RSA public key generation apparatus, RSA decryption apparatus, and RSA signature apparatus
A technology of public key and generation device, applied in the field of information security, can solve problems such as retrieval and error, and achieve the effect of reducing the required time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 2 Embodiment approach
[0233] The following describes the RSA secret communication system 20 as another embodiment of the present invention.
[0234] (1) Configuration of the RSA secret communication system 20
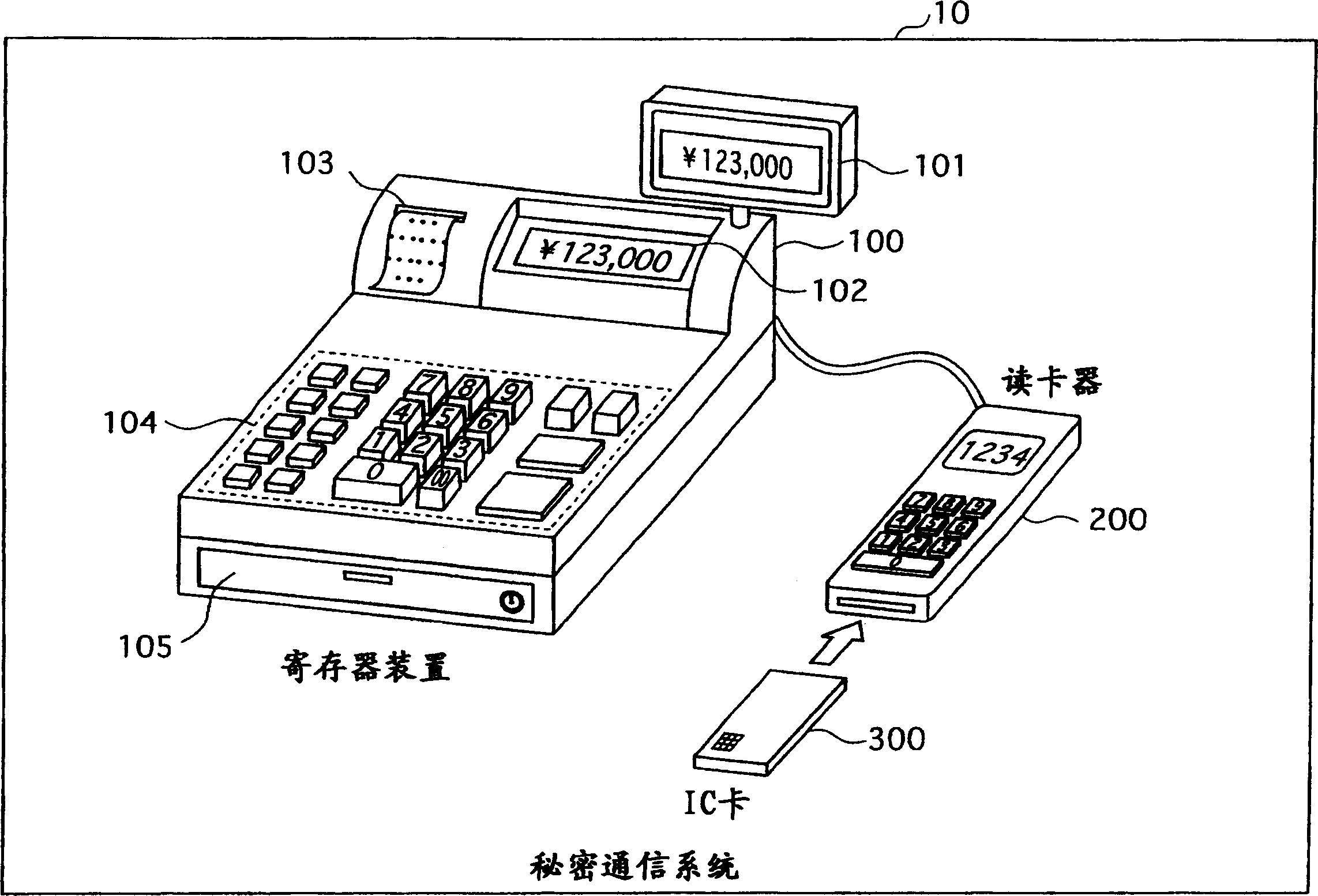
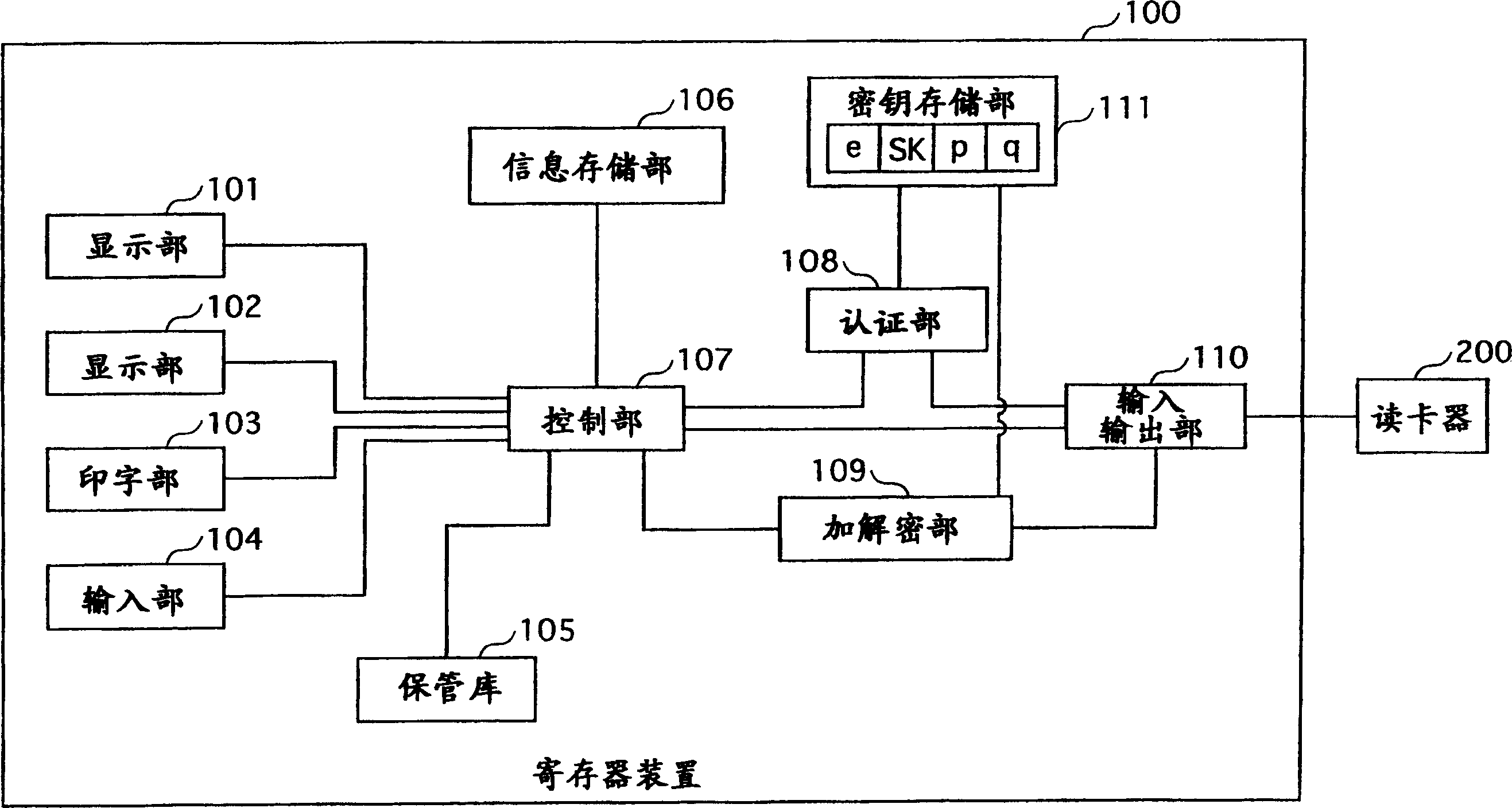
[0235] RSA secret communication system 20 such as Figure 10 As shown, the structure includes an RSA encryption device 500 , an RSA decryption device 400 and a memory card 600 , and the RSA encryption device 500 and the RSA decryption device 400 are connected via a network 50 .
[0236] In the key generation under the RSA encryption method, for two prime numbers p and prime numbers q with different sizes, the number n=p×q is generated, and is mutually prime with p-1 and the least common multiple of q-1, 1cm, and A public key e satisfying p-1>e. In addition, the inverse of the public key e is generated in the remainder body whose divisor is the least common multiple of 1cm, and the generated inverse becomes the secret key d. The public key e thus generated is notified to the RSA encryption...
no. 3 Embodiment approach
[0269] The RSA secret communication system 30 which is a modified example of the RSA secret communication system 20 of the second embodiment will be described below.
