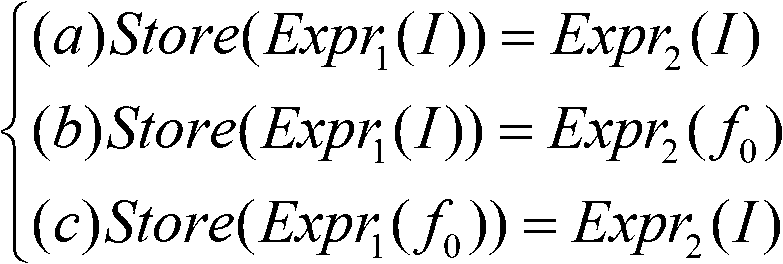Patents
Literature
32 results about "Single assignment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
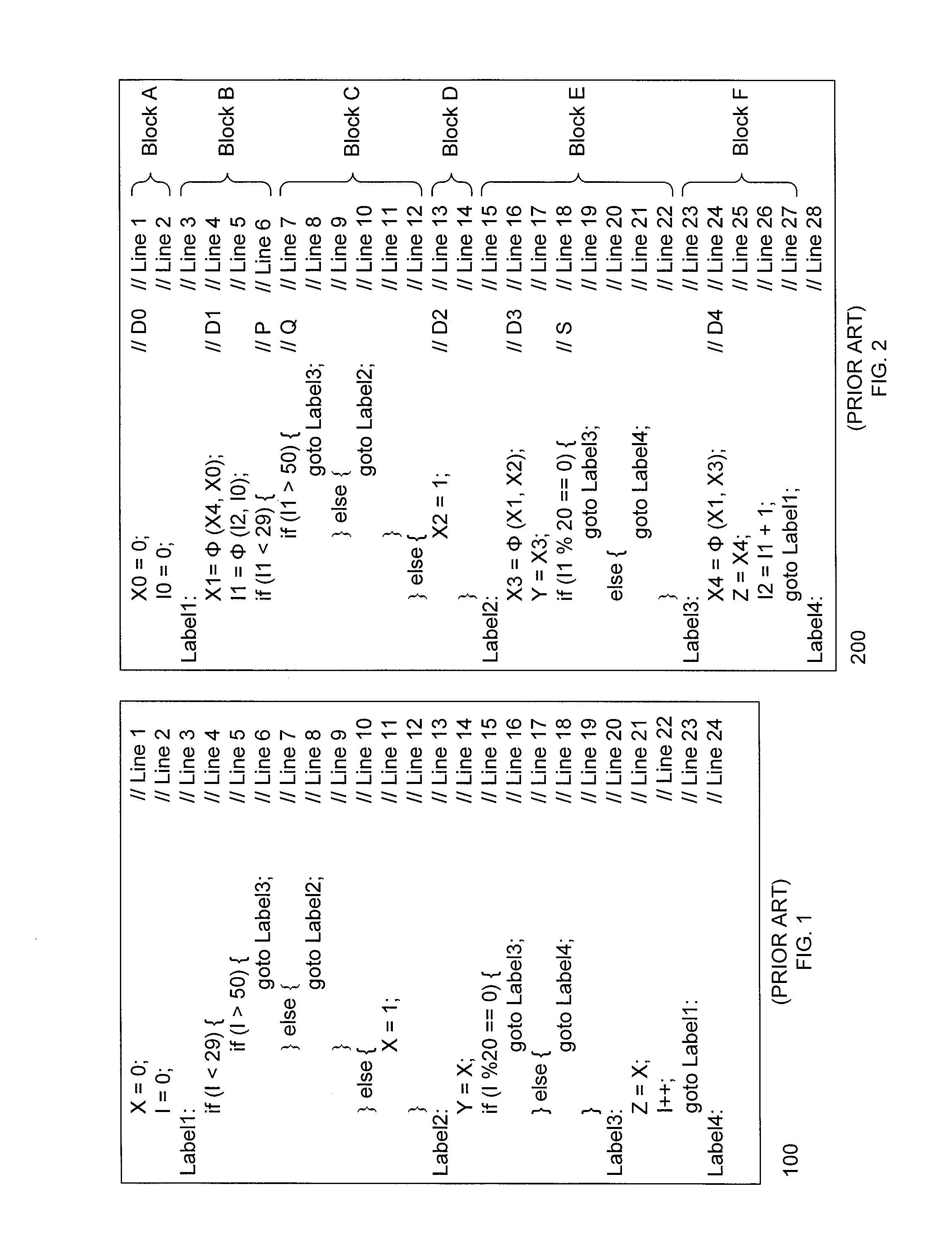
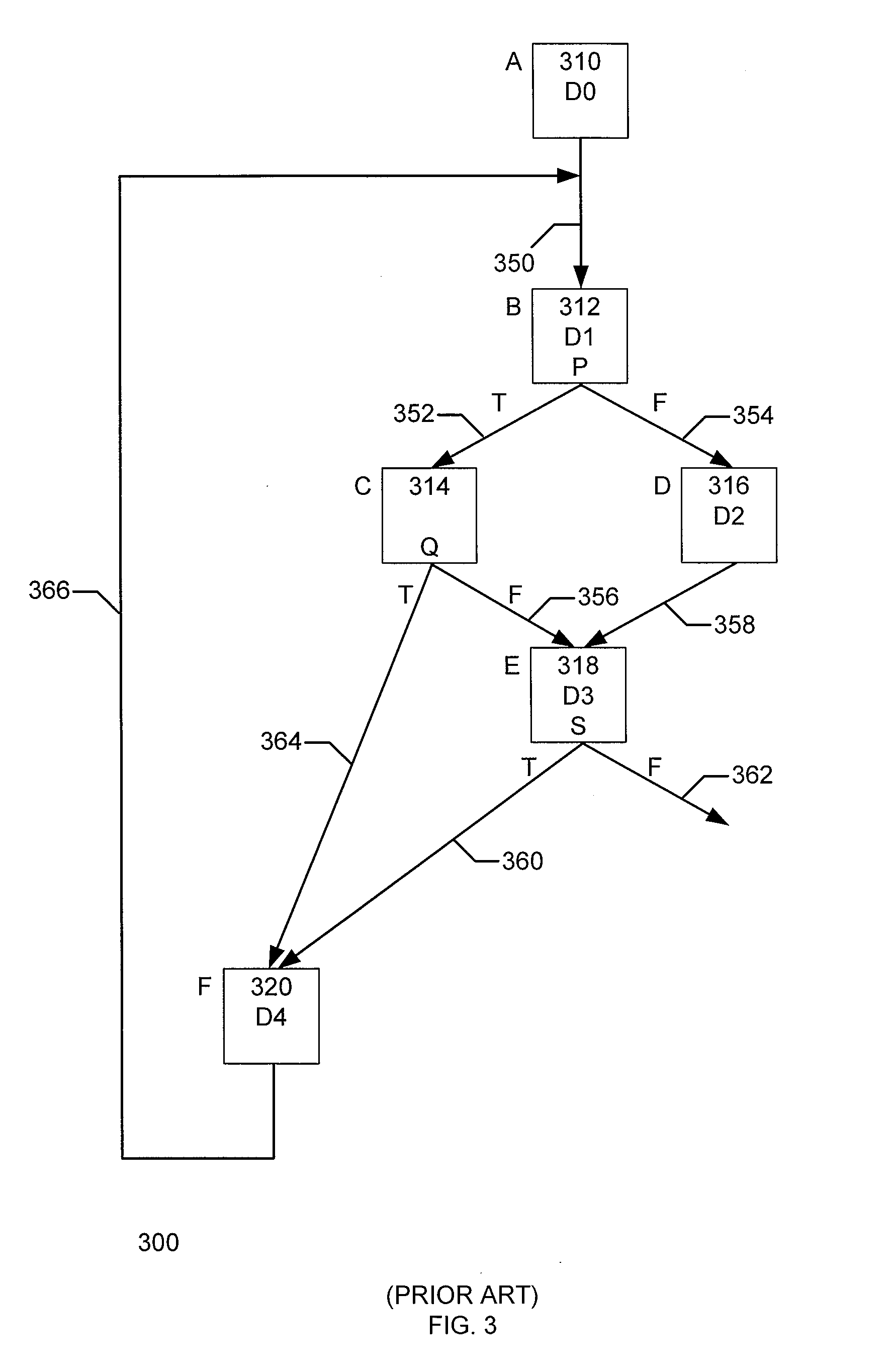
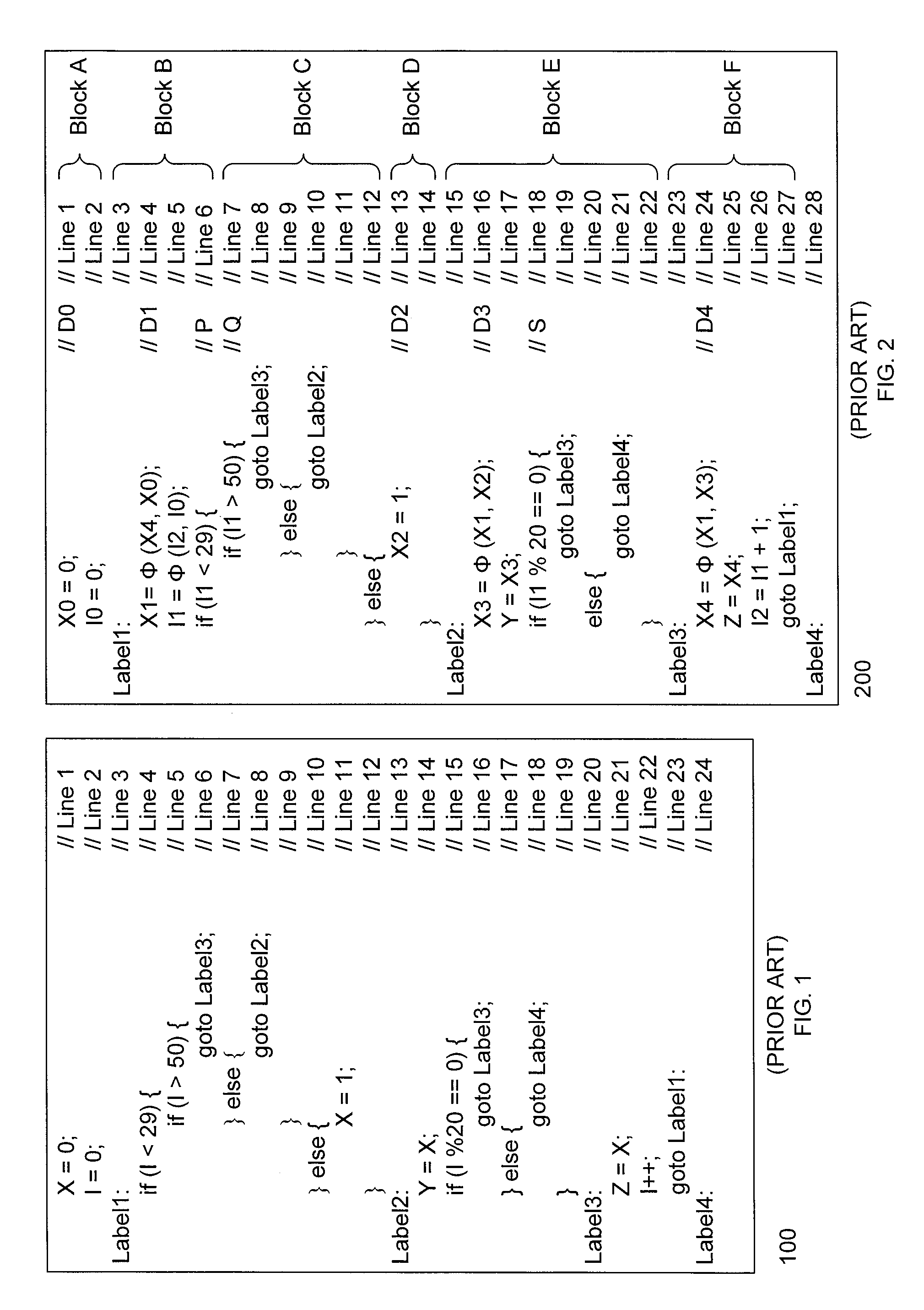
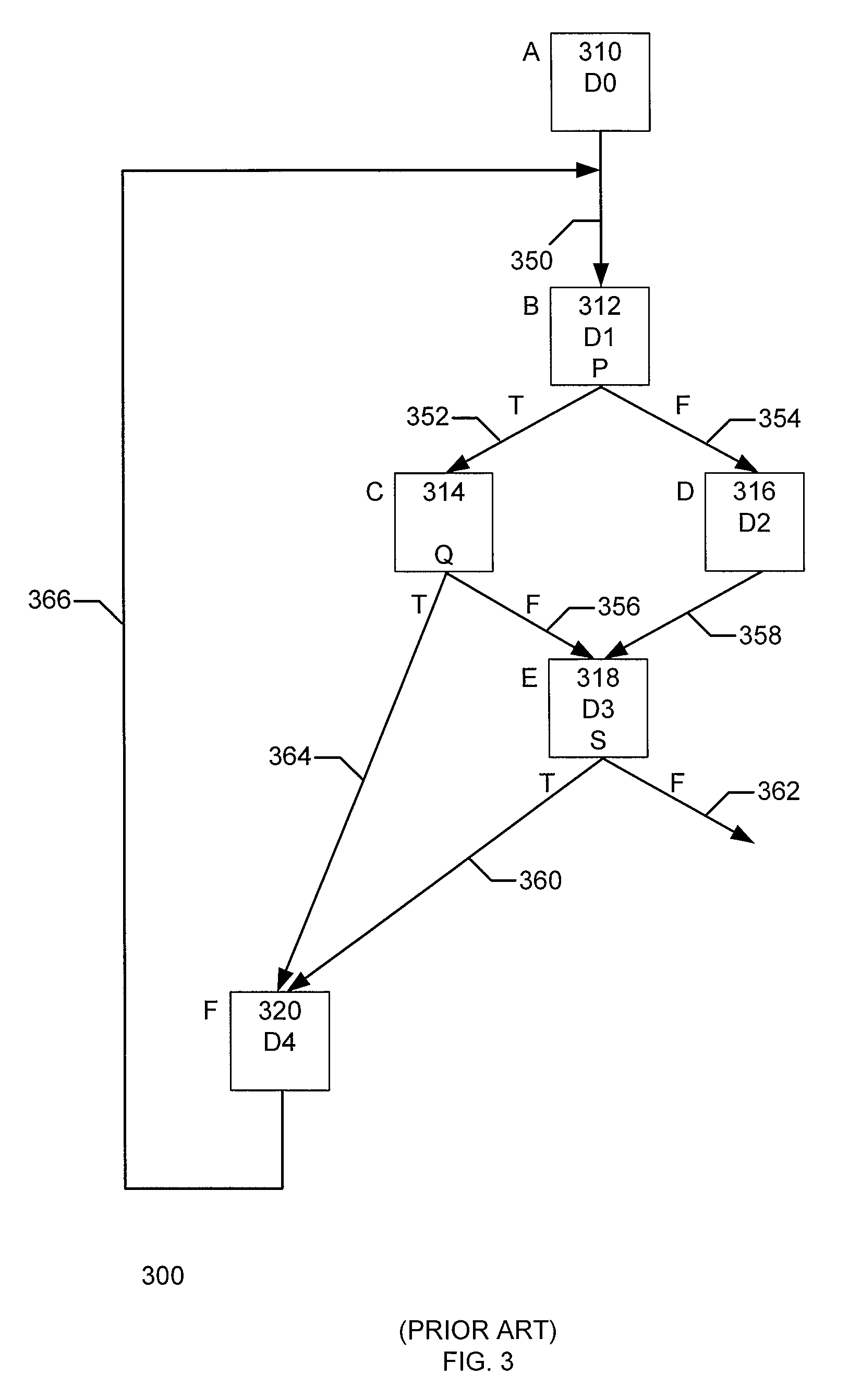
Single assignment. (programming) A property of variables in a functional language. If a variable is only assigned a value once then an instance of that variable is thereafter semantically equivalent to the value.
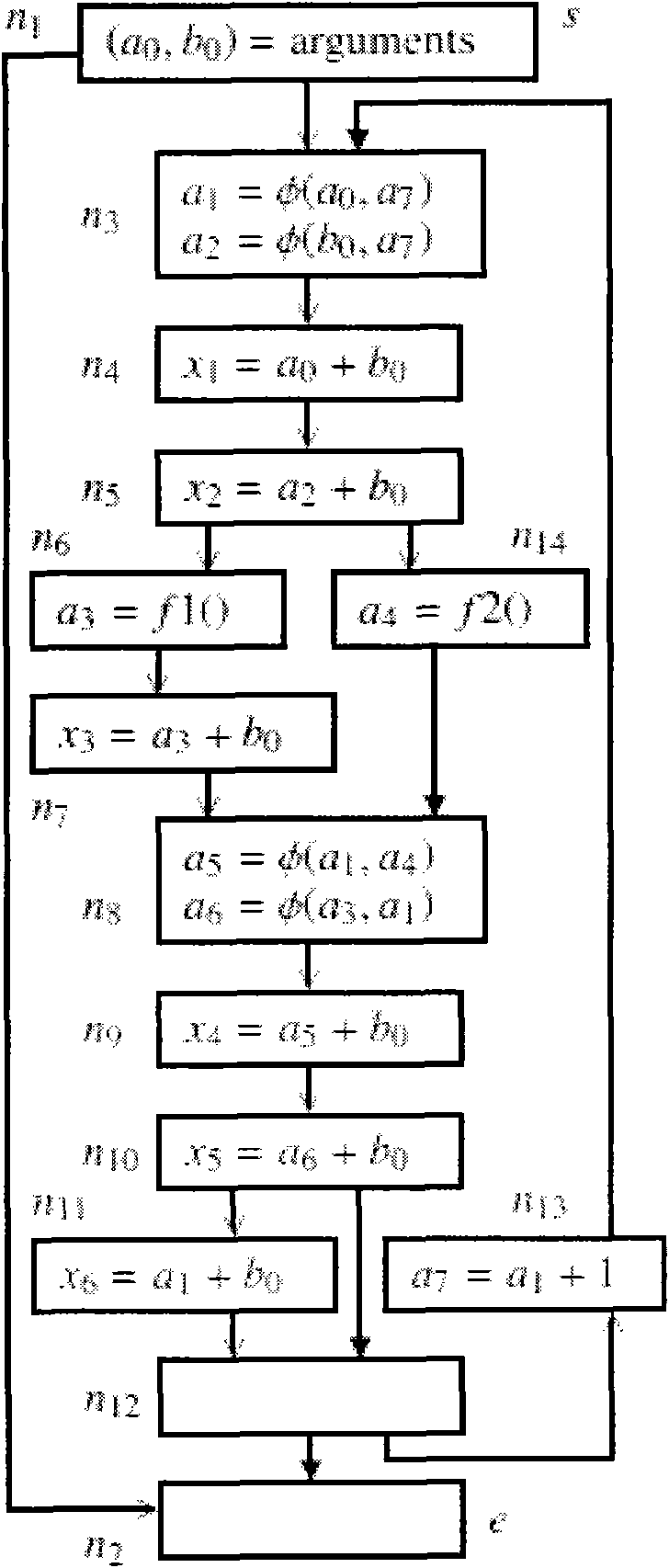
Highly scalable parallel static single assignment for dynamic optimization on many core architectures
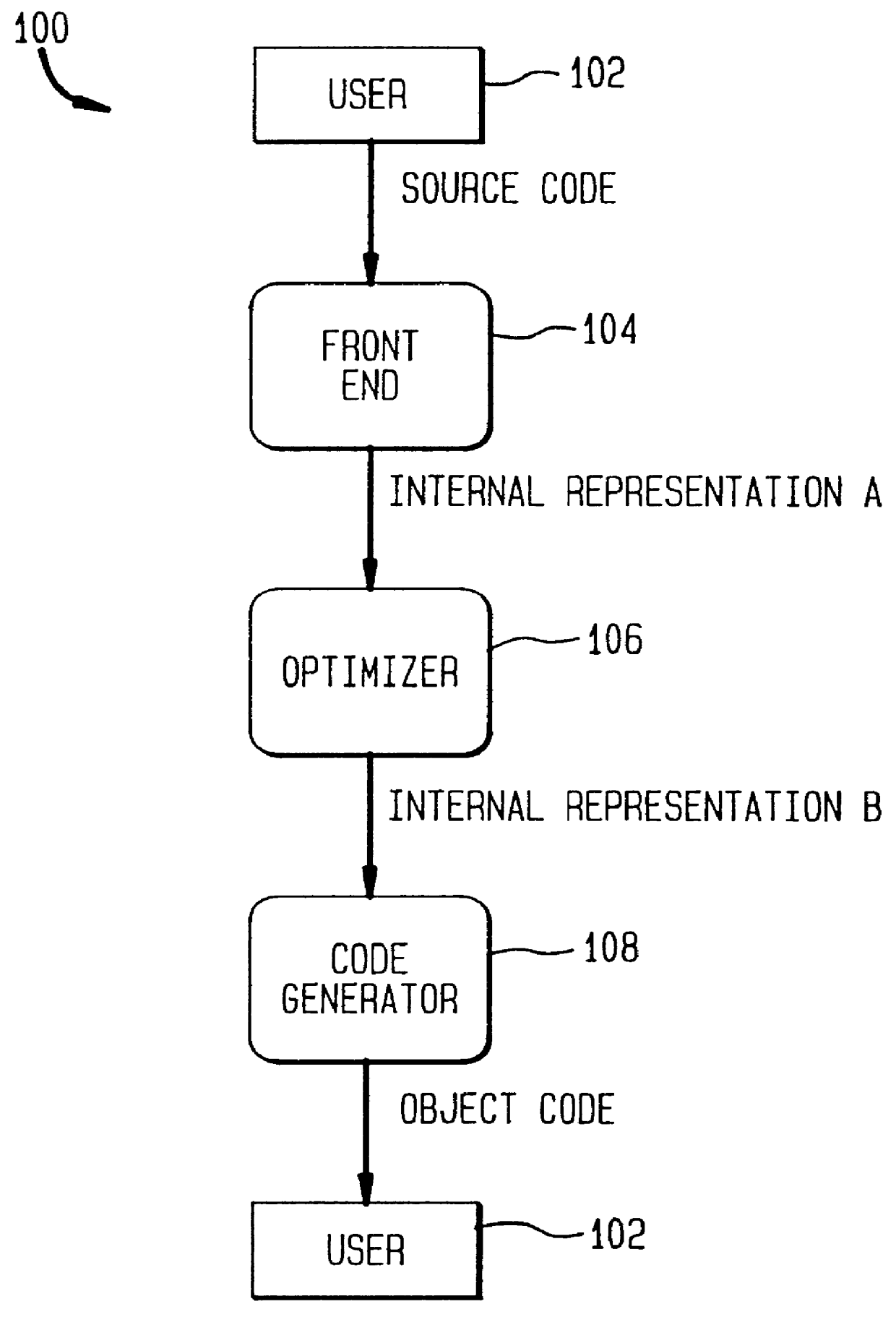
A method, system, and computer readable medium for converting a series of computer executable instructions in control flow graph form into an intermediate representation, of a type similar to Static Single Assignment (SSA), used in the compiler arts. The indeterminate representation may facilitate compilation optimizations such as constant propagation, sparse conditional constant propagation, dead code elimination, global value numbering, partial redundancy elimination, strength reduction, and register allocation. The method, system, and computer readable medium are capable of operating on the control flow graph to construct an SSA representation in parallel, thus exploiting recent advances in multi-core processing and massively parallel computing systems. Other embodiments may be employed, and other embodiments are described and claimed.
