A vulnerability detection method and device
A vulnerability detection and vulnerability technology, applied in computer security devices, instruments, computing, etc., can solve problems such as server hangs, slow test speed, and easy false negatives.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0018] The embodiment of the present invention provides a vulnerability detection method, which can be applied to various occasions that require vulnerability detection, such as malicious code analysis, vulnerability mining, real-time monitoring of application security vulnerabilities, monitoring of website backdoors, and interception of malicious requests.
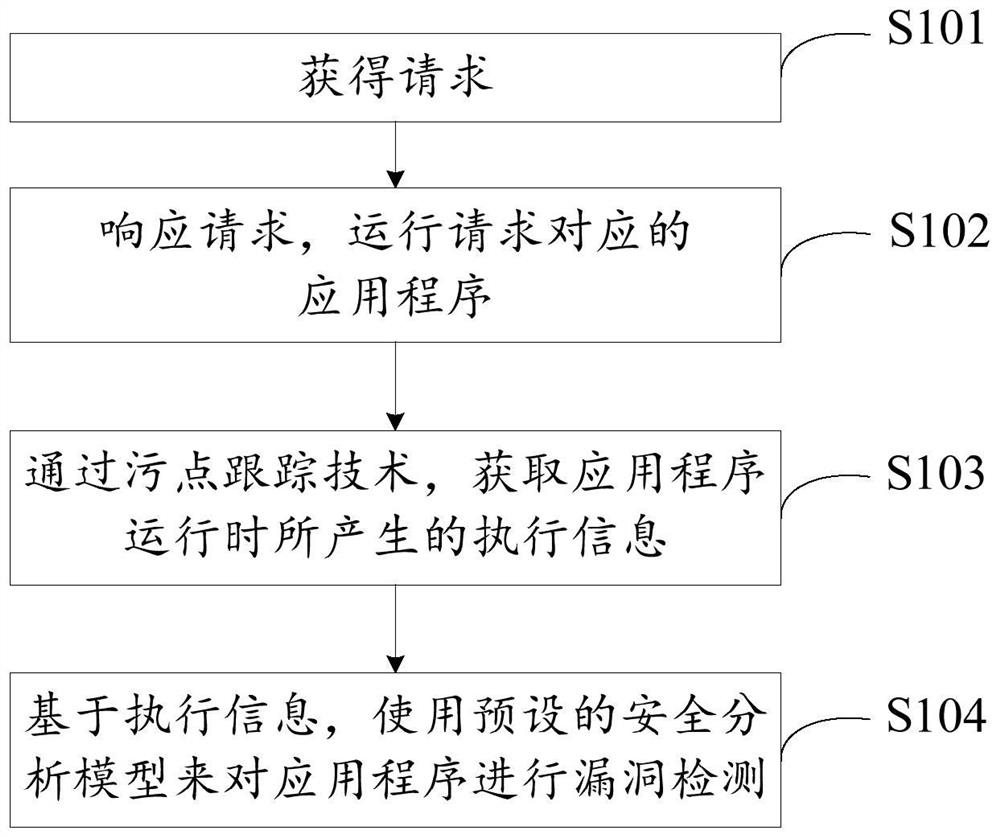
[0019] figure 1 It is a schematic flow chart of the vulnerability detection method in Embodiment 1 of the present invention, see figure 1 As shown, the vulnerability detection method includes:
[0020] S101: obtain a request;
[0021] Here, the request is used to run the application.
[0022] In practical applications, when it is necessary to test the security vulnerabilities of the application in the development phase, QA, security testing phase, etc., the request can be generated manually or by a crawler, so as to automatically detect the vulnerability of the application to determine whether the application is There ...
Embodiment 2
[0065] Based on the same inventive concept, as the implementation of the above method, the embodiment of the present invention provides a vulnerability detection device, the device embodiment corresponds to the aforementioned method embodiment, for the sake of easy reading, this device embodiment does not repeat the aforementioned method embodiment The details in the present invention will be described one by one, but it should be clear that the device in this embodiment can correspondingly implement all the content in the foregoing method embodiments.
