Patents
Literature
32results about How to "Improve the authentication success rate" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
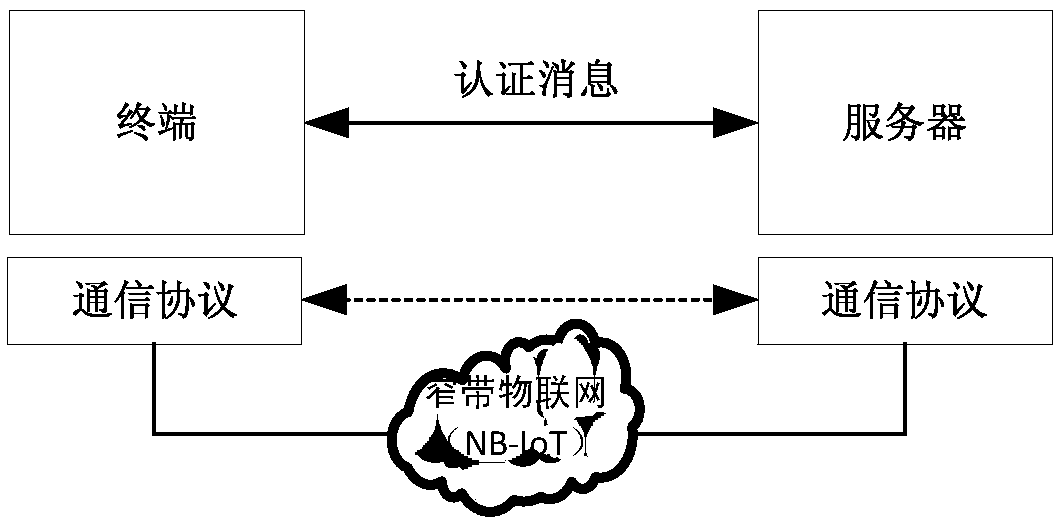
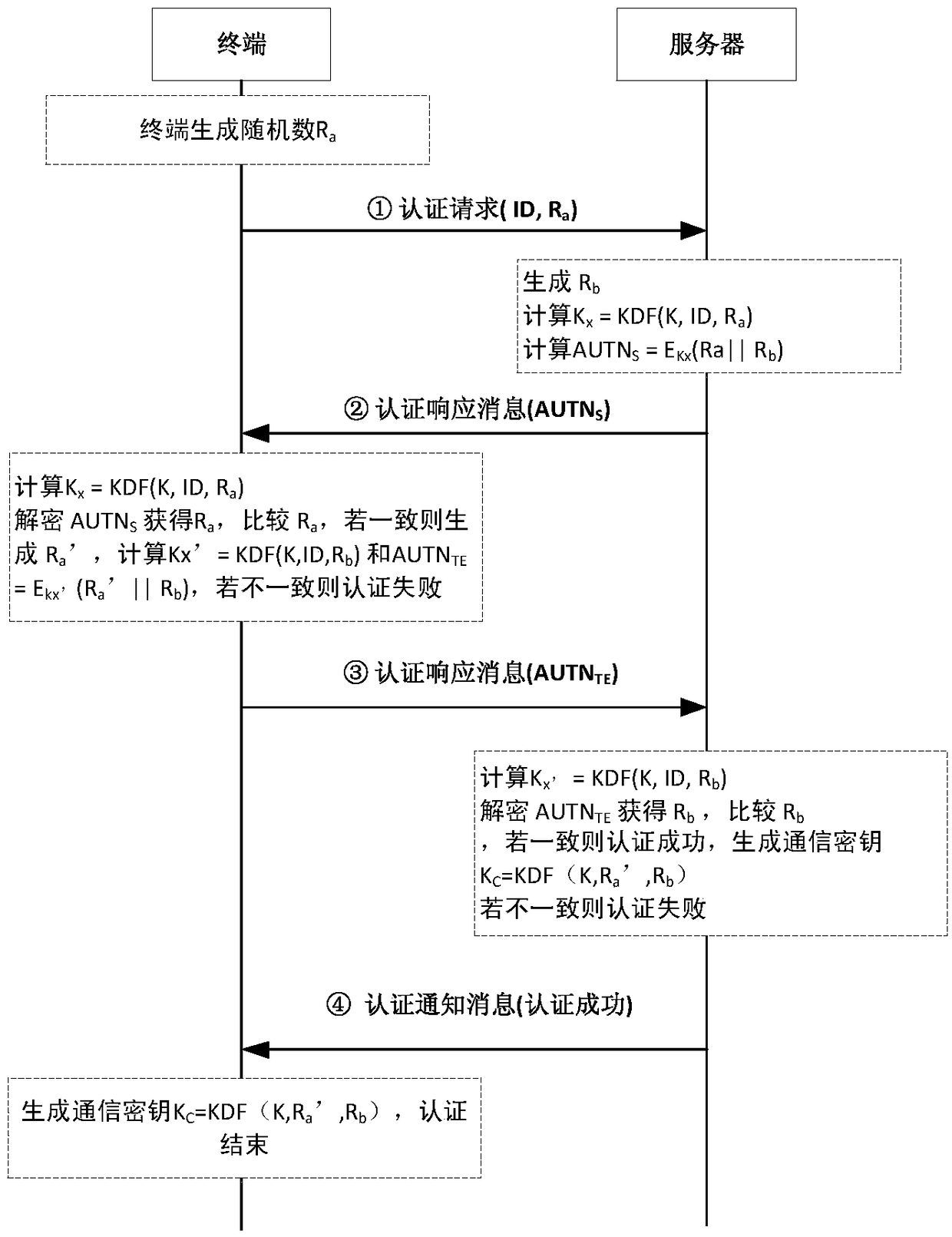
A lightweight secure authentication and key exchange method for narrowband Internet of things
ActiveCN108989318AAvoid risk of leakageReduce Interaction ComplexityTransmissionKey exchangeThe Internet
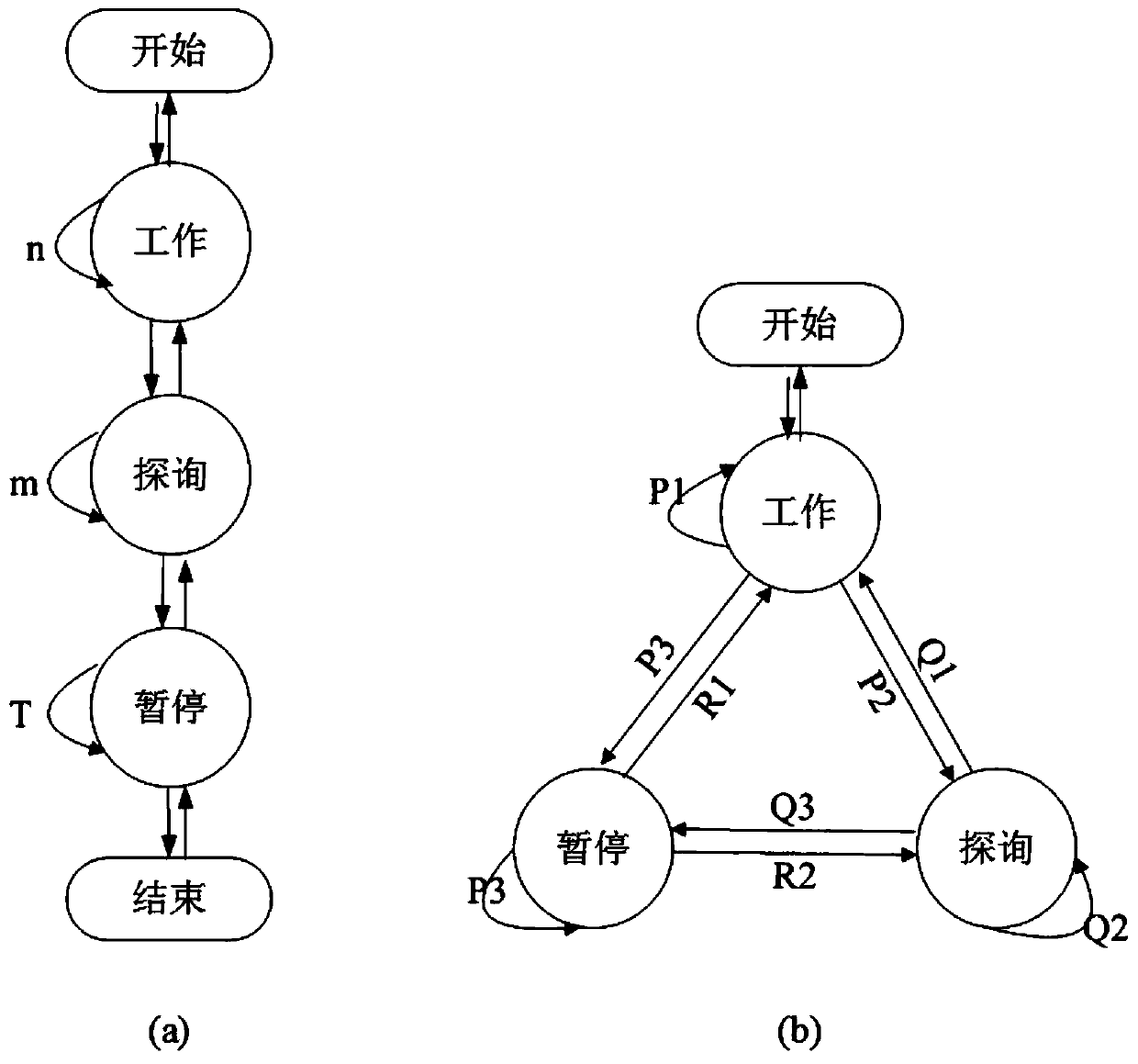
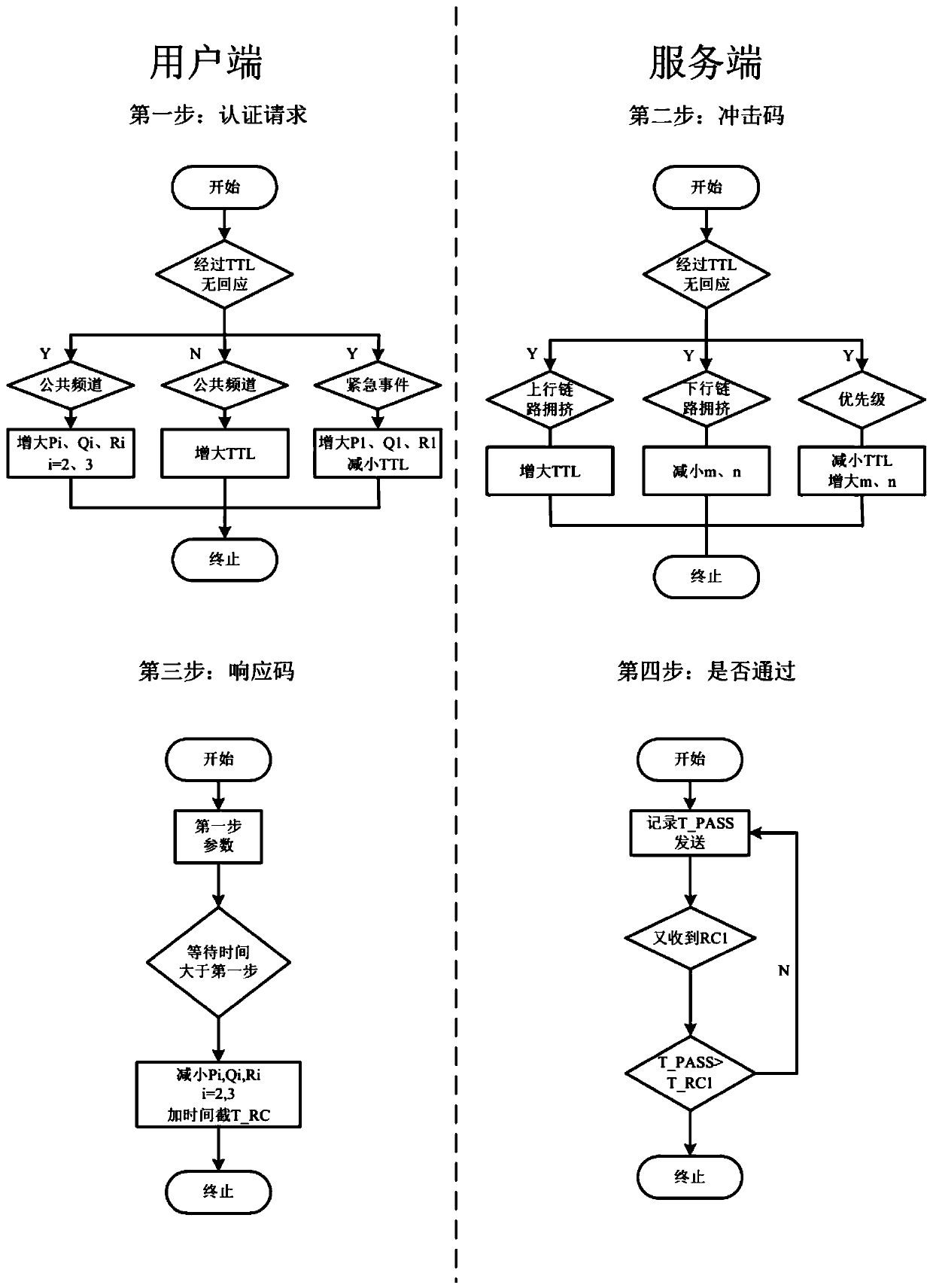
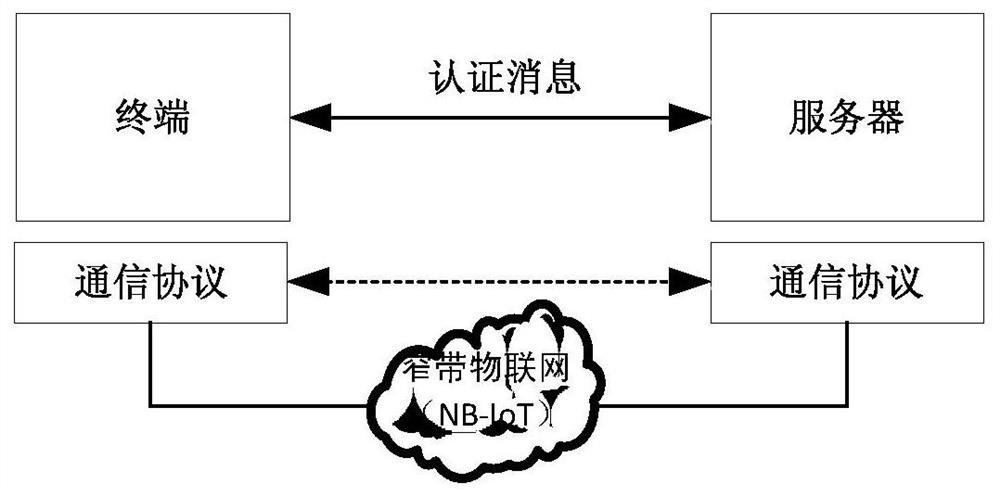
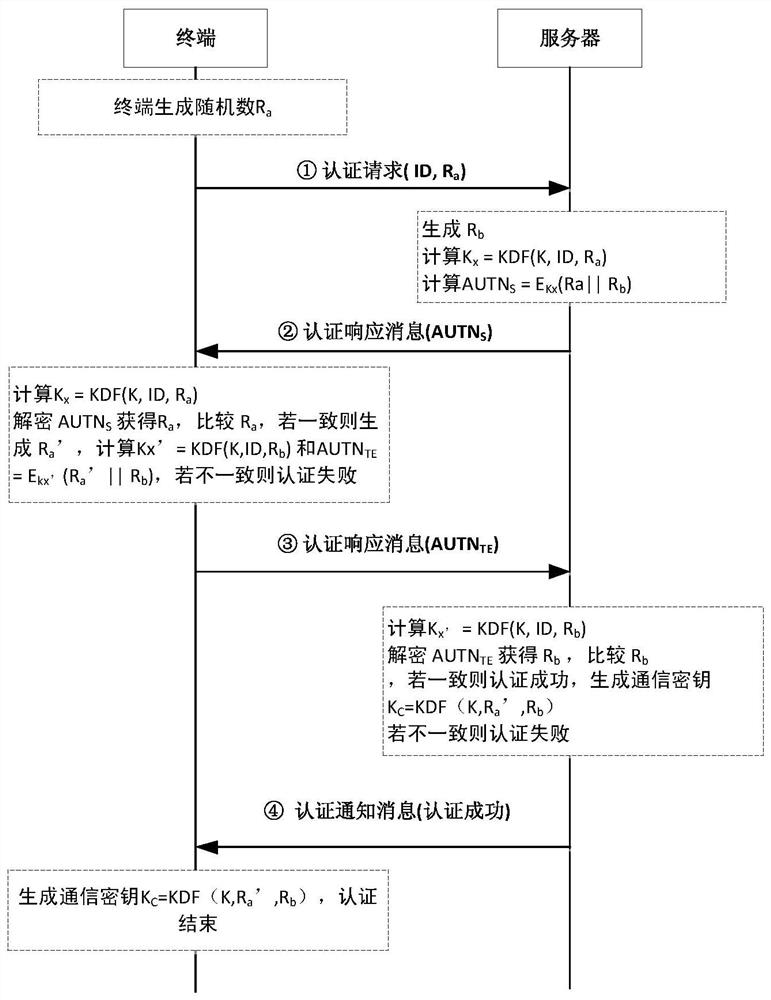
The invention discloses a lightweight security authentication and key exchange method for narrow-band internet of things. The communication main body comprises a terminal and a server. Before the communication is established, the root key is shared between the terminal and the server, and the two-way authentication is realized by adopting a challenge-response interaction mechanism based on a symmetric cryptosystem. The present invention mainly solves the problem of the two-way identity authentication and key exchange between the terminal and server in the Internet of Things application systembased on NB-IoT and other narrow-band Internet of Things connection technologies, can realize lightweight security authentication algorithm, protocol and key agreement mechanism, and meet the design requirements of low power consumption, low bandwidth consumption, low interaction frequency and high security.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
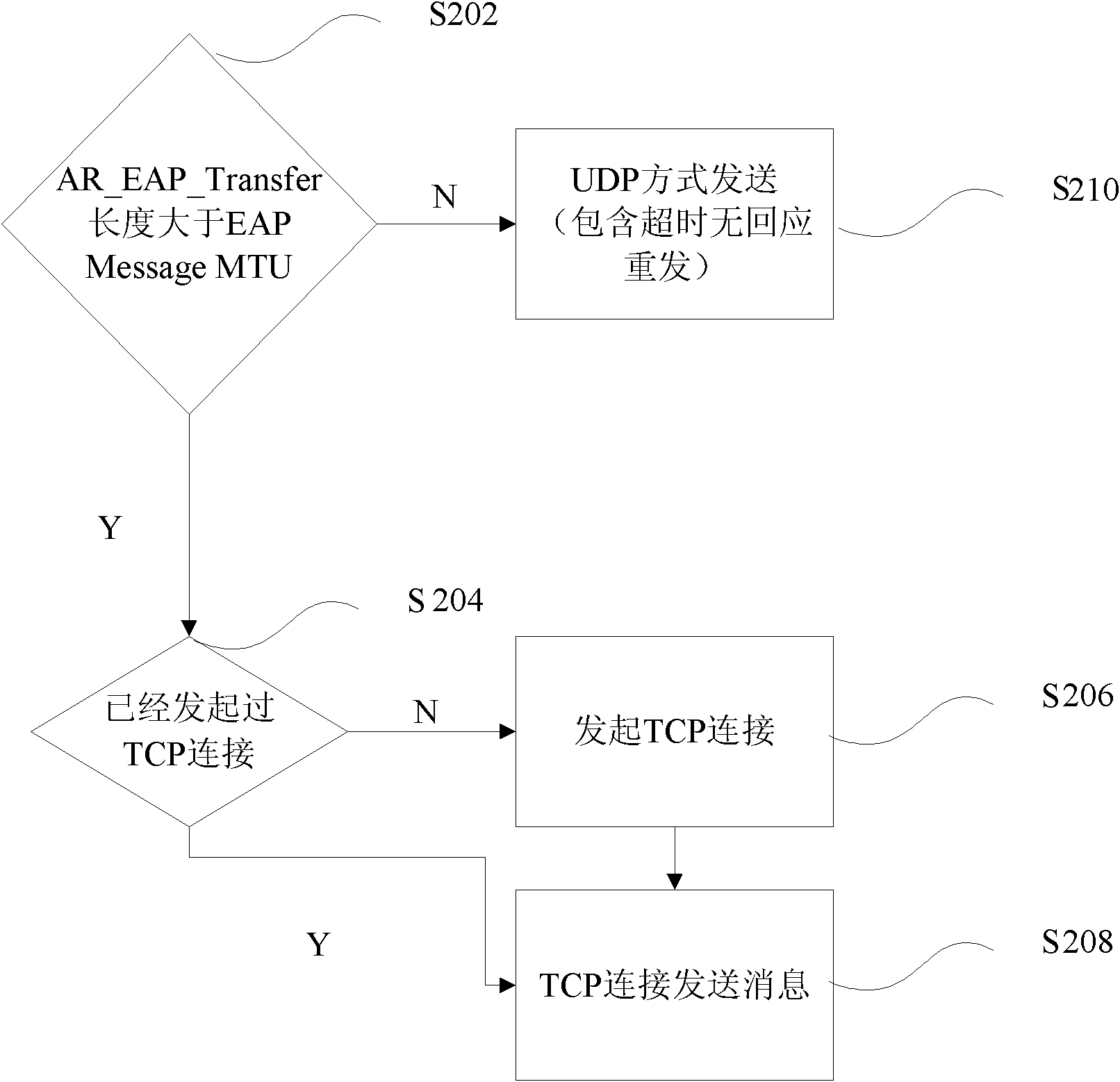
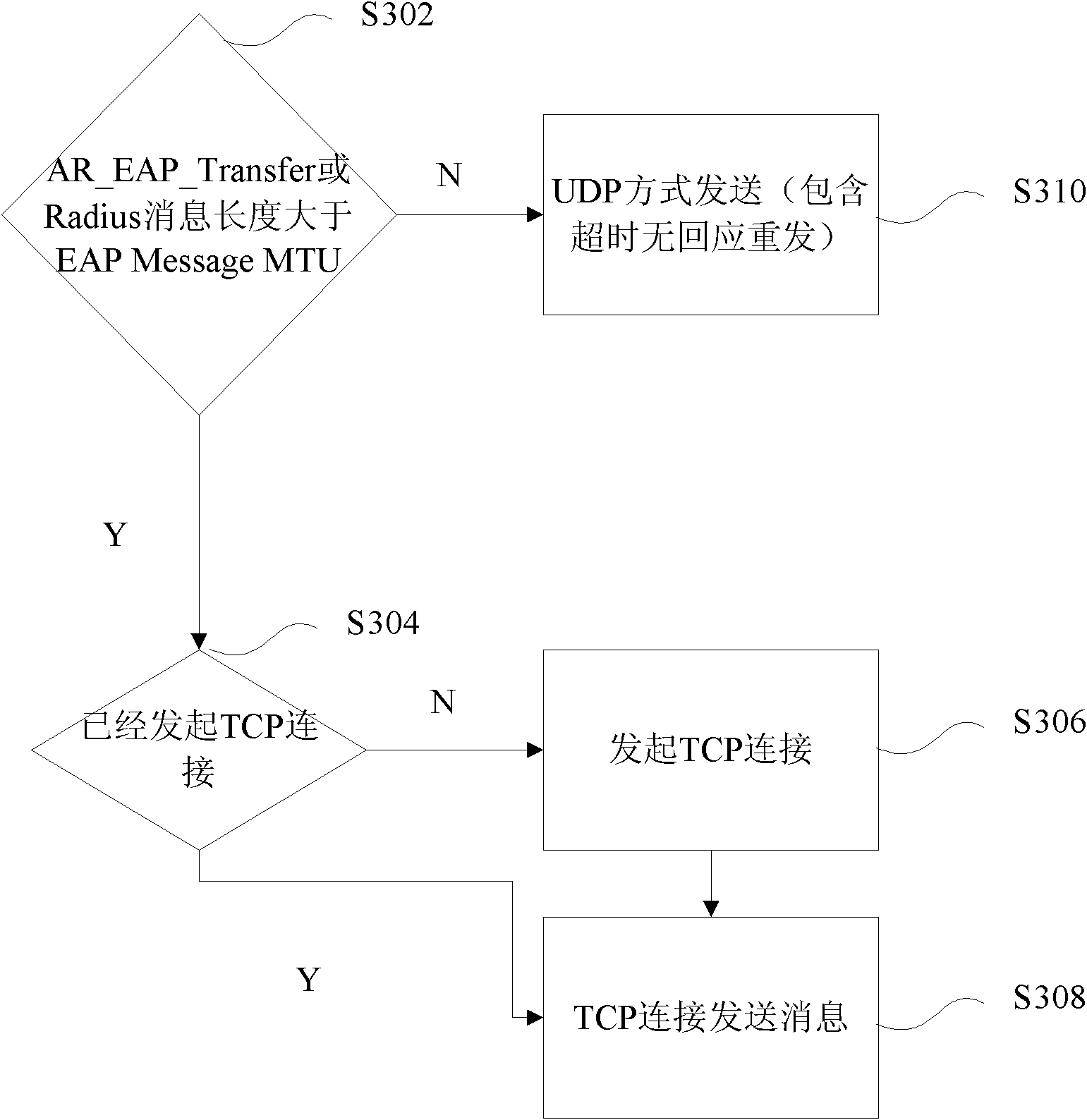
Message transmission method and device
InactiveCN102833750AReduce the possibility of packet lossImprove the authentication success rateSecurity arrangementComputer hardwareUser Datagram Protocol
The invention discloses a message transmission method and device. The message transmission method comprises the following steps: judging whether the length of the message to be transmitted is more than the preset EAP Message MTU value, and transmitting the message to be transmitted by adopting the TCP (transmission control protocol) transmission form if the length of the message to be transmitted is more than the preset EAP Message MTU value. The message transmission method and device solve the problem in the prior that the UDp (user datagram protocol) connection authentication process can lead to low authentication success rate.