Owner:INTEL CORP
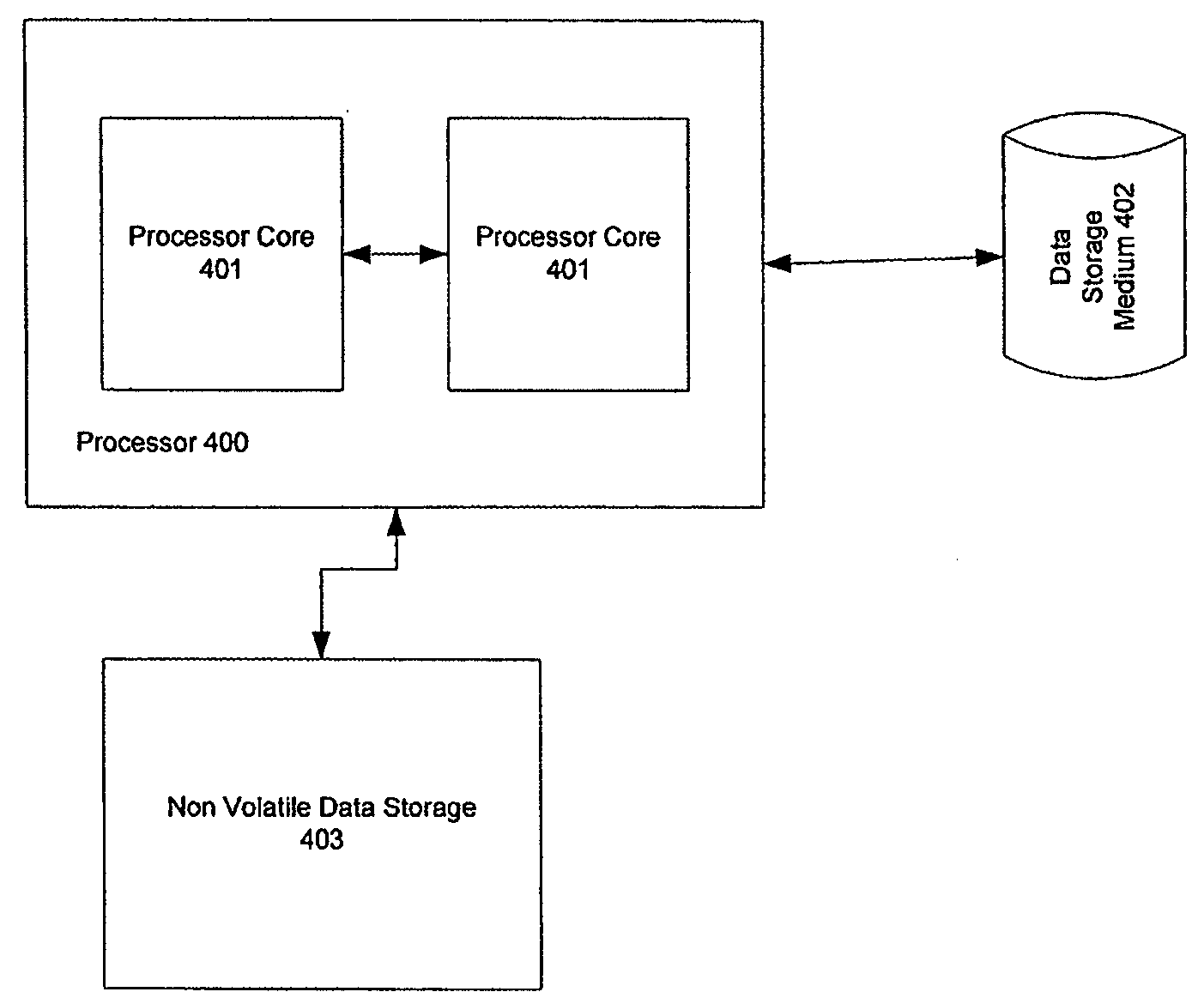
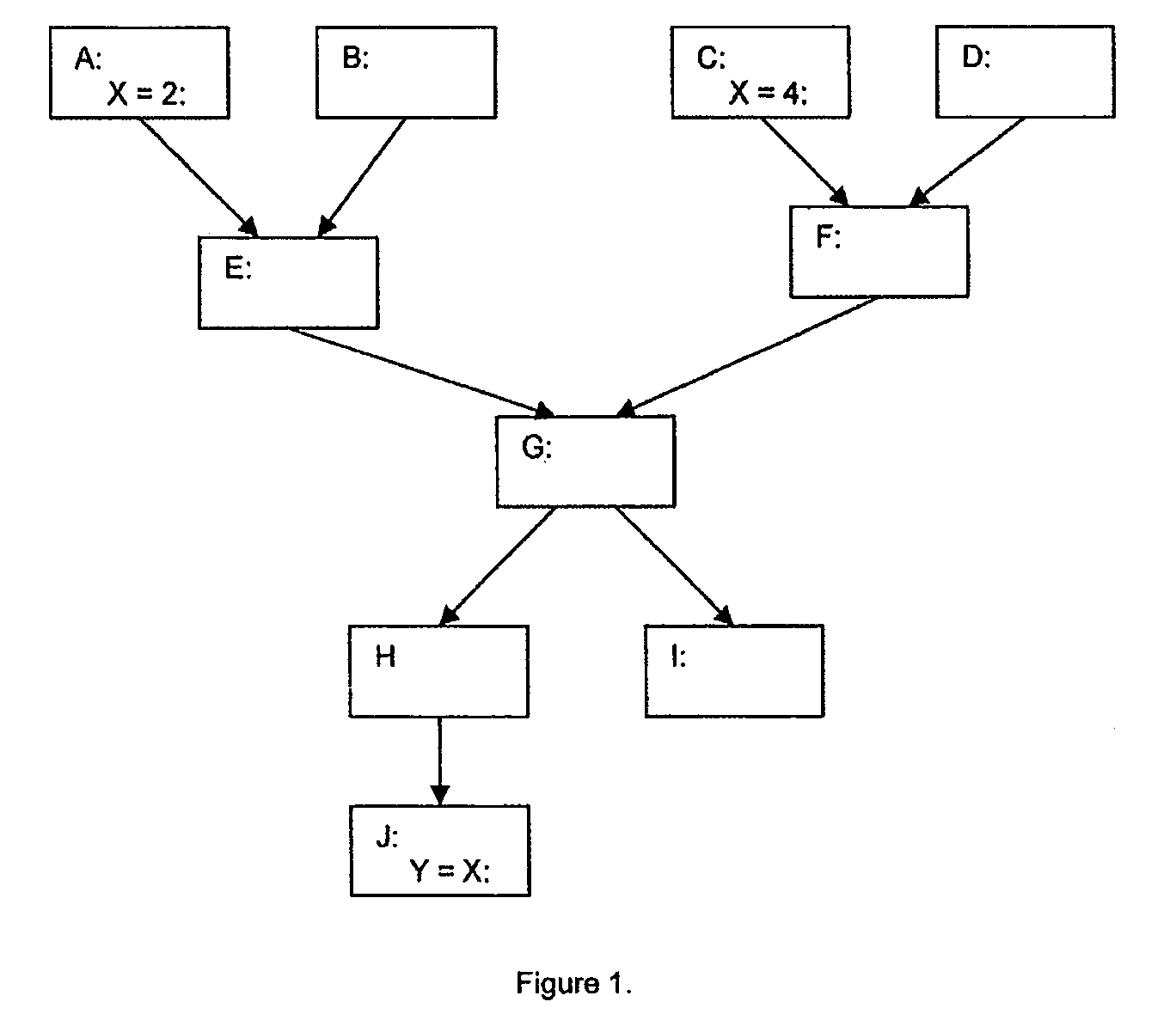
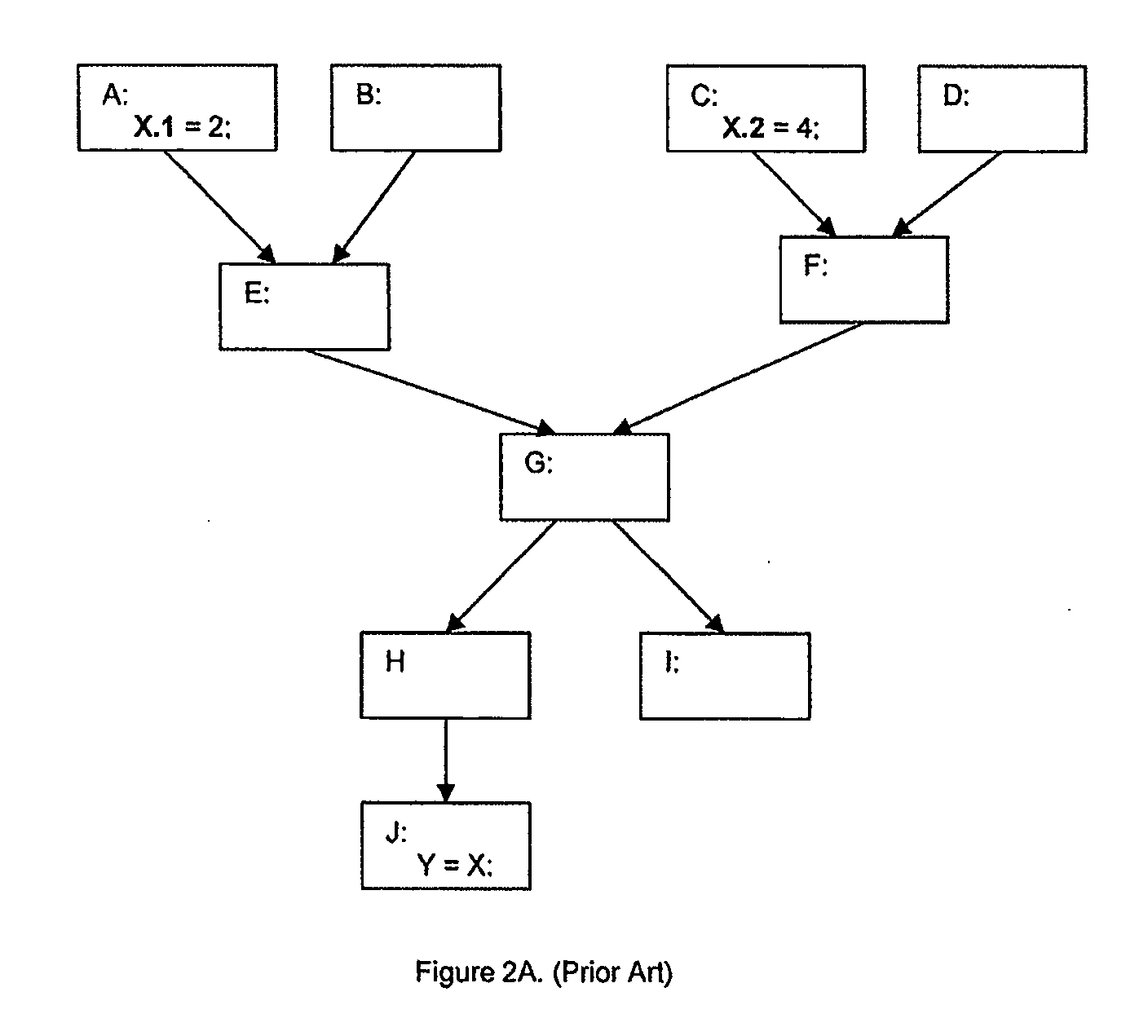
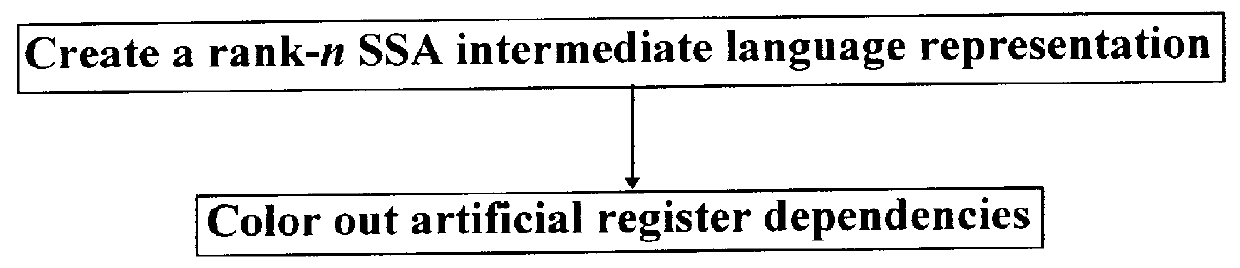
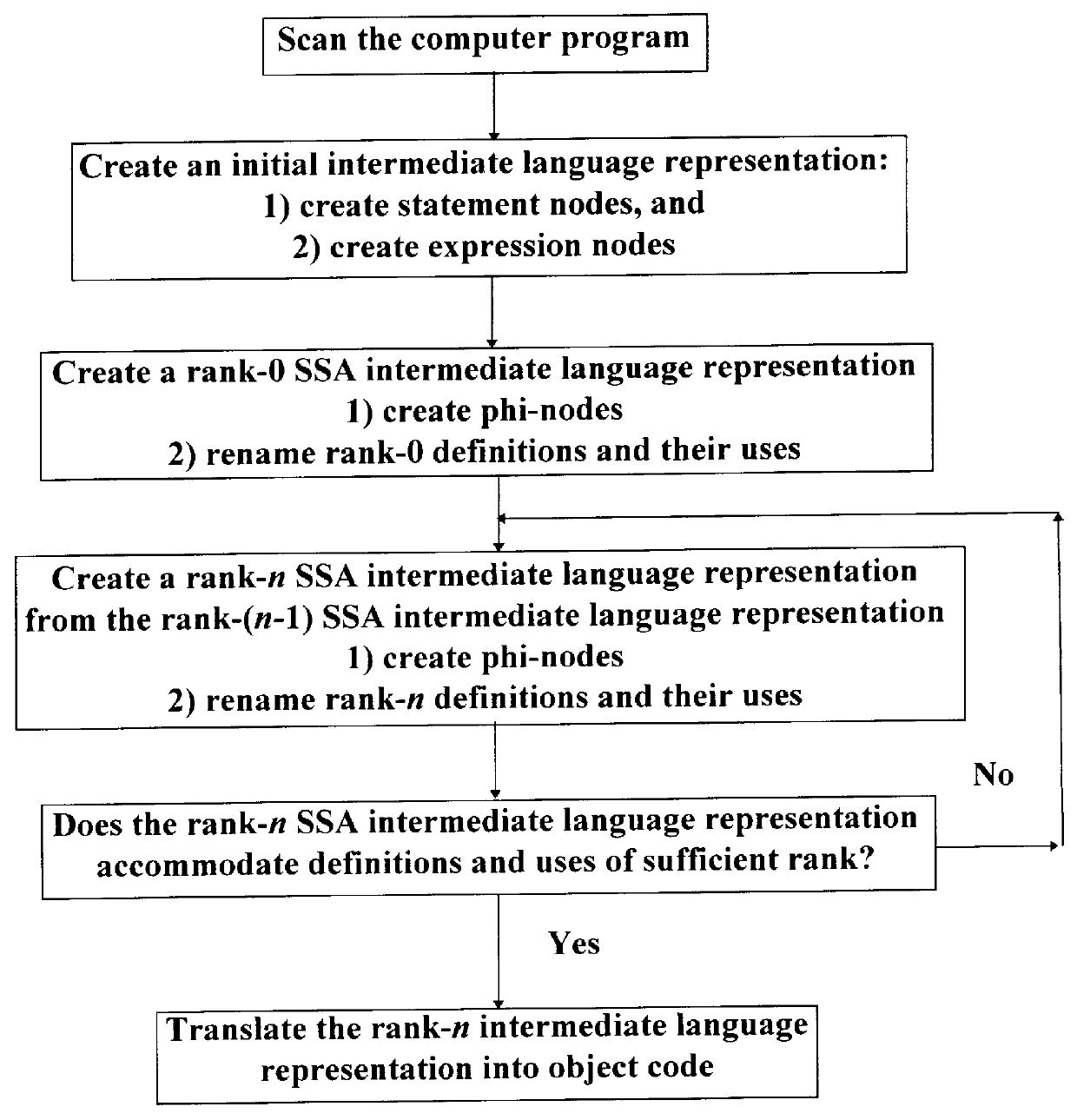
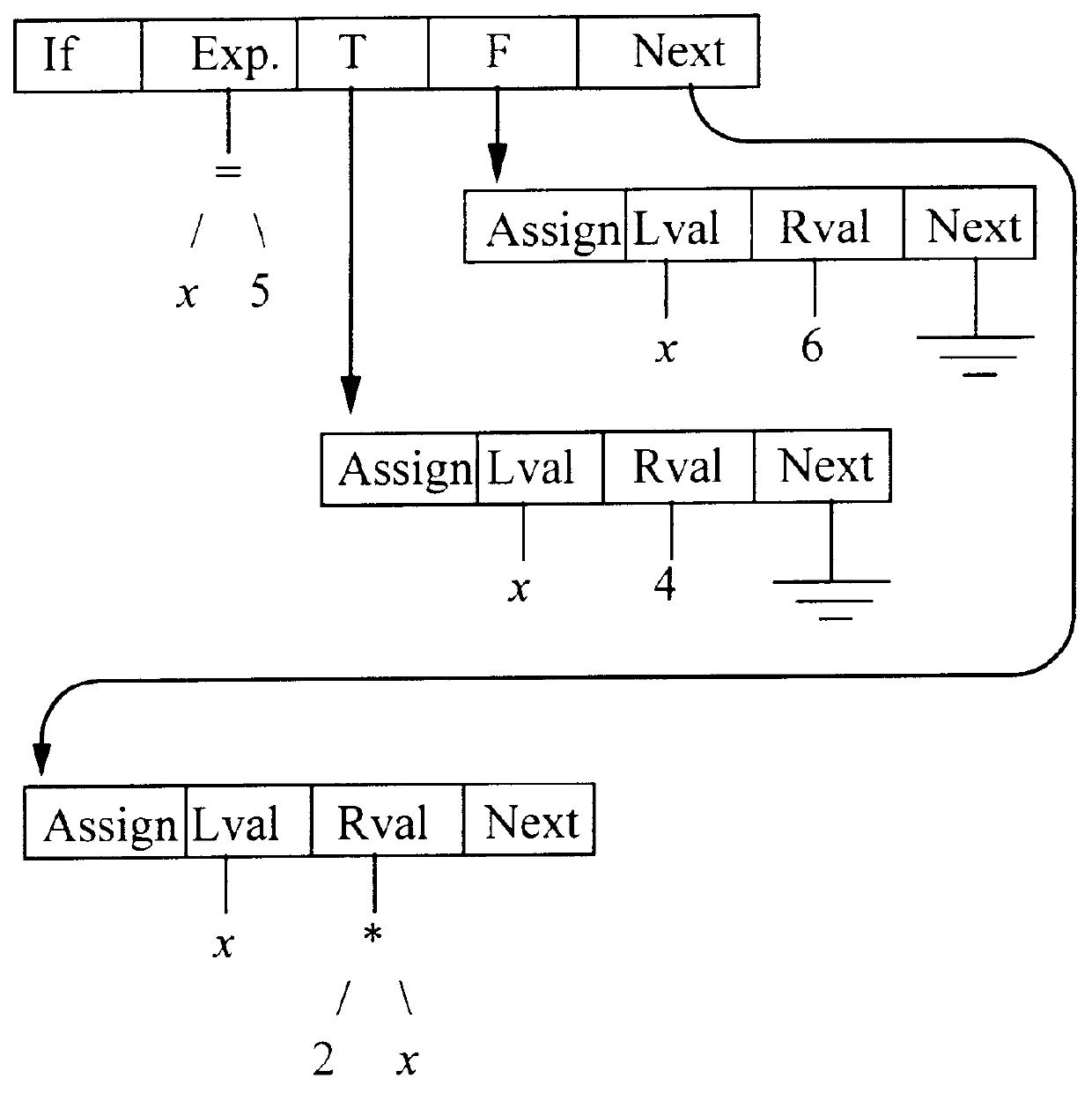
Method for using static single assignment to color out artificial register dependencies
The invention is a method of using static single assignment intermediate language to color out artificial register dependencies while compiling at least a portion of a computer program. The method comprises creating a rank-n SSA intermediate language representation of the computer program, wherein n is a positive integer greater than 1; and coloring out the artificial register dependencies.
Owner:MICRON TECH INC
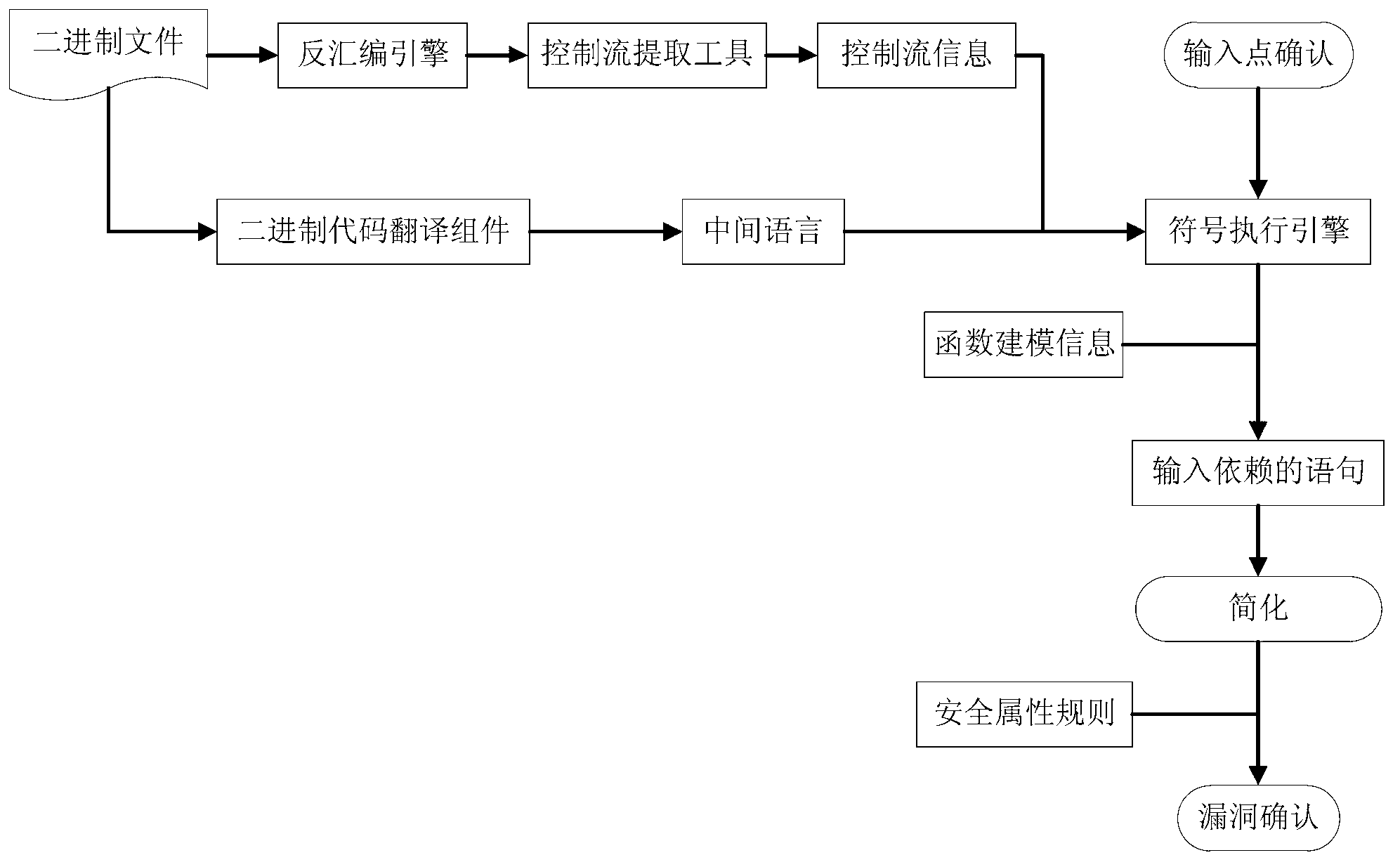
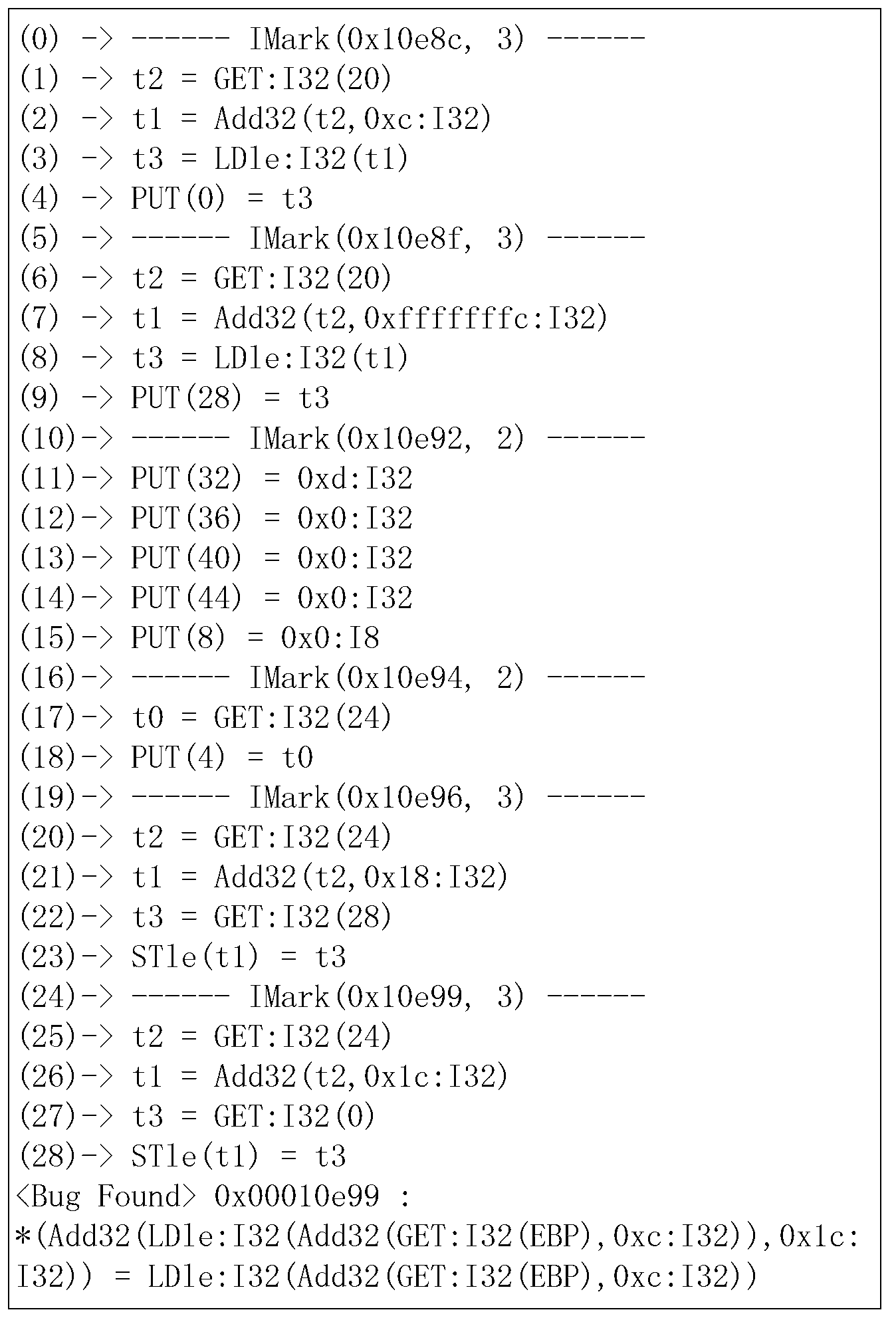
Method for binary code vulnerability discovery on basis of simple symbolic execution
The invention discloses a method for binary code vulnerability discovery on the basis of simple symbolic execution. The method comprises five steps that: firstly, binary codes are translated into an intermediate language with a static single assignment through a binary code translation component; and then, a disassembling engine is used to disassemble the binary codes, the control flow information of the binary codes is extracted, static symbolic execution is carried out in the intermediate language on the basis of the control flow information, an entrance point needs to be determined during the symbolic execution process, an input vector is converted into a symbol, and a called function is modeled. After the symbolic execution process is completed, the statement assembly of the intermediate language which depends on the input vector can be obtained, the statements of an assembly are simplified, and a vulnerability discovery confirmation report is generated after security attribute rules are used to confirm.
