Patents
Literature
46 results about "Dead code" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer programming, dead code is a section in the source code of a program which is executed but whose result is never used in any other computation. The execution of dead code wastes computation time and memory.
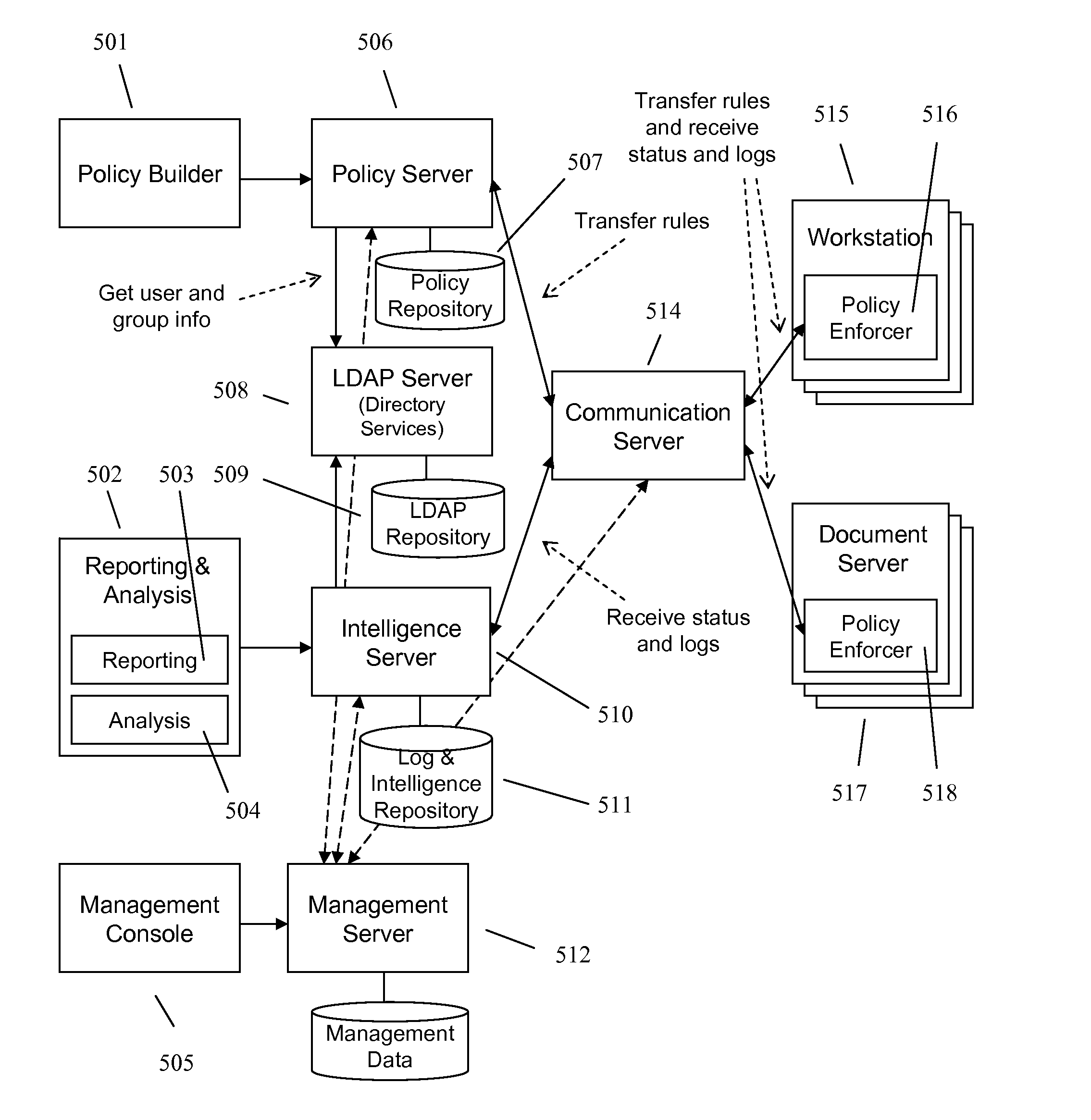
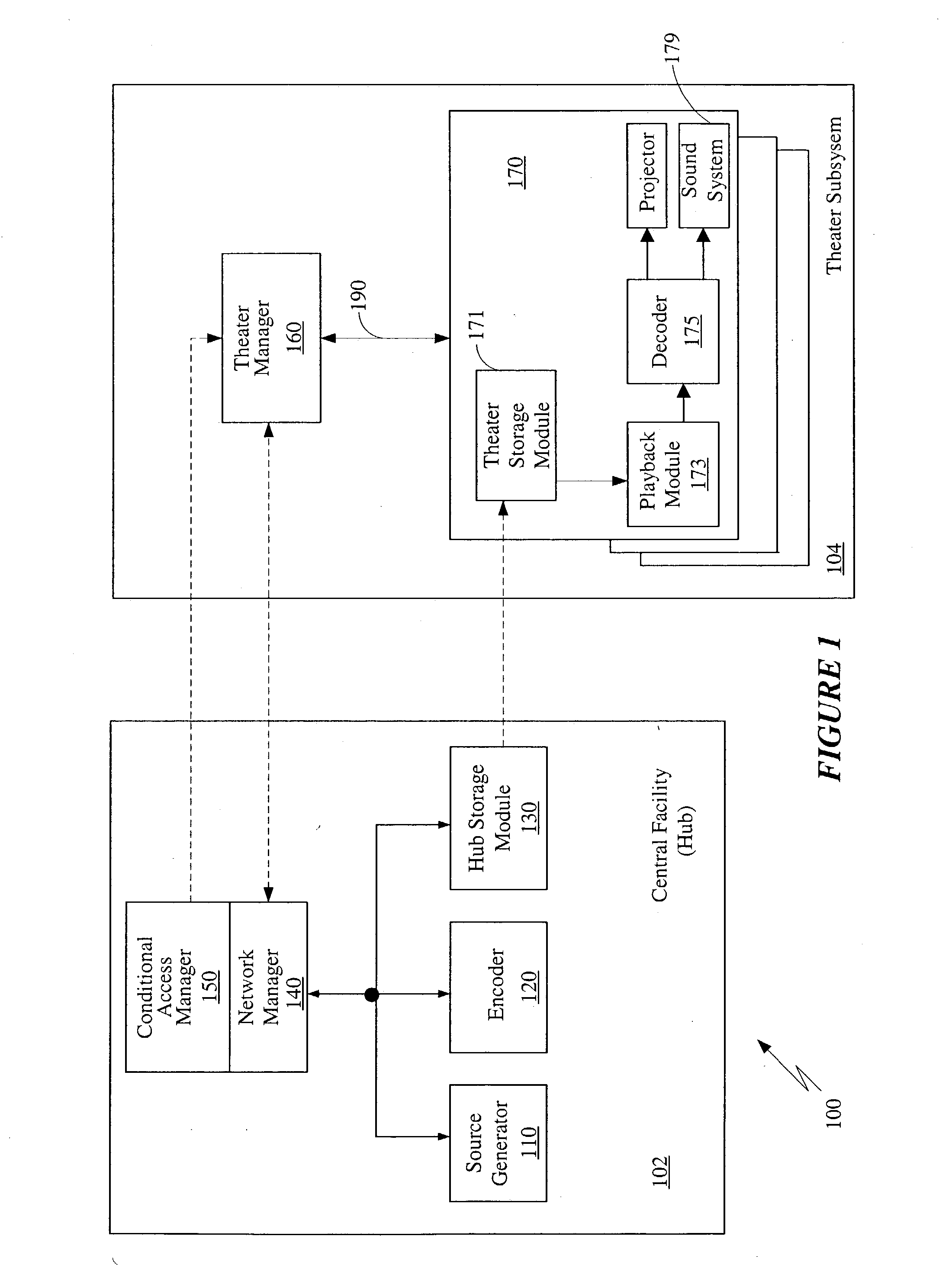
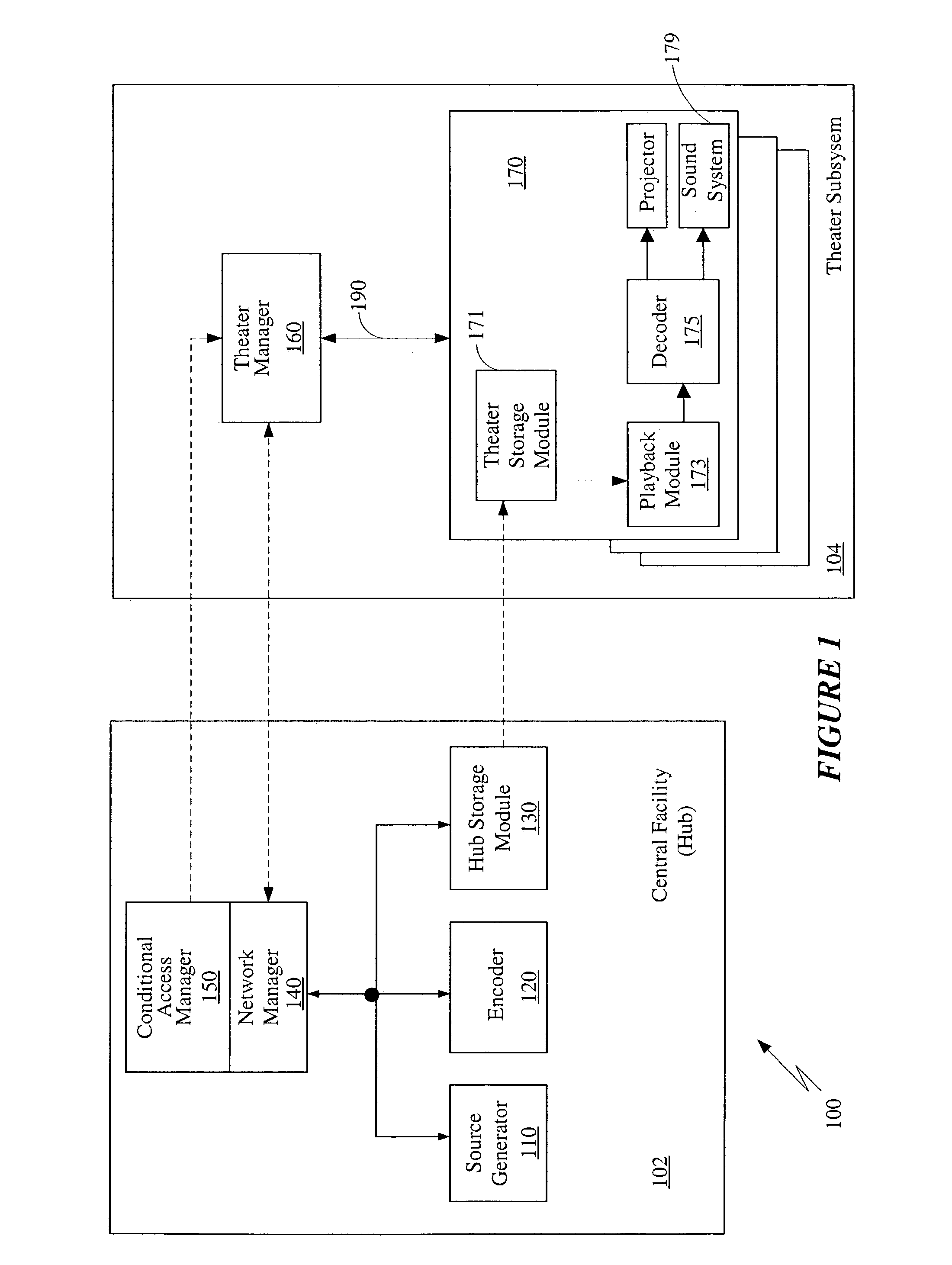
Techniques of optimizing policies in an information management system
In an information management system, policies are optimized before they are associated to a device in order to increase evaluation speed or reduce space requirements, or both. Optimization techniques may include common subexpression elimination, constant folding, constant propagation, comparison optimization, dead code or subexpression removal, map or lookup table generation, policy rewriting, redundant policy elimination, heuristic-based policy ordering, or policy-format transformation, and combinations of these.
Owner:NEXTLABS
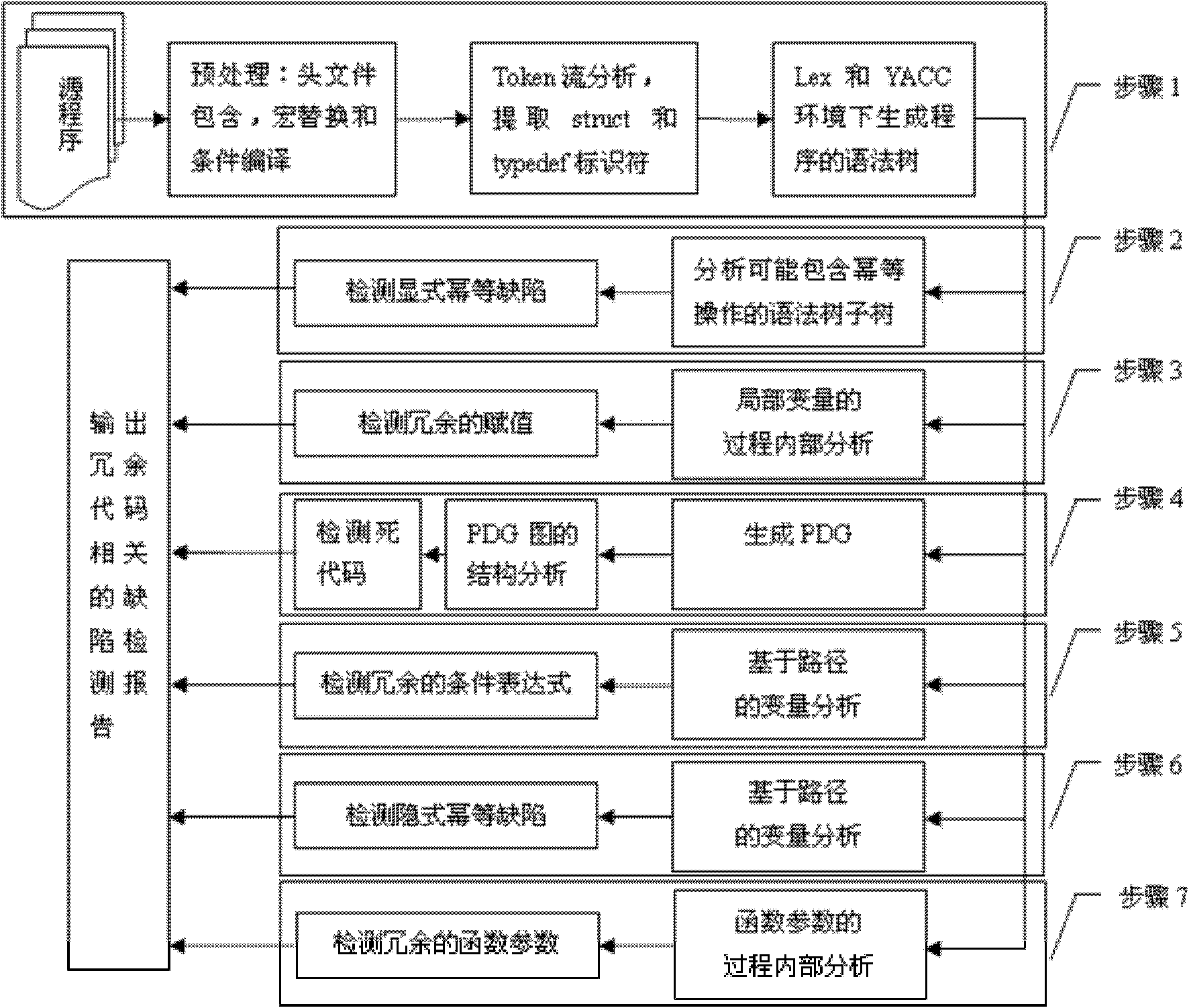
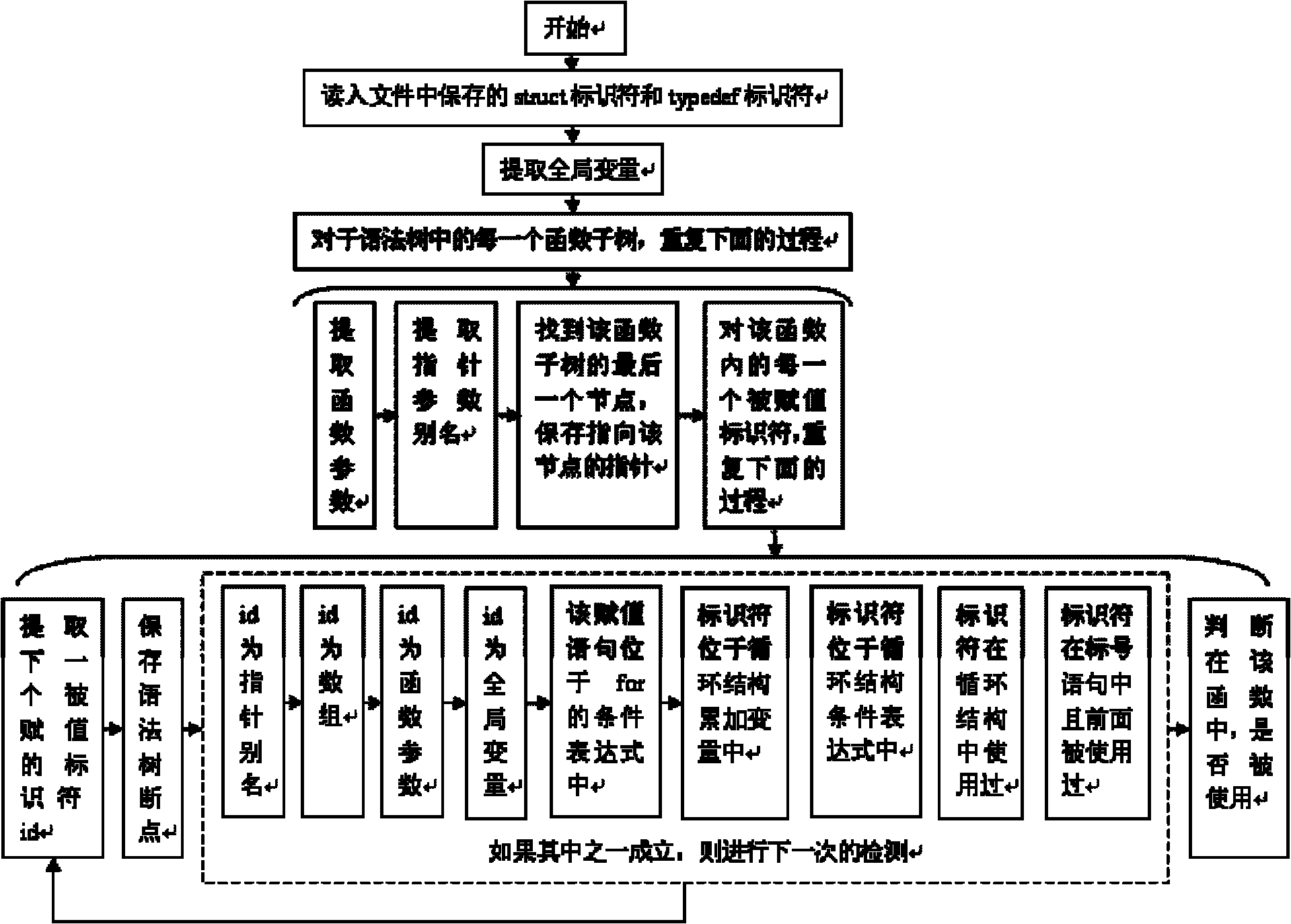
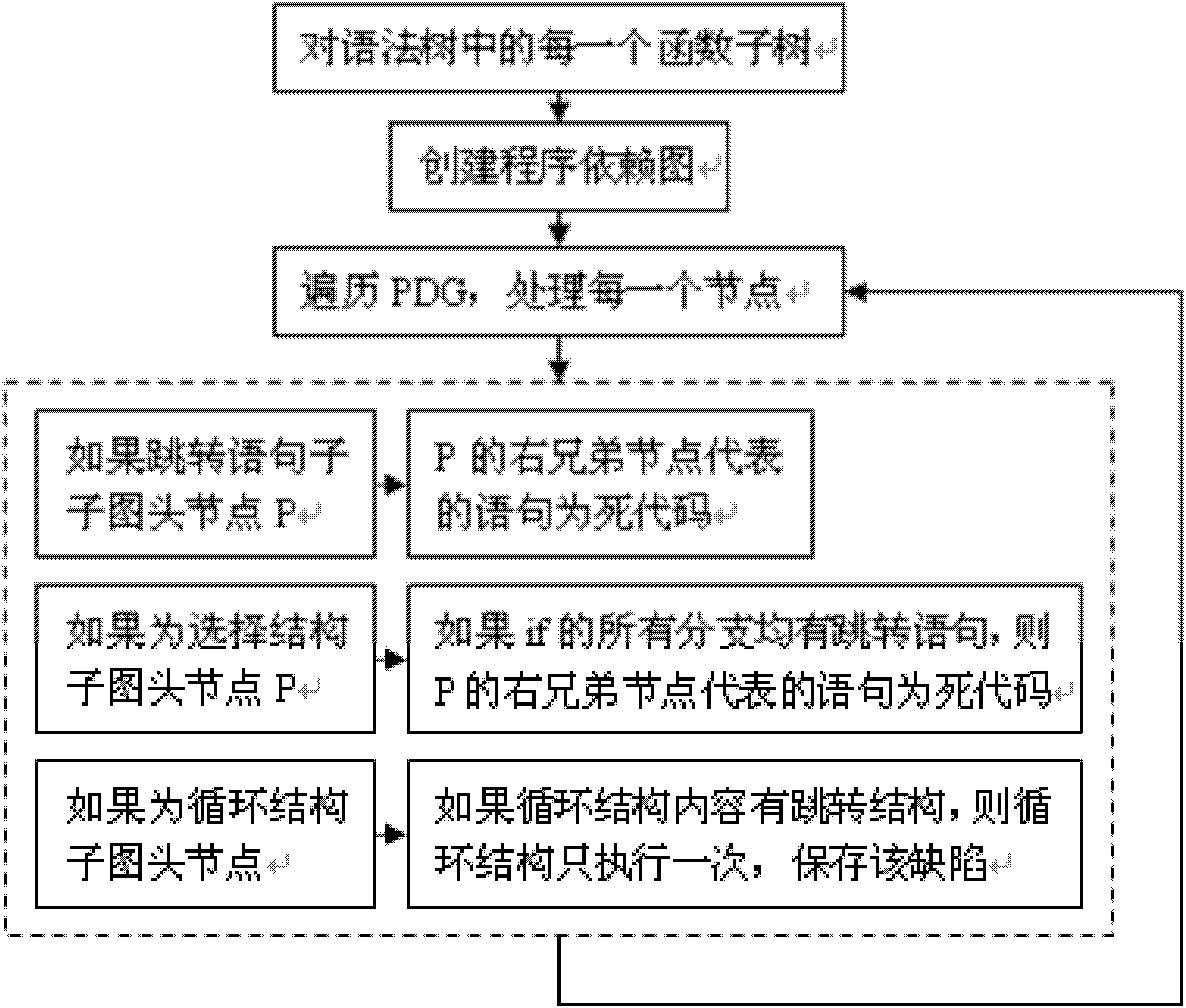
Method for detecting redundant code defects based on static analysis
InactiveCN102231134AReduce false detection rateReduce missed detection rateSoftware testing/debuggingStatic timing analysisAbstract syntax tree
The invention discloses a method for detecting redundant code defects based on static analysis, for solving the problem lacking of a mature method for detecting redundant codes and related defects currently. The method comprises the following steps of: 1, inputting a program to be tested; analyzing the program into an abstract syntax tree; 2, analyzing statements possibly including operations of explicit power and the like; detecting the operations of the explicit power and the like; 3, for locally defined variables, detecting redundant assignment statements by using an internal process analysis method; 4, traversing the abstract syntax tree of the program; searching structures including the defects on the basis of a standardized program dependency graph; detecting dead codes; 5, detecting redundant conditional expressions; 6, detecting operations of implicit power and the like; and 7, detecting redundant function parameters; and giving a defect detection report according to the six defect detection results obtained in the steps 2-7. The method disclosed by the invention is applicable for analyzing large-scale program codes.
