Patents
Literature
86 results about "Shadow memory" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
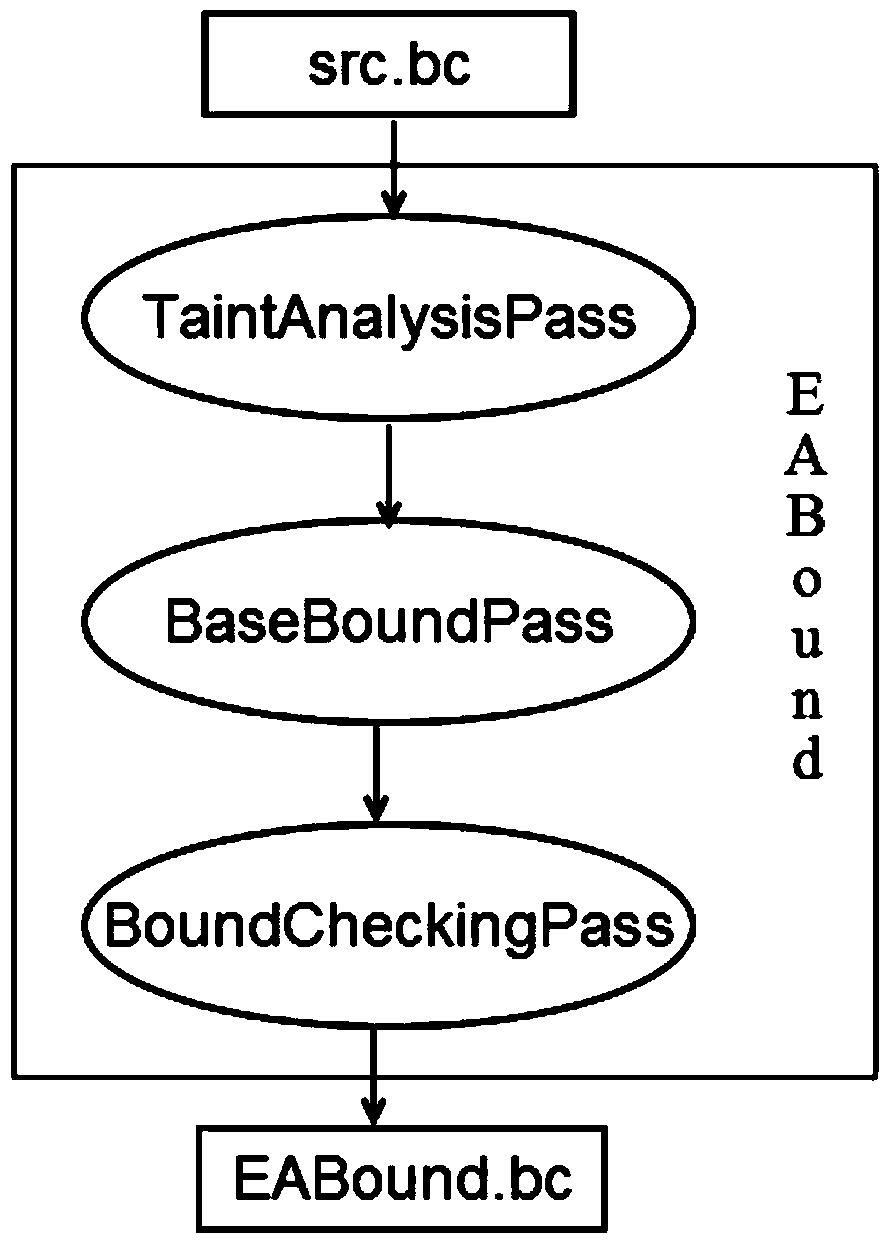
Shadow memory is a technique used to track and store information on computer memory used by a program during its execution. Shadow memory consists of shadow bytes that map to individual bits or one or more bytes in main memory. These shadow bytes are typically invisible to the original program and are used to record information about the original piece of data.
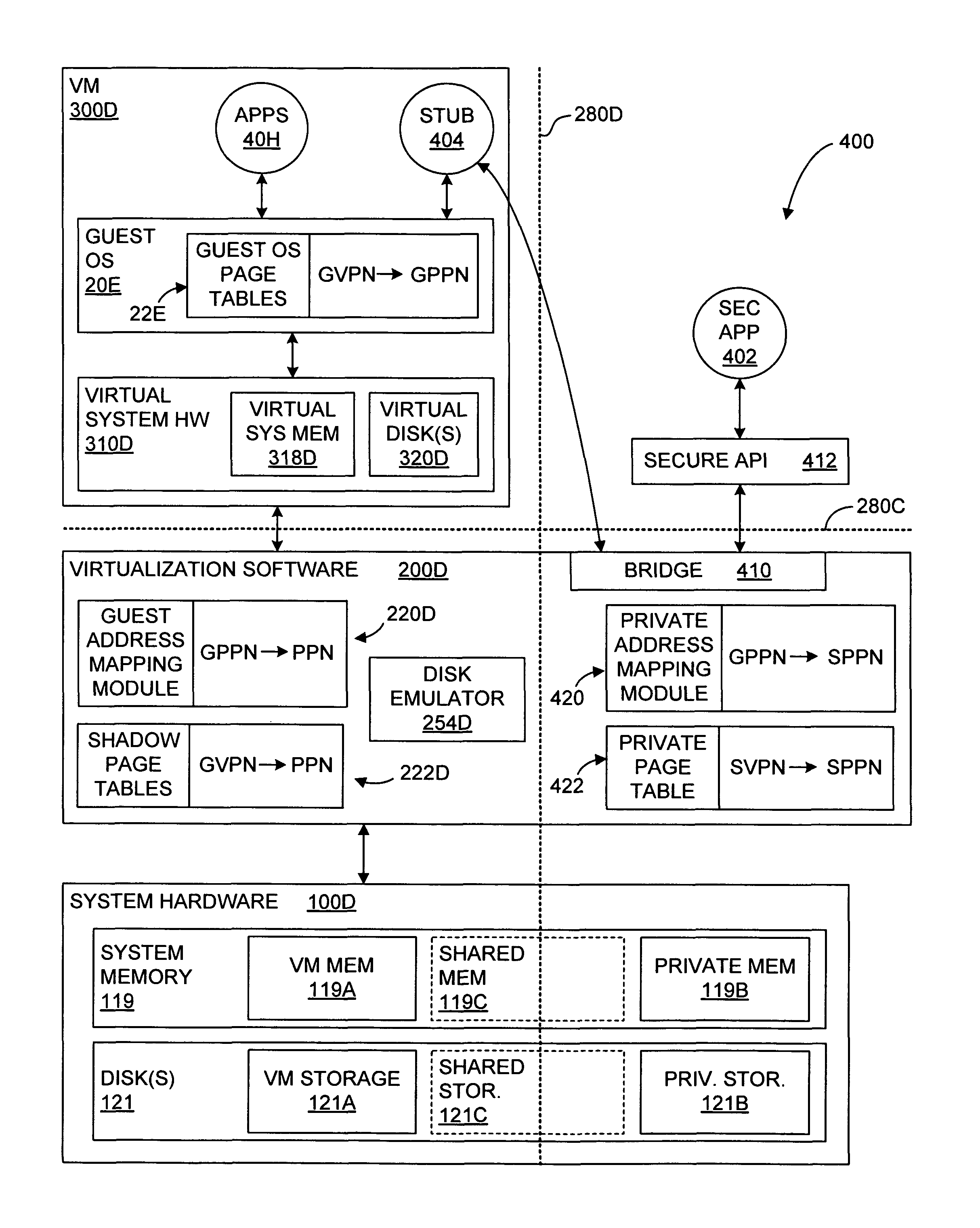
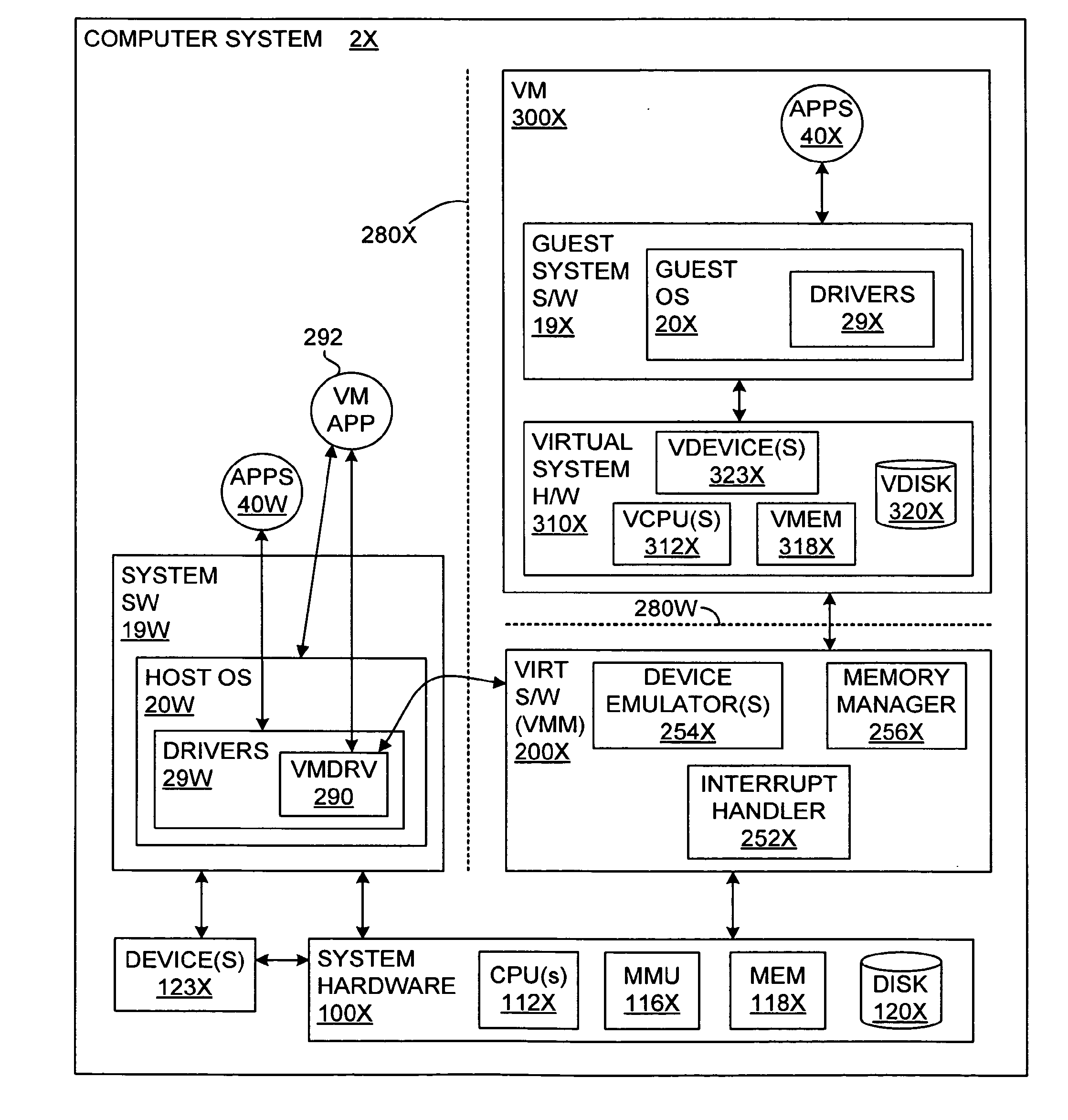
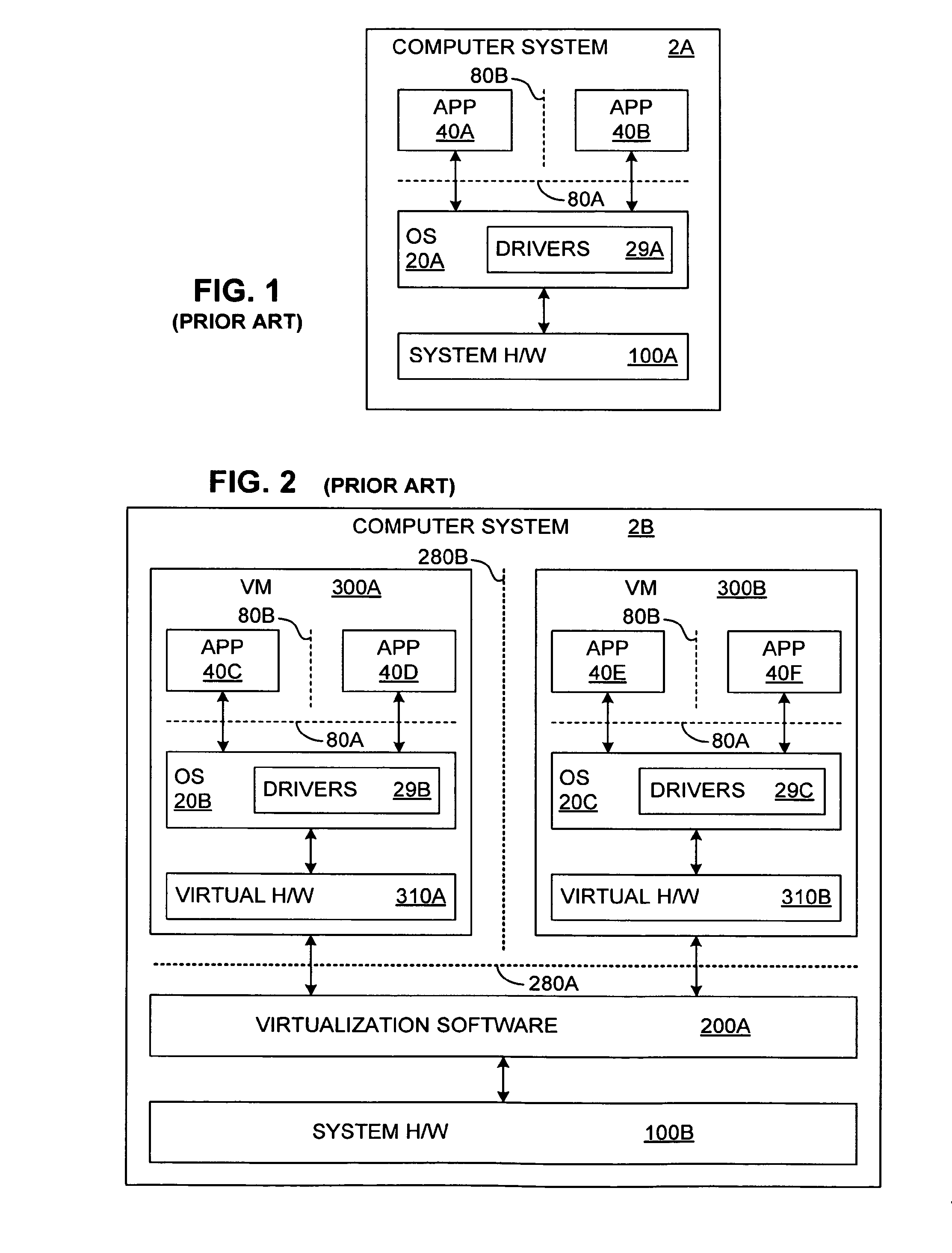
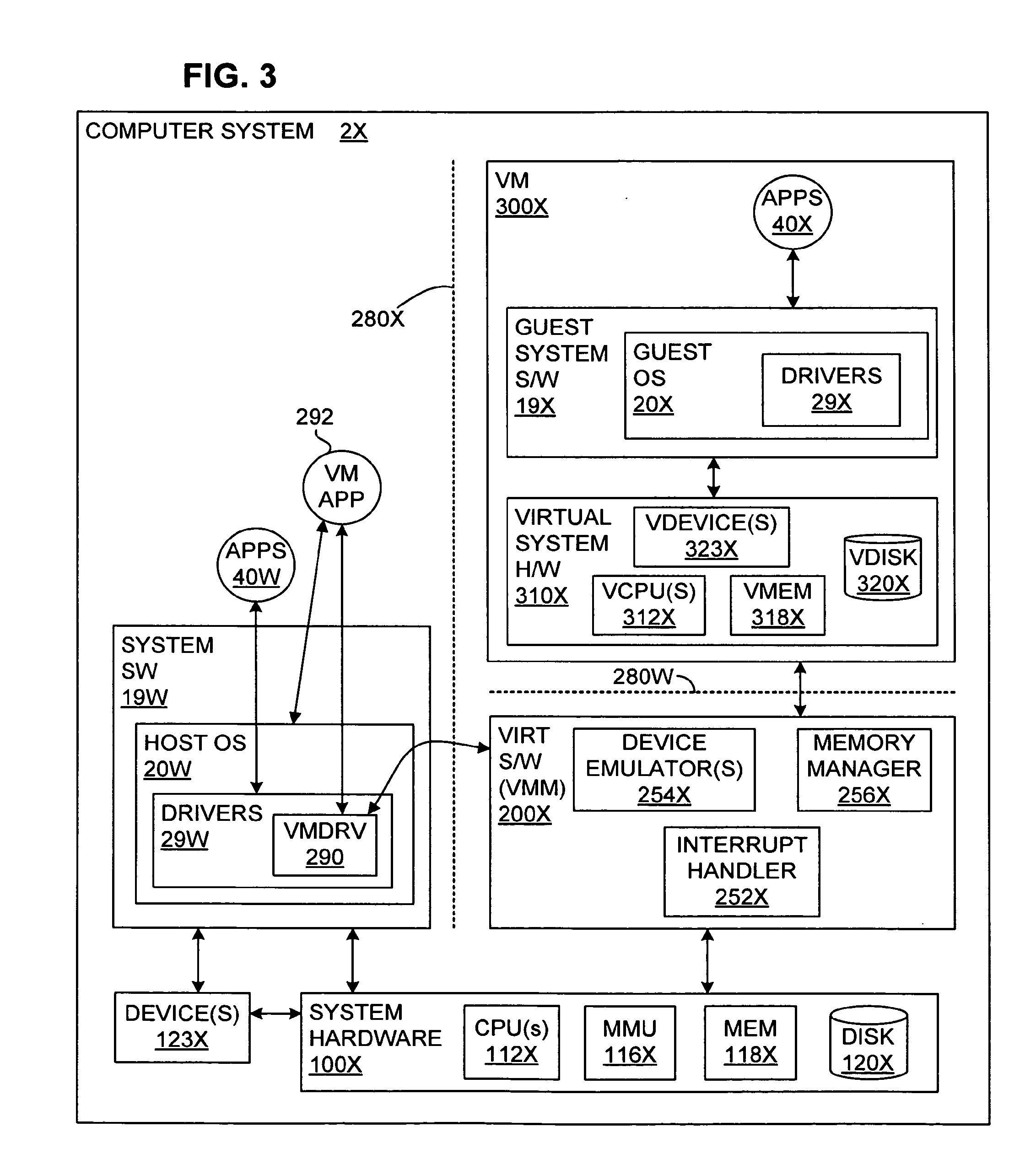
Isolating data within a computer system using private shadow mappings
ActiveUS9274974B1Avoid accessMemory architecture accessing/allocationMemory adressing/allocation/relocationVirtualizationShadow mapping
Virtualization software establishes multiple execution environments within a virtual machine, wherein software modules executing in one environment cannot access private memory of another environment. A separate set of shadow memory address mappings is maintained for each execution environment. For example, a separate shadow page table may be maintained for each execution environment. The virtualization software ensures that the shadow address mappings for one execution environment do not map to the physical memory pages that contain the private code or data of another execution environment. When execution switches from one execution environment to another, the virtualization software activates the shadow address mappings for the new execution environment. A similar approach, using separate mappings, may also be used to prevent software modules in one execution environment from accessing the private disk space or other secondary storage of another execution environment.
Owner:VMWARE INC
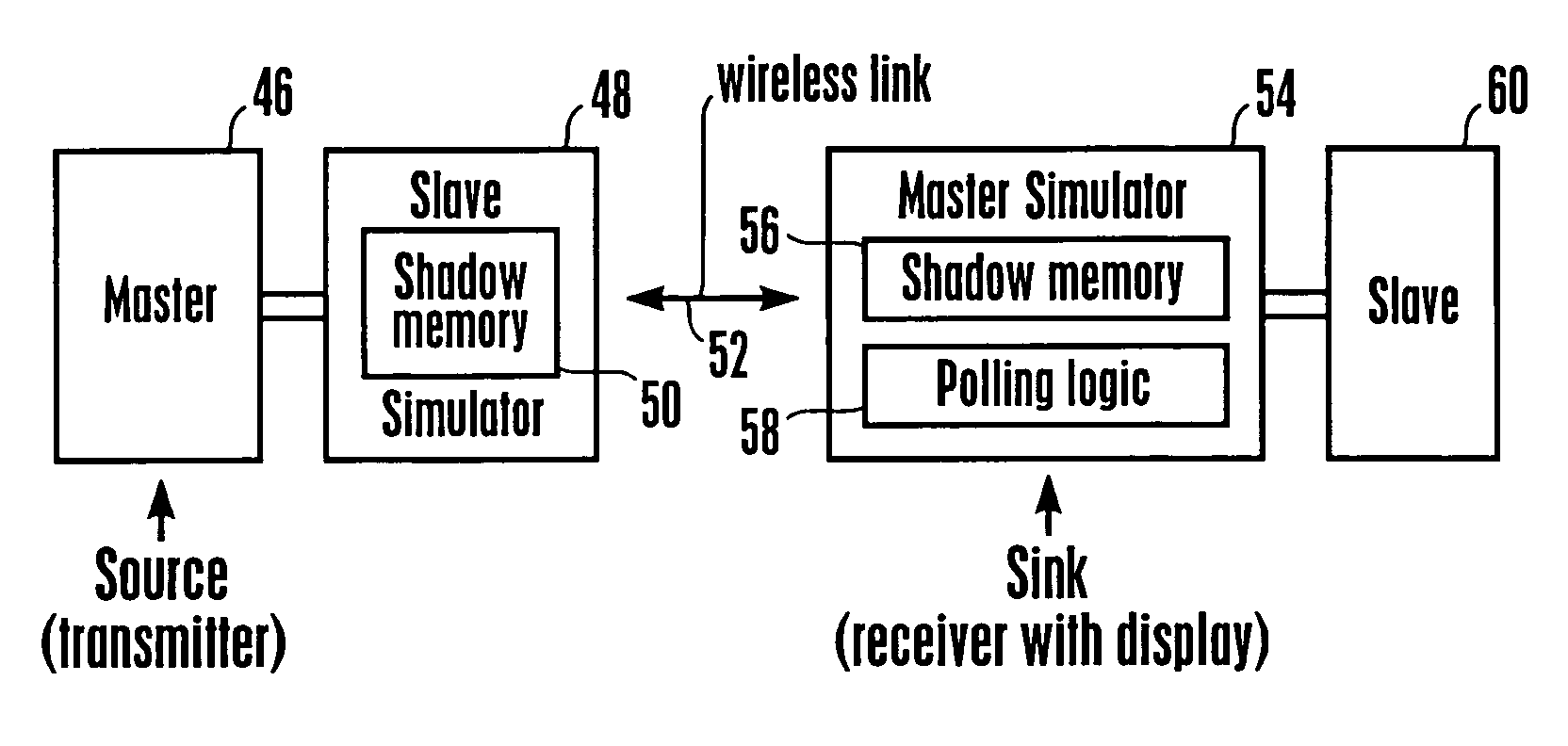
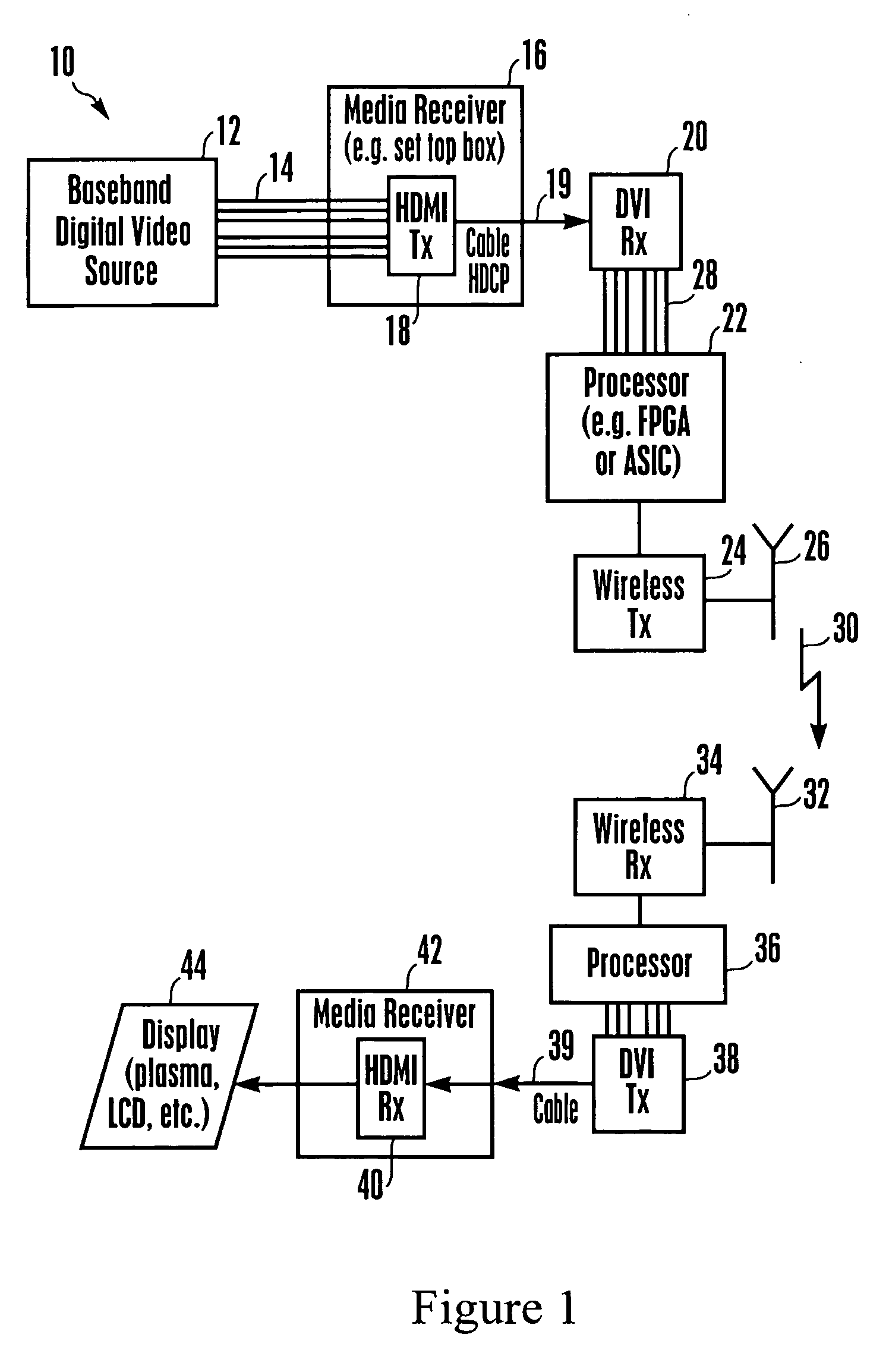
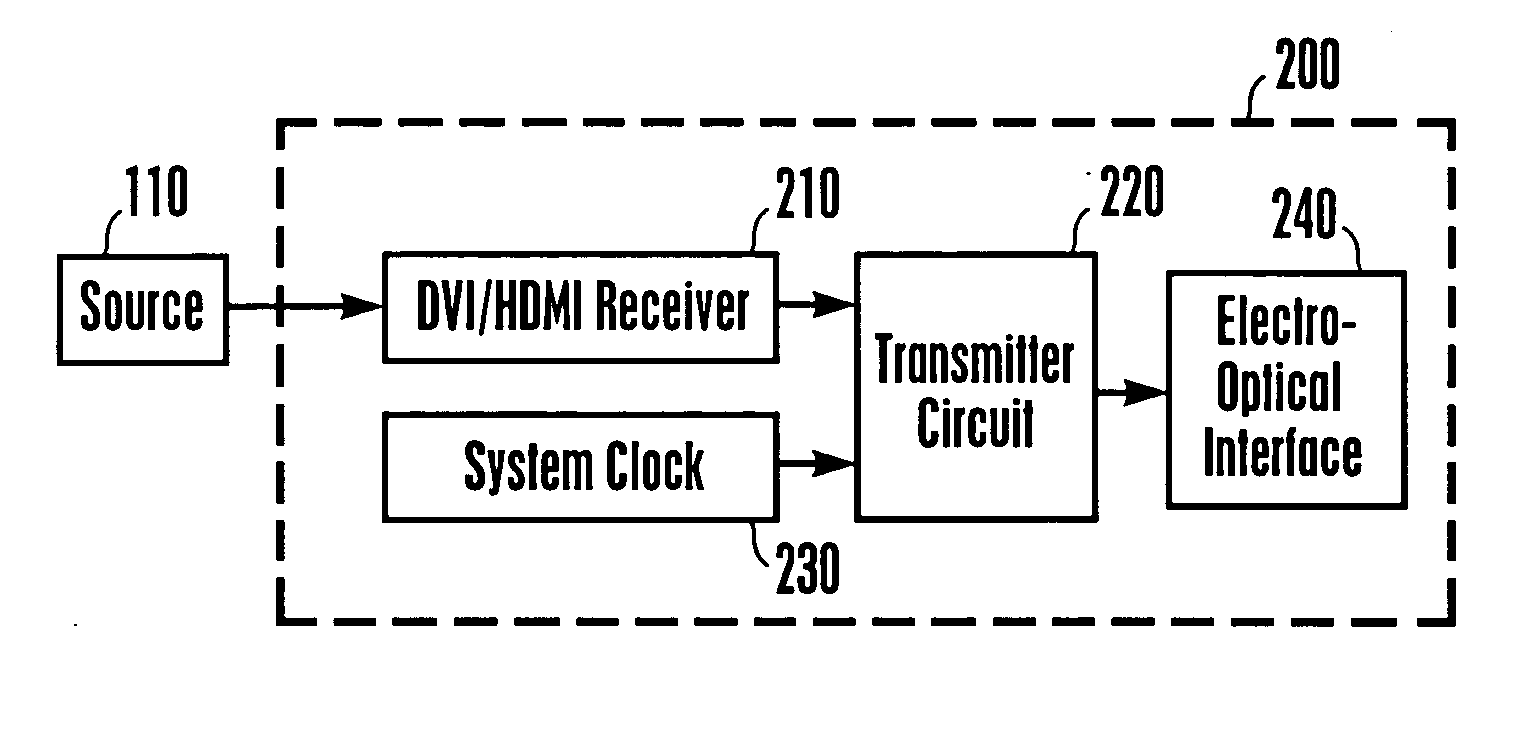
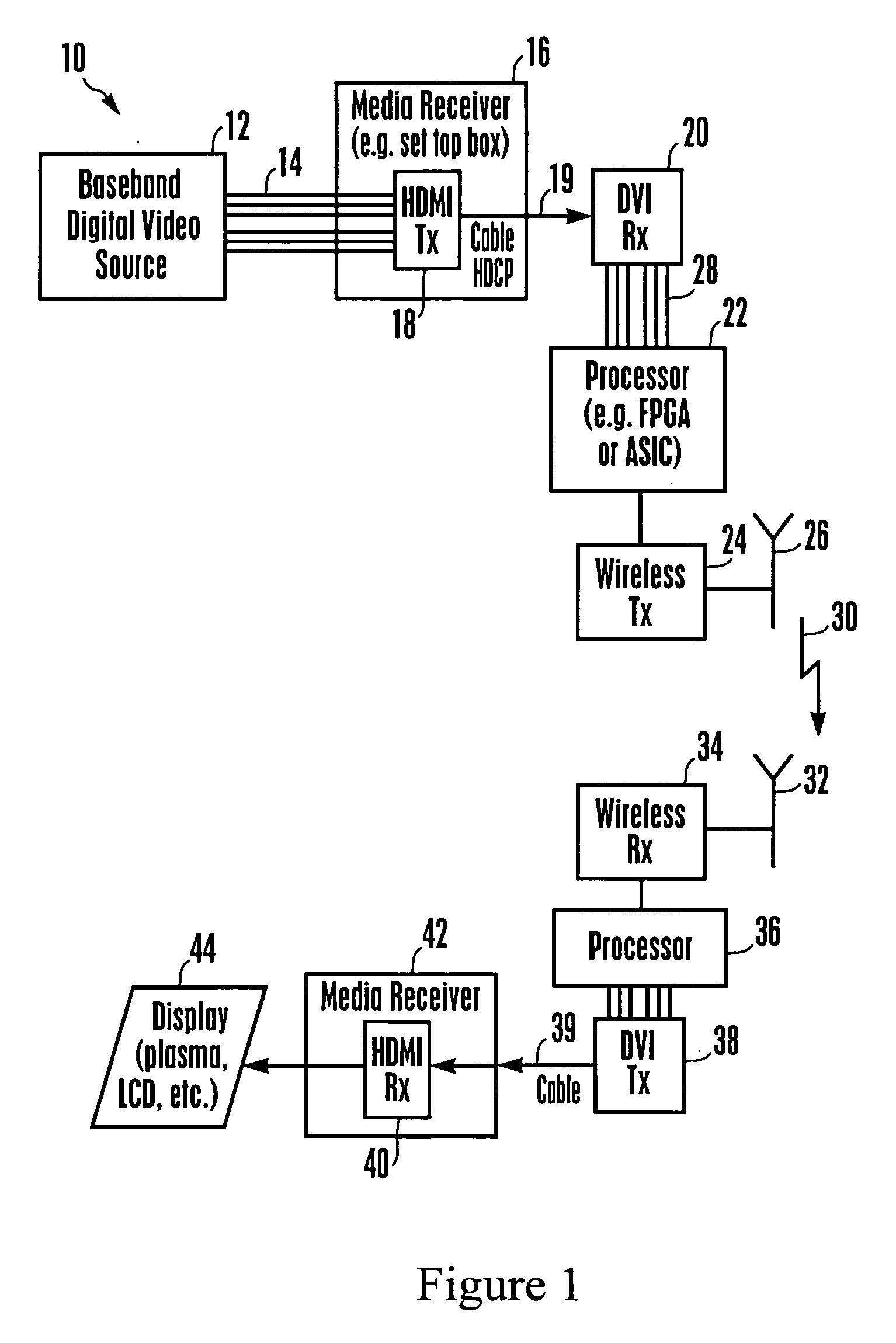
Method and system for processing wireless digital multimedia
InactiveUS20060095638A1Television system detailsCathode-ray tube indicatorsComputer graphics (images)Shadow memory
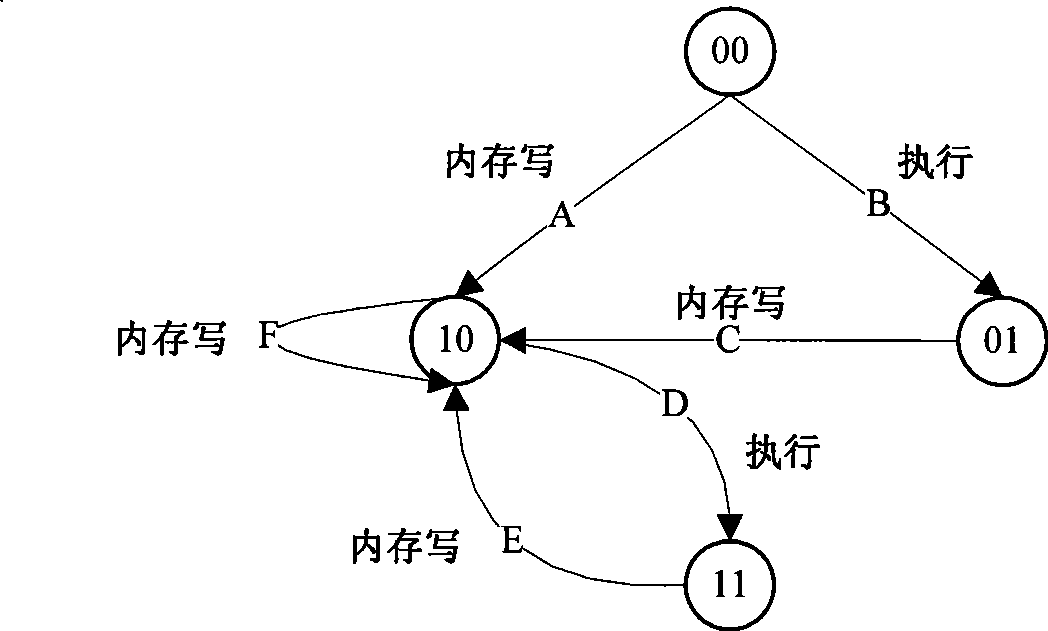
Multimedia from a source can be wirelessly transmitted in a 60 GHz system to a display. To support rapid reads of encryption, EDID, and other data written into a slave at the display by a master at the source in accordance with I2C protocol, a master simulator on the display side continually polls the slave for changes, and maintains a shadow memory in a slave simulator at the source side current, so that reads from the master may be immediately executed from the shadow memory in the slave simulator without transitting the wireless link.
