Method for preventing WLAN (Wireless Local Area Network) association-breaking attack based on prime factorization verification
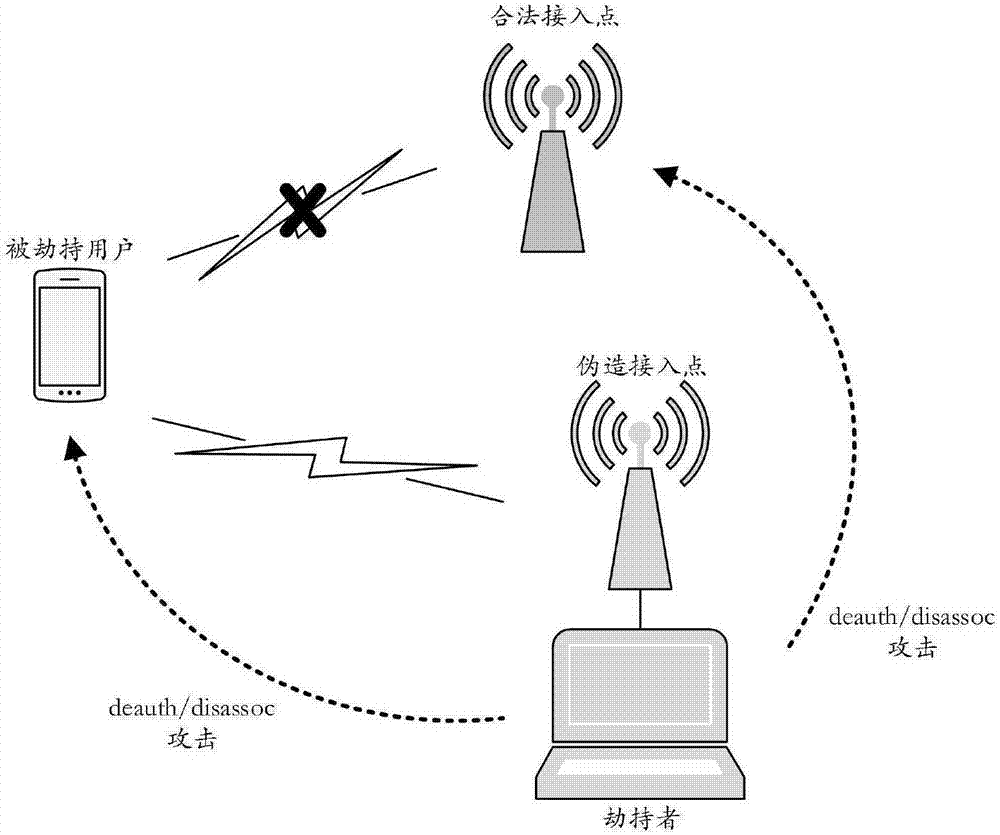
A correlation attack and prime number technology, applied in the field of communication, can solve the problems of forgery of disconnected authentication correlation frames, failure of RARP to detect forged frames, etc., and achieve the effect of increasing difficulty, high authentication success rate, and good protocol compatibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] The technical solutions in the embodiments of the present invention will be described clearly and in detail below with reference to the drawings in the embodiments of the present invention. The described embodiments are only some of the embodiments of the invention.
