Patents
Literature
51 results about "Programming constructs" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Spreadsheet programming
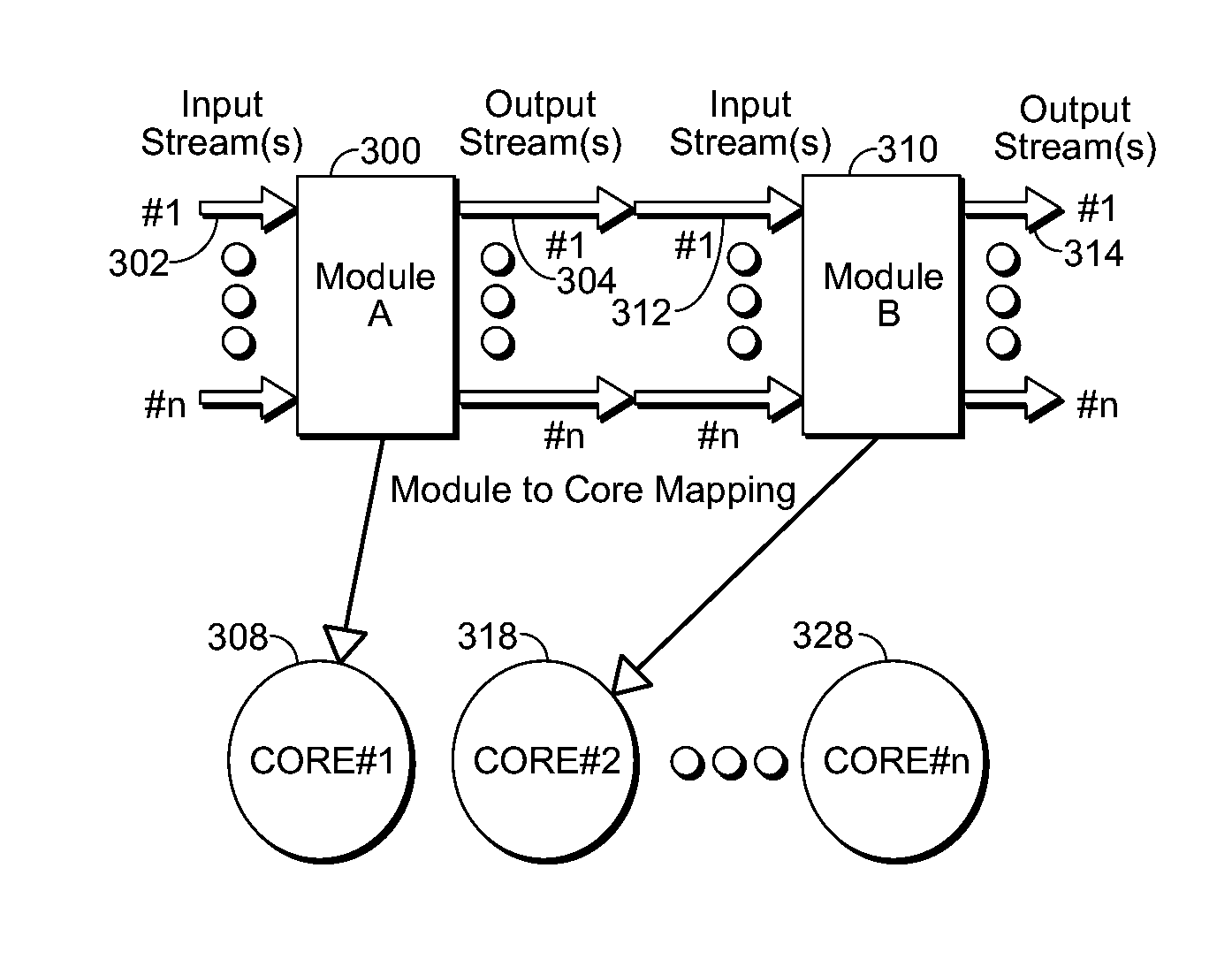
InactiveUS20060224946A1Great computational capabilityGreat expressive powerText processingDigital computer detailsElectronic formObject definition
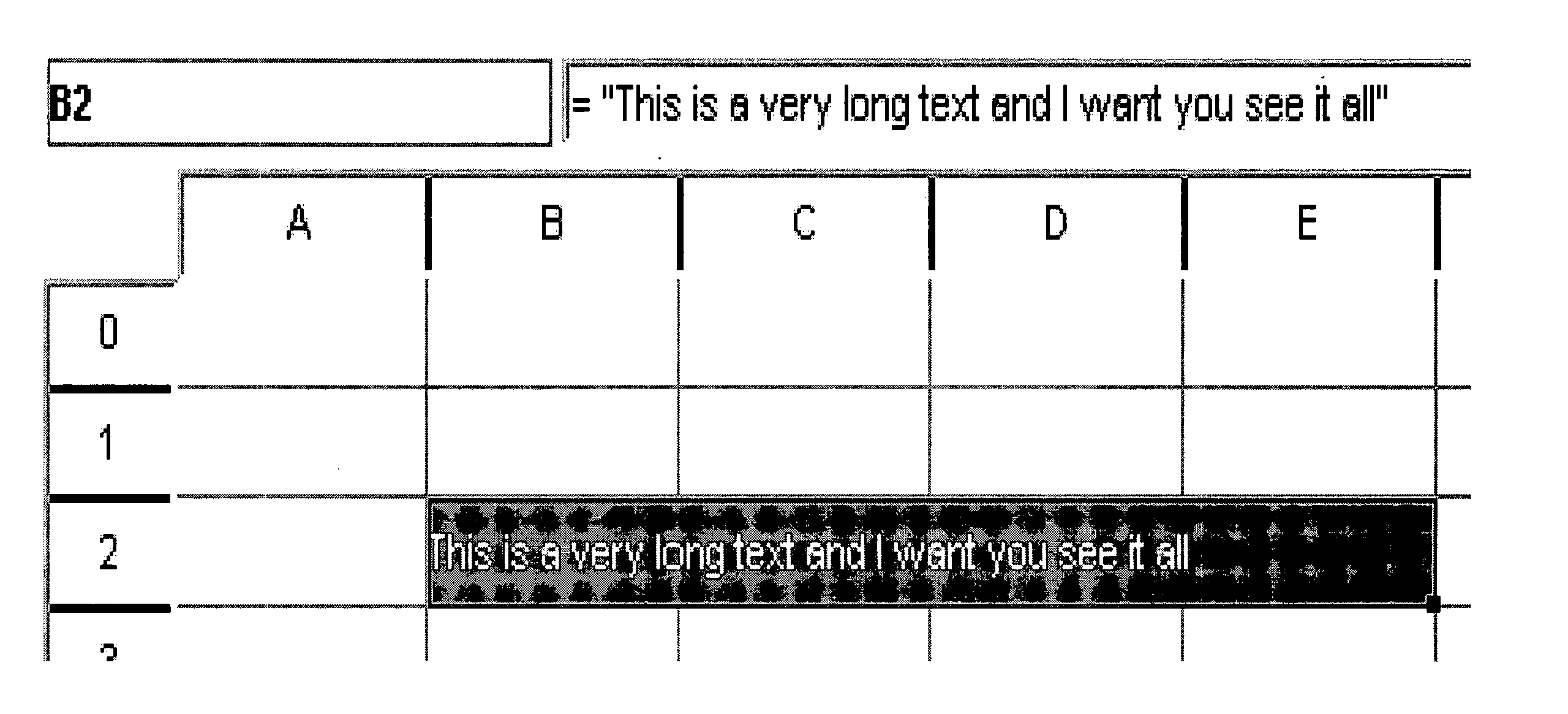
Spreadsheet programming model and language is extended to create objects, with their associated state and set of defined behaviors, as first-class spreadsheet cell residents. Desired object behaviors can be invoked by calling methods on the objects through an event-based imperative programming language that potentially modifies the state of an object. Expressions can also be defined by calling methods on objects that produce new objects in combination with operations on objects in other cells. Programming constructs are defined that allows users to perform a sequence of operations on one or more objects. Operations can also be performed automatically similar to spreadsheet triggering mechanism. Users can program to trigger operations either manually or automatically based on changes to objects, or based on conditions defined.
Owner:IBM CORP
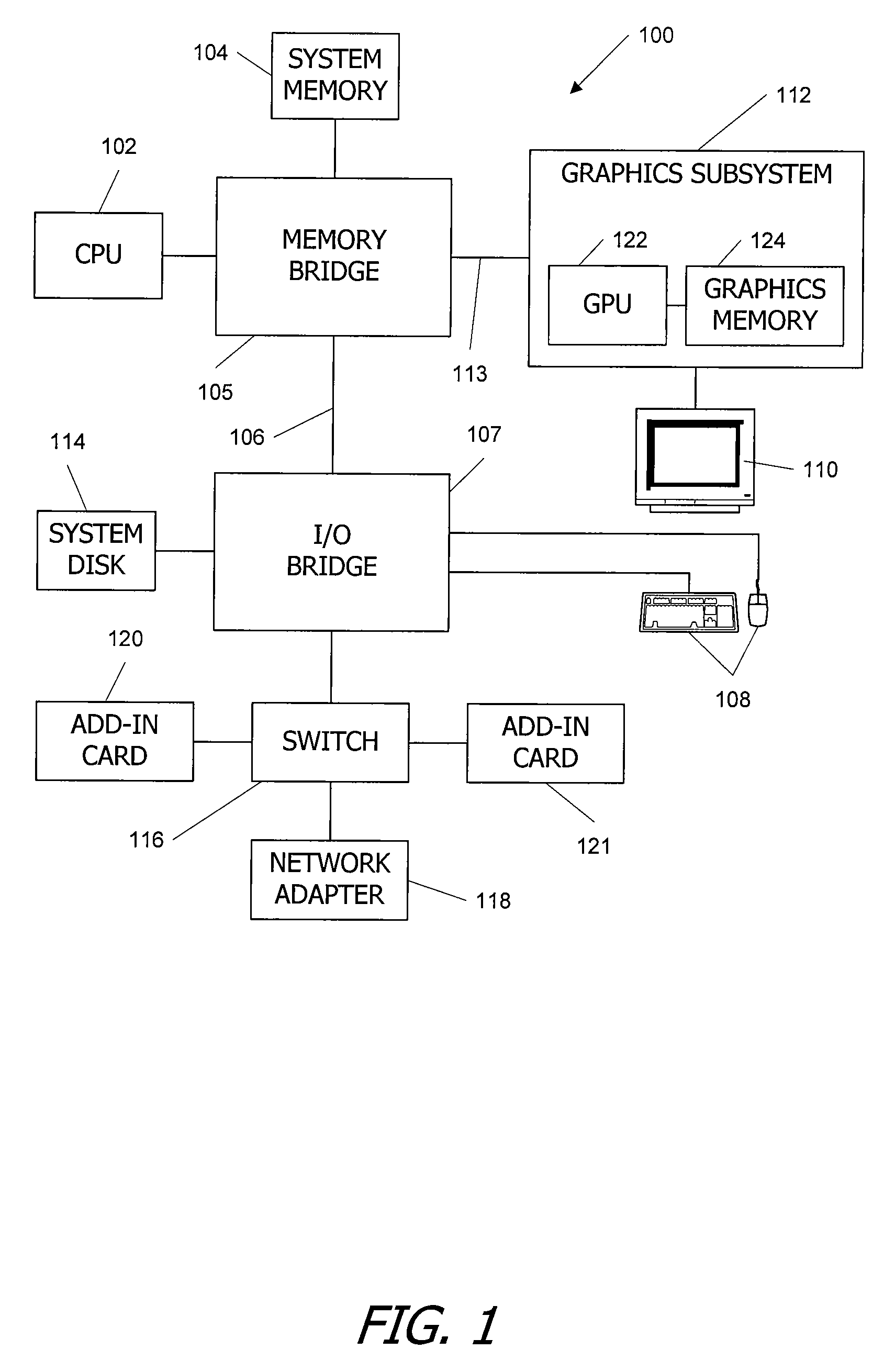
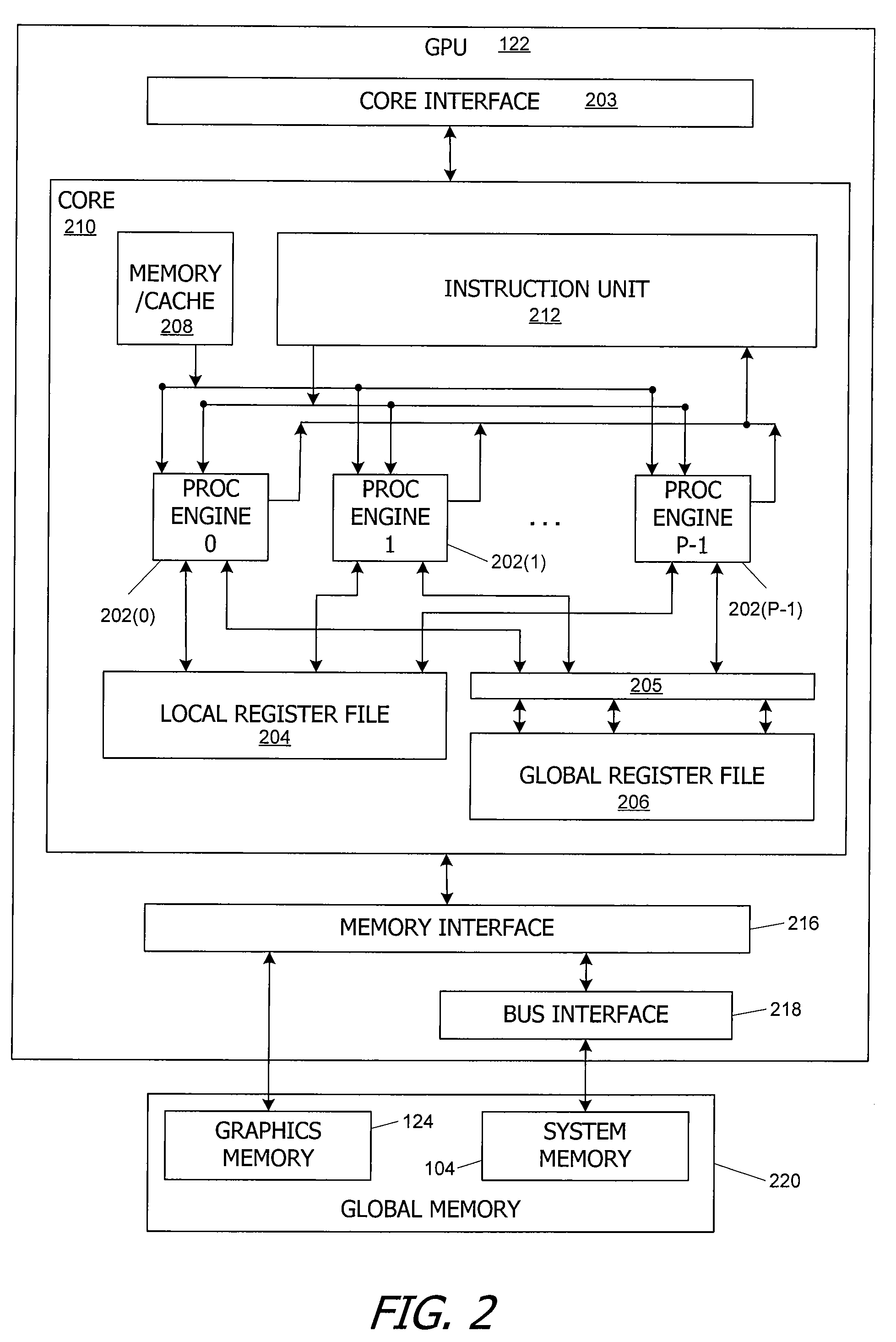
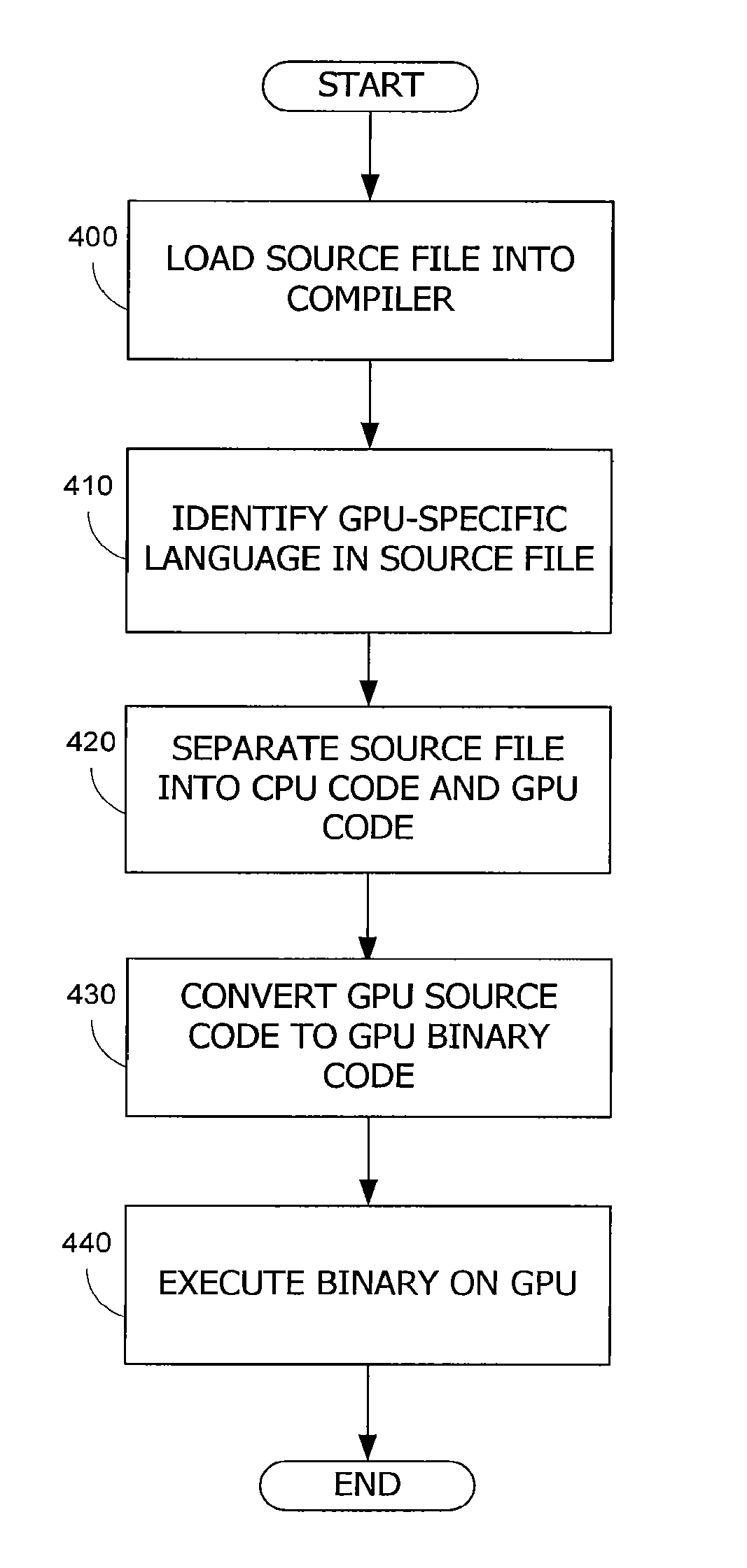
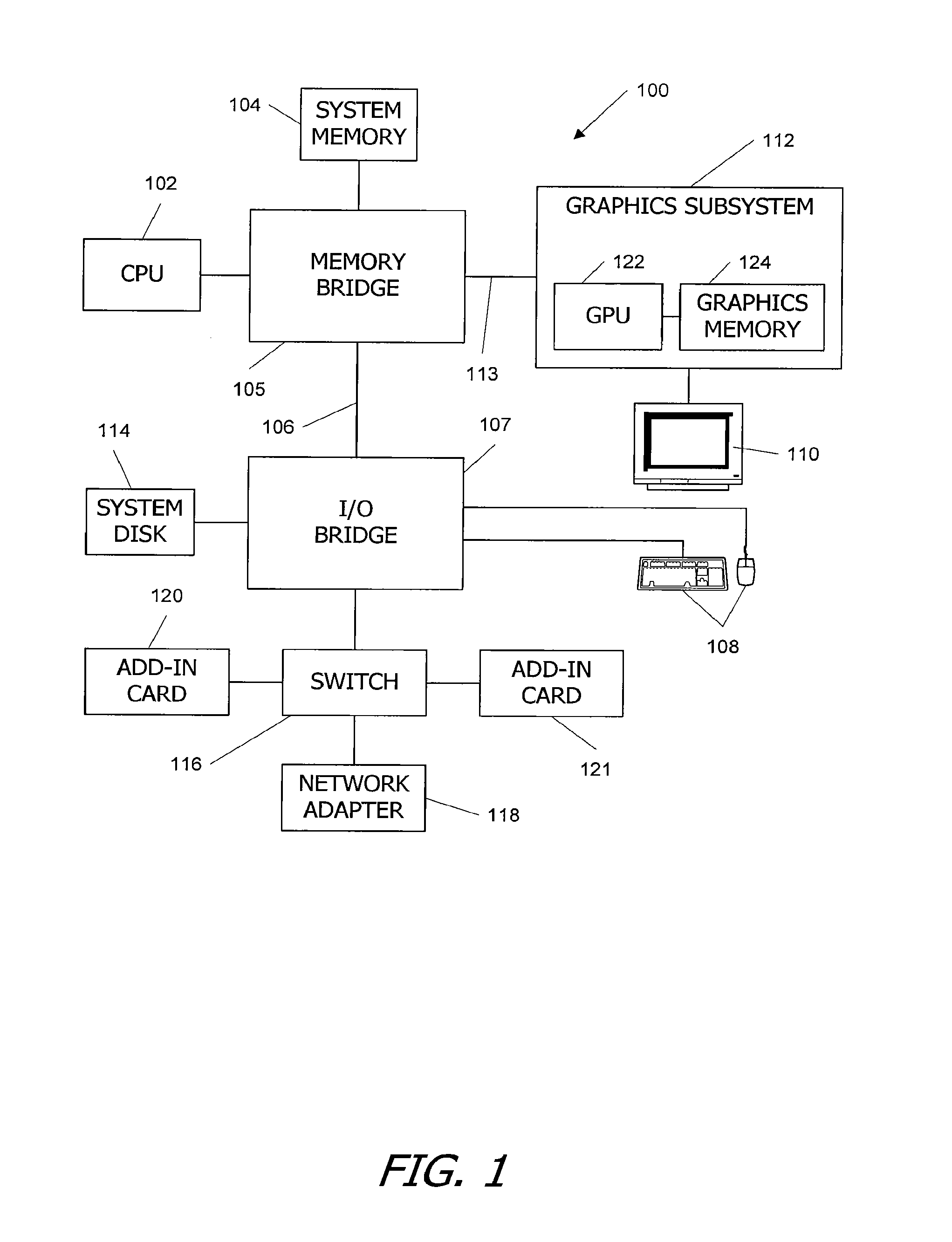
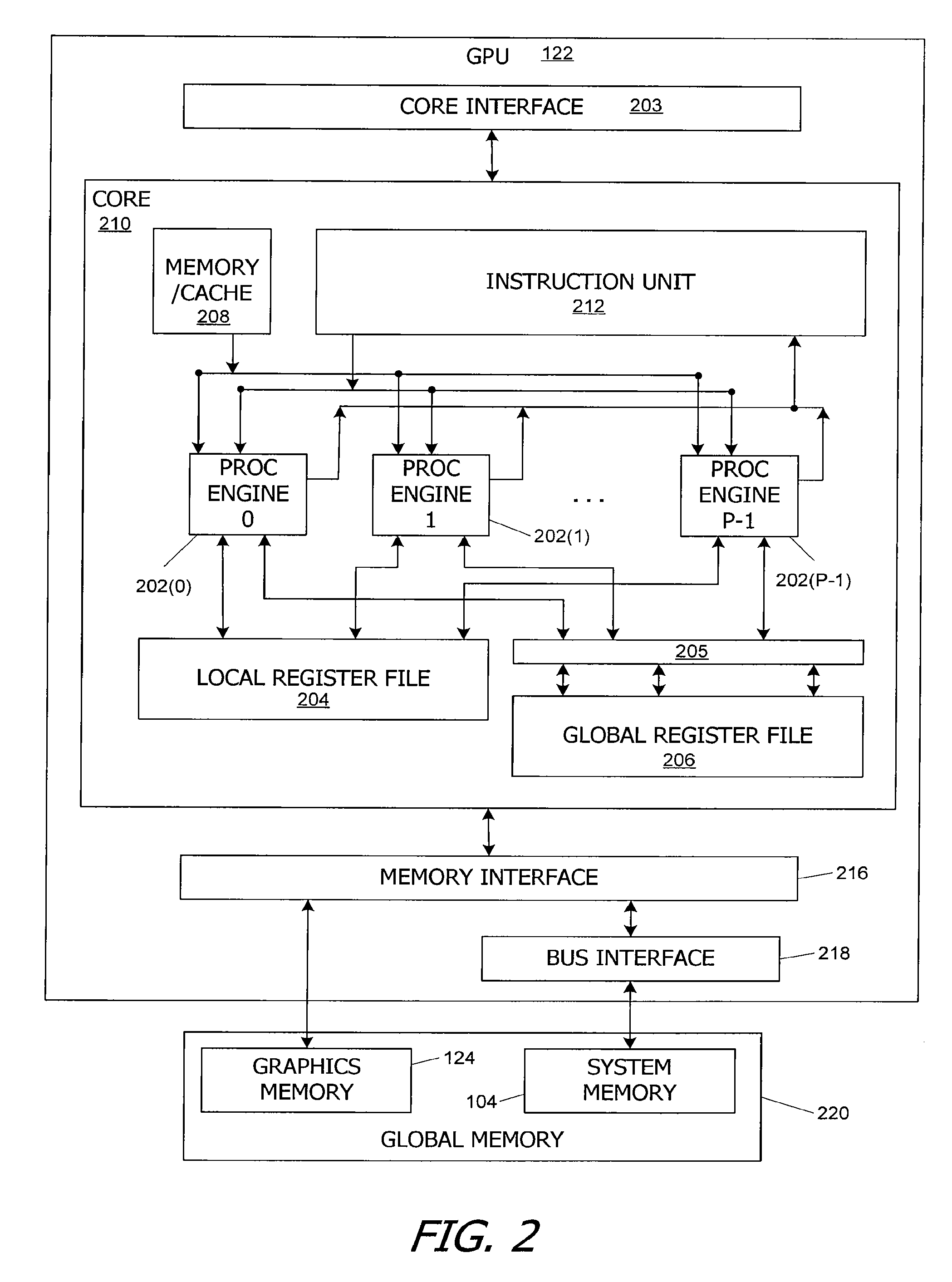
C/c++ language extensions for general-purpose graphics processing unit
A general-purpose programming environment allows users to program a GPU as a general-purpose computation engine using familiar C / C++ programming constructs. Users may use declaration specifiers to identify which portions of a program are to be compiled for a CPU or a GPU. Specifically, functions, objects and variables may be specified for GPU binary compilation using declaration specifiers. A compiler separates the GPU binary code and the CPU binary code in a source file using the declaration specifiers. The location of objects and variables in different memory locations in the system may be identified using the declaration specifiers. CTA threading information is also provided for the GPU to support parallel processing.
