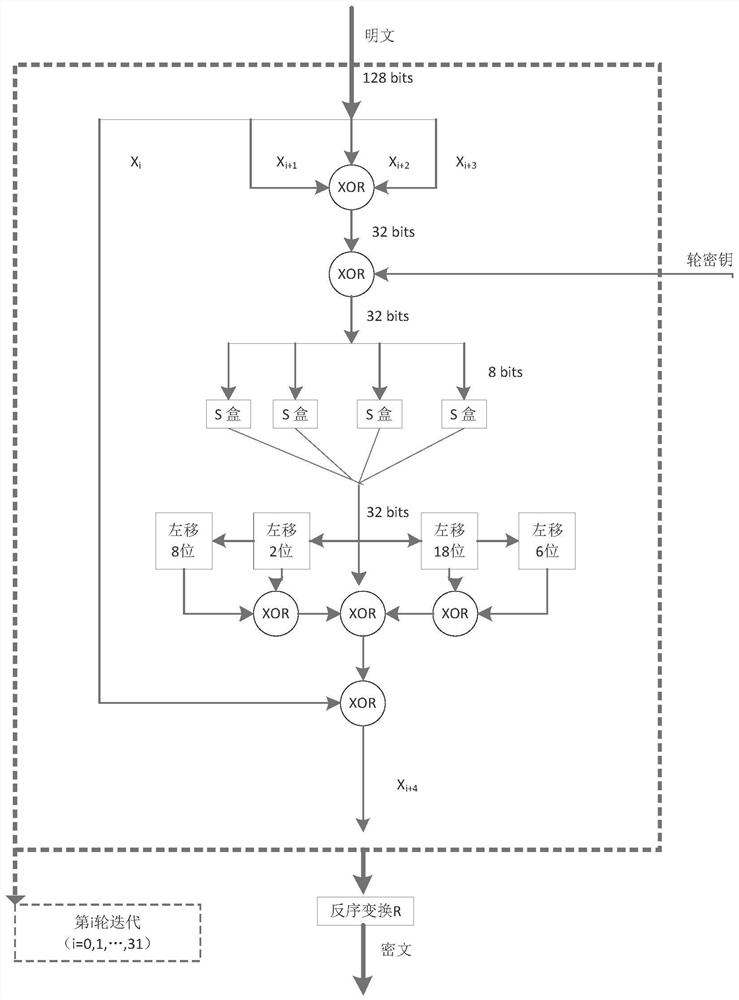
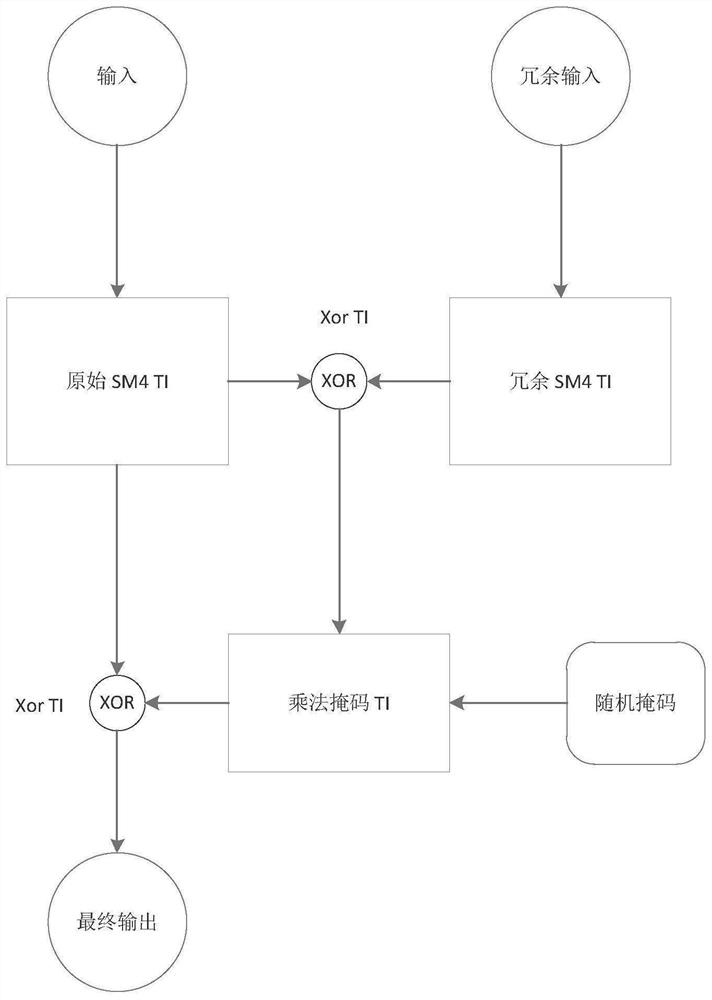
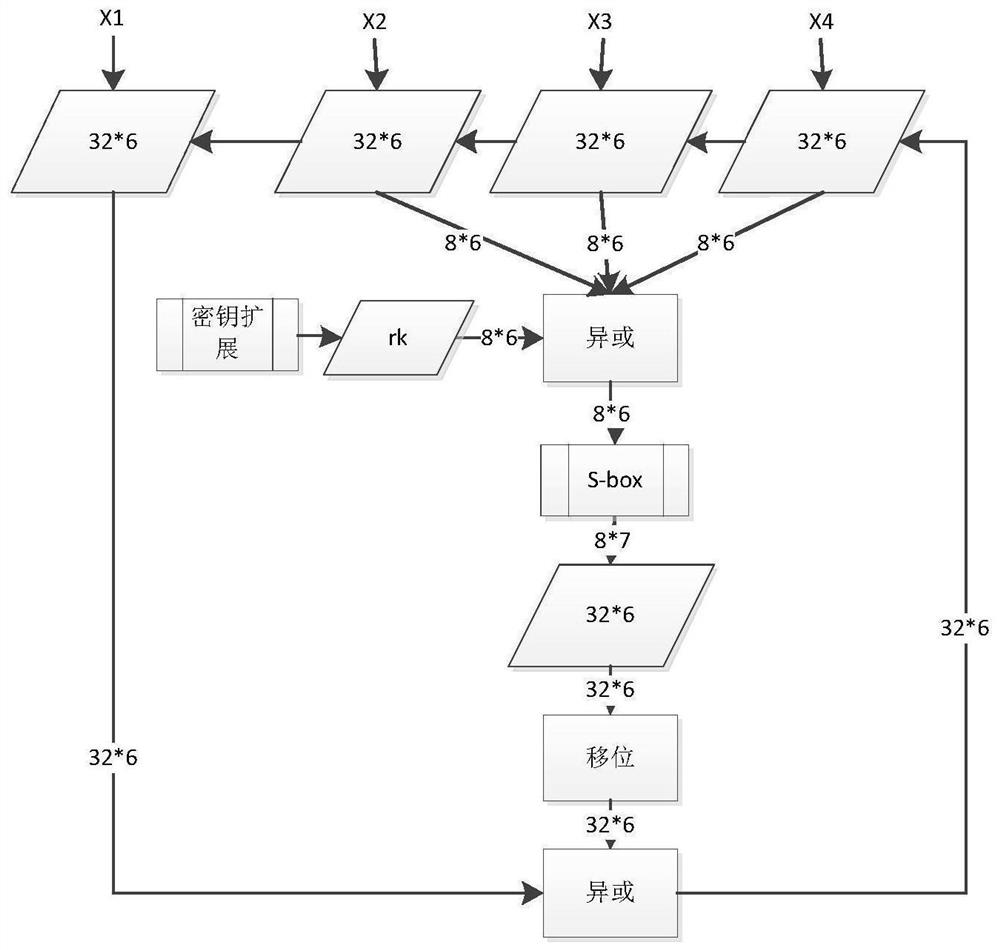
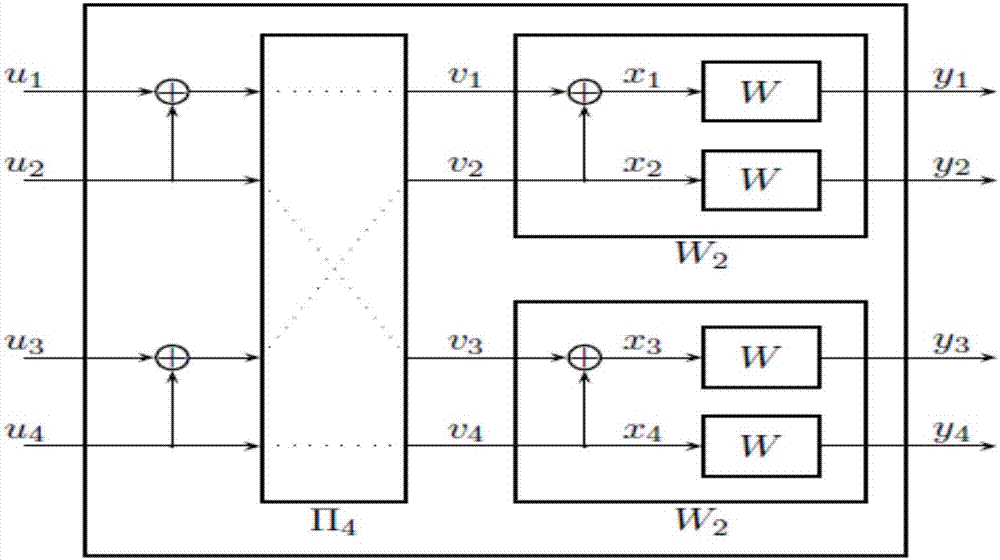
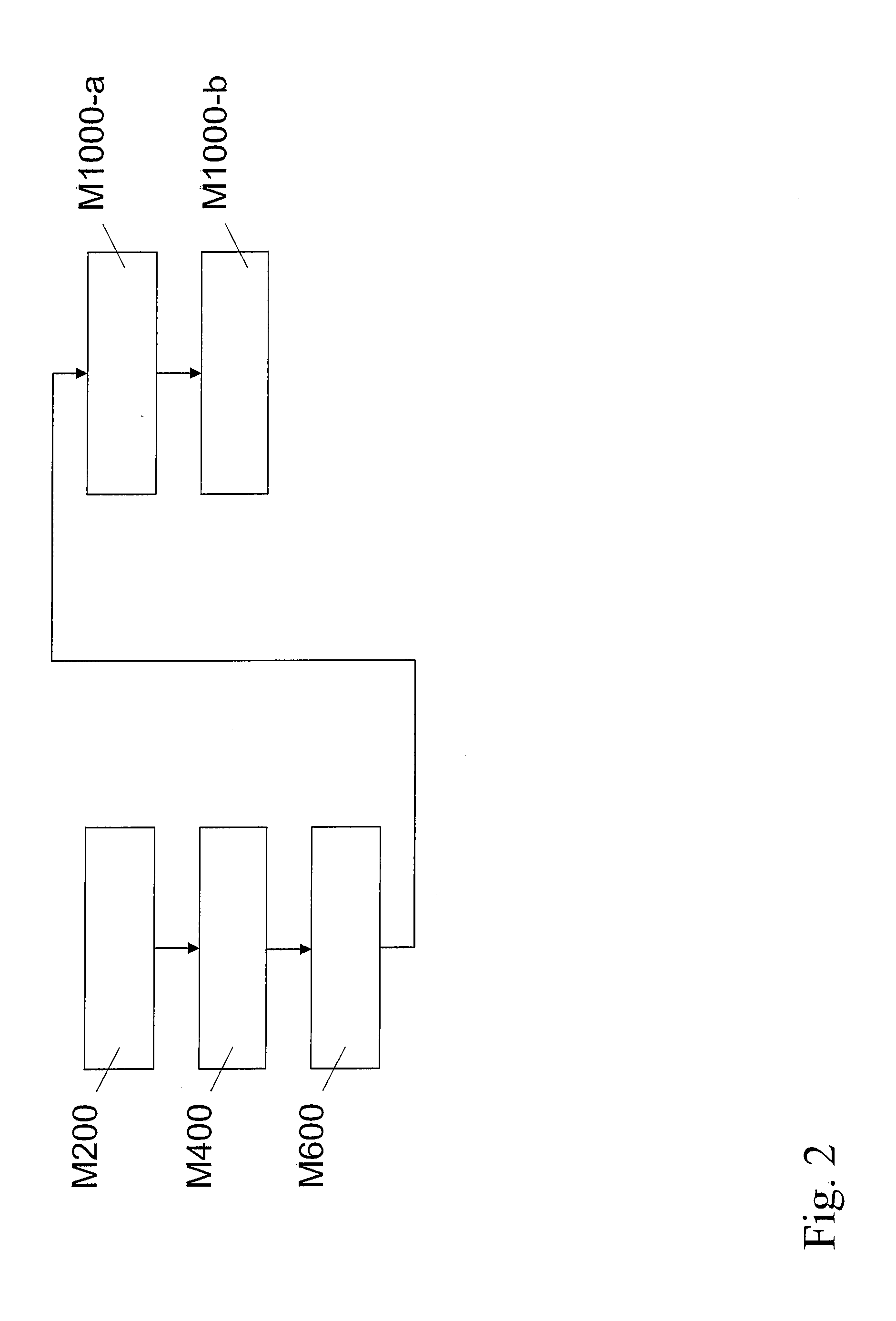Patents
Literature
129 results about "Fault attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
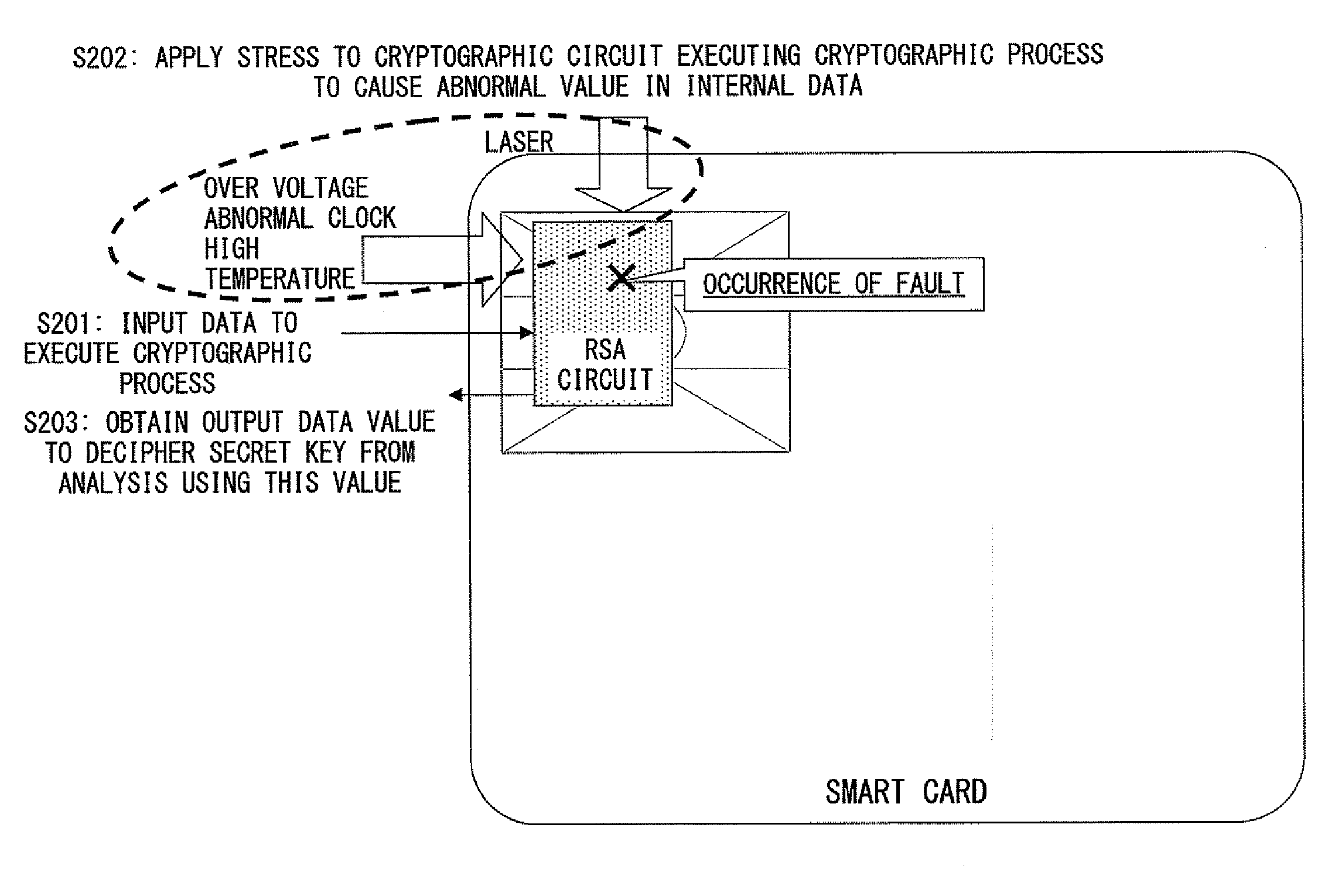
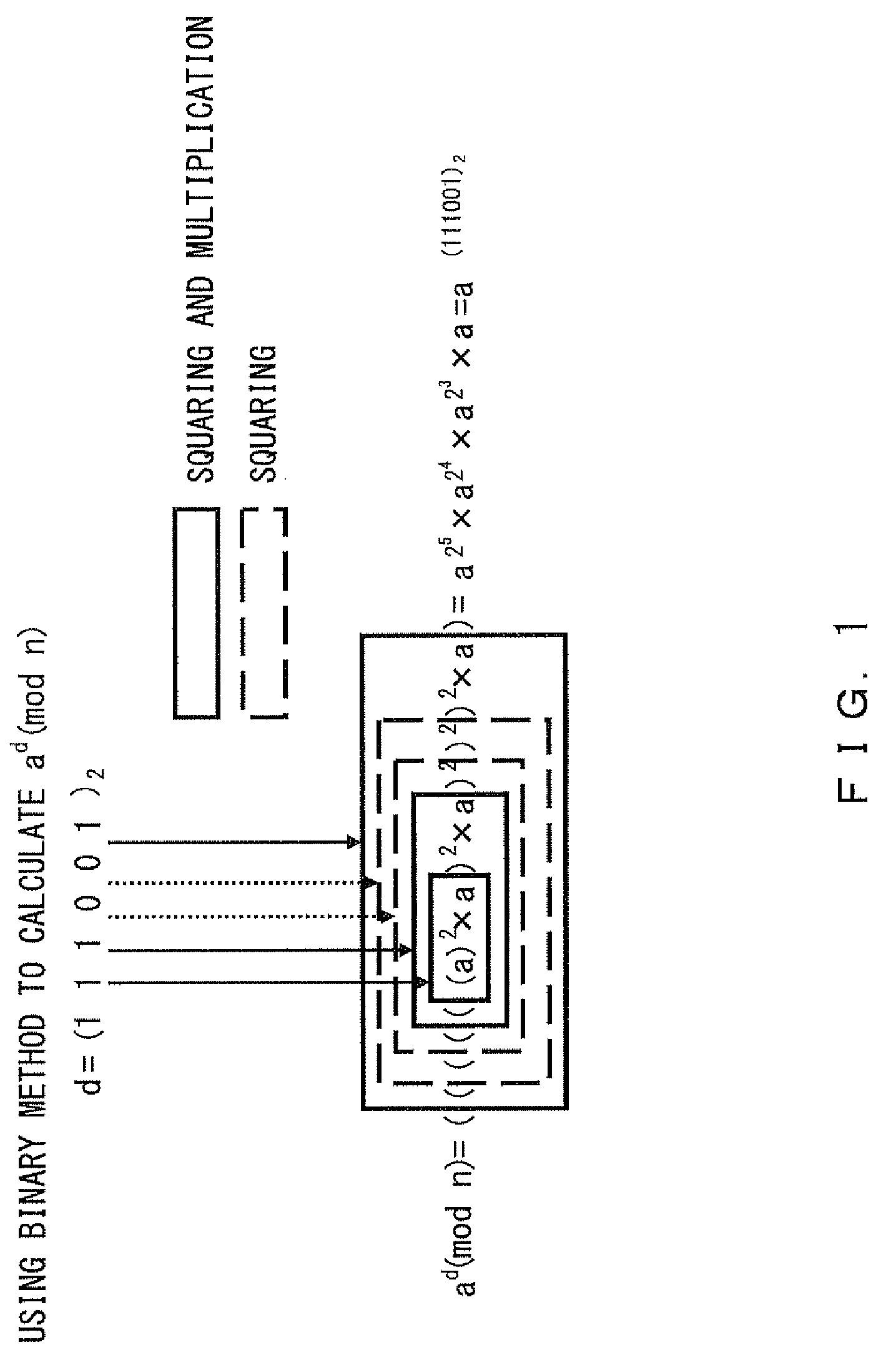
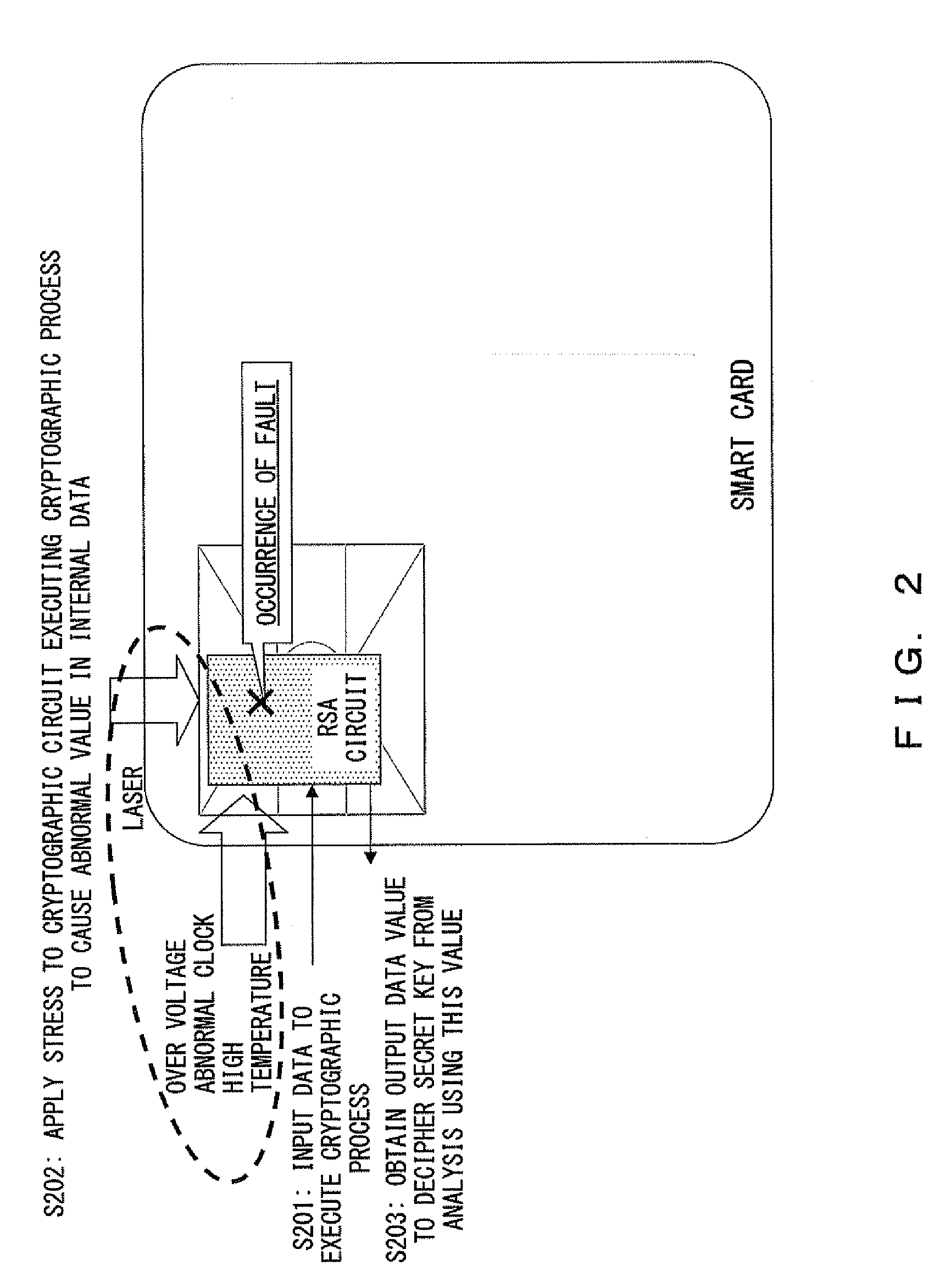
What is Fault Attack. 1. A fault attack is an intentional manipulation of the integrated circuit or its state, with the aim to provoke an error within the integrated circuit in order to move the device into an unintended state. The goal is to access security critical information or to disable internal protection mechanisms.
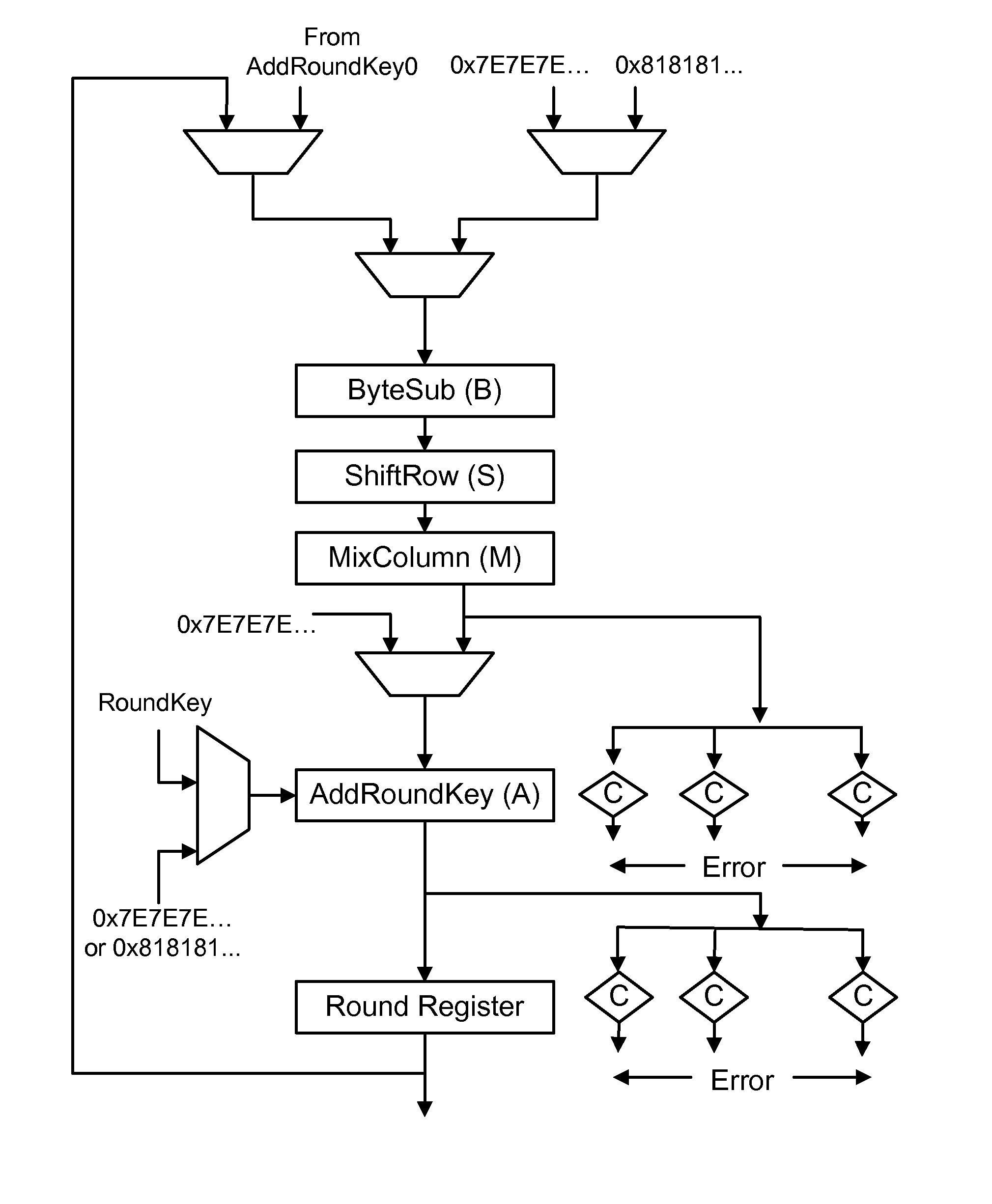
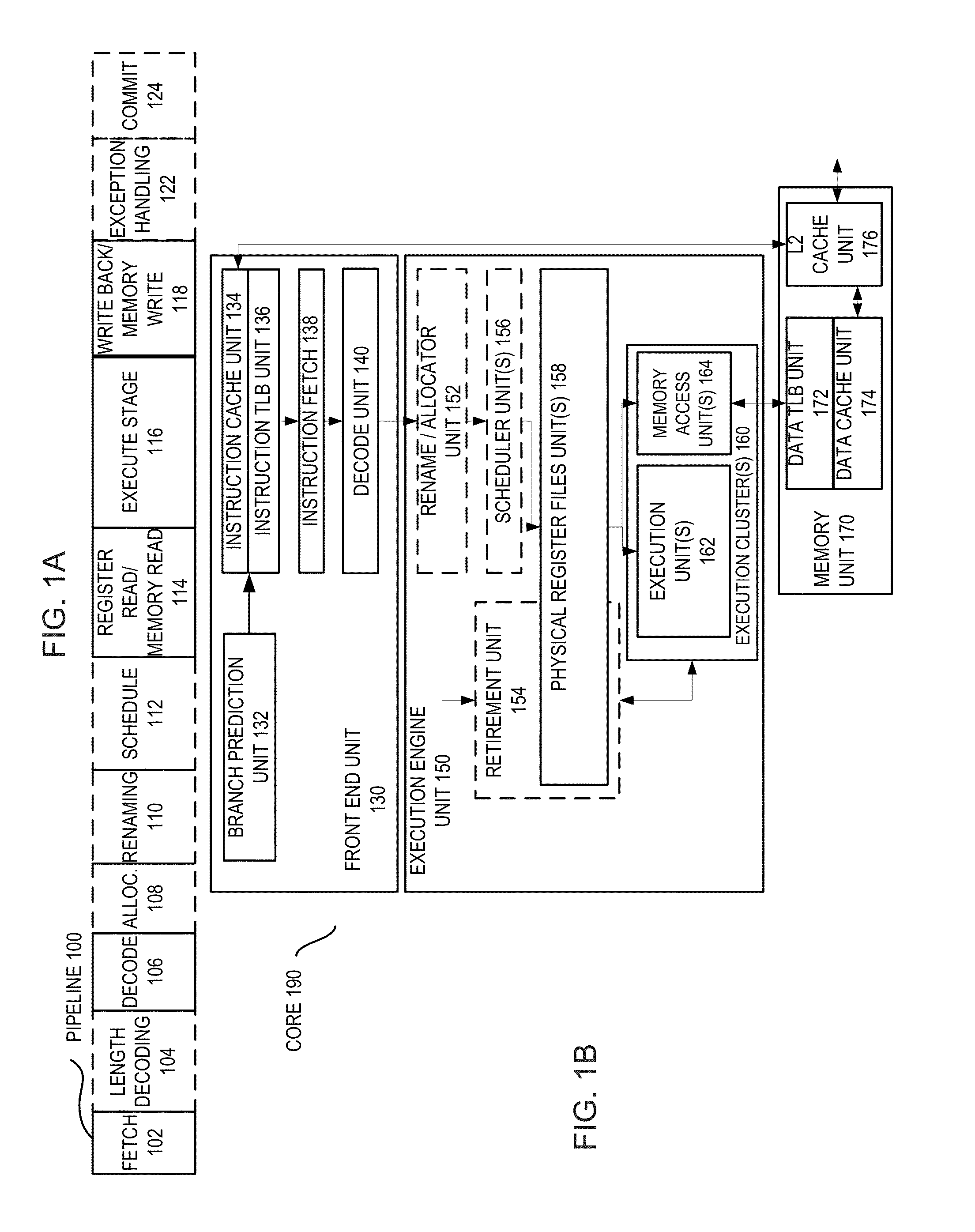
Invariance based concurrent error detection for the advanced encryption standard
ActiveUS20070014395A1Protection attackPublic key for secure communicationSecret communicationThroughput degradationAdvanced Encryption Standard
Advanced Encryption Standard (AES) is an encryption algorithm for securing sensitive unclassified material by U.S. Government agencies and, as a consequence the de facto encryption standard for commercial applications worldwide. Performing concurrent error detection (CED) for protection of such a widely deployed algorithm is an issue of paramount importance. We present a low-cost CED method for AES. In this method, we make use of invariance properties of AES to detect errors. For the first time, the invariance properties of the AES, which are for the most part used to attack the algorithm, are being used to protect it from fault attacks. Our preliminary ASIC synthesis of this architecture resulted in an area overhead of 13.8% and a throughput degradation of 16.67%.