Owner:BEIHANG UNIV
System and method to efficiently represent aliases and indirect memory operations in static single assignment form during compilation
InactiveUS6131189ALow costSoftware engineeringProgram controlGlobal value numberingTheoretical computer science
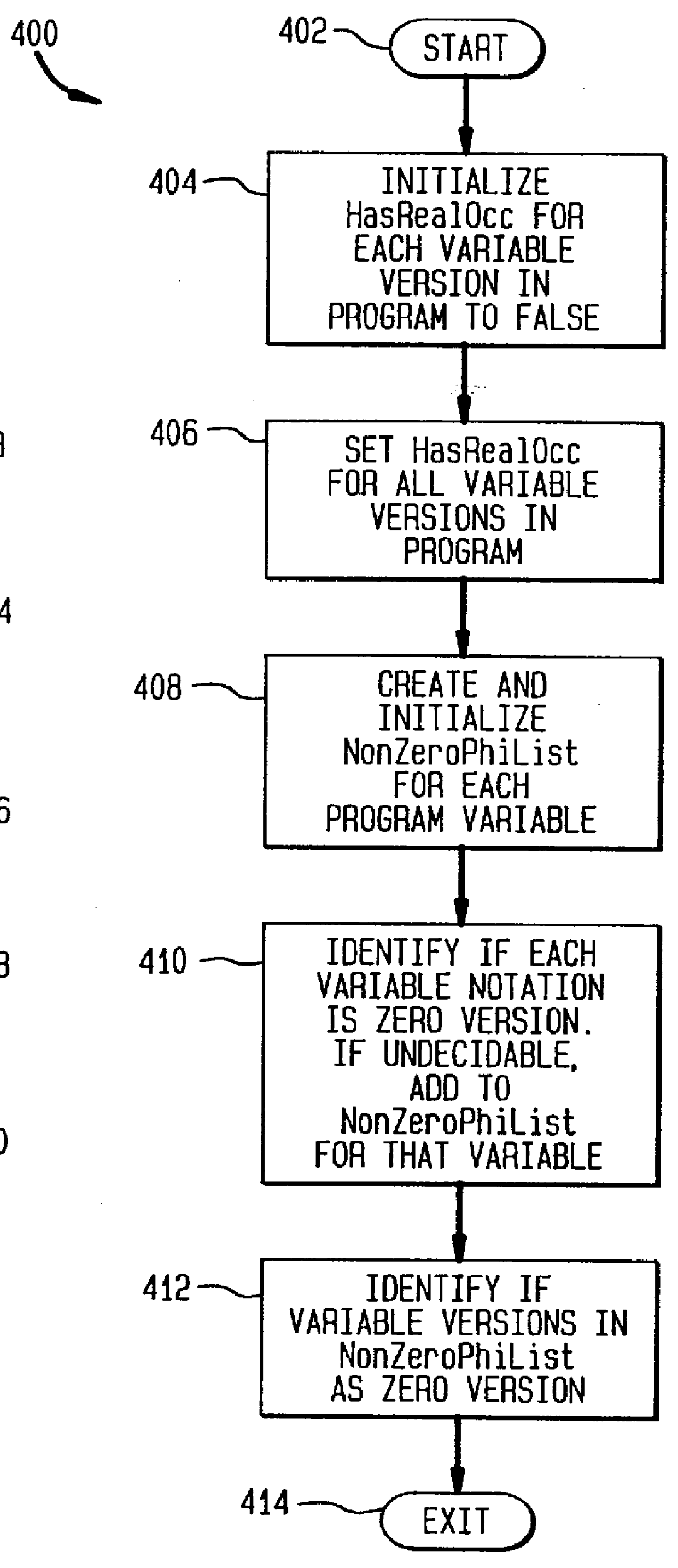
A system and method for an optimizer of a compilation suite for representing aliases and indirect memory operations in static single assignment (SSA) during compilation of a program having one or more basic blocks of source code. The optimizer converts all scalar variables of said program to SSA form, wherein said SSA form includes a plurality of variable versions, zero or more occurrences of a chi function, zero or more occurences of a phi function, and zero or more occurrences of a mu function. The chi function, phi function, and mu function are inserted for the variable versions. The optimizer also determines whether a variable version can be renamed to a zero version, and upon such a determination, the optimizer renames the variable version to a zero version. The optimizer further converts all indirect variables of a program to SSA form, wherein the SSA form includes a plurality of virtual variable versions such that a virtual variable is assigned to an indirect variable, zero or more occurrences of a chi function, zero or more occurences of a phi function, and zero or more occurrences of a mu function. The chi function, phi function, and mu function are inserted for the virtual variables. The optimizer hashes a unique value number and creates a corresponding hash table entry for each variable version and each virtual variable remaining after renaming all zero versions. The optimizer also applies global value numbering to each basic block of the program.
Owner:MORGAN STANLEY +1
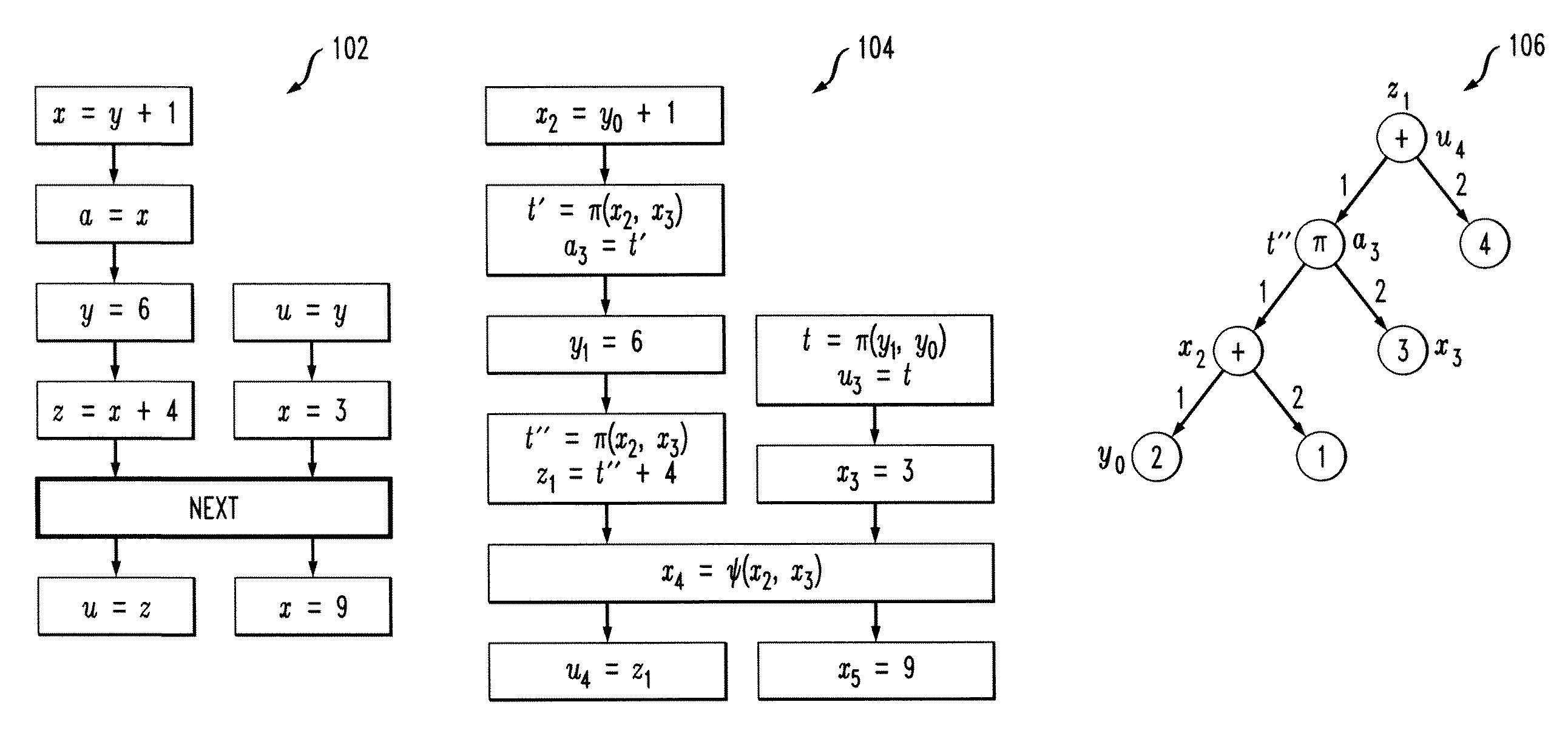
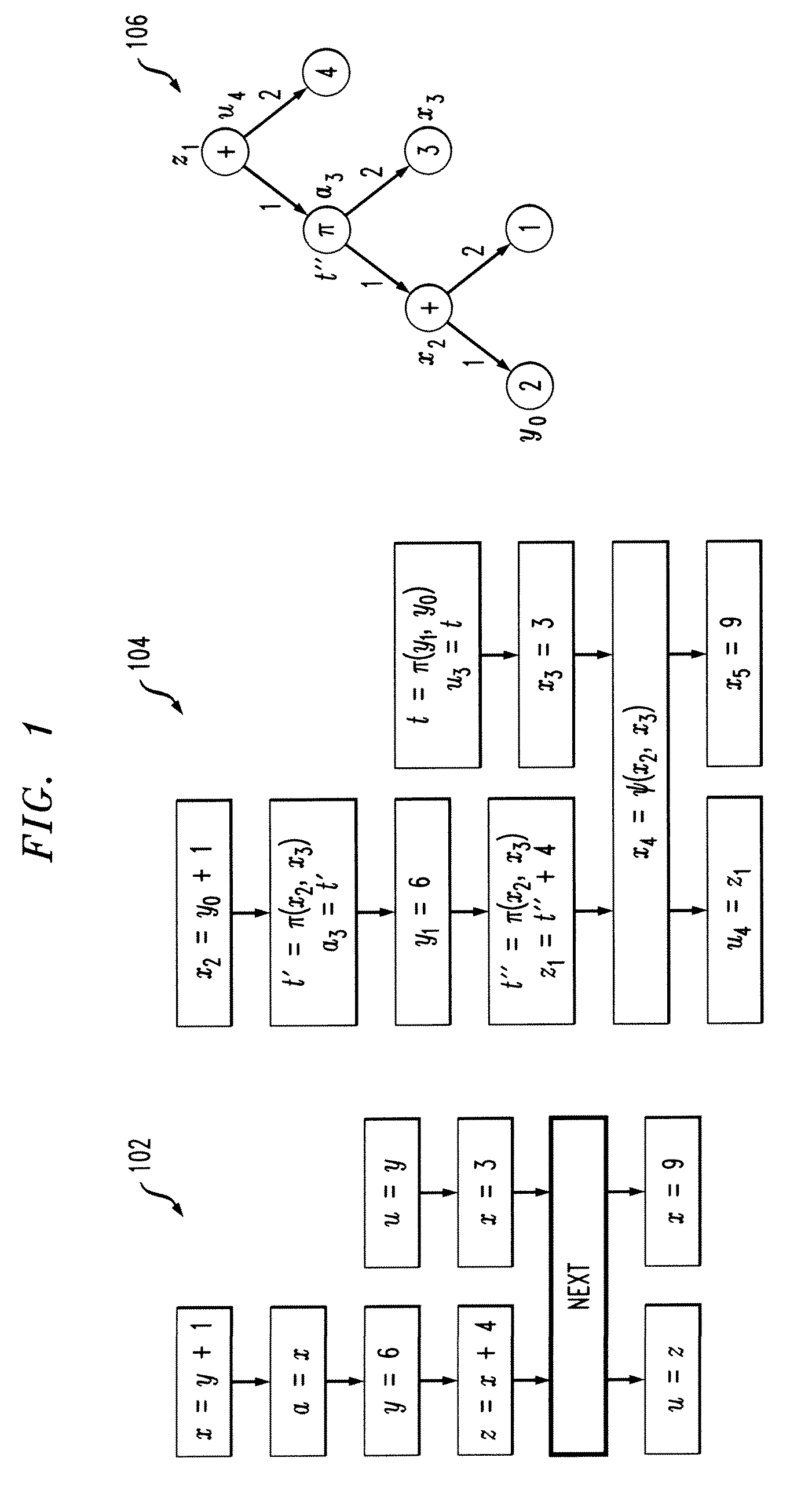
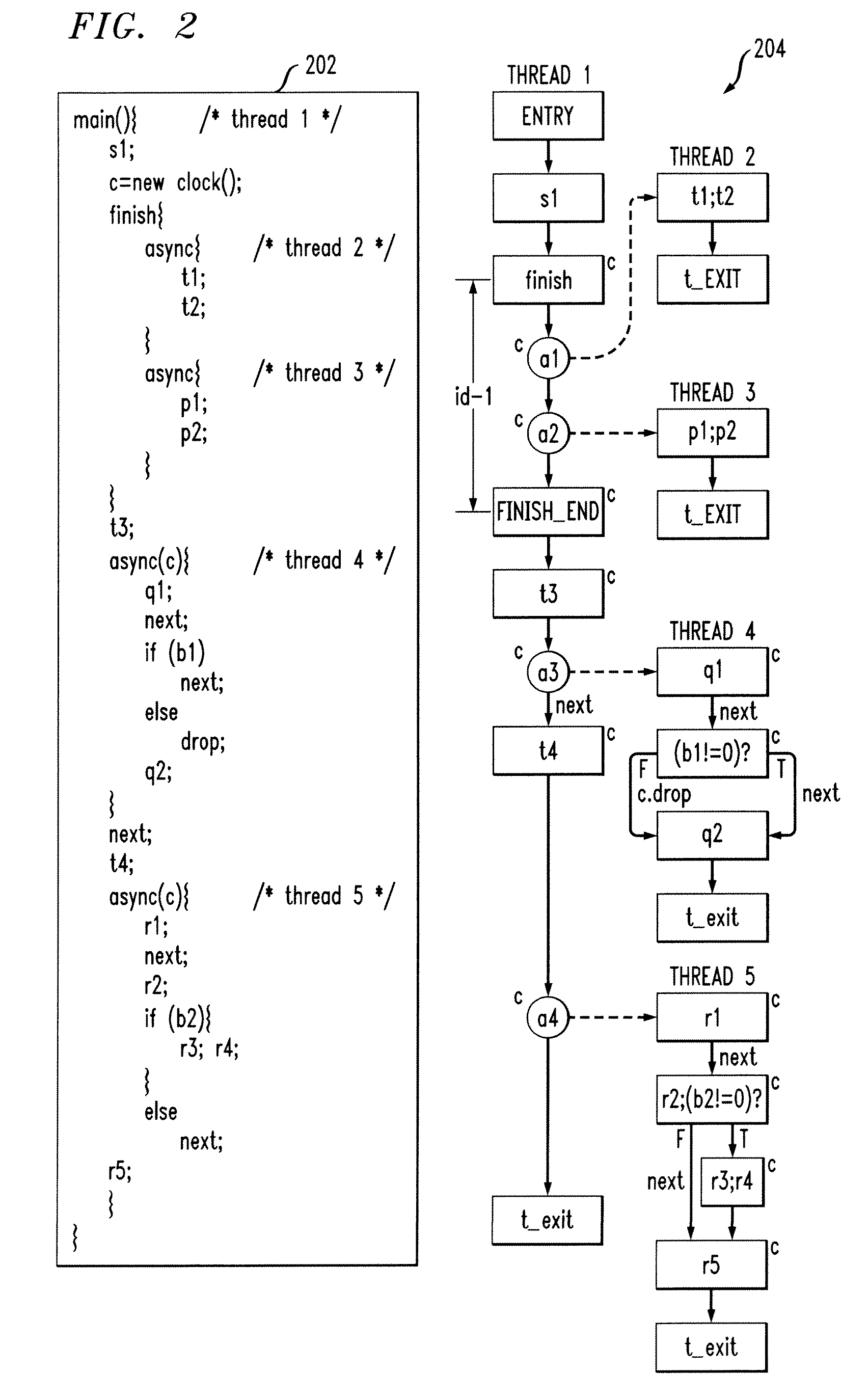
Concurrent Static Single Assignment for General Barrier Synchronized Parallel Programs
InactiveUS20100299656A1Specific program execution arrangementsMemory systemsSingle assignmentPerformed Procedure
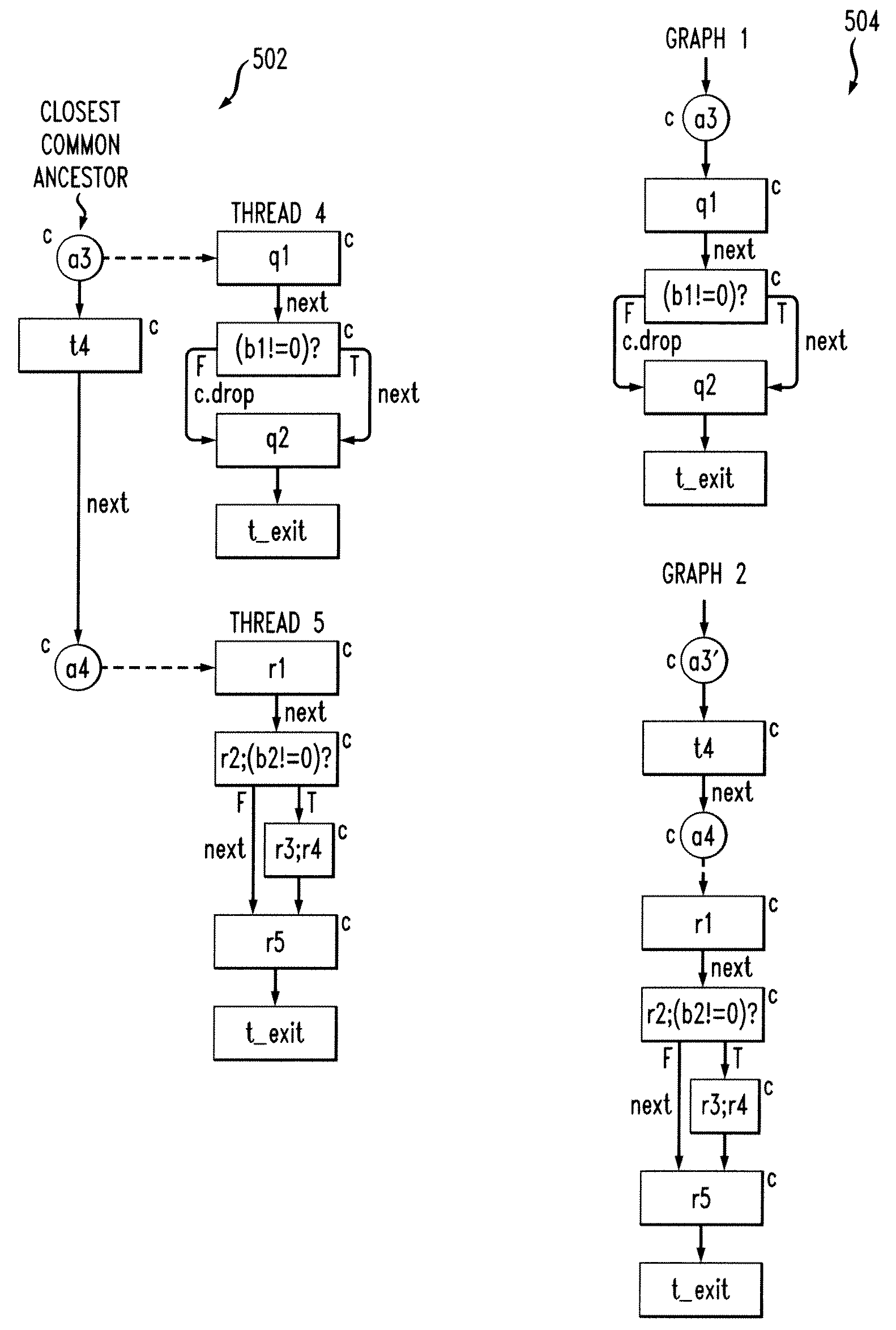
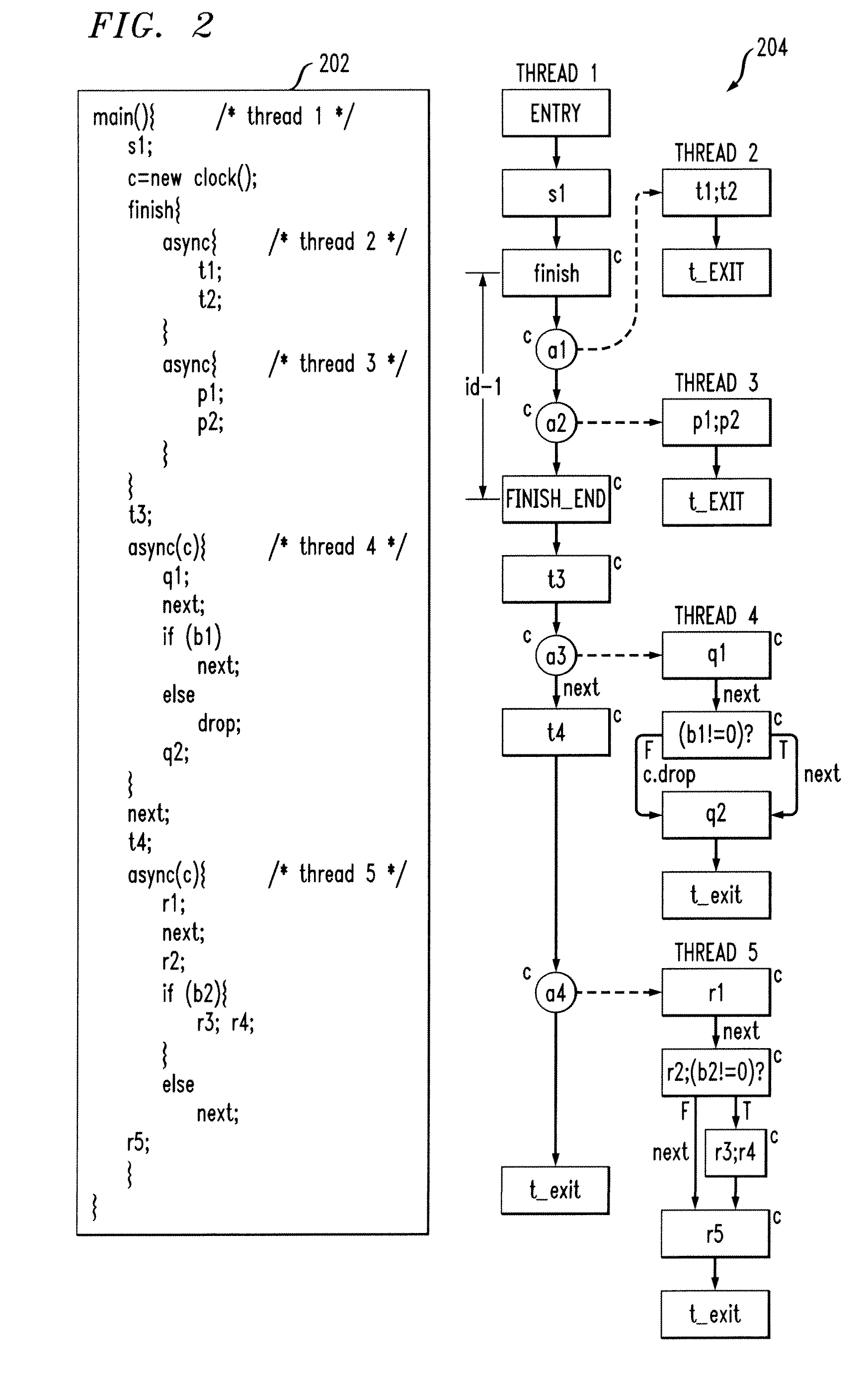
Techniques for generating concurrent static single assignment (CSSA) are provided. The techniques include generating a clocked control flow graph of a program, for each thread of the program created through async instruction, determining each part of the program that can execute concurrently with each thread to create a pair comprising a thread and a parallel program part, for each pair that can execute concurrently, using one or more flow equations to perform node-by-node matching, and using the node-by-node matching to generate CSSA form for the program.
