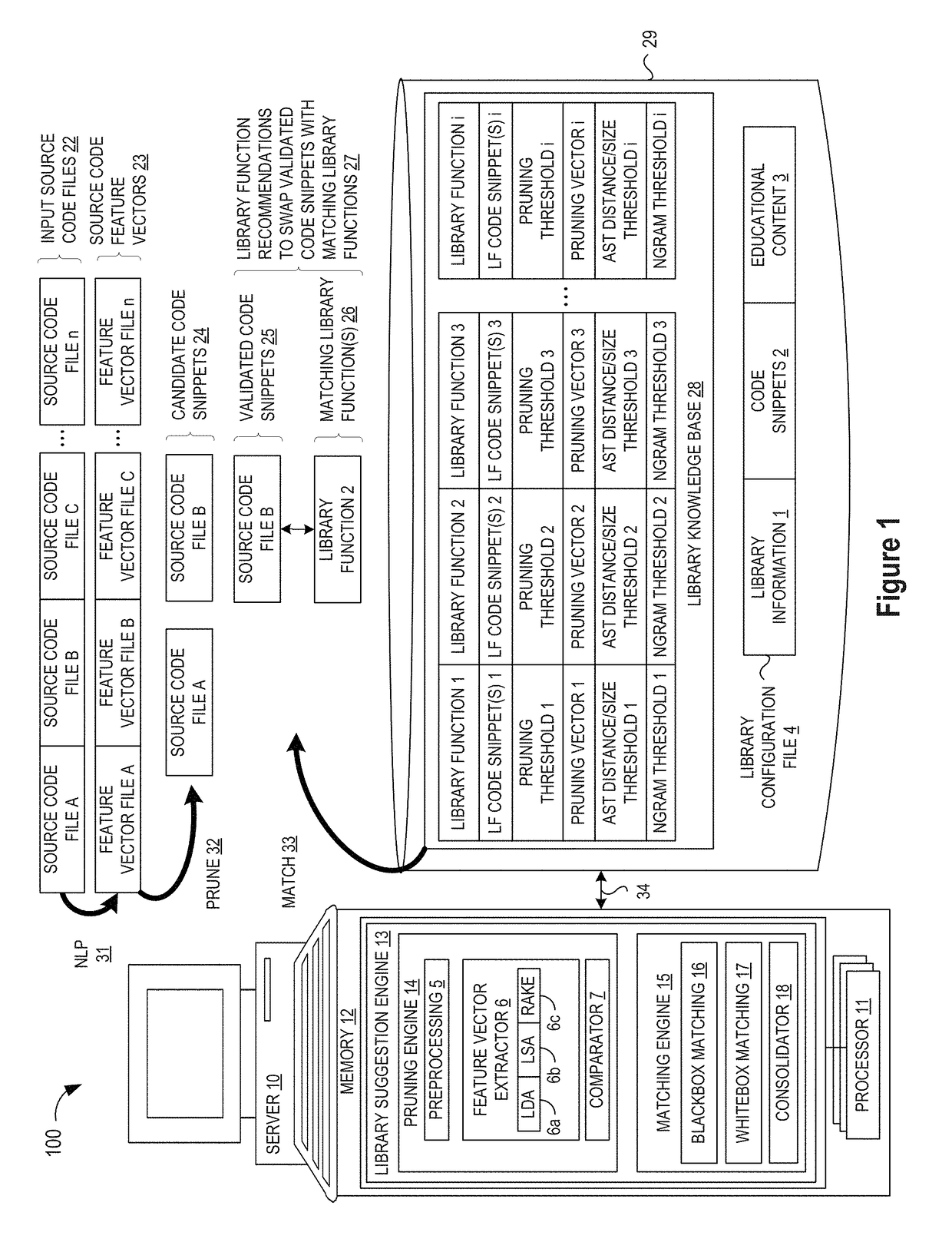
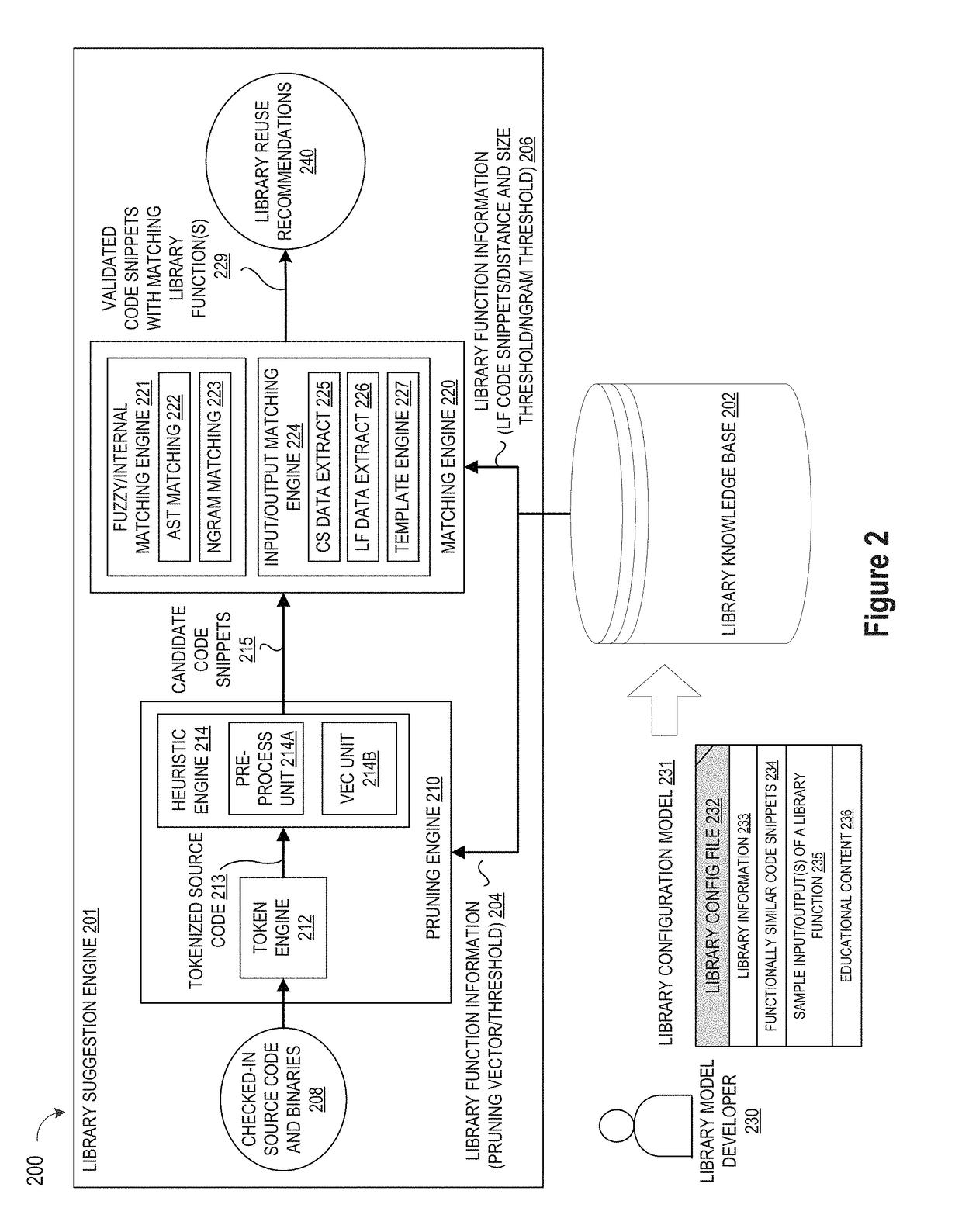
A method and apparatus are disclosed for enhancing operable functionality of input source code files from a software program by identifying a first code snippet and a first library function which generate similar outputs from a shared input by parsing each and every line of code in a candidate code snippet to generate a templatized code snippet data structure for the first code snippet, and then testing the templatized code snippet data structure against extracted library function information to check for similarity of outputs between the first code snippet and the first library function in response to a shared input so that the developer is presented with a library function recommendation which includes the first code snippet, the first library function, and instructions for replacing the first code snippet with the first library function.
