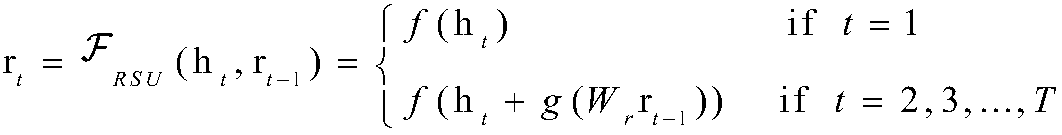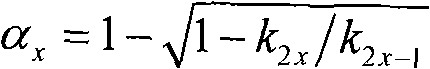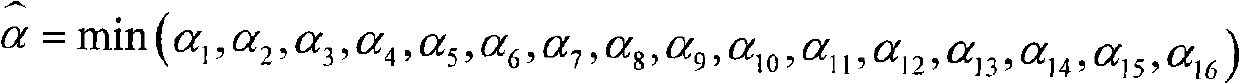Patents
Literature
80 results about "Miss rate" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
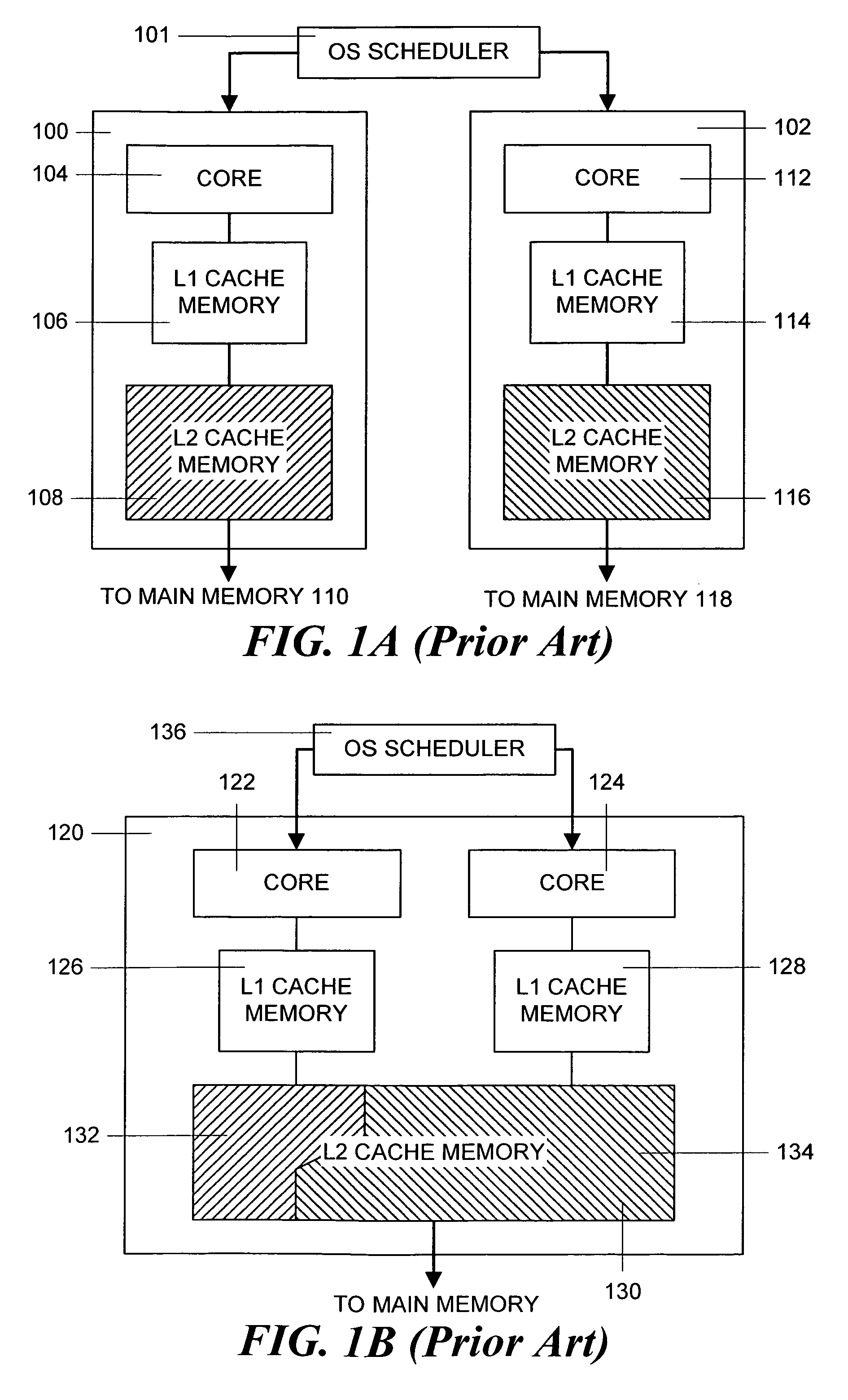
The fraction or percentage of accesses that result in a hit is called the hit rate. The fraction or percentage of accesses that result in a miss is called the miss rate. The “extra” time required to fetch a block into a level of the memory hierarchy from the lower level is called miss penalty.
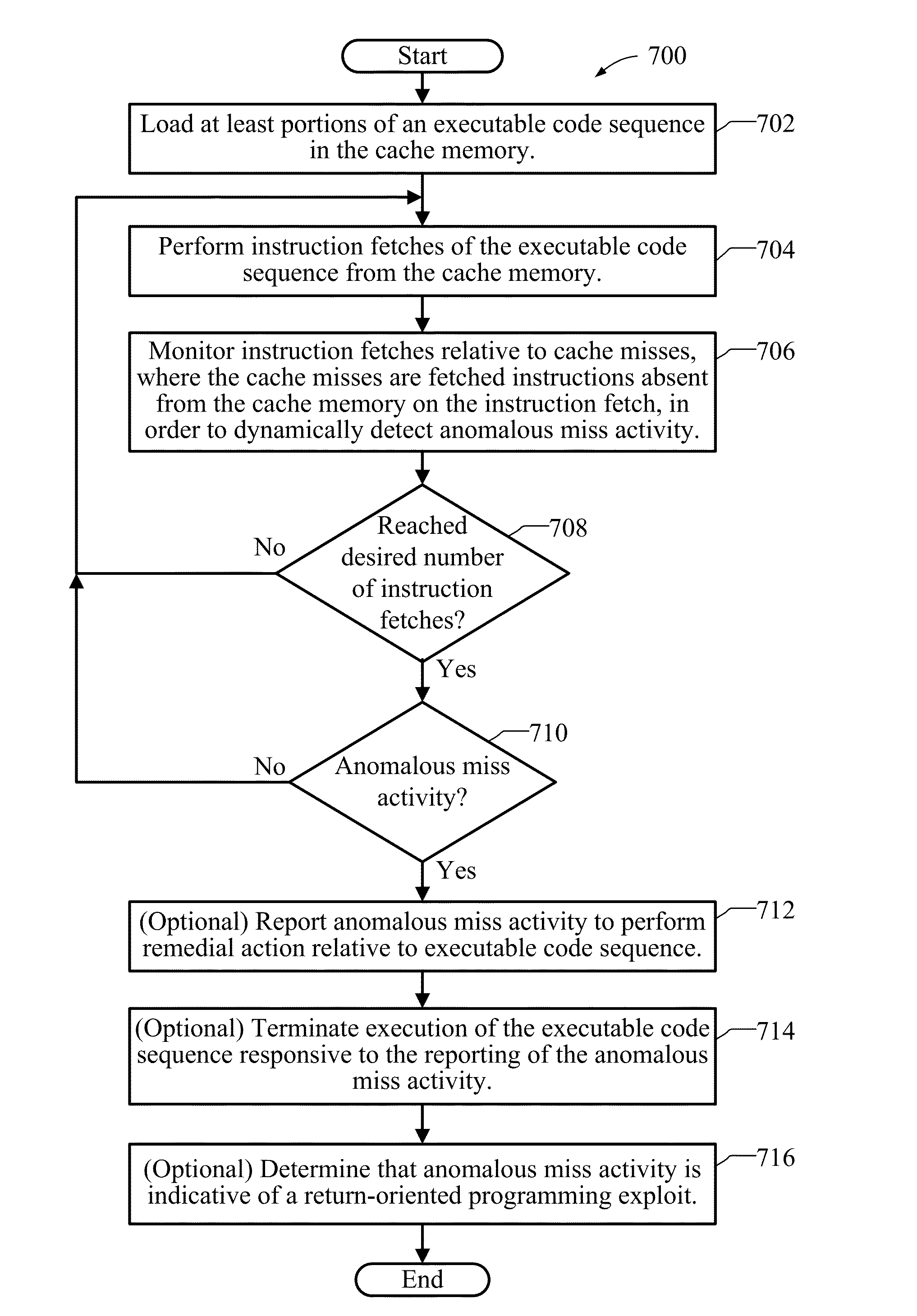
Methods, Devices, And Systems For Detecting Return-Oriented Programming Exploits
InactiveUS20130117843A1Memory architecture accessing/allocationMemory loss protectionCode snippetRemedial action
Methods, devices, and systems for detecting return-oriented programming (ROP) exploits are disclosed. A system includes a processor, a main memory, and a cache memory. A cache monitor develops an instruction loading profile by monitoring accesses to cached instructions found in the cache memory and misses to instructions not currently in the cache memory. A remedial action unit terminates execution of one or more of the valid code sequences if the instruction loading profile is indicative of execution of an ROP exploit involving one or more valid code sequences. The instruction loading profile may be a hit / miss ratio derived from monitoring cache hits relative to cache misses. The ROP exploits may include code snippets that each include an executable instruction and a return instruction from valid code sequences.
Owner:QUALCOMM INC
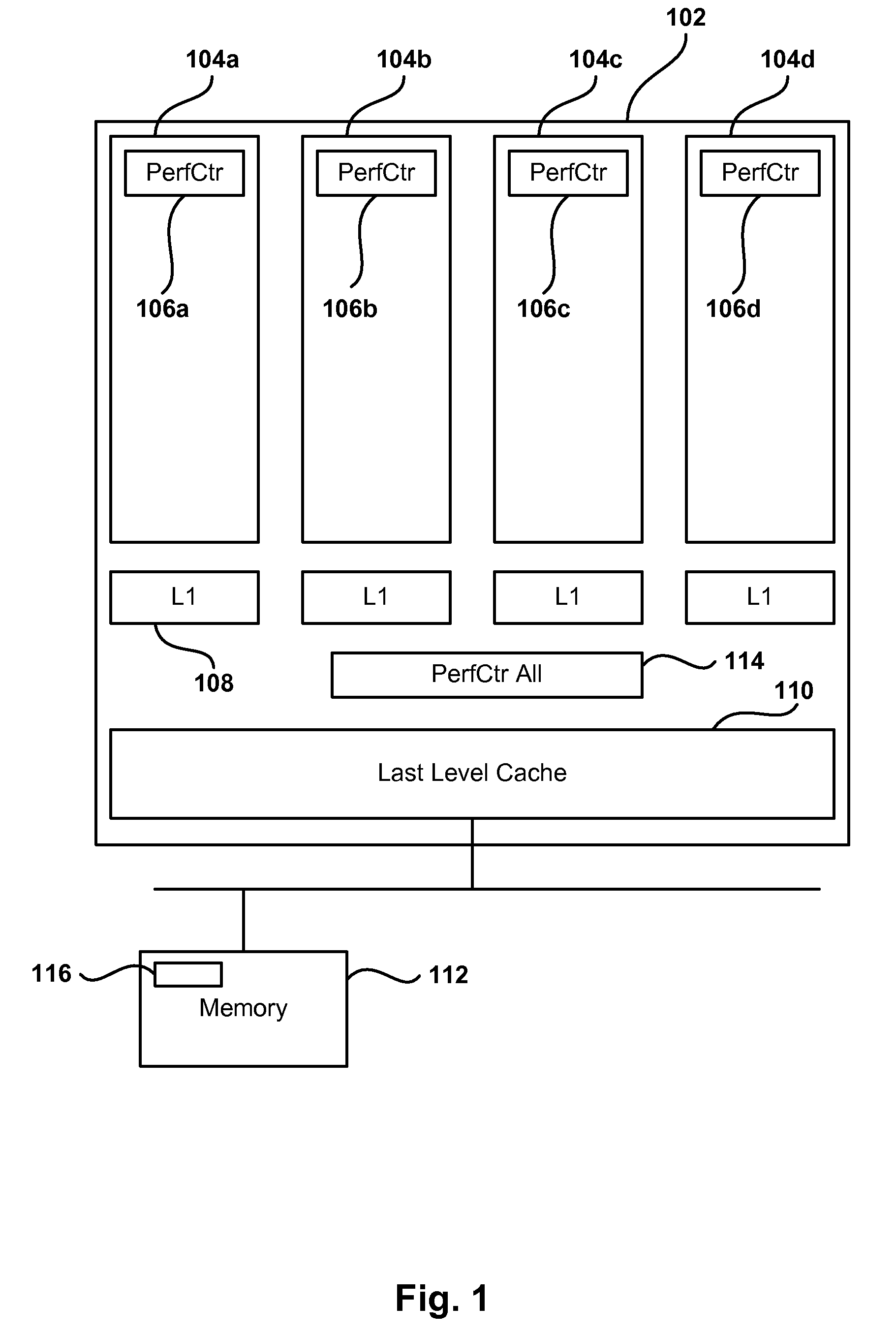
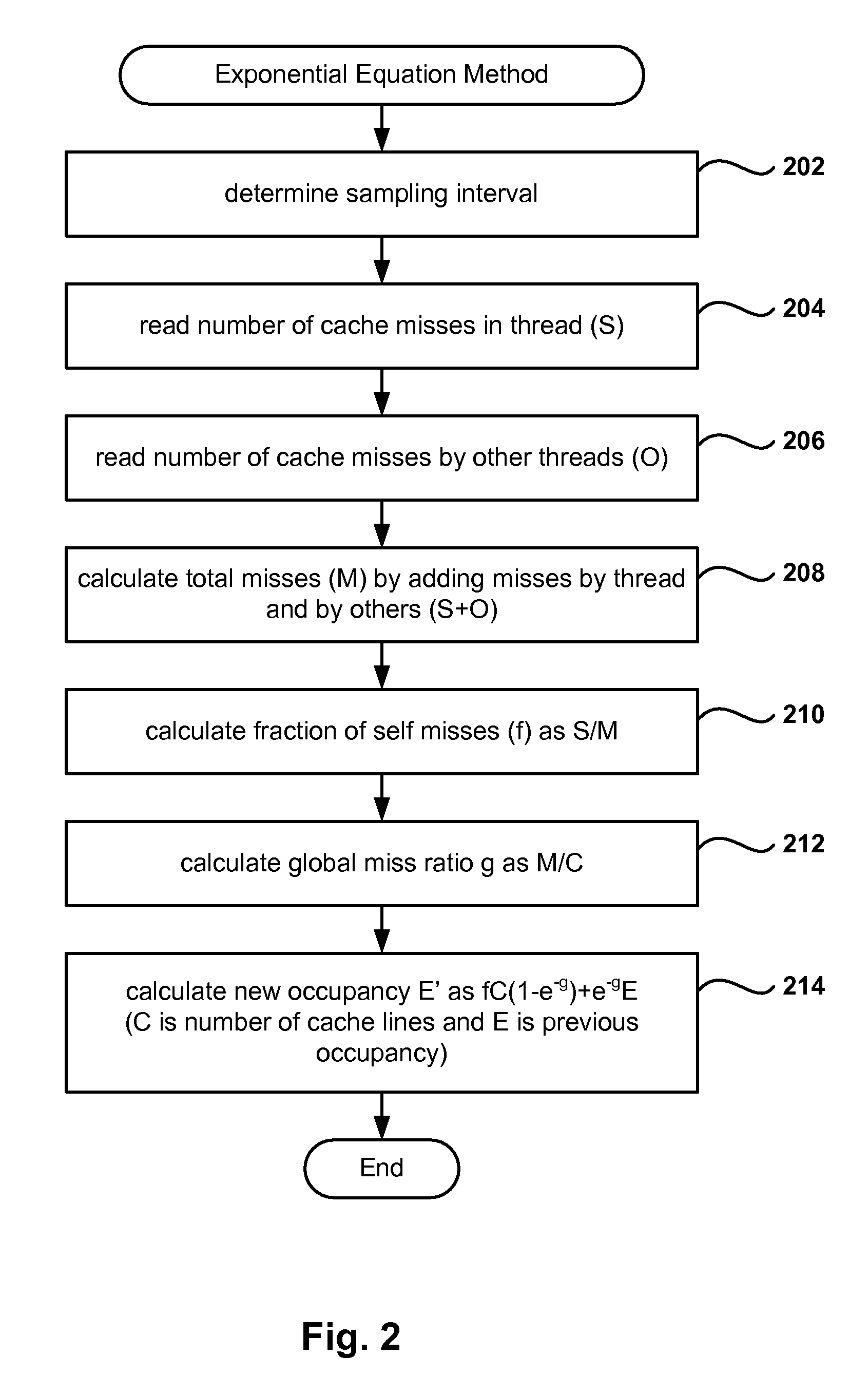
Online Computation of Cache Occupancy and Performance
Methods, computer programs, and systems for managing thread performance in a computing environment based on cache occupancy are provided. In one embodiment, a computer implemented method assigns a thread performance counter to threads being created to measure the number of cache misses for the threads. The thread performance counter is deduced in one embodiment based on performance counters associated with each core in a processor. The method further calculates a self-thread value as the change in the thread performance counter of a given thread during a predetermined period, and an other-thread value as the sum of all the changes in the thread performance counters for all threads except for the given thread. Further, the method estimates a cache occupancy for the given thread based on a previous occupancy for the given thread, and the calculated shelf-thread and other-thread values. The estimated cache occupancy is used to assign computing environment resources to the given thread. In another embodiment, cache miss-rate curves are constructed for a thread to help analyze performance tradeoffs when changing cache allocations of the threads in the system.
Owner:VMWARE INC
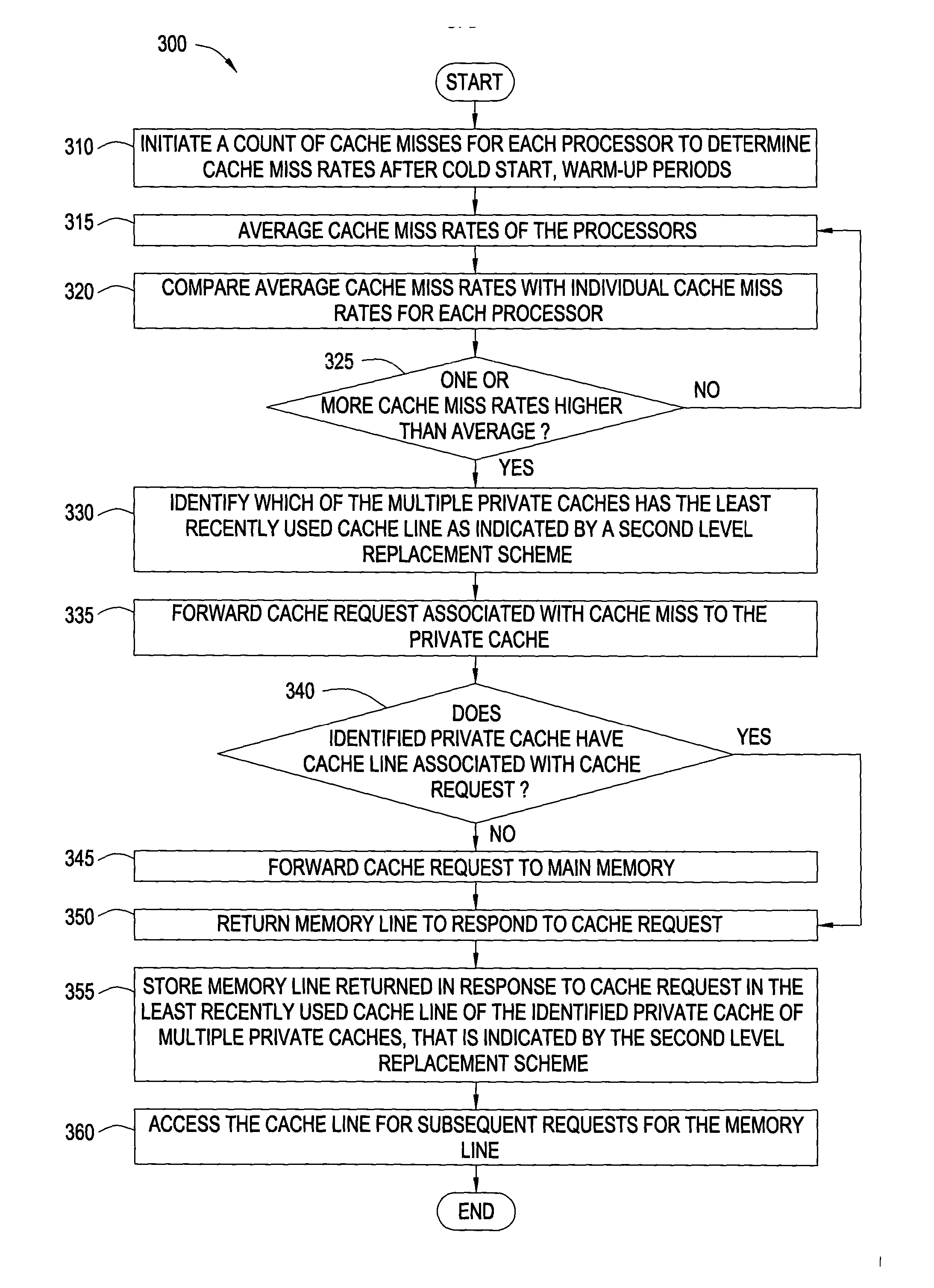
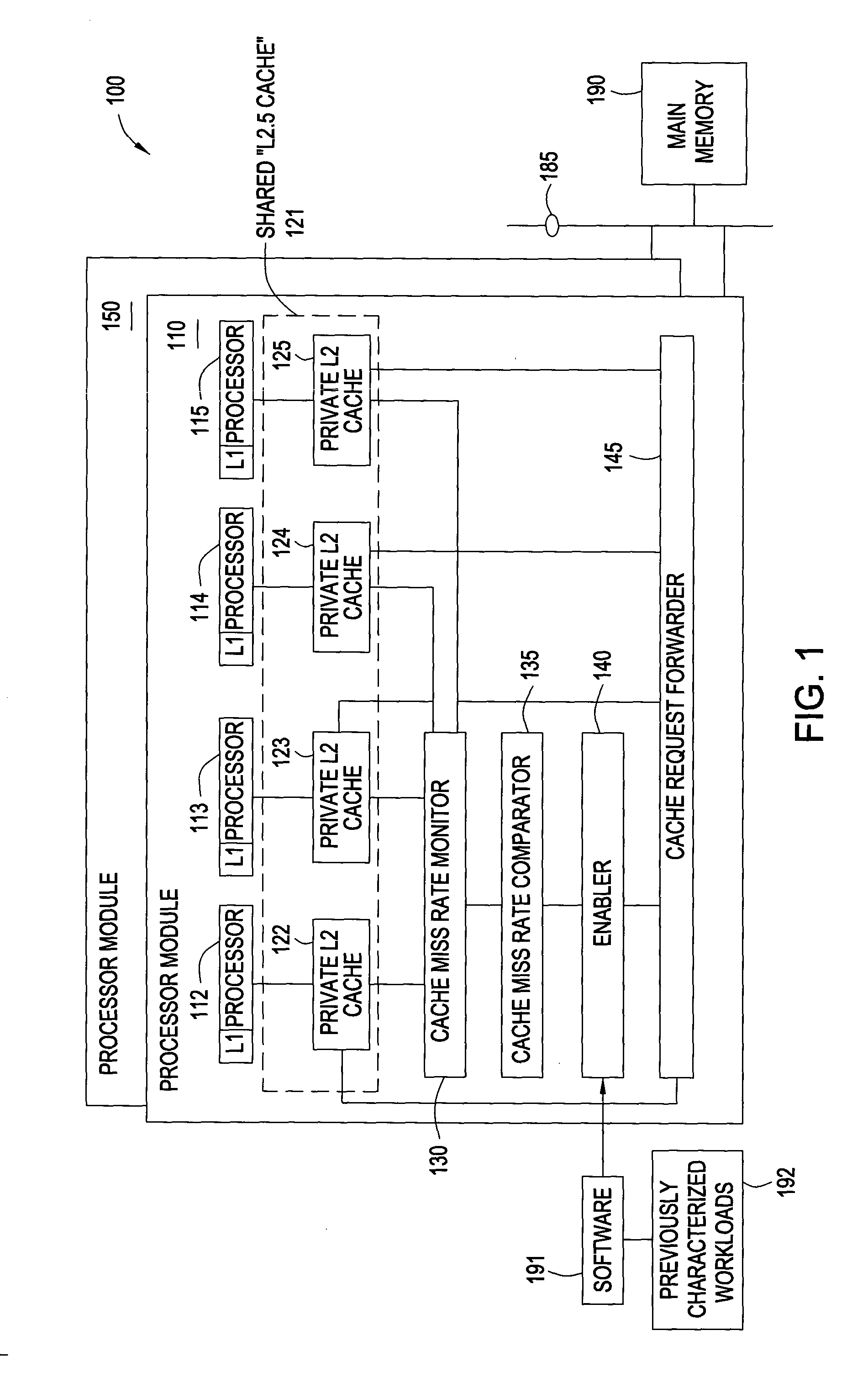
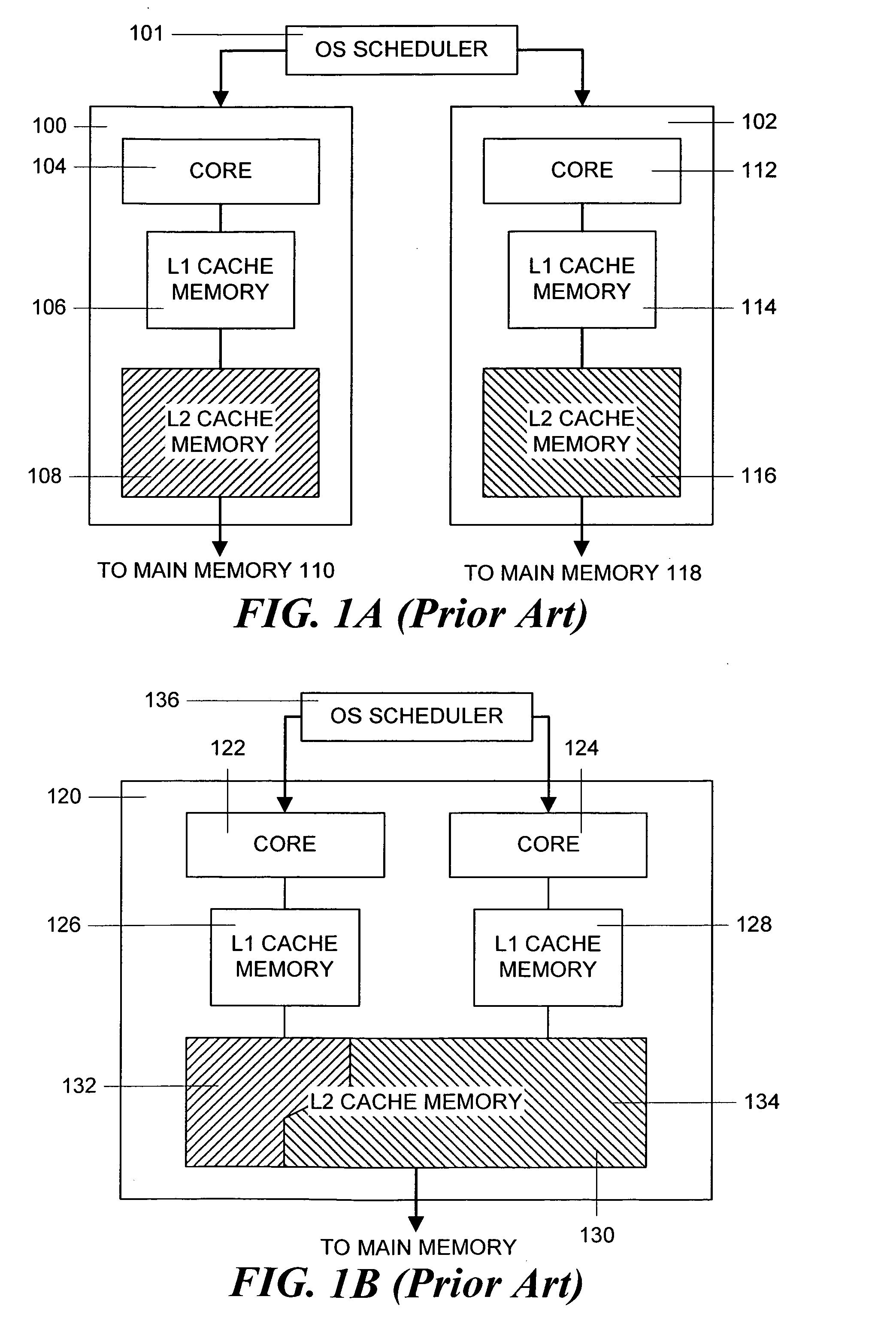
Reduction of cache miss rates using shared private caches
InactiveUS20050071564A1Reduce cache miss rateReduce rateMemory architecture accessing/allocationMemory adressing/allocation/relocationParallel computingWorkload
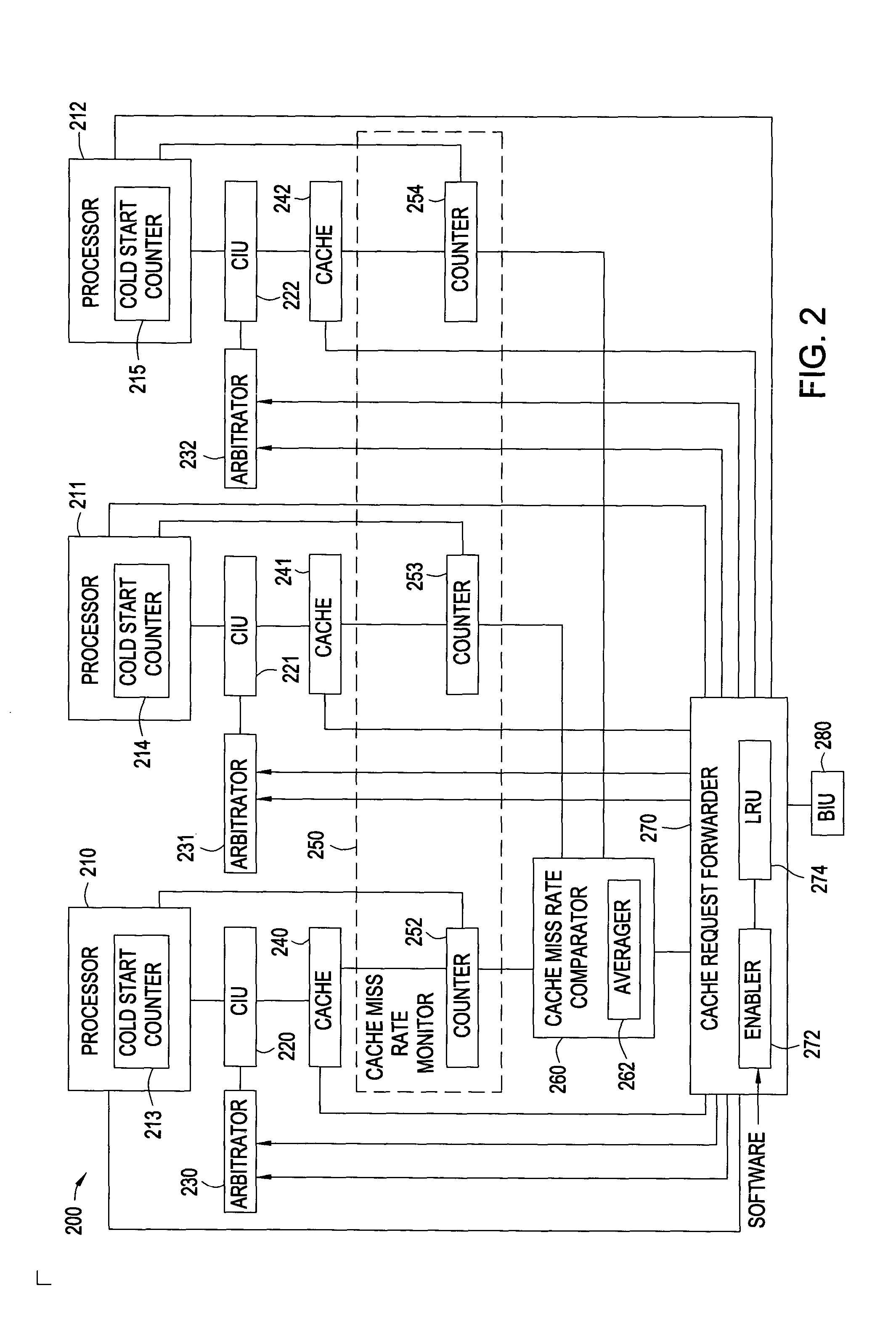
Methods and systems for reducing cache miss rates for cache are disclosed. Embodiments may include a computer system with one or more processors and each processor may couple with a private cache. Embodiments selectively enable and implement a cache re-allocation scheme for cache lines of the private caches based upon a workload or an expected workload for the processors. In particular, a cache miss rate monitor may count the number of cache misses for each processor. A cache miss rate comparator compares the cache miss rates to determine whether one or more of the processors have significantly higher cache miss rates than the average cache miss rates within a processor module or overall. If one or more processors have significantly higher cache miss rates, cache requests from those processors are forwarded to private caches that have lower cache miss rates and have the least recently used cache lines.
