Intelligent contract security auditing method based on symbol abstraction analysis
An abstract analysis, smart contract technology, applied in computer security devices, computing, instruments, etc., can solve the problems of low contract coverage, false positives and false positives, low contract coverage, etc., to improve the detection effect and accuracy, Enhanced coverage and wide detection range
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] In order to better understand the technical content of the present invention, specific embodiments are provided below, and the present invention is further described in conjunction with the accompanying drawings.
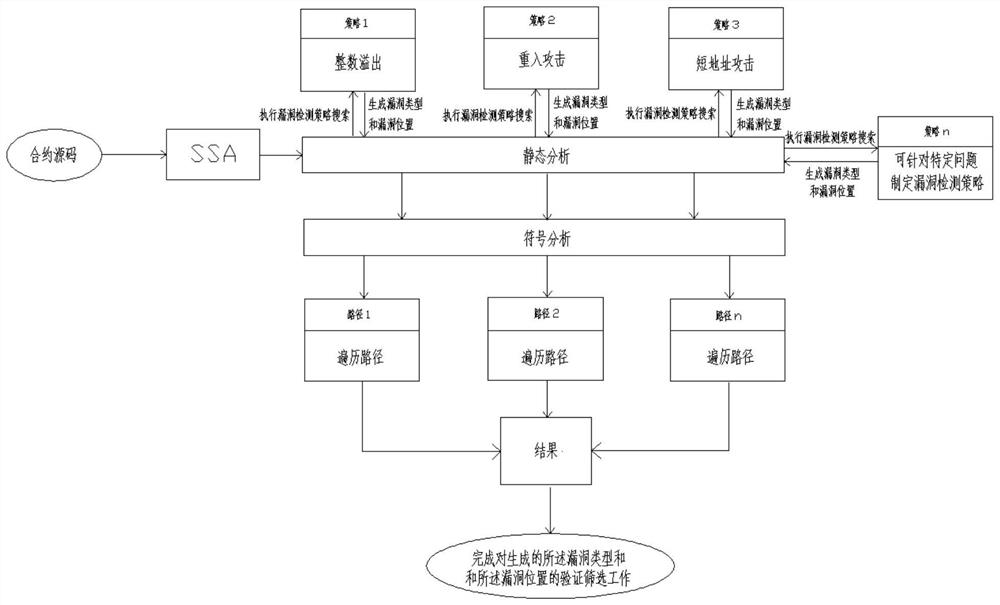
[0025] see Figure 1 to Figure 3 , the present invention is a smart contract security audit method based on symbolic abstraction analysis, comprising the following steps:
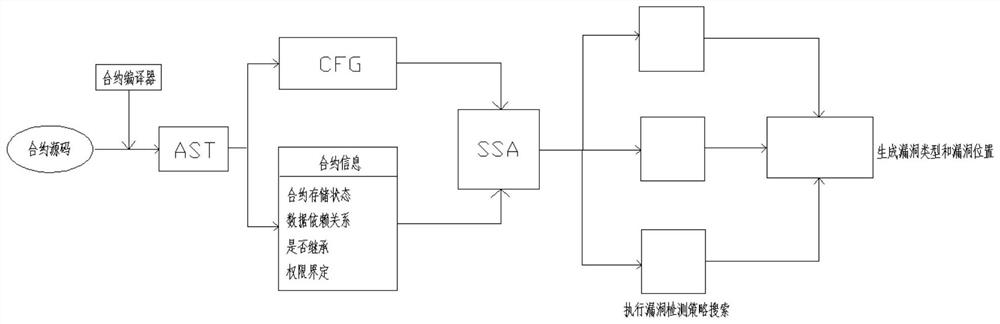
[0026] S1: Input the source code of the contract to be detected, and generate a static detection file through the contract compiler;
[0027] S2: traverse the static detection file to generate a control flow chart file CFG and collect contract information;
[0028] S3: The flowchart file CFG converts the contract information into a single-assignment statement text SSA, performs modeling analysis on the single-assignment statement text SSA, and traverses to collect contract attribute information;
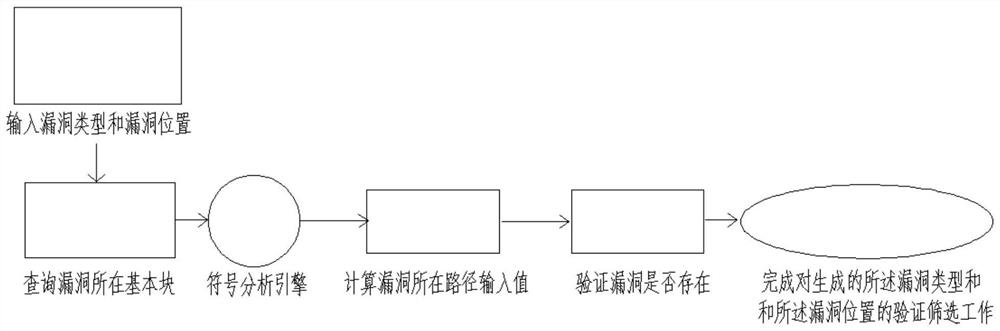
[0029] S4: Integrate the contract attribute information as input, execute vulnerability det...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com