Owner:DEVFACTORY INNOVATIONS FZ LLC
Continuous run-time validation of program execution: a practical approach
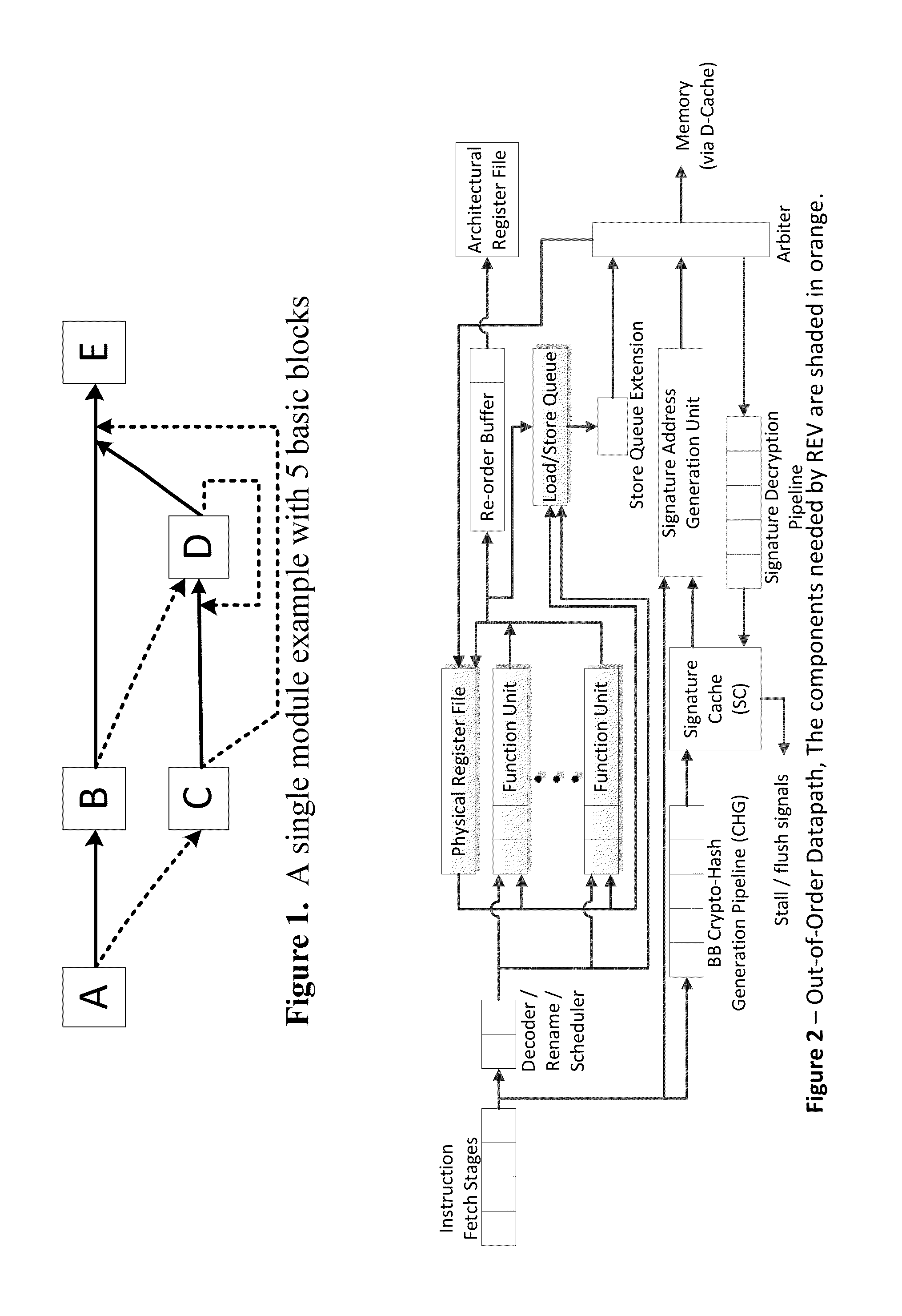
ActiveUS20140082329A1Easy to modifyGuaranteed CompatibilityError detection/correctionDigital computer detailsControl flowReal time validation
Trustworthy systems require that code be validated as genuine. Most systems implement this requirement prior to execution by matching a cryptographic hash of the binary file against a reference hash value, leaving the code vulnerable to run time compromises, such as code injection, return and jump-oriented programming, and illegal linking of the code to compromised library functions. The Run-time Execution Validator (REV) validates, as the program executes, the control flow path and instructions executed along the control flow path. REV uses a signature cache integrated into the processor pipeline to perform live validation of executions, at basic block boundaries, and ensures that changes to the program state are not made by the instructions within a basic block until the control flow path into the basic block and the instructions within the basic block are both validated.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
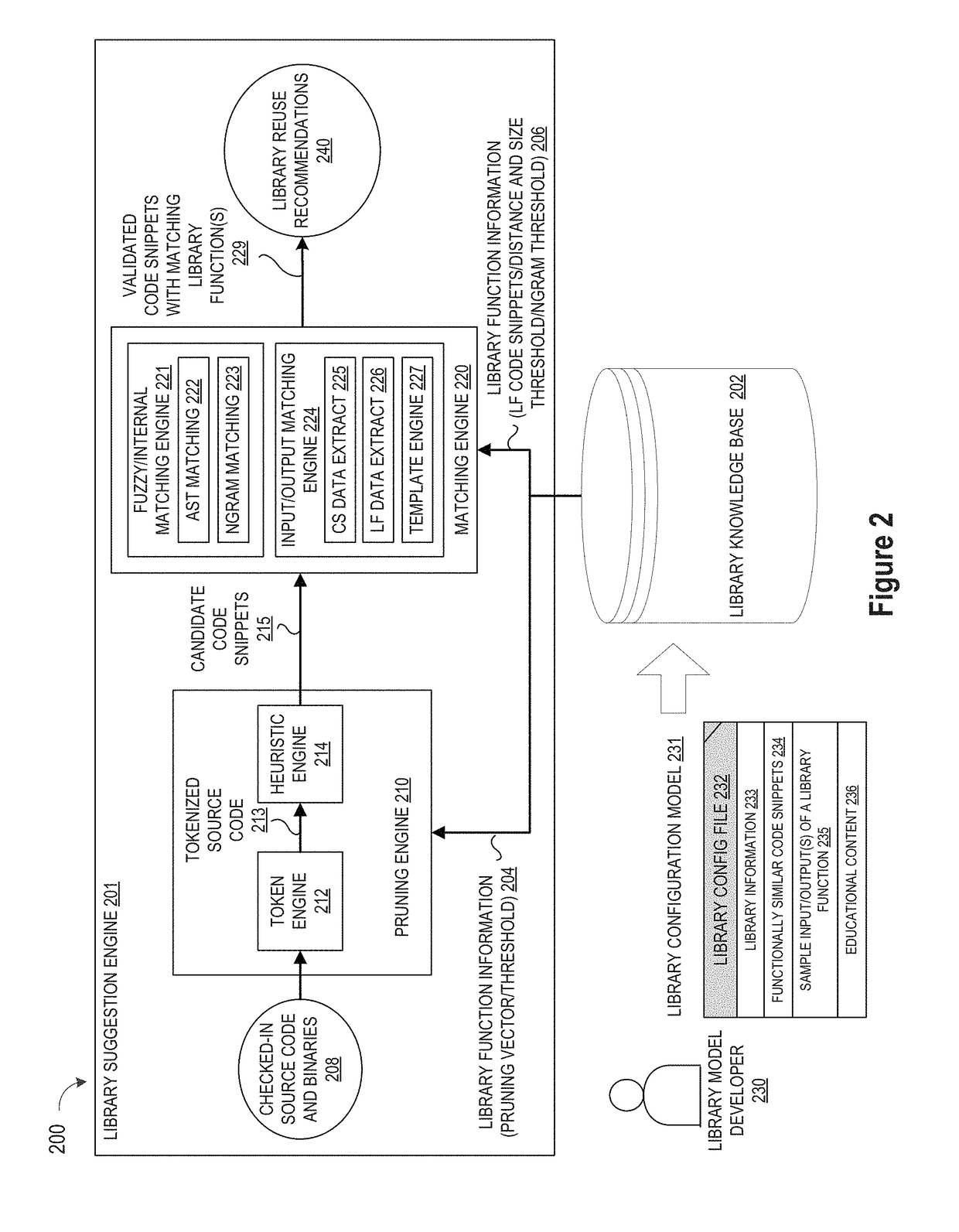
Pruning Engine
ActiveUS20190079741A1Improve code reuseImprove accuracyVersion controlCode refactoringCode snippetSource code file
A method and apparatus are disclosed for enhancing operable functionality of input source code files from a software program by preprocessing input source code files with codeword processing operations to generate a plurality of preprocessed input source code files, identifying candidate code snippets by pruning one or more preprocessed input source code files that do not meet a similarity threshold measure for library functions stored in the system library, and identifying at least a first validated code snippet from the one or more candidate code snippets that matches a first library function stored in the system memory on the basis of at least first and second matching metrics.
Owner:DEVFACTORY INNOVATIONS FZ LLC
Distributed network node operation system based on operation control unit
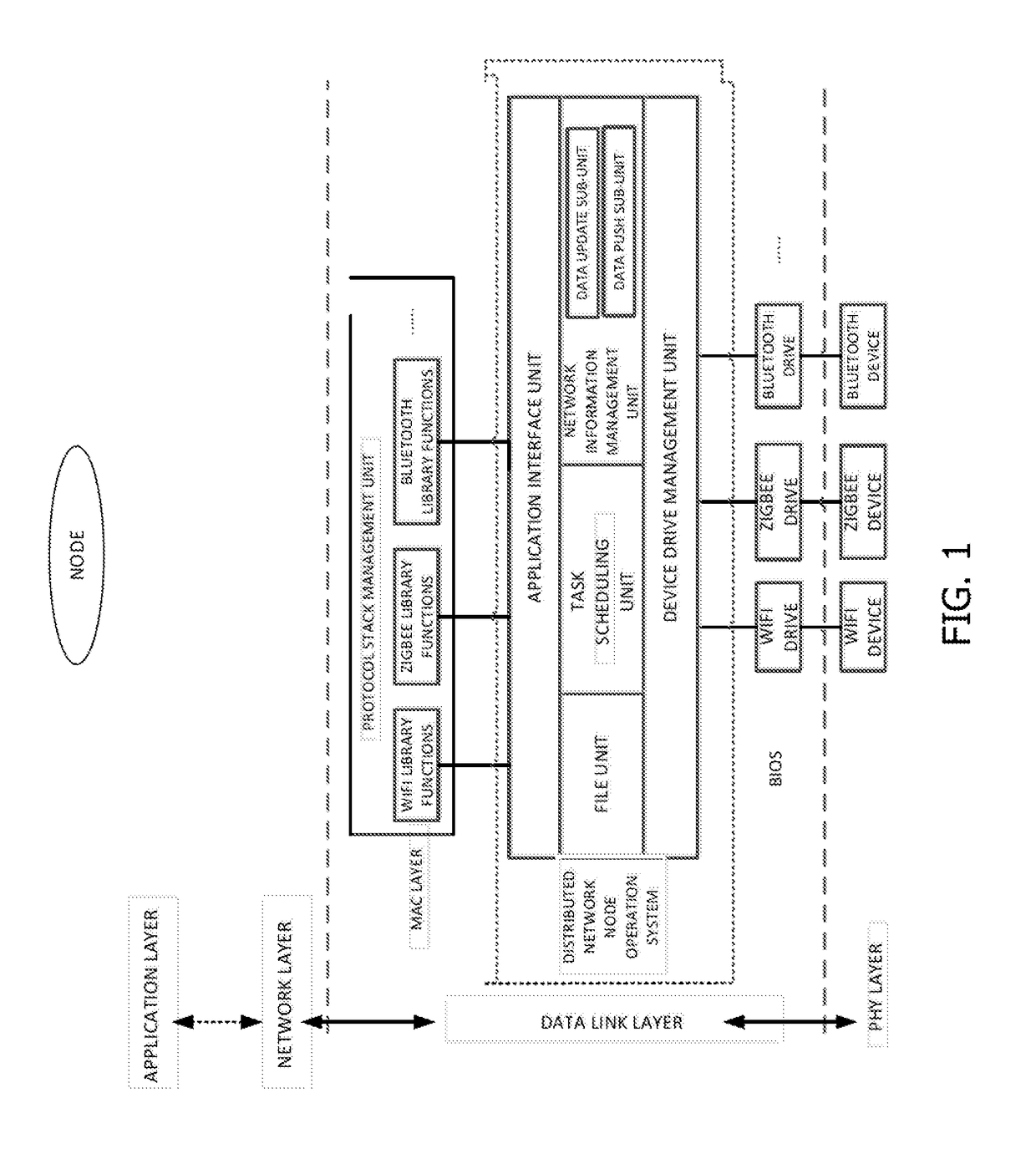
ActiveUS20170195406A1Easy for secondary developmentFacilitating improvementProgram initiation/switchingResource allocationOperational systemManagement unit
A distributed network node operation system based on an operation control unit. The operation system operates on a network node and interacts with a data link layer, and includes: an application interface unit, a network information management unit, a file unit, a task scheduling unit and a device drive management unit. The application interface unit packages the services provided by the file unit, the task scheduling unit and the network information management unit into an interface for interacting with the protocol stack management unit; the network information management unit interacts with the data link layer to perform link scheduling for transmitting information and updating node data; the file unit manages and stores file information; the task scheduling unit manages hardware resources; the device drive management unit manages underlying device application drives, and invokes different protocol stack library functions through different application drives.