Owner:NVIDIA CORP
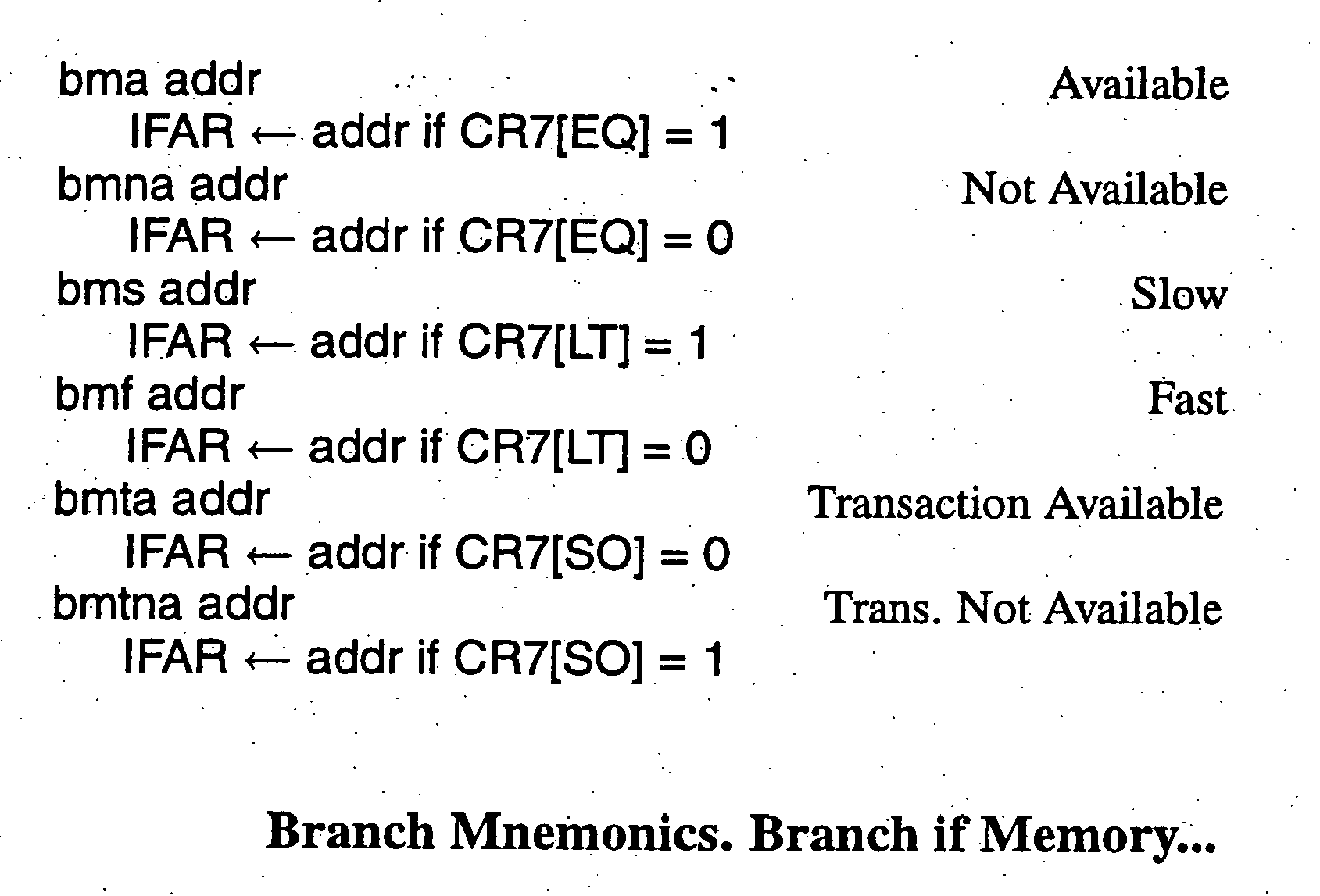
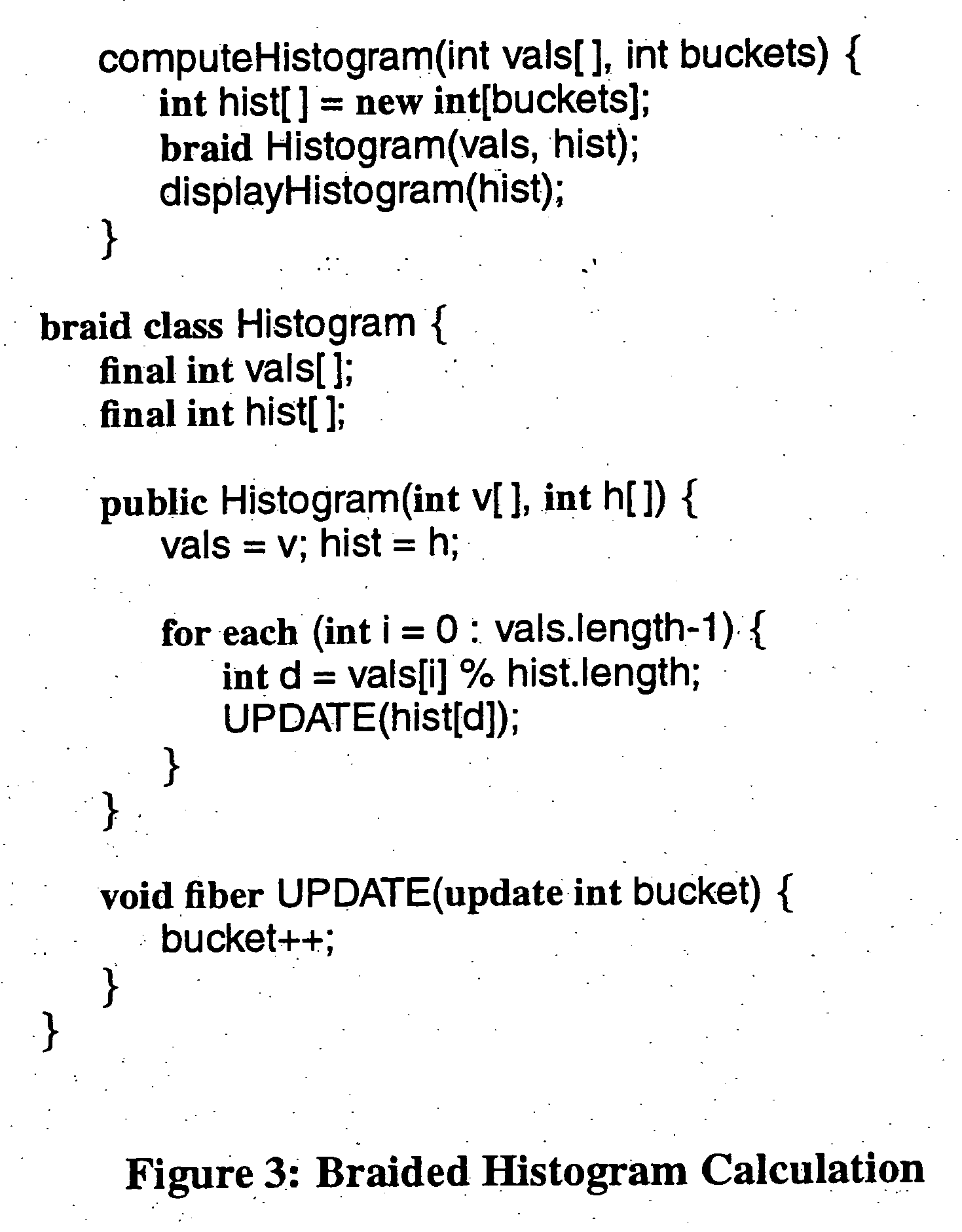
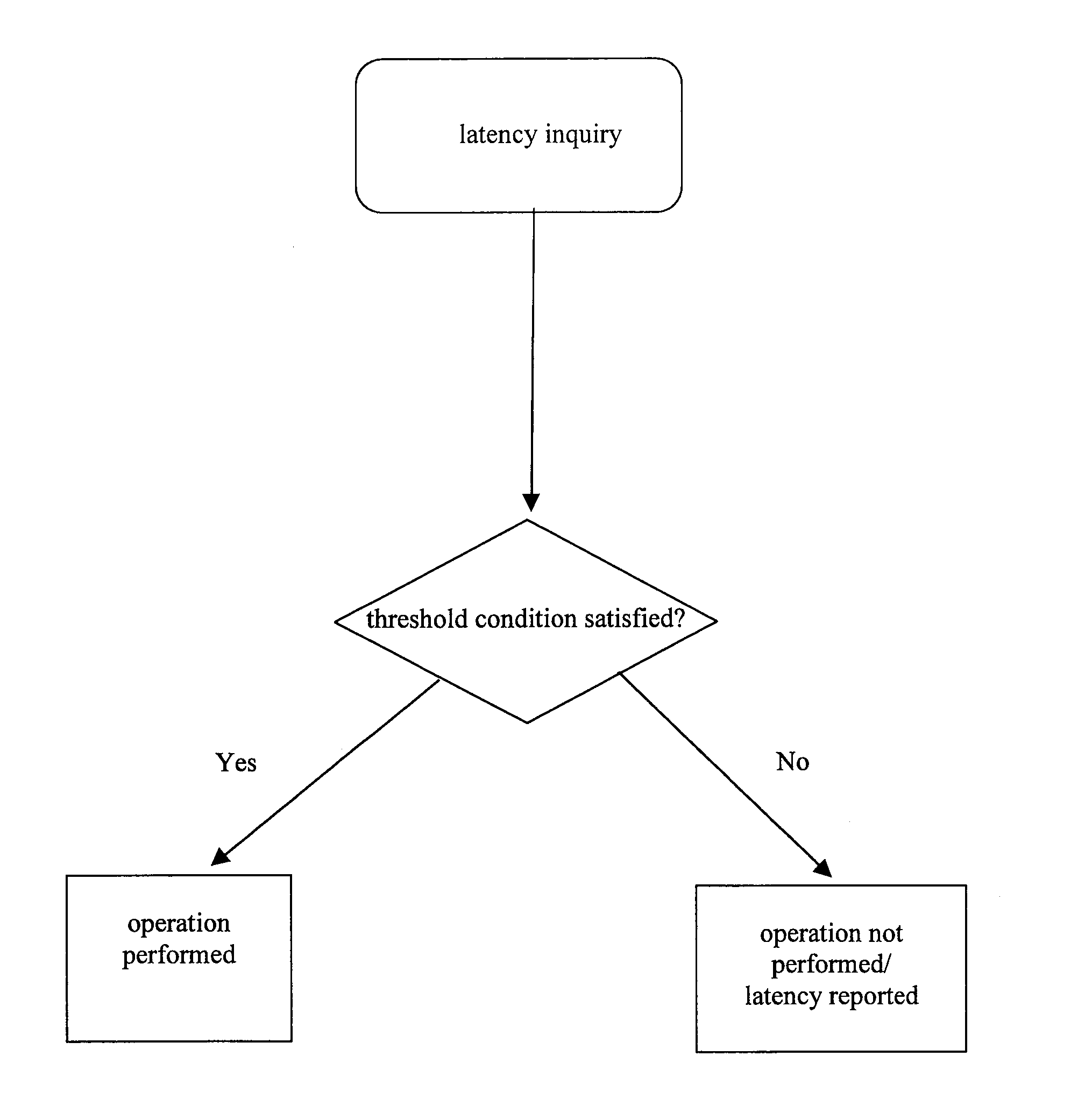
Arrangements for adaptive response to latencies
InactiveUS20060101249A1Easy to createEasy to understandRegister arrangementsSoftware engineeringFiberProgramming constructs
A response to the continuing trend of ever-increasing processor speeds and attendant increases in memory latencies. Broadly contemplated herein are braids and fibers, high-level programming constructs which facilitate the creation of programs that are partially ordered. These partial orders can be used to respond adaptively to memory latencies. It is shown how these constructs can be effectively supported with simple and inexpensive instruction set and micro-architectural extensions.
Owner:IBM CORP
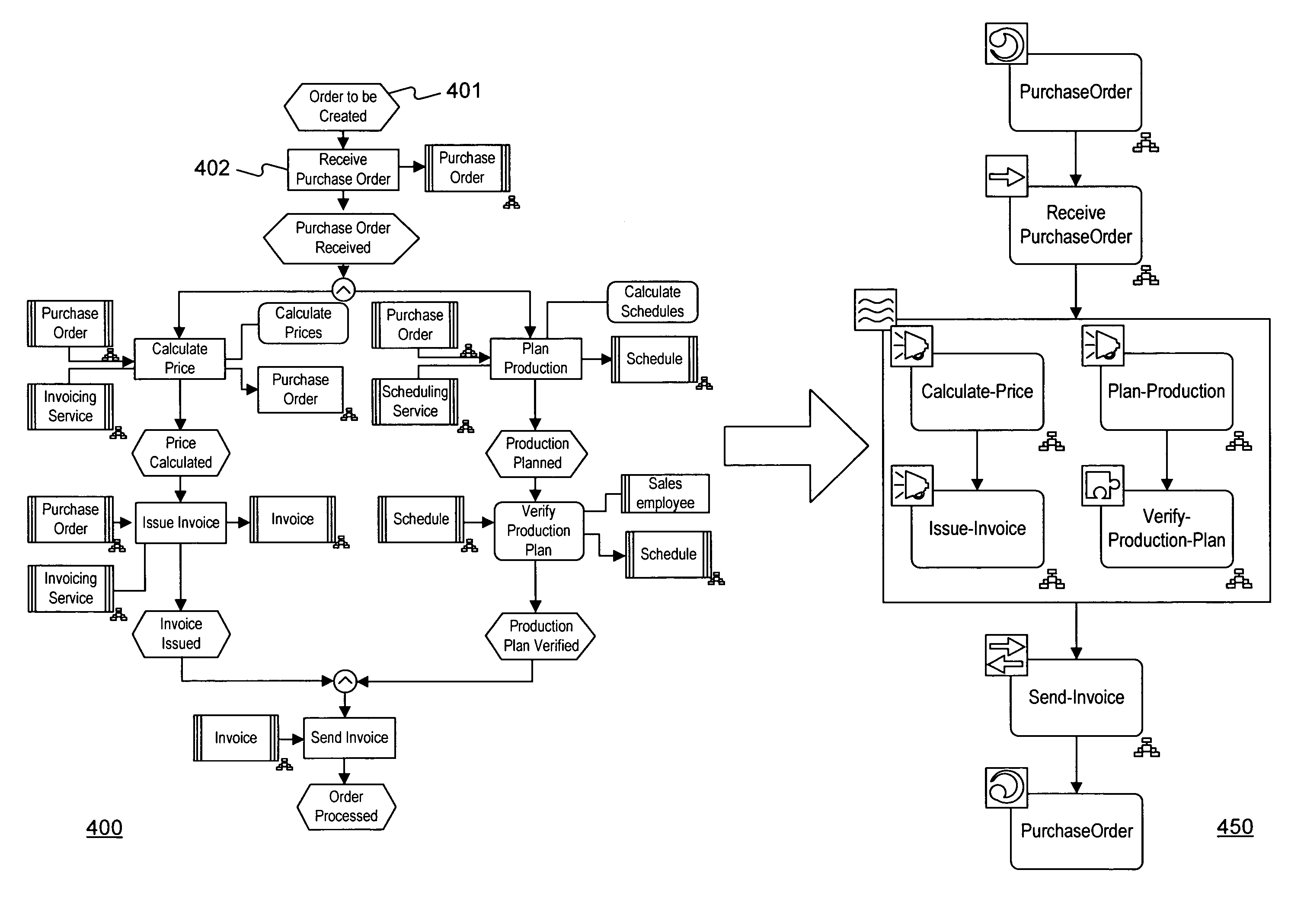
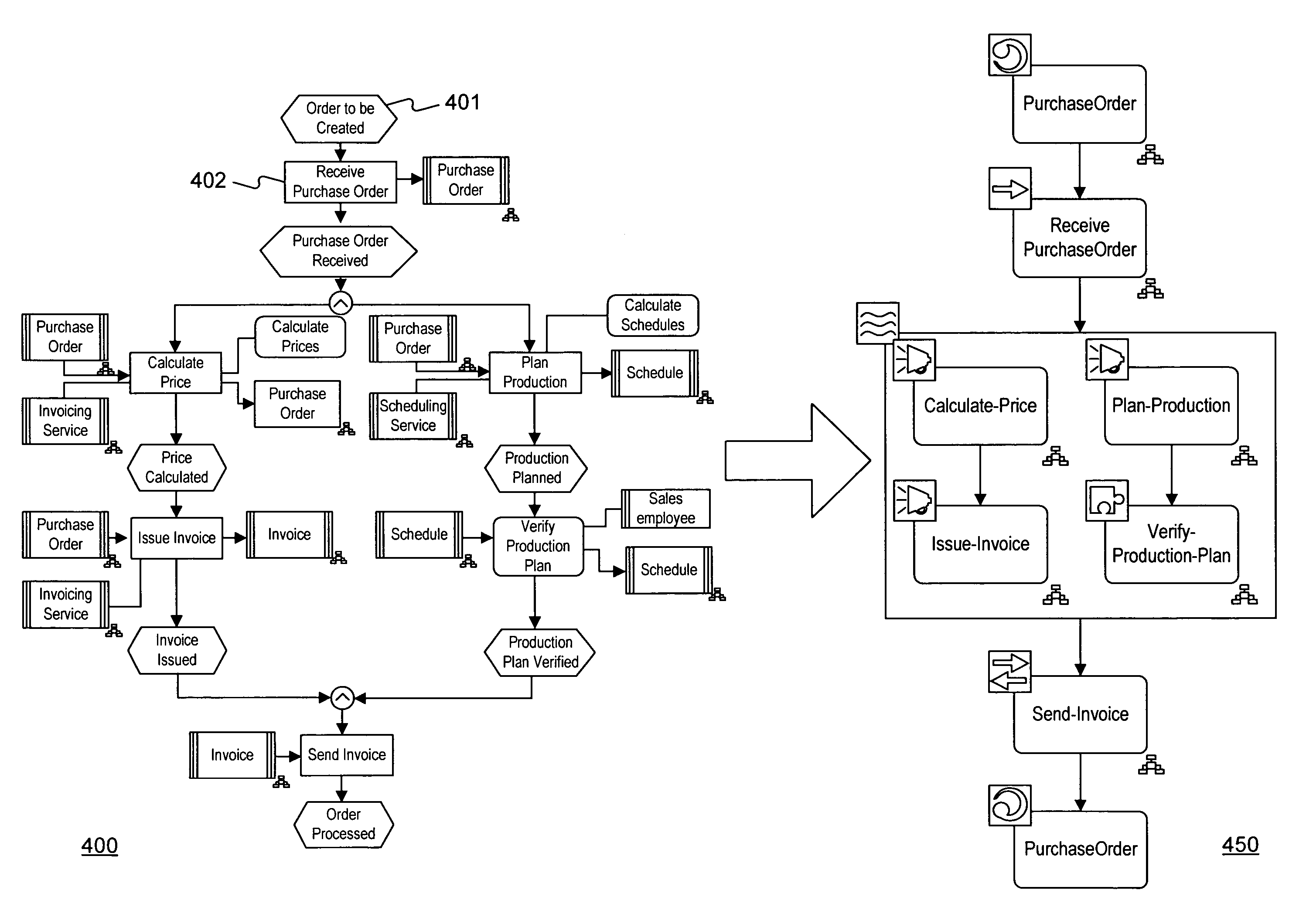
Systems and methods for transforming modeled business processes into executable processes
Systems and methods are provided for transforming modeled business processes into executable processes. The modeled processes may comprise graphically modeled business processes. The executable processes may comprise processes suitable for execution by a computerized or software-based system. In one embodiment, transformation rules are provided for mapping or converting, for example, EPC model constructs to BPEL constructs. The transformation rules can be applied to graphical constructs in a modeled business process to generate an executable business process comprising an ordered sequence of programming constructs. The ordered sequence of programming constructs can be stored in a database for subsequent execution of the executable business process.
Owner:SOFTWARE AG
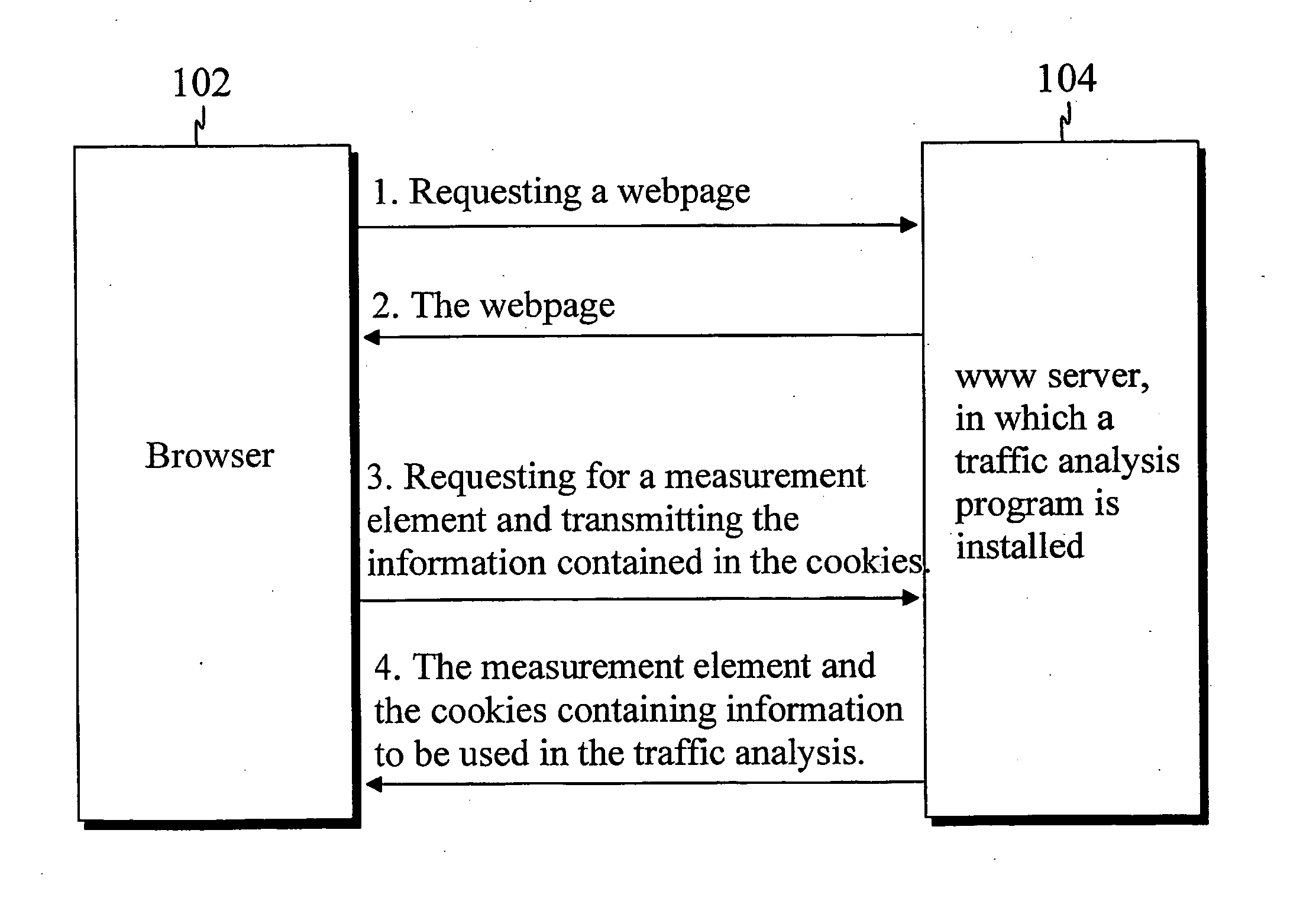
Traffic flow analysis method
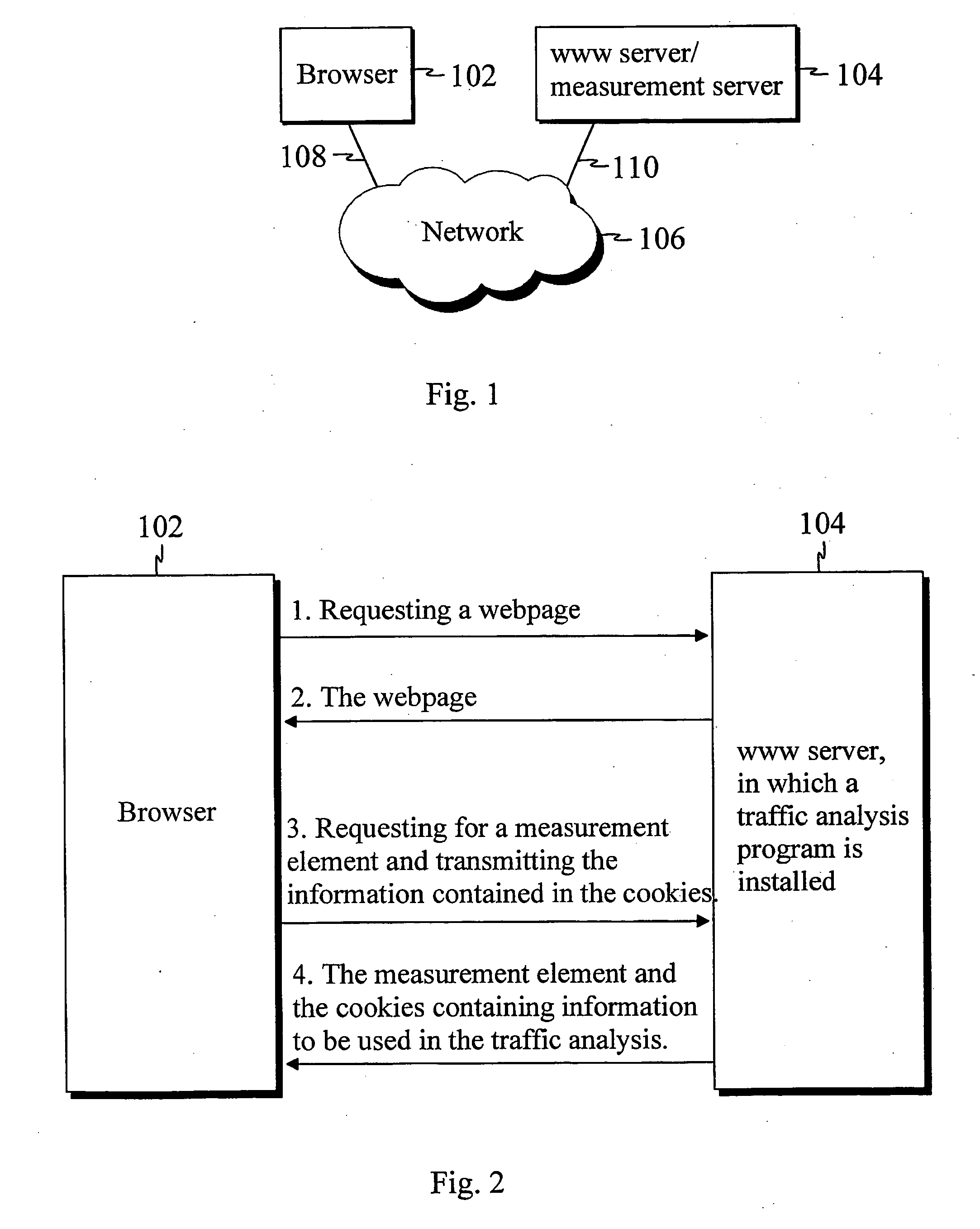
InactiveUS20050021731A1Improve measurement reliabilityFast and reliableMultiple digital computer combinationsData switching networksTraffic flow analysisInterpreted language
The present invention describes a method for collecting visitor information in a distributed browser-based traffic analysis system. The method comprises the steps of: receiving a request with a content server from a network element for an interpreted language page content; receiving the interpreted language page content, the interpreted language page content having at least one measurement code comprising a measurement element source attribute specifying a measurement program; receiving a request for the source data of the measurement element, the request comprising at least one data structure including at least one of at least one page ID and at least one category ID and at least one time stamp and other relevant data; comparing the content of the fields of the data structure(s) to a predefined set of rules in the measurement program; updating the counters or other programming structures in the measurement program based on the comparison; updating the data structure(s), and providing the network element with the updated data structure(s) and the source data for the measurement element.
