Security chip and attack detection circuit thereof
A technology of attack detection and detection circuit, applied in the direction of measuring electrical variables, measuring current/voltage, measuring devices, etc., can solve the problems of bypassing security measures, leaking confidential data, and failure of chip security operations.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0009] The invention will be described in detail below in conjunction with the accompanying drawings and embodiments.
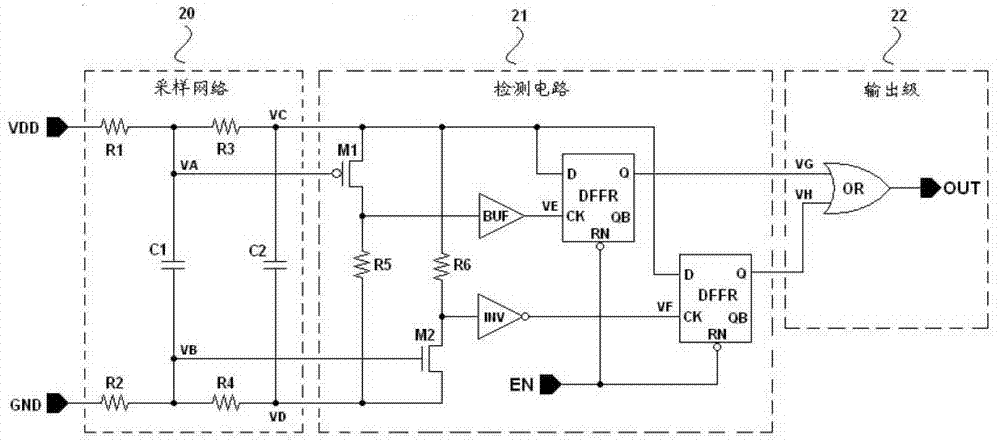
[0010] Such as figure 1 As shown, the specific implementation of the attack detection circuit of the present invention, the attack detection circuit is built into the security chip, which includes:
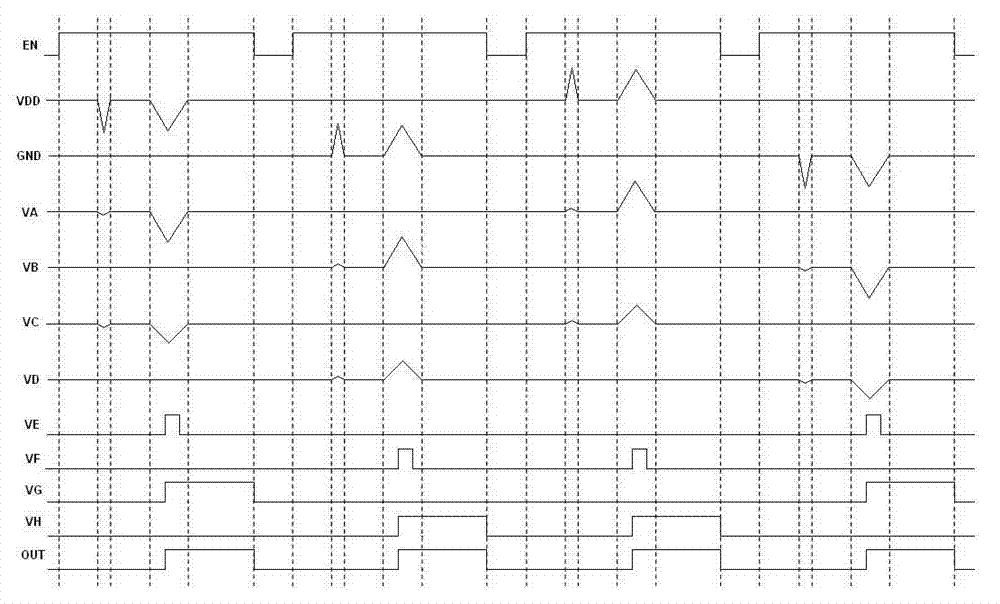
[0011] The sampling network 20 is used for sampling and filtering the voltage glitches on the power supply and the ground; and can distinguish the noise signal, jitter and voltage glitch attacks on the power supply and the ground;
[0012] The detection circuit 21 is used to detect the signal output by the sampling network;
[0013] The output stage 22 is used to process the output signal of the detection circuit and output the detection result.
[0014] Specifically, the sampling network 20, the detection circuit 21 and the output stage 22 may have the following structure:
[0015] The sampling network 20 includes: resistors R1, R2, R3, R4 and capacitors C1, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com