Owner:IBM CORP
Automatic filling method of time sequence missing value based on long-term and short-term memory network
ActiveCN108090558AAvoid relying on structureNeural architecturesNeural learning methodsMiss rateStructure dependence
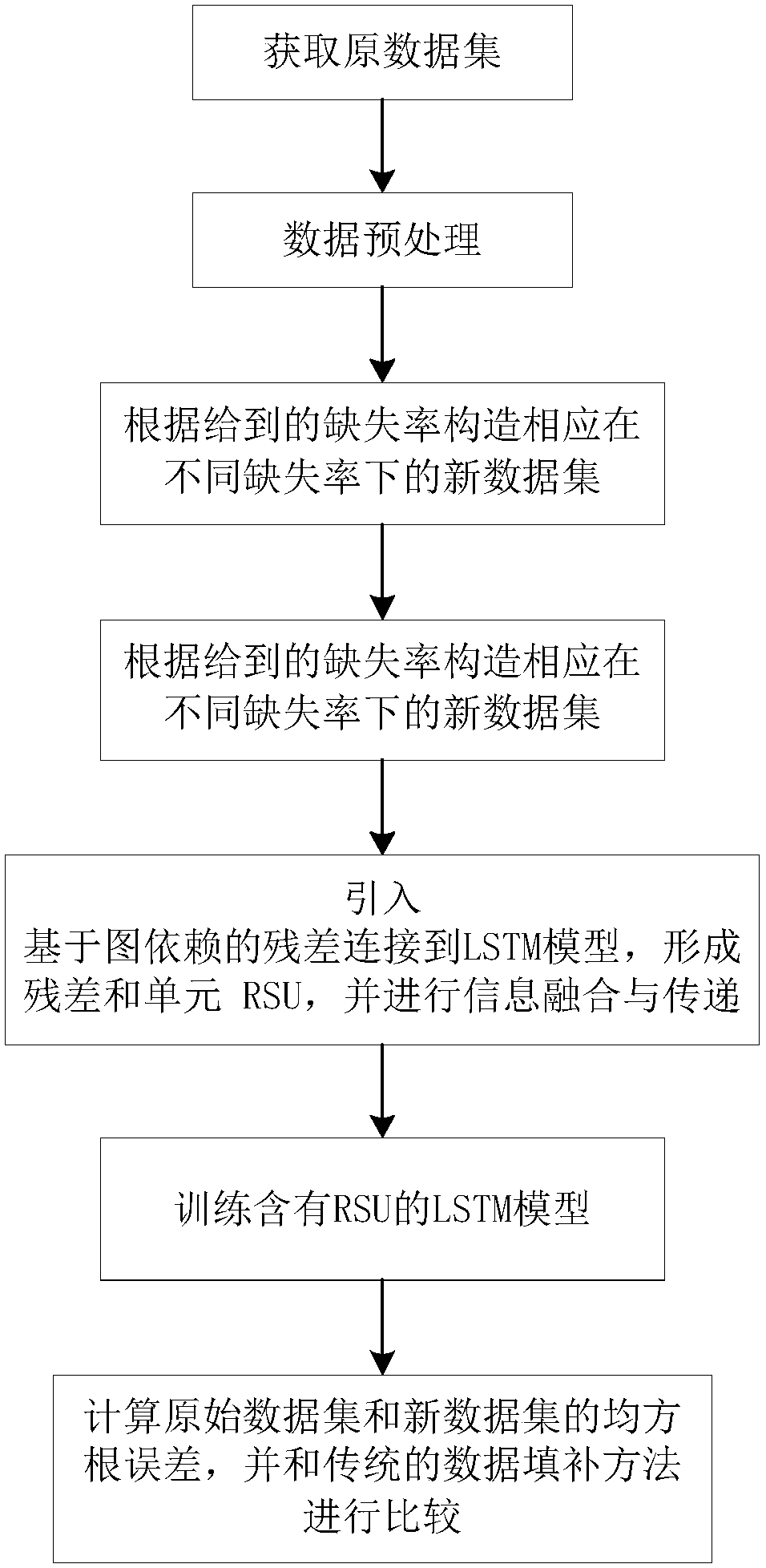
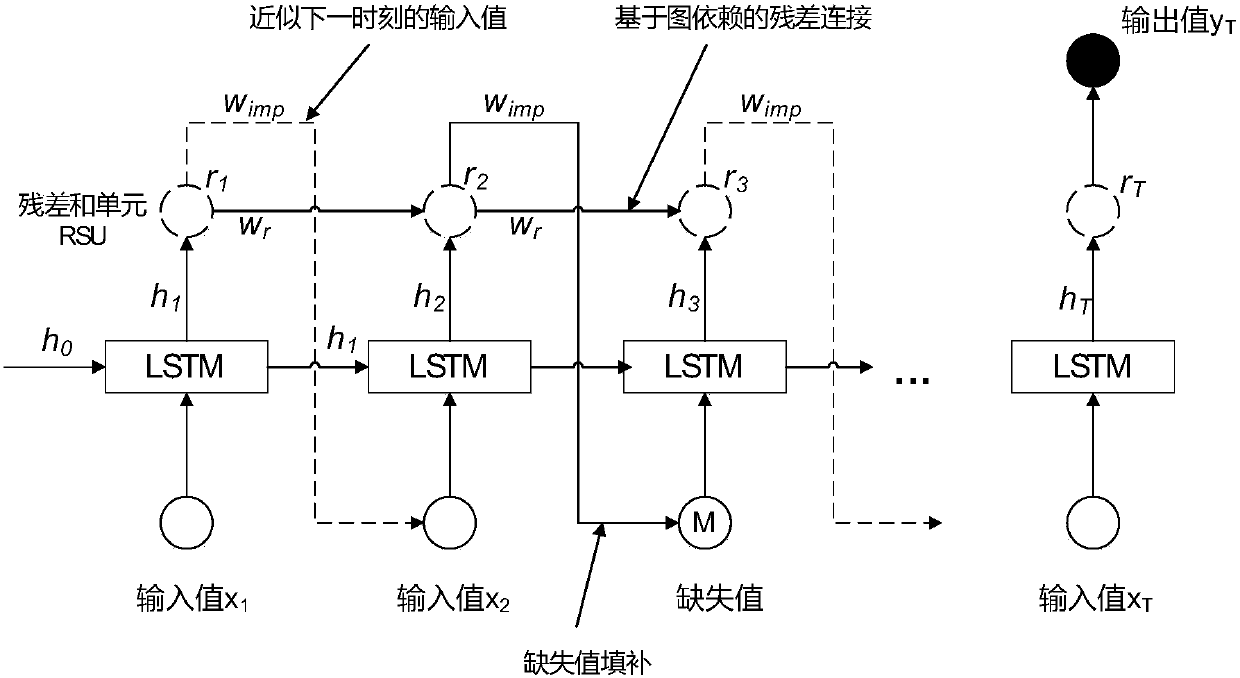
The invention discloses an automatic filling method of time sequence missing value based on long-term and short-term memory network, comprising the steps of obtaining an original data set having no missing value and conducting pre-processing; deleting certain values at random based on the given missing rate and forming a missing data set having different missing rates; introducing residual error based on graph dependence and connecting the residual error to an LSTM model to from a RSU based on deep residual network and thought of graph structure dependence, and conducting blending and transmitting on the every-minute hidden state of the LSTM model and the historical state information of the RSU; training the newly-established model and conducting filling during the propagation process by means of the RSU value according to whether the data is missing before the network training. The invention is advantageous in that the RSU integrates the anterior residual error with the hidden state information, and thereby the established model can be associated with adequate historical information related to missing data, and the end-to-end missing value training conducted on the time sequence data having missing value can be realized.
Owner:SOUTH CHINA UNIV OF TECH
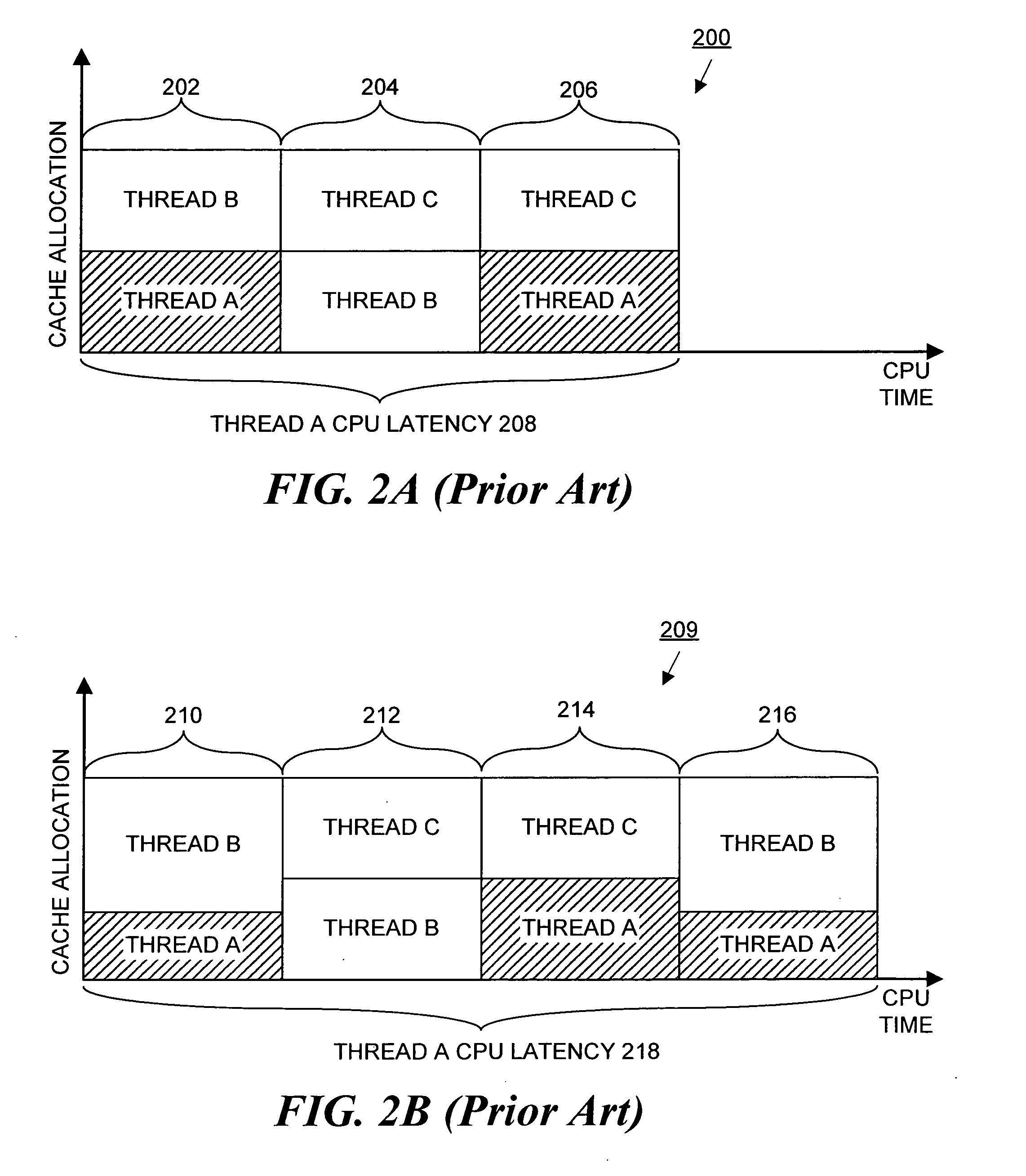
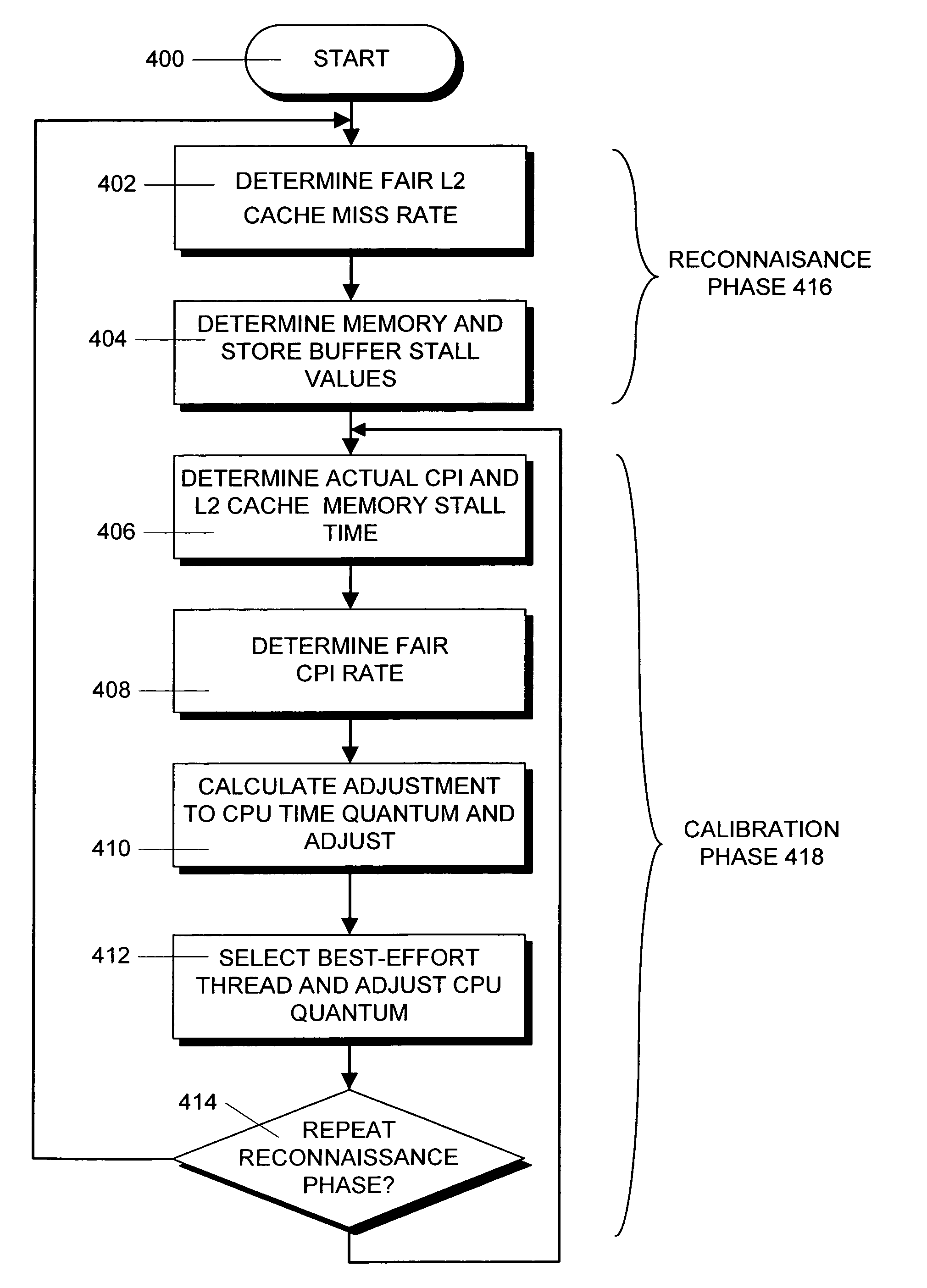
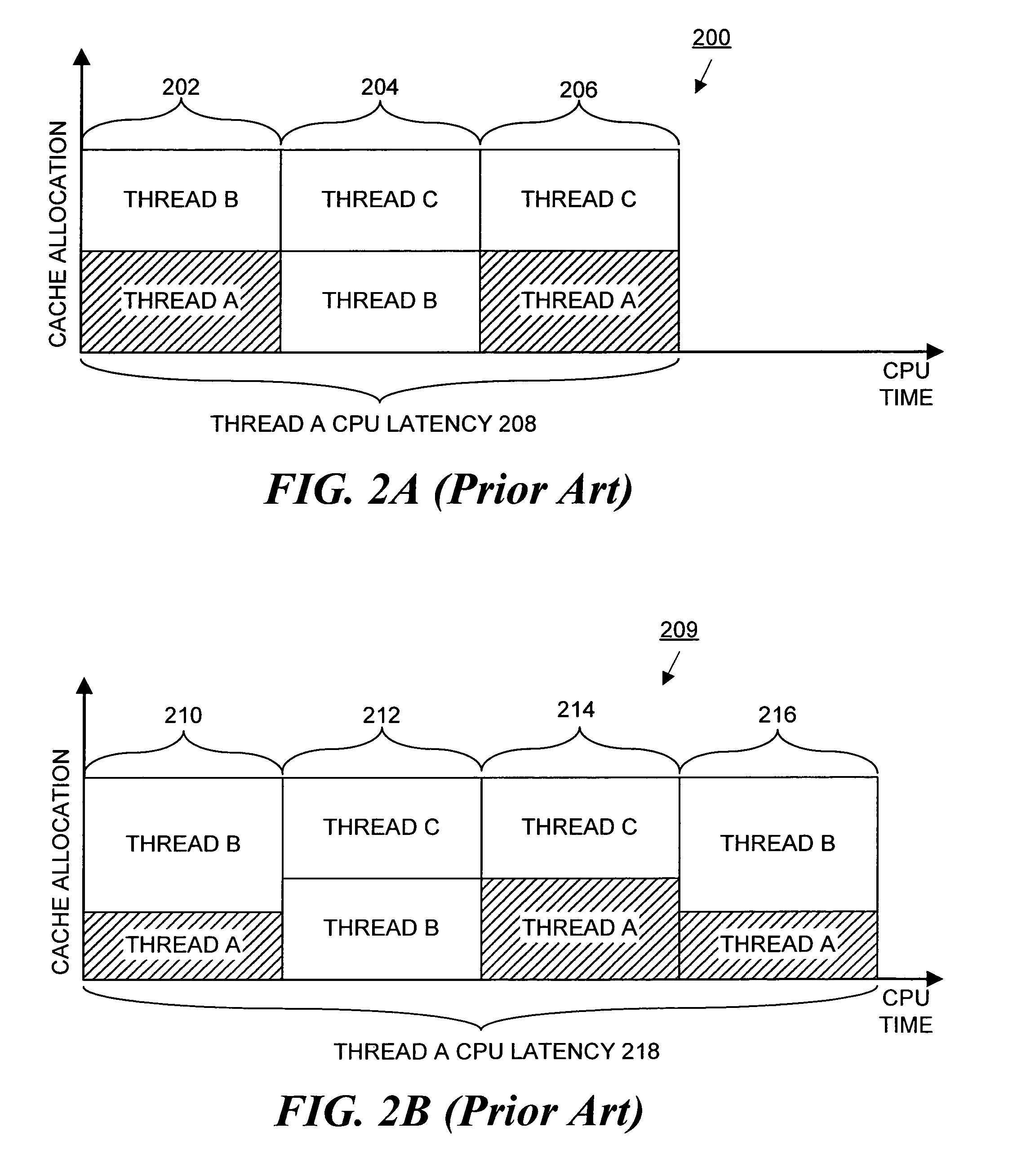
Method and apparatus for achieving fair cache sharing on multi-threaded chip multiprocessors
ActiveUS20080059712A1Fair cache miss rateMemory adressing/allocation/relocationMultiprogramming arrangementsOperational systemMulti processor
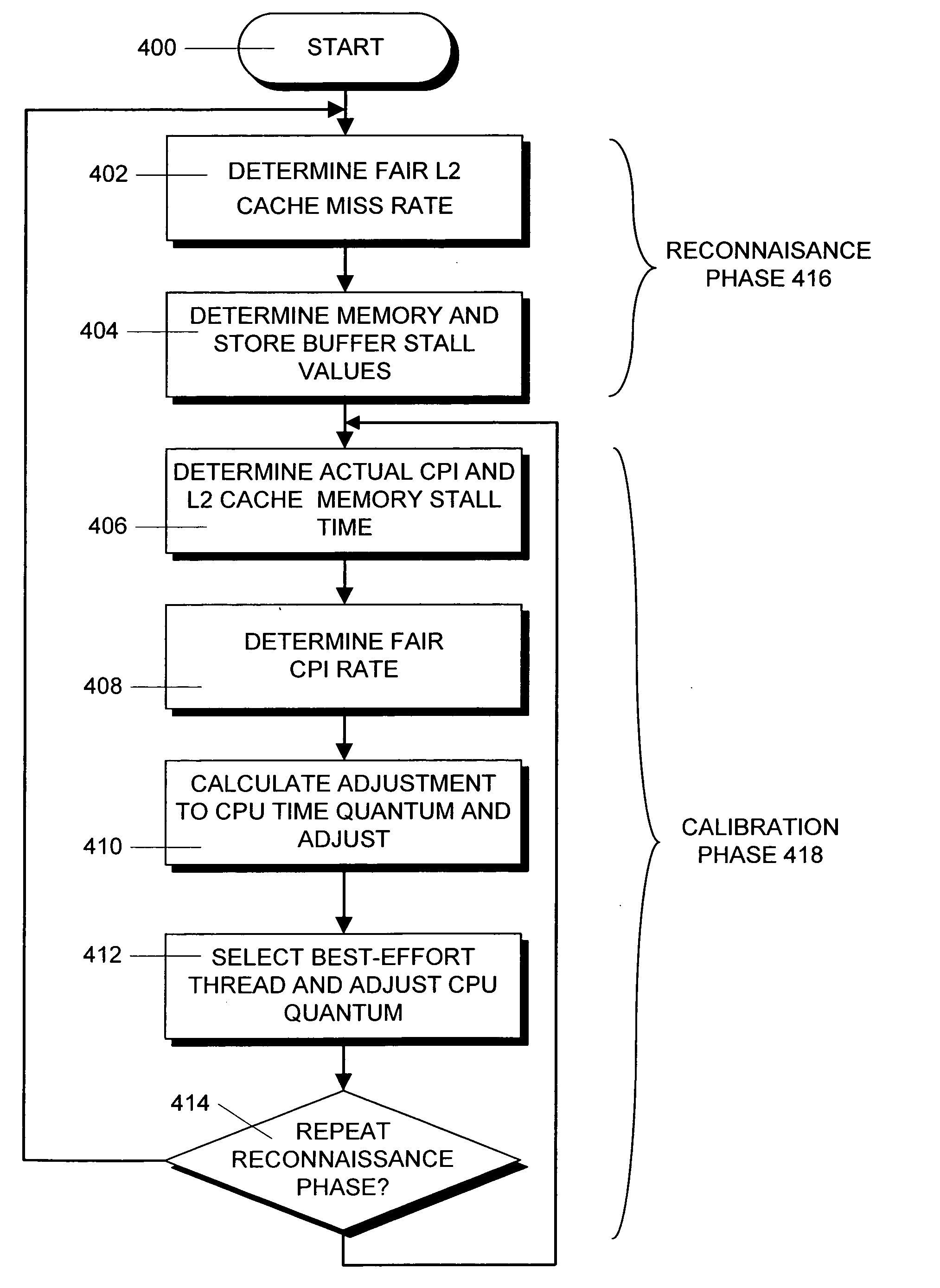
In a computer system with a multi-core processor having a shared cache memory level, an operating system scheduler adjusts the CPU latency of a thread running on one of the cores to be equal to the fair CPU latency which that thread would experience when the cache memory was equally shared by adjusting the CPU time quantum of the thread. In particular, during a reconnaissance time period, the operating system scheduler gathers information regarding the threads via conventional hardware counters and uses an analytical model to estimate a fair cache miss rate that the thread would experience if the cache memory was equally shared. During a subsequent calibration period, the operating system scheduler computes the fair CPU latency using runtime statistics and the previously computed fair cache miss rate value to determine the fair CPI value.