Owner:INTERQUEST
Systems and methods for transforming modeled business processes into executable processes
Owner:SOFTWARE AG
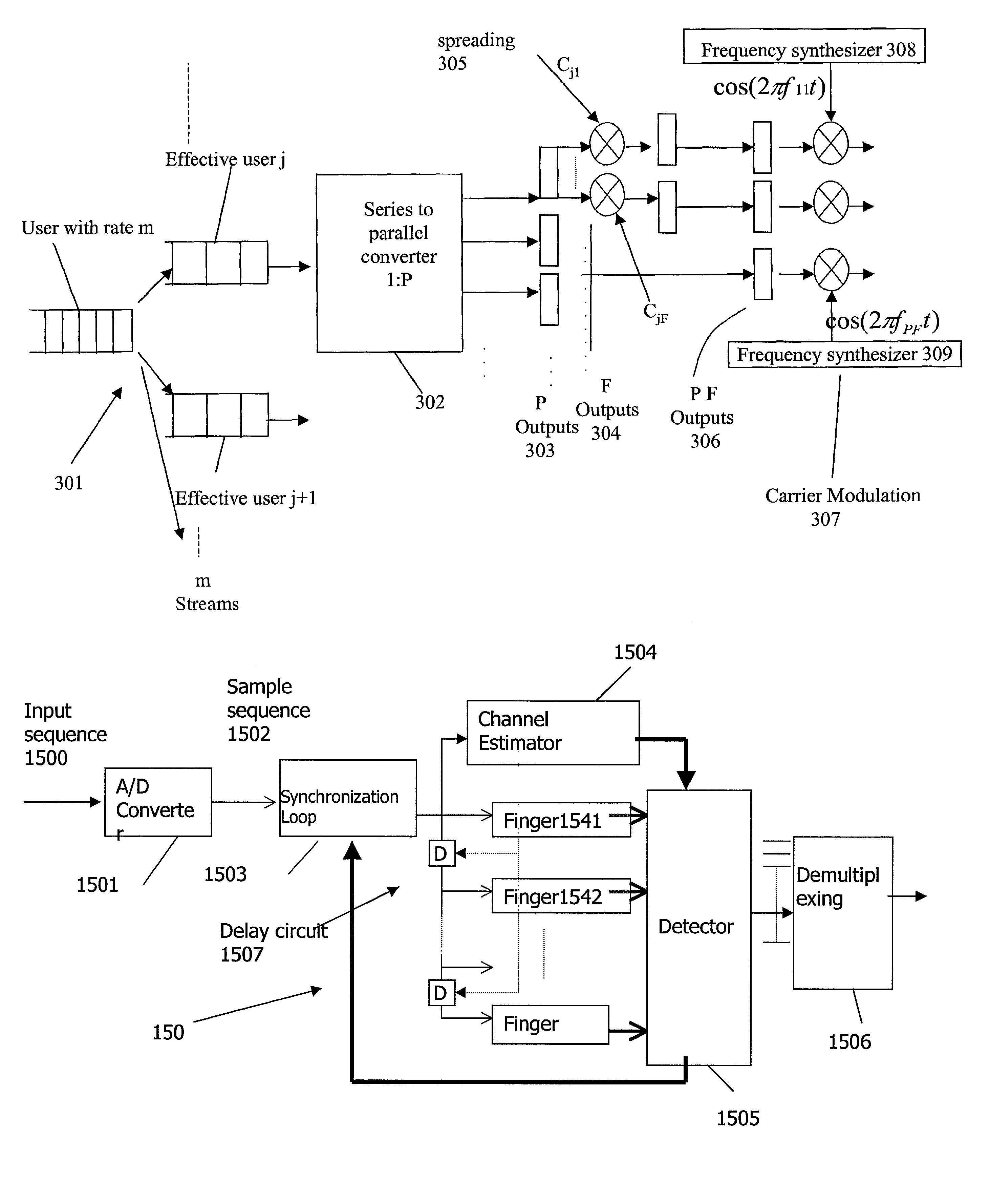
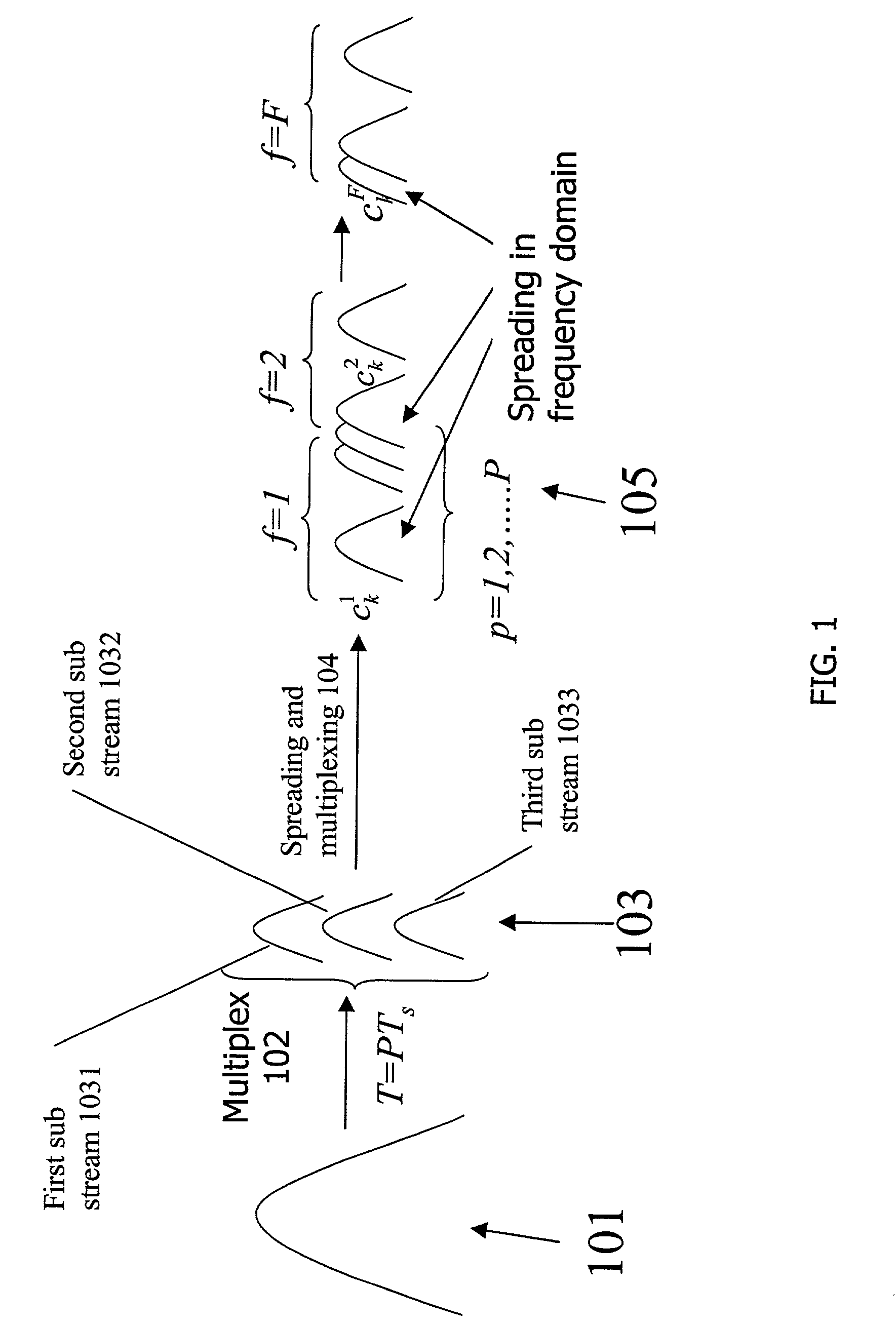
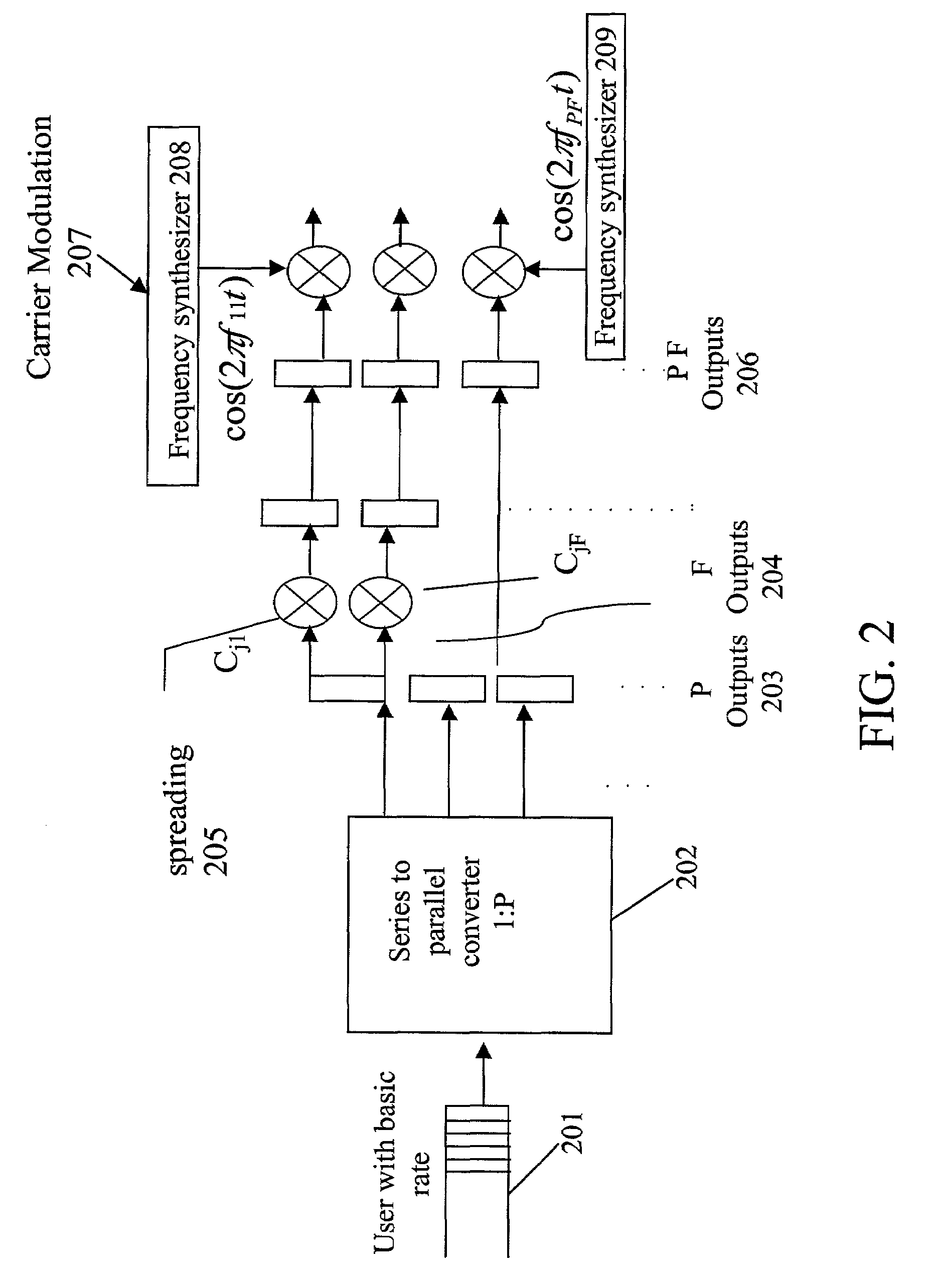
Programmable transceiver structure of multi-rate OFDM-CDMA for wireless multimedia communications
ActiveUS7035201B2Realize transmissionRadio transmissionOrthogonal multiplexHardware structureComputer hardware
Two multi-rate transmission schemes, multi-code (MC) and variable-spreading-length (VSL) code, for realizing multimedia communications on three types of OFDM-CDMA systems are proposed. These systems can be integrated into a programmable structure such that the operation can be controlled and adjusted by system parameters and thus the transceiver can be used in different systems without changing the fundamental hardware and software architecture, which serves the trend of software-radio for future application. A transceiver architecture of multi-rate OFDM-CDMA systems is illustrated and showed its programmability such that the general system can operate under different scenarios with a common hardware structure and reconfigure by software implementation.
Owner:MEDIATEK INC
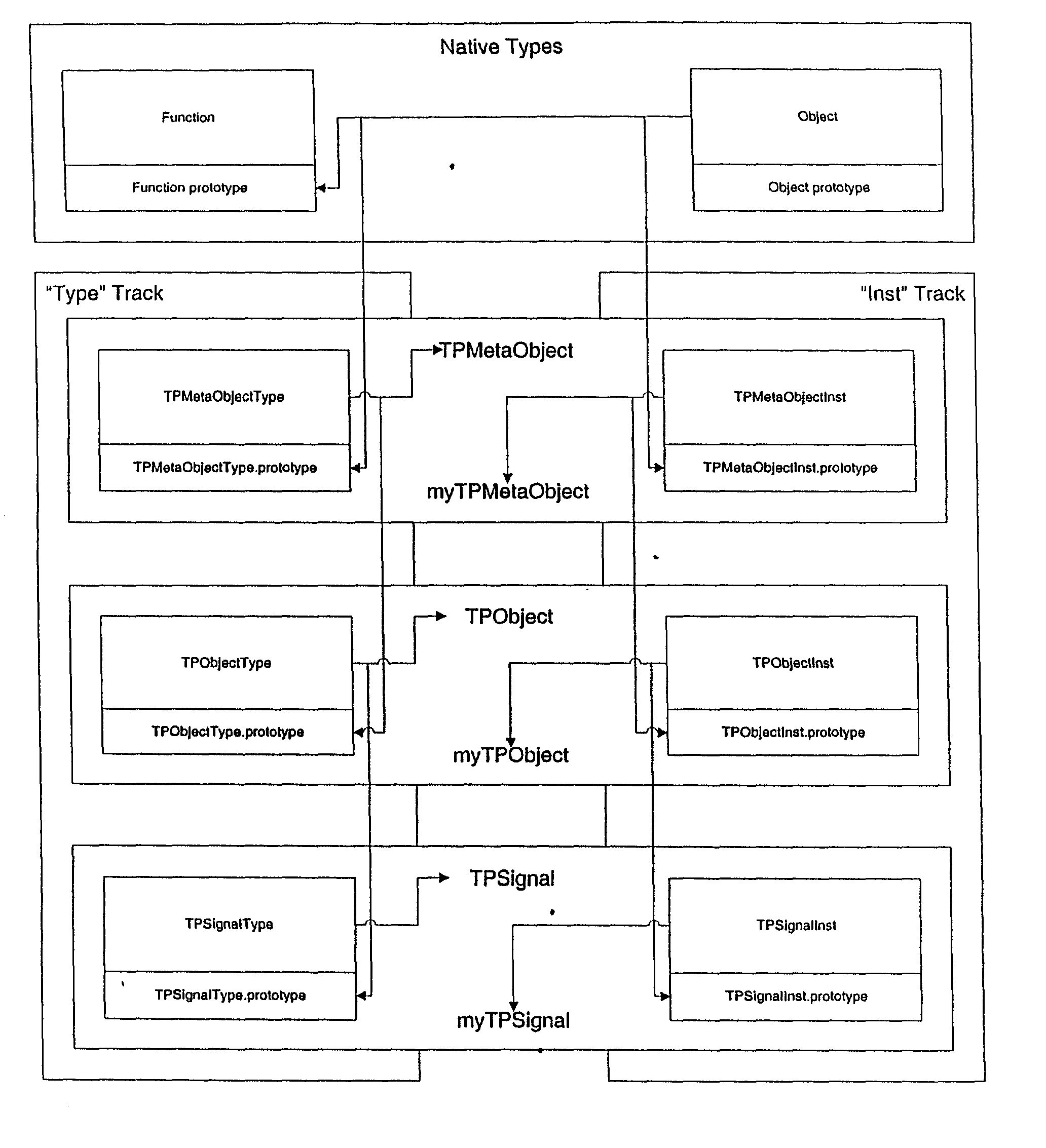
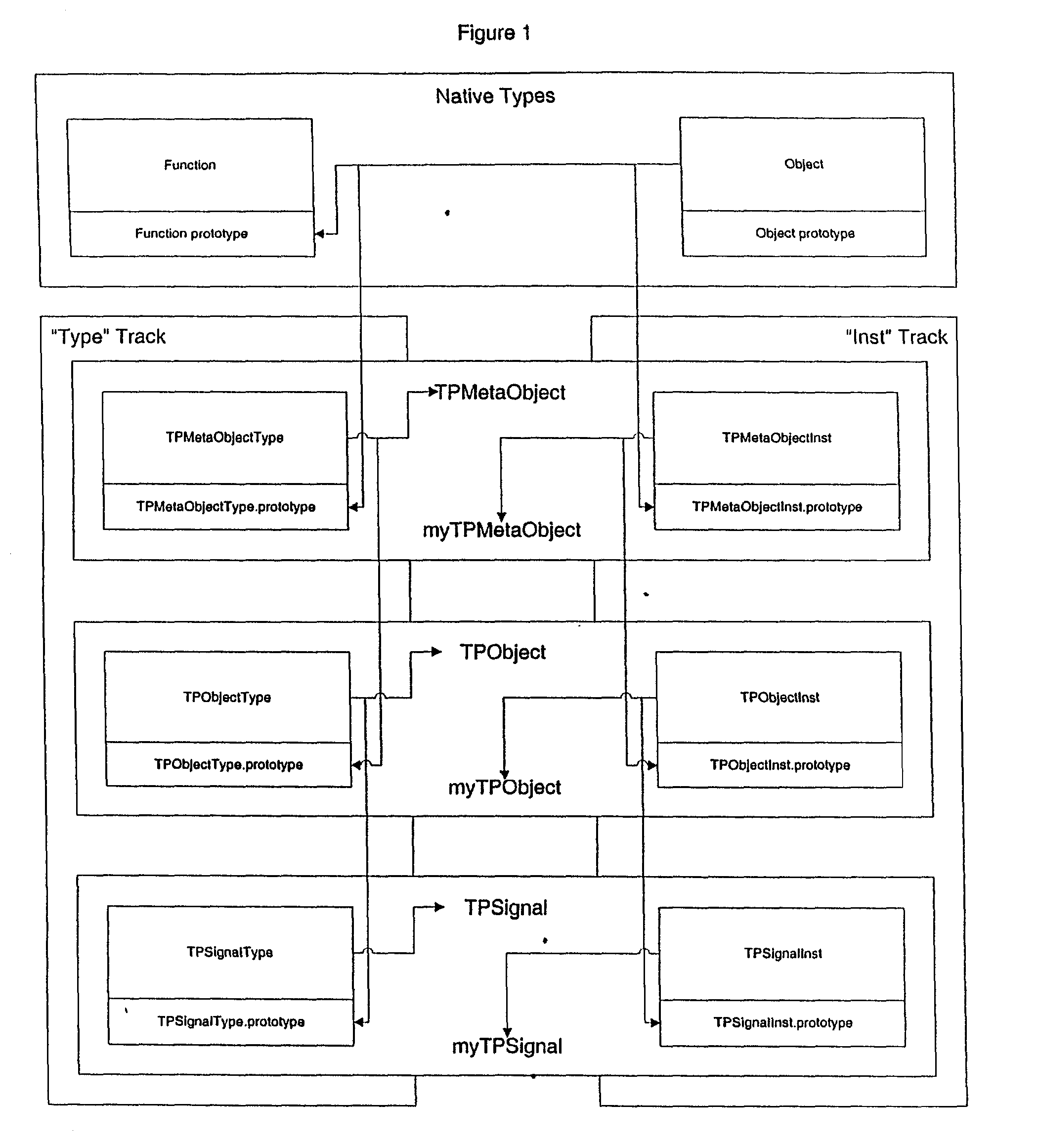
System supporting object-oriented constructs in ECMAScript
InactiveUS20030120824A1Multiprogramming arrangementsSpecific program execution arrangementsType conversionMultiple inheritance
An internally consistent system implementing object-oriented programming constructs in ECMAScript is described. First, a function, rather than the ECMAScript new keyword, is used to initiate new instance creation. The instance creation function is assigned to a non-Function instance rather than an instance of Function as required for use of new. Instances with attached instance creation functions serve as "type proxy" objects and replace the Function instances normally used as types. Since the type proxies and prototype chains created and maintained by the invention are instances of normal objects, rather than instances of Function as required by standard ECMAScript, this approach allows native ECMAScript lookup semantics to be leveraged while supporting inheritance of both state and behavior for instances and types to any level desired. A set of functions known herein as property-definition functions are used by type proxies to assign properties as global, local, instance, or type properties rather than the standard ECMAScript approach of direct assignment. Where constraints exist such as "read-only", "private", etc. the physical storage of the property may be located away from the target object in a separate storage structure. Method definitions further place a "backstop" method on Object.prototype. Invocation of the backstop triggers a callback to the non-implementing receiver followed by a scan of guardians for multiple inheritance, followed by dynamic type conversion and method creation. The result is a highly enhanced system of polymorphic behavior.
