Penetration testing method and device
A penetration test, a technology to be tested, applied in computer security devices, machine learning, instruments, etc., can solve the problems of labor-intensive, low-efficiency, and time-consuming tests
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
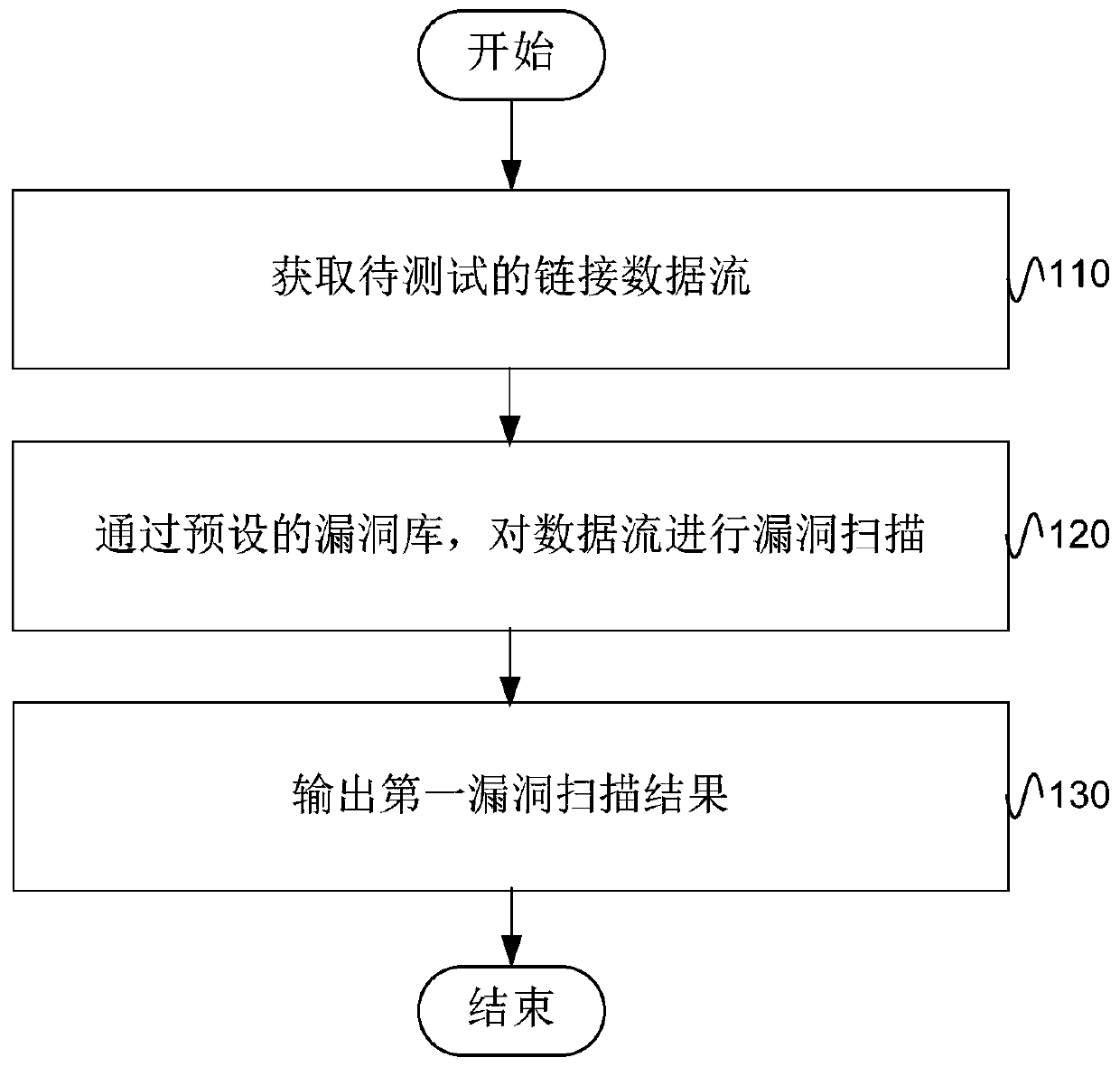
[0020] figure 1 The method flow of the penetration test provided for the embodiment of the present invention Figure 1 , the execution subject of this method may be a terminal or a server with a penetration testing function. Such as figure 1 As shown, the method of penetration testing includes the following steps:
[0021] S110, acquiring the link data stream to be tested;
[0022] A link is also called a hyperlink. The so-called hyperlink refers to a connection relationship pointing to a target from a web page, and the object used for hyperlinking in a web page can be a section of text or a picture. After the text or picture, the link target will be displayed on the browser and opened or run depending on the type of the target. A hyperlink on a web page is usually implemented using a uniform resource locator (Uniform Resource Locator, URL).
