Method and device for detecting and disposing abnormal traffic attack
A technology for abnormal traffic and attack detection, applied to electrical components, transmission systems, etc., can solve problems such as low precision, complex implementation, and insufficient real-time, and achieve the effects of low complexity, high recognition accuracy, and fast processing speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] In order to make the above-mentioned features and advantages of the present invention more comprehensible, the following specific embodiments are described in detail in conjunction with the accompanying drawings.
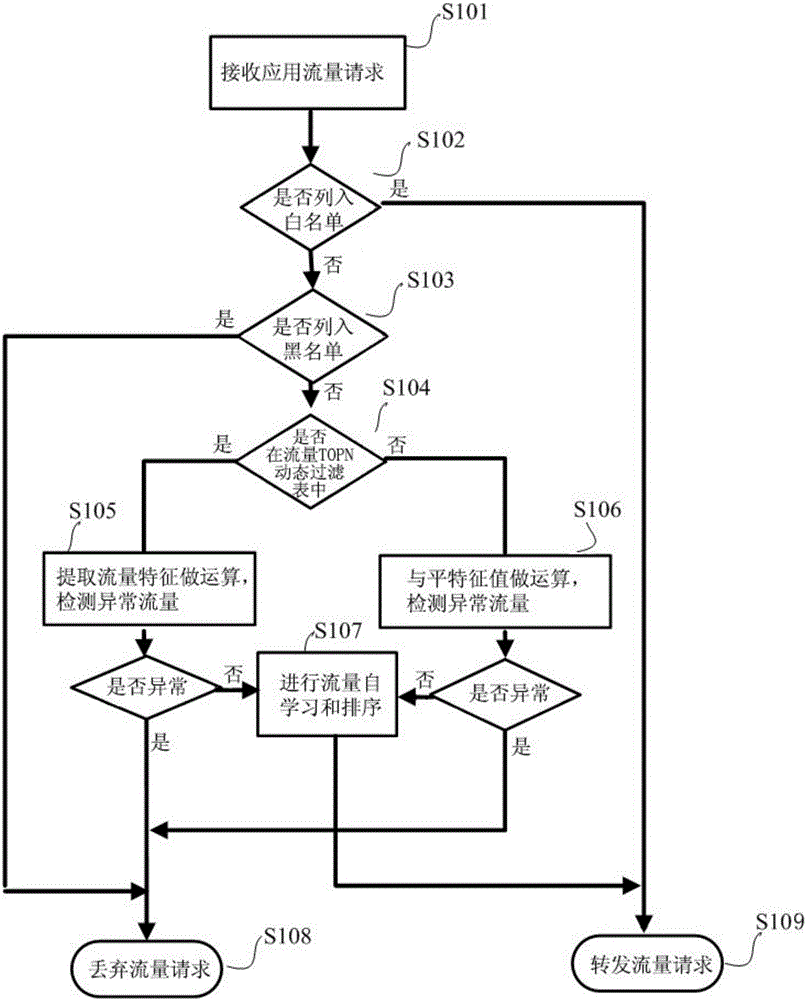
[0035] This embodiment provides a method for detecting and handling abnormal traffic attacks, such as figure 1 As shown, the detailed steps are as follows:
[0036] Step S101: Monitor the access request of the incoming IP.
[0037] Step S102: Determine whether the IP address is in the system whitelist, if yes, proceed to step S109 to directly forward the request; if not, proceed to step S103.
[0038] Step S103: Determine whether the IP address is in the system blacklist, if yes, go to step S108 and discard the traffic directly; if not, go to step S104.
[0039] Step S104: Determine whether the source address IP is in the TOPN ranking of the traffic TOPN dynamic filtering table.
[0040] The refinement of this step is as follows:
[0041] Step 1: Obtain ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com