Owner:SHATTUCK SCOTT +2
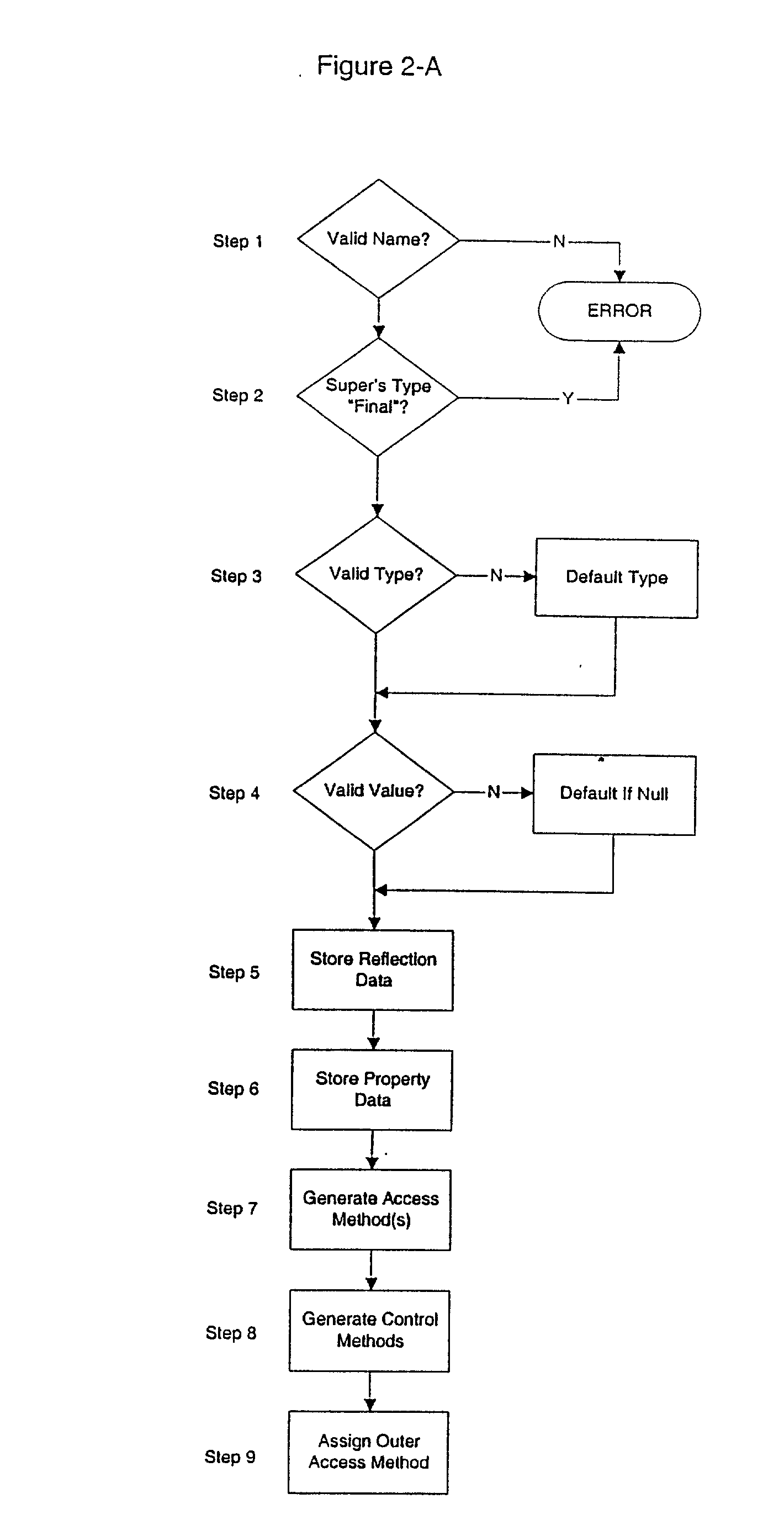
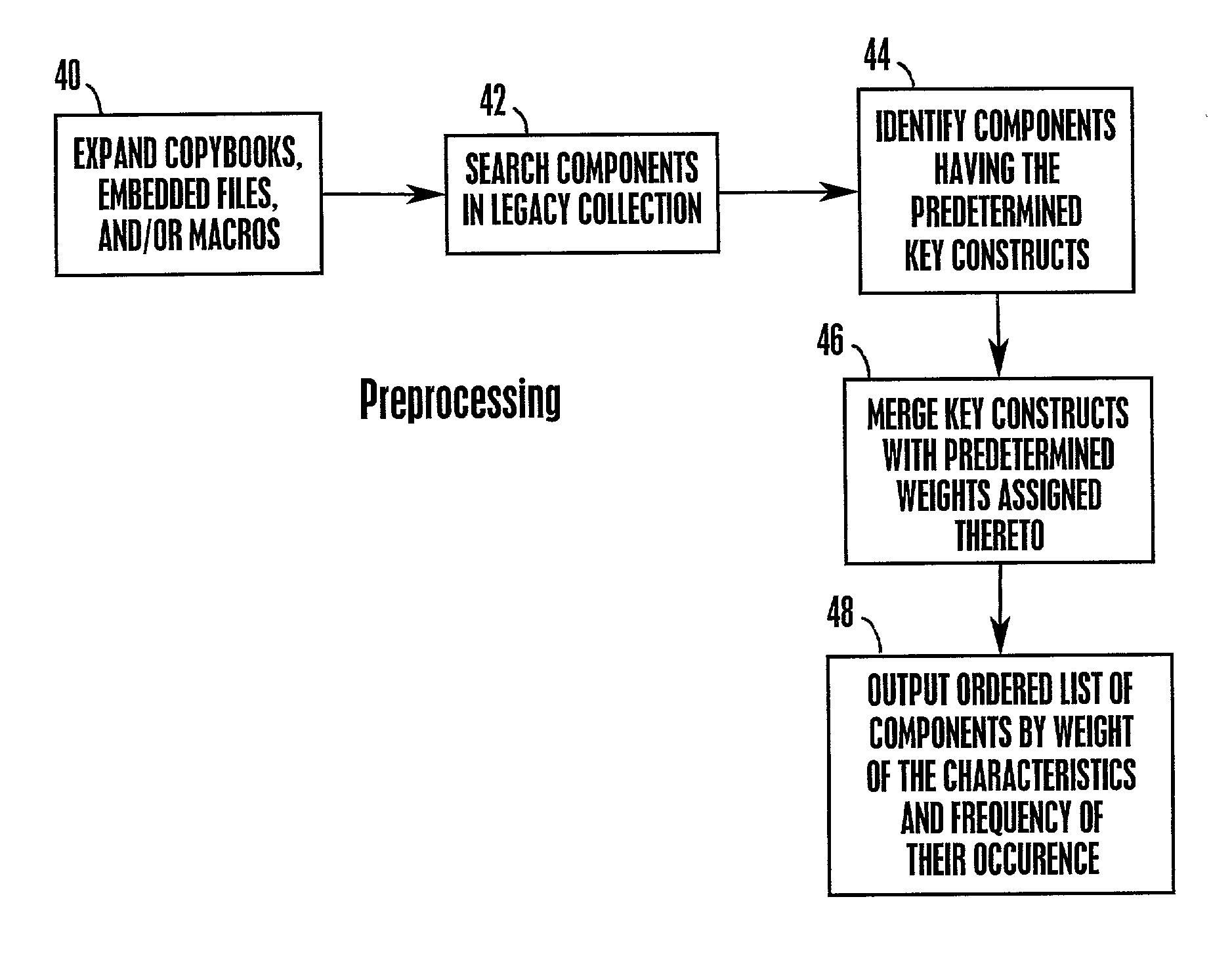
System, method, and computer program product for creating a hierarchy of software components based on the programming constructs therein
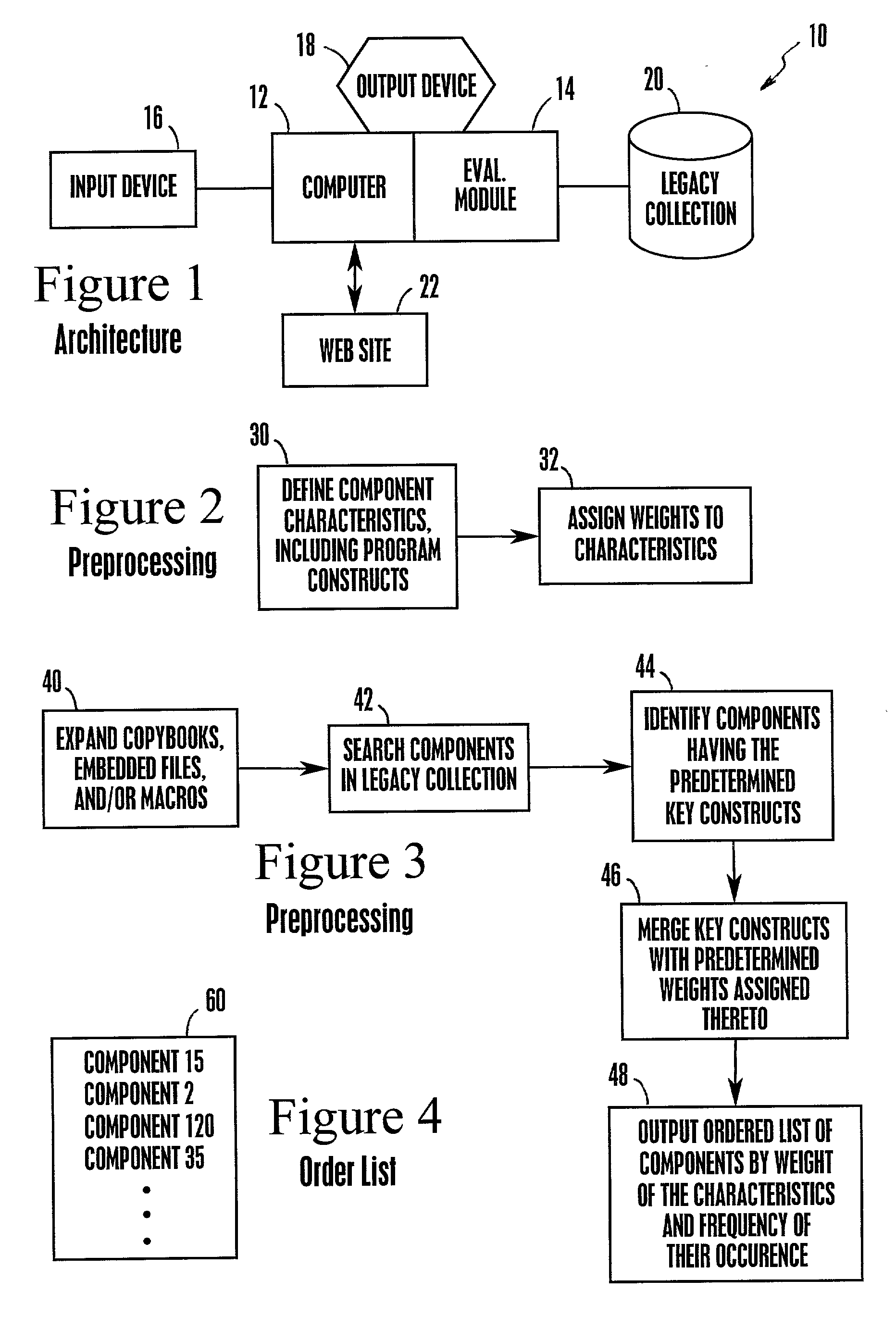
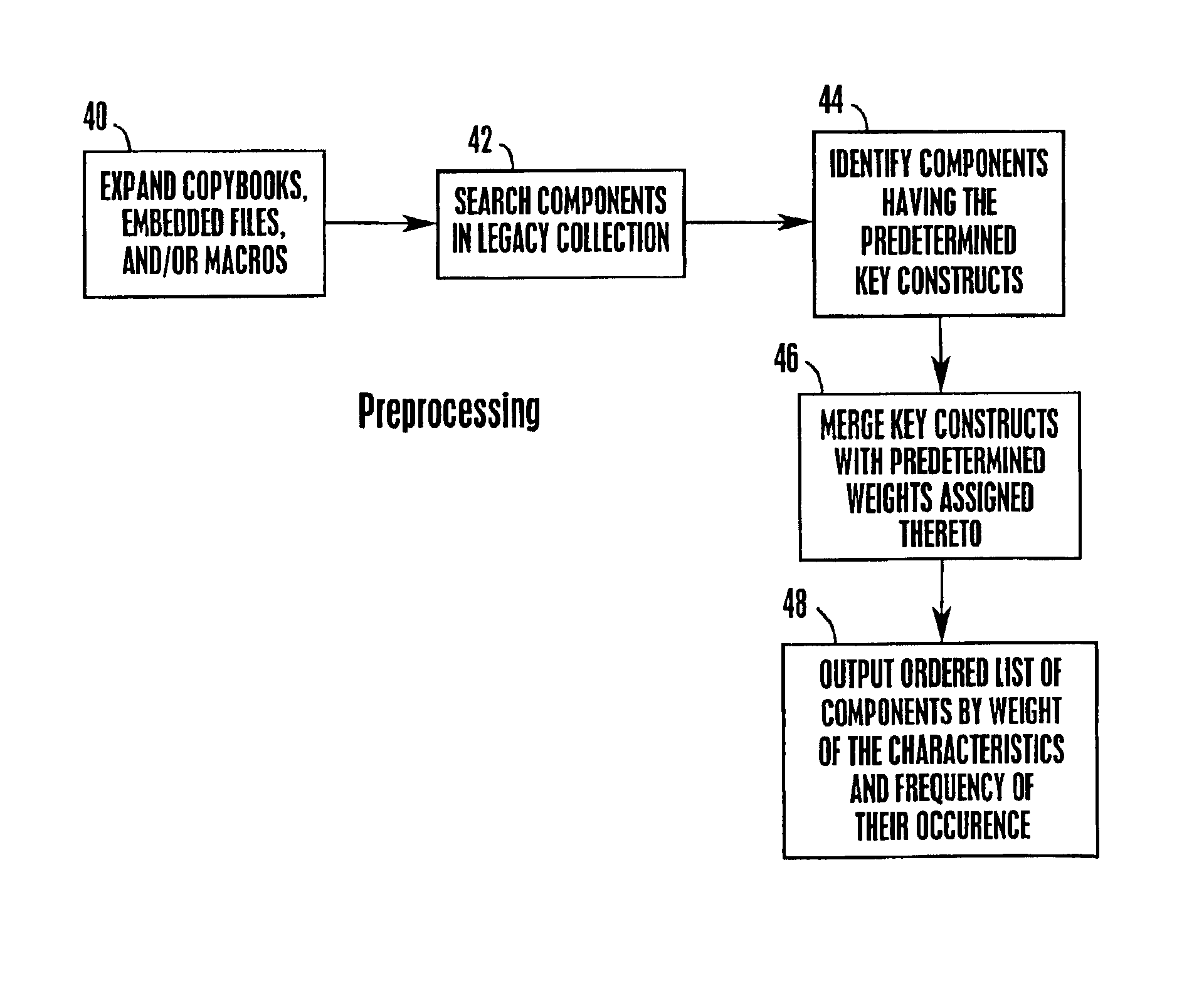
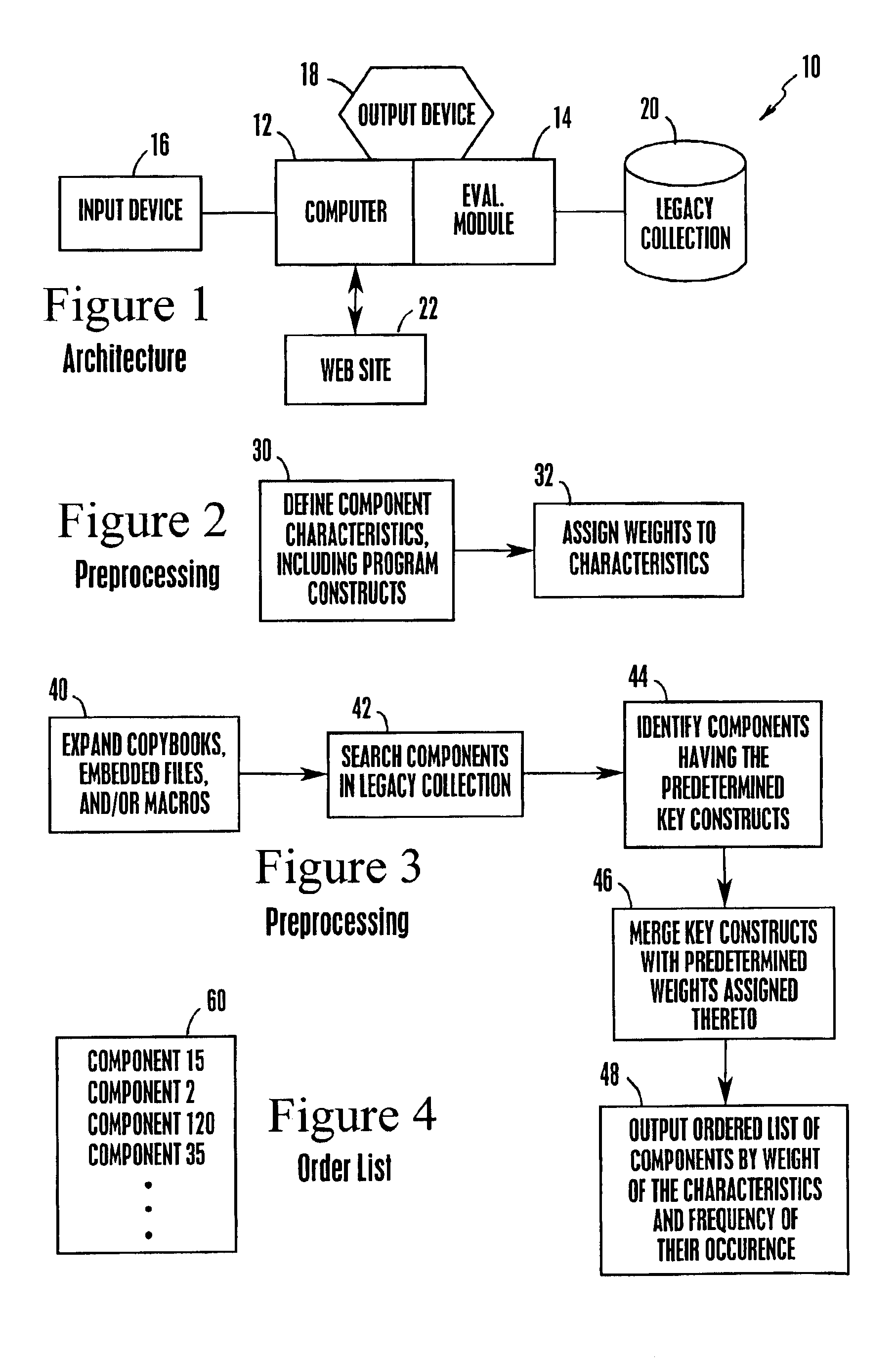
InactiveUS20020194577A1Software reuseSpecific program execution arrangementsProgramming constructsComputer program
A hierarchy of software components is created based on the programming constructs therein using a computer linked to a database having a collection of legacy software therein. Key component characteristics, e.g., programming constructs are defined. These constructs are assigned weights based on the difficulty or ease with which they can be reused in a new software component for use with a Web system or other network system. The legacy collection is searched to determine which, if any, of the key constructs are included therein. An ordered list is output that includes a list of the components containing the key constructs. The order of the list is based on the weight of the constructs in each component and the frequency with which they occur in each component. The list is then used to determine the effort and thus, the expense required to move entire components or blocks of code in the components into a Web system or other network system.
Owner:IBM CORP
Technique for computational nested parallelism
ActiveUS20130298133A1Overcome limitationsResource allocationProcessor architectures/configurationProgramming constructsSemantics
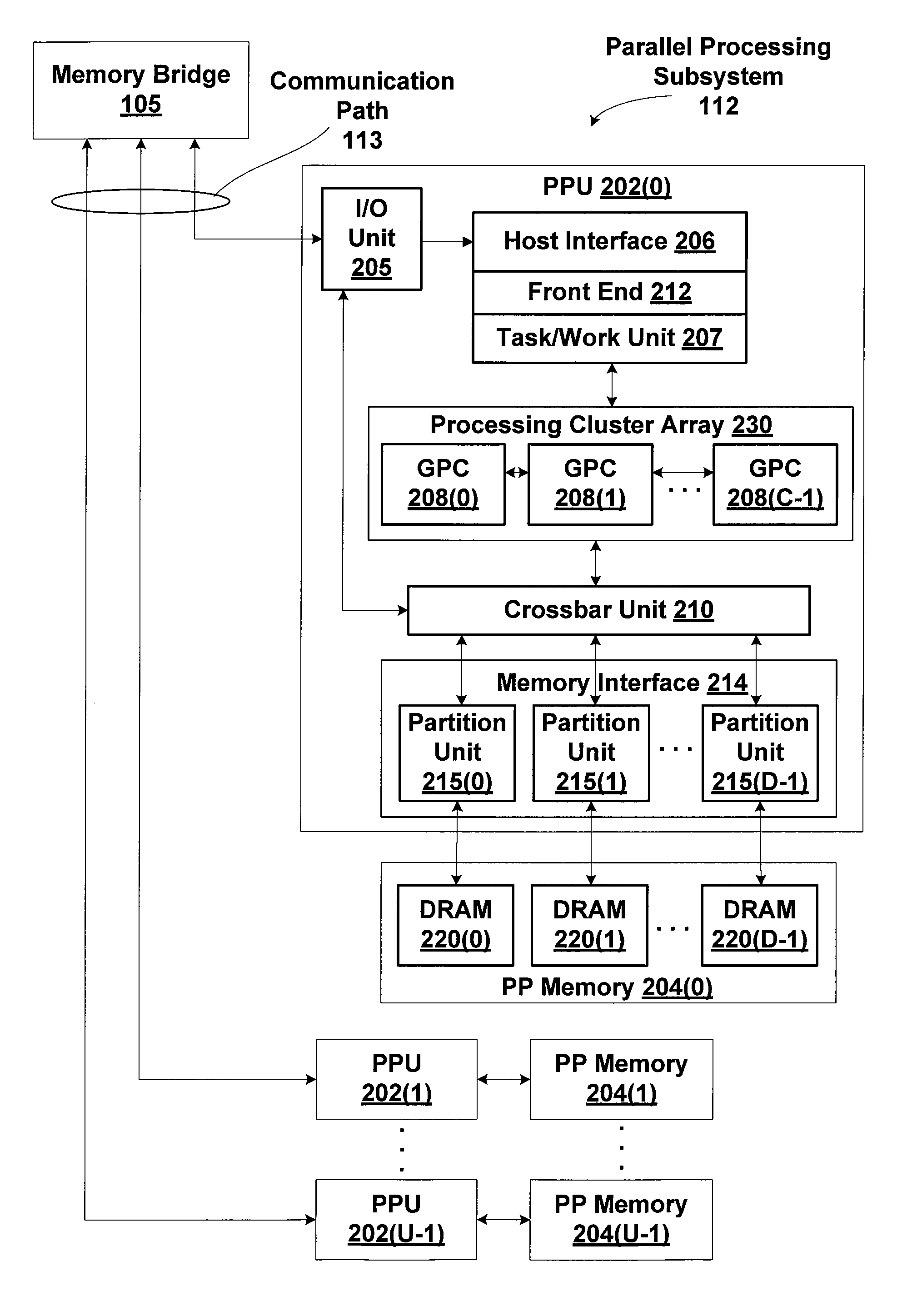
One embodiment of the present invention sets forth a technique for performing nested kernel execution within a parallel processing subsystem. The technique involves enabling a parent thread to launch a nested child grid on the parallel processing subsystem, and enabling the parent thread to perform a thread synchronization barrier on the child grid for proper execution semantics between the parent thread and the child grid. This technique advantageously enables the parallel processing subsystem to perform a richer set of programming constructs, such as conditionally executed and nested operations and externally defined library functions without the additional complexity of CPU involvement.