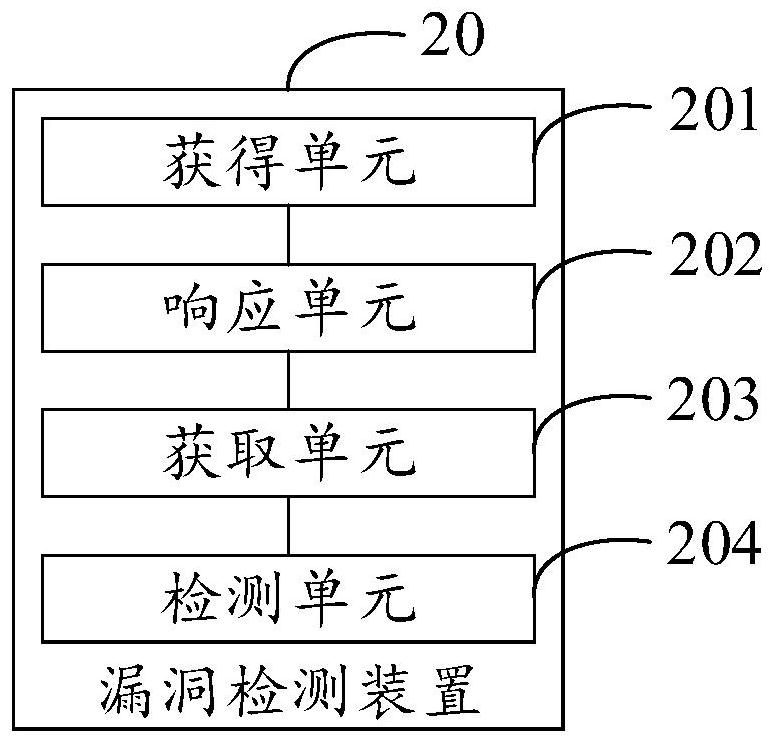
[0066] figure 2 It is a schematic structural diagram of the vulnerability detection device in Embodiment 2 of the present invention, see figure 2 As shown, the vulnerability detection device 20 includes: an obtaining unit 201, a response unit 202, an obtaining unit 203, and a detection unit 204, wherein the obtaining unit 201 is used to obtain a request; the response unit 202 is used to respond to the request and run the cor...
Embodiment 3
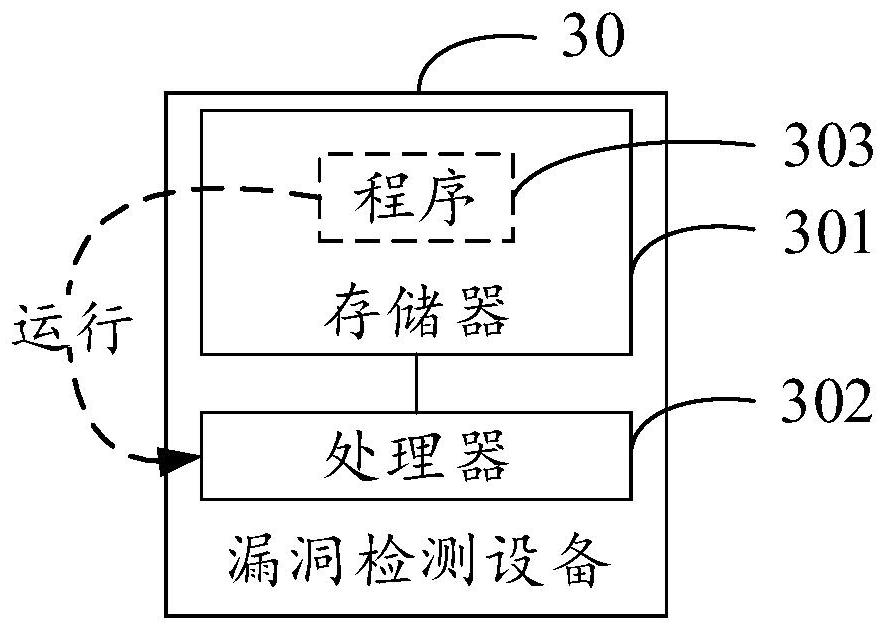
[0081] Based on the same inventive concept, an embodiment of the present invention provides a vulnerability detection device. image 3 It is a schematic structural diagram of the vulnerability detection device in Embodiment 3 of the present invention, see image 3 As shown, the vulnerability detection device 30 includes: a memory 301, a processor 302, and a computer program 303 stored on the memory 301 and operable on the processor 302. When the processor executes the program 303, the following steps are implemented: obtaining a request; responding to the request , run the application corresponding to the request, and start the pollution program; obtain the execution information generated when the application is running through the taint tracking technology; based on the execution information, use the preset security analysis model to detect the vulnerability of the application.
[0082] In the embodiment of the present invention, when the above-mentioned processor executes th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com