Owner:POLYTECHNIC INST OF NEW YORK
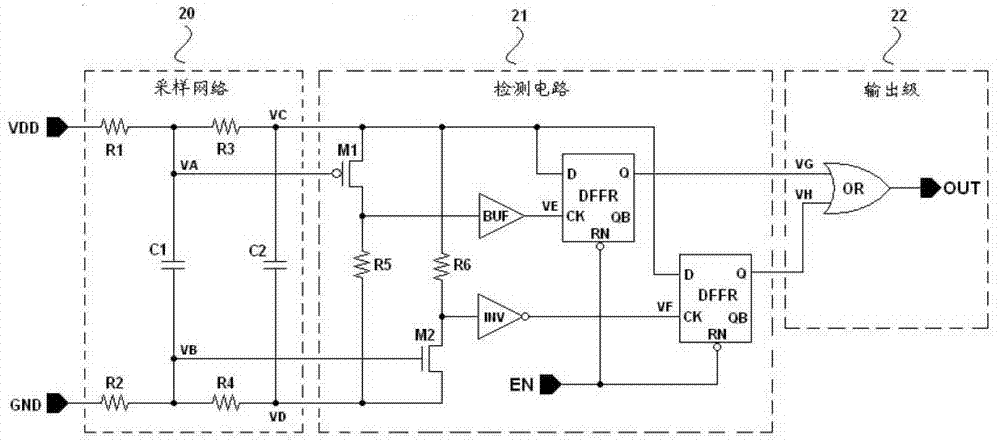
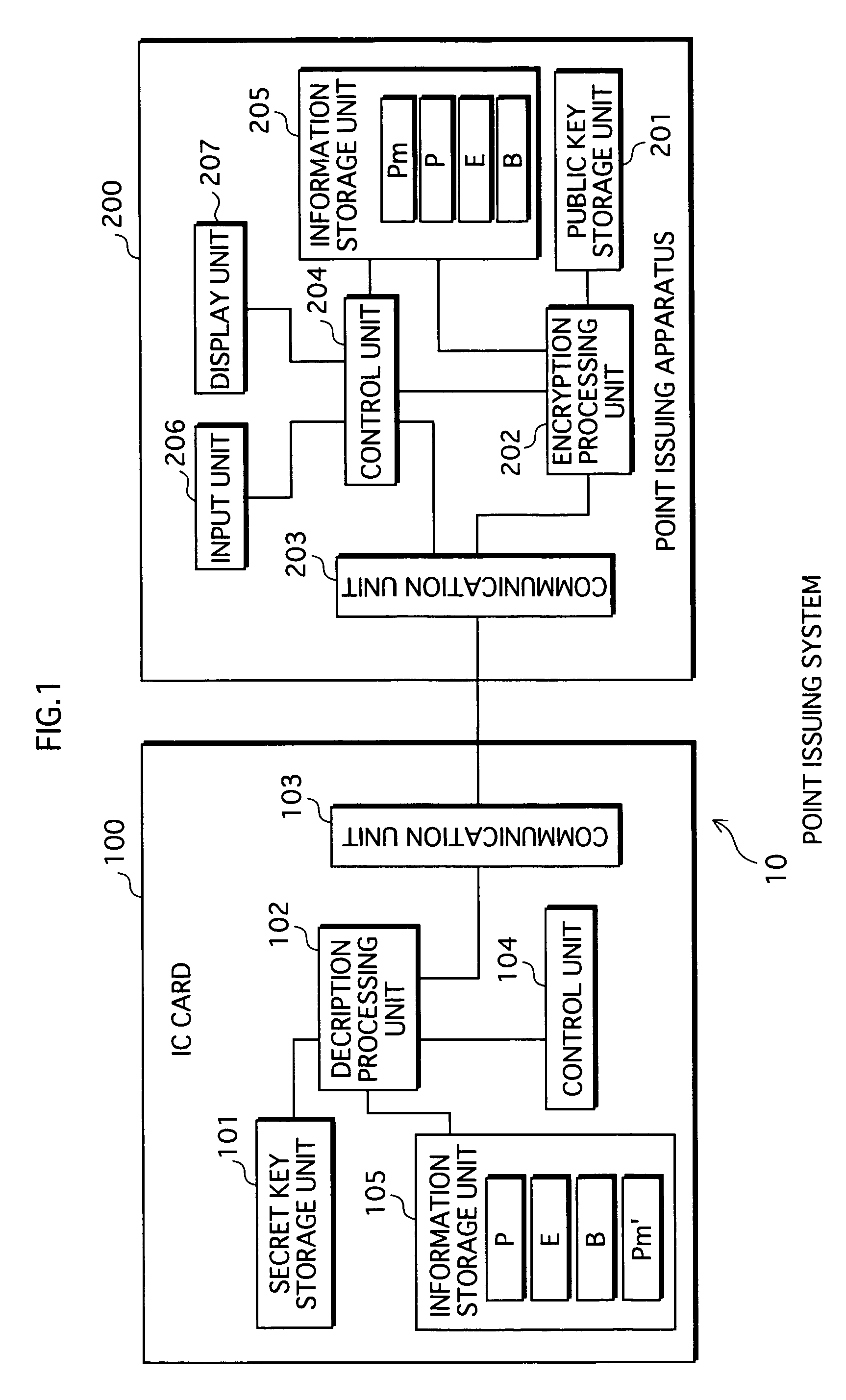
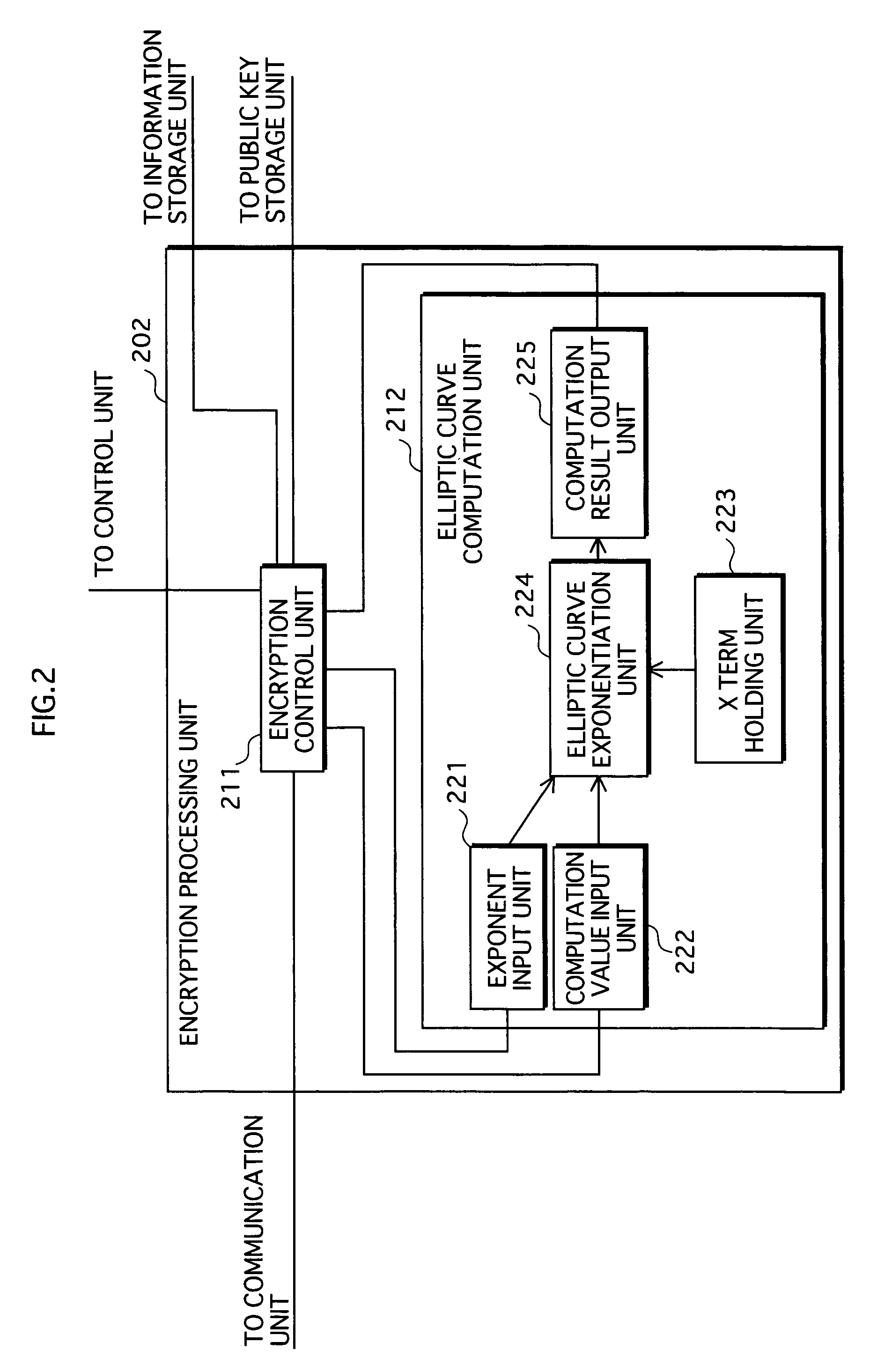
Security chip and attack detection circuit thereof
ActiveCN103034804AImprove the ability to resist fault attacksPrevent leakageCurrent/voltage measurementPlatform integrity maintainanceSecurity MeasureEngineering
The invention discloses an attack detection circuit for a security chip and the security chip of the attack detection circuit. The attack detection circuit comprises a sampling network, a detecting circuit and an output electrode, wherein the sampling network is used for carrying out sampling and filtering treatment on voltage burrs on a power supply and the ground and distinguishing noise signals and vibration on the power supply and the ground from the attack of the voltage burrs; the detecting circuit is used for detecting signals output by the sampling network; and the output electrode is used for treating output signals of the detecting circuit and outputting detecting results. The attack detection circuit is used for detecting the semi-invasion voltage burr attack to which the power supply of the security circuit or the ground is subjected and outputting corresponding detecting results, thus a security chip system can be warned when the power supply of the security chip or the ground is subjected to attack, appropriate security measures can be carried out by the security chip system for preventing potential safety hazards, and the fault attack resisting ability of the security chip system is increased.
Owner:SHENZHEN STATE MICRO TECH CO LTD
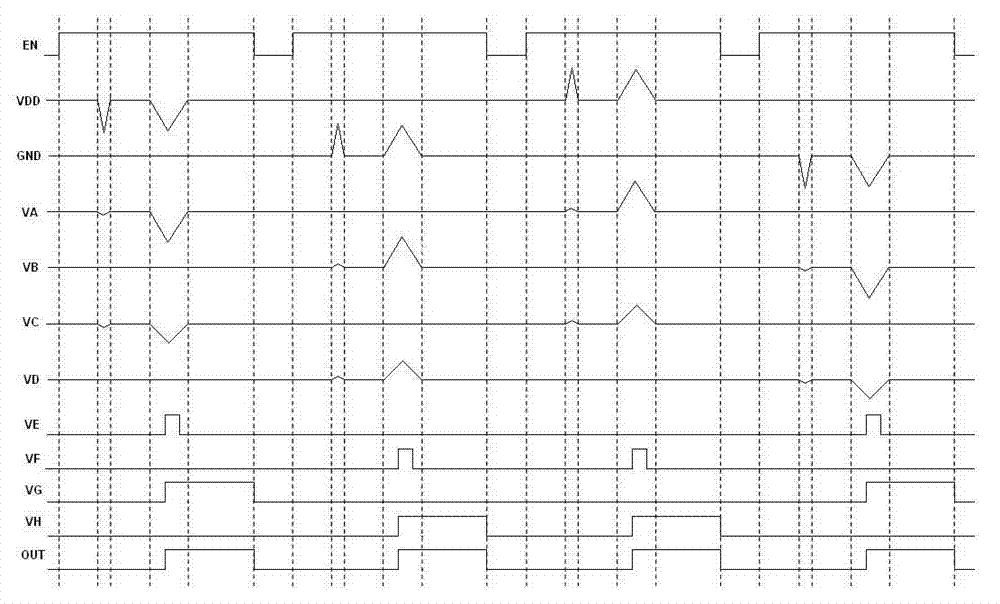
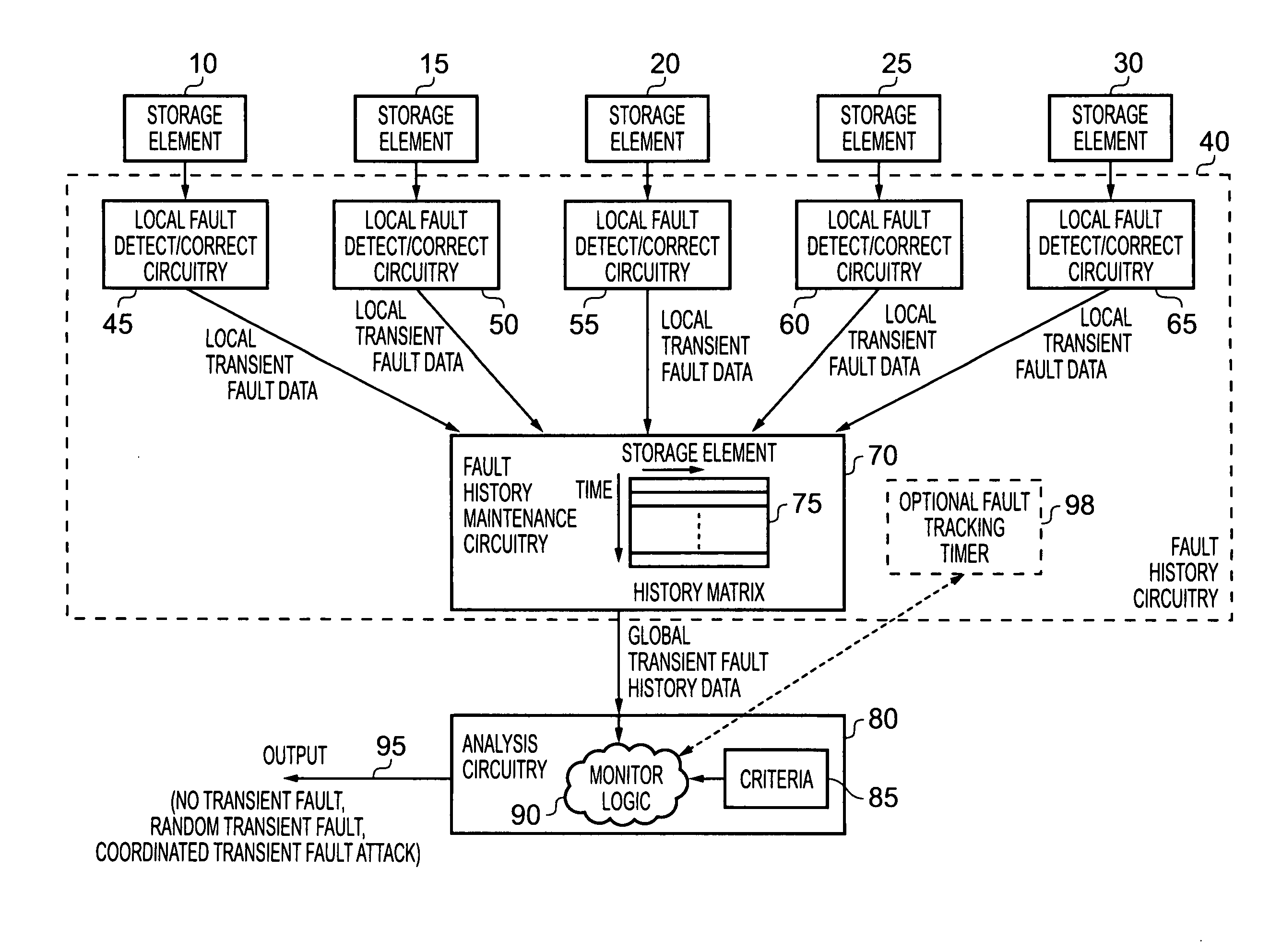
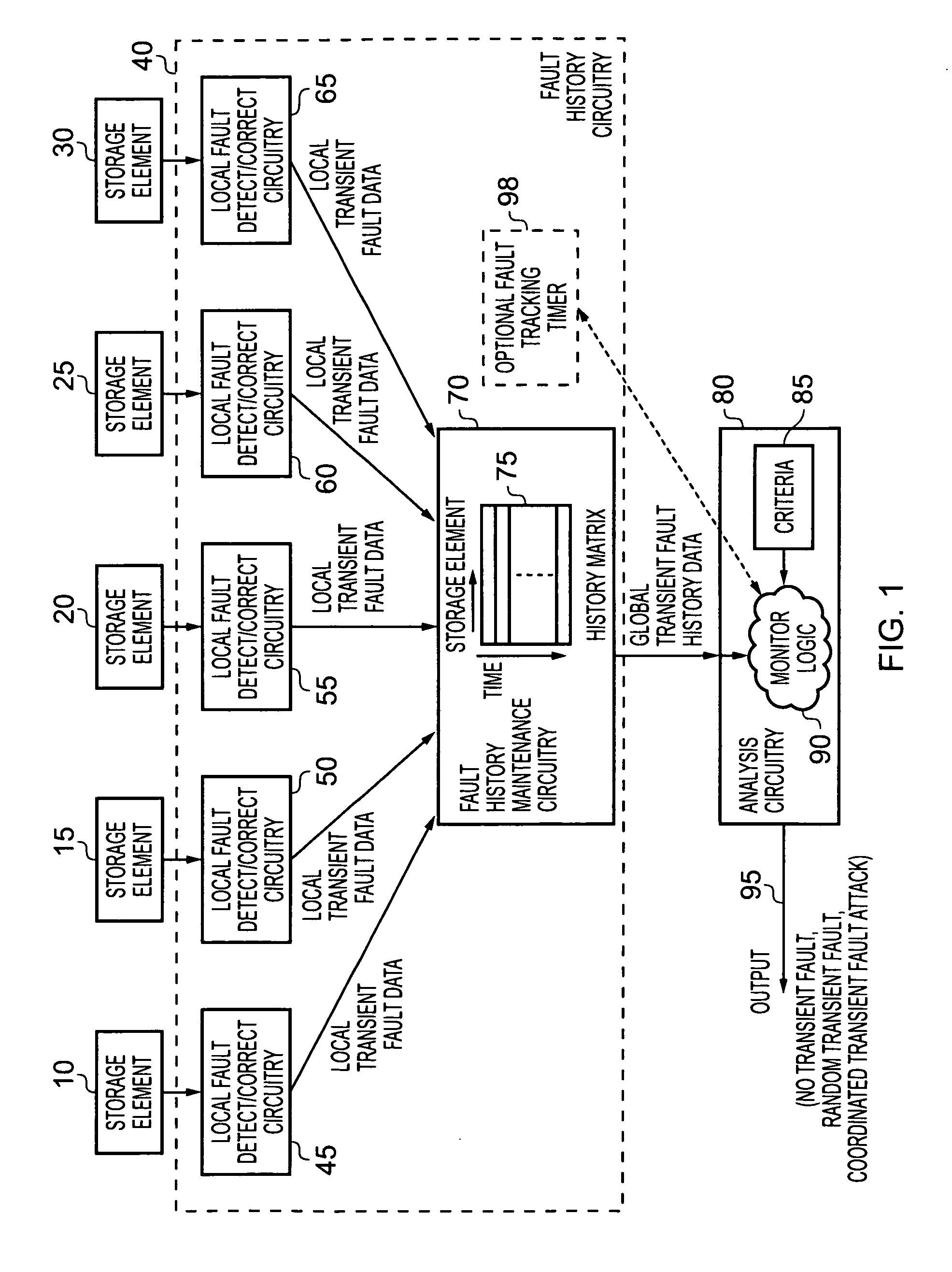
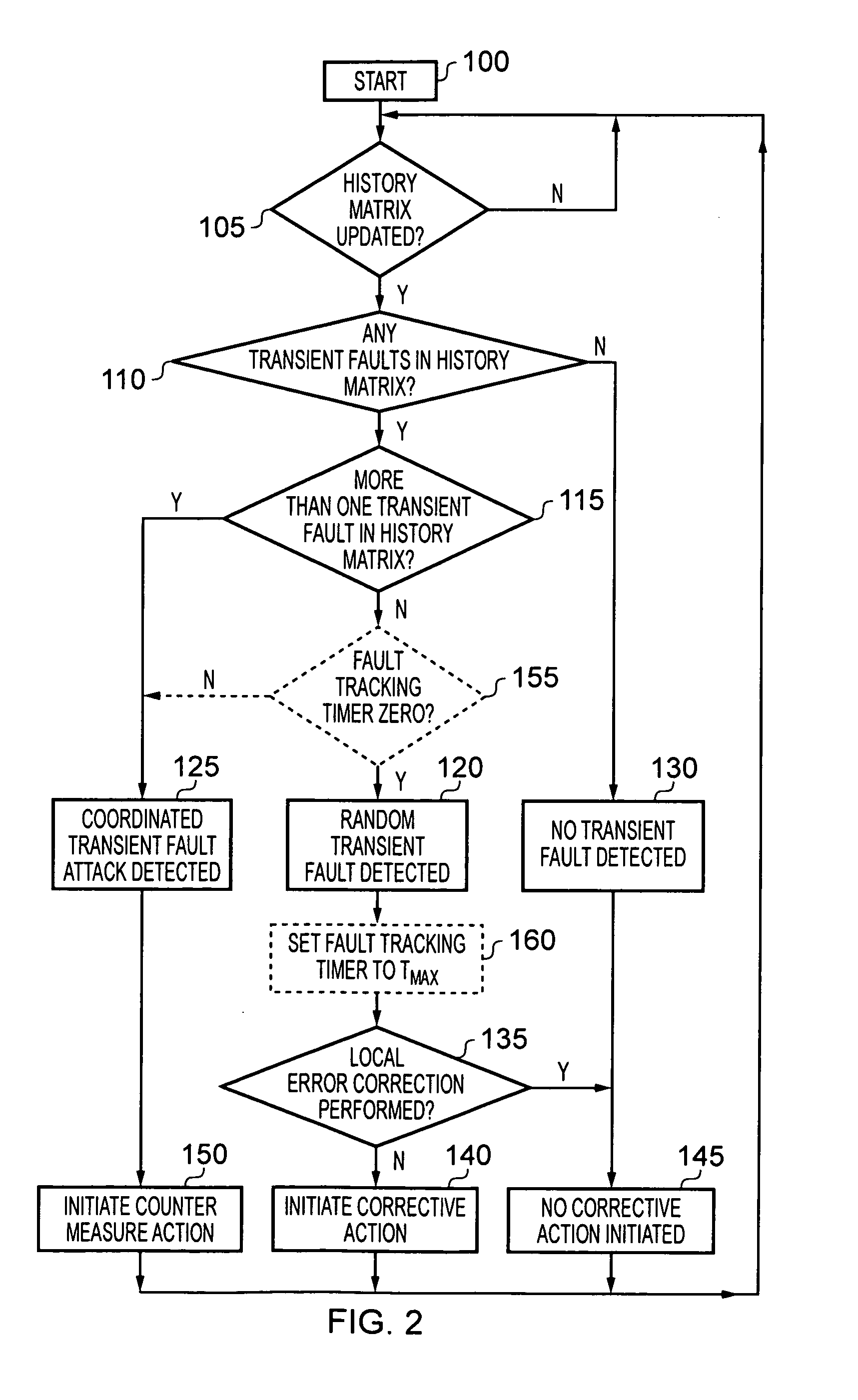
Data processing apparatus and method for analysing transient faults occurring within storage elements of the data processing apparatus
ActiveUS20130103972A1Improve performancePreclude obtainingNon-redundant fault processingCountermeasureComputer science
A data processing apparatus has a plurality of storage elements residing at different physical locations within the apparatus, and fault history circuitry for detecting local transient faults occurring in each storage element, and for maintaining global transient fault history data based on the detected local transient faults. Analysis circuitry monitors the global transient fault history data to determine, based on predetermined criteria, whether the global transient fault history data is indicative of random transient faults occurring within the data processing apparatus, or is indicative of a coordinated transient fault attack. The analysis circuitry is then configured to initiate a countermeasure action on determination of a coordinated transient fault attack. This provides a simple and effective mechanism for distinguishing between random transient faults that may naturally occur, and a coordinated transient fault attack that may be initiated in an attempt to circumvent the security of the data processing apparatus.