Owner:HARBIN INST OF TECH
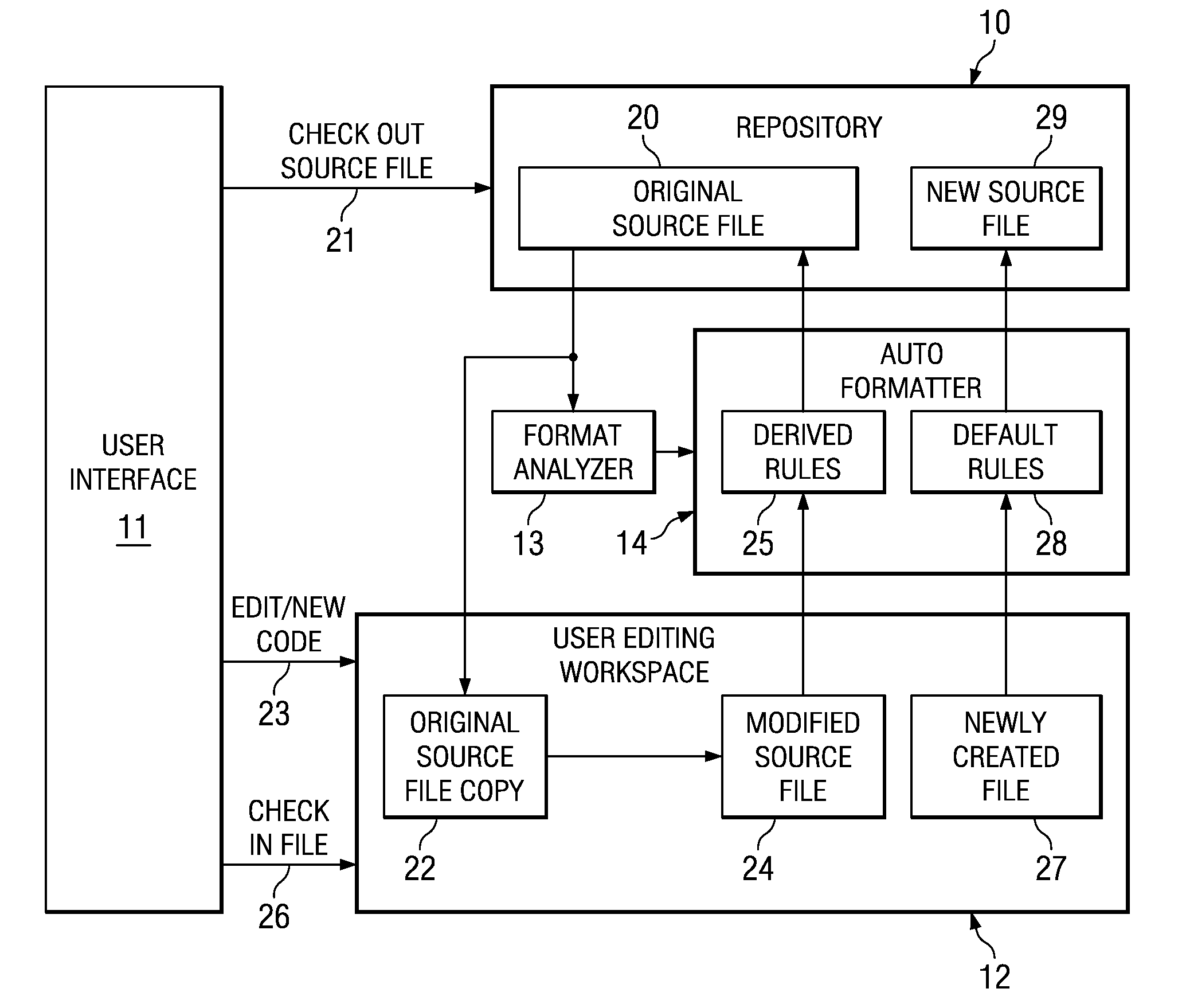
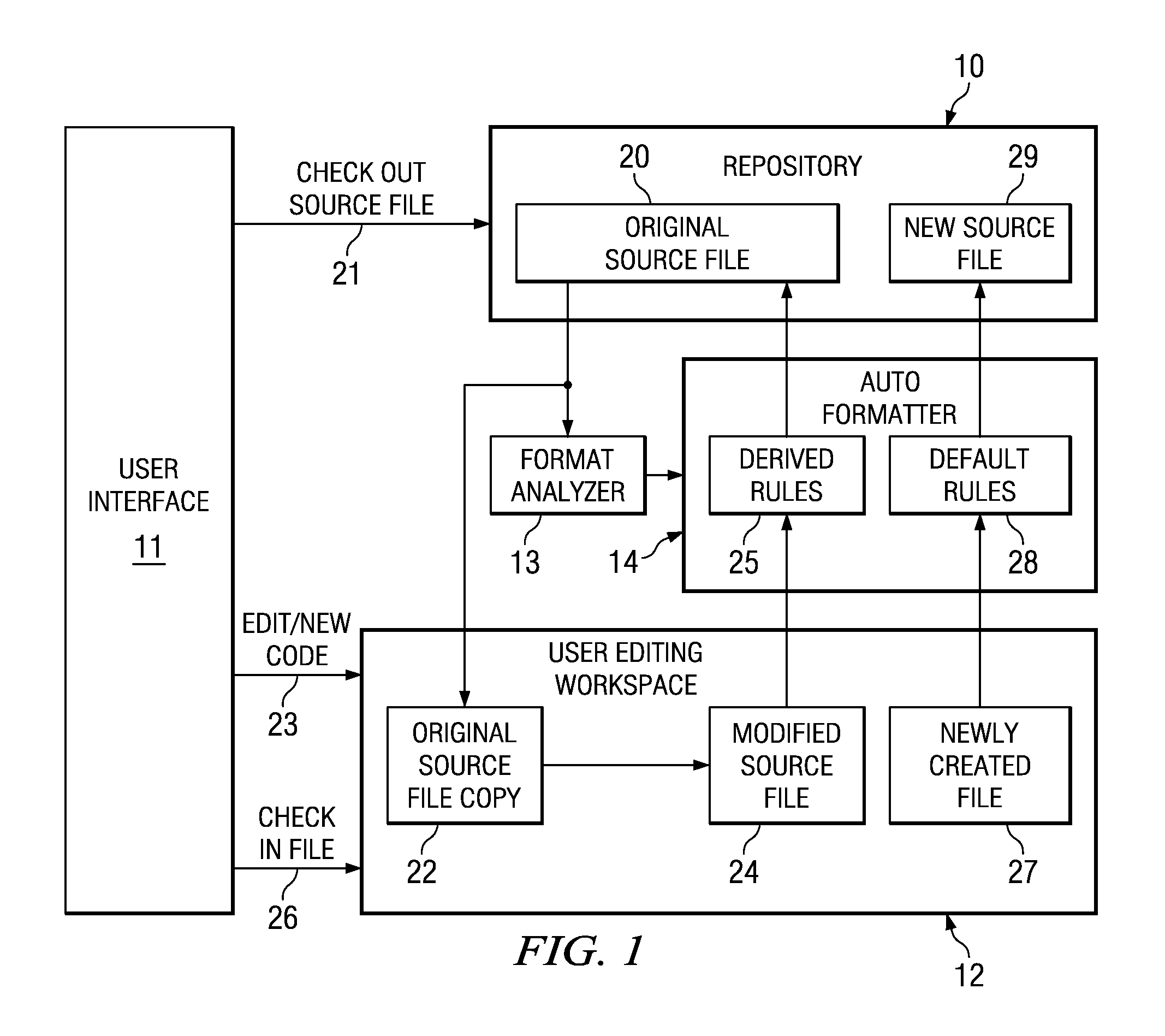
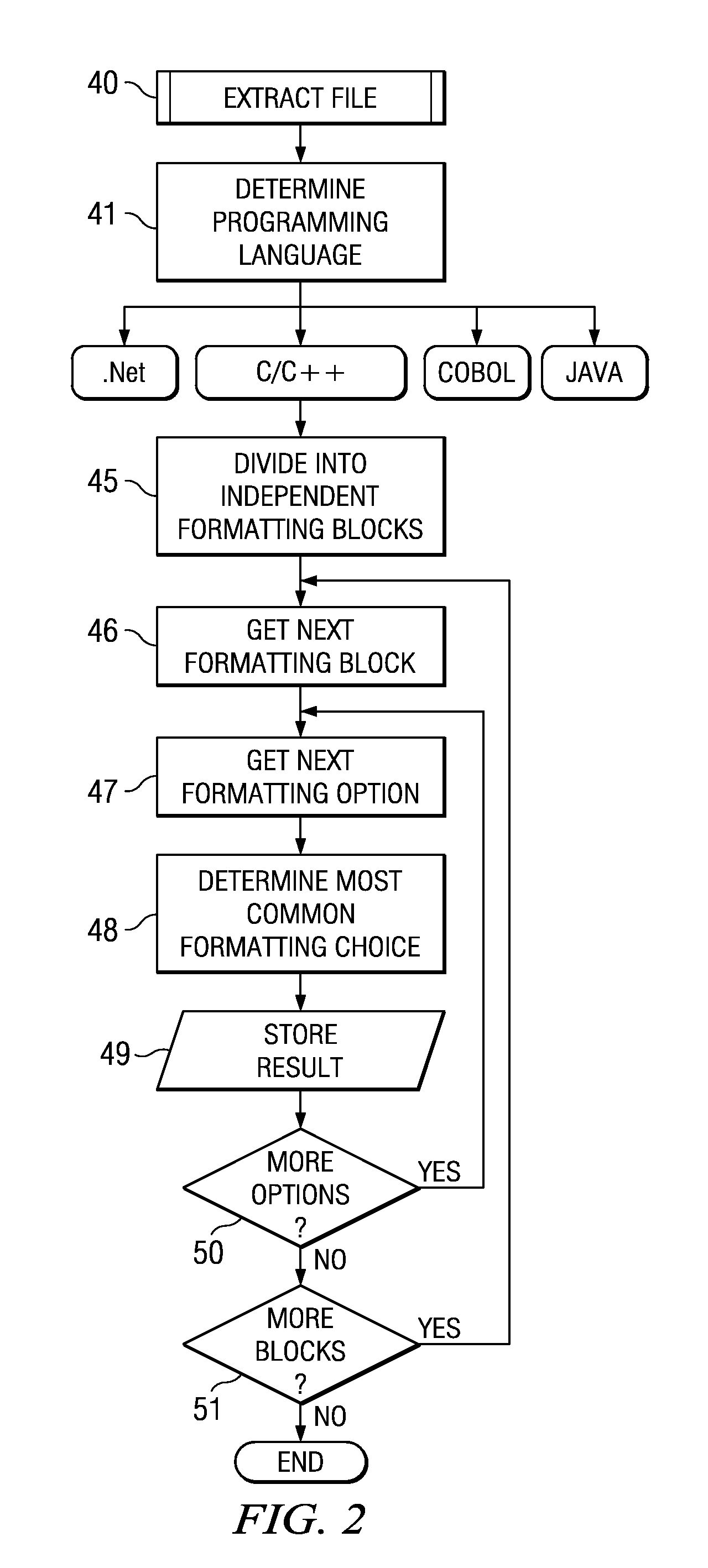
Automatic Formatting of Computer Program Source Code
ActiveUS20080229290A1Reduce the possibilityEasy to identifyError detection/correctionVersion controlDead codeUser input
A method and system is provided for auto formatting changes to computer program source code stored in a code repository. The code comprises a plurality of separately identifiable sections each of which includes non-functional formatting information which differs between at least some of the sections. In response to a user input request a selected source code section is extracted and edited via a user interface. A set of formatting rules is determined automatically from at least the code section being edited. This set of rules is one of a plurality of possible sets corresponding to the separately identifiable sections. The edited code is then formatted according to the determined set of formatting rules and stored in the code repository.
Owner:IBM CORP
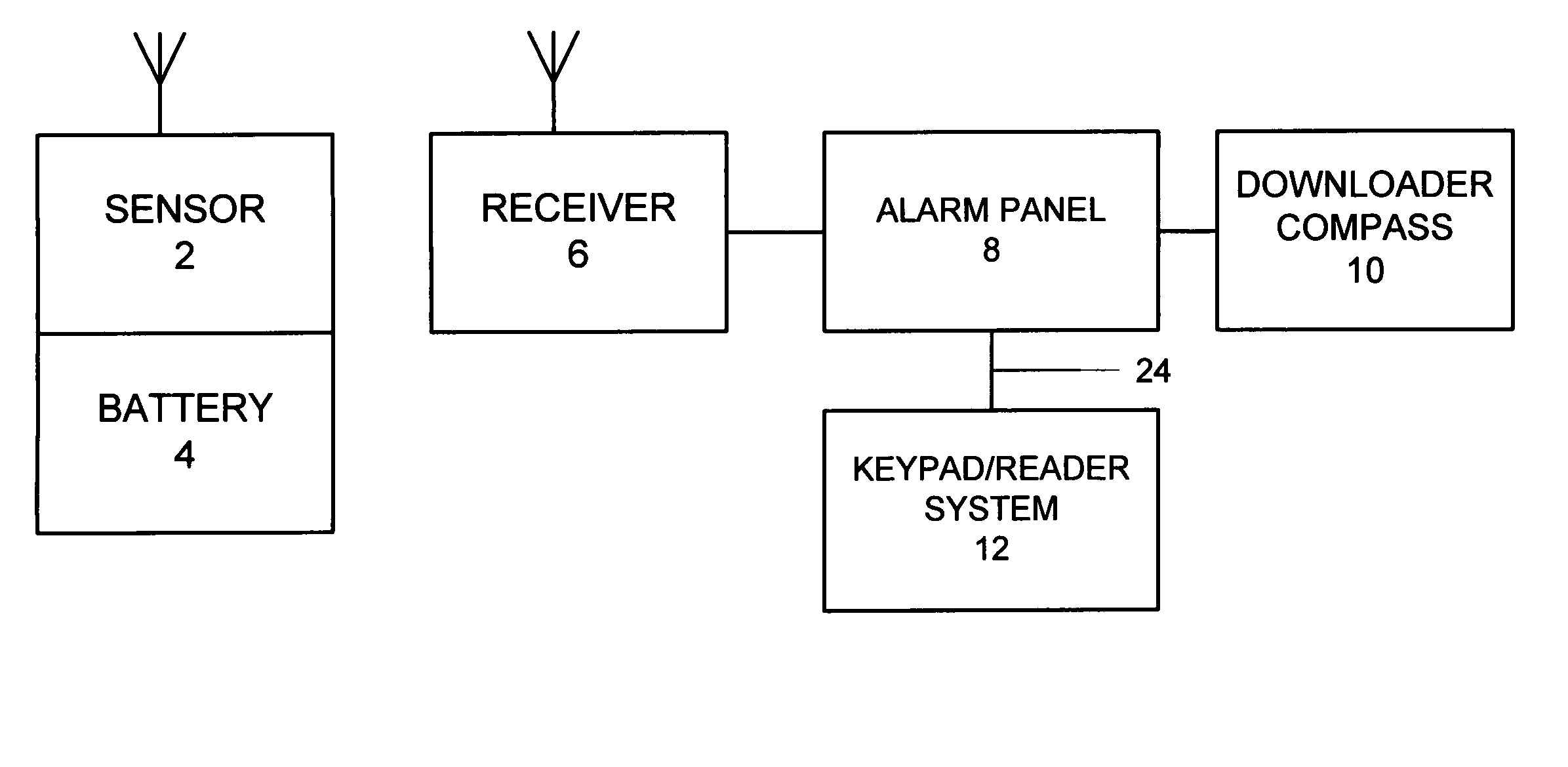
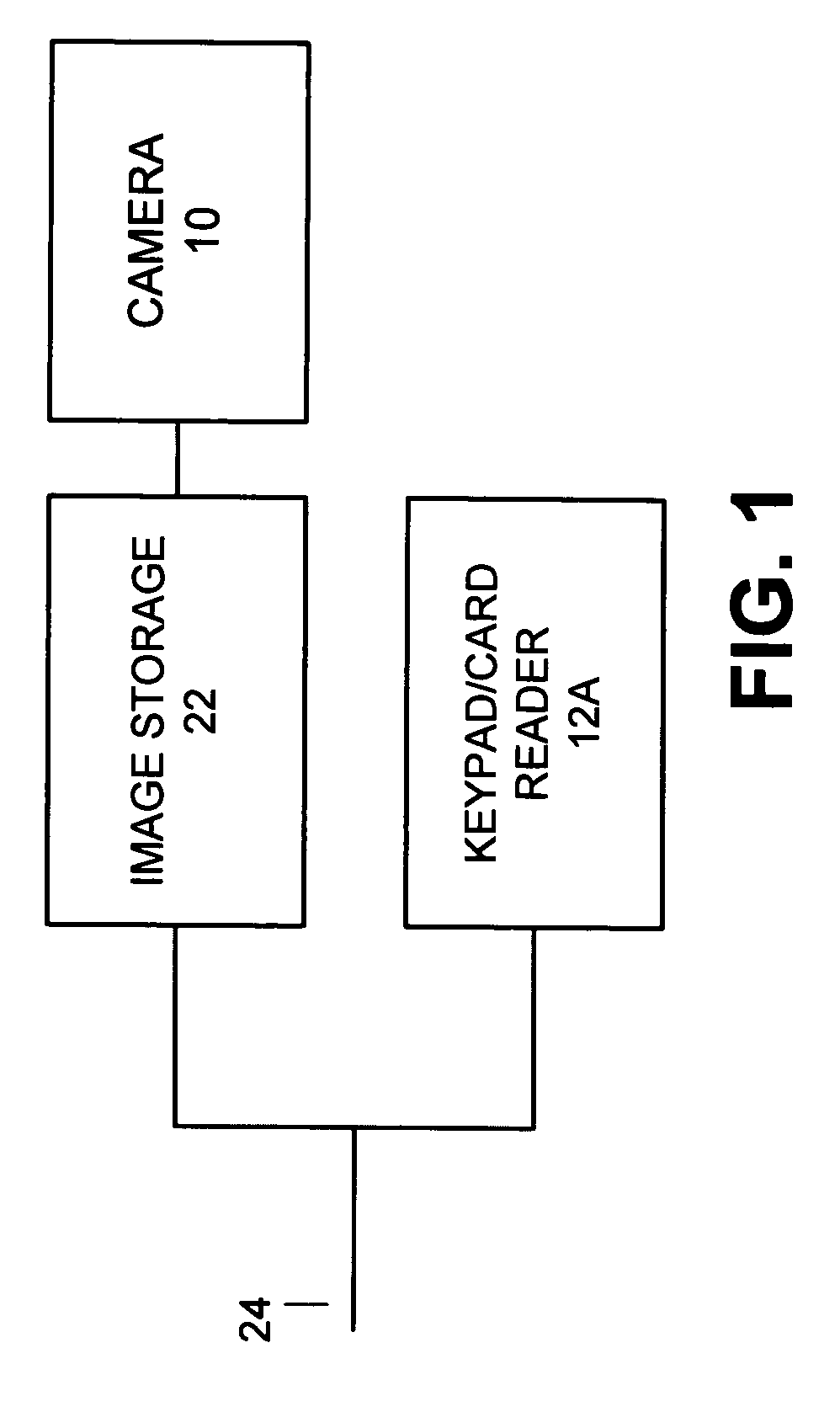
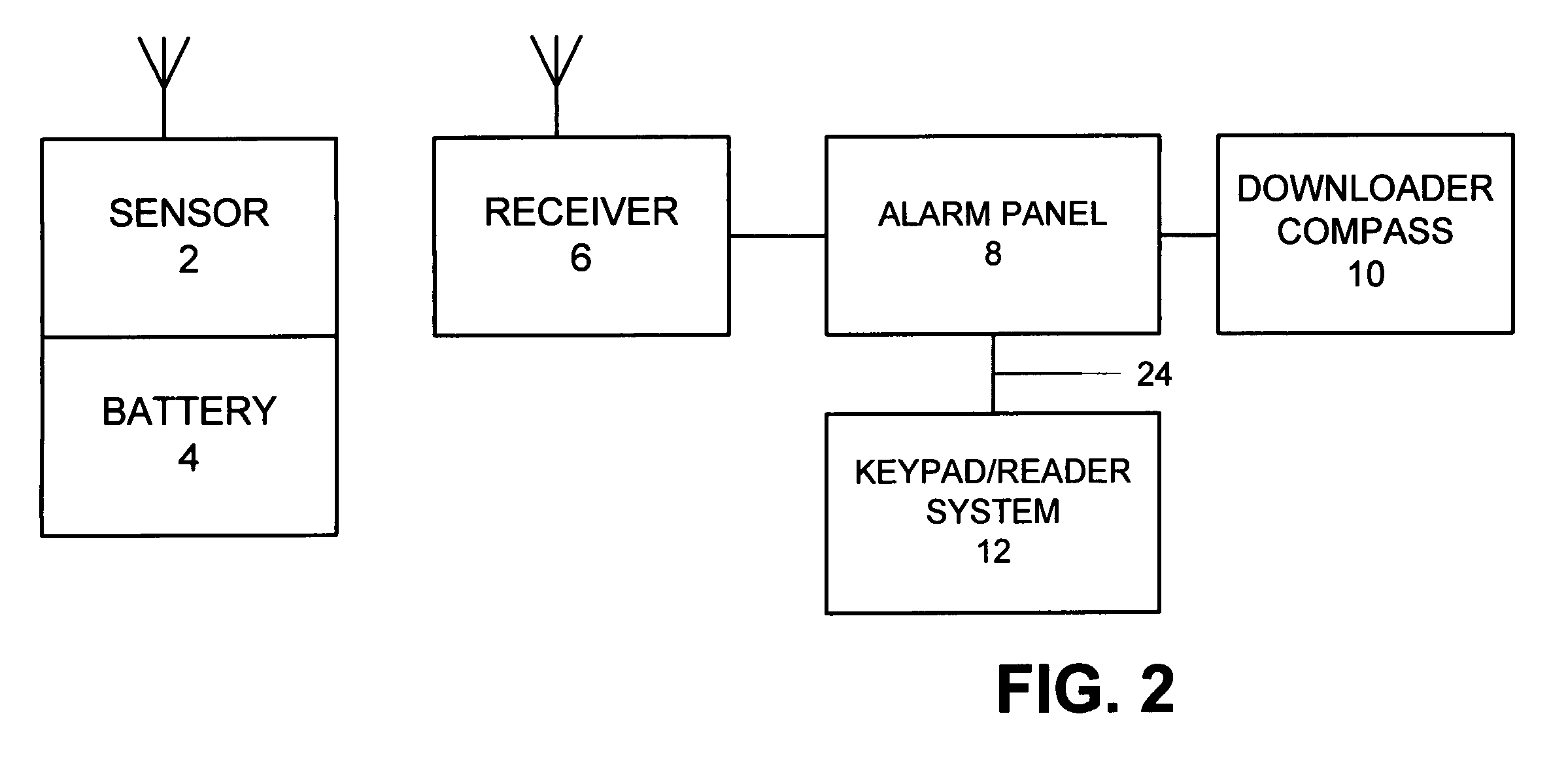
Security system access control and method
ActiveUS7397371B2Improve security levelImprove securityColor television detailsClosed circuit television systemsUser codeSecurity system
A security system which includes at least a first sensor, an alarm panel including a control system and programmable apparatus, a connection between the at least one sensor and set alarm panel, a keypad assembly including a camera, and a connection between the keypad assembly and the alarm panel. In various embodiments of the invention the camera includes a CMOS image sensor, the camera produces digital images, the camera tracks the user of the keypad assembly, the camera is remotely controllable from the alarm panel to focus on an object of interest, and / or the camera is remotely controllable from a central monitoring station to focus on an object of interest. In some cases the camera system is configured to take a picture in response to a specific user code entered by the user, take a picture in response to time of day when the input occurs, take a picture in response to invalid code entry and / or take a picture in response to an invalid card being presented. The invention also includes the method for providing enhanced security for protected premises which includes providing at least a first sensor, providing an alarm panel including a control system and programmable apparatus, providing a connection between the at least one sensor and the alarm panel, providing an input device including a camera, and initiating operation of the camera from the alarm panel.
Owner:HONEYWELL INT INC
Code protecting method and system based on hook technology in JAVA
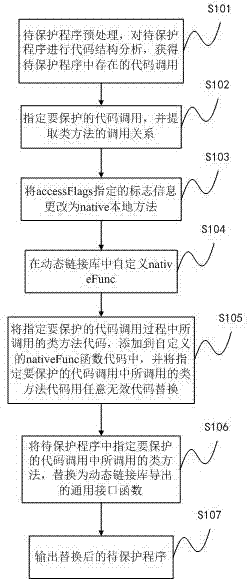
InactiveCN103902859AImprove protectionChange call flowProgram/content distribution protectionDead codeStructure of Management Information
The invention provides a code protecting method and system based on a hook technology in JAVA. The code protecting method mainly comprises the steps that a JNI mechanism is mainly used, class calling is changed by modifying class mark information to native, and a nativeFunc is customized in a dynamic link library; class method codes which are called in the calling process of codes assigned to be protected are added to codes of the customized nativeFunc, and the class method codes which are called in the calling process of the codes assigned to the protected are replaced with arbitrary invalid codes; a class method called in the calling process of the codes assigned to be protected in a program to be protected is replaced with a general interface function exported by the dynamic link library; finally, the replaced program to be protected is output. The invention further correspondingly provides a corresponding system structure. By means of the method, calling of the function can be hidden in a dynamic link library file which is compiled into binary machine instructions, and thus the difficulty of reversing the calling is greatly increased.