Owner:ORACLE INT CORP
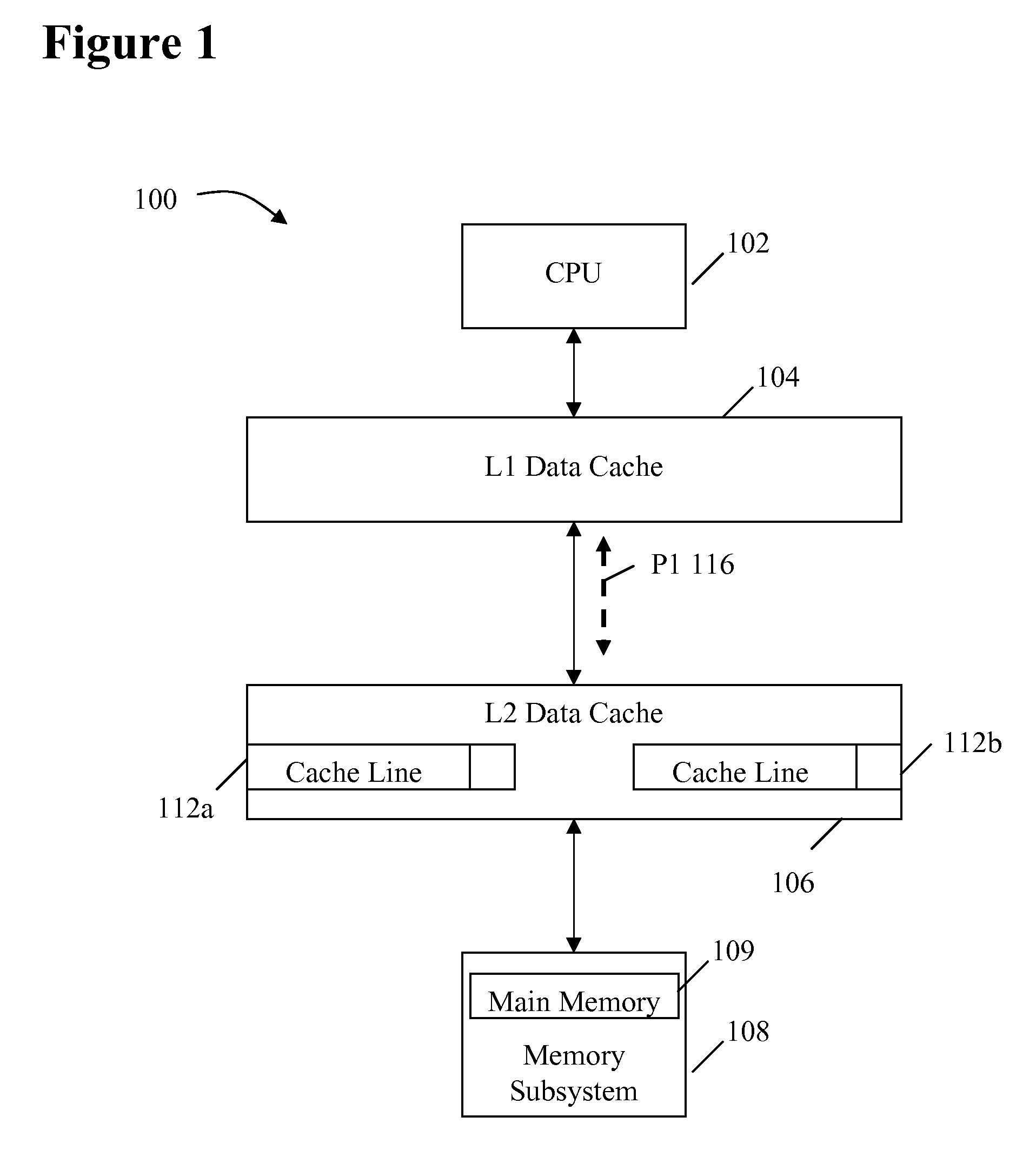
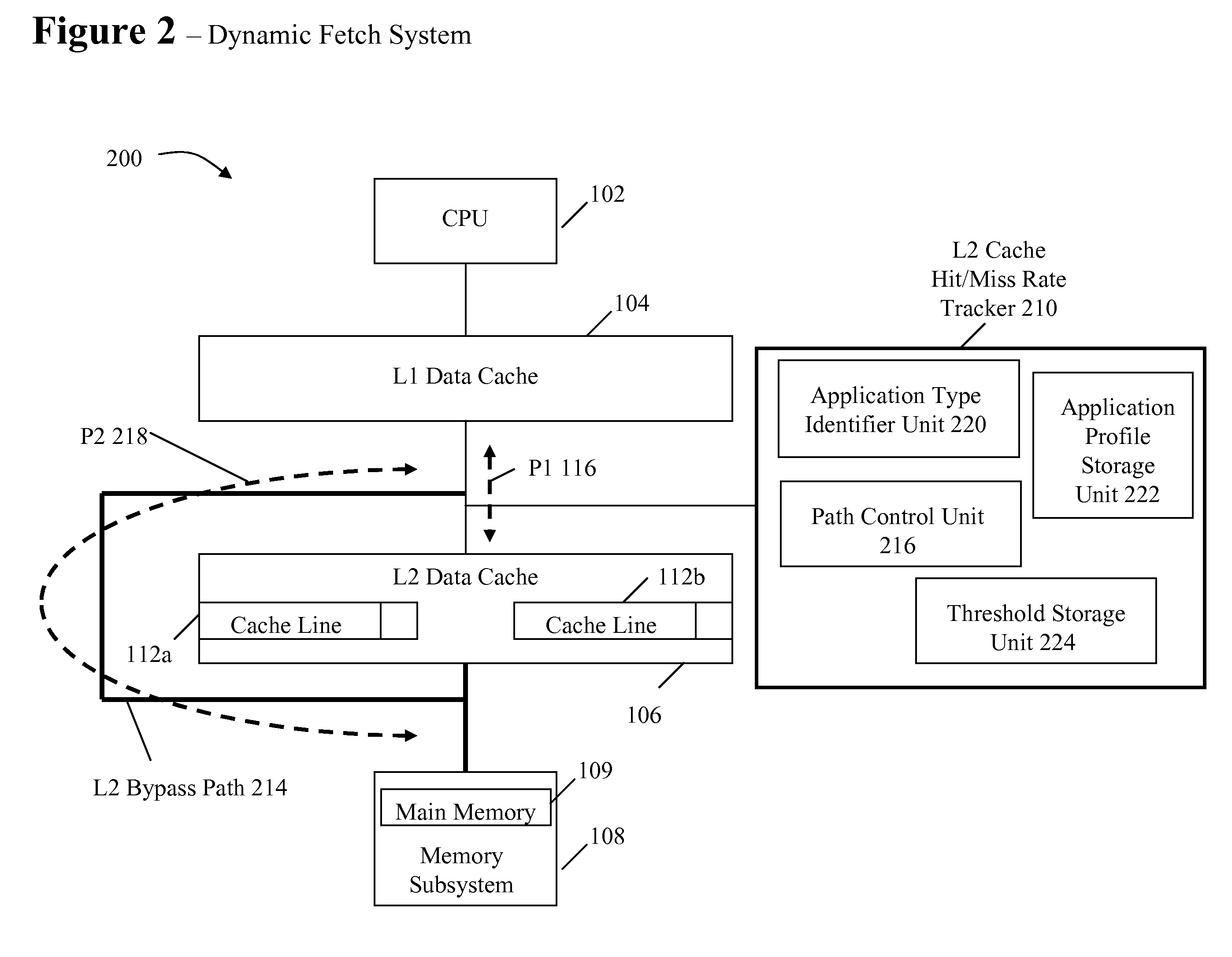
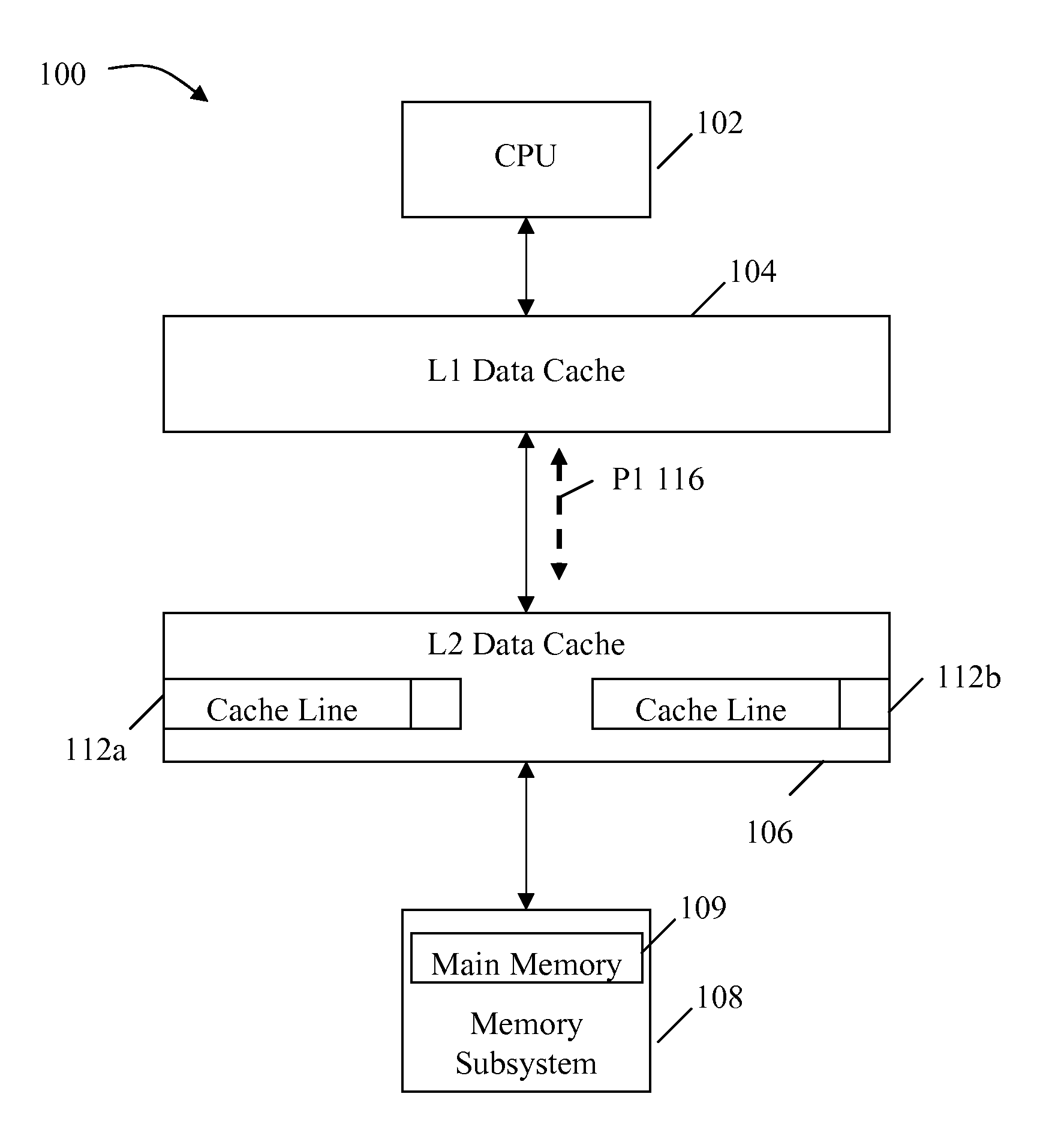
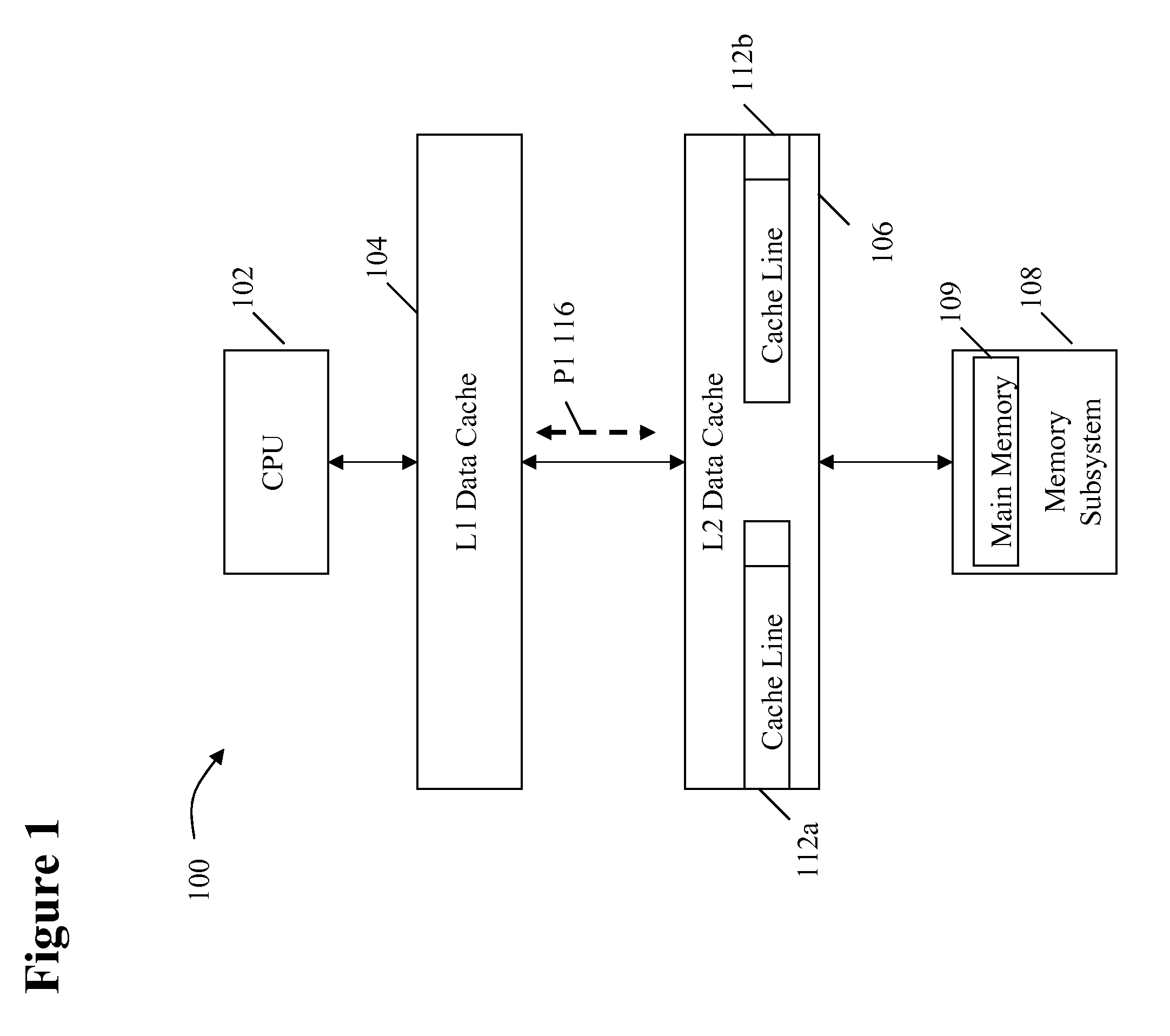
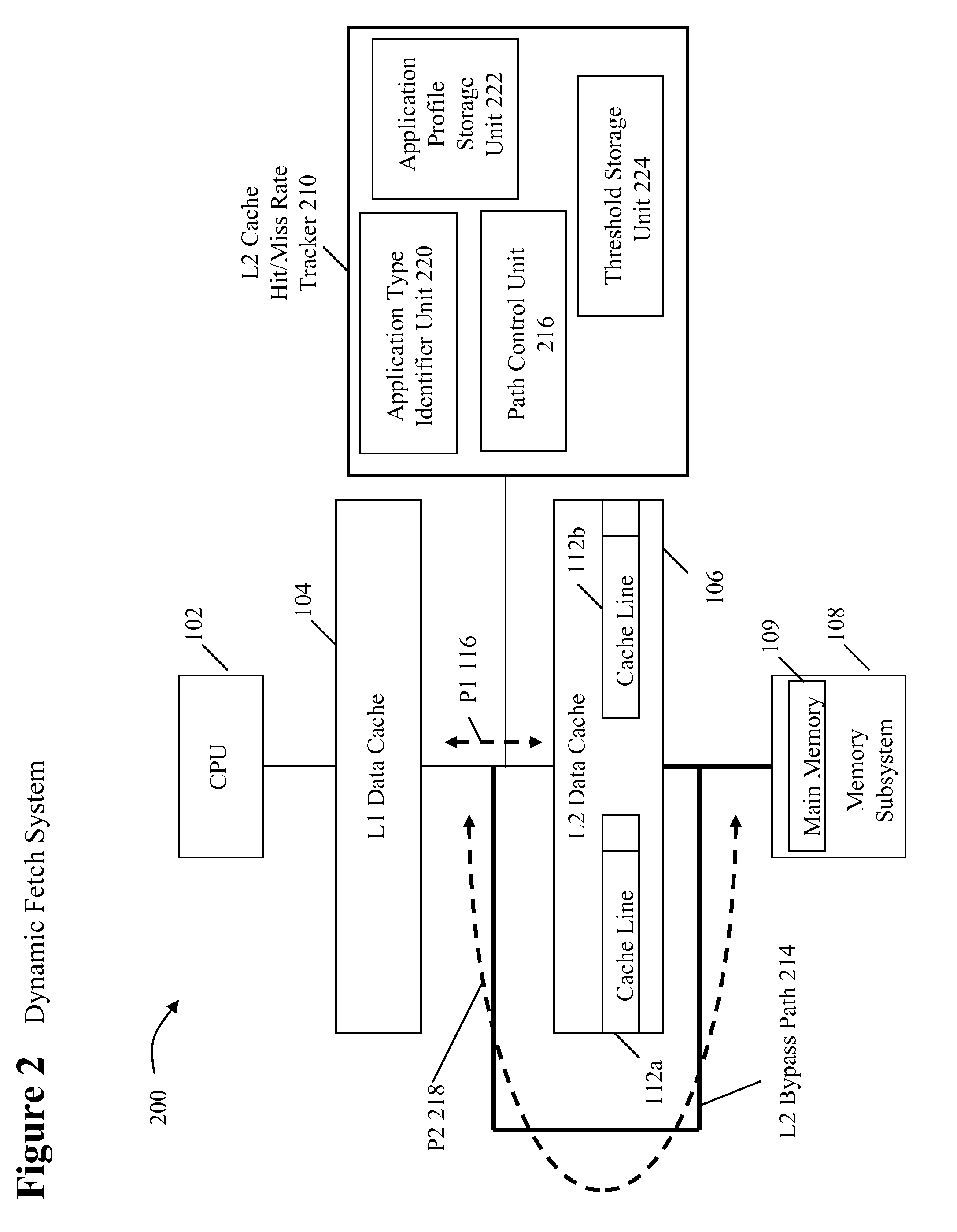
System and method for dynamically selecting the fetch path of data for improving processor performance
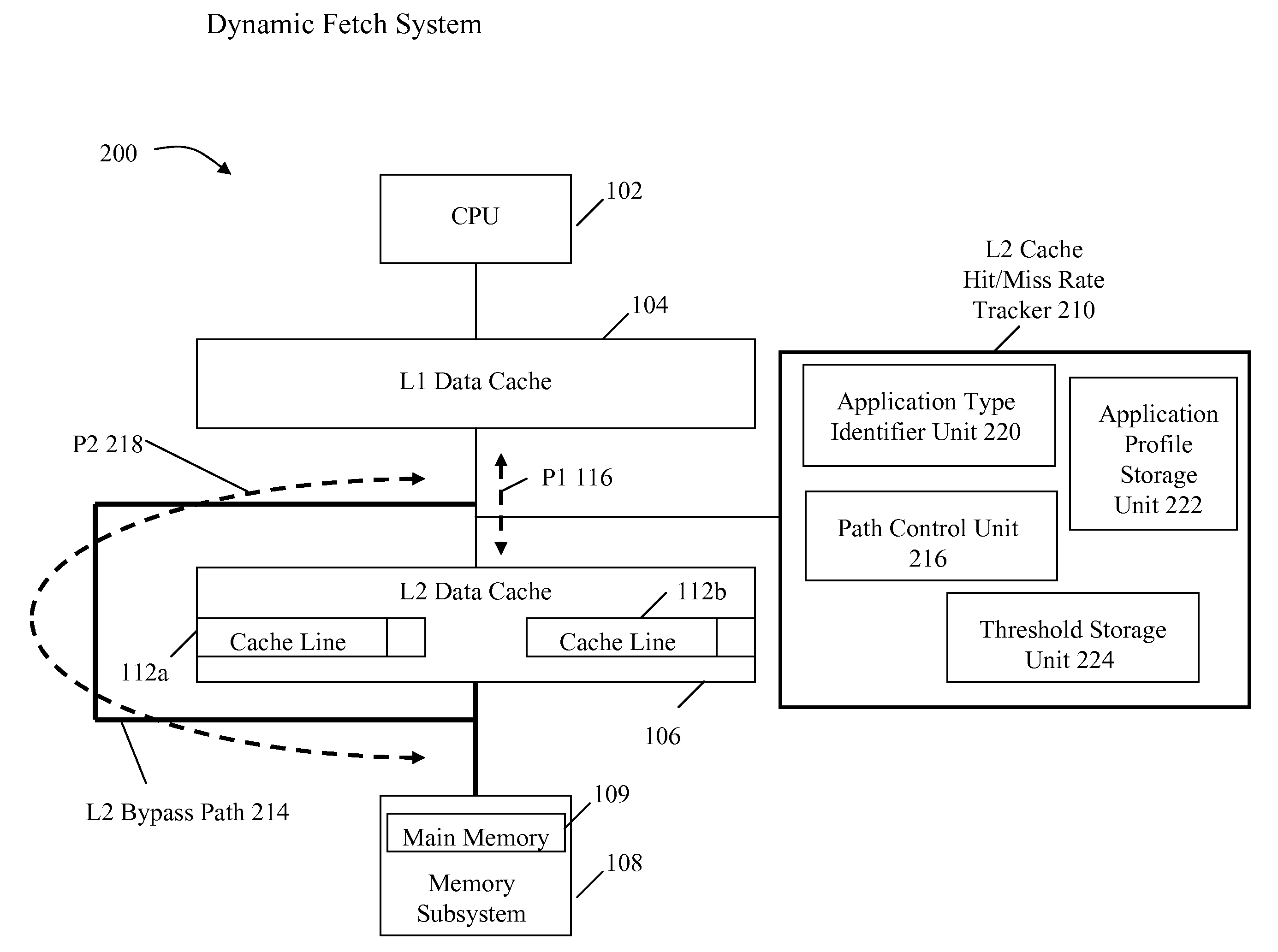
InactiveUS20090037664A1Improve system performanceImprove latencyMemory adressing/allocation/relocationData accessParallel computing
A system and method for dynamically selecting the data fetch path for improving the performance of the system improves data access latency by dynamically adjusting data fetch paths based on application data fetch characteristics. The application data fetch characteristics are determined through the use of a hit / miss tracker. It reduces data access latency for applications that have a low data reuse rate (streaming audio, video, multimedia, games, etc.) which will improve overall application performance. It is dynamic in a sense that at any point in time when the cache hit rate becomes reasonable (defined parameter), the normal cache lookup operations will resume. The system utilizes a hit / miss tracker which tracks the hits / misses against a cache and, if the miss rate surpasses a prespecified rate or matches an application profile, the hit / miss tracker causes the cache to be bypassed and the data is pulled from main memory or another cache thereby improving overall application performance.