Owner:CHONGQING GKTSINGCHIP SMARTCONET TECH CO LTD
Device power saving during exercise
ActiveUS20150293580A1Operation mode is limitedPhysical therapies and activitiesPower supply for data processingComputer hardwareOperation mode
A method includes: supporting a normal operation mode during which functionalities of a portable apparatus are available through an operating system of the apparatus, wherein the operating system includes a plurality of layers including a kernel and library functions-layer; supporting a limited operation mode during which the apparatus is configured to execute a physical activity algorithm based on physical activity data corresponding to a physical activity session performed by a user of the apparatus, wherein the physical activity algorithm applies a direct low-level hardware access bypassing at least the layers above the kernel and the library functions-layer; and switching between the normal operation mode and the limited operation mode.
Owner:POLAR ELECTRO
Framework for generating mixed-mode operations in loop-level simdization
InactiveUS8549501B2Software engineeringSpecific program execution arrangementsProgram instructionParallel computing
Generating mixed-mode operations in the compilation of program code for processors having vector or SIMD processing units is disclosed. In a preferred embodiment of the present invention, program instructions making up the body of a loop are abstracted into virtual vector instructions. These virtual vector instructions are treated, for initial code optimization purposes, as vector instructions (i.e., instructions written for the vector unit). The virtual vector instructions are eventually expanded into native code for the target processor, at which time a determination is made for each virtual vector instruction as to whether to expand the virtual vector instruction into native vector instructions, into native scalar instructions, into calls to pre-defined library functions, or into a combination of these. A cost model is used to determine the optimal choice of expansion based on hardware / software constraints, performance costs / benefits, and other criteria.
Owner:INT BUSINESS MASCH CORP
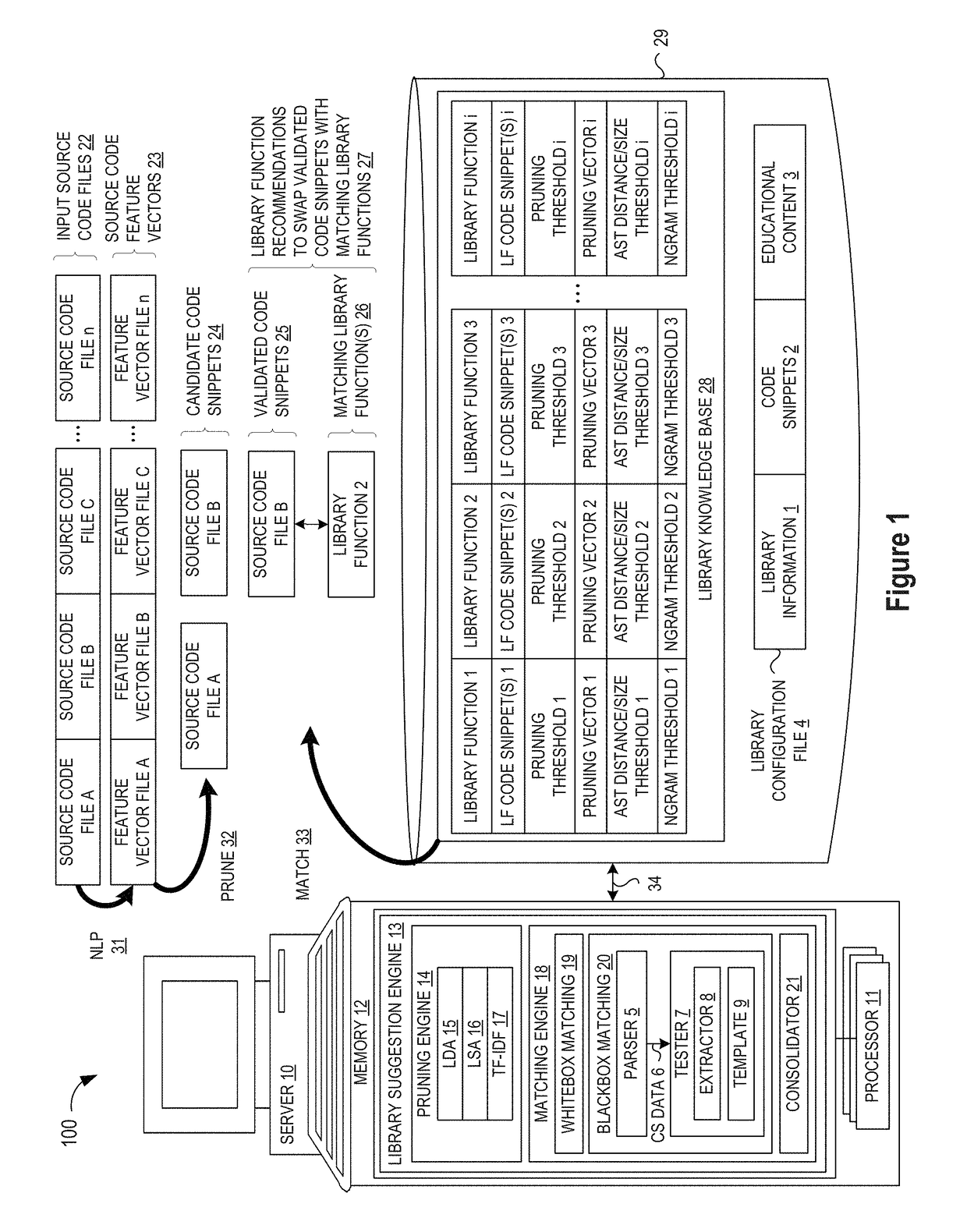
Library suggestion engine
ActiveUS10048945B1Improve code reuseImproving codebase maintainabilityIntelligent editorsSoftware reuseSource code fileCode snippet
A method and apparatus are disclosed for enhancing operable functionality of input source code files from a software program by identifying candidate code snippets from the plurality of input source code files that meet a similarity threshold measure for library functions stored in the system library and then identifying at least a first validated code snippet from the candidate code snippets that matches a first library function stored in the system memory on the basis of at least first and second matching metrics so that the developer is presented with a library function recommendation which includes the first validated code snippet, the first library function, and instructions for replacing the first validated code snippet with the first library function.
Owner:DEVFACTORY INNOVATIONS FZ LLC
Method and apparatus for generating service frameworks
InactiveUS7617479B2Software designSpecific program execution arrangementsSoftware engineeringApplication software
A method, an apparatus, and computer instructions for generating service frameworks are provided by aspects of the present invention. One aspect of the present invention provides a system library, which includes strongly typed classes that enterprise applications may use in order to obtain code assist and compile time checking from IDE tools typically used by enterprise application developers. Another aspect of the present invention provides the ability to define platform independent models that enable service use cases in order to determine what basic services are needed by the enterprise application. Yet another aspect of the present invention includes an integrated generator that generates the strongly typed components and skeleton code from the platform independent models by applying best practice pattern usage for the target platform currently used with the system library functions.
Owner:IBM CORP +1
Method and apparatus for securing indirect function calls by using program counter encoding
ActiveUS8583939B2Reduce overheadLoad minimizationDigital data processing detailsUnauthorized memory use protectionProgram counterLibrary function
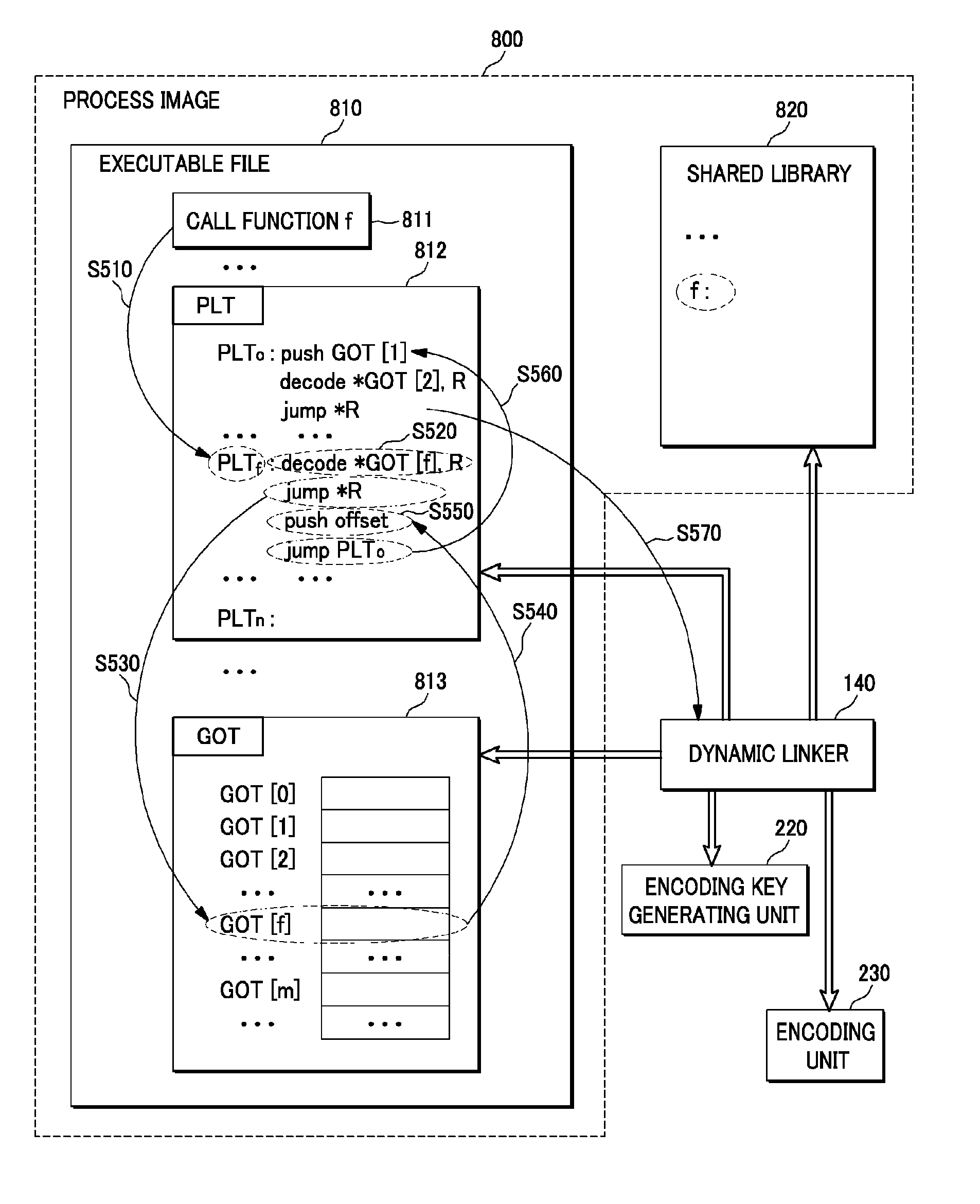
A method for securing indirect function calls by using program counter encoding is provided. The method includes inserting a decoding code for an address of a library function stored in a GOT (Global Offset Table) entry into a PLT (Procedure Linkage Table) entry when an object file is built; generating an encoding key corresponding to the decoding code; and encoding the GOT entry corresponding to the library function by using the encoding key when program execution begins.