Owner:ZTE CORP
Method, Apparatus, and Computer-Readable Recording Medium for Authenticating a User
InactiveUS20140133713A1Improve the authentication success rateIncrease ratingsCharacter and pattern recognitionDigital data authenticationComputer graphics (images)Pattern matching
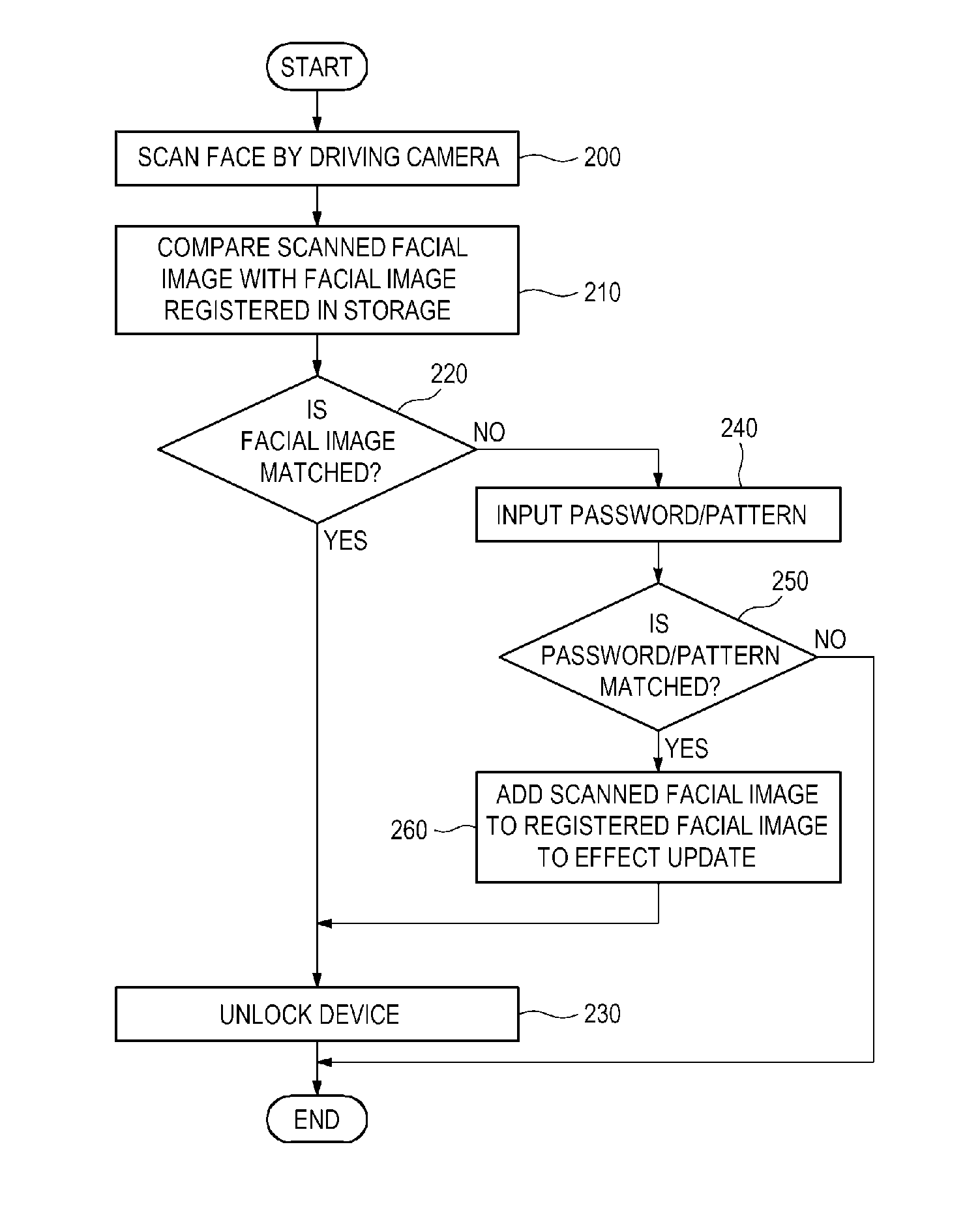
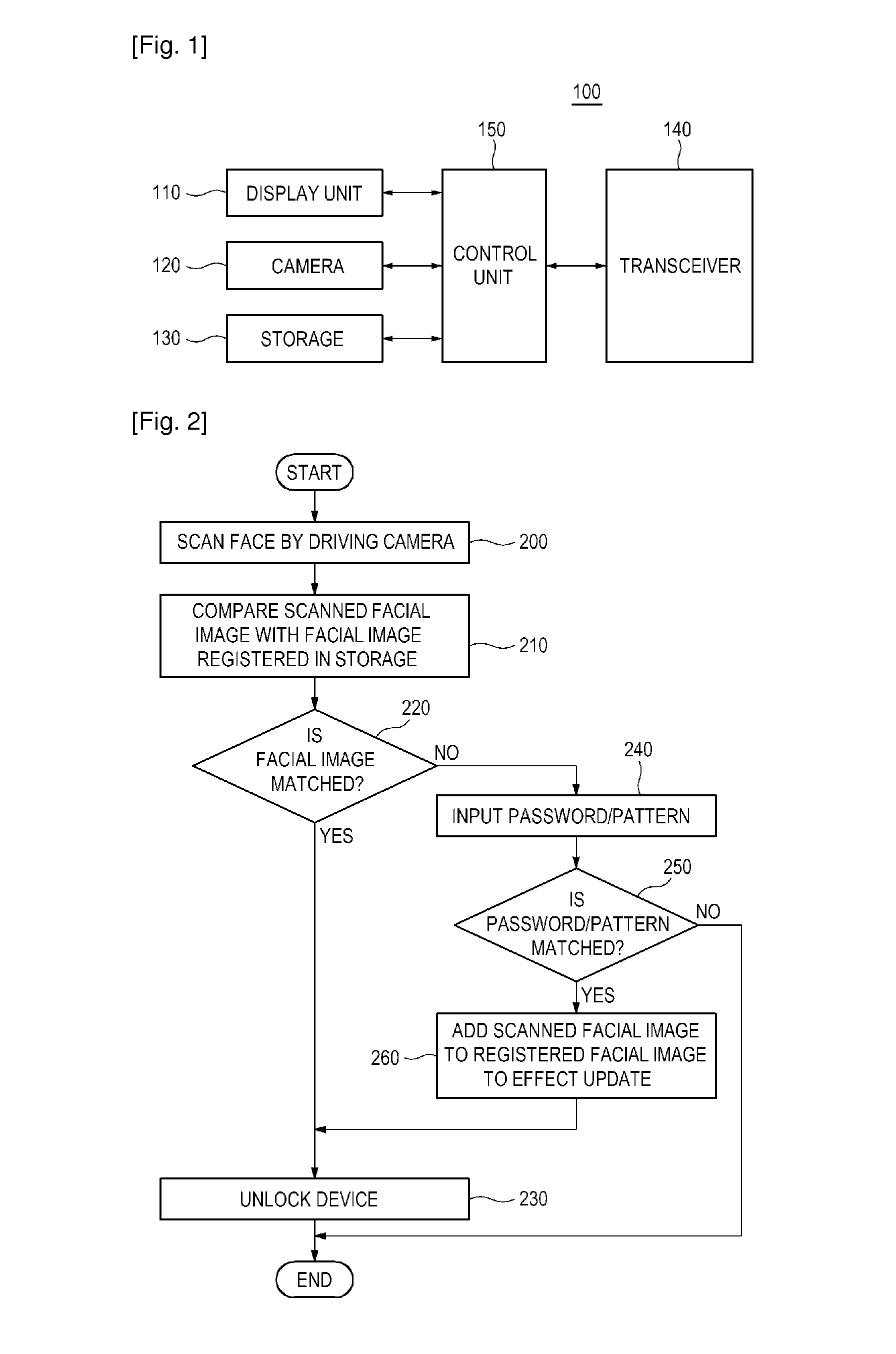
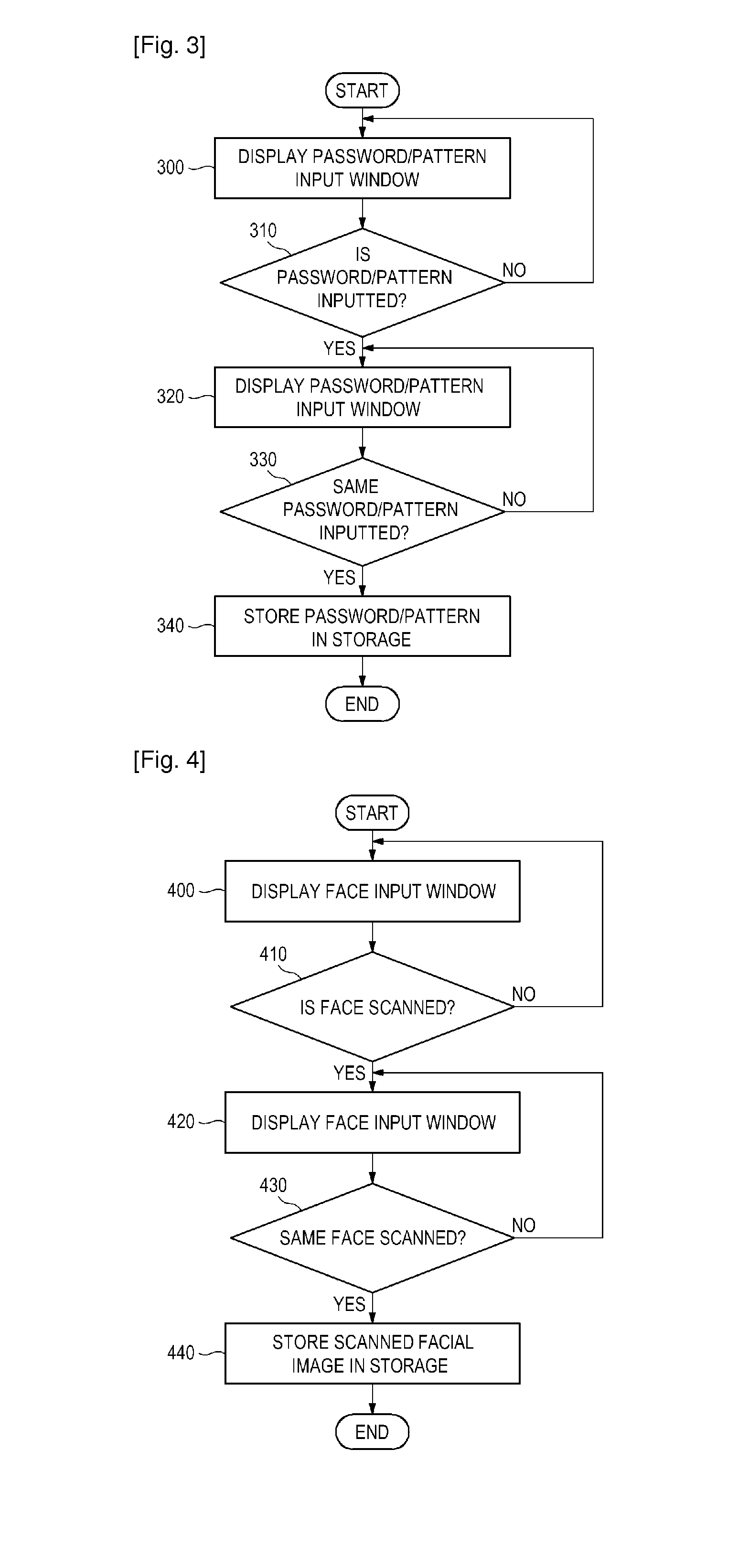
Provided are a method, apparatus, and computer-readable recording medium for authenticating a user. The user authentication method includes scanning a face by operating a camera to obtain a scanned facial image, and comparing the scanned facial image with a facial image registered in a storage. Even if the scanned facial image is mismatched to the registered facial image, a password / pattern is requested. If an input password / pattern matches a registered password / pattern, a device can be unlocked. Additionally, the scanned facial image in the storage may be updated.
Owner:INTEL CORP
A method and system for quickly authenticating a driver's identity
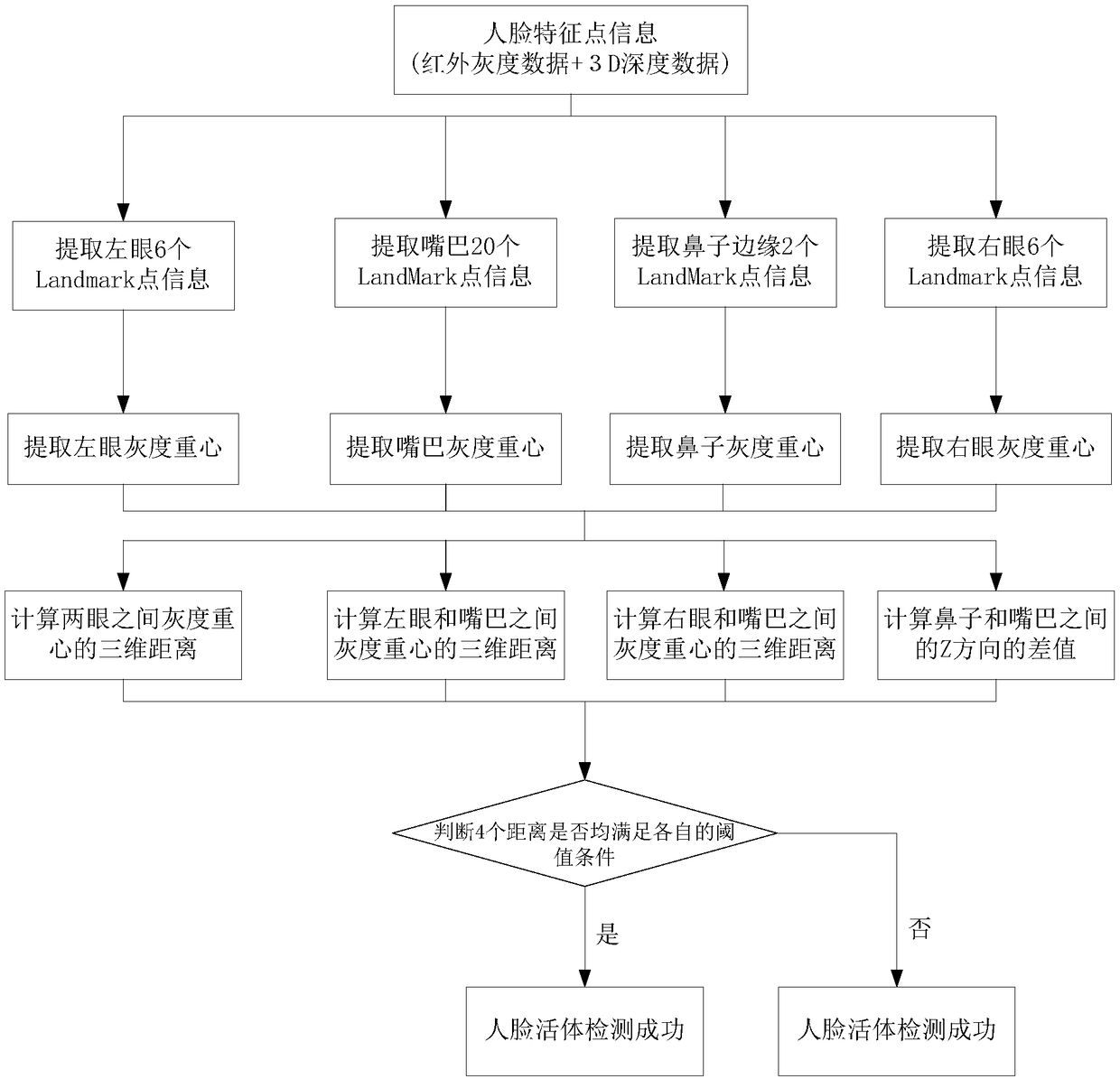
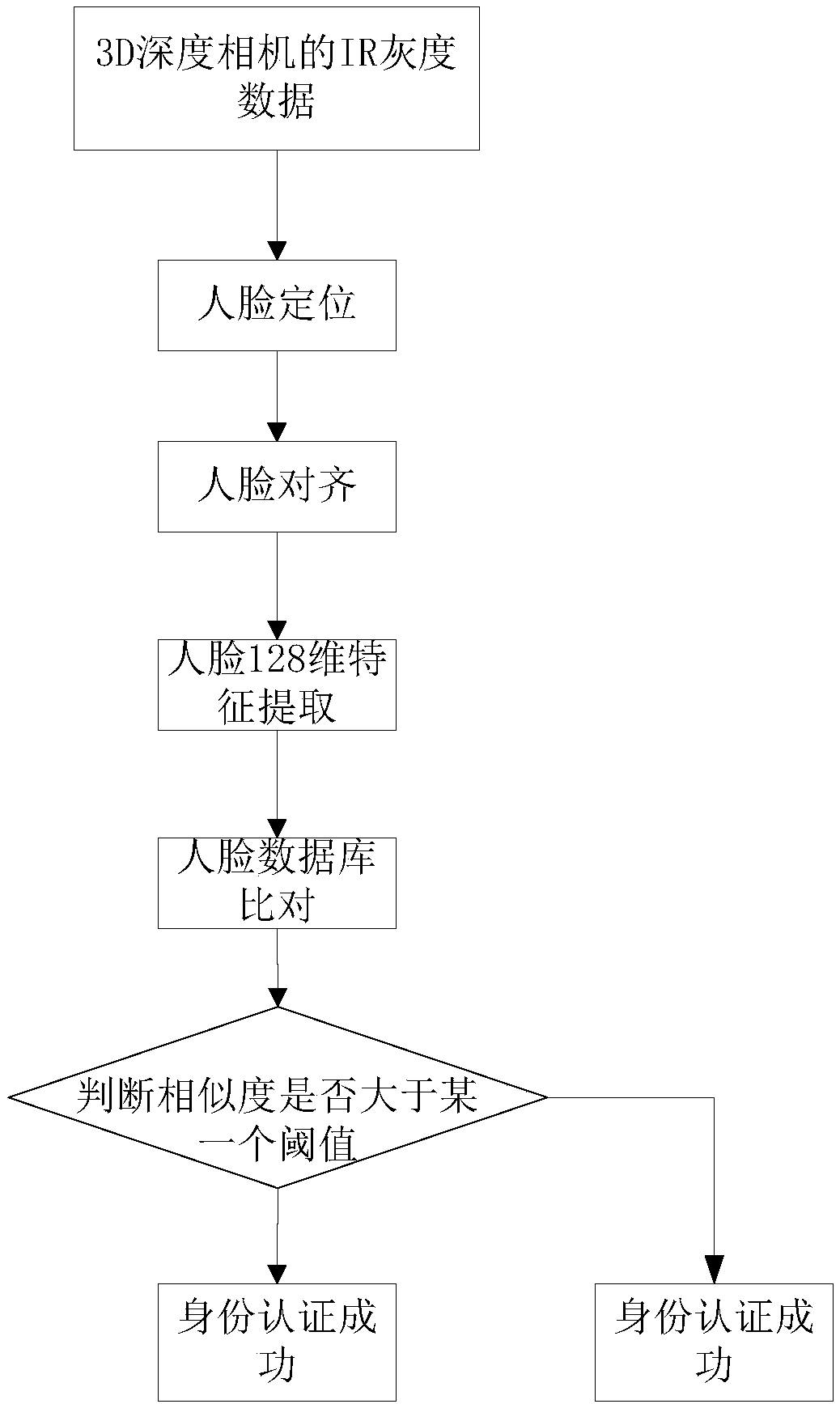
InactiveCN109145750ALiveness authentication process is simpleHigh authentication rateCharacter and pattern recognitionControl devicesAuthentication systemDriver/operator
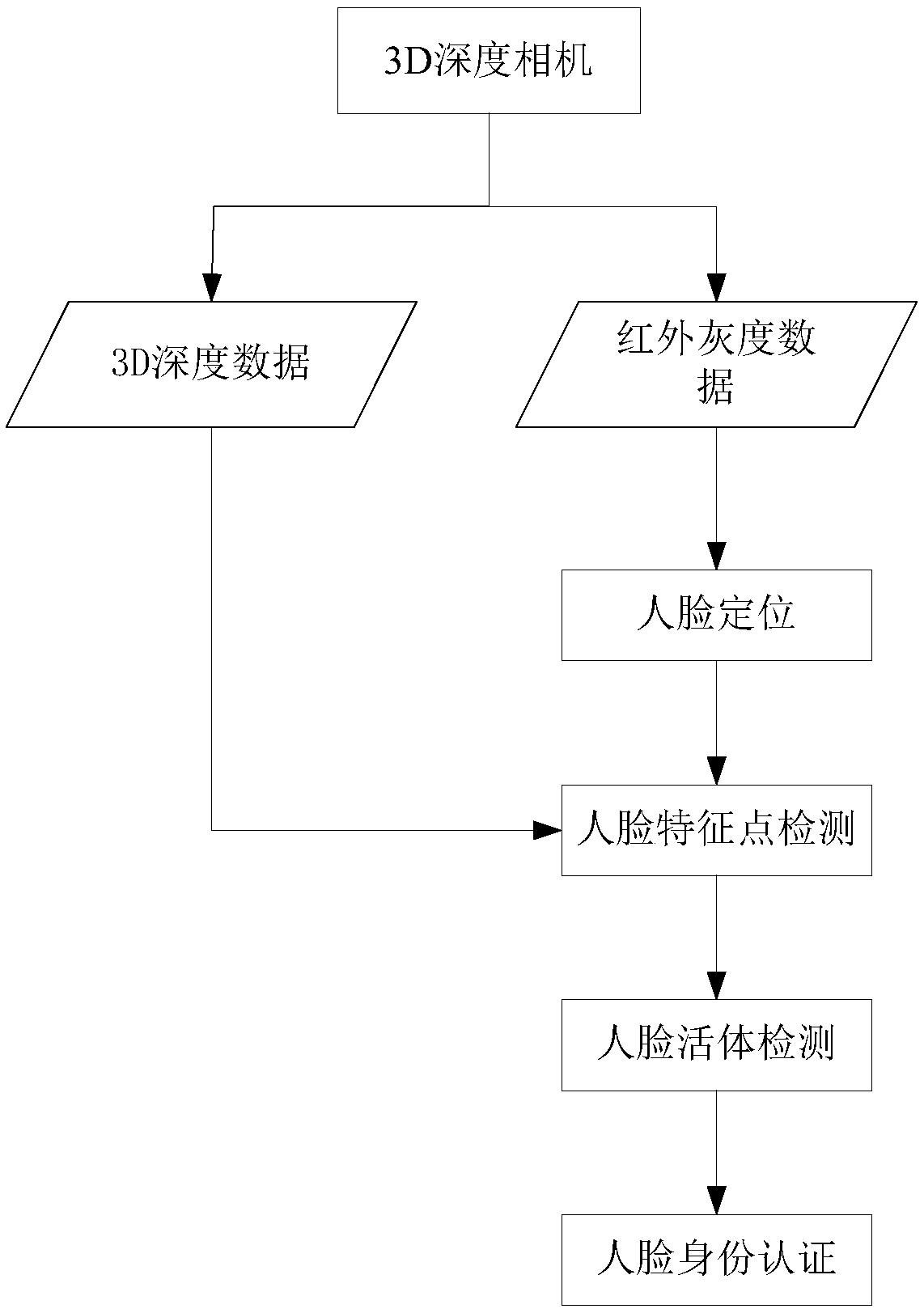
The invention discloses a driver identity fast authentication method and a driver identity fast authentication system, which comprises the following steps: a 3D depth camera acquires infrared gray data and 3D depth data of a human face; the infrared gray-scale data is used to locate the face and obtain the face region; feature point detection is performed on the face region to obtain the face feature points; based on 3D depth data of face feature points and face feature points, face detection, identity authentication and output results are carried out in vivo. The invention adopts 3D depth camera to carry out human face living detection without driver completing a series of actions, and the living authentication process is relatively simple and the authentication rate is high. The 3D depthcamera is little affected by the external environment, and the success rate of driver identification is high.