Owner:IBM CORP +1
Method and System for Intermediate Representation of Source Code
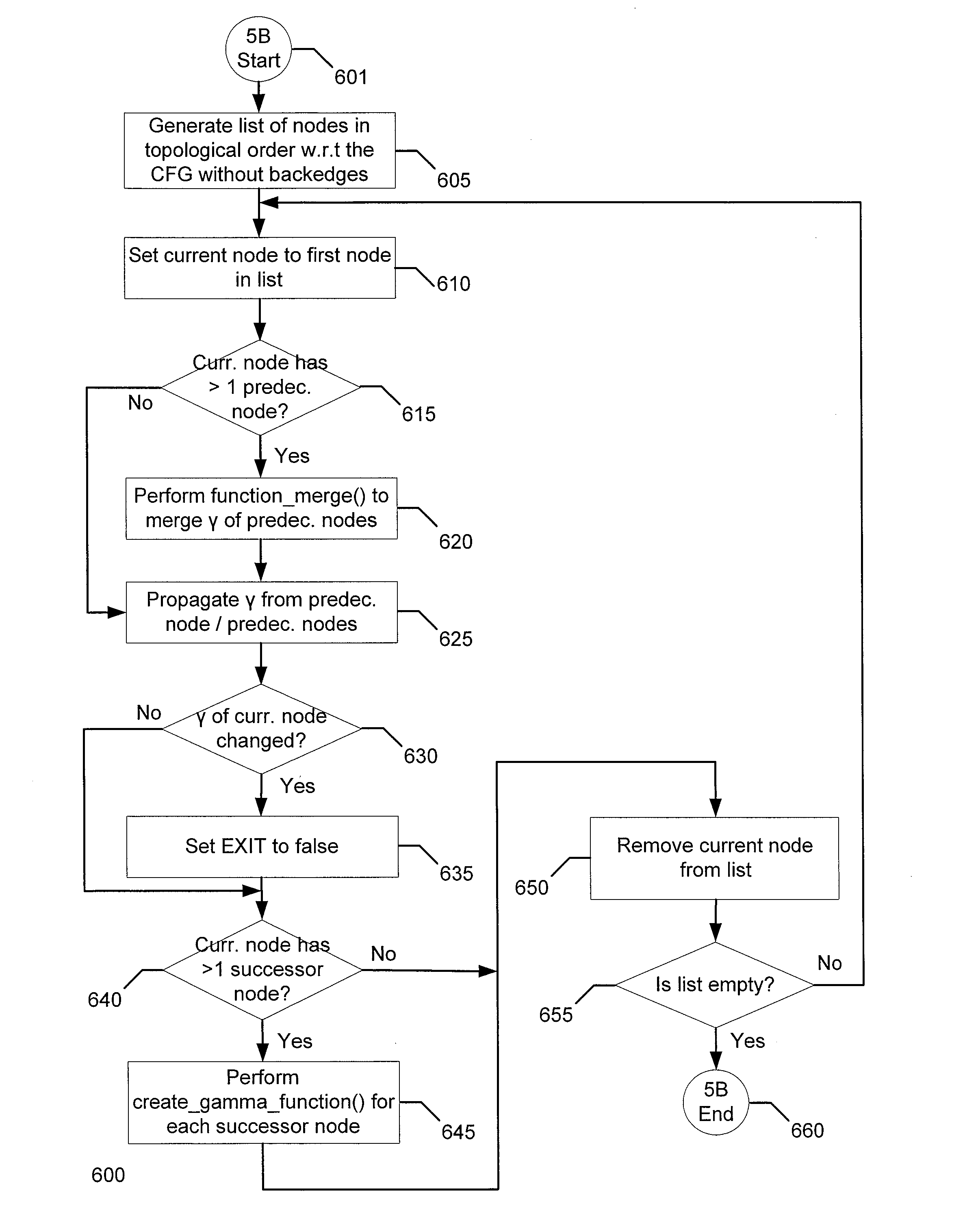
A method to provide effective control and data flow information in an Intermediate Representation (IR) form. A Path Sensitive single Assignment (PSA) IR form with effective and explicit control and data path information supports control flow sensitive optimizations such as path sensitive symbolic substitution, array privatization and speculative multi threading. In the definition of PSA form, besides defining new versioned variables, the gamma functions keep control path information. The gamma function in PSA form keeps the basic attribute of SSA IR form and only one definition exists for each use. Therefore, all existing Single Static Assignment (SSA) IR form based analysis can be applied in PSA form. The gamma function in PSA form keeps all essential control flow information and eliminates unnecessary predicates at the same time.
Owner:INTEL CORP
Method and apparatus for assigning wireless network packet resources to wireless terminals
InactiveUS20120127951A1Easy to useLow communication capacityWireless commuication servicesCommunications systemSingle assignment
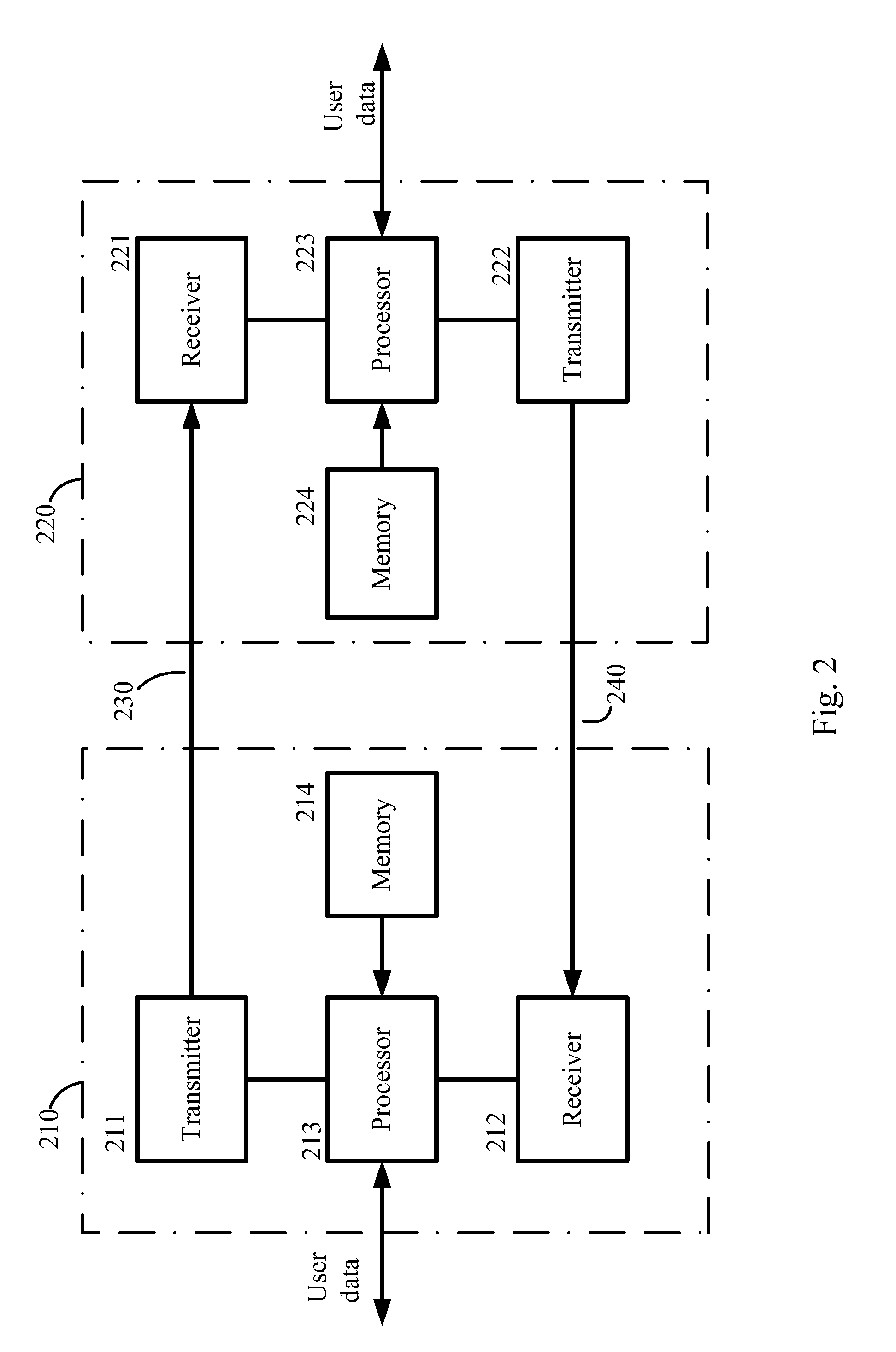
A method in which a network apparatus 210 transmits a single assignment message comprising common assignment information directed to plural wireless terminals. The single transmitted assignment message can be used to enable channel assignment to be initiated for the plural wireless terminals, thus making more efficient use of the assignment message. This may be advantageous when a channel via which the assignment message is transmitted has a lower communication capacity than a channel via which the requests are received. In a GERAN communications system (100, FIG. 1), the effective capacity of the access grant channel can be doubled or tripled, acting to reduce congestion. This increases the probability of a wireless terminal receiving a response to a channel request which it sends. The probability of a successful data transfer following a channel request is thereby increased. Other aspects, embodiments, and features are also claimed and described.
Owner:QUALCOMM INC
Systems and methods for assignment and allocation of mixed-type combinations of slots
ActiveCN101999247ANetwork traffic/resource managementTime-division multiplexSingle assignmentComputer science
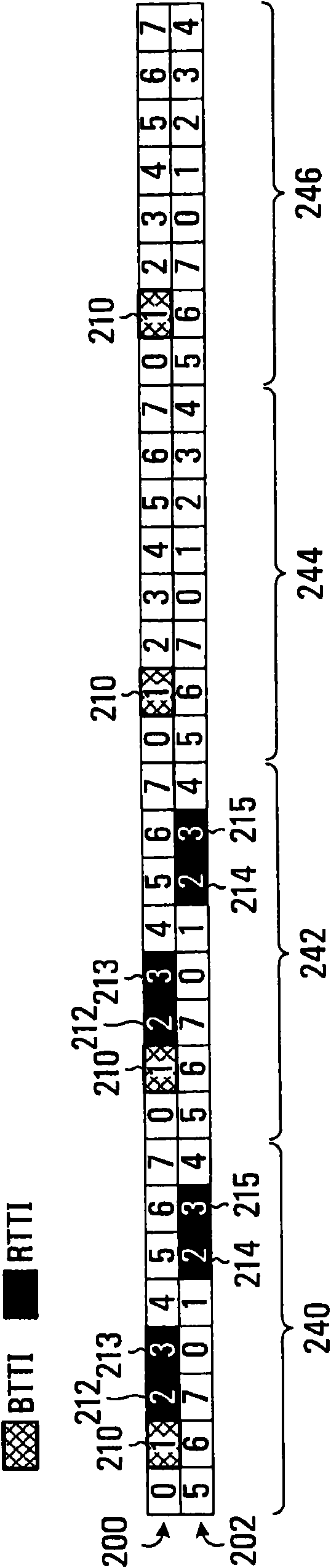
Methods and systems for performing allocation of mixed-type combinations of slots are provided. Specifically, in a single assignment message, an allocation of slots over two framed and slots over four frames is performed. These can be RTTI and BTTI blocks for example.
Owner:BLACKBERRY LTD
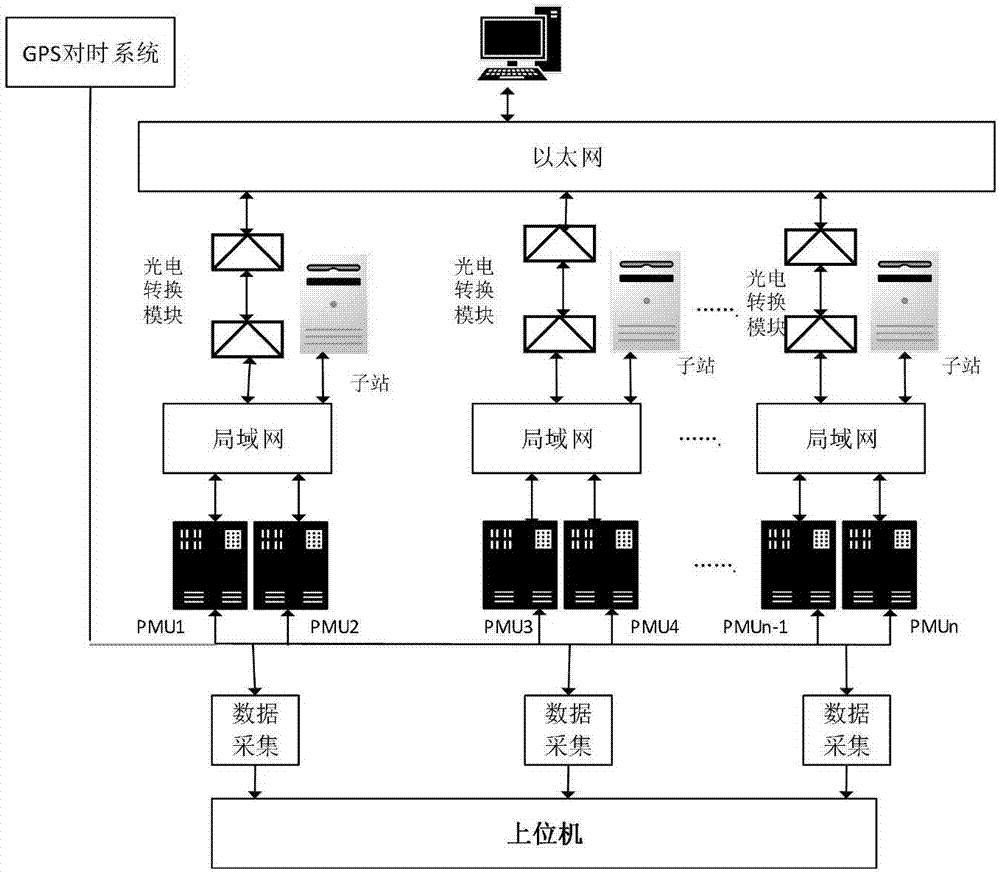
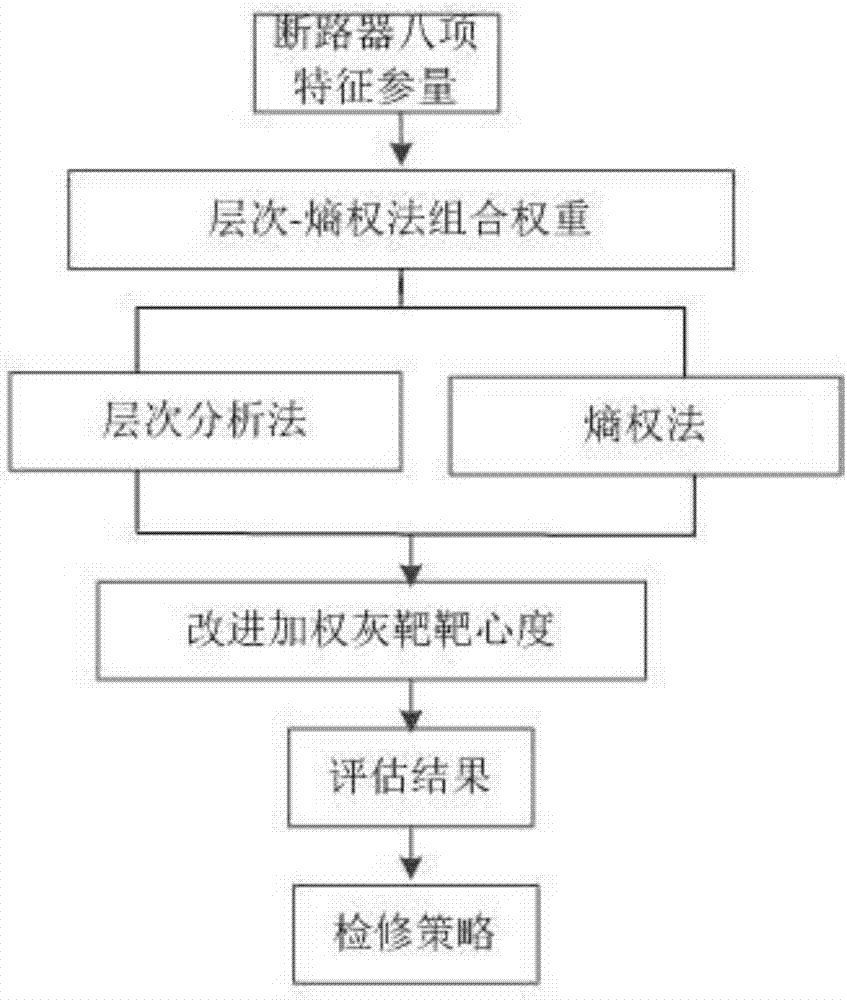
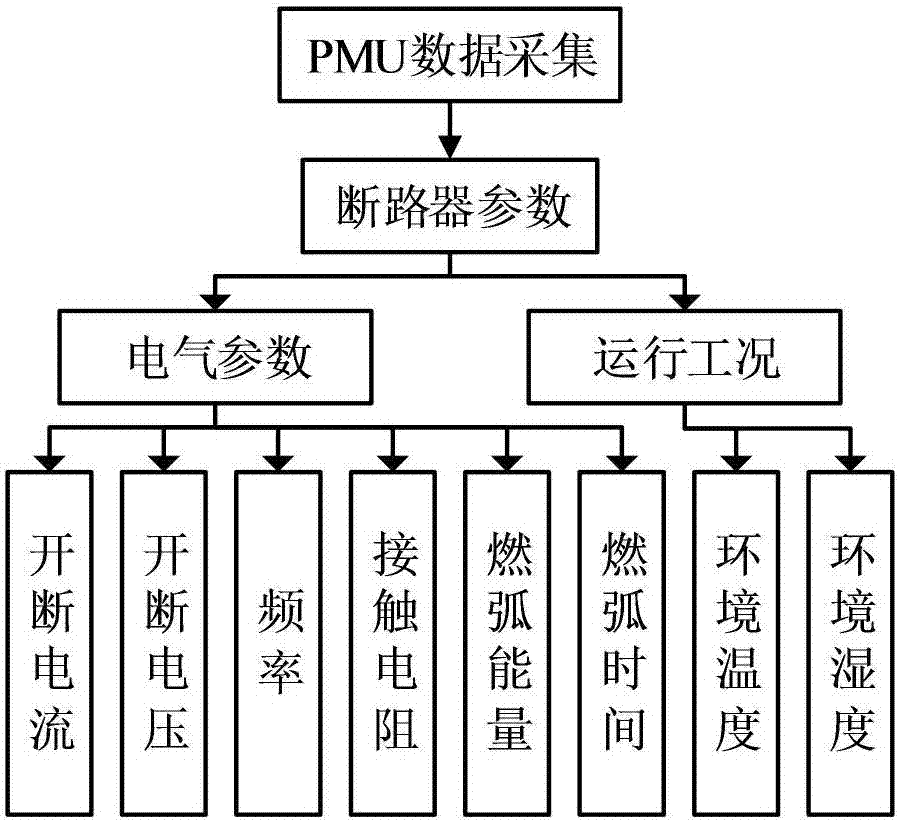
Circuit breaker state online diagnosis method and system based on PMU (Phasor Measurement Unit) data
ActiveCN107886171AEasy to operateHigh engineering application valueResourcesEvaluation resultElectric power system
The invention discloses a circuit breaker state online diagnosis method and a system based on PMU (Phasor Measurement Unit) data, which relate to the technical field of power system circuit breaker protection. A grey target theory is introduced to circuit breaker state diagnosis, the irrationality of adopting a weight average algorithm to calculate the approaching degree by the traditional grey target theory is improved, a hierarchy-entropy weight combined weight calculation method is put forward, the influence weight of each index for an evaluation result is solved, advantages of the two aretaken to remedy disadvantages of each, both subjective and objective factors are considered, defects of a single assignment method are avoided, weight determination is thus more rational, the safe andreliable operation is very important for improving reliable power supply of the power grid, and a basis is laid for realizing state maintenance for the circuit breaker.
Owner:STATE GRID LIAONING ELECTRIC POWER RES INST +2
Method and system for intermediate representation of source code
A method to provide effective control and data flow information in an Intermediate Representation (IR) form. A Path Sensitive single Assignment (PSA) IR form with effective and explicit control and data path information supports control flow sensitive optimizations such as path sensitive symbolic substitution, array privatization and speculative multi threading. In the definition of PSA form, besides defining new versioned variables, the gamma functions keep control path information. The gamma function in PSA form keeps the basic attribute of SSA IR form and only one definition exists for each use. Therefore, all existing Single Static Assignment (SSA) IR form based analysis can be applied in PSA form. The gamma function in PSA form keeps all essential control flow information and eliminates unnecessary predicates at the same time.
Owner:INTEL CORP
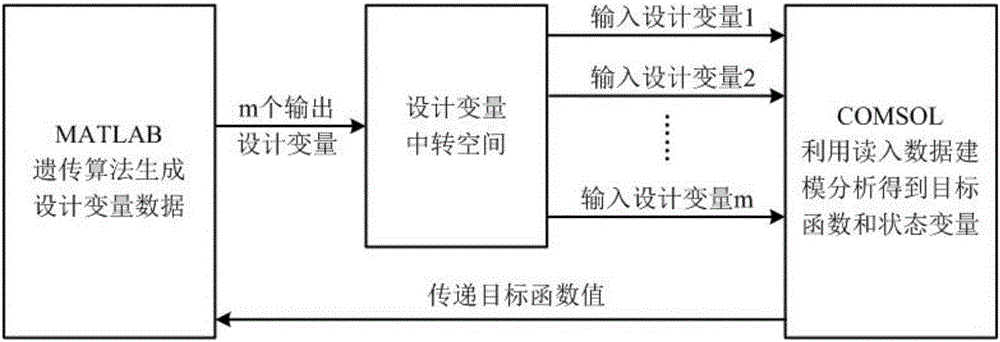
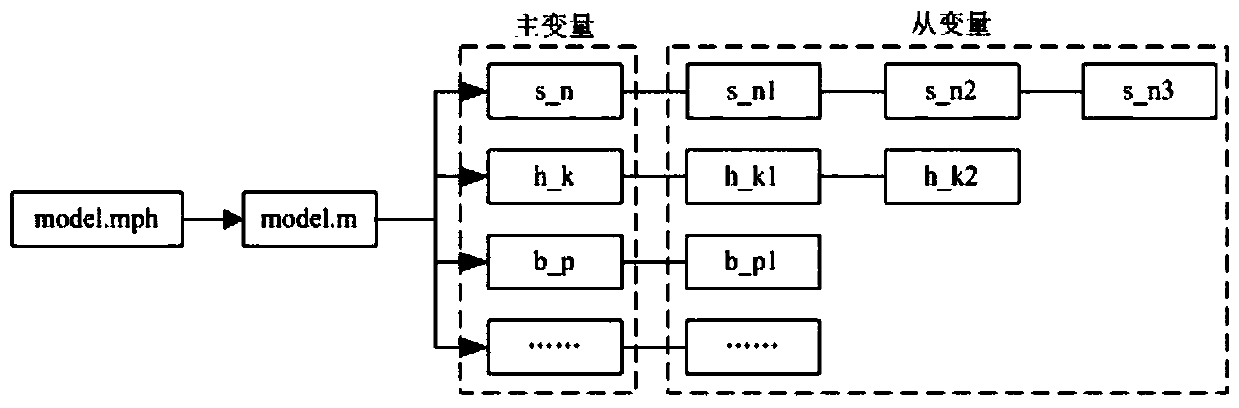
Structure optimization method for low frequency electromagnetic sensor based on genetic algorithm
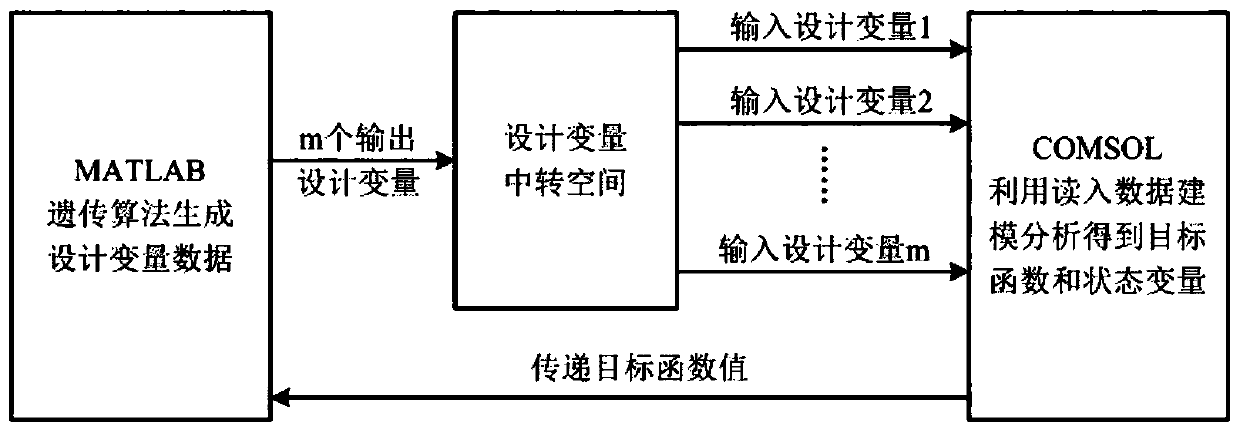
ActiveCN106446447ABreak through the limitations of a single assignment operationRealize intelligent optimizationDesign optimisation/simulationSpecial data processing applicationsSingle assignmentModel parameters
The invention relates to a structure optimization method for a low frequency electromagnetic sensor based on a genetic algorithm. The method is suitable for the structure design of a COMSOL analog low frequency electromagnetic sensor model and the shape reconstruction for defect detecting and belongs to the field of nondestructive detection. The method comprises the following steps: on the basis of simplifying the COMSOL analog low frequency electromagnetic sensor model, parameterizing an optimization model of the COMSOL analog low frequency electromagnetic sensor and defining the reading paths for different variables; setting a genetic optimized fitness function and main parameters including an algorithm running parameter and a control parameter; compiling a dynamic link function, calling for the COMSOL model by MATLAB and constructing a channel for mutually transferring data; calling a COMSOL genetic algorithm for optimizing the parameters of the low frequency electromagnetic sensor model, and while acquiring the fitness function meeting the convergence criterion, acquiring an optimized result, namely, the optimized structure parameter of the low frequency electromagnetic sensor. According to the method provided by the invention, the limitation of the COMSOL single assignment operation is broken through and the intelligent optimization of the COMSOL model parameters is realized.