Owner:ARM LTD
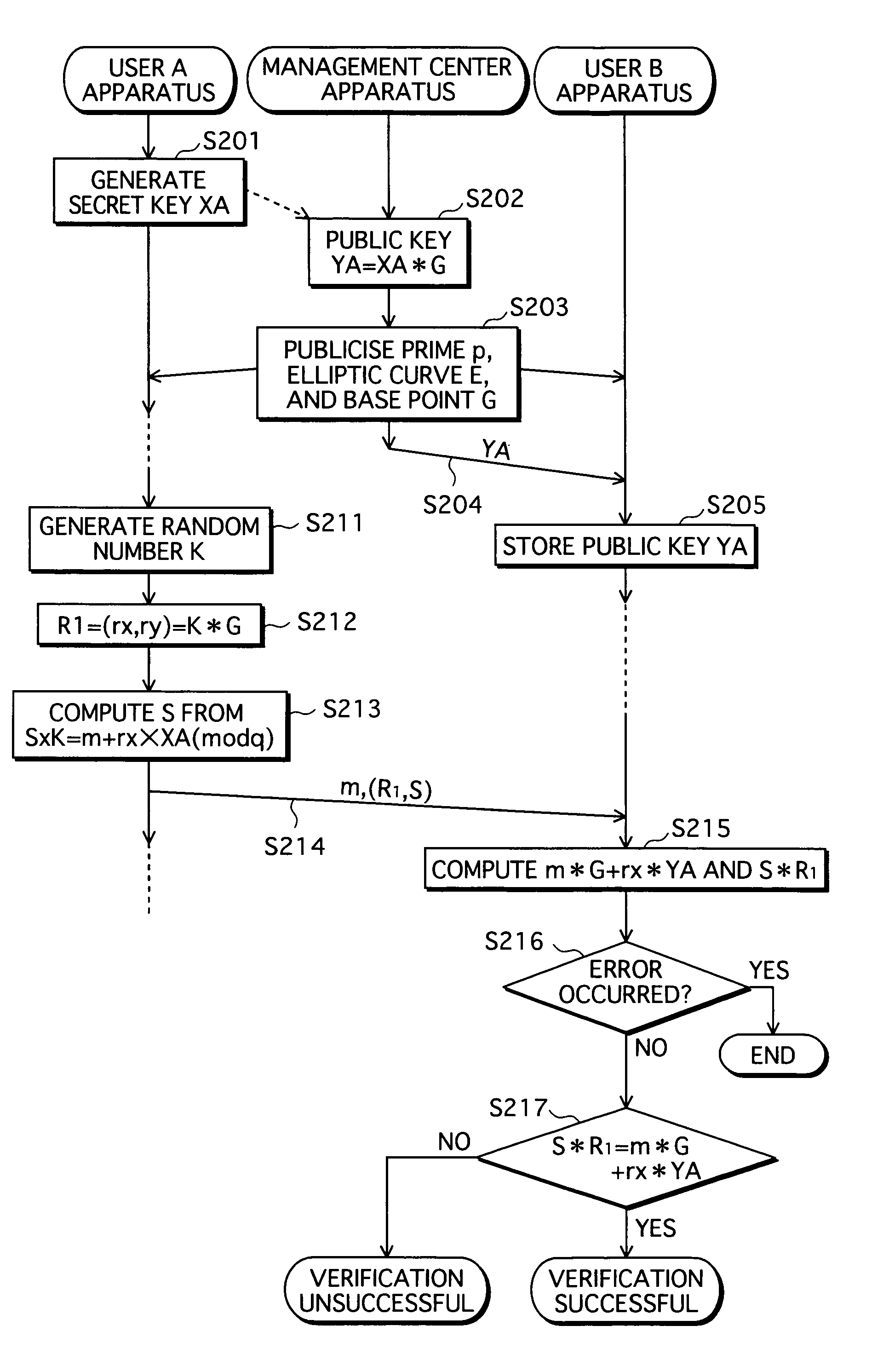
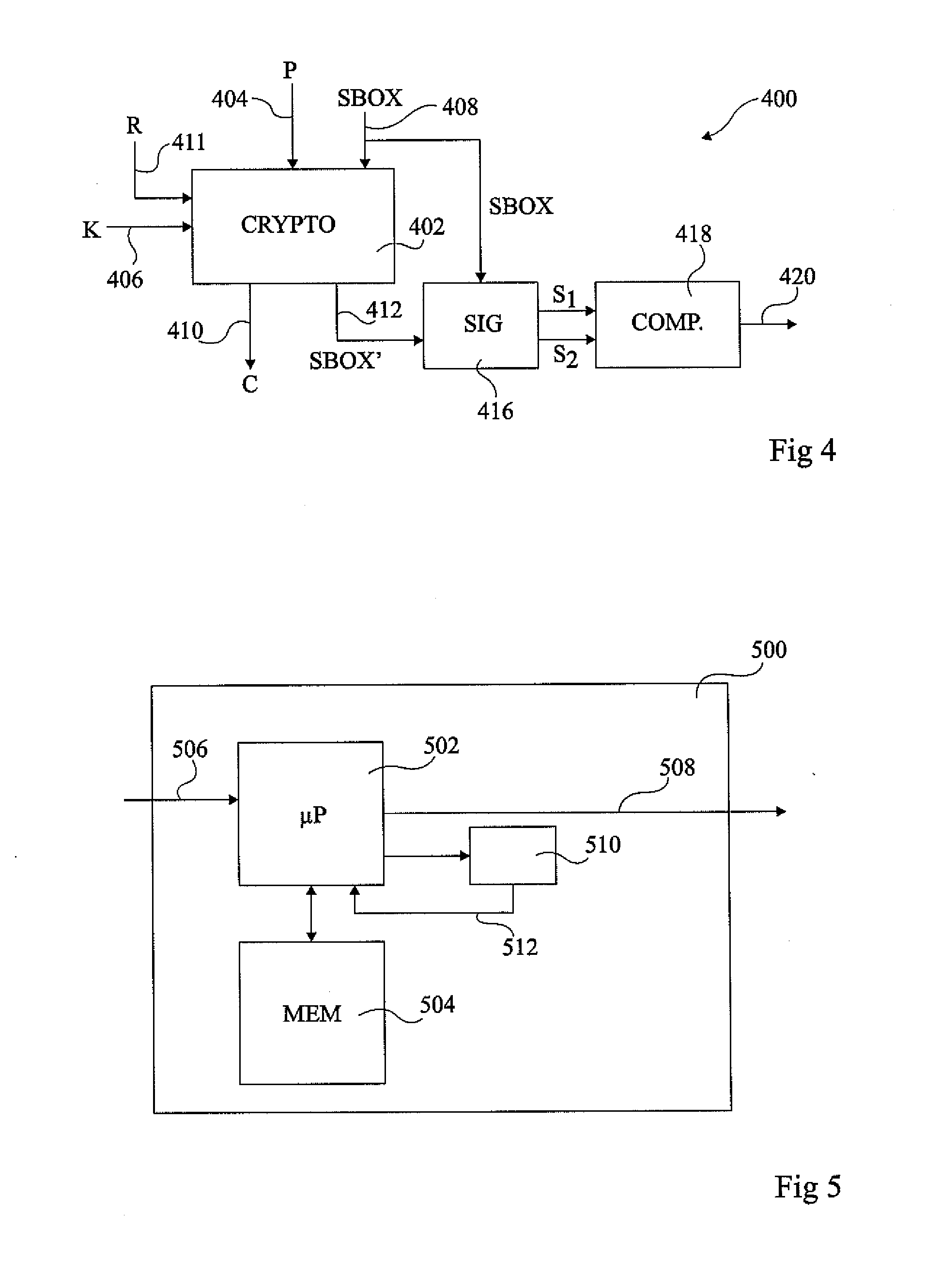
RSA public key generation apparatus, RSA decryption apparatus, and RSA signature apparatus
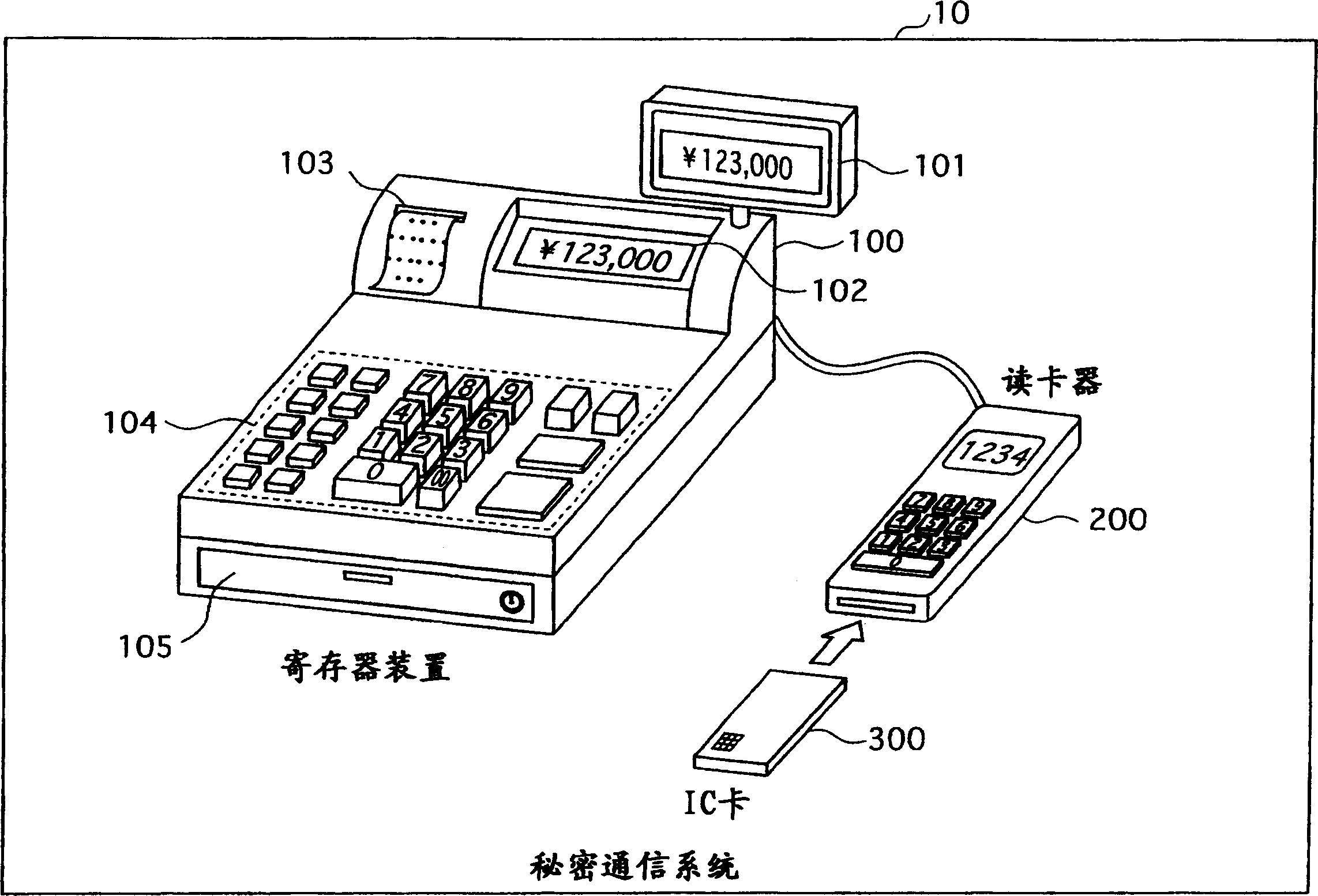
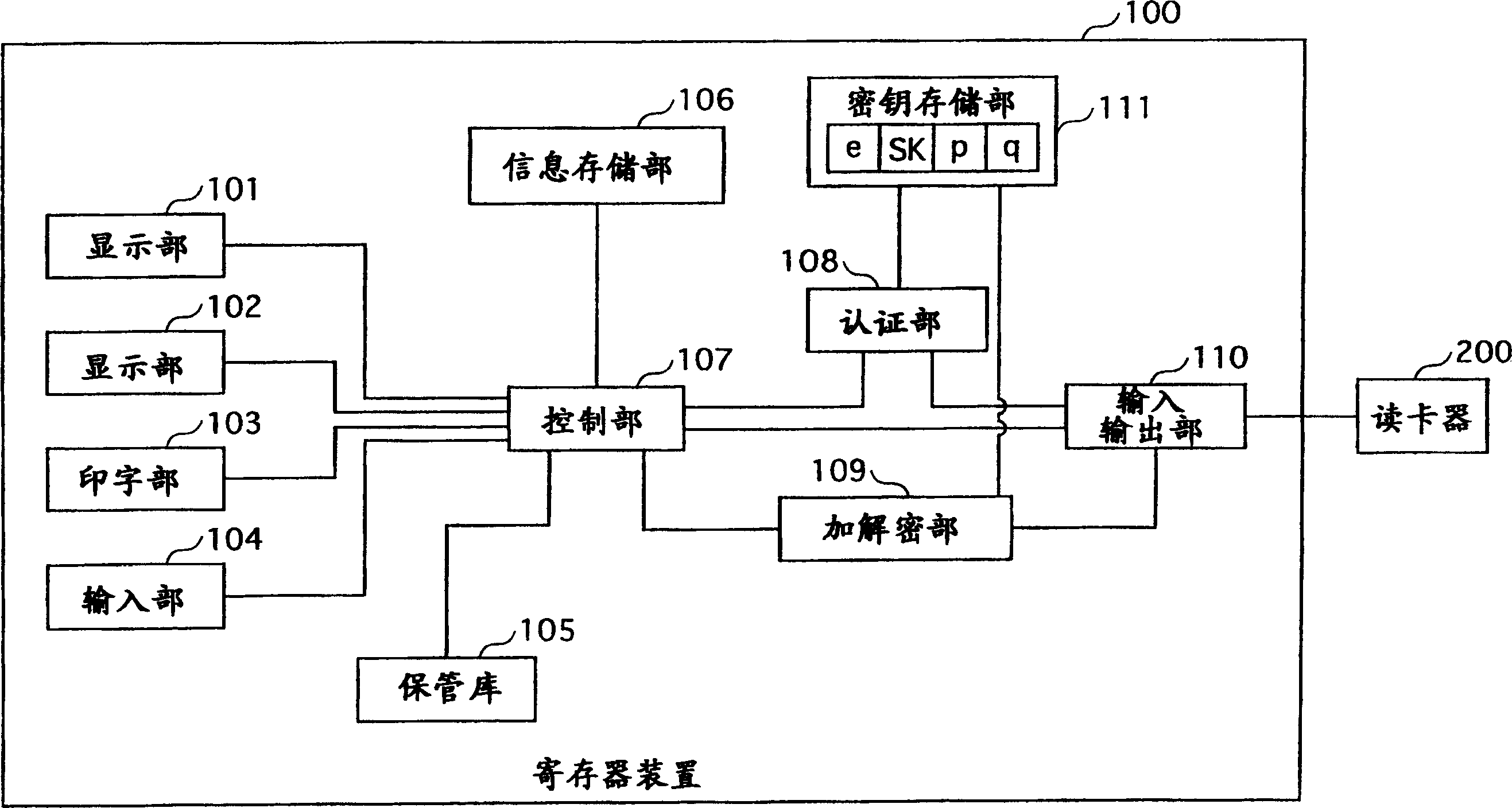
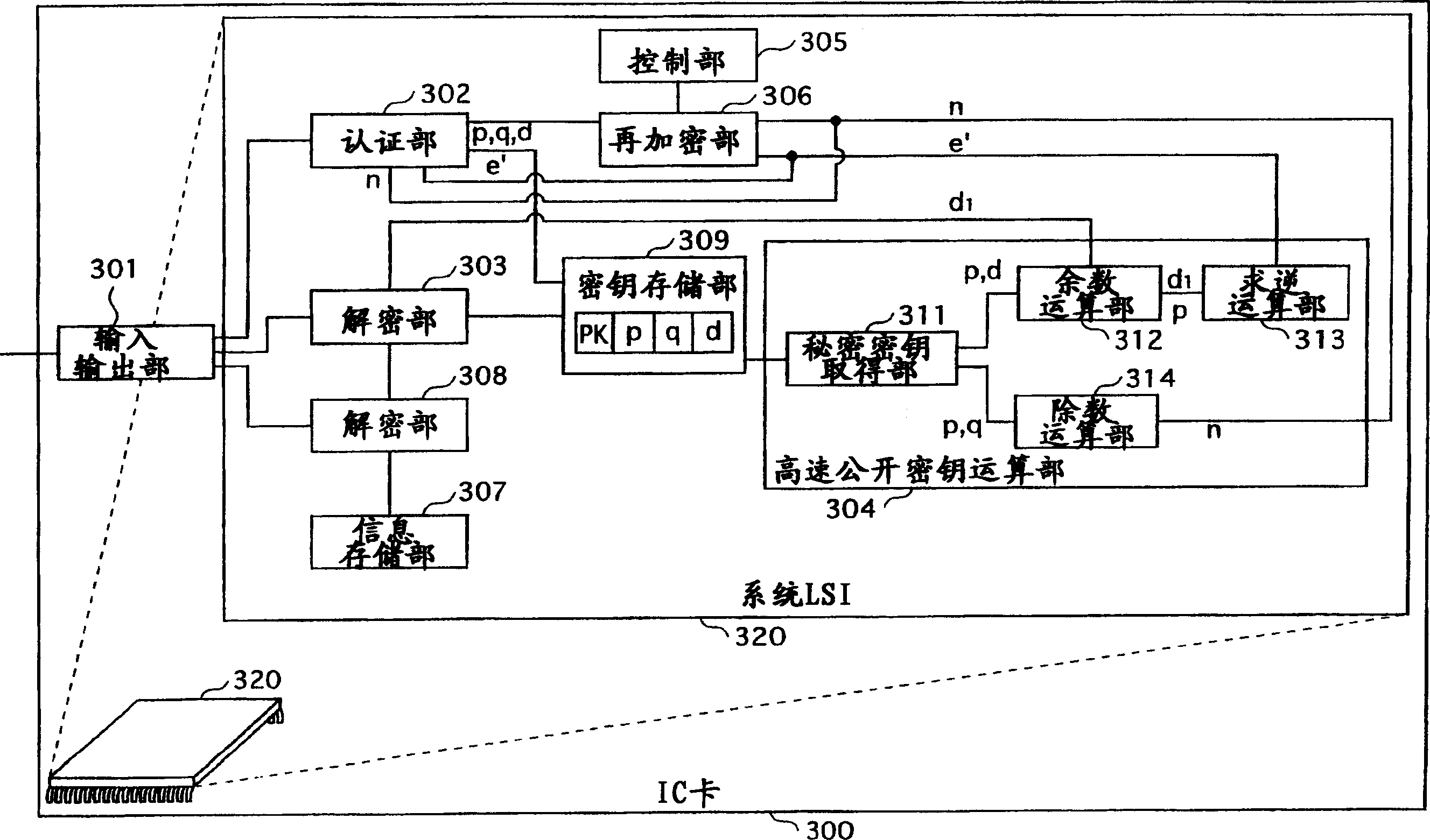
InactiveUS20050157872A1Increase speedPublic key for secure communicationUser identity/authority verificationComputer hardwareSource Data Verification
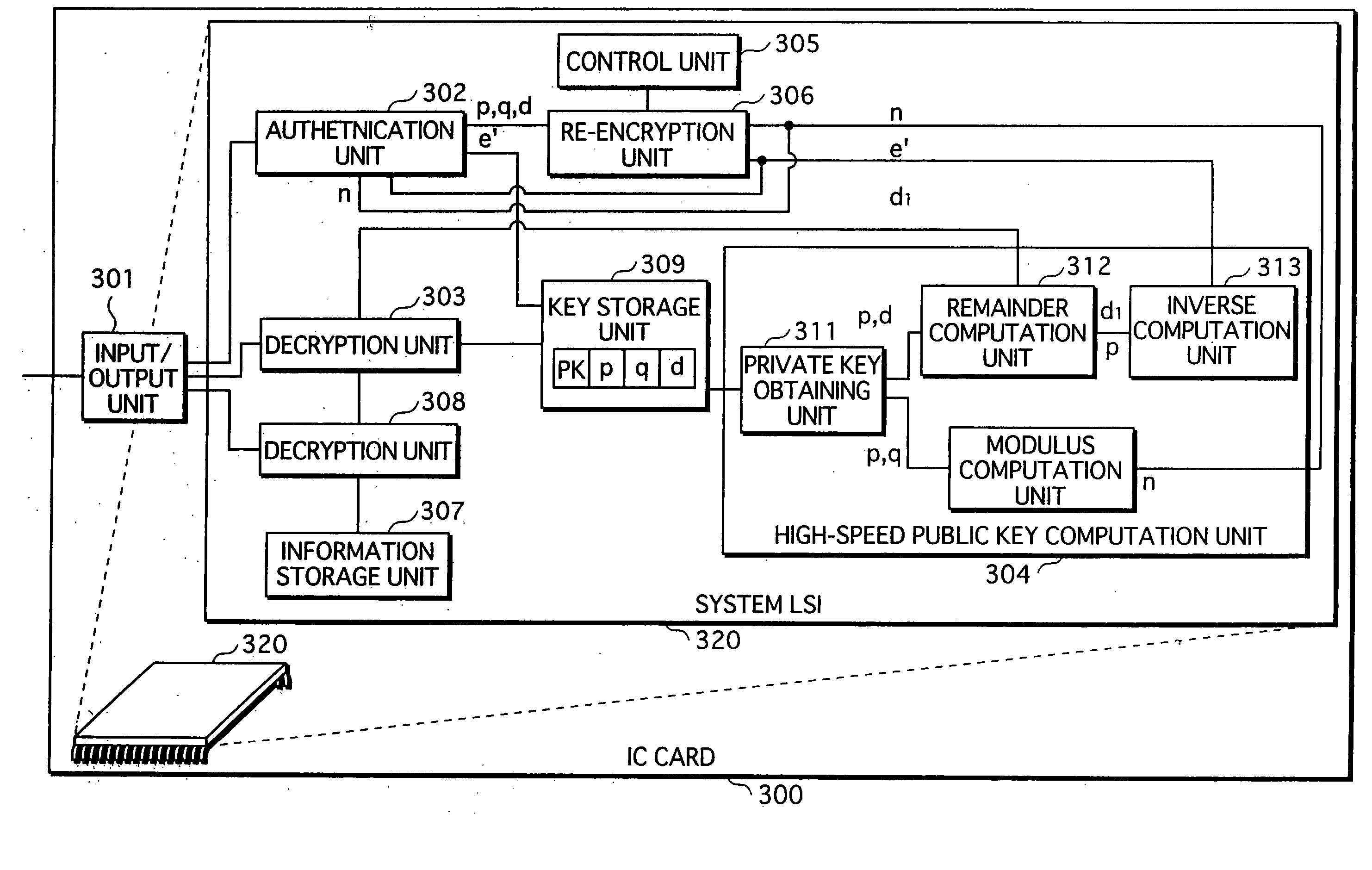
An RSA decryption apparatus that is used in an IC card or the like counters a differential fault attack. The RSA decryption apparatus computes at high speed a public key used in data verification, without having to obtain the public key from an external source. The RSA decryption apparatus includes a remainder computation unit 412 that calculates dp=d mod (p−1), and an inverse computation unit 414 that finds an inverse of dp over a residue field with p−1 as a modulus. The RSA decryption apparatus verifies a decipher text with use of the inverse of dp as the public key. The reduced bit count in inverse computation compared to if the inverse of d is found as the public key increases computing speed.
Owner:PANASONIC CORP
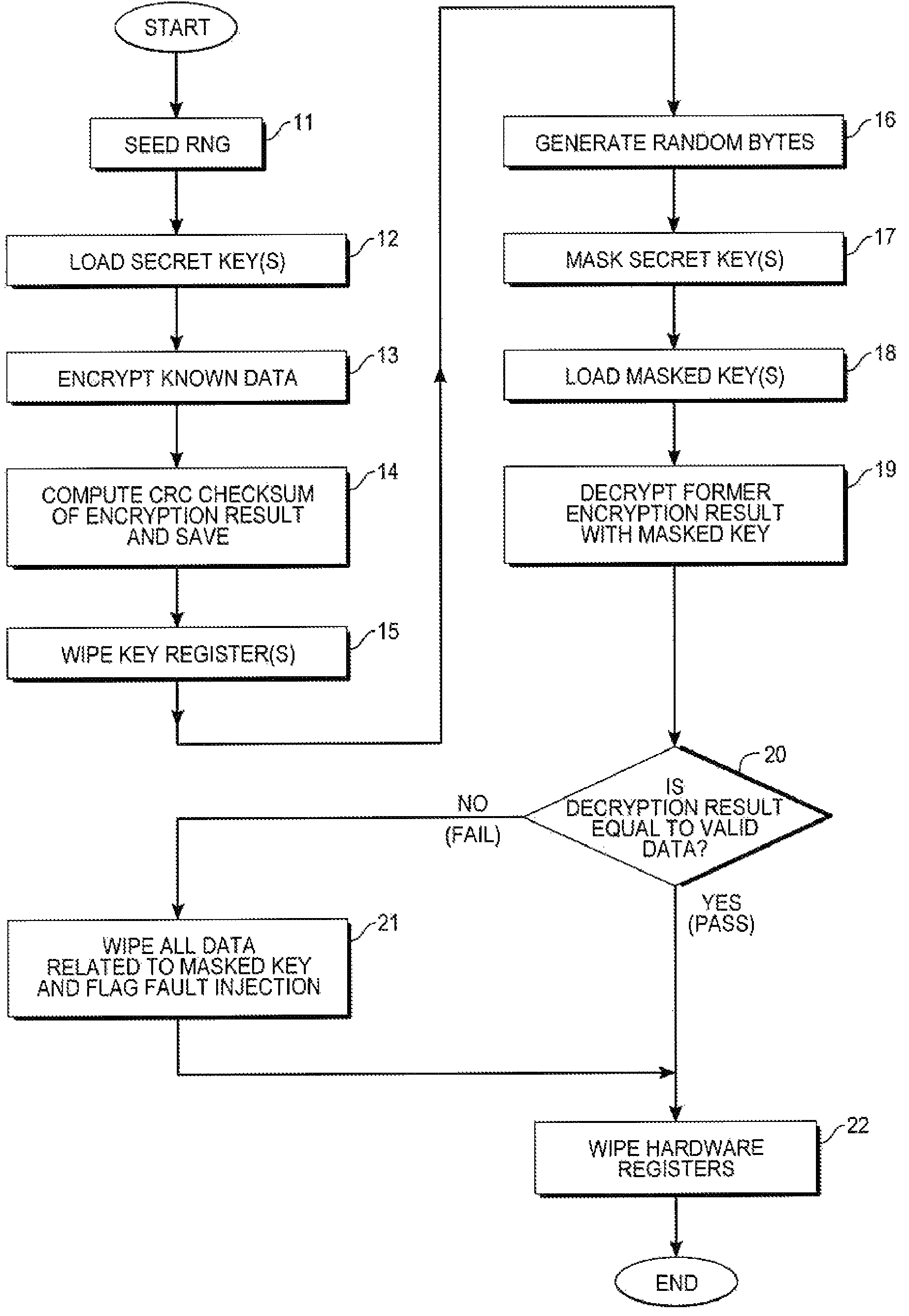
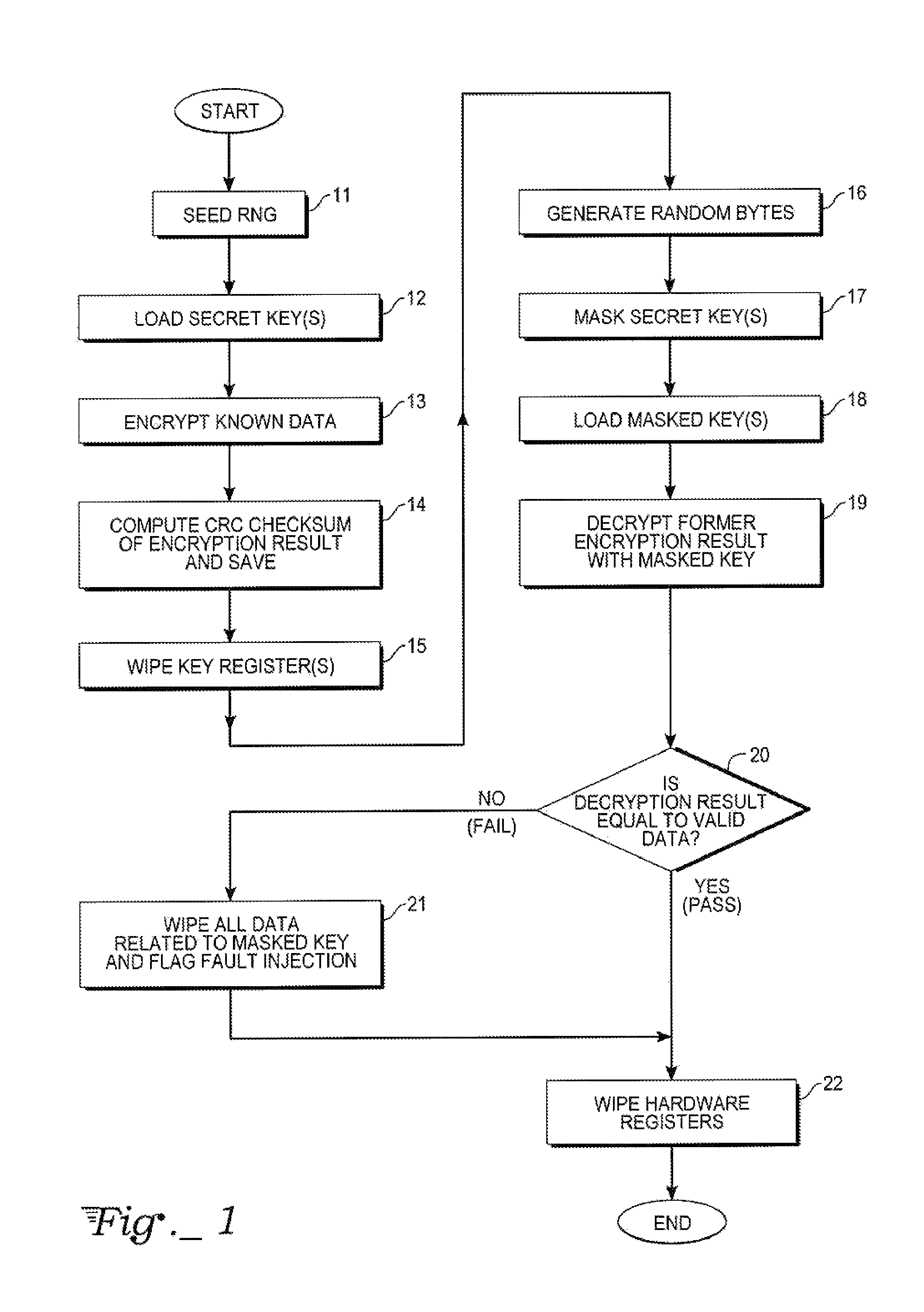
Key protection mechanism
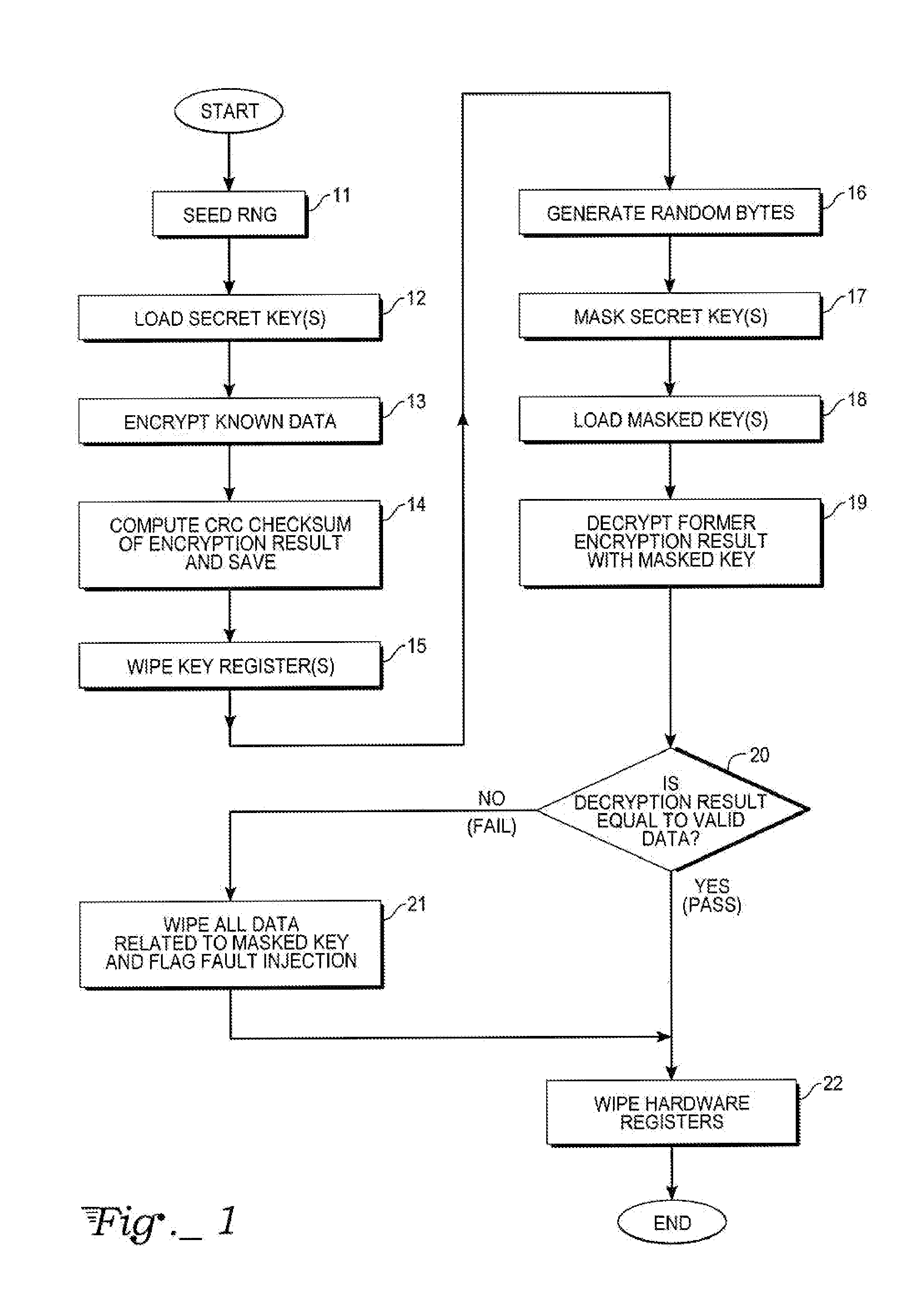
InactiveUS20080152144A1Memory loss protectionVolume/mass flow measurementProtection mechanismChecksum
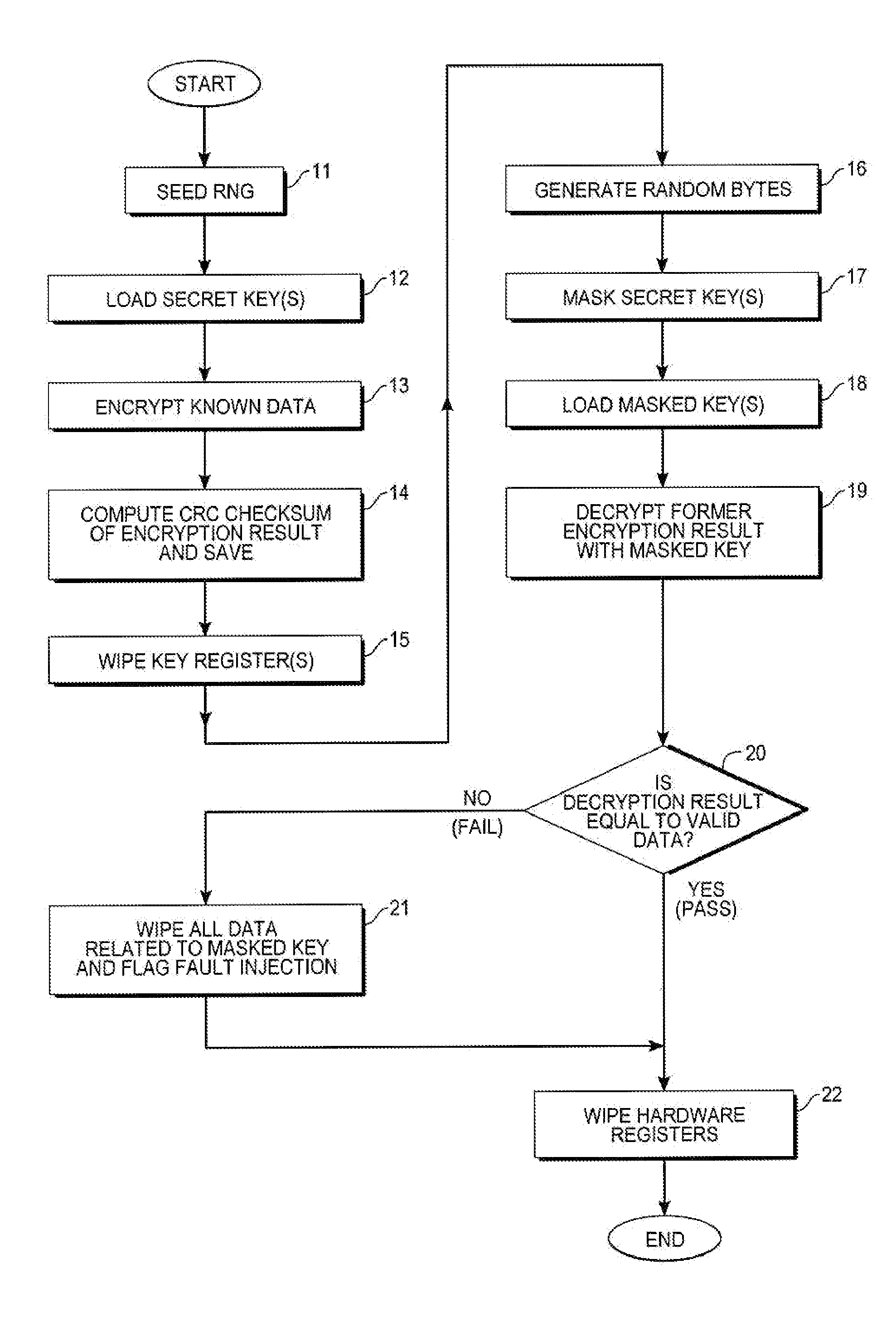
A method of protecting secret key integrity in a hardware cryptographic system includes first obtaining an encryption result and corresponding checksum of known data using the secret key, saving those results, then masking the secret key and storing the masked key. When the masked key is to be used in a cryptographic application, the method checks key integrity against fault attacks by decrypting the prior encryption results using the masked key. If upon comparison, the decryption result equals valid data, then the key's use in the cryptographic system can proceed. Otherwise, all data relating to the masked key is wiped from the system and fault injection is flagged.