Owner:华迅金安(北京)科技有限公司
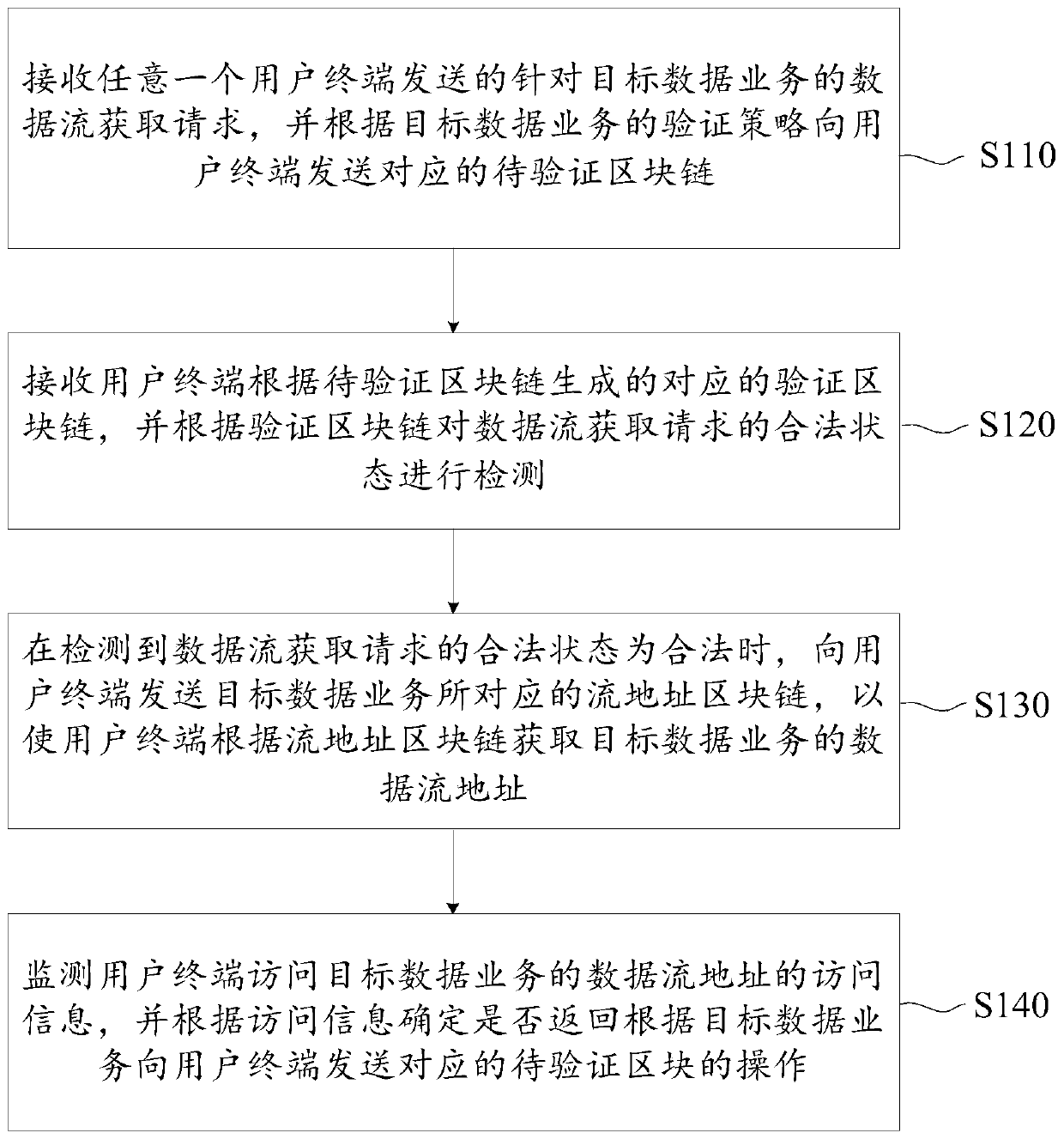
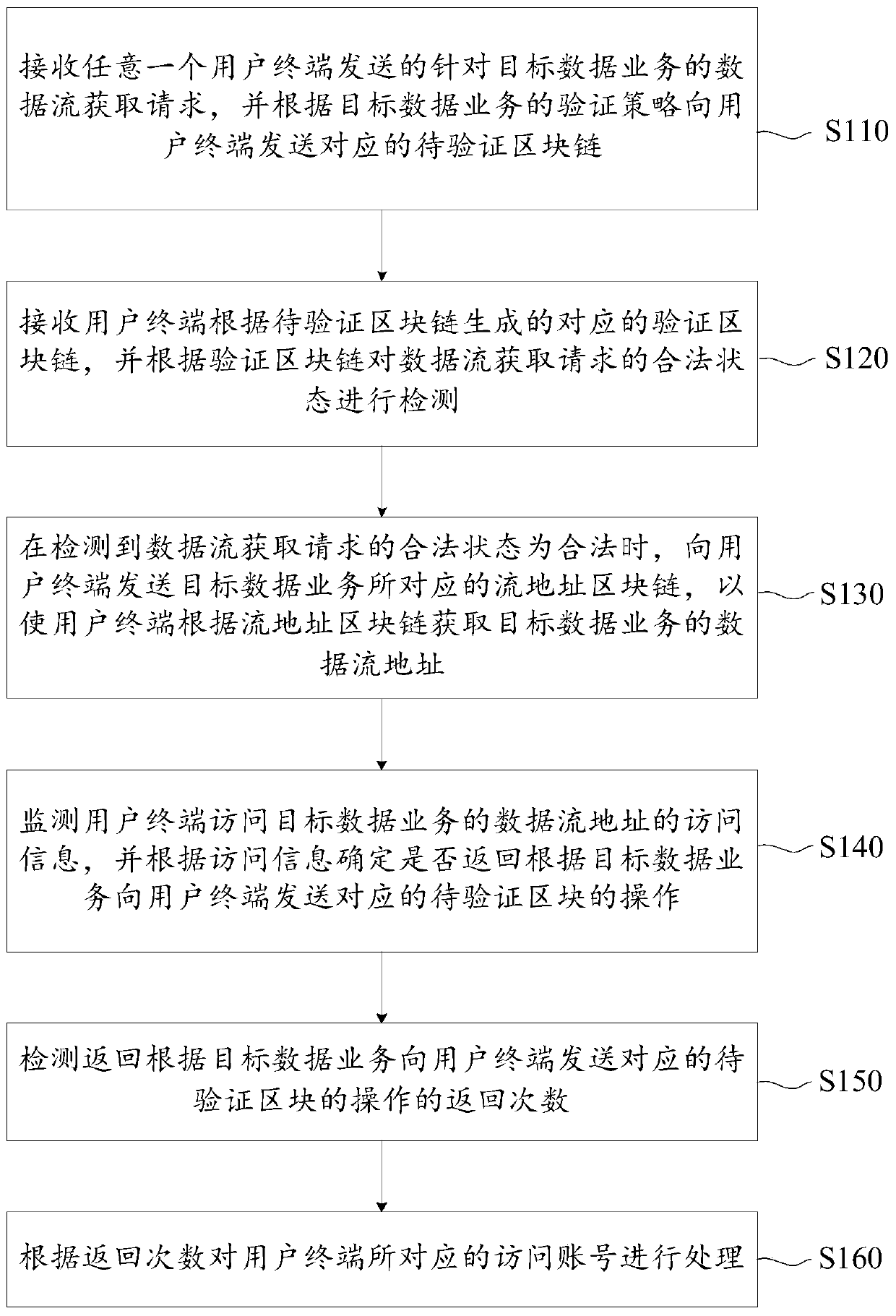
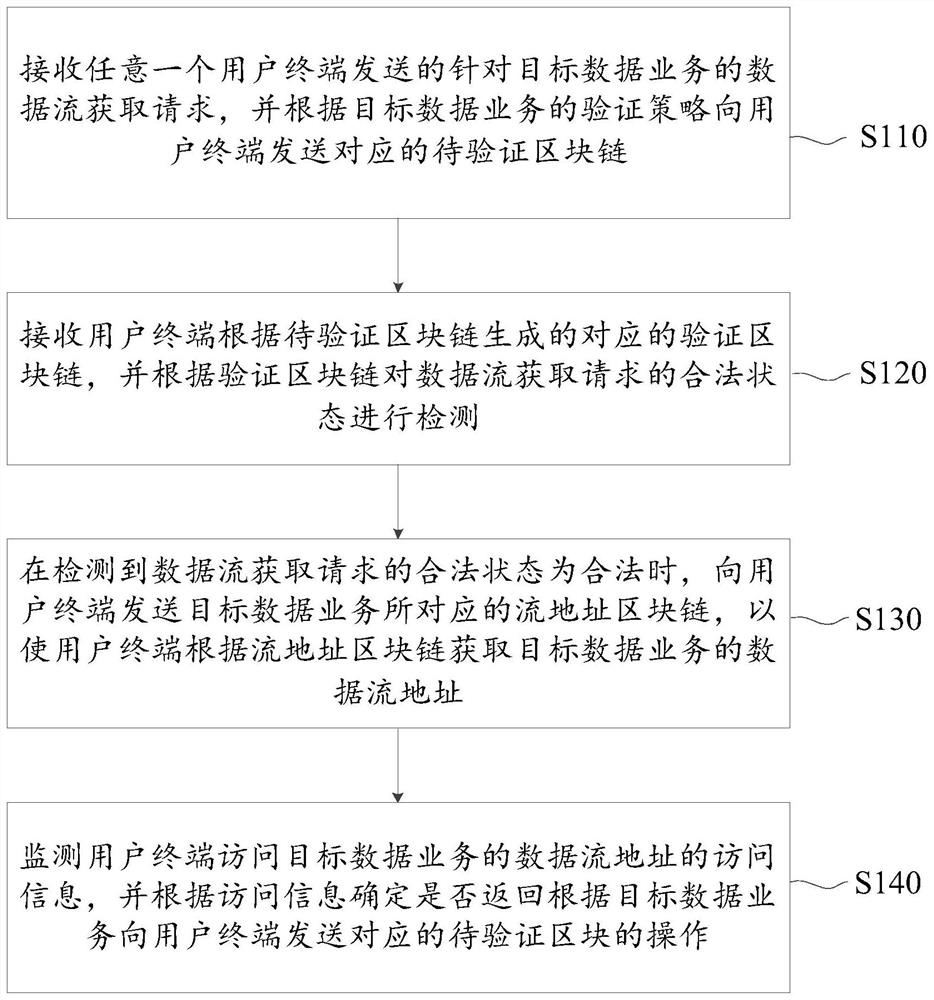
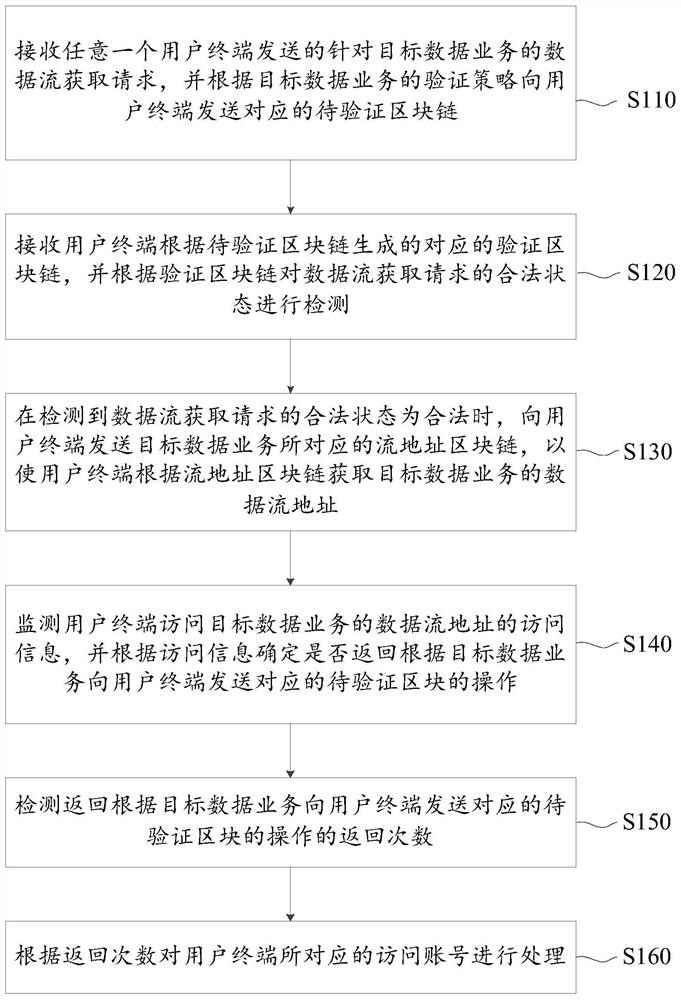
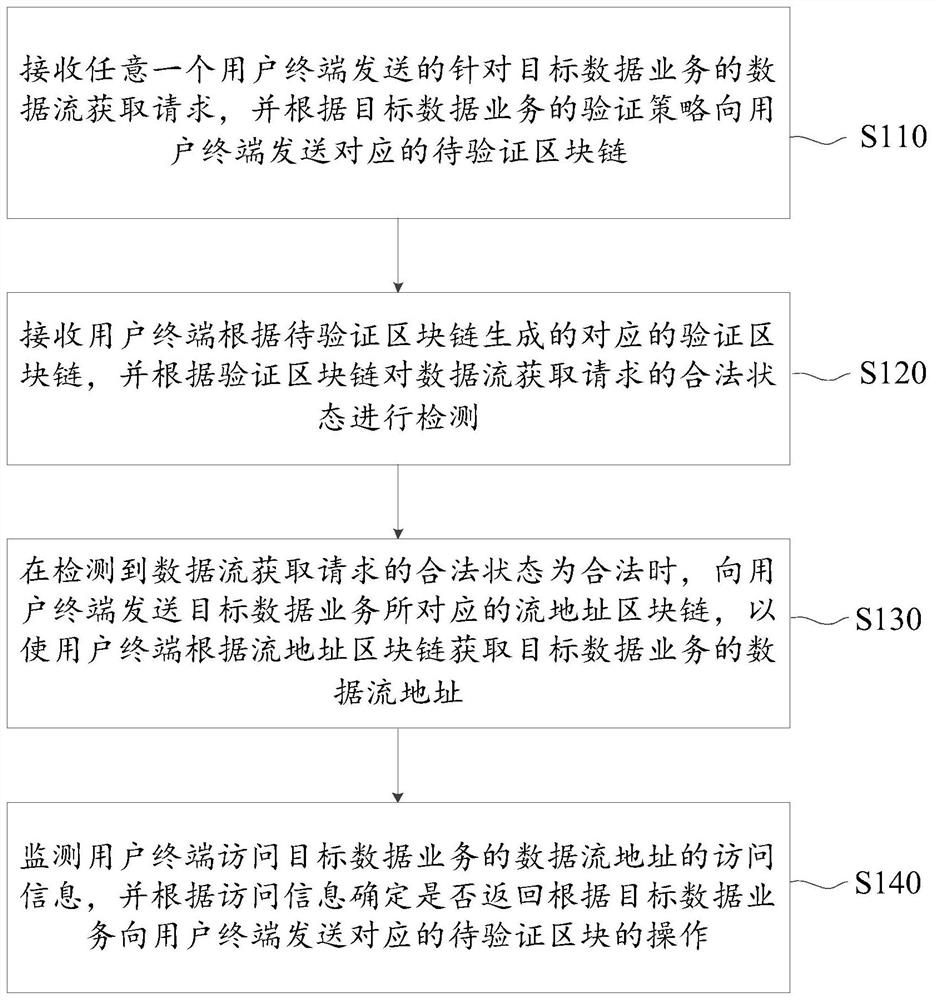
Data flow detection method and device based on block chain and server
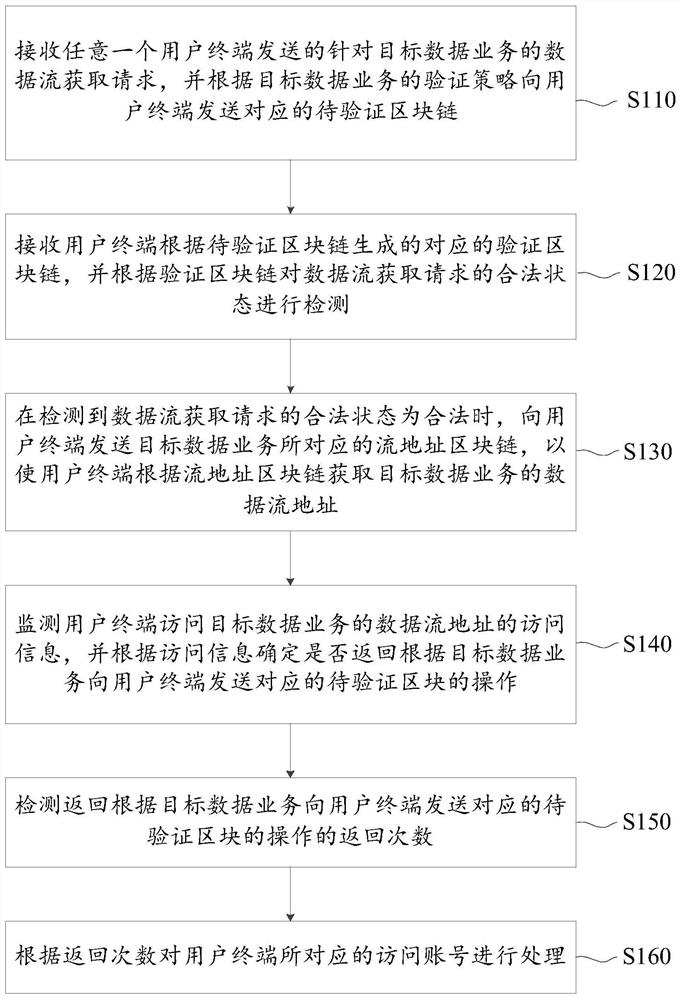
The embodiment of the invention provides a data flow detection method and device based on blockchain and a server. The method comprises the following steps: when the server receives a data stream acquisition request for a target data service sent by a user terminal, generating a to-be-verified blockchain for a verification strategy of a specific target data service, so the difference of differentdata services is considered, and the security and the pertinence of the authentication process are improved; enabling the user terminal to calculate the to-be-verified field according to the blockchain generation field in the to-be-verified block chain to generate a corresponding verification field, wherein because the fields to be verified are randomly added, and the difficulty of cracking by a hacker can be improved; performing lawful state detection after the verification blockchain is formed, allowing the user terminal to access the data stream address of the target data service after thedetection is passed, and repeatedly performing verification by monitoring the access information of the user terminal in real time during the period, so the authentication success rate and the security are further improved.
Owner:重庆浙大网新科技有限公司
Biometric authentication method
InactiveCN101170405AImprove the authentication success rateLow rate of incorrect authenticationUser identity/authority verificationDigital computer detailsBiometric dataInternet privacy
Owner:FUJITSU LTD
Data flow detection method and system based on block chain
The embodiment of the invention provides a data flow detection method and system based on a block chain, and the method comprises the steps: generating a to-be-verified block chain for a verificationstrategy of a specific target data business when a server receives a data flow obtaining request, sent by a user terminal, for the target data business, thereby considering the difference of differentdata businesses, and improving the verification efficiency. Therefore, the security and pertinence of the authentication process are improved, the user terminal can calculate the to-be-verified fieldaccording to the block chain generation field in the to-be-verified block chain to generate the corresponding verification field, and the to-be-verified field is randomly added, so that the difficulty of cracking by a hacker can be improved, the authentication success rate is further improved. And lastly, legal state detection is carried out after the verification block chain is formed, the userterminal is allowed to access the data stream address of the target data service after the detection is passed, and verification is repeatedly carried out by monitoring the access information of the user terminal in real time during the period, so that the authentication success rate and security are further improved.
Owner:朱培培
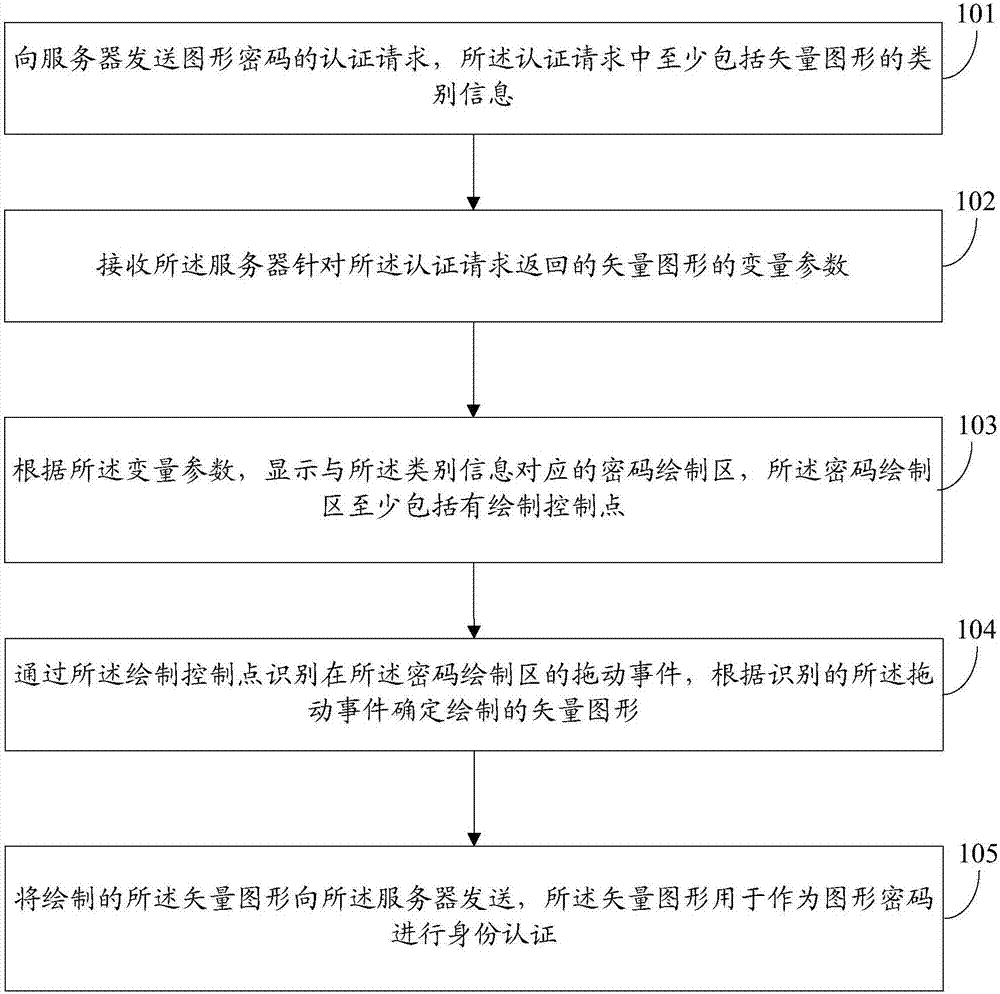
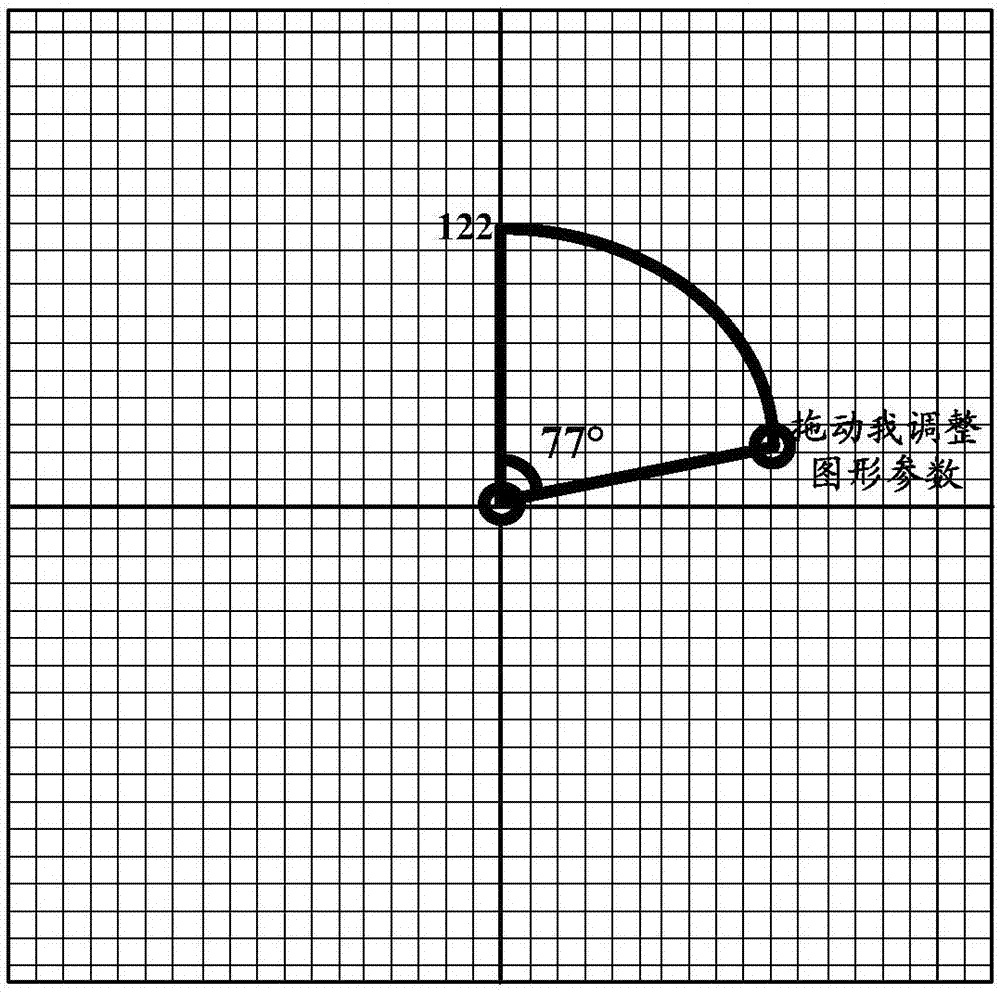
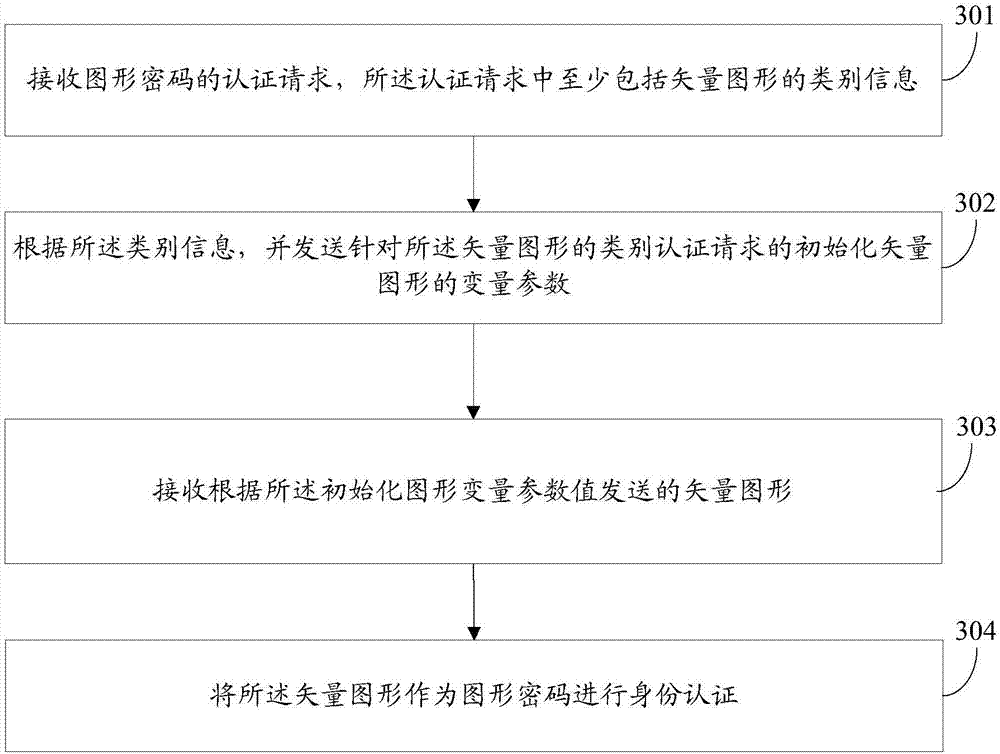
Graphical password authentication method, graphical password authentication device and storage medium
ActiveCN108009419AImprove the authentication success rateEasy to operateDigital data authenticationTransmissionPasswordAuthentication
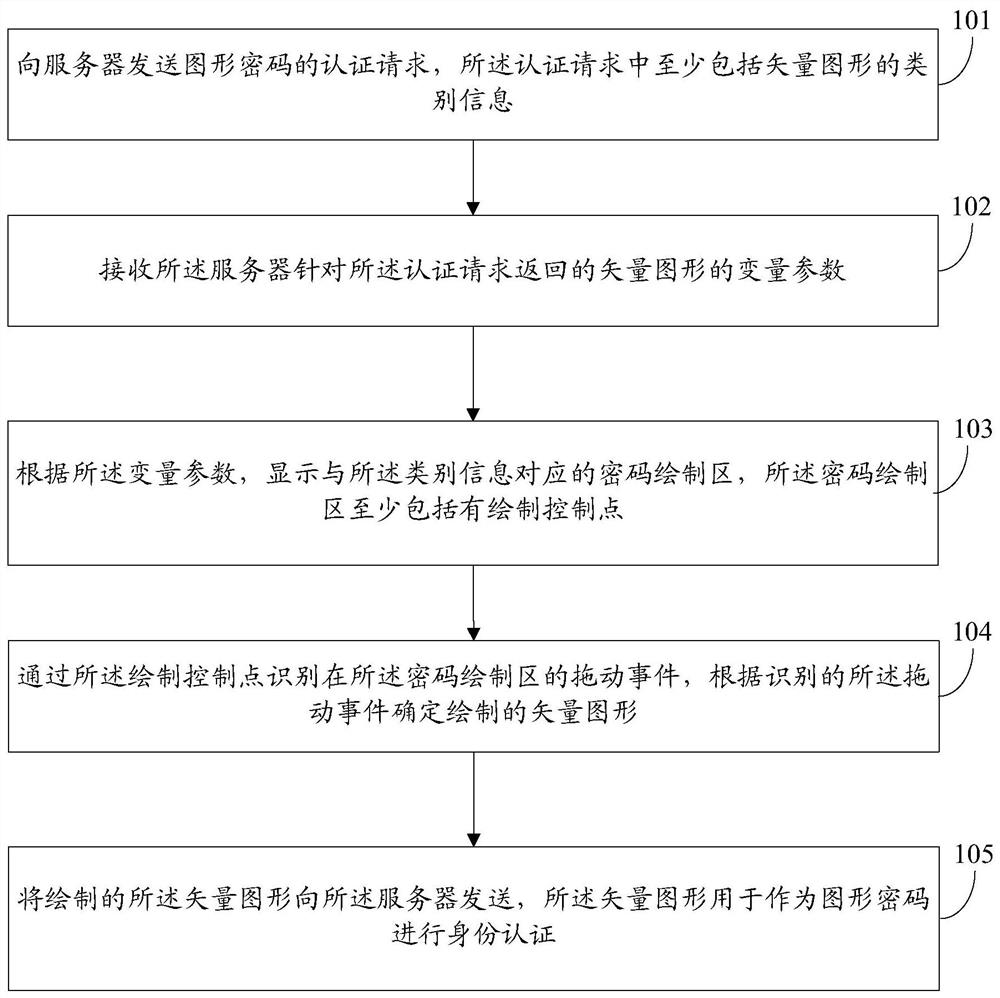
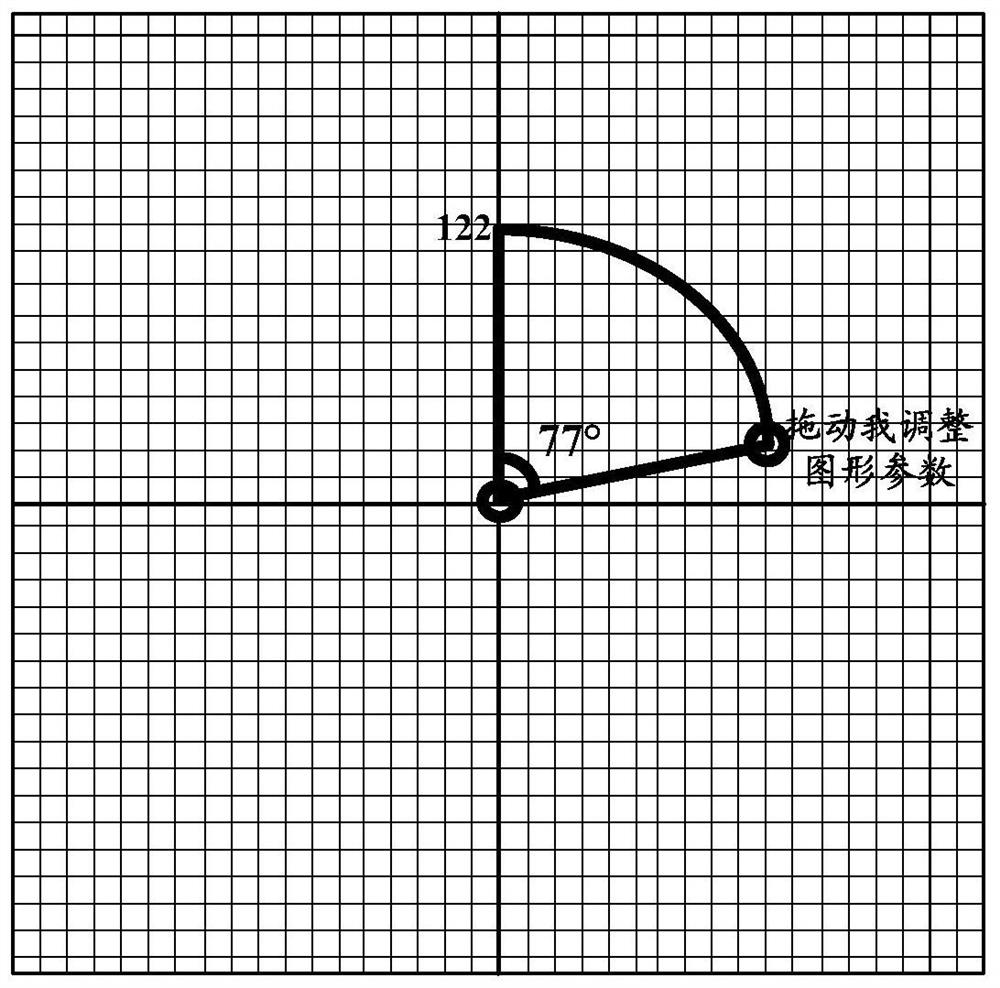
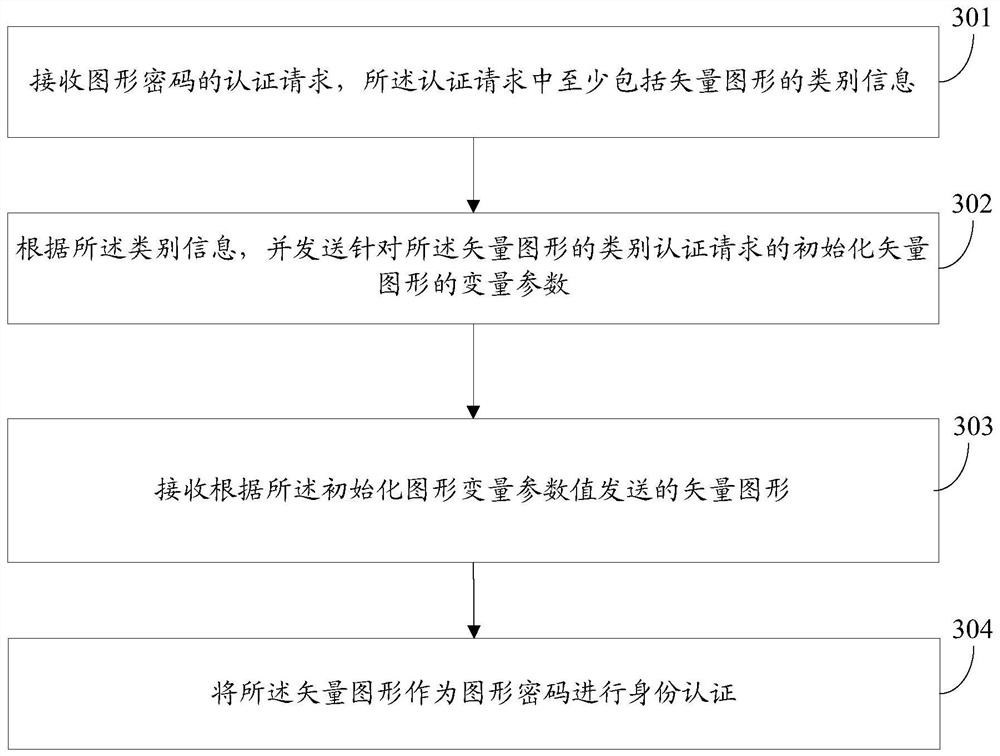
The invention discloses a graphical password authentication method which includes the steps: transmitting a graphical password authentication request to a server; receiving variable parameters of vector graphics returned by the server according to the authentication request; displaying a password drawing area corresponding to class information according to the variable parameters; recognizing a dragging event in the password drawing area by a drawing control point and determining a drawn vector graphic according to the recognized dragging event; transmitting the drawn vector graphic to the server. The authentication request at least comprises the class information of the vector graphics, the password drawing area at least comprises the drawing control point, and the vector graphics are used as graphical passwords for identity authentication. The invention further provides a graphical password authentication device and a storage medium.
