Method for technically controlling secure access to embedded system memory
A security access control, embedded system technology, applied in the protection of internal/peripheral computer components, instruments, electrical and digital data processing, etc., can solve problems such as unpredictable program running time, I/O blocking time, etc., to solve memory access problems Security Issues, Ensuring Legal Access, and Effectiveness of Secure Access Mechanisms for Reliable System Memory
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] In order to make it easy to understand the technical means, creative features, objectives and effects achieved by the present invention, the present invention will be further explained below in conjunction with specific drawings.
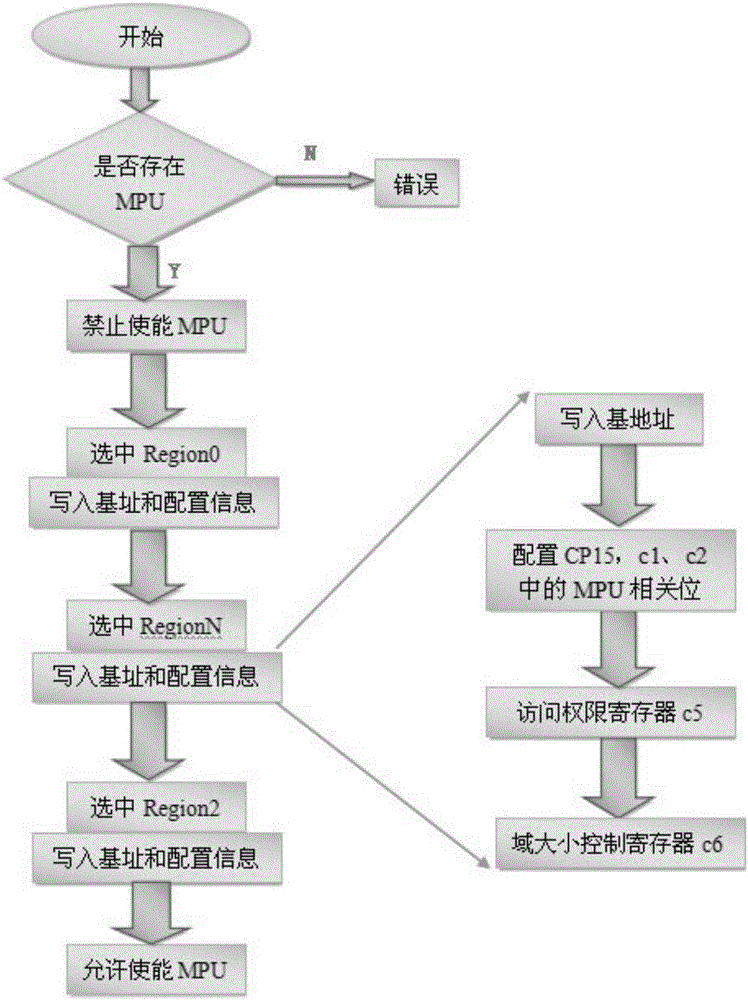
[0032] Such as Figure 8 As shown, a technical implementation method for memory security access control of an embedded system includes the following steps:
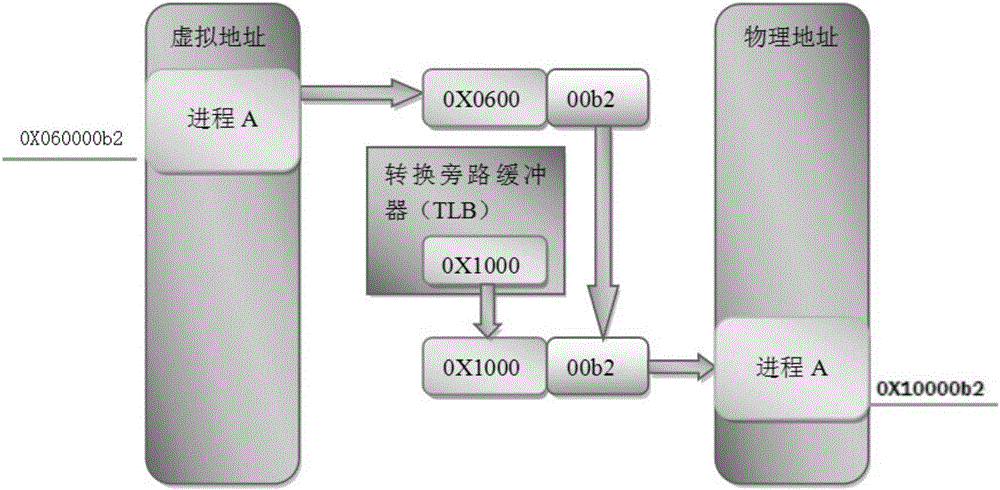
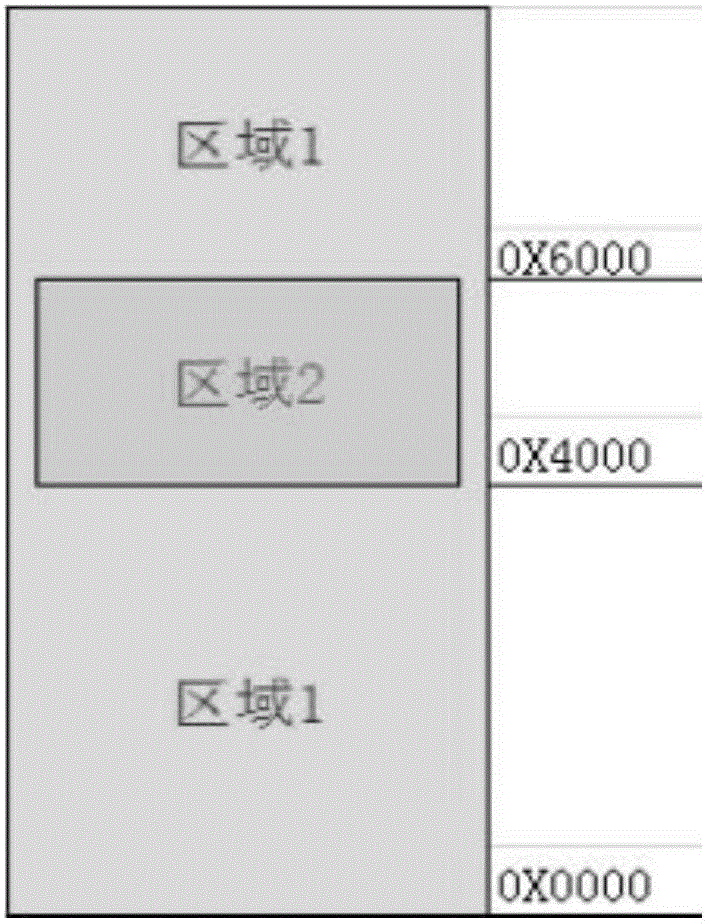
[0033] 1) System initialization design of memory security access mechanism 1: Introduce the MPU memory protection unit in the embedded system, and assign different levels of regional attributes to the memory area, including background domain, system shared domain, running task domain, sleep task domain and Device I / O domain, its priority is background domain=sleep task domain figure 2 Shown.
[0034] In the present invention, the system uses area as the main concept of system protection. A region is a collection of storage space attributes and also represents a logical storage space with spe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com