Comprehensive protection method for resisting side channel and fault attacks
A fault attack, channel technology, applied in the countermeasures of attack encryption mechanism, secure communication device, encryption device with shift register/memory, etc. Achieve the effect of perfect protection and flexible protection scheme
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] The specific implementation technology of the present invention will be introduced below in conjunction with the corresponding drawings and examples, but the scope of the present invention will not be limited in any form.
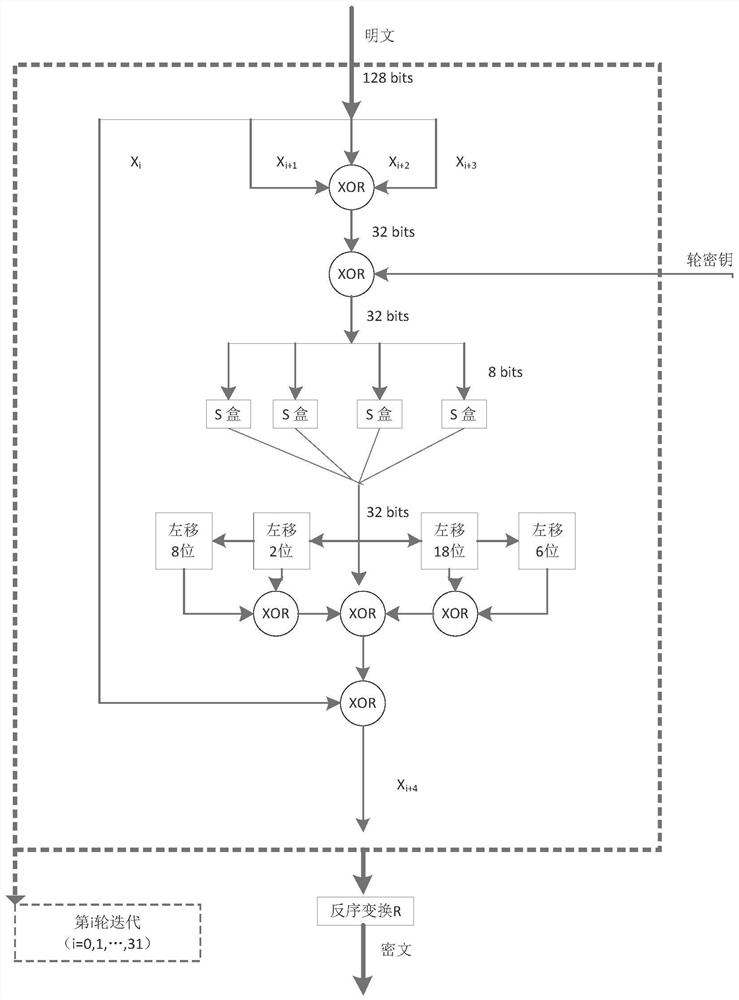
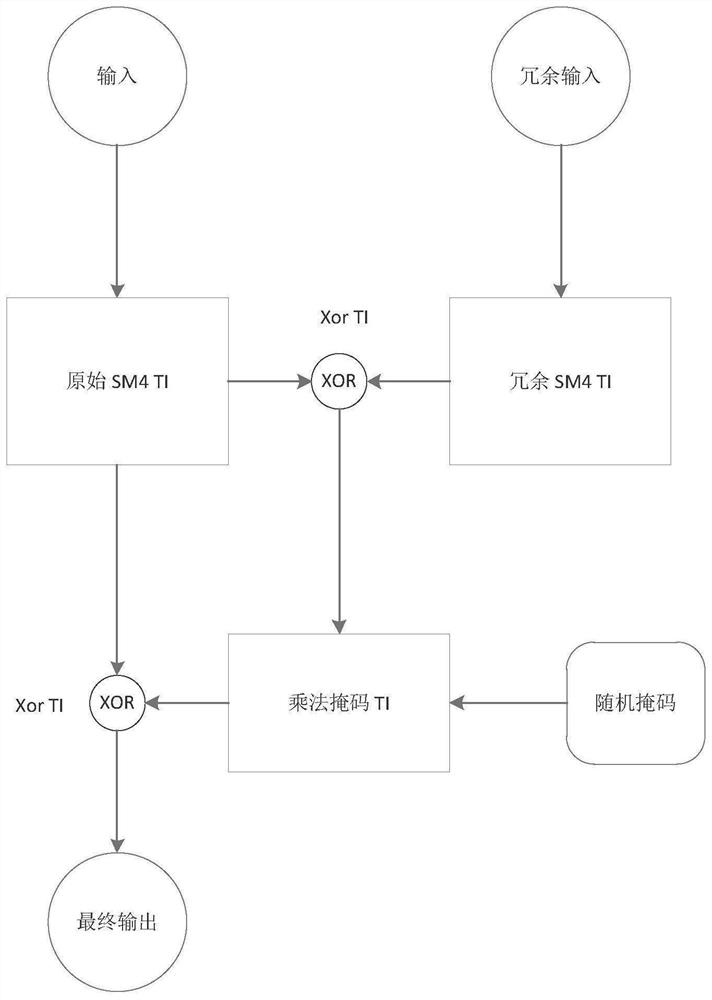
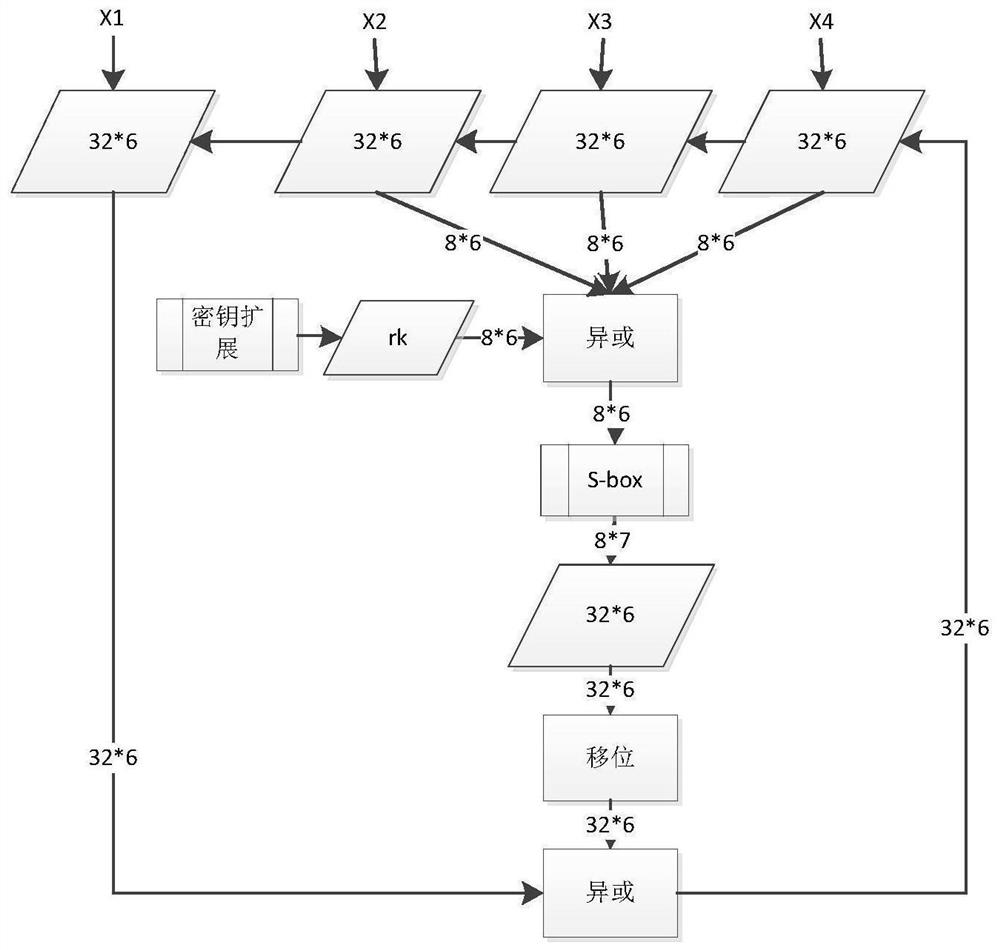
[0033] In this example, the SM4 algorithm is used as the target algorithm to implement a comprehensive protection scheme that can resist second-order side channel attacks.
[0034] The SM4 algorithm is the first commercial block cipher algorithm officially announced by my country. It is of great significance to the construction of the national cryptographic security system. It is a block cipher algorithm with a block length of 128 bits and a key length of 128 bits. Its encryption algorithm and decryption algorithm structure are the same, both adopt 32-round unbalanced Feistel iterative structure, but the encryption key and decryption key are reversed.
[0035] Such as figure 1 As shown, SM4 performs encryption operations in units of words, and the f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com