Owner:IBM CORP
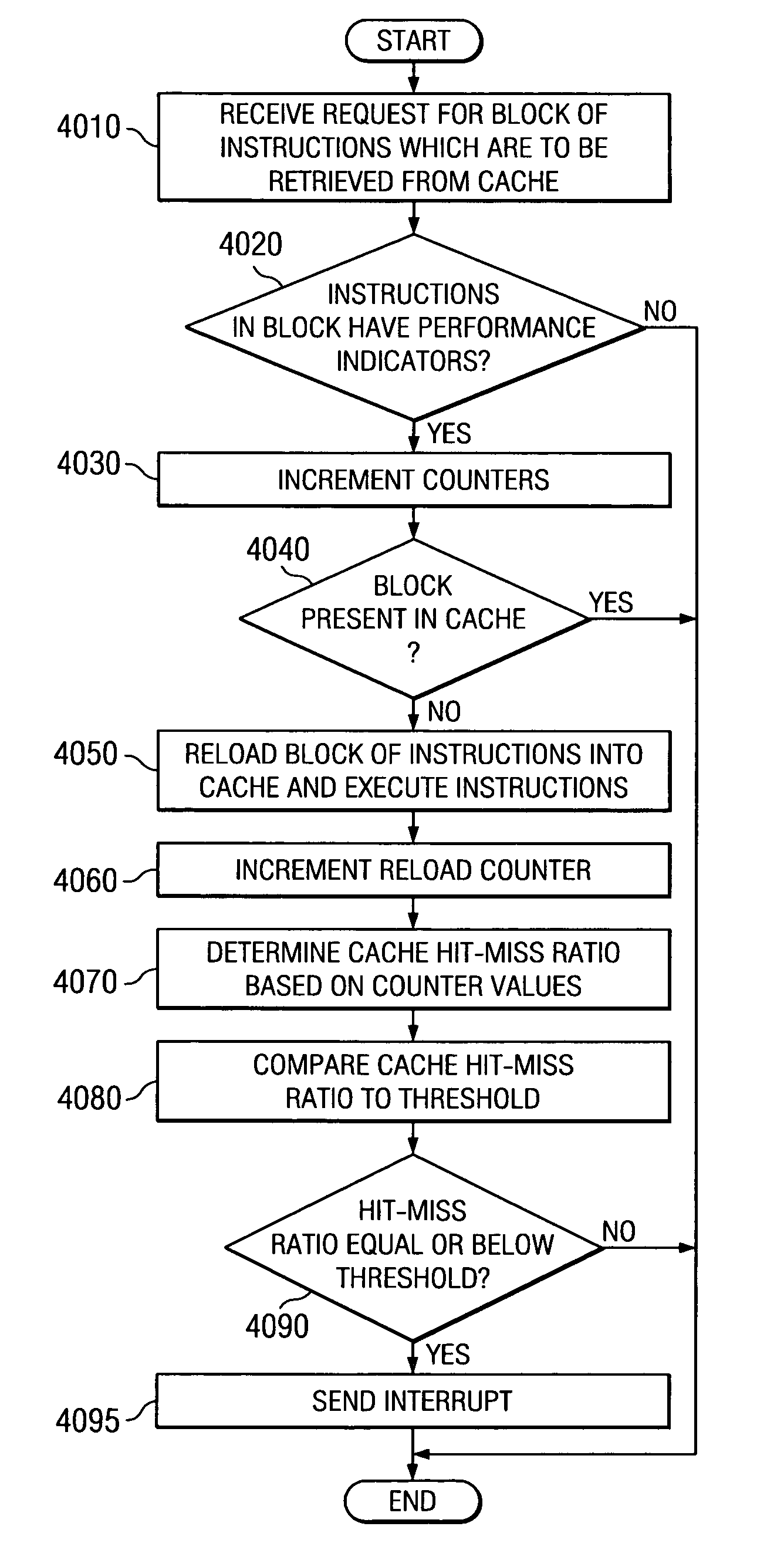
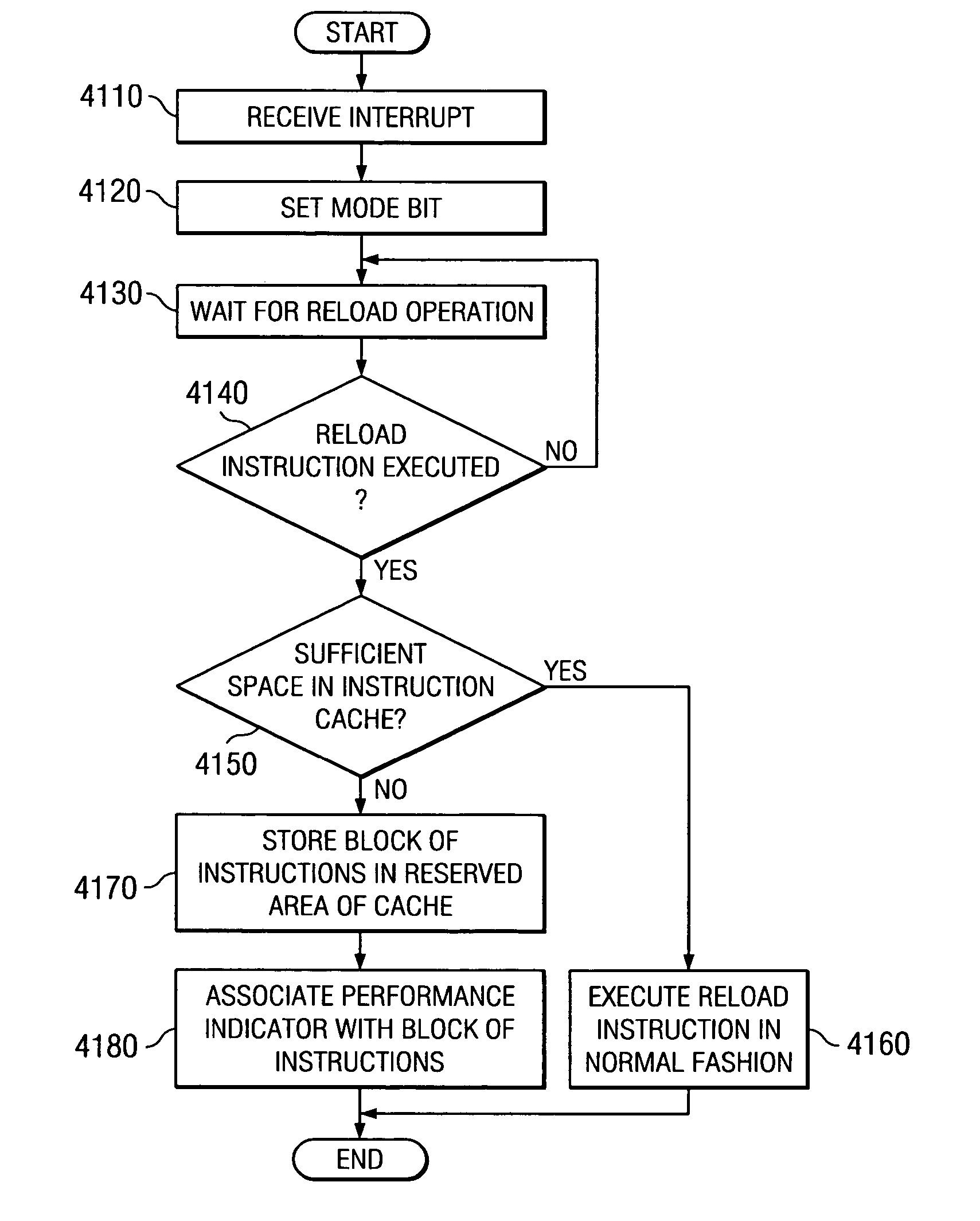
Method and apparatus for autonomic detection of cache "chase tail" conditions and storage of instructions/data in "chase tail" data structure
InactiveUS20050155020A1Improve performanceMemory adressing/allocation/relocationDigital computer detailsData processing systemProcessing Instruction
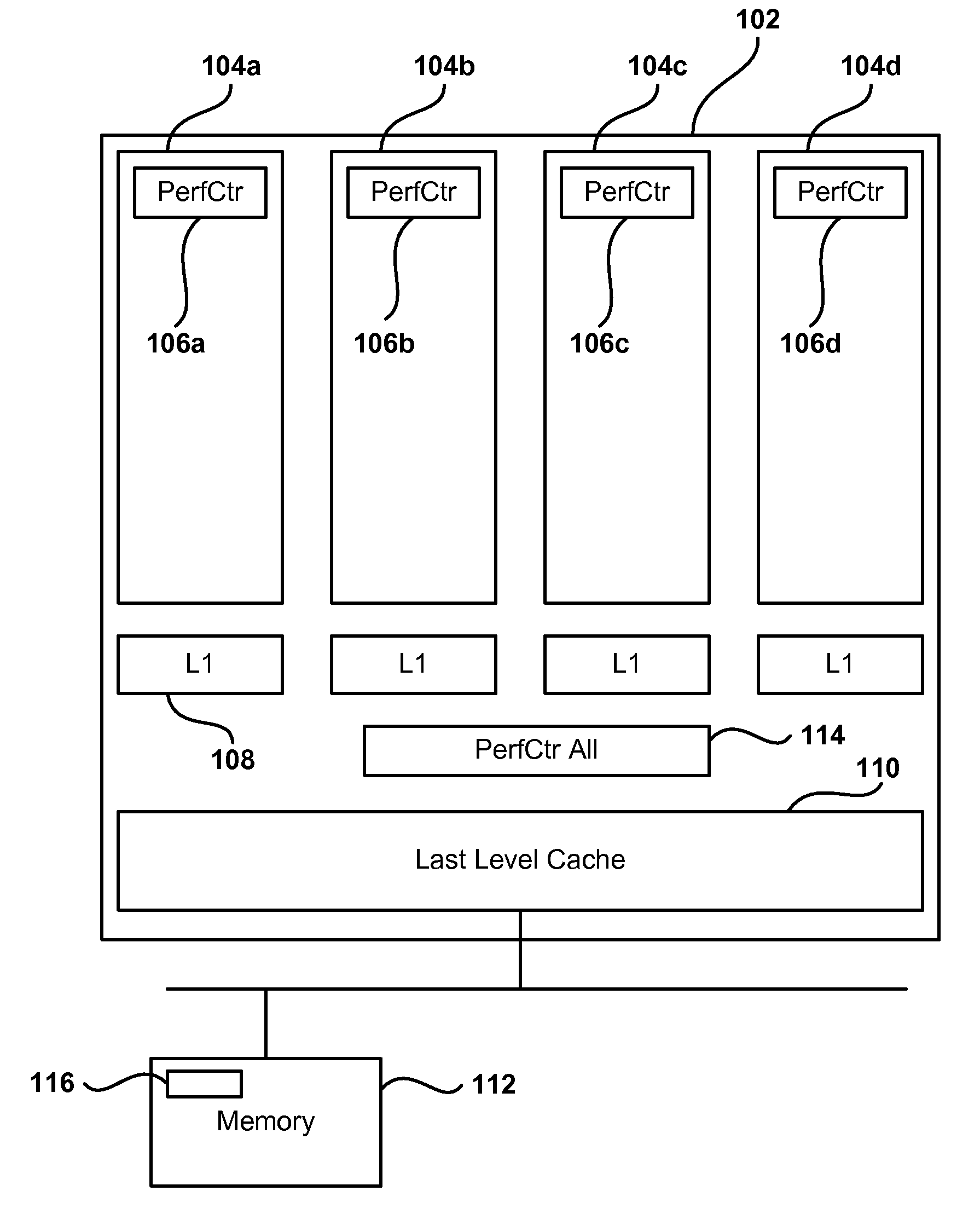
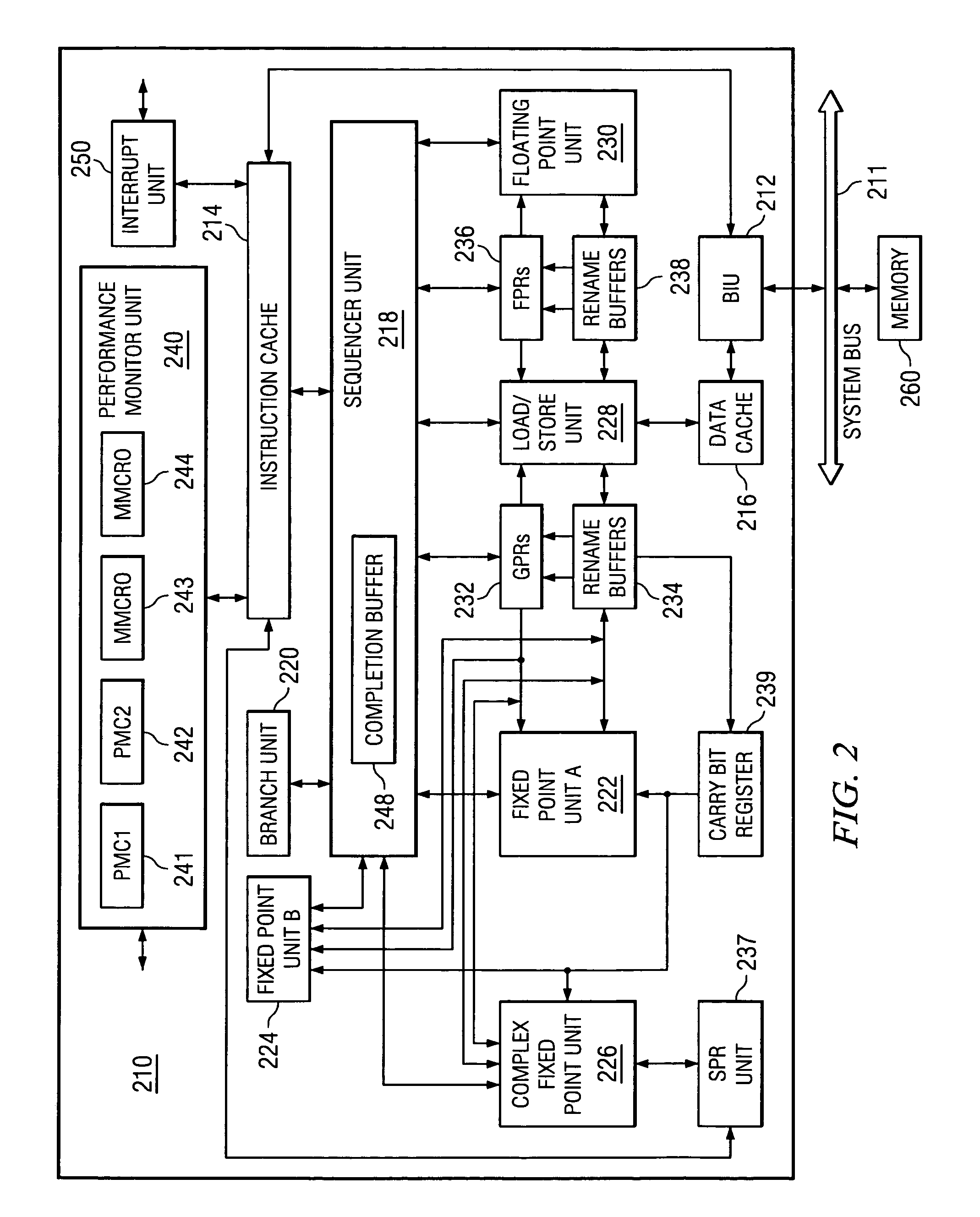
A method, apparatus, and computer instructions in a data processing system for processing instructions are provided. Instructions are received at a processor in the data processing system. If a selected indicator is associated with the instruction, counting of each event associated with the execution of the instruction is enabled. The performance indicators and counter values may be used as a mechanism for identifying cache hits and cache misses. Performance counters are incremented each time the instructions of routines of interest are executed and each time the instructions must be reloaded into the cache. From the values of these counters the cache hit-miss ratio may be determined. When the cache hit-miss ratio becomes less than a predetermined threshold, i.e. there is a greater number of cache misses than cache hits, the present invention may determine that a problem condition has occurred and initiate “chase tail” operations for avoiding overwriting of entries in the cache.
Owner:IBM CORP
Tunable processor performance benchmarking
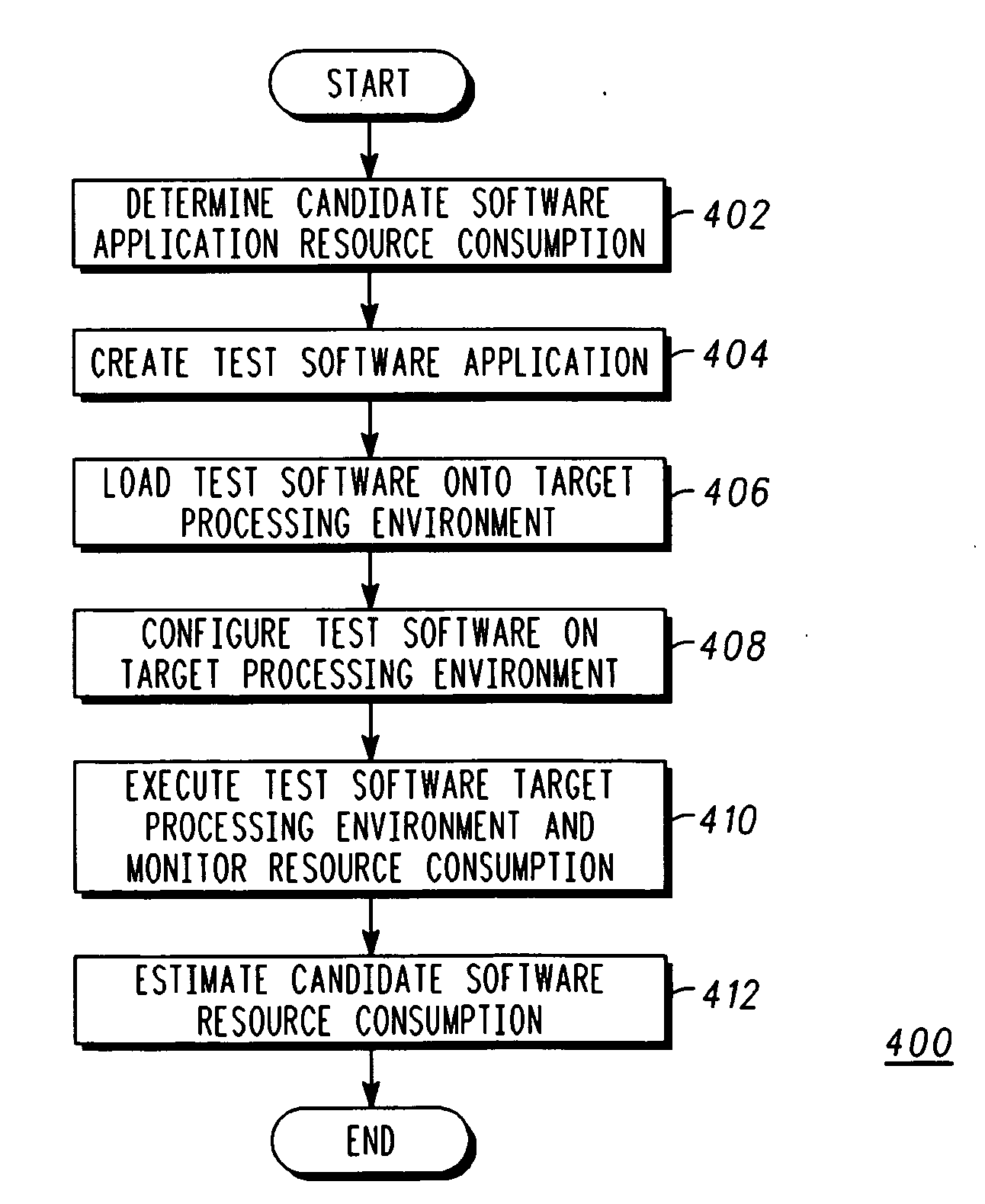
InactiveUS20070136726A1Error detection/correctionMultiprogramming arrangementsResource consumptionParallel computing
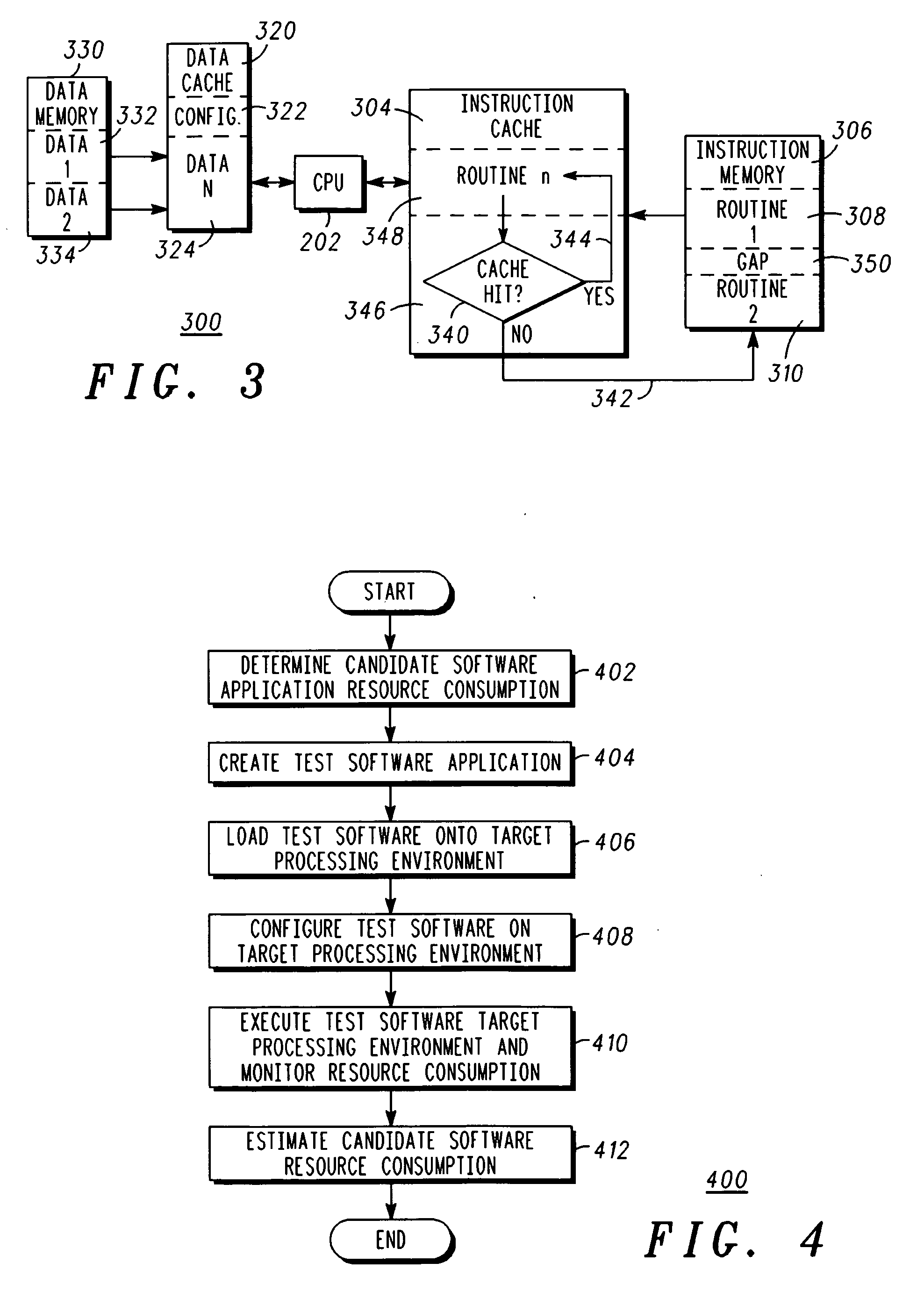
A tunable processor performance benchmarking method and system (100) estimates candidate software performance on a target processing environment (104) without porting the application. The candidate software's resource consumption is characterized to determine cache hit or miss rates. A test software generator (102) generates test software that is configured to have substantially the same cache miss rates and processor utilization, and its performance is measured when executing on the target processing environment (104). Instruction cache hit rates are maintained for the test software by selectively branching either within a routine (308, 310) that is resident in the instruction cache or to a routine (308, 310) that is not within the instruction cache. Data blocks (332, 334) are also selectively accessed in order to maintain a desired data cache miss rate.
Owner:MOTOROLA INC
Method for reducing CRISPR/Cas9 mediated embryo gene editing missing rate
InactiveCN107557394ATargeted editing efficiency is highLow rate of off-target mutationsStable introduction of DNAFermentationCompound aEmbryo
The invention relates to a method for reducing CRISPR / Cas9 mediated embryo gene editing missing rate. The method comprises the following steps: compounding a sgRNA sequence of a targeting gene and constructing a sgRNA expression plasmid carrying T7 promoter; in vitro transcribing Cas9mRNA and sgRNA; and importing intracytoplasmic sperm into unfertilized MII ovum by adopting intracytoplasmic sperminjection (ICSI) and meanwhile importing Cas9mRNA and sgRNA. According to the method provided by the invention, the targeting editing efficiency is high and the missing mutation rate is low.
Owner:NANJING DRUM TOWER HOSPITAL
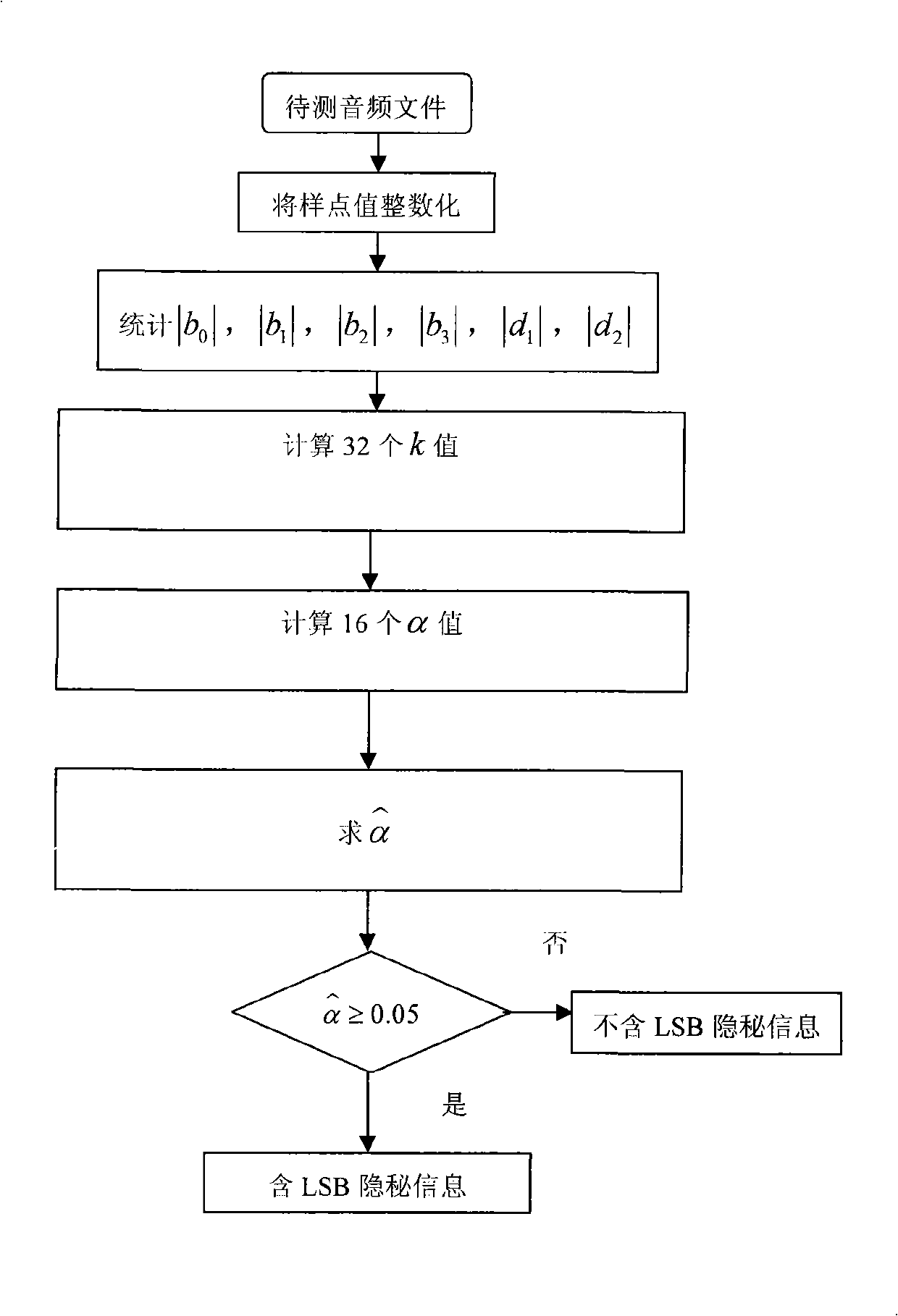
Detection method for time-domain audio LSB hidden write
The invention discloses a detection method aiming at the time-domain audio LSB insertion, which comprises the following concrete steps: an audio file to be detected is read and the value of each sampling point in the file is integralized; a sampling pair statistical change rule is obtained by observing the values of the sampling points of sampling pairs in the audio file to be detected; insertion strength is analyzed by the sampling pair statistical change rule; whether an insertion strength analysis value a reaches the strength threshold value is judged; if the insertion strength analysis value a is larger than or equal to the strength threshold value, the audio file is detected to contain LSB hiding information; conversely, the detection result is that LSB hiding information is not contained in the audio file. The method can not only detect the existence of LSB hiding information, but also evaluate the insertion strength, thereby ensuring the high detection accuracy, low false alarming rate and low detection missing rate; in addition, the method has simple use and low time complexity. The method can be applied to the field of hiding information detection and is very significant to the illegal hiding communication.
