Authentication method and system for WSN (Wireless Sensor Network) node on telecommunication network
A telecommunications network and authentication technology, applied in the communication field, can solve problems such as low authentication efficiency, authentication failure, and user loss, and achieve the effect of improving the success rate of authentication and improving authentication efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
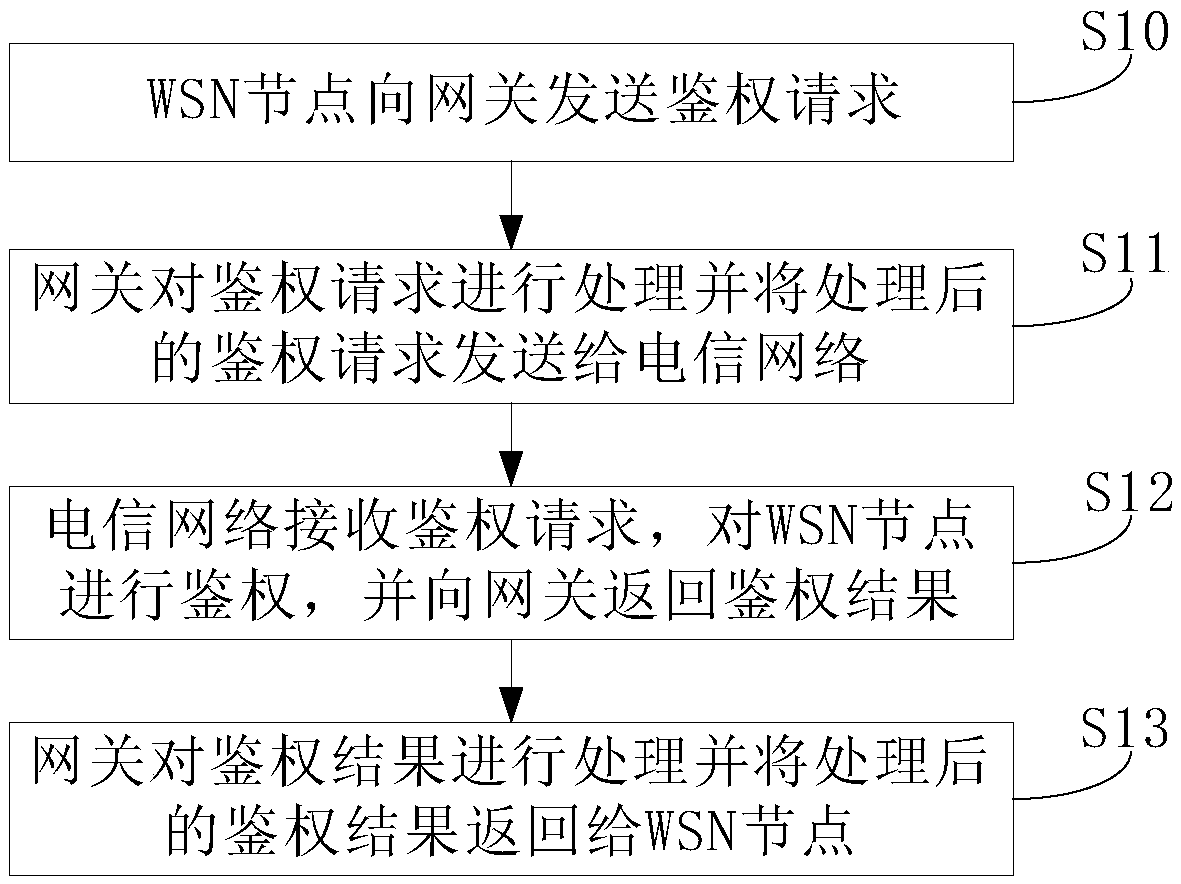
[0052] This embodiment provides an authentication method for a WSN node to a telecommunication network, such as figure 1 shown, including:
[0053] Step S10: the WSN node sends an authentication request to the gateway.
[0054] In this step, the gateway refers to the sensor gateway. A WSN node refers to a sensor node in a wireless sensor network (Wireless Sensor Network, WSN). The authentication request includes the name of the WSN node, the IP address of the WSN node, the serial number of the device managed under the WSN node, and the location information of the device.
[0055] Step S11: the gateway processes the authentication request and sends the processed authentication request to the telecommunication network.
[0056] Step S12: The telecommunication network receives the authentication request, authenticates the WSN node, and returns the authentication result to the gateway.