Owner:WUHAN ANTIY MOBILE SECURITY
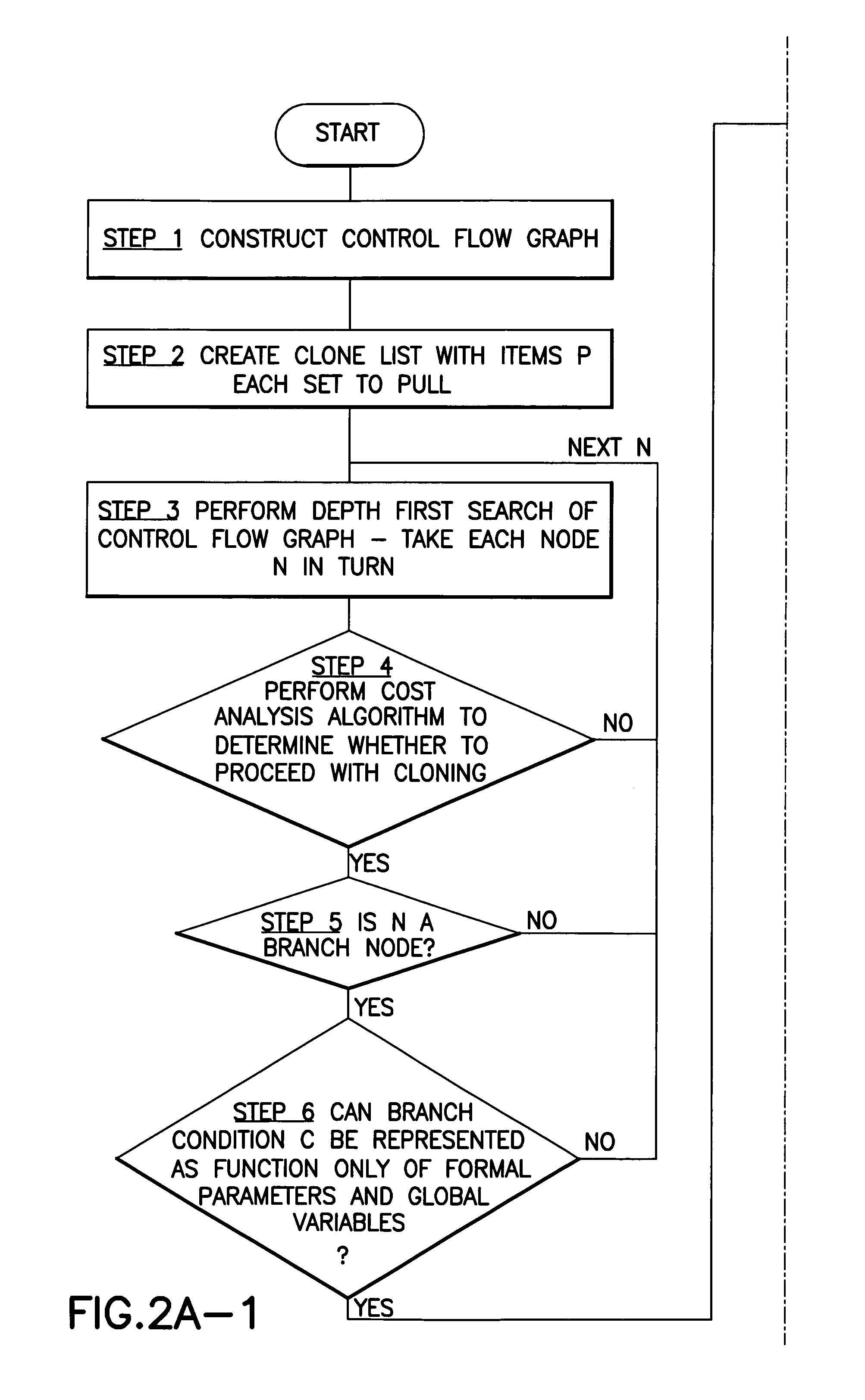
System, method and program product for optimising computer software by procedure cloning
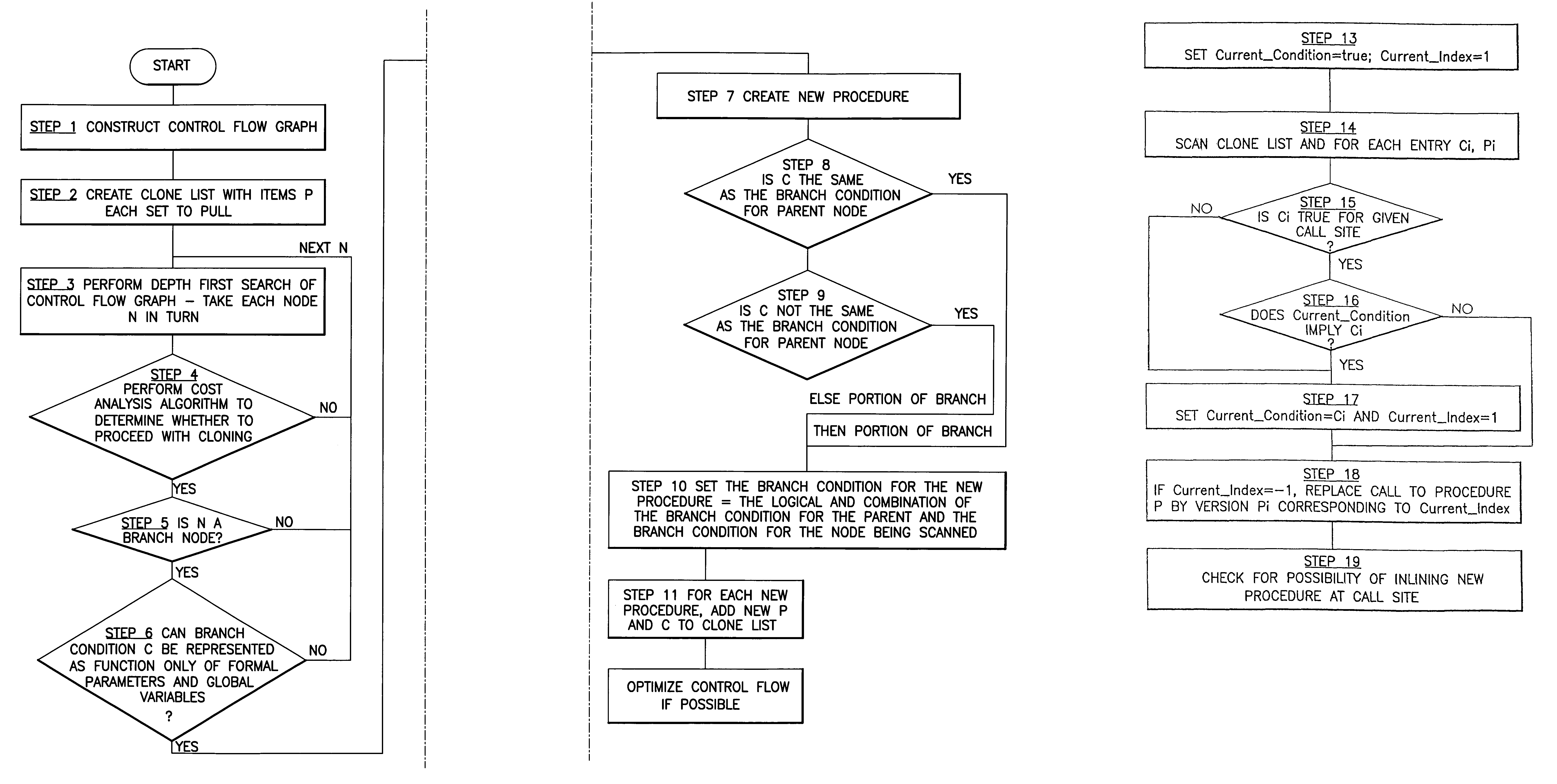
InactiveUS7058561B1Facilitate further analysis and optimisationEasy to calculateProgram controlMemory systemsDead codeControl flow
A method, system and program product for optimizing software in which procedure clones are created based on the control flow information for the procedure body. In an example, a control flow graph for a called procedure is constructed and, for a branching node which can direct program flow to two or more code branches of the procedure, respective clones or new procedures are formed one for each code branch. A list containing pointers to the clones and the respective branch conditions for those clones is formed. Then, for each call site, the list is scanned to see if a particular call could be replaced by a call to a clone. Meanwhile, each clone is optimized and this may lead to removal of dead code or the replacement of a particular call statement by a constant.
Owner:IBM CORP
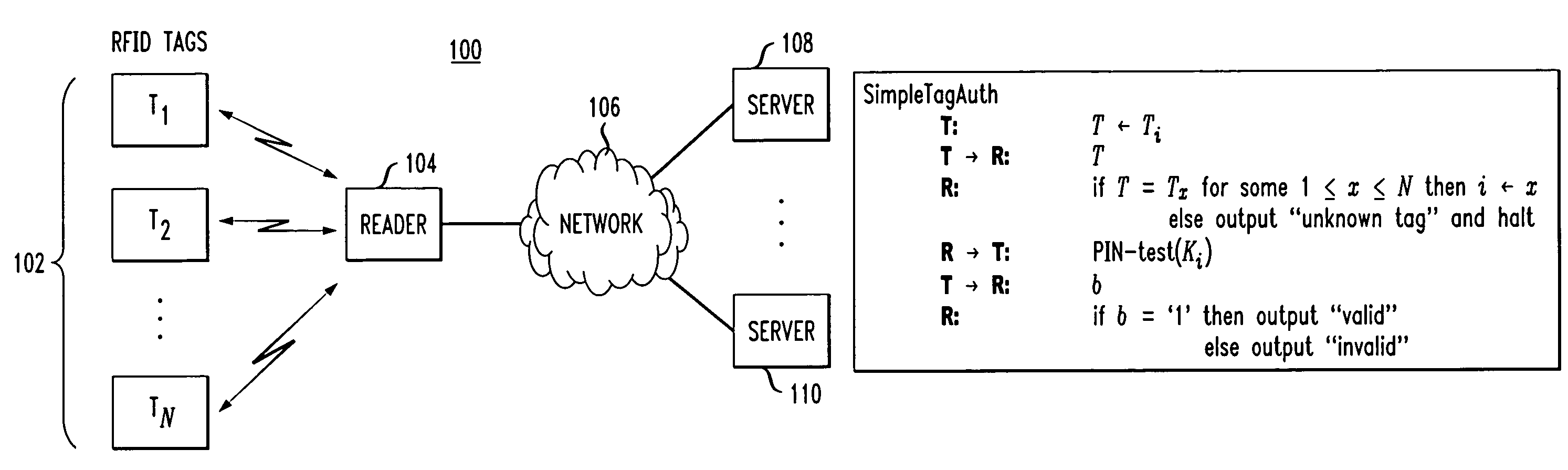
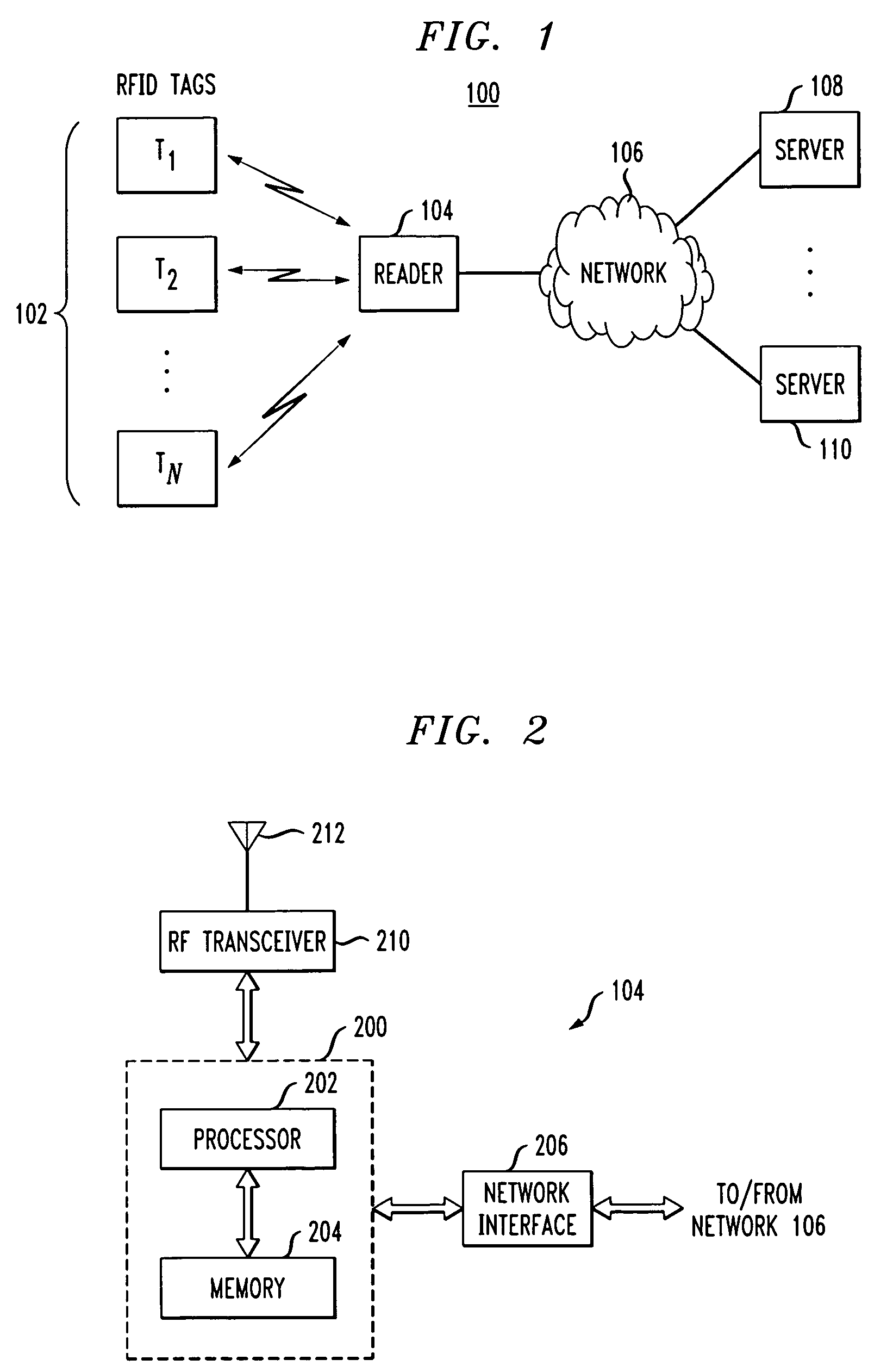
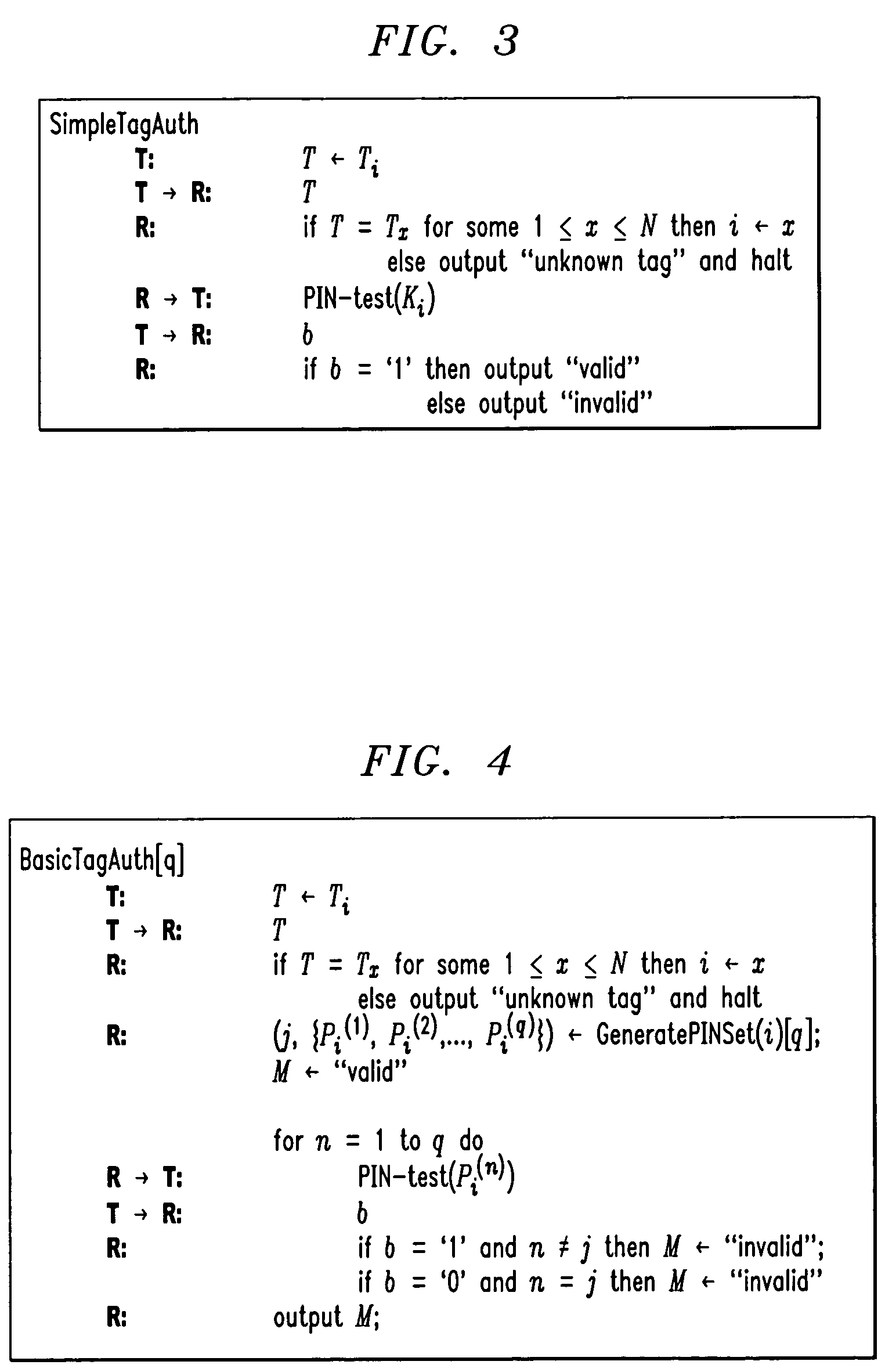
Methods and apparatus for RFID device authentication
ActiveUS7750793B2Simple and efficient techniqueProgramme controlElectric signal transmission systemsComputer hardwareDead code
Methods and apparatus are disclosed for use in an RFID system comprising a plurality of RFID devices and at least one reader which communicates with one or more of the devices. In one aspect of the invention, an identifier transmitted by a given one of the RFID devices is received by a reader or by an associated verifier via the reader. At least first and second codes are determined, by the reader or verifier, with the first code being a valid code for the identifier, and the second code being an invalid code for the identifier. The reader, or verifier via the reader, communicates with the given device to determine if the device is able to confirm that the first code is a valid code and the second code is an invalid code.
Owner:EMC IP HLDG CO LLC
Managing code samples in documentation
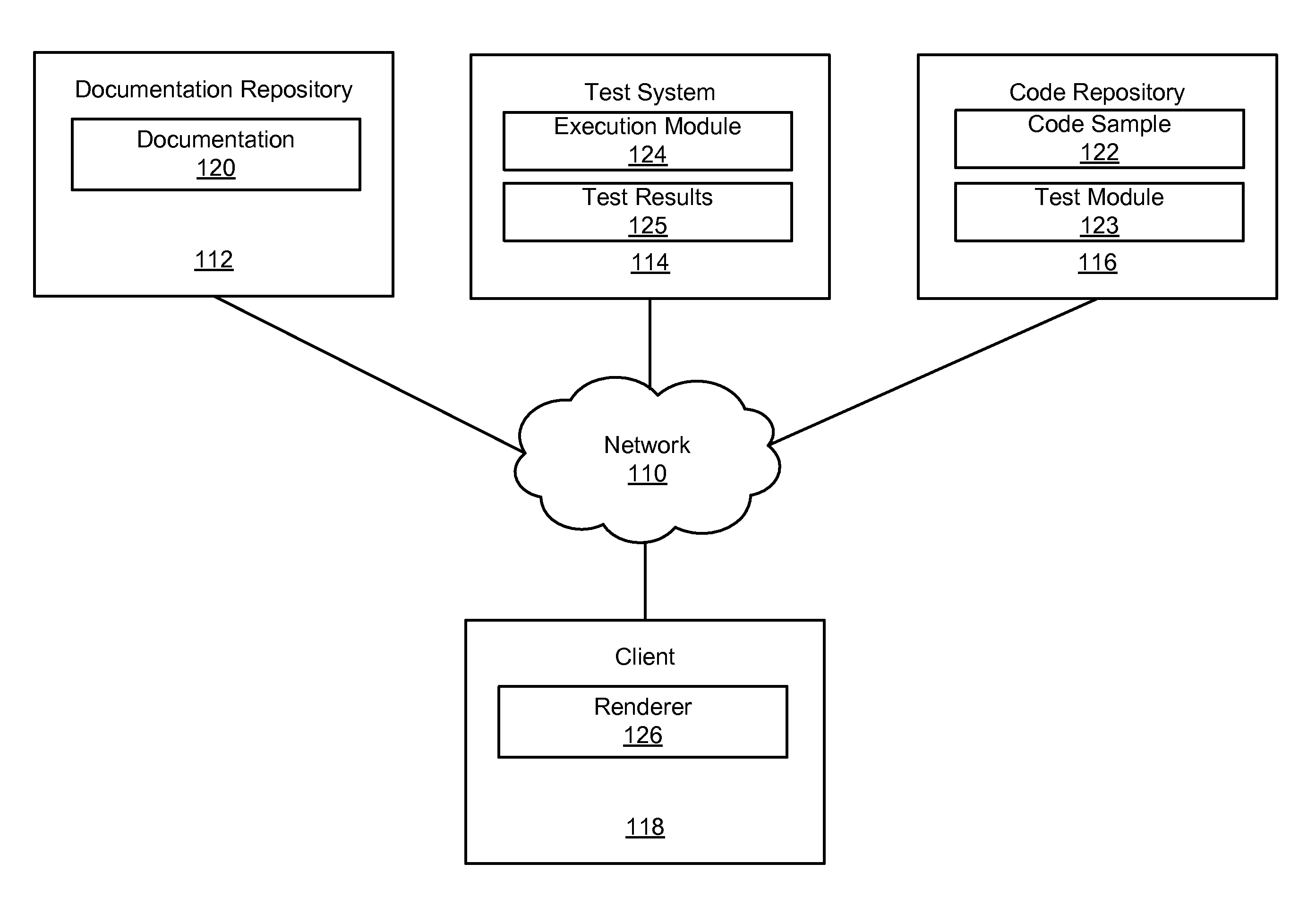
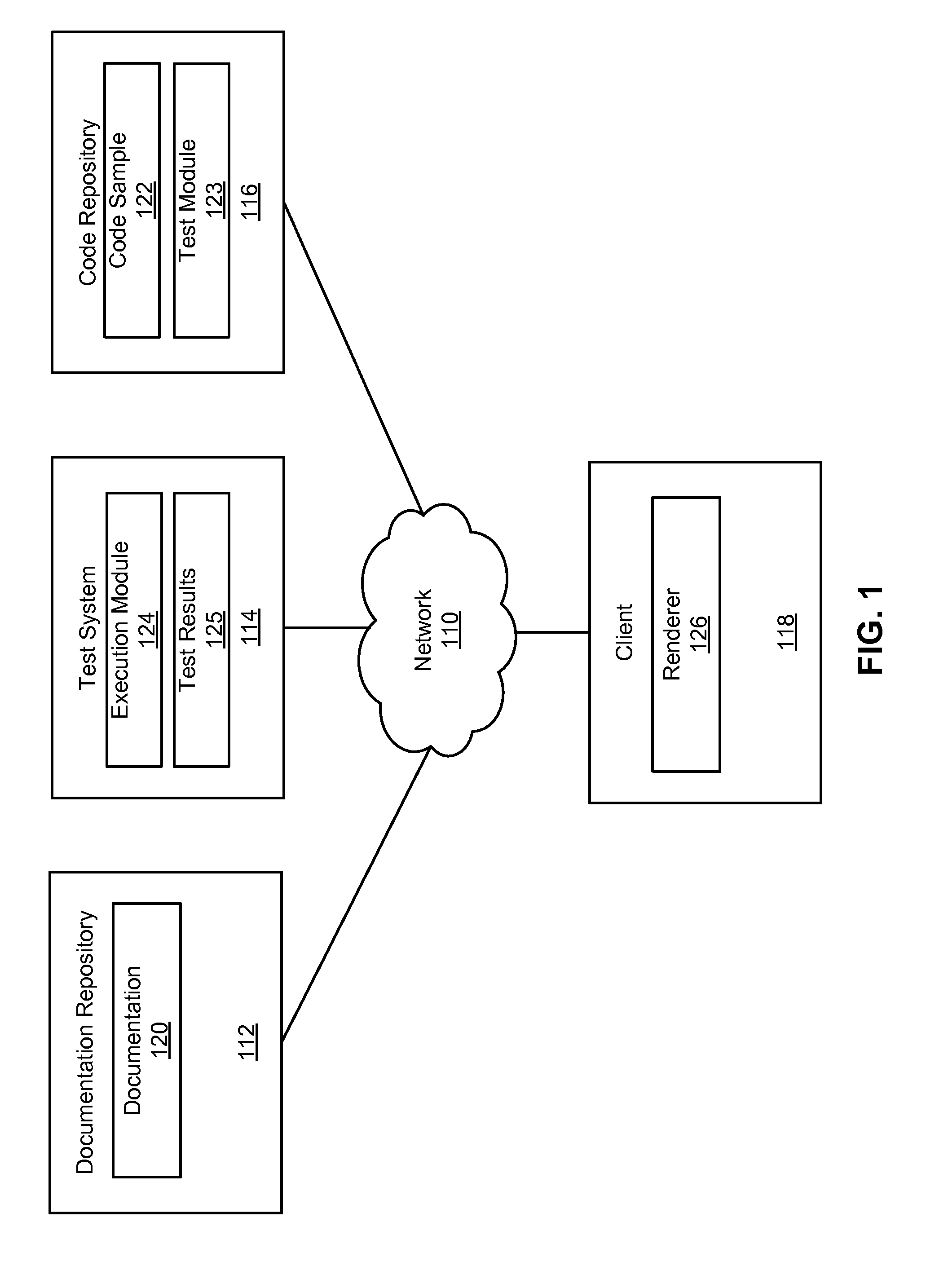
ActiveUS8694964B1Program documentationSpecial data processing applicationsDead codeDocumentation procedure
Documentation having code samples is managed. Documentation describing programming code for a software product is received. The documentation references a code sample having an associated test module for determining whether the code sample is valid. The code sample is tested by executing the associated test module to produce a test result indicating whether the code sample is valid. The documentation, code sample, and test result are stored. The documentation, code sample, and test result may be provided to a client adapted to display the code sample and test result to a user of the client. Invalid code samples in the documentation may be identified using the test modules and the invalid code samples may be replaced to make the code samples valid.