Owner:MIGU CO LTD +1
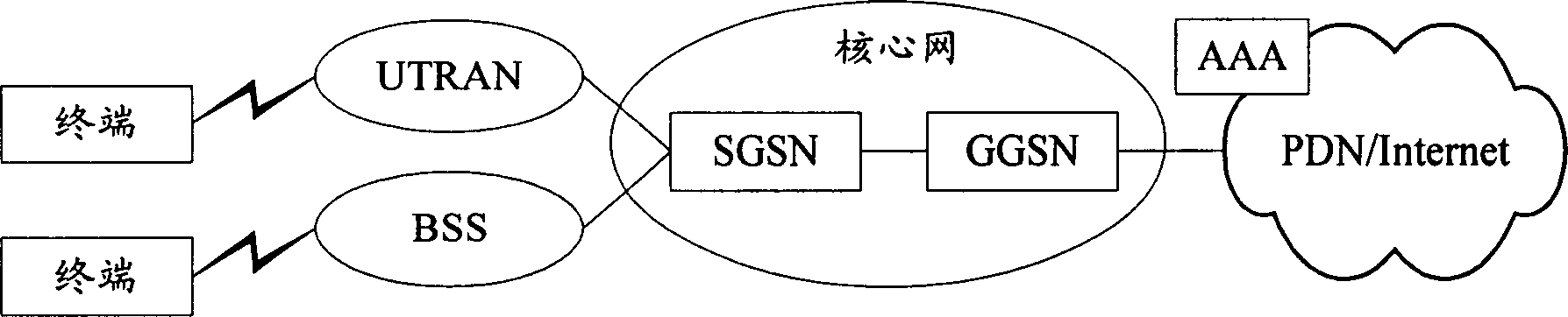
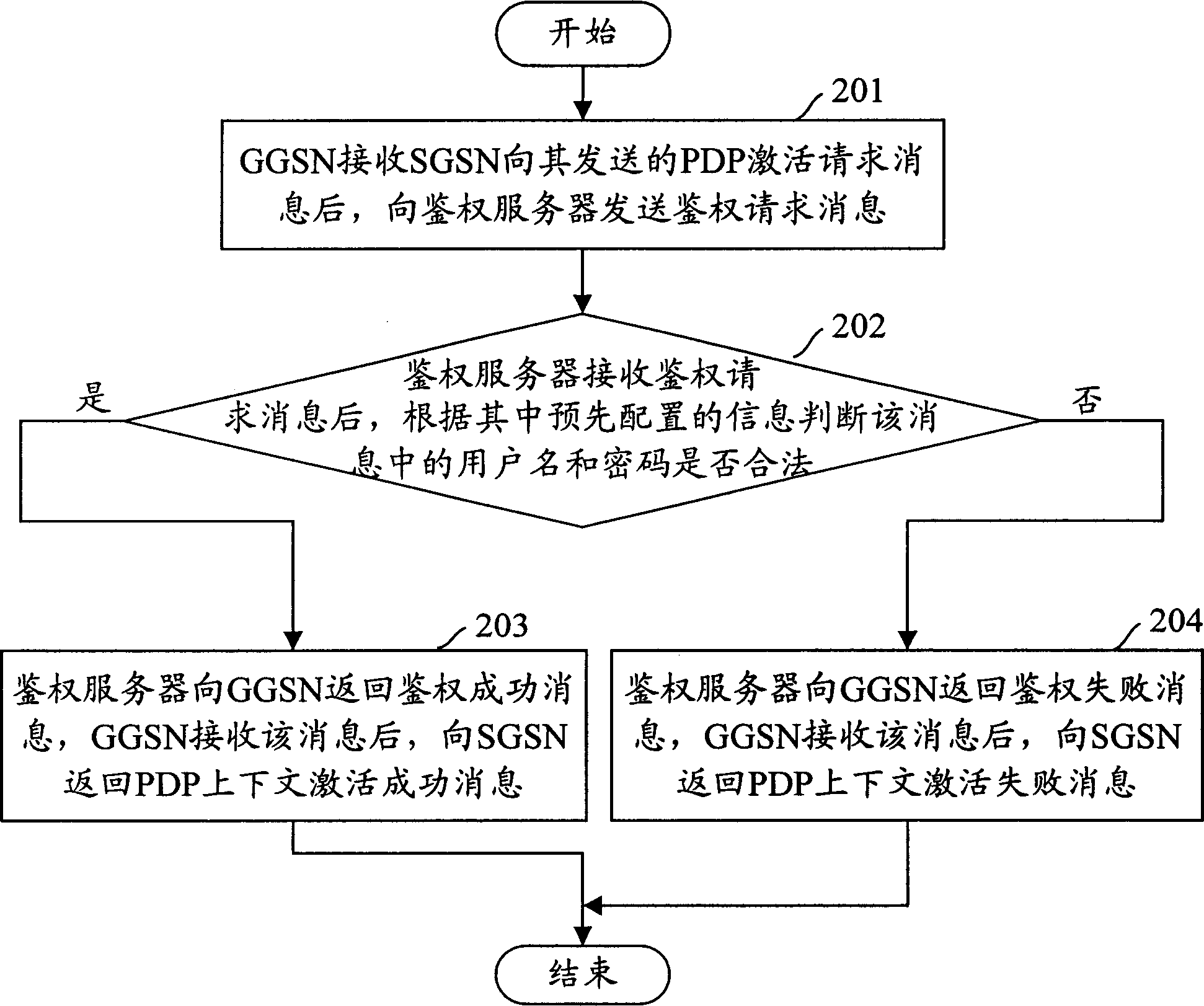
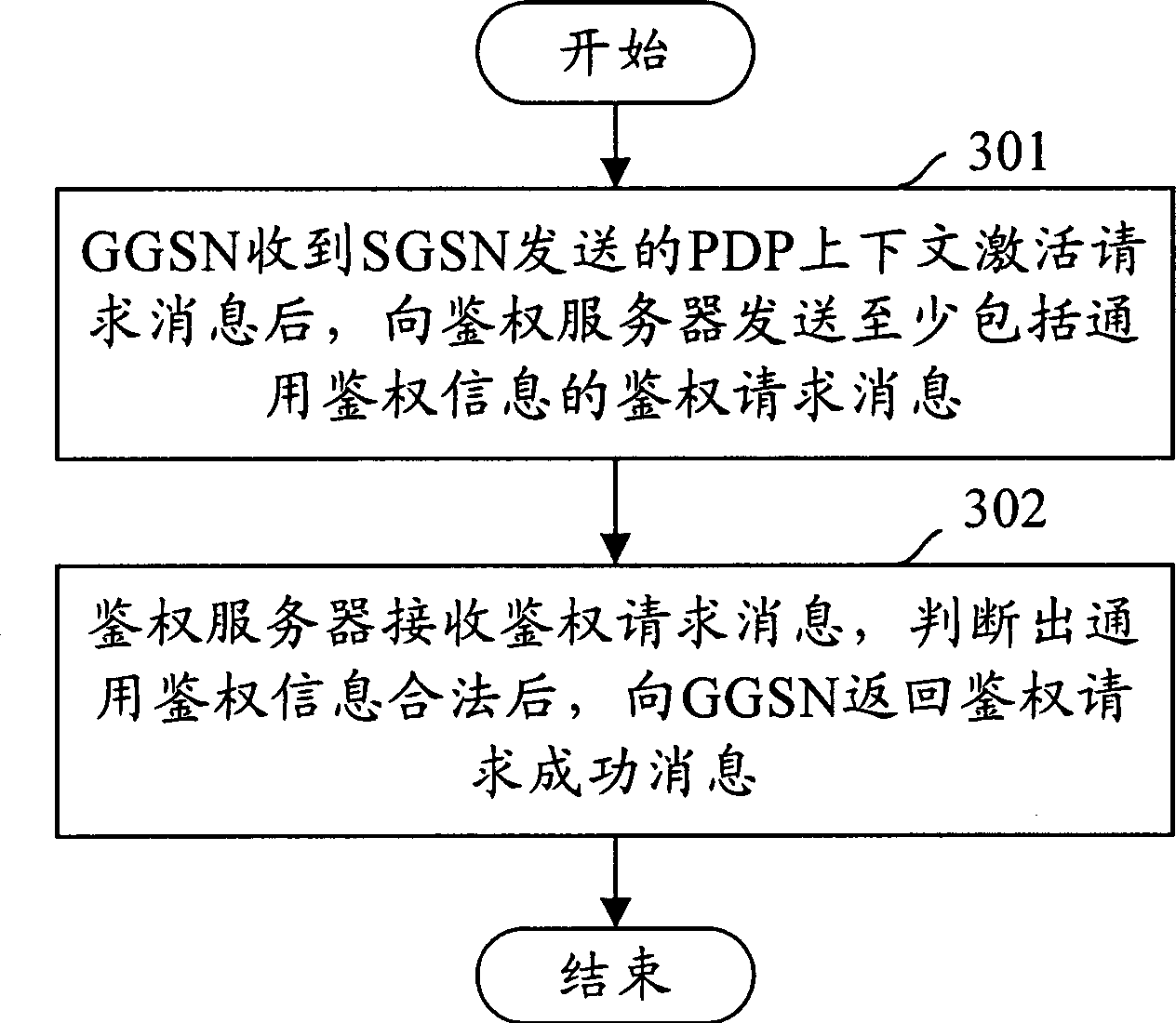
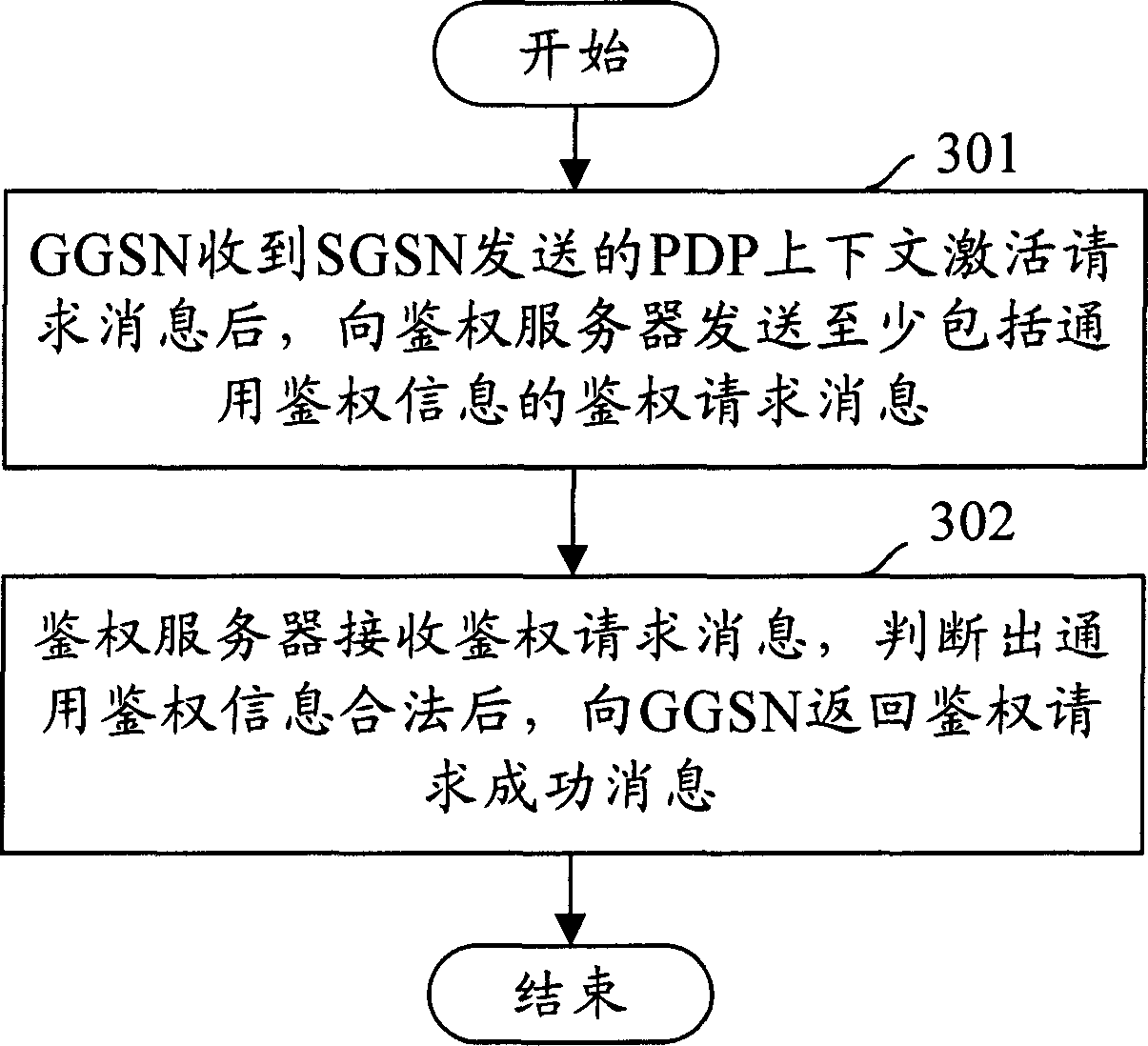
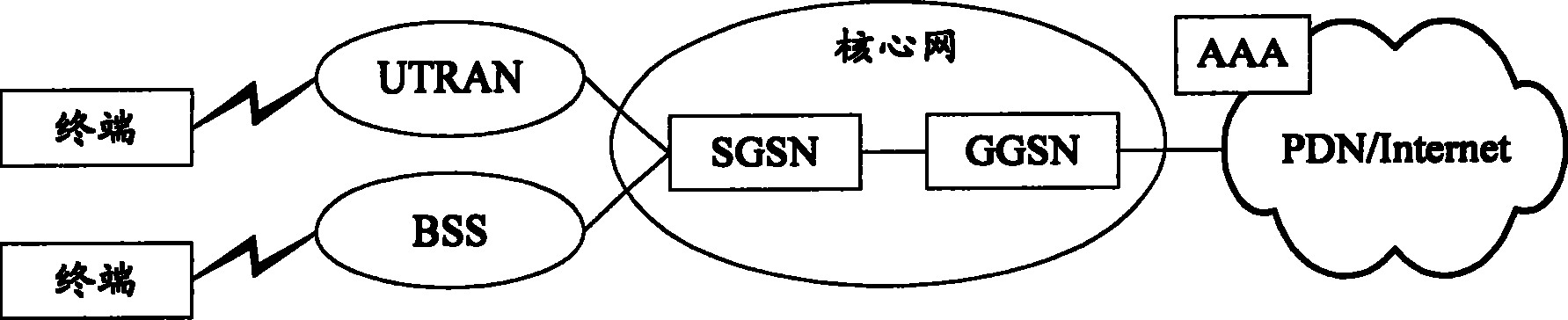
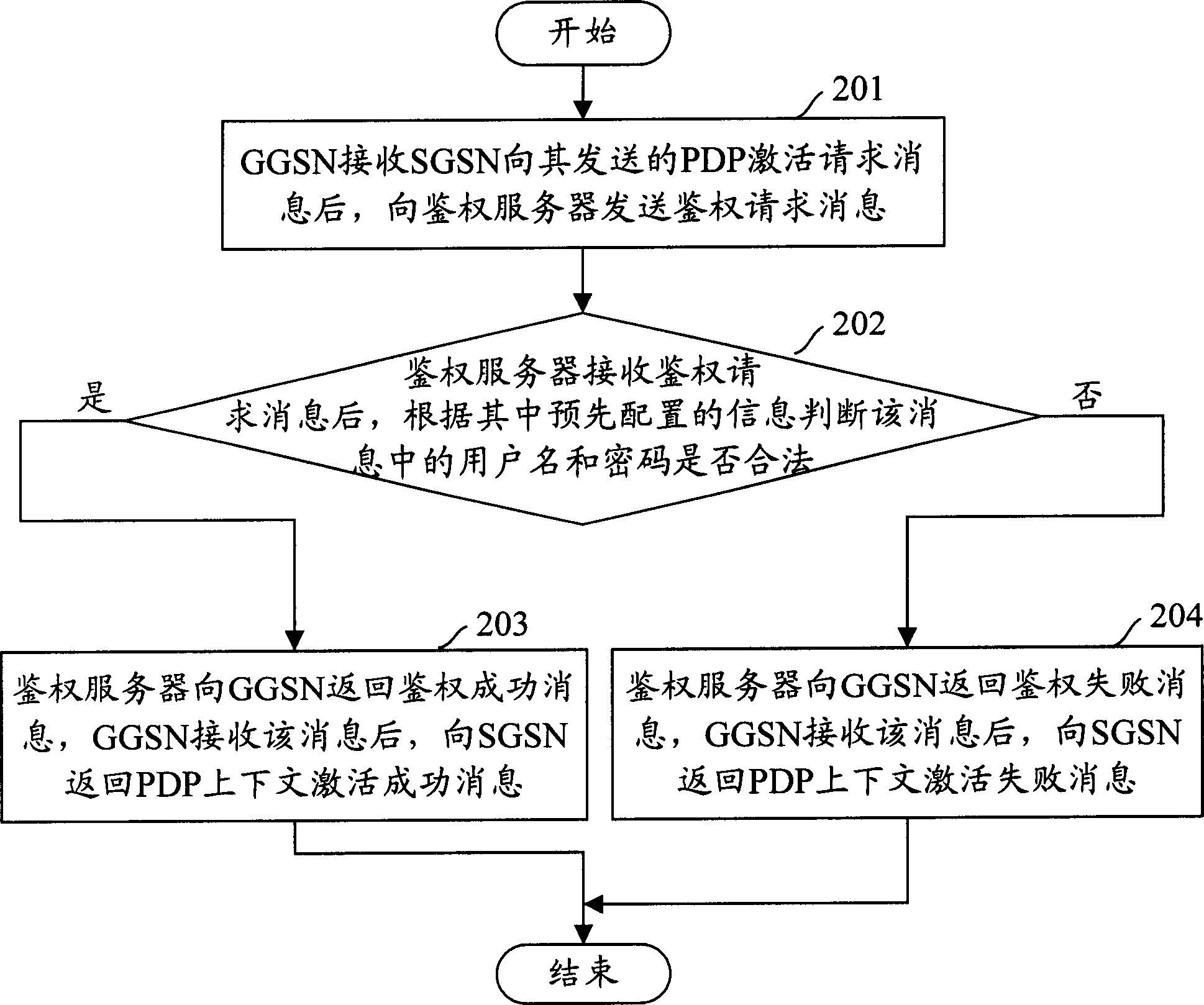
Method for identifying authority in wireless group business
ActiveCN1815956AImprove satisfactionIncrease incomeUser identity/authority verificationAuthentication serverAuthentication information
The method sets up general authentication information in GGSN and authentication server in advance. The method also includes following steps: after receiving PDP request message for activating context, based on general authentication information setup in GGSN, GGSN sends out message for requesting authentication including general authentication information to authentication server; after receiving message for requesting authentication, the authentication server determines validity of the general authentication information, and then returns back successful message of request to GGSN. The invention sets up general authentication information in GGSN and authentication server. The said general information is included in message of request sent by GGSN to the authentication server. Thus, success ratio of authentication is increased greatly so as to raise satisfying degree and increase earning of operation manager.
Owner:HUAWEI TECH CO LTD
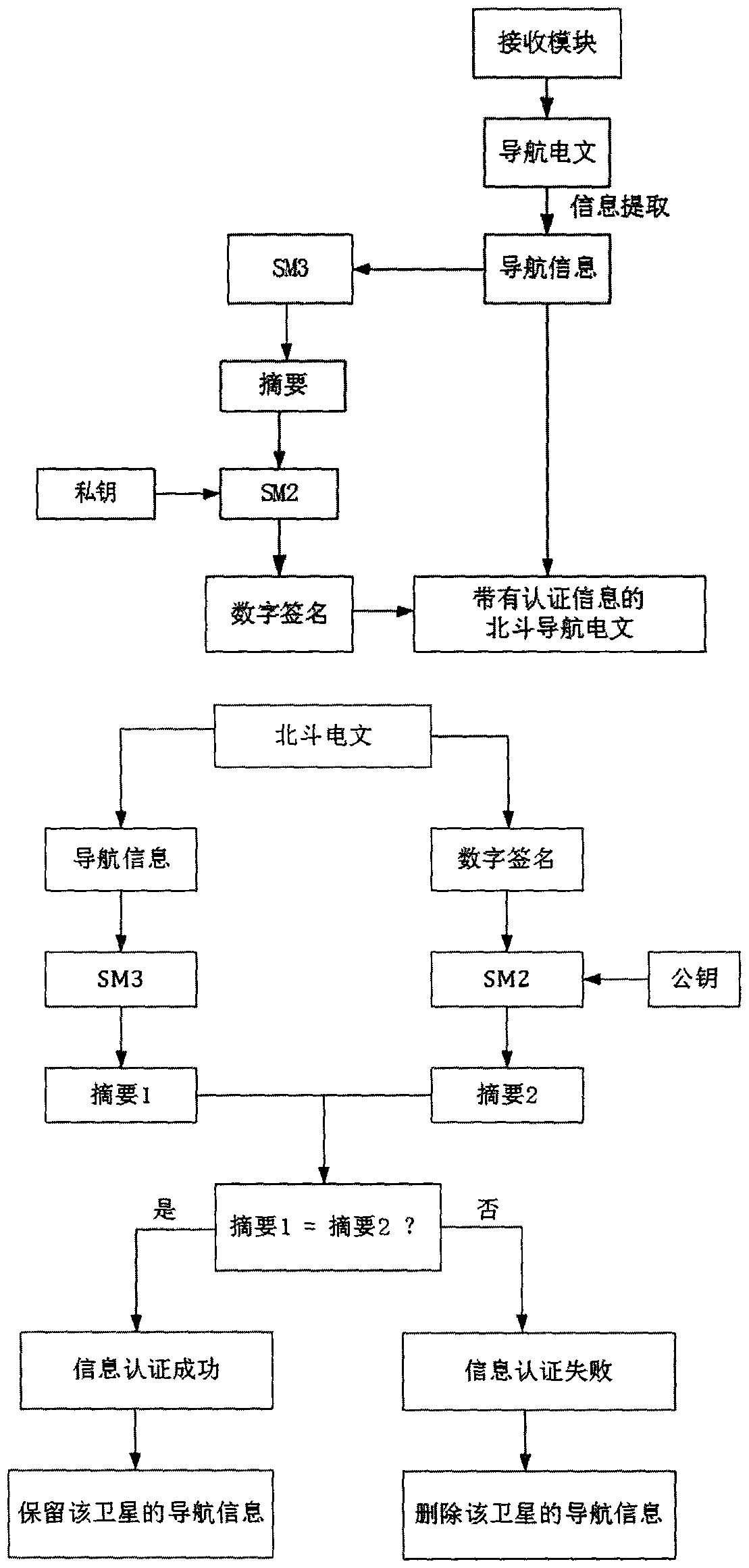
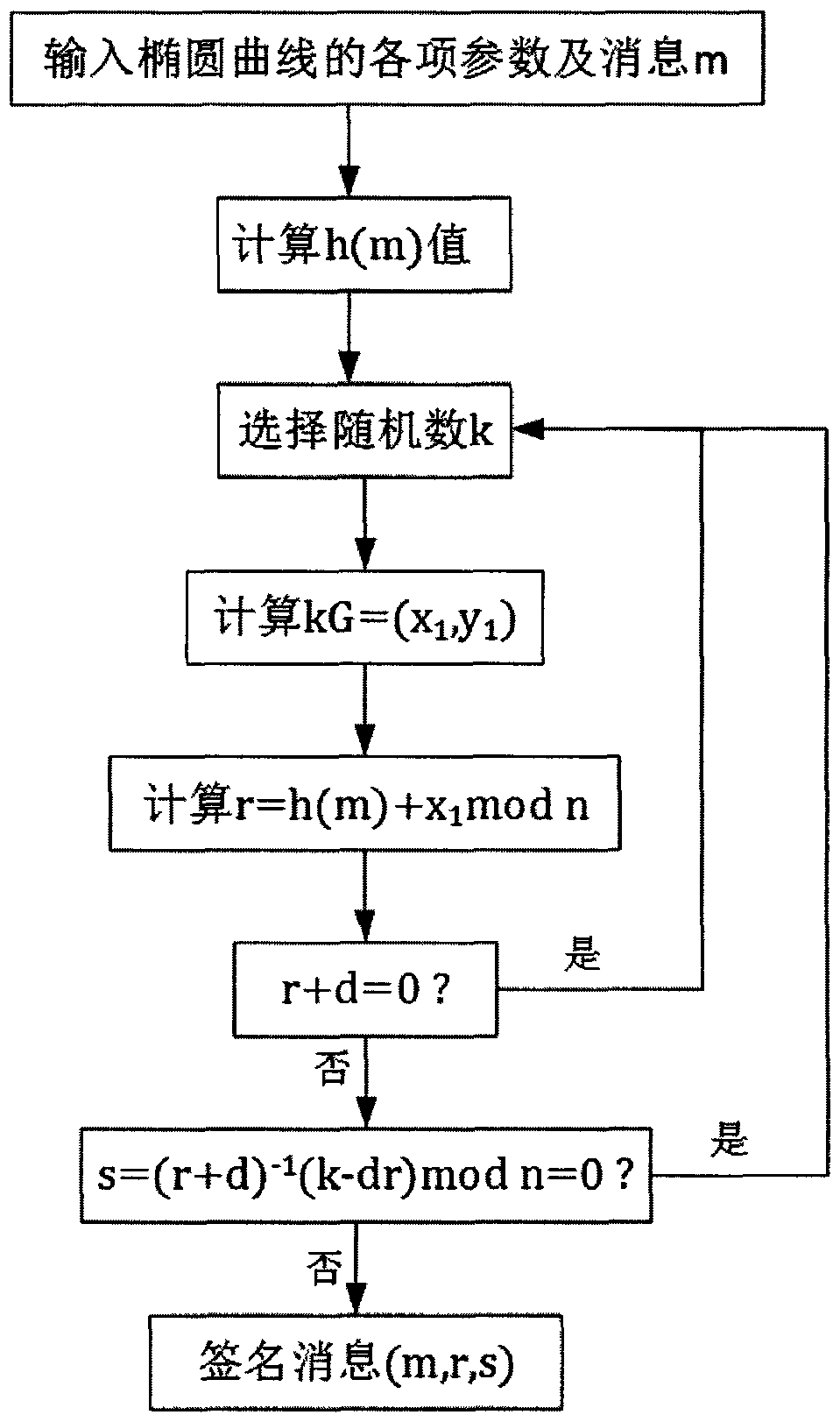
Beidou second-generation navigation message digital signature anti-cheating scheme based on domestic passwords
PendingCN109633693AOvercome the flaw of being easily deceivedImprove the authentication success rateSatellite radio beaconingInformation processingDigital signature
The invention relates to the technical field of information safety, and provides a Beidou second-generation navigation message digital signature anti-cheating scheme based on domestic passwords. A Beidou second-generation satellite navigation system in China is lack of research in the aspect of information anti-cheating, and a domestic cryptographic algorithm which is developed independently in China is adopted by the scheme, so that the authenticity and integrity of Beidou signals are guaranteed, and the purpose of anti-cheating of satellite signals is achieved. According to the method, secret key management of a public key is carried out through SM4, SM3 provides abstract information for a digital signature generated by a SM2, SM2 domestic asymmetric elliptic curve public key cryptographic algorithm is used for generating the digest information, and the digital signature receiver can authenticate the abstract through the public key to verify whether Beidou second-generation navigation message is deception. The method is effectively utilized in the field of information system safety, and experiments show that the code scheme can be realized through a computer information processing module through an OpenSSl and VisualStudio combined pair scheme, and the experiment result shows that the safety of the Beidou second-generation navigation message can be effectively improved.