Owner:BEIJING UNIV OF TECH
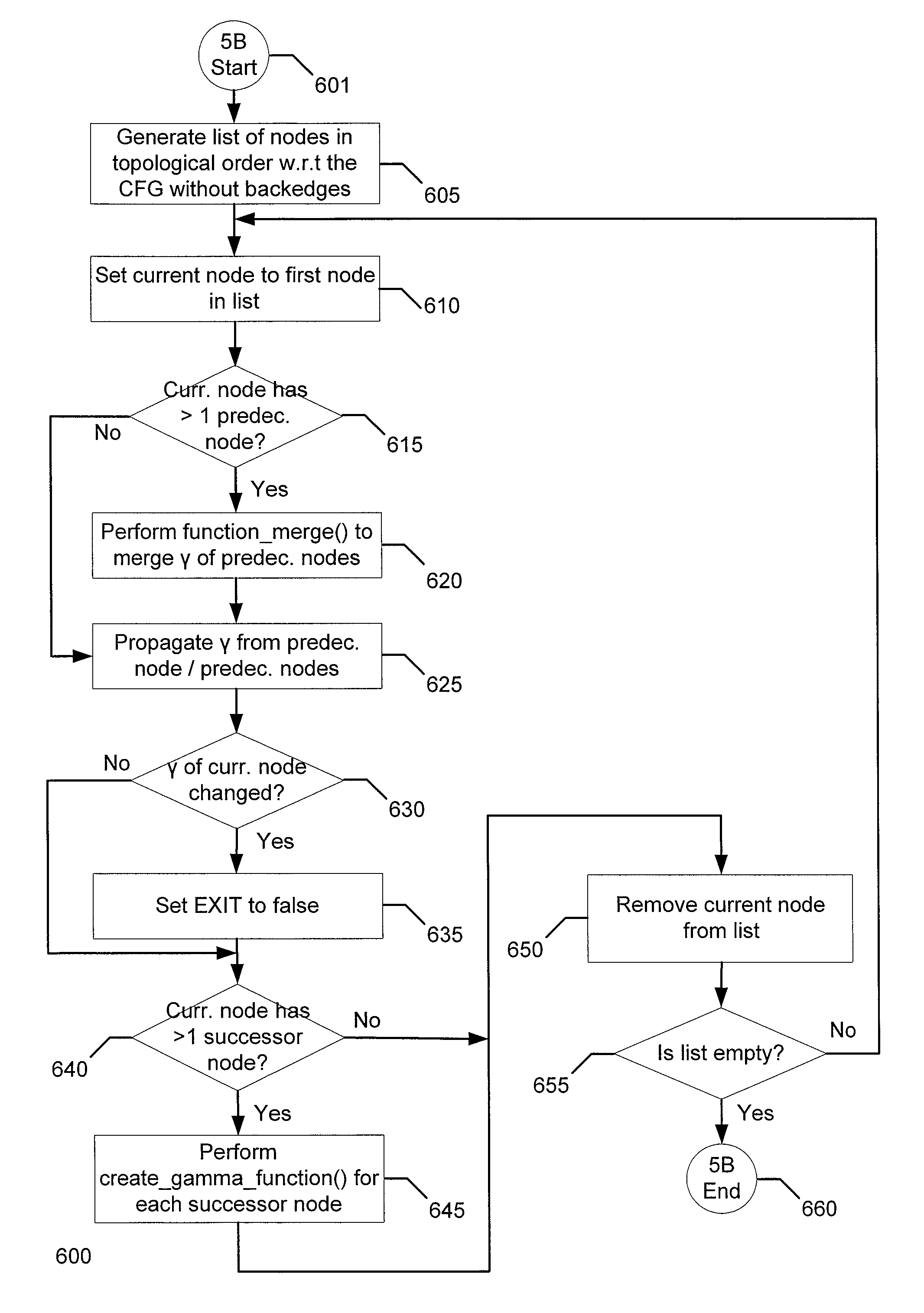
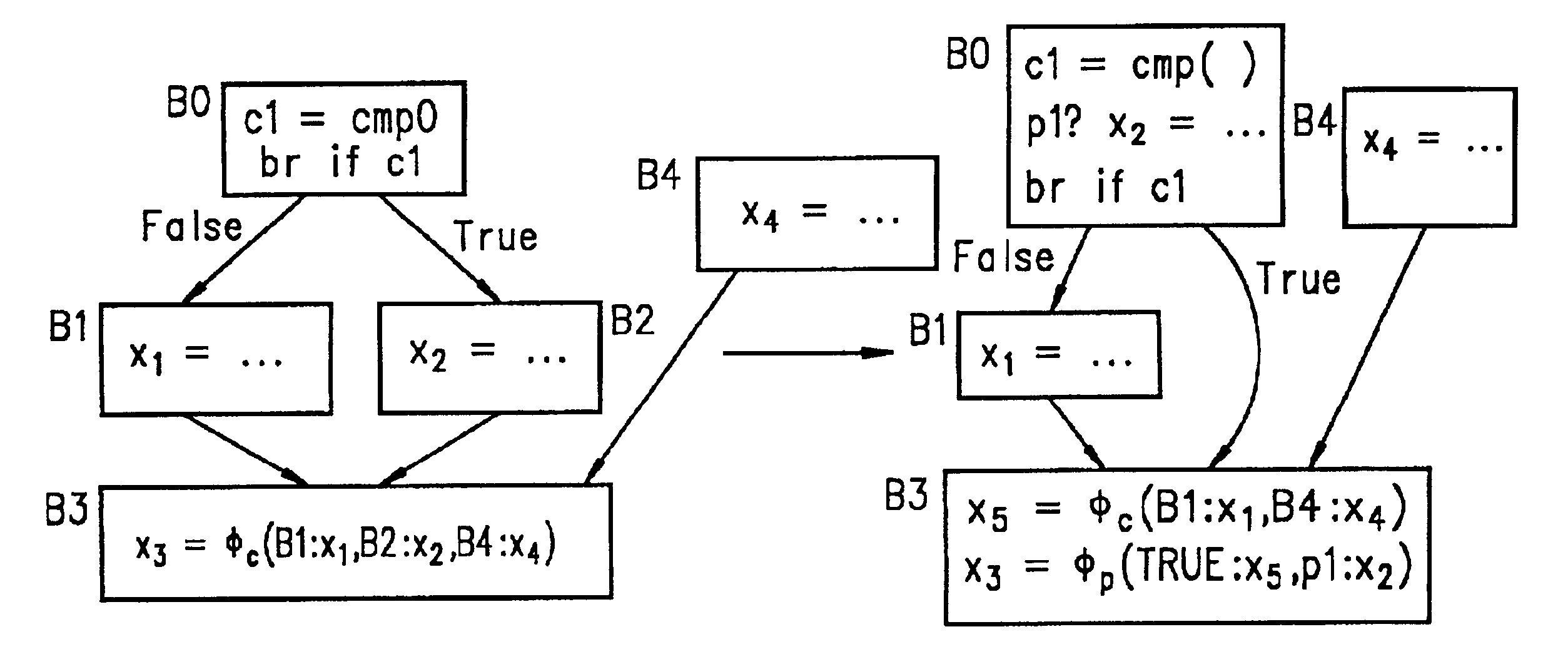
Method and apparatus for ordered predicate phi in static single assignment form
A Φ function provides a mechanism for static single assignment in the presence of predicated code. Guards placed on each source operand of the Φ function indicate the condition under which the corresponding source operand is live and provide correct materialization of the Φ functions after code reordering. For control functions Φc representing a confluence of live reaching definitions at a join point in the control flow graph, the guards indicate the basic block which is the source of the edge associated with the source operand. The Φc operands are paired with the source basic block of the incoming edge(s) along which they are live. The operands are also ordered according to a topological ordering of their associated block. This ordering is maintained through subsequent code transformations. In the topological ordering, the source of the edge from which the definition was passed is defined. A predicate Φ function Φp, represents the confluence of definitions in a straight line of code in which some of the definitions have been predicated. For Φp, the guards on the source operands indicate the predicate under which the corresponding operand is live. The order of the operands is such that the Φp function can be fully materialized by inserting a copy from each source operand to the target variable, in the corresponding order, and each predicated by the associated predicate guard.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
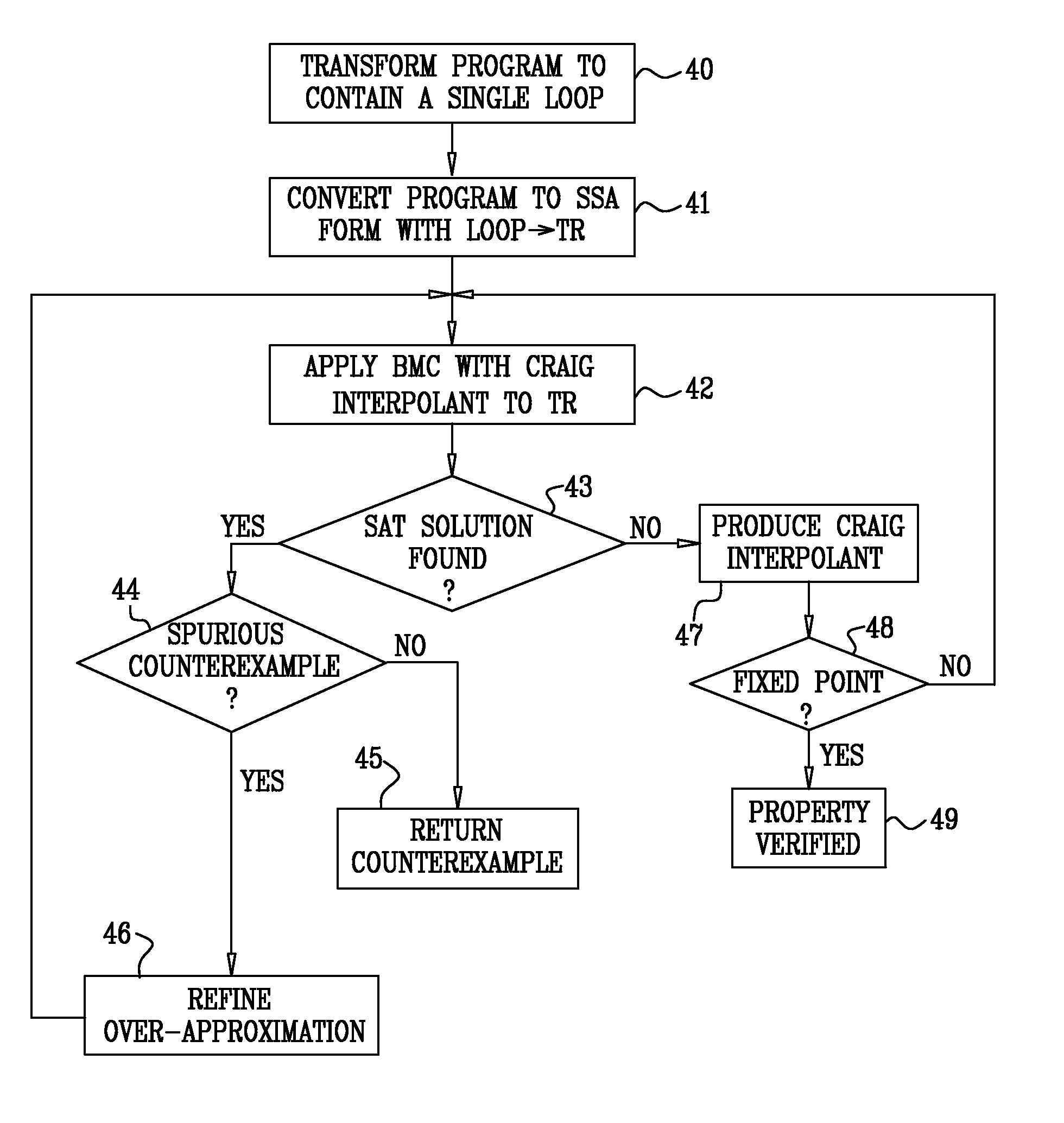
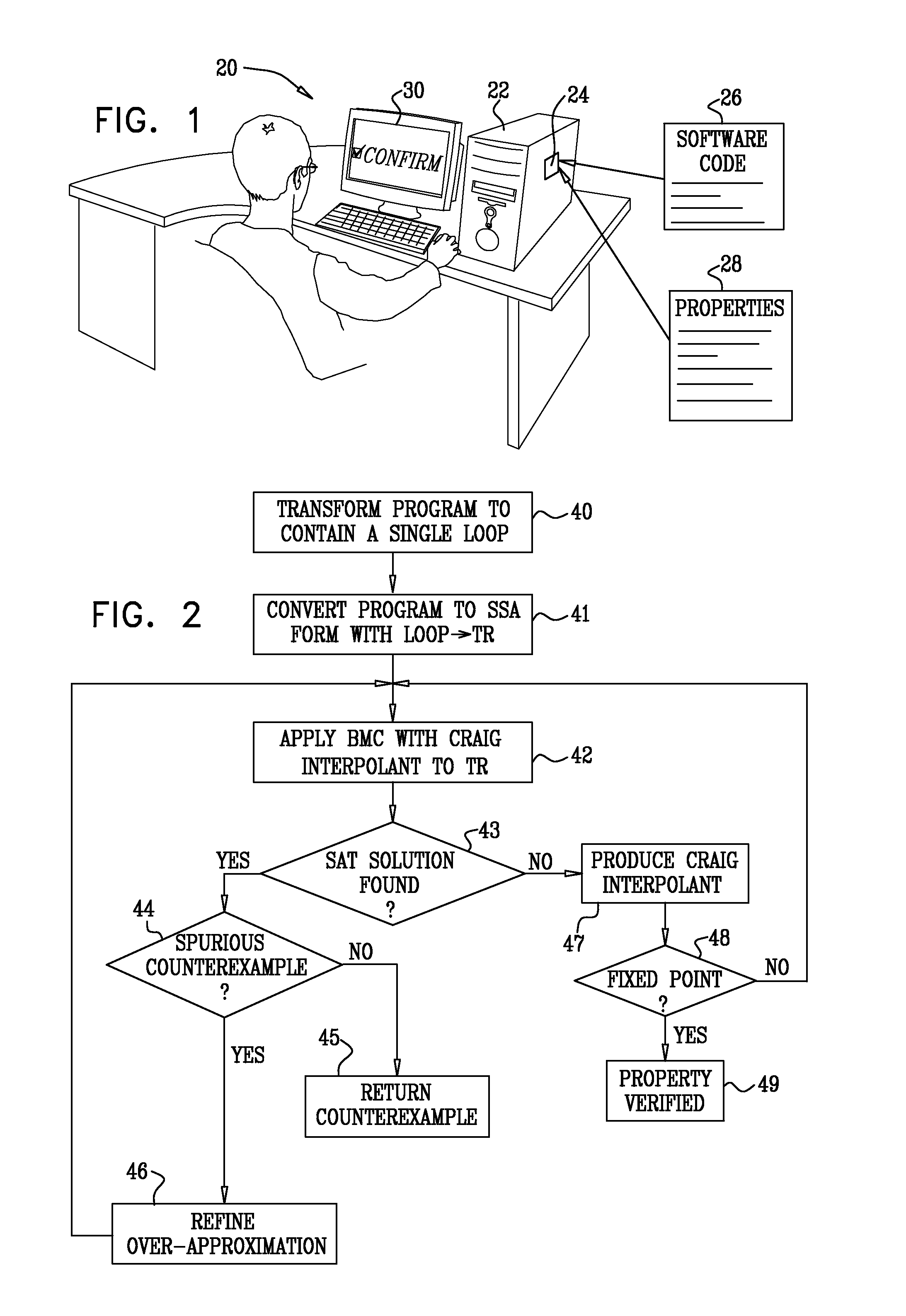
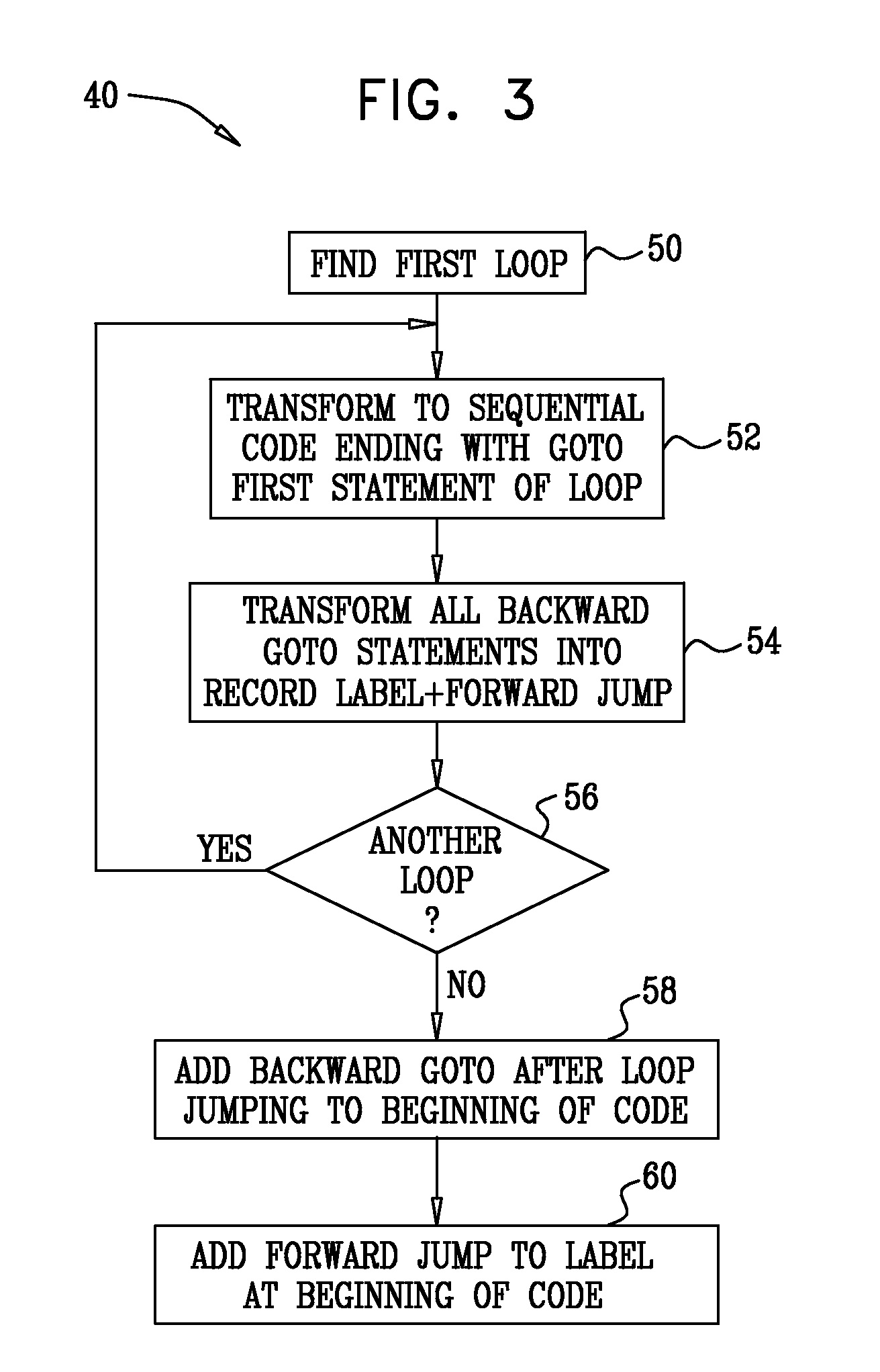
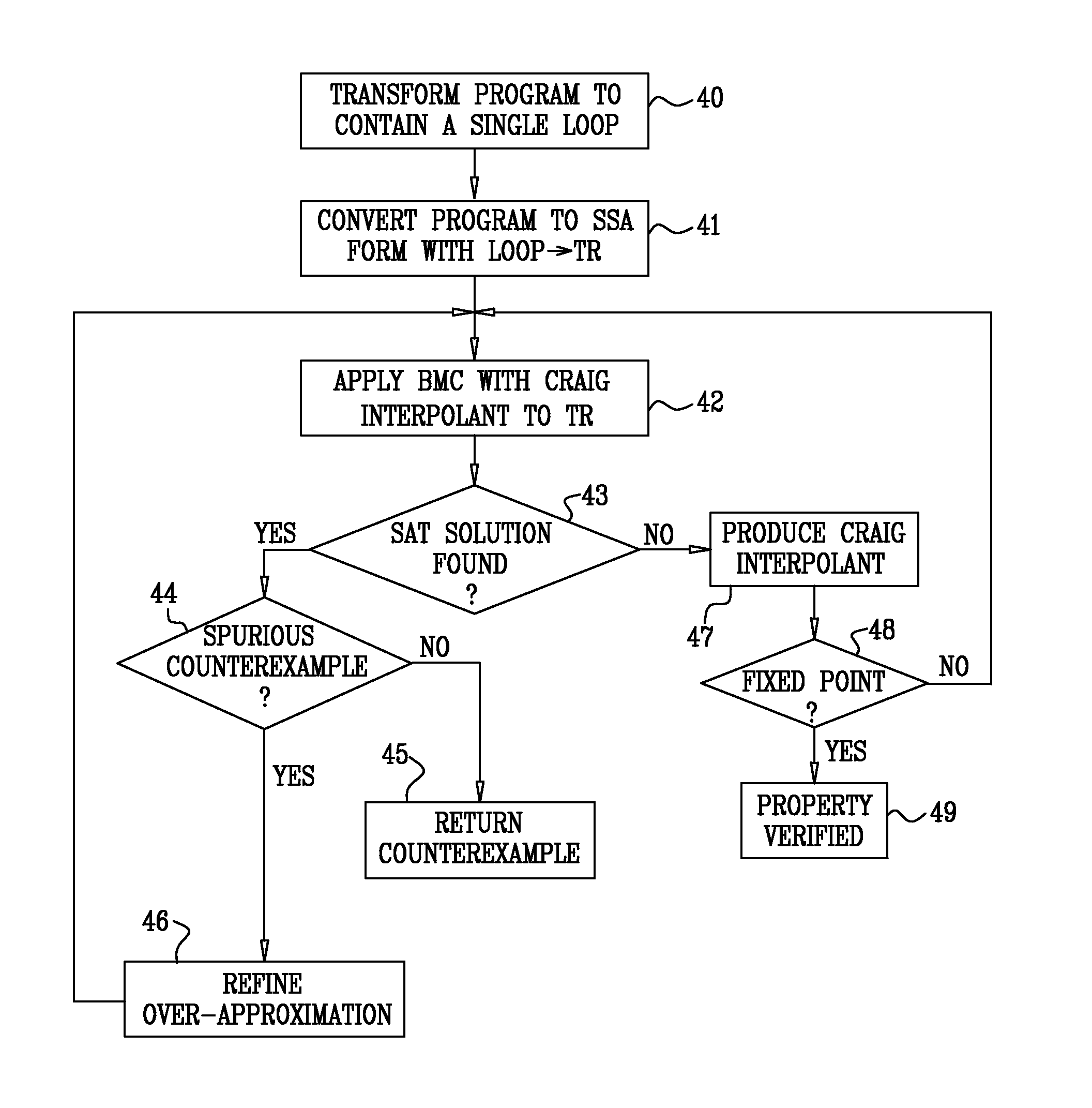
Model Checking of Non-Terminating Software Programs
InactiveUS20080098347A1Requirement analysisSpecific program execution arrangementsSingle assignmentLogical formula
Owner:IBM CORP
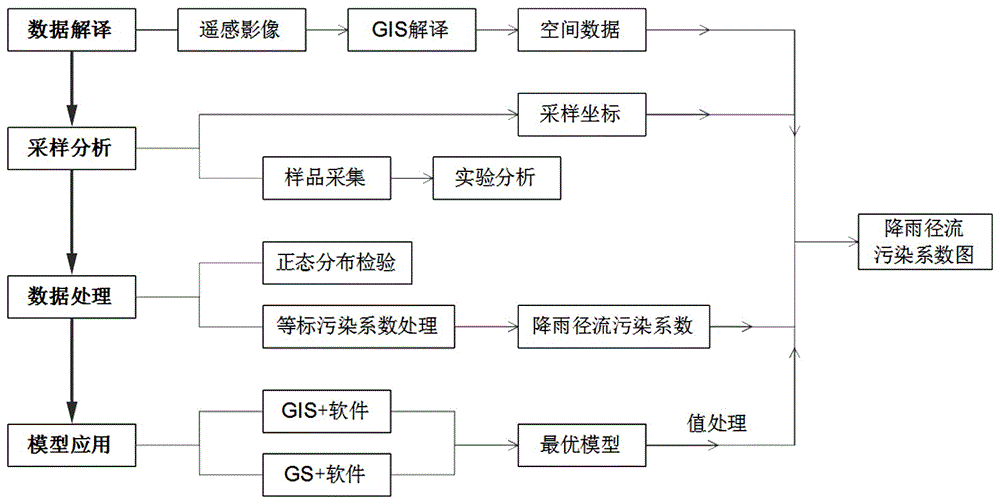
Method for analyzing space distribution feature of ground rainfall runoff pollution based on GIS (Geographic Information System) technology
ActiveCN106528788AAvoid under-assignment in generalHigh precisionData processing applicationsGeographical information databasesRainfall runoffSingle assignment
The invention relates to a method for analyzing a space distribution feature of ground rainfall runoff pollution based on a GIS (Geographic Information System) technology. The method comprises the following steps: acquiring space information data of a land area in a research area; performing sampling and analyzing; preprocessing detection data of rainfall runoff pollution and establishing a database; building an optimal GIS model; and generating a space distribution map of rainfall runoff pollution levels. In the method, the GIS technology is introduced into the analysis for the space distribution feature of the rainfall runoff pollution, so that faults caused by a subjective method are reduced. Meanwhile, the space distribution feature of the rainfall runoff pollution is simulated by the GIS technology, so that the problem of relatively low accuracy of a calculation result due to a conventional export coefficient method in which single assignment is mainly performed according to the type of land use is solved, and scientific guidance is provided for the effective making of a rainfall runoff pollution control strategy, the implementation of a pollution control measure and the development of sponge city construction.