Owner:SONY CORP +1
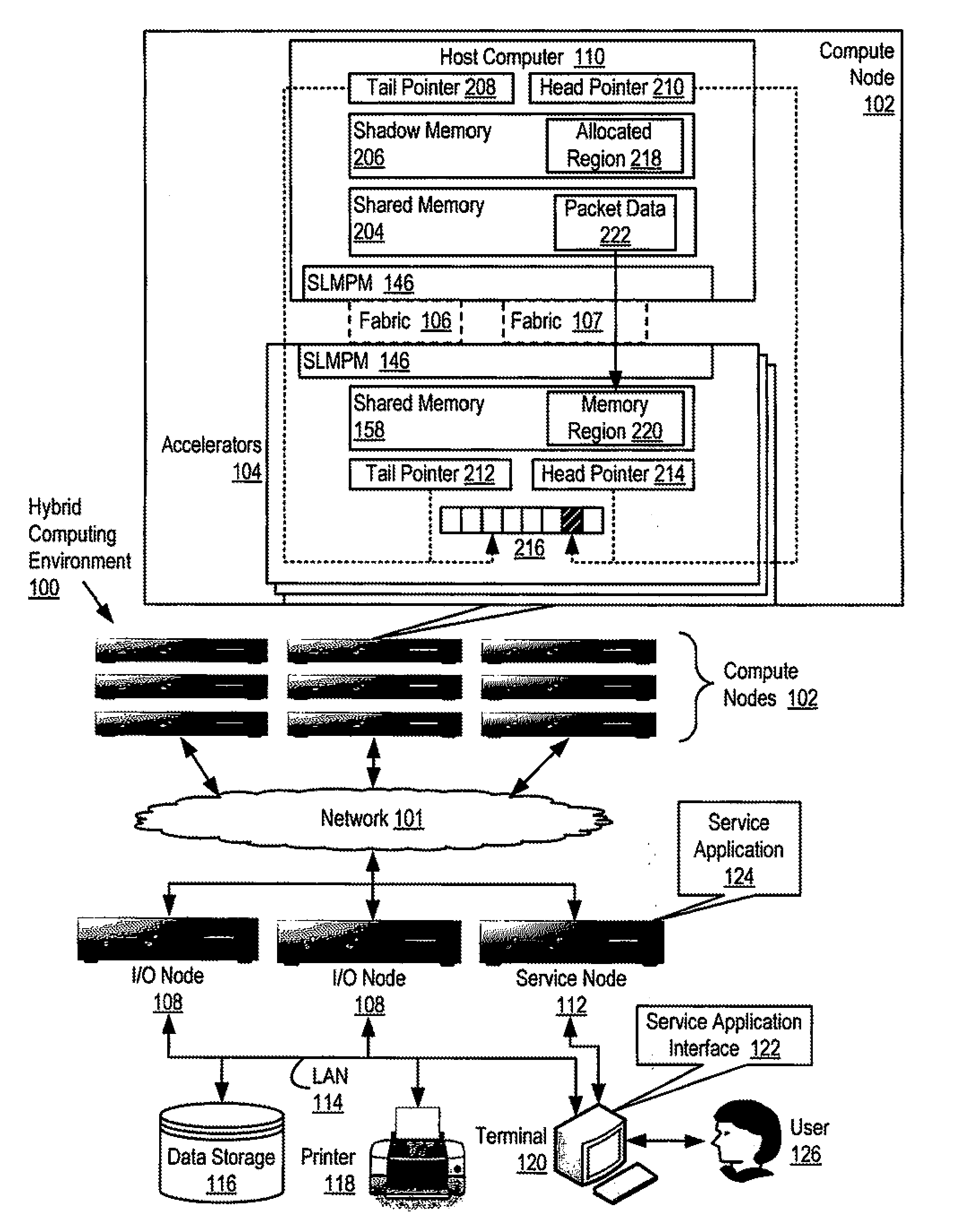
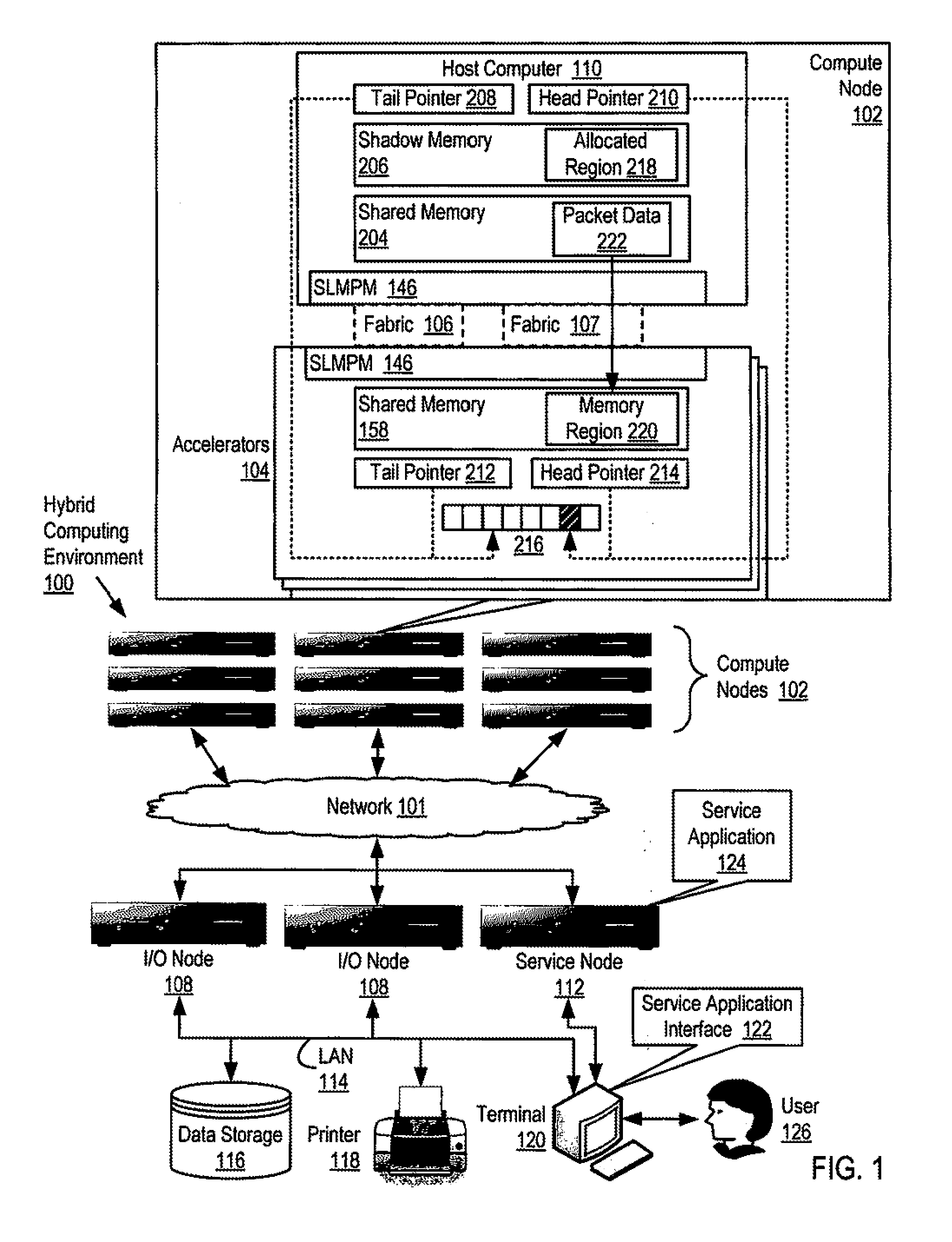
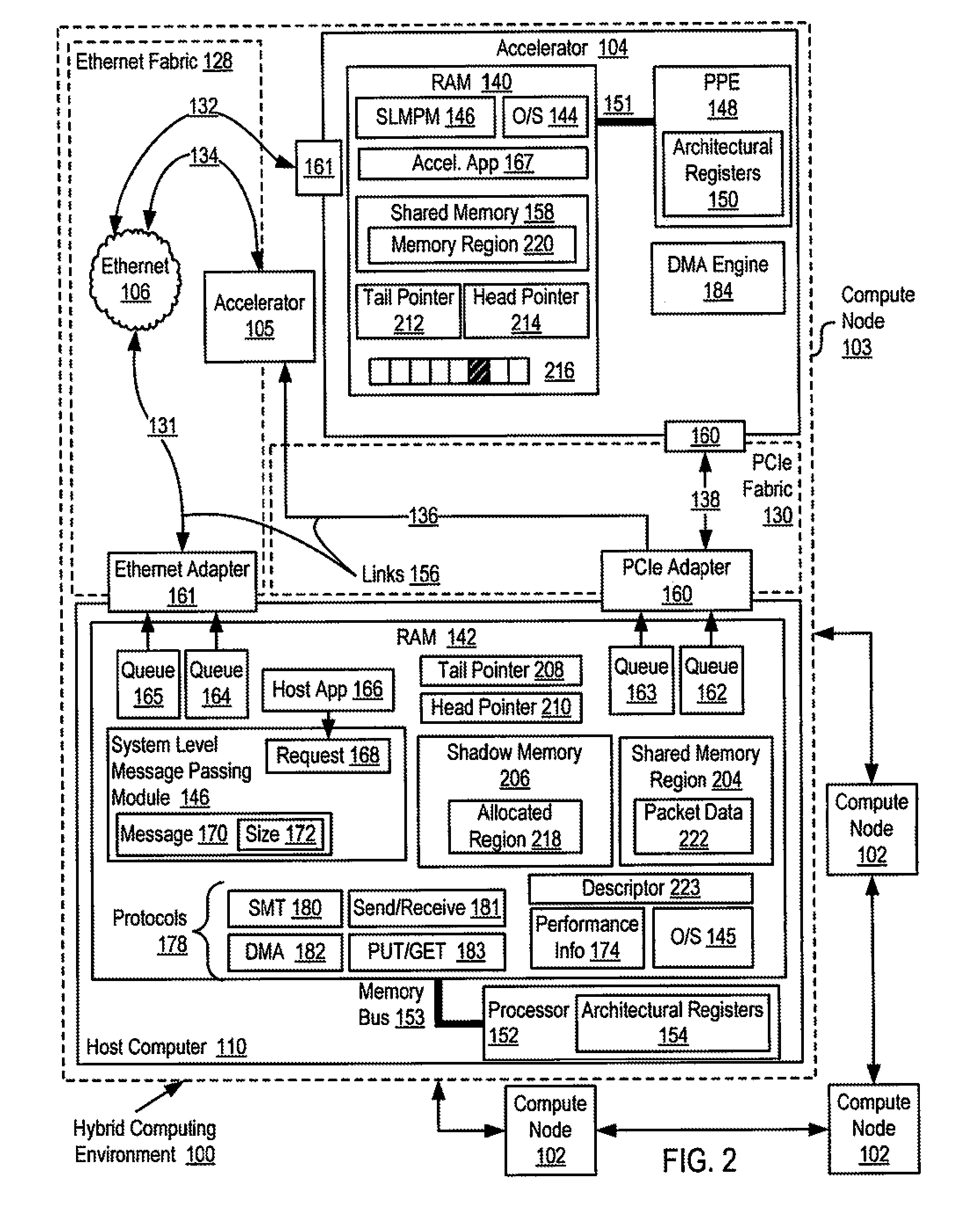
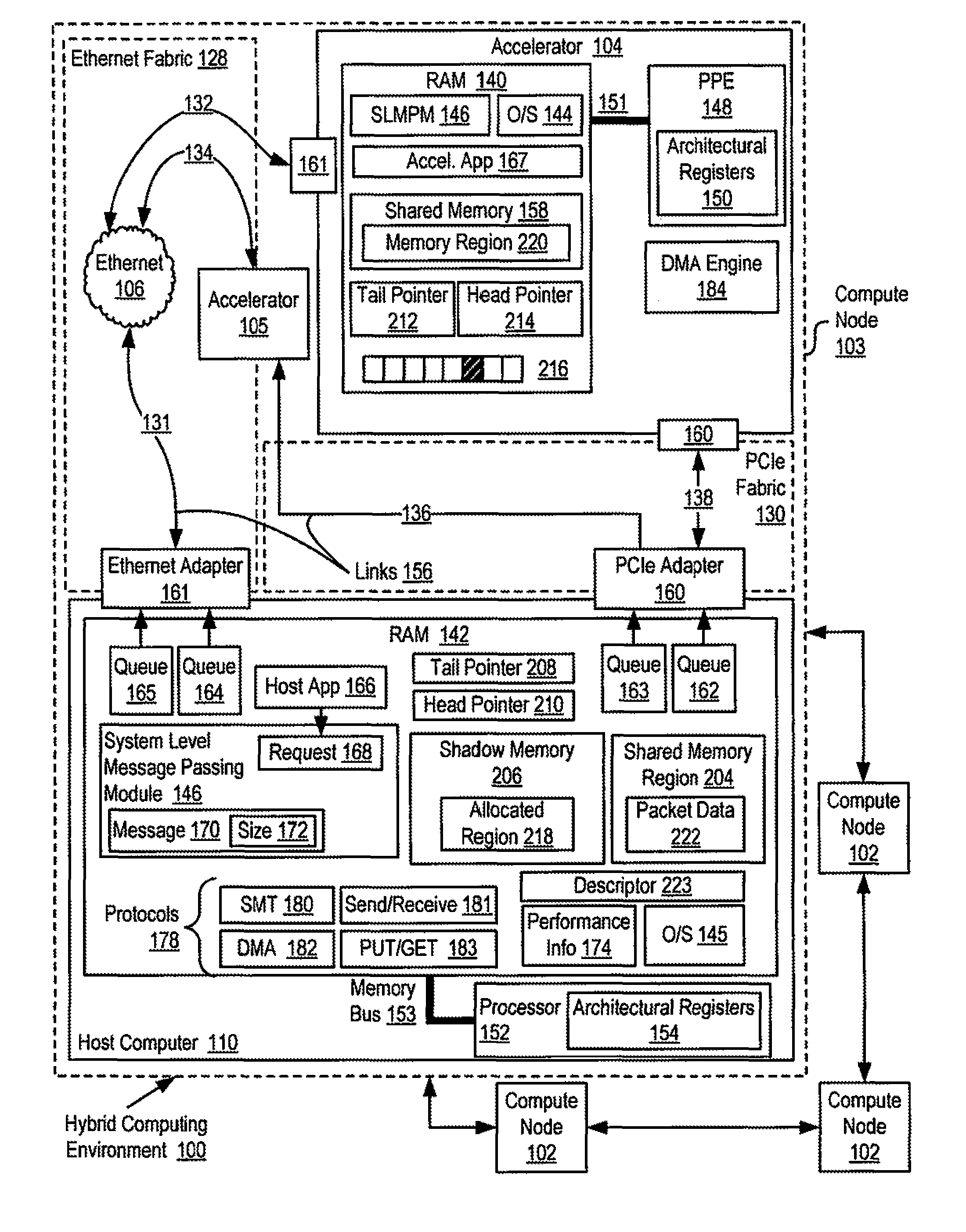
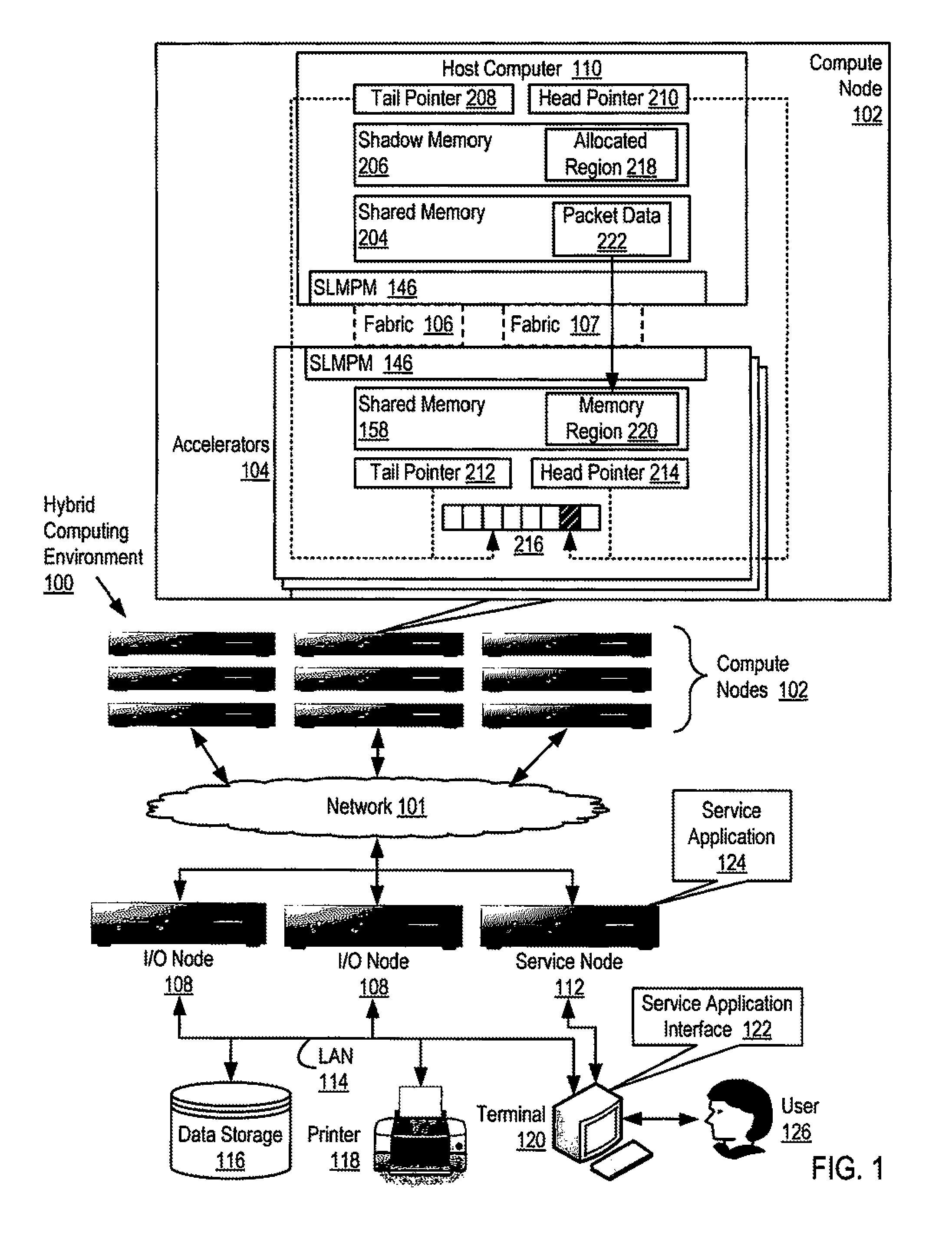
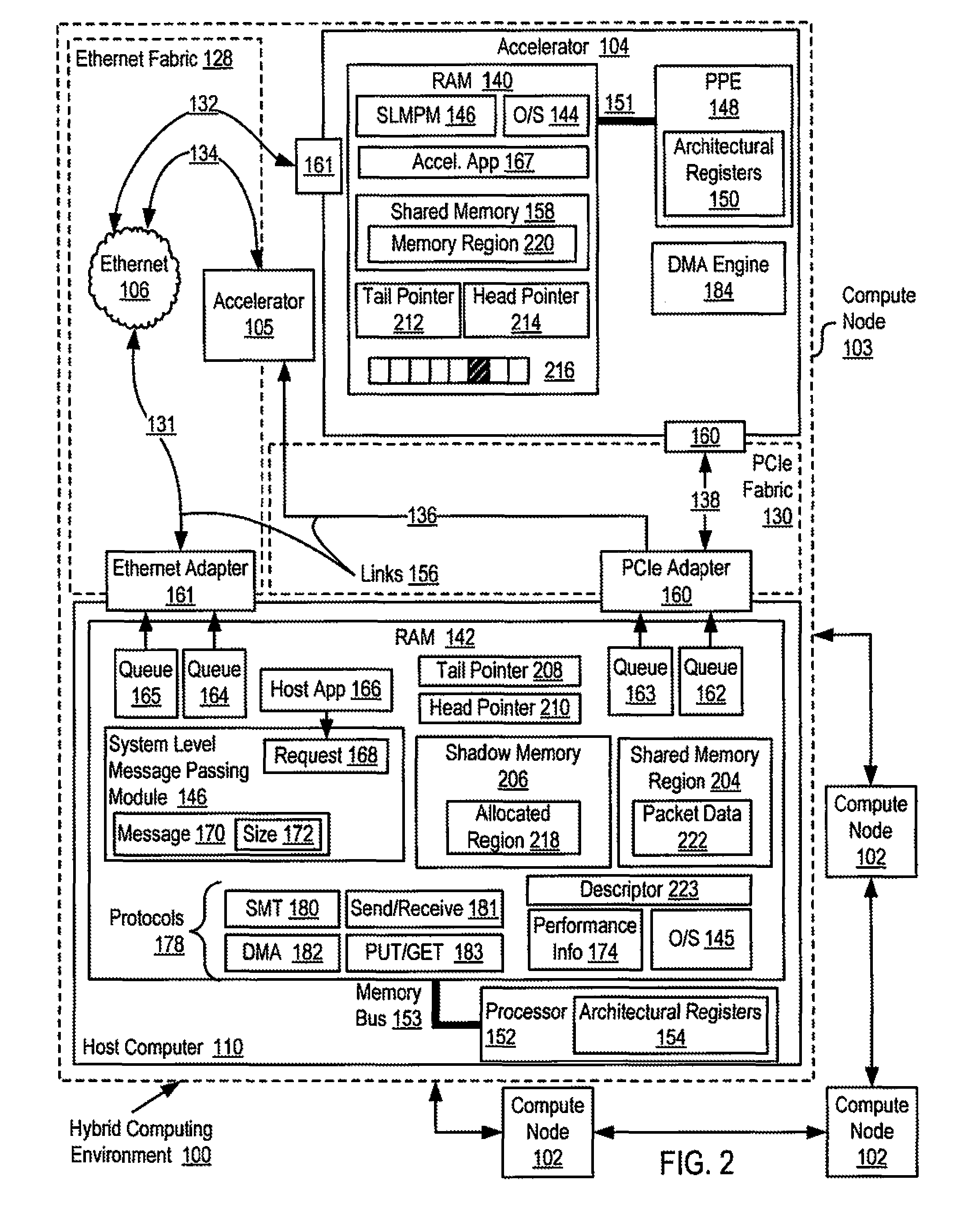
Reducing remote reads of memory in a hybrid computing environment
InactiveUS20110271059A1Reducing remote readMemory adressing/allocation/relocationDigital computer detailsArray data structureShadow memory
A hybrid computing environment in which the host computer allocates, in the shadow memory area of the host computer, a memory region for a packet to be written to the shared memory of an accelerator; writes packet data to the accelerator's shared memory in a memory region corresponding to the allocated memory region; inserts, in a next available element of the accelerator's descriptor array, a descriptor identifying the written packet data; increments the copy of the head pointer of the accelerator's descriptor array maintained on the host computer; and updates a copy of the head pointer of the accelerator's descriptor array maintained on the accelerator with the incremented copy.
Owner:IBM CORP
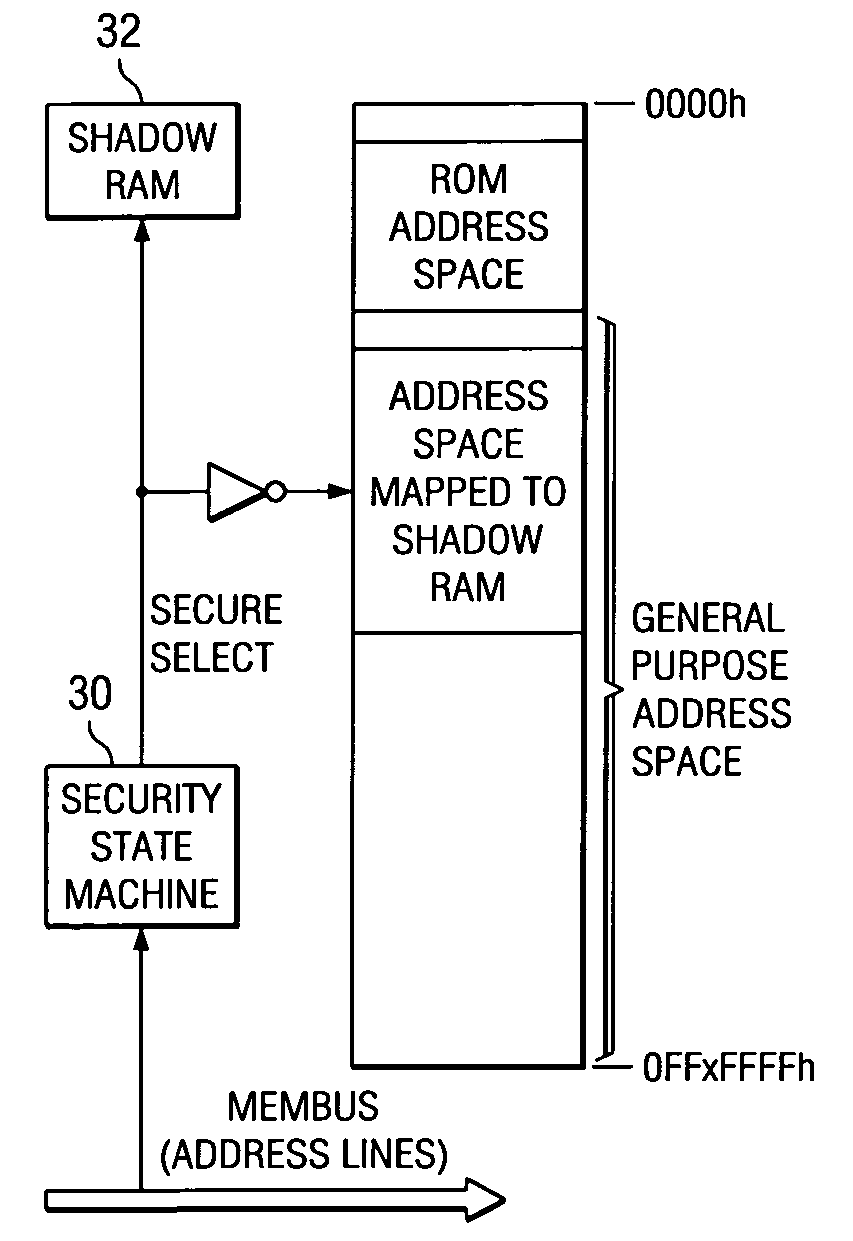
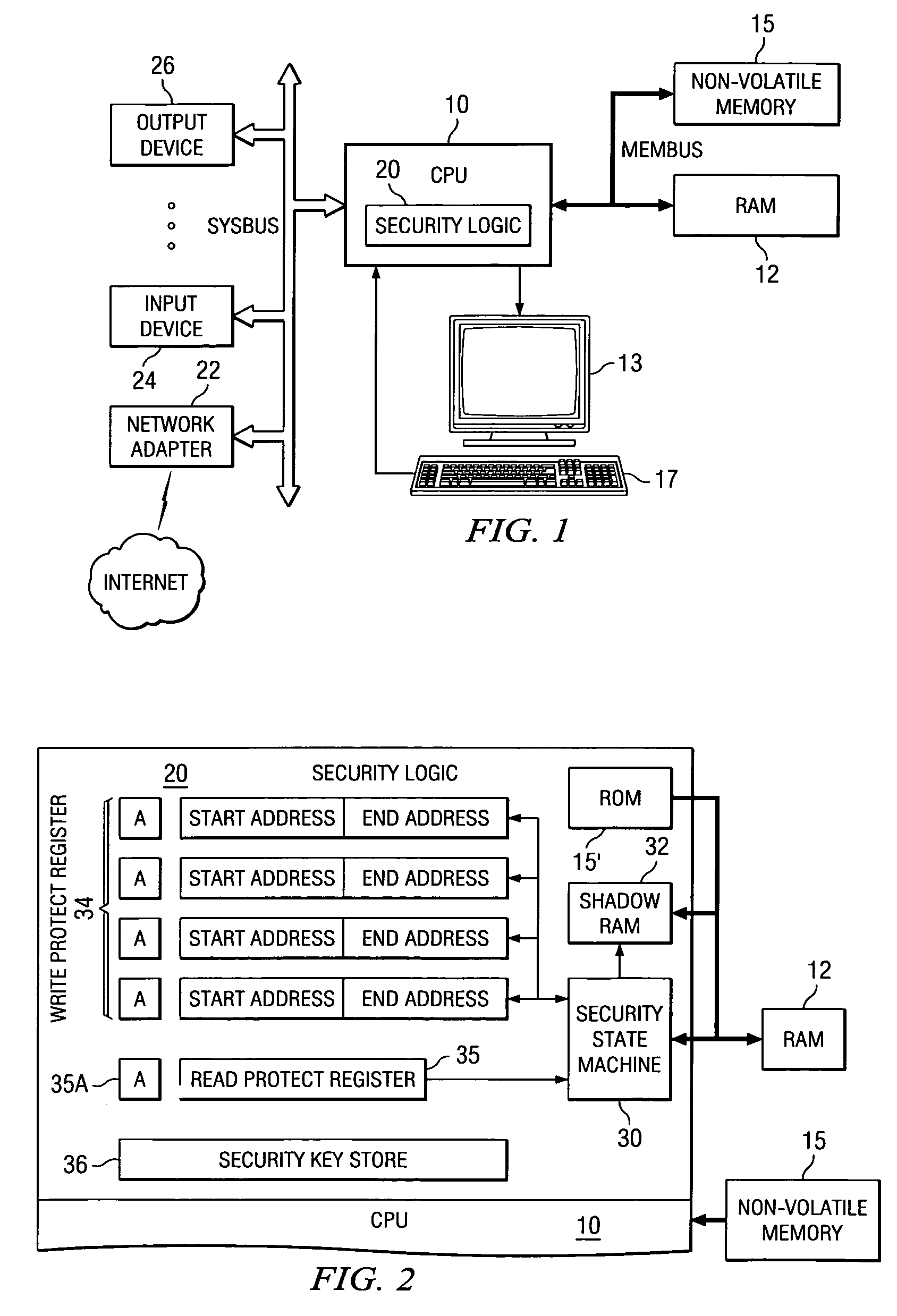
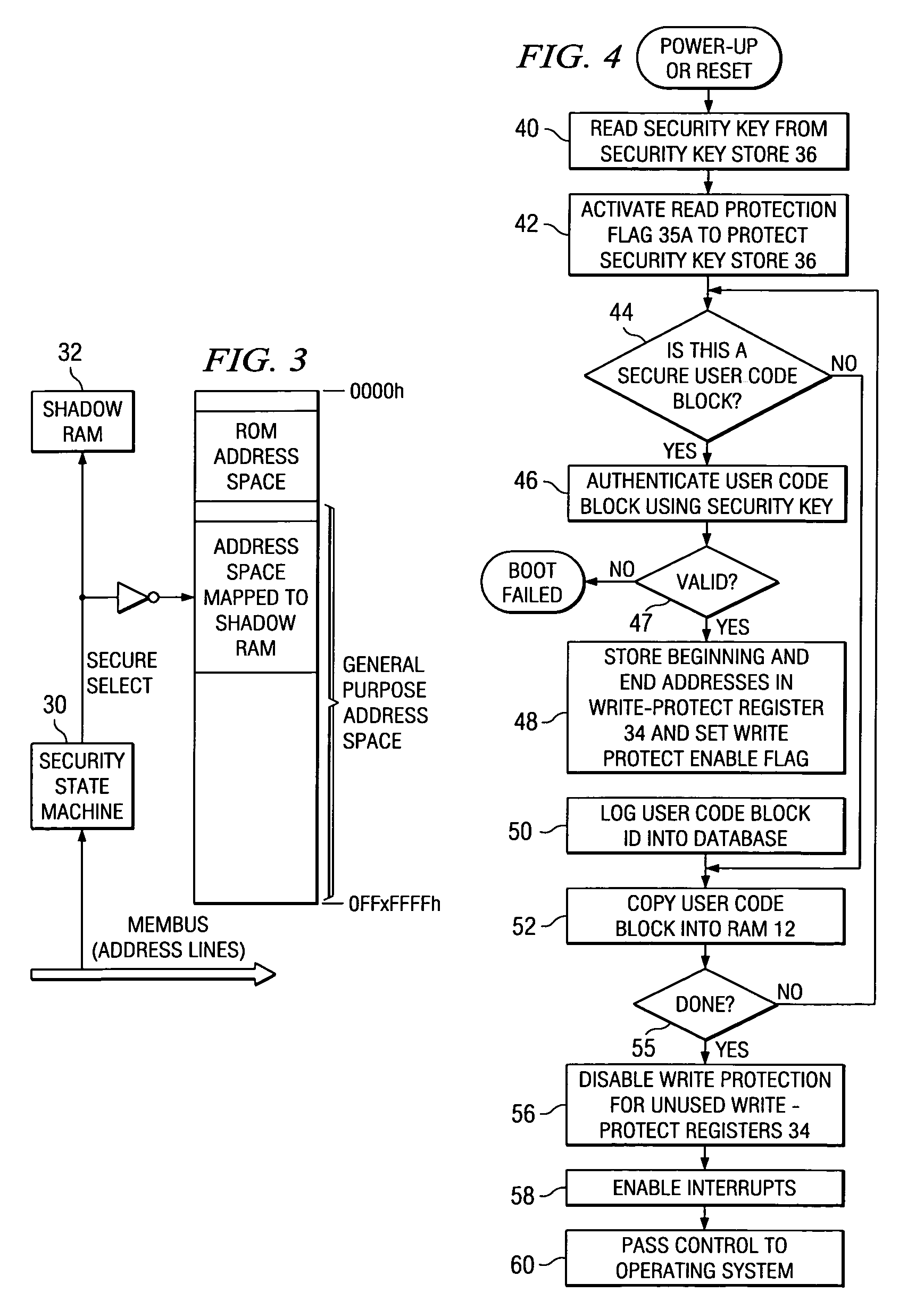
Implementation of a secure computing environment by using a secure bootloader, shadow memory, and protected memory
A computer system with a secure bootloading function is disclosed. Security logic (20) is implemented on-chip with a central processing unit (CPU) (10), and performs security functions following a system reset, such as upon power-up or a hardware or software reset. A security key value from a security key store (36), which is read-protected from subsequent read accesses, is used to authenticate each code block associated with secure applications. Write-protect registers (34) store the memory addresses of authenticated code blocks, so that these code blocks cannot be altered. A shadow memory (32) is provided on-chip with the CPU (10), to which access is granted for program instructions having a physical memory address within the memory address ranges stored in the write-protect registers (34), and thus usable by the secure applications. Successful authentication of the user code block ensures that the bootloaded code is not corrupt, prior to passing control to the operating system.