Owner:GOOGLE LLC
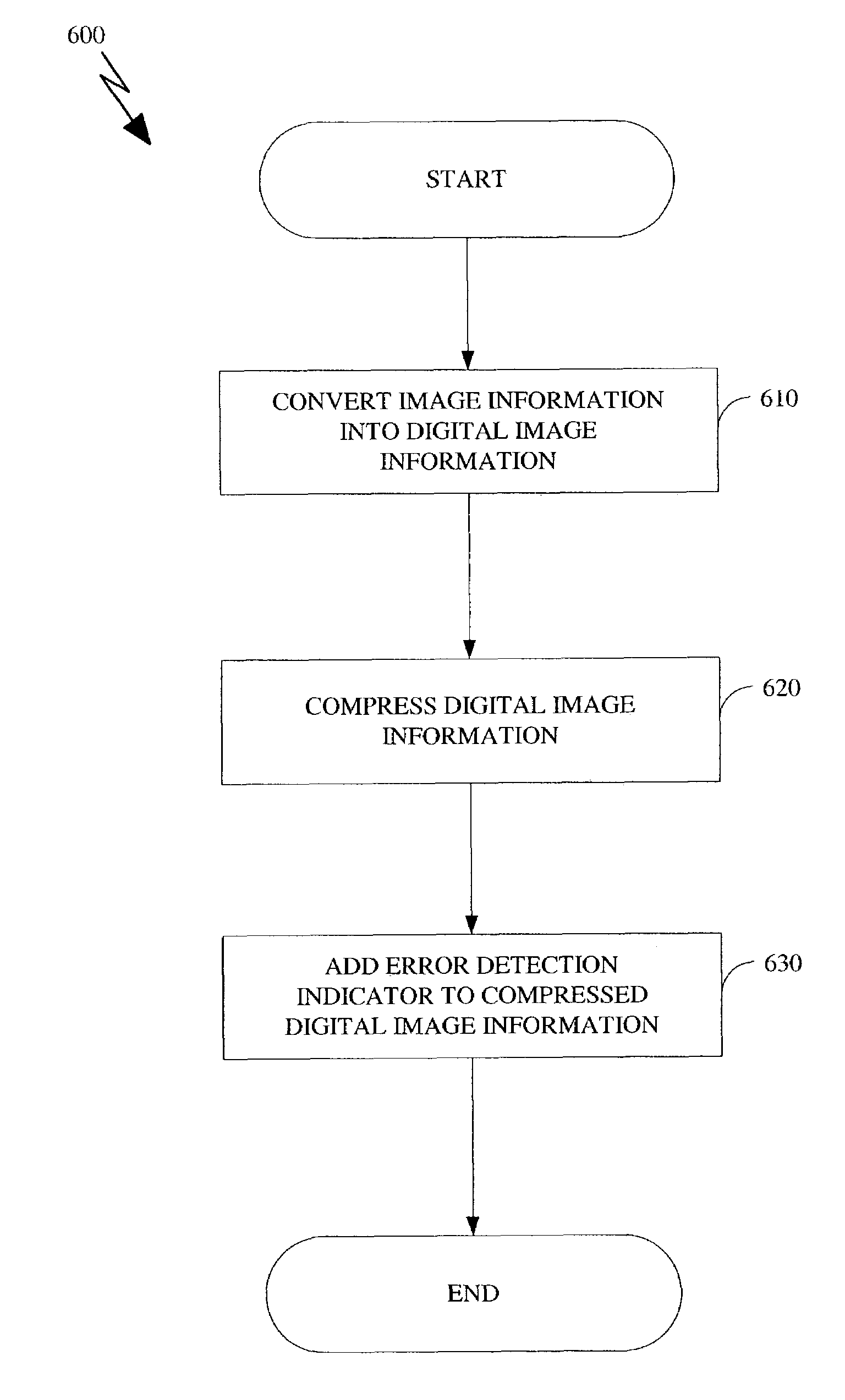
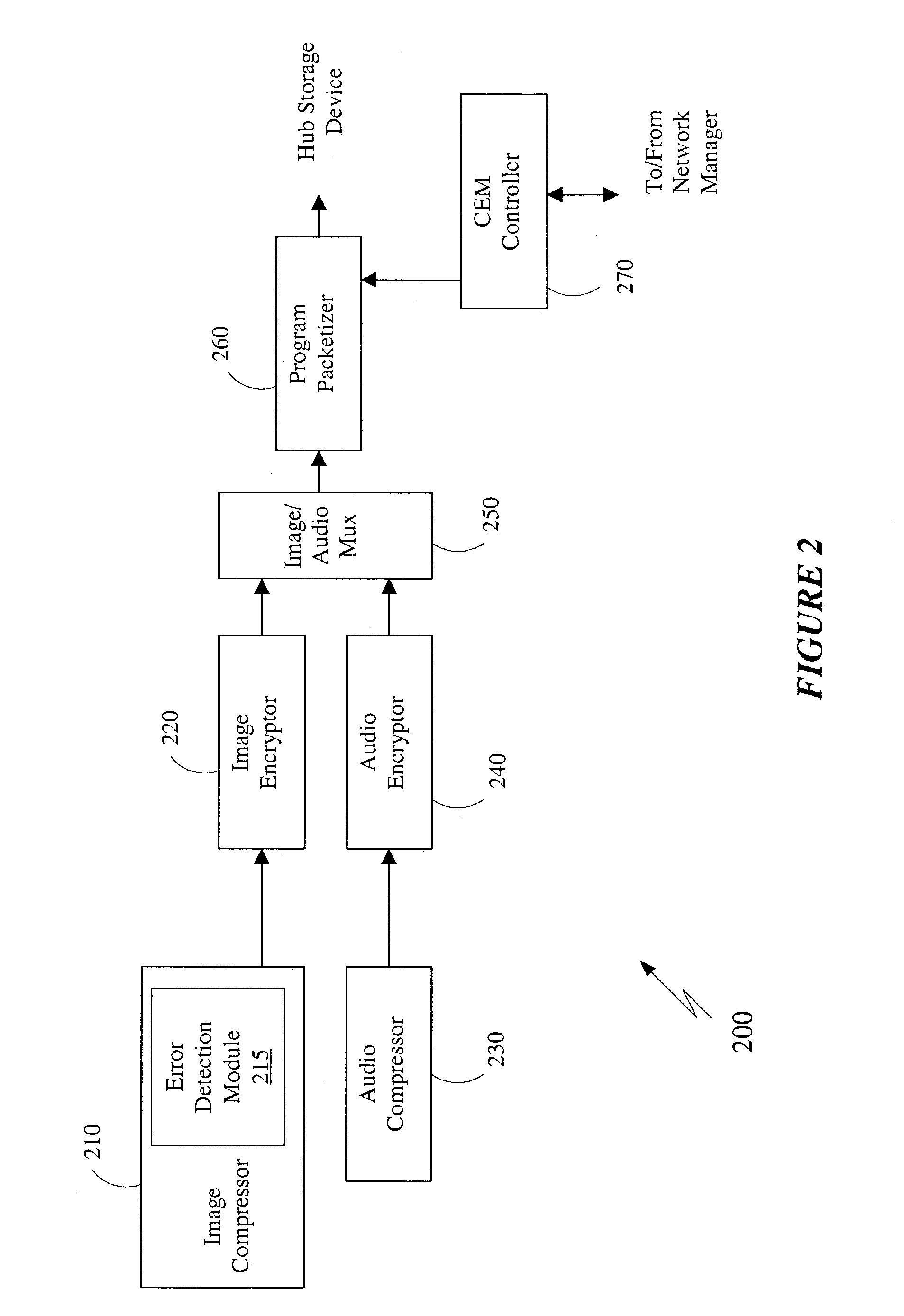
Apparatus and method for detecting error in a digital image
ActiveUS20030190078A1Picture reproducers using cathode ray tubesPicture reproducers with optical-mechanical scanningShift registerDead code
An apparatus and method for the detection of errors in compressed digital image is disclosed. In one embodiment, a signature is generated using a multiple input shift register and added to the compressed information. The signature is verified at the decoder to detect an error in the compressed information. Other information such as the frame number and / or color component type of the compressed image can also be verified to detect errors in the compressed information. In other embodiments, the decoder detects errors if there are bits remaining after decompression and / or if there are invalid codes at decompression. Once an error is detected, the compressed information can be discarded or re-sent and processed. Therefore, the detection of errors can significantly enhance at least the reliance of systems such as digital cinema that require compression of large amounts of data.
Owner:QUALCOMM INC
Code string search apparatus, search method, and program
ActiveUS20110191756A1Simple structureReduce processing burdenProgram controlSpecial data processing applicationsProgramming languageDead code
Owner:KOUSOKUYA
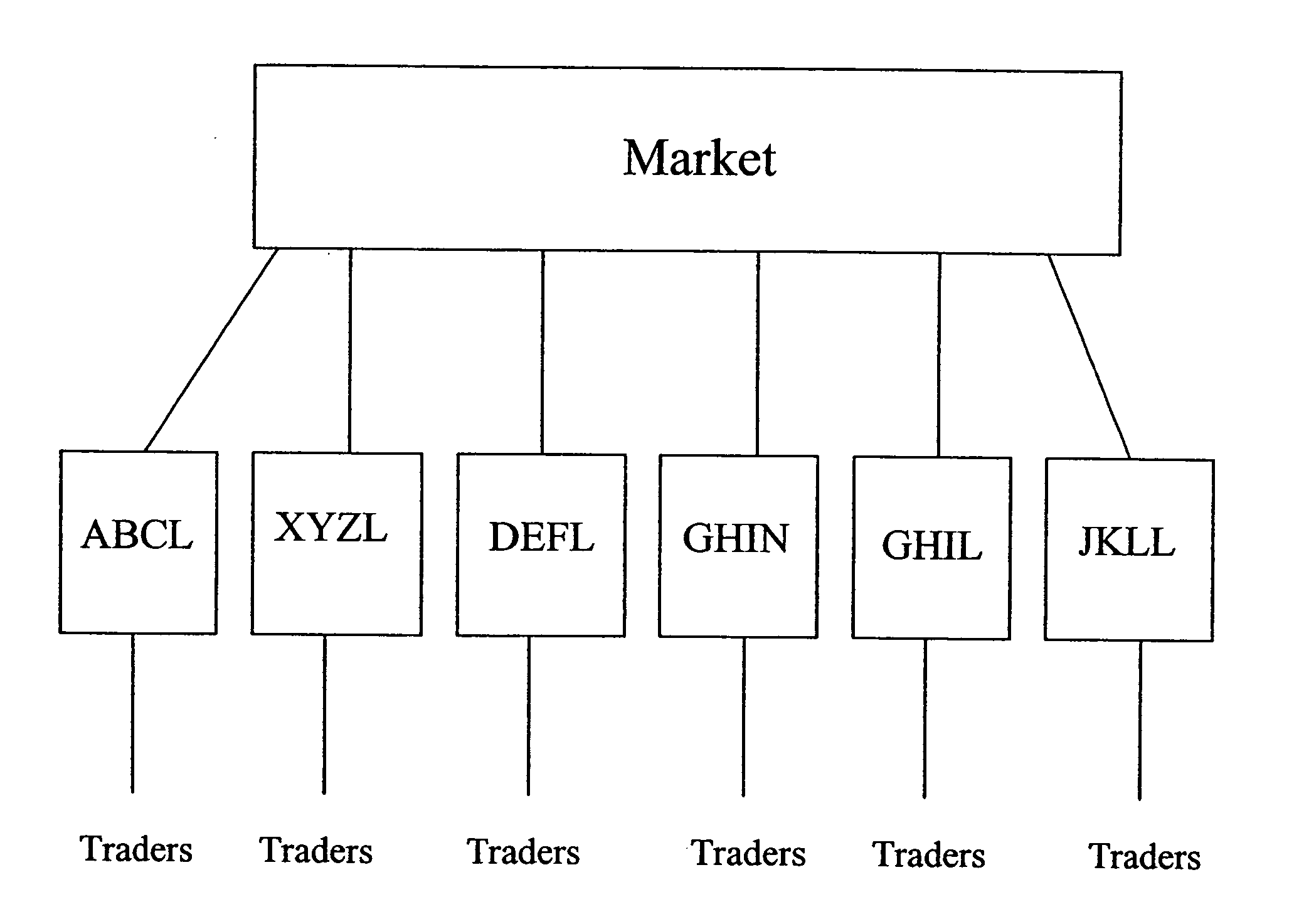
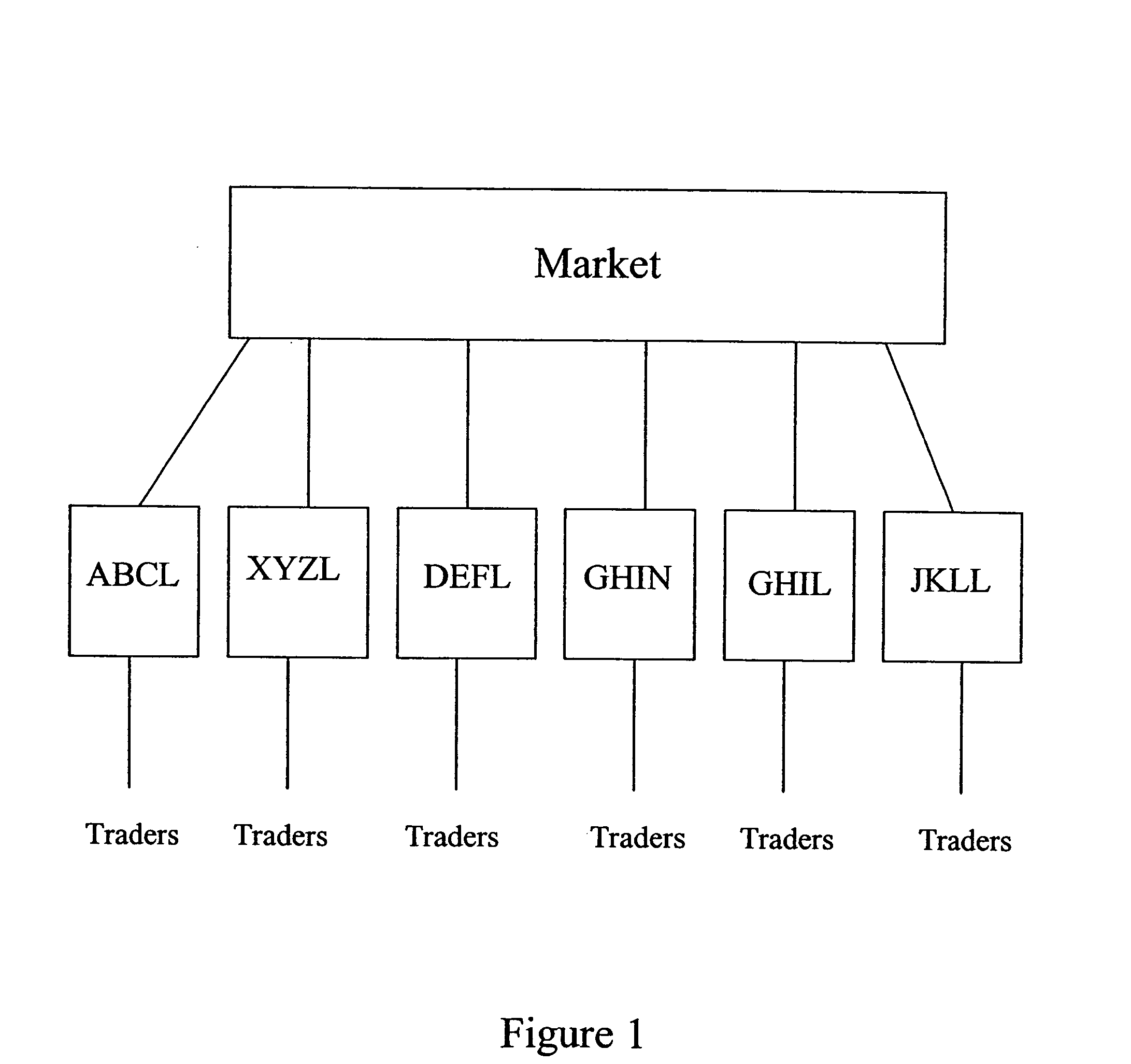
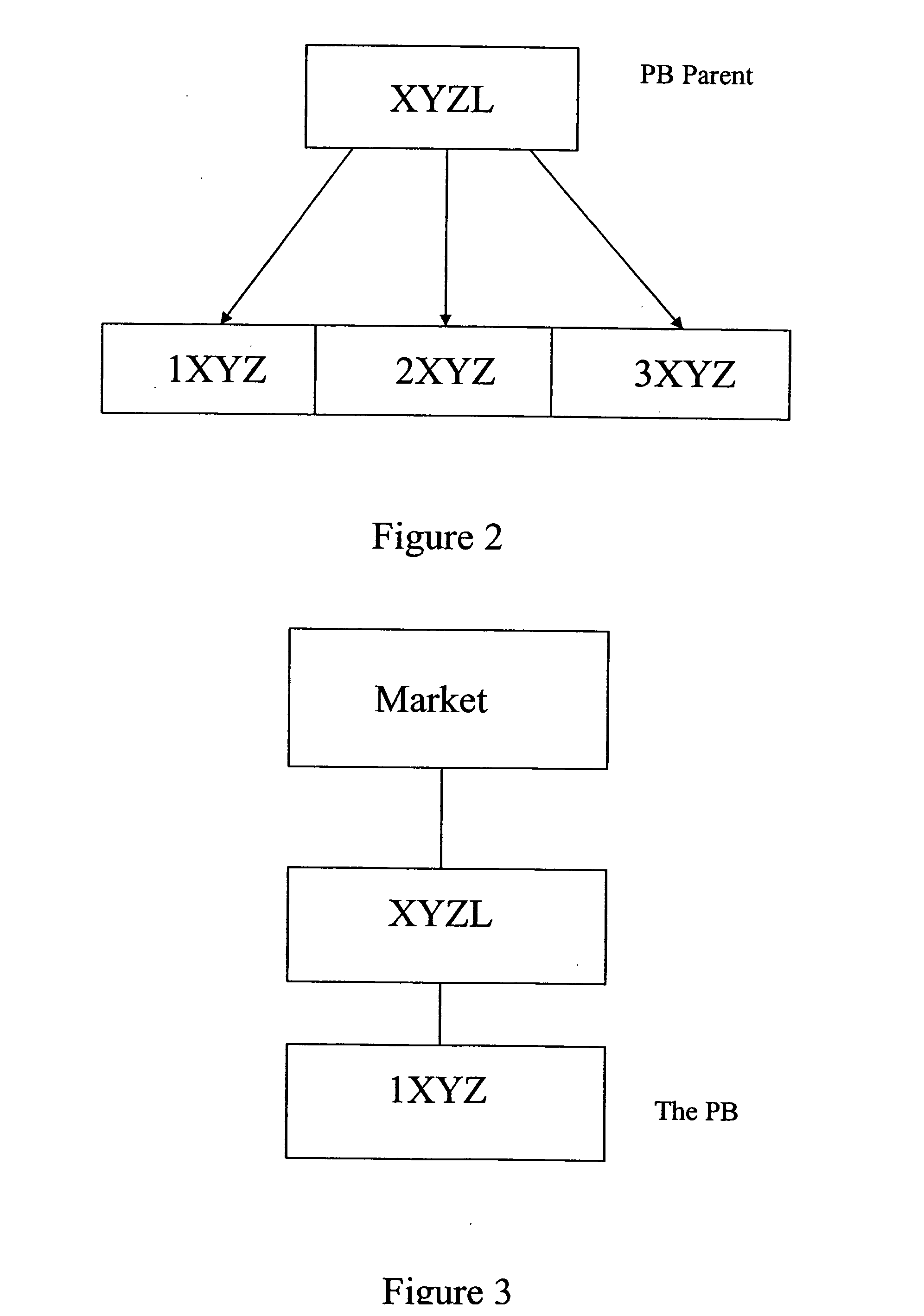
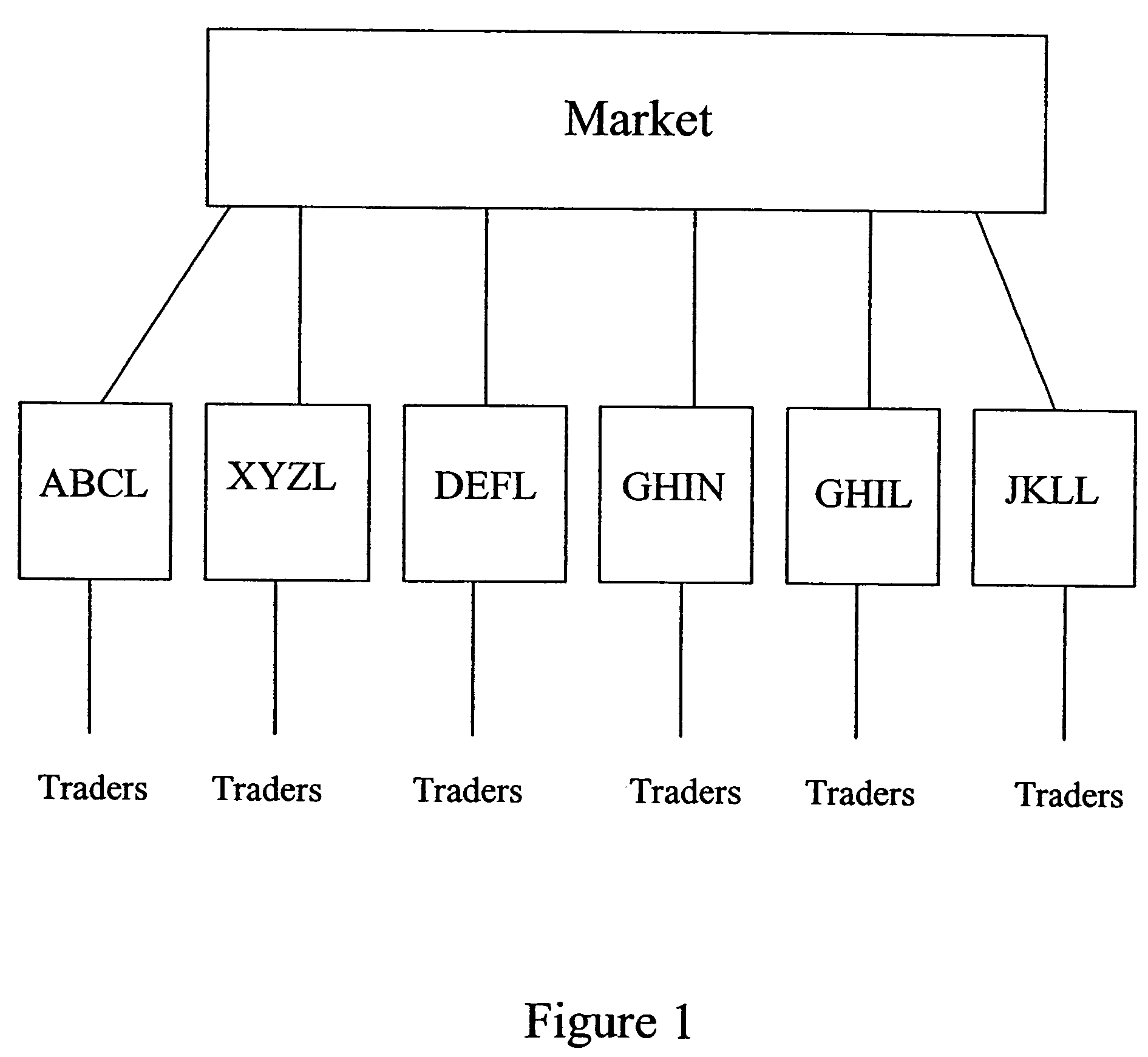
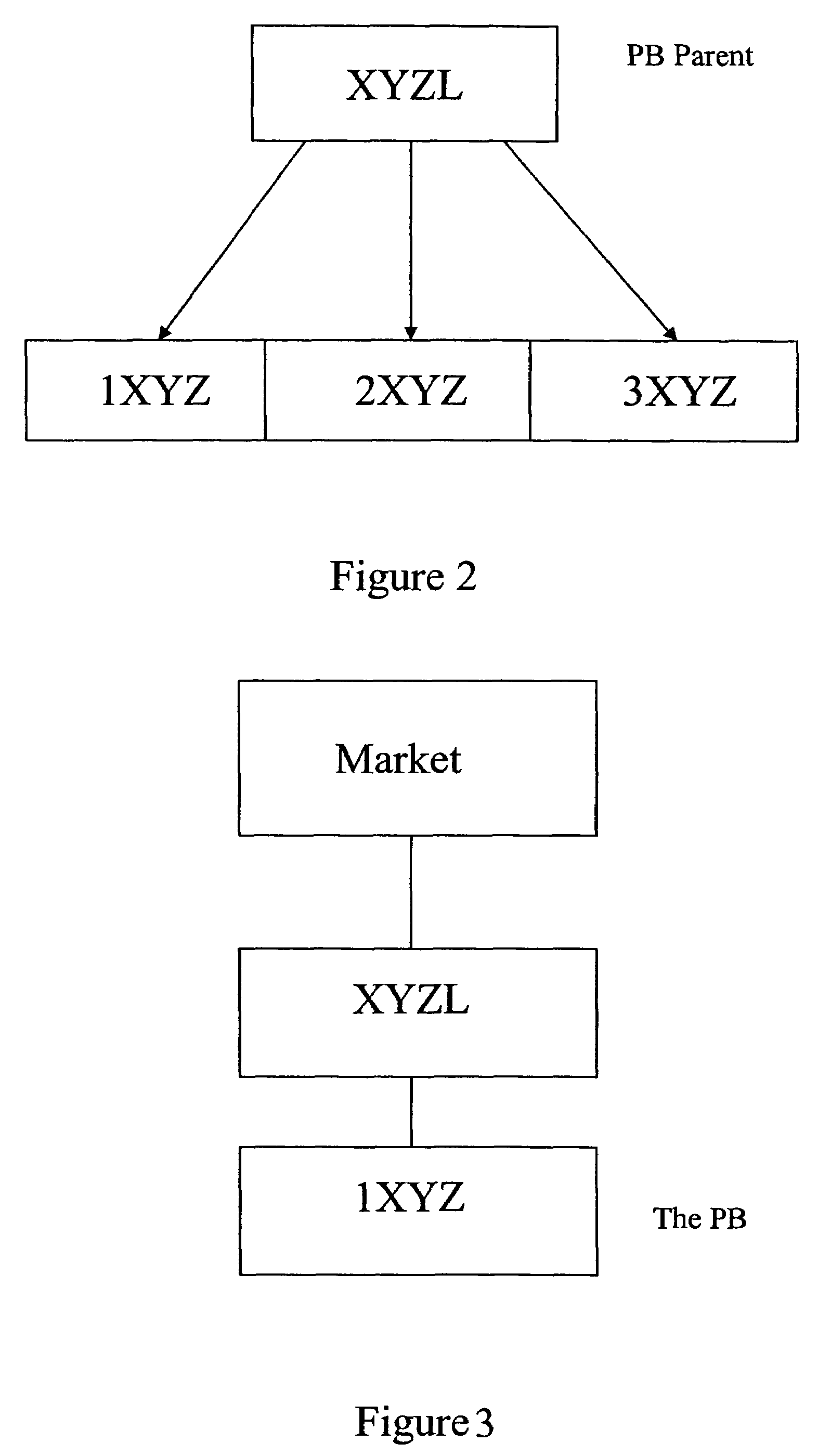
Automated trading systems
In an electronic trading system, prime brokerage services may be provided by assigning one or more dependent or child deal codes to a deal code. Prime broker trades are conducted via the dependent deal codes but appear to the market as deals with the parent deal code using credit assigned to the parent deal code. The prime bank customer is a dependent deal code of the customer bank which also trades on the system, allowing credit to be allocated by the customer dependent code for prime broker trades. A deal code may have several dependent deal codes which can trade with one another. Dependent deal codes can be used to expand the size of trading floors beyond that which can be supported by a single deal code and to assist in migration between system versions.