[0023] The link data flow in this embodiment (hereinafter referred to as "data flow") can be understood as a collection of all dat...
Embodiment 2
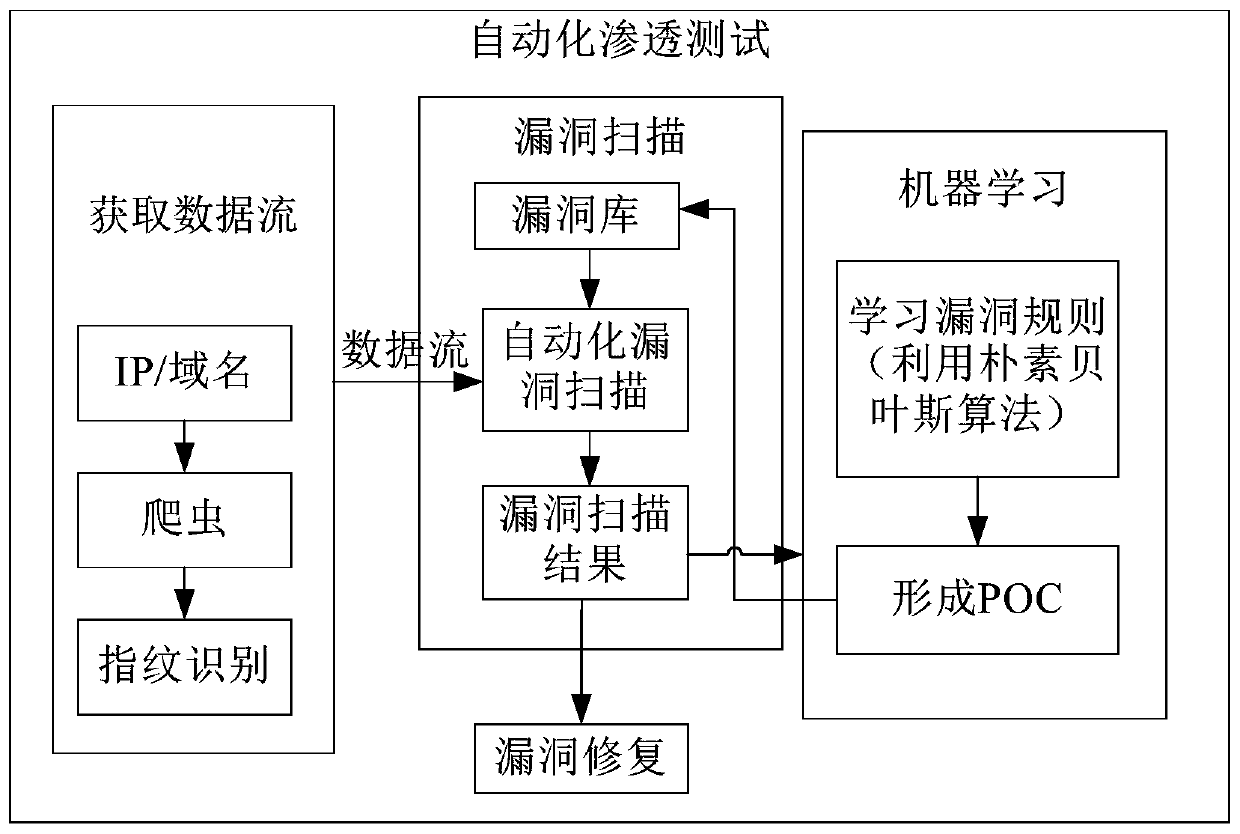
[0049] existfigure 1 In the penetration testing method shown, the continuously updated POC vulnerability library plays a key role in the entire testing process, which provides a prerequisite for finding more diverse and complex vulnerabilities.