Owner:CIVIL AVIATION UNIV OF CHINA
Mobile terminal and serial authentication method thereof in WCDMA network
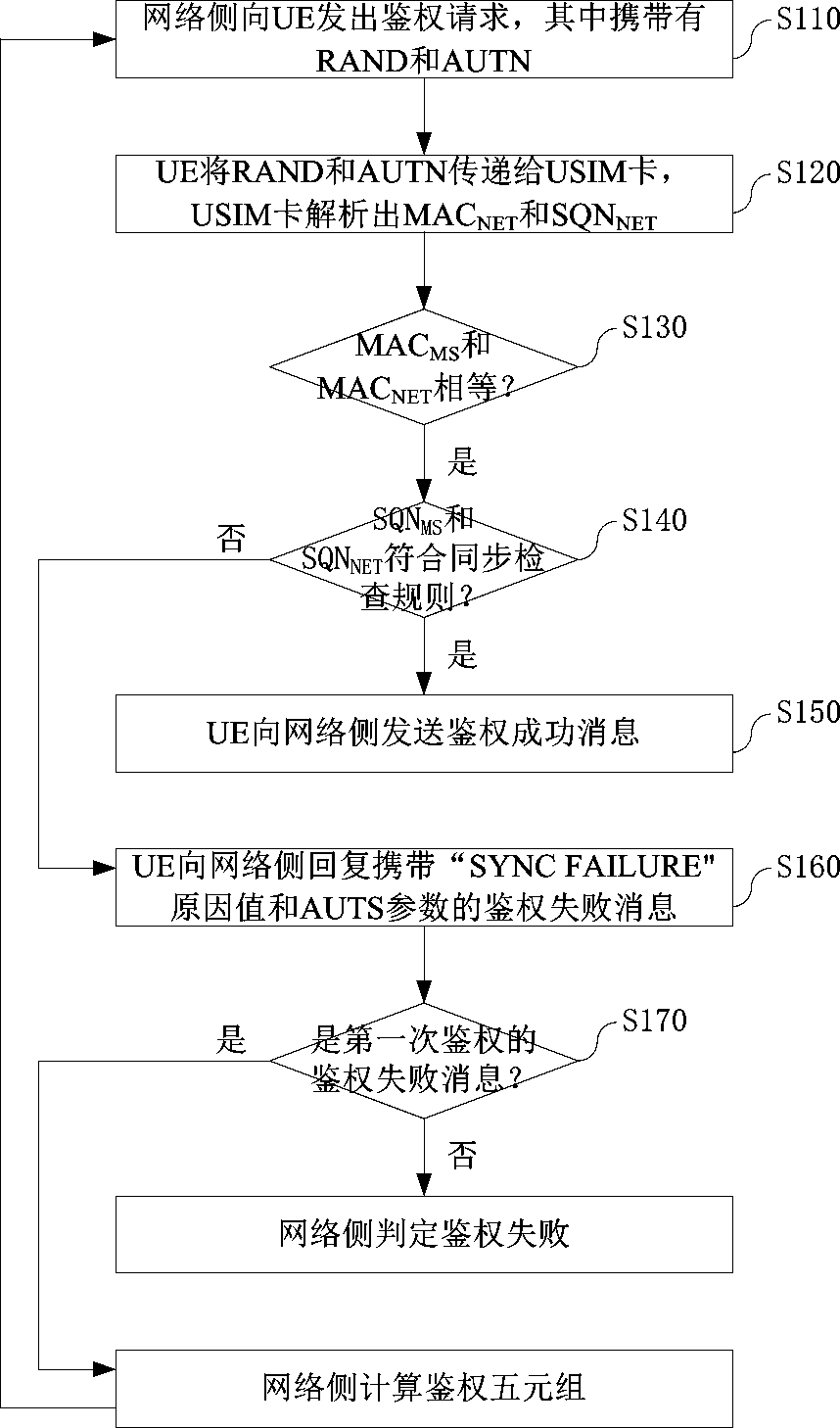
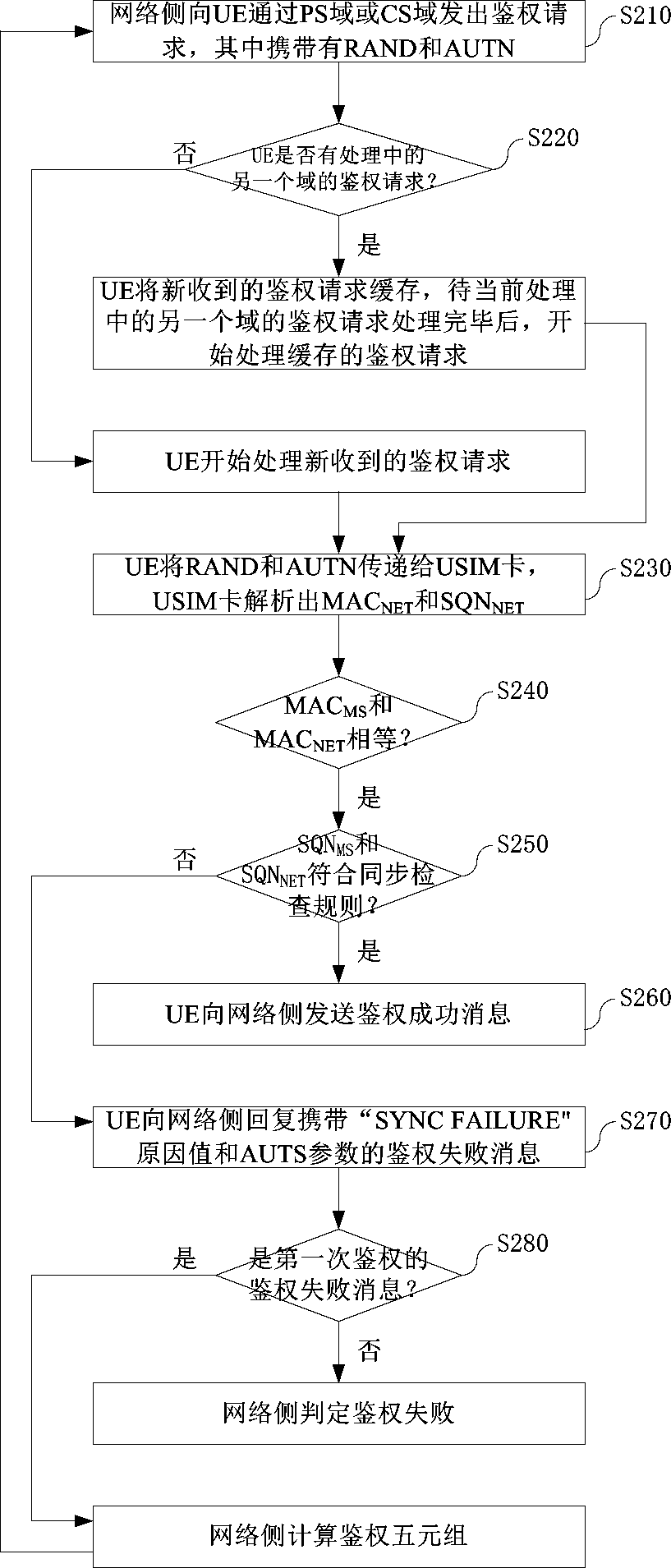
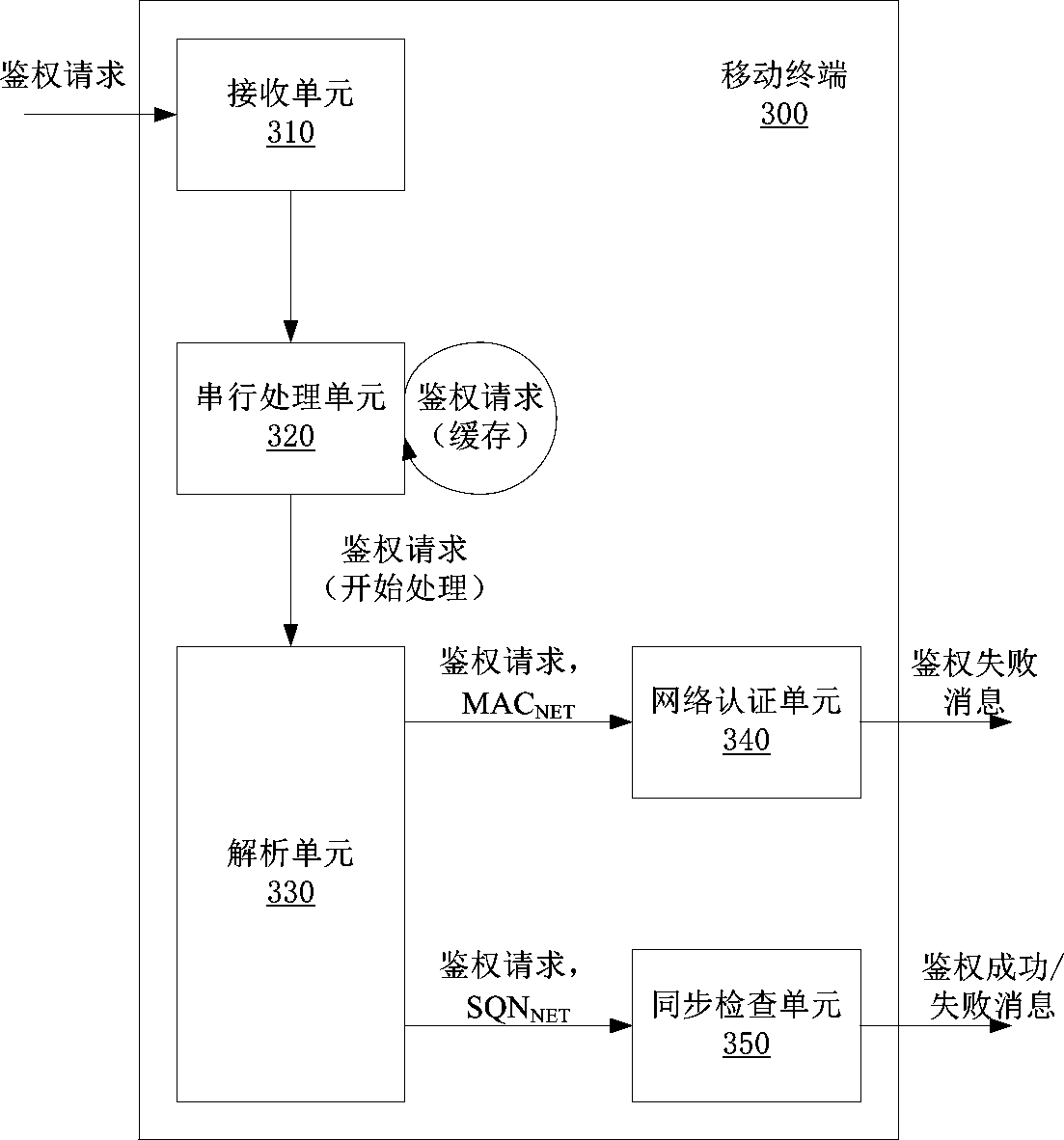
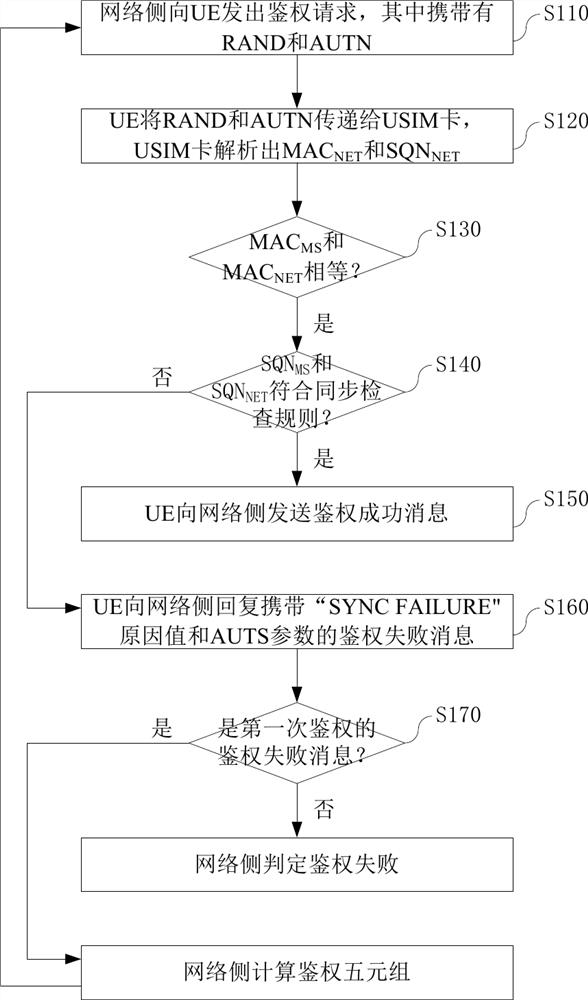
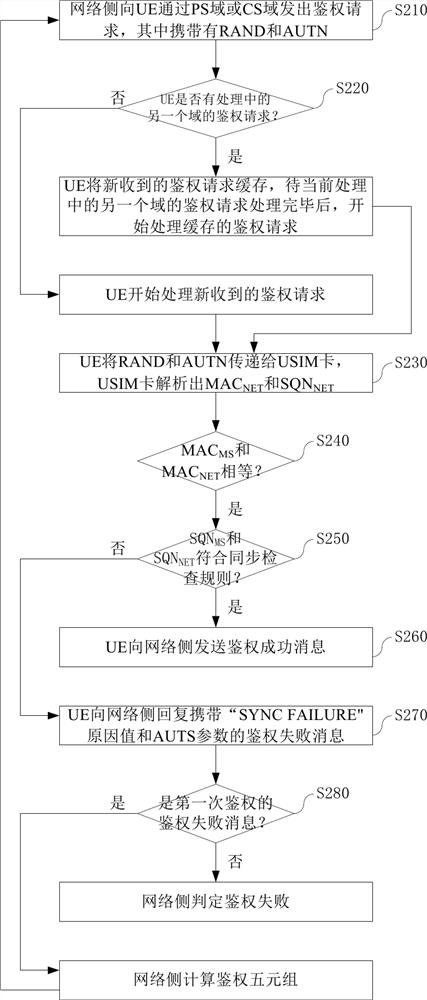
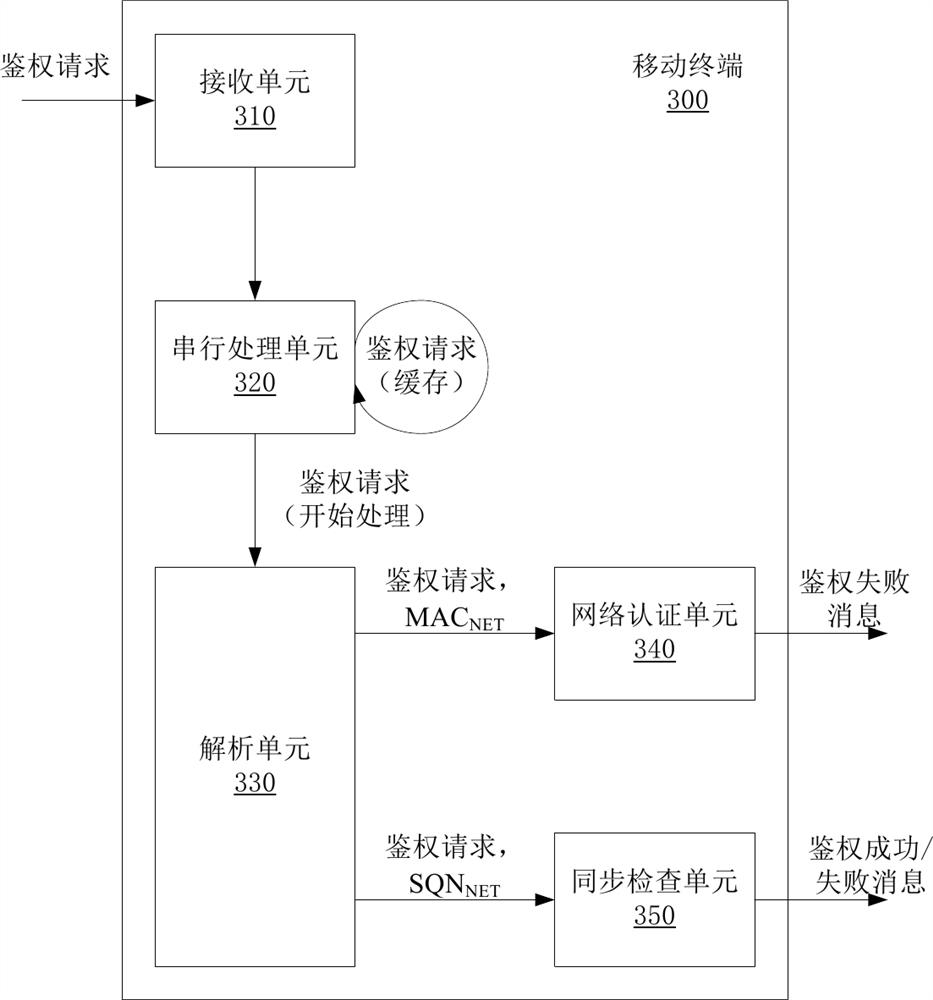
ActiveCN111182534AImprove the authentication success rateLow costSecurity arrangementEngineeringAuthentication
The invention discloses a serial authentication method of a mobile terminal in a WCDMA network. The network side sends an authentication request to the mobile terminal through a PS domain or a CS domain. If a first network parameter equals a first local parameter, a USIM card judges a second network parameter and a second local parameter according to a synchronization check rule. If checking is passed, the mobile terminal sends an authentication success message to the network side. If checking fails, the mobile terminal replies an authentication failure message with specific failure reasons and parameters to the network side. The network side recalculates the authentication quintuple after receiving the authentication failure message of the first authentication, and then initiates a secondauthentication request through the same domain. A serial processing mode is adopted for the authentication requests of the PS domain and the CS domain, so that the authentication success rate of themobile terminal to the network side is greatly improved.
Owner:ASR MICROELECTRONICS CO LTD
Authentication method, device and system in IMS network
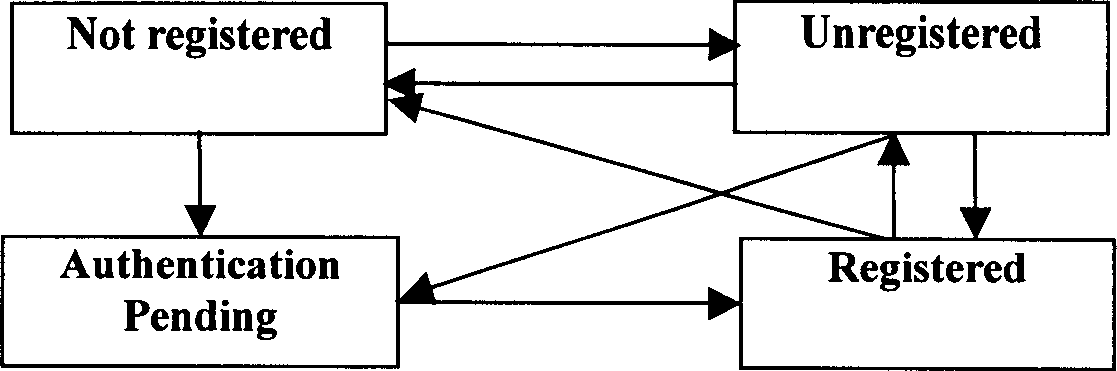
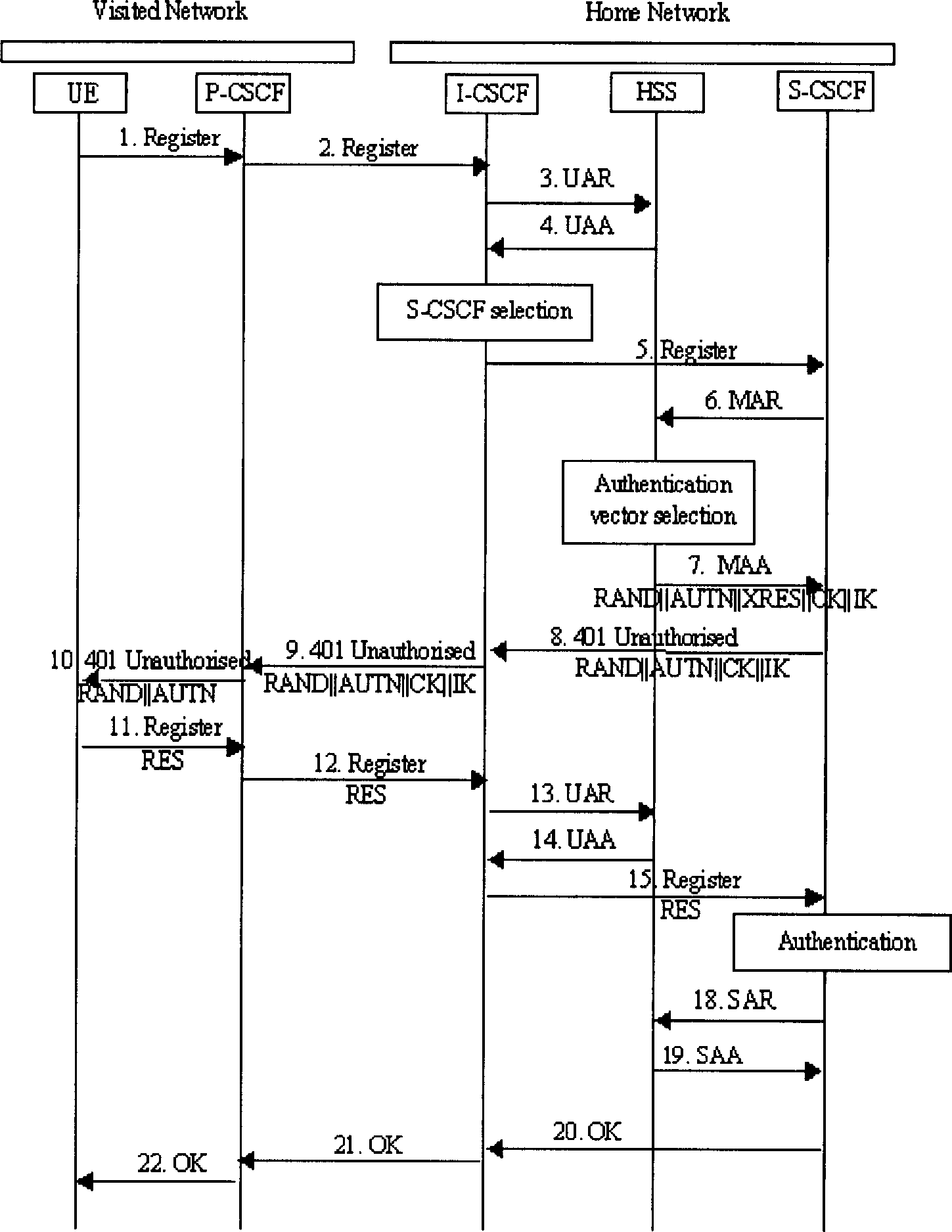
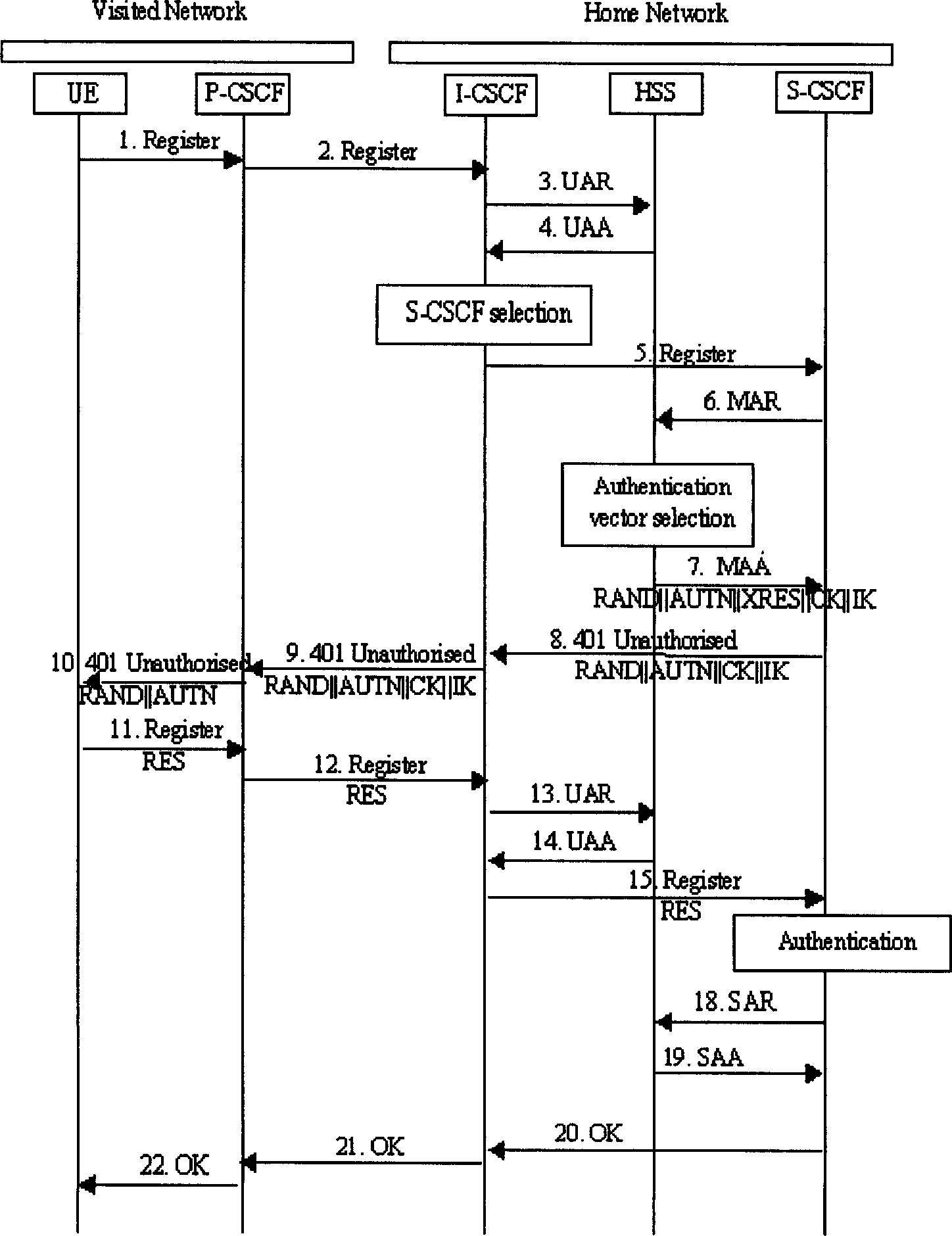
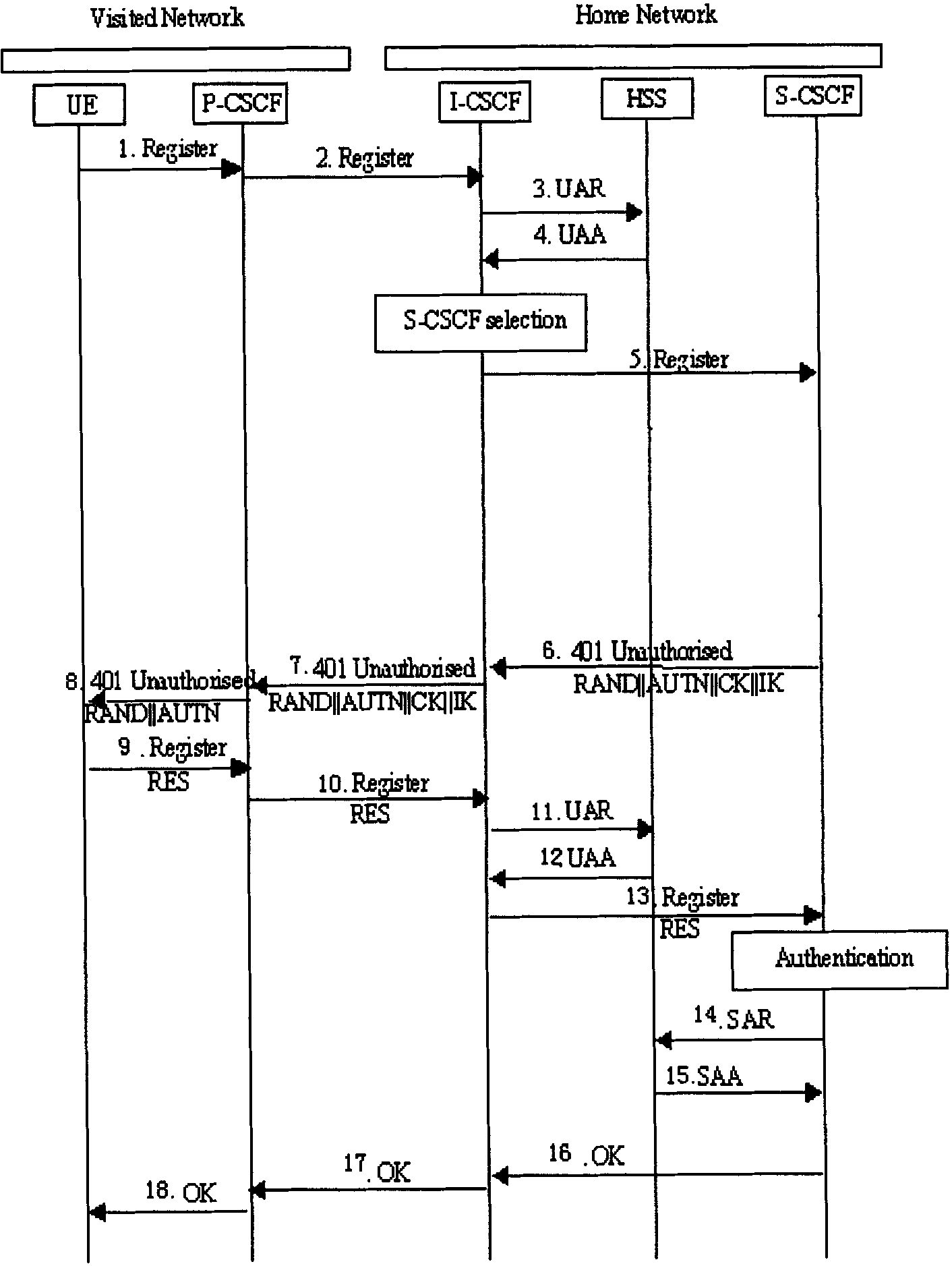
InactiveCN1866823ASave computing resourcesImprove the efficiency of first-time registrationUser identity/authority verificationComputer scienceAuthentication
The invention discloses an identifying weight method, device and system of IBM network, which comprises the following steps: using identifying weight information for UE identifying weight using which saves by S-CSCF itself; finishing UE and IMS network identifying weight processing procedure; registrating UE whose registration state is Unregistered and S-CSCF saves identifying weight information; providing dentifying weight scheme accomplish flow process of UE application identifying weight quintuple which can neglect S-CSCF and flow to HSS through MAR, MAA. The invention reduces MAR, MAA information source commutation, which optimizes identifying weight flow path of UE first registration.