Owner:EBS GROUP
Automatic debugging and mistake correcting method and system for assembly program in embedded module
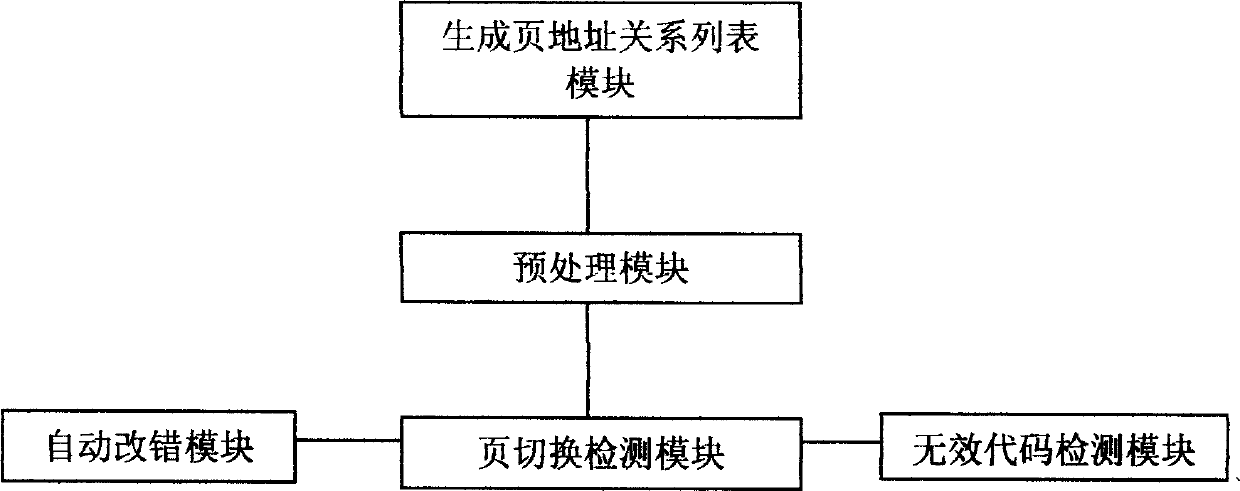
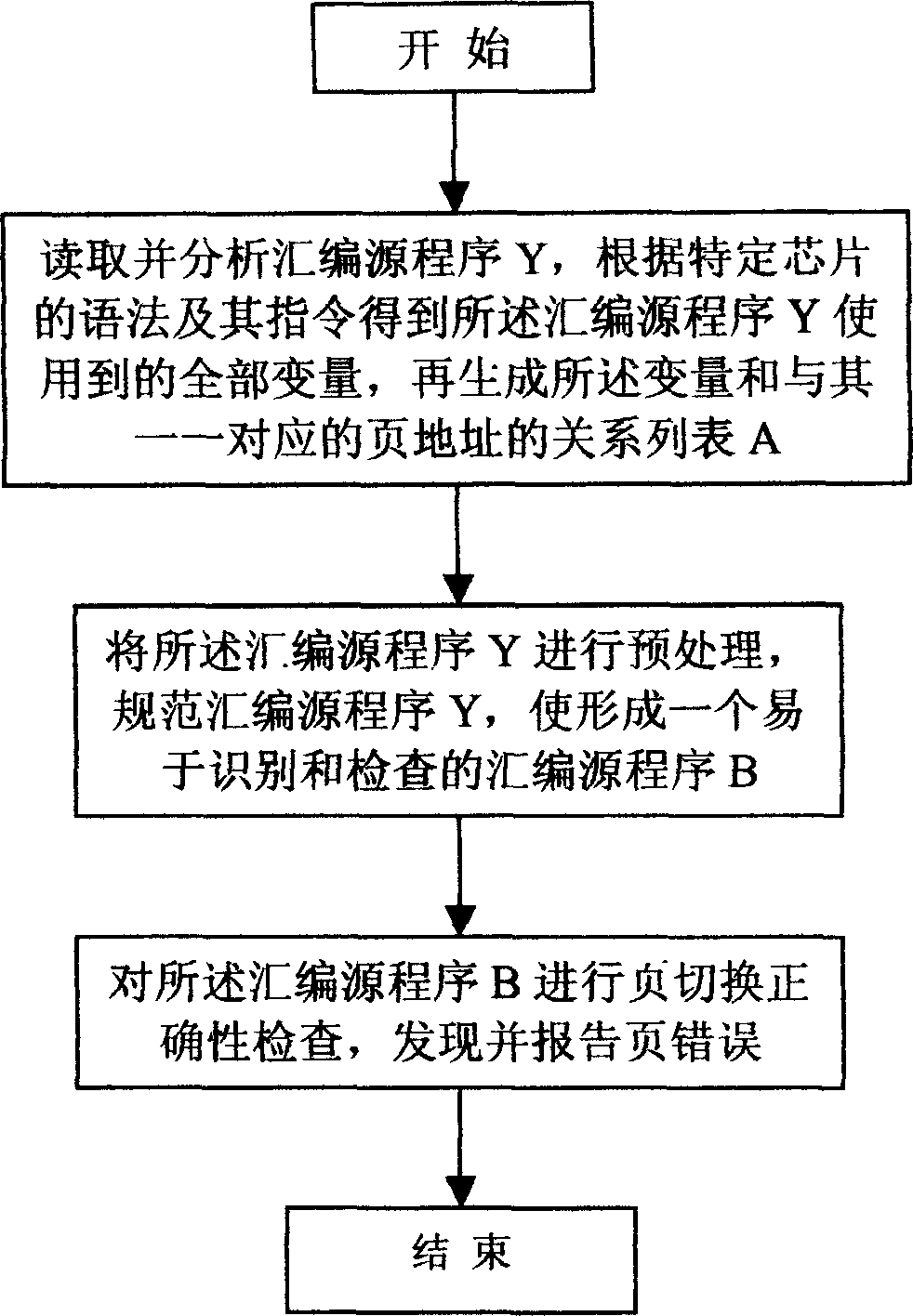
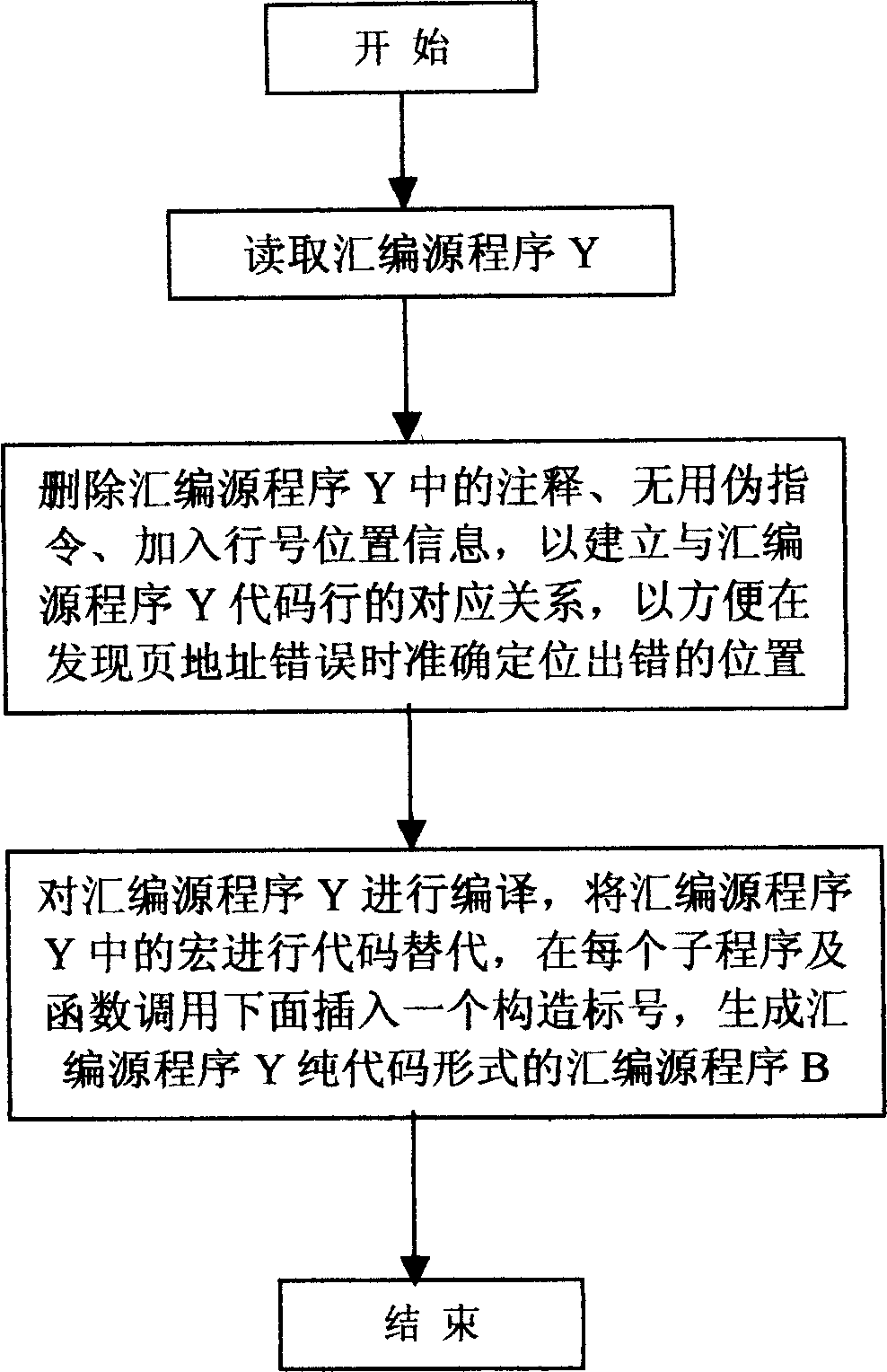
InactiveCN1632763AAccurate checkSave human effortSoftware testing/debuggingDead codeProgramming language
It is an assembler program automatic fault-finding method, which comprises the following steps: to read and analyze the assembler program Y and to get the said whole variables of the said program according to the grammar and orders of the special chip and to generate the relation form A between the variable and the web address; to pre-process the assembler program and standardize the program to form one assembler program easy to be identified and inspected; to test the web page accuracy of the program and to fine the error of the report page.
Owner:时仁帅
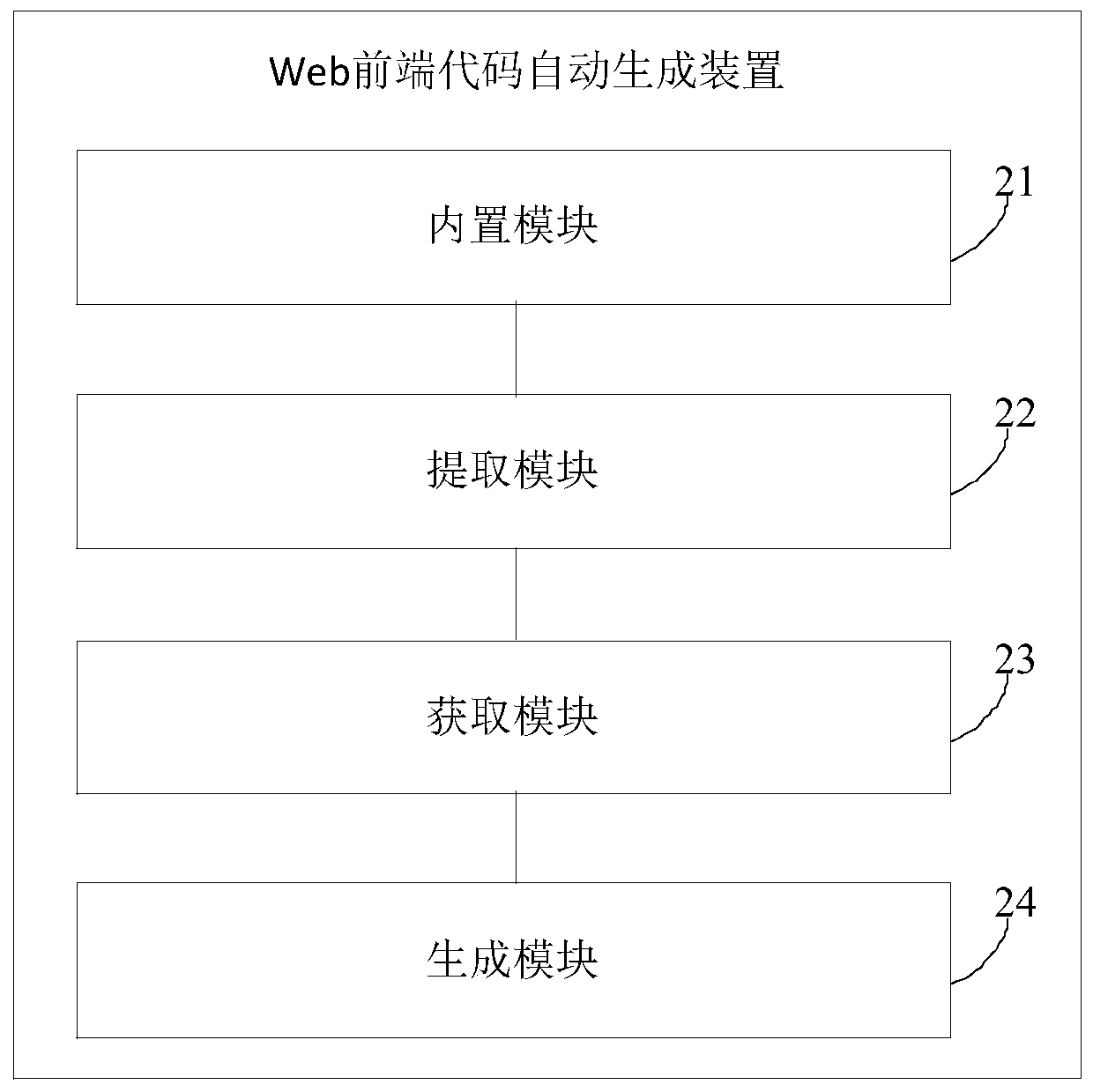
Web front-end code automatic generation method and device
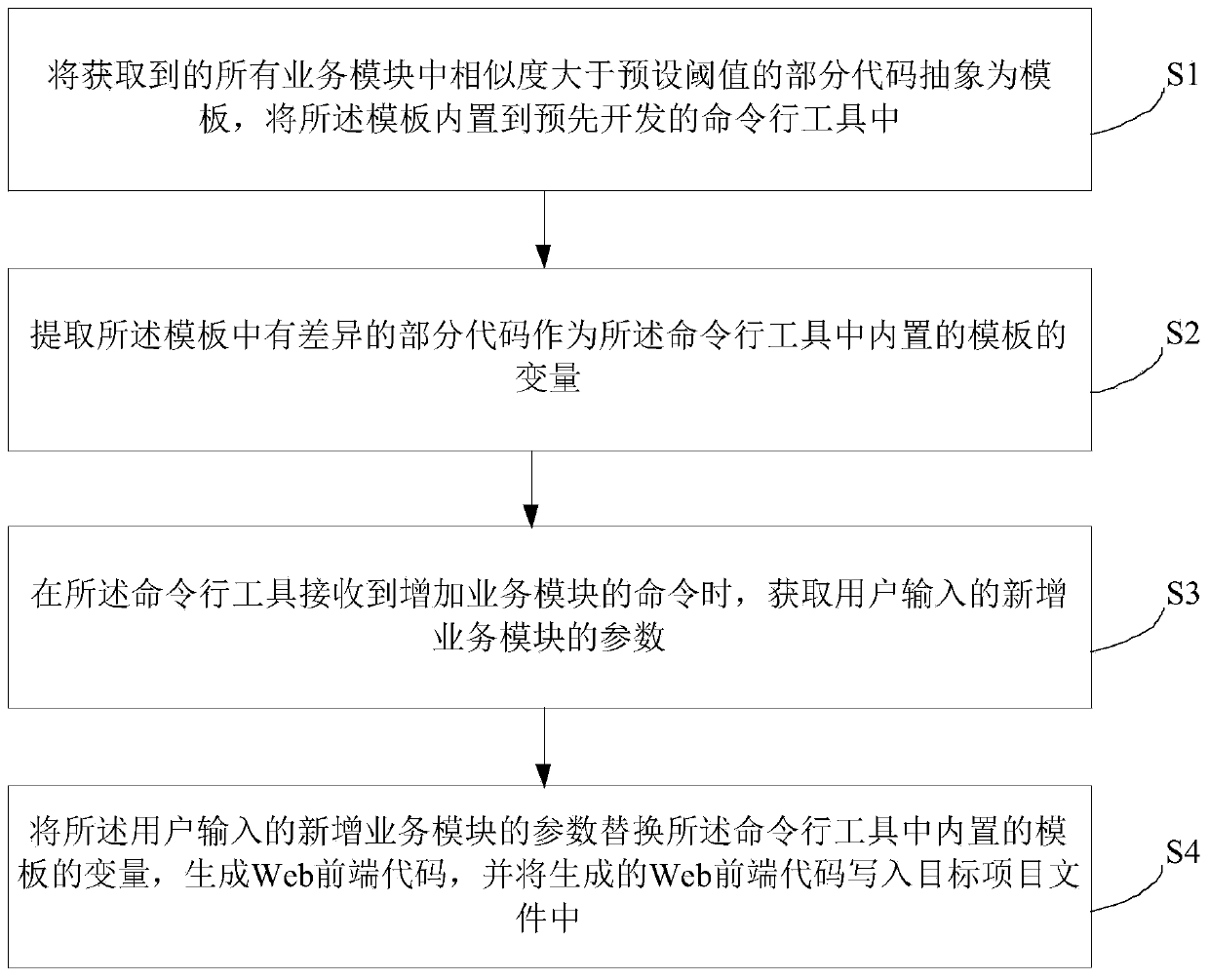
InactiveCN110096263AQuick and automatic generationImprove development efficiencyIntelligent editorsDead codeProgramming language
The embodiment of the invention provides a Web front-end code automatic generation method and device, and the method comprises the steps: abstracting a part of obtained codes with the similarity greater than a preset threshold value in all service modules as a template, and enabling the template to be built in a command line tool which is developed in advance; extracting a part of codes with differences in the template as variables of the template built in the command line tool; when the command line tool receives a command of adding a service module, obtaining parameters of the newly added service module input by a user; and replacing the variable of a template built in the command line tool with the parameter of the newly added service module input by the user, generating a Web front-endcode, and writing the generated Web front-end code into a target project file. According to the embodiment of the invention, the Web front-end code can be quickly and automatically generated, the problem of repeated workload in the business development process is solved, and the development efficiency is improved.
Owner:KE COM (BEIJING) TECHNOLOGY CO LTD
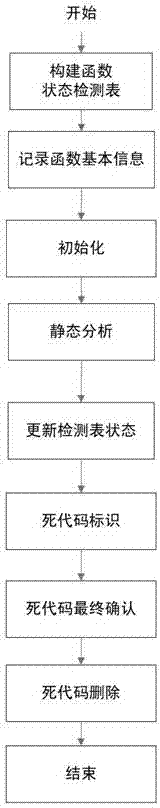
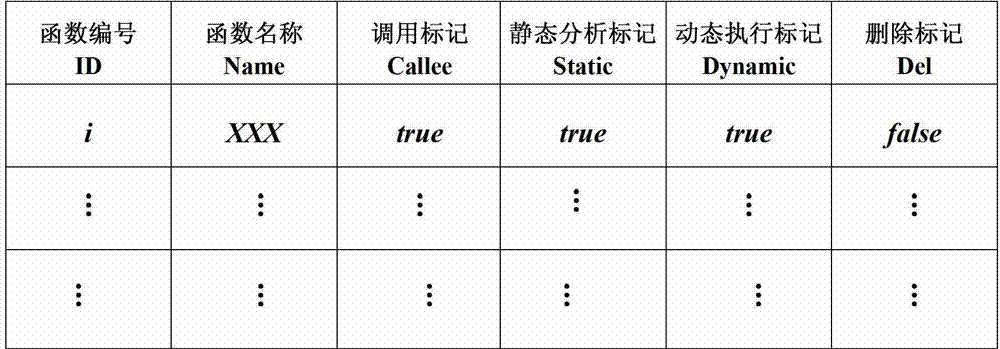
Method for accelerating operating speed of graphics processing unit (GPU) through dead code removal
InactiveCN103049304AReduce volumeImprove operational efficiencyProgram controlMemory systemsDead codeMain processing unit
The invention discloses a method for accelerating operating speed of a GPU through dead code removal. By the aid of the method, the implementation and compiling efficiency of a large-scale GPU kernel program can be improved. The technical scheme includes that firstly, a state detection table is established for all functions in the large-scale GPU kernel program; basic information of functions is recorded, and the state detection table is initialized; static analysis is conducted for the GPU program; and then the GPU kernel program is operated, information during operation of the GPU kernel program is recorded, states of all function detection table fields in the state detection table are updated, dead codes are marked and finally certified, and dead codes are deleted according to a dead code set D which is obtained finally. According to the method, dead codes which are not implemented during operation are removed, so that the code size of the GPU kernel program is reduced, the assembly code size which is generated finally is also reduced, the hit rate of single instruction multiple data (SIMD) instruction scheduling in the GPU can be improved, and the operation efficiency of the large-scale GPU kernel program can be greatly improved.
