Code auditing scheme based on Java bytecode technology
A code auditing and bytecode technology, which is applied in the field of code auditing solutions based on Java bytecode technology, can solve problems such as software at risk, analysis helplessness, and inability to audit third-party package code vulnerabilities, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
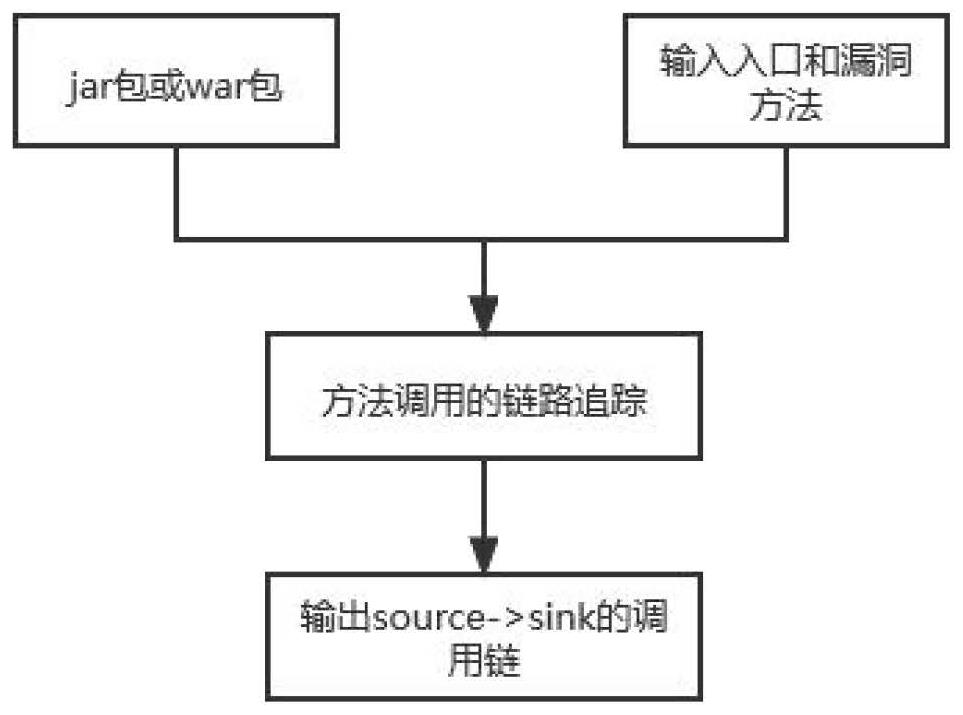
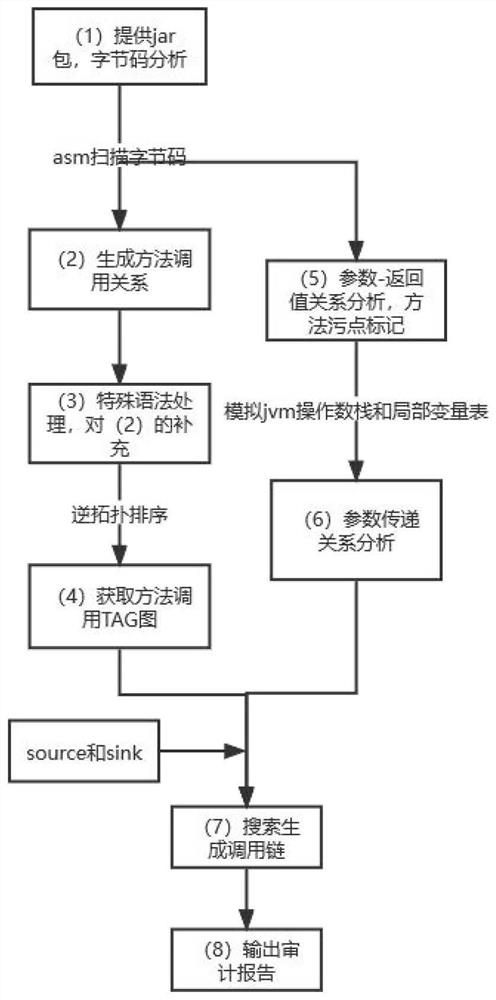
[0021] like Figure 1-2 , the present invention provides a code auditing scheme based on Java bytecode technology, taking ssrf vulnerability auditing as an example:
[0022] (1) ASM bytecode analysis: write Springboot project, custom interface SSRFService, which contains 4 methods: ssrf1, ssrf2, ssrf3, ssrf4, rewrite these 4 methods in the implementation class, where ssrf1 uses URL.openConnection () method (this method will lead to ssrf vulnerability), and the other three methods are implemented by methods that do not contain ssrf vulnerability. Package the project to generate a Jar package. Use ASM to analyze the bytecode to get all the method information, class information, and inheritance relationship. The inheritance relationship indicates which parent classes and implemented interfaces the class has.
[0023] (2) Obtain the call relationship: Use ASM to traverse the class files (bytecodes) in the Jar package, record the traversed methods and which sub-methods are calle...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com