Owner:NVIDIA CORP
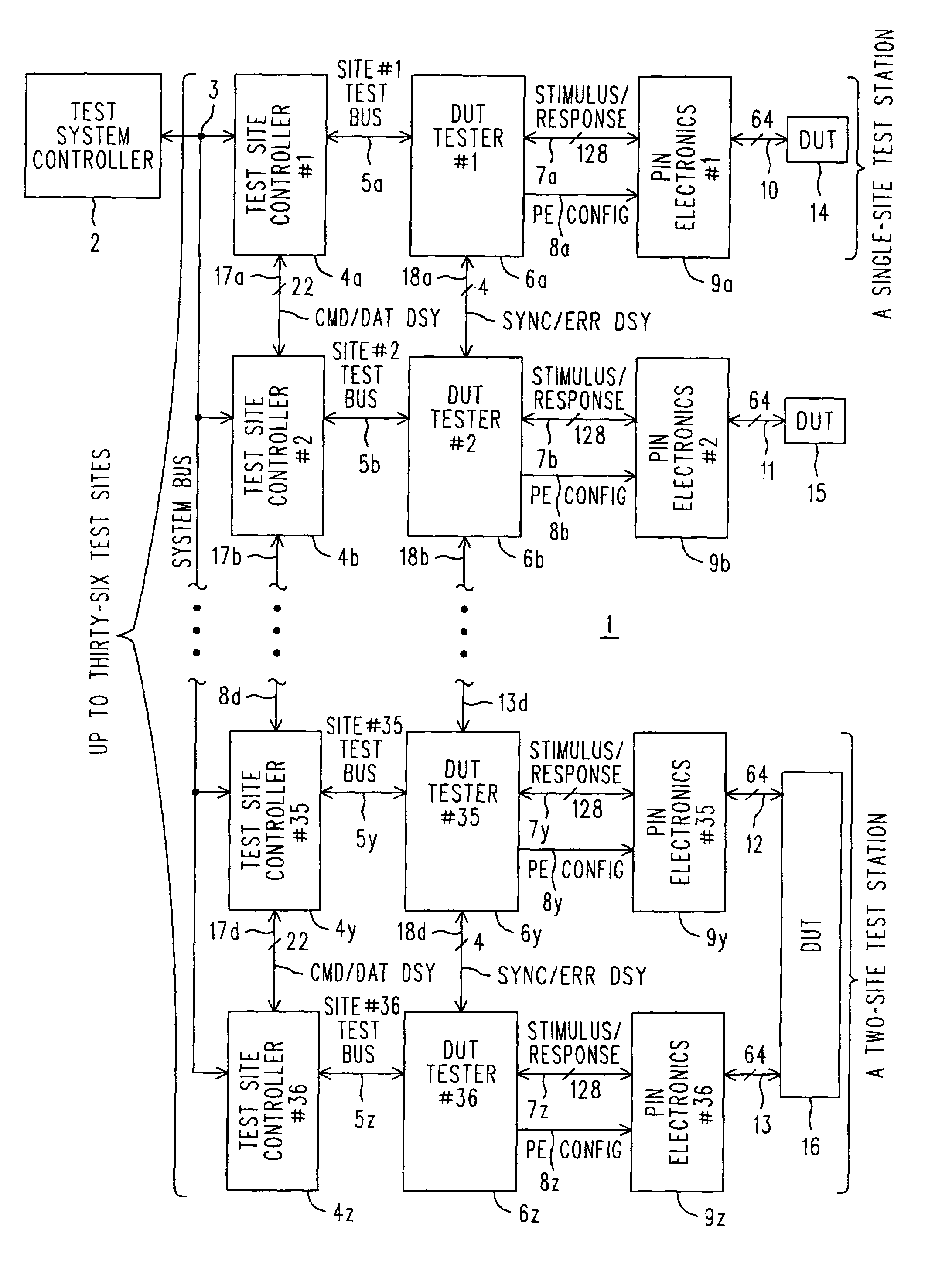
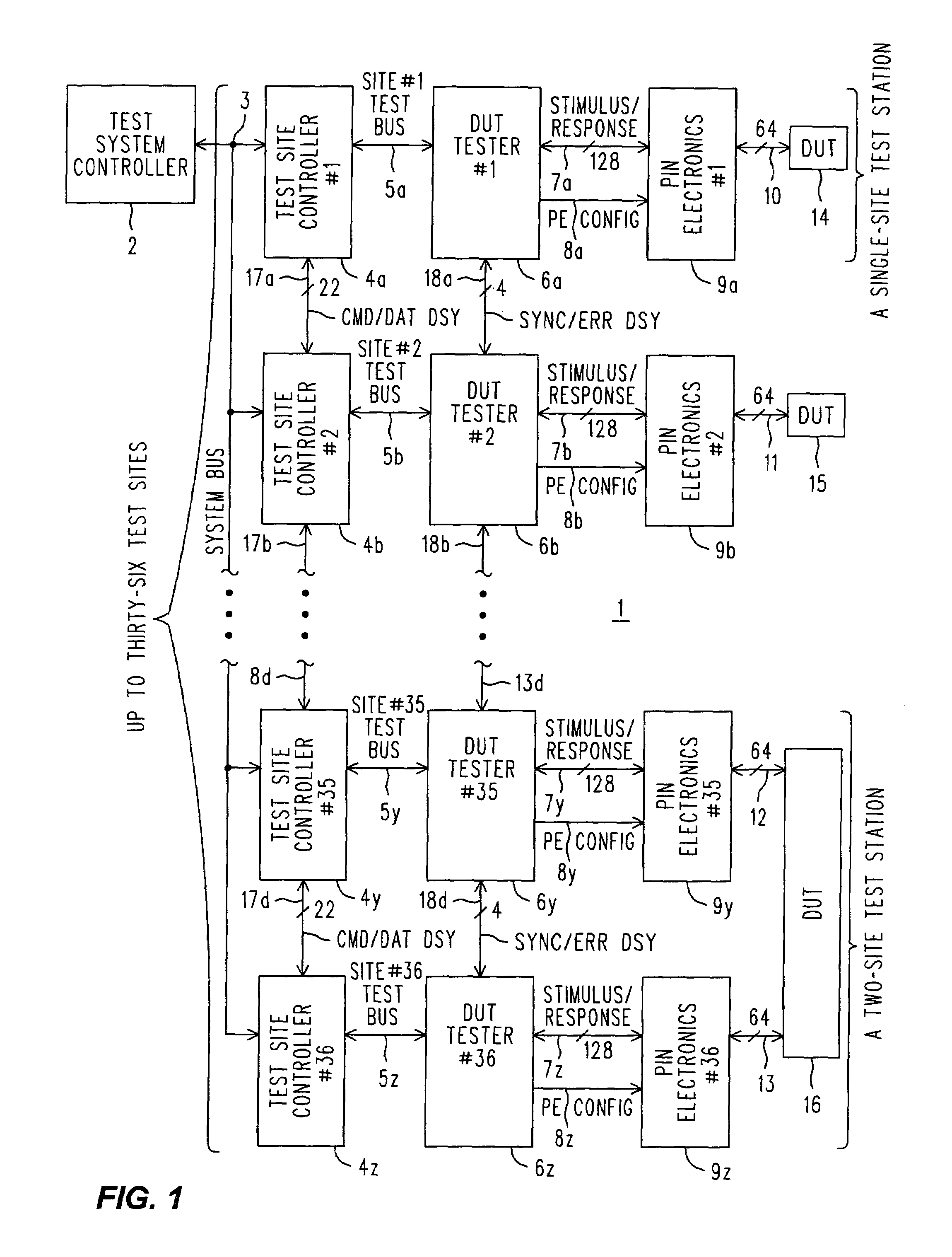
Method and system for testing communication protocols in network communication
InactiveUS20060262729A1Simplify writingError preventionTransmission systemsComputer hardwareTest script
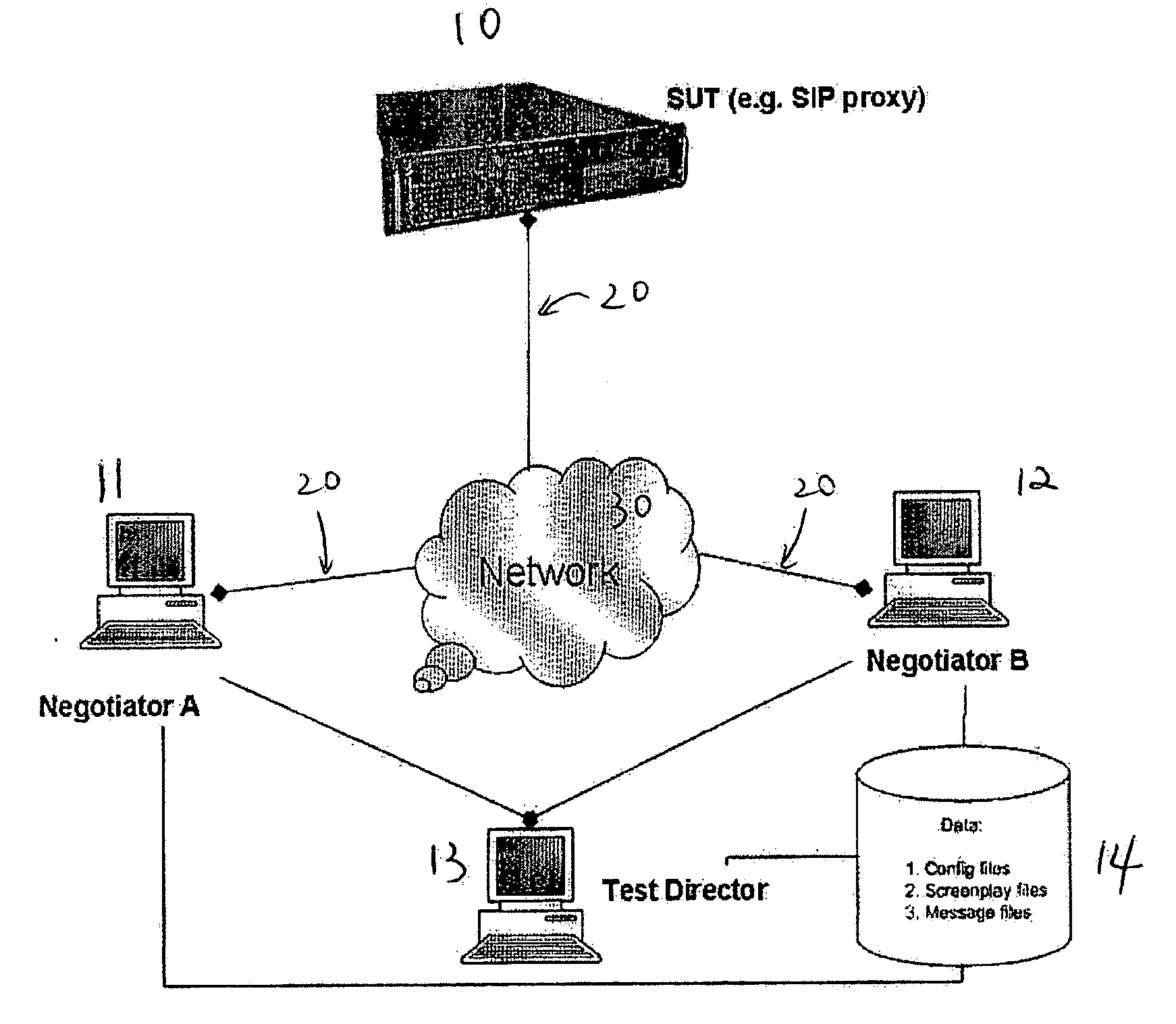
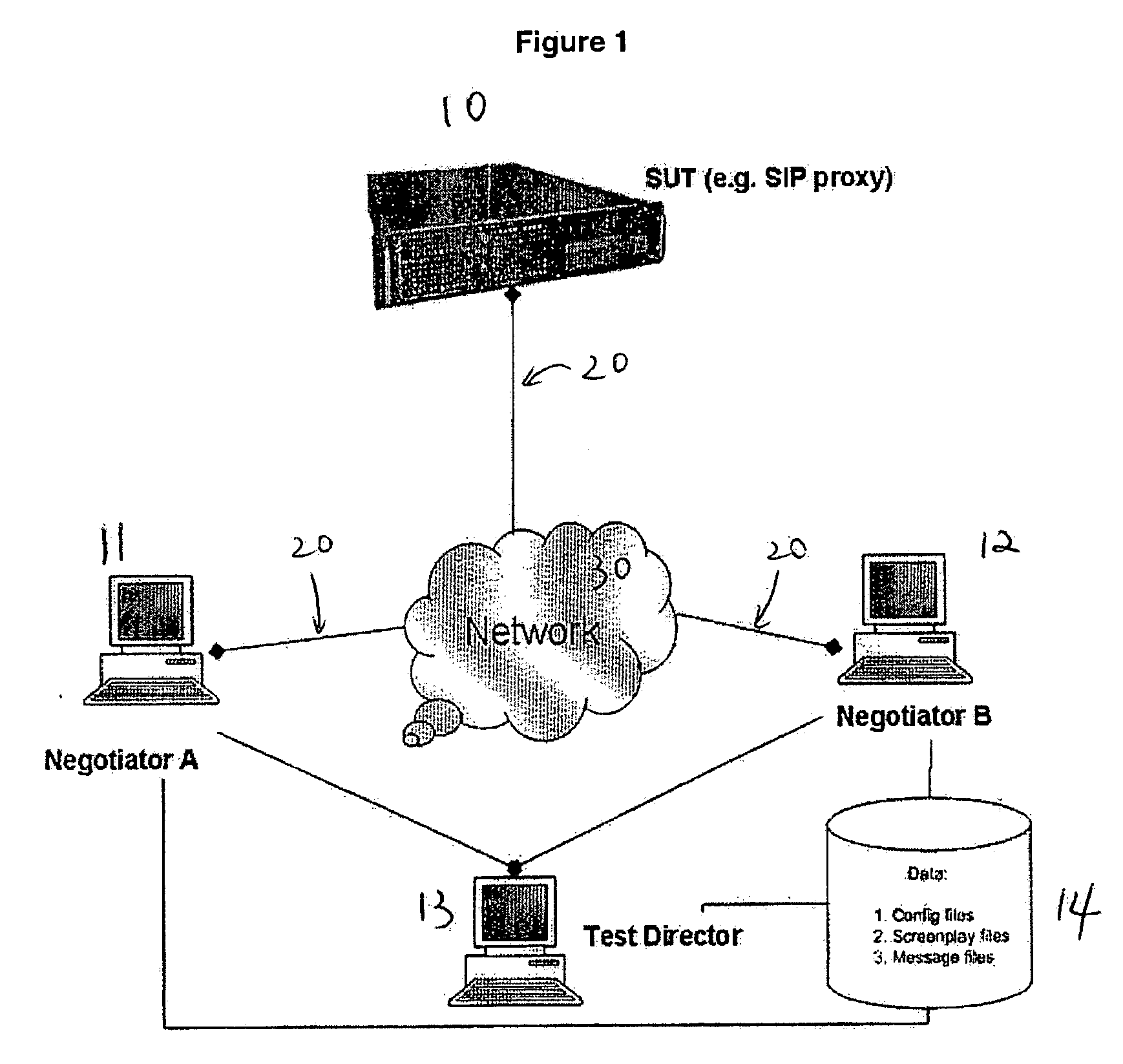
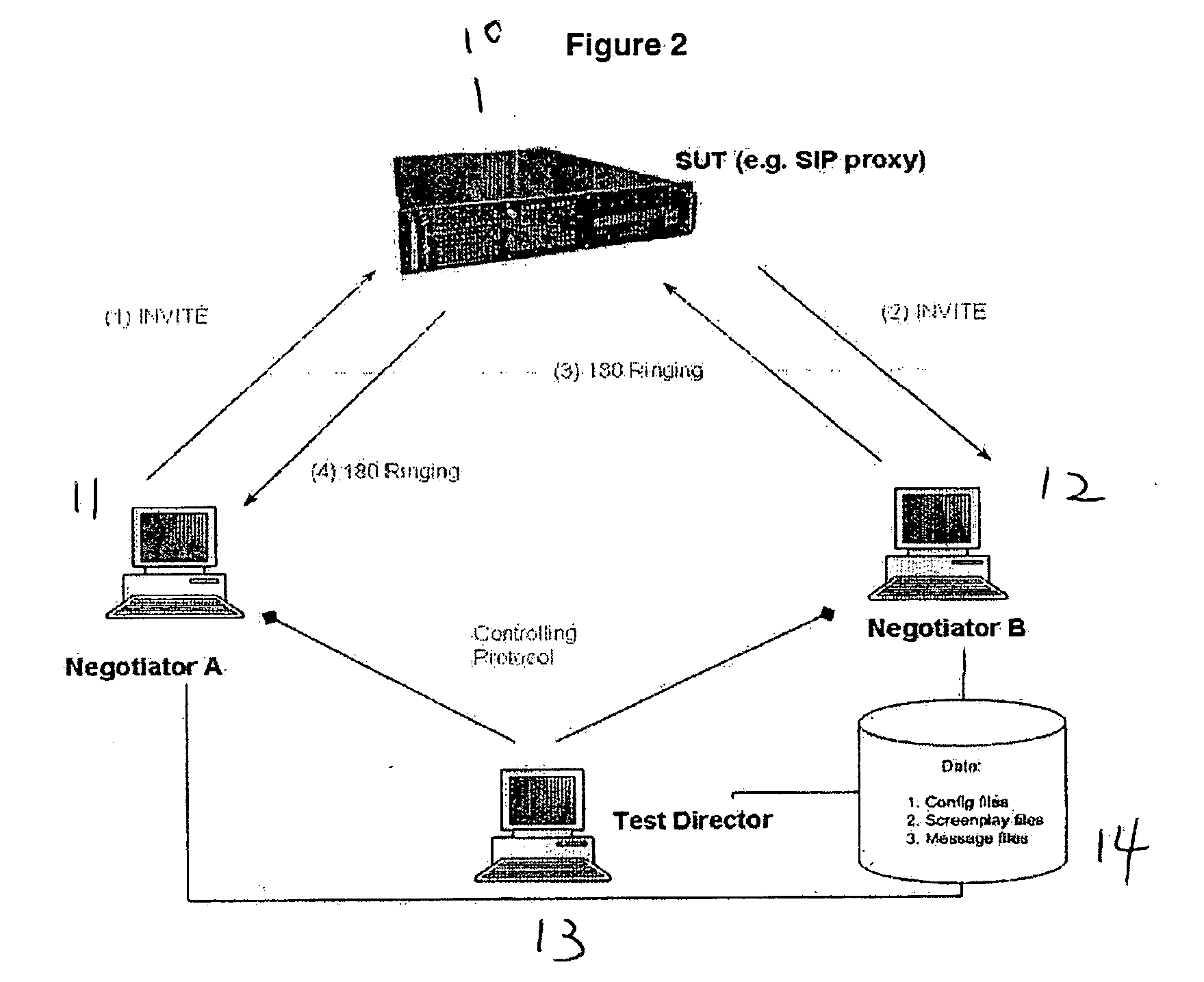
A framework or system is described for testing compliance and robustness of a communication signal protocol employed by an entity which is connected to an IP based network, particularly for testing a SIP enabled entity or device. Within the framework, multiple test clients are coordinated by a centralized test controller and thus test progress and results can be controlled and monitored in a centralized manner. The framework uses simple template-based test scripts which are easy to write and does not involve complex programming constructs.
Owner:HONG KONG APPLIED SCI & TECH RES INST
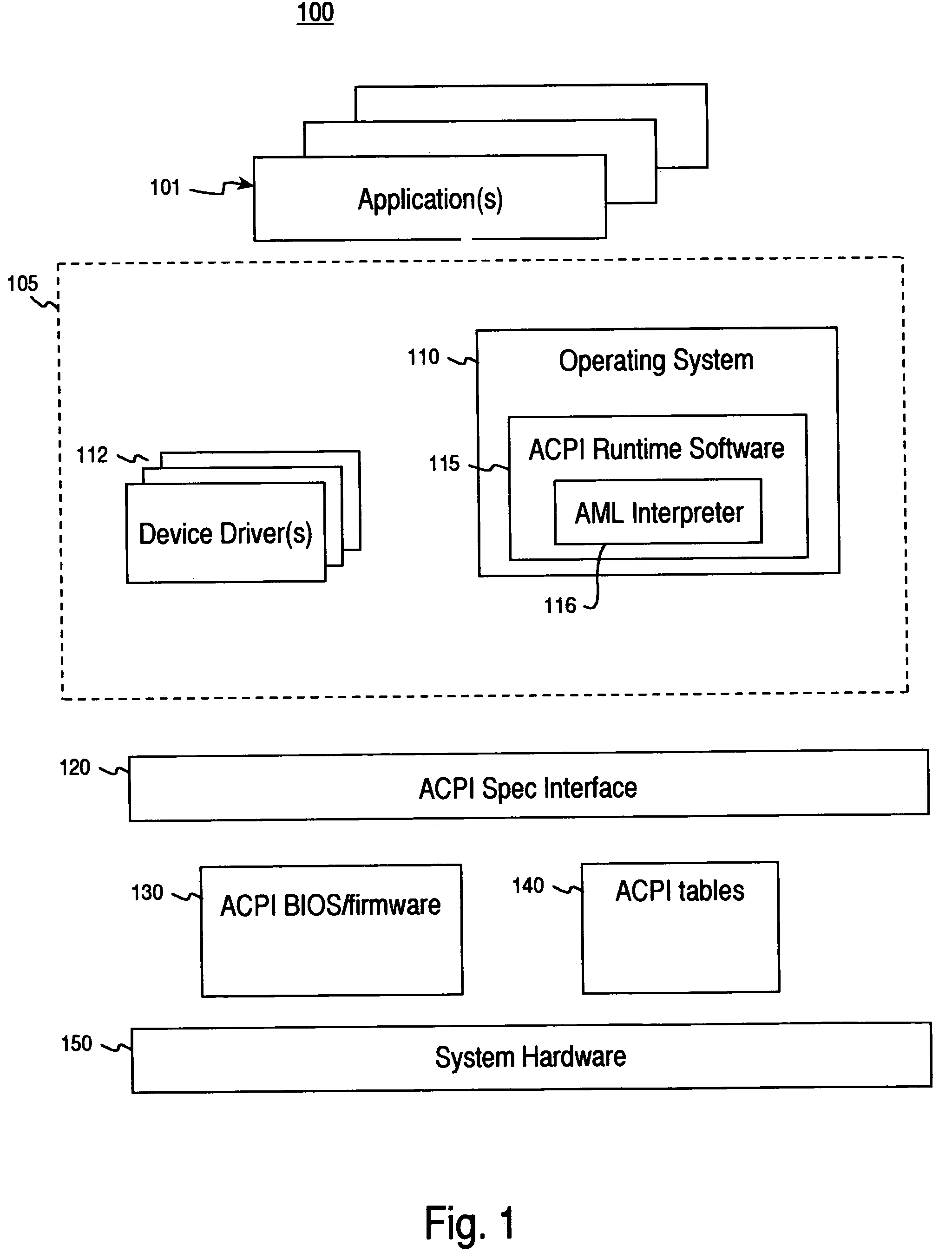
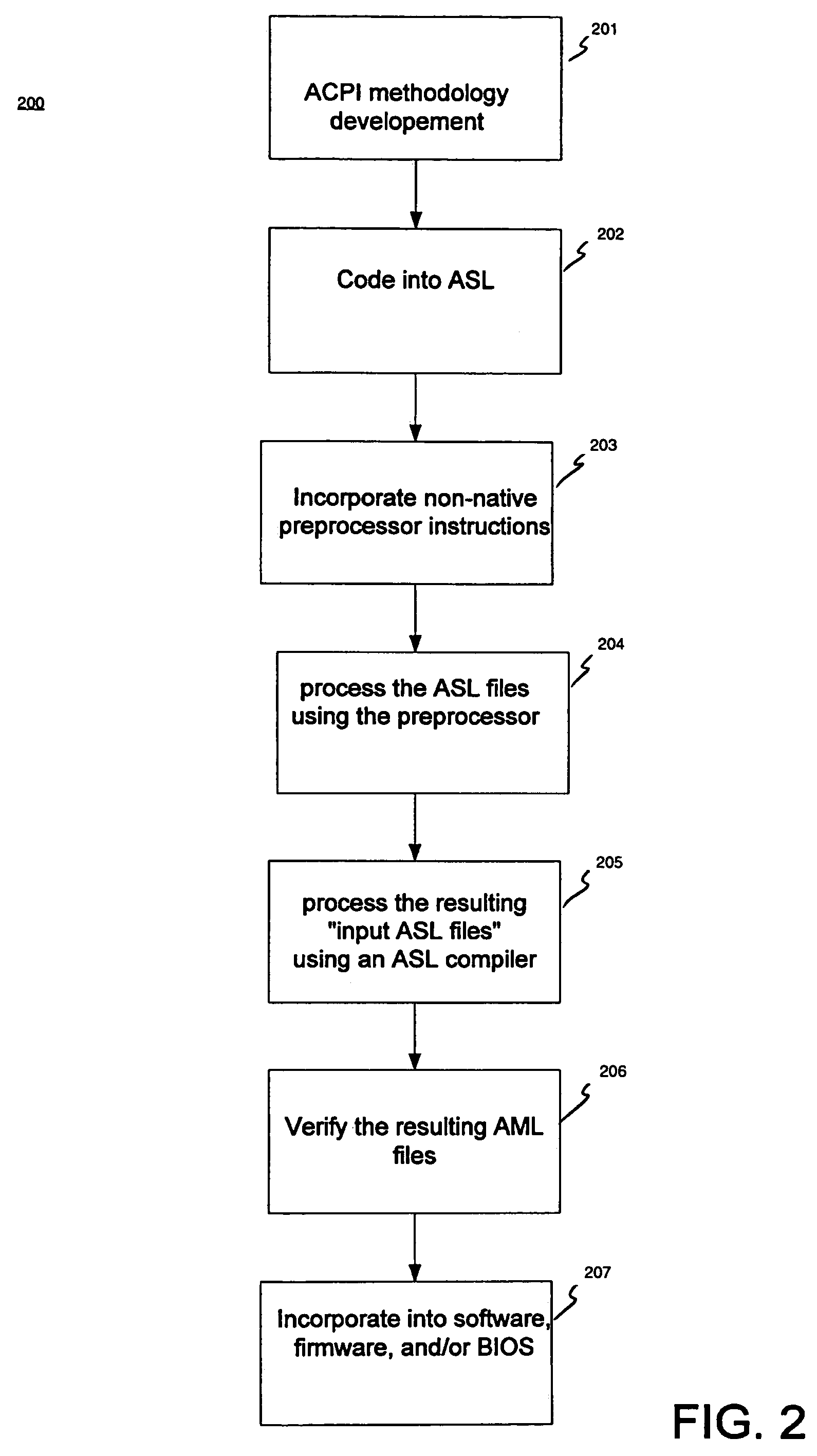
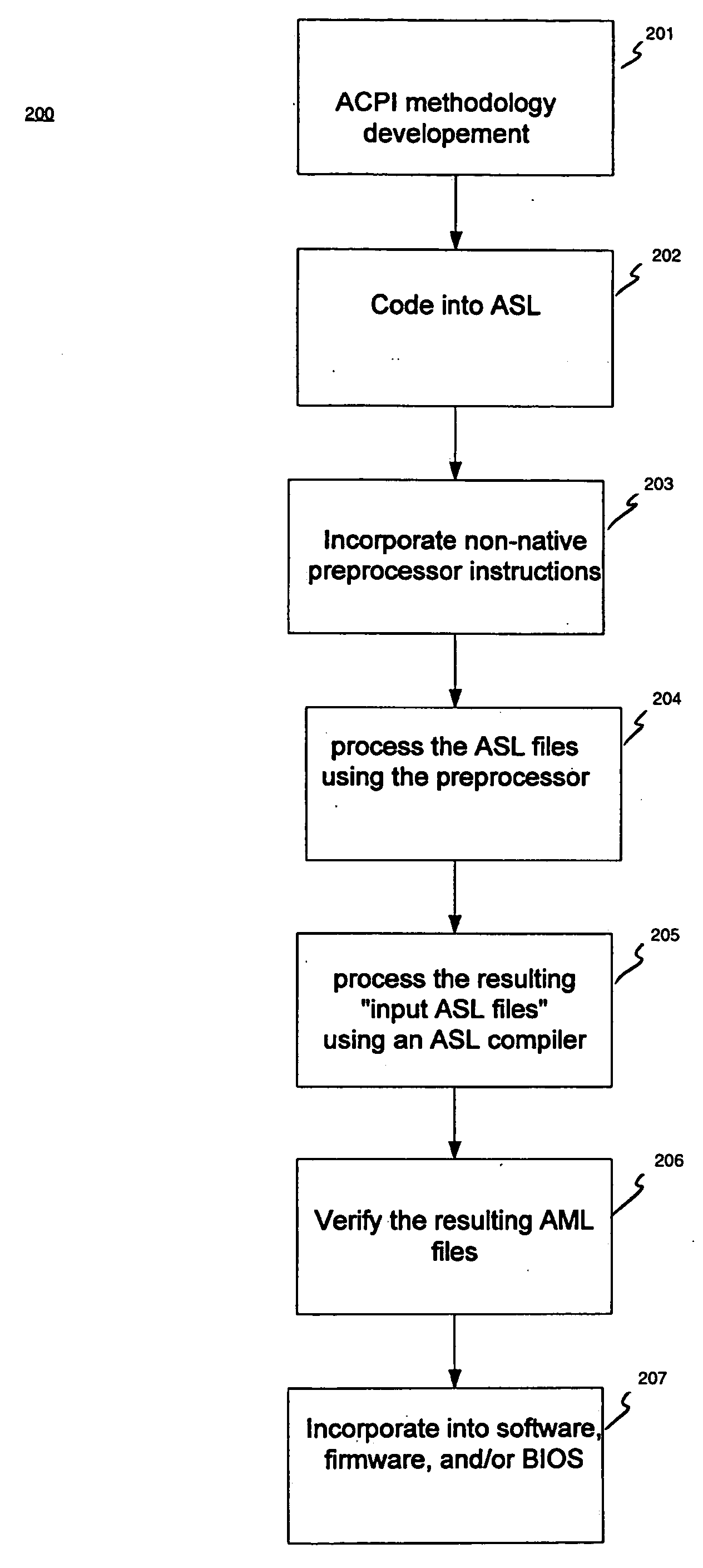
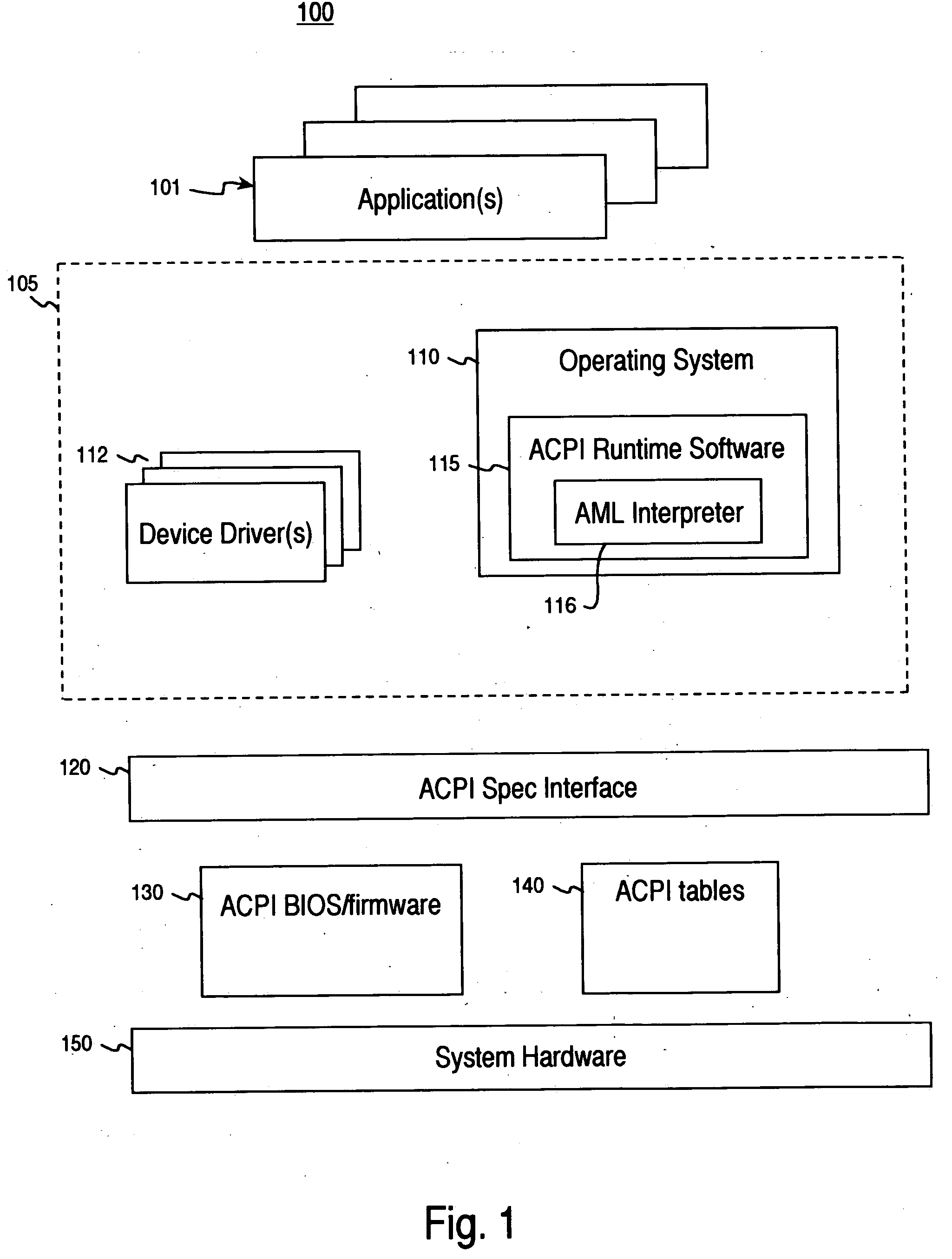
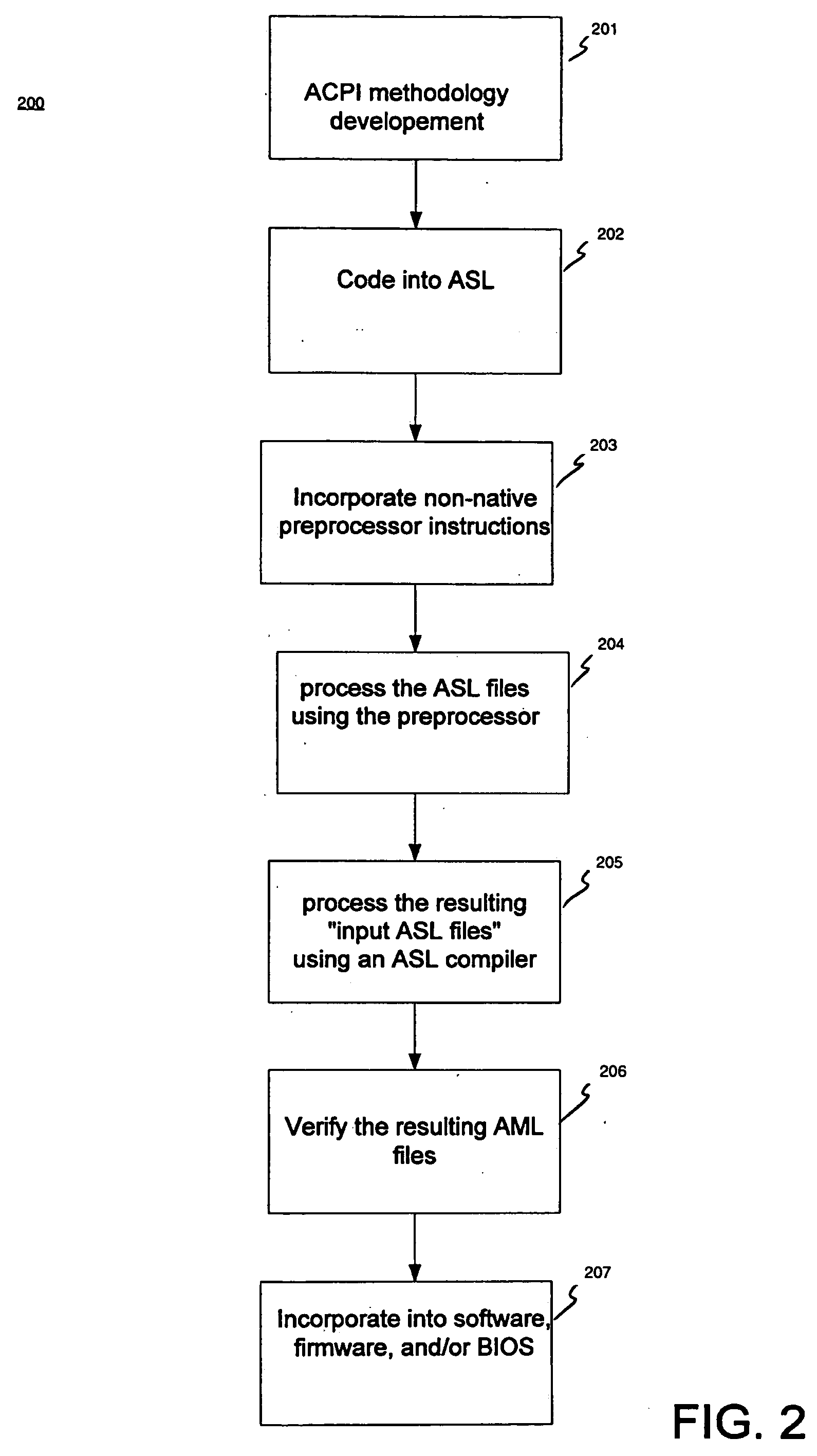
ACPI preprocessor
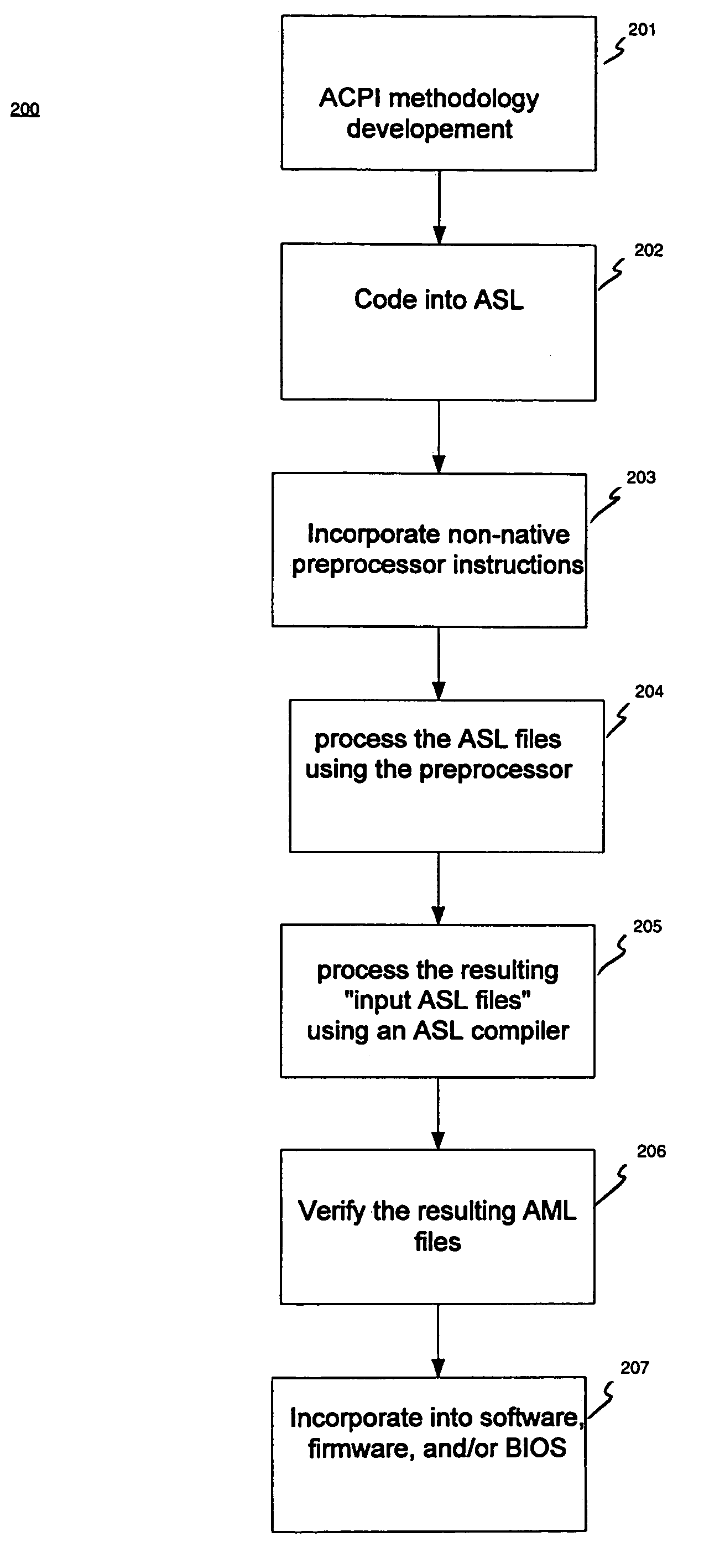
InactiveUS7188339B2Volume/mass flow measurementPower supply for data processingProgramming constructsHuman language
A computer-implemented method for compiling ASL (ACPI Source Language) code into AML (ACPI machine language) code. The method includes accessing an ASL program. A preprocessor is executed to process the ASL program and to insert support for at least one non-native programming construct. The ASL program is then processed using an ASL compiler to compile the ASL program into a resulting AML program.