Owner:NAT UNIV OF DEFENSE TECH
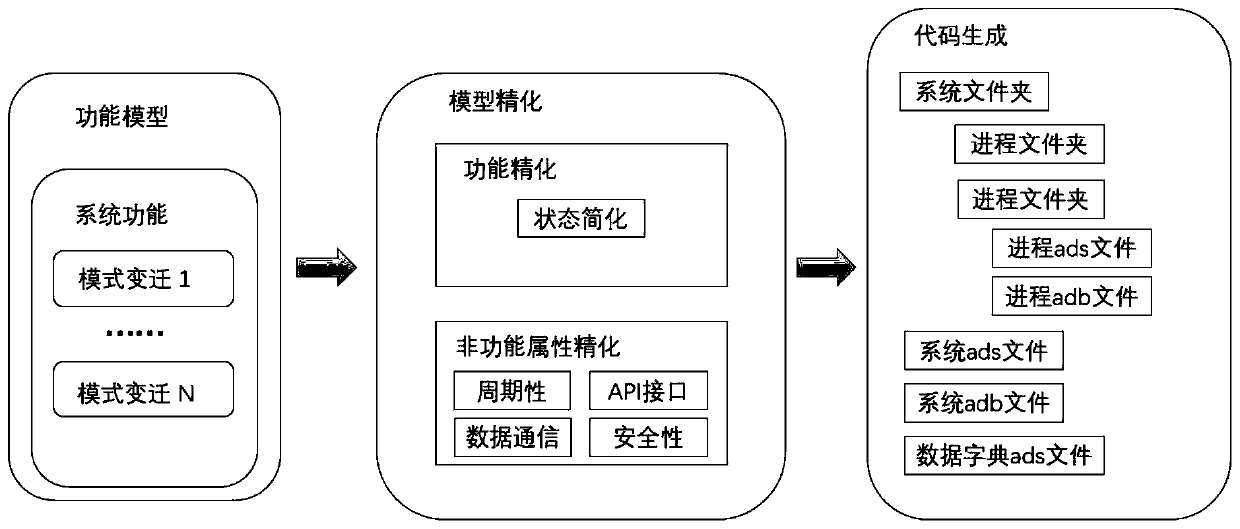
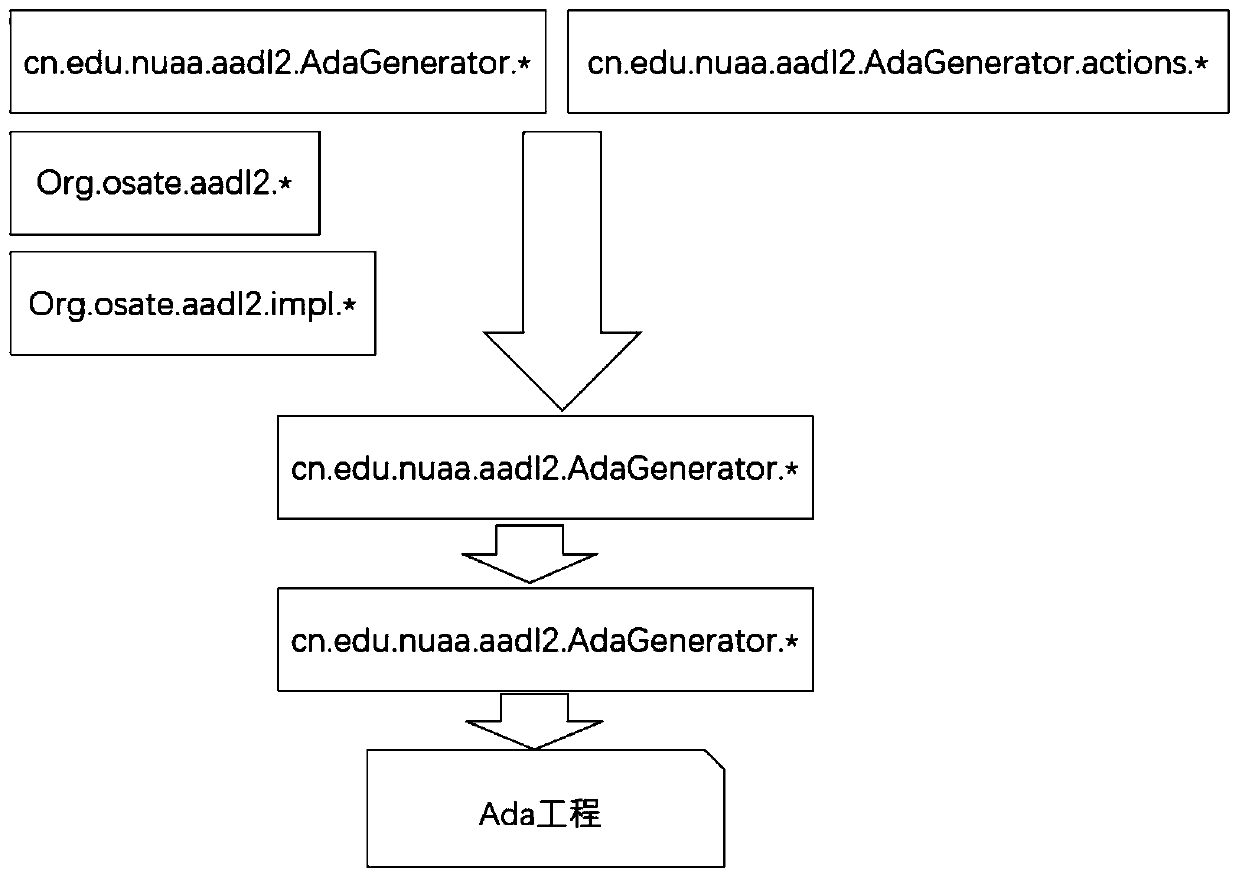
AADL model refinement method and Ada executable code automatic generation method supported by AADL model refinement method
ActiveCN110597498AImprove effectivenessImprove development efficiencyProgramming languages/paradigmsCode compilationDead codeProgramming language
The invention discloses an AADL model refinement method and an Ada executable code automatic generation method supported by the AADL model refinement method. According to the method, an existing AADLmodel is analyzed by using the AADL file analysis capability provided based on OSATE; the AADL model is subjected to functional behavior simplification and related information supplement of an execution platform through a model refinement method, so the model is complete enough; meanwhile, the automatic code generation capability provided by the Xtext technology is used, the conversion from modelssuch as system components, process and thread components, behavior attachments and modes of the AADL to Ada codes is realized by a template rule mapping function provided by an Xtend technology; andthe code can run on a specific platform, so that the Eclipse platform plug-in based on the OSATE of the AADL open source tool environment is completed.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
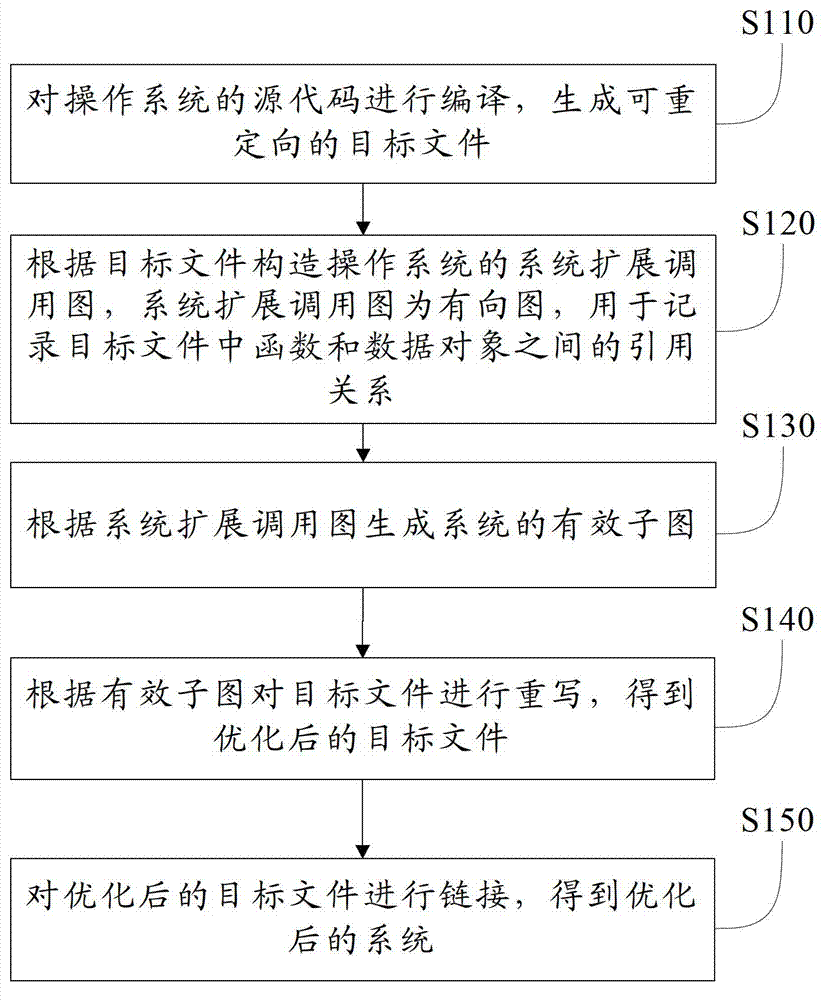
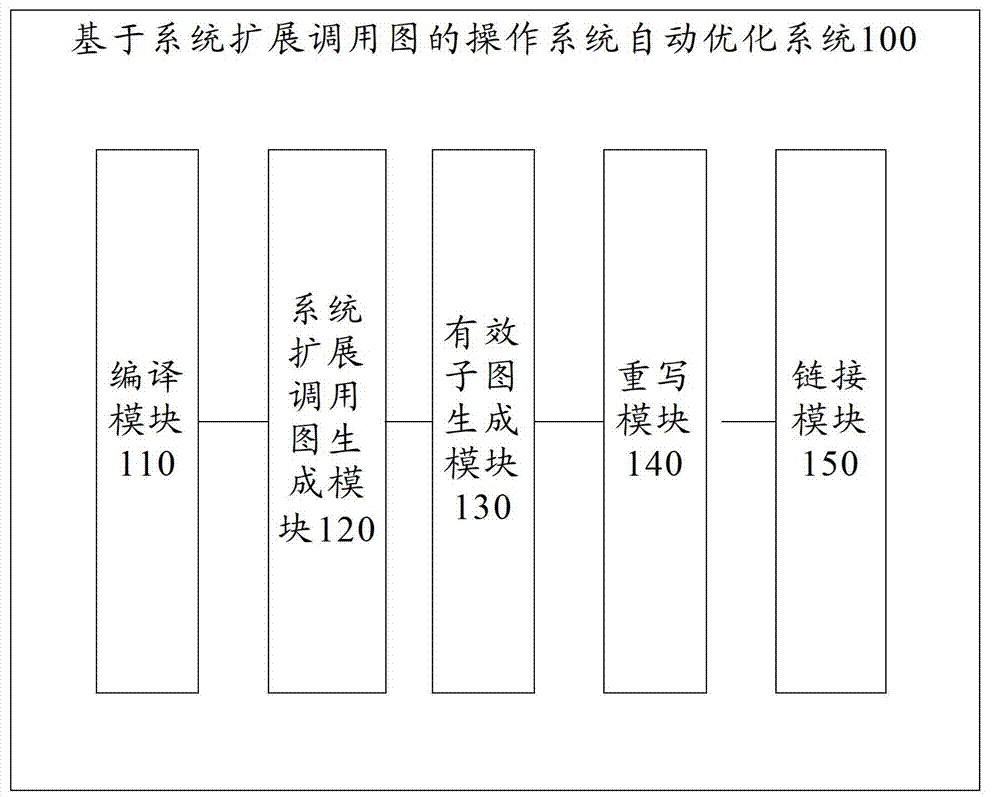
Automatic operating system optimization method and system based on system expansion call graph
InactiveCN103116514AReduce volumeImprove performanceProgram controlMemory systemsDead codeDirected graph
The invention provides an automatic operating system optimization method based on a system expansion call graph. The method comprises the following steps: compiling a source code of an operating system to generate a target file which can be redirected; constructing a system expansion call graph according to the target file, wherein the system expansion call graph is a directed graph and is used for recording a reference relationship between a function and a data object in the target file; generating an effective subgraph of the operating system according to the system expansion call graph; rewriting the target file according to the effective subgraph to obtain an optimized target file; and linking the optimized target file to obtain an optimized operating system. The dead codes are automatically eliminated in the system, the volume of the system is reduced, the system performance is improved, the operation is convenient and efficient, and the optimization effect is obvious. The invention also discloses an automatic operating system optimization system based on the system expansion call graph.
Owner:TSINGHUA UNIV
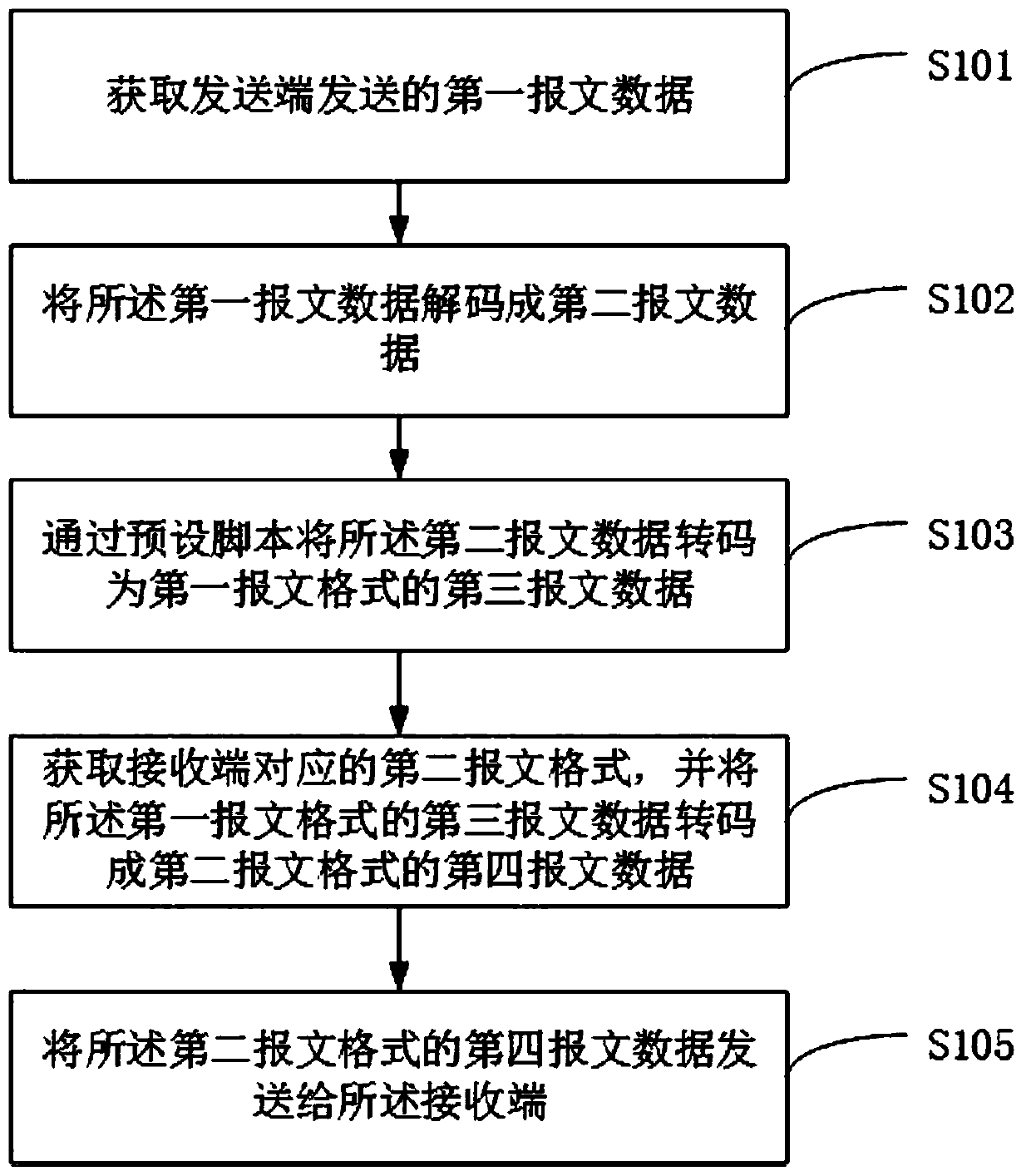
Message sending method and device, terminal equipment and storage medium
ActiveCN110445860AImprove sending efficiencyImprove transmission efficiencyTransmissionDead codeComputer hardware
The invention is applicable to the technical field of communication, and provides a message sending method and device, terminal equipment and a storage medium, and the method comprises the steps: obtaining first message data sent by a sending end; decoding the first message data into second message data; transcoding the second message data into third message data in a first message format througha preset script; obtaining a second message format corresponding to a receiving end, and transcoding the third message data in the first message format into fourth message data in the second message format; and sending the fourth message data in the second message format to the receiving end. The decoded message data is processed through the preset script, so that repeated code development and newcode writing are not needed when the sending end is newly added, dead codes and low-quality codes are avoided, the method can be used without professionals, the message transmission efficiency is improved, and the cost is reduced.
Owner:SHENZHEN KINGDOM TECH
Apparatus and method for detecting error in a digital image
ActiveUS7596277B2Improve efficiencyImprove reliabilityPicture reproducers using cathode ray tubesPicture reproducers with optical-mechanical scanningDead codeShift register
An apparatus and method for the detection of errors in compressed digital image is disclosed. In one embodiment, a signature is generated using a multiple input shift register and added to the compressed information. The signature is verified at the decoder to detect an error in the compressed information. Other information such as the frame number and / or color component type of the compressed image can also be verified to detect errors in the compressed information. In other embodiments, the decoder detects errors if there are bits remaining after decompression and / or if there are invalid codes at decompression. Once an error is detected, the compressed information can be discarded or re-sent and processed. Therefore, the detection of errors can significantly enhance at least the reliance of systems such as digital cinema that require compression of large amounts of data.
Owner:QUALCOMM INC
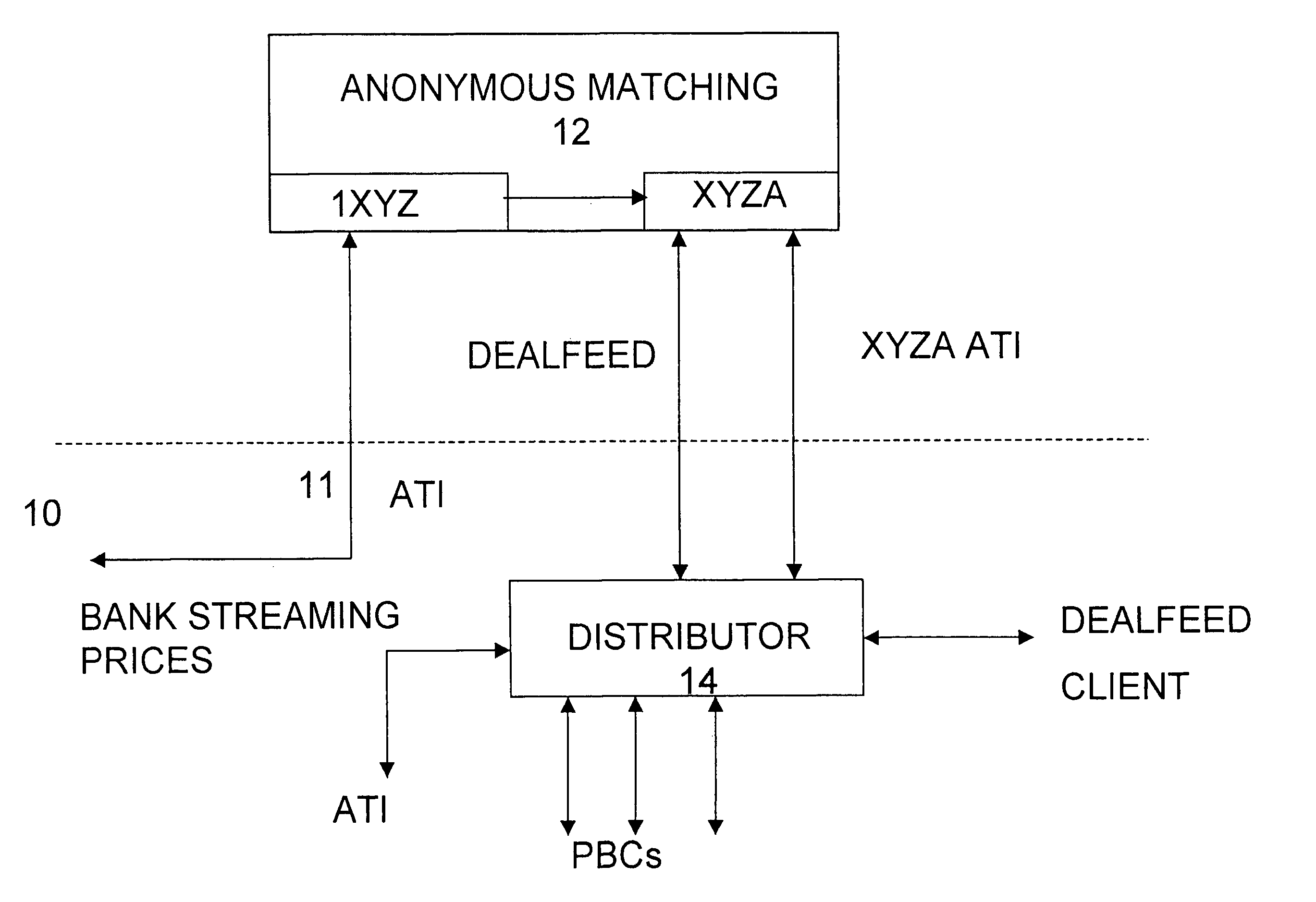
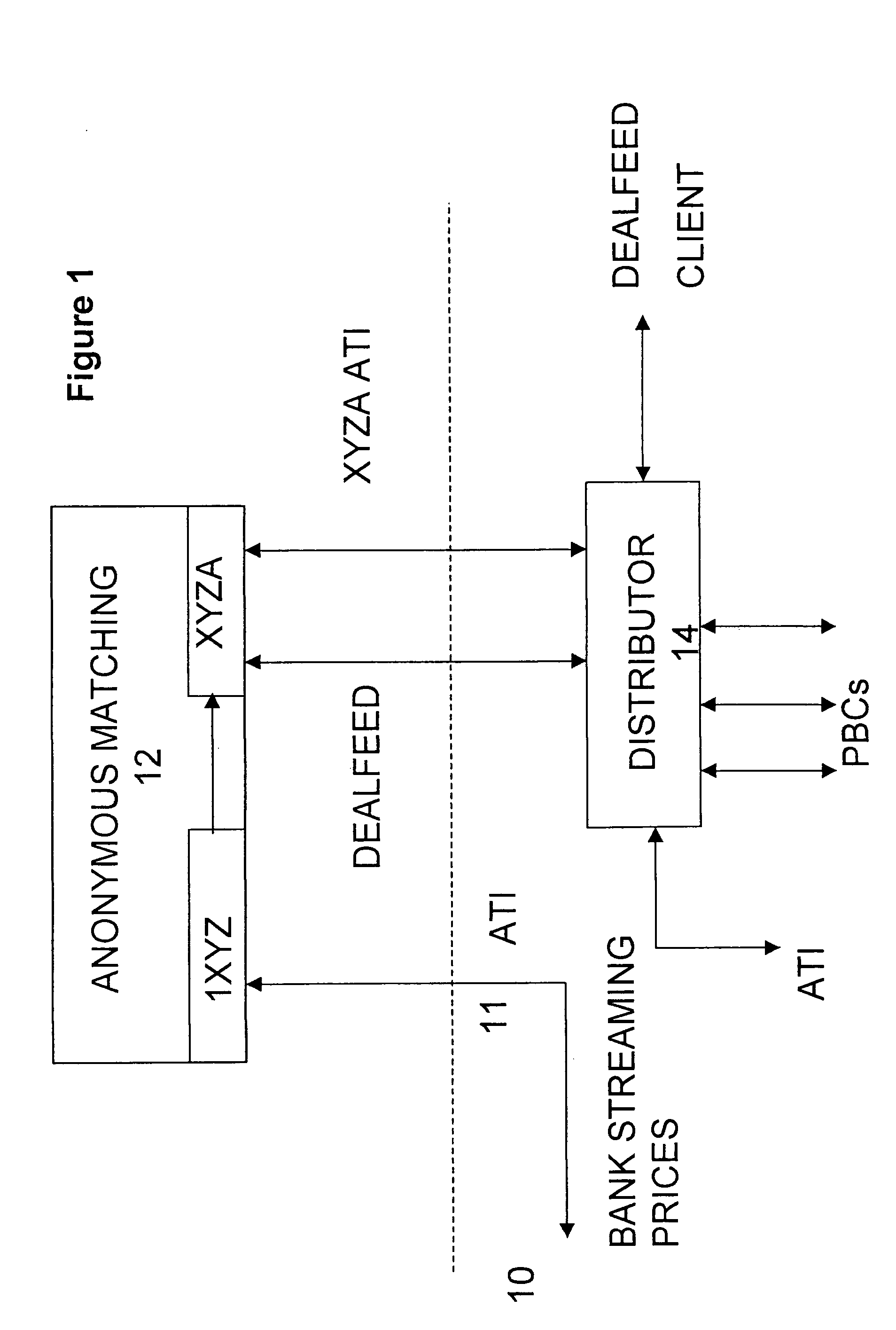
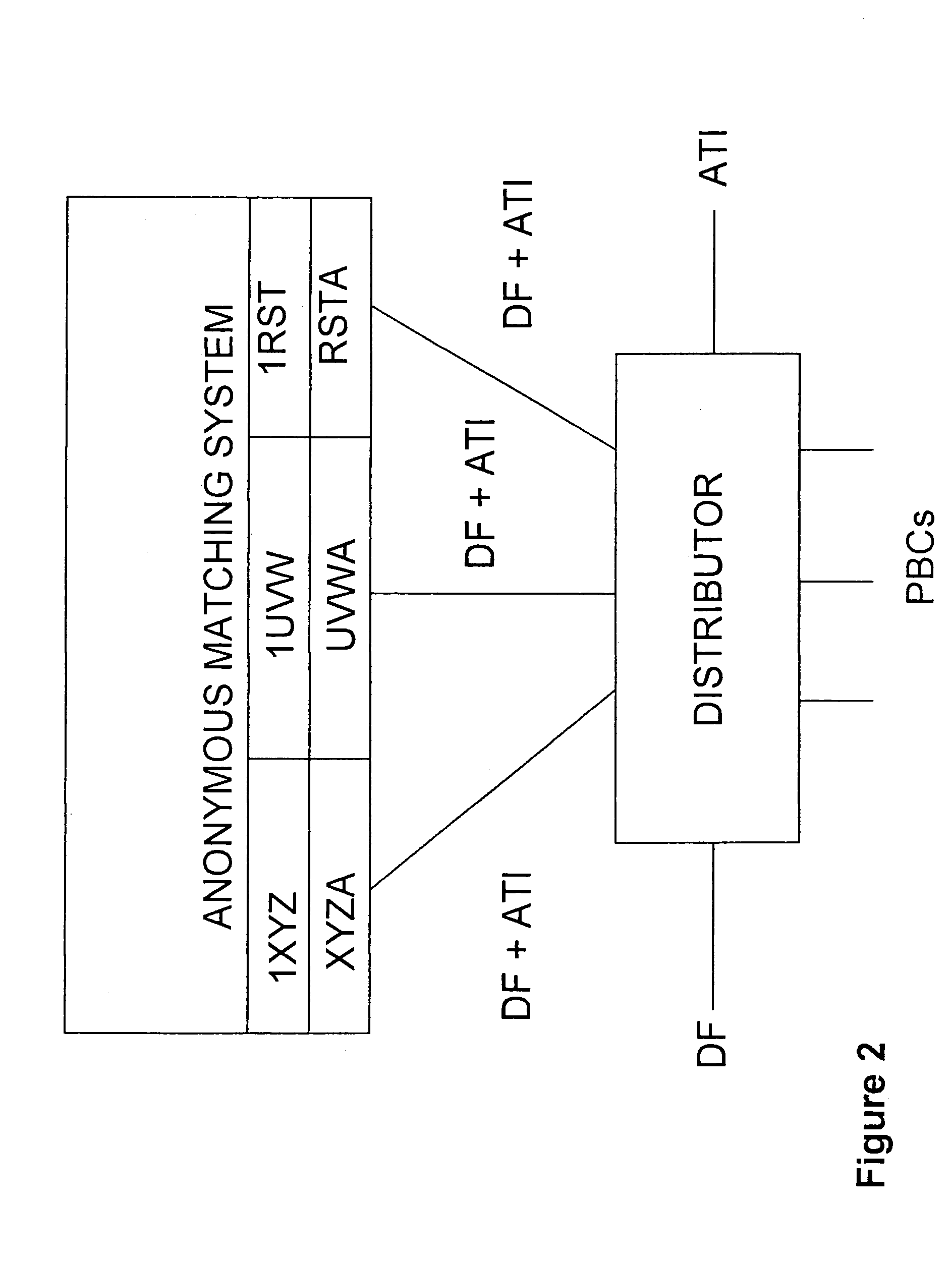
Automated trading system
An anonymous trading system is configured to receive a price stream from a bank or other institution. The price stream is converted into a quote stream and input into the trading system via an automated trading interface. The quote stream has its own deal code. The deal code credit limits are set so that the only parties that have credit with the deal code are other deal codes of the same institution. At least one of these deal codes represents a prime broker bank and prime broker customers therefore have access to the institution's price stream to the exclusion of other parties trading on the system. A distributor distributes the quotes from the trading system to the prime broker customers' traders, to prime broker customer automated trading interfaces, and to prime broker customer deal feed systems for logging of deal tickets and communication of those deal tickets to back office systems.