Owner:RAMBUS INC
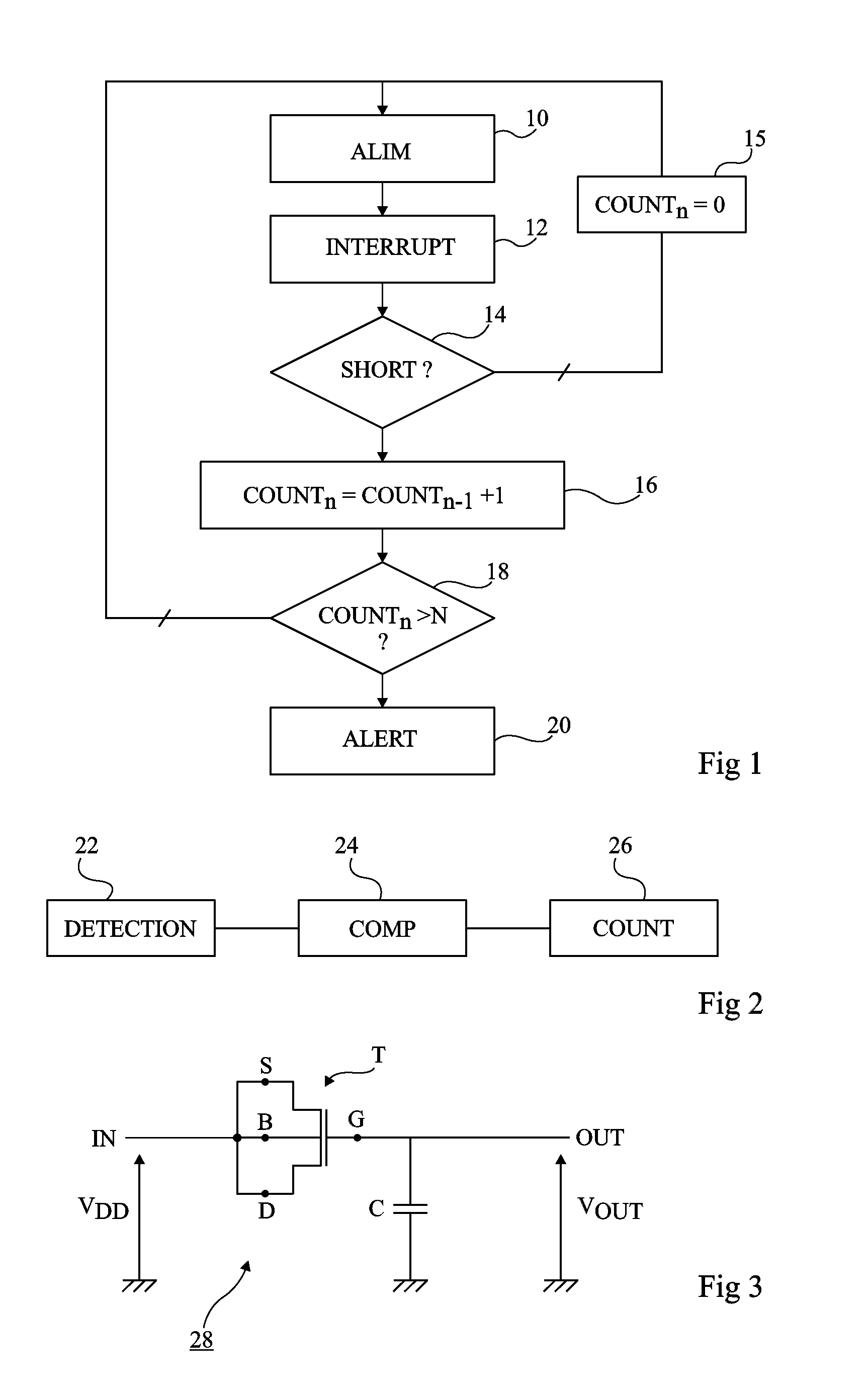
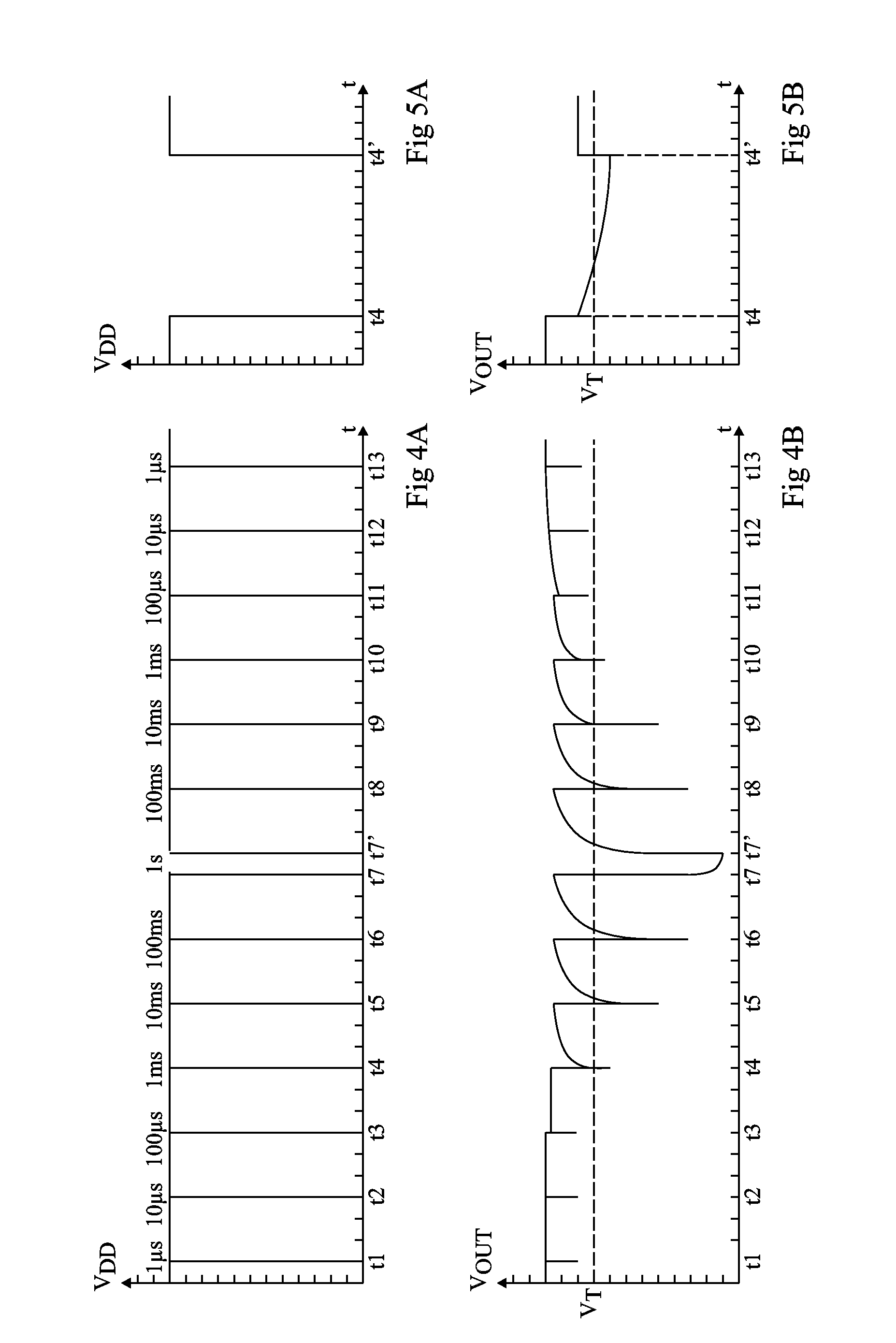
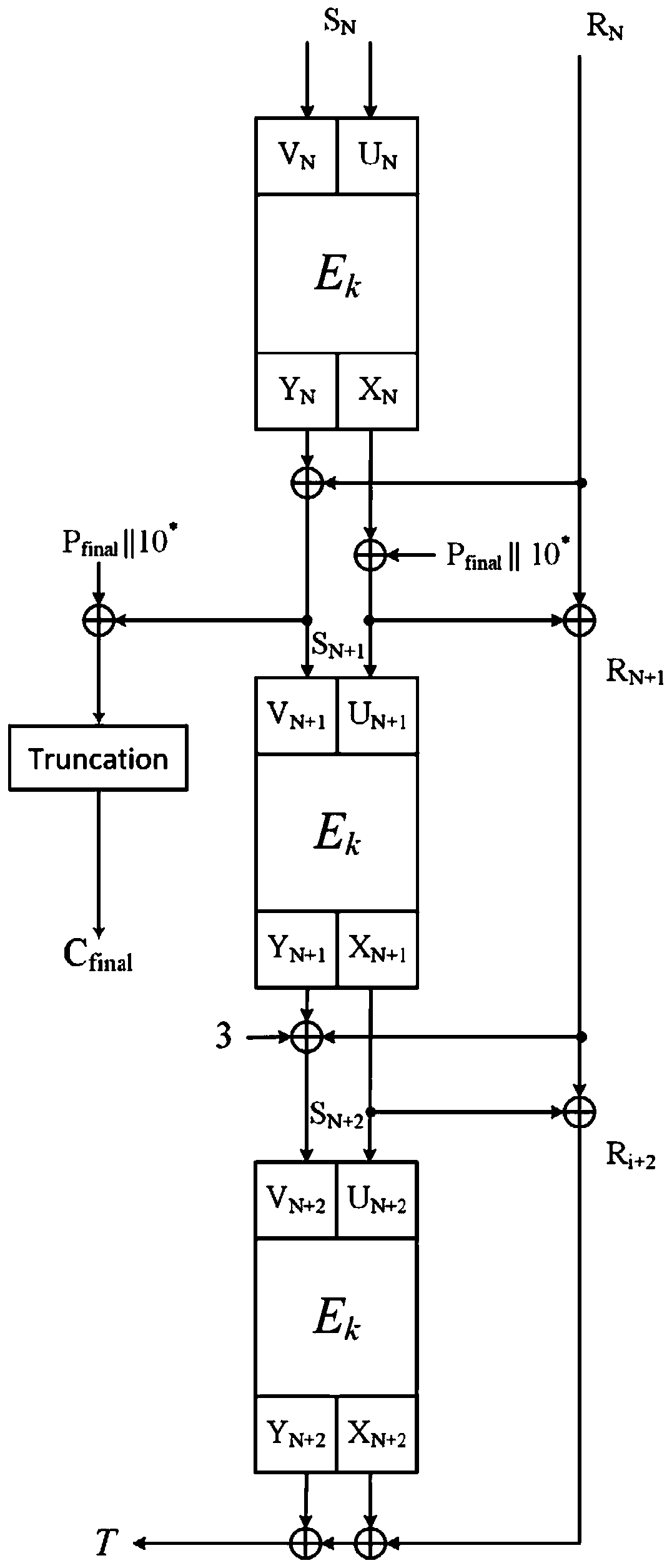
Method of detecting fault attack
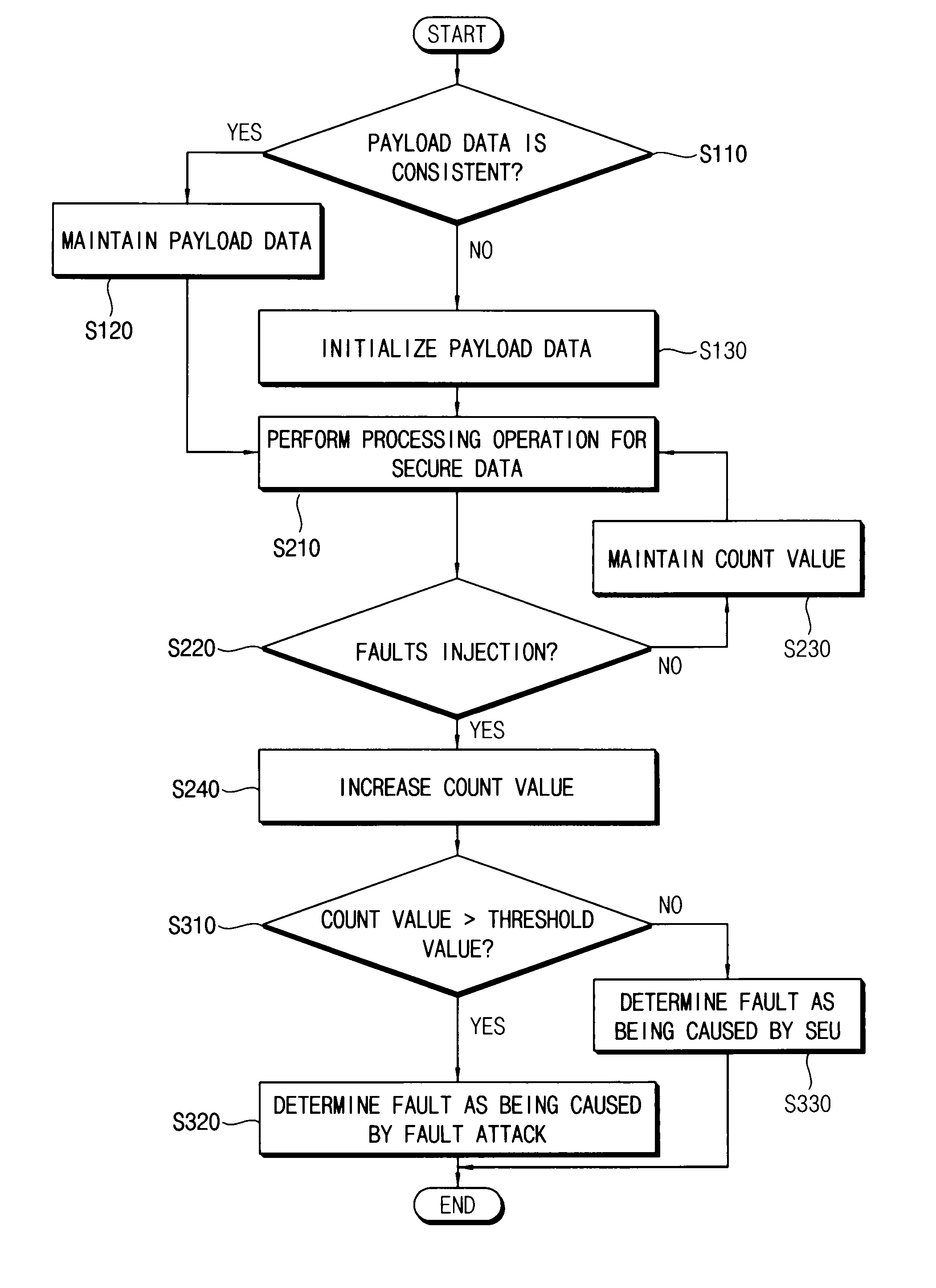
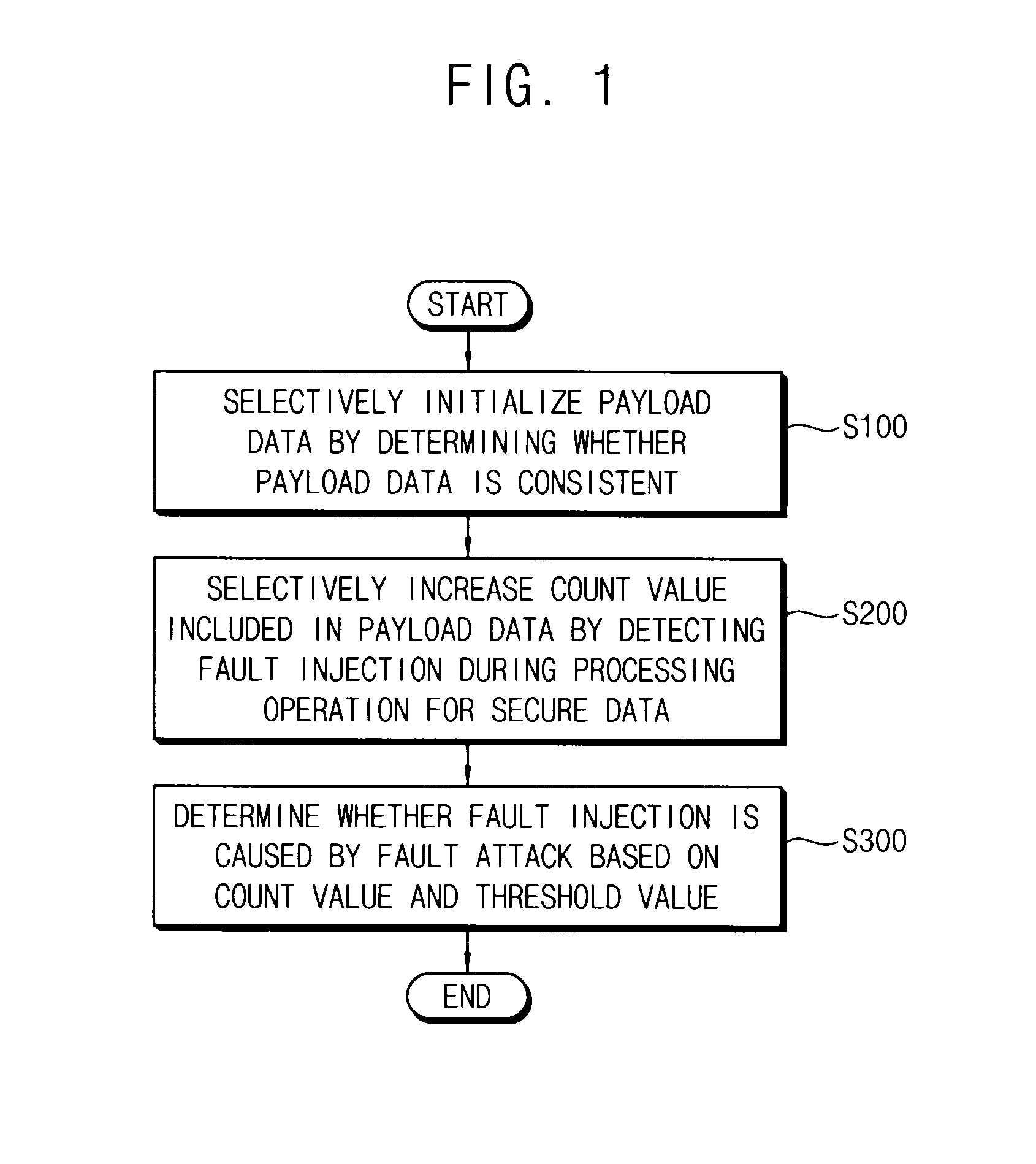
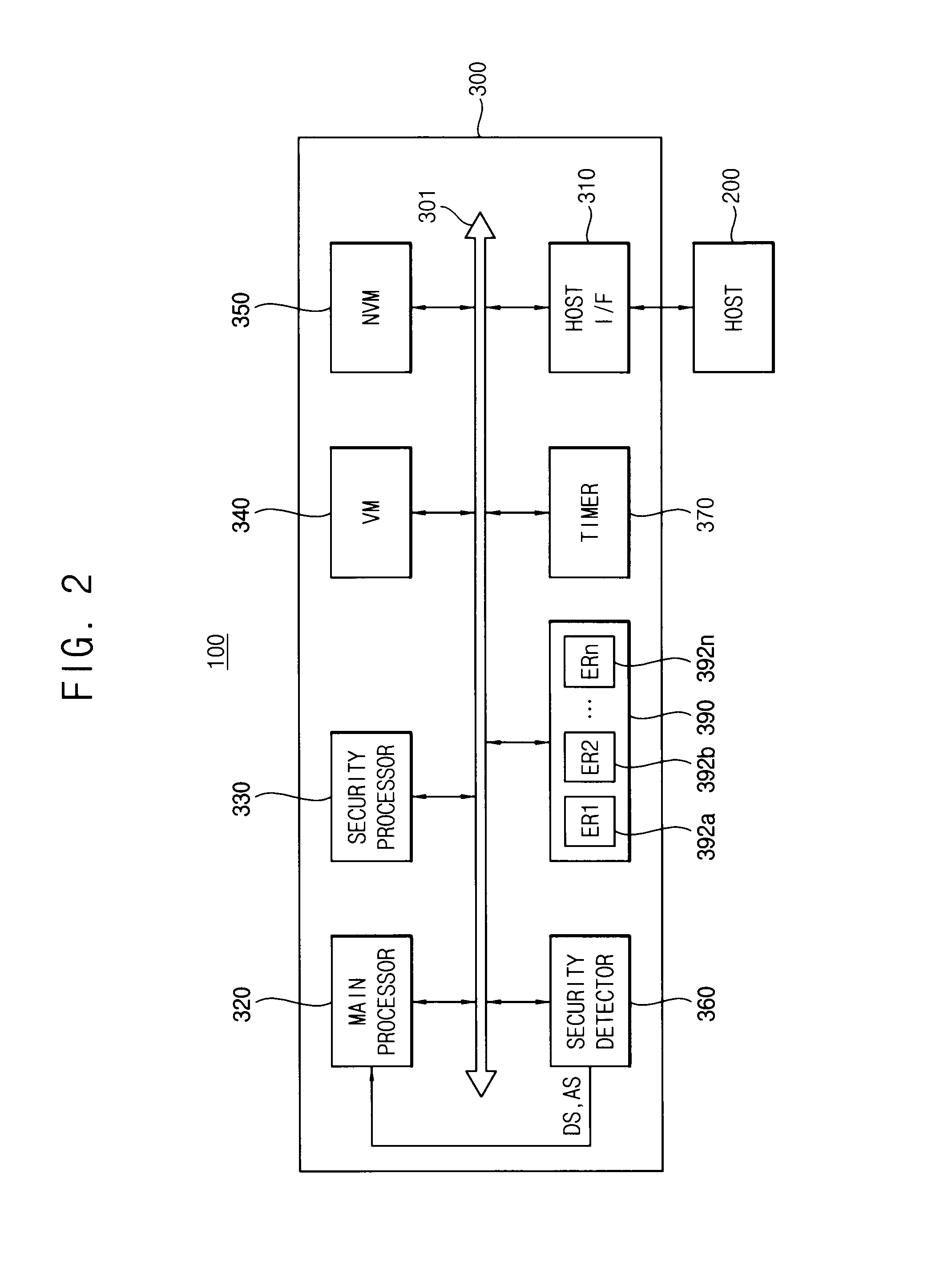
ActiveUS20140020097A1Effective distinctionMemory loss protectionUnauthorized memory use protectionComputer hardwareInit
In a method of detecting a fault attack in a secure memory device, payload data is initialized by determining whether the payload data is consistent. The payload data is stored in a plurality of ephemeral registers included in the secure memory device. A count value included in the payload data is increased by detecting whether a fault is injected in the secure memory device from outside, during a processing operation of secure data, stored in the secure memory device. It is determined whether the fault injected in the secure memory device from the outside is caused by the fault attack based on the count value and a threshold value.
Owner:SAMSUNG ELECTRONICS CO LTD
Method and circuitry for detecting a fault attack
A method of detecting a fault attack during a cryptographic operation using at least one look-up table including a plurality of sub-tables each having a same number of values of a fixed bit length, a fixed relation existing between values at same locations in each sub-table, the method including: performing a load operation to retrieve from the look-up table data values from a same location in each sub-table; verifying that the fixed relation exists between at least two of the data values; and generating an output signal based on the verification.