Owner:ZEUS SW DEFENDER LLC
APK application reinforcing method and system
InactiveCN103902858ACopyright protectionReduce the possibility of reverse engineeringProgram/content distribution protectionCoding blockReverse analysis
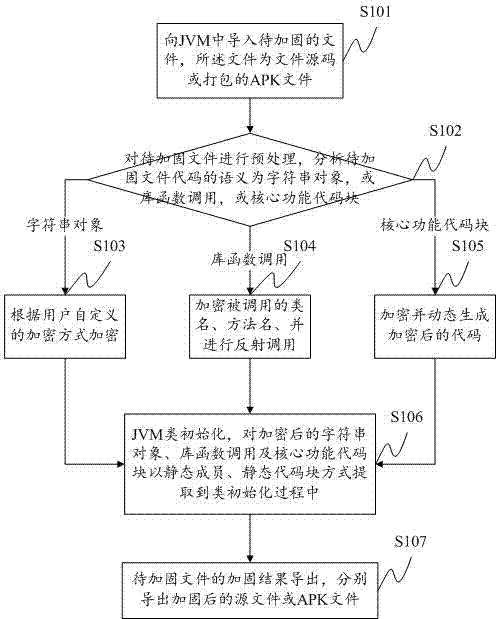
The invention provides an APK application reinforcing method and system. The method comprises the steps of inputting the source code of files to be reinforced or APK files, preprocessing the files to be reinforced, analyzing the semantics, using different encryption ways according to different objects, conducting JVM class initialization processing on the encrypted objects, extracting the encrypted objects to the class initialization process in the modes of static members, static code blocks and the like, and at last outputting a reinforcing result. Through the APK application reinforcing method, APK application programs under the Android can be reinforced, displaying and calling of any cleartext character string or library functions can not occur to a decompilation result, a core code function is hidden, the difficulty of reverse analysis of the APK files is greatly increased, and therefore the effect of protecting the application codes of a developer is achieved.
Owner:WUHAN ANTIY MOBILE SECURITY
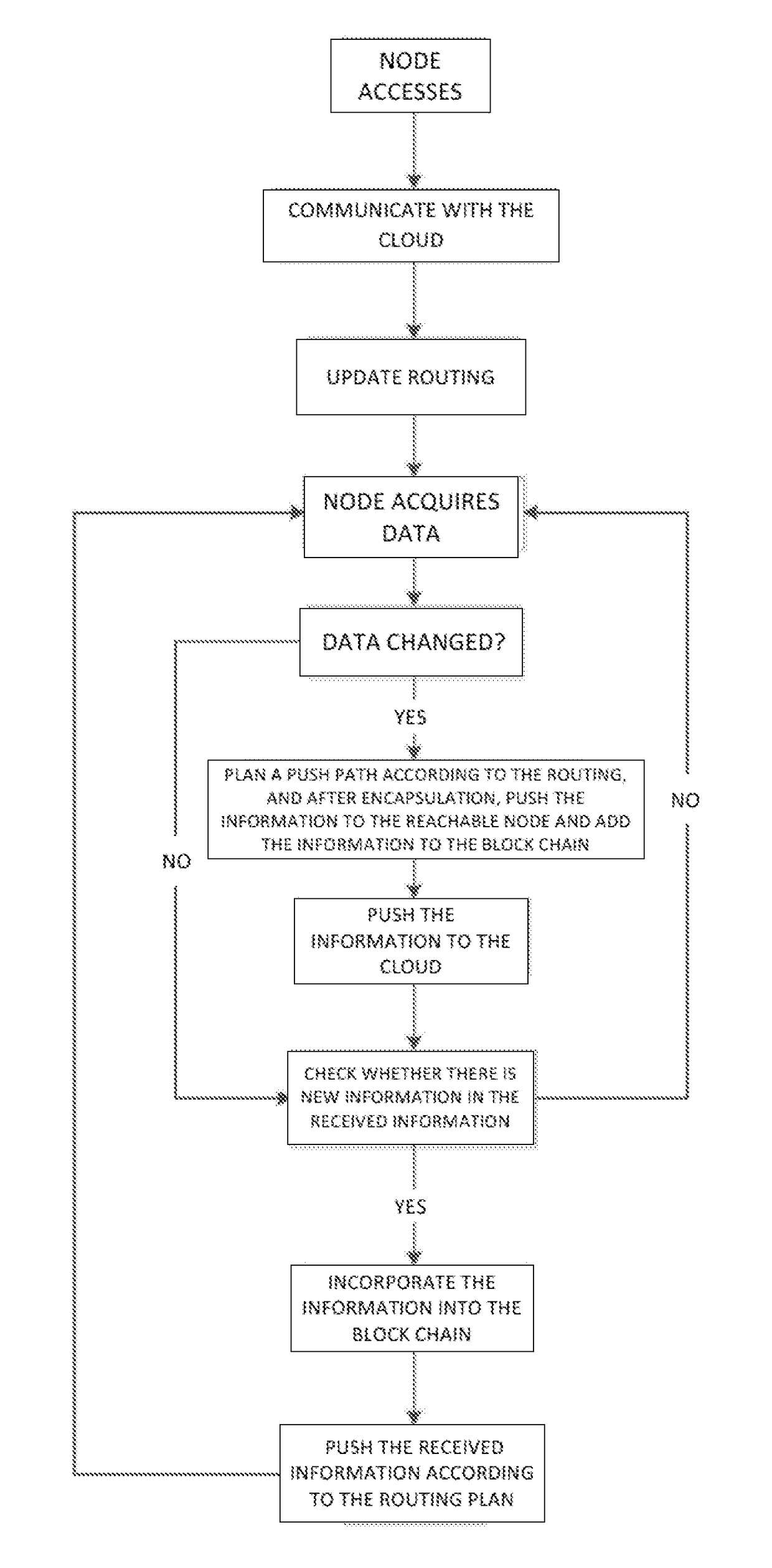
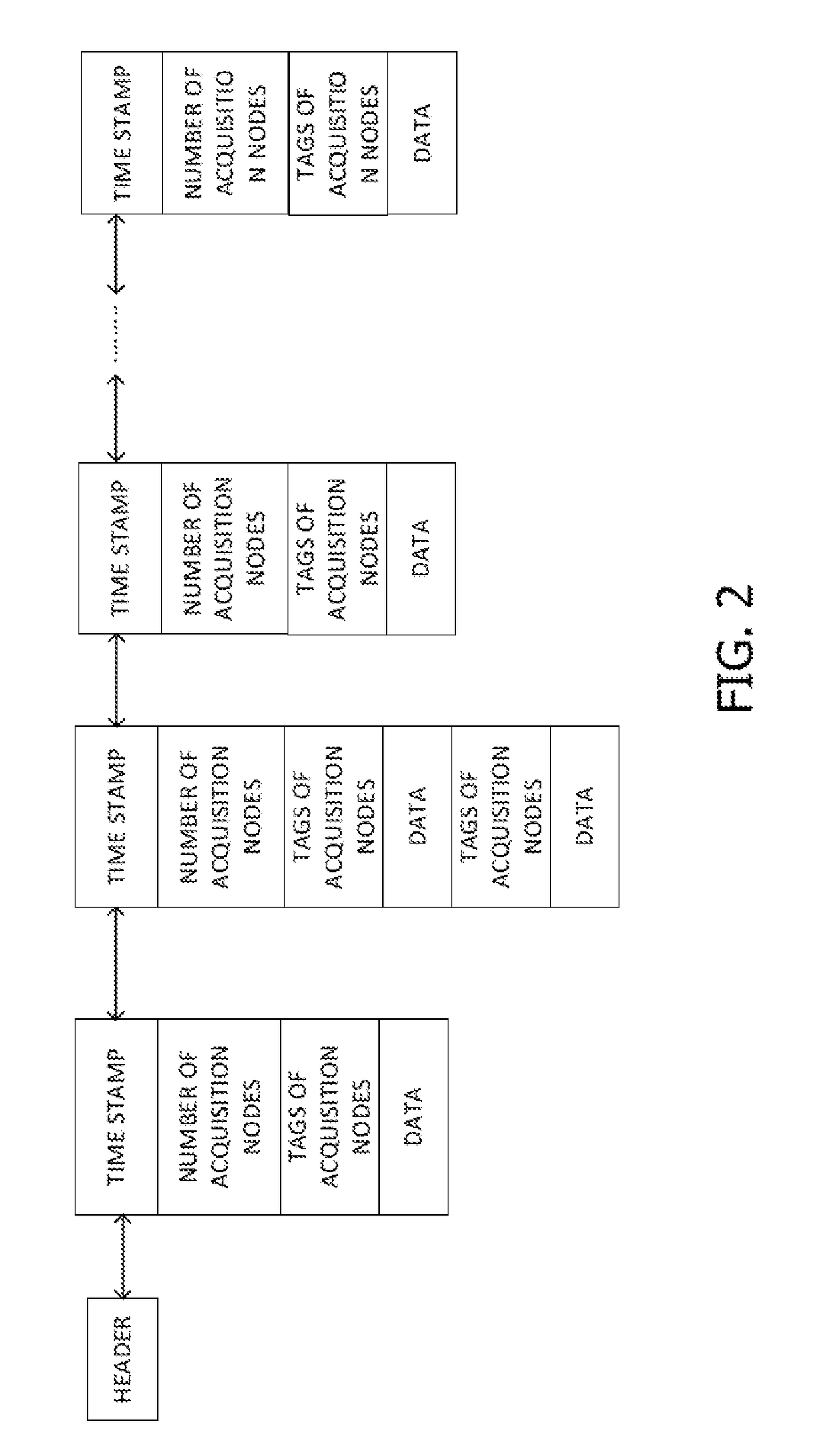
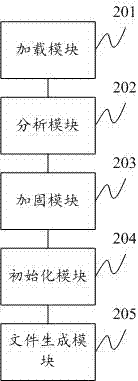