Owner:WUHAN UNIV
System and method for dynamically selecting the fetch path of data for improving processor performance
InactiveUS7865669B2Improve system performanceImprove latencyMemory adressing/allocation/relocationSensuData access
A system and method for dynamically selecting the data fetch path for improving the performance of the system improves data access latency by dynamically adjusting data fetch paths based on application data fetch characteristics. The application data fetch characteristics are determined through the use of a hit / miss tracker. It reduces data access latency for applications that have a low data reuse rate (streaming audio, video, multimedia, games, etc.) which will improve overall application performance. It is dynamic in a sense that at any point in time when the cache hit rate becomes reasonable (defined parameter), the normal cache lookup operations will resume. The system utilizes a hit / miss tracker which tracks the hits / misses against a cache and, if the miss rate surpasses a prespecified rate or matches an application profile, the hit / miss tracker causes the cache to be bypassed and the data is pulled from main memory or another cache thereby improving overall application performance.
Owner:INT BUSINESS MASCH CORP
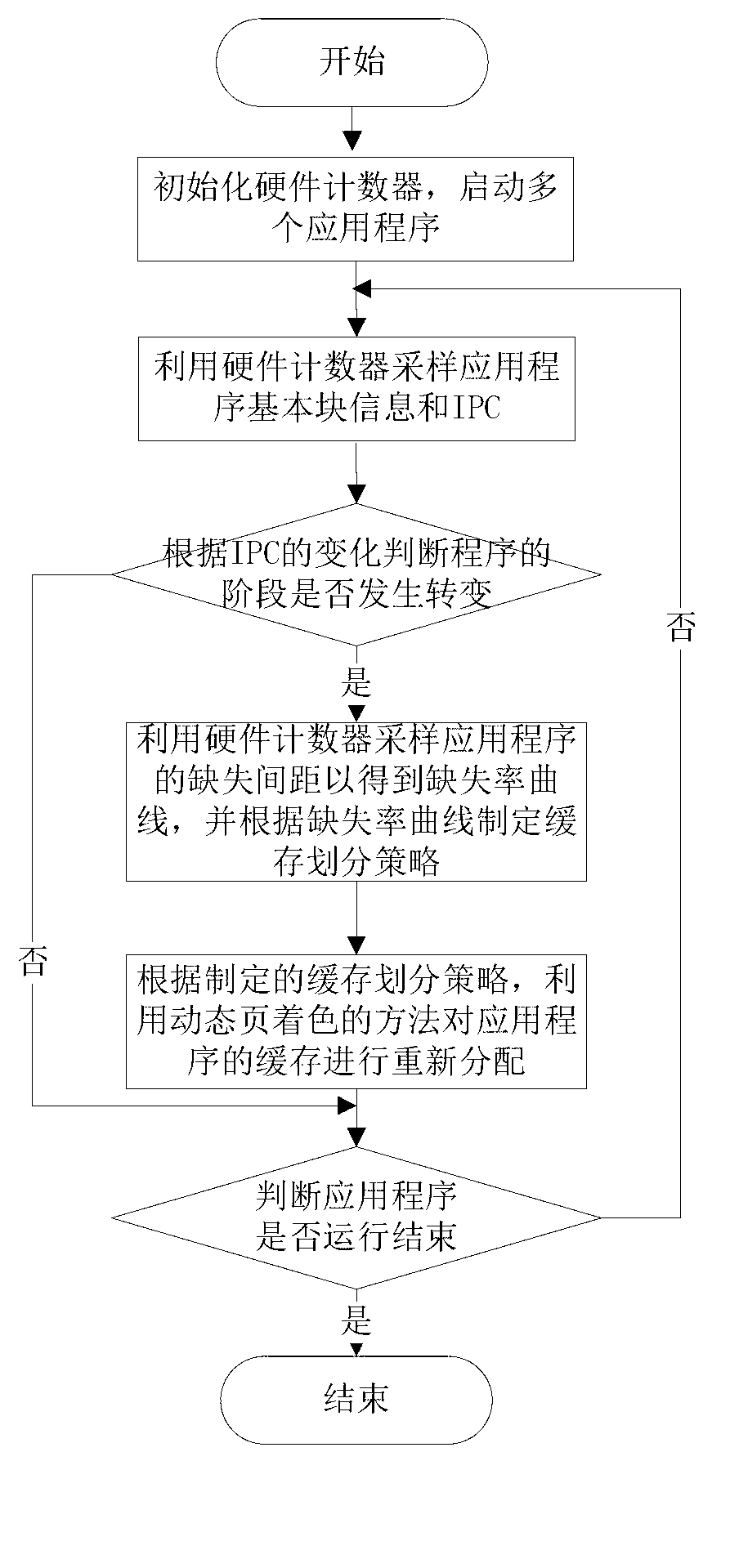
Method for dynamically partitioning shared cache in multi-core environment
InactiveCN103077128ACache fitImprove performanceResource allocationMemory adressing/allocation/relocationMiss rateApplication software
The invention discloses a method for dynamically partitioning a shared cache in a multi-core environment. The method comprises the following steps of: initializing a hardware counter, starting a plurality of applications, sampling running information of the applications by using the hardware counter, obtaining basic block information of the applications by using the hardware counter, analyzing phase behaviors of the applications, judging whether phases of the applications are changed or not through extracting the IPC (Instruction Per Cycle) coefficient of variation of the applications, obtaining cache miss pitches of the applications by using the hardware counter if the phases of the applications are changed so as to obtain miss rate curves, establishing cache partitioning strategies for the applications according to the miss rate curves, and reallocating caches of the applications by using a dynamic page coloring method according to the established cache partitioning strategies. According to the method, the cache demand changes of the applications can be perceived, so that the caches of the applications are subjected to adjustment at the best time; and furthermore, compared with the existing phase behavior analysis method, the method has the advantages that the performance of the applications is hardly affected, and the overall performance of a system can be effectively improved.
Owner:HUAZHONG UNIV OF SCI & TECH
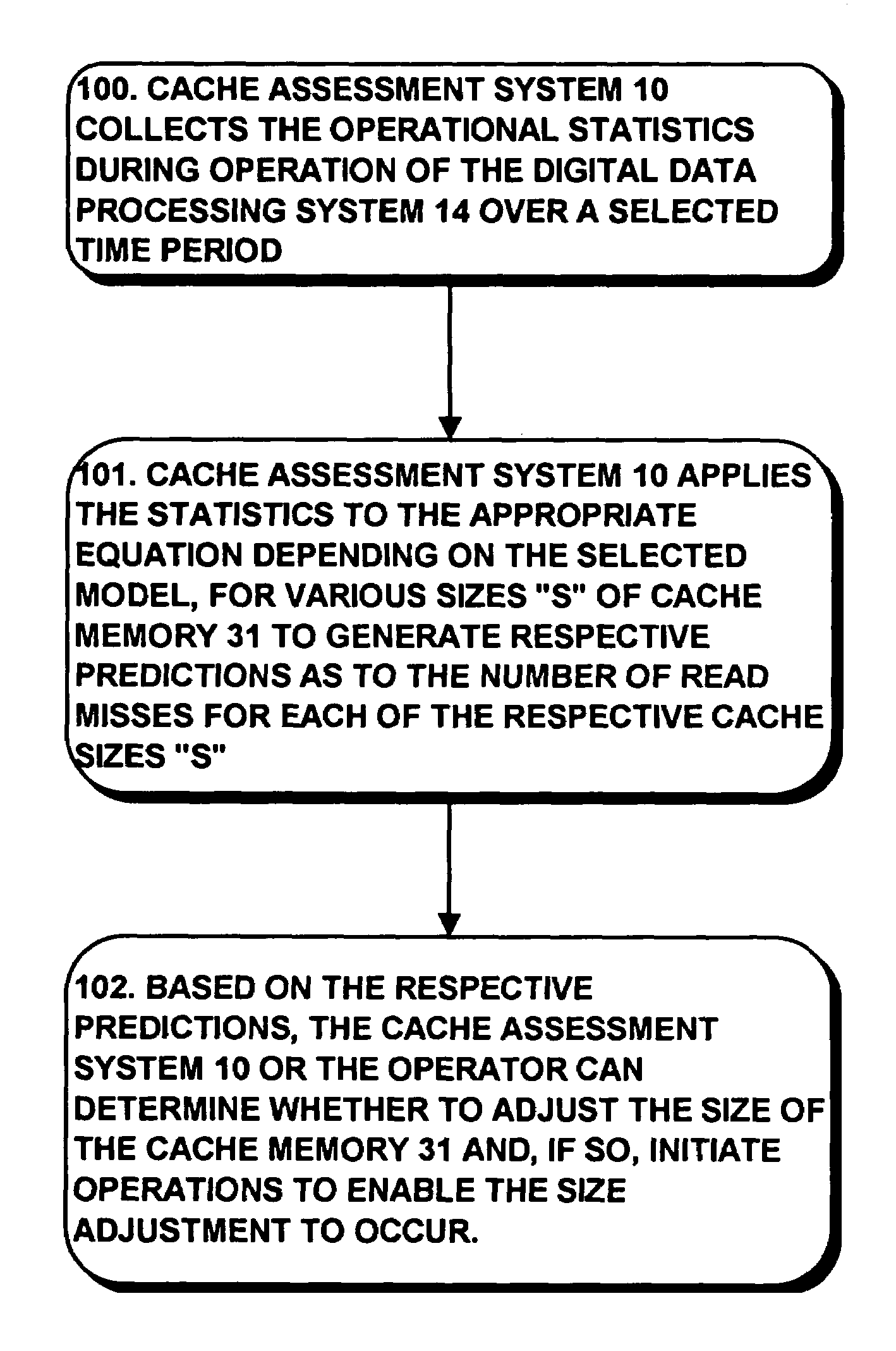
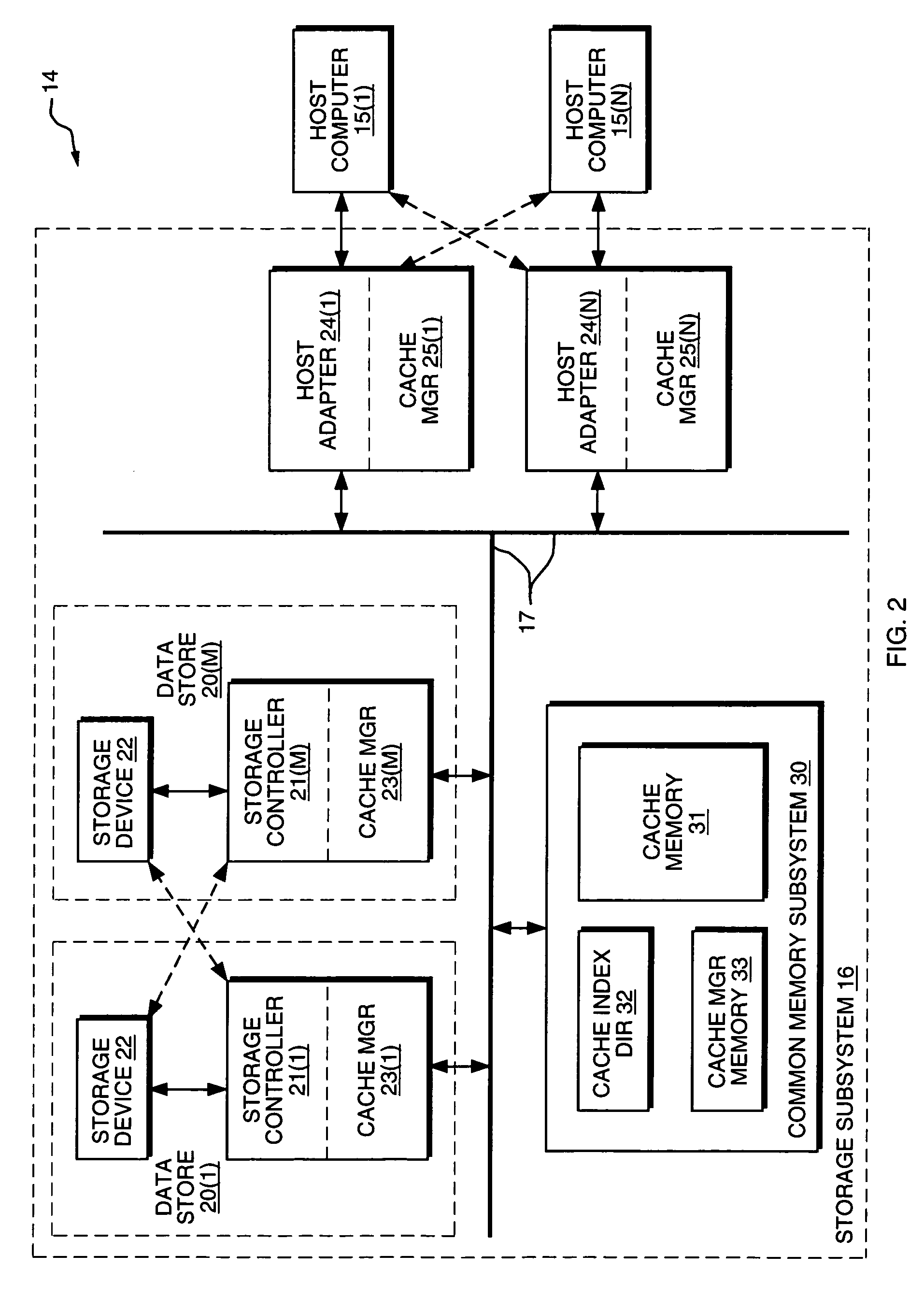
System and method for assessing the effectiveness of a cache memory or portion thereof using FIFO or LRU using cache utilization statistics
InactiveUS7139872B1Facilitates efficient determinationIncreasing and decreasing size of cacheMemory architecture accessing/allocationError detection/correctionParallel computingLeast recently frequently used
A system efficiently determines of the likely effectiveness of the cache memory for various cache memory sizes, based on a prediction of the likely cache miss rate, the prediction being based on operational statistics which are gathered during actual use of the cache memory over one or more time periods, and based on a variety of cache management methodologies. Based on the prediction, the operator or the system can facilitate increasing or decreasing the size of the cache memory, or maintaining the cache memory at its then-current size. The system determines the cache memory's read miss rate from statistics that are collected during use of the cache memory over an arbitrary time interval, including statistics concerning the file information retrieval activity and the extent of activity per unit time for system. Based on the statistics, equations, which are based on the respective cache memory management methodology, including the FIFO (first-in / first-out) methodology or the LRU (least-recently used) methodology, used in managing the cache memory, are solved to generate a prediction of the cache miss rate for a particular cache memory size, which may be larger or smaller than the current cache memory size, and for the particular cache memory management methodology. The system can repeat this a number of times over respective time intervals to determine corresponding predictions based on the cache memory utilization for respective sets of statistics determined during each time interval. Thereafter, the system or an operator can effect a change in the cache memory size based on the cache miss rate predictions.
Owner:EMC CORP
Method and system for cache eviction
InactiveUS7457920B1Memory architecture accessing/allocationMemory systemsParallel computingMiss rate
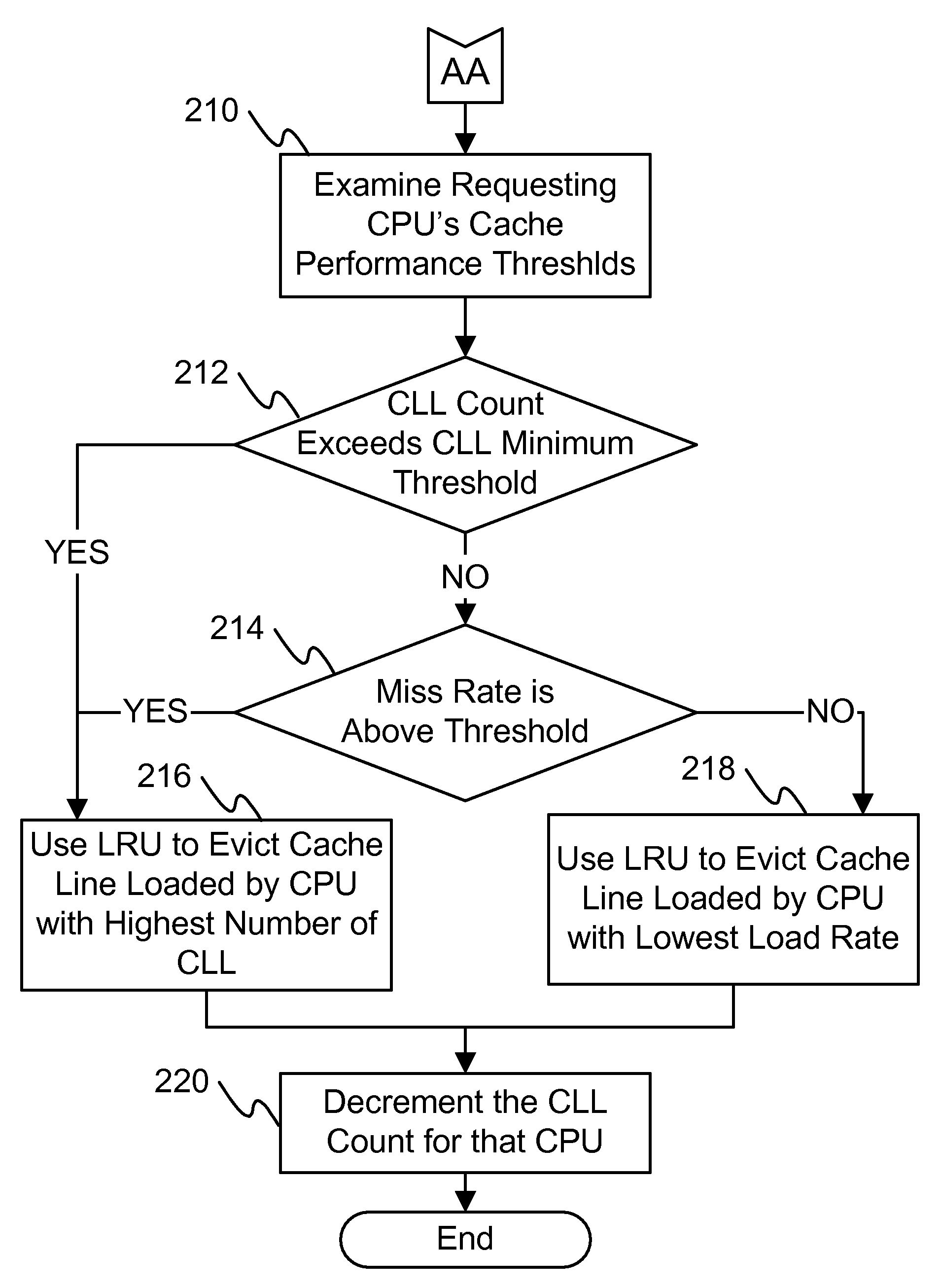
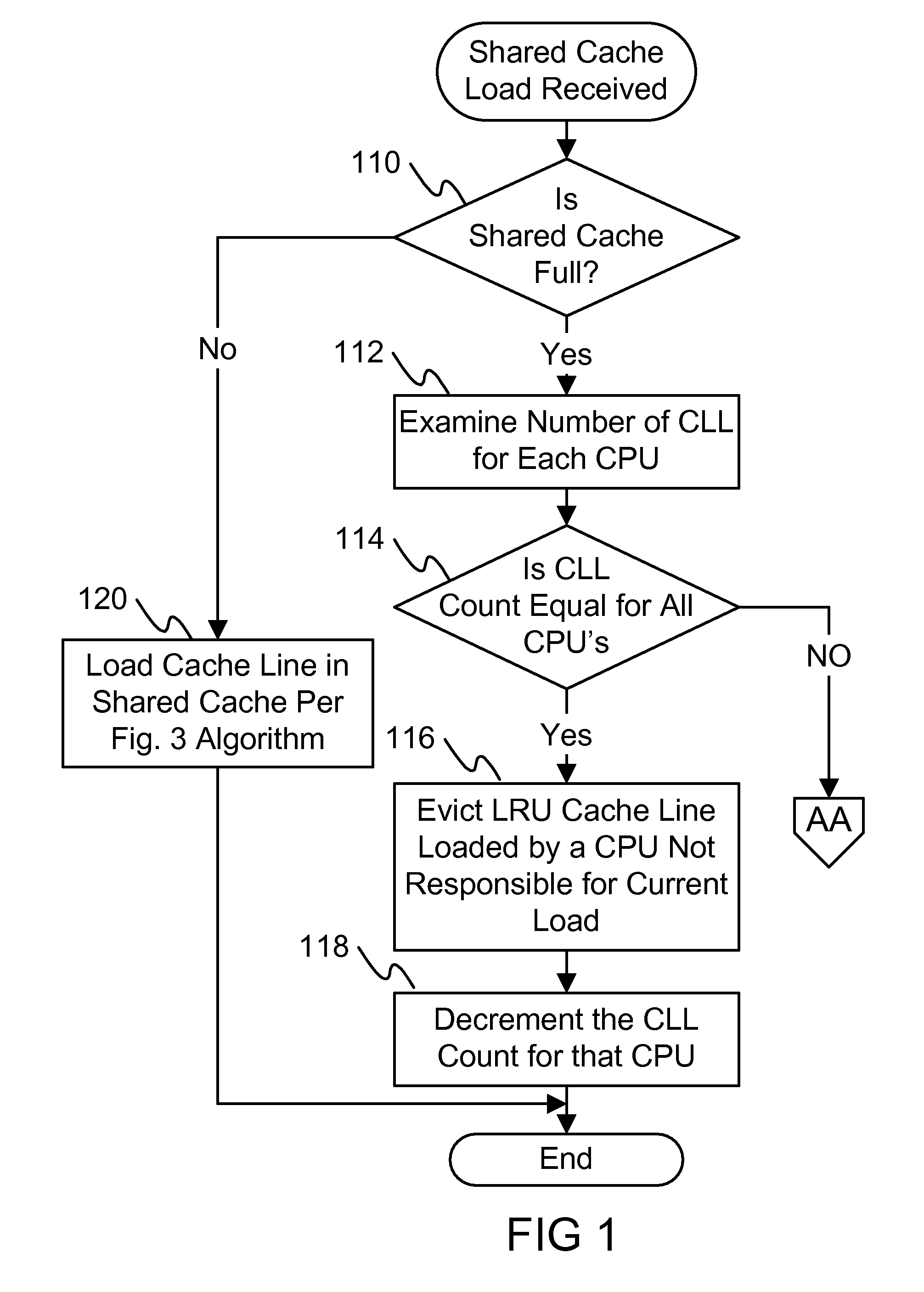
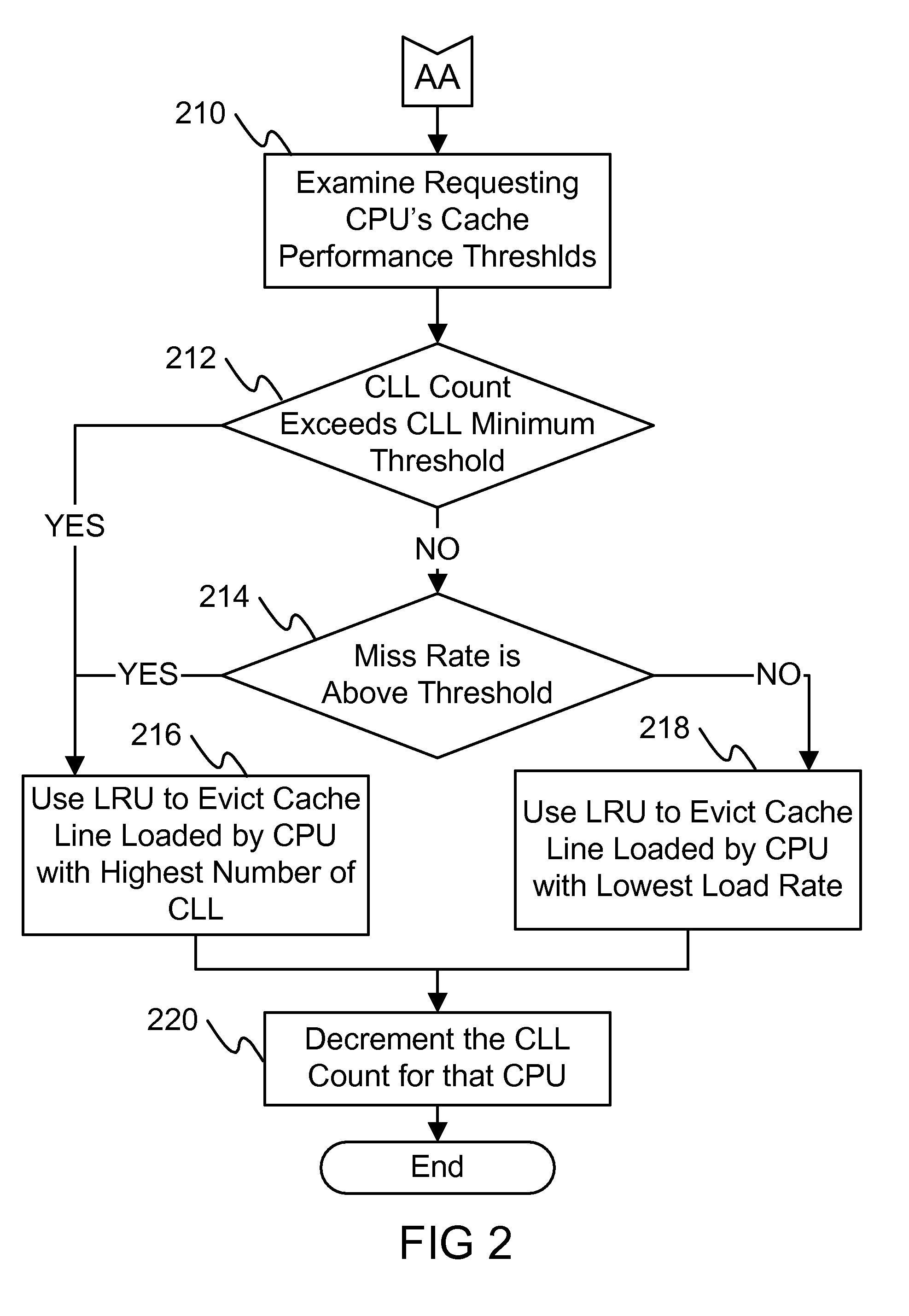
The proposed system and associated algorithm when implemented improves the processor cache miss rates and overall cache efficiency in multi-core environments in which multiple CPU's share a single cache structure (as an example). The cache efficiency will be improved by tracking CPU core loading patterns such as miss rate and minimum cache line load threshold levels. Using this information along with existing cache eviction method such as LRU, results in determining which cache line from which CPU is evicted from the shared cache when a capacity conflict arises. This methodology allows one to dynamically allocate shared cache entries to each core within the socket based on the particular core's frequency of shared cache usage.