Owner:STMICROELECTRONICS (ROUSSET) SAS
Method for secure data reading and data handling system
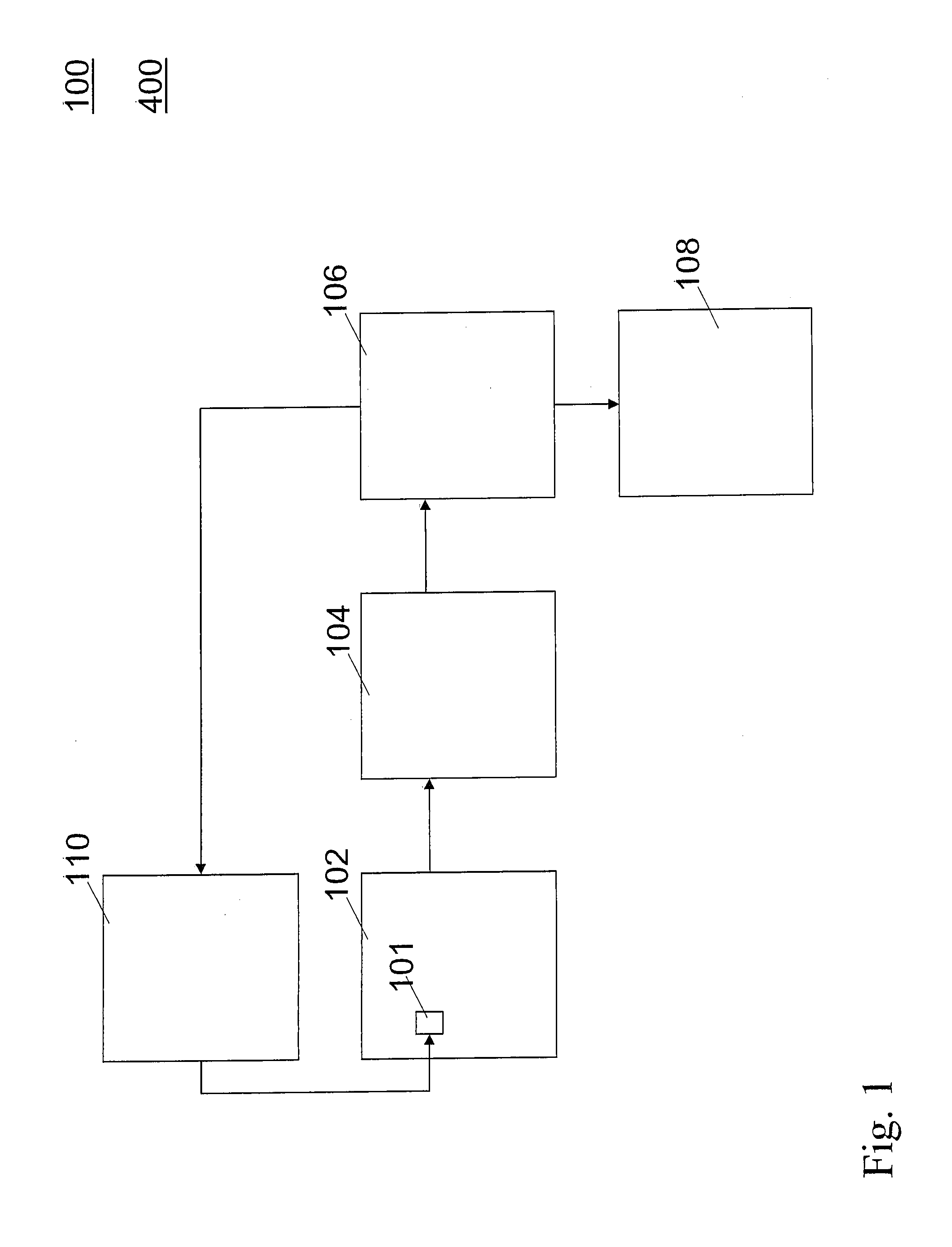
ActiveUS20110072222A1Easy to detectConvenient teachingDigital computer detailsInternal/peripheral component protectionData processing systemHandling system
A method for secure data reading and a data handling system is provided. The method protects the data reading from fault attacks by repeating read request in an interleaved manner, in particular the method comprises the steps of (M200) dispatching a first read request; (M400) dispatching a second read request; (M600) dispatching a further first read request; and (M1000-a) producing an anomaly signal if a first result produced by the memory in response to the first read request does not agree with a further first result produced by the memory in response to the further first read request.
Owner:NXP BV
Method and apparatus for detection of a fault attack
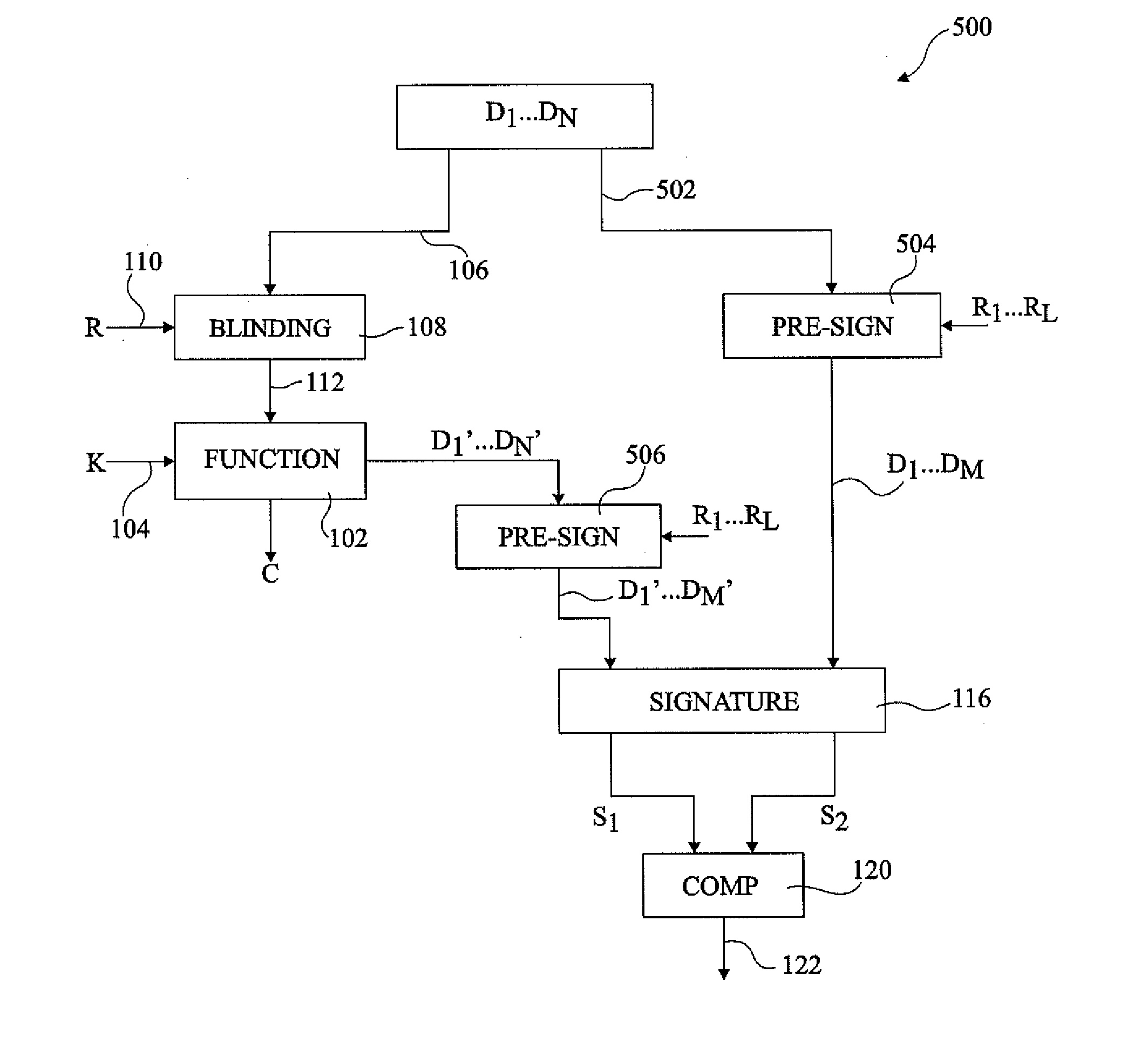
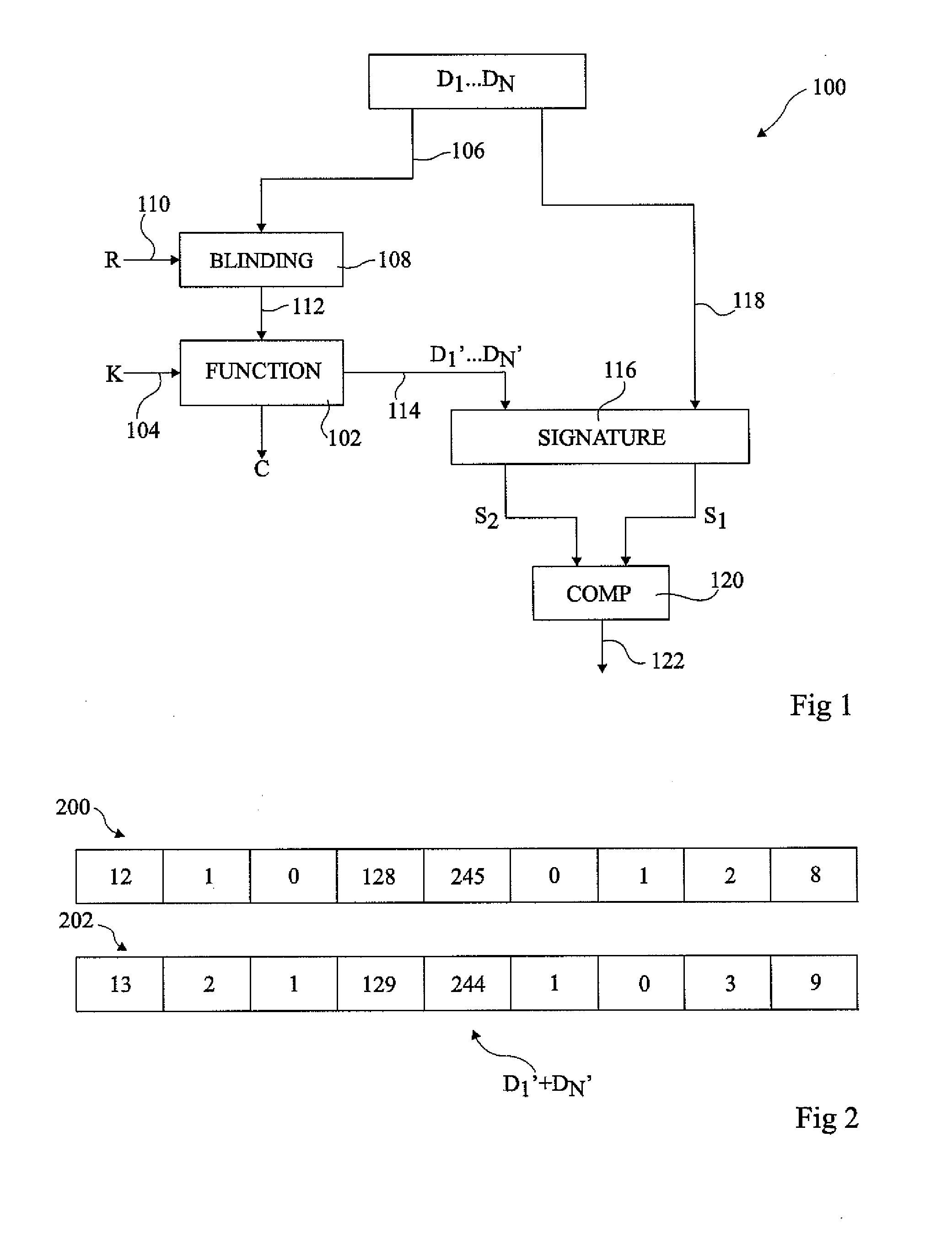
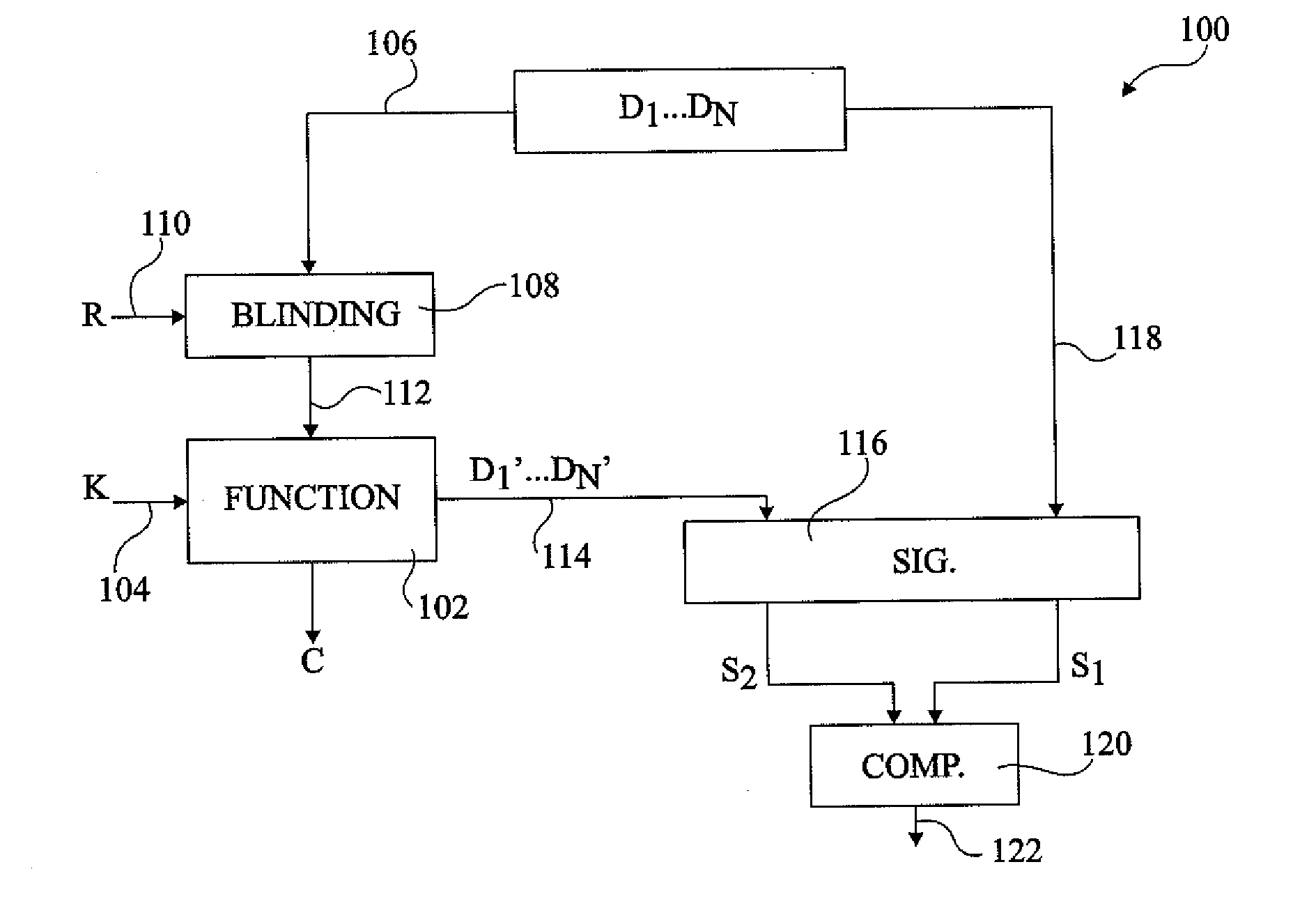
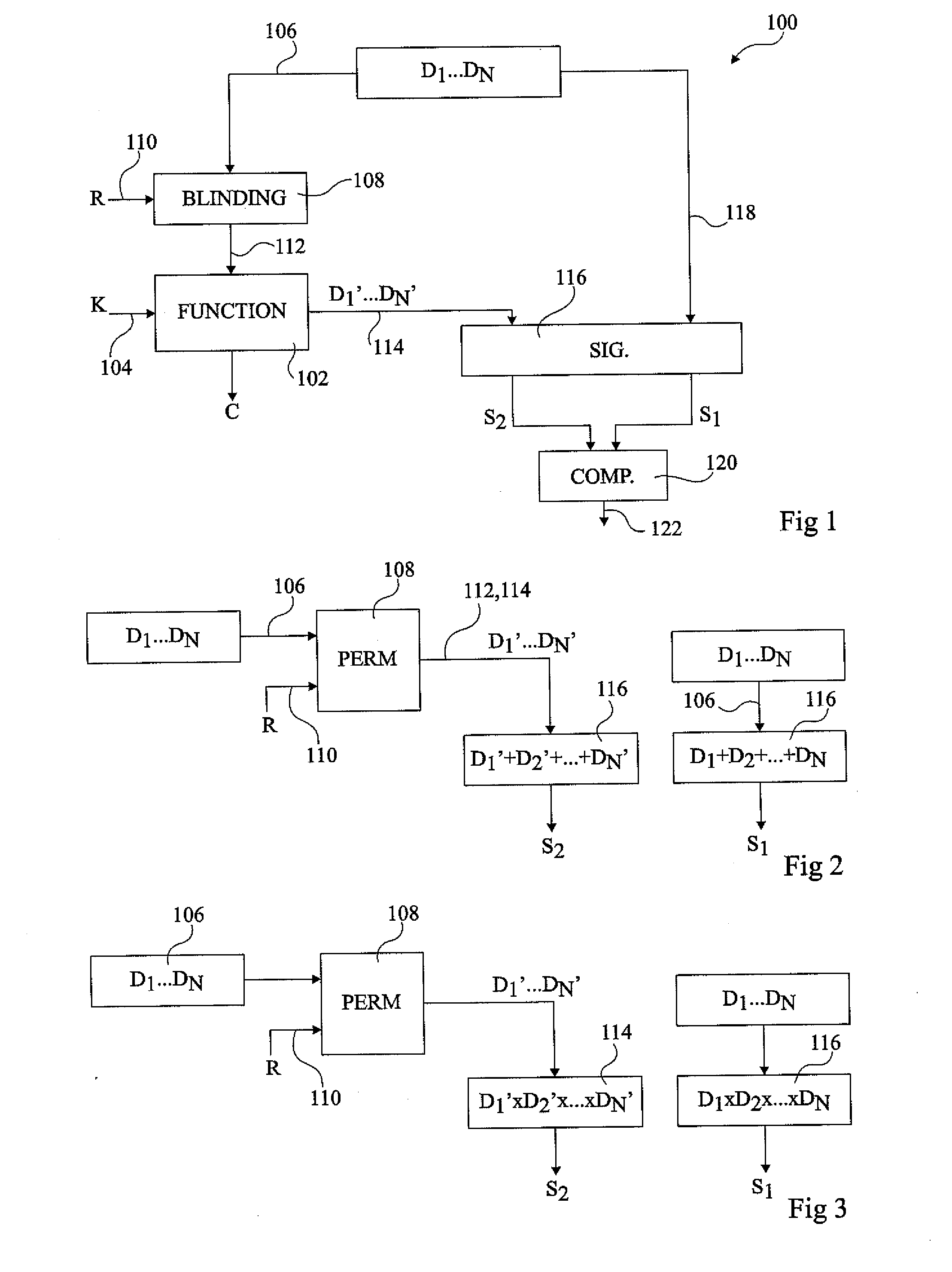
ActiveUS20110119762A1Problem be addressMemory loss protectionError detection/correctionExclusive orData element
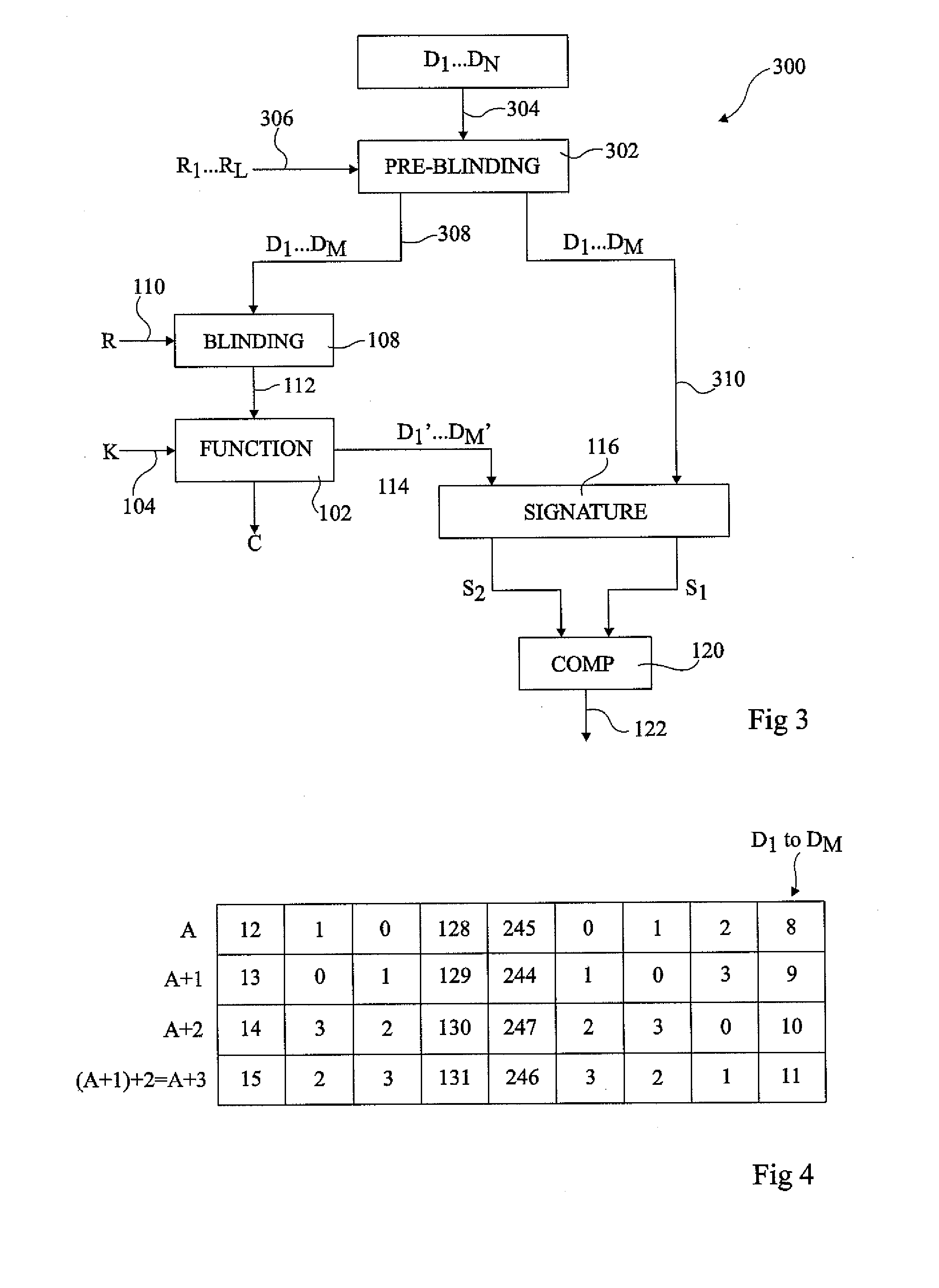
The invention concerns a method of detecting a fault attack including providing a plurality of blinding values; generating a first set of data elements including a first group of data elements and at least one additional data element generated by performing the exclusive OR between at least one data element in the first group and at least one of the blinding values; generating a second set of data elements corresponding to the exclusive OR between each data element of the first set and a selected one of the plurality of blinding values; generating a first signature by performing a commutative operation between each of the data elements of the first set; generating a second signature by performing the commutative operation between each of the data elements of the second set; and comparing the first and second signatures to detect a fault attack.
