Out-of-authority vulnerability automatic detection method, equipment and medium
An automatic detection and vulnerability technology, applied in the field of network security, can solve the problem of low efficiency of unauthorized vulnerability detection, and achieve the effects of reducing the number of packets sent, improving the success rate and improving efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
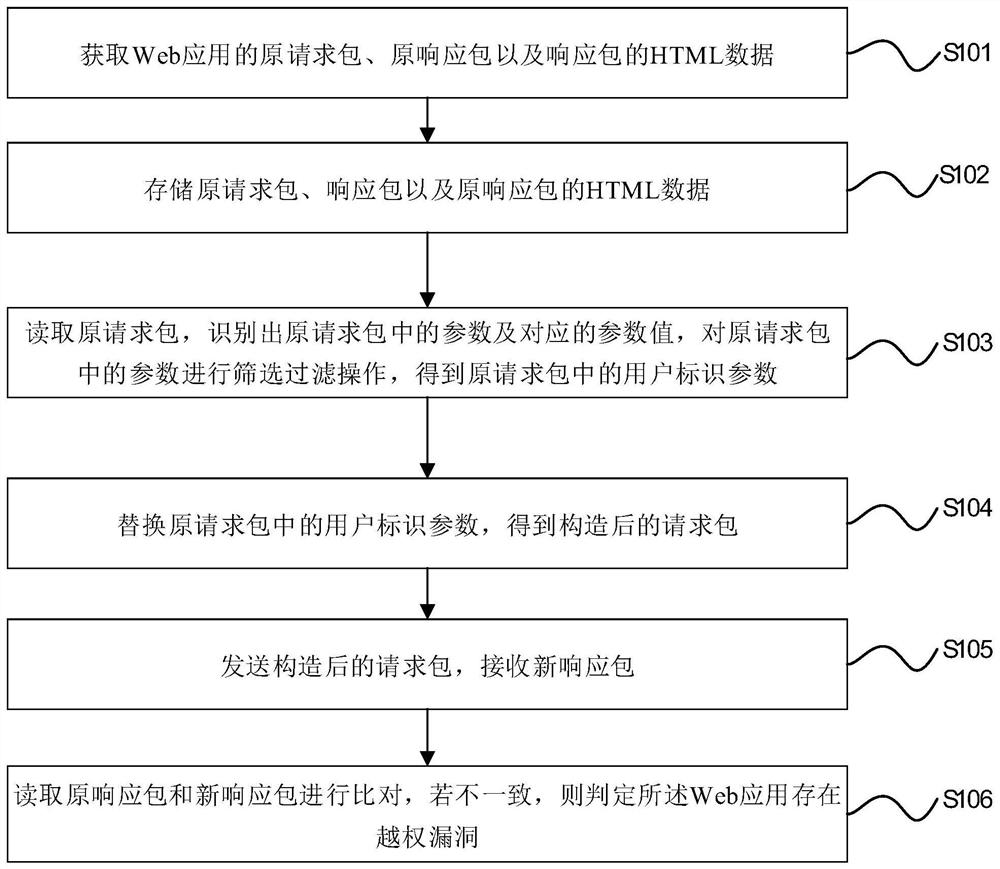
[0059] Based on the above principles, this embodiment provides an automatic detection method for unauthorized vulnerabilities, figure 1 It is a flow chart of the automatic detection method for unauthorized loopholes of the present invention, such as figure 1 As shown, the automatic detection method for unauthorized vulnerabilities includes the following steps:
[0060] S101. Obtain an original request packet, an original response packet, and HTML data of the response packet of the web application.
[0061] The packet capture operation is performed through the proxy tool to intercept the data packets uploaded and received by the web application, so as to obtain the original request packet, original response packet and HTML code of the original response packet of the web application.
[0062] S102. Store the original request packet, the response packet, and the HTML data of the original response packet.
[0063] Because the rate of sending packets again after replacing paramet...