[0049] The technical scheme that the present invention solves the problems of the technologies described above is:
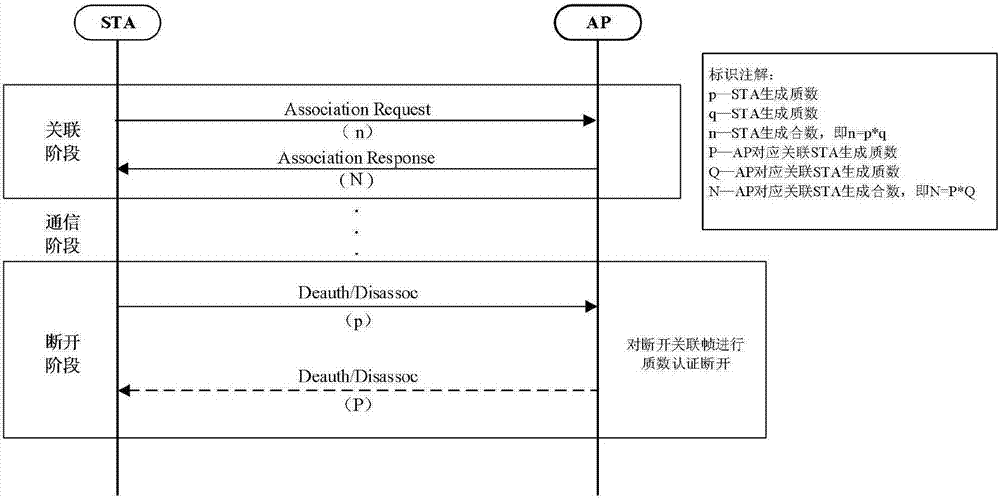
[0050] A method for preventing WLAN disconnection attacks based on prime number decomposition verification includes the following steps:
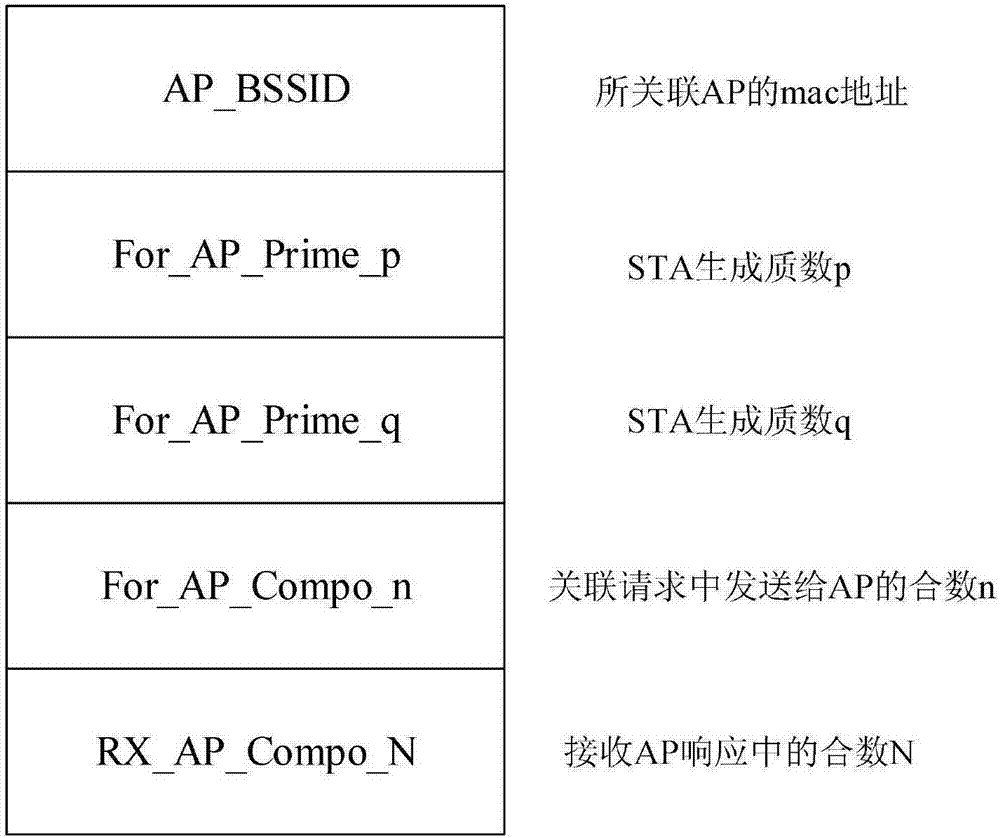
[0051] Step 1: First, the STA locally establishes the global data structure assoc_ap_info. The members include: AP_BSSID, For_AP_Prime_p, For_AP_Prime_q, For_AP_Compo_n, RX_AP_Compo_N, which are used to store the BSSID of the associated AP, the large prime number p generated for the associated AP, and the large prime number generated for the associated AP. q, the large composite number n=p*q generated for the associated AP, and the large composite number...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com