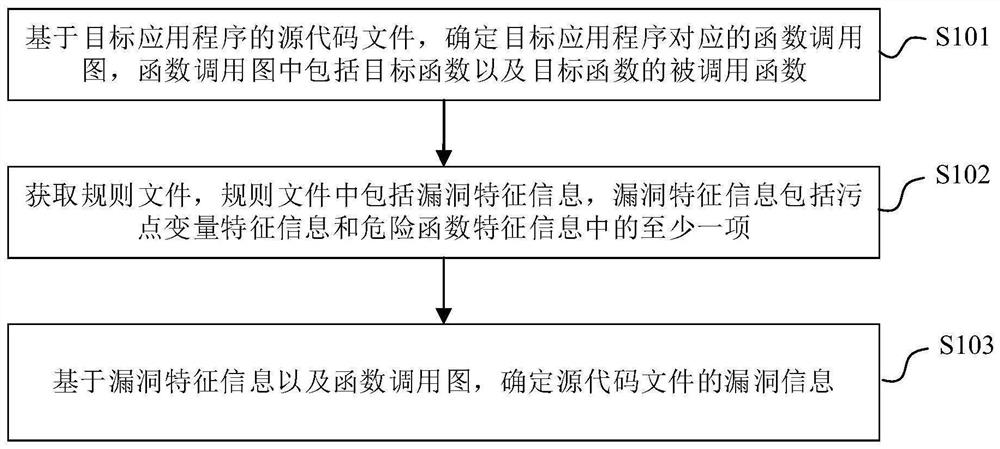
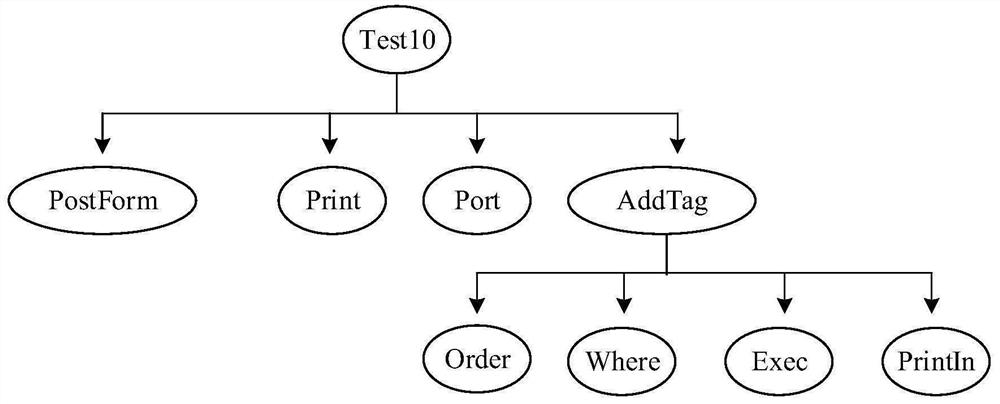
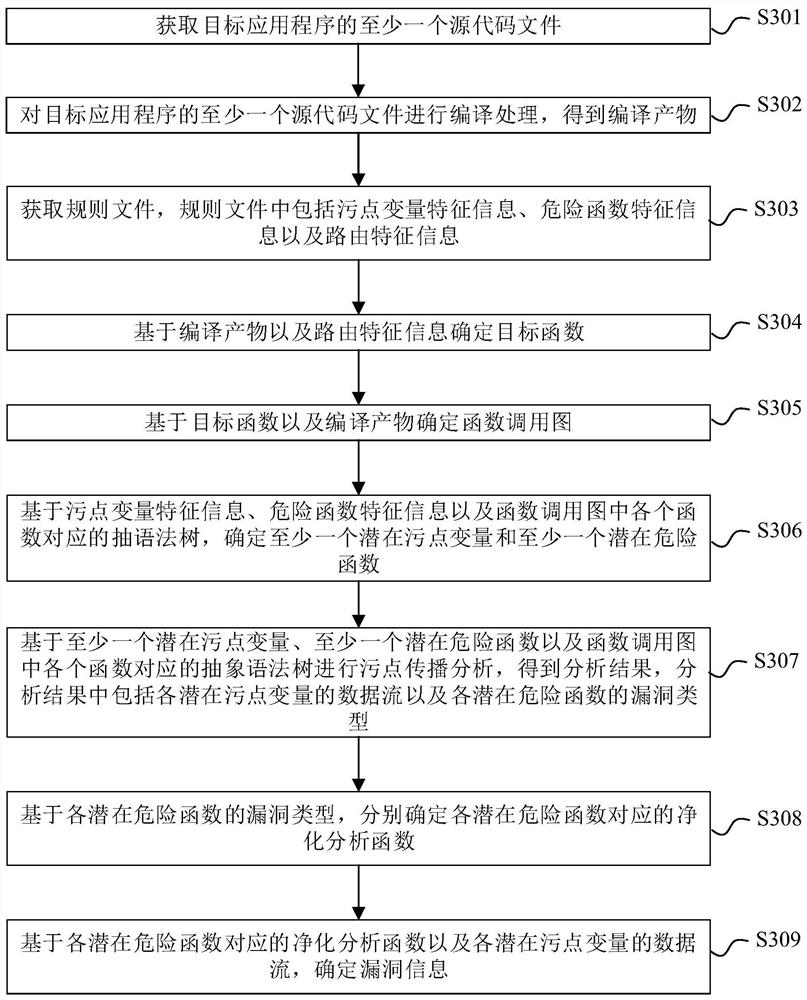
Code auditing method and device, electronic equipment and medium
A code auditing and source code technology, applied in the direction of code compilation, program code conversion, multi-programming device, etc., can solve the problems of reducing software development efficiency and high false alarm rate, reducing the consumption of human resources and time resources, reducing False positive rate and the effect of improving development efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific example
[0125] As a specific example, for the following code:
[0126] imageName:=c.Param("image")
[0127] image:="xxx"+imageName
[0128] exec. Command(" / bin / bash", "-c", image)
[0129] Among them, "imageName" is a potential taint variable, "exec.Command" is a potentially dangerous function, and the security processing result can be determined based on the purification analysis function corresponding to "exec.Command" and the data flow of "imageName", that is, "imageName" to Whether security processing is performed in the propagation path of "exec.Command".
[0130]Specifically, through the code "image:="xxx"+imageName", "imageName" is propagated to "image", and through the code "exec.Command(" / bin / bash", "-c", image)", So that "image" is propagated to "exec.Command", therefore, the security processing result is that security processing is not performed in the propagation path from "imageName" to "exec.Command", so "imageName" and "exec.Command" are determined is the vulnerabil...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com