Owner:IBM CORP
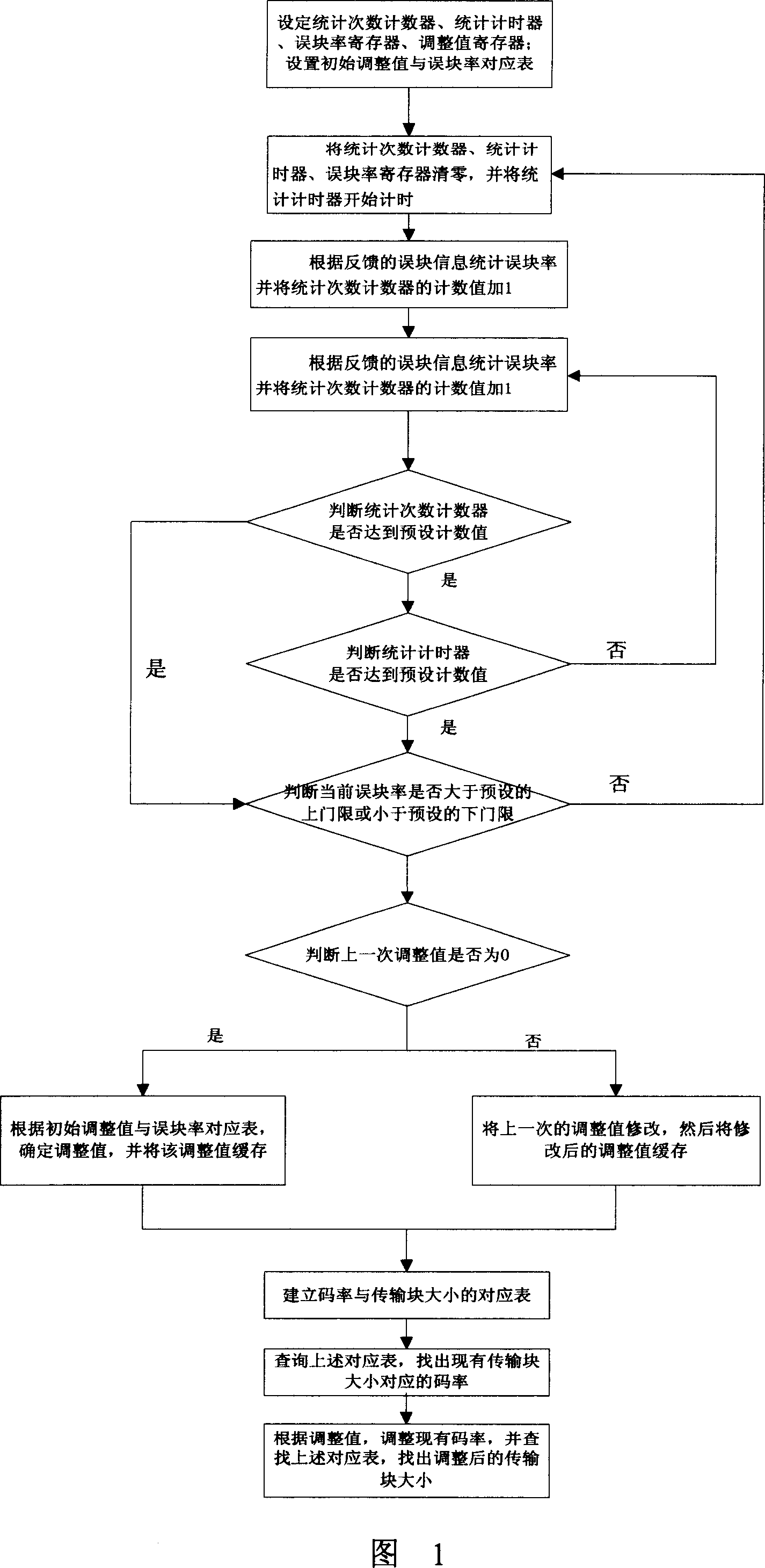
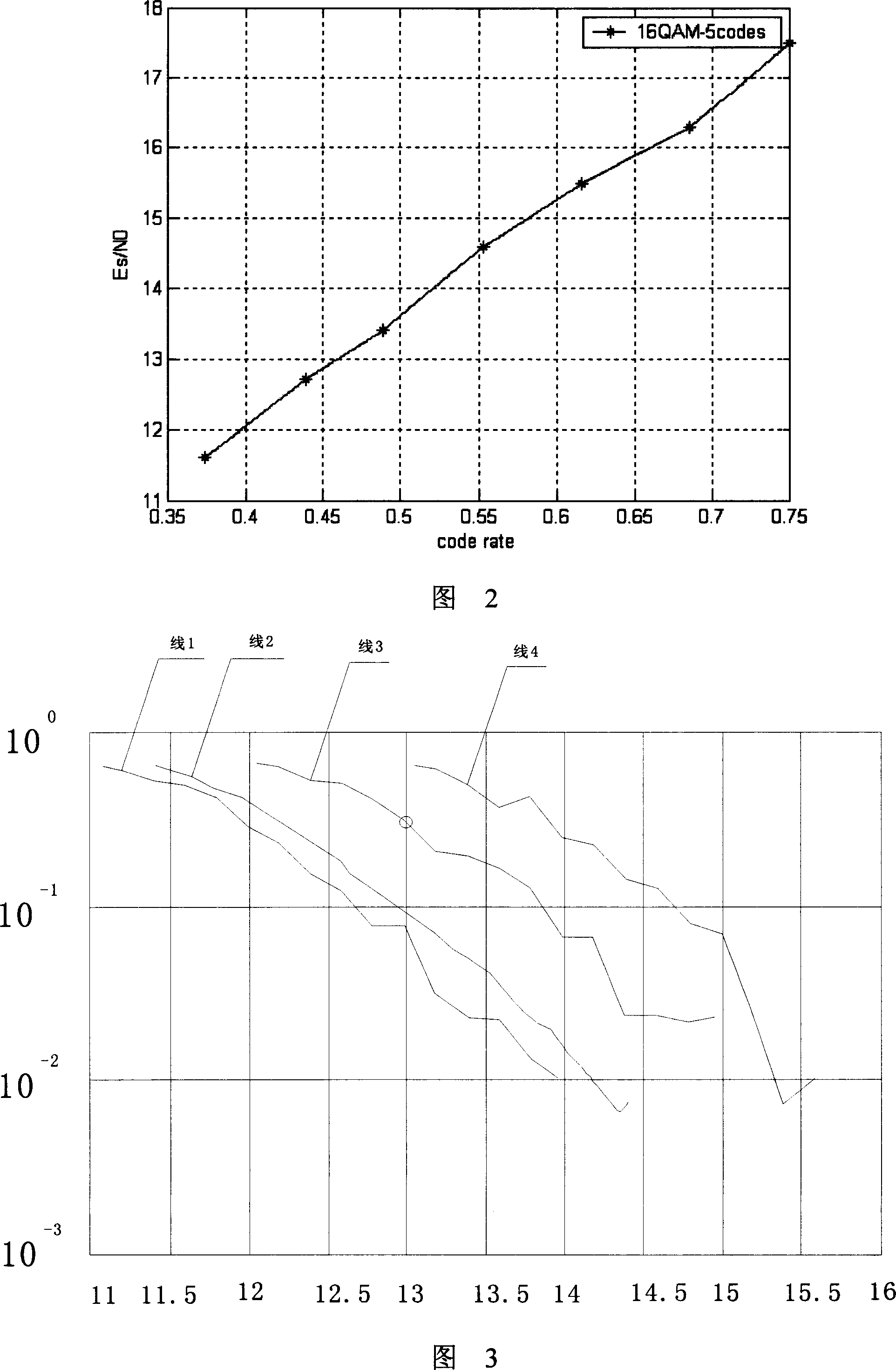
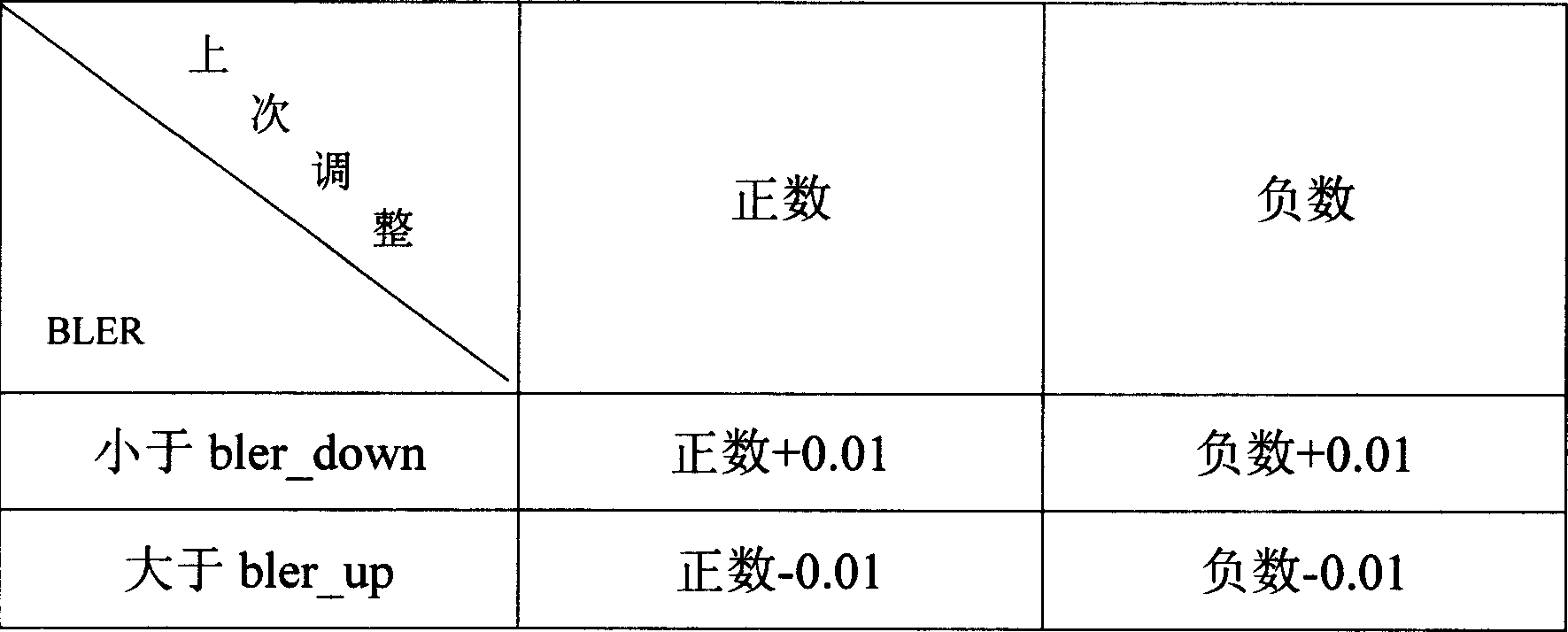
Method for controlling block error ratio in mobile communication system
InactiveCN101094164AAvoid influenceImprove throughputError preventionData switching networksFrequency counterMobile communication systems
The invention is used for solving the issue that is the currently-used technology can't control the block-missing rate so as to cause low throughout. It comprises: setting up a corresponding table between the initial adjustment value and the block-missing rate, and calculating the block-missing rate at unit time and at a certain times; if the block-missing rate is more than an upper threshold and less than a threshold, then according to the block-missing rate, the code rate is adjusted. By setting up a frequency counter and a timer, the invention ensures the accuracy and real-time statistic of block-missing rate. The invention is mainly used in high speed downlink packet access (HSDPA) system.
Owner:ZTE CORP
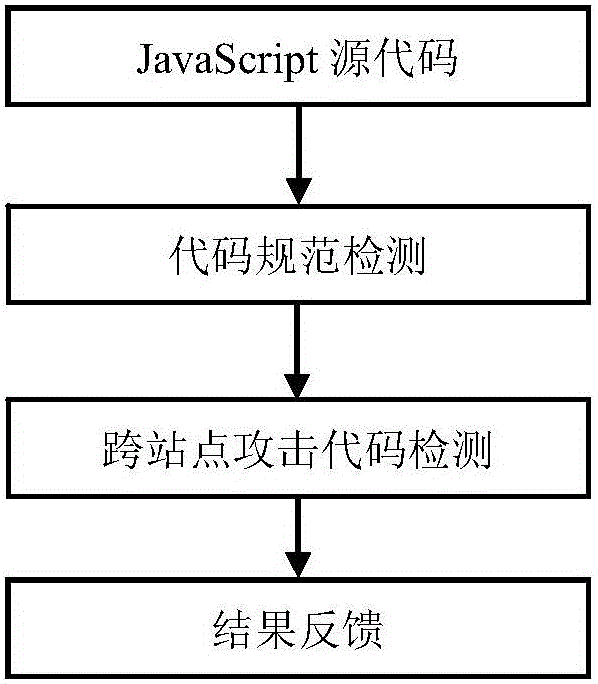
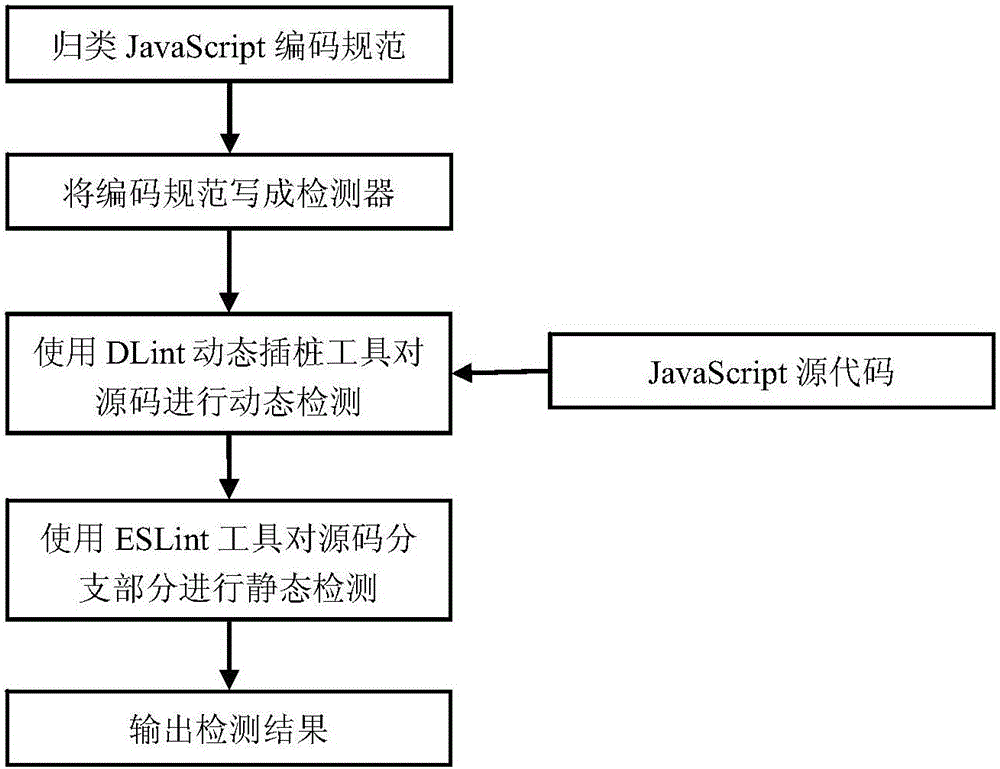
Rule-based JavaScript security testing method
ActiveCN106055980AReduce missed detection rateImprove efficiency in detecting security issuesPlatform integrity maintainanceWeb siteDynamic instrumentation
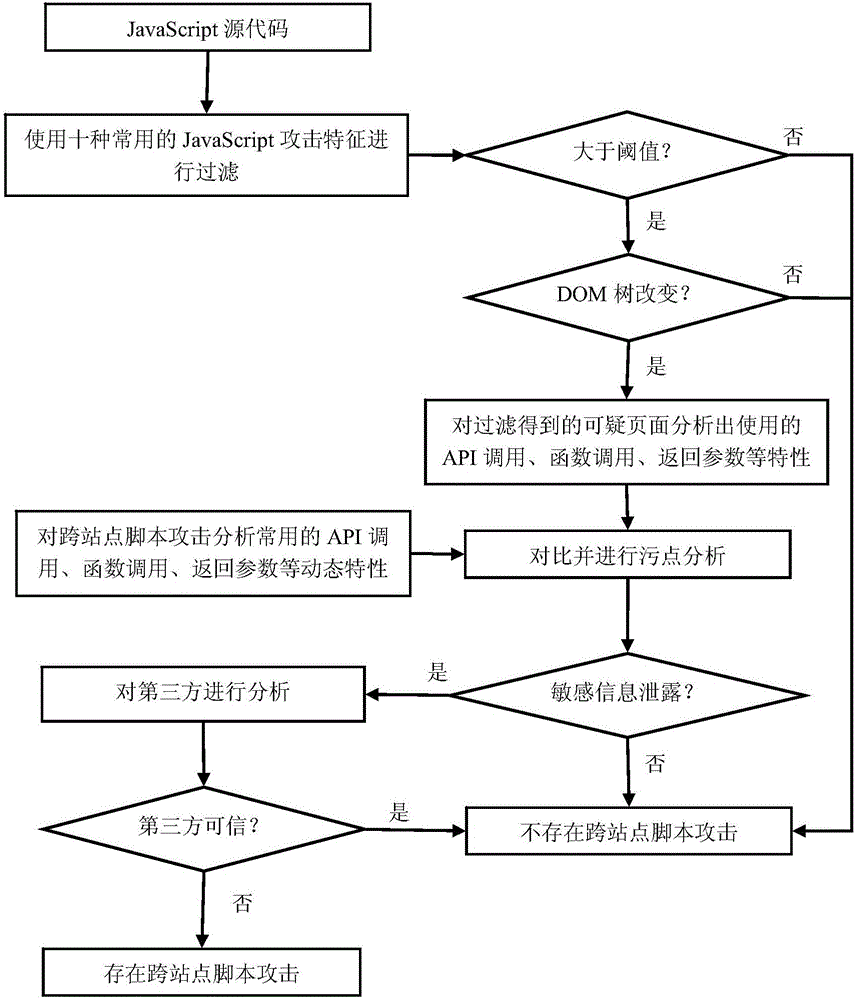
The invention discloses a rule-based JavaScript security testing method. A program analysis method in which static analysis and dynamic analysis are combined is utilized for testing the security problem of a JavaScript code in a website and performing feedback, thereby finding out the security problems which comprise JavaScript coding standardization un-qualification and over-site script attack malicious codes. The method comprises the steps of dynamically finding out a JavaScript coding standardization un-qualification problem by means of a DLint tool, then testing the branched parts of a source code by means of an open-source static code standardization testing tool ESLint; then filtering a page which may contain over-site script attack malicious codes in the source code according to JavaScript page characteristics and a preset threshold according to a static analysis method; and then performing dynamic Instrumentation on the filtered page for performing strain analysis by means of a Jalangi frame, thereby determining whether the filtered page contains an over-site script attack. The rule-based JavaScript security testing method effectively improves testing efficiency for code standardization and malicious codes based on miss rate reduction.
Owner:NANJING UNIV OF POSTS & TELECOMM
Method and system for intelligent and dynamic cache replacement management based on efficient use of cache for individual processor core
InactiveUS20090157970A1Memory architecture accessing/allocationMemory adressing/allocation/relocationParallel computingHandling system
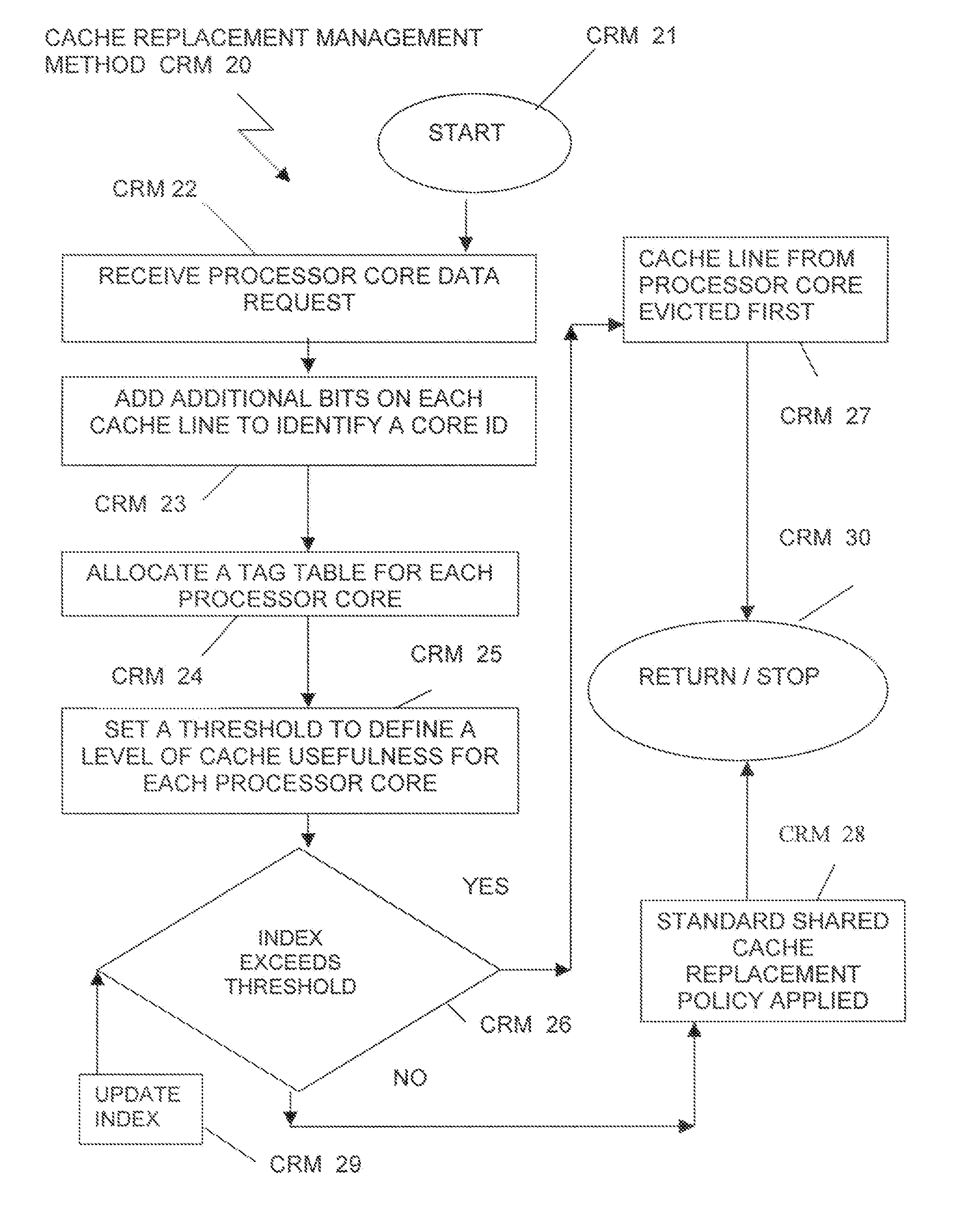
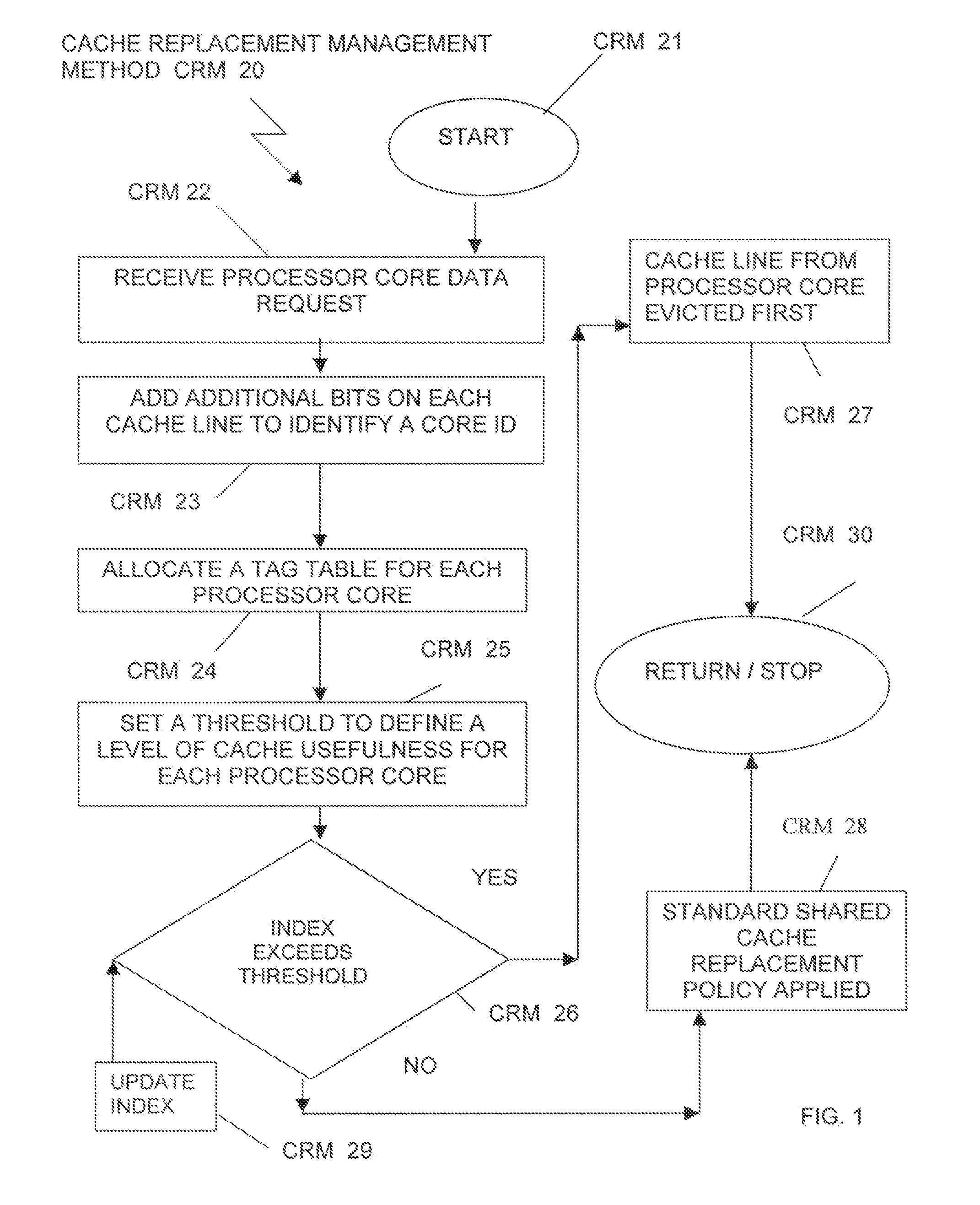
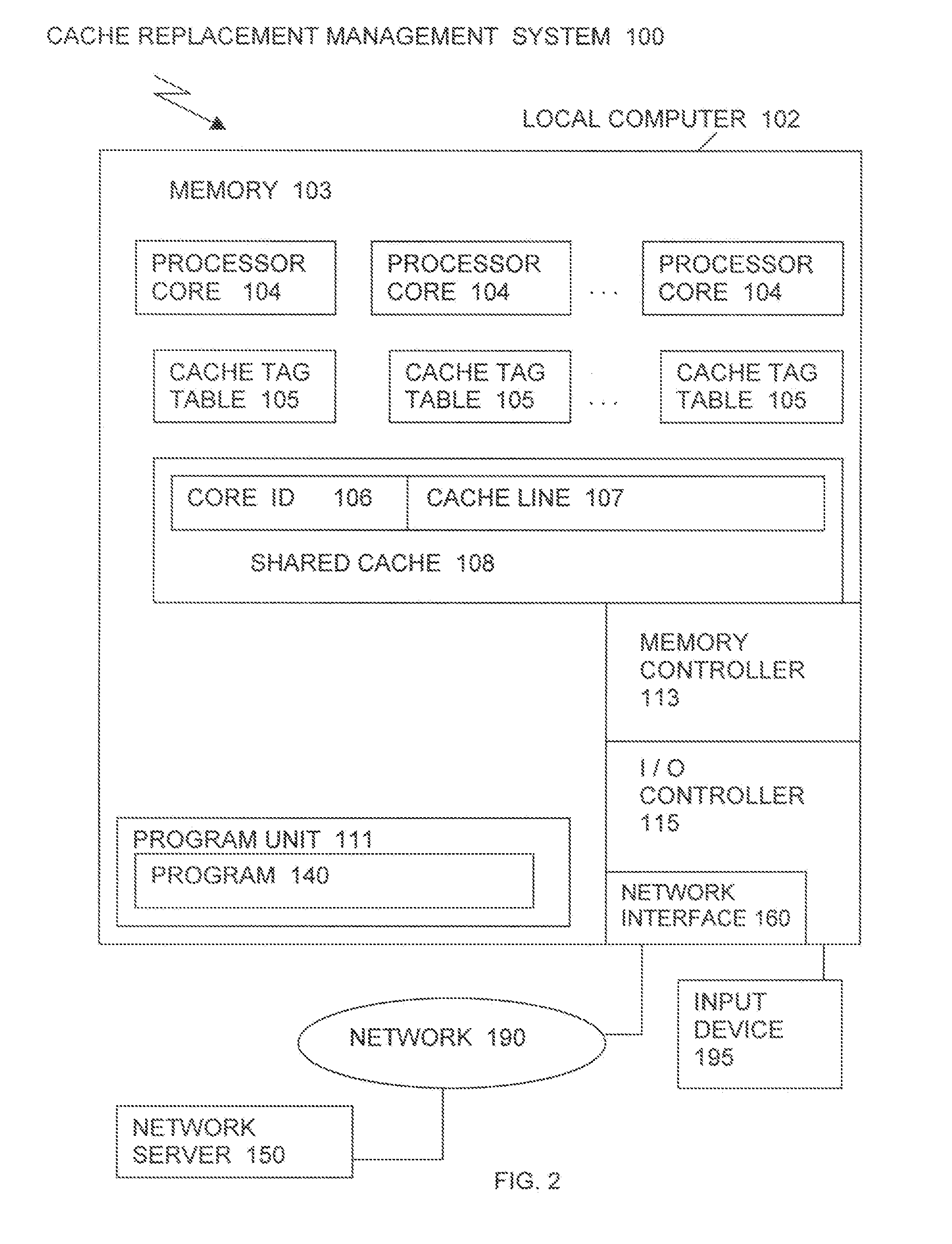
Determining and applying a cache replacement policy for a computer application running in a computer processing system is accomplished by receiving a processor core data request, adding bits on each cache line of a plurality of cache lines to identify a core ID of an at least one processor core that provides each cache line in a shared cache, allocating a tag table for each processor core, where the tag table keeps track of an index of processor core miss rates, and setting a threshold to define a level of cache usefulness, depending on whether or not the index of processor core miss rates exceeds the threshold. Checking the threshold and when the threshold is not exceeded, then a shared cache standard policy for cache replacement is applied. When the threshold is exceeded, then the cache line from the processor core running the application is evicted from the shared cache.