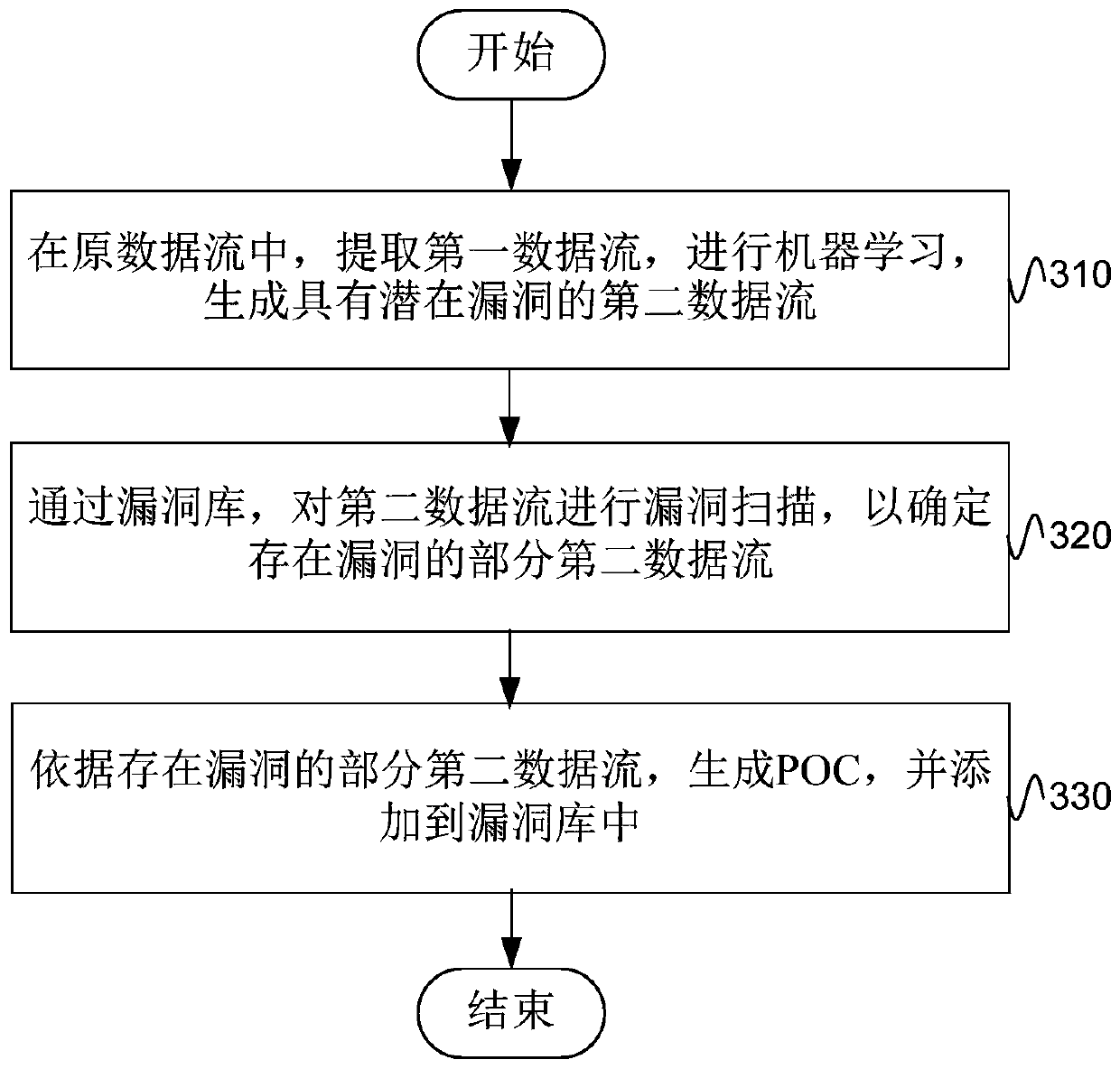
[0050] figure 2 It shows the process frame diagram of updating the POC in the vulnerability database during the penetration test, as shown in figure 2 As shown in , the entire penetration test is roughly divided into three parts, obtaining the data flow, scanning the data flow for vulnerabilities, and learning the data flow to form a POC.
[0051] Specifically, you can enter the IP address / domain name in the address input field, obtain the original URL data through crawler technology, and then perform fingerprint identification on these original URL data to remove duplicate URL data, and finally the remaining URL data The data is used as the data flow to be tested; the data flow to be tested is automatically scanned for vulnerabili...
Embodiment 3
[0096] Figure 4 Schematic diagram of the penetration test device provided for the embodiment of the present invention Figure 1 , which can be used to execute as figure 1 The method steps shown. Such as Figure 4 As shown, the device of the penetration test includes: a data acquisition module 410, a first vulnerability scanning module 420 and a vulnerability output module 430, wherein:
[0097] The data collection module 410 is used to obtain the link data stream to be tested; the first vulnerability scanning module 420 is used to scan the data stream for vulnerabilities through a preset vulnerability database; A plurality of loophole verification codes with loopholes are POC, and the POC is obtained through machine learning on historical data streams; the loophole output module 430 is configured to output the first loophole scanning result.
[0098] The penetration testing device of the embodiment of the present invention scans the data flow to be tested for vulnerabilit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com