Owner:TEXAS INSTR INC
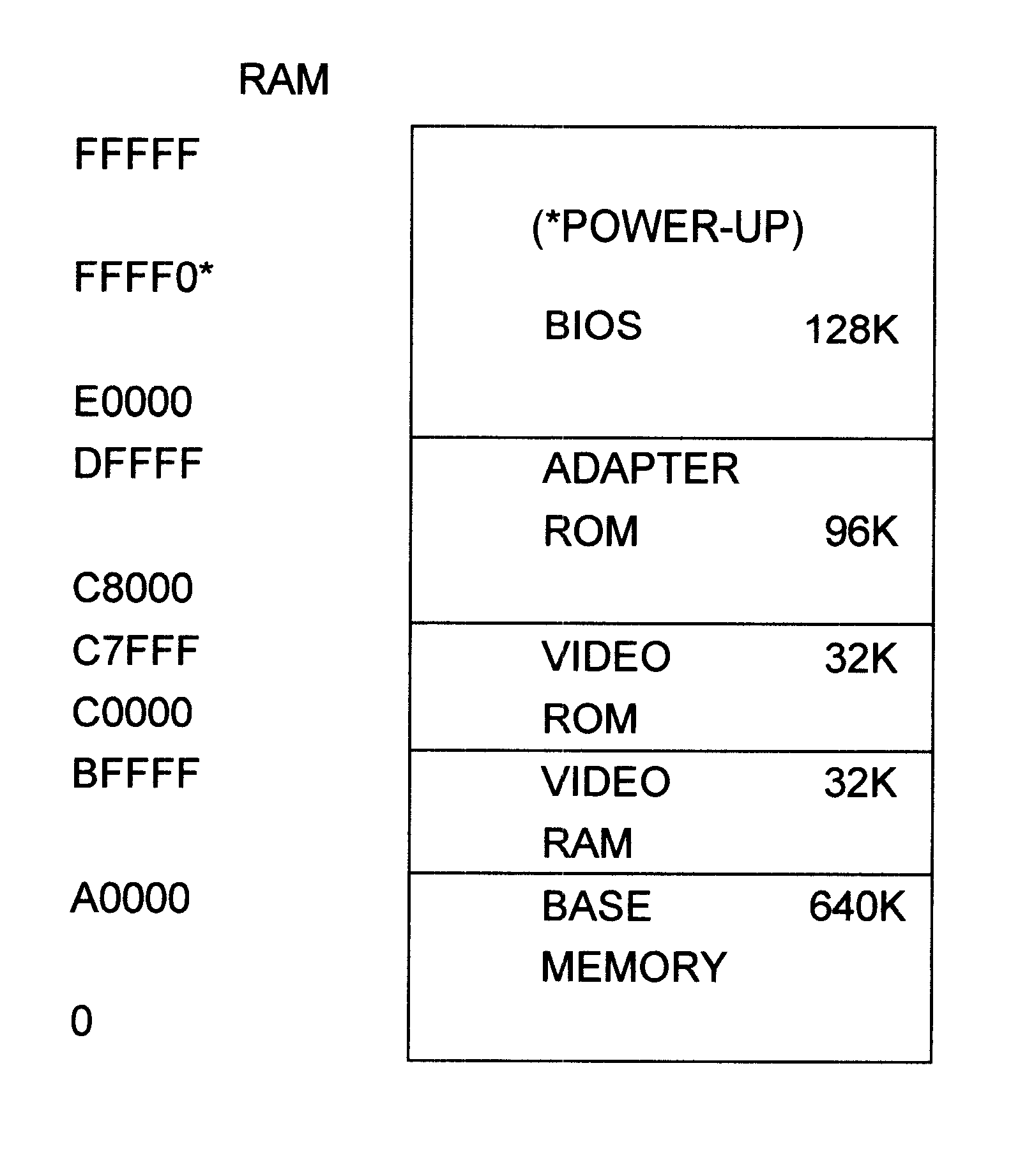
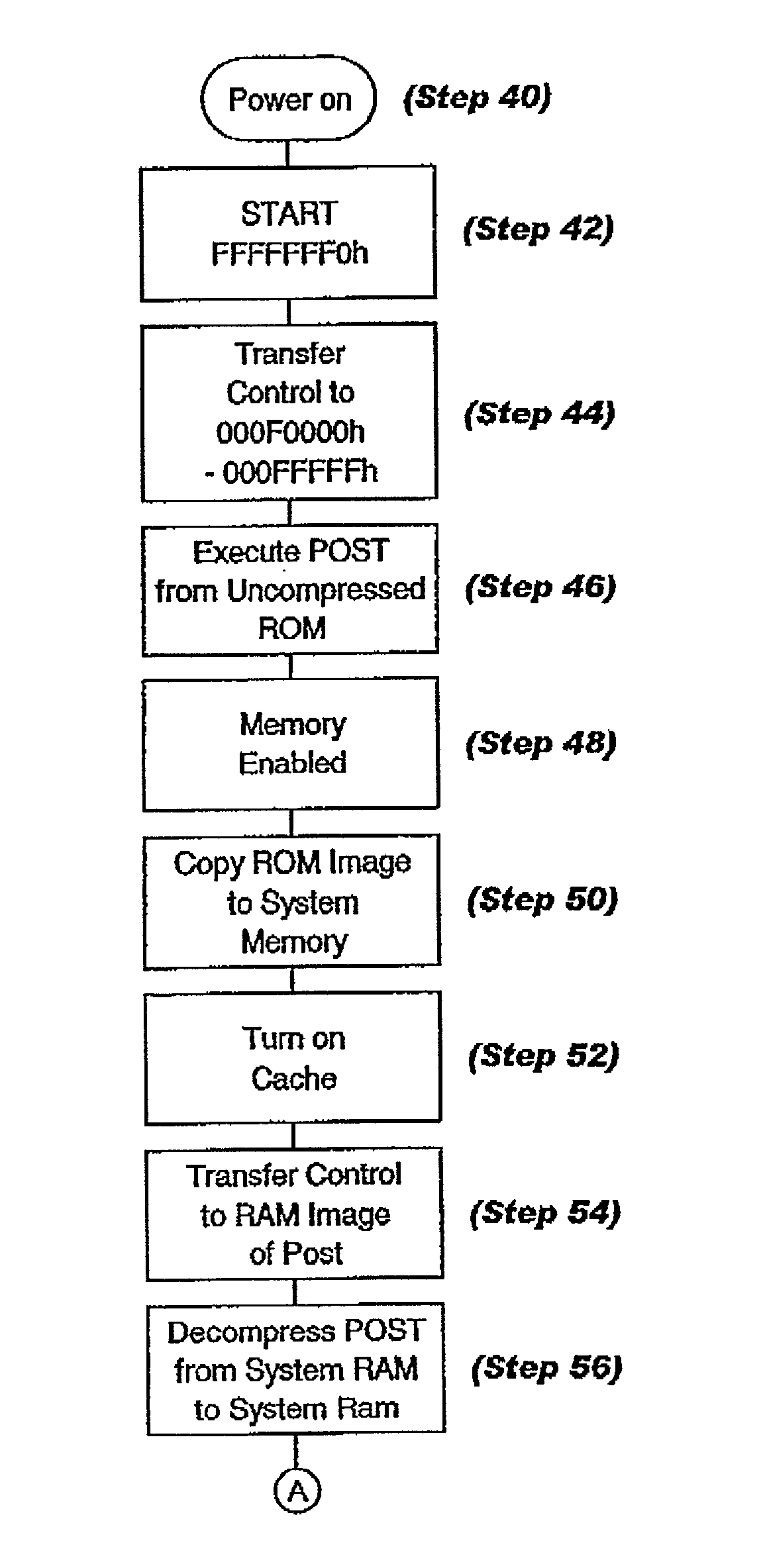
Data processor having BIOS packing compression/decompression architecture
InactiveUS6421776B1Maintain compatibilityShorten the timeDigital computer detailsCharacter and pattern recognitionShadow memoryParallel computing
To increase the effective capacity of BIOS, an initial portion of the power on system reset (POST) code that is required to enable the system memory is stored in ROM in uncompressed form, and substantially the remaining portion of the BIOS code is stored in compressed form. Upon system initialization during a cold boot, the uncompressed portion of POST is executed from the ROM to enable the system memory, and then an image of the BIOS code is written to shadow memory. As BIOS code is needed during the remainder of the boot, the code is selectively decompressed from the shadow memory to another region of the system memory to which control is transferred. Variations based upon different boot scenarios are described.
Owner:LENOVO PC INT
Semiconductor memory device
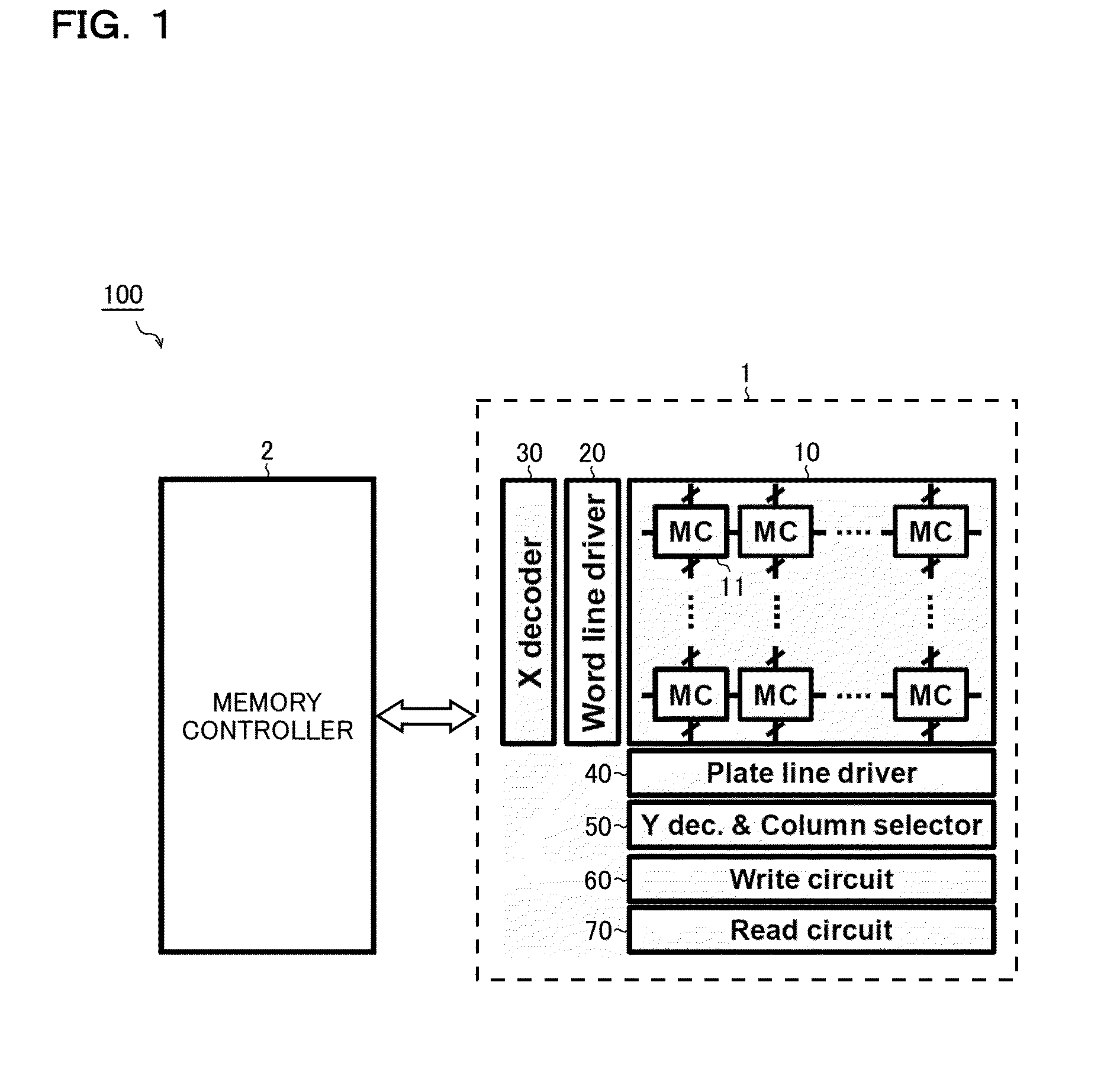
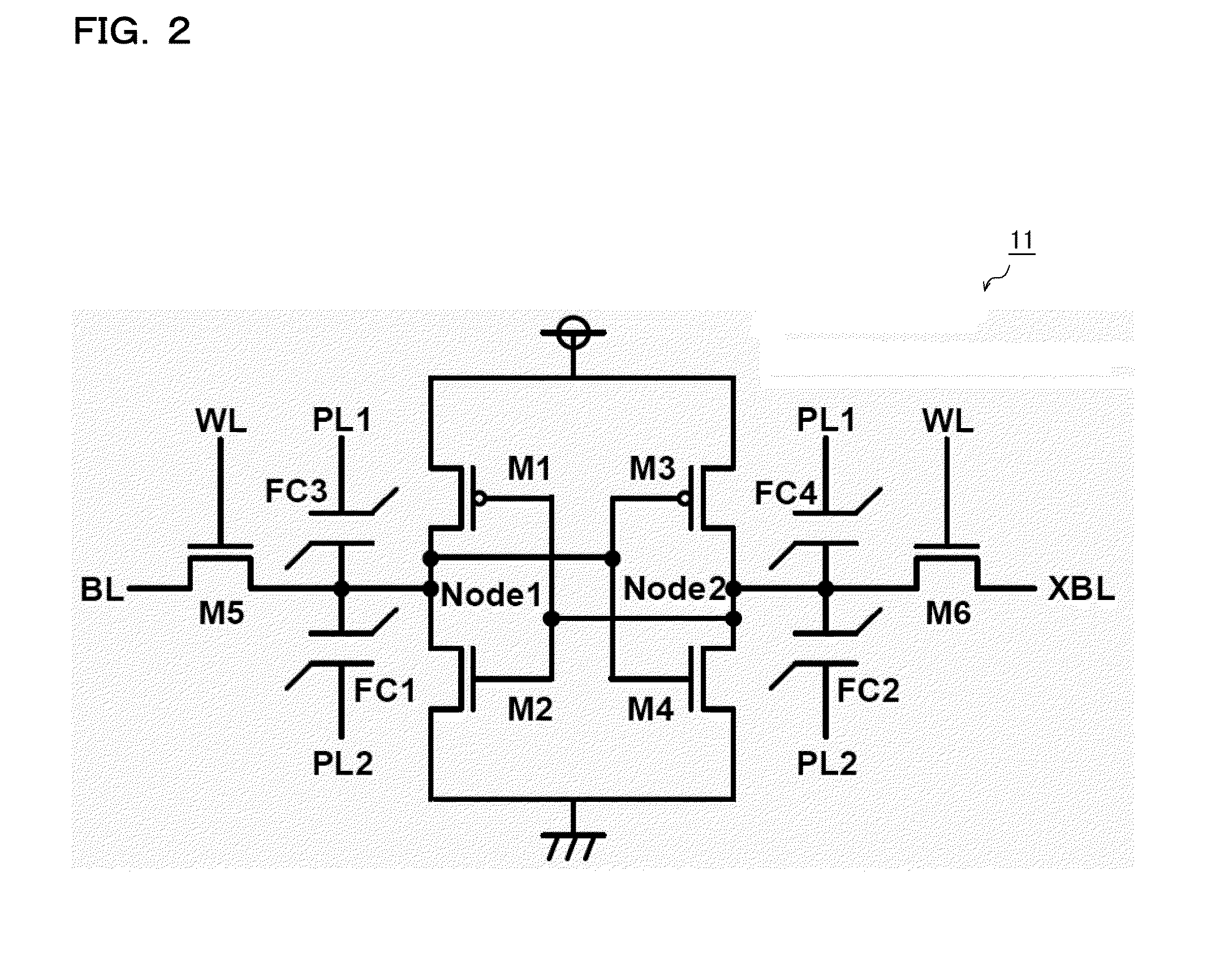
Proposed as a configuration, a controlling method, and a testing method for a ferroelectric shadow memory are (1) a bit line non-precharge method, in which no precharging of a bit line is performed during a read / write operation; (2) a plate line charge share method, in which electric charge is shared between plate lines that are driven sequentially during store / recall operation; (3) a word line boost method, in which the potential on a word line is raised during a write operation; (4) a plate line driver boost method, in which the driving capacity of a plate line driver is raised during a store / recall operation; and (5) a testing method for detecting a defect in a ferroelectric capacitor by arbitrarily setting a potential on a bit line from outside a chip.
Owner:ROHM CO LTD
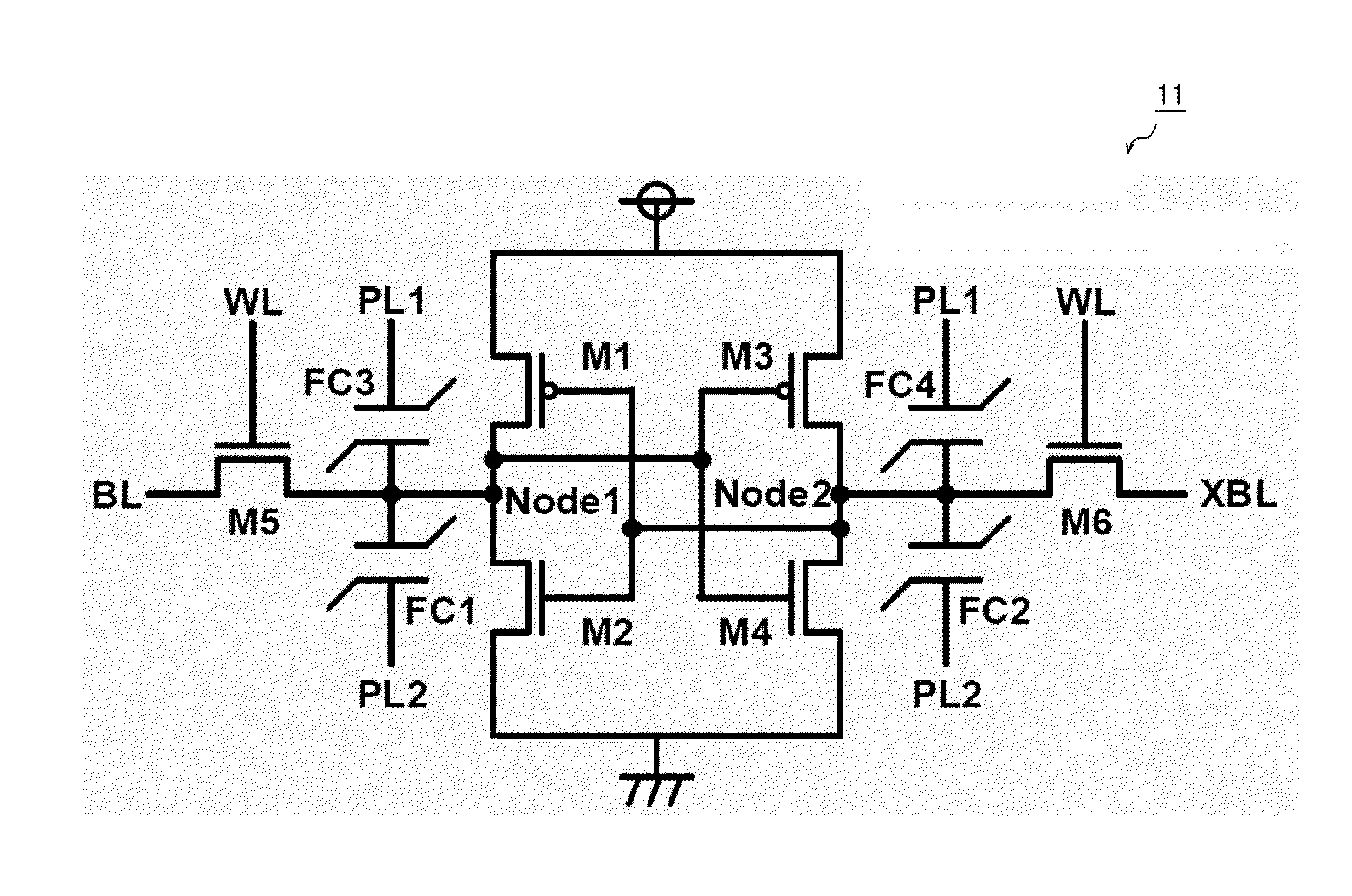
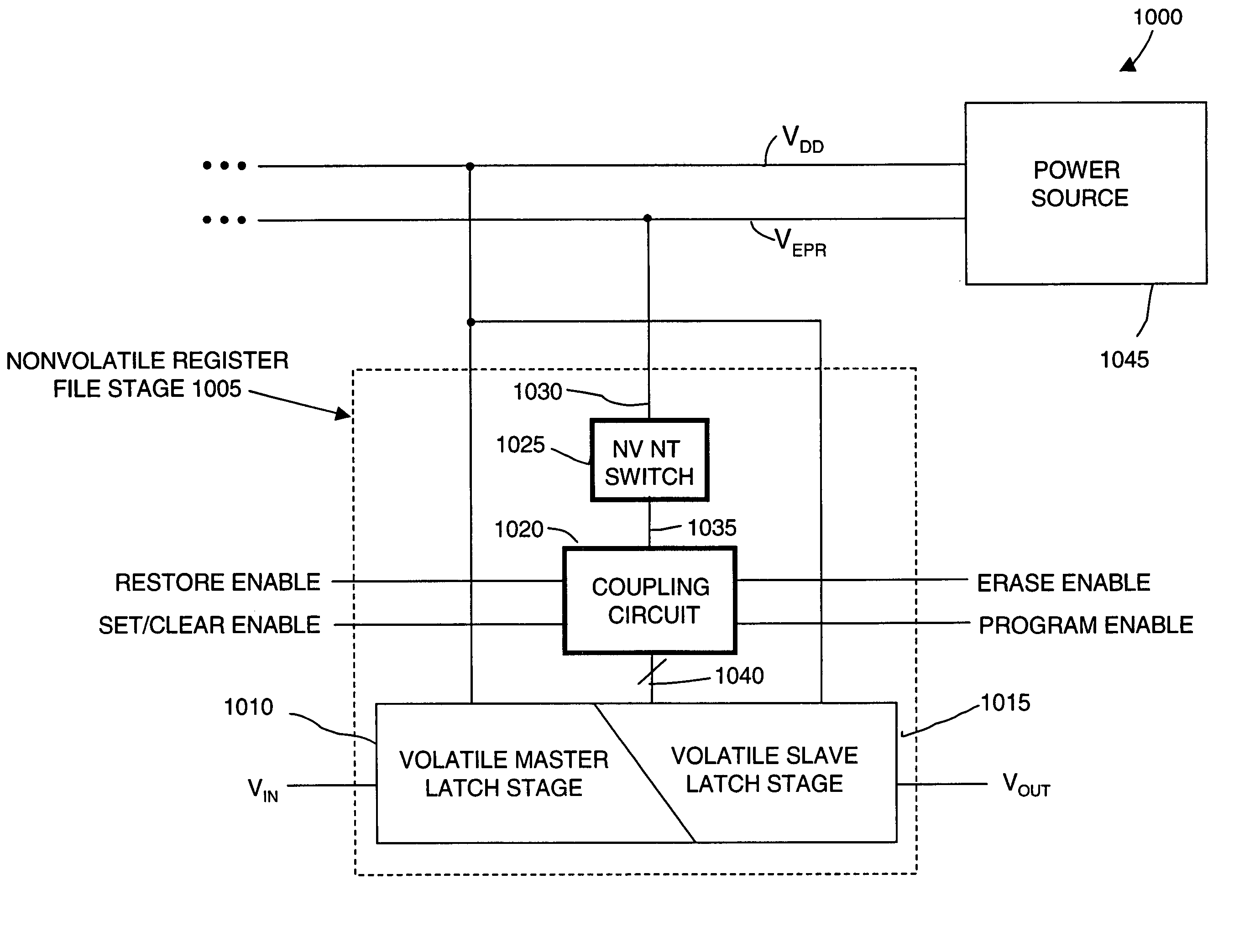
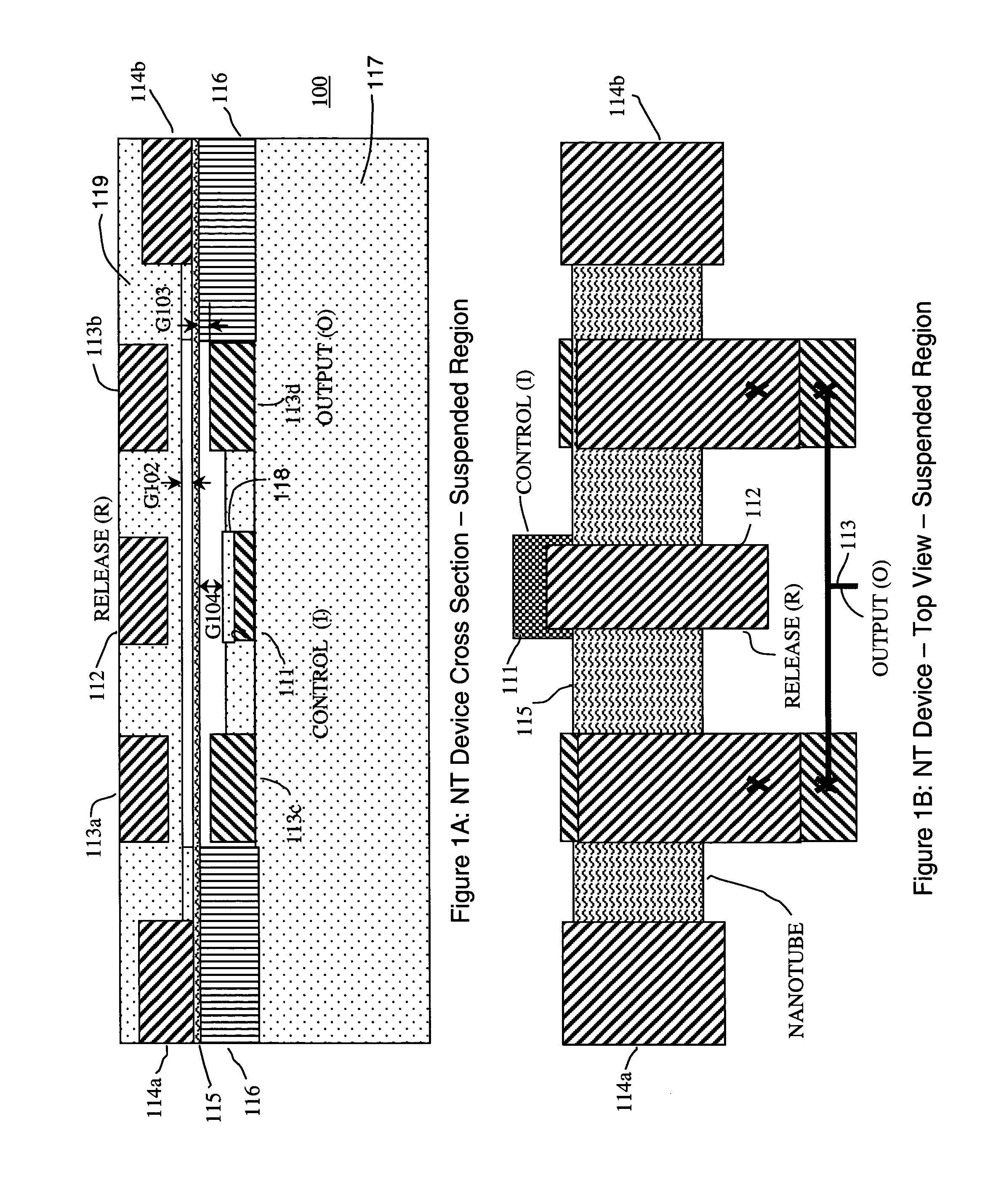
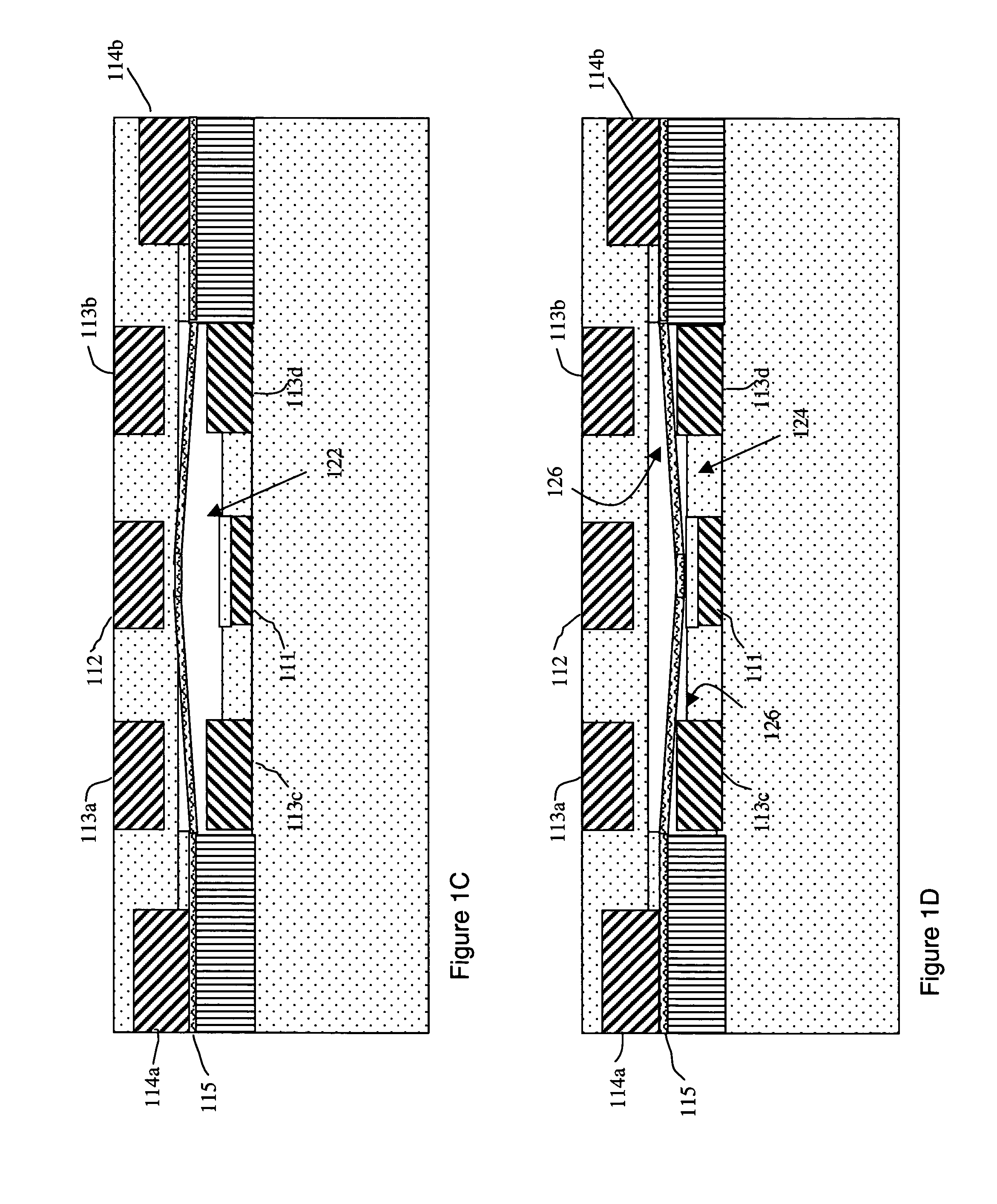
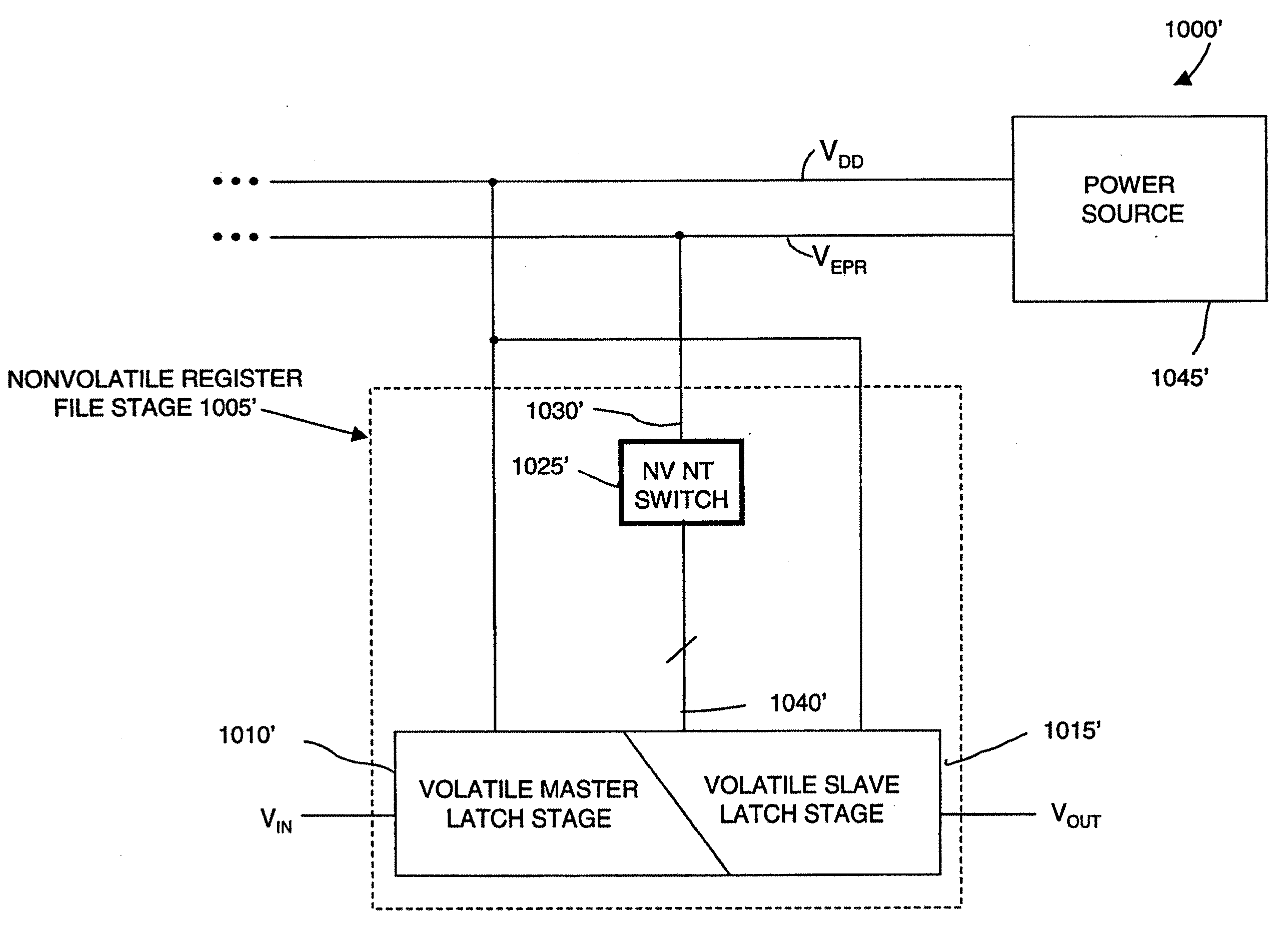
Non-volatile-shadow latch using a nanotube switch
A non-volatile memory cell includes a volatile storage device that stores a corresponding logic state in response to electrical stimulus; and a shadow memory device coupled to the volatile storage device. The shadow memory device receives and stores the corresponding logic state in response to electrical stimulus. The shadow memory device includes a non-volatile nanotube switch that stores the corresponding state of the shadow device.