Owner:IBM CORP
Adaptive boundary abnormity detection method based on multistage strategies
The invention relates to an adaptive boundary abnormity detection method based on multistage strategies. The method comprises steps that, a peak value and a valley value of a network flow at each time segment in a normal operation state are taken as acquisition bases, log information and network flow data of equipment are acquired; according to the message type of the network flow data, a datum line of the network flow data in the normal index operation state is established, and whether the network flow data is abnormal is determined; the abnormal network flow data and the log information corresponding to the abnormal network flow data are stored by employing an HASH algorithm; a normal network behavior database and an abnormal network behavior database are established, and matching for the abnormal network flow data is carried out; the network flow data which can not be matched is analyzed by employing a BP nerve network method, and network behaviors of the network flow data are determined and are stored to the corresponding behavior database. Through the method, a step-by-step progressive discrimination mode is employed to realize detection on abnormal boundary behaviors, and thereby the error reporting rate and the report missing rate of abnormality detection are reduced.
Owner:GLOBAL ENERGY INTERCONNECTION RES INST CO LTD +2
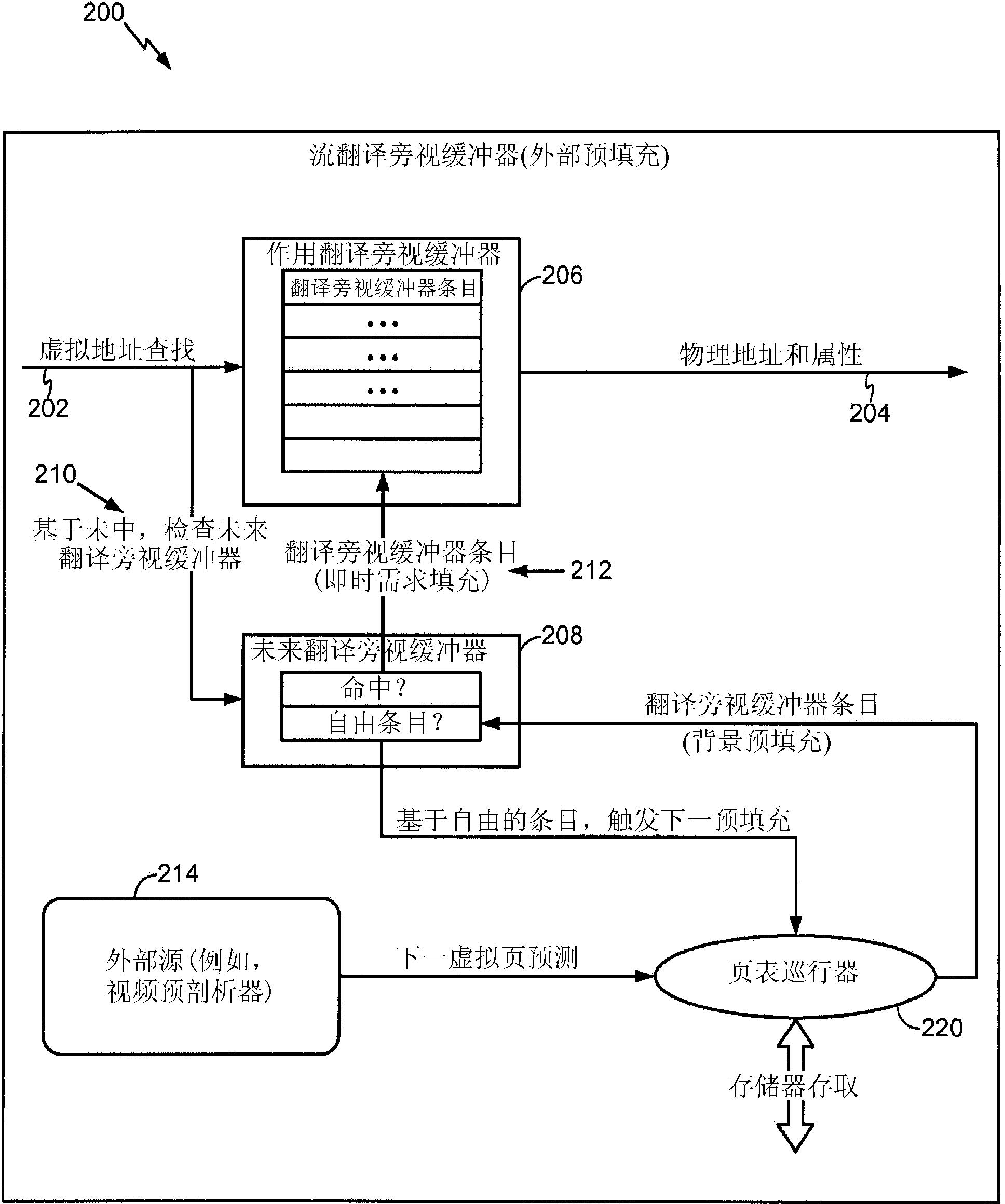
Memory management unit with pre-filling capability
InactiveCN103443777AMemory architecture accessing/allocationMemory adressing/allocation/relocationManagement unitCritical path method
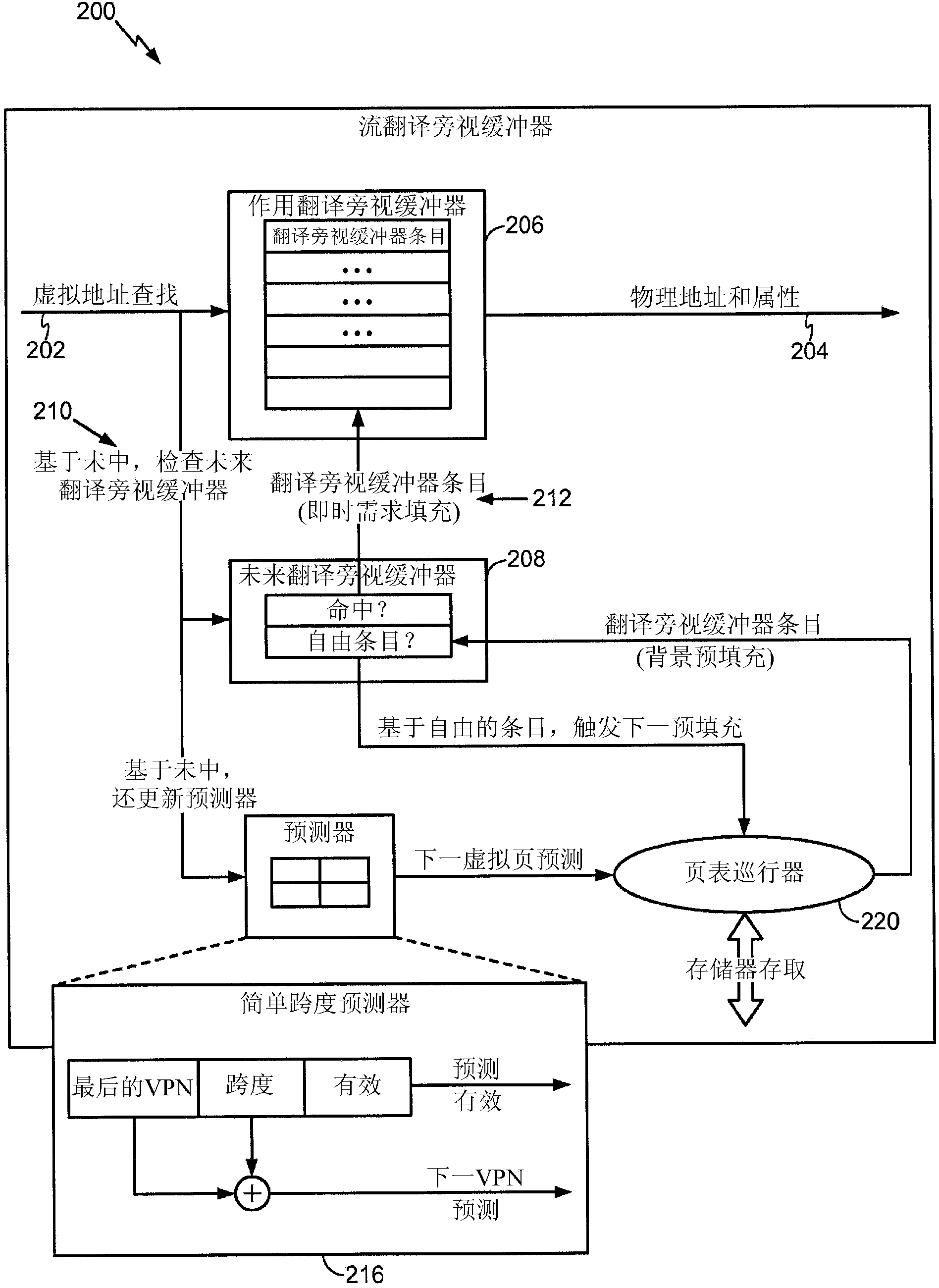
Systems and method for memory management units (MMUs) configured to automatically pre-fill a translation lookaside buffer (TLB) (206, 208) with address translation (202-204) entries expected to be used in the future, thereby reducing TLB miss rate and improving performance. The TLB may be pre-filled with translation entries, wherein addresses corresponding to the pre-fill may be selected based on predictions. Predictions may be derived from external devices (214), or based on stride values, wherein the stride values may be a predetermined constant or dynamically altered based on access patterns (216). Pre-filling the TLB may effectively remove latency involved in determining address translations for TLB misses from the critical path.
Owner:QUALCOMM INC
Method and apparatus for filtering prefetches to provide high prefetch accuracy using less hardware
InactiveUS20020129205A1Memory architecture accessing/allocationMemory adressing/allocation/relocationComputer hardwareMiss rate
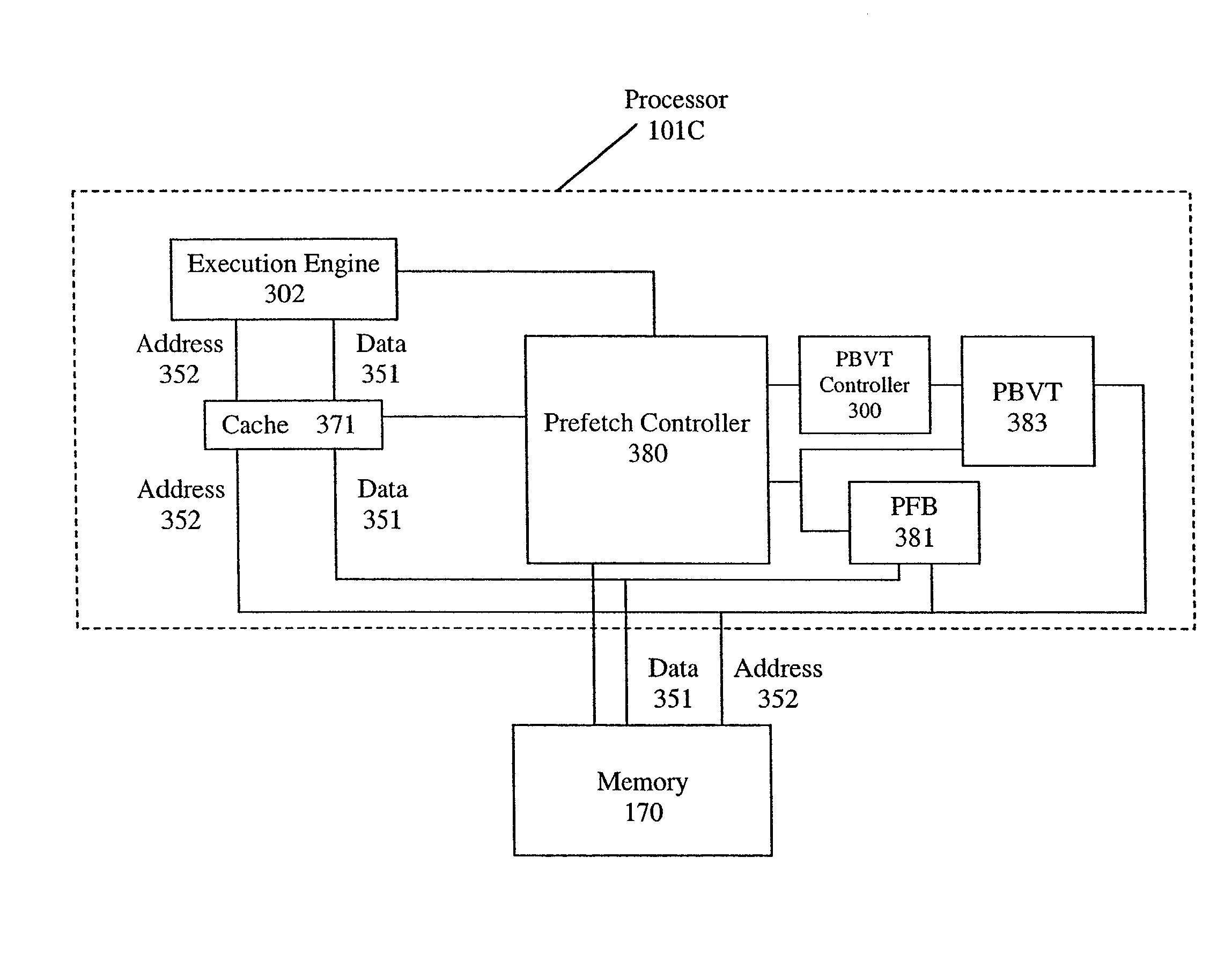
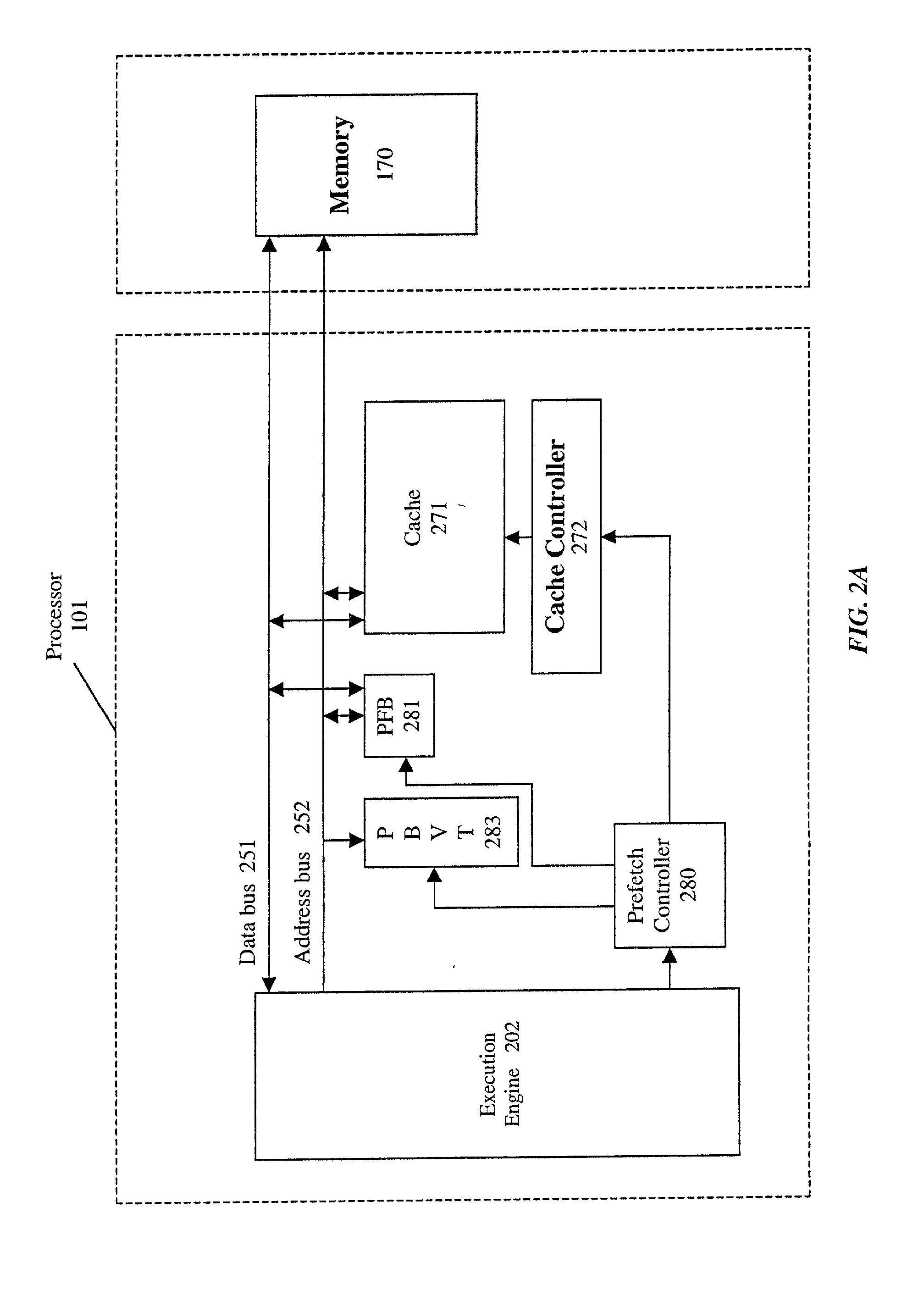
In general, the PBVT structure provides an effective method of filtering a stream of hardware generated prefetches by eliminating prefetch addresses that have proven to be inaccurate in the past. When compared to a design that uses a PFB of equal number of entries, the PBVT along with a small PFB provides virtually equivalent prefetch accuracy and miss rate reduction while using much less hardware area (97% less data storage space for a 1024-entry PFB case).
Owner:INTEL CORP
Method and apparatus for autonomic detection of cache "chase tail" conditions and storage of instructions/data in "chase tail" data structure
InactiveUS7181599B2Improve performanceMemory adressing/allocation/relocationDigital computer detailsData processing systemProcessing Instruction
Owner:INT BUSINESS MASCH CORP
Method and apparatus for achieving fair cache sharing on multi-threaded chip multiprocessors
ActiveUS8069444B2Memory adressing/allocation/relocationMultiprogramming arrangementsOperational systemMulti processor
In a computer system with a multi-core processor having a shared cache memory level, an operating system scheduler adjusts the CPU latency of a thread running on one of the cores to be equal to the fair CPU latency which that thread would experience when the cache memory was equally shared by adjusting the CPU time quantum of the thread. In particular, during a reconnaissance time period, the operating system scheduler gathers information regarding the threads via conventional hardware counters and uses an analytical model to estimate a fair cache miss rate that the thread would experience if the cache memory was equally shared. During a subsequent calibration period, the operating system scheduler computes the fair CPU latency using runtime statistics and the previously computed fair cache miss rate value to determine the fair CPI value.
Owner:ORACLE INT CORP
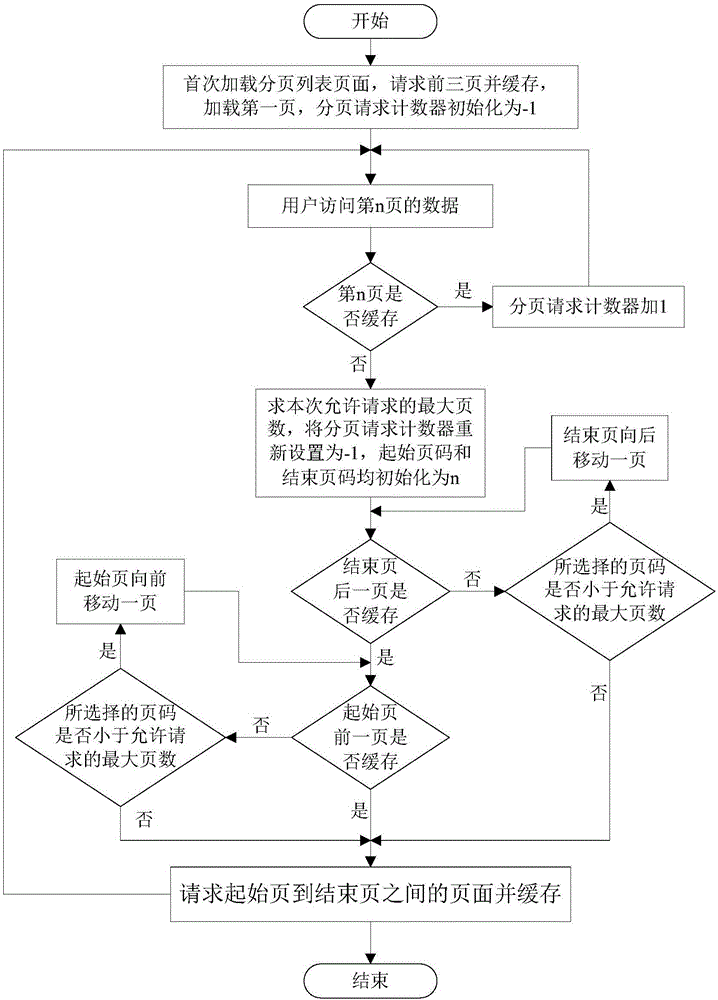
WEB caching method based on paging
ActiveCN106339508AReduce average rendering timeImprove experienceSpecial data processing applicationsArray data structureWeb cache
The invention discloses a WEB caching method based on paging. The WEB caching method comprises the steps that during initial loading, requesting the data of former three pages, then obtaining the allowably requested maximum page each by addition of the page requested last time and a counter, and after successful request each time, enabling the largest page number to be as the length of a current page data caching array; when loading a new page, taking the page number of the page as an index subscript, reading the page data caching array, and if the read data is empty, illustrating that the page is not cached, and requesting the page and the adjacent page which is not requested. According to the WEB method, only a small quantity of requests are sponsored to a server, the visit hit rate of caching data is increased, and the page missing rate is reduced, so that the average showing time of a webpage is shortened, and further the user experience is improved.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Filament tube capsule oesophagoscope capable of being released and magnetically controlled
InactiveCN103156568AOvercome timeOvercoming the high missed detection rateSurgeryEndoscopesEsophageal diseaseMedicine
The invention provides a filament tube capsule oesophagoscope capable of being released and magnetically controlled. The filament tube capsule oesophagoscope capable of being released and magnetic controlled comprises a needle cylinder, a filament tube, a vacuum sucking disc and a capsule endoscope. The filament tube capsule oesophagoscope capable of being released and magnetic controlled is characterized in that one end of the filament tube is connected with the needle cylinder, the other end of the filament tube is connected with the vacuum sucking disc, and the capsule endoscope is a micro-camera with magnetic dipoles. According to the filament tube capsule oesophagoscope capable of being released and magnetic controlled, the speed of the capsule endoscope passing through an esophagus is controlled through the filament tube and the vacuum sucking disc, viewing angles of the capsule endoscope can be controlled freely, and the defects that a common capsule endoscope is short in dwelling time in the esophagus, high in a missing rate, single in viewing angles and the like are overcome. The filament tube capsule oesophagoscope capable of being released and magnetic controlled is simple in structure, low in cost, convenient to use and capable of greatly improving a detectable rate of esophageal diseases after being popularized and used.
Owner:安翰科技(武汉)股份有限公司
Apparatus for mediating communication between controller and transponders of many moving objects and method for controlling the same
InactiveUS7239228B2Reduce error rateImprove performanceArrangements for variable traffic instructionsMemory record carrier reading problemsComputer scienceMiss rate
Disclosed are a communication mediation apparatus and a method for controlling the same for performing communication mediation while reducing a communication miss rate caused by collision of data. A performance of a moving object recognition system unavoidably varies with the number of moving objects to be recognized by a controller, and with a mediation parameter for use in a communication mediation algorithm. The apparatus / method dynamically varies a mediation parameter according to a difference in numbers of many moving objects, thus reducing a communication miss rate regardless of the difference (i.e., traffic volume variation) in numbers of the moving objects.