[0057] Wherein, the telecommunication network includes a remote service management platfor...
Embodiment 2
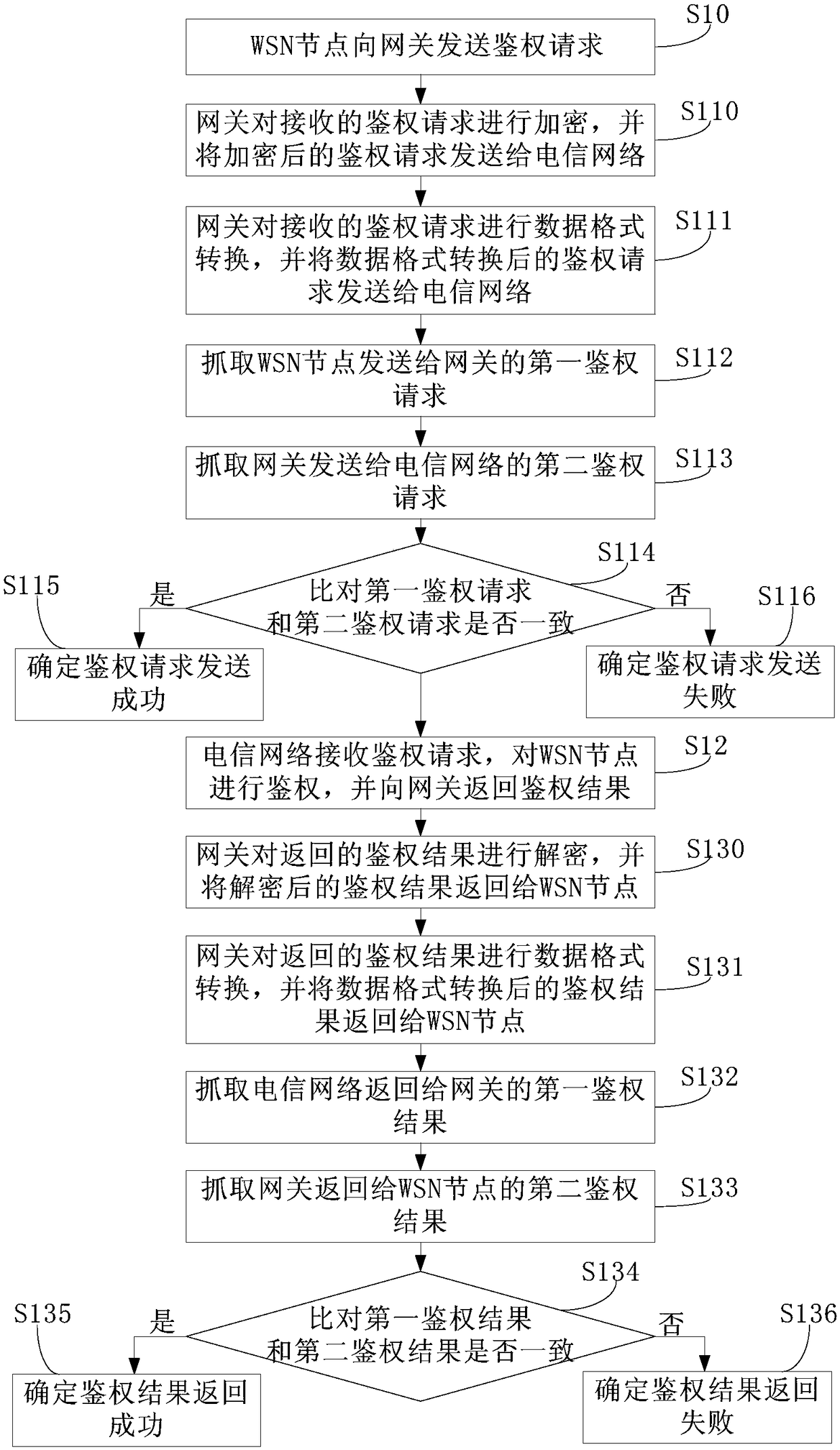
[0062] This embodiment provides an authentication method for a WSN node to a telecommunication network, such as figure 2 shown, including:
[0063] Step S10: the WSN node sends an authentication request to the gateway.
[0064] In this step, the gateway refers to the sensor gateway. A WSN node refers to a sensor node in a wireless sensor network (Wireless Sensor Network, WSN). The authentication request includes the name of the WSN node, the IP address of the WSN node, the serial number of the device managed under the WSN node, and the location information of the device.