Owner:STMICROELECTRONICS (ROUSSET) SAS
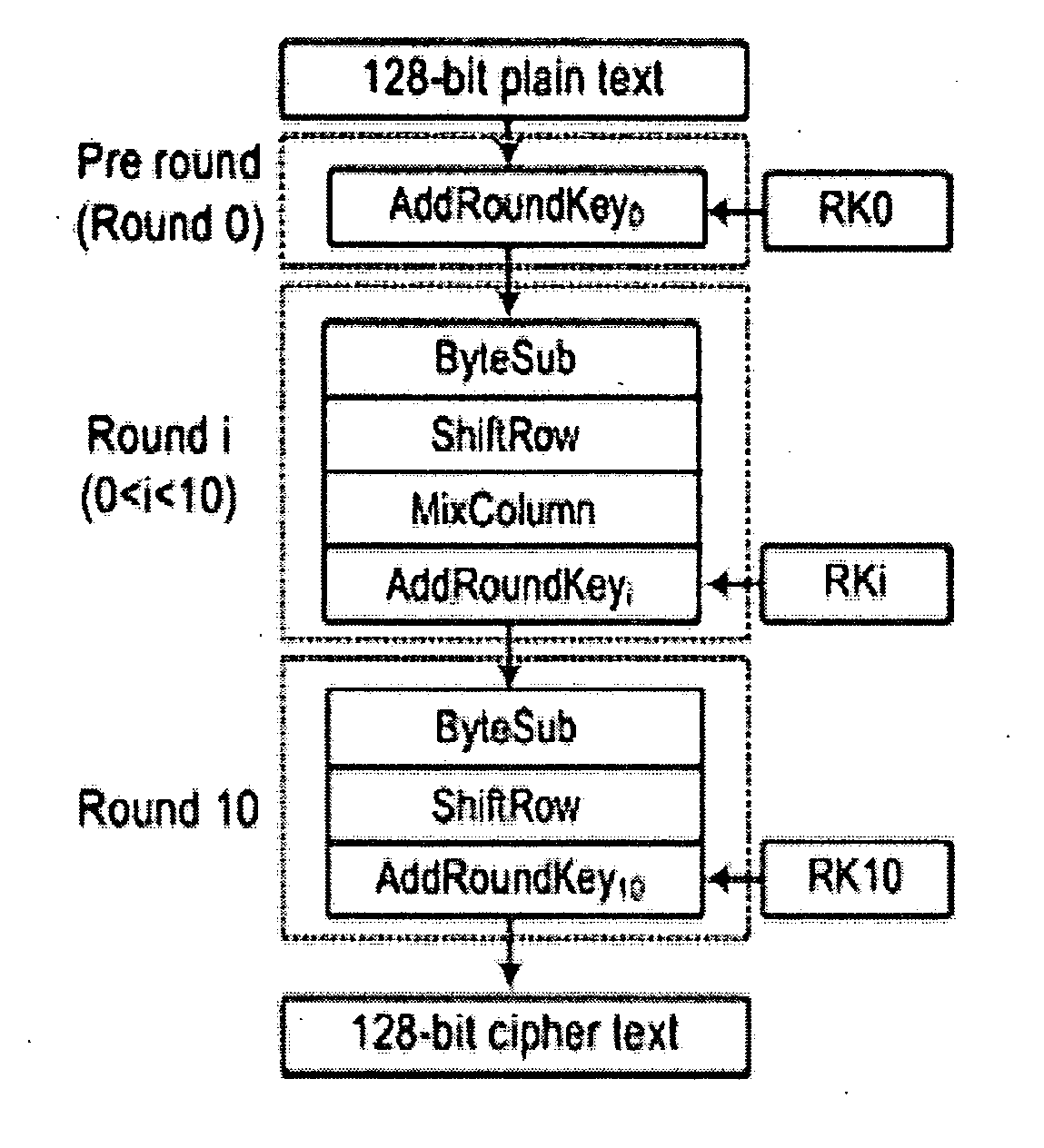
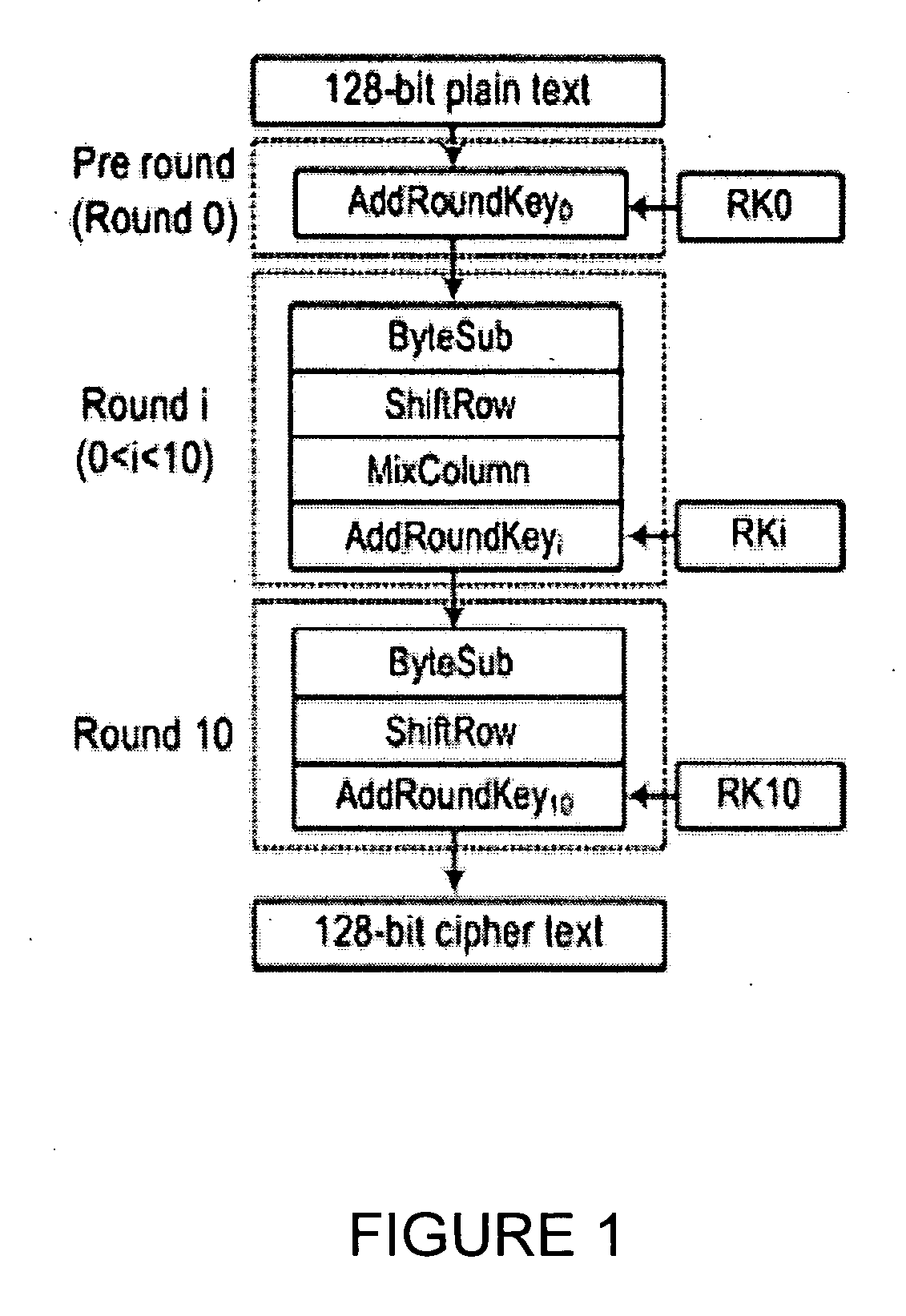
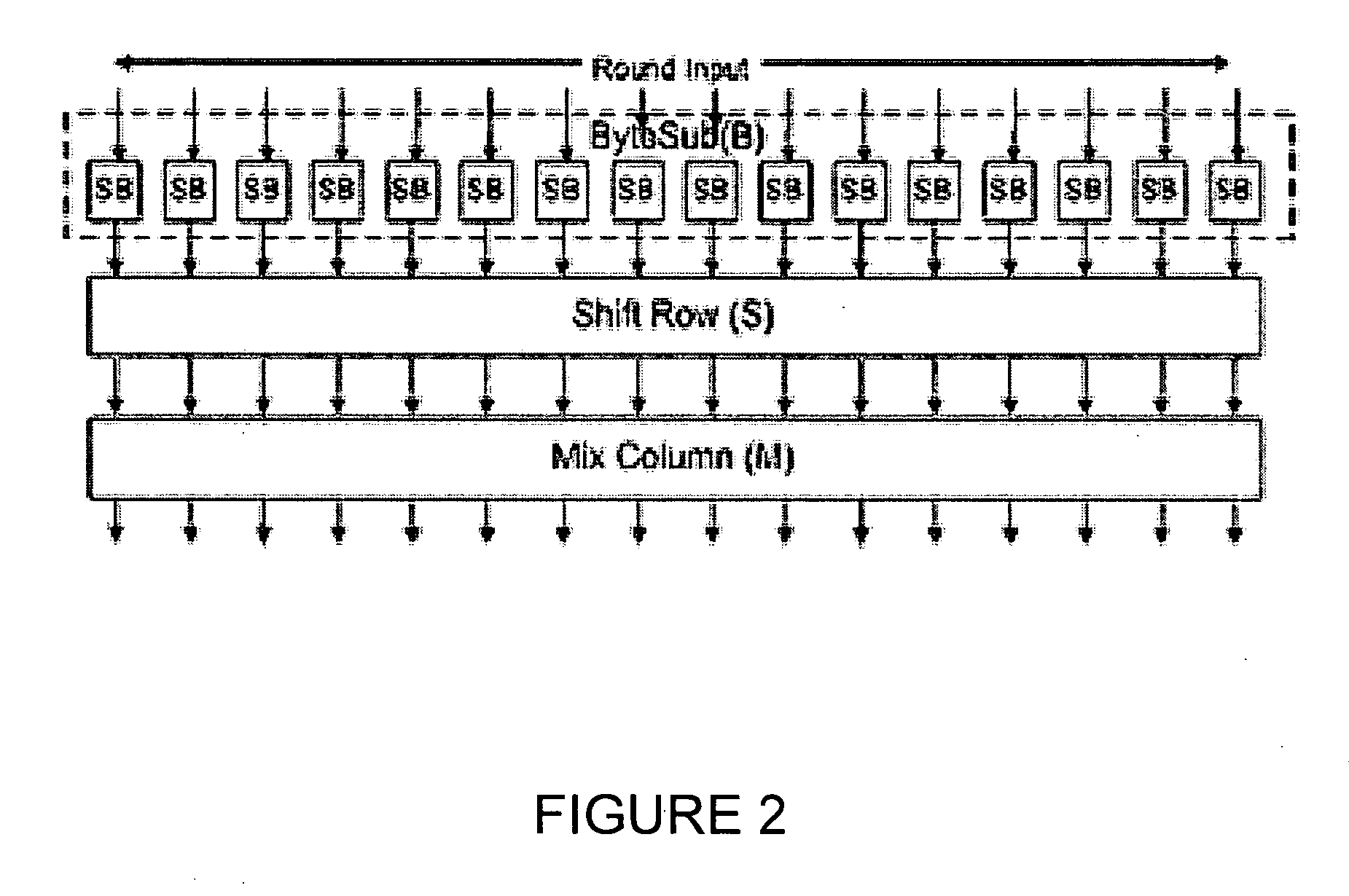
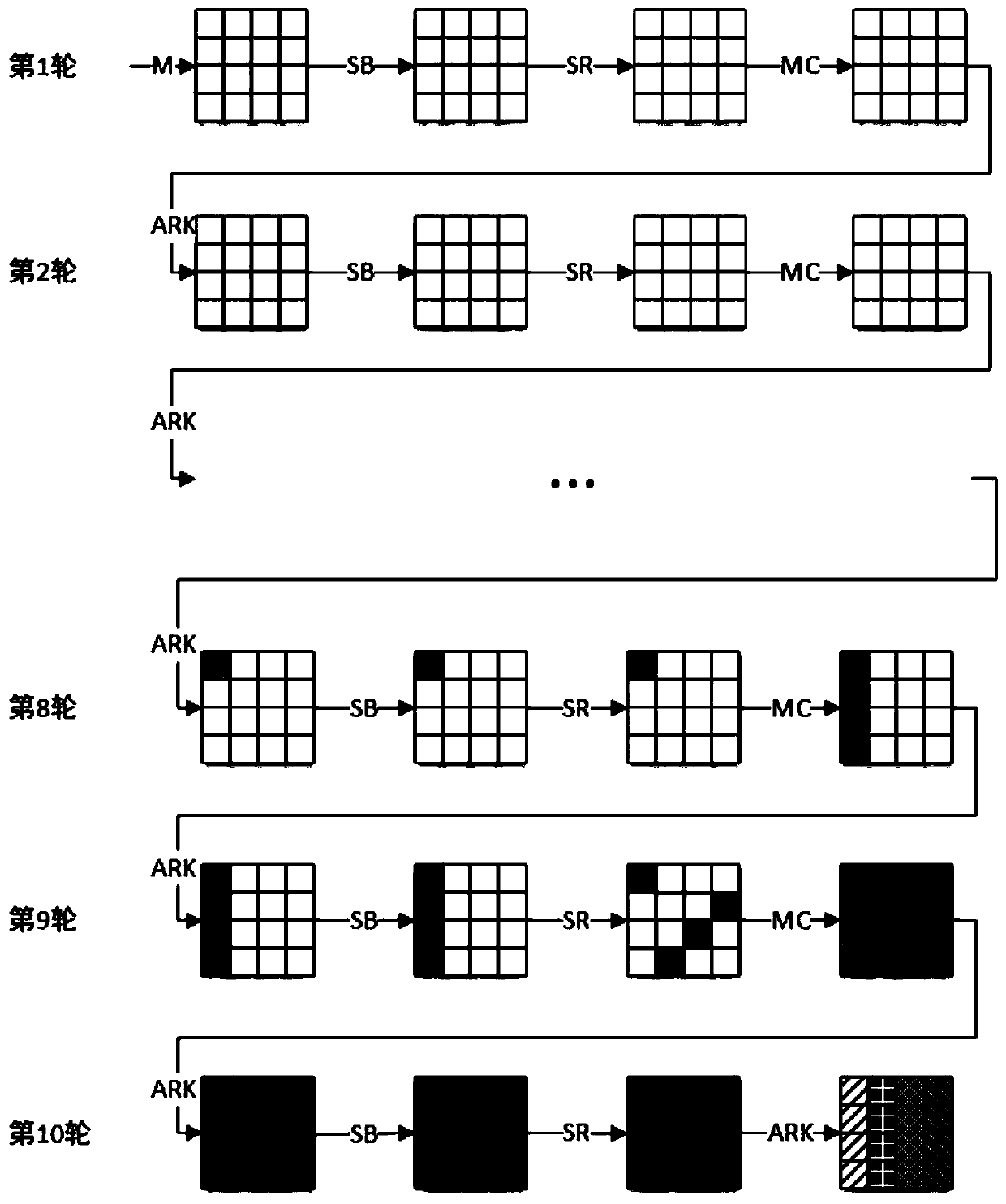
Novel fault attack method aiming at Advanced Encryption Standard (AES-128) algorithm
InactiveCN102404108AQuick screeningShorten the timeKey distribution for secure communicationEncryption apparatus with shift registers/memoriesPlaintextPassword
The invention discloses a novel fault attack method aiming at the Advanced Encryption Standard (AES-128) algorithm, which comprises the steps that: firstly, an attacker randomly selects a plaintext, acquires the correct ciphertext of the plaintext under the action of an initial secret key; and then the attacker encrypts the randomly selected plaintext, optionally selects any one of first three columns of sub-secrete keys at the ninth round in an encryption operation progress, performs multi-byte random fault induction to the one column of sub-secret keys, and acquires a wrong ciphertext comprising random faults; next, the attacker performs multi-byte random fault induction to the rest three columns of sub-secret keys at the ninth round through the same operation till the rest three columns of sub-secret keys are recovered completely and sub-secrete keys at the tenth round are acquired; at last, the initial secret key is acquired through reverse calculation. The novel fault attack method aiming at the AES-12 algorithm disclosed by the invention attacks the sub-secret keys at the ninth round and operates any column of the needed sub-secret keys without affecting operation results of each other, therefore, an AES-128 password system can be treated by differential fault attack by a plurality of equipments at the same time, thus acquiring initial secret key information rapidly and saving more time.
Owner:HANGZHOU MAEN TECH
Circuit and method for detecting a fault attack
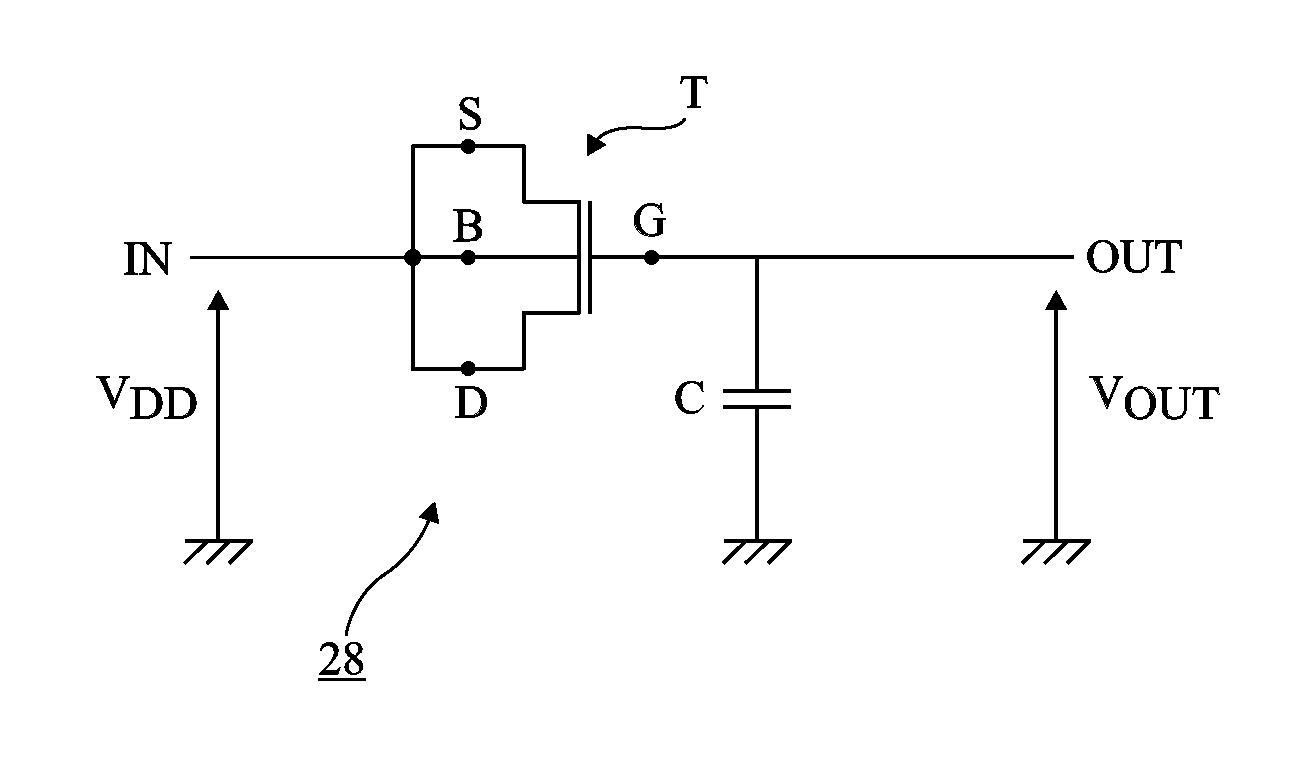
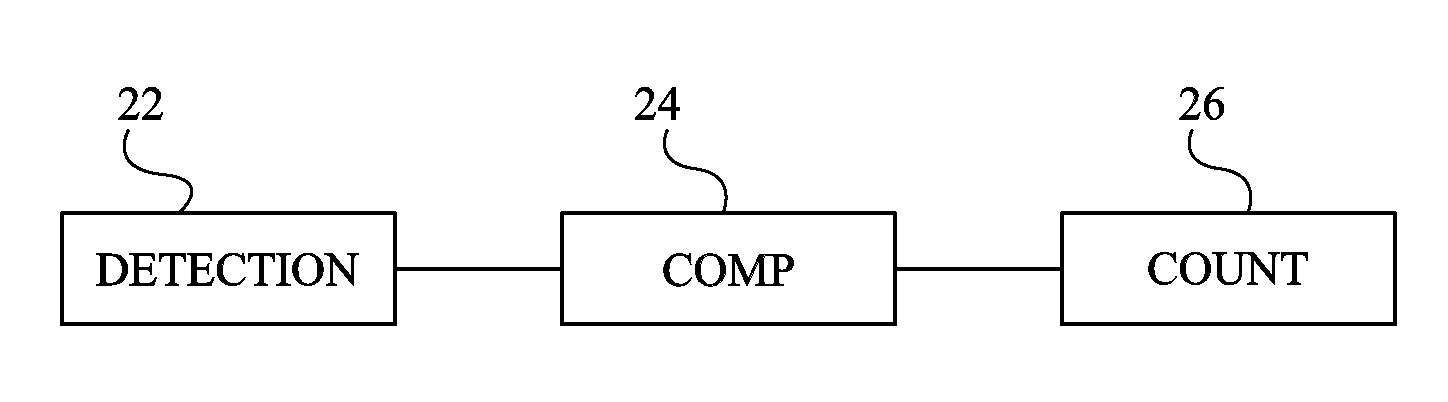
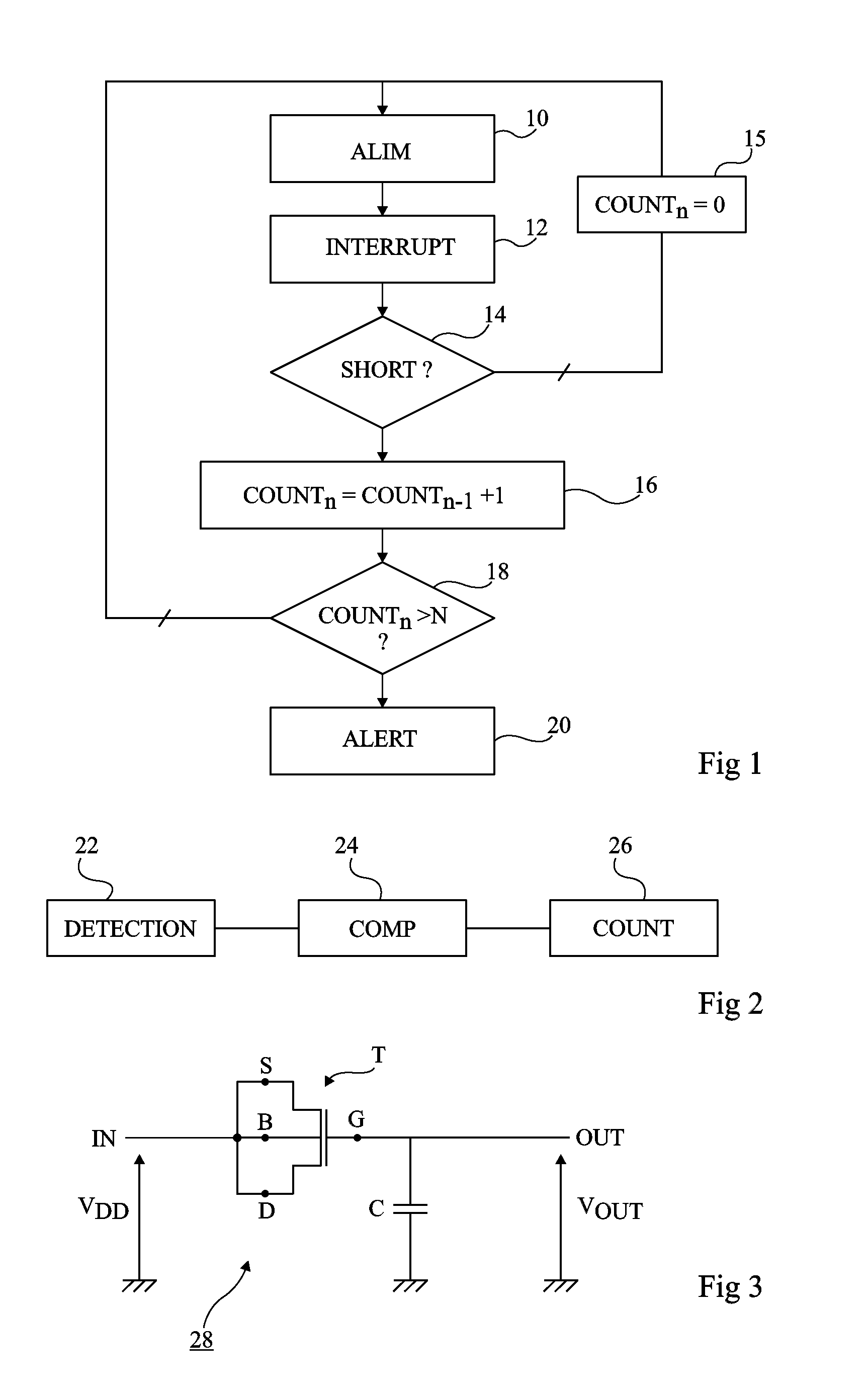
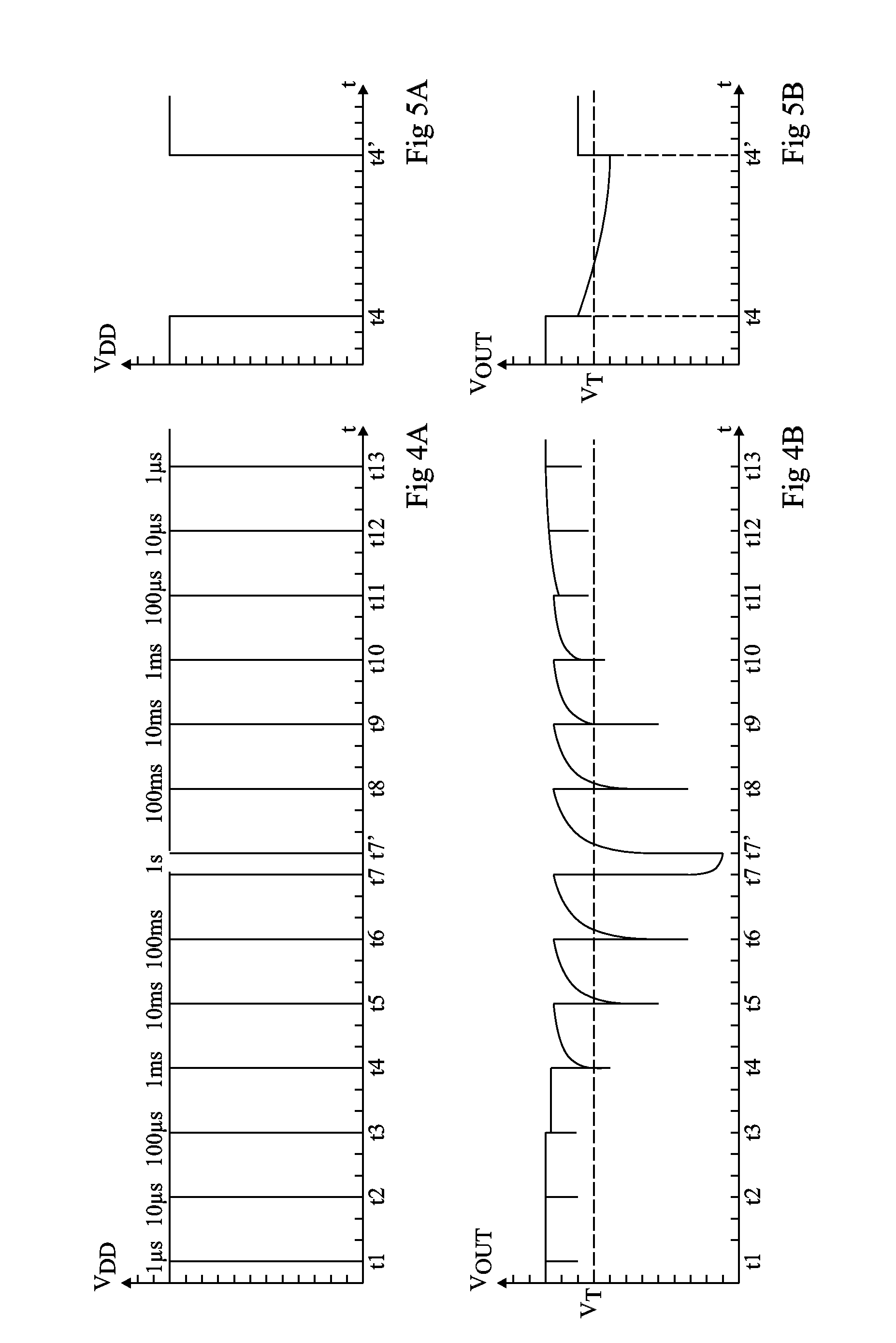
ActiveUS8963574B2Resistance/reactance/impedenceSolid-state devicesFault attackElectrical and Electronics engineering
A device for detecting a fault attack, including: a circuit for detecting an interruption of a power supply; a circuit for comparing the duration of said interruption with a first threshold; and a counter of the number of successive interruptions of the power supply having a duration which does not exceed the first threshold.
Owner:STMICROELECTRONICS (ROUSSET) SAS
Invariance based concurrent error detection for the advanced encryption standard
ActiveUS8005209B2Public key for secure communicationSecret communicationTechnical standardThroughput degradation
Advanced Encryption Standard (AES) is an encryption algorithm for securing sensitive unclassified material by U.S. Government agencies and, as a consequence the de facto encryption standard for commercial applications worldwide. Performing concurrent error detection (CED) for protection of such a widely deployed algorithm is an issue of paramount importance. We present a low-cost CED method for AES. In this method, we make use of invariance properties of AES to detect errors. For the first time, the invariance properties of the AES, which are for the most part used to attack the algorithm, are being used to protect it from fault attacks. Our preliminary ASIC synthesis of this architecture resulted in an area overhead of 13.8% and a throughput degradation of 16.67%.
Owner:POLYTECHNIC INST OF NEW YORK
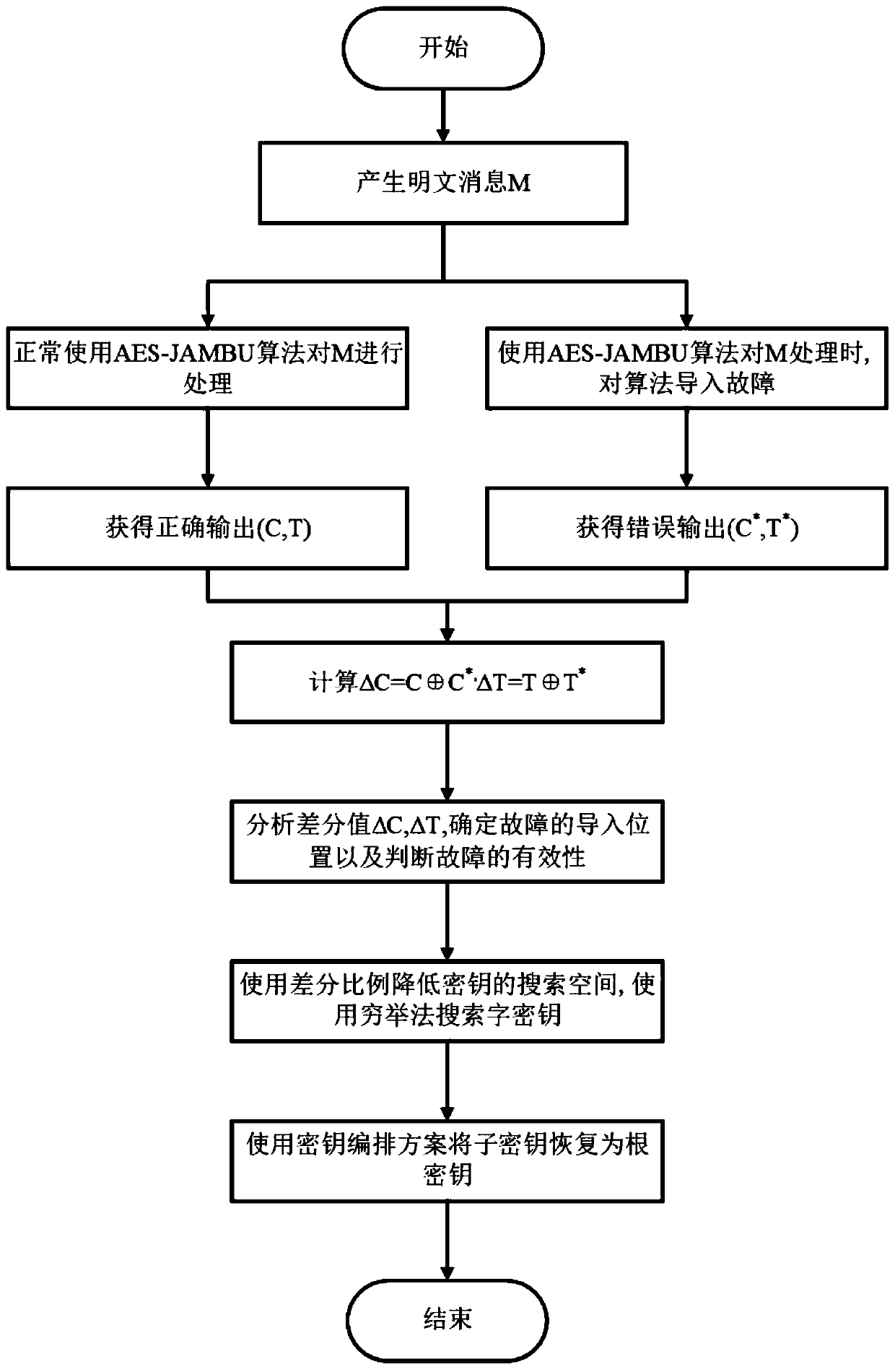
A method for detecting AES-JAMBU resistance to differential fault attacks
InactiveCN109842483ASimple methodFast wayEncryption apparatus with shift registers/memoriesComputer scienceEncryption
The invention provides a method for detecting AES-JAMBU resistance to differential fault attacks. The method comprises the steps that firstly, through an AES-JAMBU authentication encryption algorithm,the plaintext message is processed, and two different experiment environments at the stage are controlled, wherein one is that the experiment environment is not interfered at all, and it is guaranteed that the algorithm processes the plaintext message correctly; And in the other way, in the process of processing the plaintext message through the algorithm, some physical means are used for interfering the processing process, the processing process is induced to generate faults, and wrong output is obtained. And the resistance of the algorithm to the differential fault attack is evaluated by calculating the difference value of the correct result and the error result. And then, by judging the validity of the imported fault and determining the position of fault importing, the key is recovered. The method has the characteristics of simplicity, rapidness, accuracy, easiness in realization and the like; And the a good analysis basis for the capability of resistance to differential fault attacks of the AES-JAMBU authentication encryption algorithm.