Owner:SHANGHAI MUNICIPAL ENG DESIGN INST GRP
Model checking of non-terminating software programs
InactiveUS7921411B2Requirement analysisSpecific program execution arrangementsSingle assignmentLogical formula
A method for verifying software program code includes specifying a property that the software program code is expected to satisfy. The software program code and the property are transformed into an initial logical formula in a static single assignment (SSA) form, the formula including variables. A loop in the software program code is identified. Successive over-approximations are applied to a portion of the initial logical formula corresponding to the loop in order to produce a modified logical formula in the SSA form that represents a finite over-approximation of a set of states that are reachable by the loop. It is verified that the software program code satisfies the specified property by determining whether there is an assignment of the variables that satisfies the modified logical formula.
Owner:IBM CORP
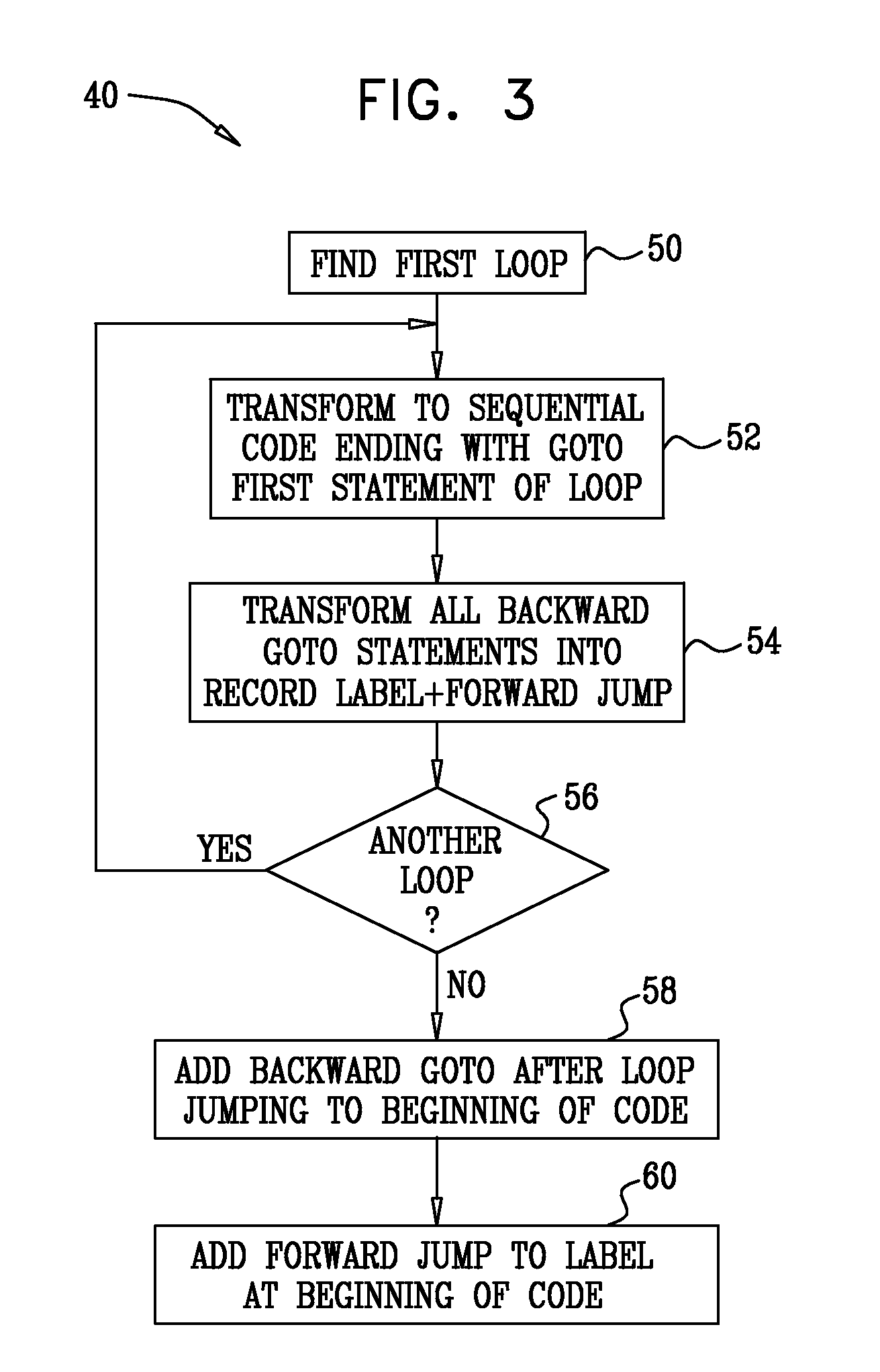
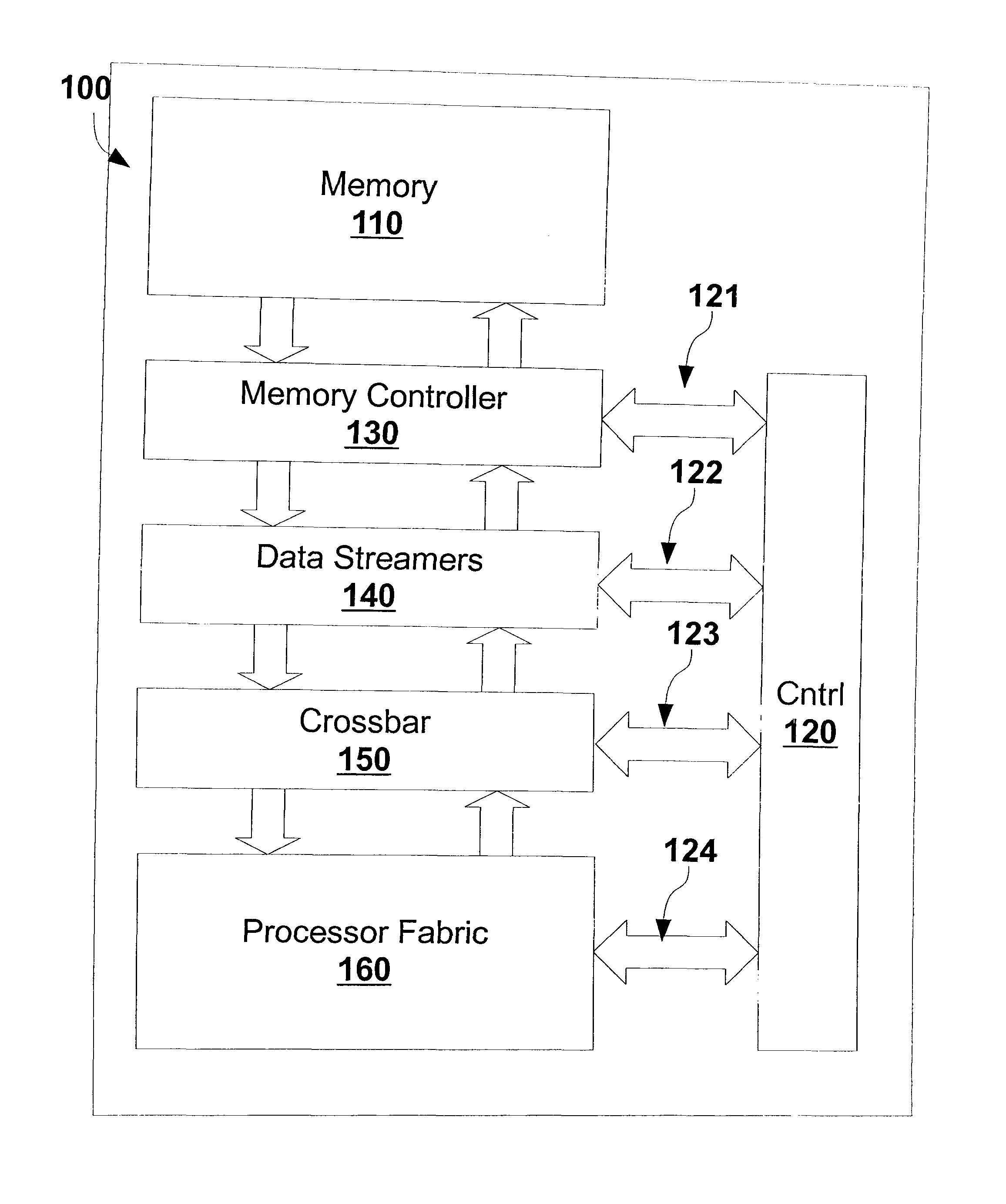
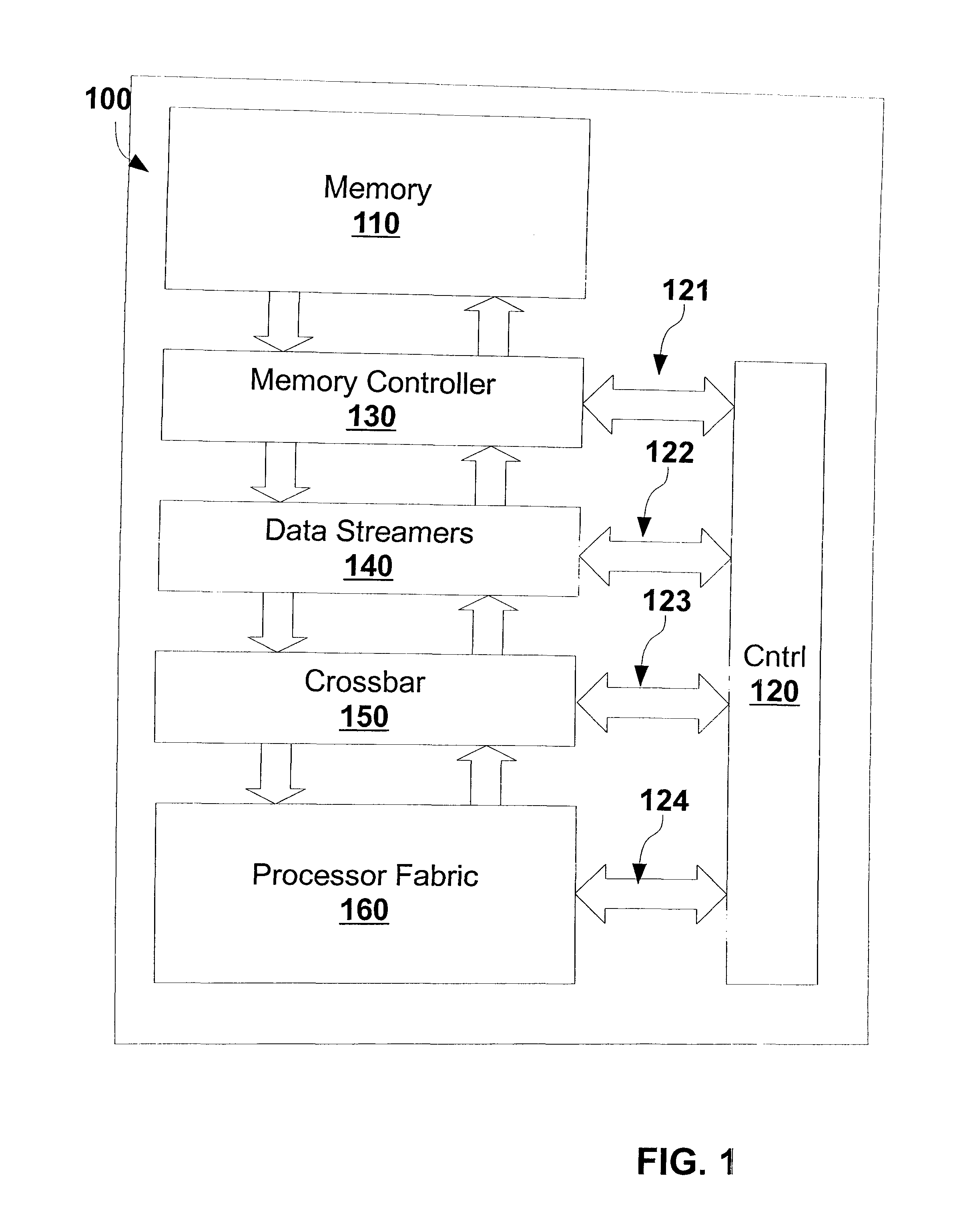
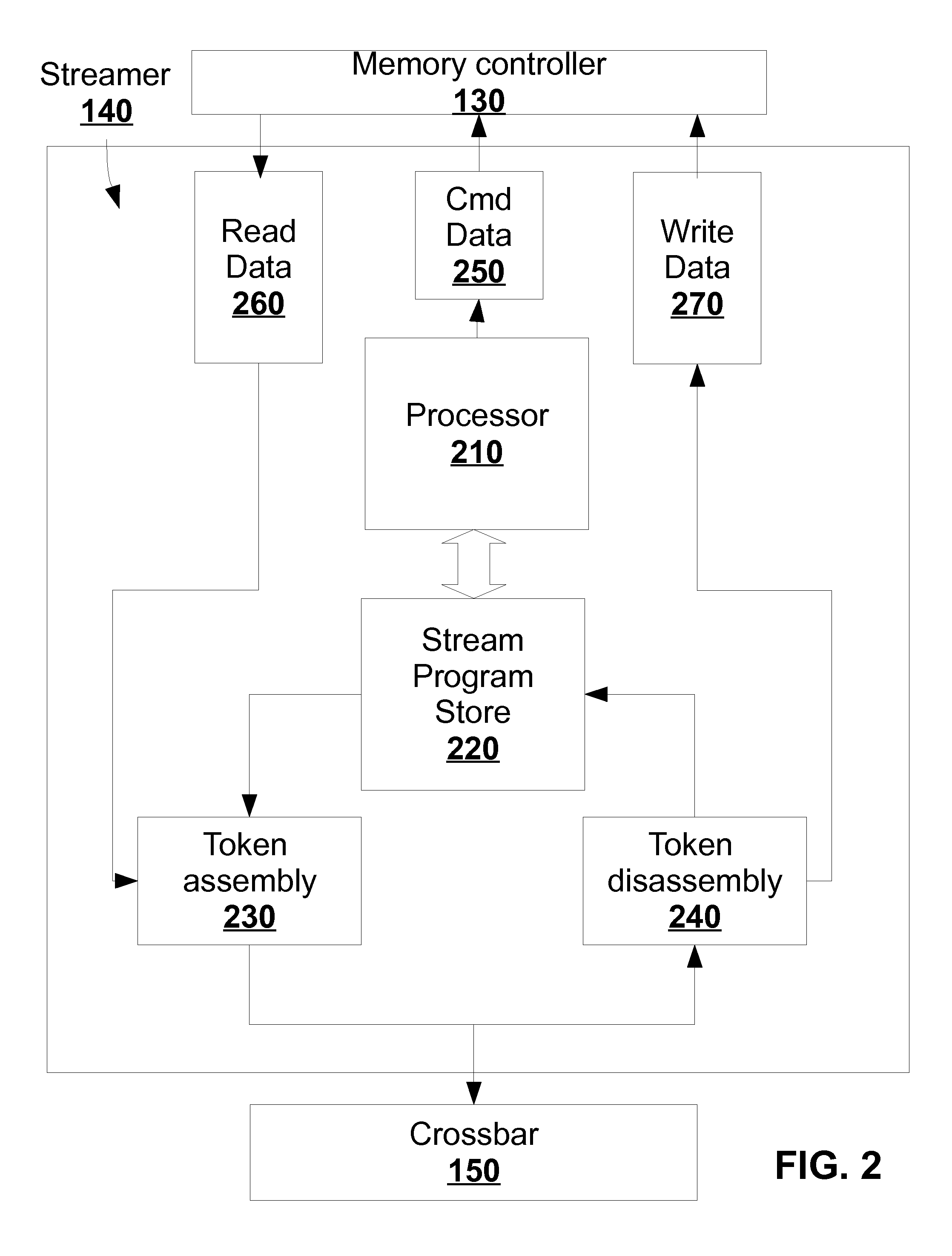
Execution engine for executing single assignment programs with affine dependencies
ActiveUS8688956B2Efficient executionEnergy consumptionSingle instruction multiple data multiprocessorsMemory systemsExecution unitSingle assignment
Owner:STILLWATER SUPERCOMPUTING
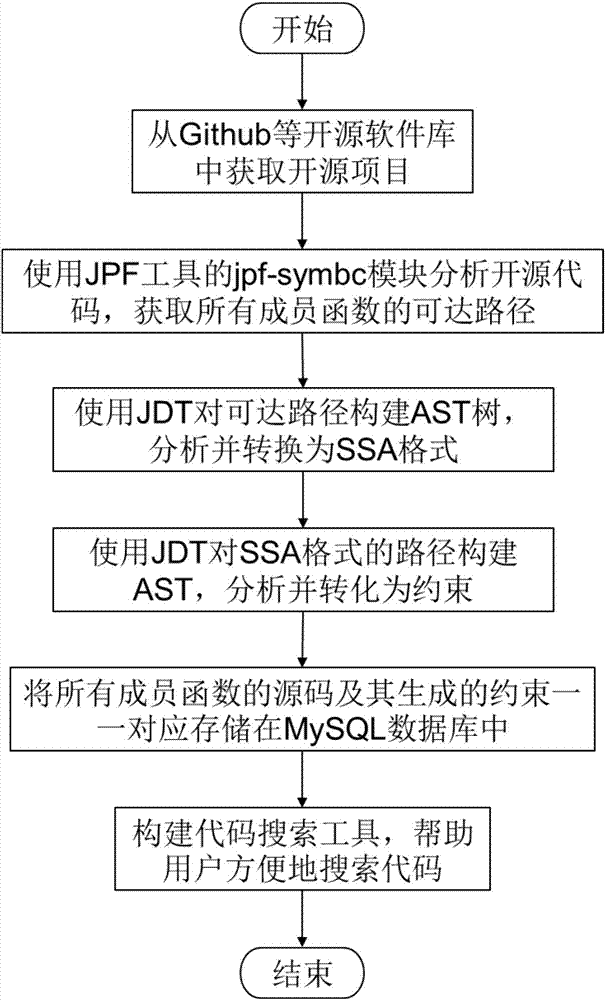
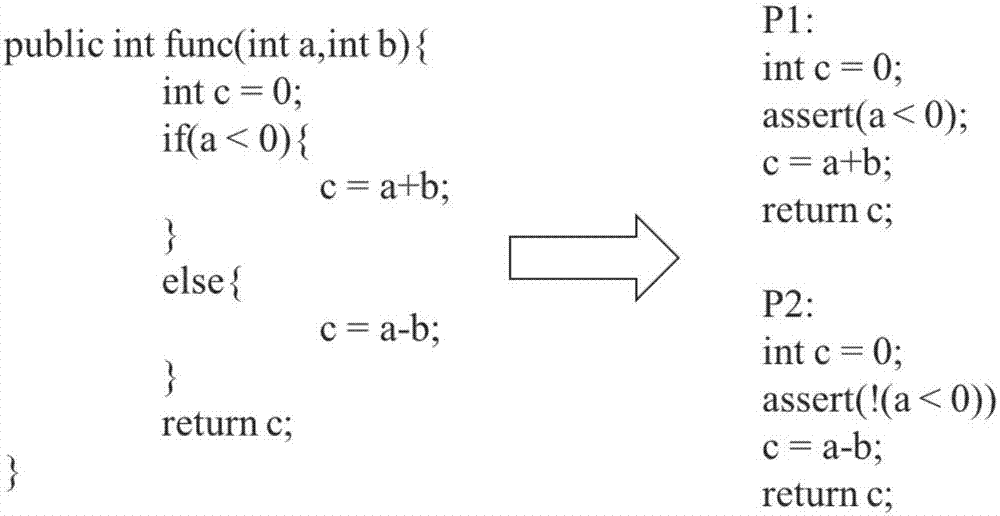
Constraint solving based code search method
InactiveCN107992324AExact searchSolve the problem of artificial screening of available codeTransformation of program codeSoftware maintainance/managementBase codeSearch problem
The invention discloses a constraint solving based code search method. The constraint solving based code search method specifically includes the steps of 1), acquiring an open source project from an open source community; 2), analyzing a source code by adopting JPF (Java Pathfinder) and JDT (Java Development tools) and converting the source code into an SSA (static single-assignment) format; 3), analyzing a code of the SSA format by using the JDT and converting the source code into constraint; 4), subjecting the source code and the generated constraint to one-to-one correspondence and establishing a code-constraint library; 5), establishing a code search system and helping a user search the code. The main characteristic of the method is to solve the code search problem on the basis of constraint solving and deal with loop statements and class member variables, lack of previous work is made up, accuracy rate in code search is greatly improved, and the required code can be searched by aprogrammer during the software development process with reference and reuse to improve software development efficiency and quality.
Owner:NANJING UNIV
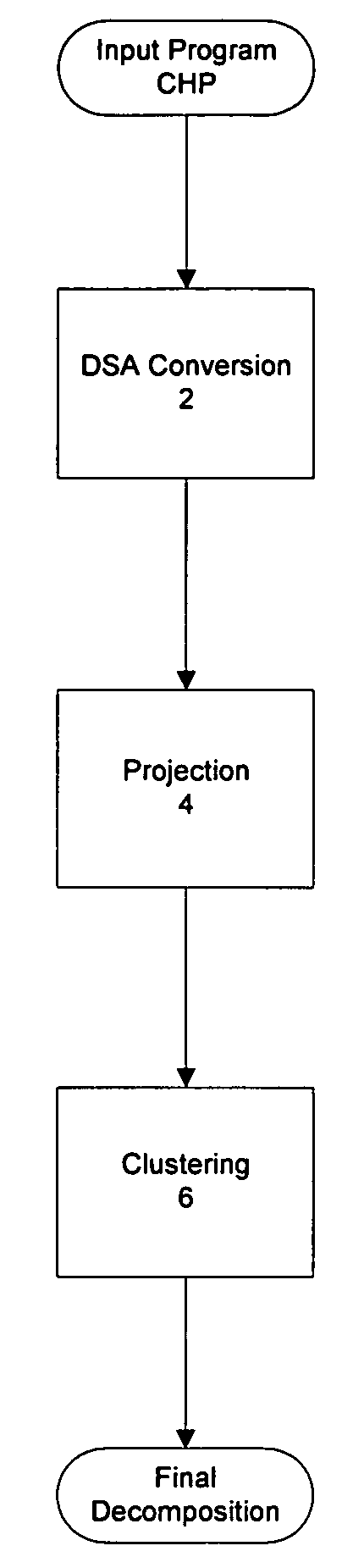
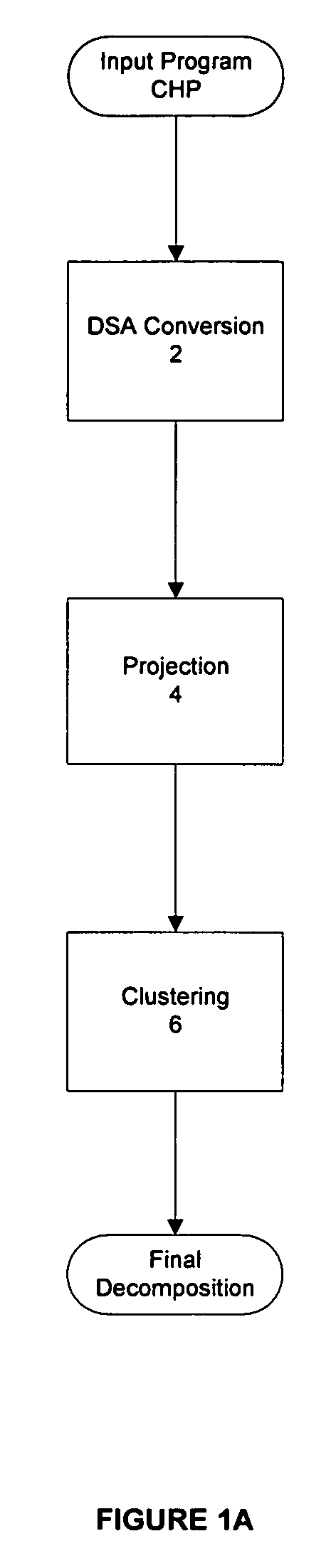
Method for the synthesis of VLSI systems based on data-driven decomposition
InactiveUS7404172B2High energyImprove performanceCAD circuit designSoftware simulation/interpretation/emulationQR decompositionComputer architecture
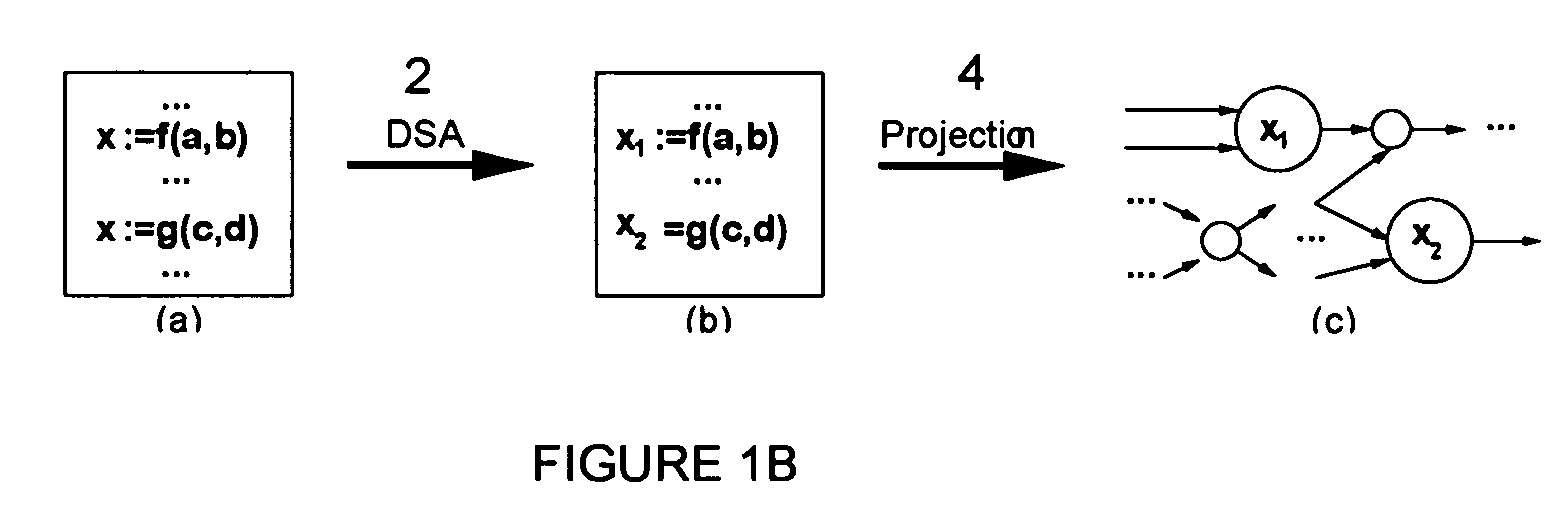
The present invention is a systematic and data-driven-decomposition (DDD) method and apparatus for use in VLSI synthesis. The invention decomposes a high level program circuit description into a collection of small and highly concurrent modules that can be implemented directly into transistor networks. This enables an automatic implementation of a decomposition process currently done by hand. Unlike prior art syntax-based decompositions, the method of the present invention examines data dependencies in the process' computation, and then attempts to eliminate unnecessary synchronization in the system. In one embodiment, the method comprises: a conversion to convert the input program into an intermediate Dynamic Single Assignment (DSA) form, a projection process to decompose the intermediate DSA into smaller concurrent processes, and a clustering process that optimally groups small concurrent processes to make up the final decomposition. Another embodiment is a decomposition, projection, and clustering tool implemented in computer program codes.
