Firewall policy processing method and device
A firewall policy and firewall technology, applied in the field of network security, can solve the problems of large number of firewall rules, labor-intensive, and poor timeliness of manual auditing, so as to reduce the possibility of being attacked, achieve effective management, and improve auditing efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
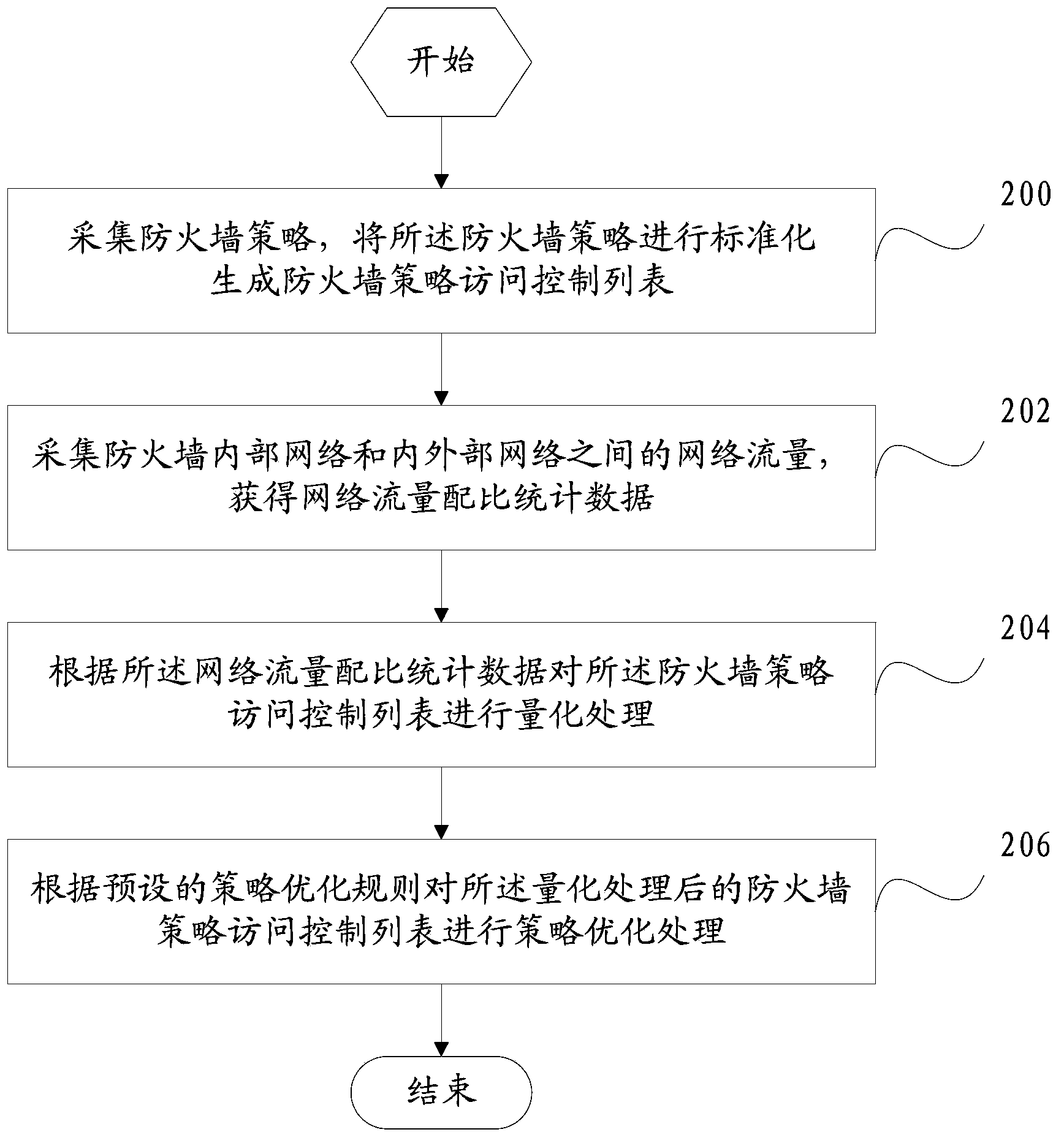
[0020] figure 1 It is a flow chart of a firewall policy processing method in an embodiment of the present invention. Such as figure 1 shown, including the following steps:
[0021] Step 100, collecting firewall policies, and standardizing the firewall policies to generate a firewall policy access control list;
[0022] Step 102, collect network traffic between the internal network of the firewall and the internal and external networks, and obtain network traffic ratio statistics;
[0023] Step 104, performing quantitative processing on the firewall policy access control list according to the network traffic ratio statistical data;
[0024] Step 106: Perform policy optimization processing on the quantized firewall policy access control list according to preset policy optimization rules.
[0025] Preferably, after step 106, the method may further include: performing security audit processing on the quantified firewall policy access control list according to preset security a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com