Owner:NANTERO
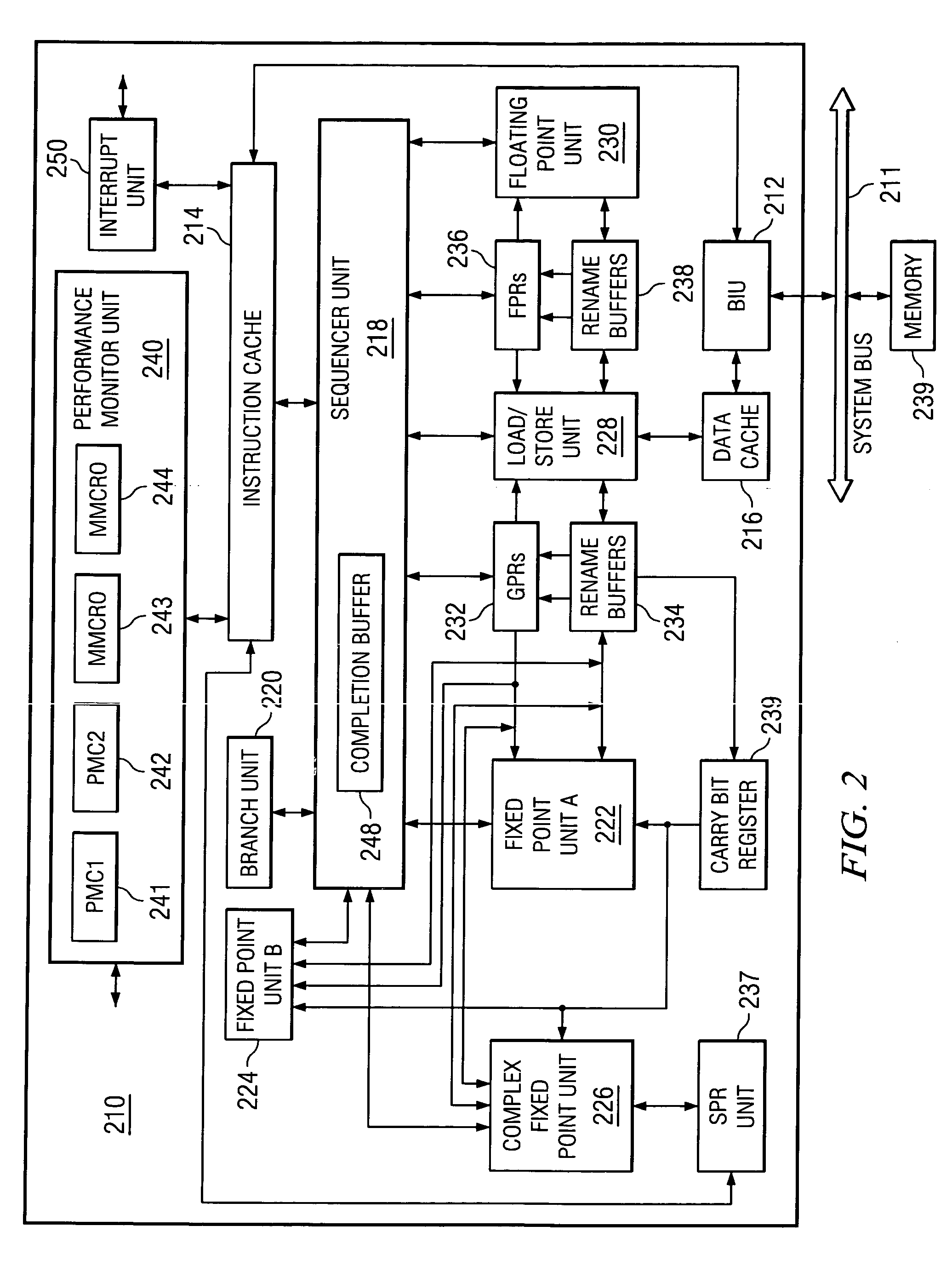
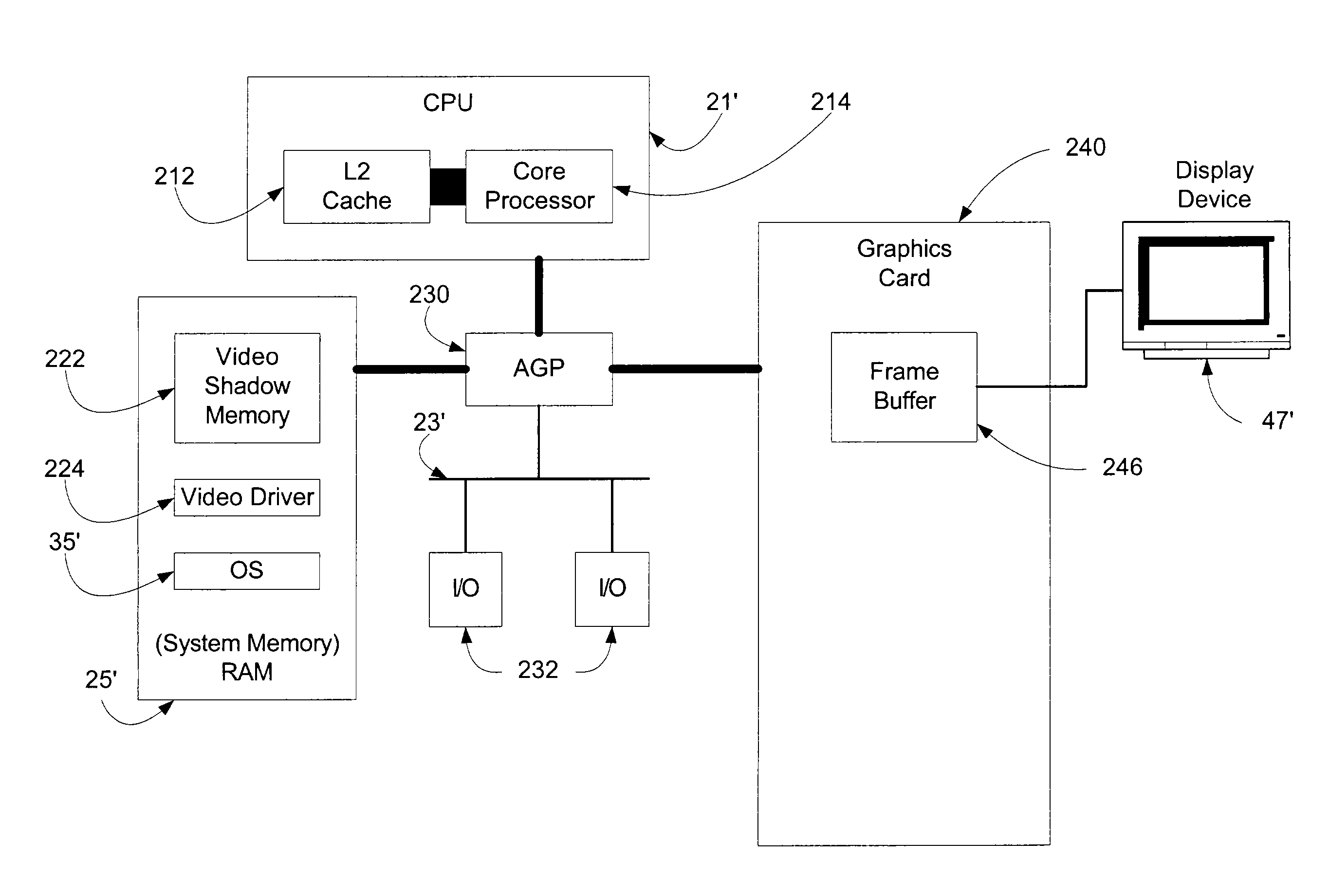
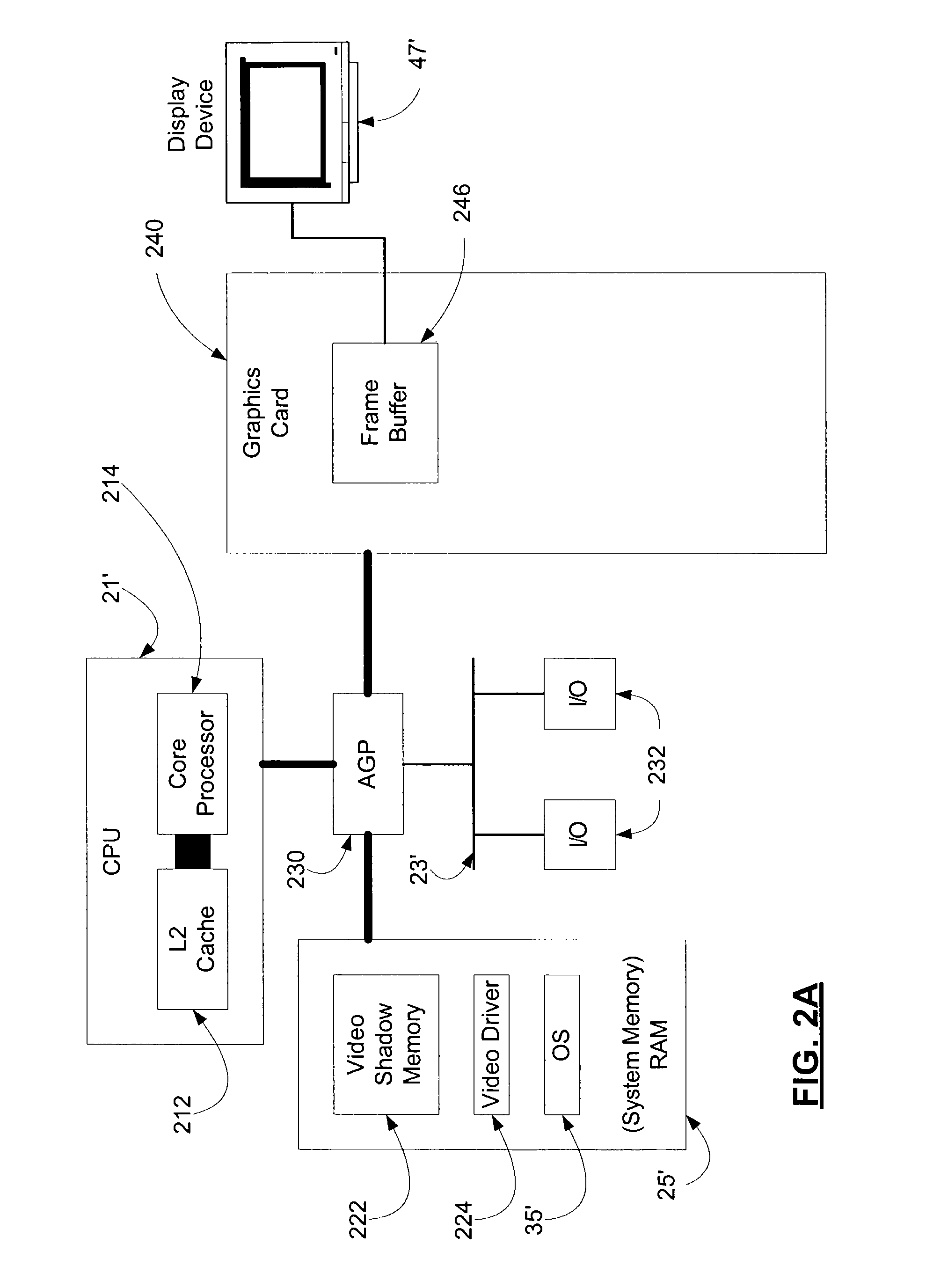
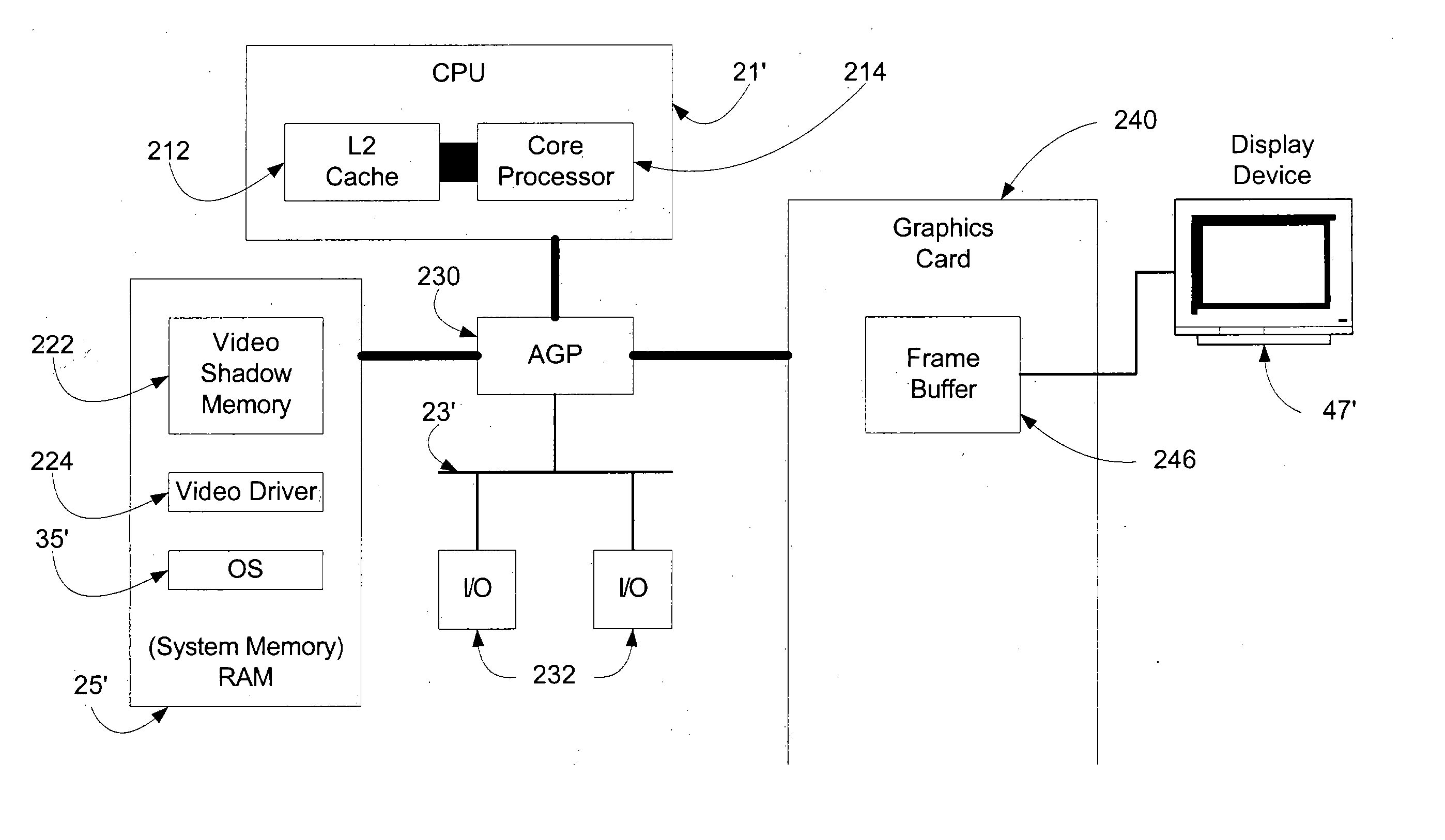
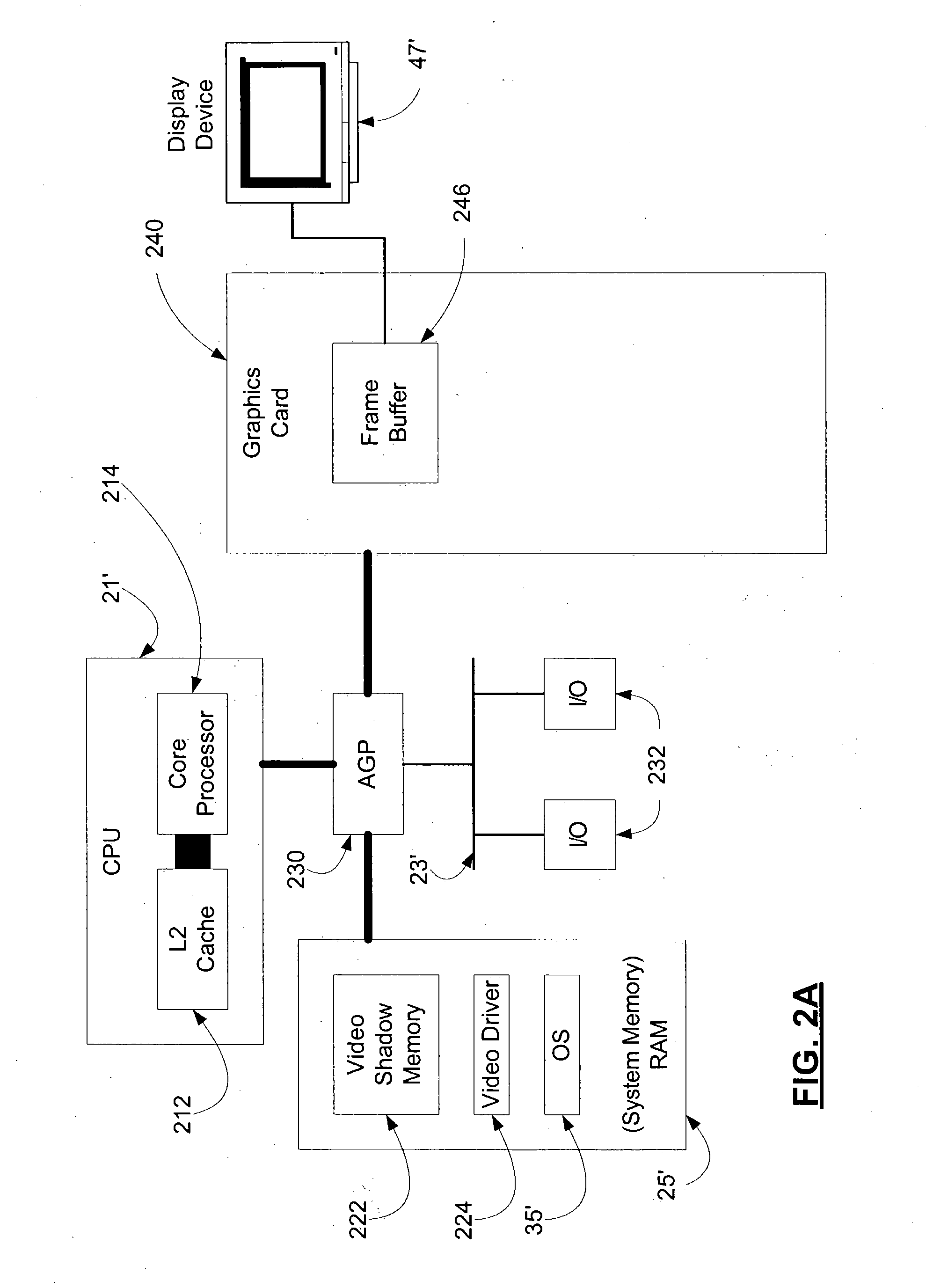
Systems and methods for efficiently updating complex graphics in a computer system by by-passing the graphical processing unit and rendering graphics in main memory
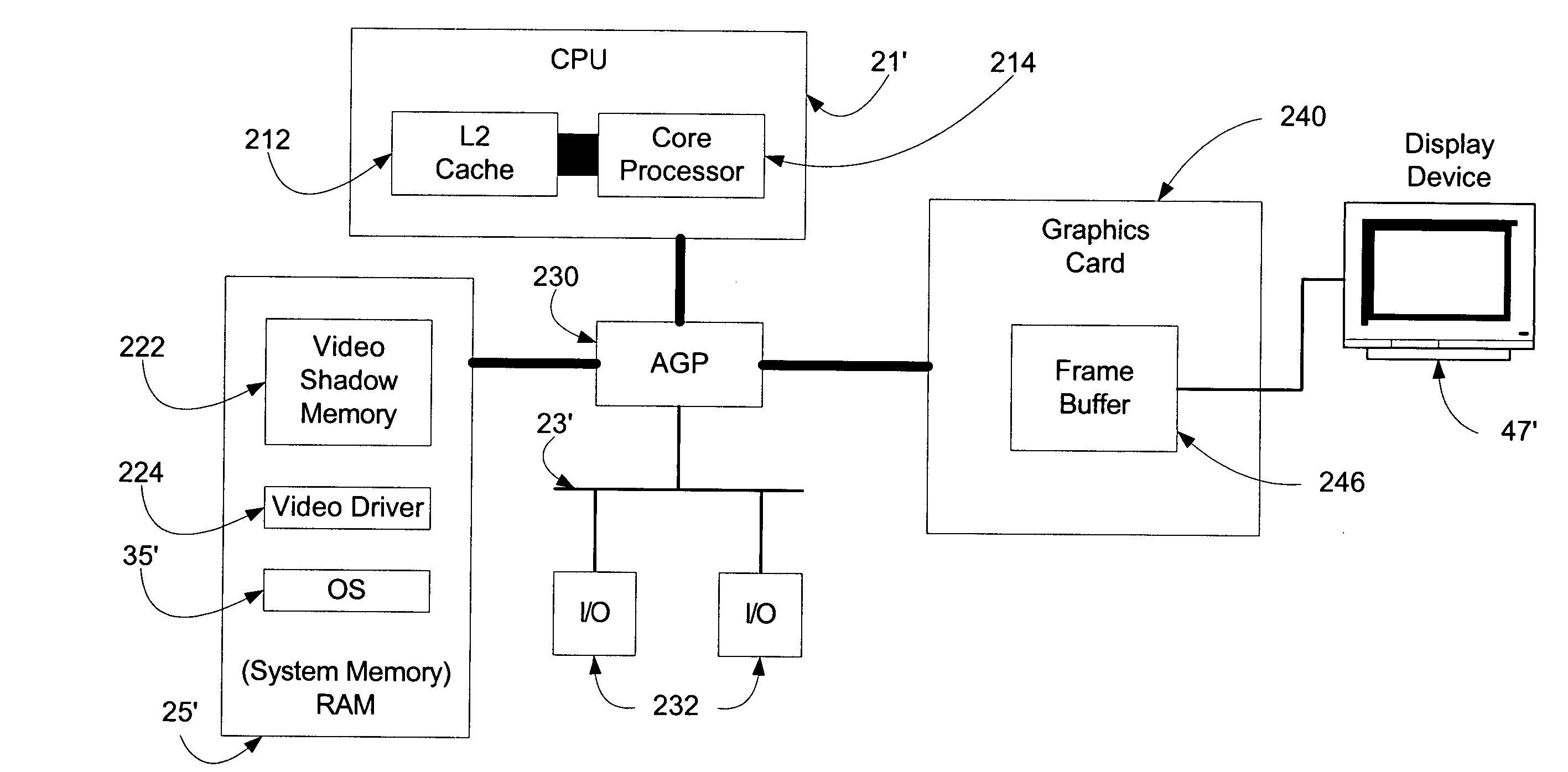
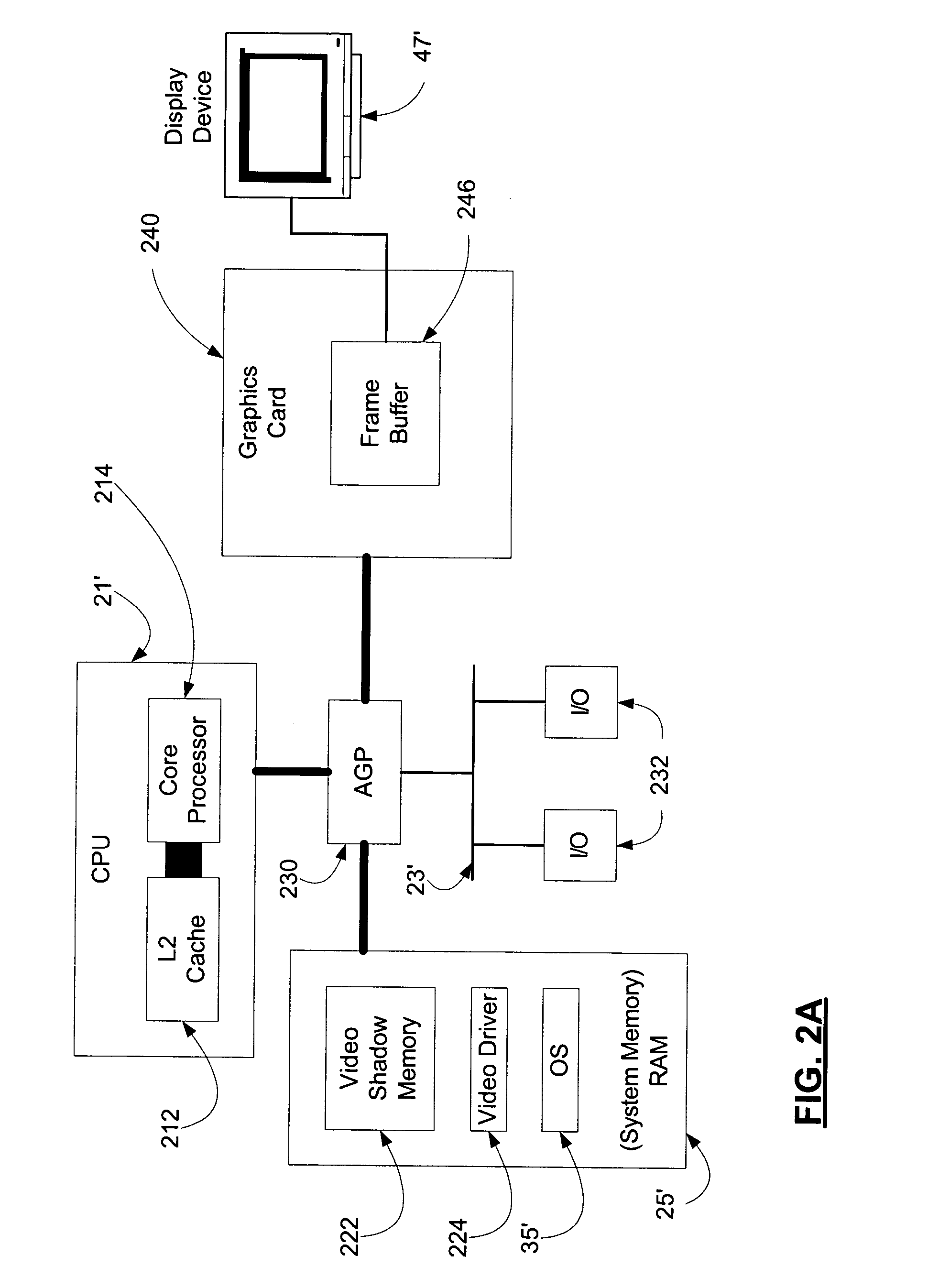
InactiveUS20050012751A1Avoids data flow problemIncrease computing speedCathode-ray tube indicatorsDigital output to display deviceGraphicsAnti-aliasing
In one embodiment of the present invention, a method for rendering complex graphics —comprising “orientation-change graphics” for display on display devices in alternate orientations (e.g., portrait or inverse landscape); compositing of overlays; shading; texturing; anti-aliasing: alpha-blending; and / or sub-pixel manipulation technologies—is disclosed wherein the graphical processing unit (GPU) and video RAM shadow memory (VRAMSM) are bypassed and graphics are rendered in video shadow memory (VSM) by the central processing unit (CPU) and copied directly to the frame buffer. This method avoids the data flow problems of computer systems favoring system-to-video flow of data (that is, systems using an accelerated graphics port (AGP)) and leverages modern CPUs' increased computational speeds wherein the burden of rendering graphics in the CPU is no longer a significant resource cost such that the gains in graphics rendering more than offset any such CPU processing cost.