Embodiment 2
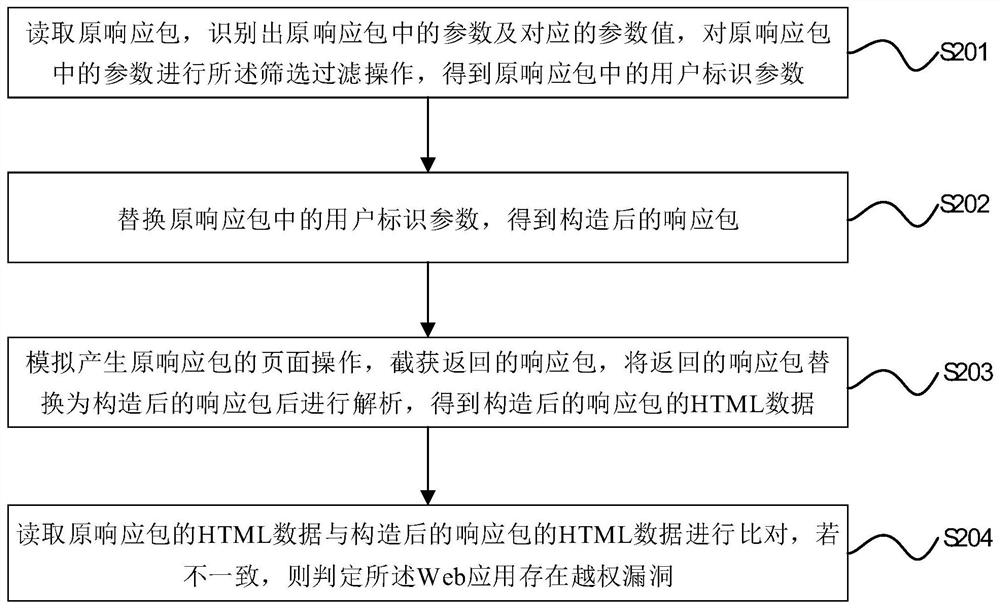
[0101] The difference between this embodiment and the foregoing embodiments is that obtaining the original request packet, the original response packet, and the HTML data of the original response packet of the Web application includes:
[0102] Passive packet capture by proxy tool to obtain the original request packet, original response packet and HTML data of the original response packet of the first account in the Web application, and obtain the original request packet, original response packet and all HTML data of the Web application. Describe the HTML data of the original response packet;
[0103] Automatically load the pre-configured JS script through the browser plug-in to obtain the page operation of the first account, call the selenium module to simulate the login of the second account, and execute the page operation of the first account synchronously, capture packets through the proxy tool, and obtain The request packet of the second account, the response packet of th...
Embodiment 3
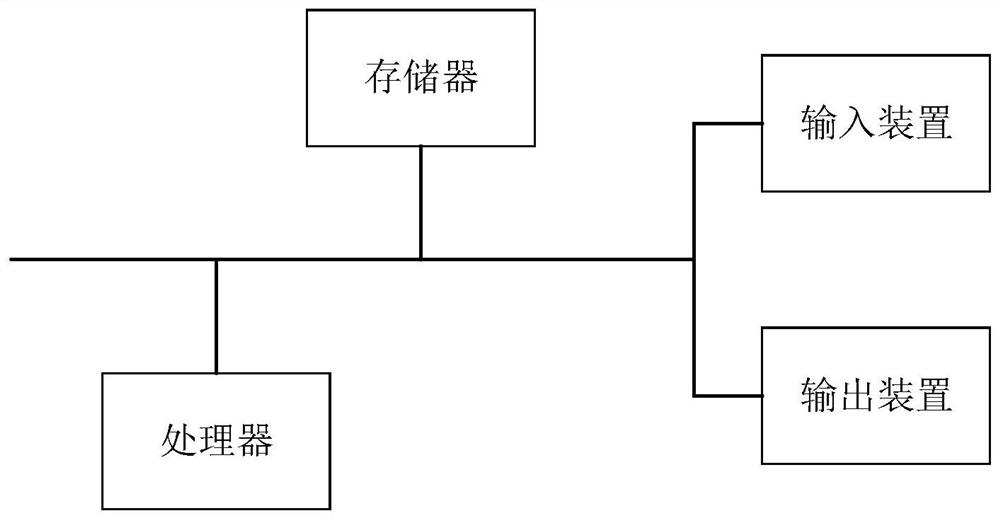
[0114] image 3 It is a schematic structural diagram of an electronic device according to an embodiment of the present invention, such as image 3 As shown, an electronic device is provided, which can be a server, and its internal structure diagram can be as follows image 3 shown. The electronic equipment includes a processor, a memory, an input device, and an output device; wherein the number of processors in the electronic equipment can be one or more, image 3 Take a processor as an example; the processor, memory, input device and output device in the electronic device can be connected by bus or other means, image 3 Take connection via bus as an example.
[0115] Memory, as a computer-readable storage medium, can include high-speed random access memory, non-volatile memory, etc., and can be used to store operating systems, software programs, computer executable programs and databases, such as the unauthorized loophole in Embodiment 1 of the present invention The progr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com