Mobile terminal and its serial authentication method under wcdma network
A mobile terminal and authentication technology, applied in electrical components, security devices, wireless communications, etc., can solve the problems of secondary authentication failure in the CS domain, and achieve the effects of improving the authentication success rate, simple implementation, and low implementation cost.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
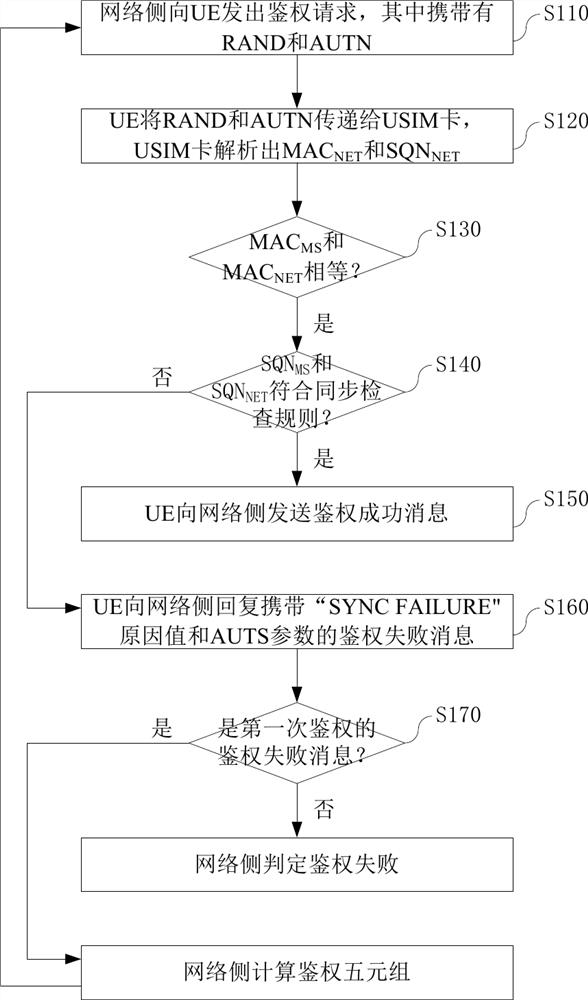
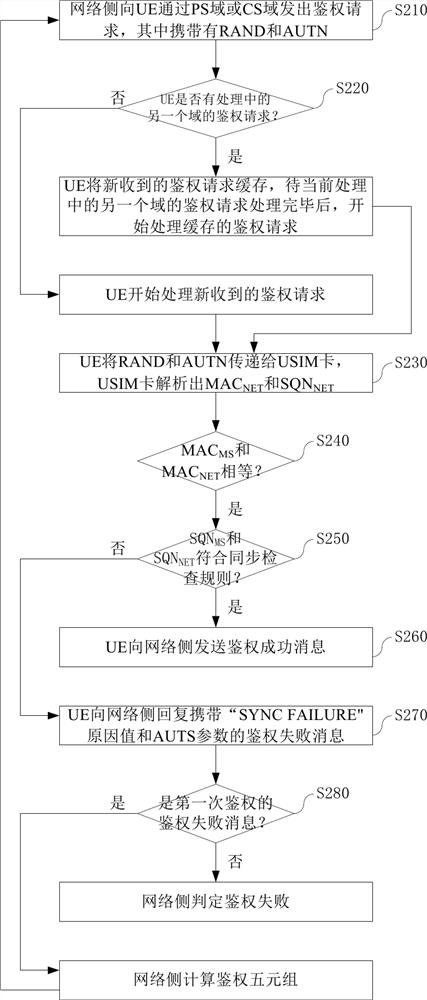
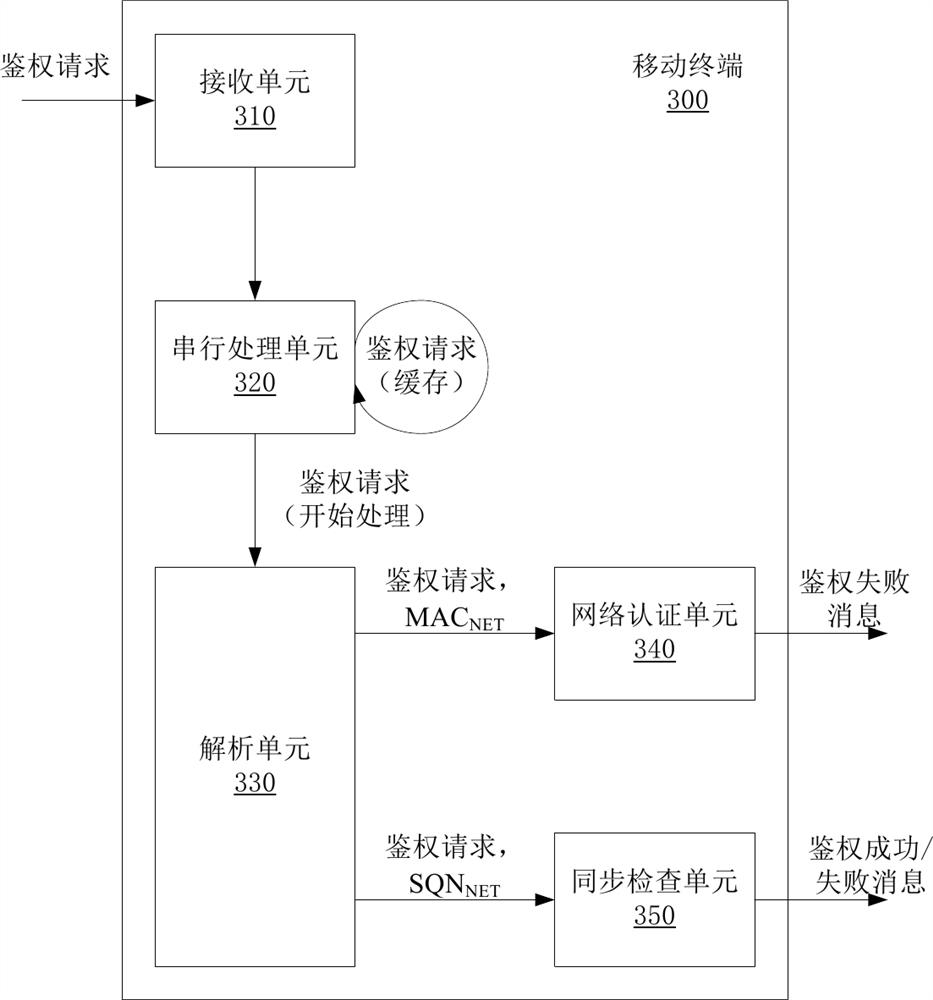
[0043] see figure 2 Embodiment 1 of the method for serial authentication of a mobile terminal under a WCDMA network provided by this application includes the following steps.
[0044] Step S210: the network side sends an authentication request to the mobile terminal through the PS domain or the CS domain. Which carries RAND and AUTN. The AUTN contains the SQN NET and MAC NET , the subscript NET indicates that it is generated by the network side.
[0045] Step S220: After receiving the authentication request from the network side through the PS domain or the CS domain, the mobile terminal determines whether there is an authentication request from another domain that is being processed. If so, the newly received authentication request is cached, and the mobile terminal starts to process the cached authentication request after the authentication request of another domain currently being processed is processed. If not, the mobile terminal starts processing the newly received...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com