[0270] (1) Configuration of the RSA secret communication system 30
[0271] The RSA secret communication system 30 has a configuration similar to that of the RSA secret communication system 20 . Here, the difference from the RSA secret communication system 20 will be mainly explained.
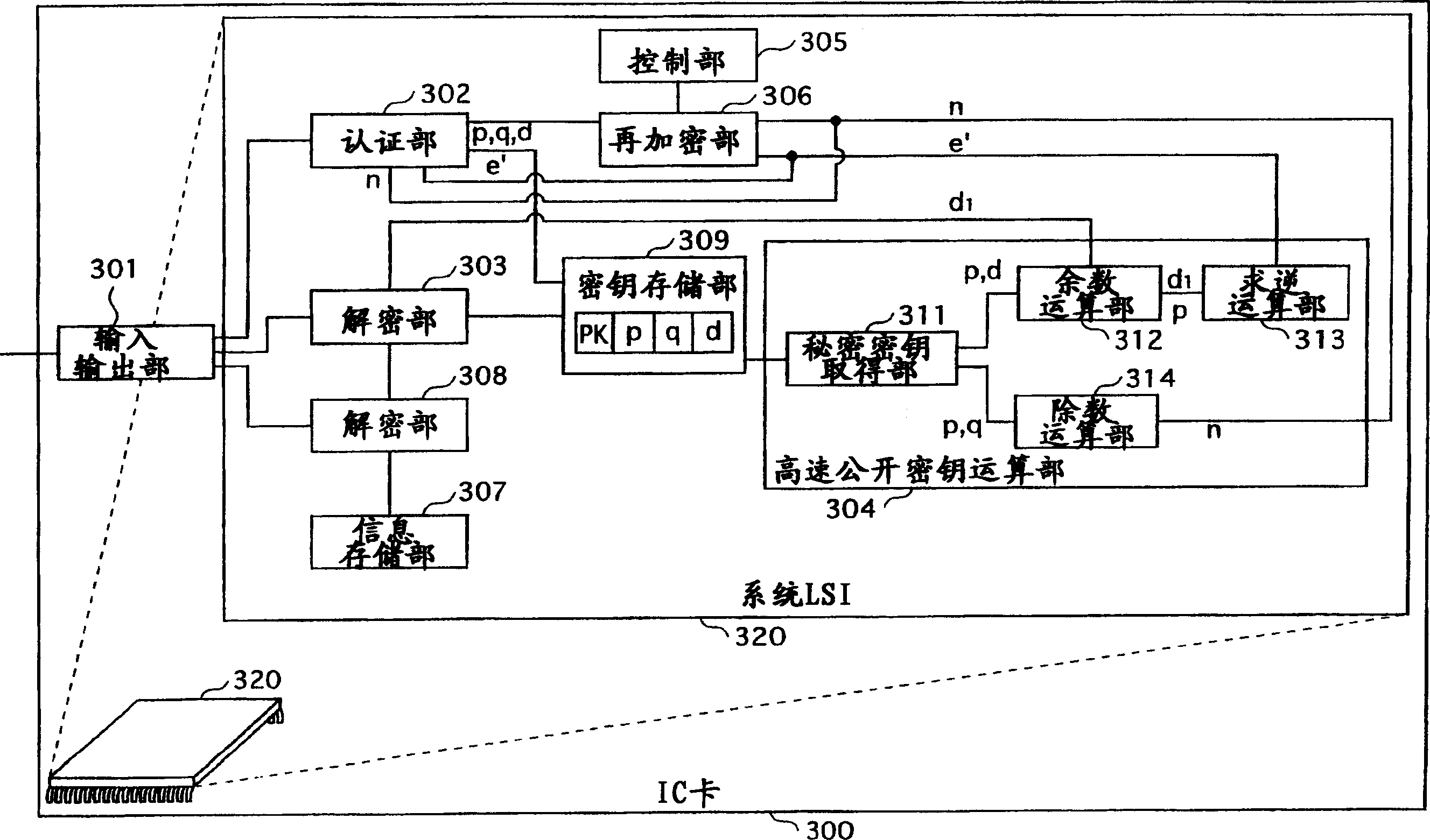
[0272] RSA secret communication system 30 such as Figure 12 As shown, its composition includes an RSA encryption device 500 , an RSA decryption device 400 b , a CRT information generation device 700 , and a memory card 600 b. The RSA encryption device 500 and the RSA decryption device 400 are connected via a network 50 .
[0273] The memory card 600b is a removable semiconductor memory similar to the memory card 600, and stores in advance a secret key d for decryption processing, a prime number p, and a prime number q.
[027...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com