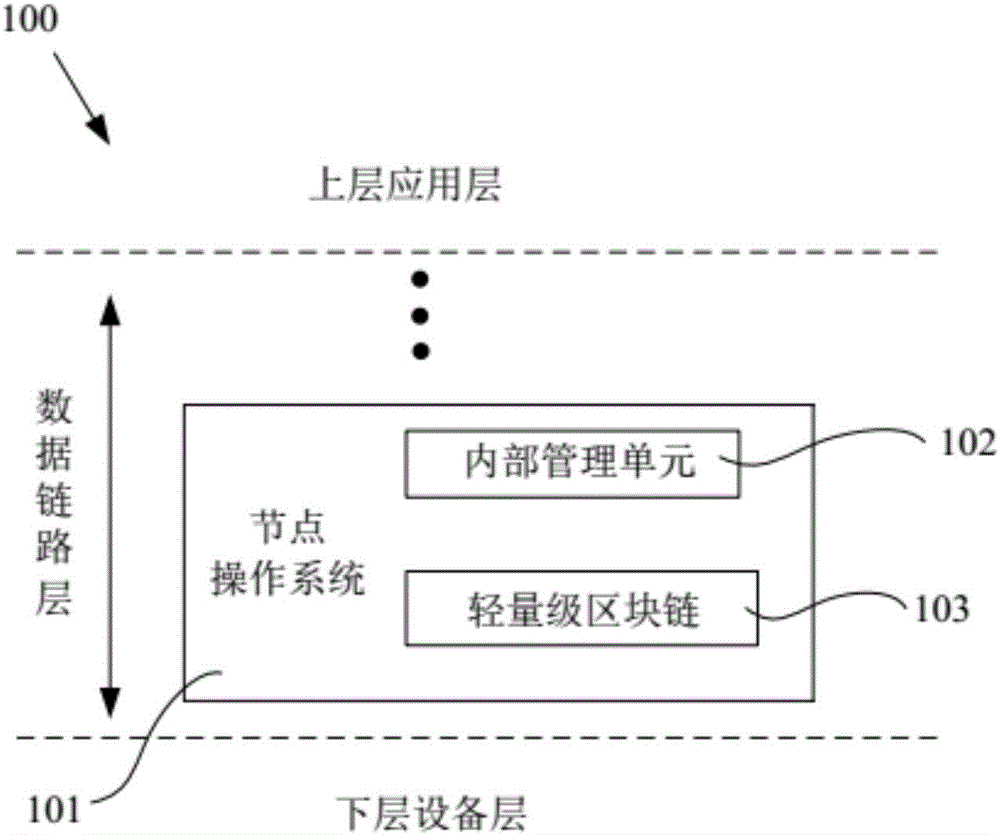
Node operating system integrated with lightweight block chain and method for data updating
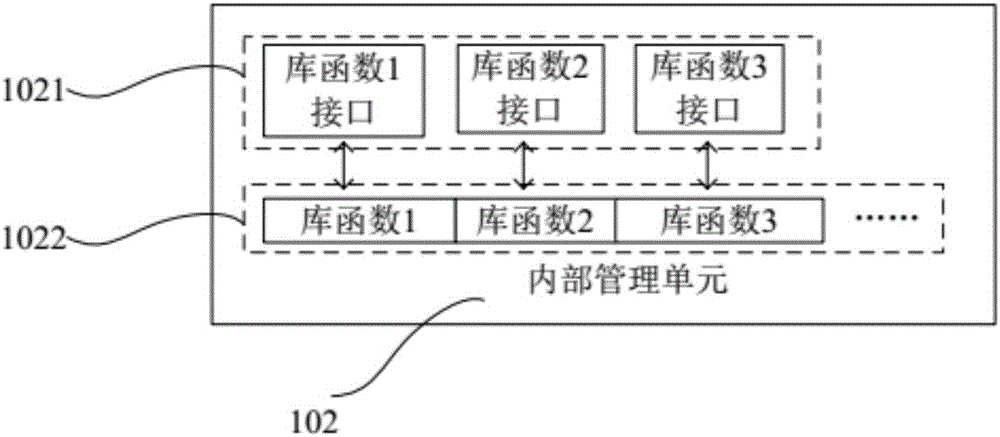
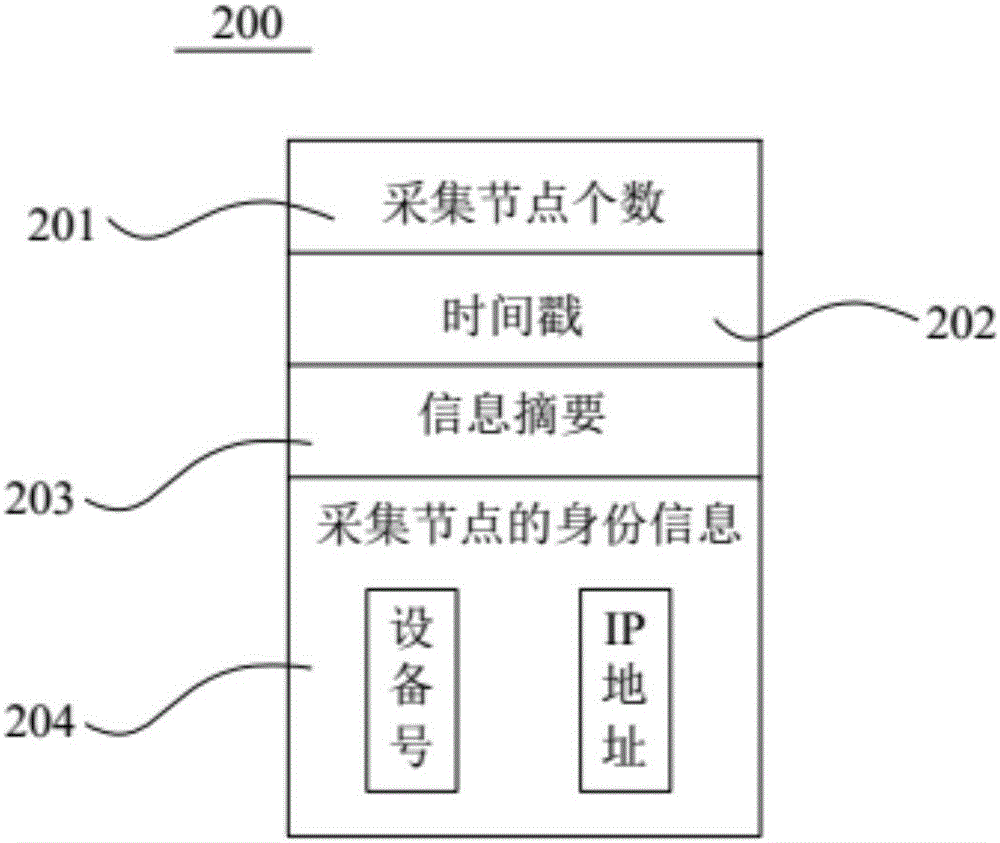
ActiveCN106790112AImprove compatibilityCollaborate efficientlyDatabase updatingTransmissionOperational systemTimestamp
The invention provides a node operating system integrated with a lightweight block chain. The node operating system is embedded in the data link layer bottom of a communication protocol stack of each communication node. The node operating system comprises an internal managing unit and the lightweight block chain integrated in the node operating system. Library functions of different network protocol stacks are packaged in the internal managing unit, and a protocol stack interface interacting with the library functions of the network protocol stacks is provided. The block chain data of the lightweight block chain defines a unified data chain list. The data chain list comprises sampling node number, timestamp, information abstract and identity information of sampling node. While the communication nodes are communicated mutually, the lightweight block chain only stores the information abstract and the identity information of the sampling node. The node operating system is capable of providing an improvable and developable open platform to a user, so the whole system has the good expandability.