Owner:CALIFORNIA INST OF TECH
Method for accelerating the generation of an optimized gate-level representation from a rtl representation
InactiveUS20080244472A1The process is convenient and fastHigh trafficComputer aided designSoftware simulation/interpretation/emulationFast optimizationTheoretical computer science
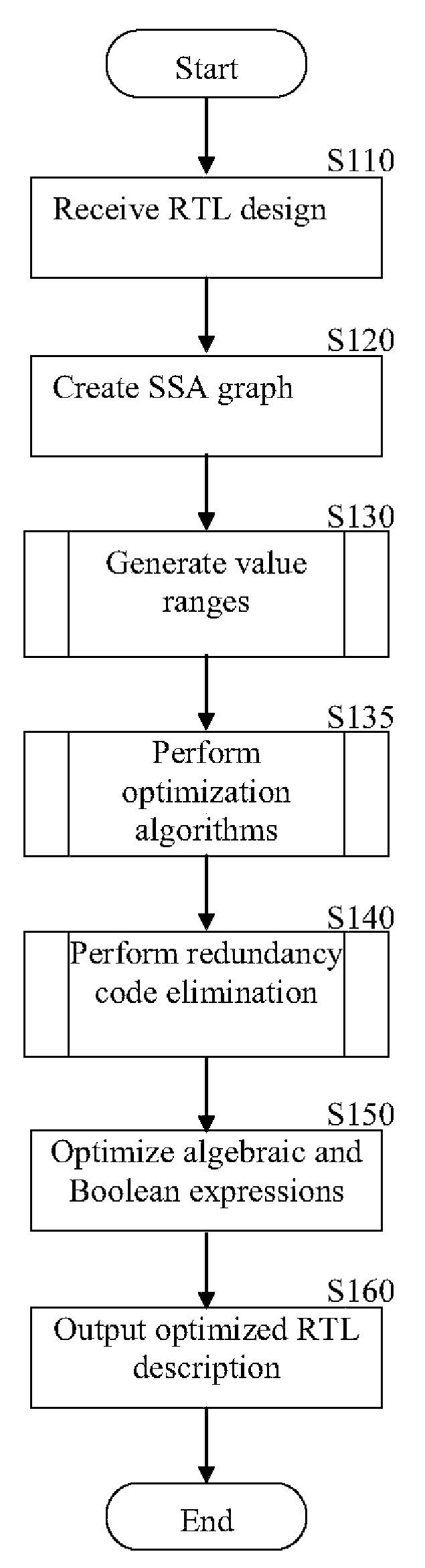
A method for accelerating the generation of an optimized netlist from a RTL representation is provided. The method optimizes a given RTL description of an integrated circuit (IC) design by: generating a static single assignment (SSA) graph; creating value range propagation for each variable in the SSA graph; and, applying one or more of a set of optimization algorithms on the SSA graph. The optimization algorithms include, but are not limited to, dead-code elimination, bitwidth analysis, redundancy elimination, iteration loop optimization, algebraic simplification and so on. These algorithms operate on a word-level description to enable fast optimization. Furthermore, the optimized RTL accelerates the overall flow of an IC design.
Owner:ATRENTA
Execution engine for executing single assignment programs with affine dependencies
ActiveUS20150356055A1Efficient executionEnergy consumptionDataflow computersSingle instruction multiple data multiprocessorsDigital dataComputer architecture
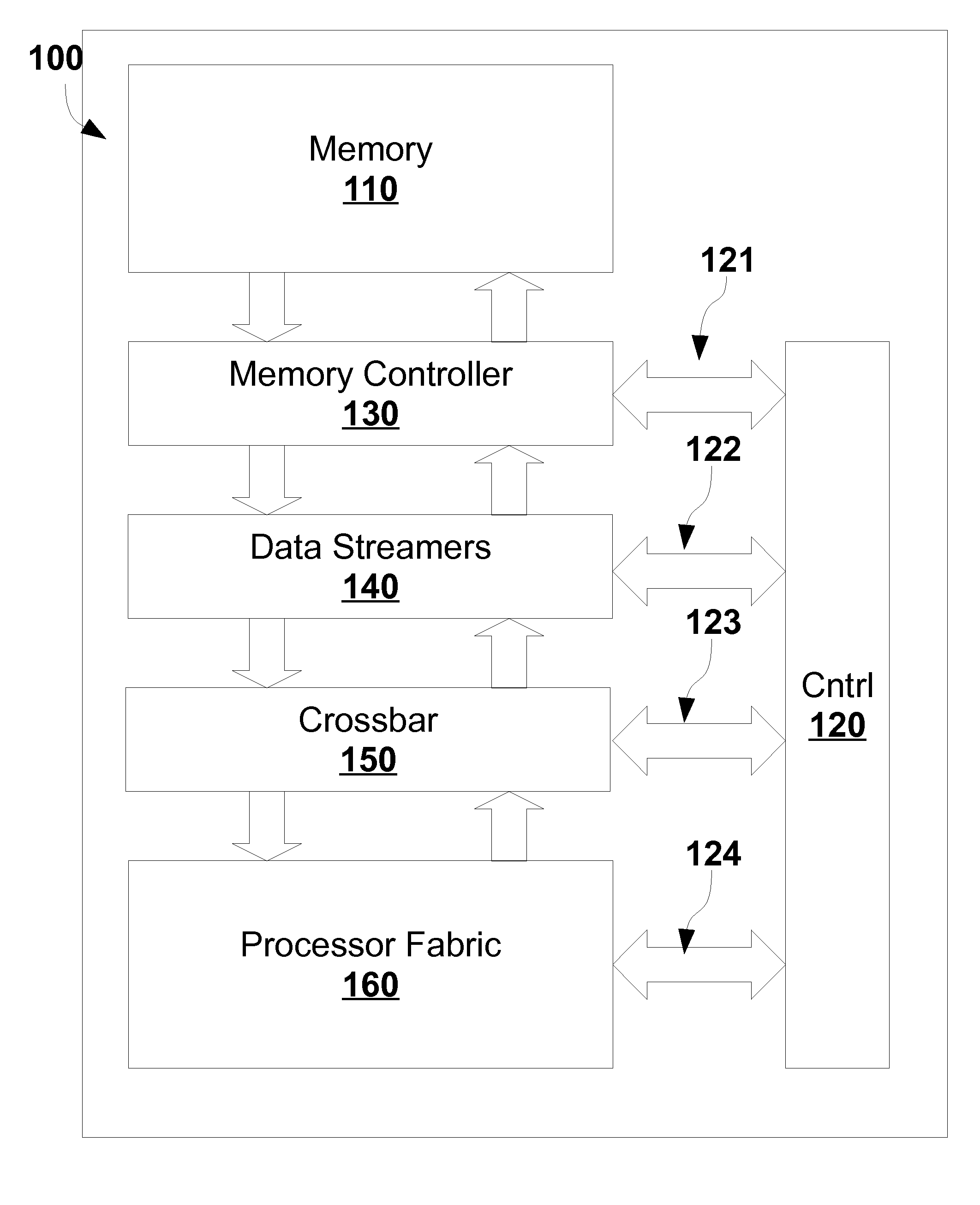
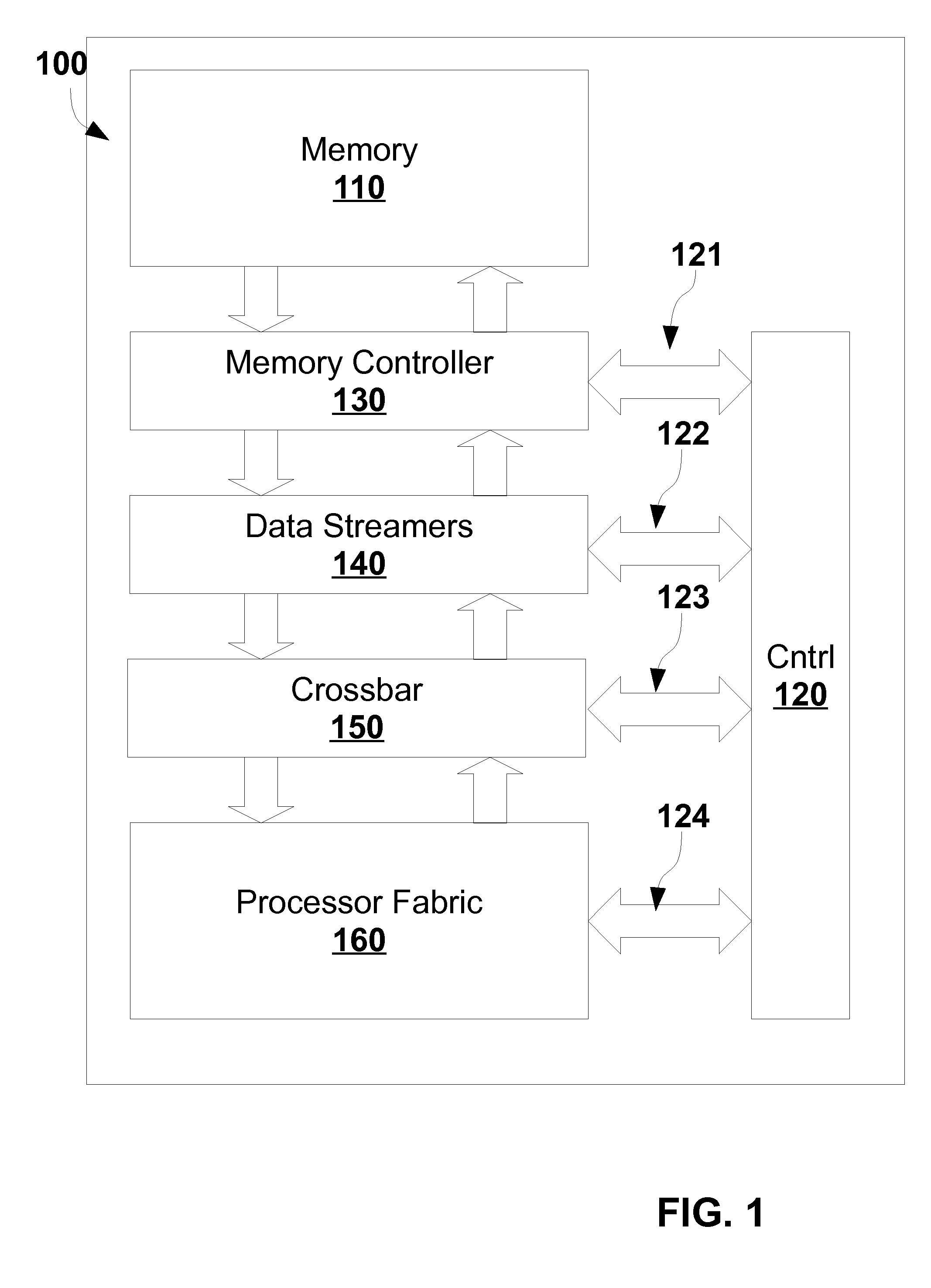
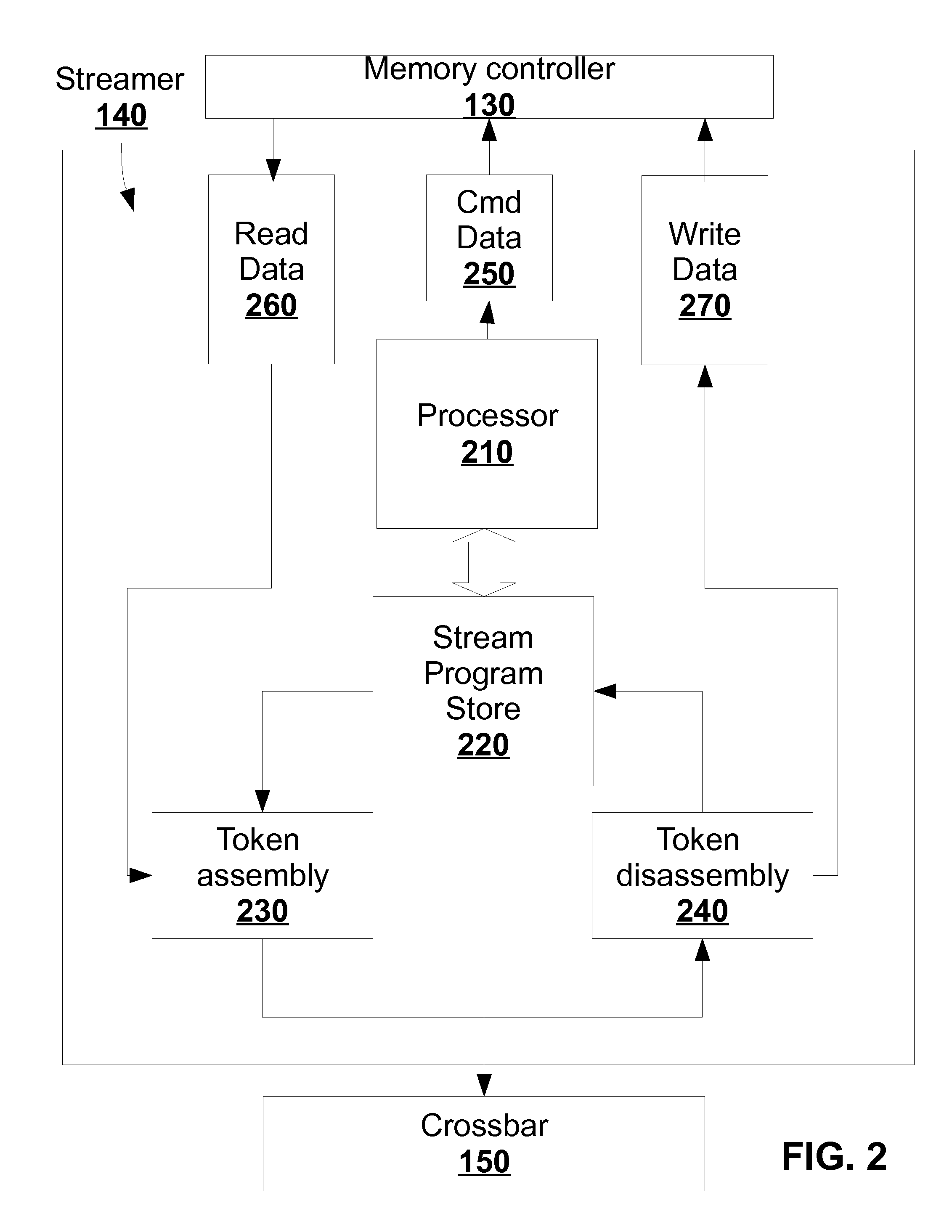
The execution engine is a new organization for a digital data processing apparatus, suitable for highly parallel execution of structured fine-grain parallel computations. The execution engine includes a memory for storing data and a domain flow program, a controller for requesting the domain flow program from the memory; and further for translating the program into programming information, a processor fabric for processing the domain flow programming information and a crossbar for sending tokens and the programming information to the processor fabric.
Owner:STILLWATER SUPERCOMPUTING
Method and apparatus for assigning wireless network packet resources to wireless terminals
ActiveCN103202078ALow communication capacityReduce congestionWireless communicationCommunications systemComputer terminal
A method in which a network apparatus 210 transmits a single assignment message comprising common assignment information directed to plural wireless terminals. The single transmitted assignment message can be used to enable channel assignment to be initiated for the plural wireless terminals, thus making more efficient use of the assignment message. This may be advantageous when a channel via which the assignment message is transmitted has a lower communication capacity than a channel via which the requests are received. In a GERAN communications system (100, FIG. 1), the effective capacity of the access grant channel can be doubled or tripled, acting to reduce congestion. This increases the probability of a wireless terminal receiving a response to a channel request which it sends. The probability of a successful data transfer following a channel request is thereby increased. Other aspects, embodiments, and features are also claimed and described.
Owner:QUALCOMM INC
Method and system for optimizing computer program
ActiveCN101876899AImprove optimization efficiencyImprove optimization effectSpecific program execution arrangementsScalar optimizationSingle assignment
The invention relates to a method and a system for optimizing a computer program. The method comprises the following steps of: step 1, acquiring value numbers of each variable and each expression through value number analytic calculations; step 2, converting a static single assignment type computer program into a semi-sparse value flow graph type computer program; step 3, calculating the initial attribute, required for performing scalar optimization, of the semi-sparse value flow graph type computer program, if the initial attribute comprises all required optimization information, performing the step 4, otherwise expanding the semi-sparse value flow graph type computer program into a sparse value flow graph type computer program, calculating the attribute required for performing the scalar optimization, and when all the attributes are calculated, performing the step 4; and step 4, performing program transformation on the semi-sparse value flow graph type computer program or the sparse value flow graph type computer program according to the calculated attributes so as to optimize the computer program. The method and the system can improve the efficiency of program optimization.
Owner:BEIJING PKUNITY MICROSYST TECH
Methods and systems for generating new vocabulary specific assignments using a continuously updated remote vocabulary database
InactiveUS20170178530A1Electrical appliancesTeaching apparatusTheoretical computer scienceSingle assignment
A method and system for generating a new vocabulary based writing assignment, performed by at least one computer processor executing computer program instructions stored on at least one non-transitory computer-readable medium, the method including: receiving additional input from the user regarding a desired subject; receiving input from the user regarding one or more students to be associated with the new writing project, wherein the one or more students are selected from a student database; generating a potential vocabulary word list; selecting one or more individual vocabulary words from the potential vocabulary word list; forming a word bank being associated with the new writing project using the selected individual vocabulary words; receiving assignment instructions from the administrator, the assignment instructions correlating to the new writing project; and generating a complete writing project including the word bank, and the assignment instructions.
Owner:BOOMWRITER MEDIA INC
Intelligent contract security auditing method based on symbol abstraction analysis
PendingCN114201754AImprove acceleration performanceIncrease coveragePlatform integrity maintainanceSingle assignmentModelling analysis
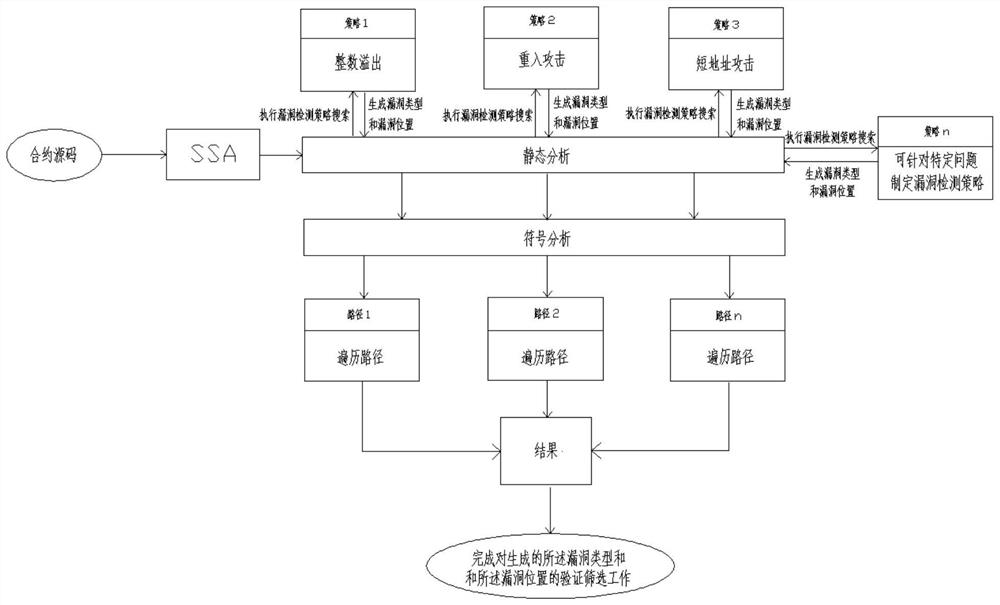
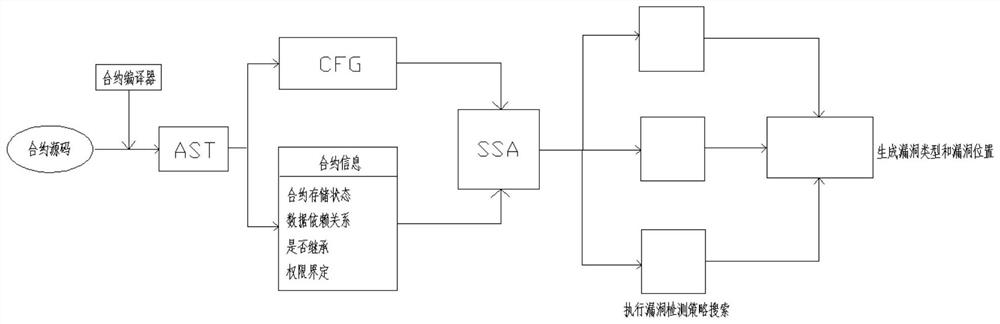
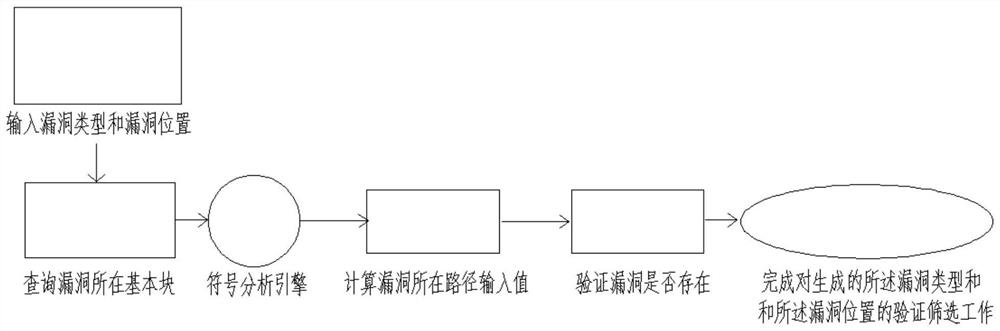
The invention discloses an intelligent contract security auditing method based on symbol abstraction analysis, and the method comprises the following steps: S1, inputting a to-be-detected contract source code, and generating a static detection file through a contract compiler; s2, traversing the static detection file to generate a control flow chart (CFG) file and collecting contract information; s3, converting the CFG into a single assignment statement text SSA by using the contract information, performing modeling analysis on the single assignment statement text SSA, and traversing and collecting contract attribute information; s4, integrating the contract attribute information as input, executing vulnerability detection strategy search, and generating vulnerability types and vulnerability positions; s5, the vulnerability type and the vulnerability position serve as input of a symbolic analysis engine, a basic block where the vulnerability is located is inquired, the symbolic analysis engine analyzes the vulnerability type and the vulnerability position, traceability traversal is conducted on an execution path of the vulnerability, and the vulnerability is obtained. And completing verification and screening work of the generated vulnerability type and the vulnerability position.