Owner:MICROSOFT TECH LICENSING LLC
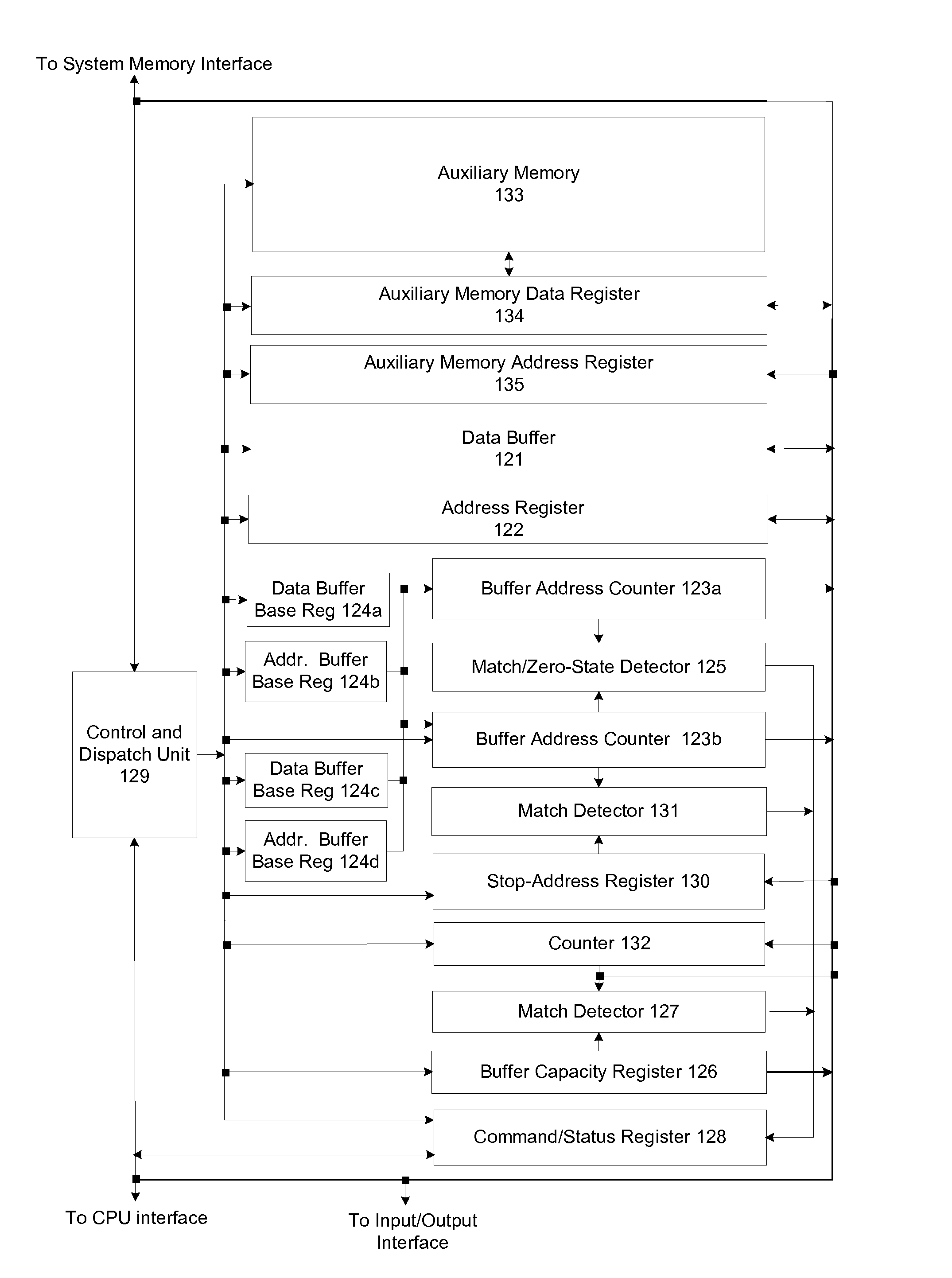
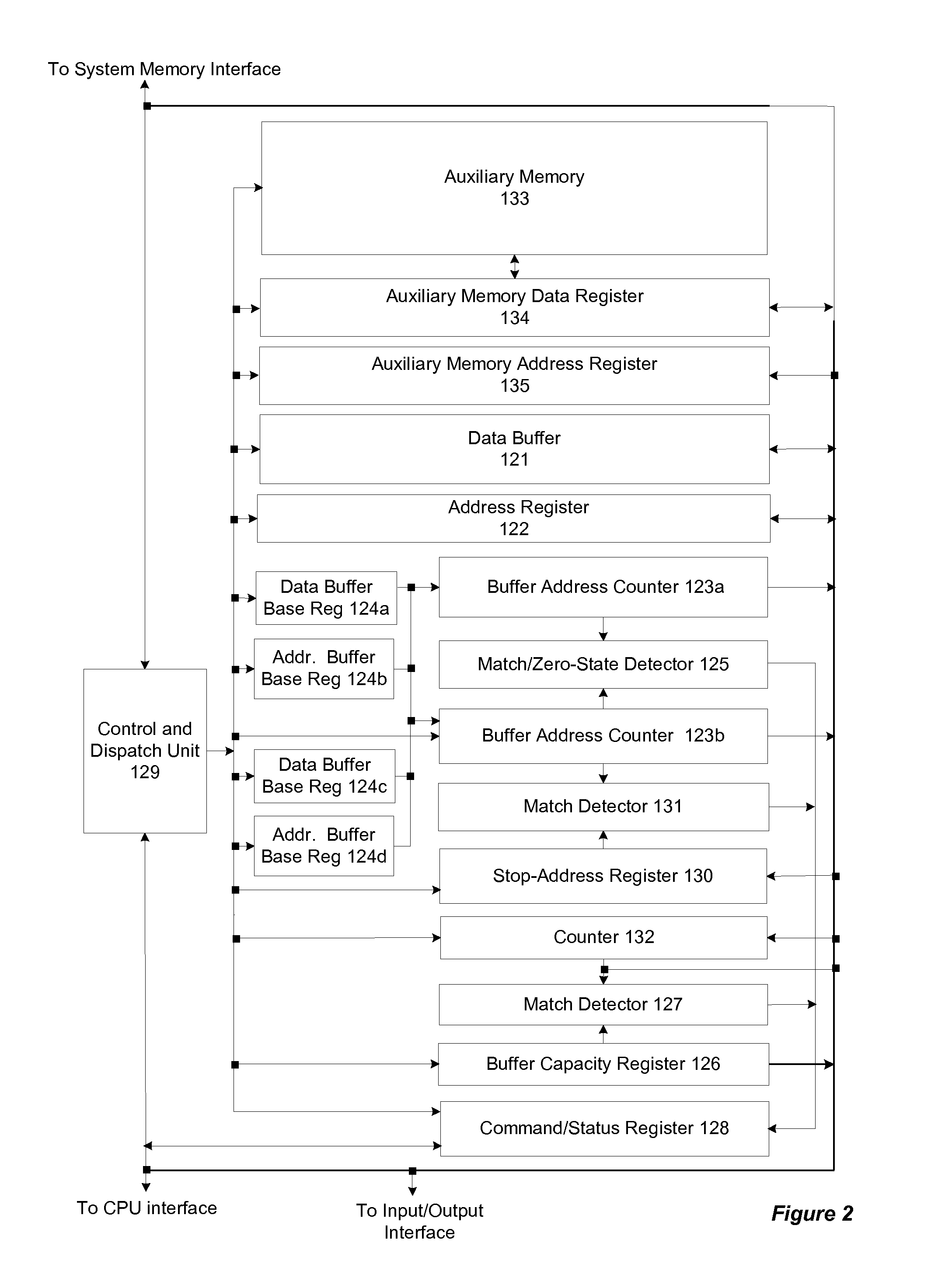
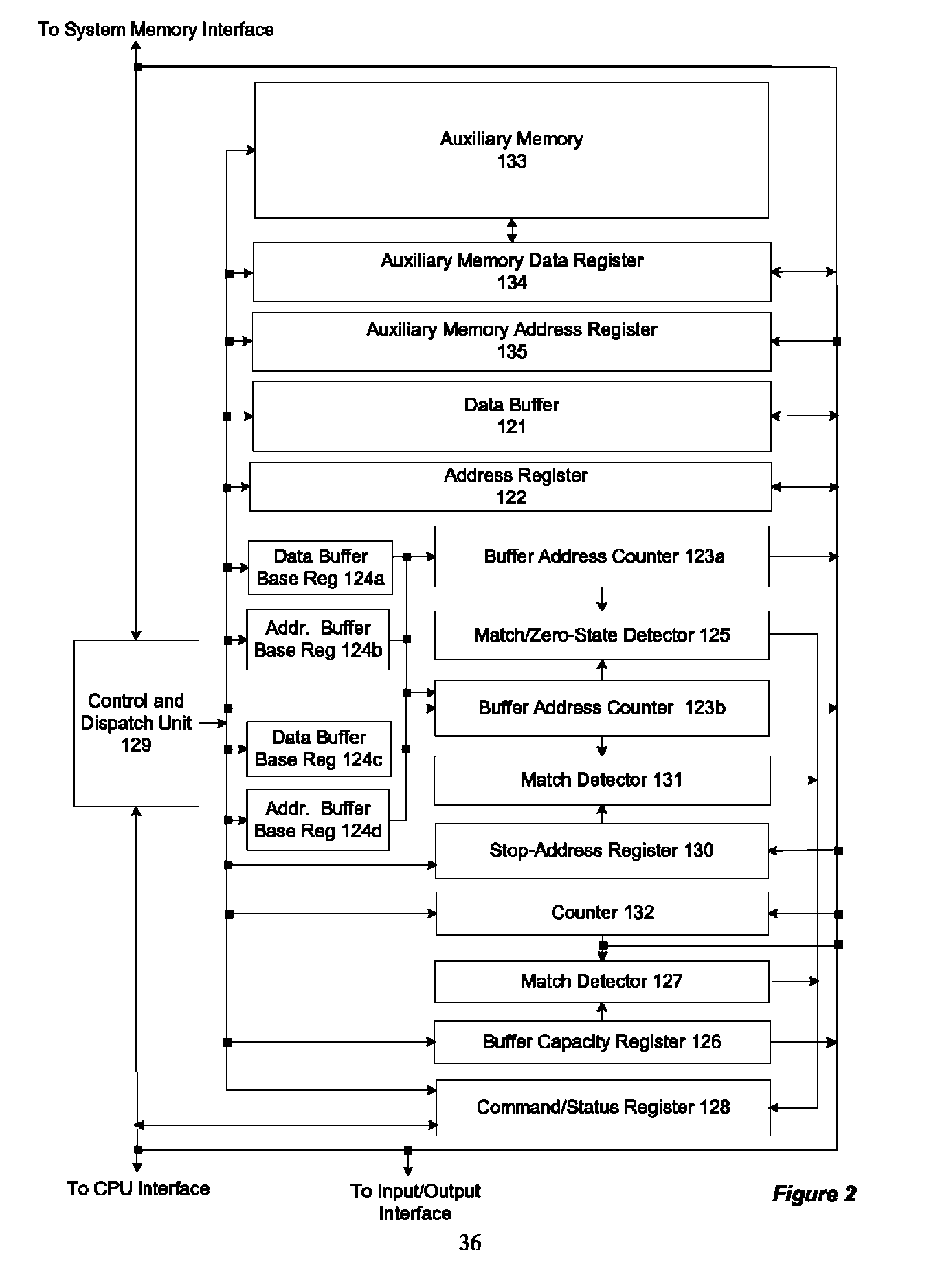
Memory-controller-embedded apparatus and procedure for achieving system-directed checkpointing without operating-system kernel support
ActiveUS20100077164A1Eliminate needSafety arrangmentsMemory loss protectionSupporting systemImage Inspection
System-directed checkpointing is enabled in otherwise standard computers through relatively straightforward augmentations to the computer's memory controller hub. Firmware routines executed by a control and dispatch unit that is normally part of any memory controller hub enable it to implement any of six different checkpointing strategies: post-image checkpointing in which an image of the system state at the time of the last checkpoint is maintained in a local shadow memory; post-image checkpointing in which an image of the system state at the time of the last checkpoint is maintained in a shadow memory located in a second, backup computer; post-image checkpointing using a bit-map memory, having one bit representing each data block in system memory, to reduce the amount of memory-to-memory copying required to establish a checkpoint; post-image checkpointing to a local shadow memory using two bit map memories to enable normal processing to continue while the shadow is being updated, post-image checkpointing to a local shadow memory using a block-state memory that eliminates the need for any memory-to-memory copying; and local pre-image checkpointing that does not require a shadow memory. Since each of these implementations has advantages and disadvantages relative to the others and since similar mechanisms are used in the memory controller hub for all of these options, it can be designed to support all of them with hardwired or settable status bits defining which is to be supported in a given situation.
Owner:CHEMTRON RES
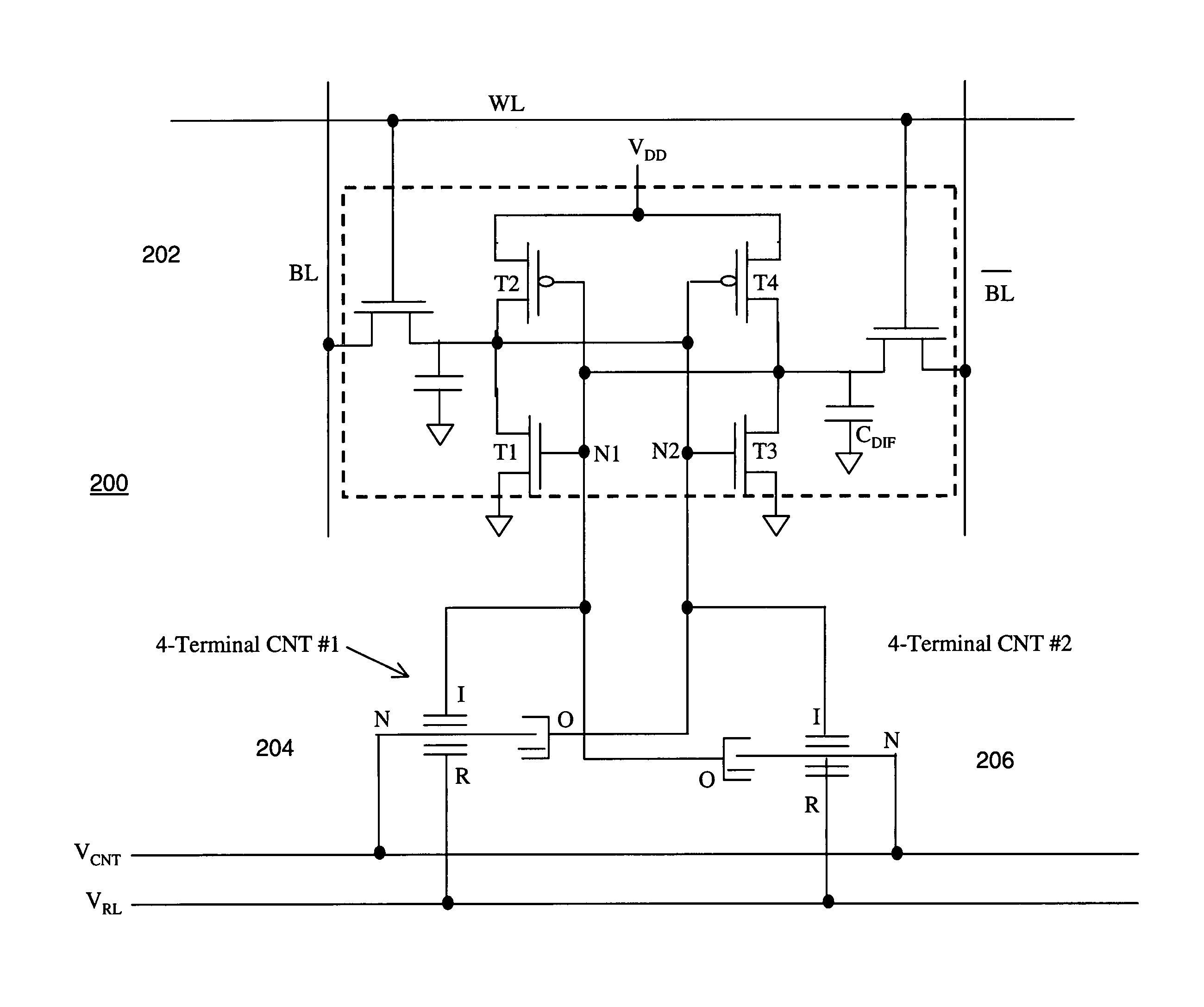
Random access memory including nanotube switching elements
ActiveUS7245520B2Individual molecule manipulationNanoinformaticsStatic random-access memoryShadow memory
A random access memory cell includes first and second nanotube switching elements and an electronic memory with cross-coupled first and second inverters. Each nanotube switching element includes a nanotube channel element having at least one electrically conductive nanotube, and a set electrode and a release electrode disposed in relation to the nanotube channel element to controllably form and unform an electrically conductive channel between a channel electrode and an output node. Input nodes of the first and second inverters are coupled to the set electrodes and the output nodes of the first and second nanotube switching elements. The cell can operate as a normal electronic memory, or in a shadow memory or store mode to transfer the electronic memory state to the nanotube switching elements. The device may later be operated in a recall mode to transfer the state of the nanotube switching elements to the electronic memory.
Owner:NANTERO
Method and apparatus for debug support for individual instructions and memory locations
InactiveUS20050071610A1Digital computer detailsConcurrent instruction executionData processing systemShadow memory
A method, apparatus, and computer instructions in a data processing system for monitoring processing of instructions and memory locations. An instruction is received in the data processing system for execution. If an enabled state is present, a determination is made whether the instruction is associated with an indicator in a shadow memory. A selected action is performed in response to the indicator being associated with the instruction. Responsive to being in an enabled state when a data access to a memory location occurs, a determination is made as to whether the memory location is associated with an indicator in a shadow memory. A selected action is performed in response to the indicator being associated with the memory location.
Owner:IBM CORP
Systems and methods for updating a frame buffer based on arbitrary graphics calls
InactiveUS7145566B2Maximum performanceDigital computer detailsImage memory managementShadow memoryDisplay device
A method for dividing a display into zones at system initialization for tracking which zones have any pixels revised so that, when the time comes to update the display, only the zones requiring revision (that is, those zones in which any pixel has been revised) are copied from shadow memory to the frame buffer for display on the display device. The memory for tracking these zones can be allocated at initialization and held since it is relatively small. Consequently, a significant performance gain may be achieved by avoiding the shortcomings of the existing methods in the art notwithstanding the fact that some “clean” pixels in each zone having even a single changed pixel are also rewritten to the frame buffer.
Owner:MICROSOFT TECH LICENSING LLC
Method and Apparatus for Accessing Data of a Message Memory of a Communication Module
ActiveUS20080282041A1Increase transfer speedAssure integrity of dataTransmissionMemory systemsShadow memoryData input
A method and an apparatus for accessing data of a message memory of a communication module by inputting or outputting data into or from the message memory, the message memory being connected to a buffer memory assemblage and the data being transferred to the message memory or from the message memory, the buffer memory assemblage having an input buffer memory in the first transfer direction and an output buffer memory in the second transfer direction; and the input buffer memory and the output buffer memory each being divided into a partial buffer memory and a shadow memory, the following steps being performed in each transfer direction: inputting data into the respective partial buffer memory, and transposing access to the partial buffer memory and shadow memory, so that subsequent data can be inputted into the shadow memory while the previously inputted data are already being outputted from the partial buffer memory in the stipulated transfer direction.
Owner:ROBERT BOSCH GMBH
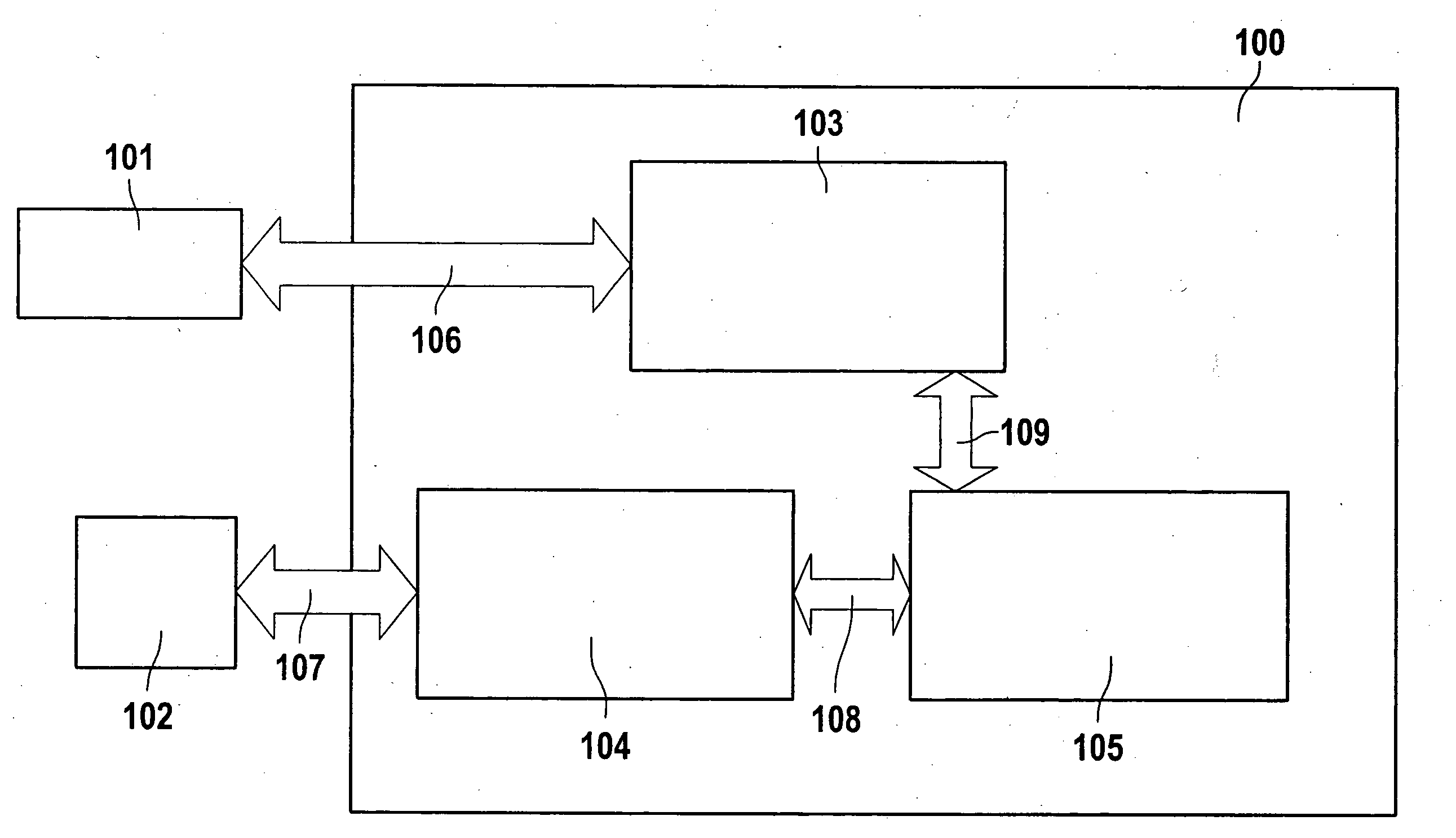
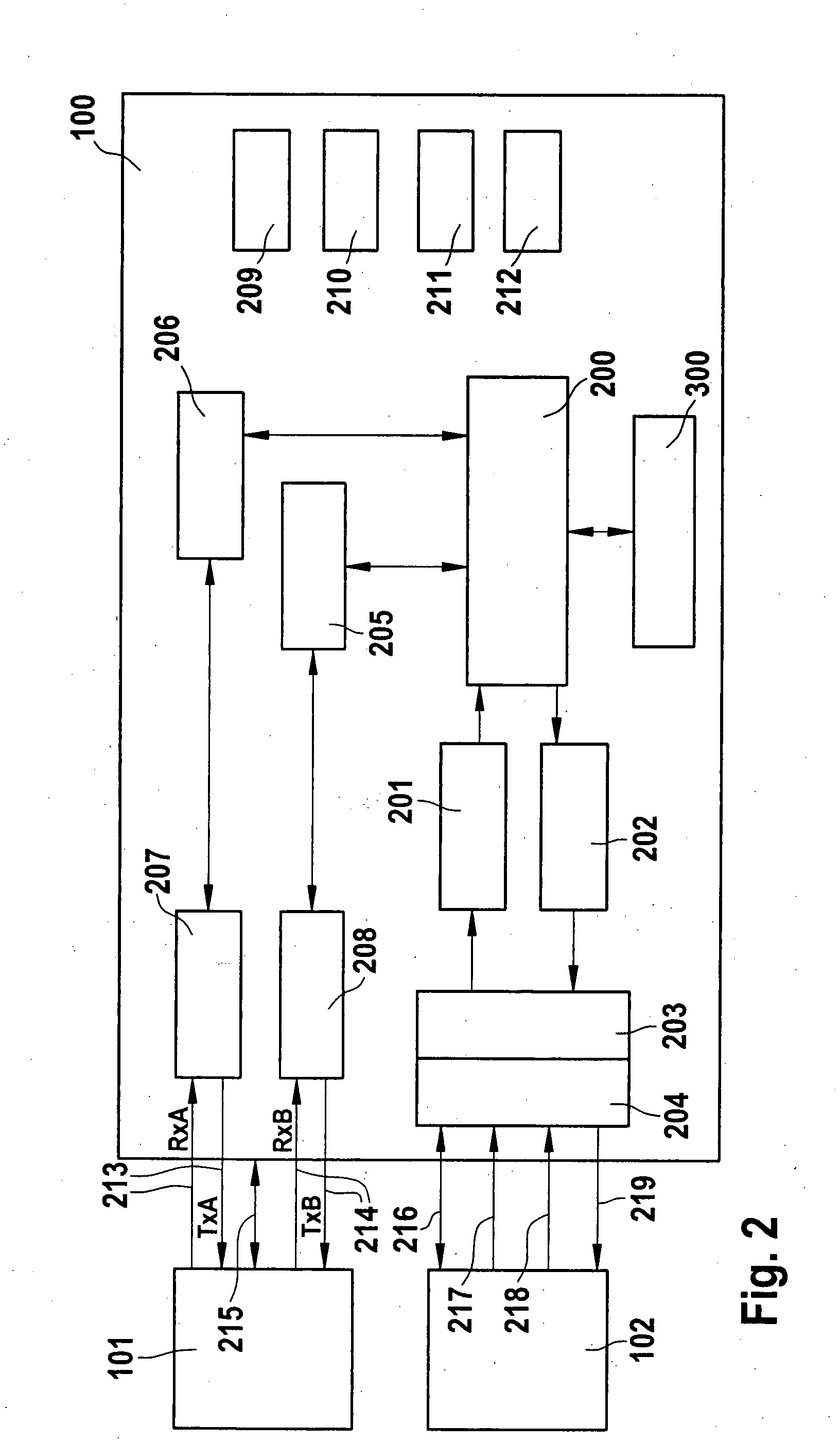
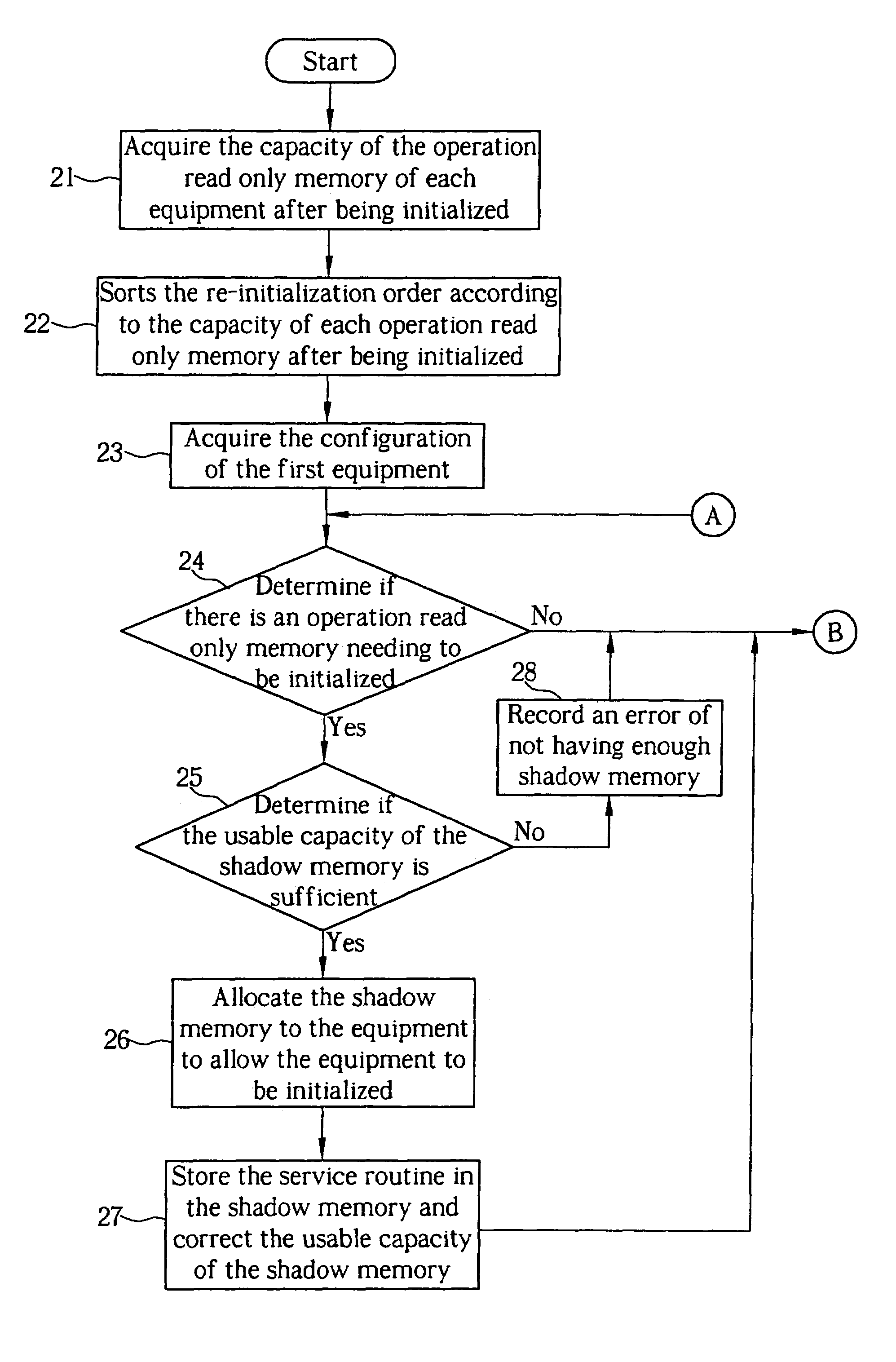
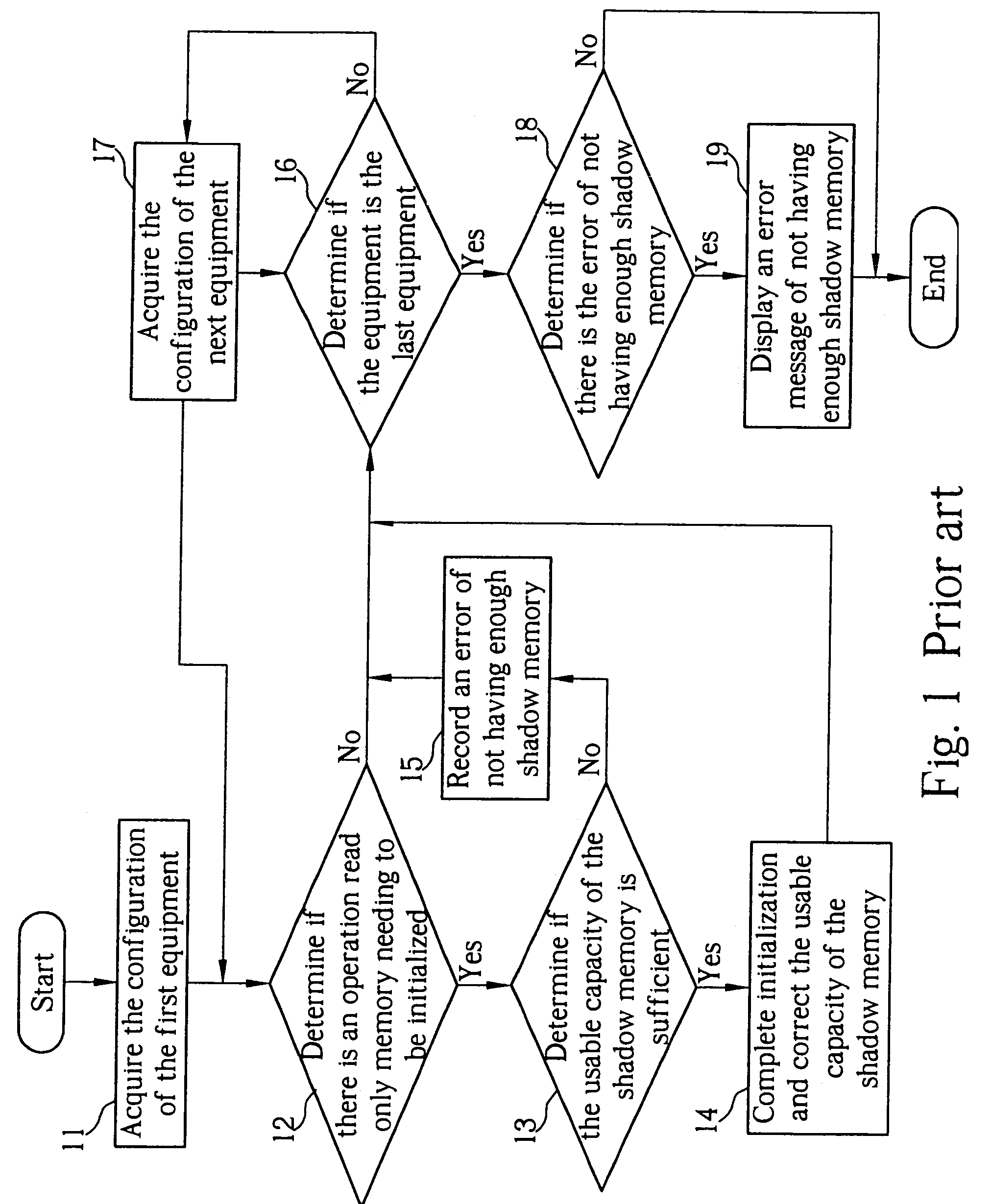
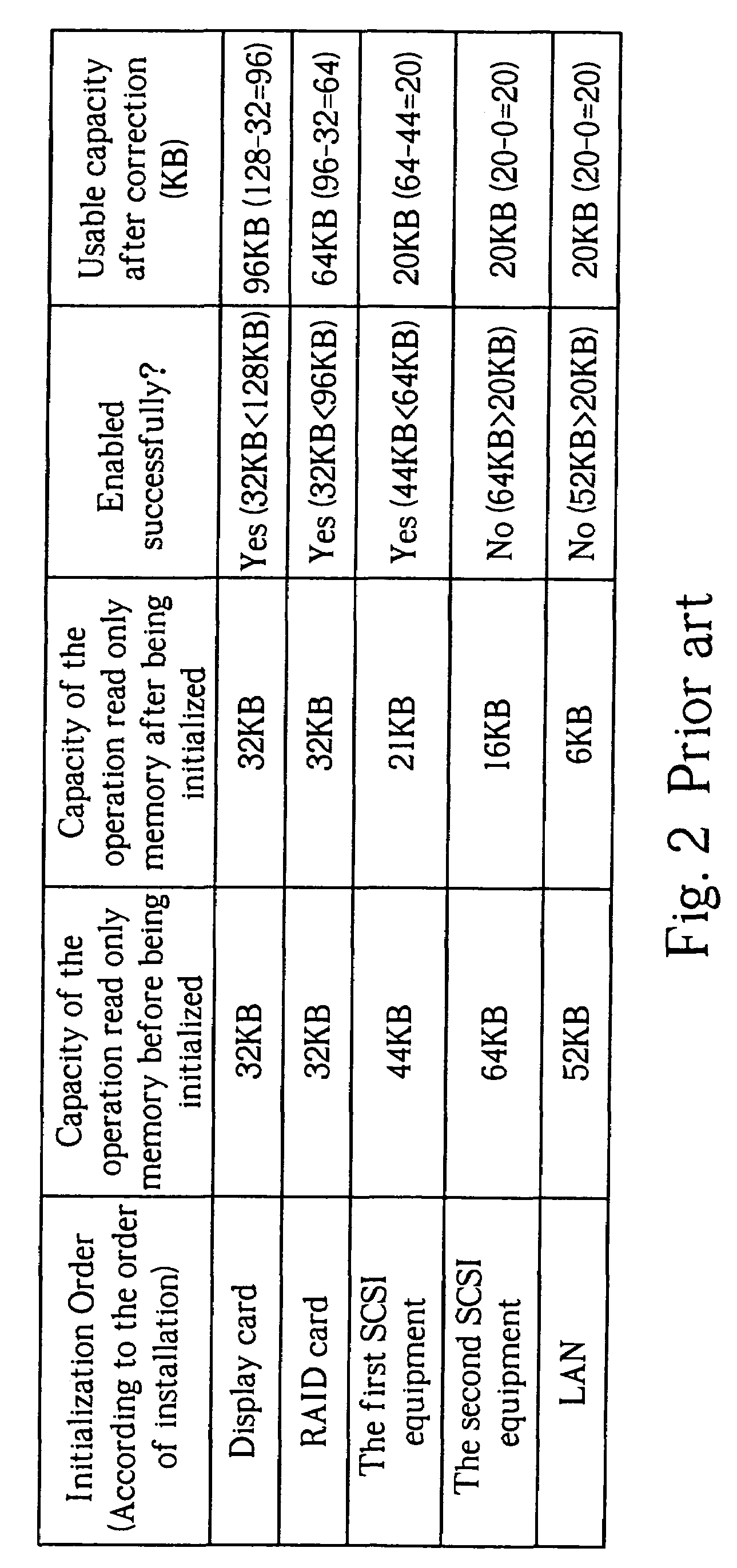
Method of allocating a basic input/output system to a shadow memory
InactiveUS7039797B2Increases number of equipmentEffective distributionMemory adressing/allocation/relocationDigital computer detailsShadow memoryRead-only memory
A method of allocating a basic input / output system to a shadow memory applied to a computer including a plurality of equipment having an operation read only memory and a shadow memory. The method includes executing the preliminary initialization of the equipment to acquire the capacity of the operation read only memory of each equipment after being initialized. Then the equipment is re-initialized according to the order of the capacity of each operation read only memory after being initialized from smallest capacity to largest capacity to allocate the shadow memory more effectively and increase the number of equipment to be enabled.
