Safety modular exponentiation method for resisting energy analysis and fault attack
A technology of error attack and energy analysis, applied in the field of secure execution of public key cryptosystem, can solve the problem of low security and achieve the effect of improving algorithm performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] Embodiments of the present invention will be described in further detail below in conjunction with the accompanying drawings, but the present embodiments are not intended to limit the present invention, and any similar structures, methods and similar changes of the present invention should be included in the scope of protection of the present invention.
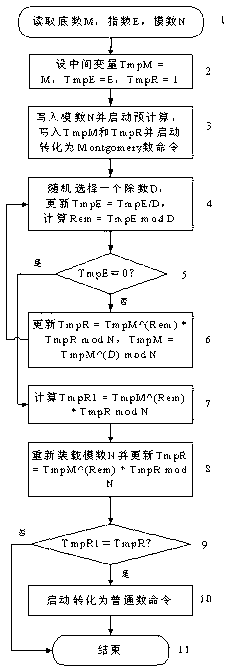
[0041] Such as figure 1 As shown, the present invention discloses a method for calculating a safe modular exponentiation against energy analysis and error attacks, the method comprising the following steps:
[0042] Step 1. Read the base M, the exponent E, and the modulus N;
[0043] Step 2, set the intermediate variable TmpM = M, TmpE = E, TmpR = 1;
[0044] Step 3. Corresponding hardware is set to realize this step 3. The hardware includes 5 SRAMs of 64×32 bit size, named as A, B, N, R, T SRAM respectively;
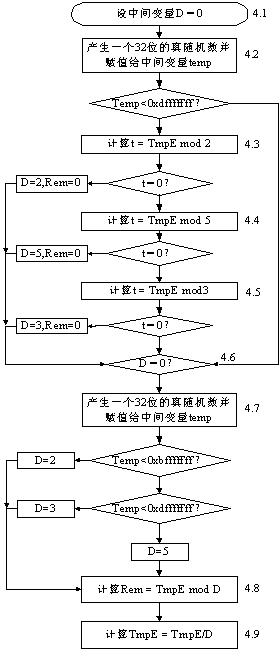
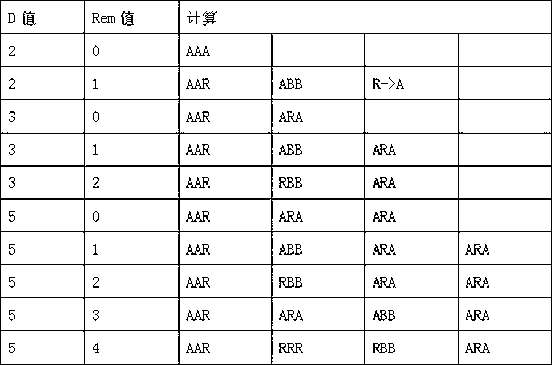
[0045] Write modulus N to N SRAM and start precomputation (its purpose is to calculate parameters Nacc and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com