Owner:NEX GRP PLC
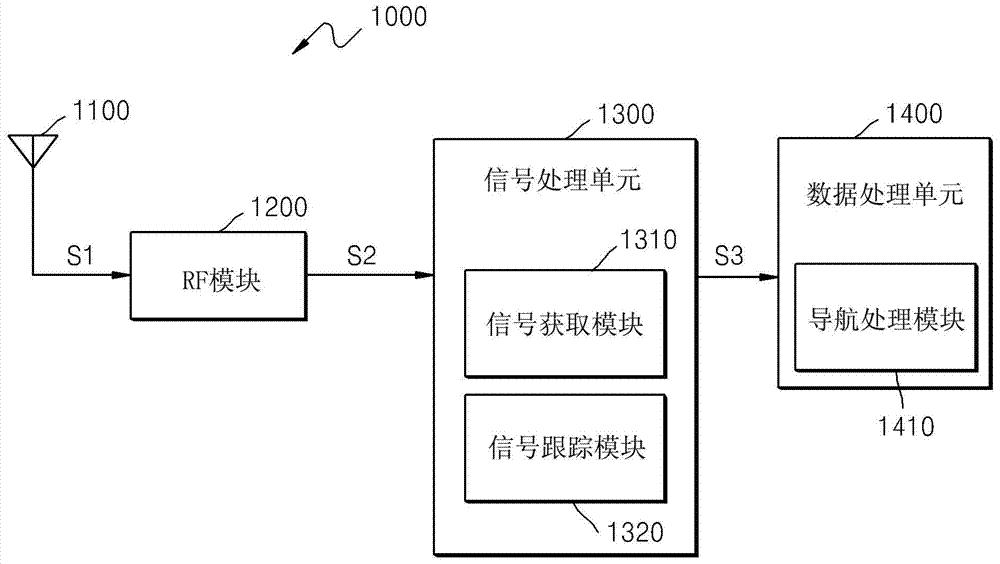
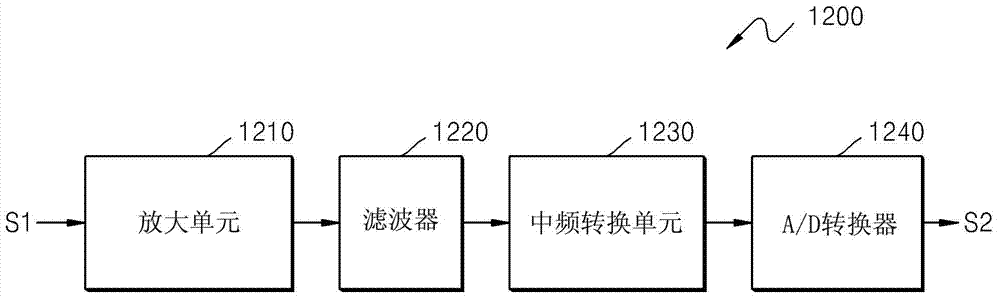
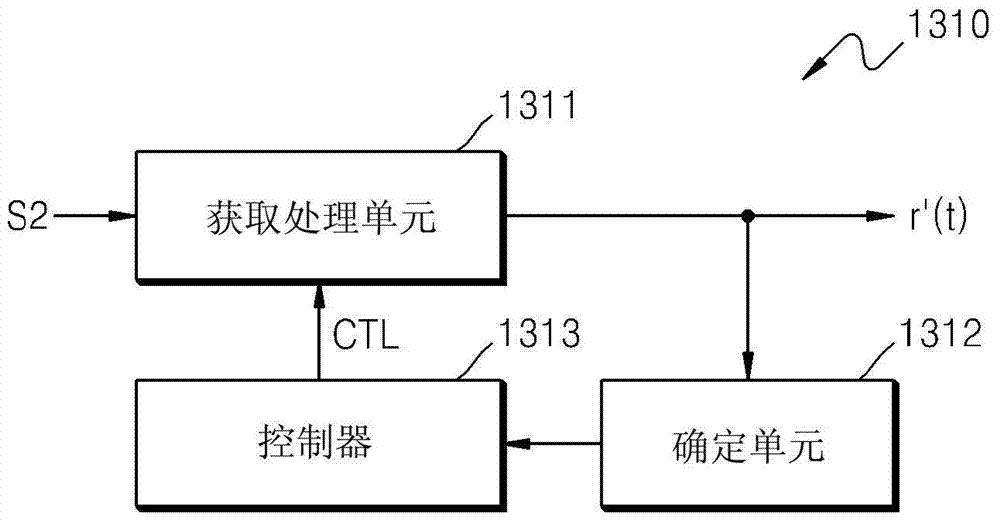
Signal tracking method of global navigation satellite system, signal tracking apparatus and satellite signal reciever having the same
The invention provides a signal tracking method of a global navigation satellite system, a signal tracking apparatus and a satellite signal reciever having the same. The method comprises the steps: generating duplication codes including an E code, a P code, an L code, a first code, and a second code; calculating the correlation value of the received satellite signal and the duplication codes; identifying the gradients of a plurality of slopes derived from correlated points respectively corresponding to the duplication codes; and detecting the time delay caused by multipath signal components according to the identification results.
Owner:SAMSUNG ELECTRONICS CO LTD
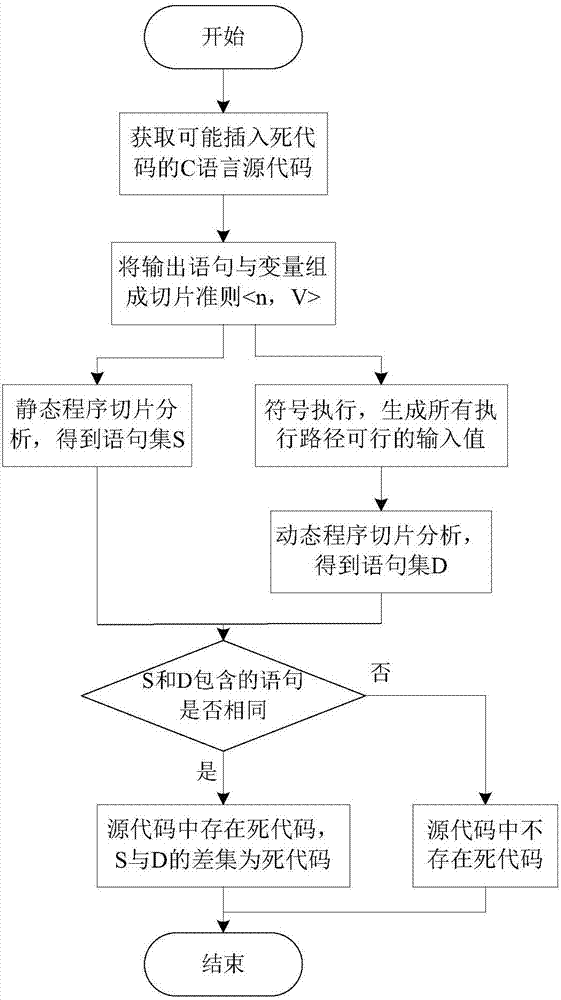
Program slicing technique-based C language dead code detection method
InactiveCN106951366AImprove accuracyStrong targetingSoftware testing/debuggingDead codeProgram slicing
The invention discloses a program slicing technique-based C language dead code detection method. The method mainly comprises the steps of forming a slicing criterion <n,V> by an output statement in a source code and a variable set in the output statement; performing static backward program slicing analysis and dynamic backward program slicing analysis on the source code; and comparing obtained analysis results to obtain a conclusion about whether a dead code exists or not. According to the method, a dead code statement contained in a C language code can be effectively detected, and the detection accuracy and efficiency are improved.
Owner:NANJING UNIV OF POSTS & TELECOMM
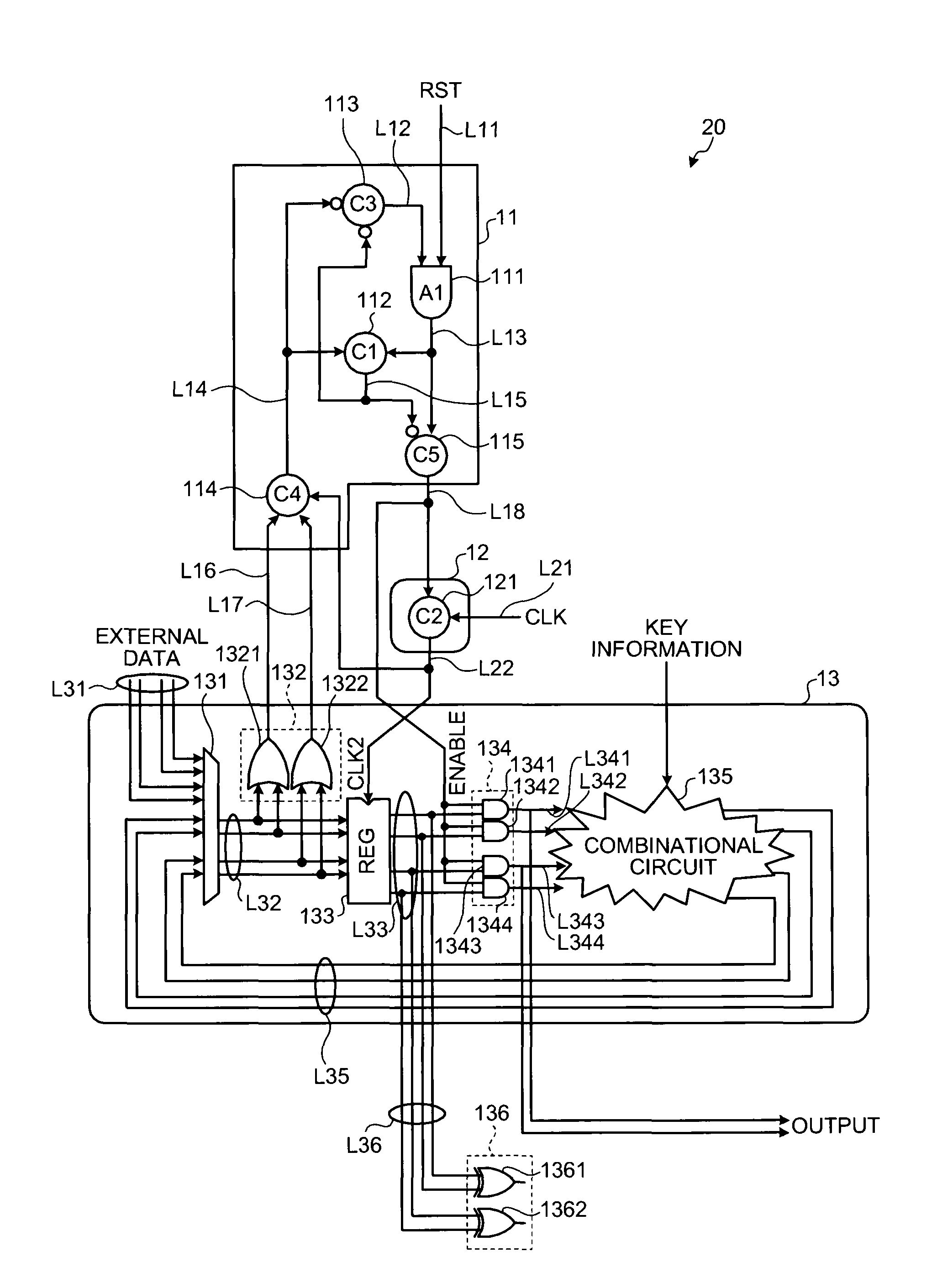
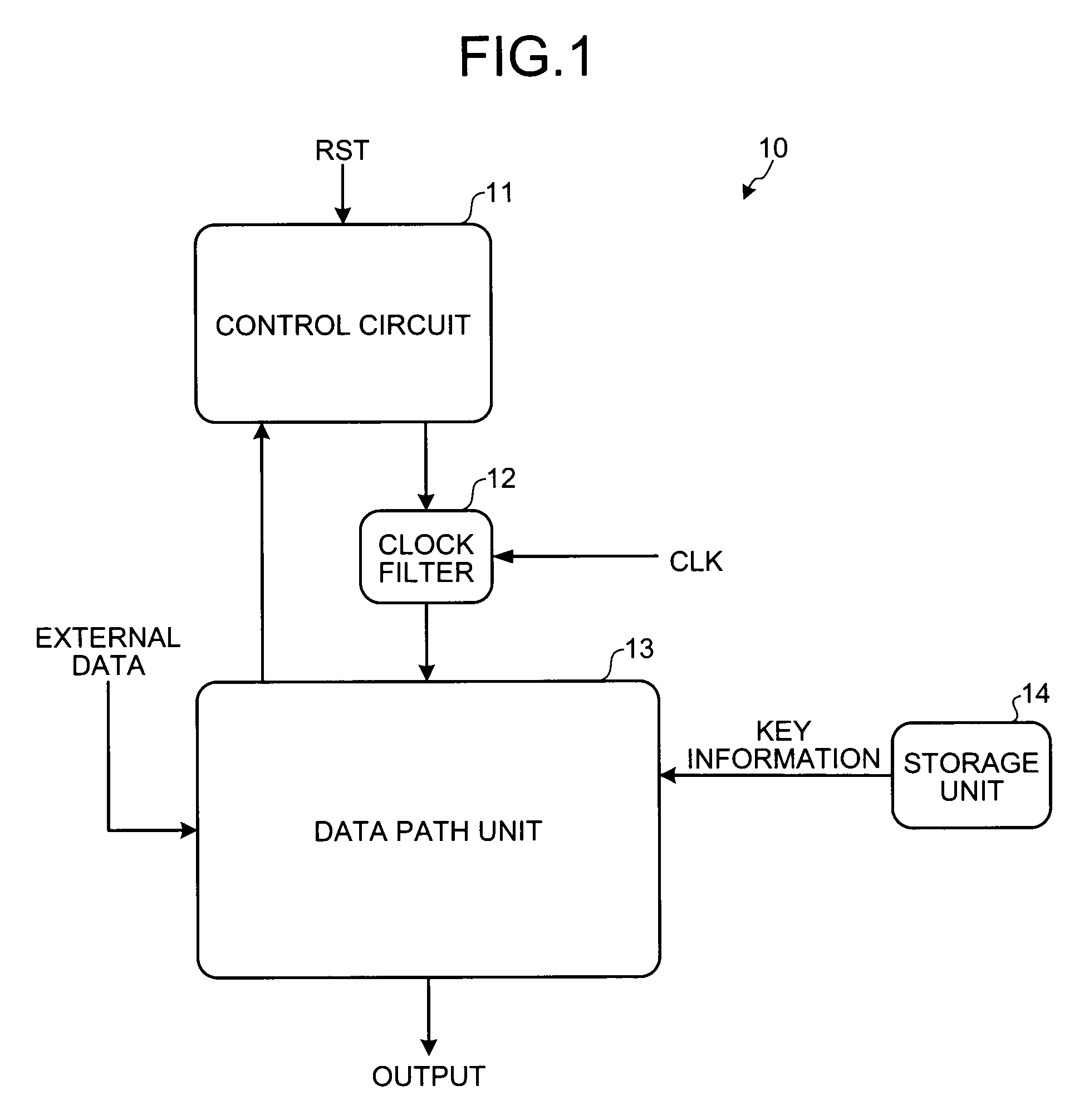
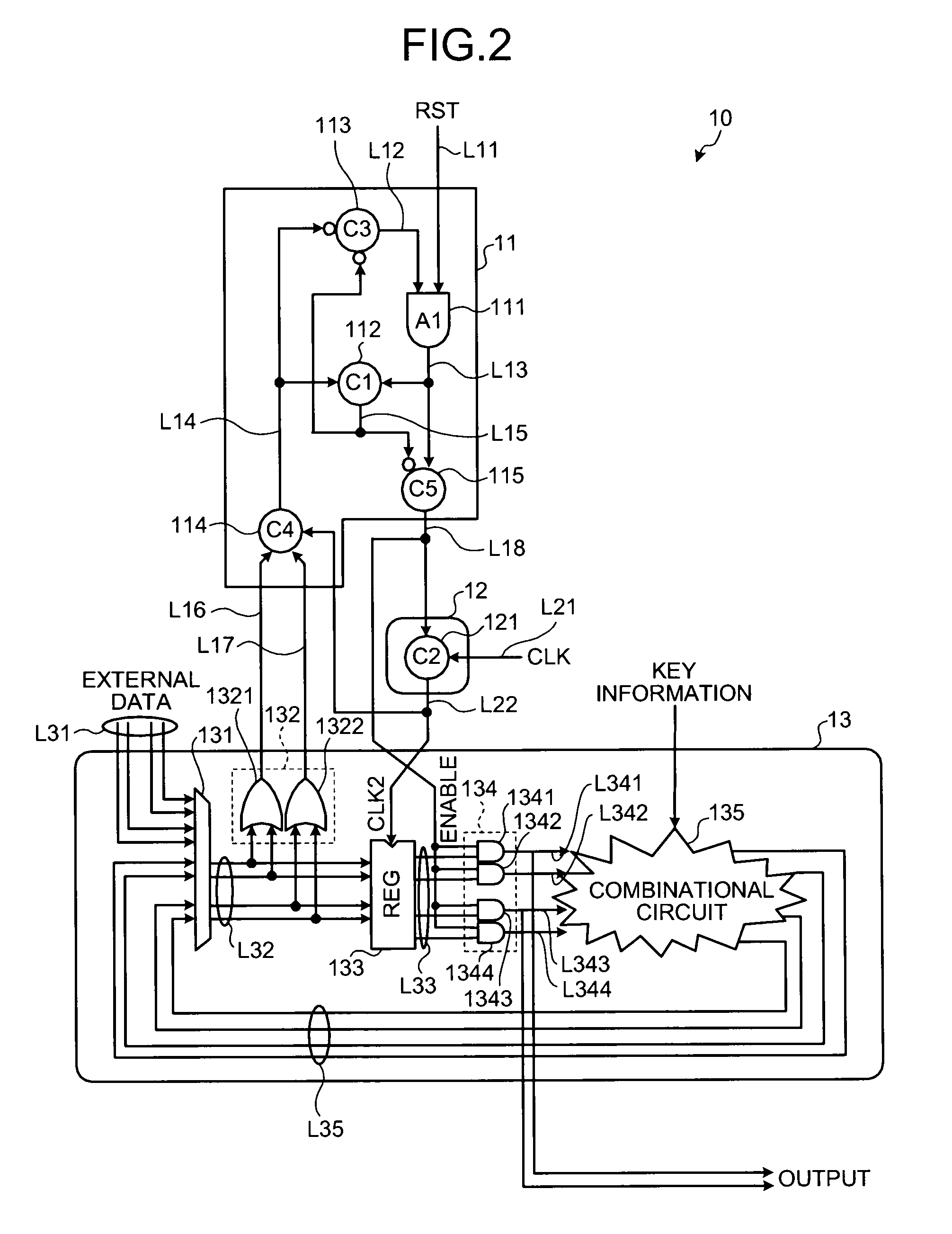
Encryption operating apparatus
Valid code data and invalid code data are alternately input to a register that fetches data synchronously with a clock signal. A state of a data value input to the register is monitored. Each time when it is determined that the data is stabilized by the valid code data, the register holds the valid code data.
Owner:KK TOSHIBA
Program automatic debugging method
The invention relates to a program automatic debugging method which includes the following steps: 101, reading and analyzing an assembly source program Y to obtain all variables used by the assembly source program Y, and generating a relation list A of the variables and page addresses respectively corresponding to the variables; 102, preprocessing and standardizing the assembly source program Y to form an assembly source program B easy to distinguish and check; and 103, performing page switching correctness check for the assembly source program B and finding and reporting page faults. By aid of the program automatic debugging method, page address faults in the programs can be fast and accurately checked, further invalid codes in the programs can be checked easily, manpower is saved, and efficient proceeding of development work is ensured. The program automatic debugging method is wide in application range and can be widely used for debugging of the programs with data spaces or program spaces having distinguishing of pages or section. The program automatic debugging method includes page address fault check for the programs with page / section characteristic storage spaces and of chips of digital signal processors (DSPs), micro-programmed control units (MCUs), microprocessor units (MPUs) and the like.
Owner:徐下兵
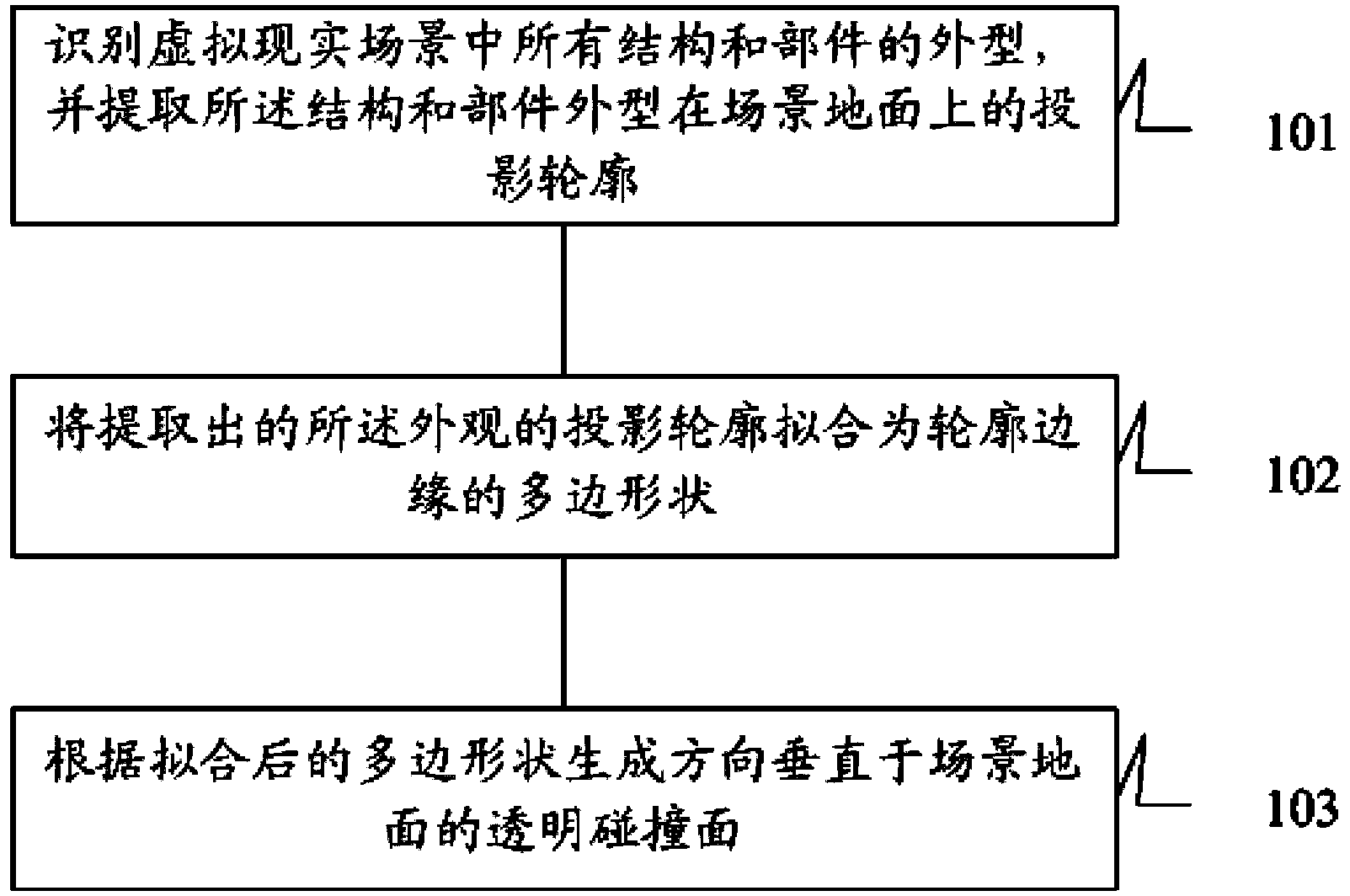
Virtual reality roaming process collision detection optimization design method and system thereof
InactiveCN103413348AEasy to operateAvoid stickingSpecial data processing applications3D modellingDead codeCollision detection
The invention discloses a virtual reality roaming process collision detection optimization design method and a system thereof. The method comprises the steps of identifying the appearances of all structures and parts on a roaming plane in a virtual reality scene and extracting the projection profile of the appearances of the structures and parts on a scene ground, fitting the extracted projection profile of the appearances of the structures and parts as a polygon shape of a profile edge, and generating a transparent collision surface which is perpendicular to the scene ground according to the polygon shape after fitting. According to the method and the system, a problem that a user can not walk out of a dead corner after entering into the dead corner in virtual reality roaming and the amount of computation is increased caused by nearness to a scene detail in the prior art is solved.