Owner:HAINAN NORMAL UNIV
Data processing method, device and system
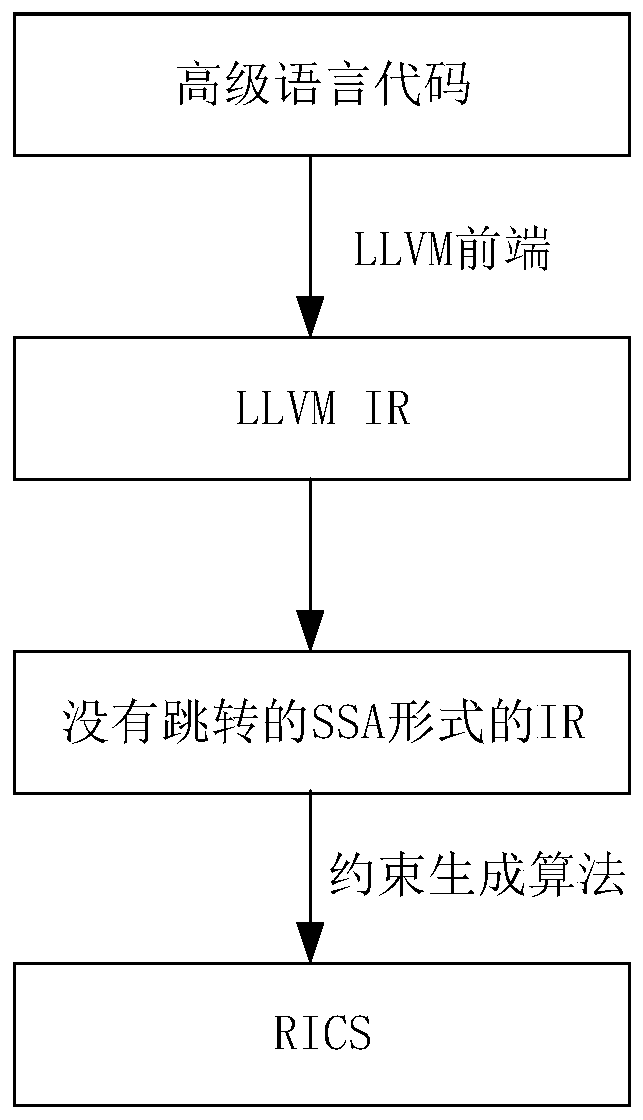
PendingCN110209397AImprove simplicityImplement conversion processingCode compilationEnergy efficient computingPasswordSingle assignment
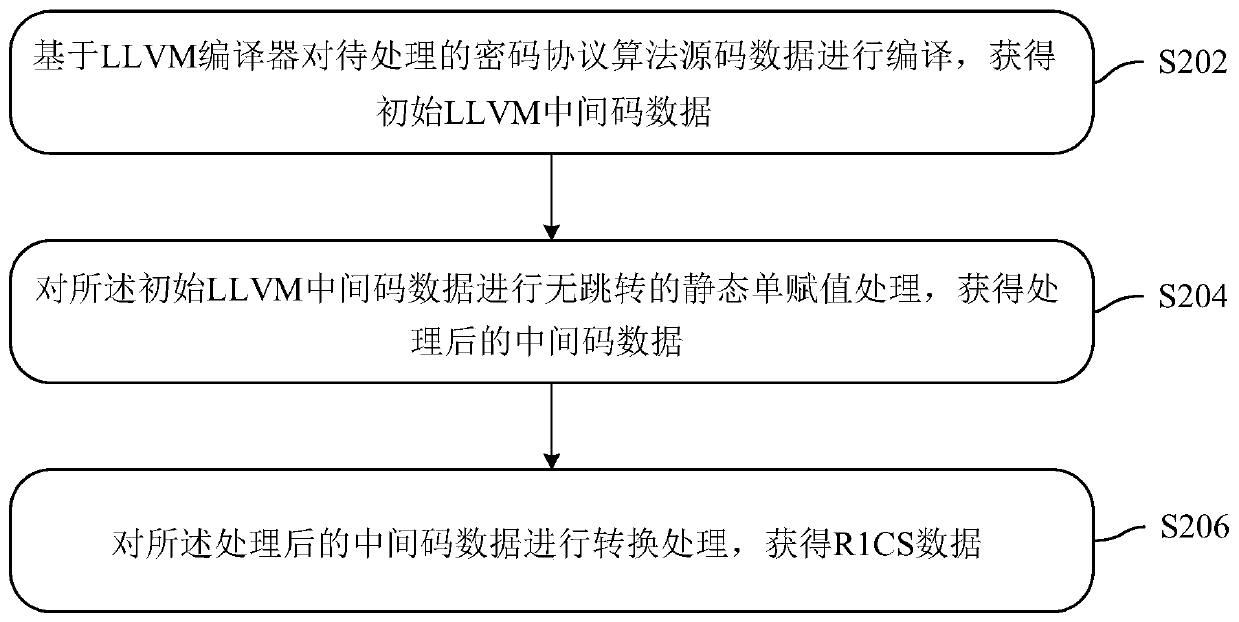
The embodiment of the invention discloses a data processing method, device and system. The data processing method comprises the steps: compiling password protocol algorithm source code data to be processed based on an LLVM compiler, and obtaining initial LLVM intermediate code data; performing skip-free static single assignment processing on the initial LLVM intermediate code data to obtain processed intermediate code data; and performing conversion processing on the processed intermediate code data to obtain R1CS data. By utilizing each embodiment of the specification, the source code data ofthe cryptographic algorithm can be compiled to the R1CS data more simply and efficiently.
Owner:JUZIX TECH SHENZHEN CO LTD
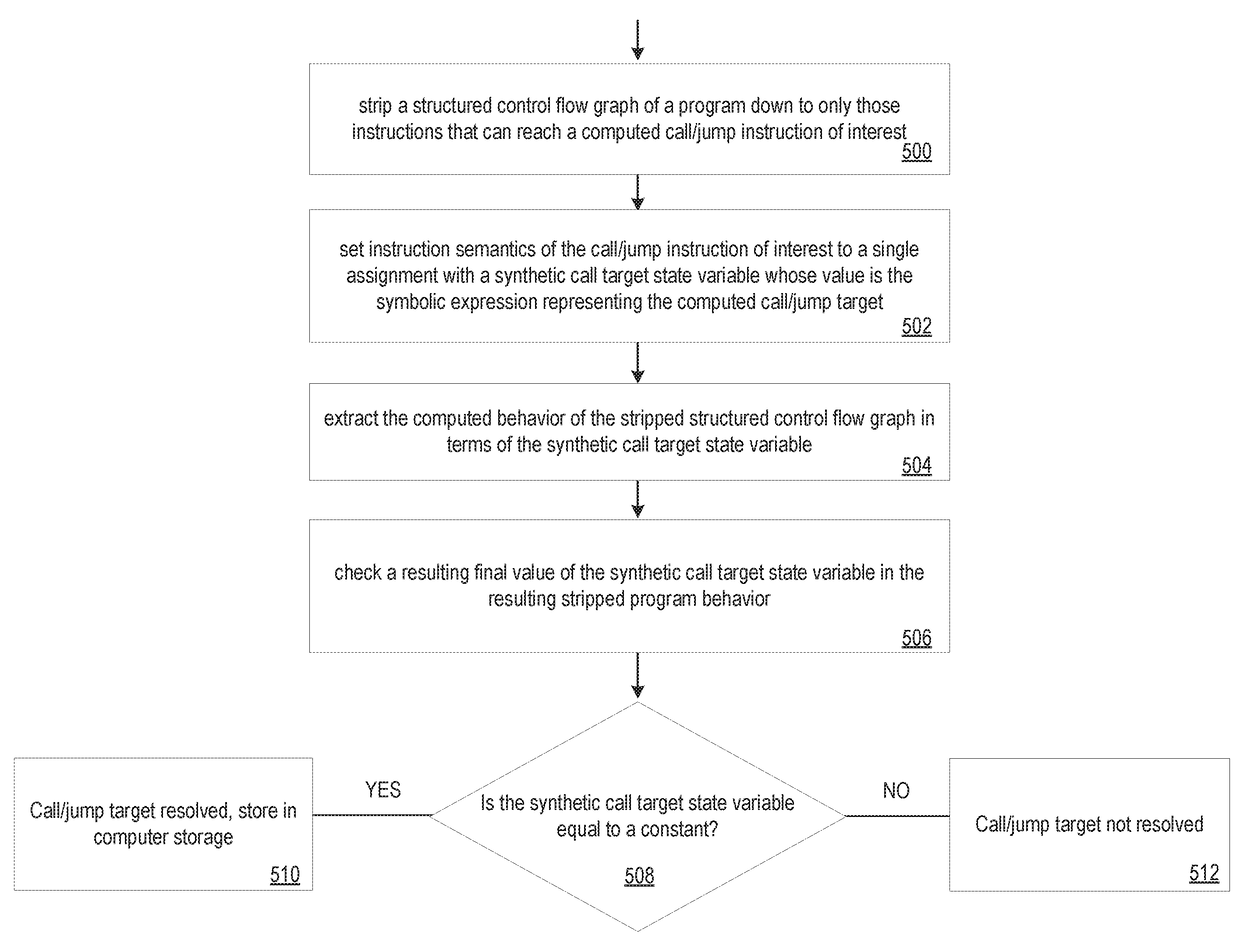
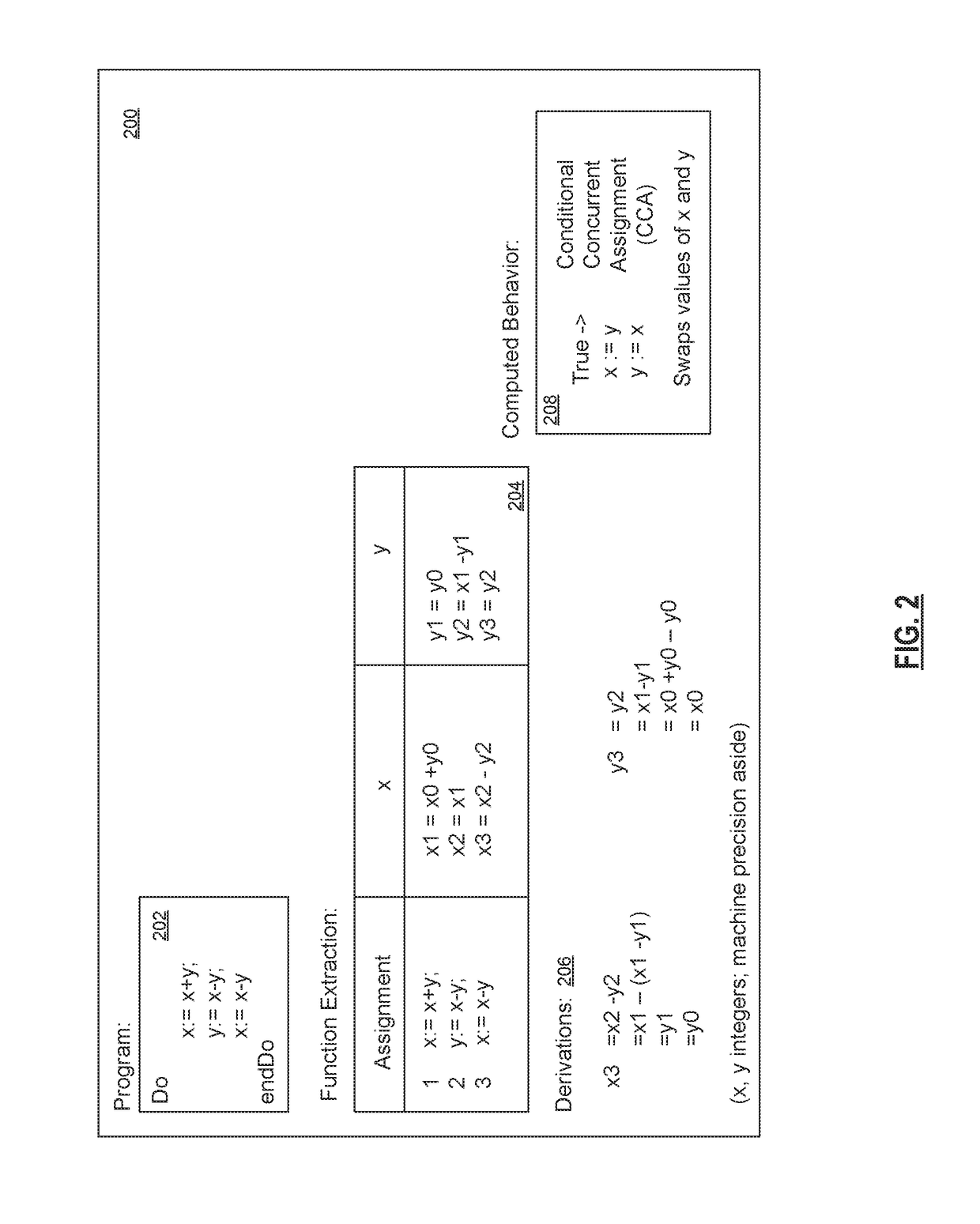
Computed call/jump target resolution via behavior computation
ActiveUS20180081699A1Error detection/correctionConcurrent instruction executionControl flowAlgorithm
A method and system resolving a computed call / jump target with computed behavior. The method begins with stripping a structured control flow graph of a computer program down to only those instructions that can reach a computed call / jump instruction of interest. The method continues by setting instruction semantics of the computed call / jump instruction of interest to a single assignment with a synthetic call target state variable whose value is a symbolic expression representing the computed call / jump target. The method continues by extracting a computed behavior of the stripped structured control flow graph in terms of the synthetic call target state variable and checking a resulting final value of the synthetic call target state variable in the resulting stripped program behavior. When the synthetic call target state variable is equal to a constant, the computed call / jump target has been resolved to the constant value, which is stored to computer storage.
Owner:LENVIO INC
System and method for static detection and categorization of information-flow downgraders
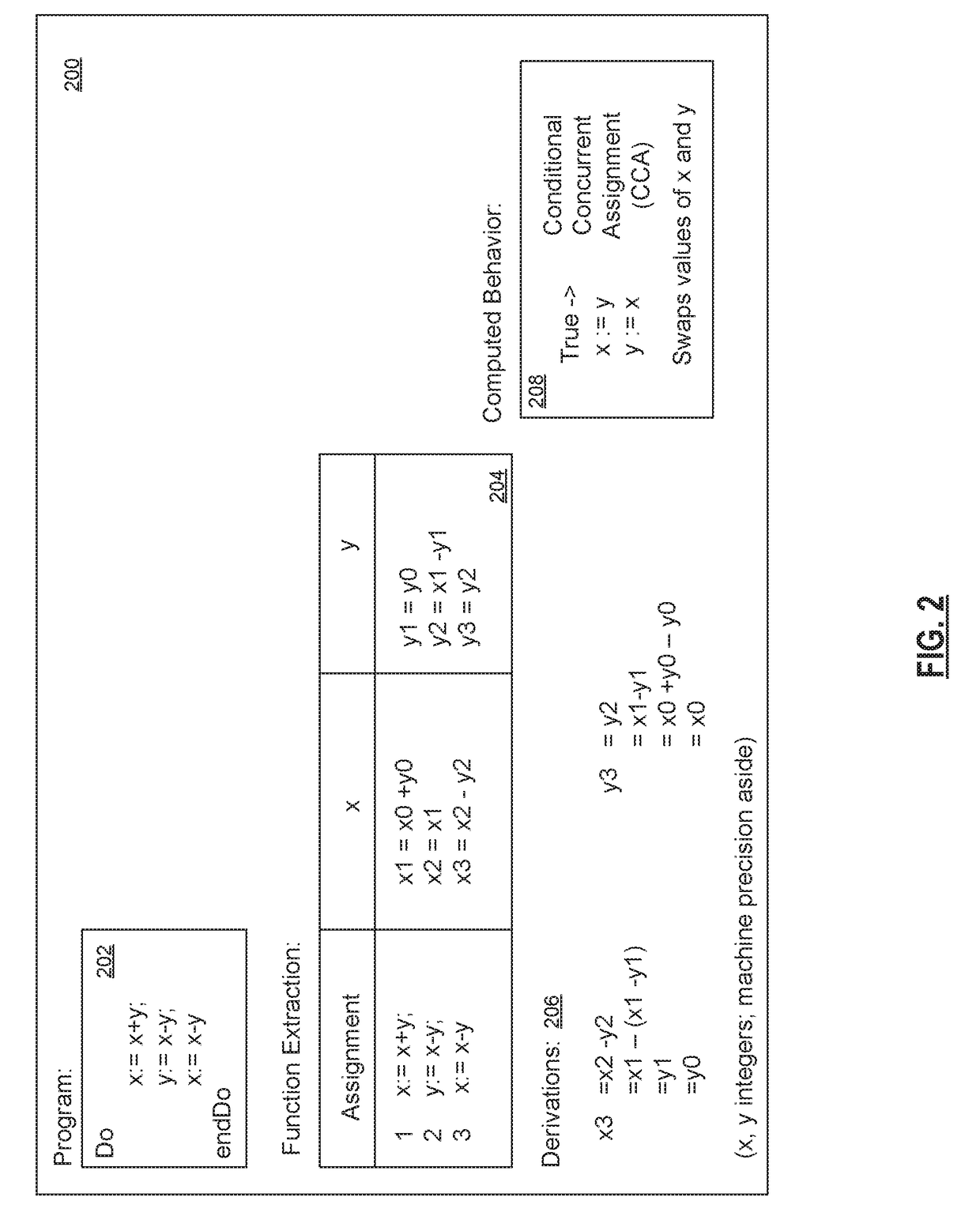
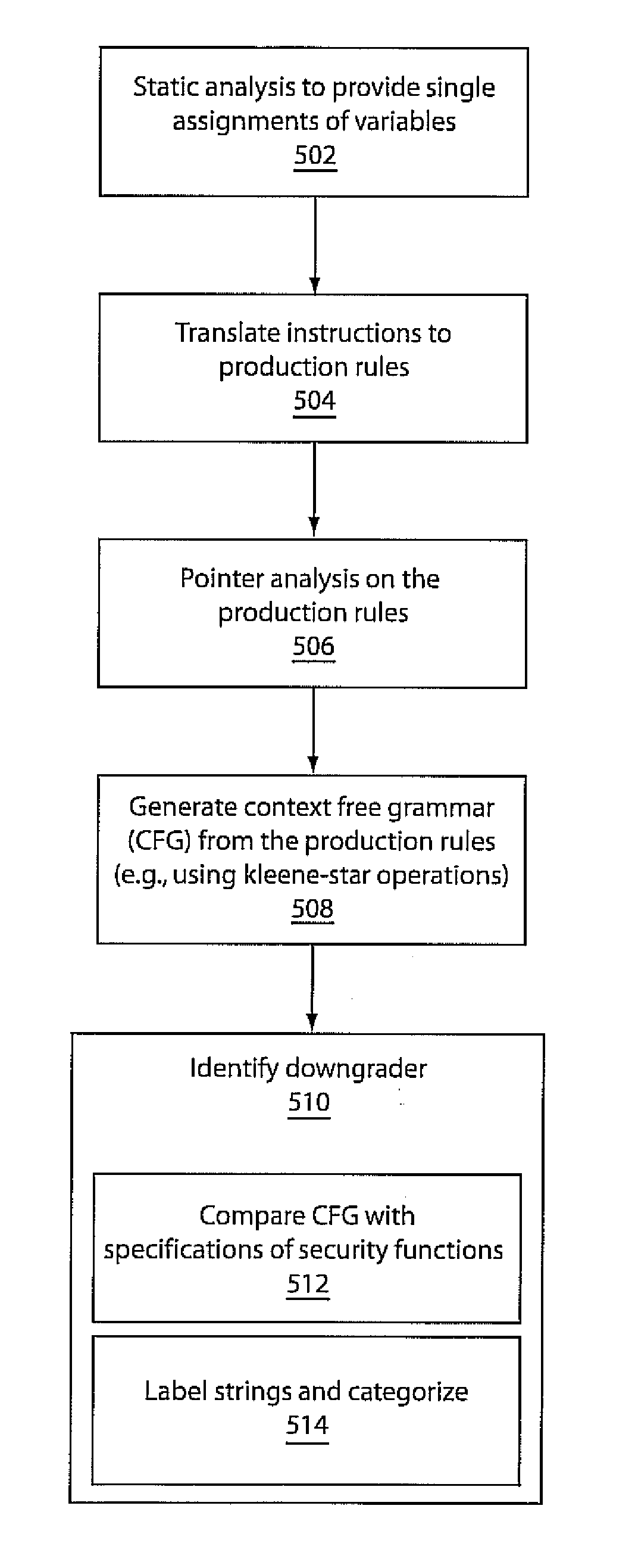
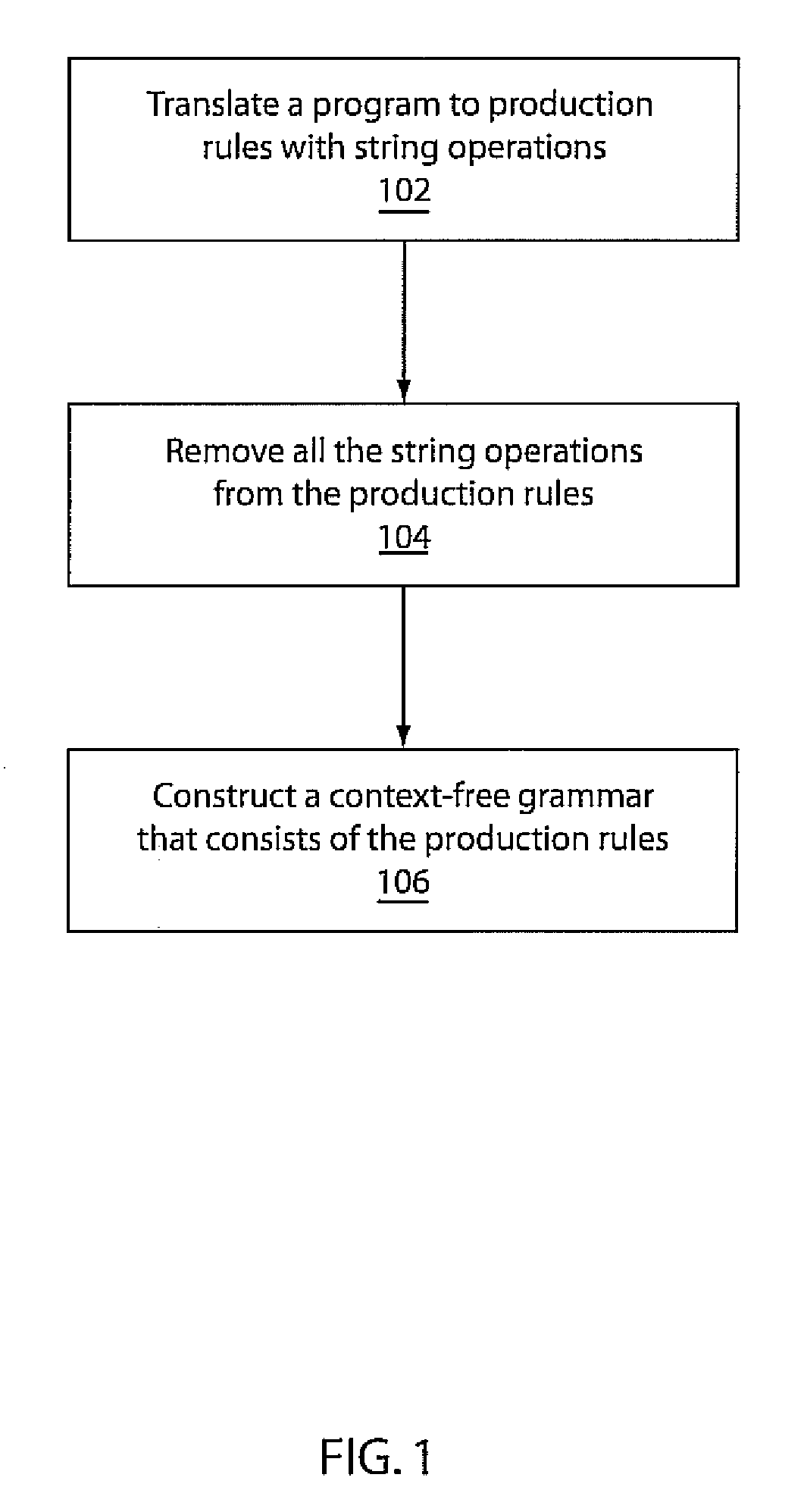
ActiveUS9275246B2Digital data processing detailsDigital data protectionString operationsTheoretical computer science
A system and method for static detection and categorization of information-flow downgraders includes transforming a program stored in a memory device by statically analyzing program variables to yield a single assignment to each variable in an instruction set. The instruction set is translated to production rules with string operations. A context-free grammar is generated from the production rules to identify a finite set of strings. An information-flow downgrader function is identified by checking the finite set of strings against one or more function specifications.
Owner:INT BUSINESS MASCH CORP
Concurrent static single assignment for general barrier synchronized parallel programs
InactiveUS8566801B2Specific program execution arrangementsMemory systemsTheoretical computer scienceSingle assignment
Techniques for generating concurrent static single assignment (CSSA) are provided. The techniques include generating a clocked control flow graph of a program, for each thread of the program created through async instruction, determining each part of the program that can execute concurrently with each thread to create a pair comprising a thread and a parallel program part, for each pair that can execute concurrently, using one or more flow equations to perform node-by-node matching, and using the node-by-node matching to generate CSSA form for the program.
Owner:IBM CORP +1
Computed call/jump target resolution via behavior computation
A method and system resolving a computed call / jump target with computed behavior. The method begins with stripping a structured control flow graph of a computer program down to only those instructions that can reach a computed call / jump instruction of interest. The method continues by setting instruction semantics of the computed call / jump instruction of interest to a single assignment with a synthetic call target state variable whose value is a symbolic expression representing the computed call / jump target. The method continues by extracting a computed behavior of the stripped structured control flow graph in terms of the synthetic call target state variable and checking a resulting final value of the synthetic call target state variable in the resulting stripped program behavior. When the synthetic call target state variable is equal to a constant, the computed call / jump target has been resolved to the constant value, which is stored to computer storage.
Owner:LENVIO INC
A Genetic Algorithm-Based Structural Optimization Method for Low-Frequency Electromagnetic Sensors
ActiveCN106446447BBreak through the limitations of a single assignment operationRealize intelligent optimizationDesign optimisation/simulationSpecial data processing applicationsSingle assignmentModel parameters
The invention relates to a structure optimization method for a low frequency electromagnetic sensor based on a genetic algorithm. The method is suitable for the structure design of a COMSOL analog low frequency electromagnetic sensor model and the shape reconstruction for defect detecting and belongs to the field of nondestructive detection. The method comprises the following steps: on the basis of simplifying the COMSOL analog low frequency electromagnetic sensor model, parameterizing an optimization model of the COMSOL analog low frequency electromagnetic sensor and defining the reading paths for different variables; setting a genetic optimized fitness function and main parameters including an algorithm running parameter and a control parameter; compiling a dynamic link function, calling for the COMSOL model by MATLAB and constructing a channel for mutually transferring data; calling a COMSOL genetic algorithm for optimizing the parameters of the low frequency electromagnetic sensor model, and while acquiring the fitness function meeting the convergence criterion, acquiring an optimized result, namely, the optimized structure parameter of the low frequency electromagnetic sensor. According to the method provided by the invention, the limitation of the COMSOL single assignment operation is broken through and the intelligent optimization of the COMSOL model parameters is realized.
Owner:BEIJING UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com