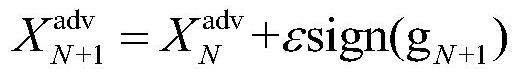Method and system for detecting camouflage attack resistance of face recognition system
A technology of face recognition system and recognition system, which is applied in the field of detection of face recognition system against camouflage attacks, and can solve the problems of inability to guarantee face recognition system attacks, only applicable, low applicability, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
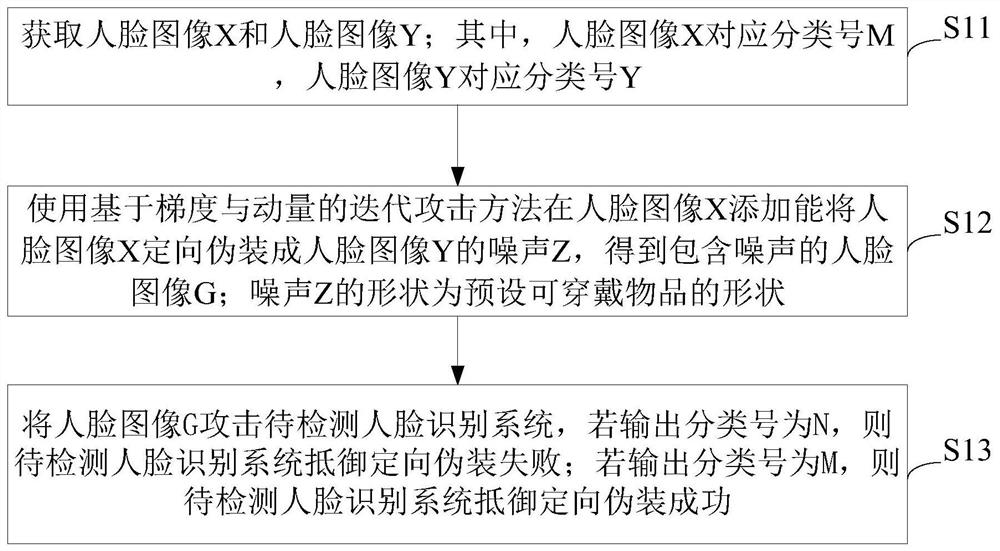
[0039] see figure 1 , a method for detecting face recognition systems against masquerading attacks, comprising:
[0040] S11, acquiring face image X and face image Y; wherein, face image X corresponds to classification number M, and face image Y corresponds to classification number N; before step S1, it includes: collecting face image data, and processing face image data Perform preprocessing to obtain a face dataset M including face images X and Y.
[0041]Furthermore, the preprocessing of the face image data includes: locating the face in the face image data, extracting the face area and feature points, aligning and saving all the faces according to the feature points, and obtaining the aligned face Face dataset M; After face alignment, the 68 checkpoints of all face images in the face dataset M are distributed in the same position.
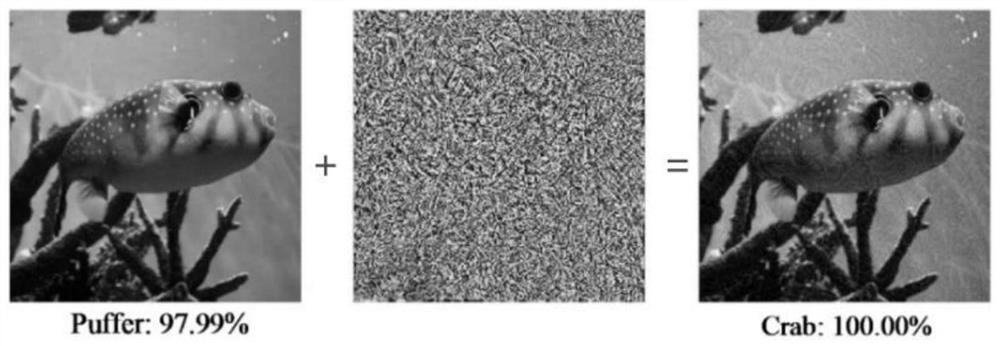
[0042] S12, using an iterative attack method based on gradient and momentum to add noise Z to the face image X that can disguise the face im...
Embodiment 2
[0070] The difference between Embodiment 2 and Embodiment 1 is that the iterative attack method based on gradient and momentum is used to add noise Z to the face image X to misclassify the face image X. In terms of the judgment of the face recognition system to be detected, if the face recognition system to be detected determines that the face image G and the face image X are not the same person, the face recognition system to be detected fails to resist the directional camouflage attack; if the face recognition system to be detected If the system determines that the face image G and the face image X are the same person, the face recognition system to be detected succeeds in resisting masquerade.
[0071] In summary, the present invention has the following beneficial effects:
[0072] 1. The present invention uses an iterative attack method based on gradient and momentum, which can add disturbances in the shape of glasses, hats, headscarves, scarves, etc. to the face picture, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com