Owner:HUAWEI TECH CO LTD
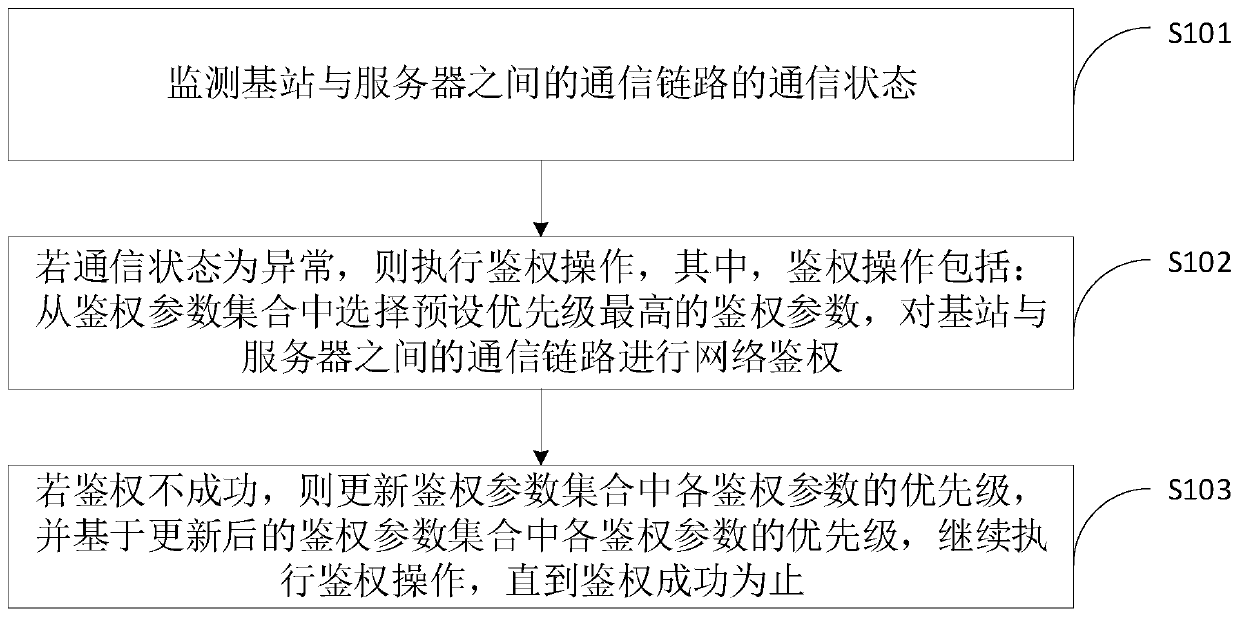
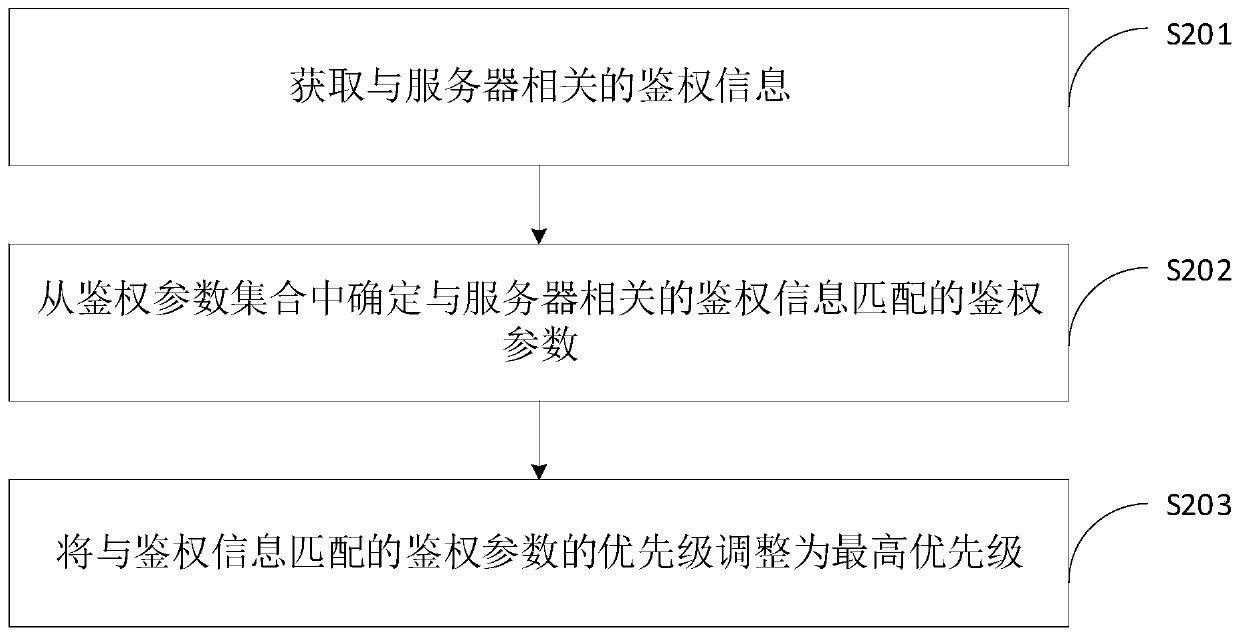
Network authentication method and device, computer equipment and storage medium
PendingCN111148102AEnsure safetyImprove stabilitySecurity arrangementTelecommunications linkComputer equipment
The invention relates to a network authentication method and device, computer equipment and a storage medium. The method comprises the following steps: monitoring a communication state of a communication link between a base station and a server; if the communication state is abnormal, executing authentication operation, wherein the authentication operation comprises the steps that an authentication parameter with the highest preset priority is selected from an authentication parameter set, and network authentication is conducted on a communication link between the base station and the server;and if the authentication is not successful, the priority of each authentication parameter is updated in the authentication parameter set, and the authentication operation is continued to execute based on the updated priority of each authentication parameter in the authentication parameter set until the authentication is successful. According to the authentication method, an automatic authentication process is realized, and compared with an existing network authentication method needing manual intervention for manual operation, the network authentication method provided by the invention greatly shortens the link recovery time of network interruption between the base station and the server, so that the stability of network operation is ensured.
Owner:COMBA TELECOM SYST CHINA LTD
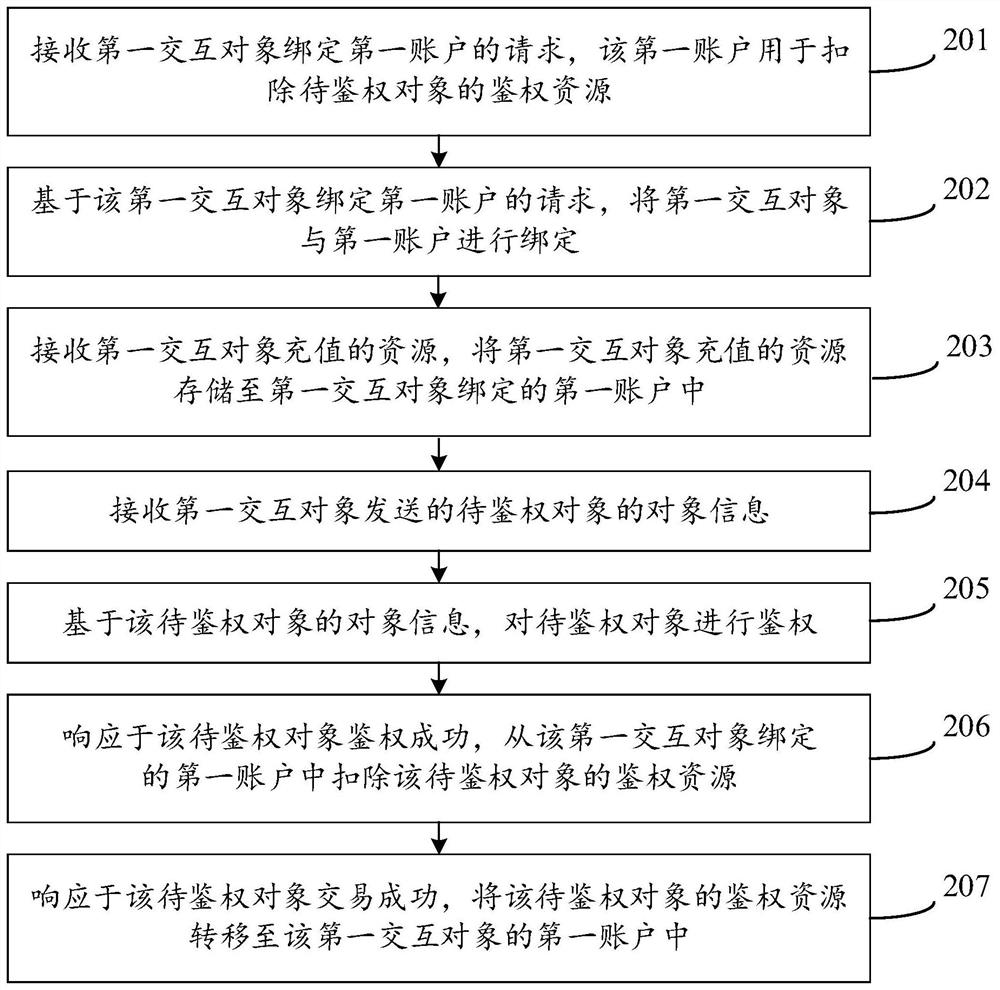
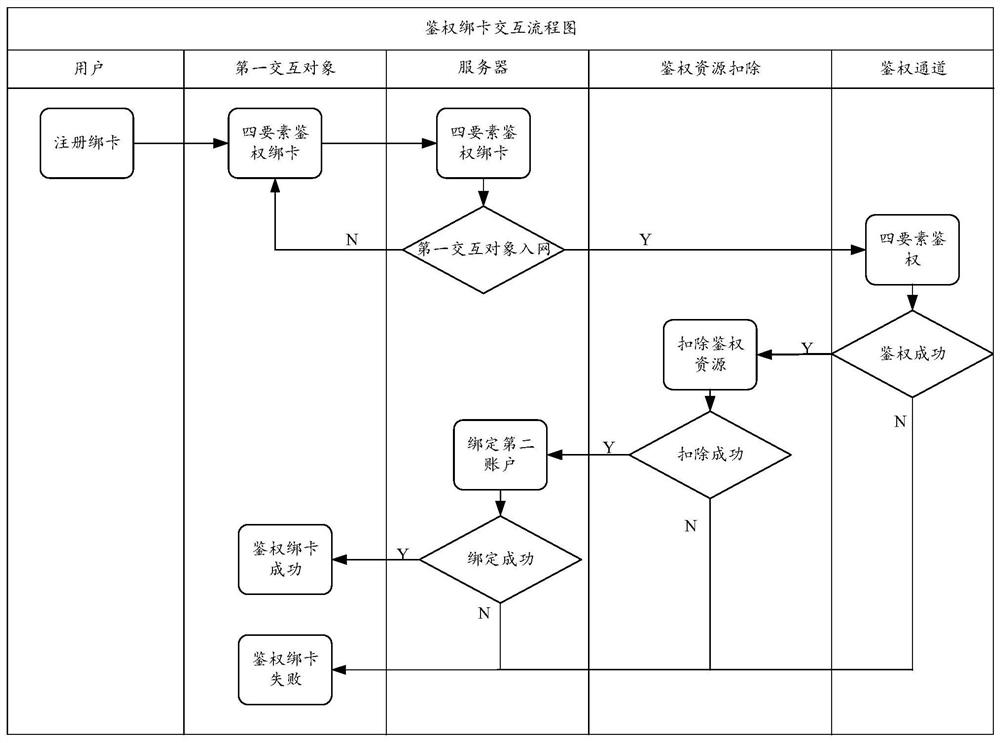
Resource transfer method and device, server and computer readable storage medium
The invention discloses a resource transfer method and device, a server and a computer readable storage medium, and belongs to the technical field of the Internet. The method comprises the following steps: receiving a request of binding a first interaction object with a first account; binding the first interaction object with the first account based on the request of binding the first interactionobject with the first account; receiving resources recharged by the first interaction object, and storing the resources recharged by the first interaction object into a first account bound with the first interaction object; receiving object information of a to-be-authenticated object sent by the first interaction object; authenticating the to-be-authenticated object based on the object informationof the to-be-authenticated object; in response to successful authentication of the to-be-authenticated object, deducting authentication resources of the to-be-authenticated object from a first account bound with the first interaction object; and in response to successful transaction of the to-be-authenticated object, transferring the authentication resource of the to-be-authenticated object to the first account of the first interaction object. According to the method, the accuracy and reliability of the authentication result can be improved, and the authentication success rate is improved.
Owner:BEIJING SANKUAI ONLINE TECH CO LTD
Terminal authentication method and server
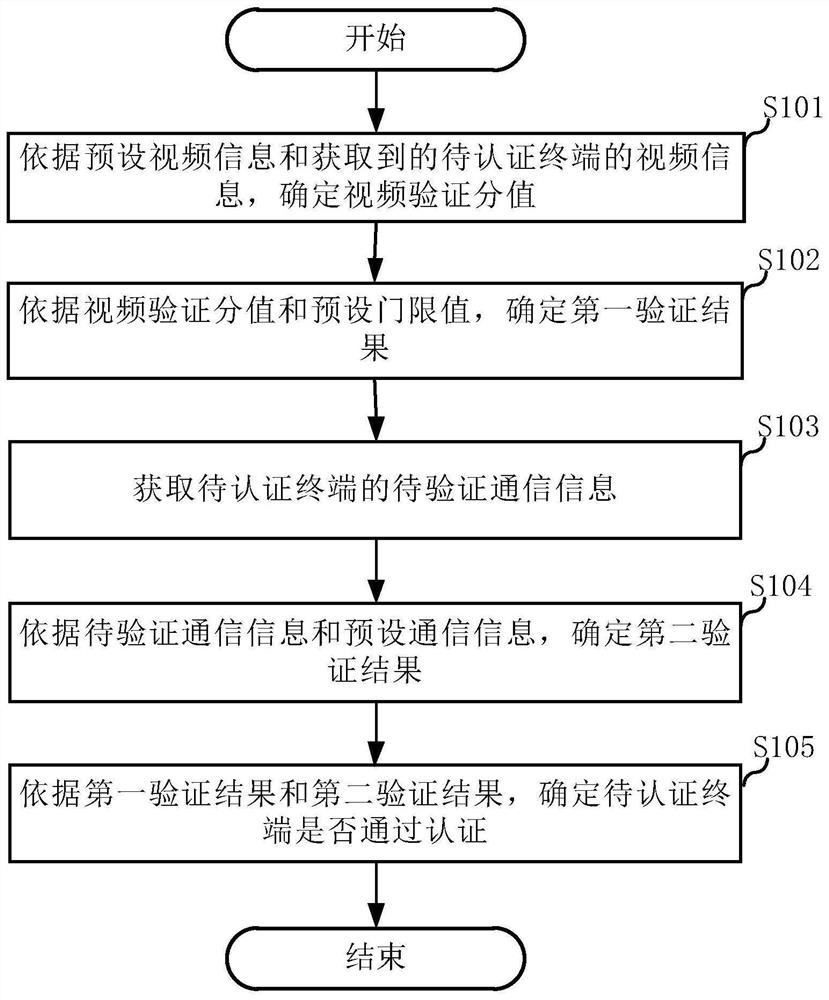
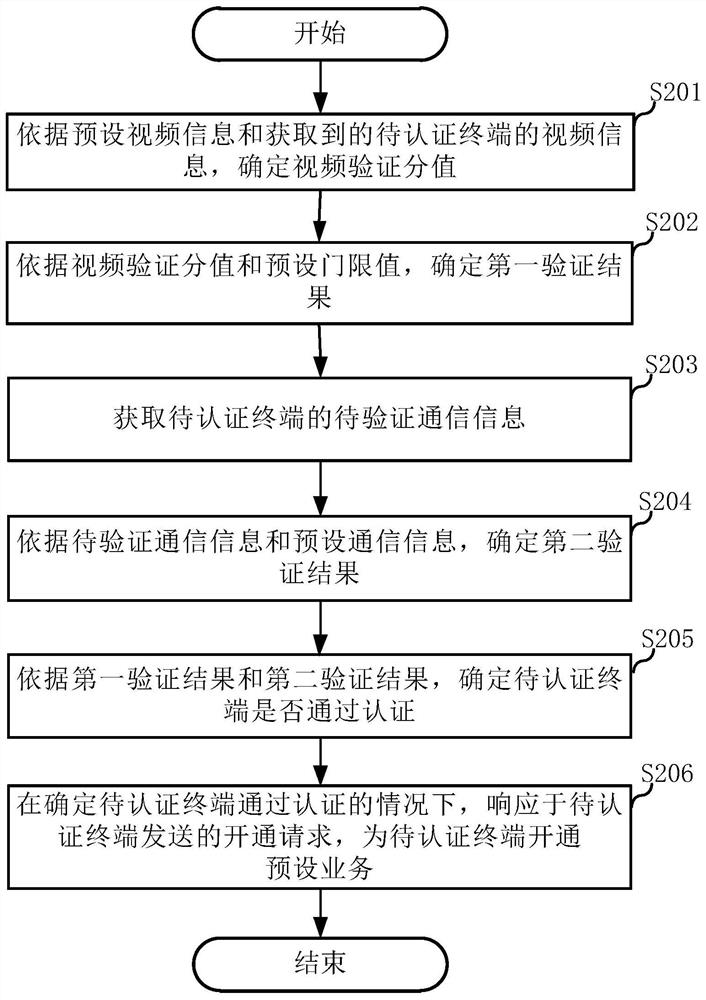
PendingCN113068178AEnsure safetyImprove the authentication success rateSecurity arrangementNetwork data managementEngineeringServer
The invention discloses a terminal authentication method and a server, and relates to the technical field of communication. The terminal authentication method comprises the following steps: determining a video verification score according to preset video information and obtained video information of a to-be-authenticated terminal; determining a first verification result according to the video verification score and a preset threshold value; acquiring to-be-verified communication information of the to-be-authenticated terminal; determining a second verification result according to the to-be-verified communication information and preset communication information; and determining whether the to-be-authenticated terminal passes authentication according to the first verification result and the second verification result. Through different verification dimensions, the accuracy of the authentication result is determined, the authentication success rate of the to-be-authenticated terminal is improved, a user can safely complete opening of online services in a self-service manner, and the user experience is improved.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Identity verification method, device, equipment and computer readable storage medium
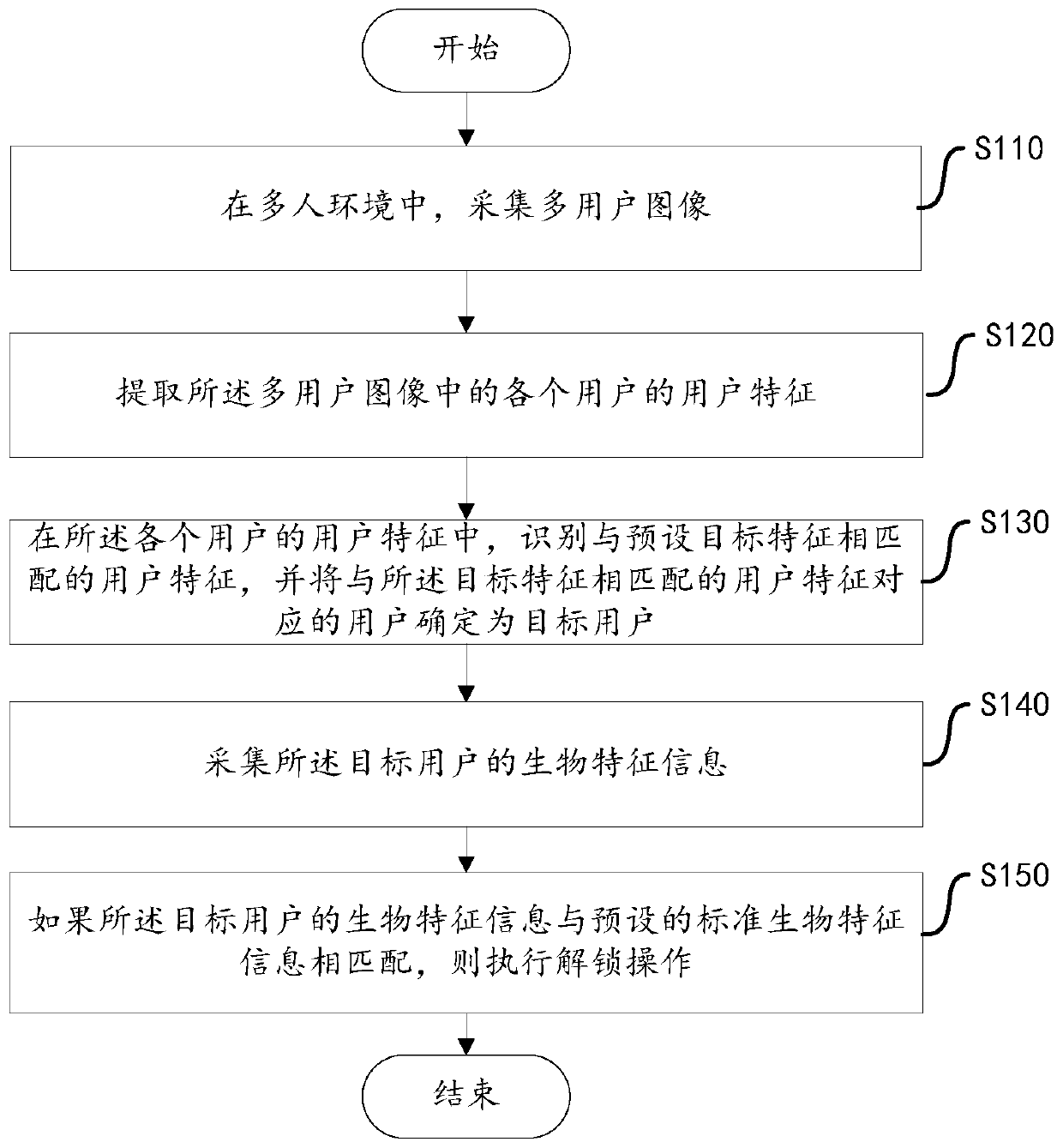
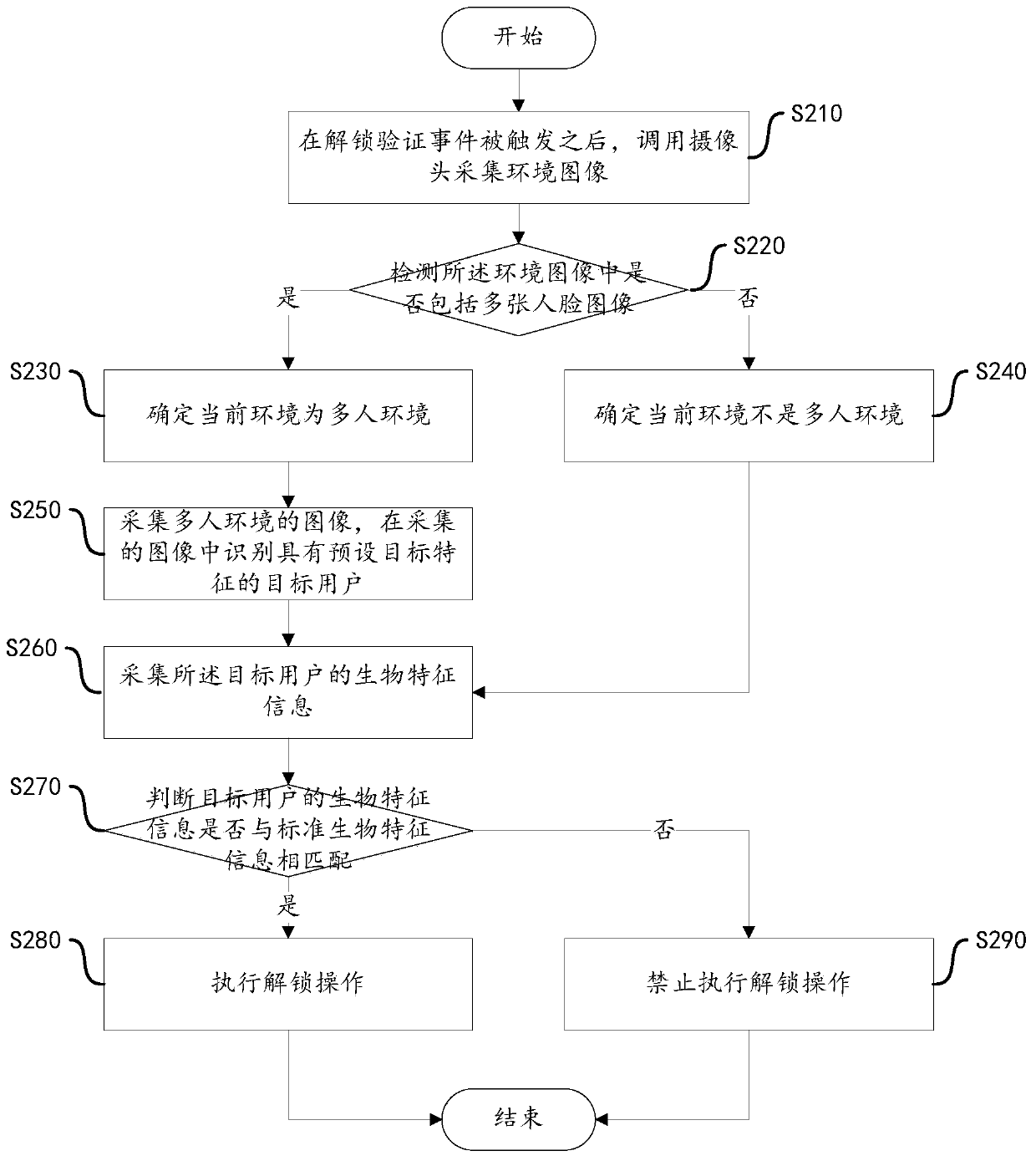
PendingCN110991239AImprove experienceReduce adverse effectsMultiple biometrics useEngineeringUser environment
The invention discloses an identity verification method, a device, equipment and a computer readable storage medium. The method comprises the following steps: acquiring a multi-user image in a multi-user environment; extracting user characteristics of each user in the multi-user image; in the user characteristics of each user, identifying the user characteristics matched with the preset target characteristics, and determining the user corresponding to the user characteristics matched with the target characteristics as the target user; collecting biological characteristic information of a target user; and if the biological characteristic information of the target user is matched with the preset standard biological characteristic information, executing an unlocking operation. According to the method, the target user is identified in the multi-user environment, only the biological characteristic information of the target user is collected in the multi-user environment, and whether the identity verification operation can be executed or not is judged according to the biological characteristic information. According to the method, the adverse effect of environmental factors on the identity authentication process can be reduced, the identity authentication time is shortened, the identity authentication success rate is improved, and the user experience effect is improved.
Owner:GREE ELECTRIC APPLIANCES INC
Biometric authentication processing system
InactiveCN101334916BAdd placementImprove reliabilityPerson identificationCharacter and pattern recognitionImaging processingImaging quality
The invention provides a biometric authentication processing system. When the reading quality during the authentication process is less than a predetermined level of quality, image processing to improve the quality of a read image that is not performed during the registration process is performed to improve the image quality, thus making the biometric authentication successful. Software to improve the image quality is added by upgrading the version of the authentication software to successively add image improvement software to the authentication software irrespective of the registration process. This version upgrading method enables changes to be made to enhance the authentication success rate regardless of the version of the registration software. Further, an area in which to read biometric information during the registration process is set larger than that in which to read biometric information during the authentication process, so that if a subject body part is placed slightly deviated from a correct position, a matching check can still be made. The biometric information reading area is not only used as an entire single image but divided into sub-areas, in each of which characteristic quantities are extracted. According to the result of a matching check in each divided sub-area, an overall authentication result is determined as either OK or NG. Since which of the divided sub-areas is NG can be known, NG causes can be analyzed precisely.