[0065] Step S11: the gateway processes the authentication request and sends the processed authentication request to the telecommunication network.
[0066] This step specifically includes:
[0067] Step S110: the gateway encrypts the received authentication request, and sends the encrypted authentication request to the telecommunication network.
[0068] By encrypting the authentication request, import...
Embodiment 3
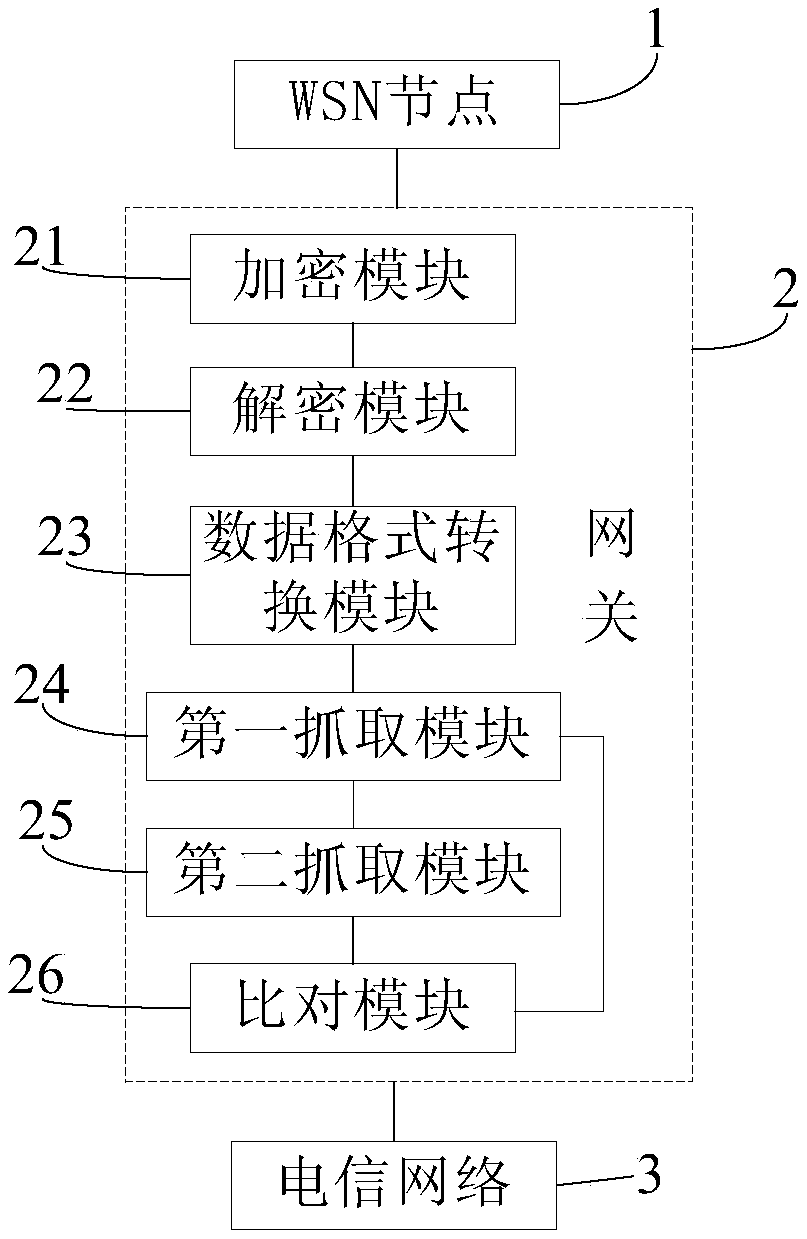
[0095] Based on the authentication method for the WSN node to the telecommunication network provided in Embodiment 2, this embodiment provides an authentication system, such as image 3 As shown, it includes: WSN node 1, gateway 2 and telecommunication network 3. The WSN node 1 is configured to send an authentication request to the gateway 2; and receive the authentication result returned by the gateway 2. The gateway 2 is used to process the authentication request and send the processed authentication request to the telecommunication network 3 ; it is also used to process the authentication result and return the processed authentication result to the WSN node 1 . The telecommunication network 3 is used for receiving the authentication request, authenticating the WSN node 1, and returning the authentication result to the gateway 2.
[0096] In this authentication system, a gateway 2 is set on the communication link between the WSN node 1 and the telecommunication network 3, a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com