Owner:重庆高开清芯智联网络科技有限公司
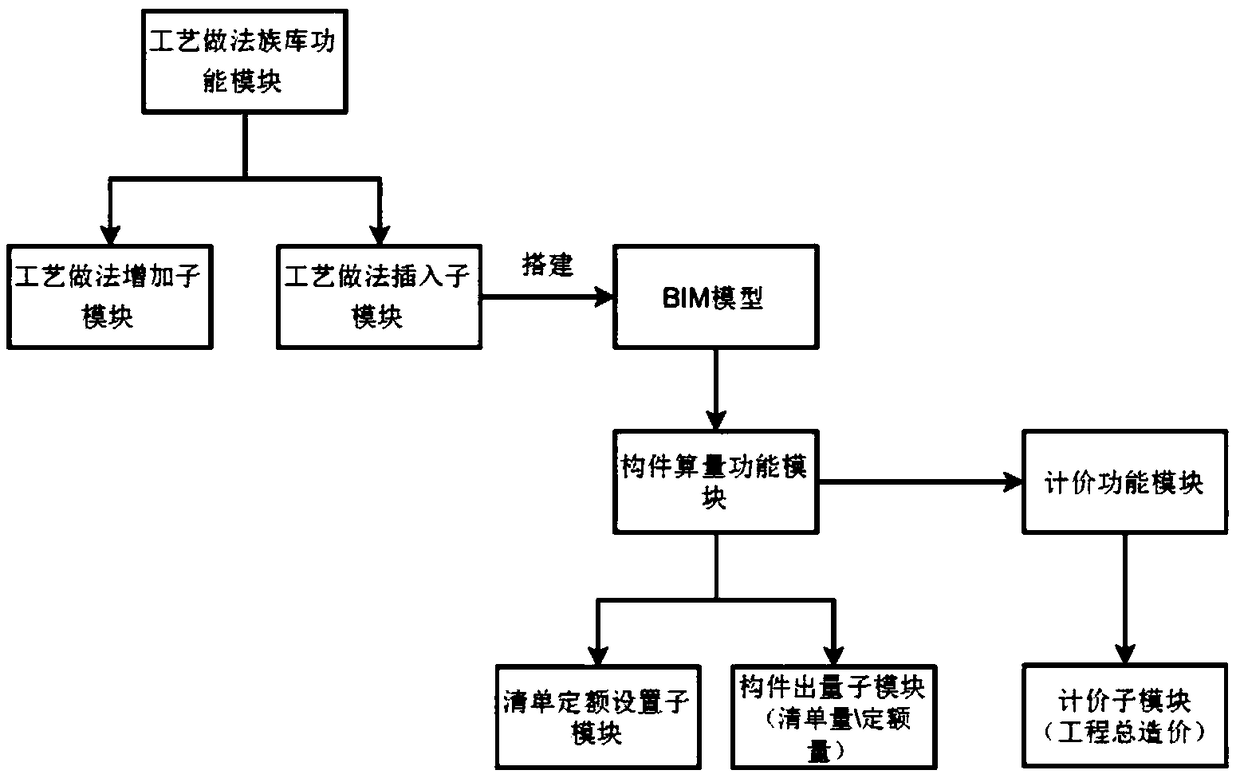
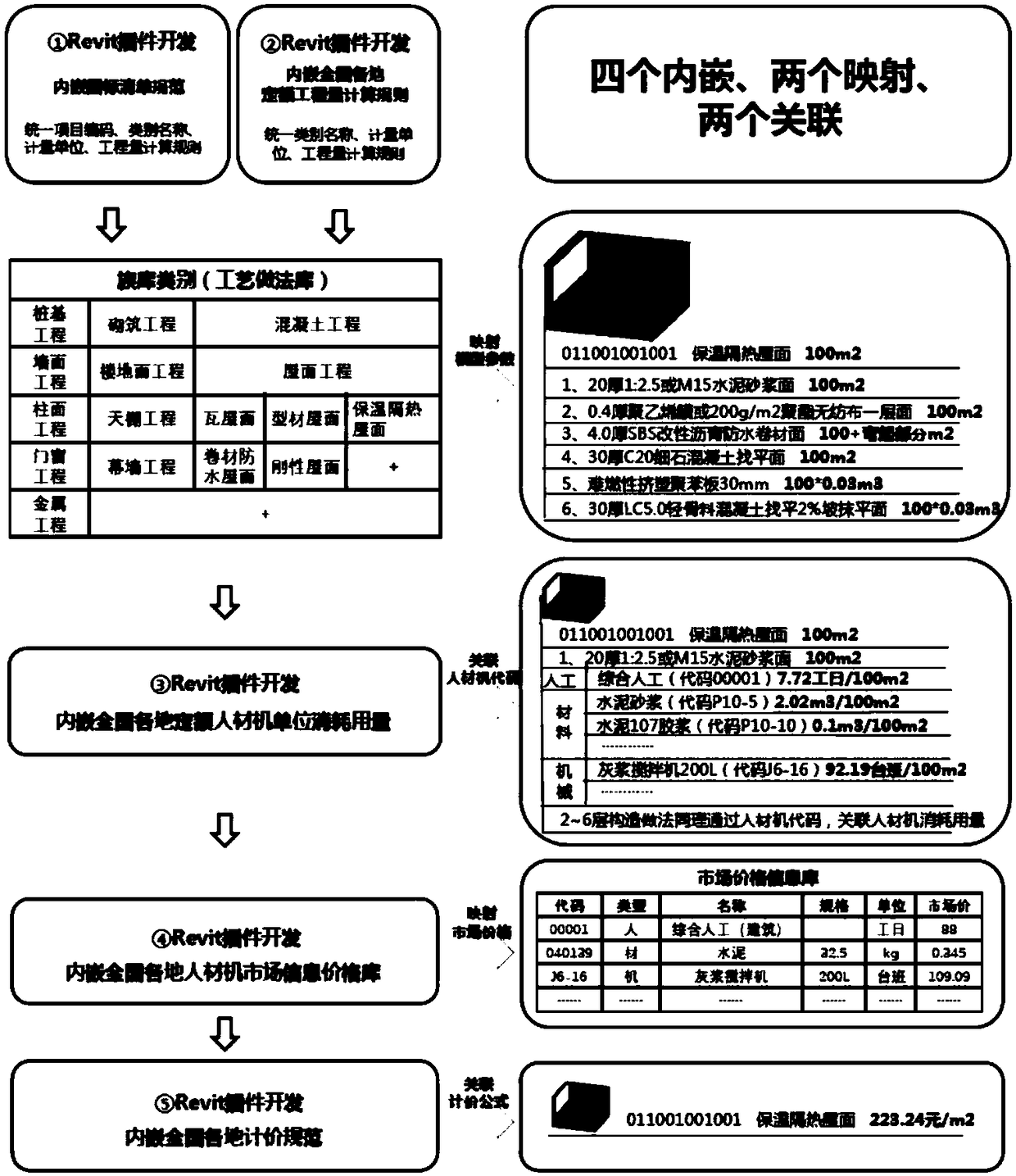
Design and construction valuation management system and method based on BIM technology
The invention provides a design and construction valuation management system and a design and construction valuation management method. The system comprises a Revit plug-in developed based on BIM modeling software, wherein a process approach family library function module, a component operand function module and a valuation function module are embedded. According to the system and method providedby the invention, the component information database is integrated via the BIM model built by the Revit plug-in, the overall project cost statistics during a construction process is performed throughreading all component information in the model, compared with the other systems and methods using the other third-party operand software, the system and method provided by the invention are simpler, more convenient, and greatly improved in efficiency.
Owner:HUNAN CONSTR ENG GRP COR +1
Automated, transparent and secure system and method for remotely managing network elements
InactiveUS20070083628A1Reliable and flexible and cost-efficient managementSimple and inexpensive to implementDigital computer detailsTransmissionCyber operationsGeneral purpose computer
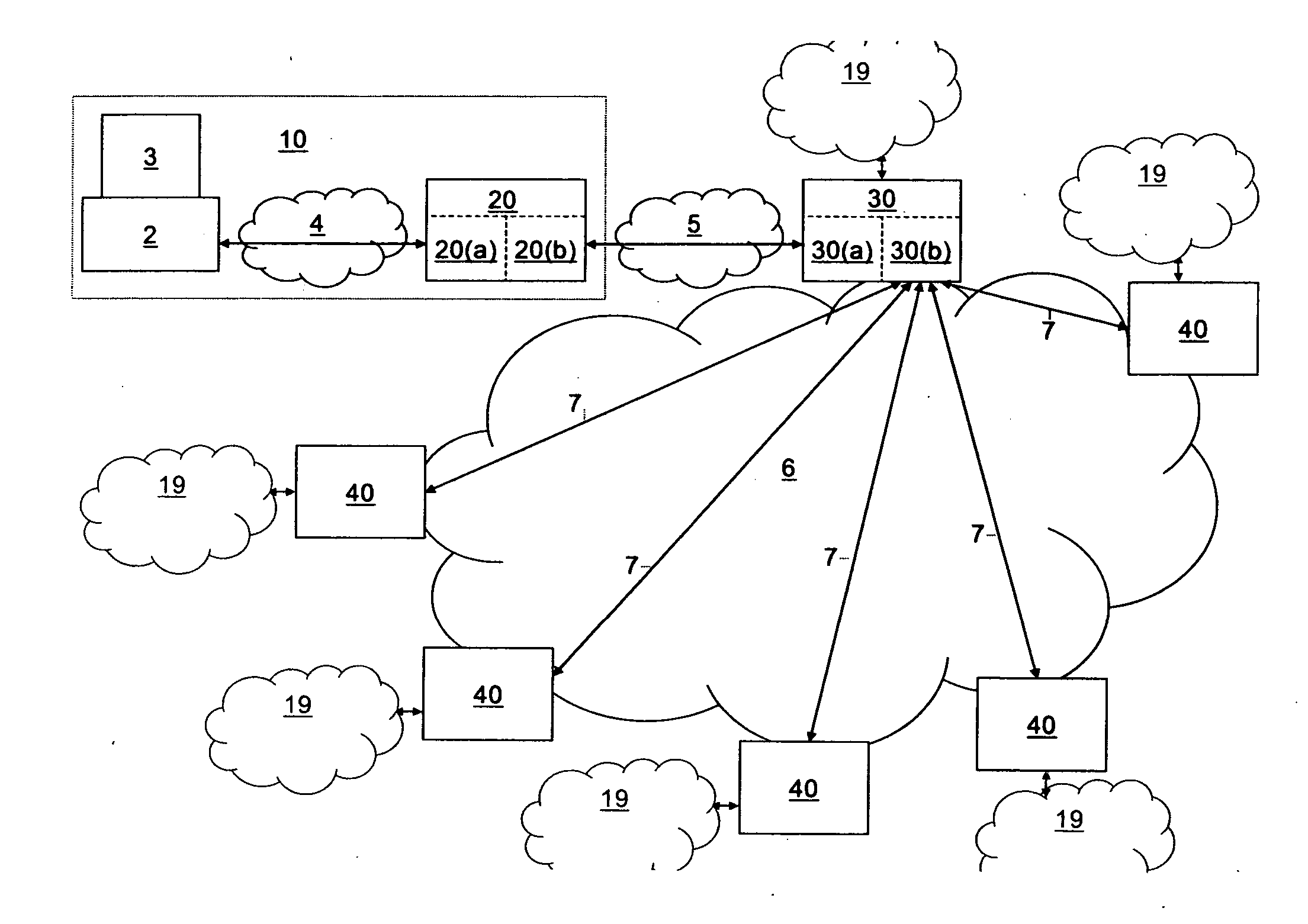
A network management system for securely managing network elements (NEs) over arbitrary multi-operator networks, via managing copies of NE configuration files on general purpose computers on a network operations center (NOC). The NEs operate automatically and dynamically, under non-dynamic control by the NE configuration files sent from the NOC. The NE hardware implements automated routines by which NE configuration files, including NE program, control and status memory contents, are transferred between NOC and NEs in a customized, secure fashion, while providing an abstraction for software such that the software at both the NOC computers and NEs can handle the NMS communications simply via using common standard file system and networking library functions. This is accomplished by a portal device that functions as a transparent converter between regular LAN file transfers between NOC computers and the portal, and between the customized, secured file transfer format used between the portal and NEs.