Owner:HITACHI OMRON TERMINAL SOLUTIONS CORP
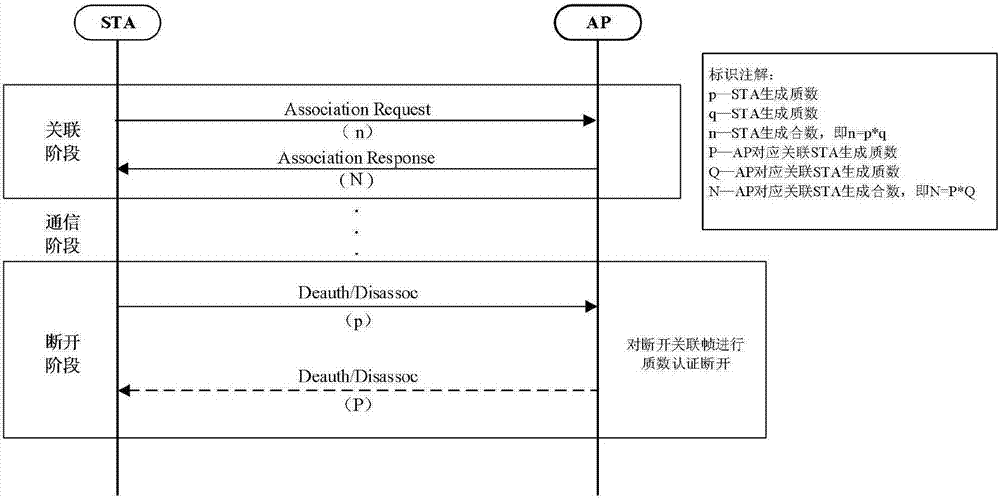
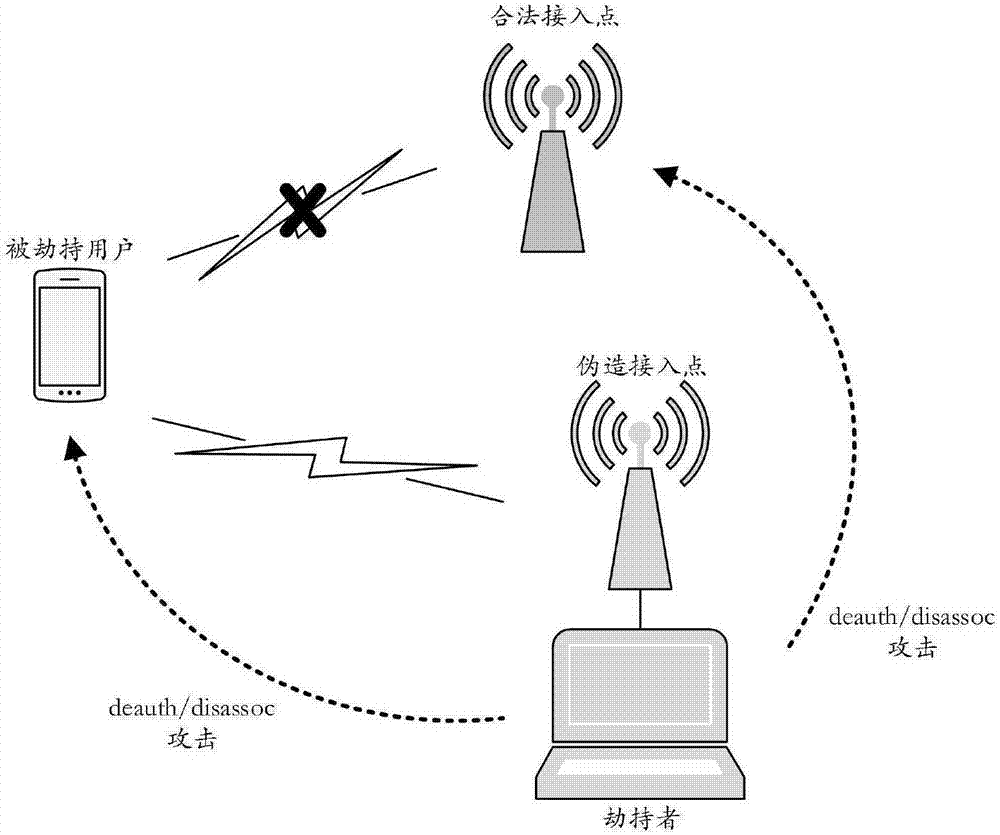
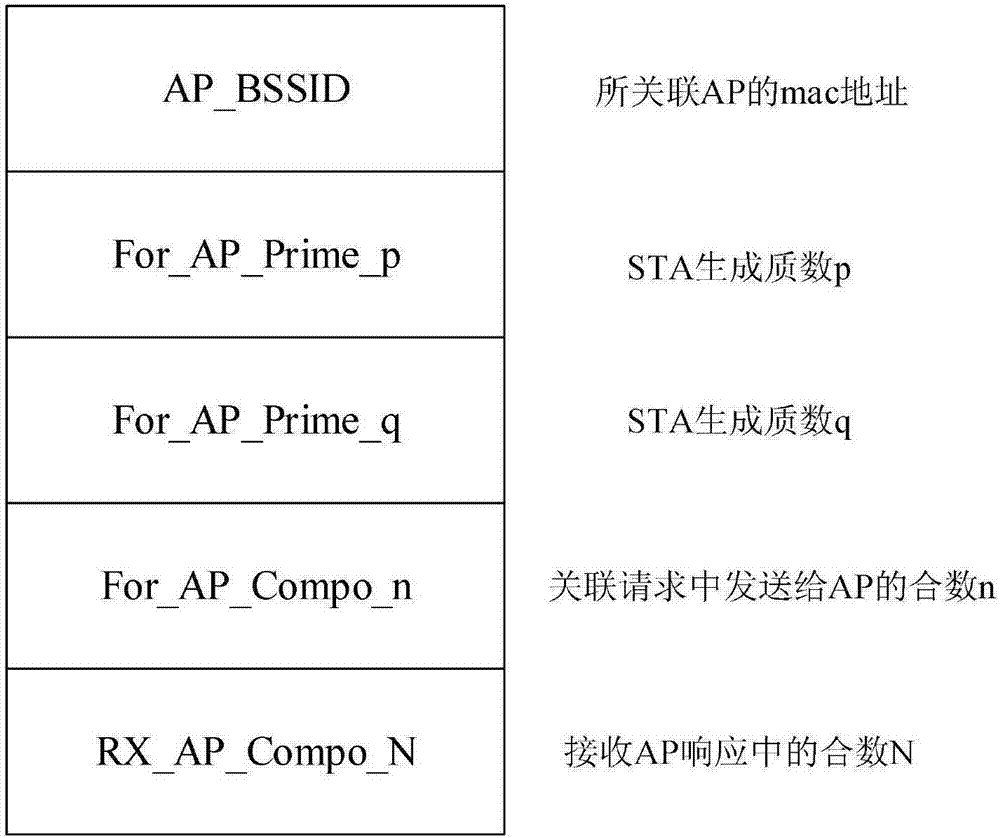
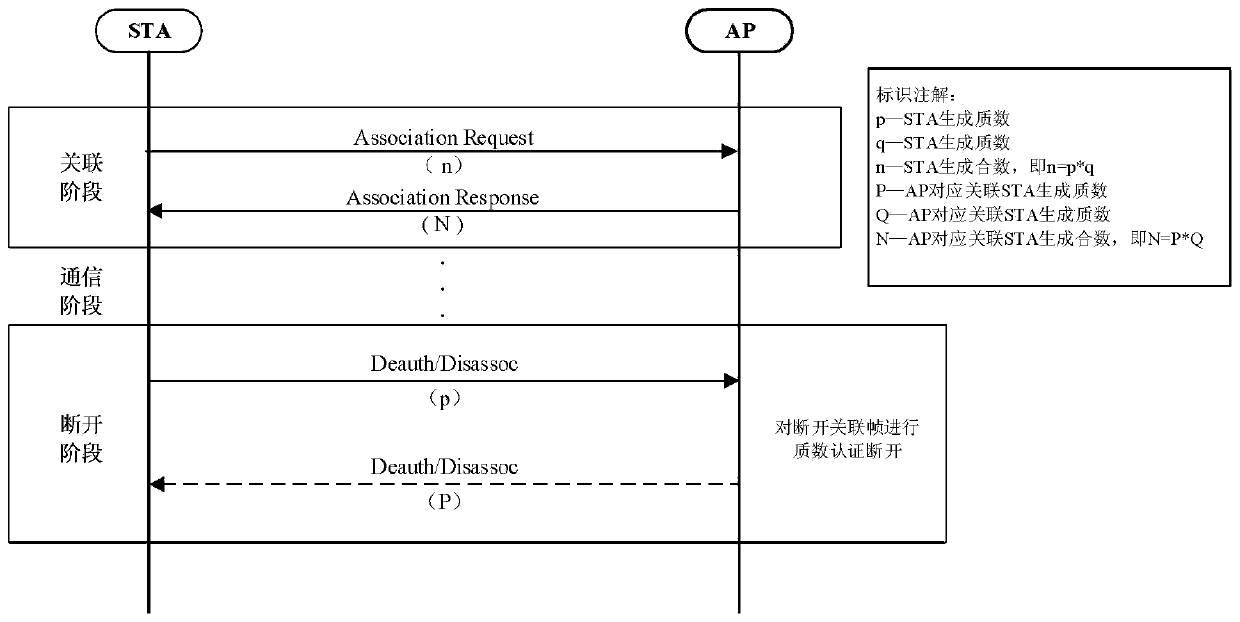
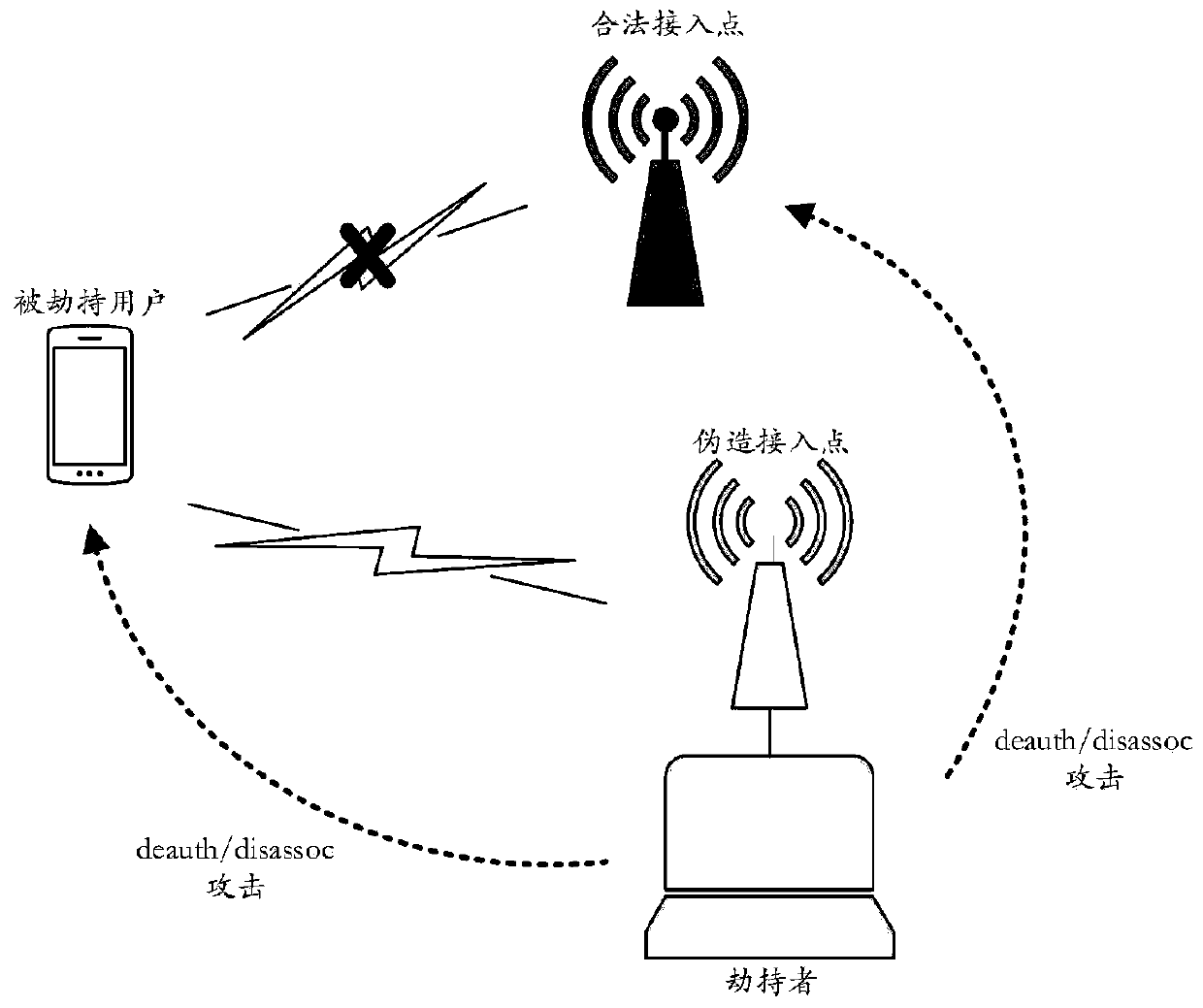
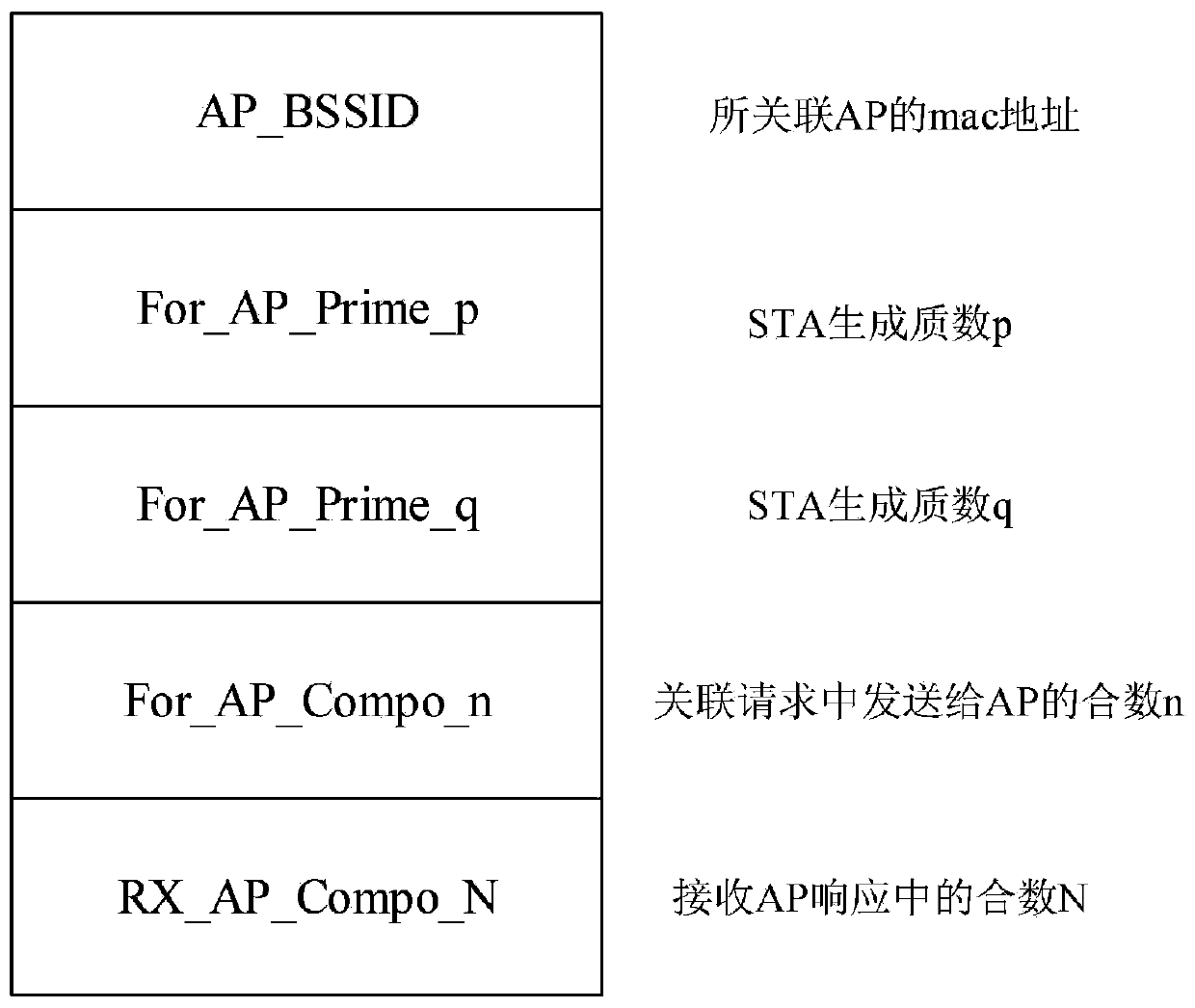
Method for preventing WLAN (Wireless Local Area Network) association-breaking attack based on prime factorization verification
The invention discloses a method for preventing WLAN (Wireless Local Area Network) association-breaking attack based on prime factorization verification, and belongs to the technical field of communication. The method comprises the following steps that: a STA (Station) transmits an association request frame carrying a generated large composite number; an AP (Access Point) receives the associationrequest frame; the AP transmits an association response frame carrying the generated large composite number; the STA receives the association response frame; the STA transmits a breaking authentication association frame carrying a large prime number; the AP receives the breaking authentication association frame and verifies the large prime number in the breaking authentication association frame; the AP transmits the breaking authentication association frame carrying the large prime number; and the STA receives the breaking authentication association frame and verifies the large prime number inthe breaking authentication association frame. The STA and the AP generate the large prime number and the large composite number which are required during association breaking of the other party at an association stage, and the transmission of the large composite and the large prime number is realized through a frame extension field. Frame reception is authenticated at a breaking stage, so that the STA and the AP are protected from being disconnected exceptionally due to an association-breaking authentication frame transmitted by a malicious third party. Through adoption of the method, the security, protocol compatibility and authentication success rate are improved greatly.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
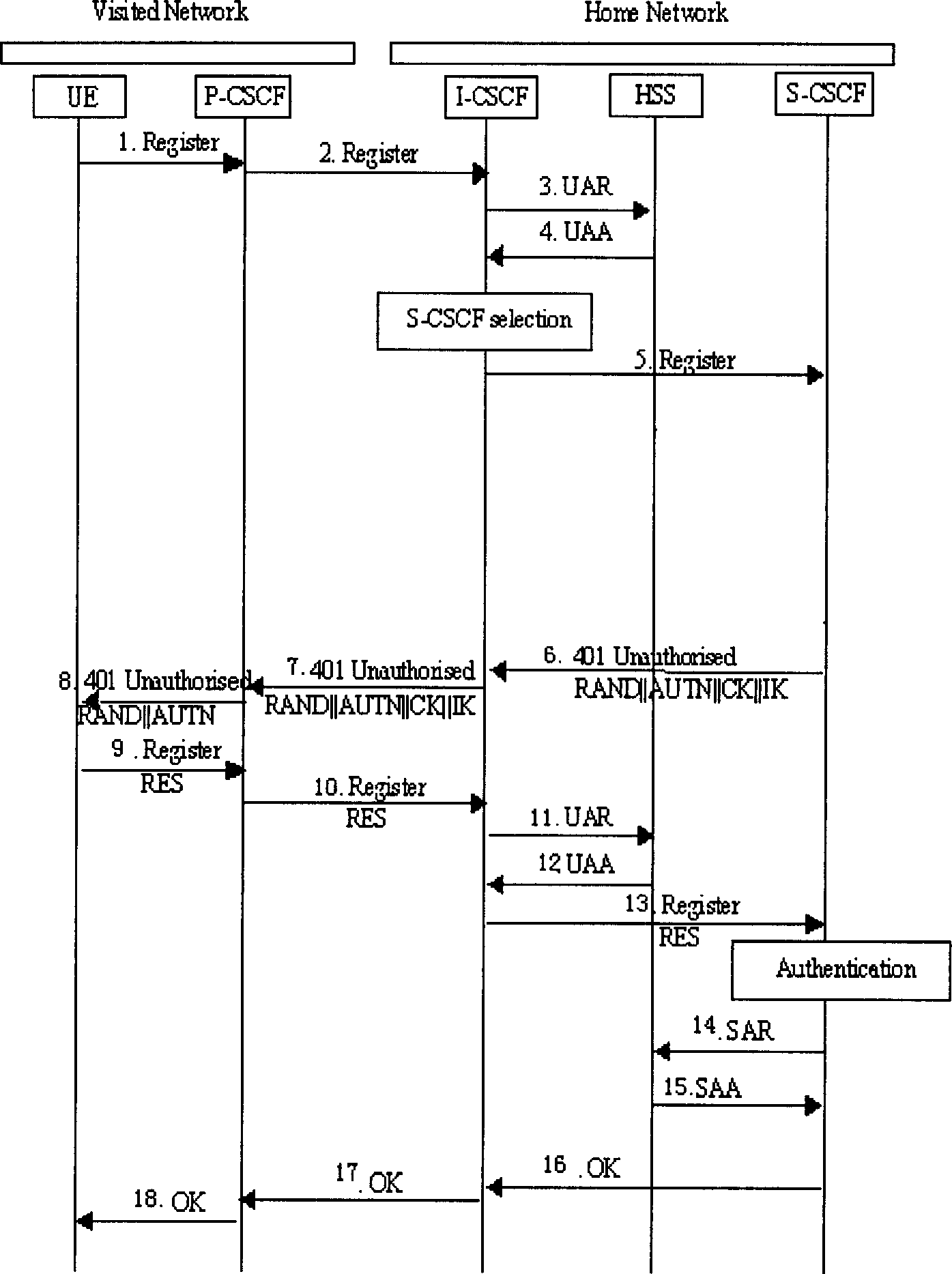
Authentication method, device and system in IMS network
InactiveCN1866823BSave computing resourcesImprove the efficiency of first-time registrationUser identity/authority verificationComputer scienceAuthentication
The invention discloses an identifying weight method, device and system of IBM network, which comprises the following steps: using identifying weight information for UE identifying weight using which saves by S-CSCF itself; finishing UE and IMS network identifying weight processing procedure; registrating UE whose registration state is Unregistered and S-CSCF saves identifying weight information;providing dentifying weight scheme accomplish flow process of UE application identifying weight quintuple which can neglect S-CSCF and flow to HSS through MAR, MAA. The invention reduces MAR, MAA information source commutation, which optimizes identifying weight flow path of UE first registration.
Owner:HUAWEI TECH CO LTD
A physical layer watermark authentication method and system for LTE system
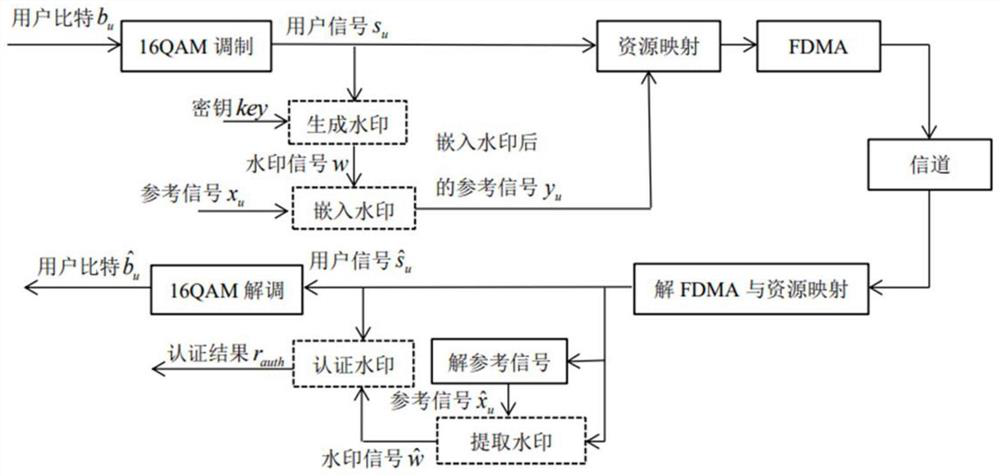
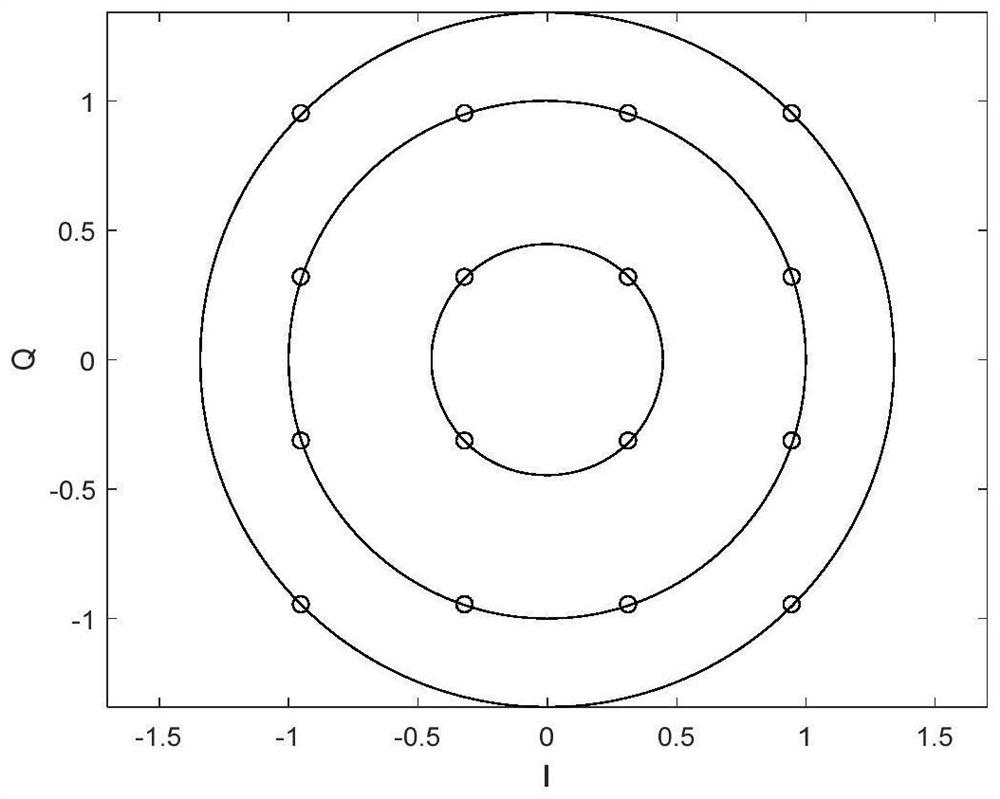
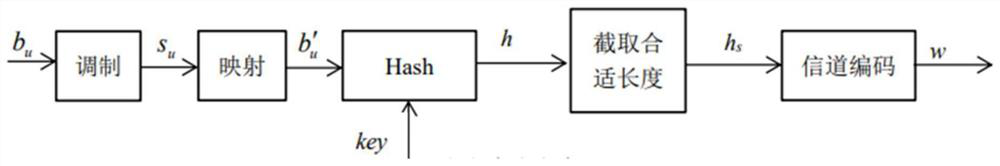
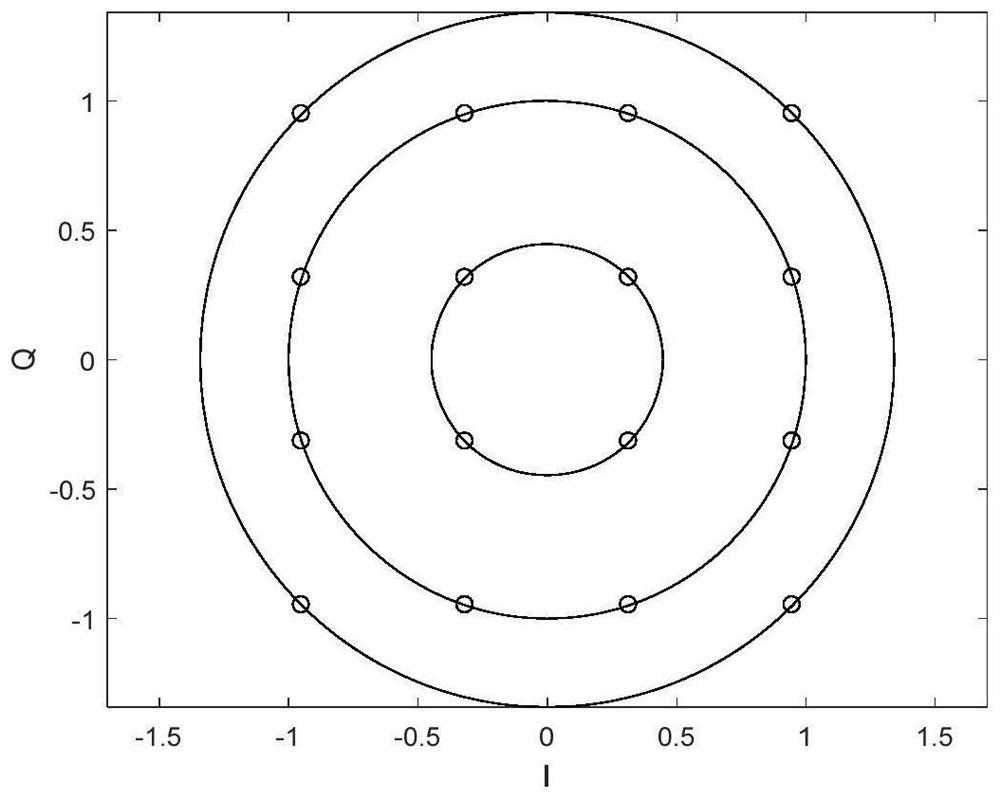
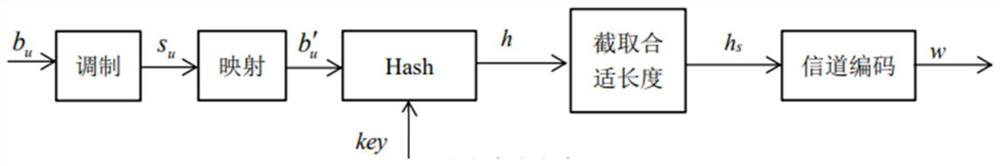
ActiveCN113453225BProtect the certification labelReduce overheadSecurity arrangementHigh level techniquesComputer hardwarePhysical layer
The invention discloses an LTE system-oriented physical layer watermark authentication method and system, belonging to the field of physical layer watermark authentication. The invention applies the physical layer authentication technology to the LTE system, reduces the system overhead required by the traditional high-level authentication, and makes the following improvements to the traditional watermark authentication scheme: the invention proposes to embed the watermark in the phase of the reference signal, reducing The small watermark causes interference to the user signal, and at the same time, by adopting the method of phase symmetry embedding, the influence of the watermark on the channel estimation of the reference signal is reduced; the present invention proposes the concept of pseudo-user bits, and uses pseudo-user bits instead of user bits as the generated watermark parameters to reduce the authentication error caused by the demodulation error of the user signal at the receiving end; the present invention also adds channel coding into the watermark generation scheme to reduce the bit error that occurs during the transmission of the watermark.
