Method and device for detecting Android malicious application
A malicious application and detection method technology, applied in the field of mobile Internet, can solve problems such as low accuracy, and achieve the effect of improving accuracy and large detection range
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
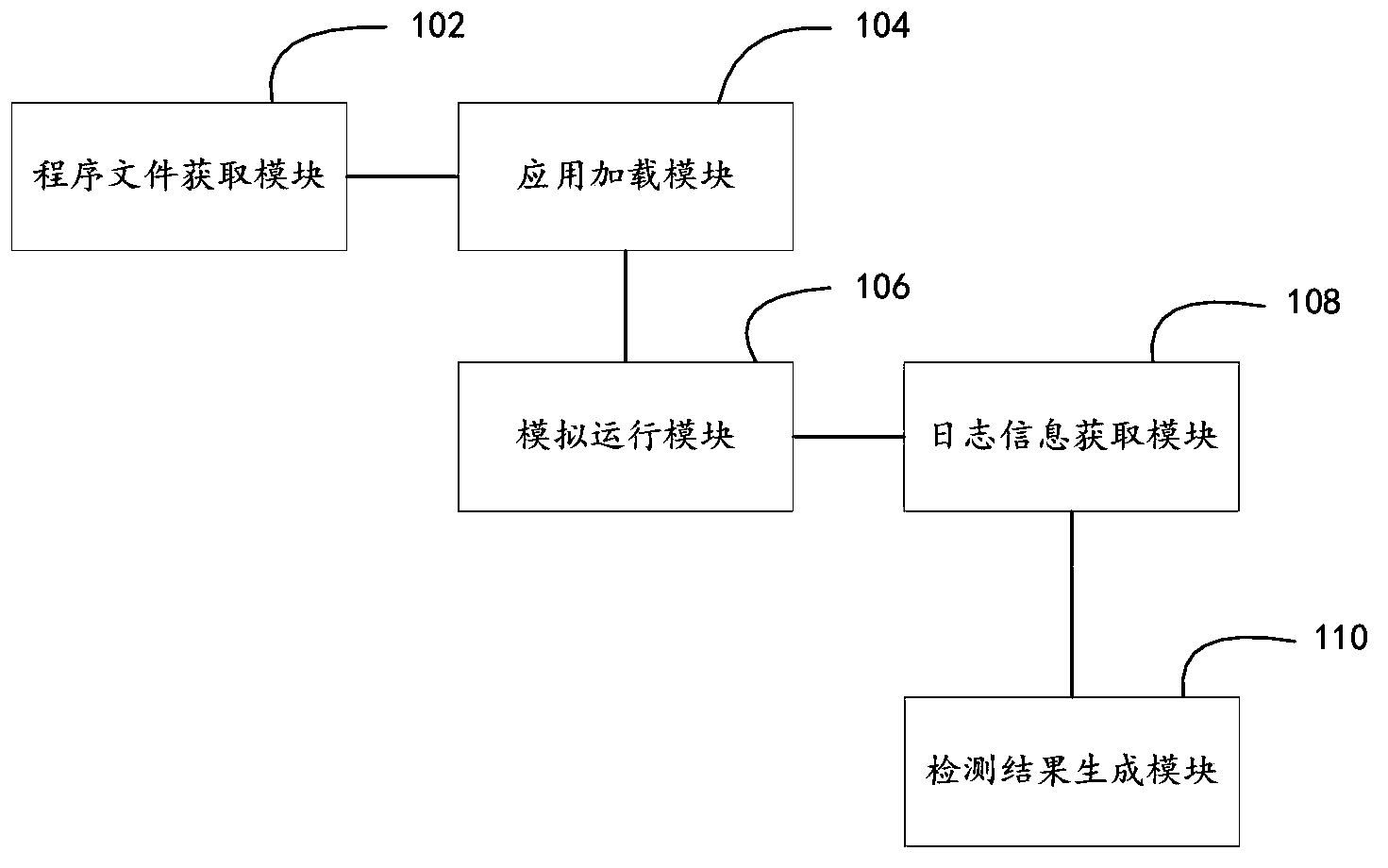
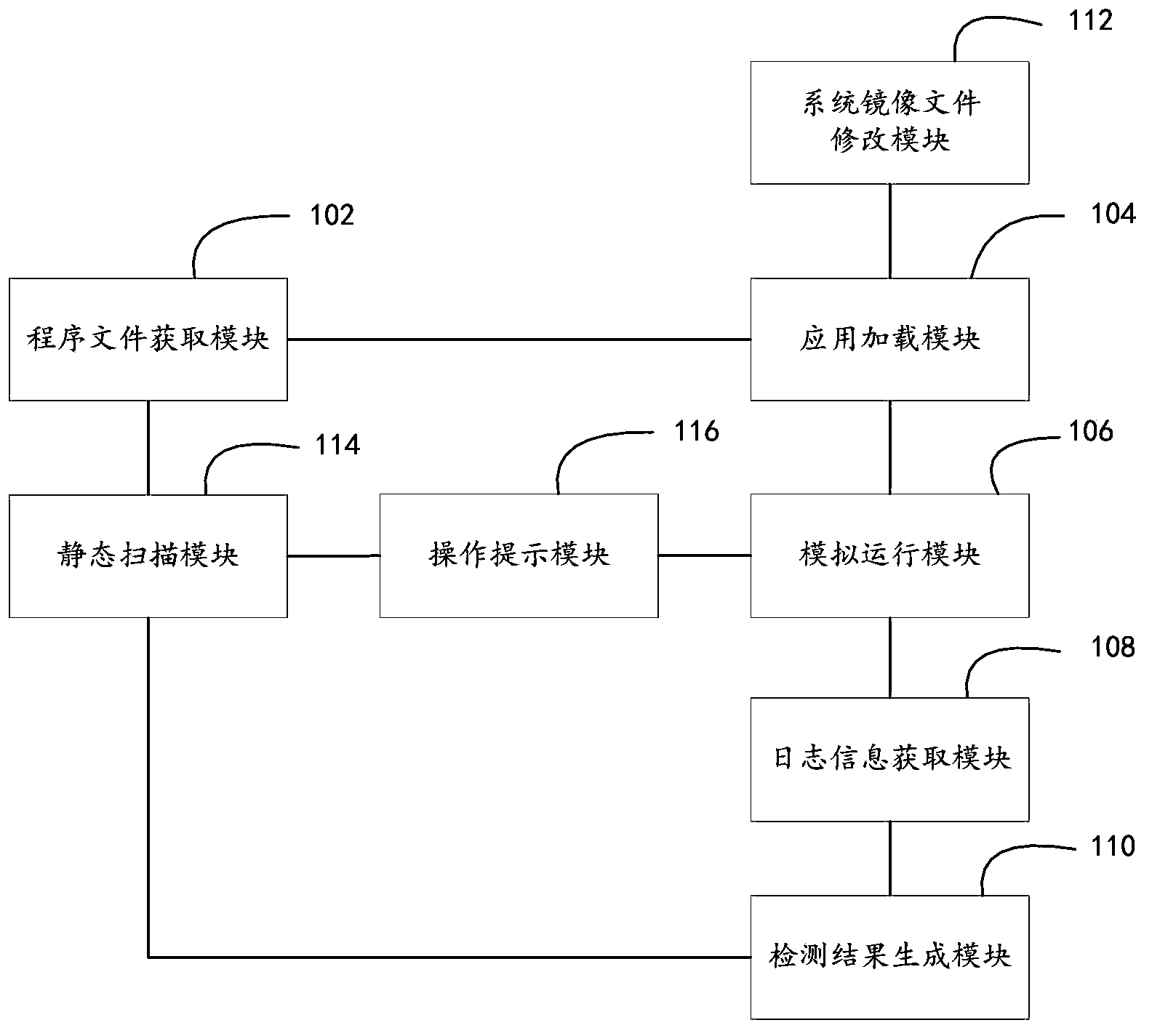
Image
Examples
Embodiment Construction
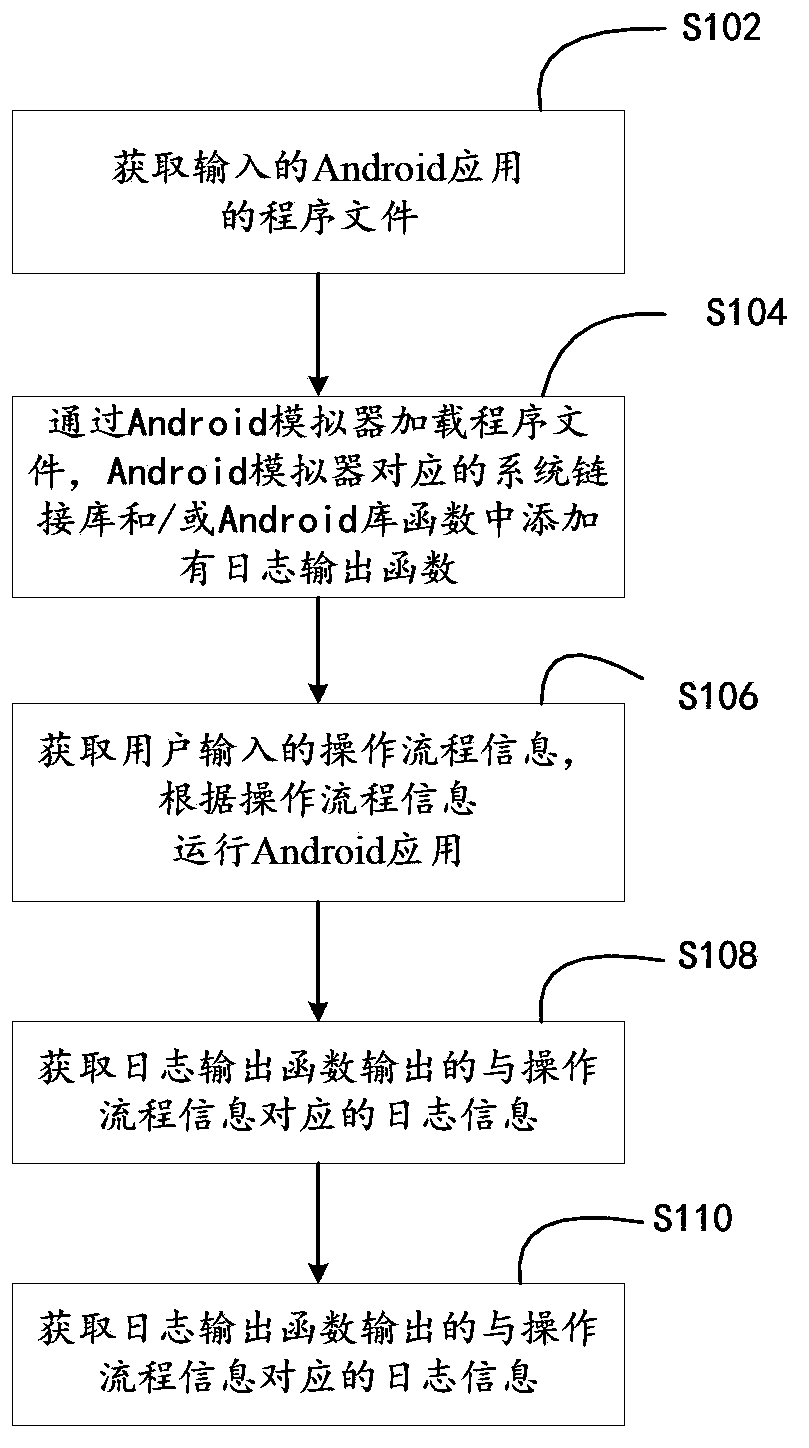
[0023] In one embodiment, such as figure 1 As shown, a method for detecting Android malicious applications, the method completely depends on a computer program, and the computer program can run on a computer system based on the von Neumann architecture.
[0024] The method includes the following steps:
[0025] Step S102, acquiring the input program file of the Android application.
[0026] The program file corresponding to the Android application is usually an apk file. In this embodiment, a file selection box component can be displayed. The user can select the apk file of the corresponding Android application in the local file through the file selection box for input, and then the input program file of the Android application can be obtained through the file selection box component.
[0027] In step S104, the program file is loaded through the Android emulator, and a log output function is added to the system link library and / or Android library functions corresponding to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com