Owner:OPTIMUM COMM SERVICES
Technique for computational nested parallelism
ActiveUS20130298133A1Overcome limitationsResource allocationProcessor architectures/configurationProgramming constructsSemantics
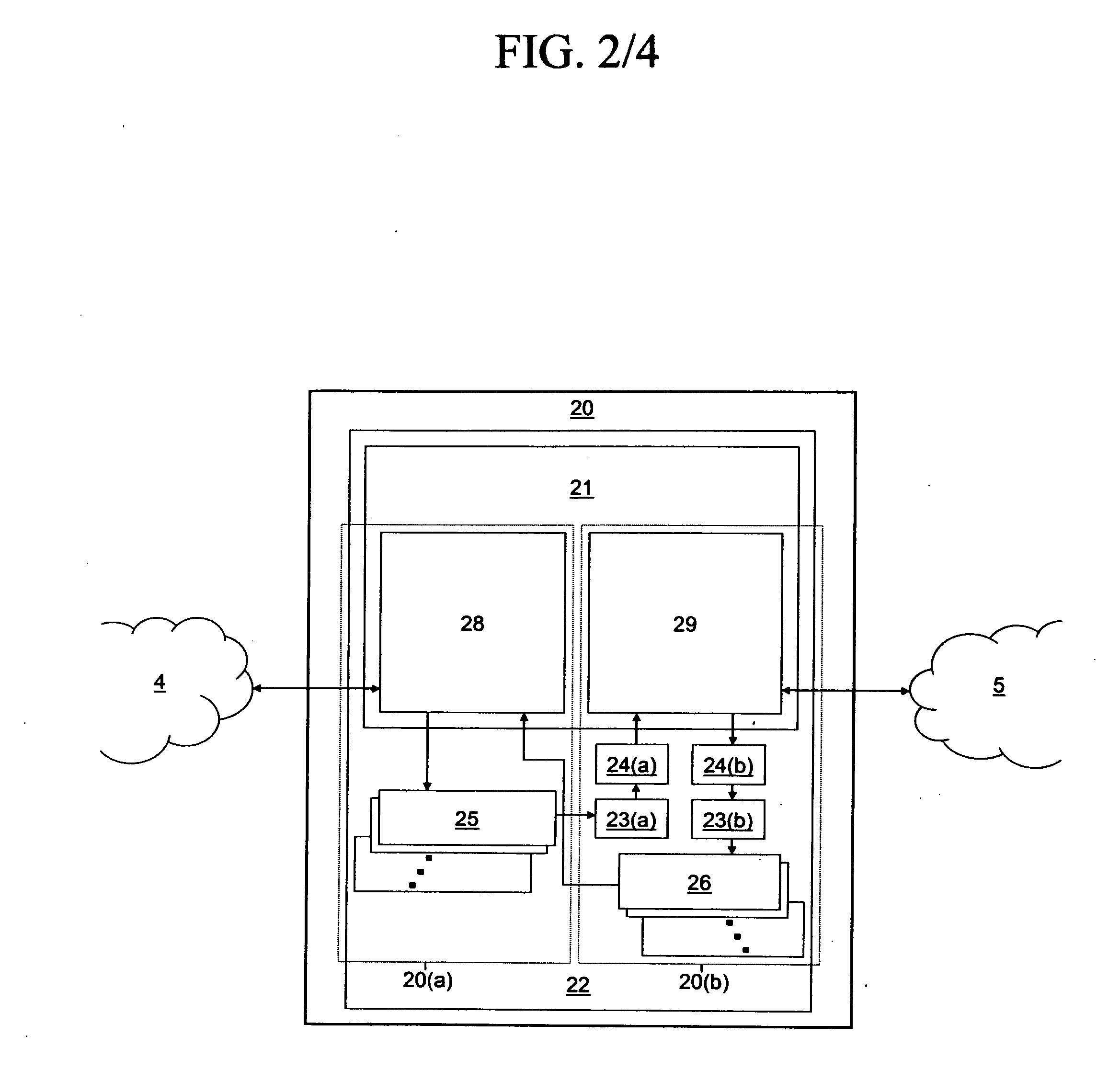
One embodiment of the present invention sets forth a technique for performing nested kernel execution within a parallel processing subsystem. The technique involves enabling a parent thread to launch a nested child grid on the parallel processing subsystem, and enabling the parent thread to perform a thread synchronization barrier on the child grid for proper execution semantics between the parent thread and the child grid. This technique advantageously enables the parallel processing subsystem to perform a richer set of programming constructs, such as conditionally executed and nested operations and externally defined library functions without the additional complexity of CPU involvement.
Owner:NVIDIA CORP
Method and device for detecting Android malicious application
ActiveCN104331662AIn line with operating habitsExpand the scope of detectionSoftware testing/debuggingPlatform integrity maintainanceUser inputOperating system
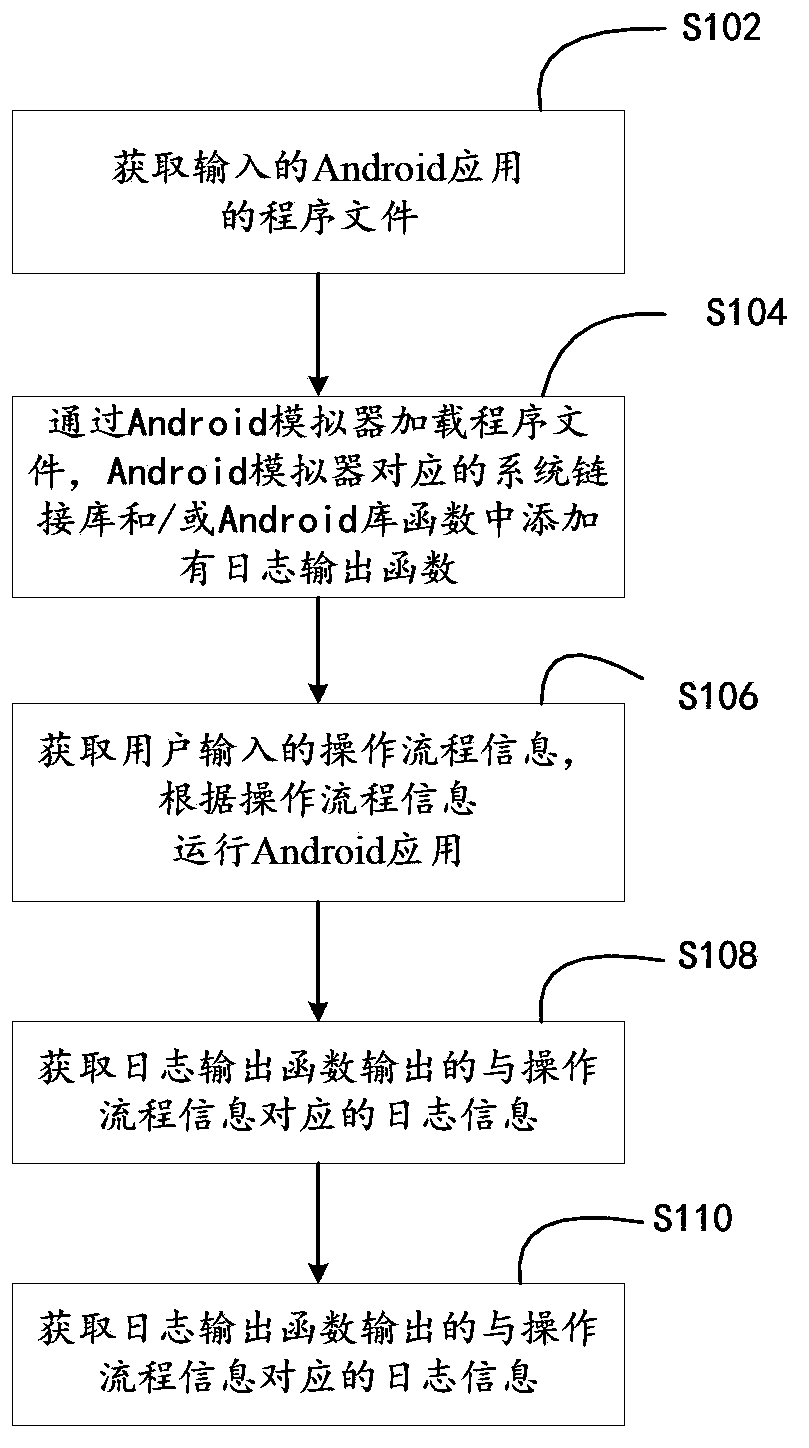
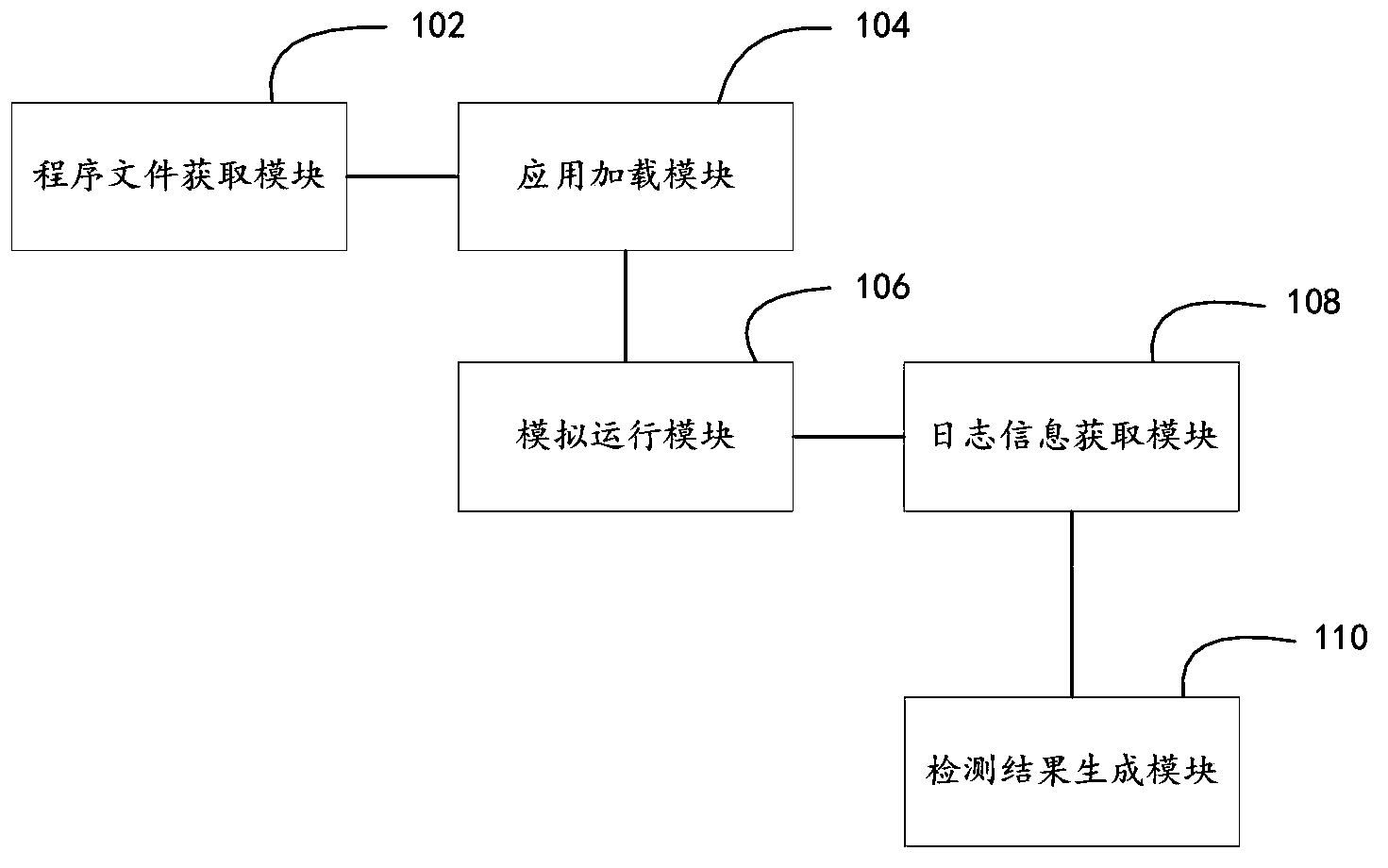
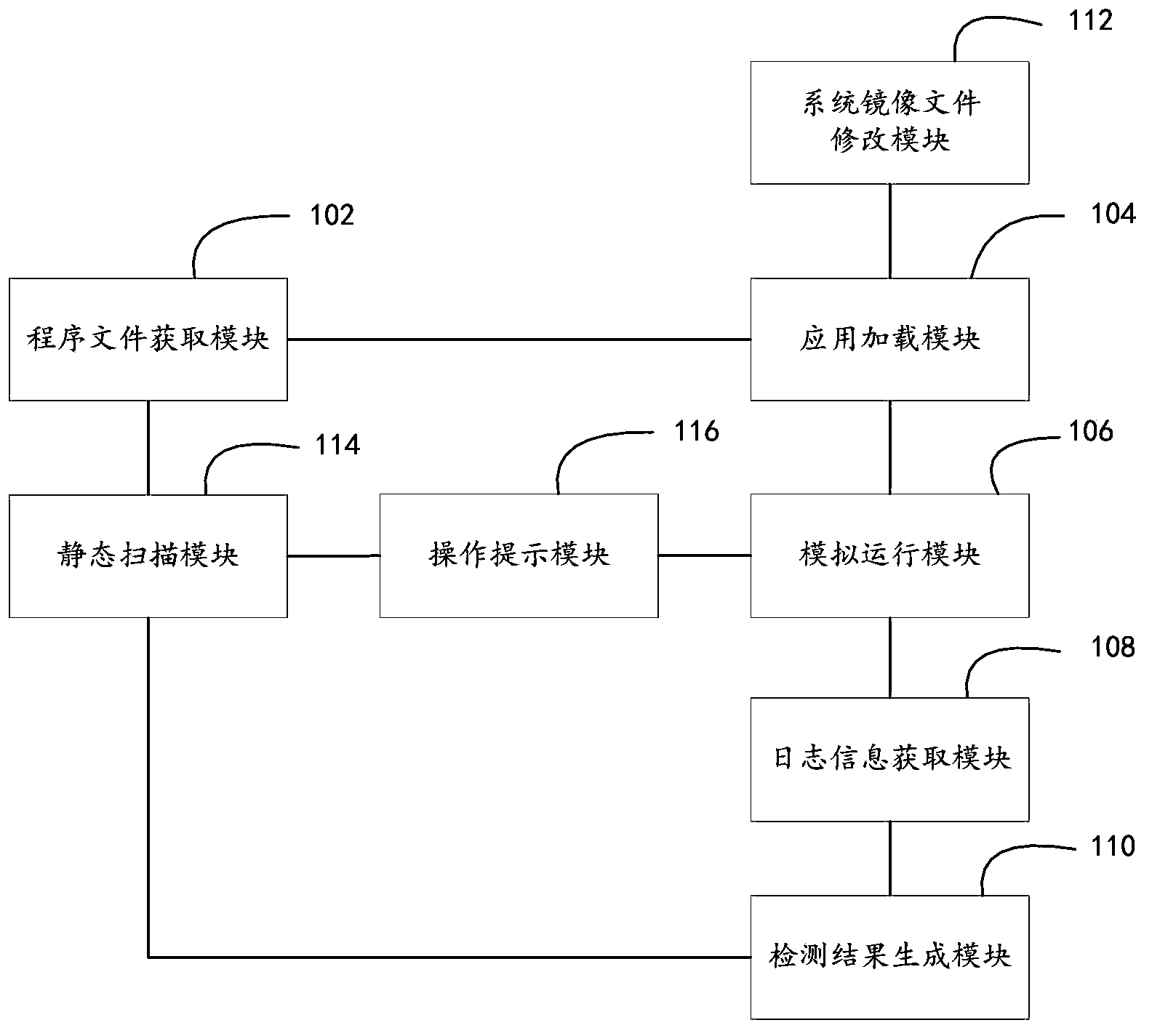
The invention discloses a method and a device for detecting an Android malicious application. The method comprises the following steps: obtaining an input program file of an Android application; loading the program file through an Android simulator, wherein a log output function is added into a system link library and / or Android library function corresponding to the Android simulator; obtaining operation flow information input by a user, and operating the Android application according to the operation flow information; obtaining log information which is output by the log output function and corresponds to the operation flow information; and according to the log information, generating a detection result. In addition, the invention also provides a device for detecting the Android malicious application. Detection accuracy can be improved.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