Owner:HUAZHONG UNIV OF SCI & TECH
Method, device and system for treating authentication message
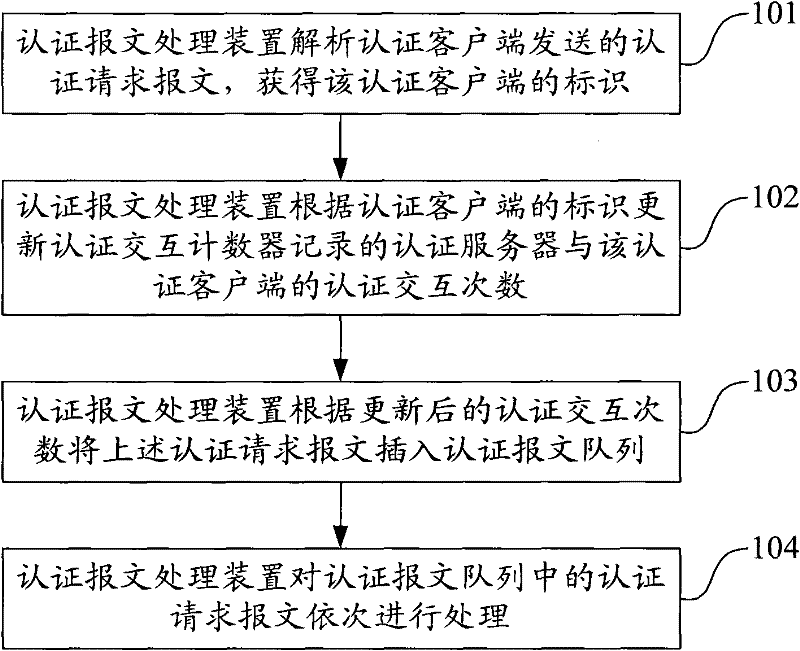
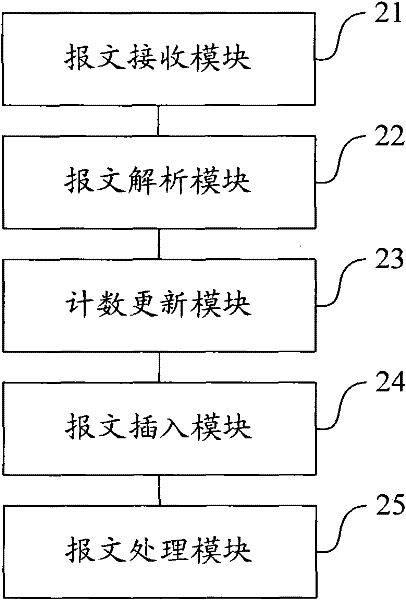
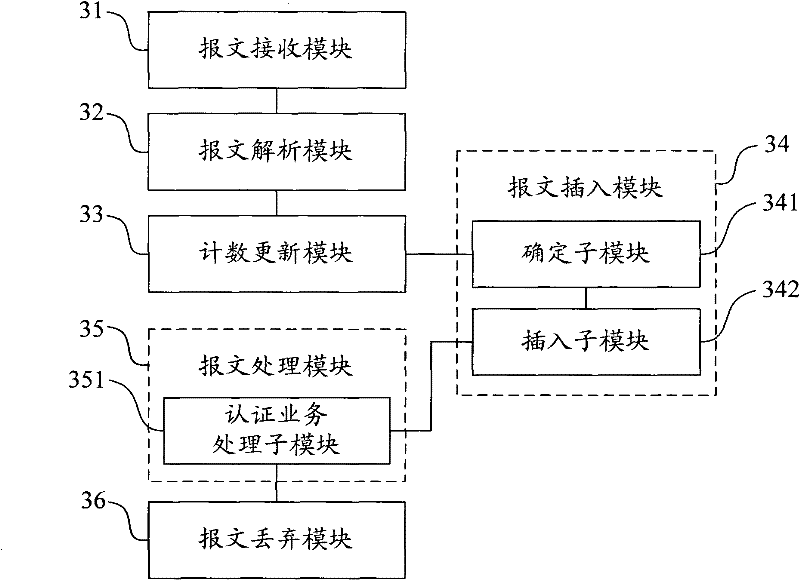
ActiveCN101697529BImprove the authentication experienceImprove authentication efficiencyData switching networksMessage queueUser authentication
The embodiment of the invention provides a method, a device and a system for treating an authentication message. The method for treating the authentication message comprises the following steps of: analyzing authentication request messages sent by an authentication client to obtain a mark of the authentication client; updating an authentication server recorded by an authentication interactive counter and an authentication interactive frequency of the authentication client according to the mark of the authentication client; and inserting the authentication request messages into an authentication message queue according to the updated authentication interactive frequency, and sequentially treating the authentication request messages in the authentication message queue. The embodiment of theinvention realizes control to a treating sequence and flow of the authentication messages, enhances the authentication efficiency, the authentication success rate and the user authentication experience, and particularly initiates an authentication process when authenticating clients in a large amount and efficiently filters the authentication request messages under the condition that the authentication server achieves the performance bottleneck, thereby greatly enhancing the authentication efficiency and the user authentication experience.
Owner:BEIJING XINWANG RUIJIE NETWORK TECH CO LTD
A method of preventing wlan disconnection attack based on prime number decomposition verification
The invention discloses a method for preventing WLAN (Wireless Local Area Network) association-breaking attack based on prime factorization verification, and belongs to the technical field of communication. The method comprises the following steps that: a STA (Station) transmits an association request frame carrying a generated large composite number; an AP (Access Point) receives the associationrequest frame; the AP transmits an association response frame carrying the generated large composite number; the STA receives the association response frame; the STA transmits a breaking authentication association frame carrying a large prime number; the AP receives the breaking authentication association frame and verifies the large prime number in the breaking authentication association frame; the AP transmits the breaking authentication association frame carrying the large prime number; and the STA receives the breaking authentication association frame and verifies the large prime number inthe breaking authentication association frame. The STA and the AP generate the large prime number and the large composite number which are required during association breaking of the other party at an association stage, and the transmission of the large composite and the large prime number is realized through a frame extension field. Frame reception is authenticated at a breaking stage, so that the STA and the AP are protected from being disconnected exceptionally due to an association-breaking authentication frame transmitted by a malicious third party. Through adoption of the method, the security, protocol compatibility and authentication success rate are improved greatly.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
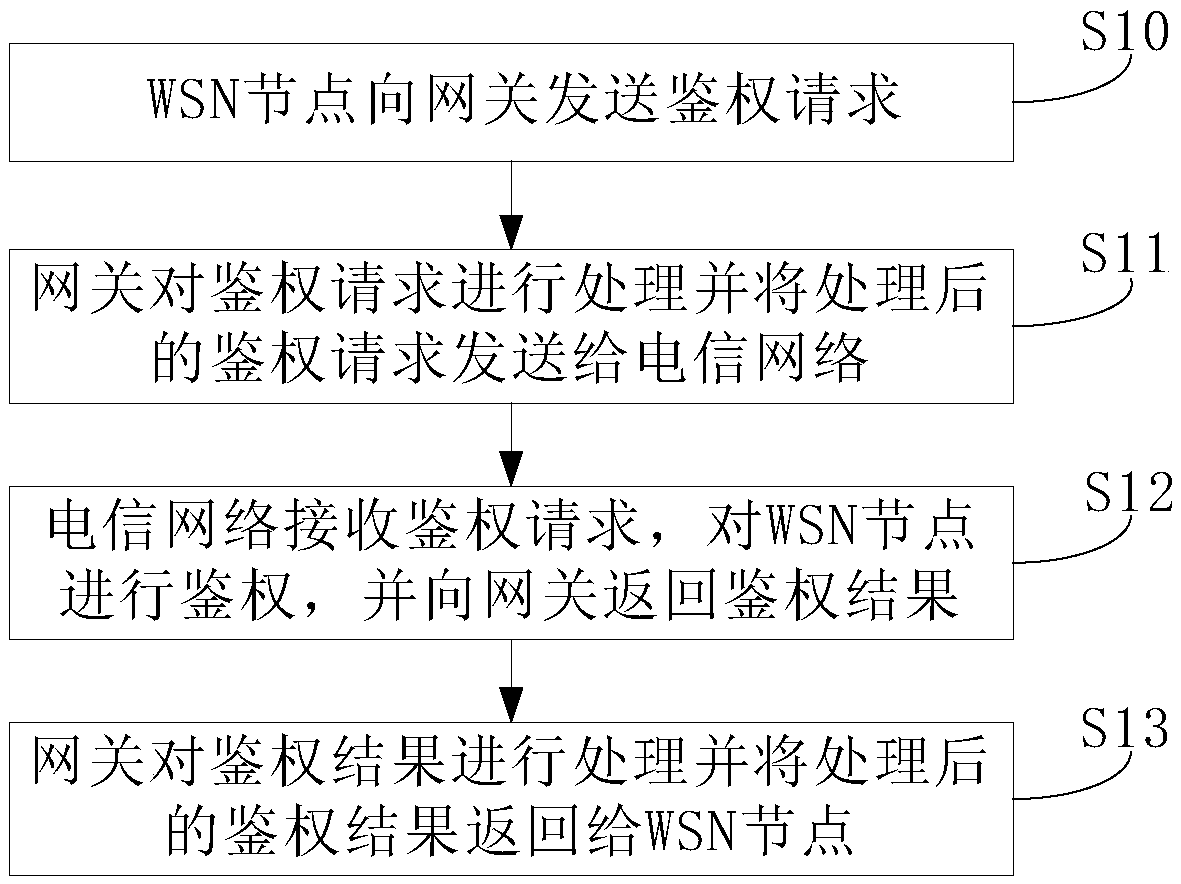
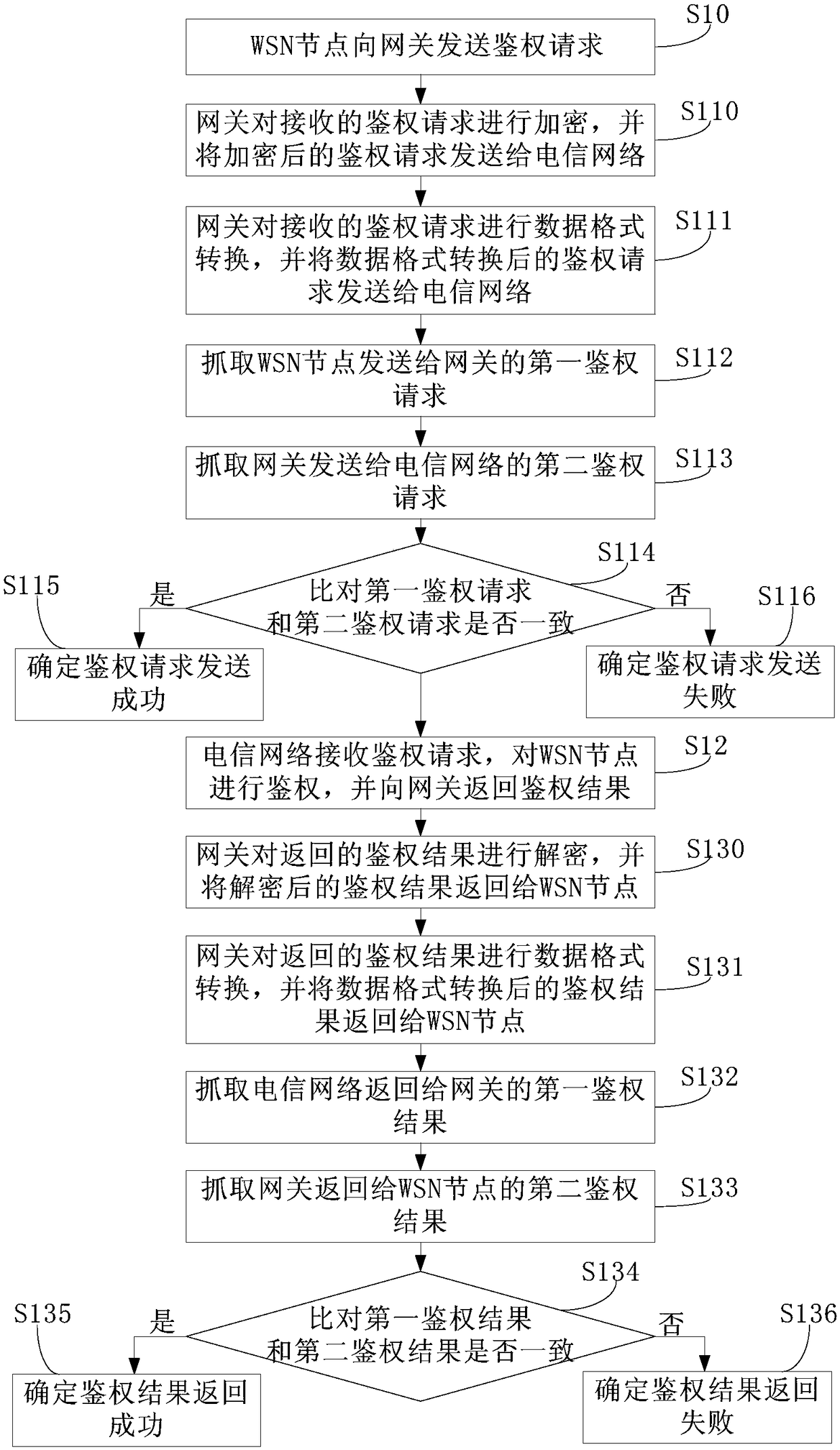
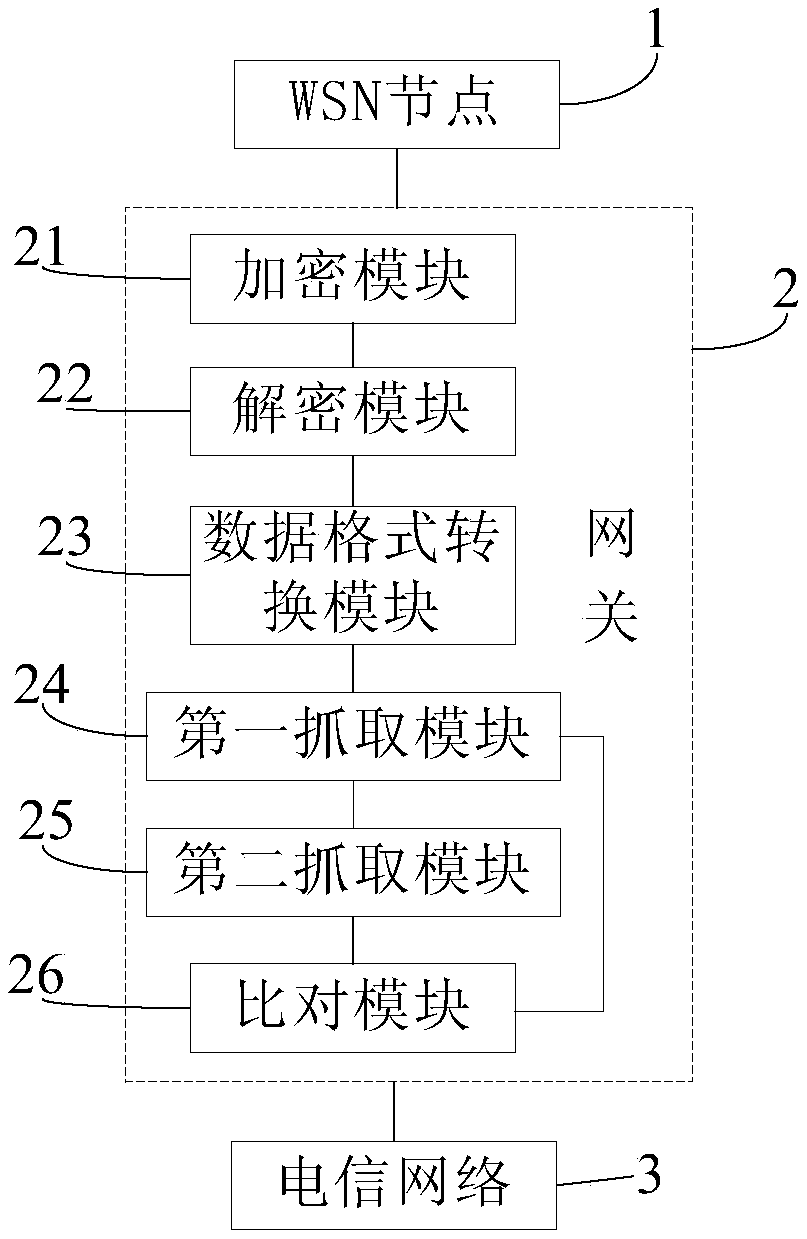
Authentication method and system for WSN (Wireless Sensor Network) node on telecommunication network
InactiveCN108777864AImprove the authentication success rateImprove authentication efficiencySecurity arrangementTelecommunications linkWireless sensor network
The invention provides an authentication method and system for a WSN (Wireless Sensor Network) node on a telecommunication network. The authentication method for the WSN node on the telecommunicationnetwork comprises the following steps that the WSN node sends an authentication request to a gateway; the gateway processes the authentication request and sends the processed authentication request tothe telecommunication network; the telecommunication network receives the authentication request, authenticates the WSN node and sends an authentication result back to the gateway; and the gateway processes the authentication result and sends the processed authentication result back to the WSN node. According to the authentication method, the gateway is arranged on a communication link between the WSN node and the telecommunication network, the authentication request sent by the WSN node and the authentication result sent back by the telecommunication network are processed and transmitted through the gateway, so that the authentication request and the authentication result can be transmitted to a target network more smoothly and more quickly, and therefore the authentication success rateof the WSN node is increased, and meanwhile the authentication efficiency of the WSN node is further improved.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Block chain-based data flow detection method, device and server
The embodiment of the present application provides a block chain-based data flow detection method, device, and server. When the server receives a data flow acquisition request for a target data service sent by a user terminal, it generates a waiting list for a verification strategy for a specific target data service. Verify the blockchain, so as to take into account the differences in different data services, improve the security and pertinence of the authentication process, and then enable the user terminal to generate fields in the blockchain to be verified according to the fields to be verified The corresponding verification fields generated by calculation, because the fields to be verified are randomly added, can increase the difficulty of being cracked by hackers, thereby improving the success rate of authentication. Afterwards, the user terminal is allowed to access the data flow address of the target data service. During this period, the access information of the user terminal is monitored in real time to repeat the verification, so as to further improve the authentication success rate and security.
Owner:重庆爱责慧科技有限公司
Mobile terminal and its serial authentication method under wcdma network
ActiveCN111182534BImprove the authentication success rateLow costSecurity arrangementEngineeringAuthentication
The application discloses a serial authentication method for a mobile terminal under a WCDMA network. The network side sends an authentication request to the mobile terminal through the PS domain or the CS domain. If the first network parameter is equal to the first local parameter, the USIM card judges the second network parameter and the second local parameter according to a synchronization check rule. If the check is passed, the mobile terminal sends an authentication success message to the network side. If the check fails, the mobile terminal replies to the network side with an authentication failure message with specific failure reasons and parameters. After the network side receives the above-mentioned authentication failure message of the first authentication, it will recalculate the authentication quintuple, and then the network side initiates a second authentication request through the same field. The present application adopts a serial processing method for the authentication requests of the PS domain and the CS domain, which greatly improves the success rate of authentication of the mobile terminal to the network side.
Owner:ASR MICROELECTRONICS CO LTD
Authentication method, device and storage medium of graphic password
ActiveCN108009419BImprove the authentication success rateEasy to operateDigital data authenticationTransmissionInternet privacyPassword
The invention discloses a graphical password authentication method which includes the steps: transmitting a graphical password authentication request to a server; receiving variable parameters of vector graphics returned by the server according to the authentication request; displaying a password drawing area corresponding to class information according to the variable parameters; recognizing a dragging event in the password drawing area by a drawing control point and determining a drawn vector graphic according to the recognized dragging event; transmitting the drawn vector graphic to the server. The authentication request at least comprises the class information of the vector graphics, the password drawing area at least comprises the drawing control point, and the vector graphics are used as graphical passwords for identity authentication. The invention further provides a graphical password authentication device and a storage medium.
Owner:MIGU CO LTD +1
Retransmission method based on finite-state machine and effectiveness verification method thereof
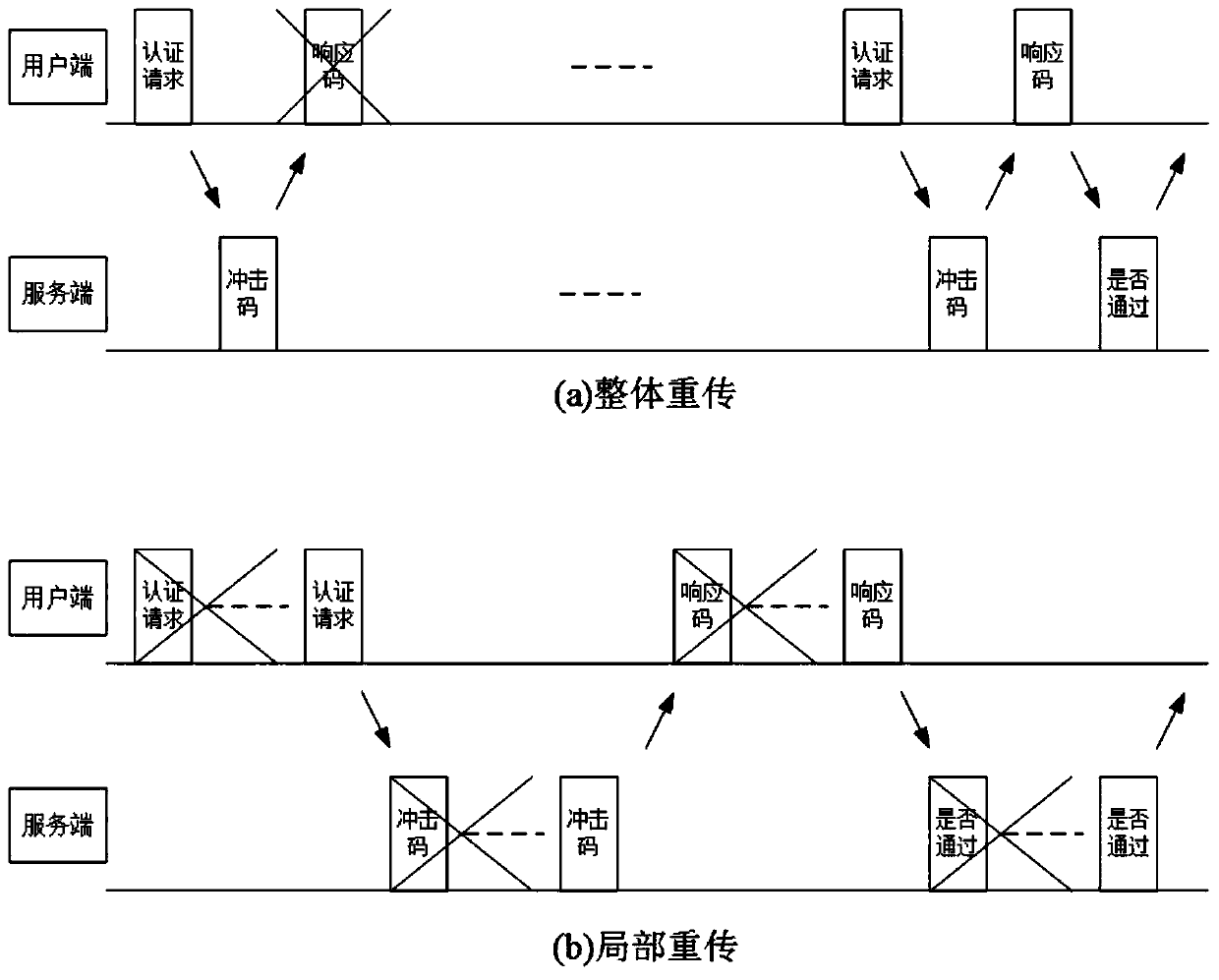
ActiveCN110535566AReduce theftEnsure safetyError prevention/detection by using return channelData switching networksInformation transmissionValidation methods
The invention provides a retransmission method based on a finite-state machine. The retransmission method is based on a local retransmission technology. The user side and the server side adopt finite-state machines; wherein the finite-state machine comprises a working state, a polling state and a pause state; when a data packet is lost in a user data transmission process, data packet retransmission is carried out through conversion of the three states; information transmission quality is improved, data transmission safety is enhanced, channel congestion and user information stealing are prevented, the main algorithm model and the reference algorithm model are established, the success rate, time delay and safety of the data retransmission method are investigated, and a purpose of verifyingvalidity of the retransmission method based on the finite state machine is realized.
Owner:重庆高开清芯科技产业发展有限公司
A lightweight security authentication and key exchange method for NB-IoT
ActiveCN108989318BAvoid risk of leakageReduce Interaction ComplexityTransmissionKey exchangeInternet privacy
The invention discloses a lightweight security authentication and key exchange method for narrow-band internet of things. The communication main body comprises a terminal and a server. Before the communication is established, the root key is shared between the terminal and the server, and the two-way authentication is realized by adopting a challenge-response interaction mechanism based on a symmetric cryptosystem. The present invention mainly solves the problem of the two-way identity authentication and key exchange between the terminal and server in the Internet of Things application systembased on NB-IoT and other narrow-band Internet of Things connection technologies, can realize lightweight security authentication algorithm, protocol and key agreement mechanism, and meet the design requirements of low power consumption, low bandwidth consumption, low interaction frequency and high security.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
Physical layer watermark authentication method and system for LTE system
ActiveCN113453225AReduce system overheadReduce distractionsSecurity arrangementHigh level techniquesChannel codeAuthentication scheme
The invention discloses a physical layer watermark authentication method and system for an LTE system, and belongs to the field of physical layer watermark authentication. A physical layer authentication technology is applied to an LTE system, system overhead required by traditional high-level authentication is reduced, and a traditional watermark authentication scheme is improved as follows: a watermark is embedded into a phase of a reference signal, interference of the watermark to a user signal is reduced, and meanwhile, by adopting a phase symmetric embedding mode, the influence of the watermark on the channel estimation of the reference signal is reduced; according to the method, the concept of pseudo user bits is provided, the pseudo user bits are used for replacing user bits to serve as parameters for watermark generation, and authentication errors caused by user signal demodulation errors of a receiving end are reduced; in addition, channel codes are added into a watermark generation scheme, and error codes generated in the watermark transmission process are reduced.
Owner:HUAZHONG UNIV OF SCI & TECH
Method for identifying authority in wireless group business
ActiveCN1815956BImprove satisfactionIncrease incomeUser identity/authority verificationAuthentication serverAuthentication information
The method sets up general authentication information in GGSN and authentication server in advance. The method also includes following steps: after receiving PDP request message for activating context, based on general authentication information setup in GGSN, GGSN sends out message for requesting authentication including general authentication information to authentication server; after receiving message for requesting authentication, the authentication server determines validity of the general authentication information, and then returns back successful message of request to GGSN. The invention sets up general authentication information in GGSN and authentication server. The said general information is included in message of request sent by GGSN to the authentication server. Thus, success ratio of authentication is increased greatly so as to raise satisfying degree and increase earning of operation manager.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com