Novel fault attack method aiming at Advanced Encryption Standard (AES-128) algorithm
A technology of fault attack and algorithm, applied in encryption device with shift register/memory, key distribution, can solve problems such as strictness, attack, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0066] The present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
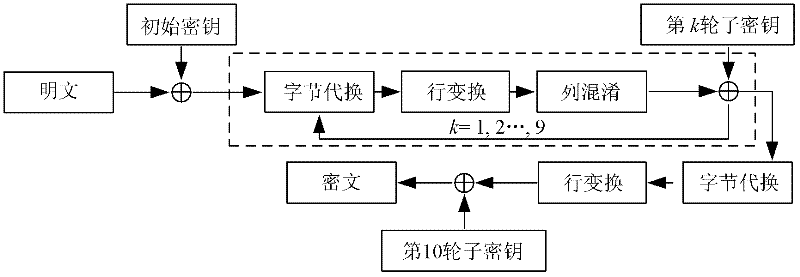
[0067] A kind of novel fault attack method aimed at AES-128 algorithm that the present embodiment proposes, it mainly comprises the following steps:
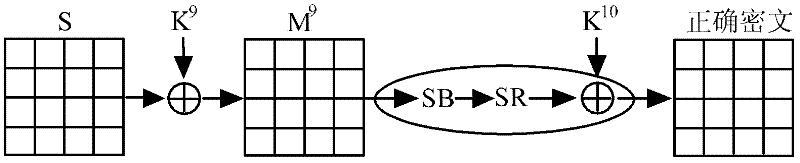
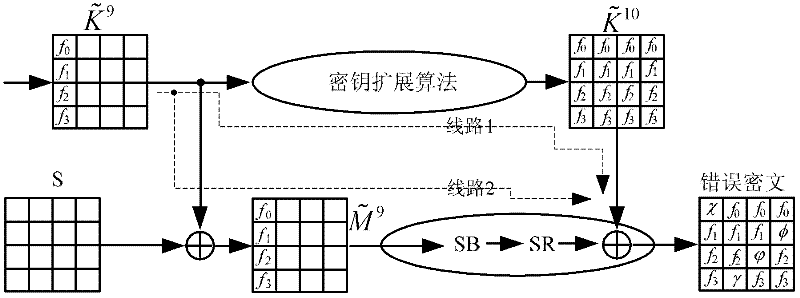
[0068] 1) The attacker randomly selects a plaintext, obtains the correct ciphertext of the plaintext under the action of the initial key, and marks the correct ciphertext as C, such as figure 2 as shown, C = SR ( SB ( S ⊕ K 9 ) ) ⊕ K 10 , Among them, S represents the state after the ninth round of column obfuscation in the AES-128 encryption algorithm, and K 9 Indicates the subkey required for the ninth round of key plus operation i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com