Owner:MICRO-STAR INTERNATIONAL
Isolating data within a computer system using private shadow mappings
ActiveUS20160179564A1Memory architecture accessing/allocationSoftware simulation/interpretation/emulationVirtualizationShadow mapping
Virtualization software establishes multiple execution environments within a virtual machine, wherein software modules executing in one environment cannot access private memory of another environment. A separate set of shadow memory address mappings is maintained for each execution environment. For example, a separate shadow page table may be maintained for each execution environment. The virtualization software ensures that the shadow address mappings for one execution environment do not map to the physical memory pages that contain the private code or data of another execution environment. When execution switches from one execution environment to another, the virtualization software activates the shadow address mappings for the new execution environment. A similar approach, using separate mappings, may also be used to prevent software modules in one execution environment from accessing the private disk space or other secondary storage of another execution environment.
Owner:VMWARE INC
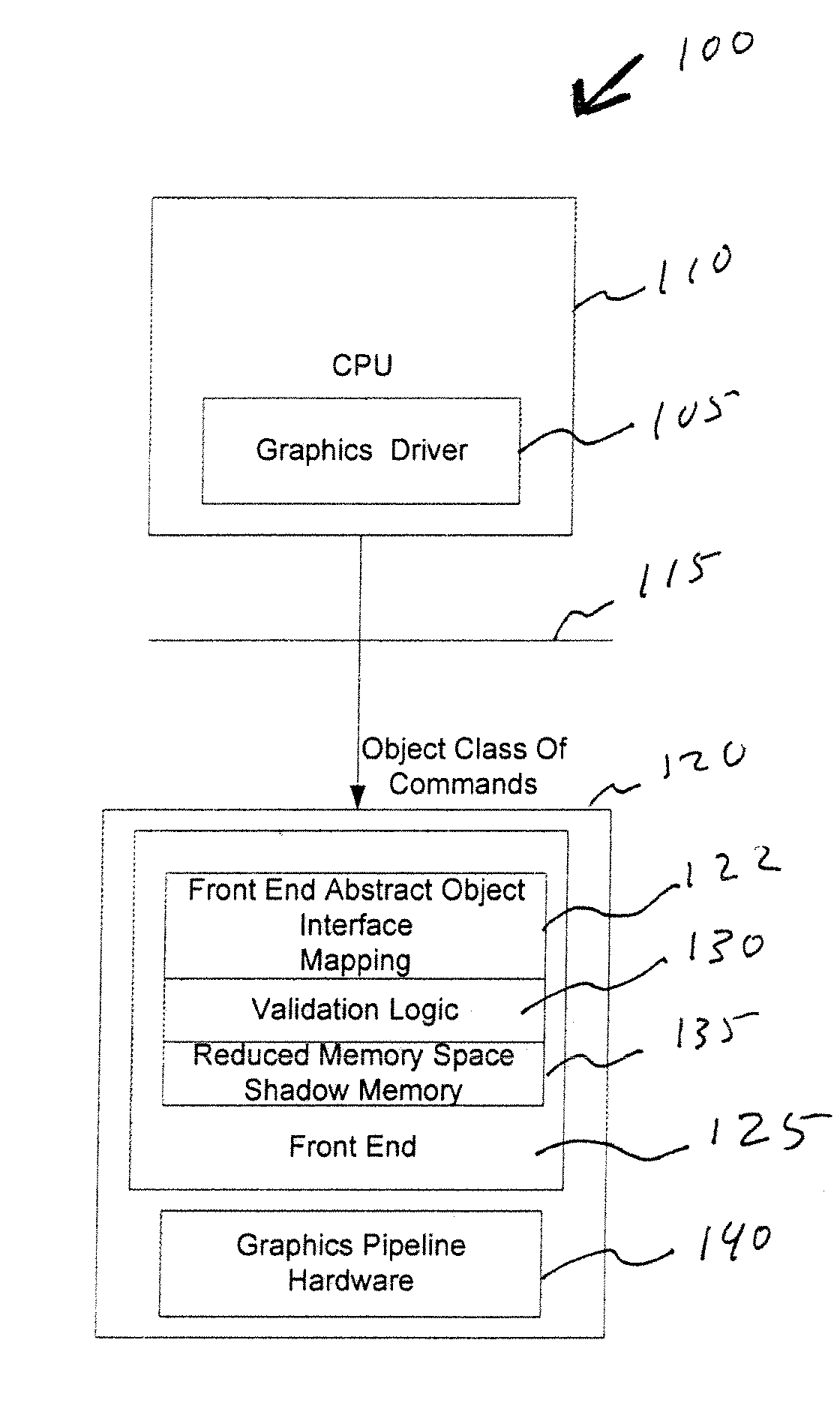
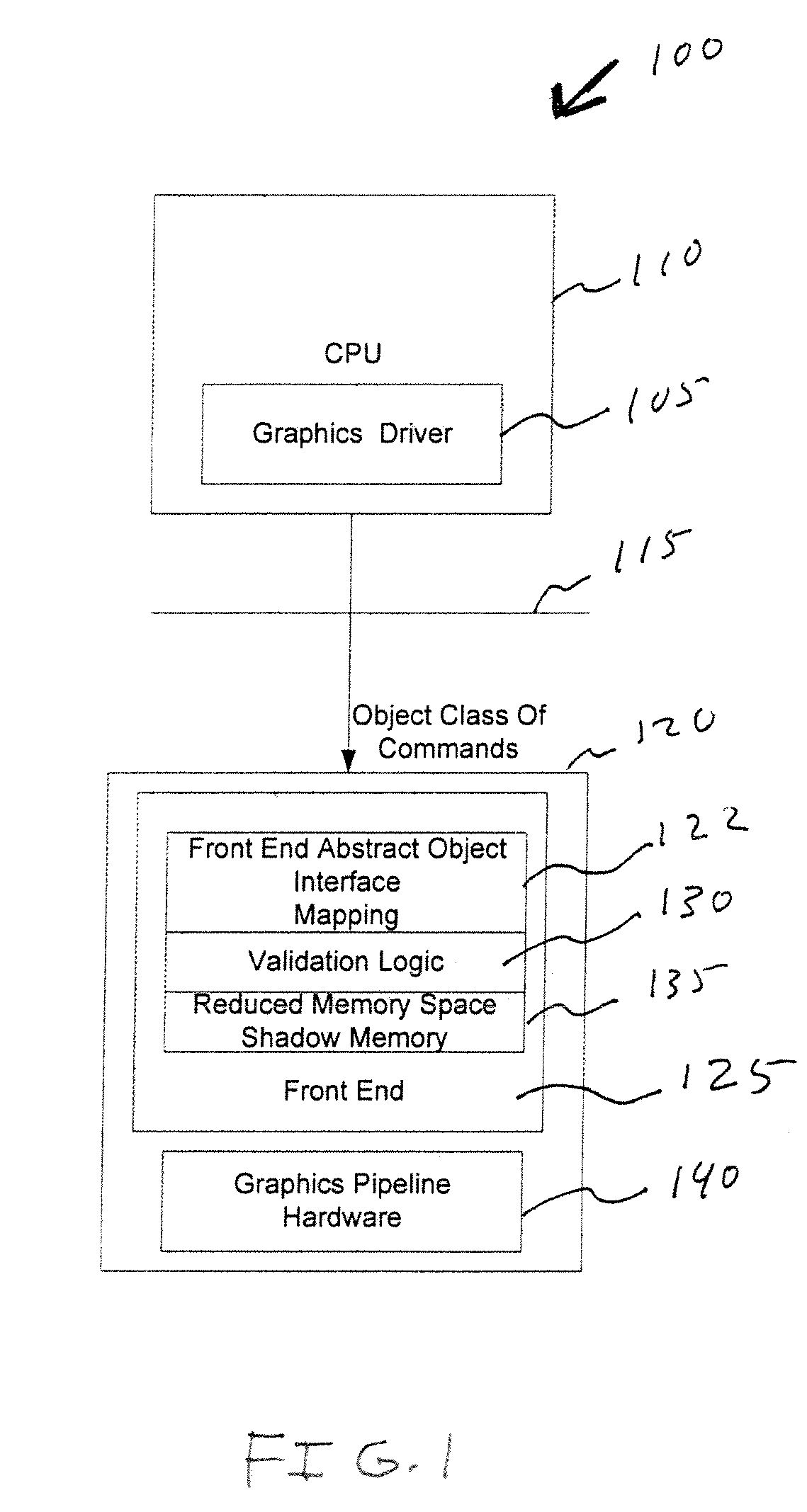
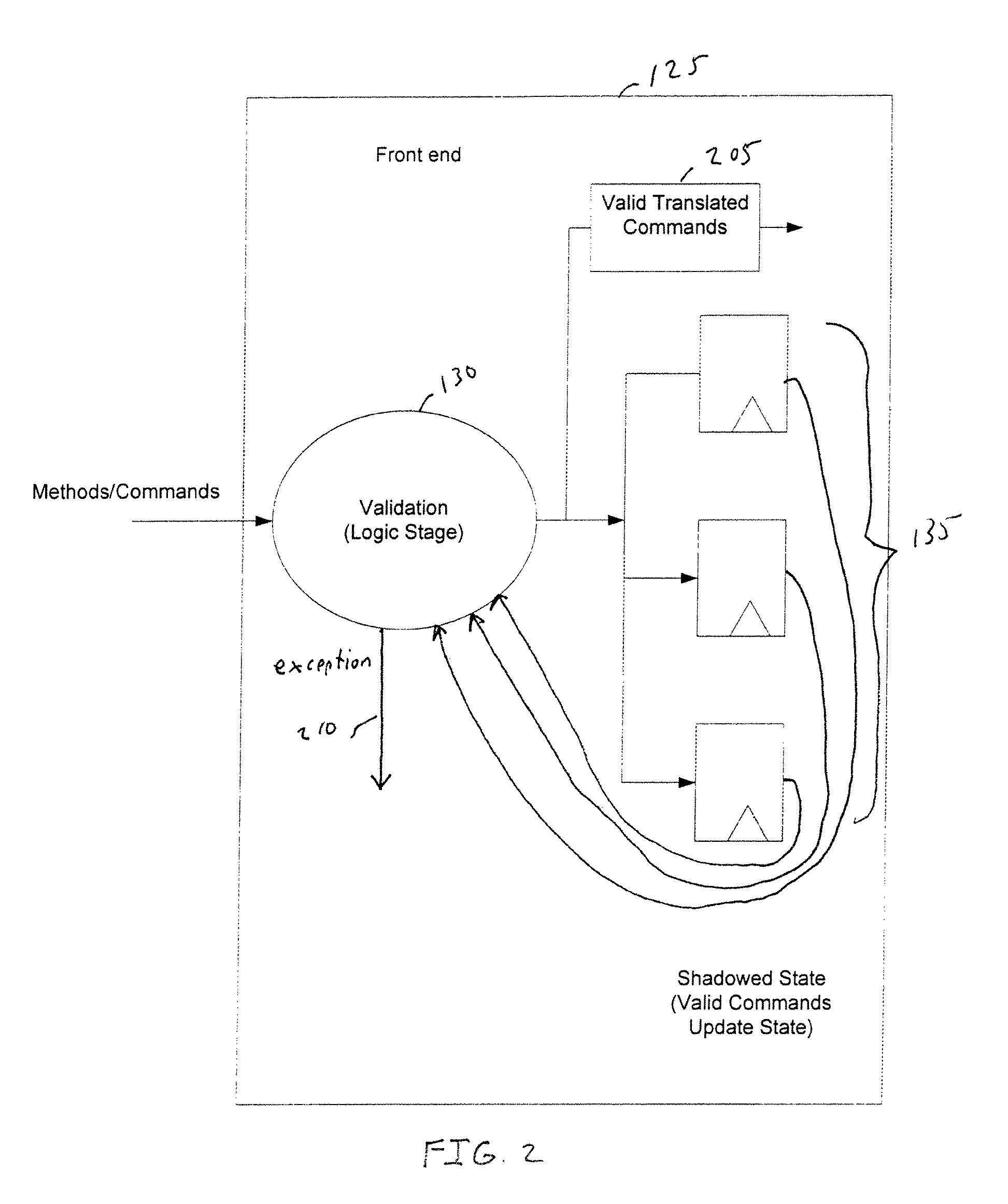
Graphics system with reduced shadowed state memory requirements
A graphics processing unit has a reduced memory space shadow memory as a source of state information for performing validation of commands. The reduced memory space shadow memory is smaller in size than a full version of state variables associated with an abstract state machine representation of a class of commands received from a software driver.
Owner:NVIDIA CORP
Data processor having bios packing compression/decompression architecture
InactiveUS20020129233A1Maintain compatibilityShorten the timeDigital computer detailsBootstrappingComputer architectureShadow memory
To increase the effective capacity of BIOS, an initial portion of the power on system reset (POST) code that is required to enable the system memory is stored in ROM in uncompressed form, and substantially the remaining portion of the BIOS code is stored in compressed form. Upon system initialization during a cold boot, the uncompressed portion of POST is executed from the ROM to enable the system memory, and then an image of the BIOS code is written to shadow memory. As BIOS code is needed during the remainder of the boot, the code is selectively decompressed from the shadow memory to another region of the system memory to which control is transferred. Variations based upon different boot scenarios are described.
Owner:INT BUSINESS MASCH CORP
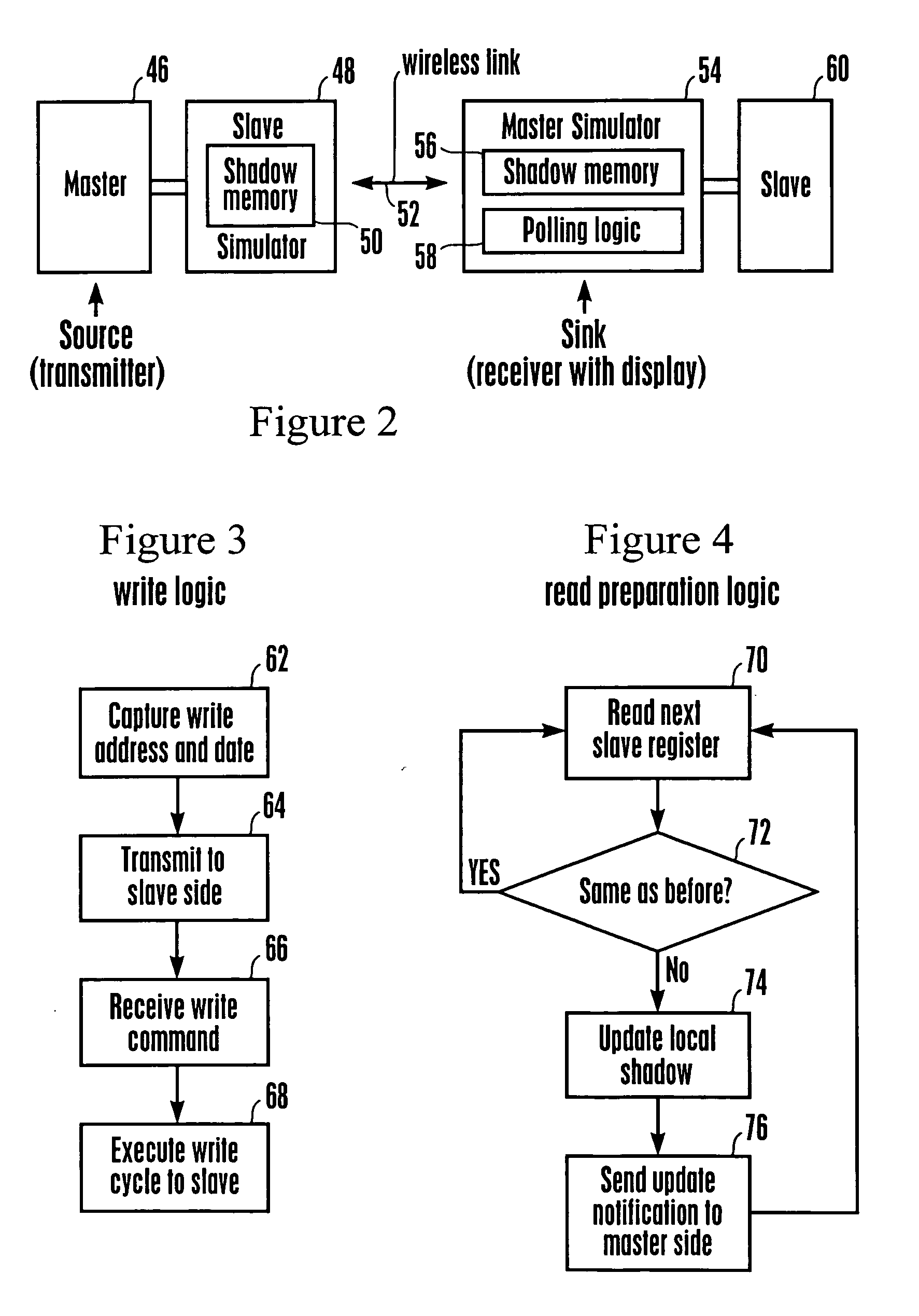
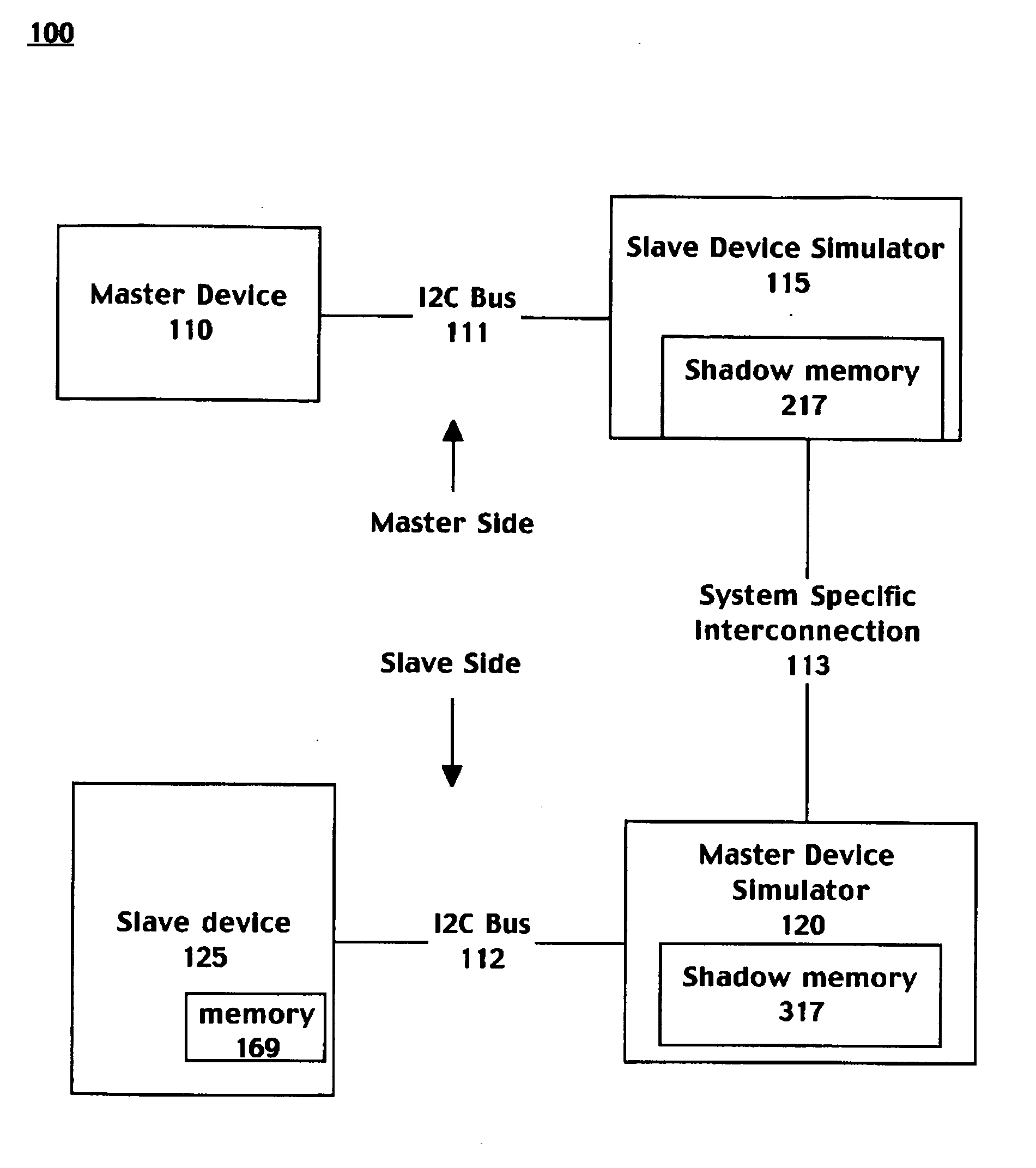
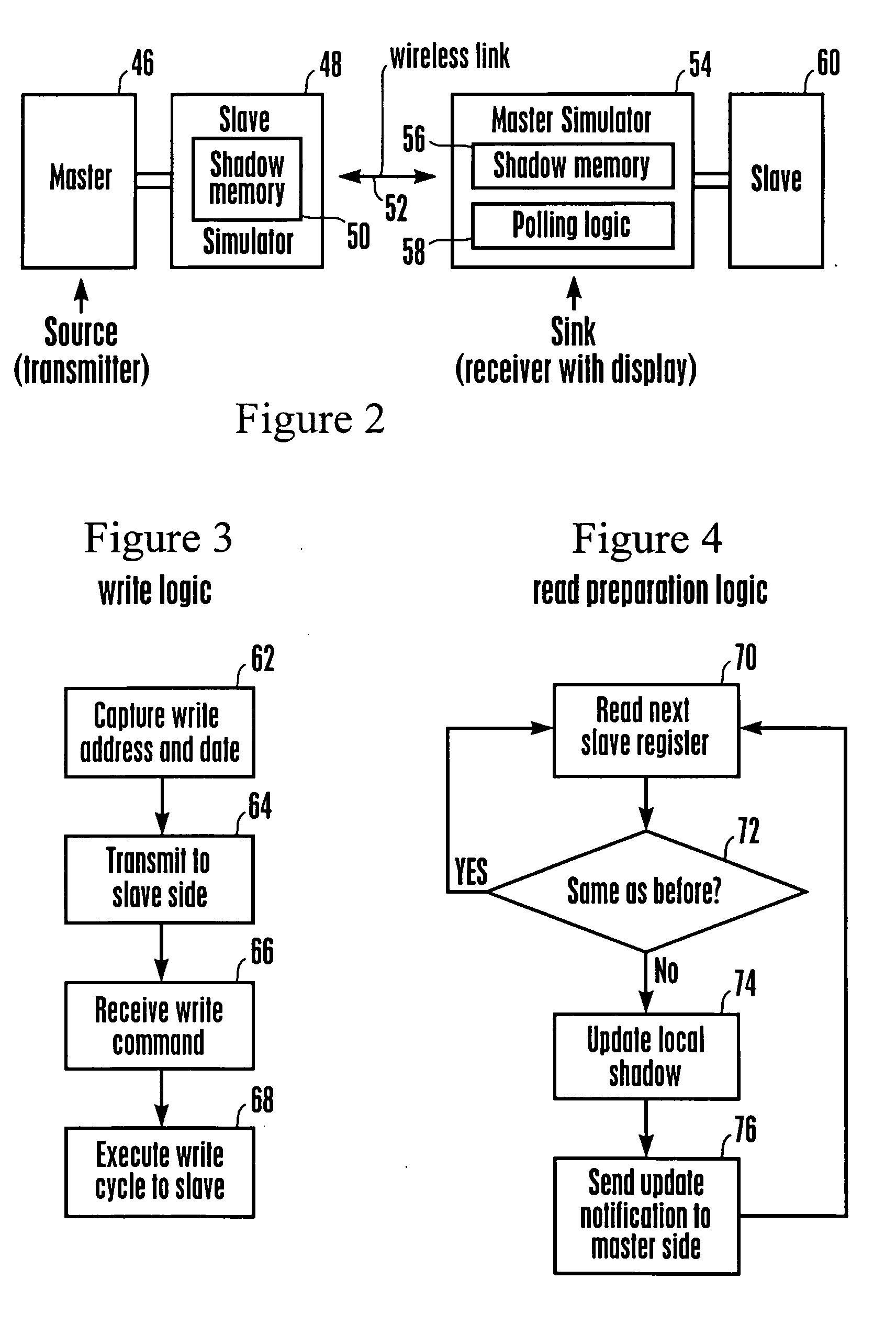
Inter integrated circuit extension via shadow memory
InactiveUS20060129370A1Analogue computers for electric apparatusSubstation equipmentSimulator couplingShadow memory
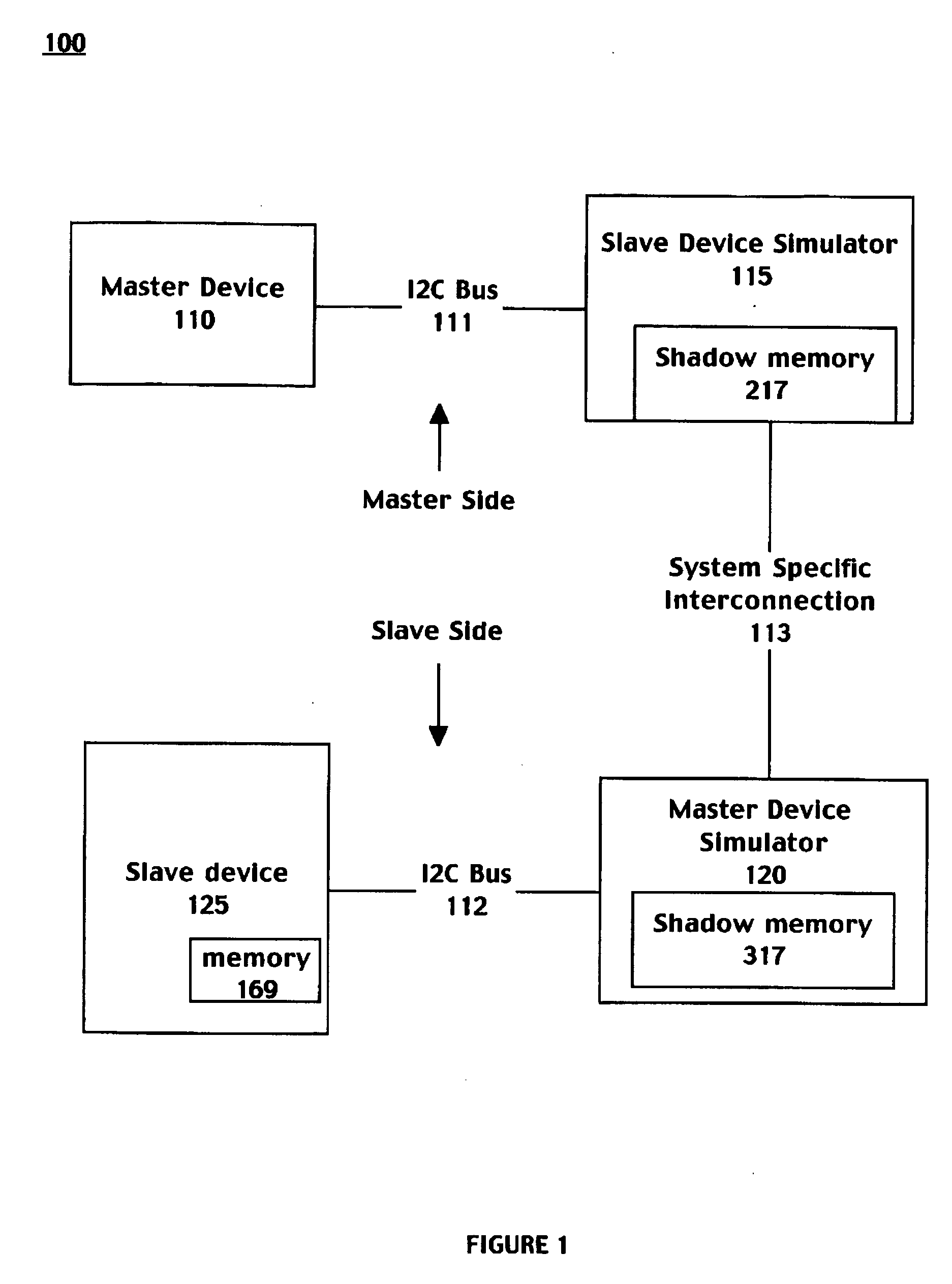
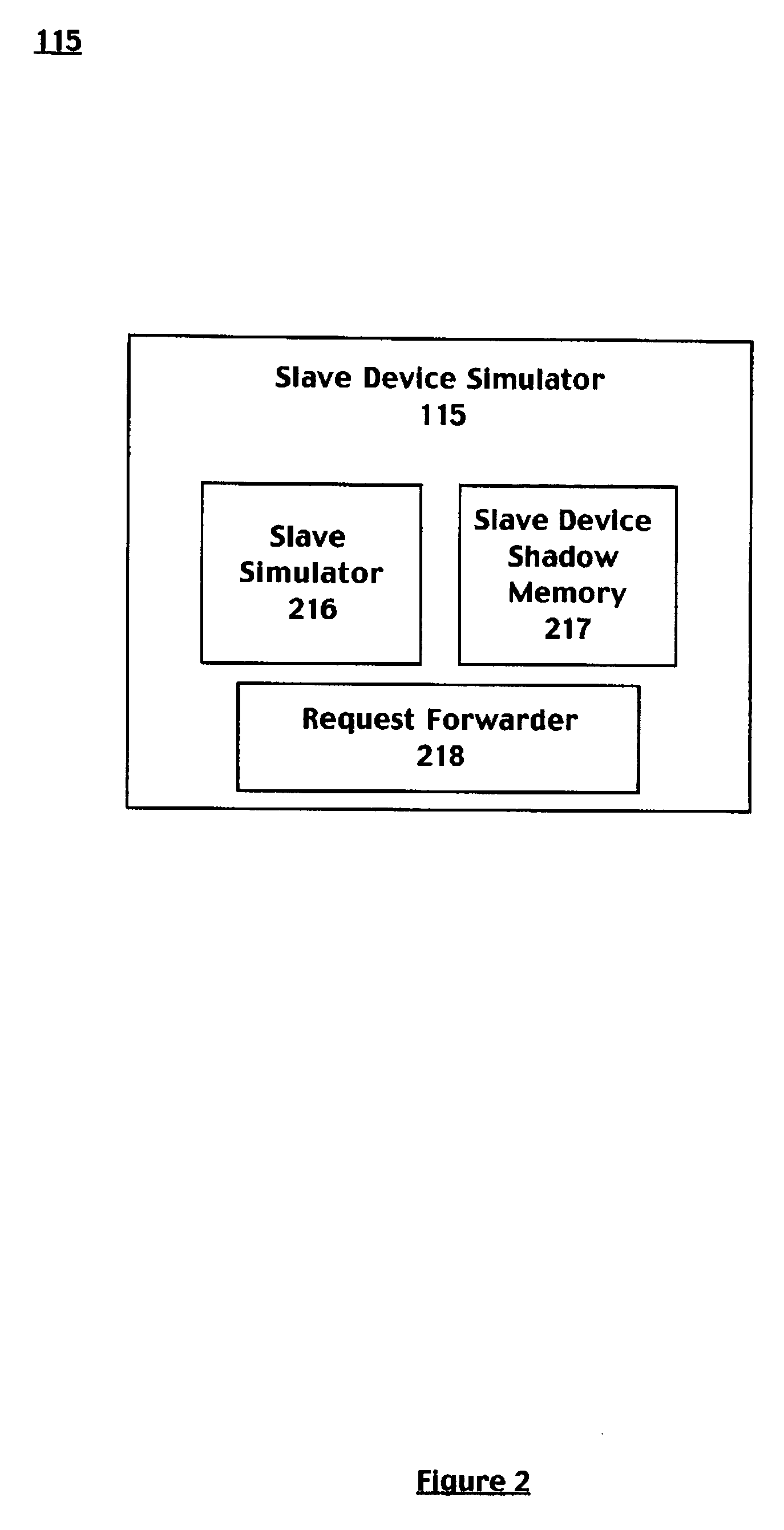
Embodiments of the present invention include a system for accessing a memory device comprising a master device coupled to a first serial bus. The system further comprises a slave device coupled to a second serial bus wherein the slave device comprises a first memory. The system further includes a slave device simulator coupled to the first serial bus and coupled to a long distance system specific interconnection, wherein the slave device simulator comprises a first shadow memory of the first memory and wherein a master device simulator is coupled to the second serial bus and coupled to the system specific interconnection. The master device comprises a second shadow memory of the slave device. Data read operations of the master may be satisfied directly from the slave device simulator shadow memory. Data writes from the master are propagated to the slave device and data coherency routines update the shadow memories accordingly.