Owner:DIGITALSIS
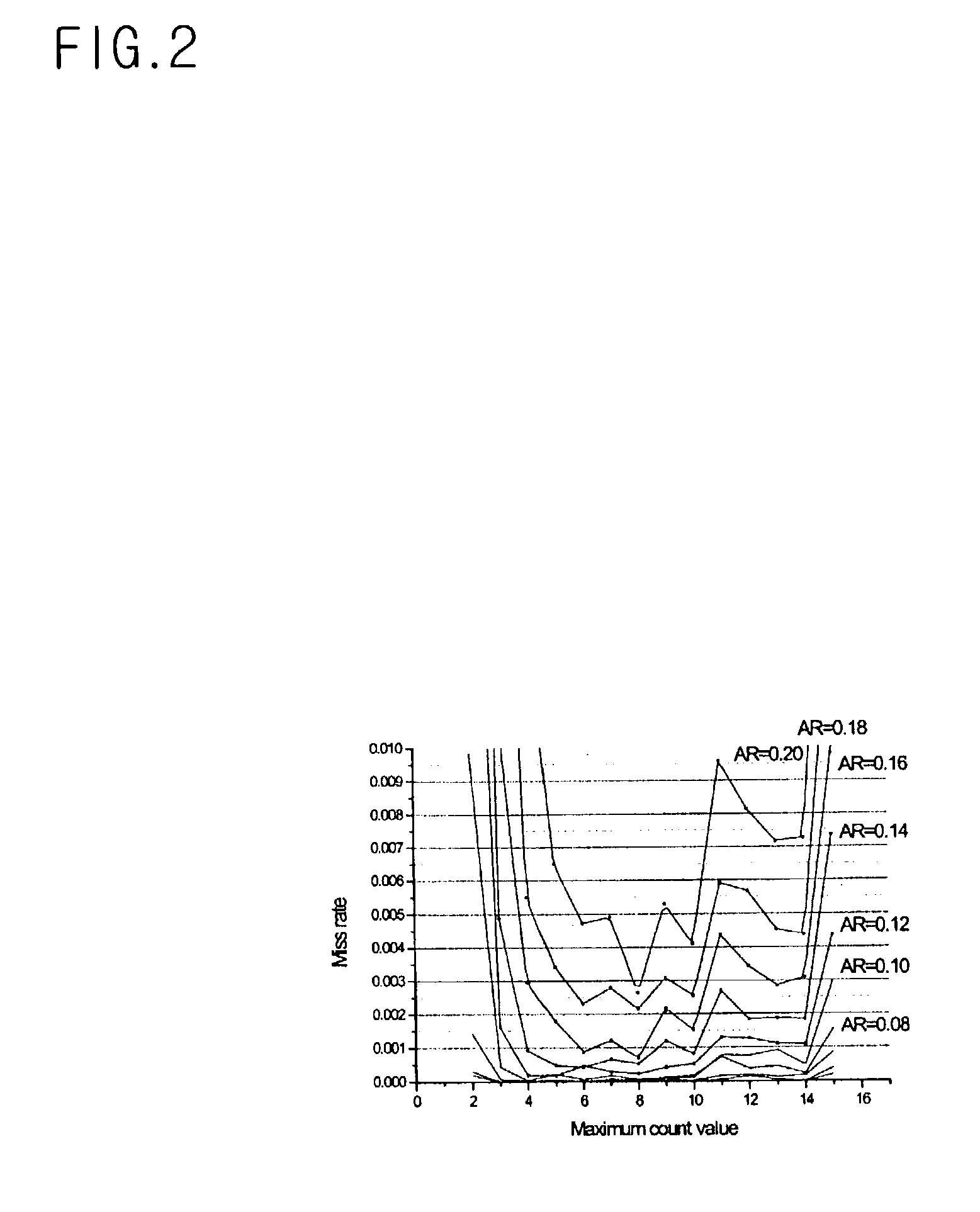
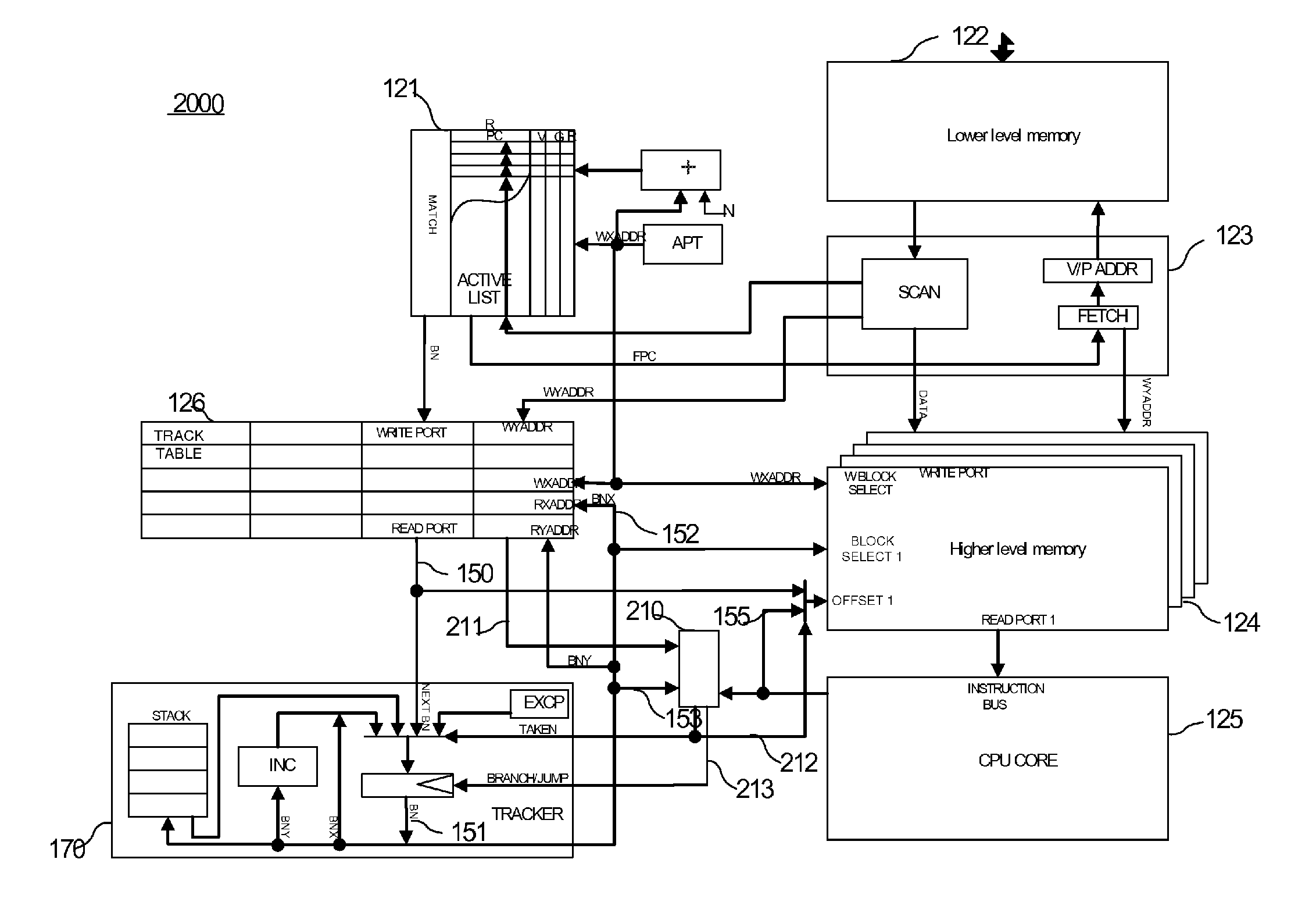
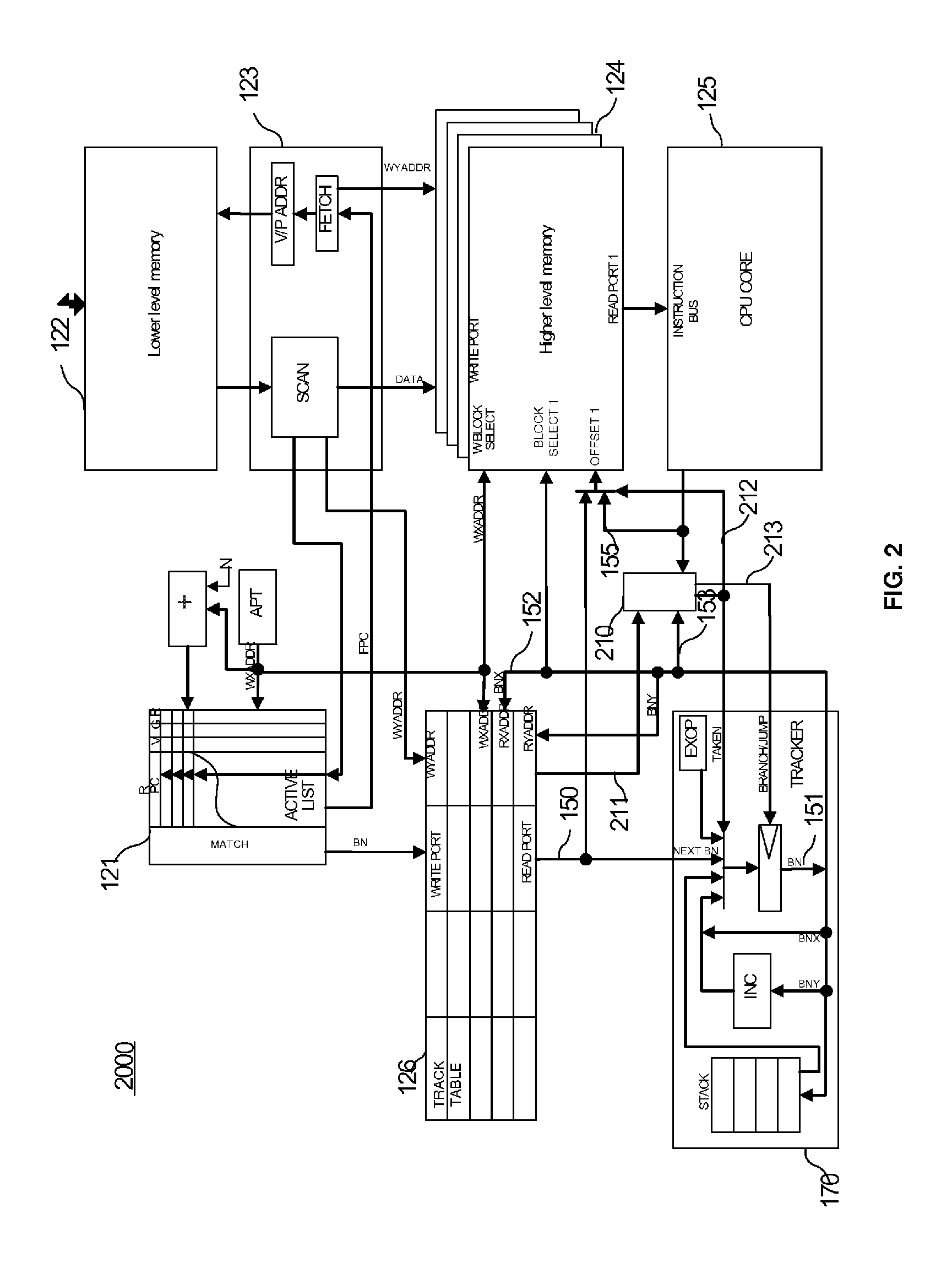
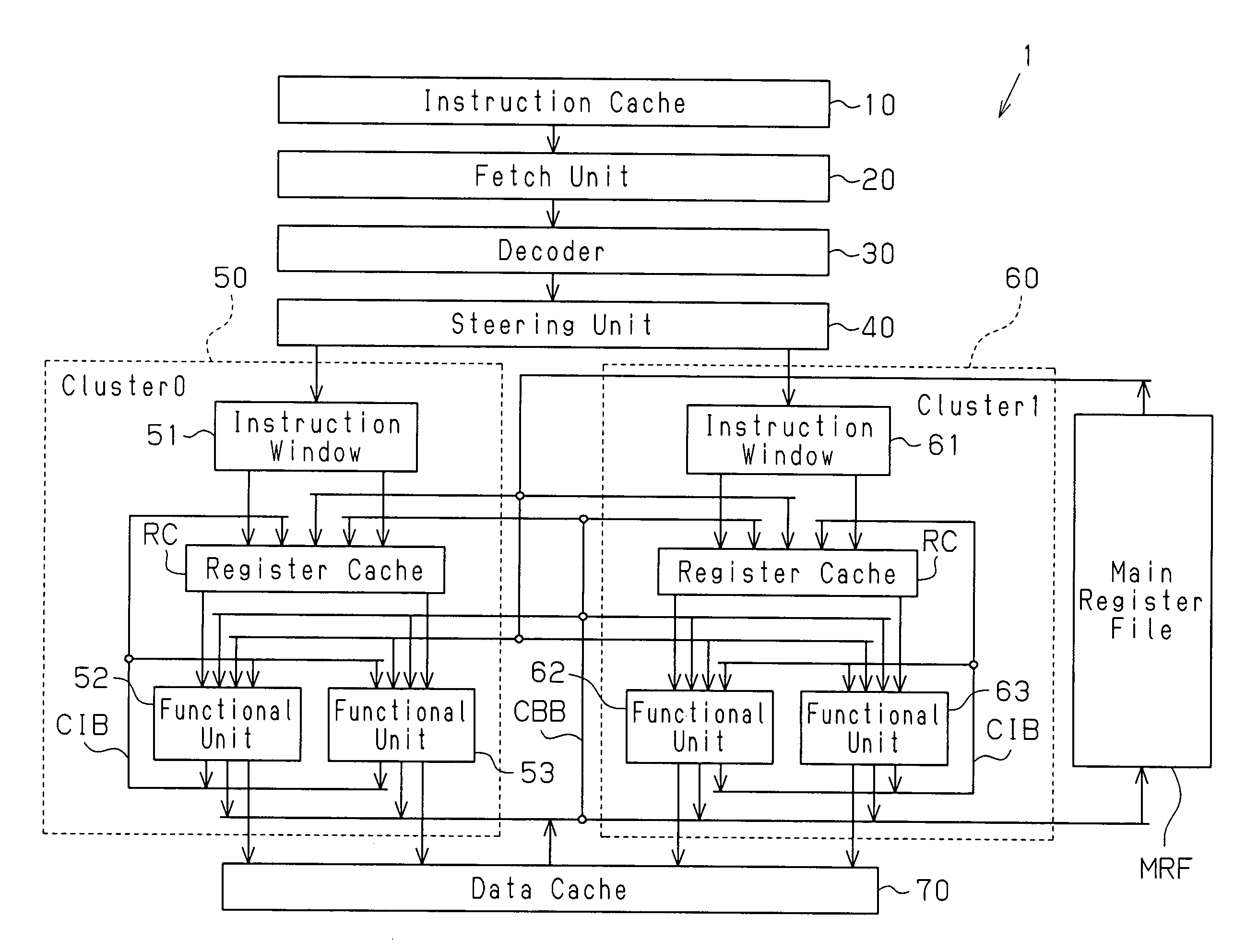
Low-miss-rate and low-miss-penalty cache system and method
ActiveUS20150193236A1Reduce processing stepsBroaden applicationMemory architecture accessing/allocationDigital computer detailsParallel computingMiss rate
A method for assisting operations of a processor core coupled to a first memory and a second memory includes: examining instructions being filled from the first memory to the second memory to extract instruction information containing at least branch information of the instructions, and creating a plurality of tracks based on the extracted instruction information. Further, the method includes filling one or more instructions from the first memory to the second memory based on one or more tracks from the plurality of tracks before the processor core starts executing the instructions, such that the processor core fetches the instructions from the second memory for execution. Filling the instructions further includes pre-fetching from the first memory to the second memory instruction segments containing the instructions corresponding to at least two levels of branch target instructions based on the one or more tracks.
Owner:SHANGHAI XINHAO MICROELECTRONICS
Animal viral vaccine pulsatile release system, and preparation method and application thereof
The invention relates to the field of biomedical engineering, and specifically relates to an animal viral vaccine pulsatile release system, a preparation method thereof, and an application thereof in animal disease prevention. According to the invention, a vaccine pulsatile release system composed of polymer microspheres comprising vaccine antigens and with different release characteristics and compositions of the microspheres; injection medication is adopted; and full immunization is realized with single dose injection. Therefore, immunization process is simplified, immunization effect is improved, labor intensity is reduced, and immunization missing rate is reduced.
Owner:HAINAN UNIVERSITY
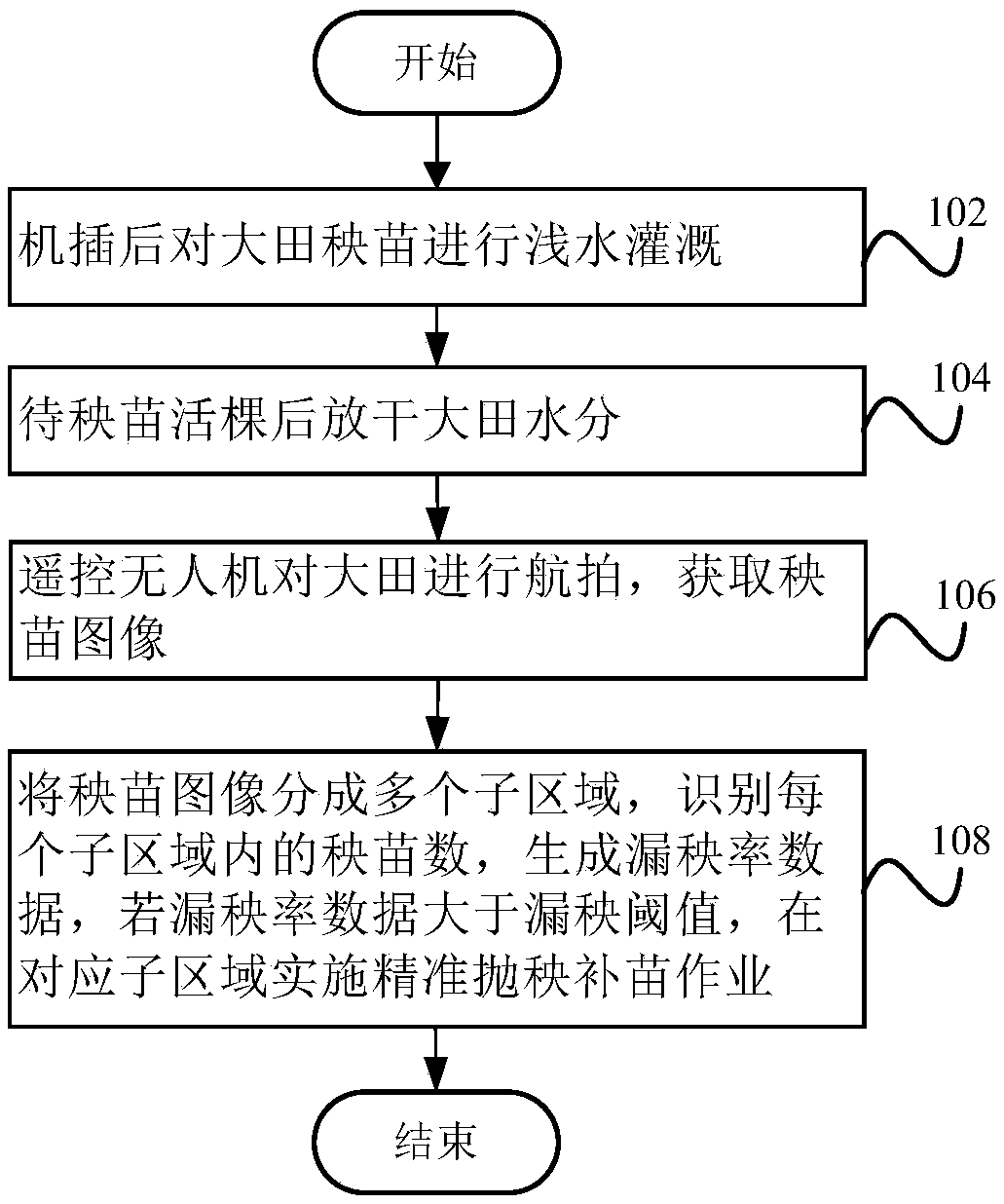
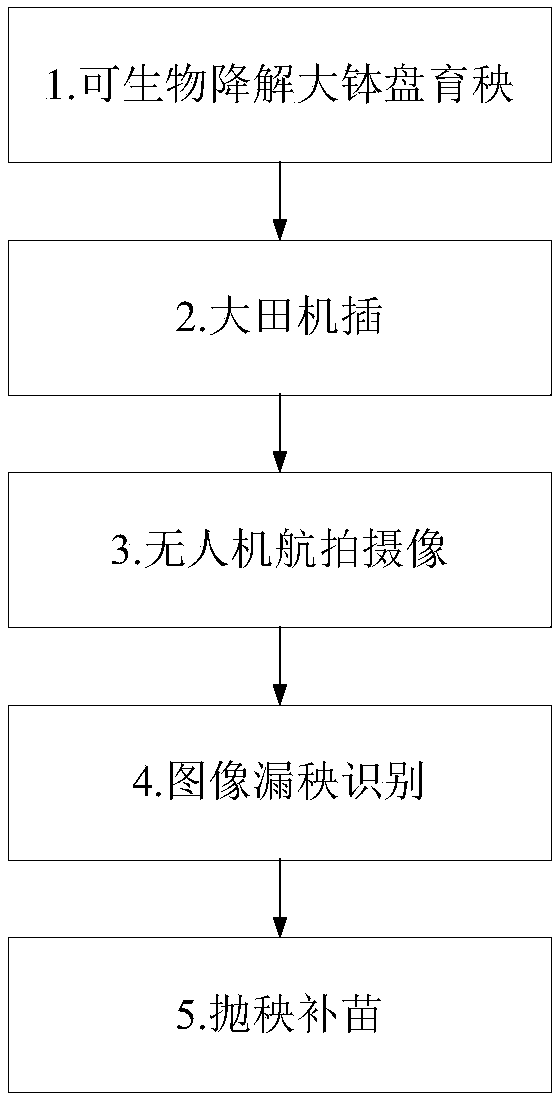
Machine transplanted seedling missing identification and gap-filling method
InactiveCN109275395ABalanced fertilizationAchieving Balanced High YieldTransplantingAerial photographyWater irrigation
The invention provides a machine transplanted seedling missing identification and gap-filling method, and belongs to the technical field of agricultural production. The machine transplanted seedling missing identification and gap-filling method includes the following steps: performing shallow water irrigation on field seedlings after machine transplanting; draining water in a field after the seedlings are alive; remotely controlling an unmanned aerial vehicle to perform aerial photography on the field to obtain a seedling image; and dividing the seedling image into multiple sub-regions, identifying numbers of the seedlings in the sub-regions, generating seedling missing rate data, and performing precise seedling throwing gap-filling operation in the corresponding sub-regions if the seedling missing rate data is greater than a seedling missing threshold. The machine transplanted seedling missing identification and gap-filling method overcomes the problems that conventional manual seedling transplanting gap-filling is labor-consuming, time-consuming, high in seedling gap-filling cost, not ideal in seedling gap-filling effect and the like, and is beneficial to population optimizationand fertilization balance to realize balanced and high yield of hybrid rice in different areas.
Owner:江苏年豊现代农业科技有限公司
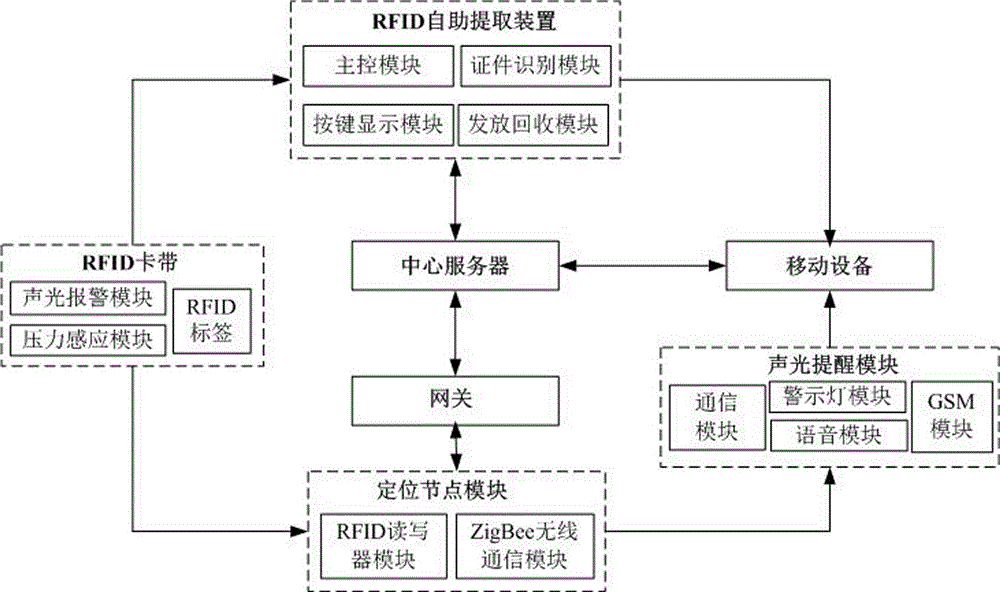
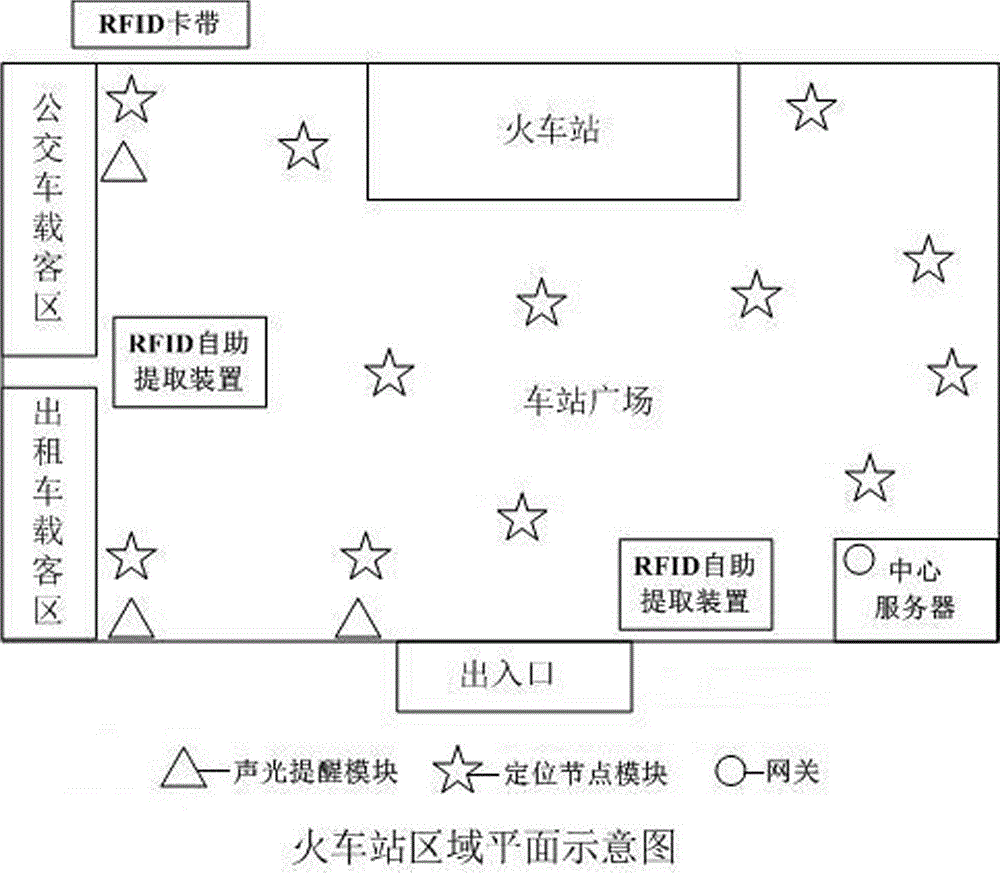
Complex environment personnel missing prevention system
The invention discloses a complex environment personnel missing prevention system. The complex environment personnel missing prevention system comprises a hand-held device, a gateway, a central server, an RFID card belt, an RFID card belt self-service extraction device, a positioning node module and anc. The RFID card belt is a wristband device worn on a wrist and is internally provided with an RFID label, a pressure sensing module and an acousto-optic alarm module. The RFID card belt self-service extraction device comprises a certificate identification module, an issuing and recovery module, a button display module and a main control module. The positioning node module comprises an RFID reader-writer module and a ZigBee wireless communication module. The positioning node module comprises a voice module, a GSM module, an alarm lamp module and a communication module and is placed at an entrance of a safe area. By adopting the system, positioning obstacles and difficulties under a complex environment are effectively avoided, the usage is convenient and rapid, a large number of manual and material resources are saved, and the missing rate of children and old people under the complex environment is lowered.
Owner:ANQING NORMAL UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com