Owner:DONGHUA UNIV
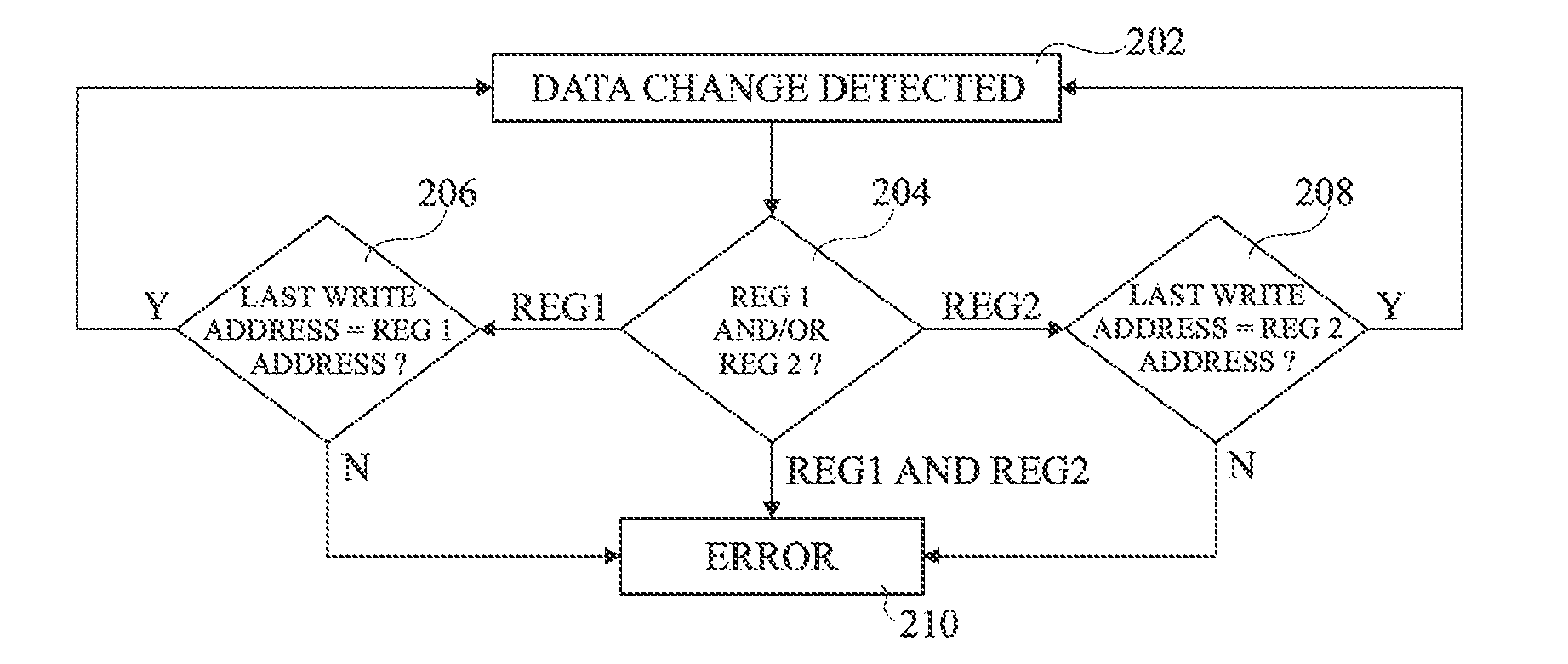
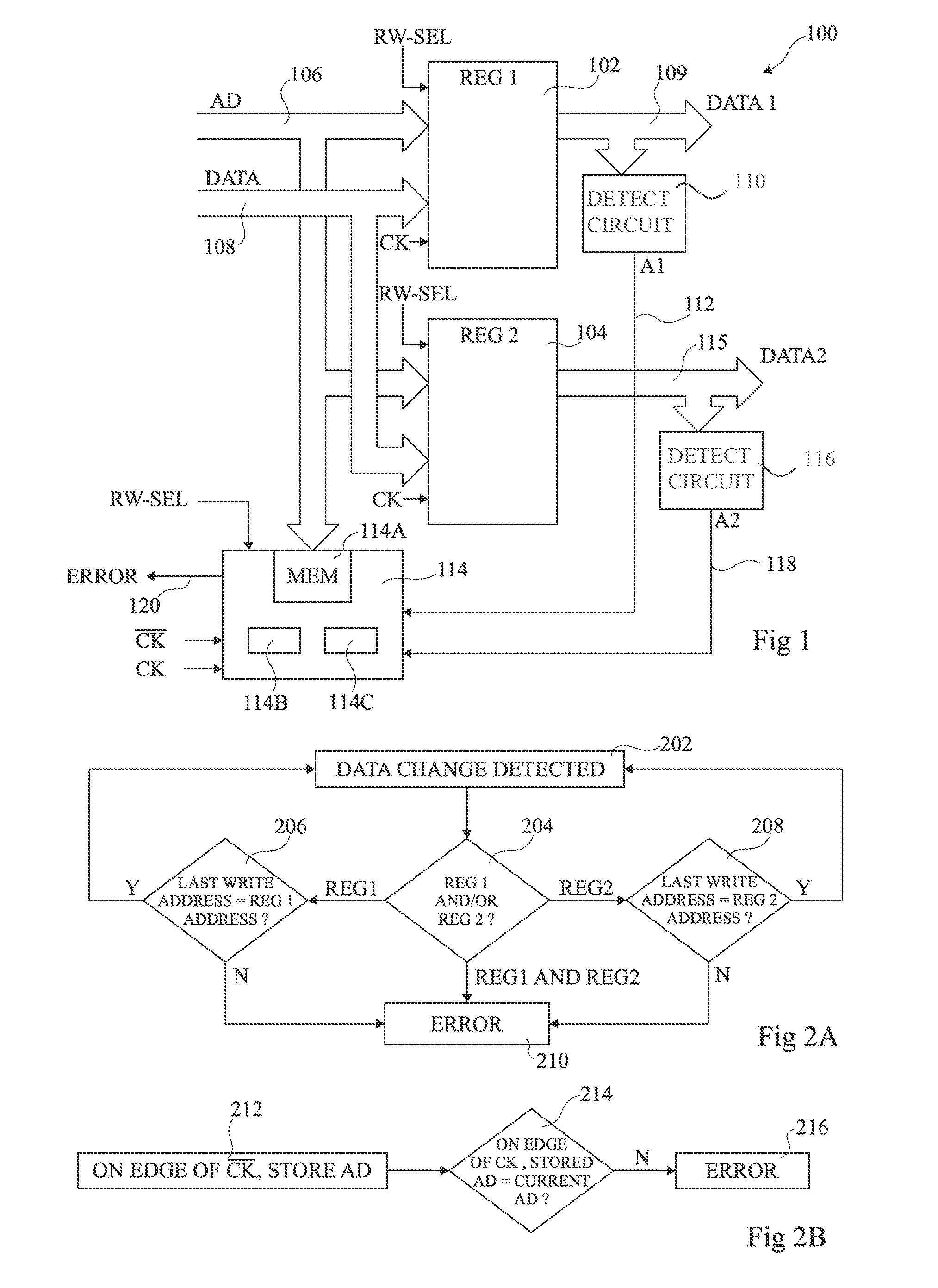
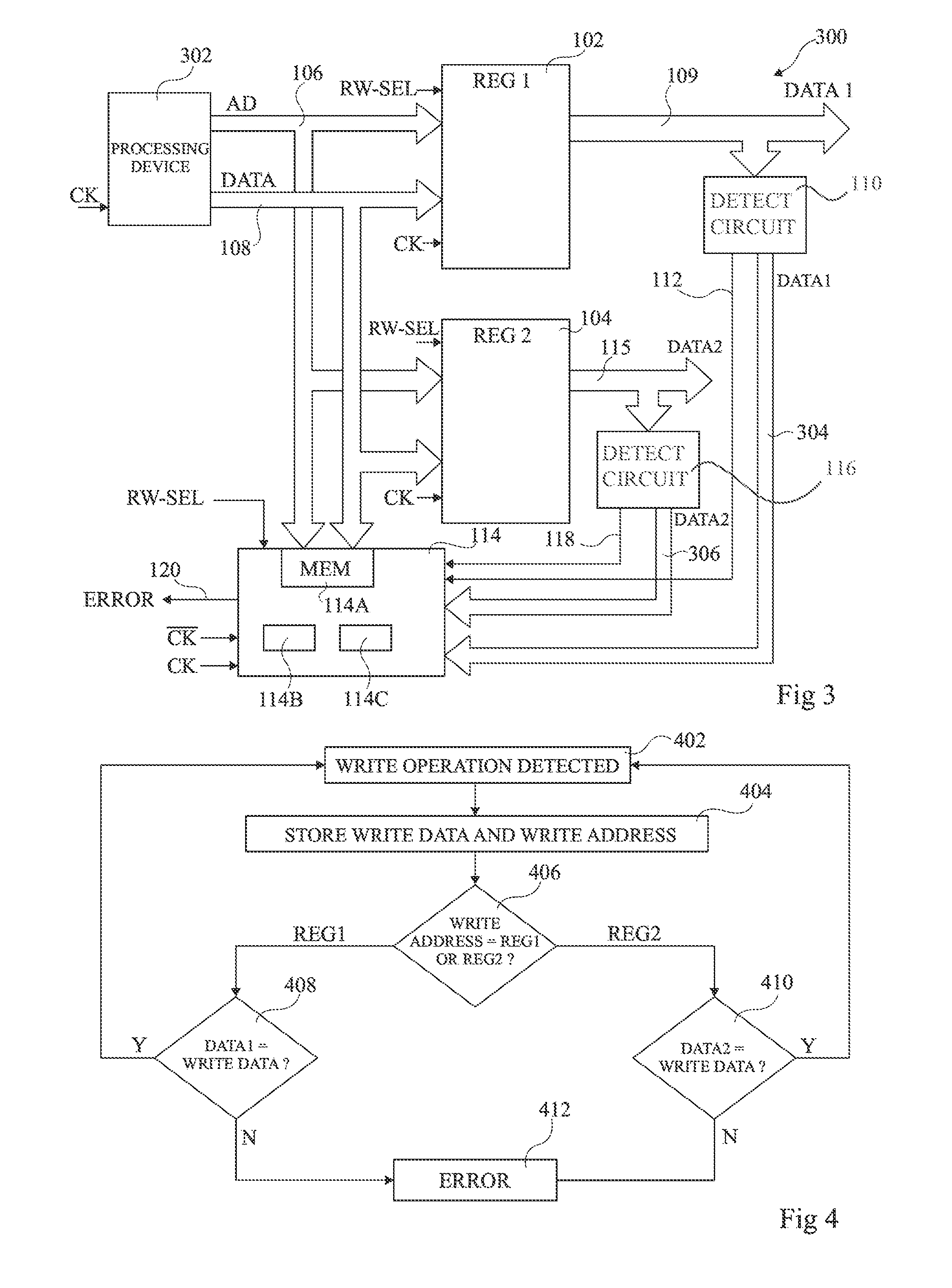
Register protected against fault attacks
A circuit and method of detecting a fault attack in a circuit includes a plurality of registers each identified by an address. The method includes storing in a memory the address present on an address bus during a write operation to one of said registers. In response to a first alert signal indicating that the data stored by a first of said registers has been modified, comparing the address identifying said first register with said stored address.
Owner:STMICROELECTRONICS (ROUSSET) SAS
RSA public key generation apparatus, RSA decryption apparatus, and RSA signature apparatus
InactiveCN1645791AEncryption apparatus with shift registers/memoriesPublic key for secure communicationComputer hardwareSource Data Verification
An RSA decryption apparatus that is used in an IC card or the like counters a differential fault attack. The RSA decryption apparatus computes at high speed a public key used in data verification, without having to obtain the public key from an external source. The RSA decryption apparatus includes a remainder computation unit 412 that calculates dp= d mod (p-1), and an inverse computation unit 414 that finds an inverse of dp over a residue field with p-1 as a modulus. The RSA decryption apparatus verifies a deciphertext with use of the inverse of dp as the public key. The reduced bit count in inverse computation compared to if the inverse of d is found as the public key increases computing speed.
Owner:PANASONIC CORP
Fault tolerant apparatus and method for elliptic curve cryptography
InactiveUS20150092941A1Public key for secure communicationUnauthorized memory use protectionData treatmentComputer science
A fault tolerant apparatus and method for elliptic curve cryptography. For example, one embodiment of a processor includes one or more cores to execute instructions and process data; and fault attack logic to ensure that the execution of the instructions and processing of the data is not vulnerable to memory safe-error attacks after a fault is injected by hiding any correlation between processor behavior and secret bits in a secret key.
Owner:INTEL CORP
Key protection mechanism
A method of protecting secret key integrity in a hardware cryptographic system includes first obtaining an encryption result and corresponding checksum of known data using the secret key, saving those results, then masking the secret key and storing the masked key. When the masked key is to be used in a cryptographic application, the method checks key integrity against fault attacks by decrypting the prior encryption results using the masked key. If upon comparison, the decryption result equals valid data, then the key's use in the cryptographic system can proceed. Otherwise, all data relating to the masked key is wiped from the system and fault injection is flagged.
Owner:RAMBUS INC
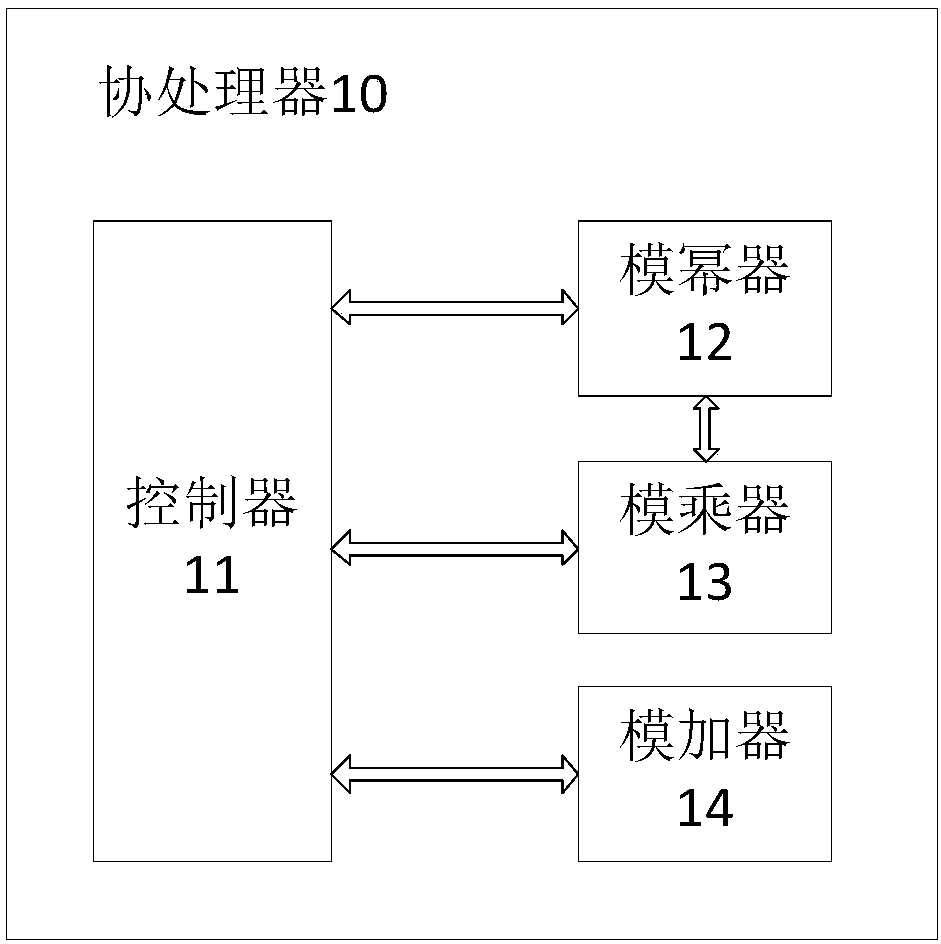
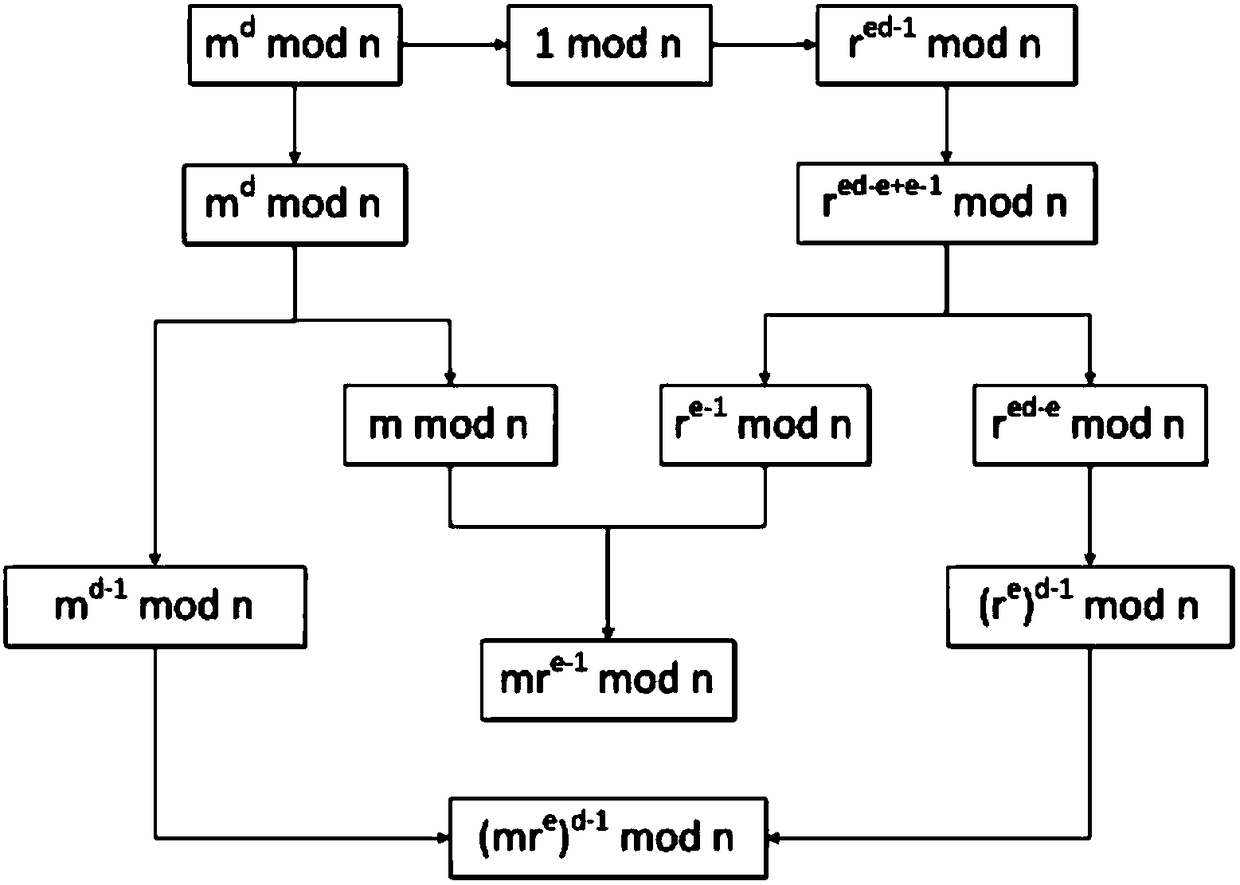
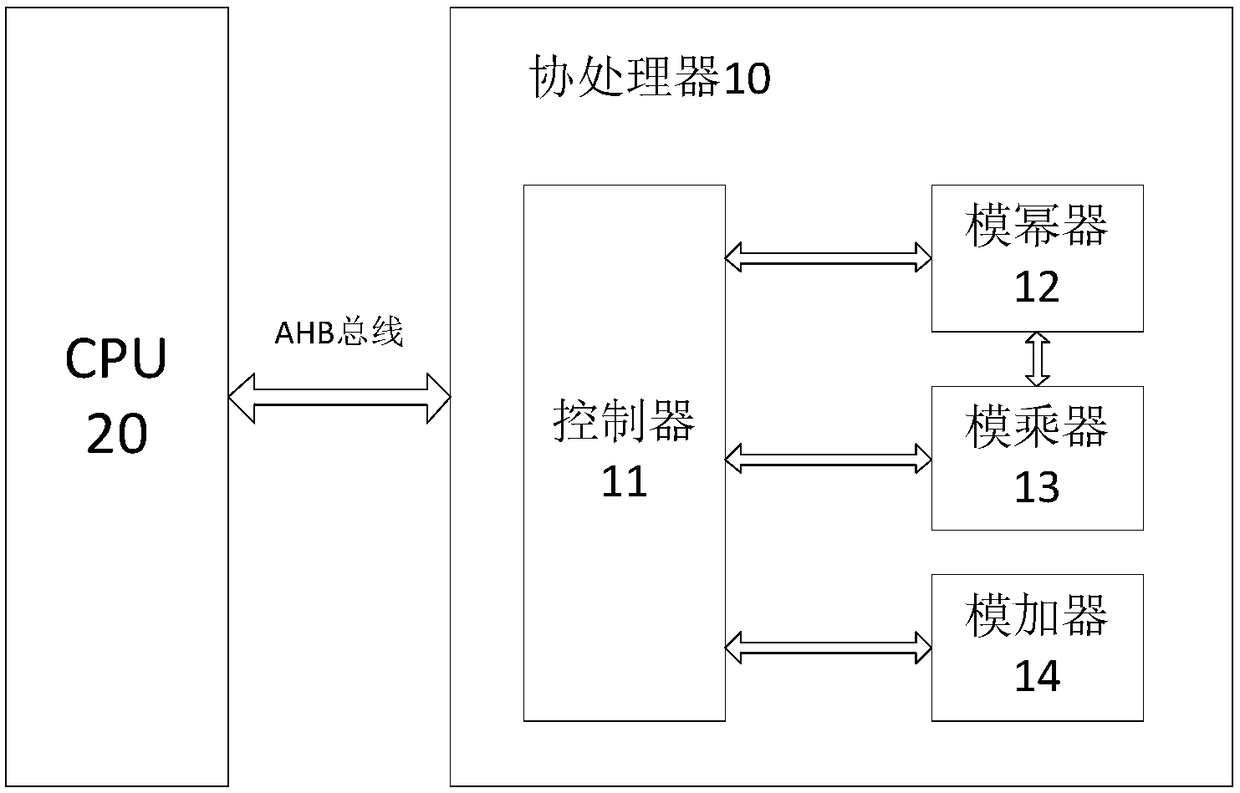
RSA private key mask operation method, coprocessor and RSA arithmetic device
InactiveCN108111309APrevent inversionLower cover costPublic key for secure communicationCryptographic attack countermeasuresCoprocessorModular multiplier
The invention provides a RSA private key mask operation method, a coprocessor and a RSA arithmetic device, wherein when a controller receives a start operation instruction sent by a master processor,the controller acquires a to-be-decrypted content m, a random number r, a public key e, a private key d and a modulus n of a RSA algorithm, and sends the decrypted content to the master processor; a modular adder calculates e-1 and calculates d-1; a modular exponentiation device calculates r<e-1>modn based on the e-1, calculates (mr<e>)<d-1>modn based on the mr<e>modn and the d-1; a modular multiplier calculates mr<e-1>modn based on the r<e-1>modn, calculates mr<e-1>.rmodn based on the mr<e-1>modn to obtain mr<e>modn, and calculates (mr<e>)<d-1>.mr<e-1>modn based on the (mr<e>)<d-1>modn and the mr<e-1>modn to obtain m<d>modn, and sends the decrypted content of the m<d>modn to the controller, thus, technical effects of reducing mask base cost, having relatively higher security in aspects, such as resisting side channel attacks and resisting fault attacks, are achieved.
Owner:北京融通高科微电子科技有限公司
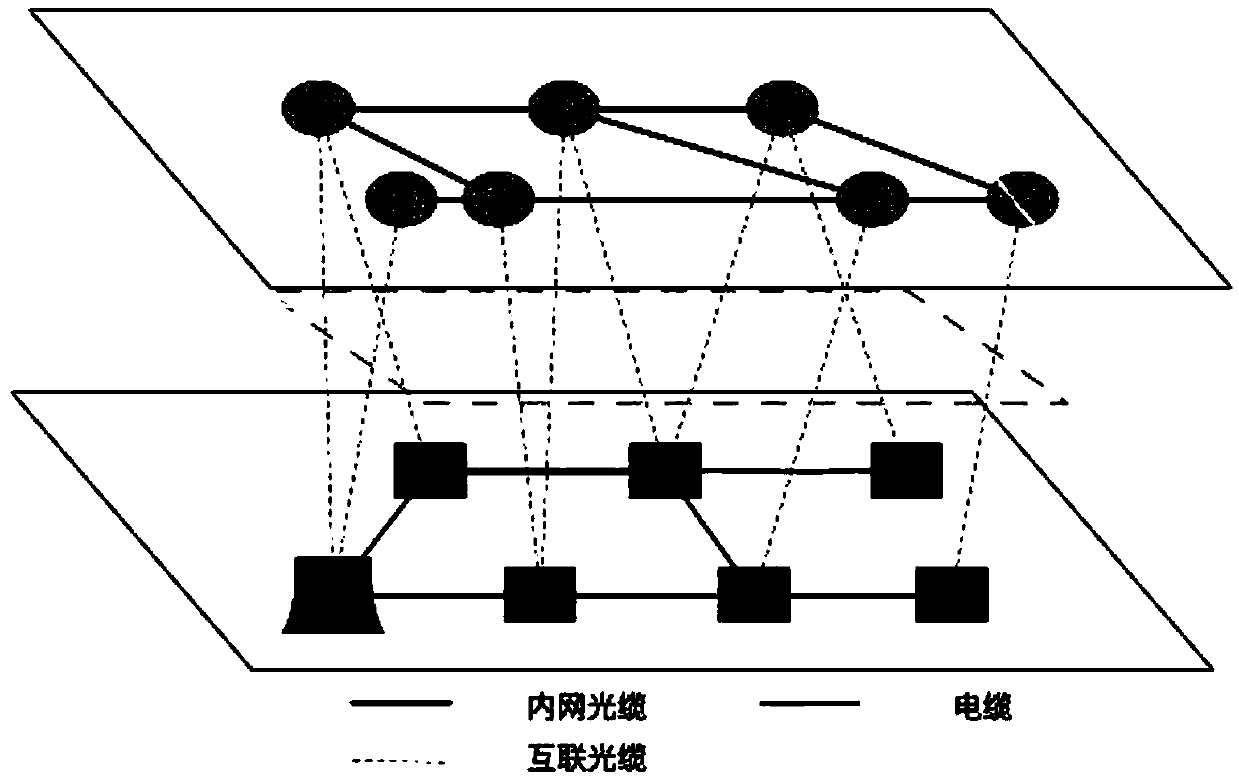
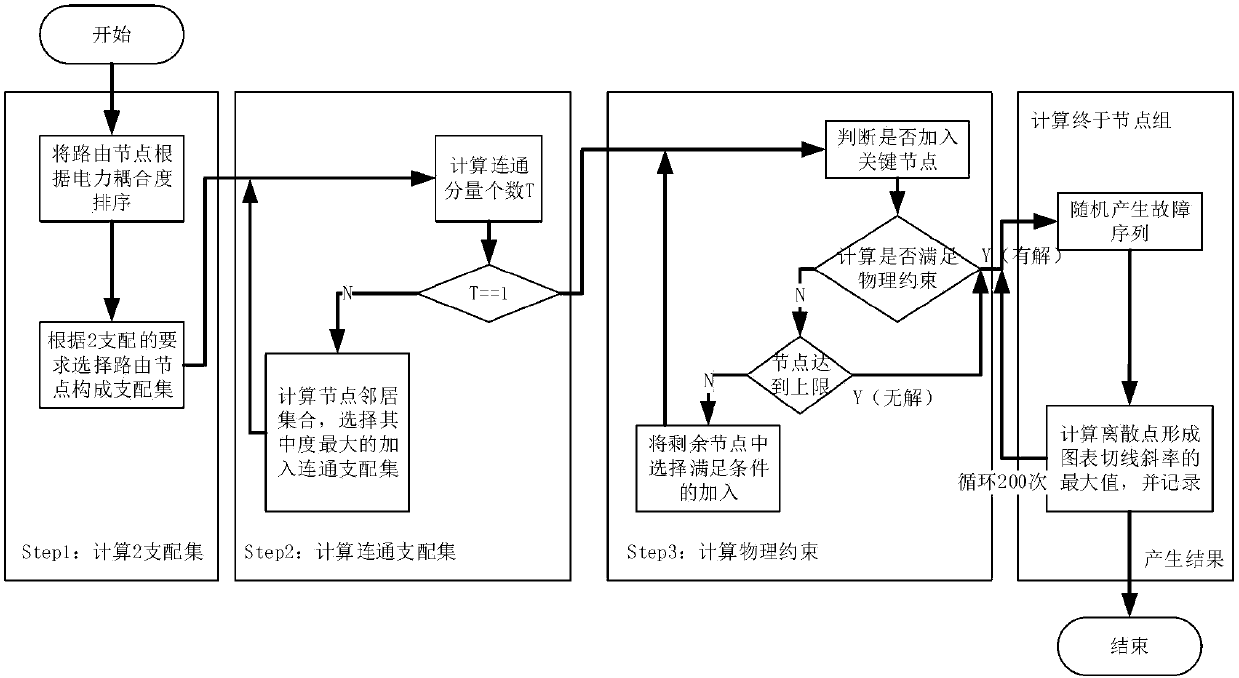
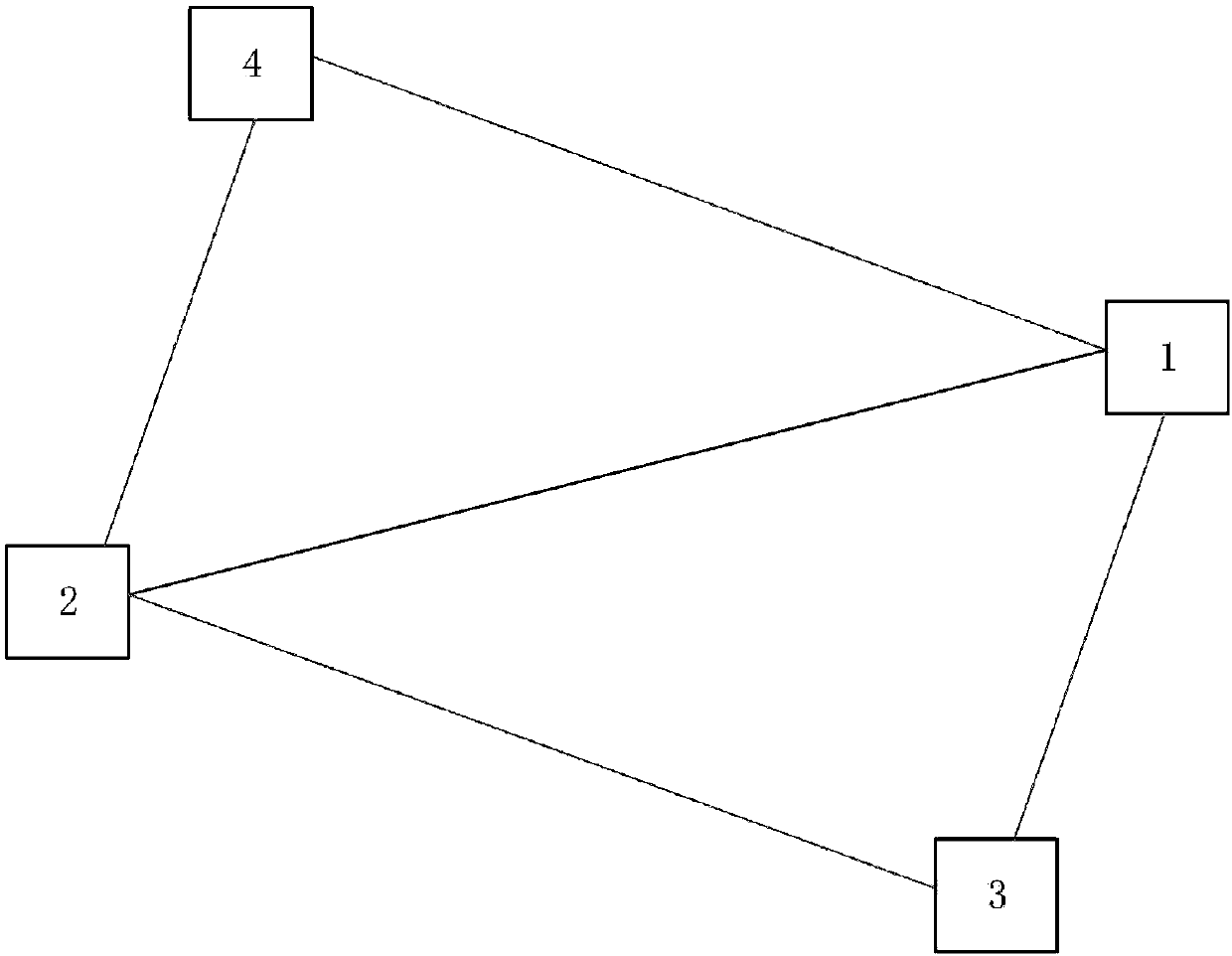
Anti-attack communication network fault cascade risk influence analysis method
InactiveCN107769962AExcellent failure suppression effectData switching networksElectric power systemPower grid
The invention relates to an anti-attack communication network fault cascade risk influence analysis method, and belongs to the technical field of the network. The method comprises the following steps:S1, establishing a coupling network model: establishing a power network model, establishing an overall network model, and refining the overall network model; S2, analyzing the coupling network model:respectively giving out the clear definition of the power system node fault and the communication network node fault; analyzing a necessary condition for the fault formation on the basis of the cleardefinition; introducing a virtual backbone network concept by adopting the thought of damaging the necessary condition based on the considerations of avoiding or inhibiting the fault occurrence and optimizing the communication sub-network; and finally putting forward an important node group backup optimization strategy. Through the adoption of the anti-attack communication network fault cascade risk influence analysis method disclosed by the invention, the important node group backup optimization algorithm of a power communication network is put forward by comprehensively considering the influence on the power communication network by the physical attribute of an optical cable based on the complicated network theory, the production of the cascade fault can be well inhibited under the fault attack condition, and the robustness of the power communication network is effectively improved.