Owner:SONY CORP +1
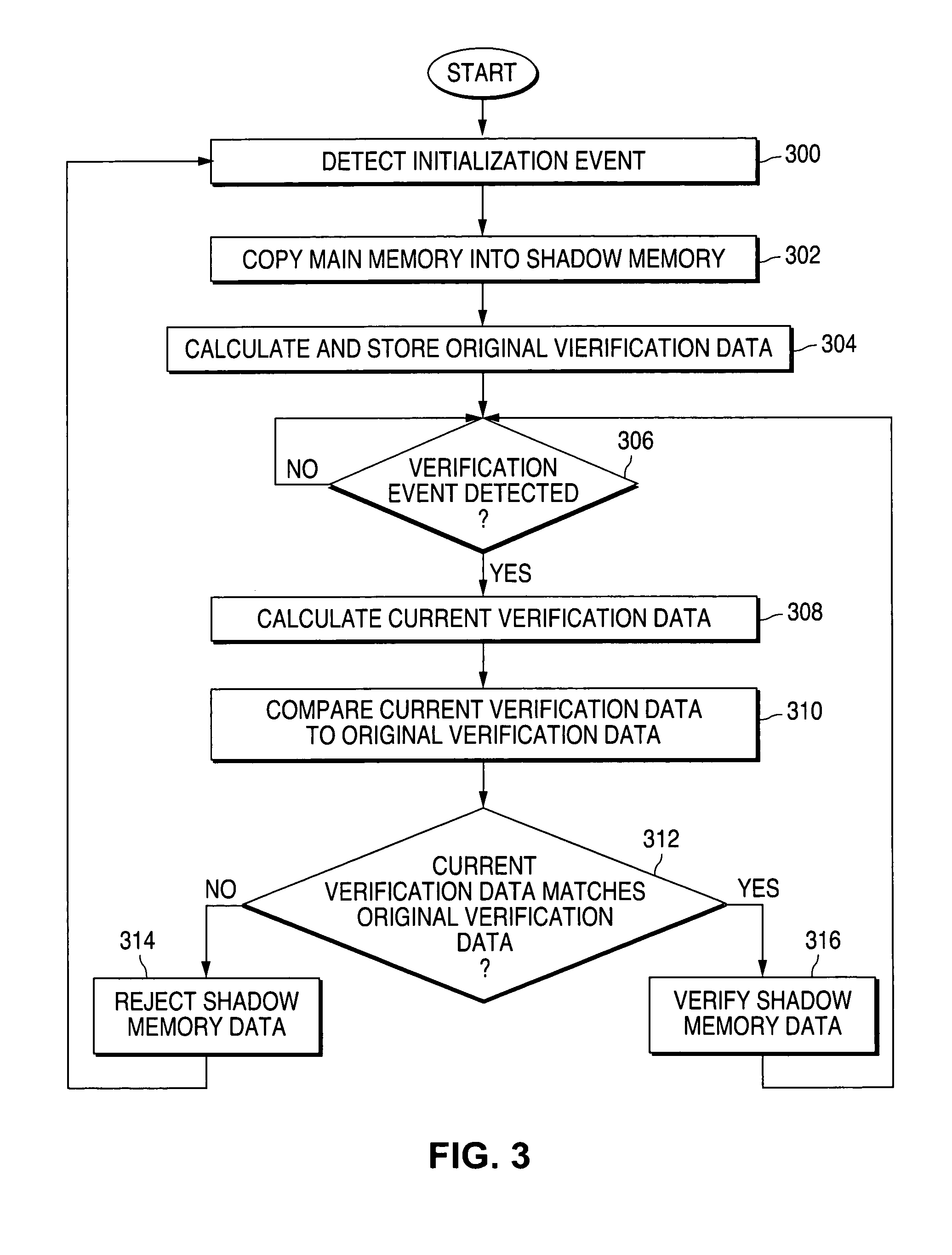
Method and system for verifying data in a shadow memory
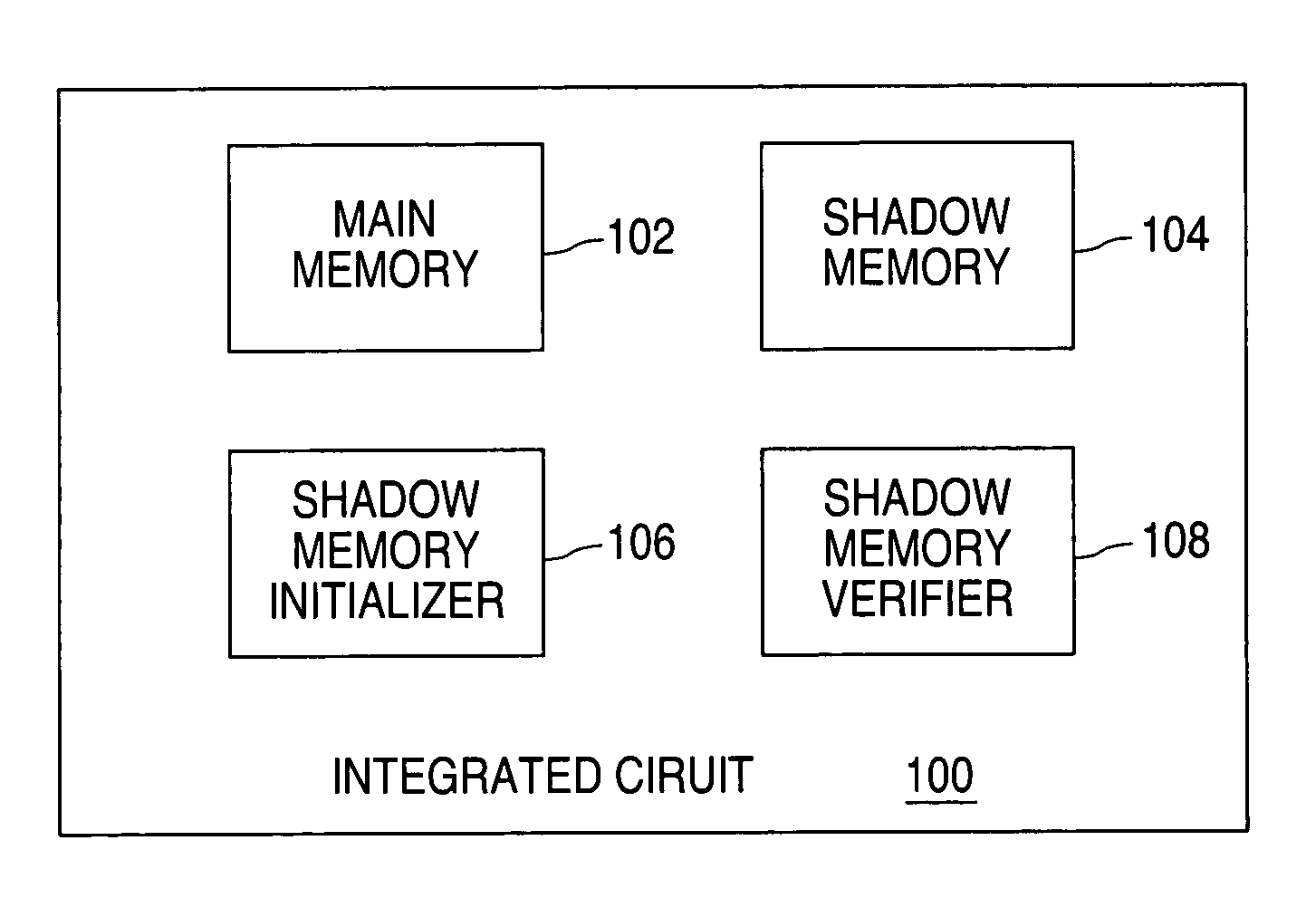
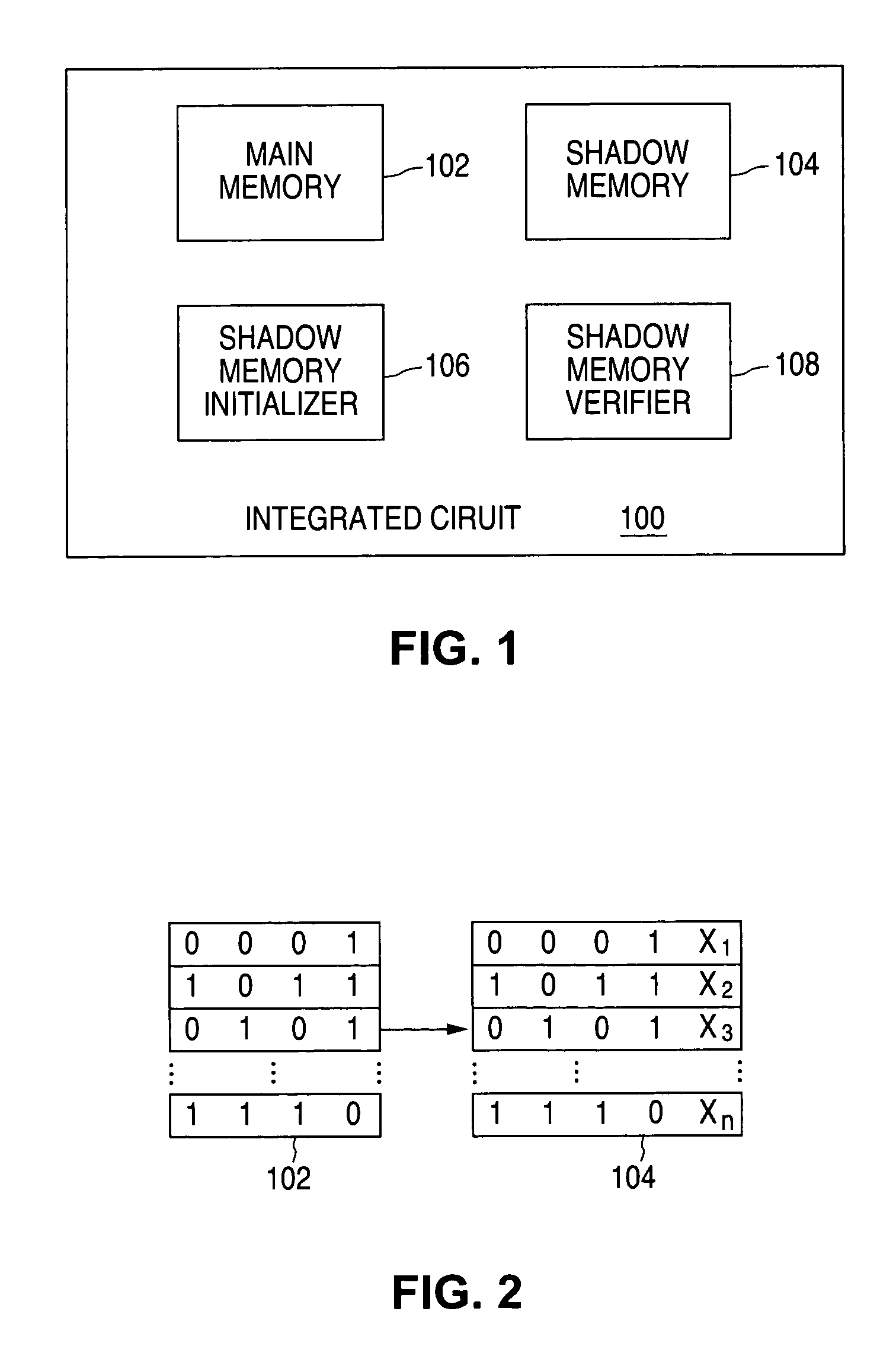
A system for verifying data in a shadow memory is provided that includes a main memory, a shadow memory, a shadow memory initializer, and a shadow memory verifier. The main memory is operable to store main data persistently. The shadow memory is operable to store shadow data temporarily. The shadow data comprises a copy of the main data. The shadow memory initializer is operable to detect an initialization event and to initialize the shadow memory based on the initialization event. The shadow memory verifier is operable to detect a verification event and to verify the shadow data based on the verification event.
Owner:NAT SEMICON CORP
Systems and methods for updating a frame buffer based on arbitrary graphics calls
InactiveUS20050012679A1Significant performance gainMaximum performanceDigital computer detailsImage memory managementGraphicsShadow memory
A method for dividing a display into zones at system initialization for tracking which zones have any pixels revised so that, when the time comes to update the display, only the zones requiring revision (that is, those zones in which any pixel has been revised) are copied from shadow memory to the frame buffer for display on the display device. The memory for tracking these zones can be allocated at initialization and held since it is relatively small. Consequently, a significant performance gain may be achieved by avoiding the shortcomings of the existing methods in the art notwithstanding the fact that some “clean” pixels in each zone having even a single changed pixel are also rewritten to the frame buffer.
Owner:MICROSOFT TECH LICENSING LLC
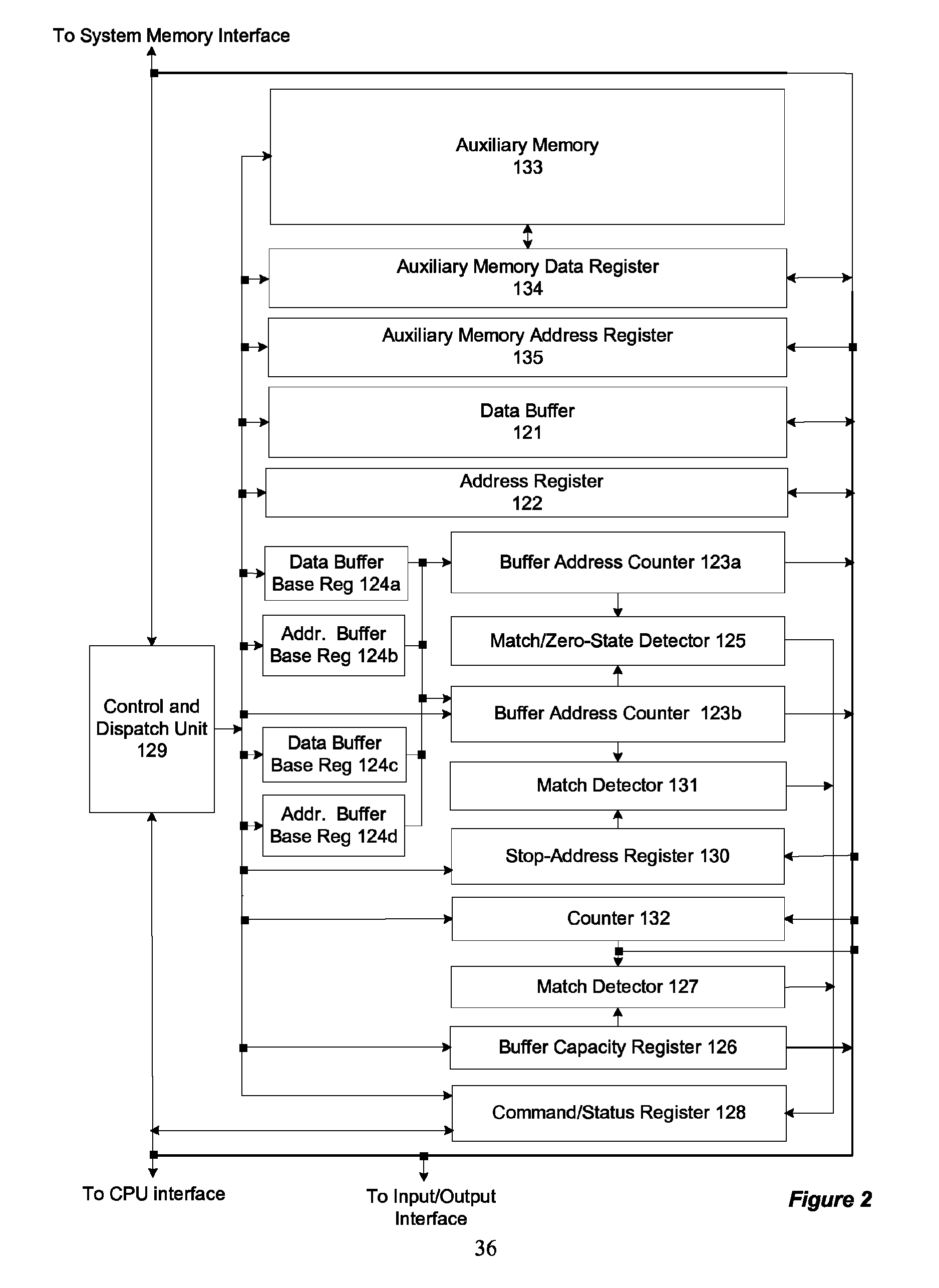
Memory-controller-embedded apparatus and procedure for achieving system-directed checkpointing without operating-system kernel support
ActiveUS7840768B2Eliminate needSafety arrangmentsDigital data processing detailsSupporting systemImage Inspection
System-directed checkpointing is enabled in otherwise standard computers through relatively straightforward augmentations to the computer's memory controller hub. Firmware routines executed by a control and dispatch unit that is normally part of any memory controller hub enable it to implement any of six different checkpointing strategies: post-image checkpointing in which an image of the system state at the time of the last checkpoint is maintained in a local shadow memory; post-image checkpointing in which an image of the system state at the time of the last checkpoint is maintained in a shadow memory located in a second, backup computer; post-image checkpointing using a bit-map memory, having one bit representing each data block in system memory, to reduce the amount of memory-to-memory copying required to establish a checkpoint; post-image checkpointing to a local shadow memory using two bit map memories to enable normal processing to continue while the shadow is being updated, post-image checkpointing to a local shadow memory using a block-state memory that eliminates the need for any memory-to-memory copying; and local pre-image checkpointing that does not require a shadow memory. Since each of these implementations has advantages and disadvantages relative to the others and since similar mechanisms are used in the memory controller hub for all of these options, it can be designed to support all of them with hardwired or settable status bits defining which is to be supported in a given situation.
Owner:CHEMTRON RES
Non-volatile shadow latch using a nanotube switch
A non-volatile memory cell includes a volatile storage device that stores a corresponding logic state in response to electrical stimulus; and a shadow memory device coupled to the volatile storage device. The shadow memory device receives and stores the corresponding logic state in response to electrical stimulus. The shadow memory device includes a non-volatile nanotube switch that stores the corresponding state of the shadow device.
Owner:NANTERO
Self-modifying code identification method based on hardware emulator
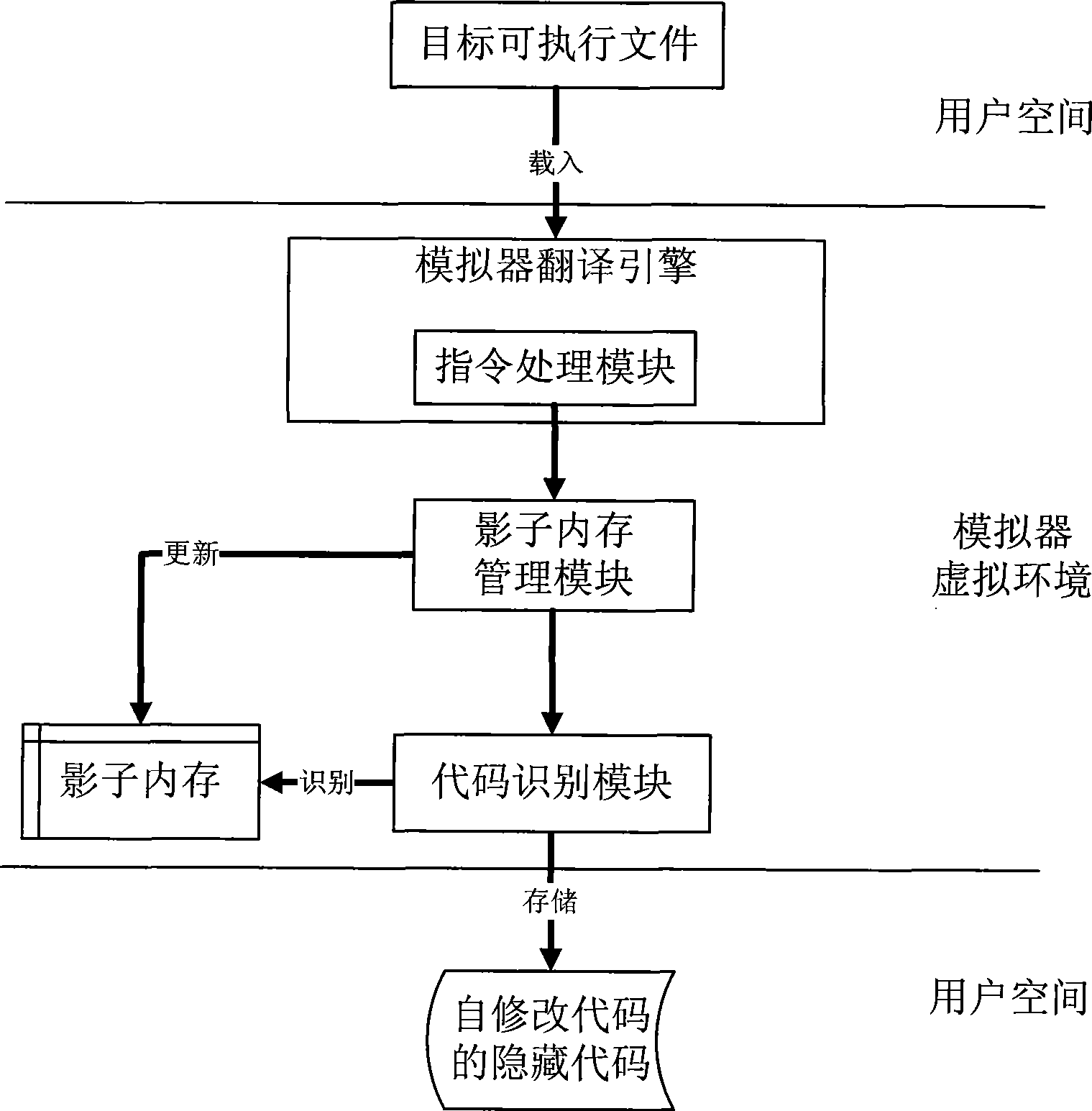
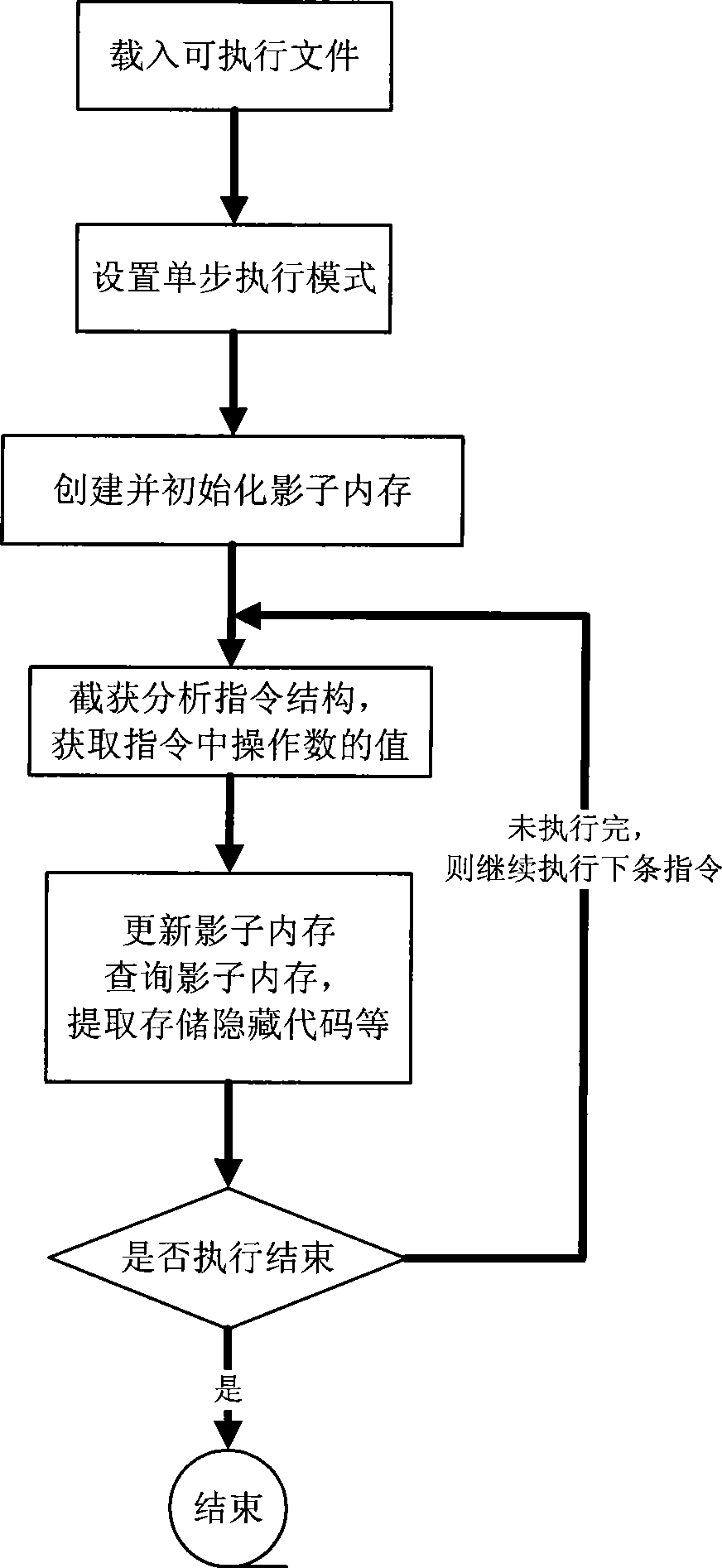
ActiveCN101458630AImprove analysis efficiencyHigh transparencyProgram controlProgram/content distribution protectionSelf-modifying codeSecurity measurement
The invention belongs to the technical field of software security measurement and evaluation, especially relates to a self-modifying code recognition method based on a hardware simulator. The invention is provided with a marker in the hardware simulator in order to only execute a target executable file by one step and capture a virtual system execute instruction, the information in the process can be executed by using a shadow memory monitoring program, the code which is dynamically released into the memory and is executed can be recognized and executed in the course of program execution, so that data information of the analysis target can be acquired. The data acquisition of the invention is implemented by the simulation hardware, is not executed by placing the malevolence code on a true CPU, so the actual system can not be affected. The invention adopts the hardware simulator as a dynamic analysis platform, which can improve the transparency between the analysis platform and the code and can effectively defend against the detection of the code.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Method and system for wireless transmission
InactiveUS20060092959A1Cathode-ray tube indicatorsData switching by path configurationWireless transmissionShadow memory
Multimedia from a source can be wirelessly transmitted in an infrared system to a display. To support rapid reads of data written into a slave at the display by a master at the source in accordance with I2C protocol, a master simulator on the display side continually polls the slave for changes, and maintains a shadow memory in a slave simulator at the source side current, so that reads from the master may be immediately executed from the shadow memory in the slave simulator without transitting the wireless link.
Owner:SONY CORP +1
Transceiver having shadow memory facilitating on-transceiver collection and communication of local parameters
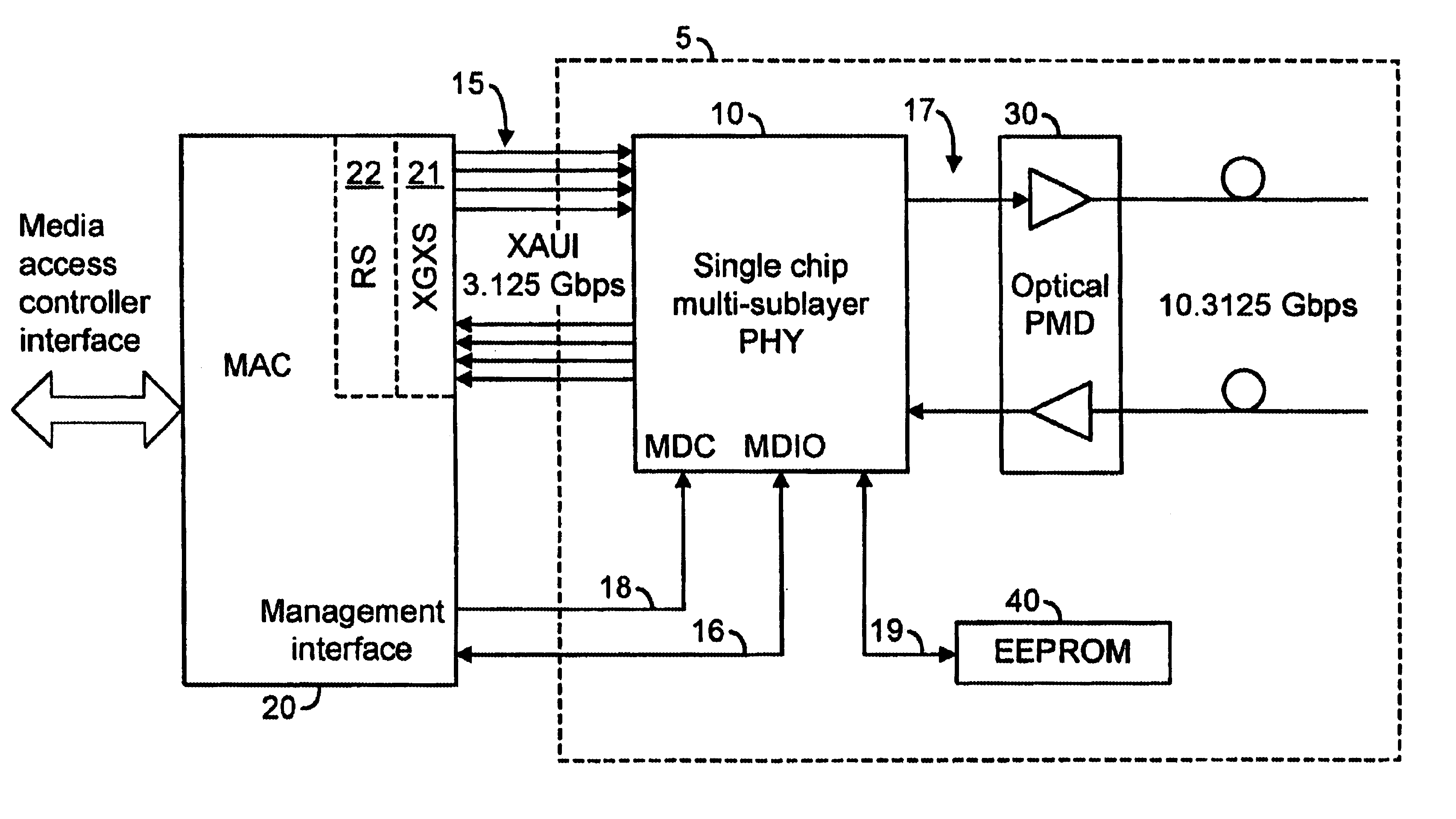
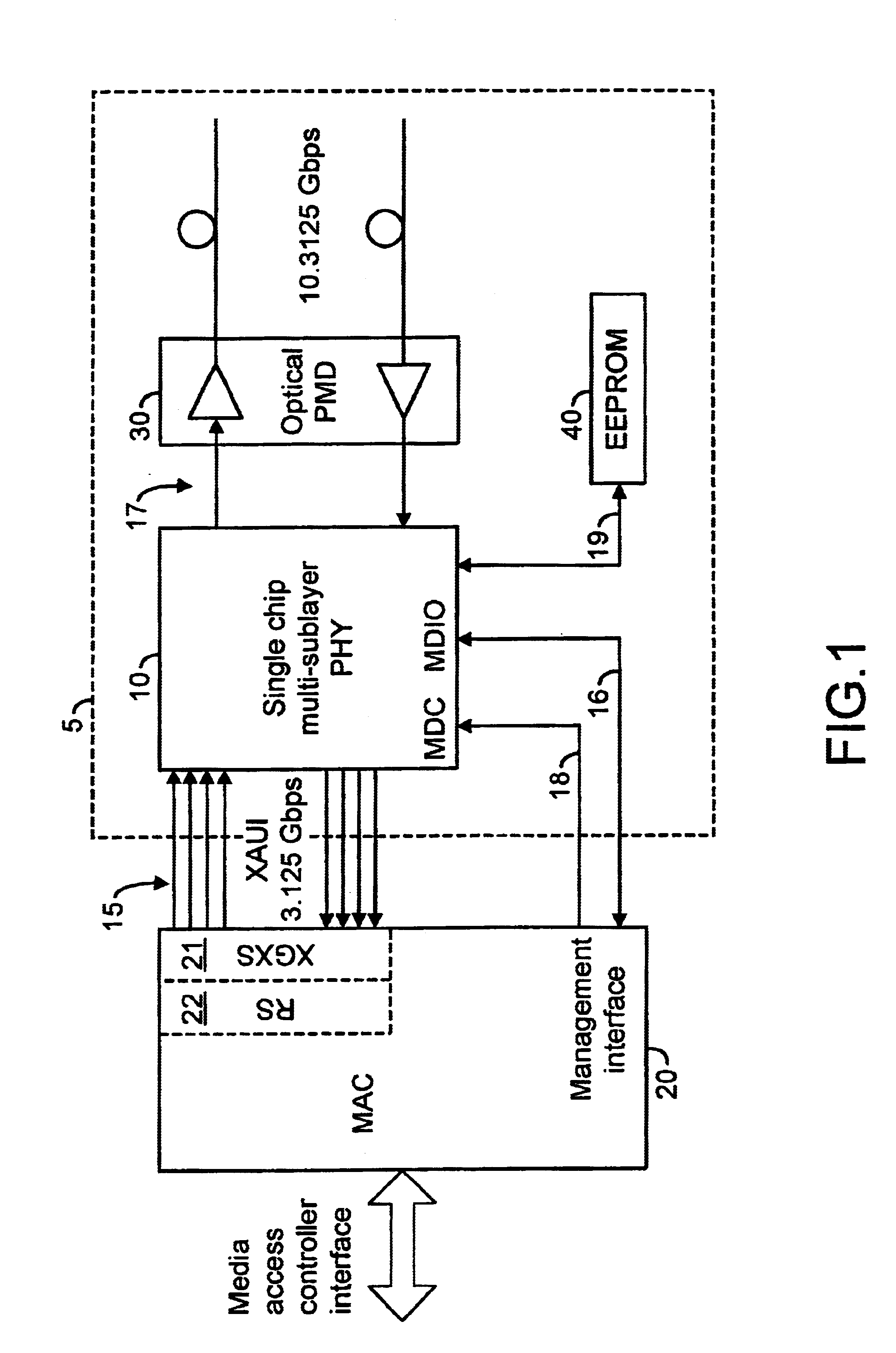
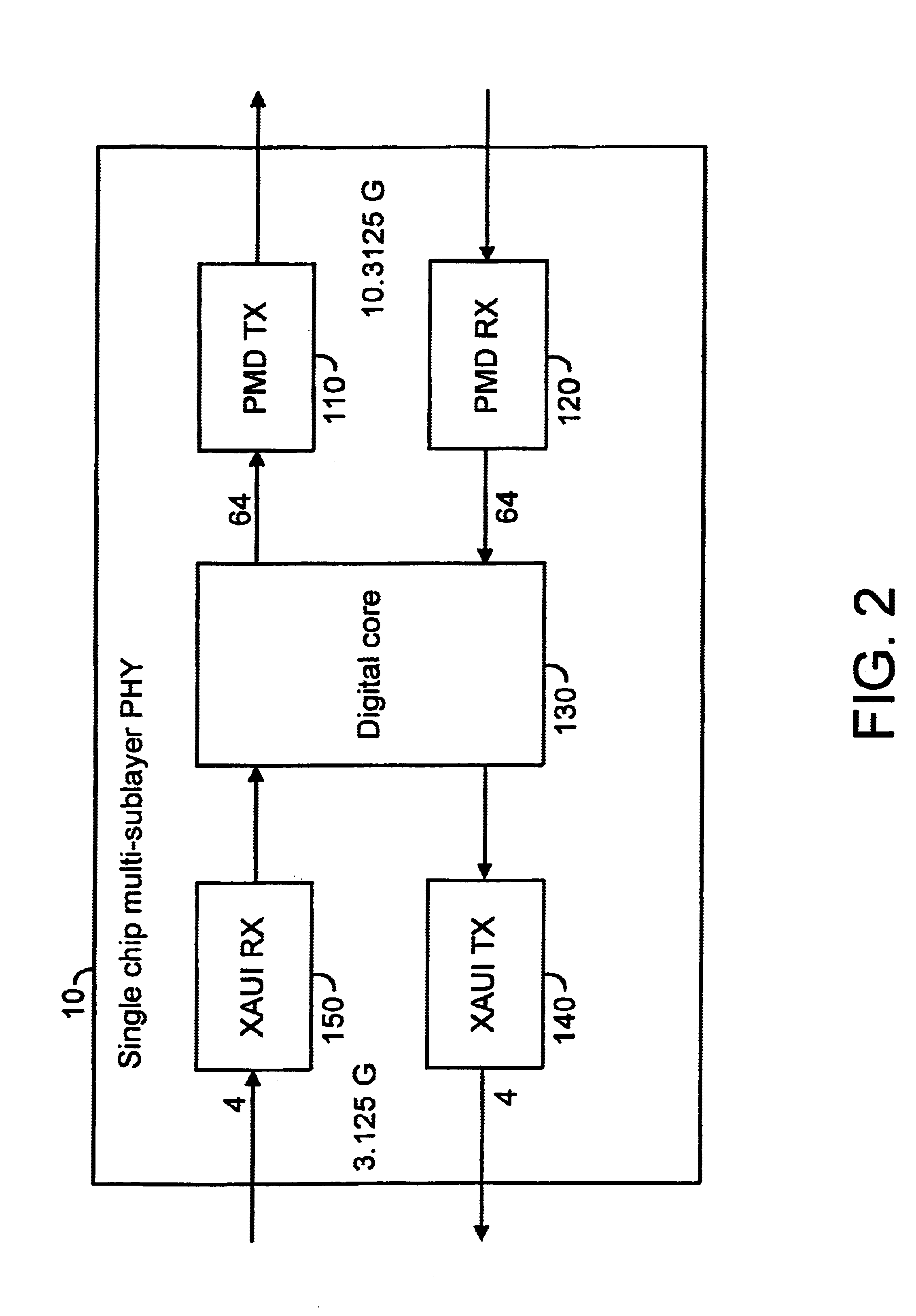
InactiveUS6906426B2Improve liquidityTransistorSemiconductor/solid-state device detailsTransceiverProcessor register
The present invention relates to a register for a single chip multi-sublayer PHY. More specifically, the present invention relates to a transceiver module including a single chip multi-layer PHY having one or more shadow registers. The transceiver module includes one or more storage modules adapted to store transceiver module local data. The shadow registers are adapted to facilitate collection of the local data from the storage modules and communicate the collected data to another portion of the transceiver module and / or to the upper lever system using at least one interface communicating with the shadow register.