Pruning engine
A method and apparatus are disclosed for enhancing operable functionality of input source code files from a software program by preprocessing input source code files with codeword processing operations to generate a plurality of preprocessed input source code files, identifying candidate code snippets by pruning one or more preprocessed input source code files that do not meet a similarity threshold measure for library functions stored in the system library, and identifying at least a first validated code snippet from the one or more candidate code snippets that matches a first library function stored in the system memory on the basis of at least first and second matching metrics.
Owner:DEVFACTORY INNOVATIONS FZ LLC
Minimizing memory access conflicts of process communication channels
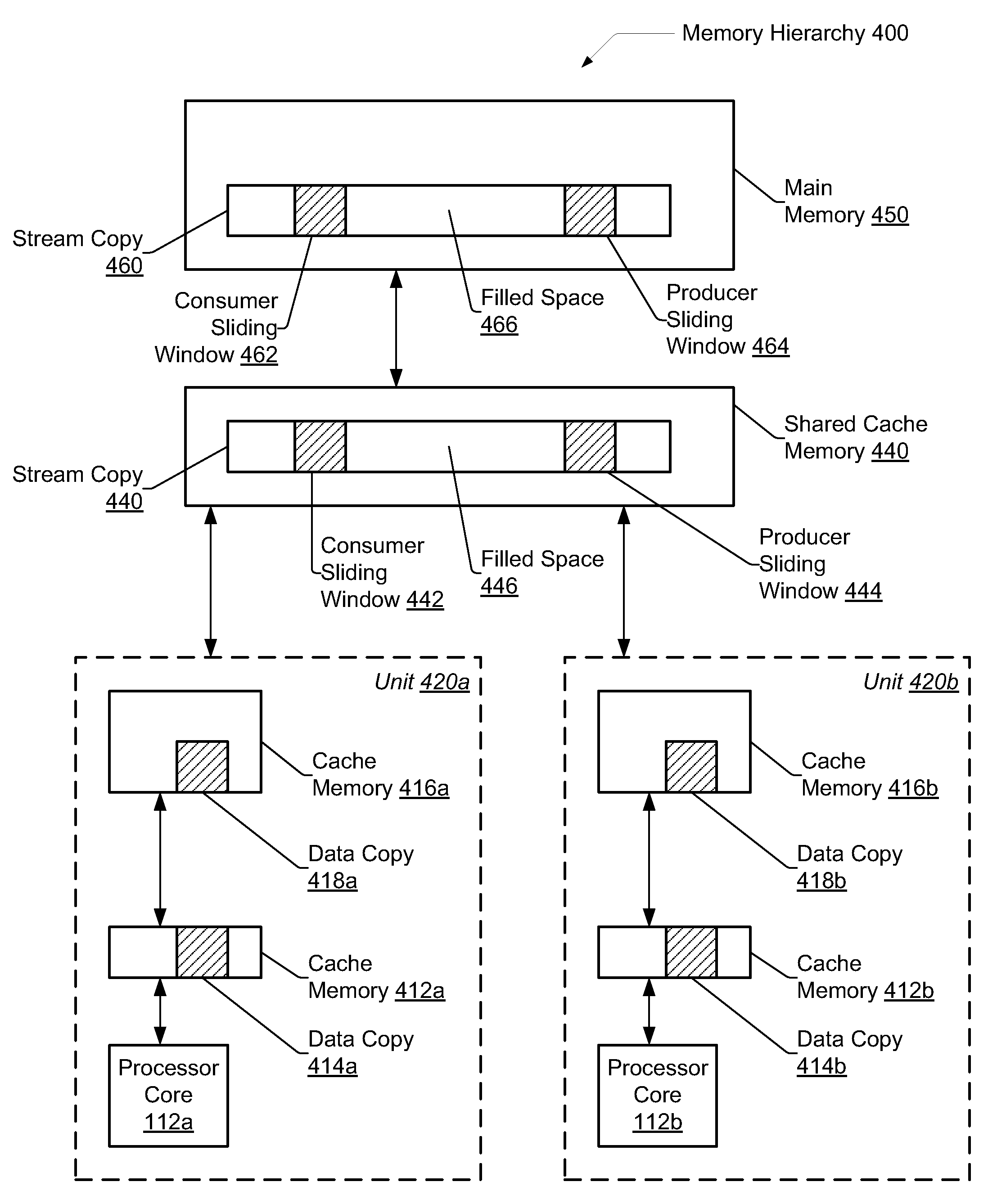
InactiveUS20100070730A1Minimizing cache conflictsSoftware engineeringMemory systemsSlide windowParallel computing
A system and method for minimizing cache conflicts and synchronization support for generated parallel tasks within a compiler framework. A compiler comprises library functions to generate a queue for parallel applications and divides it into windows. A window may be sized to fit within a first-level cache of a processor. Application code with producer and consumer patterns within a loop construct has these patterns split into producer and consumer tasks. Within a producer task loop, a function call is placed for a push operation that modifies a memory location within a producer sliding window without a check for concurrent accesses. A consumer task loop has a similar function call. At the time a producer or consumer task is ready to move, or slide, to an adjacent window, its corresponding function call determines if the adjacent window is available.
Owner:GLOBALFOUNDRIES INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com