Code audit method and device
A code auditing and source code technology, applied in the field of information security, can solve problems such as misdetection and missed detection of security vulnerabilities, inability to apply the scope of application, and inability to fully reflect security vulnerabilities, etc., to reduce the amount of calculation, improve accuracy, and improve efficiency Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
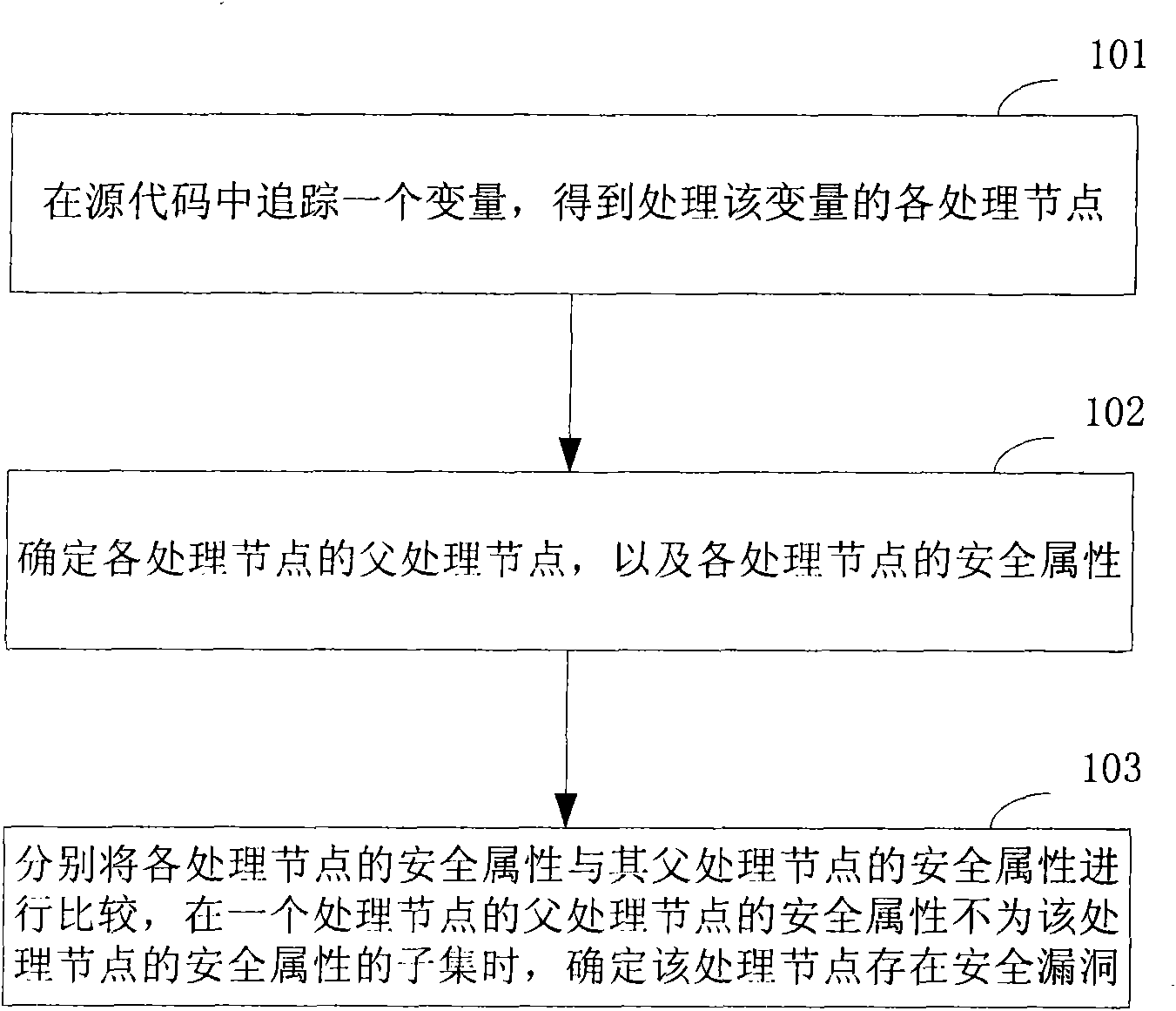
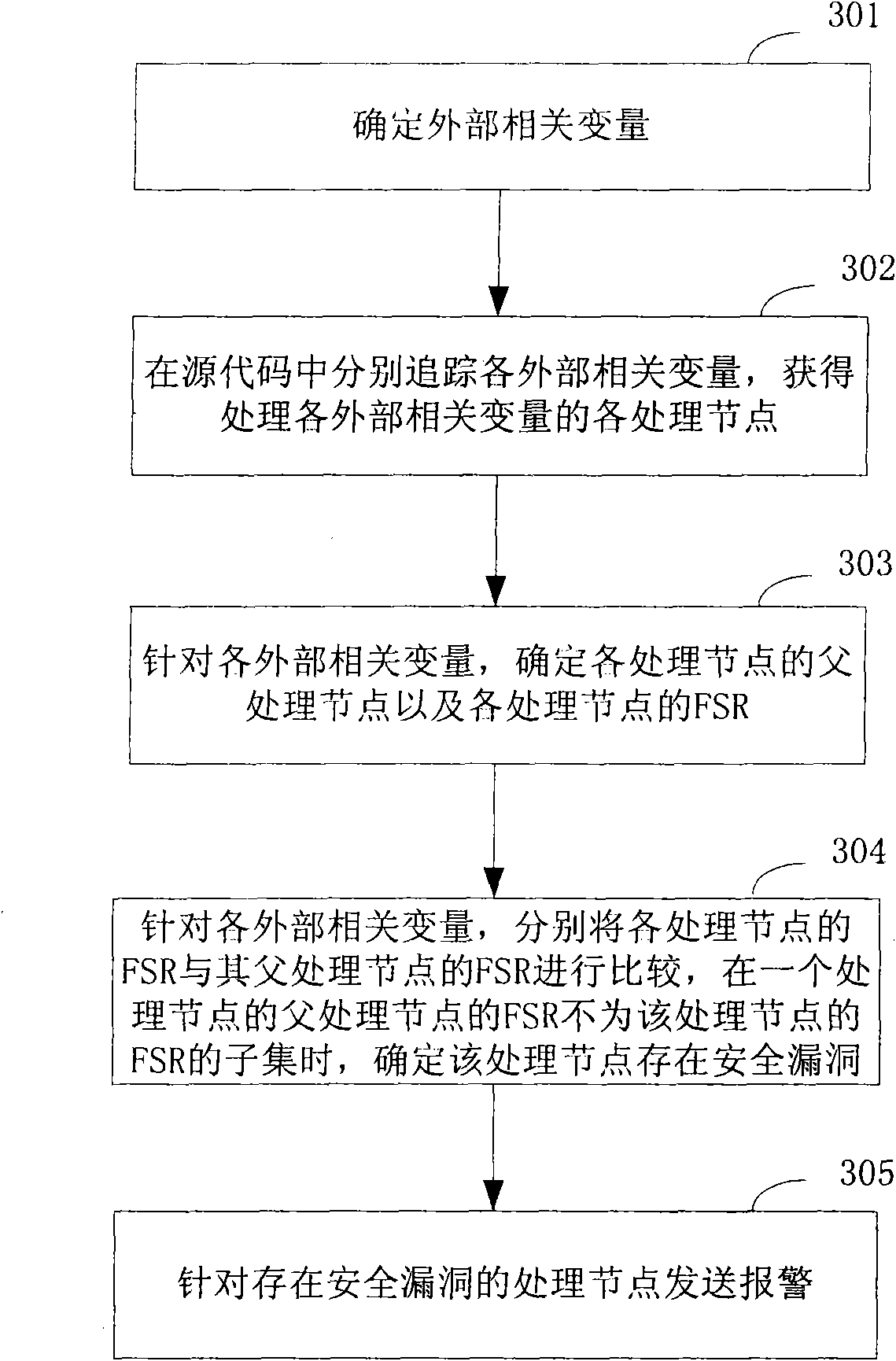
[0043] The inventors of the present invention have analyzed the situation that the program code is attacked and concluded that the reason why the program code has security holes and can be exploited by attackers is that some processing nodes in the source code often actively or passively perform some A processing operation that is not expected by itself.
[0044] Based on the above analysis of program code security vulnerabilities, the technical solution of the present invention mainly compares the security attribute of the processing node in the source code with the security attribute of the parent processing node of the processing node, when the security attribute of the parent processing node is the If the processing node's security attributes are a subset, the processing node does not have a security hole; if the parent processing node's security attributes are not a subset of the processing node's security attributes, the processing node has a security hole. That is, assu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com