Owner:HEWLETT PACKARD DEV CO LP
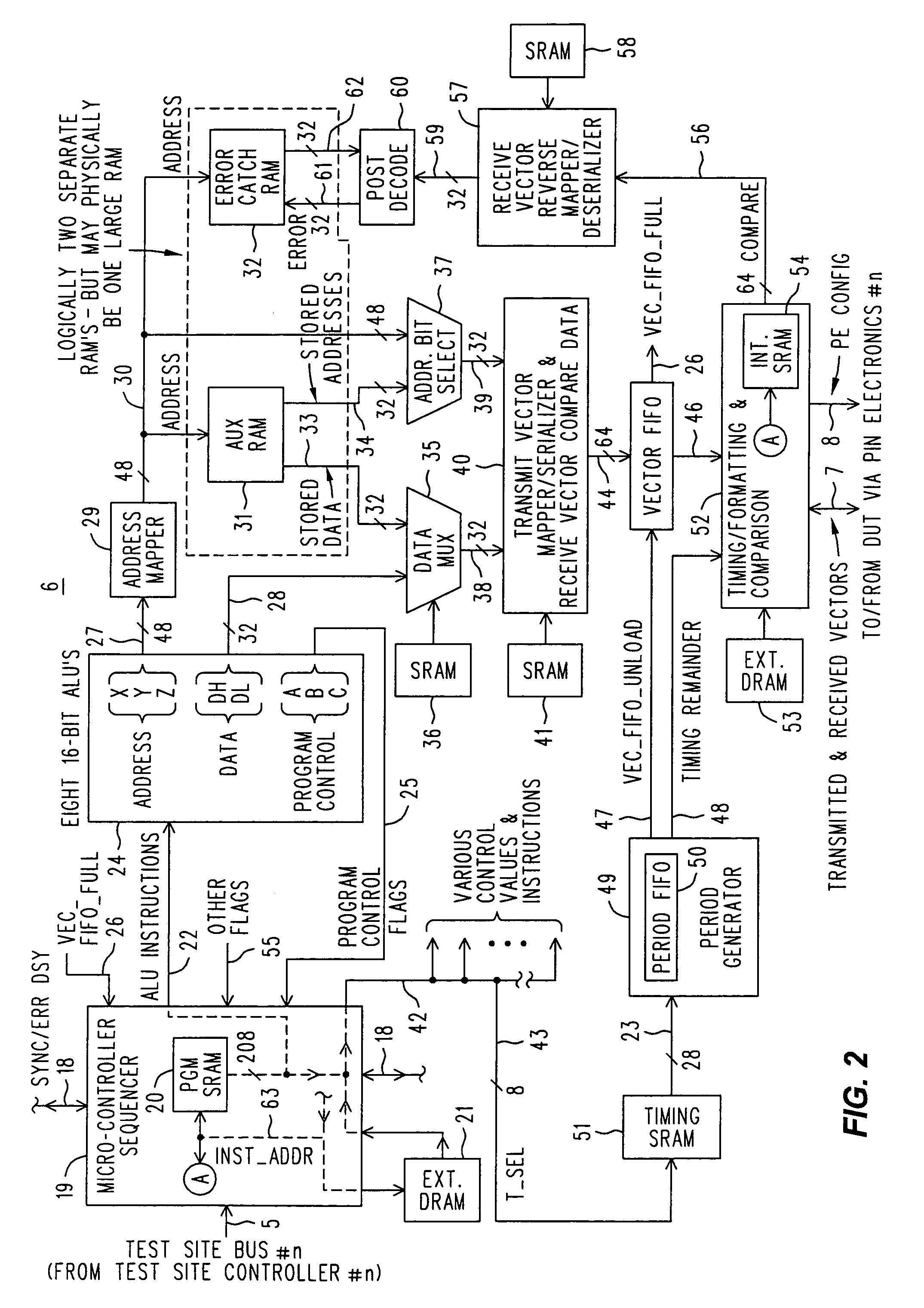
Memory tester uses arbitrary dynamic mappings to serialize vectors into transmitted sub-vectors and de-serialize received sub-vectors into vectors
InactiveUS7076714B2Solve the real problemElectronic circuit testingError detection/correctionTheoretical computer scienceProgramming constructs
The problem of sequentially “squeezing” small fields of data in a larger data path in and out of a memory device can be solved in an algorithmically driven memory tester by defining sub-vectors to represent data in the small field, where a sequence of sub-vectors represents the data that would be represented by a full sized vector if such a full sized vector could be applied to the DUT. A programming construct in the programming language of the algorithmically driven memory tester allows sub-vectors to be defined, as well as an arbitrary mapping that each is to have. The arbitrary mapping is not static, but changes dynamically as different sub-vectors are encountered. Arbitrary dynamic mappings change as sub-vectors are processed, and may include the notion that, during the activity for a sub-vector, this (or these) bit(s) of a vector do not (presently) map to any pin at all of the DUT. The arbitrary dynamic mapping is implemented by a collection of MUX's configured by data stored ahead of time in an SRAM, in accordance with what defining program constructs are encountered by the compiler as it processes the test program. A dynamic reverse mapper, also a collection of MUX's similarly controlled by an SRAM, serves as a de-serializer that assembles a sequence of received sub-vectors into a final received full-sized vector.
Owner:ADVANTEST CORP
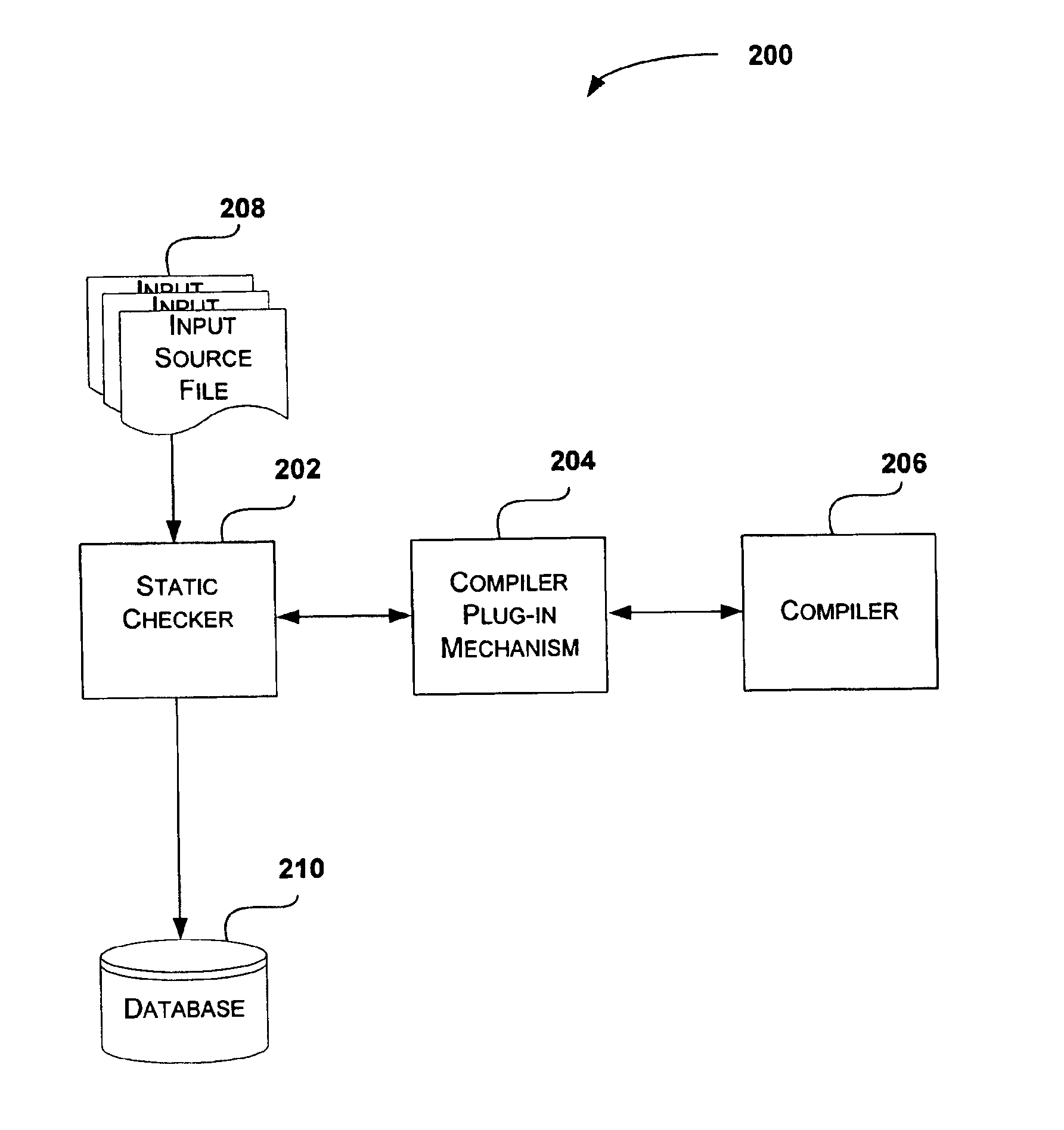
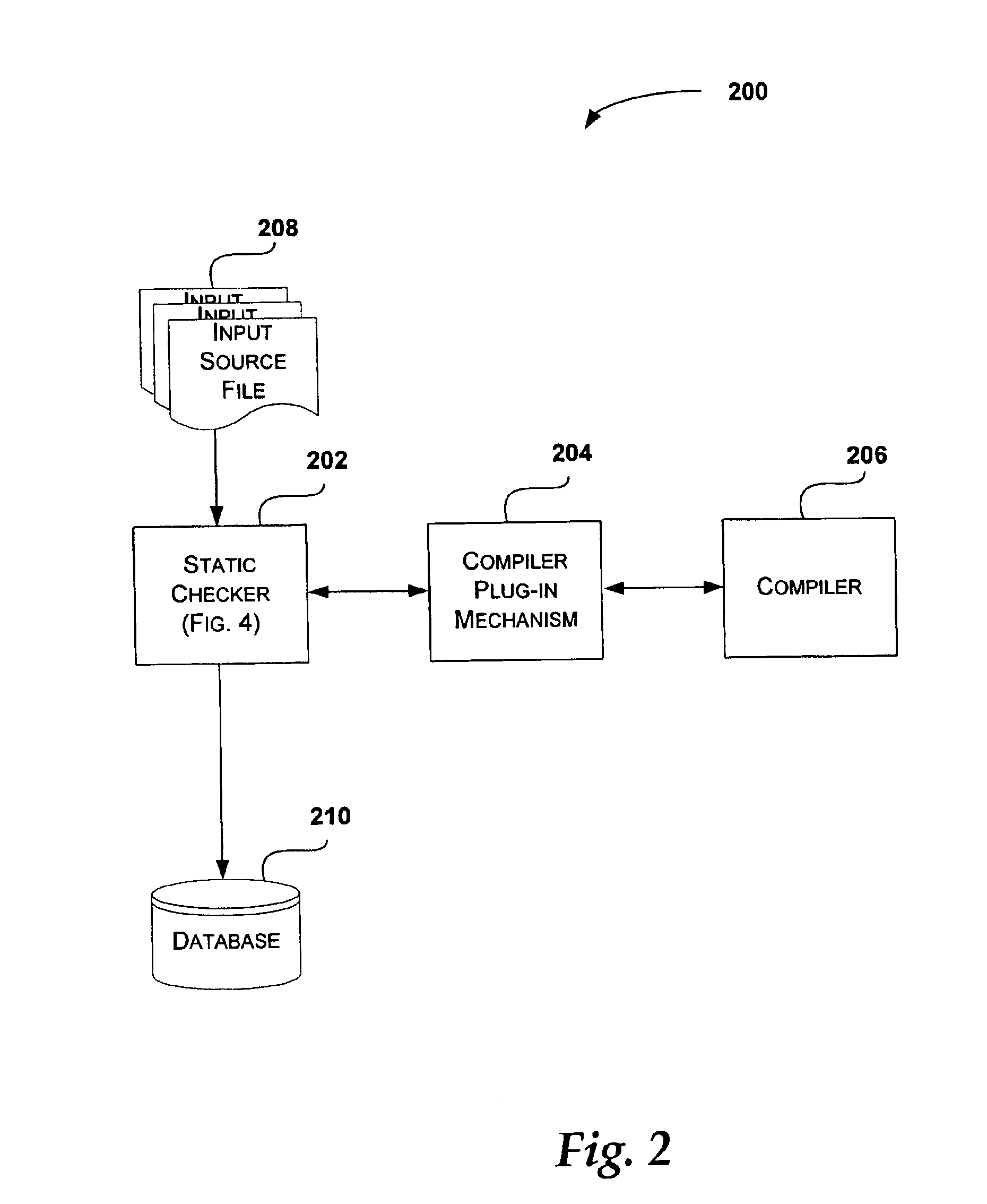
System and method for statically checking source code
InactiveUS6873935B2Minimize the numberAmplifier modifications to reduce noise influenceNuclear monitoringStatic checkSource code file
The present invention is directed at a system and method for statically checking source code to determine potential compatibility issues with a new software release. The system and method perform a static check on input source files associated with a software release. The static check includes identifying programming constructs, such as function prototypes, structures, unions, and the like, within source code files associated with the software release. The programming constructs undergo a filtering process that reduces the number of potentially false change errors. The filtered programming constructs are saved in a database associated with the software release. The database is then compared with another database containing programming constructs for another software release in order to identify differences between the two software releases. A list of changes is generated that identifies the differences between the two software releases. These changes are used to identify potential incompatibilities between the two software releases.
Owner:MICROSOFT TECH LICENSING LLC
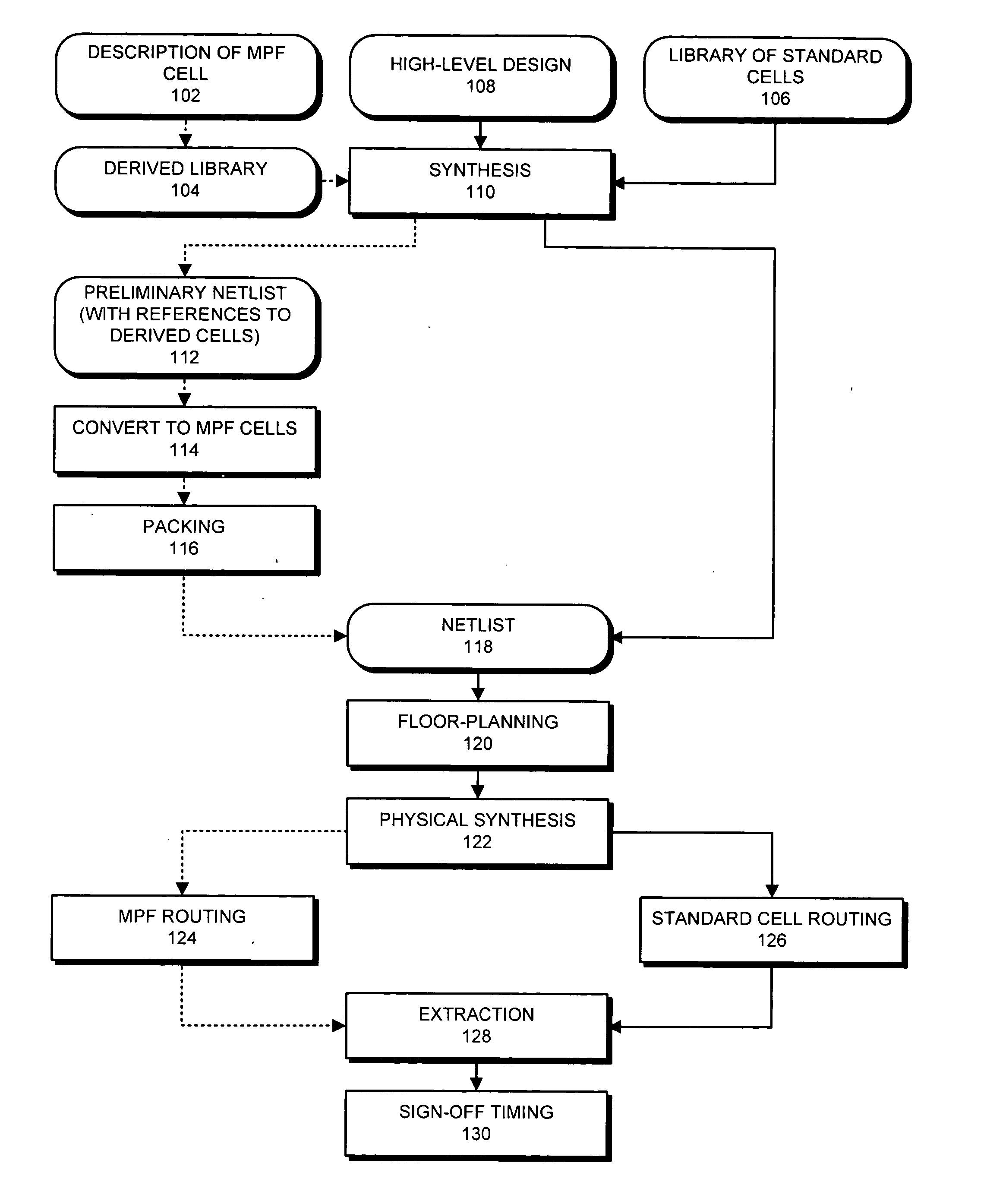
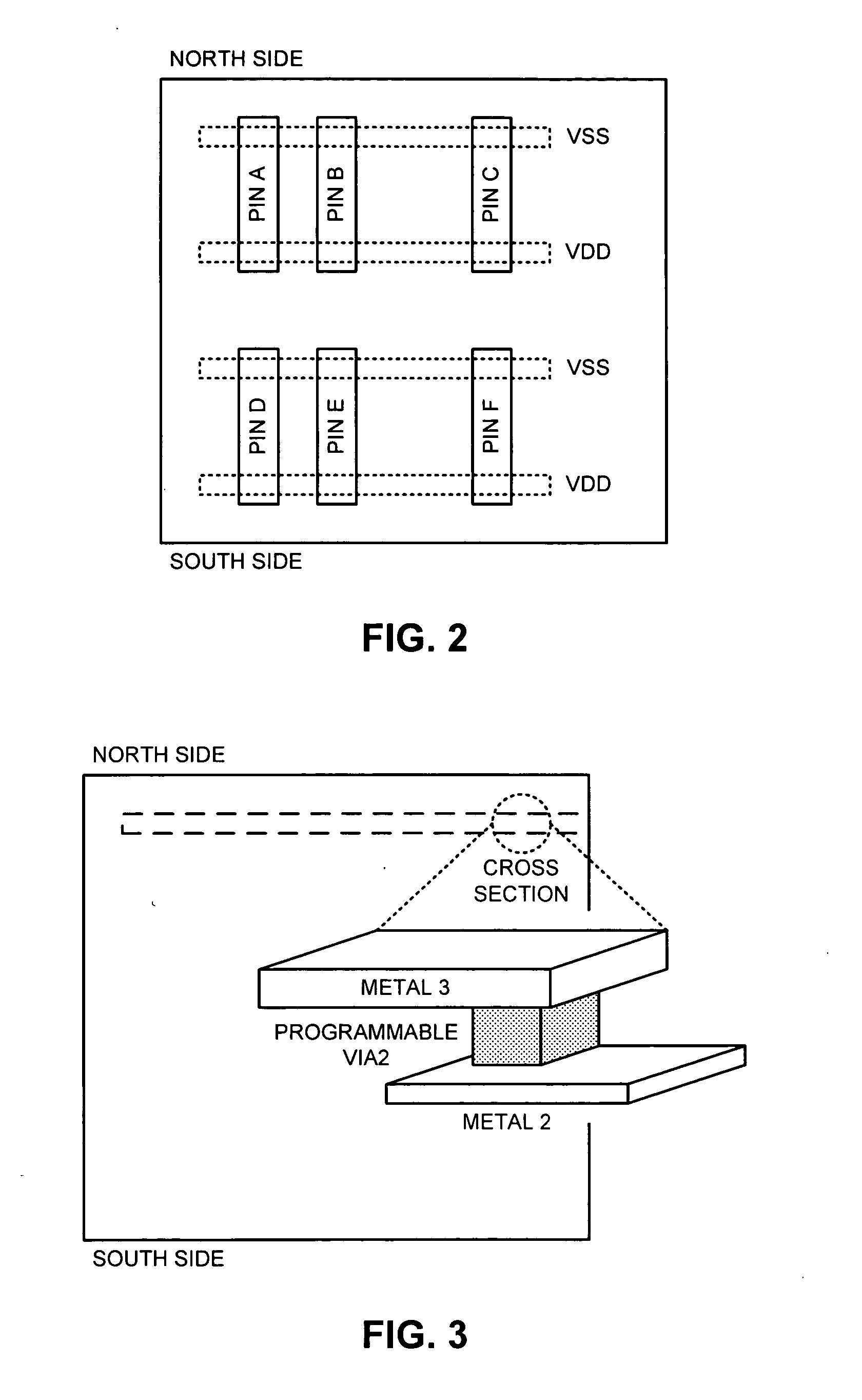
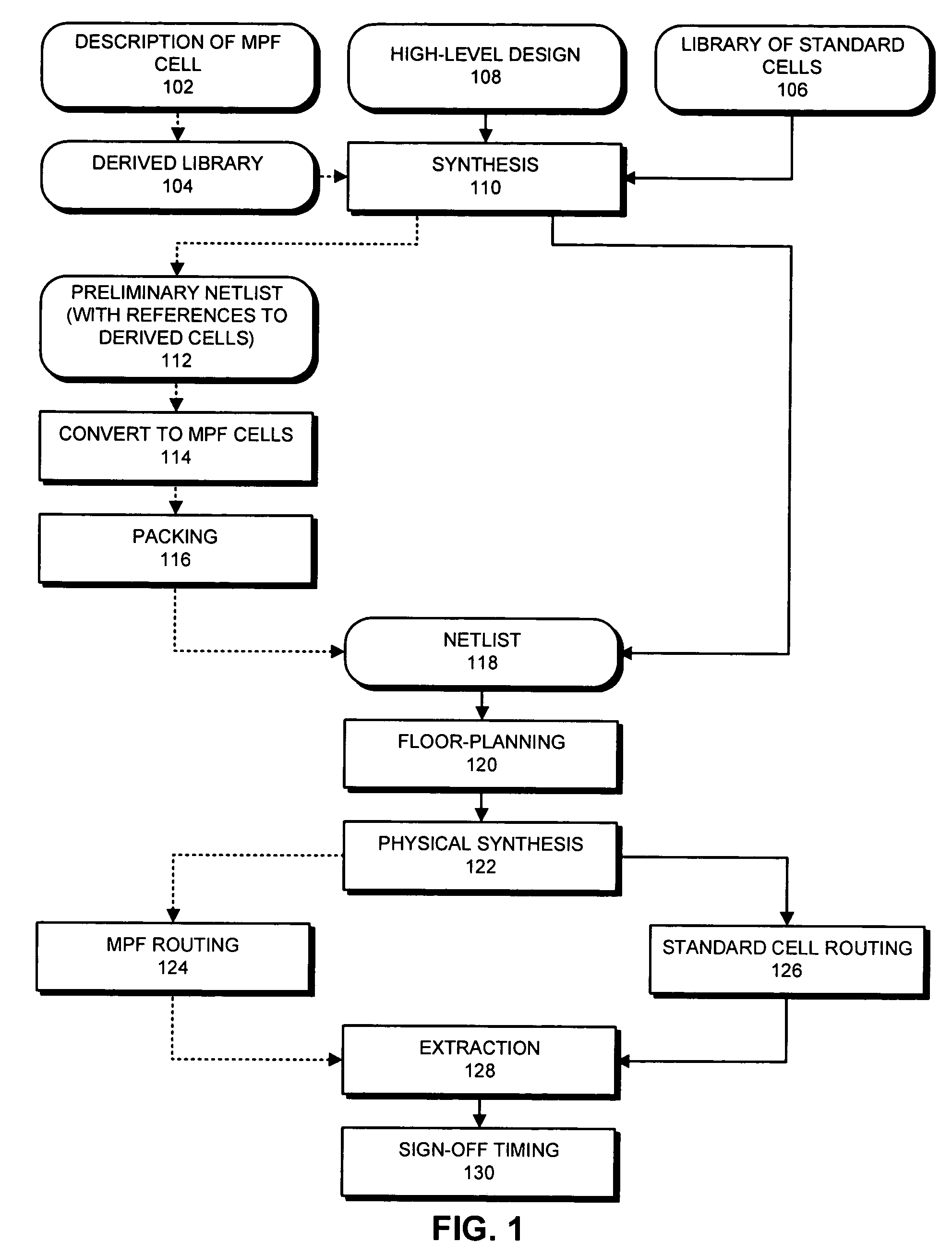
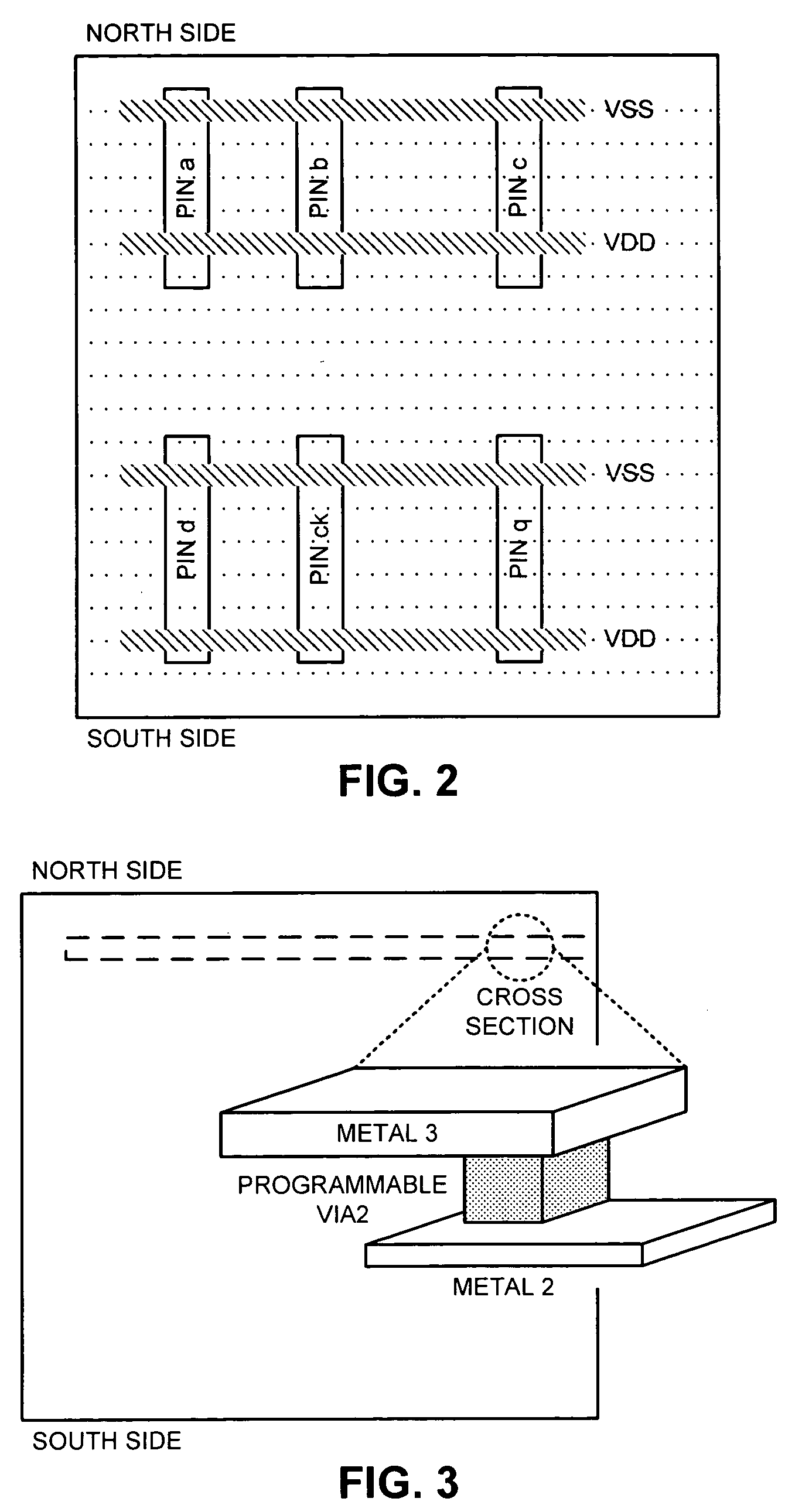
Method and apparatus for creating a mask-programmable architecture from standard cells
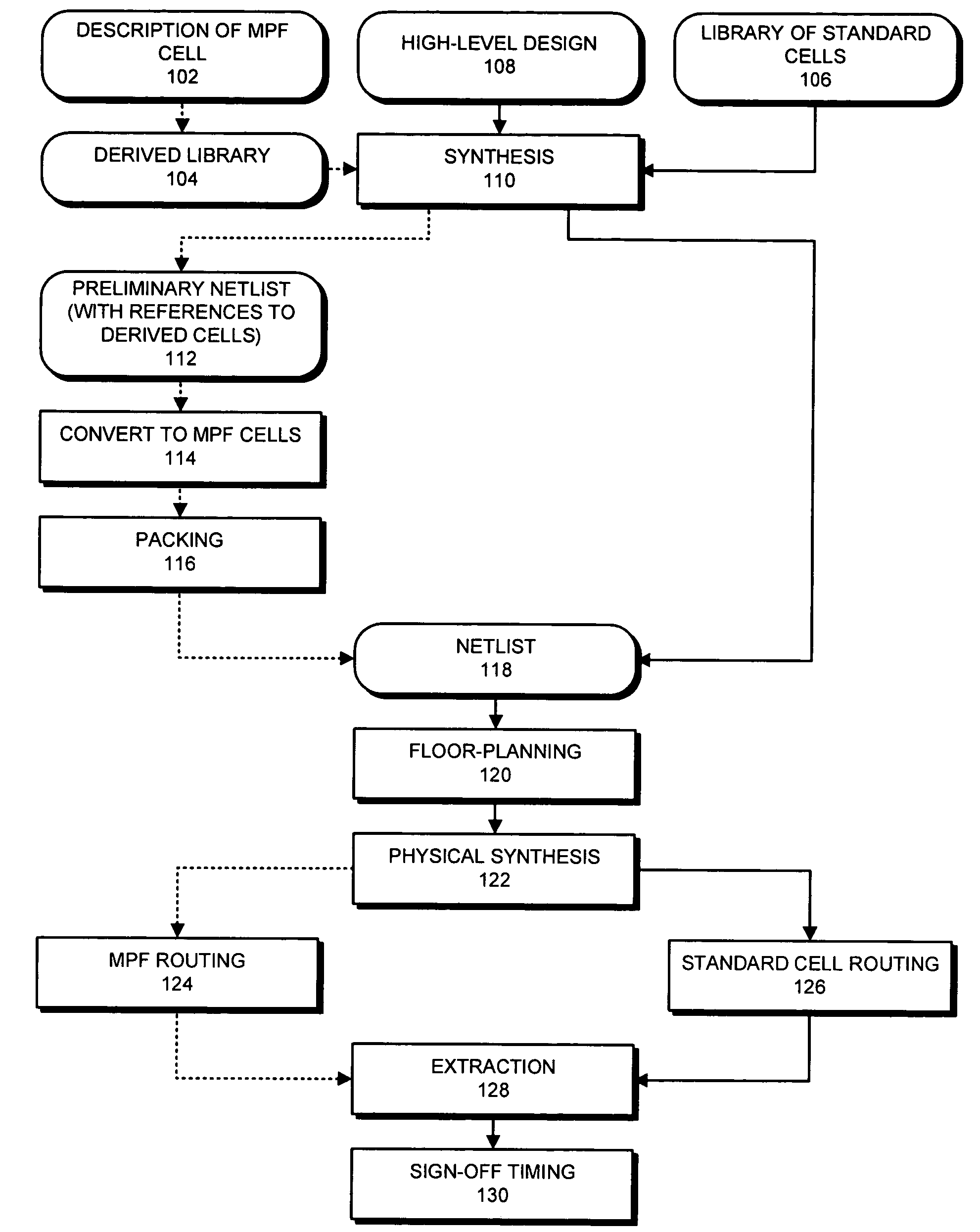
ActiveUS20050229141A1CAD circuit designSpecial data processing applicationsComputer architectureProgramming constructs
One embodiment of the invention provides a system for creating a mask-programmable module from standard cells. The system operates by first specifying characteristics of an end design and then selecting a plurality of standard cells from a standard cell library based on the characteristics of the end design. Next, the system combines the plurality of standard cells into a mask-programmable module, wherein instances of the mask-programmable module are repeated to form a mask-programmable fabric. The system also designs a mask-programmable interconnect to match the mask-programmable module, whereby connections within the mask-programmable module and between mask-programmable modules can be generated by programming the mask-programmable interconnect.
Owner:SYNOPSYS INC
ACPI preprocessor
InactiveUS20050091649A1Volume/mass flow measurementPower supply for data processingProgramming constructsHuman language
A computer-implemented method for compiling ASL (ACPI Source Language) code into AML (ACPI machine language) code. The method includes accessing an ASL program. A preprocessor is executed to process the ASL program and to insert support for at least one non-native programming construct. The ASL program is then processed using an ASL compiler to compile the ASL program into a resulting AML program.
Owner:HEWLETT PACKARD DEV CO LP
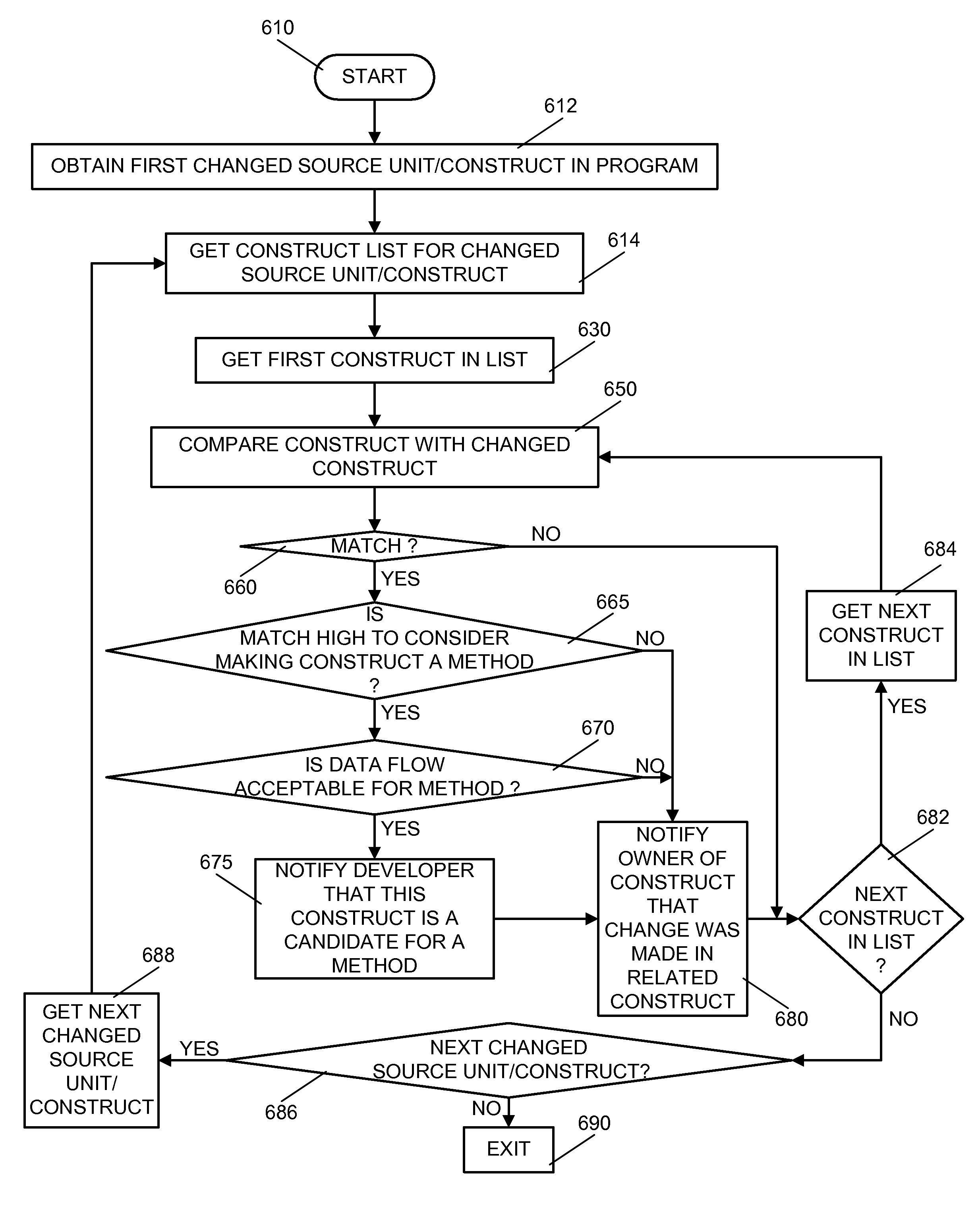
Tracking and maintaining related and derivative code
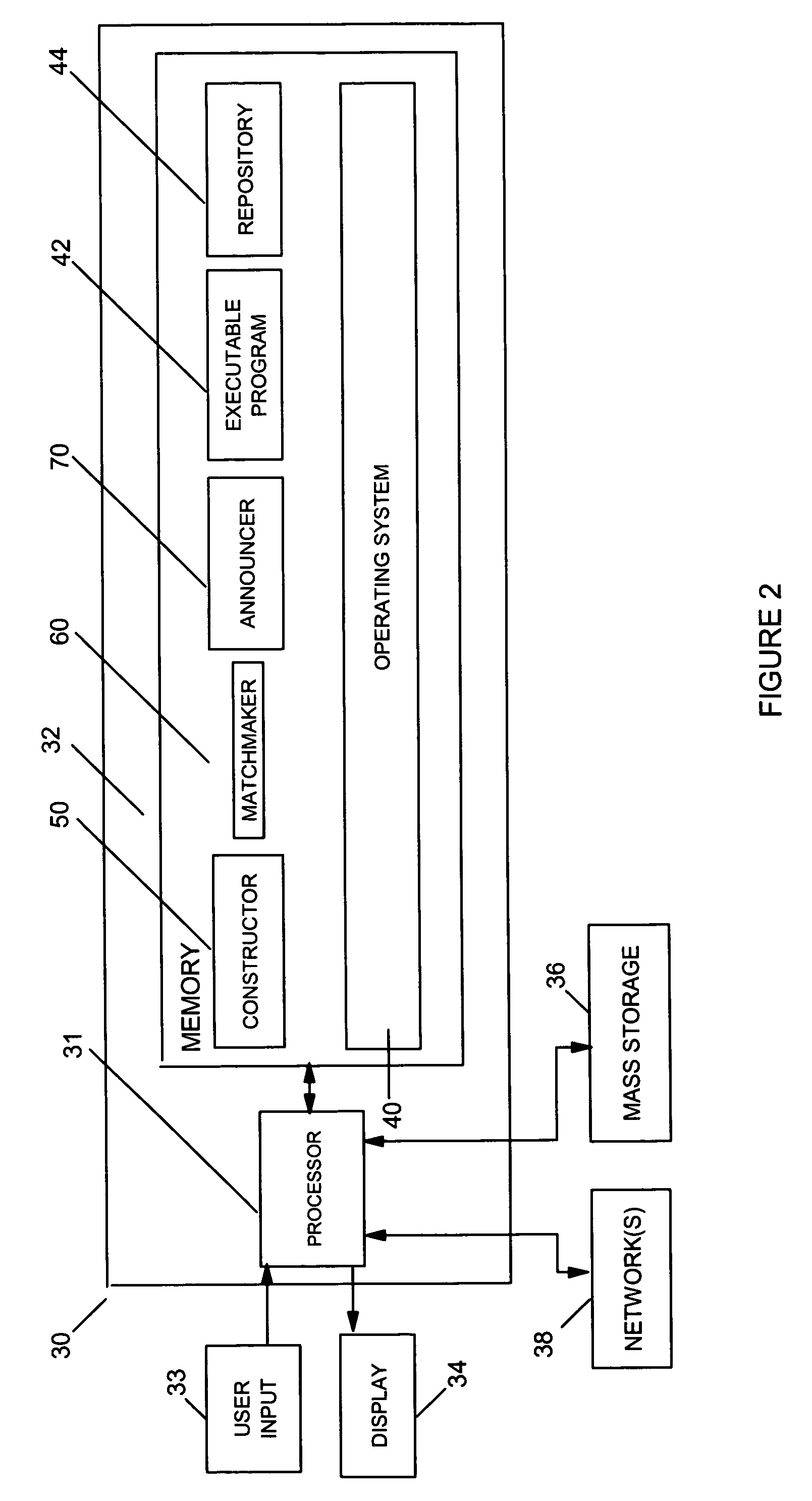
InactiveUS7500222B2Software maintainance/managementSoftware reuseProgramming constructsDegree of similarity
A method and an apparatus within an integrated development environment to increase the efficiency of tracking changes made to source code. The method and apparatus comprise three modes: a constructor mode, a matchmaker mode, and an announcer mode. The constructor first determines what source code / programming constructs are contained within an executable sequence of instructions, evaluates the size of the constructs, and then parses the tokens of the constructs to construct a construct list. The matchmaker determines the degree of similarity between any two constructs in the construct list. If the degree of similarity is sufficient, that is, if the sequence of code between two constructs is so similar that the sections of code may be considered as related and / or derivatives of one another, the matchmaker then determines if any changes made to one section of code may impact the other construct by weighting the changed tokens between the two sets of code. If the change is deemed significant, then the announcer takes over and determines if the developer who owns the related / derived code will be notified that a change has occurred in the first code.
