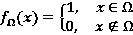A non-contact industrial control system or equipment static vulnerability detection system and detection method
An industrial control system and vulnerability detection technology, which is applied in general control systems, control/regulation systems, comprehensive factory control, etc., can solve problems such as difficult industrial control systems, illegal intrusion, and occupation of industrial control network bandwidth, and achieve efficient and accurate detection The effect of the method
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
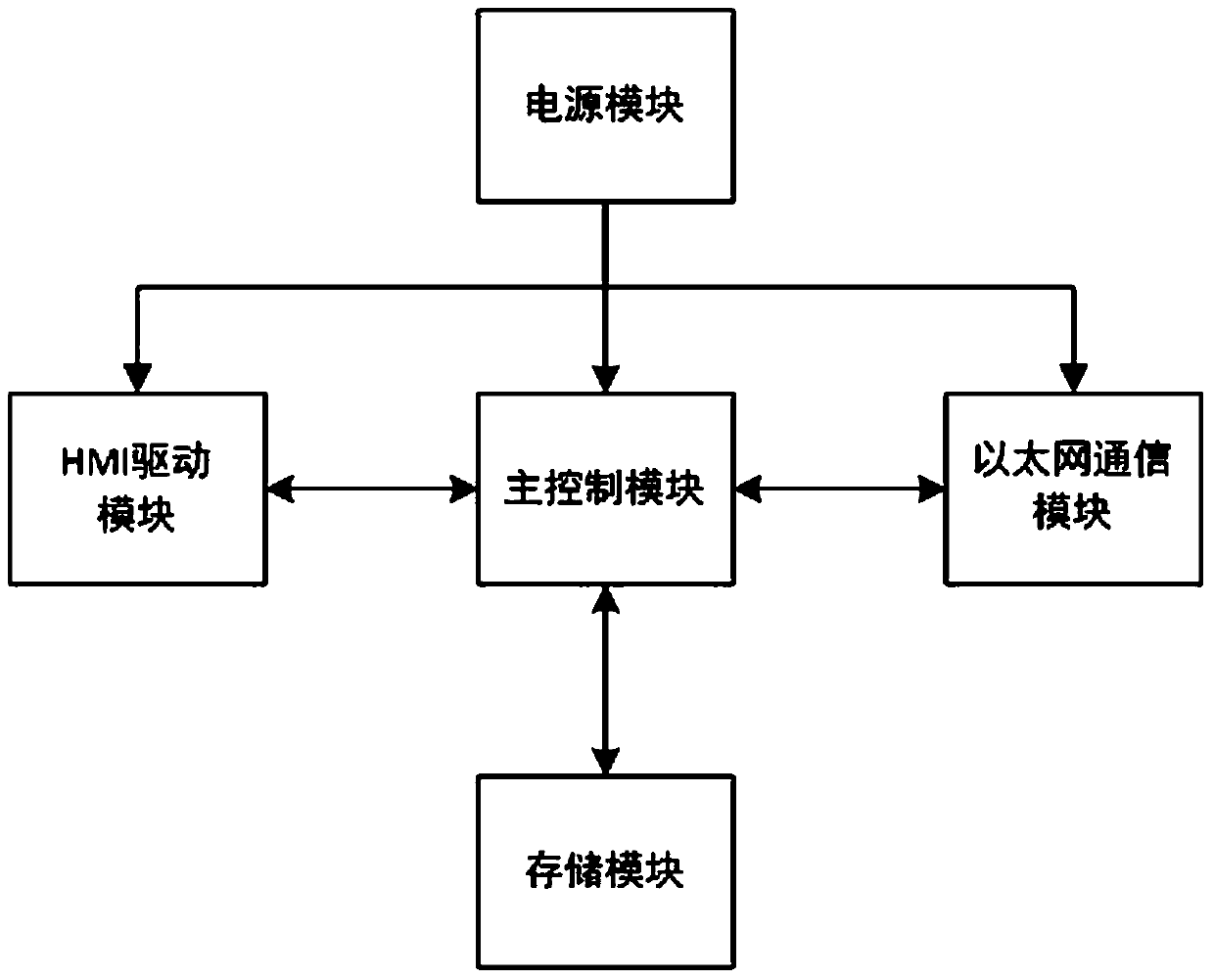
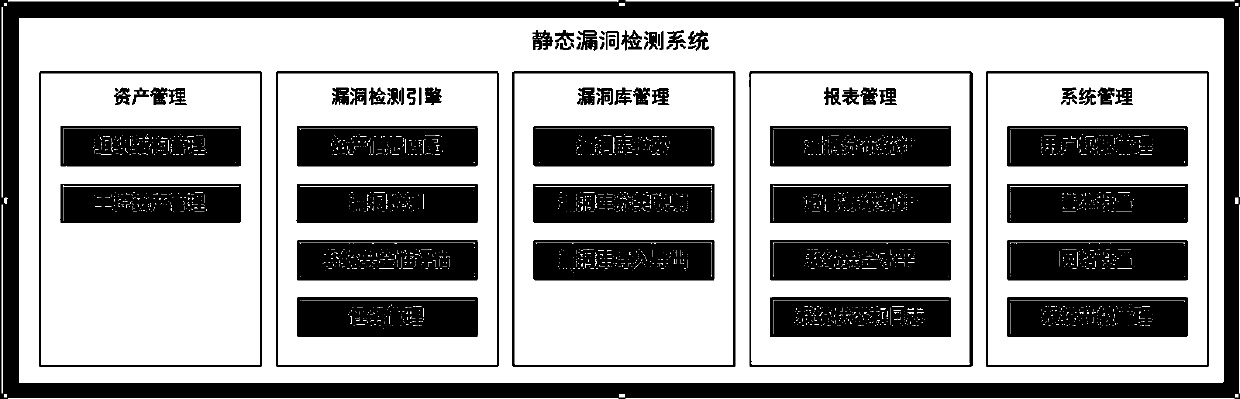
[0046] Such as figure 1 and figure 2 , a non-contact industrial control system or equipment static vulnerability detection system, including an asset management unit, a vulnerability detection engine unit, a vulnerability library management unit, a report management unit and a system management unit; the asset management unit transmits the information of the assets to be detected To the vulnerability detection engine unit, the vulnerability detection engine unit compares the information of the assets to be detected with the vulnerability information in the vulnerability library management unit to detect vulnerabilities, and sends the detection results to the report management unit for recording. For setup and upgrade management.
[0047] This is the most basic embodiment of a non-contact industrial control system or equipment static loophole detection system of the present invention. The asset management unit transmits the information of the assets to be detected to the vul...
Embodiment 2
