A source code vulnerability detection method based on deep learning
A vulnerability detection and deep learning technology, which is applied in the field of source code vulnerability detection based on deep learning, can solve the problems of not being able to cover all execution paths of the program, the difficulty of solving the overhead, the high rate of false negatives and false negatives, etc., to reduce the Dependence, improve the detection effect, improve the effect of efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
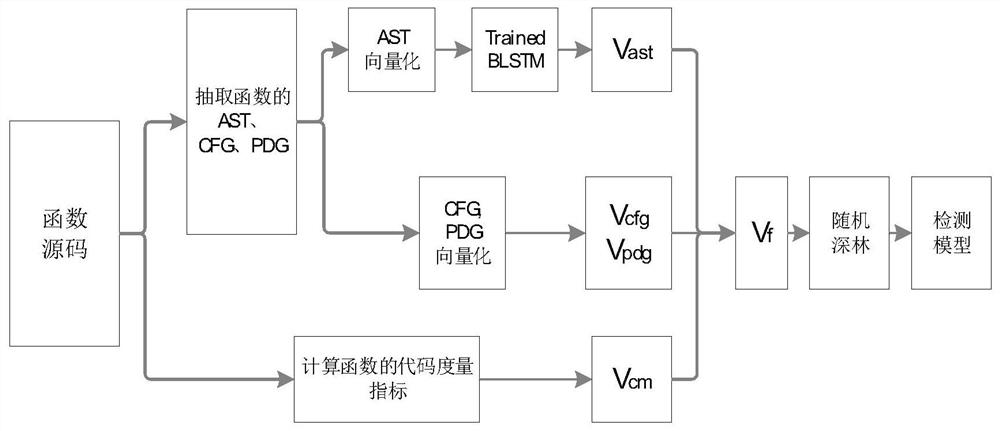
[0032] Please refer to figure 1 , a source code vulnerability detection method based on deep learning, comprising the following steps:
[0033] S1. Calculate the code metrics of the functions in the source code file and integrate them into a code metrics vector V cm ;
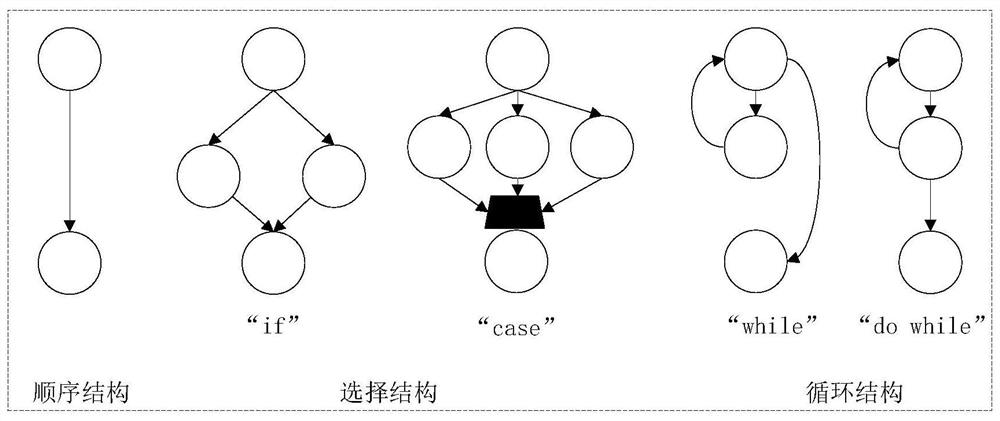
[0034] S2. Using the function in the source code as the basic unit, use the deep learning method to complete the automatic extraction of function features; extract the abstract syntax tree AST, control flow graph CFG, and program dependency graph PDG in the source code;
[0035] S21. Using a bidirectional long short-term memory network BLSTM to automatically extract features from the function AST;
[0036] S211. Perform a depth-first traversal operation on the AST, and store the signs in the AST in a sign vector in order;
[0037] S212. Use the set of symbols in all symbol vectors as a lexicon, perform word embedding on the symbols and convert the AST symbol vector into a numerical vector, and select an appr...
Embodiment 2
[0047] This embodiment is consistent with the content of Embodiment 1. The prerequisite for implementation is that there is an available large-scale software vulnerability database and the type of vulnerability and the location of the vulnerability in the source code can be clearly known from the vulnerability database. From this database, Collect source codes that contain a certain type of vulnerability and have the same programming language as a dataset.
[0048] A method for detecting source code vulnerabilities based on deep learning, comprising the following steps:
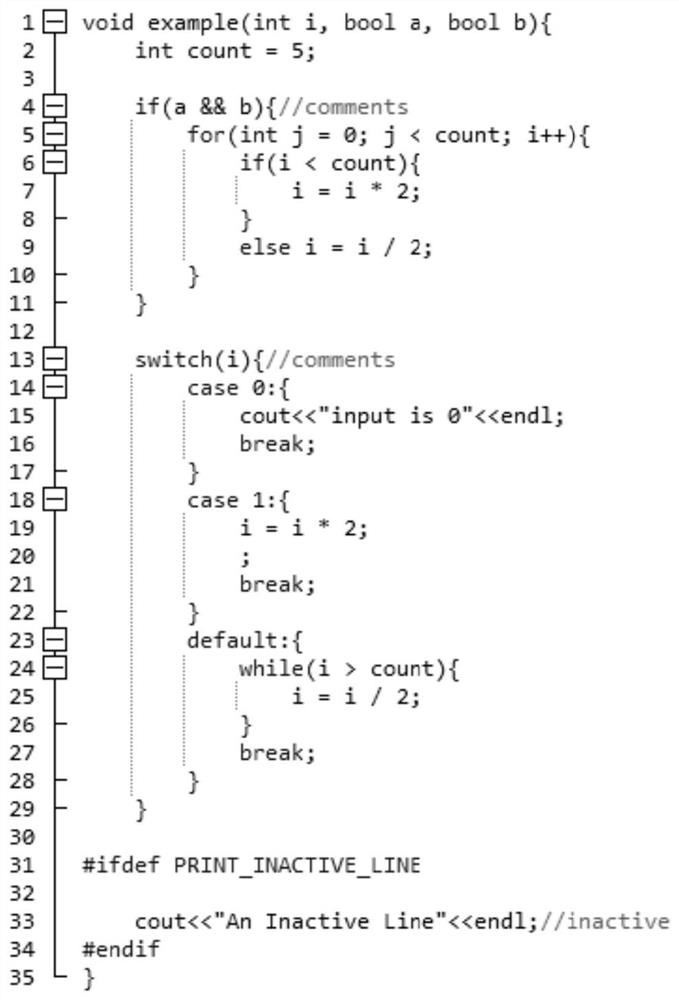
[0049] S1. Calculate the code metrics of the functions in the source code, where the code metrics of the functions include statistical metrics and complexity metrics. Statistical indicators of the number of lines in the statistical indicators include: total number of lines, number of code lines, number of blank lines, number of comment lines, number of preprocessed code lines, number of inactive lines, ratio ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com