Owner:GUIZHOU POWER GRID CO LTD
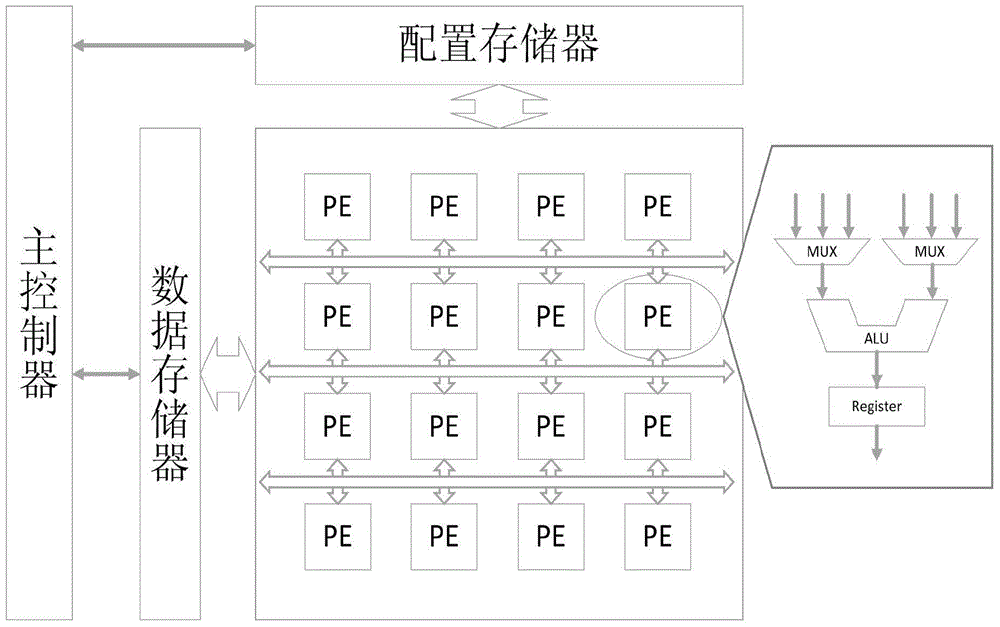
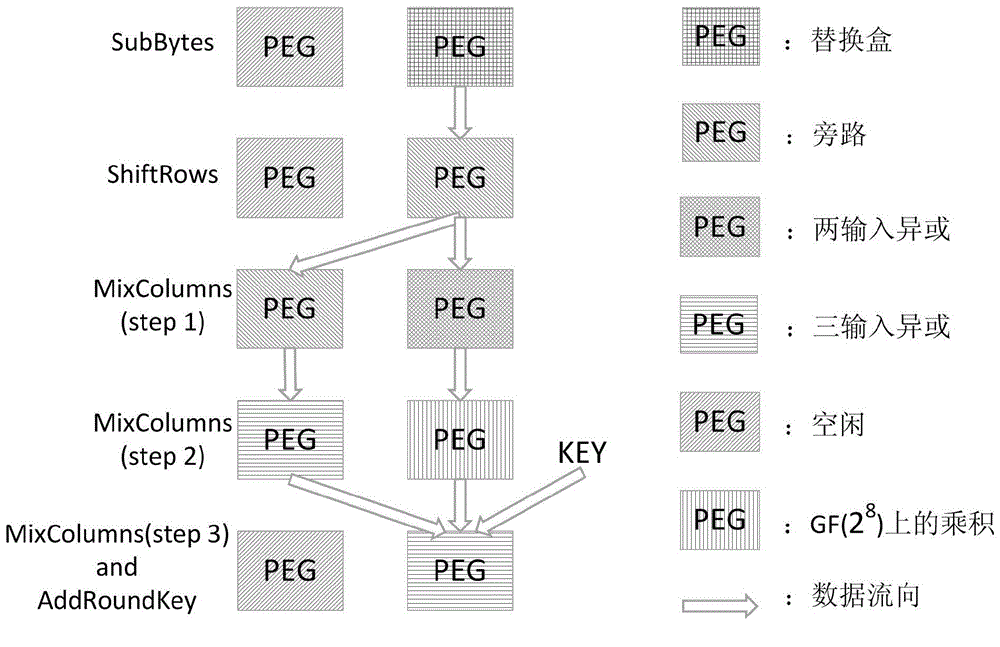
Space-randomization-based fault attacking resisting method applicable to reconfigurable array framework
ActiveCN104484615AIncrease the difficultyResistant to single-fault attacksDigital data protectionInternal/peripheral component protectionPasswordRandomization
The invention relates to a space-randomization-based fault attacking resisting method applicable to a reconfigurable array framework. The method comprises the following steps of (1) setting an application scenario of a password processor, wherein the application scenario comprises an encryption algorithm running inside the password processor, an oriented fault attack injection mode and a fault injection type; (2) under the set application scenario, analyzing and finding the executing step with sensitive spots from the encryption algorithm, and determining specific parameters adopted when the executing step with the sensitive spots is executed in a reconfigurable computational array; (3) according to the specific parameters adopted when the executing step with the sensitive spots is executed in the reconfigurable computational array, configuring the encryption algorithm executing step with the sensitive spots so that the sensitive spots can be distributed randomly on the space of the configurable computational array. According to the space-randomization-based fault attacking resisting method, a single fault attach can be resisted, dual-fault and multi-fault injection attacks can be resisted, and the attack resistance of an integrated circuit at the fault injection stage is effectively improved.
Owner:WUXI RES INST OF APPLIED TECH TSINGHUA UNIV
Circuit and method for detecting a fault attack
A device for detecting a fault attack, including: a circuit for detecting an interruption of a power supply; a circuit for comparing the duration of said interruption with a first threshold; and a counter of the number of successive interruptions of the power supply having a duration which does not exceed the first threshold.
Owner:STMICROELECTRONICS (ROUSSET) SAS
Elliptic curve exponentiation apparatus that can counter differential fault attack, and information security apparatus
InactiveUS7388957B2Secret communicationComputations using residue arithmeticComputer hardwareInformation security
Provided is an elliptic curve exponentiation apparatus that can counter the DFA when an elliptic curve exponentiation technique is used. A computation result verification unit 127 receives, as a computation result, an exponentiation-result-point (X, Y) from an elliptic curve computation unit 124. The computation result verification unit 127 computes X3+a×X+b, and computes Y2, and outputs the received exponentiation-result-point when judging that Y2=X3+a×X+b, and does not output the received exponentiation-result-point when not judging that Y2=X3+a×X+b.
Owner:PANASONIC CORP
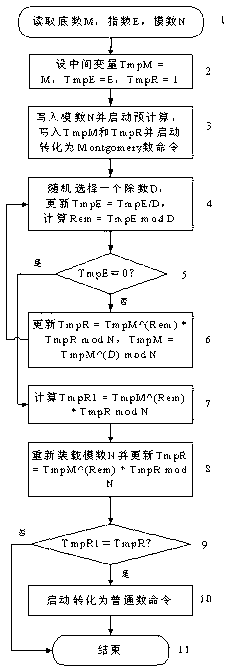
Safety modular exponentiation method for resisting energy analysis and fault attack
InactiveCN103246494AImprove performanceComputations using residue arithmeticStatic random-access memoryRandom access memory
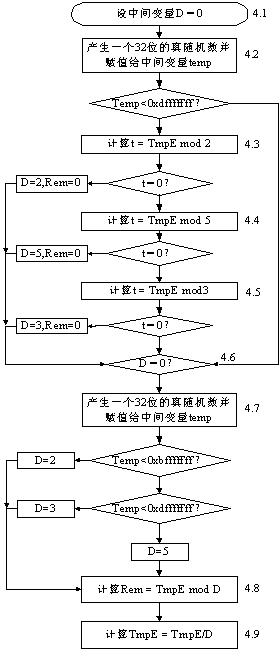
The invention discloses a safety modular exponentiation method for resisting energy analysis and fault attack. The safety modular exponentiation method includes the steps: reading a base number M, an index E and a modulus N; setting an intermediate variable TmpM=M, TmpE=E and TmpR=1; writing the modulus N into an NSRAM (non-volatile static random access memory), starting pre-computation and converting the TmpM and the TmpR into Montgomery numbers by the aid of an ASRAM (asynchronous static random access memory) and a BSRAM (burst static random access memory); randomly selecting a divisor D, updating TmpE=TmpE / D and computing the intermediate variable Rem=TmpEmodD; updating TmpR=TmpM^(Rem)*TmpRmodN and TmpM=TmpM^(D)modN according to a divisor remainder pair (D, Rem) if TmpE=0 and switching to the step of selecting the divisor; computing the intermediate variable TmpR1=TmpM^(Rem)*TmpRmodN according to a remainder Rem if TmpE=0; reloading the modulus N into the NSRAM and updating TmpR=TmpM^(Rem)*TmpRmodN according to the remainder Rem; comparing the TmpR1 with the TmpR and converting the TmpR into a general number command and outputting results if the TmpR1 is equal to the TmpR; and finishing the operation if the TmpR1 is unequal to the TmpR. By the safety modular exponentiation method, both energy attack and fault attack can be resisted.
Owner:SHANGHAI AISINOCHIP ELECTRONICS TECH
Embedded device having countermeasure function against fault attack
InactiveUS20100031055A1Improve securityAvoid crackingUnauthorized memory use protectionHardware monitoringCountermeasureValue set
A cryptographic processing device, comprising: a storage unit; initial setting unit for setting a value to be stored in the storage unit; Montgomery modular multiplication operation unit for performing a Montgomery modular multiplication operation plural times for a value set by the initial setting unit; and fault attack detection unit for determining whether or not a fault attack occurred for each of at least some parts of the Montgomery modular multiplication operations performed plural times.
Owner:FUJITSU LTD
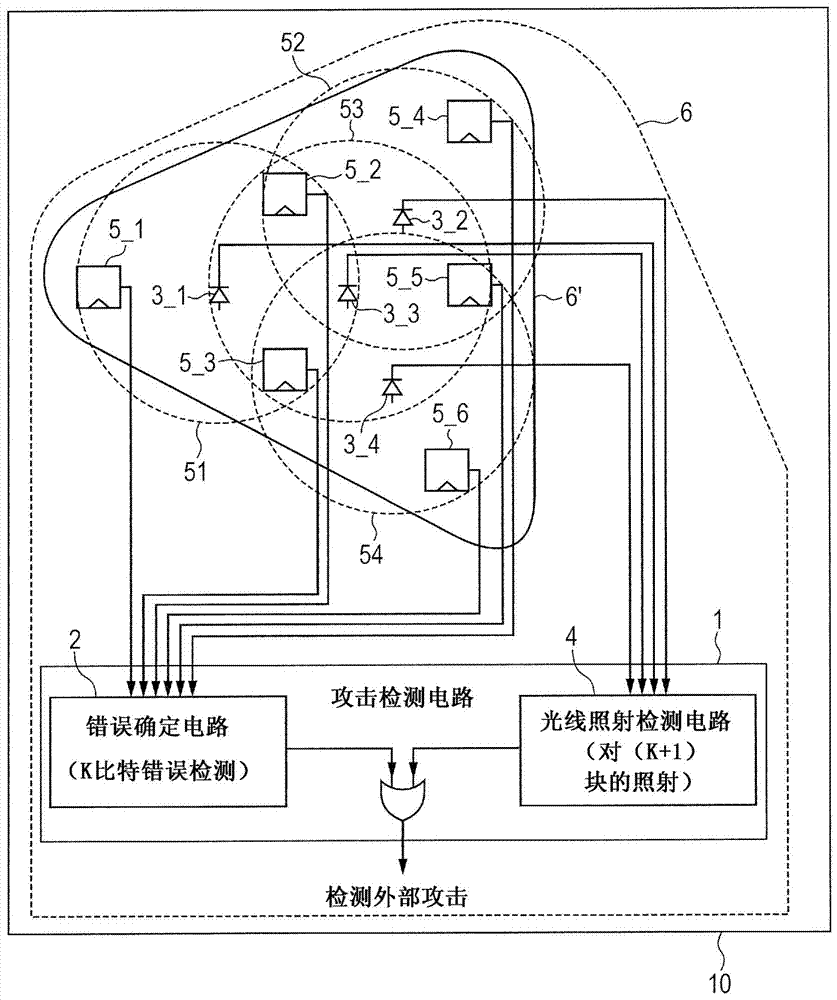
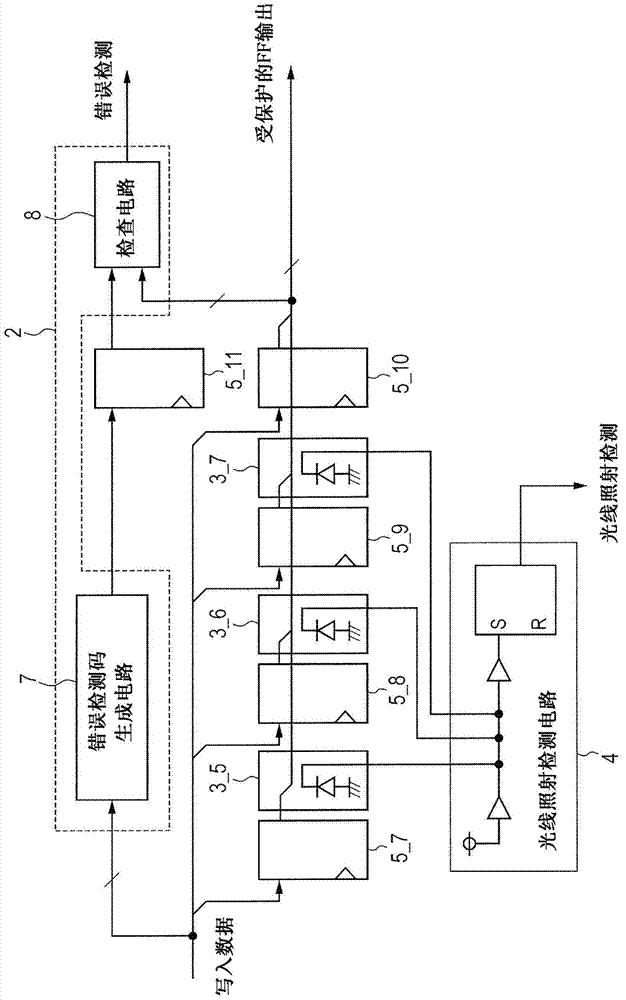
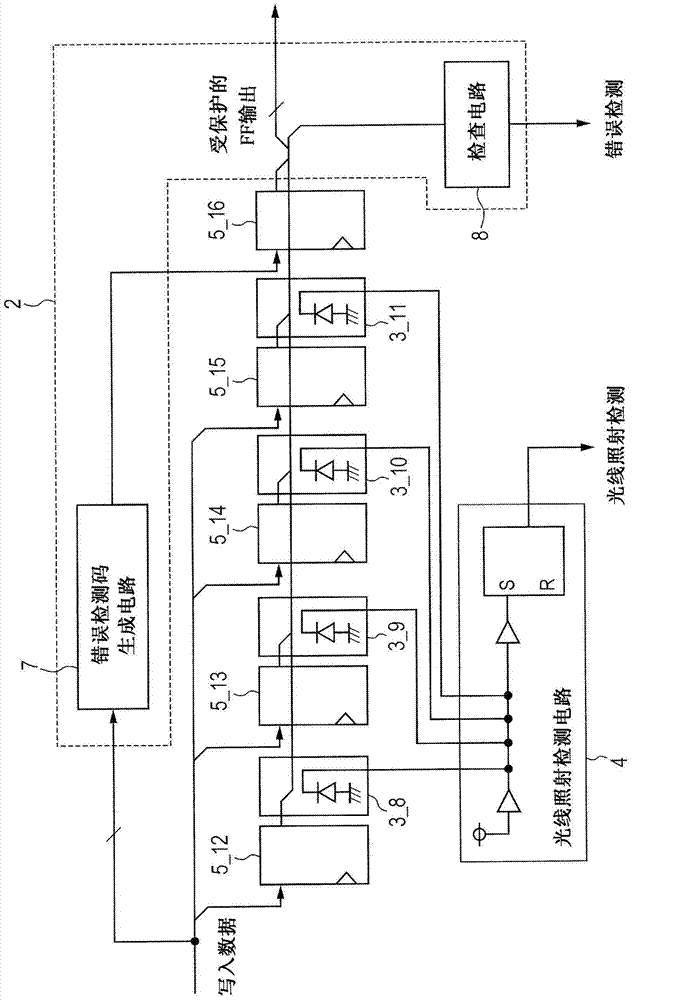
Semiconductor integrated circuit
InactiveCN103679011AReliability increasing modificationsDigital data protectionComputer hardwareLight irradiation
The invention relates to a semiconductor integrated circuit. Confidential information stored in an LSI can be protected against laser attacks for the purpose of obtaining or forging confidential information through breakdown of the LSI. Laser attacks are detected whatever the number of error bits caused by laser attacks in multi-bit storage elements. Provided is an attack detection circuit for detecting multi-bit storage elements contained in a logic circuit. The attack detection circuit includes an error determination circuit capable of detection through a logic operation such as a code theory and a light irradiation detection circuit having light detection elements, and the light detection elements are arranged so that the light irradiation detection circuit can detect errors of the number of bits beyond the detection limit of the error determination circuit. Due to error detection by the error determination circuit and light irradiation detection by the light irradiation detection circuit, the circuits complementarily detect fault attacks from outside.
Owner:RENESAS ELECTRONICS CORP
Comprehensive protection method for resisting side channel and fault attacks
InactiveCN112187444AImprove protectionExcellent areaEncryption apparatus with shift registers/memoriesCryptographic attack countermeasuresCiphertextExclusive or
The invention discloses a comprehensive protection method for resisting side channel and fault attacks, which comprises the following steps of: 1) for a target algorithm to be protected, constructingan algorithm which is the same as the target algorithm as a redundancy algorithm of the target algorithm; respectively constructing the same d-order threshold protection scheme for the target algorithm and the redundant algorithm thereof, wherein the same d-order threshold protection scheme is used for protecting the d-order side channel attack; 2) carrying out exclusive OR on the output of the target algorithm and the output of the redundant algorithm, then carrying out multiplication mask operation on the output of the target algorithm and a random number, and protecting the multiplication operation by adopting a threshold implementation technology; 3) carrying out exclusive OR on the processing result of the step 2) and the d-order threshold implementation structure of the target algorithm or the d-order threshold implementation structure of the redundant algorithm to obtain a result, and taking the result as a final output result of the target algorithm. The method can resist faultsensitivity attacks not based on ciphertext, differential fault attacks based on ciphertext and side channel attacks.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI +1
AWGN-wiretap channel anti-wiretapping security structure based on polar code and implementation method thereof
ActiveCN107017960ASimple compositionImprove confidentialityCommunication jammingForward error control useS-boxWiretap channels
The invention discloses an AWGN-wiretap channel anti-wiretapping security structure based on polar code and an implementation method thereof, belonging to the field of communication. The anti-wiretapping security structure includes a sending end confusing structure and a legal receiving end de-confusing structure; the sending end confusing structure includes a sequential exclusive or (XOR) device, a confusion interleaver and a nonlinear searching table S-box; and the legal receiving end de-confusing structure includes a sequential XOR device, a de-confusing interleaver and a reverse S-box. The de-confusing structure is symmetric with the confusing structure. The de-confusing structure and the confusing structure can be completed in the same set of hardware, so that the composition of the anti-wiretapping security structure is simpler. The sequential XOR device and the confusion interleaver are of linear confusion structures, but the S-box is of a nonlinear confusion structure. The nonlinear confusion structure can reduce the correlation between input and output, and can resist differential fault attacks effectively, but the linear confusion structure is helpful for error bit spread of a single-bit code unit, therefore, it is difficult for an eavesdropper to obtain any information by means of violent enumeration or analysis of differential probability of signals.
Owner:BEIHANG UNIV
Method of detecting a fault attack
ActiveUS20110119532A1Encryption apparatus with shift registers/memoriesHardware monitoringData valueFault attack
A method of detecting a fault attack including generating a first signature of a first group of data values by performing a single commutative non-Boolean arithmetic operation between all the data values of the first group; generating a second set of data values by performing a permutation of the first set of data values; generating a second signature of the second group of data values by performing said single commutative non-Boolean arithmetic operation between all the data values of the second group; and comparing the first and second signatures to detect a fault attack.
Owner:STMICROELECTRONICS SRL
Charging pile communication system encryption/decryption method
InactiveCN106850670AImprove securityAvoid the problem of poor resistance to differential attacksMultiple keys/algorithms usagePublic key for secure communicationCommunications systemReal-time data
The invention discloses a charging pile communication system encryption / decryption method. The method comprises the following steps: base on an asymmetric encryption way for transmitting a key and a symmetric encryption way for transmitting real-time, the symmetric encryption way is used for transmitting real-time data; the asymmetric encryption way uses a public key and private key pair in the encryption and decryption of the information, a server-side issues the public key to the charging pile, wherein the public key is used for encrypting the information, the private key for decryption is saved in the charging pile, the private key is used for decrypting the information encrypted by the public key, and the public key cannot be used for speculating the private key; the asymmetric encryption way transmits the key by use of the improved RSL algorithm. By use of above mentioned technical scheme, the security of system information transmitting is effectively improved, and the technical scheme is good in difference fault attack resistance, safe and reliable, capable of fast decrypting ciphertext, and good in practicability.
Owner:浙江晨泰科技股份有限公司
Method for detecting resistance of HAS-160 algorithm to differential fault attack
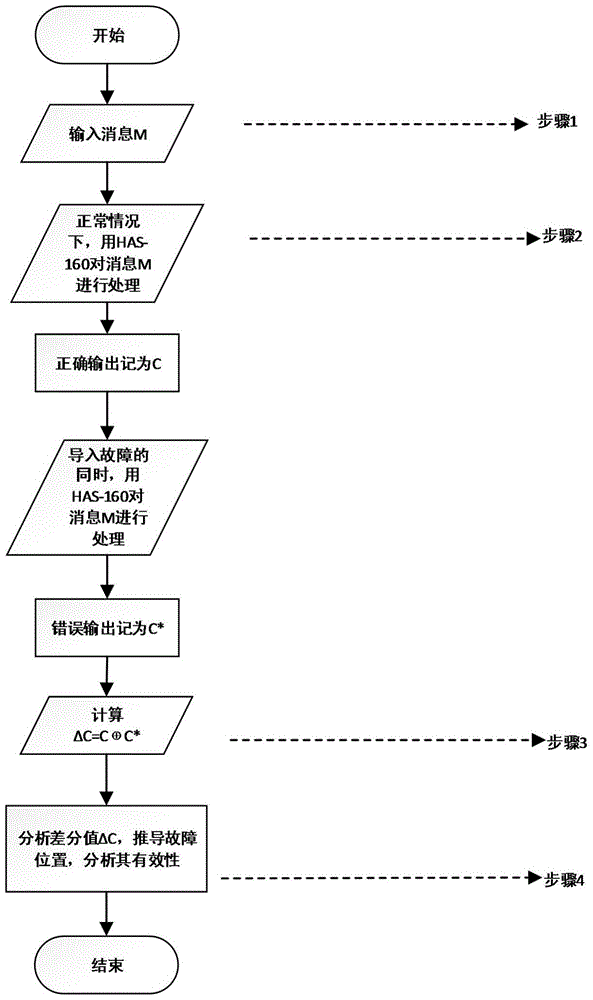
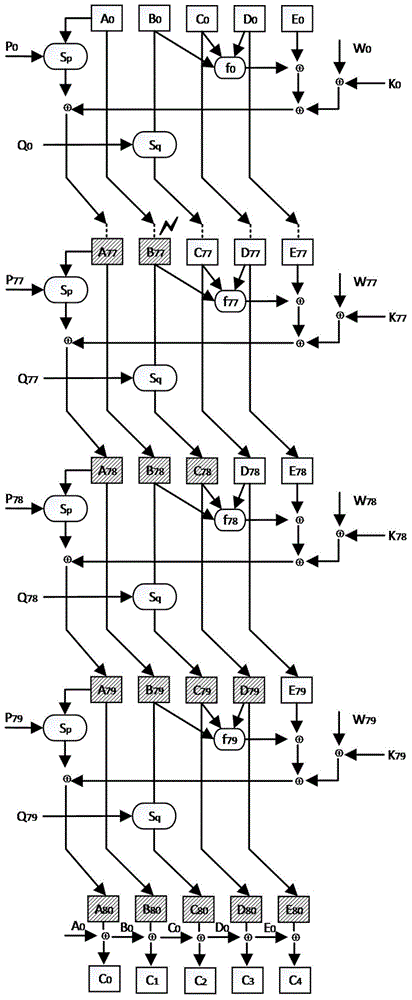
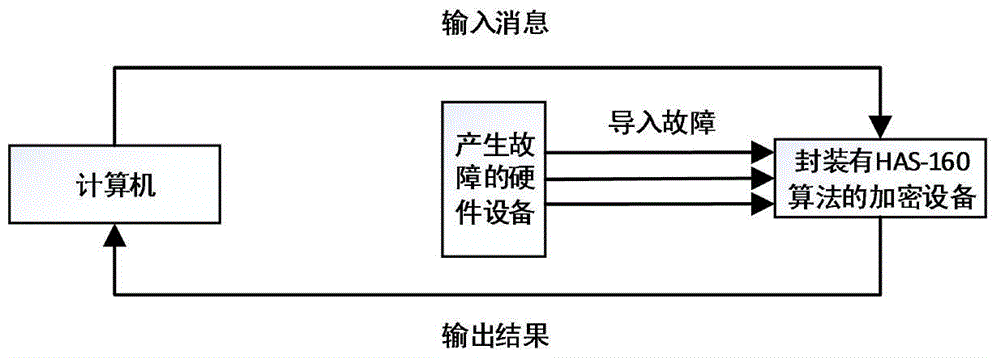
PendingCN105703896AThe method is simple and accurateEasy to implementCryptographic attack countermeasuresPlaintextAlgorithm
The invention relates to a method for detecting resistance of an HAS-160 algorithm to a differential fault attack. The method includes the steps of: randomly generating a plaintext message to be processed; utilizing the HAS-160 algorithm to process the plaintext message to obtain correct output and error output; calculating difference values of the correct output and the error output; and analyzing the difference values, judging whether the HAS-160 algorithm is influenced by a differential fault attack, deriving the position of fault import, and analyzing validity of the position. The method provided by the invention can assess the capability of the HAS-160 algorithm of resisting the differential fault attack.
Owner:DONGHUA UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com