Code auditing method and apparatus
A code auditing and source code technology, applied in the field of information security, can solve the problems of inability to completely make up for omissions, inability to meet business needs, and high implementation costs, and achieve the effect of shortening audit time, improving audit efficiency, and reducing workload.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
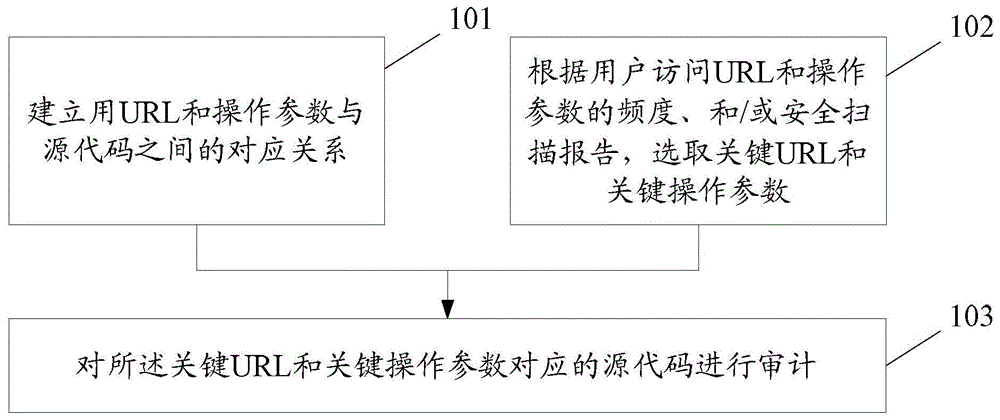
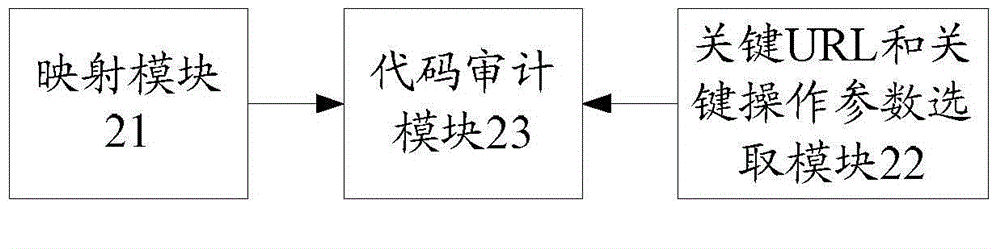
[0045] In the embodiment of the present invention, the corresponding relationship between the URL and the operating parameters and the source code is established; according to the frequency of user access to the URL and the operating parameters, and / or the security scanning report, the key URL and the key operating parameters are selected; The source code corresponding to the URL and key operating parameters is audited.
[0046] Generally, an HTTP request will include URL and operation parameters at the same time. Here, the URL is a concise representation of the location and access method of resources available on the Internet, and is the address of standard resources on the Internet. Every file on the Internet has a unique URL, which contains information indicating where the file is located and how the browser should handle the URL. Generally, the URL consists of the following parts from left to right: Internet resource type (scheme), server address (host), port (port), path ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com