Owner:AVAGO TECH INT SALES PTE LTD
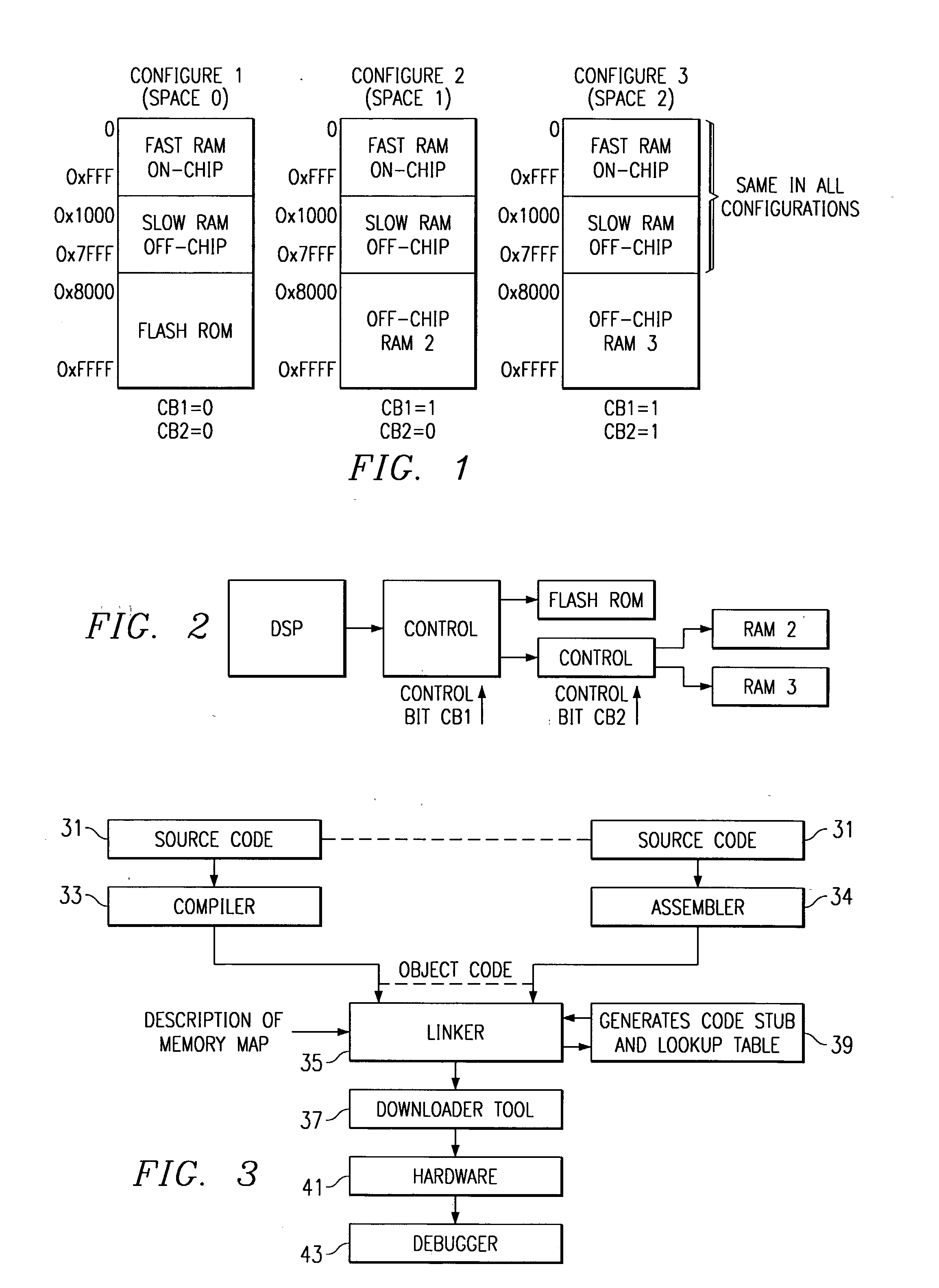
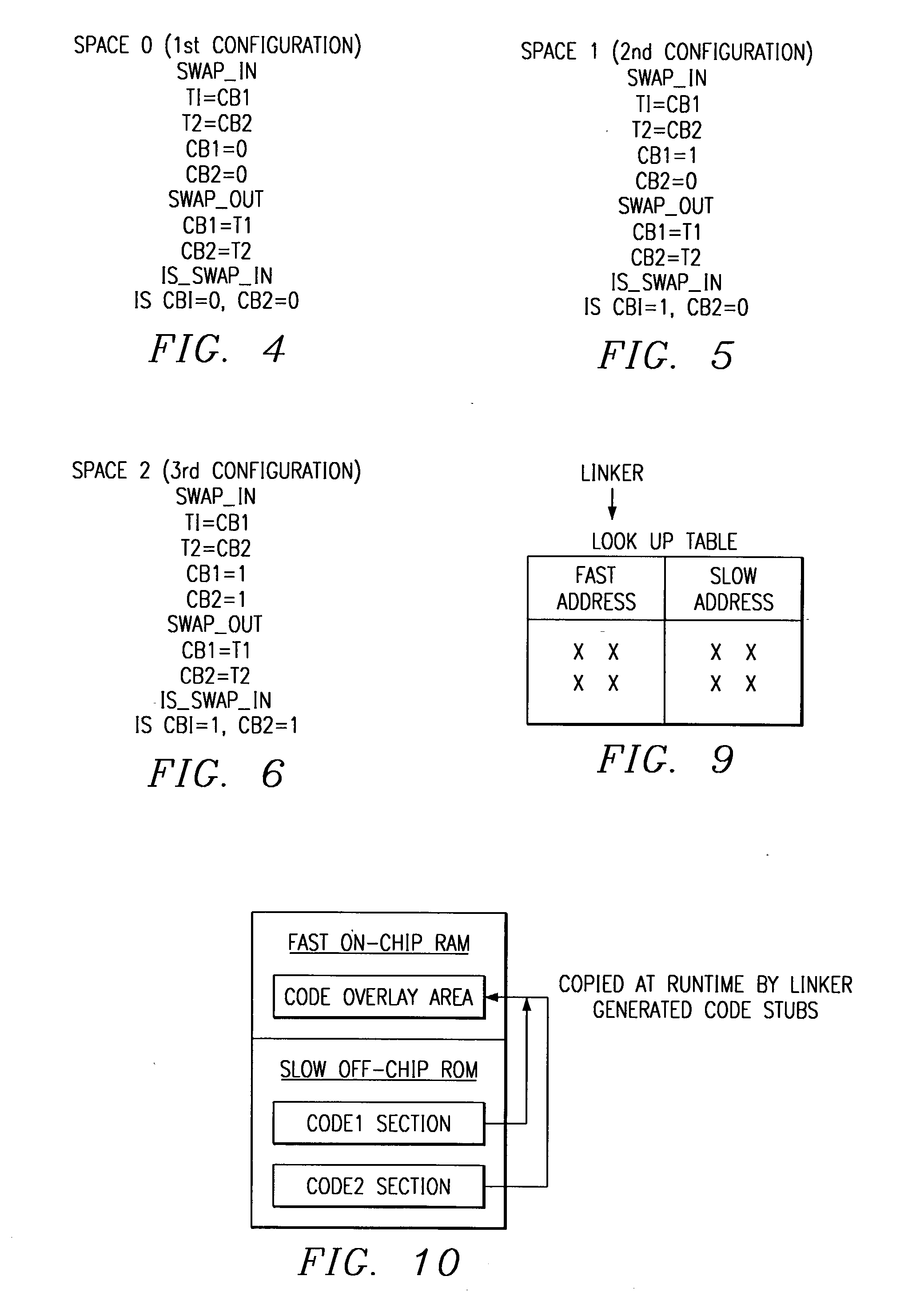
Linking of applications into devices having overlays and shadow memories
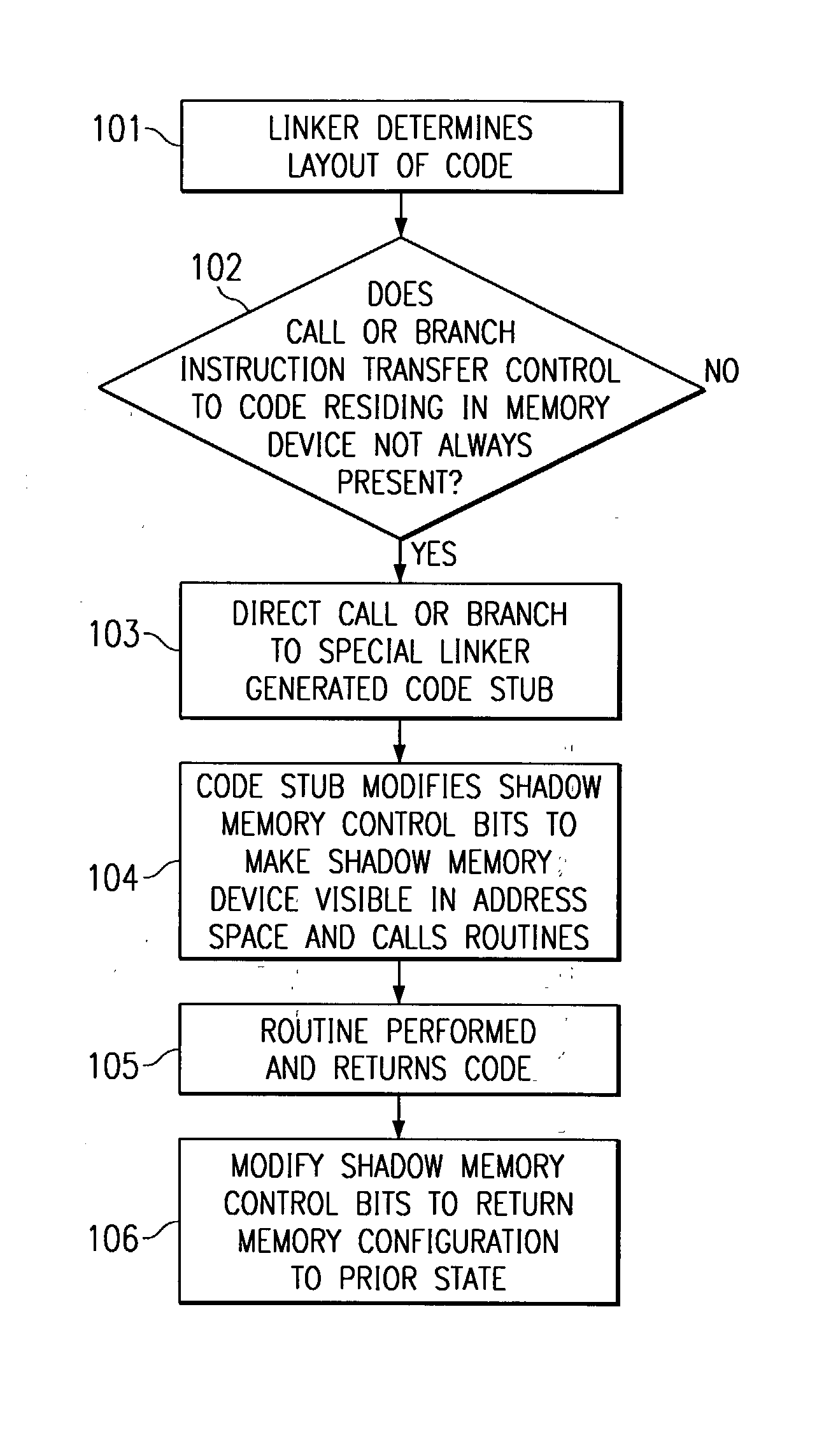
ActiveUS20020188929A1Automate processingMemory adressing/allocation/relocationProgram loading/initiatingShadow memoryApplication software
In one embodiment a method for handling shadow or overlay memories is described wherein a linker contains a description of the memory of a target embedded system so that each memory space is described for each state of the control devices. The linker in one embodiment contains the shadow memory configuration information so that post linker tools such as loaders and debuggers can utilize this information. The information for each configuration includes how to get the device into the state that makes each configuration visible in address space, how to get the device back into the state it was in before the state was changed and how to find out the state the device is in.
Owner:TEXAS INSTR INC
Reducing remote reads of memory in a hybrid computing environment
InactiveUS9015443B2Reducing remote readInterprogram communicationMemory adressing/allocation/relocationArray data structureShadow memory
A hybrid computing environment in which the host computer allocates, in the shadow memory area of the host computer, a memory region for a packet to be written to the shared memory of an accelerator; writes packet data to the accelerator's shared memory in a memory region corresponding to the allocated memory region; inserts, in a next available element of the accelerator's descriptor array, a descriptor identifying the written packet data; increments the copy of the head pointer of the accelerator's descriptor array maintained on the host computer; and updates a copy of the head pointer of the accelerator's descriptor array maintained on the accelerator with the incremented copy.
Owner:IBM CORP
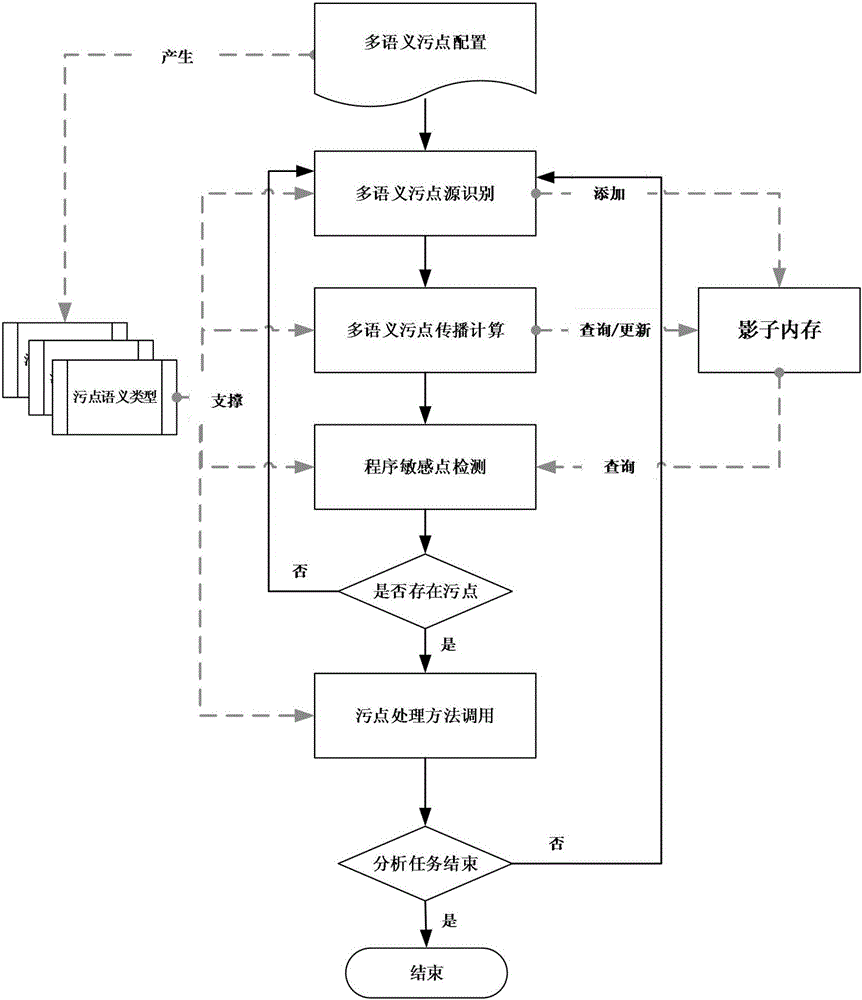
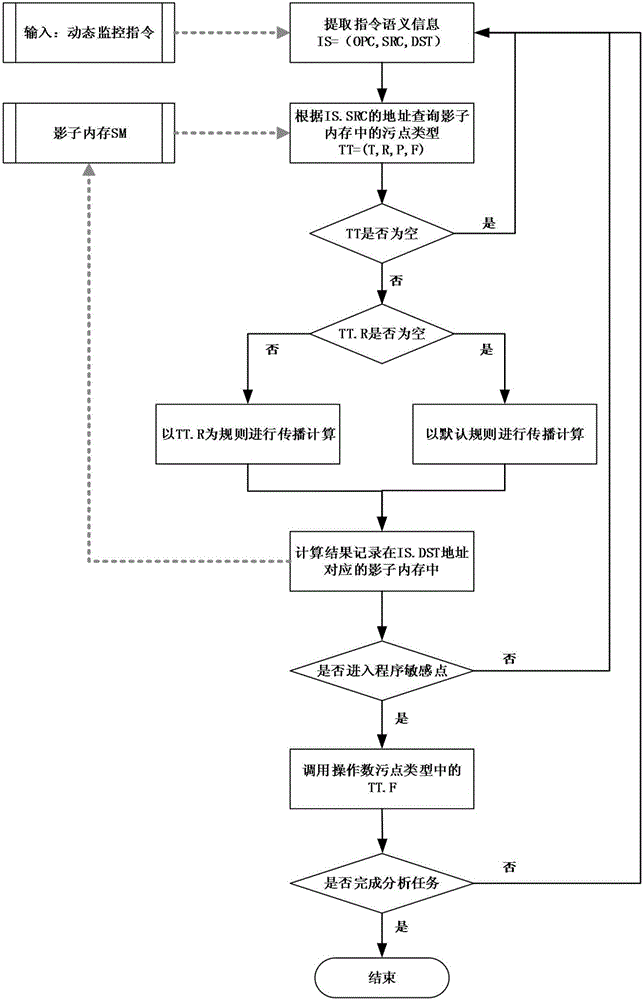
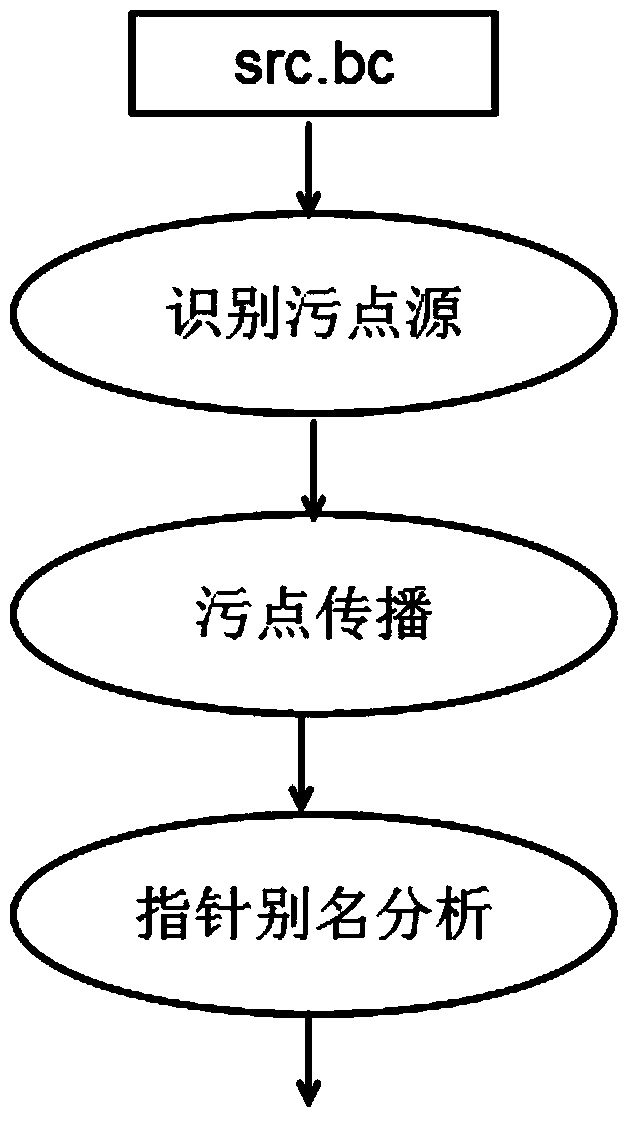
Multi-semantic dynamic taint analysis method
ActiveCN105808430AEnhanced description abilityEasy to handleSoftware testing/debuggingPlatform integrity maintainanceShadow memoryOperand
The invention discloses a multi-semantic dynamic taint analysis method. The method comprises the steps of 1) setting a unique taint semantic type for each type of to-be-tracked semantic data; performing configuration in a one-time dynamic taint analysis process to simultaneously track various semantic information data; 2) according to each taint semantic type, monitoring whether a function of generating the semantic information data of the taint semantic type is called or not in a program running process; if yes, judging that a corresponding taint source exists, and performing recording; 3) according to the monitored semantic information of each instruction and a taint state of an operand, performing taint spread calculation, and recording a calculation result to a shadow memory; and 4) after the spread calculation, judging whether an instruction executed by a program is a sensitive instruction or not according to a preset program sensitive instruction set in the existing taint semantic type, and if yes, performing taint detection to determine whether a taint of the corresponding type exists or not in the position of the instruction. According to the method, the analysis efficiency of a dynamic taint spread method is improved.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Space memory error detection method with high efficiency and high availability
InactiveCN103745755AReduced time performance overheadShorten the timeStatic storageShadow memoryHigh availability
The invention provides a space memory error detection method with high efficiency and high availability. The method comprises the following steps: carrying out static taint analysis on a program, and carrying out taint marking on a pointer which may be controlled by an attacker; building a shadow memory space before the program runs; storing boundary information of the taint marked pointer; creating the boundary information for the taint marked pointer in the program, and transmitting the information to other related pointers; and finally carrying out pointer boundary detection on an instruction for writing the memory by using the taint marked pointer in the program, inserting a code of tolerating the error into the program, so that the program can tolerate the space memory error to ensure the availability of the program. By adopting the method, performance overhead when the converted program runs is reduced, and the space memory error can be effectively detected. In addition, the availability of the program is improved by adopting an error-tolerating method, and the program is prevented from being attacked by denial of service.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI +1
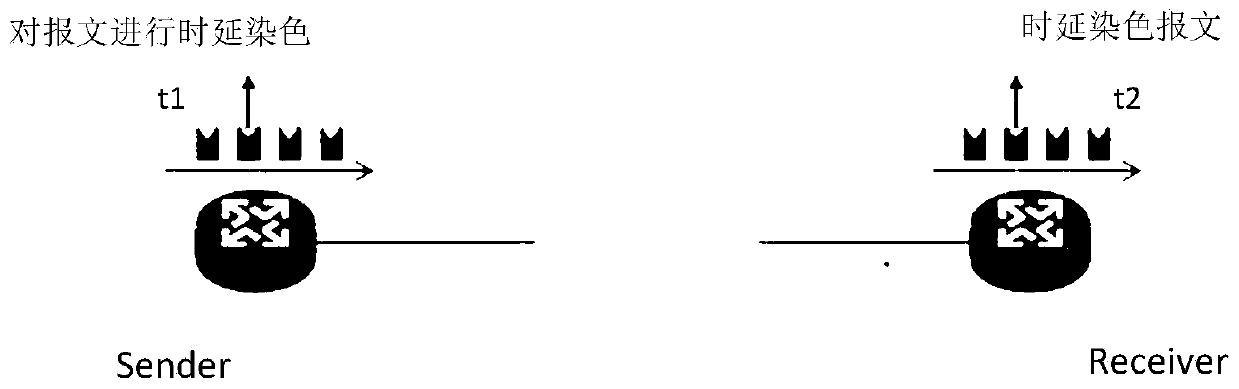
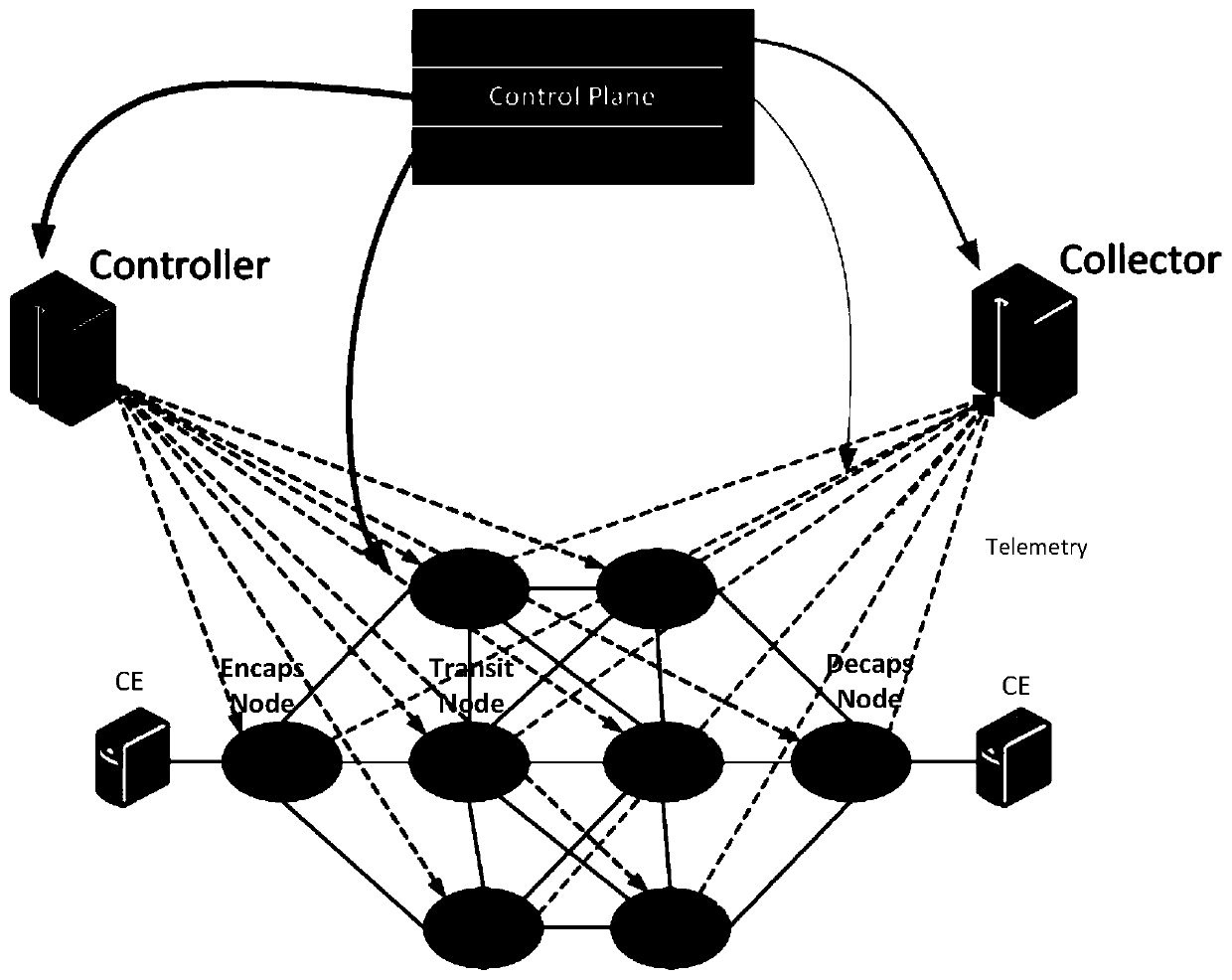
Network performance detection system and method
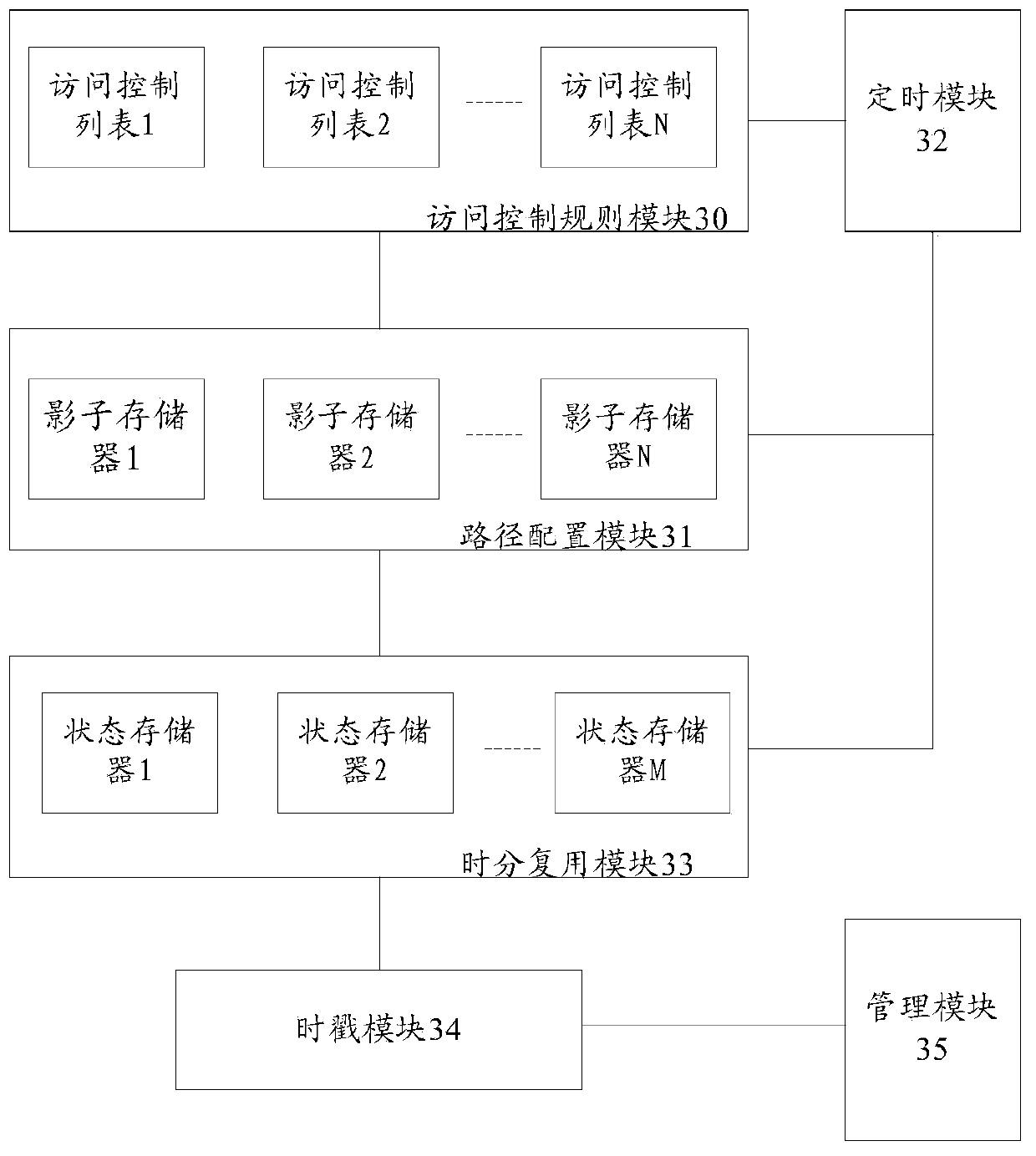
ActiveCN111277454AConducive to smooth evolutionSmooth evolutionData switching networksService flowTimestamp
The invention discloses a network performance detection system. According to the invention, a measurement period is divided into a plurality of time slices; a plurality of shadow memories are correspondingly arranged for one state memory; therefore, in a measurement period, message dyeing operation is started for a plurality of service flows, the message dyeing operation of one service flow in each group of service flows is controlled to be started in each time slice, a system timestamp is stamped on a dyed message, and the system timestamp is sent to a server. Correspondingly, the invention further discloses a network performance testing method. According to the invention, the resources of the state memory can be flexibly expanded so as to meet the network performance test of more serviceflows.
Owner:UTSTARCOM TELECOM CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com