Owner:IBM CORP
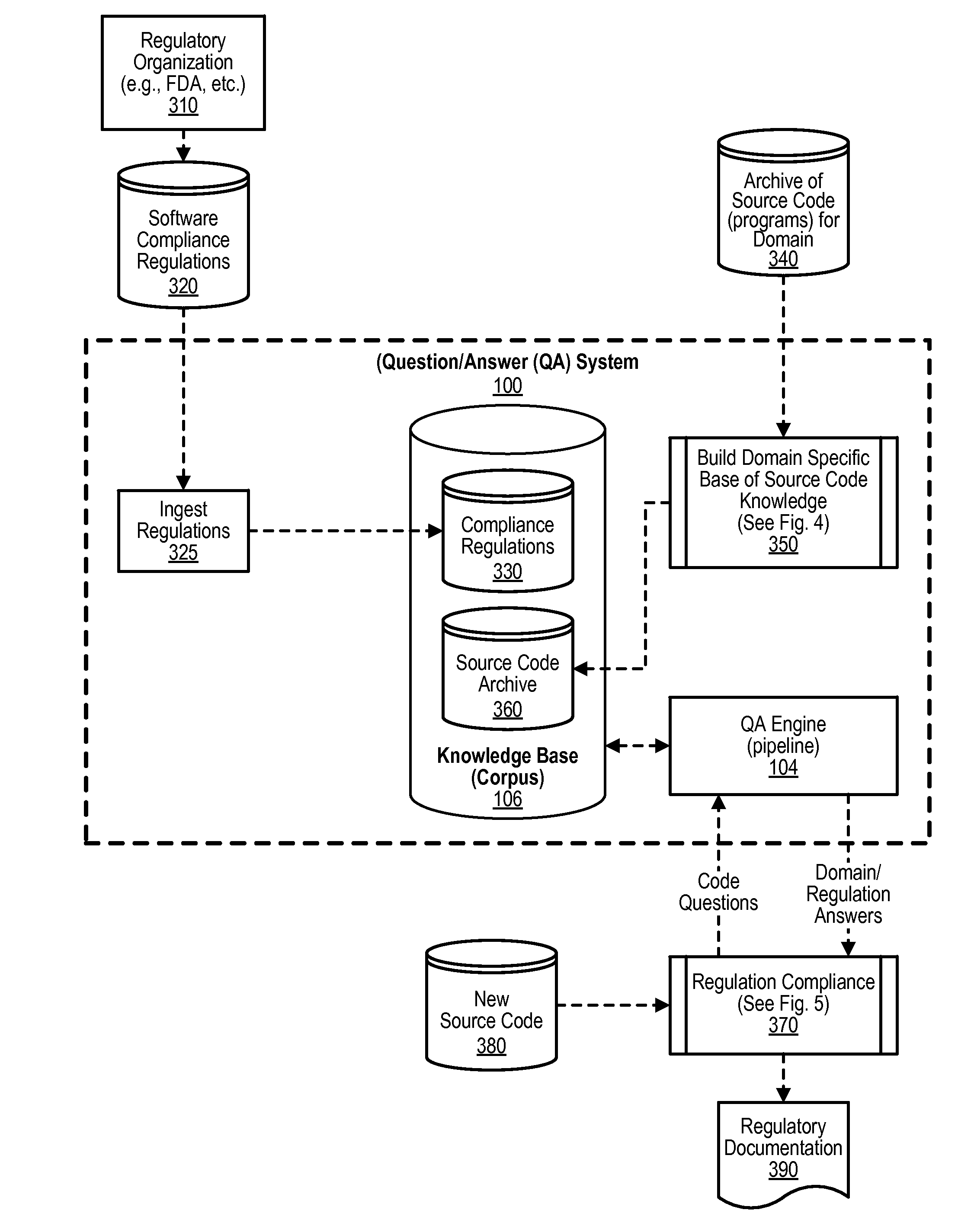
Searching Code Based on Learned Programming Construct Patterns and NLP Similarity
An approach is provided to ingest software source code files into a question / answering (QA) system. During ingestion, source code blocks are classified to identify one or more constructs in the blocks as being domain-specific. Relationships between the blocks are then mapped. Software compliance regulations are ingested into the QA system. Using the QA system, a source code file is analyzed for compliance to the software compliance regulations. The analysis identifies code sections within the source code file as being domain-specific and subject to the ingested set of software compliance regulations.
Owner:IBM CORP
System, method, and computer program product for creating a hierarchy of software components based on the programming constructs therein
InactiveUS6859921B2Software reuseSpecific program execution arrangementsProgramming constructsComputer program
A hierarchy of software components is created based on the programming constructs therein using a computer linked to a database having a collection of legacy software therein. Key component characteristics, e.g., programming constructs are defined. These constructs are assigned weights based on the difficulty or ease with which they can be reused in a new software component for use with a Web system or other network system. The legacy collection is searched to determine which, if any, of the key constructs are included therein. An ordered list is output that includes a list of the components containing the key constructs. The order of the list is based on the weight of the constructs in each component and the frequency with which they occur in each component. The list is then used to determine the effort and thus, the expense required to move entire components or blocks of code in the components into a Web system or other network system.
Owner:IBM CORP
Using context prefixes that correspond to user input modes to control execution of scripting language
InactiveUS6889374B1Visual presentationSpecific program execution arrangementsScripting languageUser input
A mechanism for incorporating user input modes in a scripting language are provided for. A context allows use of user input modes in a scripting language in a manner that corresponds to their use in a GUI. A programming construct, referred to as a context, specifies at least one user input mode and a state for the user input mode that are applied to a set of instructions. The operations specified by the instructions that are referenced by a context are executed as if the user input modes referred to by the contexts have the state specified by the contexts.
Owner:AUTODESK INC
Parameterization of programming structures
A method for transforming at least a portion of at least one programming structure into a type parameter includes receiving a first list of at least one declaration of at least one programming structure for transforming to a type parameter. The method further includes generating a second list of at least one declaration of the at least one programming structure that must be transformed into a type parameter if the at least one declaration of the first list is transformed to a type parameter. The method further includes generating a third list of at least one declaration of the at least one programming structure that may optionally be transformed into a type parameter and receiving a selection of zero or more declarations from the second list and zero or more declarations from the third list.
Owner:IBM CORP
Computer program instruction architecture, system and process using partial ordering for adaptive response to memory latencies
InactiveUS7516306B2Easy to createEasy to understandRegister arrangementsSoftware engineeringFiberProgramming constructs
The present invention broadly contemplates braids and fibers, high-level programming constructs which facilitate the creation of programs that are partially ordered, to address the continuing trend of ever-increasing processor speeds and attendant increases in memory latencies. These partial orders can be used to respond adaptively to memory latencies. It is shown how these constructs can be effectively supported with simple and inexpensive instruction set and micro-architectural extensions.
Owner:INT BUSINESS MASCH CORP
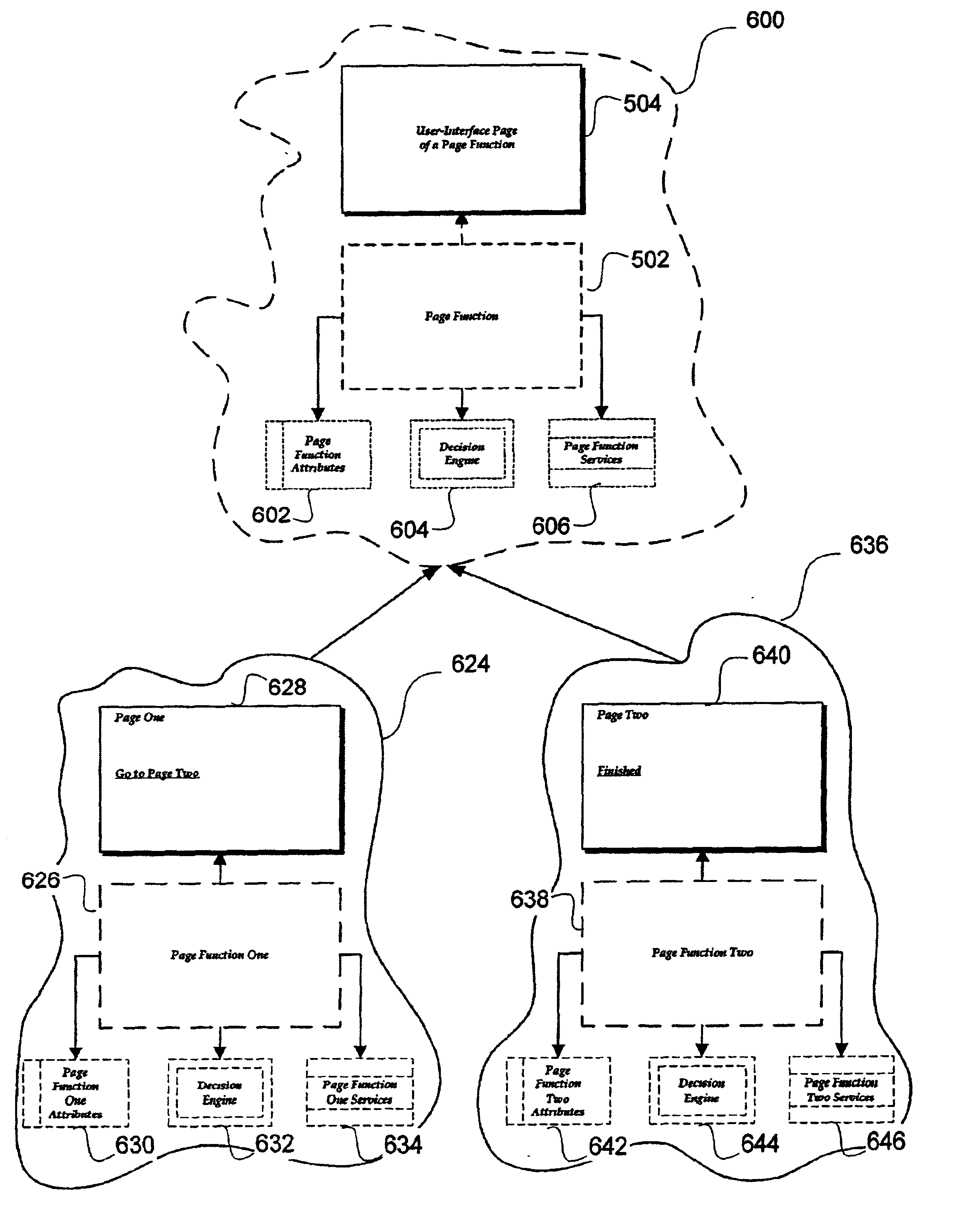
Page function architectural framework
InactiveUS6973624B2Cathode-ray tube indicatorsWebsite content managementApplication program softwareProgramming constructs
An architectural software framework is provided for creating Web-style application software incorporating protocols and means for expansion and interfacing with other Web-style programs, as well as a reusable basic programming structure, including abstract and concrete data types, that assist in building Web-style applications. The architectural software framework includes a page function and frame. Each Web-style application includes one or more page functions which communicate via the frame.