[0049] Such as figure 1 and figure 2 , a non-contact industrial control system or equipment static vulnerability detection system, including an asset management unit, a vulnerability detection engine unit, a vulnerability library management unit, a report management unit and a system management unit; the asset management unit transmits the information of the assets to be detected To the vulnerability detection engine unit, the vulnerability detection engine unit compares the information of the assets to be detected with the vulnerability information in the vulnerability library management unit to detect vulnerabilities, and sends the detection results to the report management unit for recording. Set and upgrade management; the asset management unit includes an organizational structure management module and an industrial control asset management module, the organizational structure management module is used to manage the group management functions of the industrial control sys...
Embodiment 3
[0052] Such as figure 1 and figure 2 , a detection method of a non-contact industrial control system equipment static vulnerability detection system, characterized in that it comprises the following steps
[0053] Step 1: Input industrial control assets, import the data in the factory-level or upper-level information management system into the industrial control assets to be tested;
[0054] Step 2: Retrieve the vulnerability database, search and match the entered industrial control assets in the data table corresponding to the vulnerability database according to the manufacturer information, product name, product model and product version, and calculate the matching function value;
[0055] Step 3: Static vulnerability detection, according to the matching function value calculated in step 2, calculate the result of the vulnerability judgment function, determine the vulnerability information according to the result of the vulnerability judgment function, and match the vulnerab...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com