Owner:MICROSOFT TECH LICENSING LLC
Technique for computational nested parallelism
ActiveUS9513975B2Overcome limitationsProgram synchronisationProcessor architectures/configurationProgramming constructsSemantics
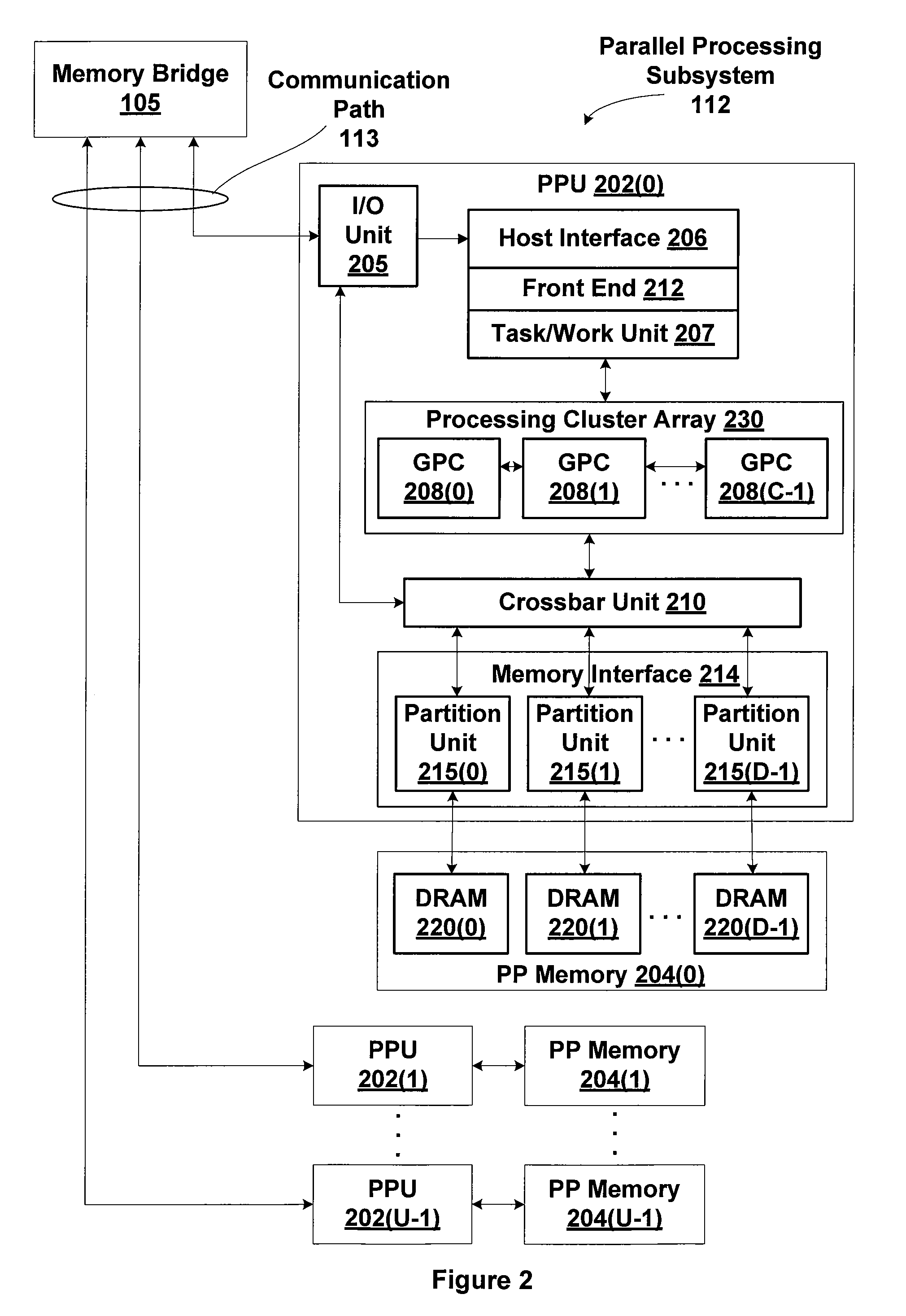
One embodiment of the present invention sets forth a technique for performing nested kernel execution within a parallel processing subsystem. The technique involves enabling a parent thread to launch a nested child grid on the parallel processing subsystem, and enabling the parent thread to perform a thread synchronization barrier on the child grid for proper execution semantics between the parent thread and the child grid. This technique advantageously enables the parallel processing subsystem to perform a richer set of programming constructs, such as conditionally executed and nested operations and externally defined library functions without the additional complexity of CPU involvement.
Owner:NVIDIA CORP
Method and apparatus for designing an integrated circuit using a mask-programmable fabric
Owner:SYNOPSYS INC
C/c++ language extensions for general-purpose graphics processing unit
A general-purpose programming environment allows users to program a GPU as a general-purpose computation engine using familiar C / C++ programming constructs. Users may use declaration specifiers to identify which portions of a program are to be compiled for a CPU or a GPU. Specifically, functions, objects and variables may be specified for GPU binary compilation using declaration specifiers. A compiler separates the GPU binary code and the CPU binary code in a source file using the declaration specifiers. The location of objects and variables in different memory locations in the system may be identified using the declaration specifiers. CTA threading information is also provided for the GPU to support parallel processing.
Owner:NVIDIA CORP
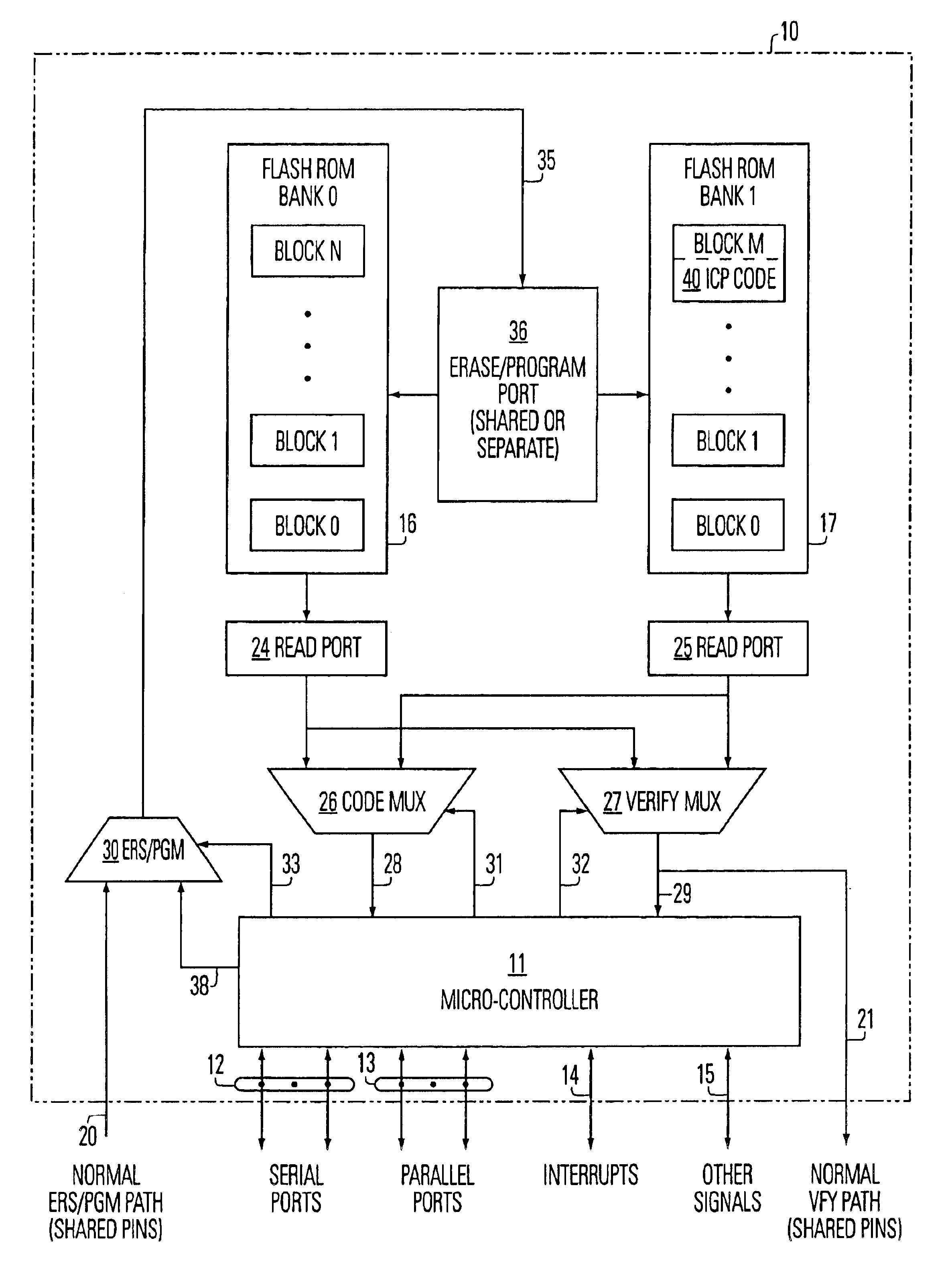
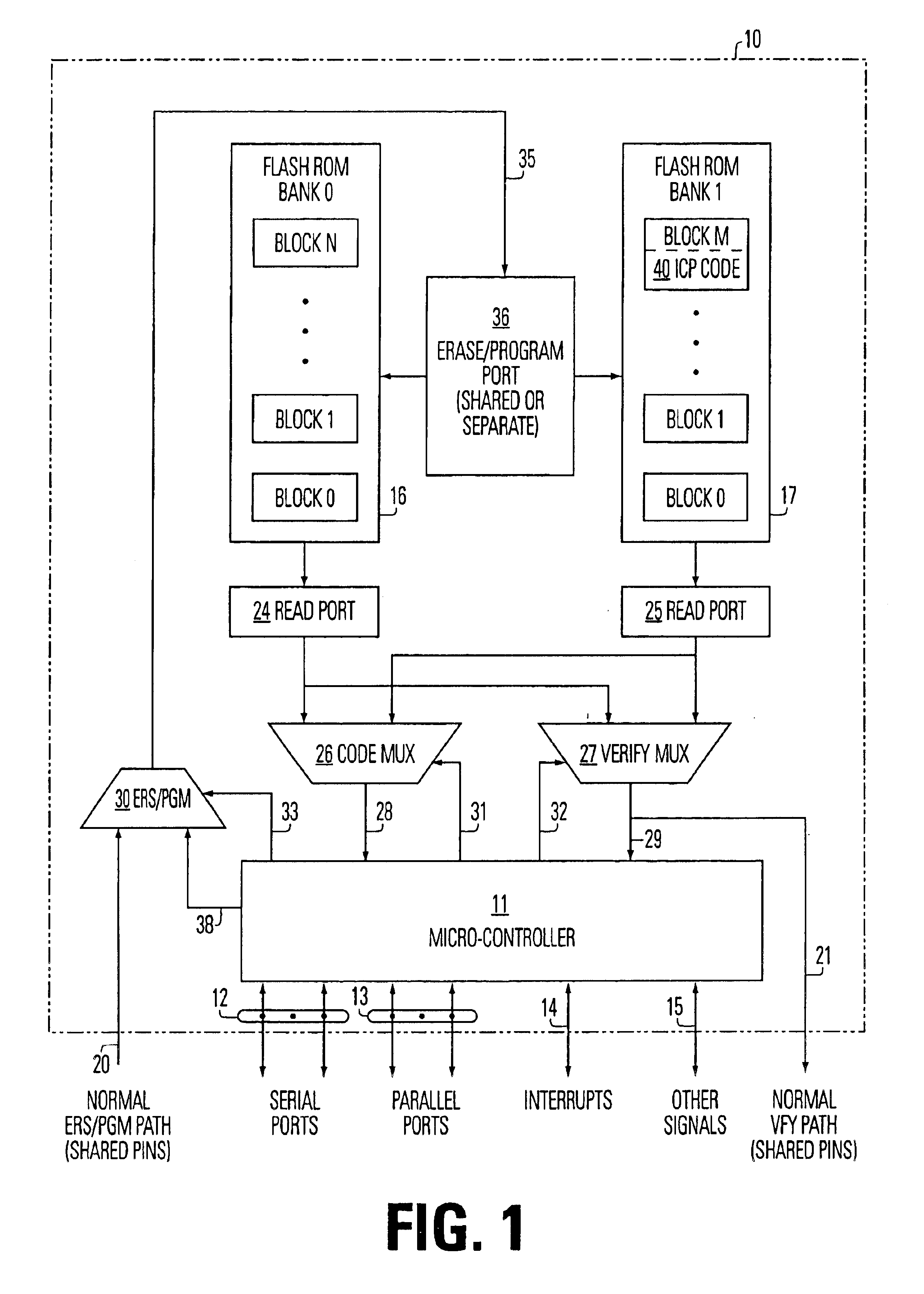
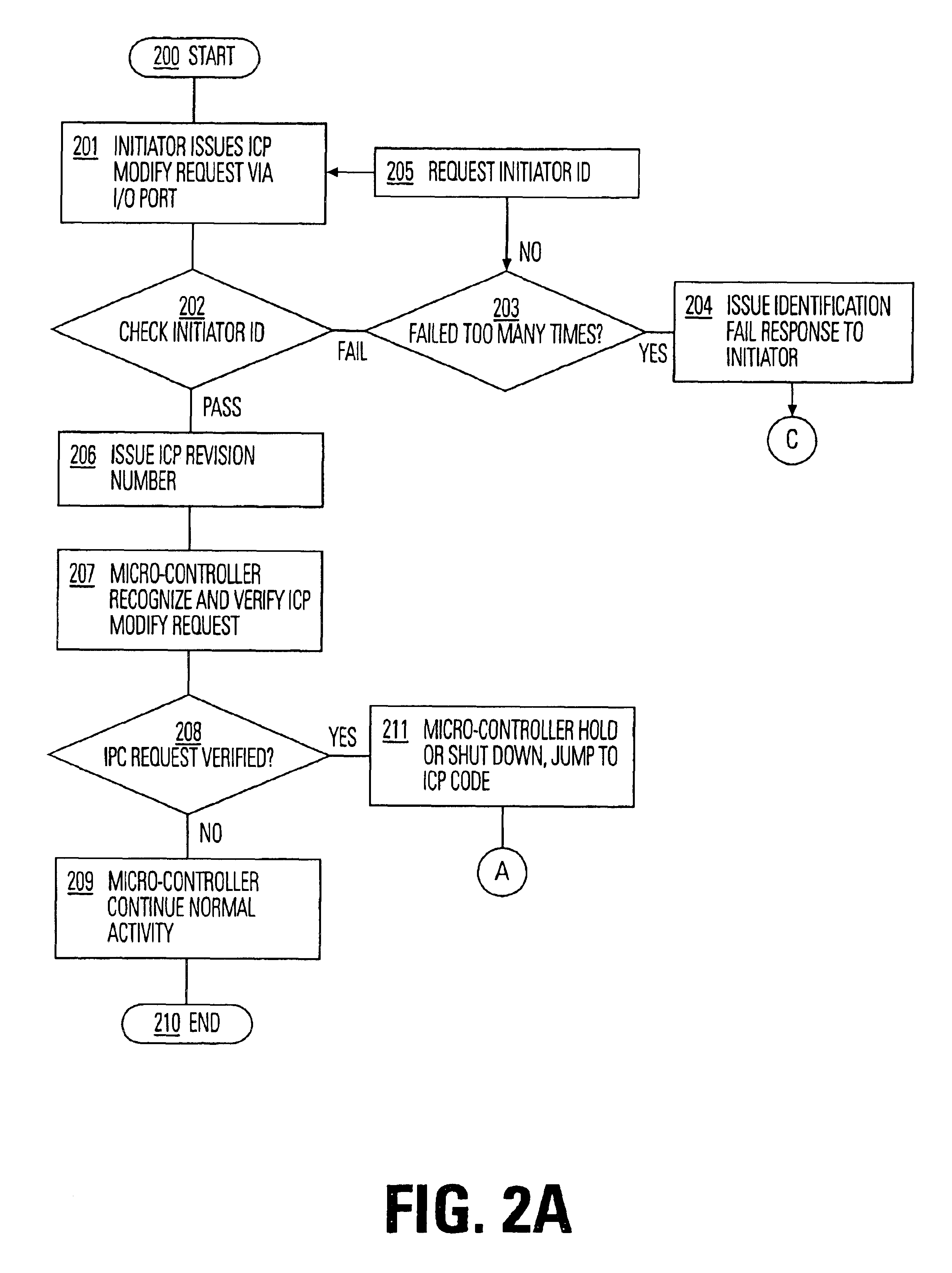
Processor with embedded in-circuit programming structures
InactiveUS6842820B2Improve usabilityFacilitate communicationSoftware engineeringProgram loading/initiatingMicrocontrollerProgramming constructs
An architecture for an integrated circuit with in-circuit programming, allows for dynamically altering the in-circuit programming instruction set itself, as well as other software stored on the chip. The architecture is based on a microcontroller on an integrated circuit having two or more banks of embedded non-volatile memory arrays which store instructions, including an in-circuit programming instruction set. Using a control program stored on the device, the device interactively establishes an in-circuit programming exchange with a remote partner, and updates data and software, including the in-circuit programming instruction set, when needed. The processor and ICP code are responsive to an in-circuit programming update command to write a copy of the in-circuit programming set from a first memory array to a second memory array, and to cause the in-circuit programming to execute the in-circuit programming set from the second memory array to program the non-volatile memory cells of the first memory array with data from the external port.
Owner:MACRONIX INT CO LTD
Method and apparatus for a general-purpose, multiple-core system for implementing stream-based computations
ActiveUS8843928B2Resource allocationSpecific program execution arrangementsGeneral purposeProcessing core
A method and system of efficient use and programming of a multi-processing core device. The system includes a programming construct that is based on stream-domain code. A programmable core based computing device is disclosed. The computing device includes a plurality of processing cores coupled to each other. A memory stores stream-domain code including a stream defining a stream destination module and a stream source module. The stream source module places data values in the stream and the stream conveys data values from the stream source module to the stream destination module. A runtime system detects when the data values are available to the stream destination module and schedules the stream destination module for execution on one of the plurality of processing cores.
Owner:CORNAMI INC
Searching Code Based on Learned Programming Construct Patterns and NLP Similarity
An approach is provided to ingest software source code files into a question / answering (QA) system. During ingestion, source code blocks are classified to identify one or more constructs in the blocks as being domain-specific. Relationships between the blocks are then mapped. Software compliance regulations are ingested into the QA system. Using the QA system, a source code file is analyzed for compliance to the software compliance regulations. The analysis identifies code sections within the source code file as being domain-specific and subject to the ingested set of software compliance regulations.
Owner:IBM CORP
Self-adaptive method for building Ajax application for end user
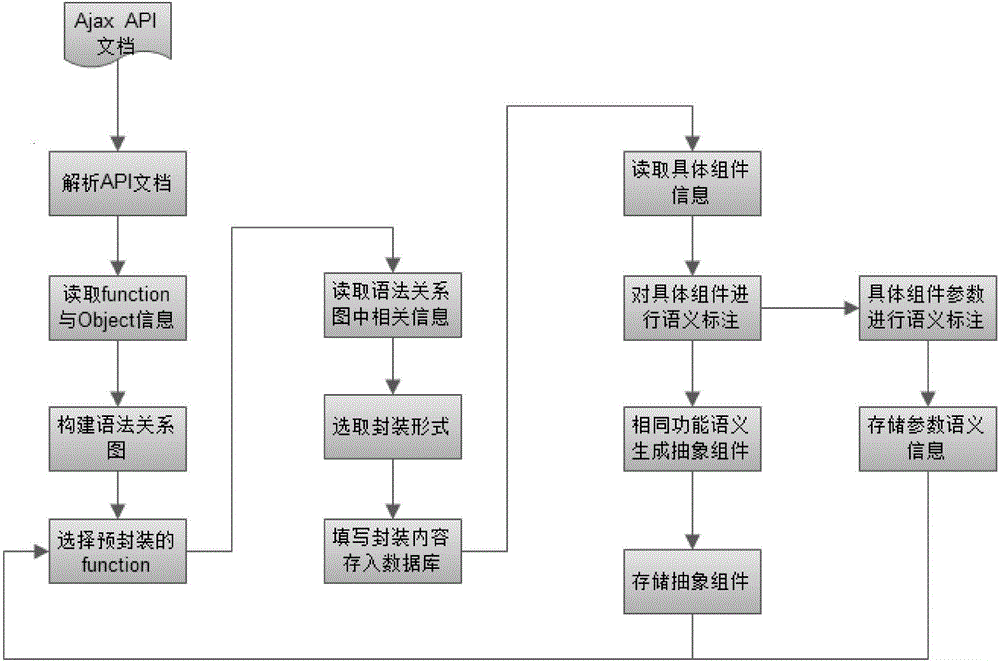
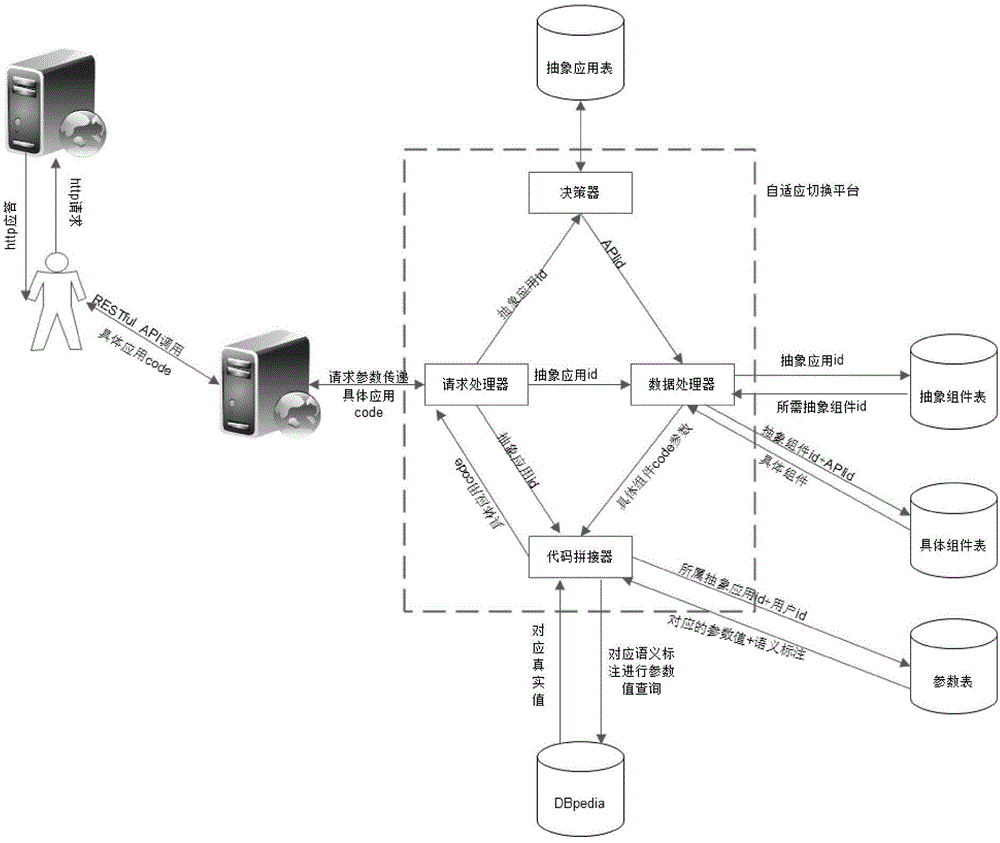
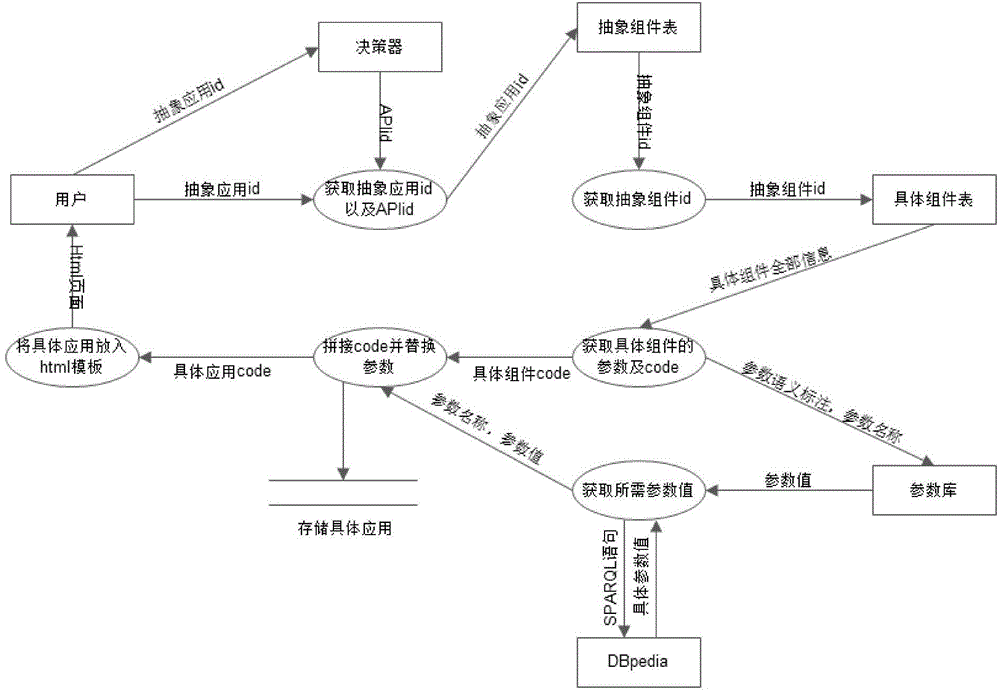
ActiveCN104572095AActive implementation effectImproving the Efficiency of Developing Ajax ApplicationsProgram initiation/switchingTransmissionProgramming constructsSemantics
The invention discloses a self-adaptive method for building Ajax application for an end user. The method comprises the steps of 1, packaging Ajax API to form a concrete assembly and an abstract assembly; 2, performing Ajax API self-switching during operation according to the packaging characteristics. Compared with the prior art, the method has the advantages that the Ajax API can be adapted to user demand in semantics through the semantics and semantics packaging of different Ajax API; the Ajax application can be developed by the mode of splicing the assemblies, so as to achieve the purpose of zero-programming constructing to Ajax application which meets the user demand; in addition, the Ajax API self-switching frame under the operation is utilized to achieve the replacing of Ajax API during operation, and therefore, the application efficiency of the user in Ajax development is greatly increased, and the user experience is improved.
Owner:深圳芳园天伦科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com