Owner:中国大唐集团科学技术研究总院有限公司
Method for initializing and utilizing a memory device for a plc
InactiveCN1922556AError detection/correctionProgramme control in sequence/logic controllersDead codeProgrammable logic controller
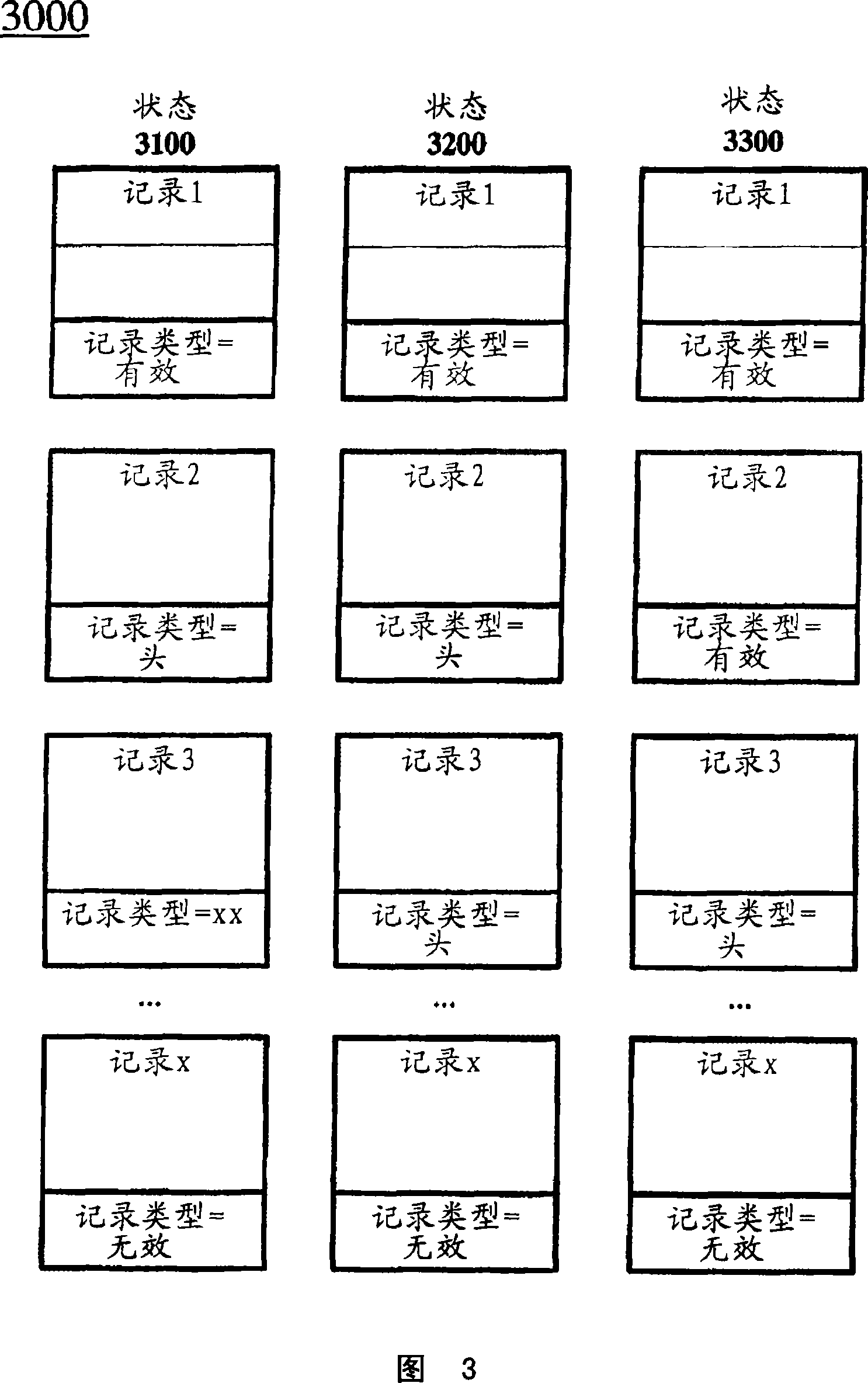
Certain exemplary embodiments comprise a method comprising a plurality of activities comprising: at a programmable logic controller comprising a memory device, receiving a request to create a data log that is adapted to receive data from a process; initializing the data log by writing to the data log a head marker code in the record type field of a first record and an invalid code in the record type field of a last record of the data log, the last record logically preceding and logically adjacent to the first record.
Owner:SIEMENS IND INC
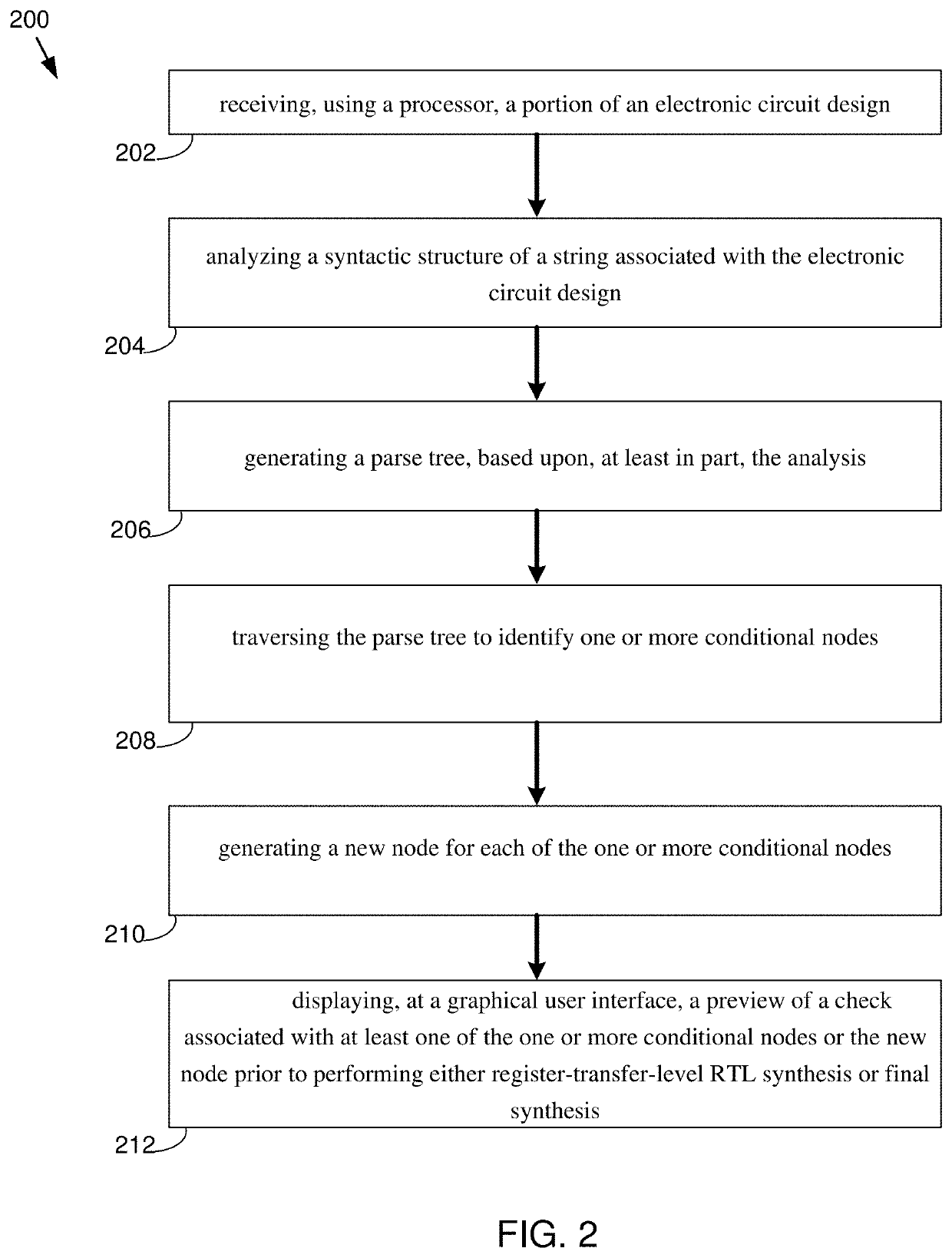
System, method, and computer program product for over-constraint/deadcode detection in a formal verification
The present disclosure relates to a method for use in the formal verification of an electronic circuit. Embodiments may include receiving, using a processor, a portion of an electronic circuit design and analyzing a syntactic structure of a string associated with the electronic circuit design. Embodiments may also include generating a parse tree, based upon, at least in part, the analysis and traversing the parse tree to identify one or more conditional nodes. Embodiments may further include generating a new node for each of the one or more conditional nodes and displaying, at a graphical user interface, a check, at least one of the one or more conditional nodes or the new node prior to performing either register-transfer-level RTL synthesis or final synthesis.
Owner:CADENCE DESIGN SYST INC
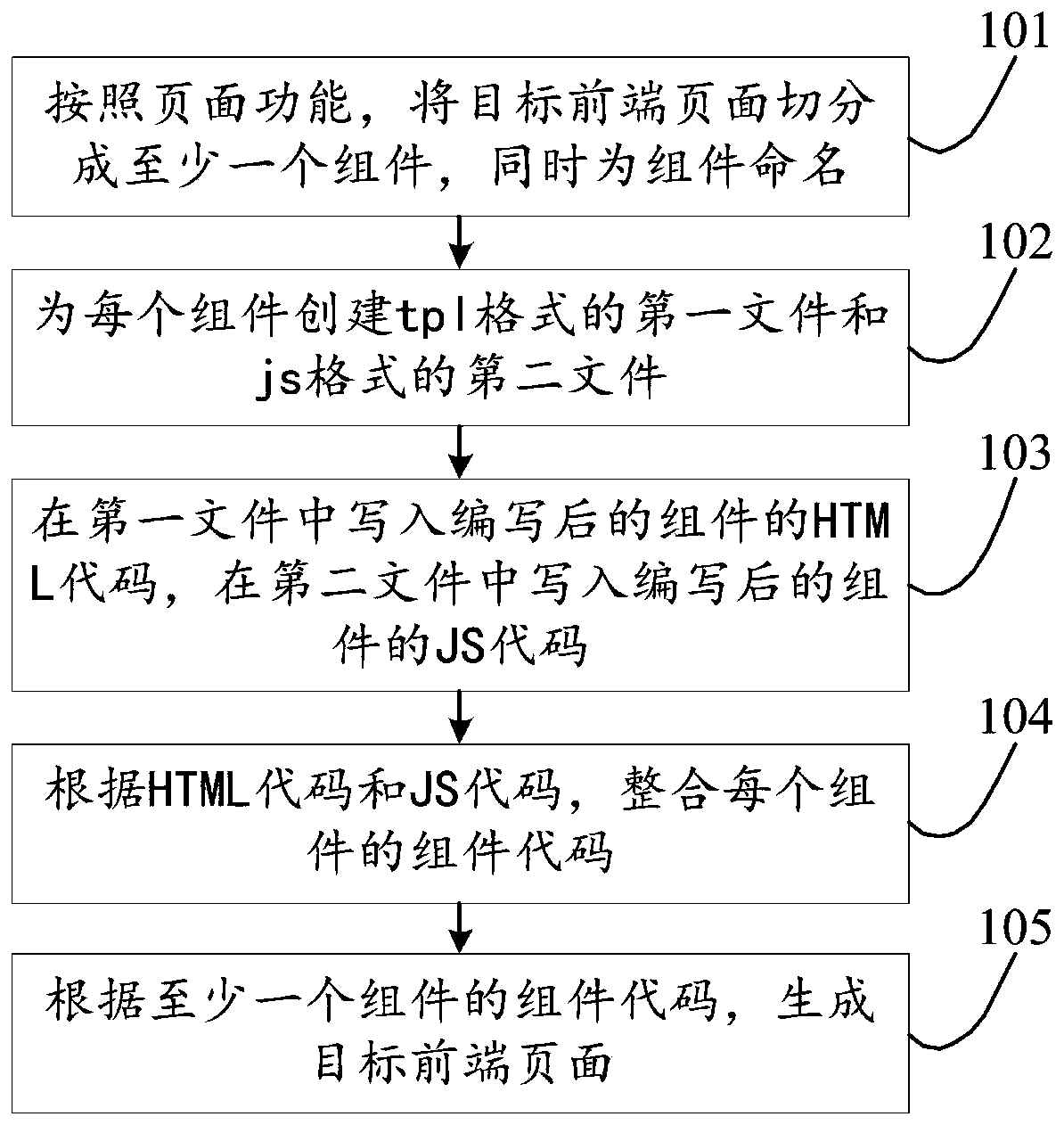
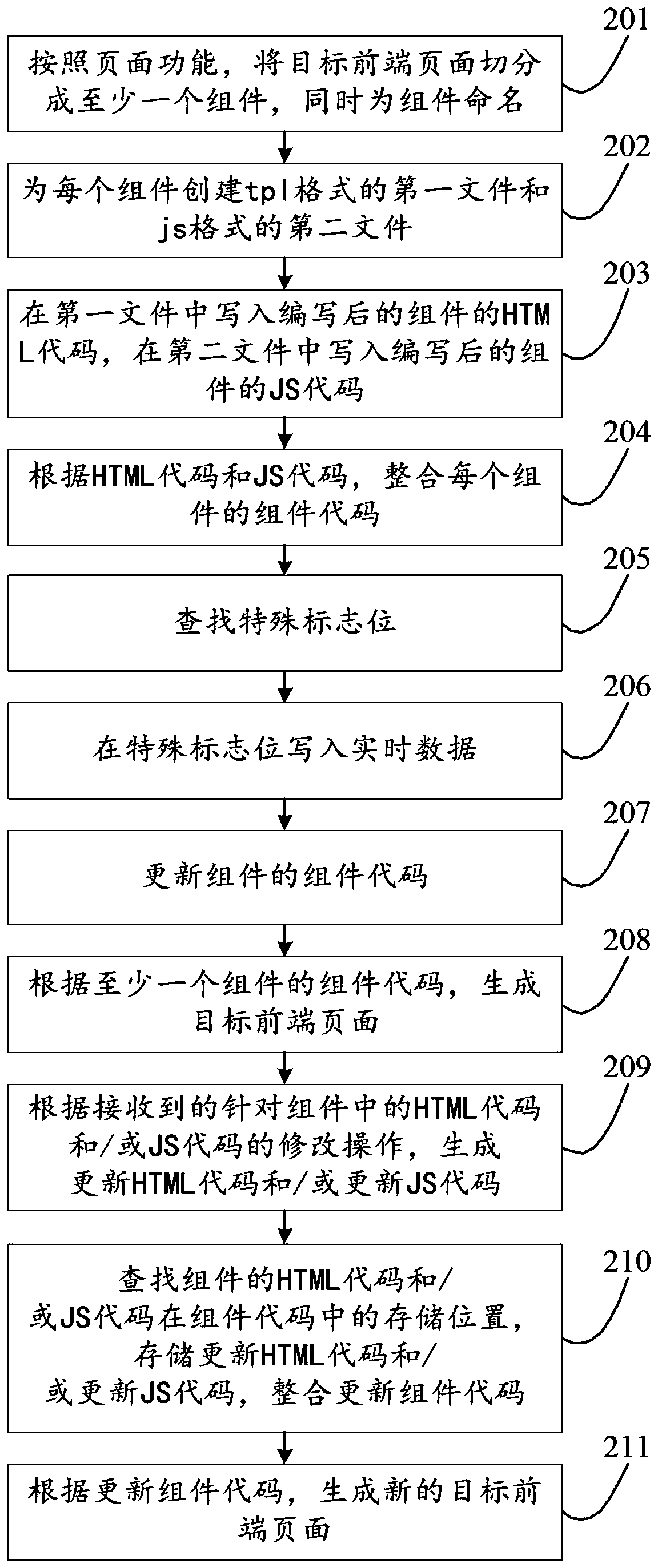
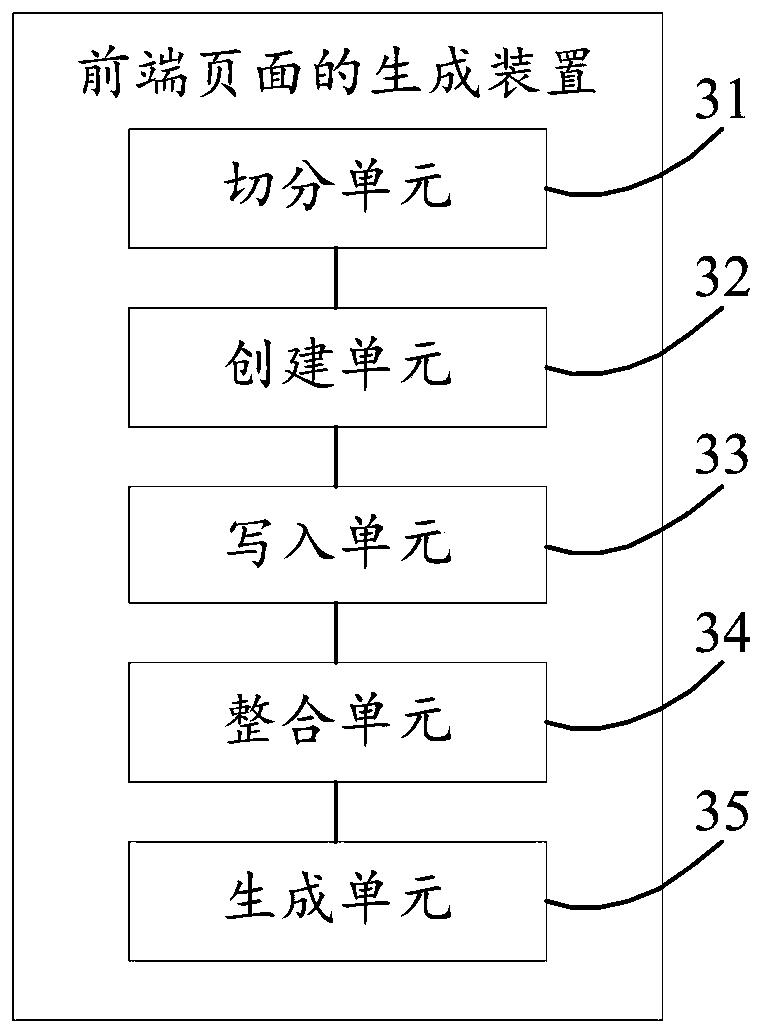
Front-end page generation method and device, storage medium and computer device
PendingCN109857398AEfficient managementSmall modificationSoftware engineeringDead codeComputer science
The invention discloses a front-end page generation method and device, a storage medium and a computer device, relates to the technical field of webpage development, and aims to solve the problem thata front-end code is difficult to maintain and improve. The method mainly comprises: segmenting a target front-end page into at least one component according to the page function, meanwhile, the components are named, and the component names of the components are different; creating a first file in a tpl format and a second file in a js format for each component, wherein the file names of the firstfile and the second file are component names of the components; Writing the HTML code of the compiled component into the first file, and writing the JS code of the compiled component into the secondfile; according to the HTML code and the JS code, the component code of each component is integrated; and generating a target front-end page according to the component code of the at least one component. The method adopted by the invention is mainly applied to the development and maintenance process of the front-end page.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
Anti-interception method and device for program installation package
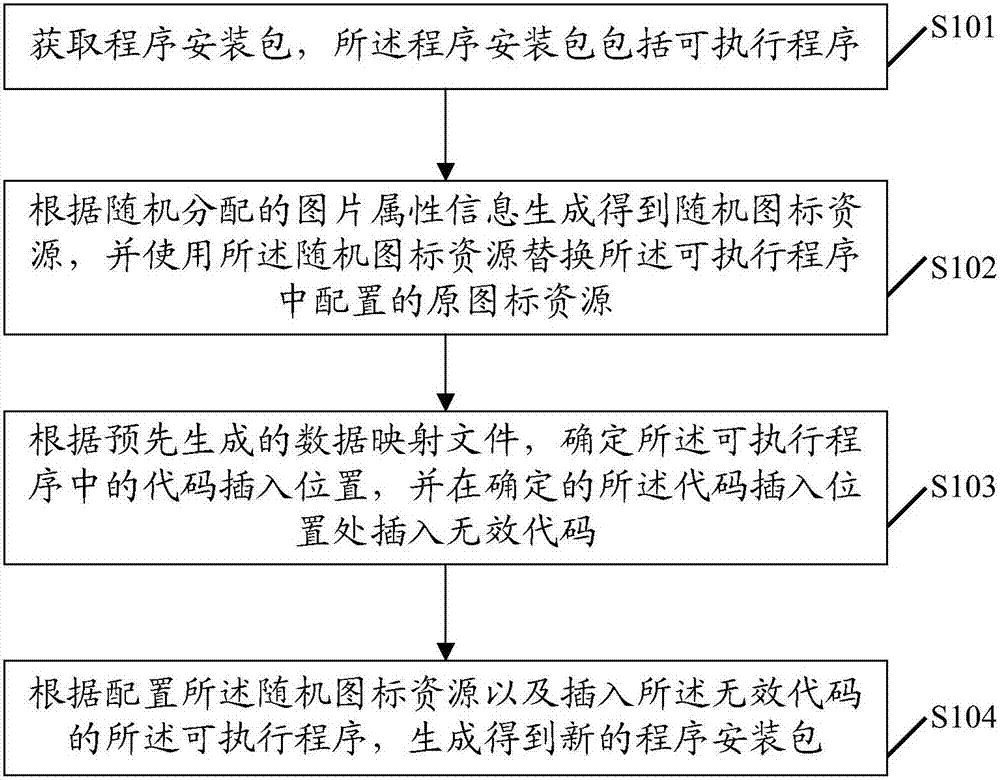
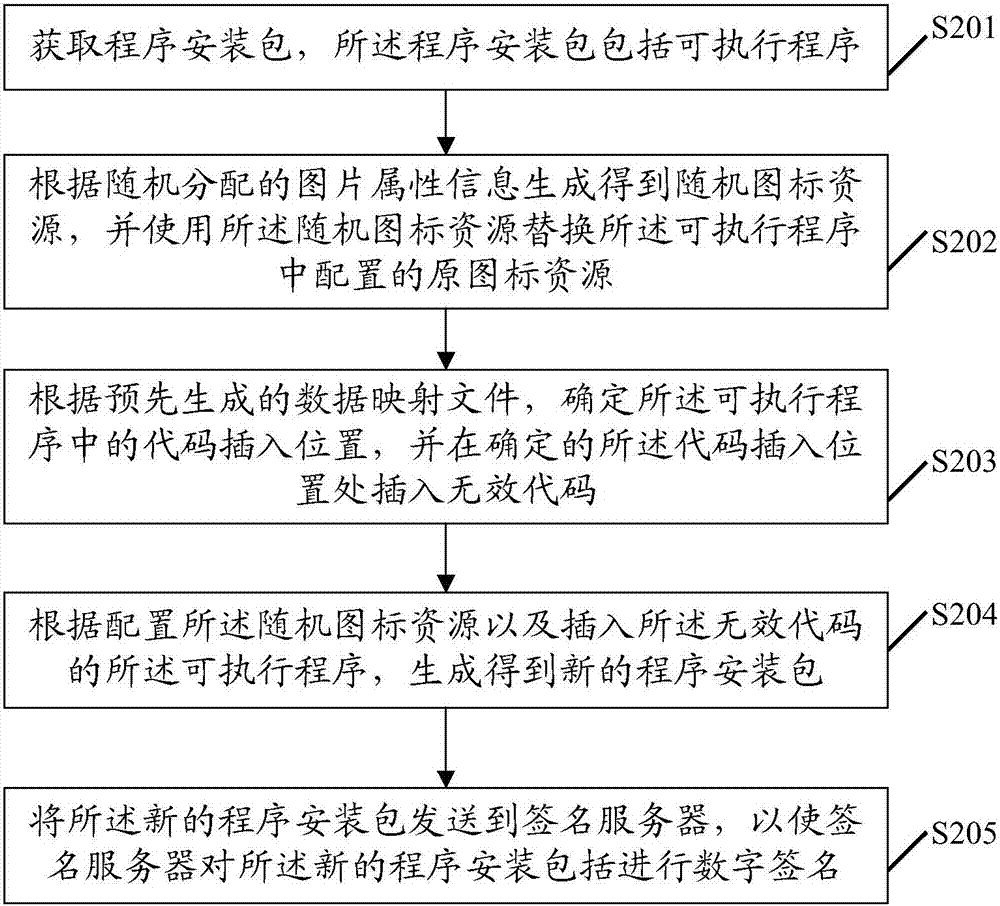
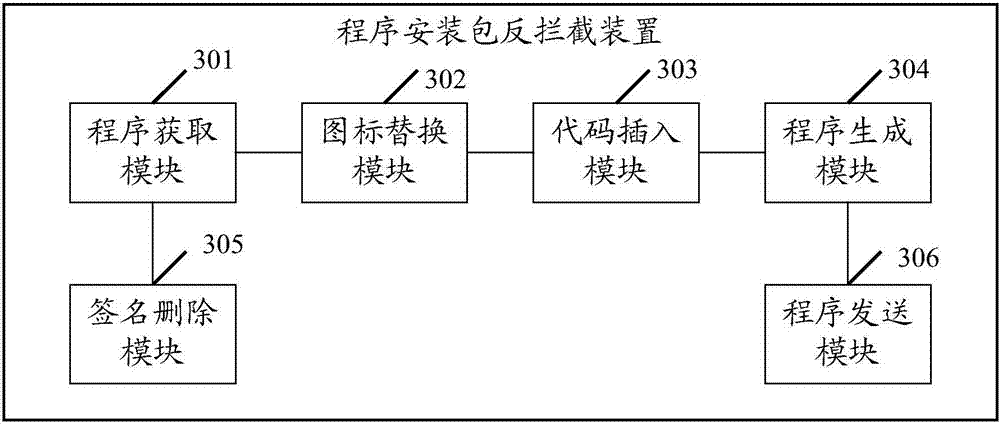
ActiveCN107315951AReduce the chance of interceptionPlatform integrity maintainanceDead codeComputer science
The embodiment of the invention discloses an anti-interception method for a program installation package. The method comprises the following steps that: obtaining the program installation package, wherein the program installation package comprises an executable program; according to randomly distributed picture attribute information, generating and obtaining a random icon resource, and using the random icon resource to replace an original icon resource configured in the executable program; according to a data mapping file generated in advance, determining a code insertion position in the executable program, and inserting an ineffective code into the determined code insertion position; and according to the configured random icon resource and the executable program in which the ineffective code is inserted, generating and obtaining a new program installation package. The embodiment of the invention also discloses an anti-interception device for the program installation package. When the embodiment of the invention is adopted, a probability that the program installation package is intercepted can be lowered.
Owner:TENCENT TECH (SHENZHEN) CO LTD
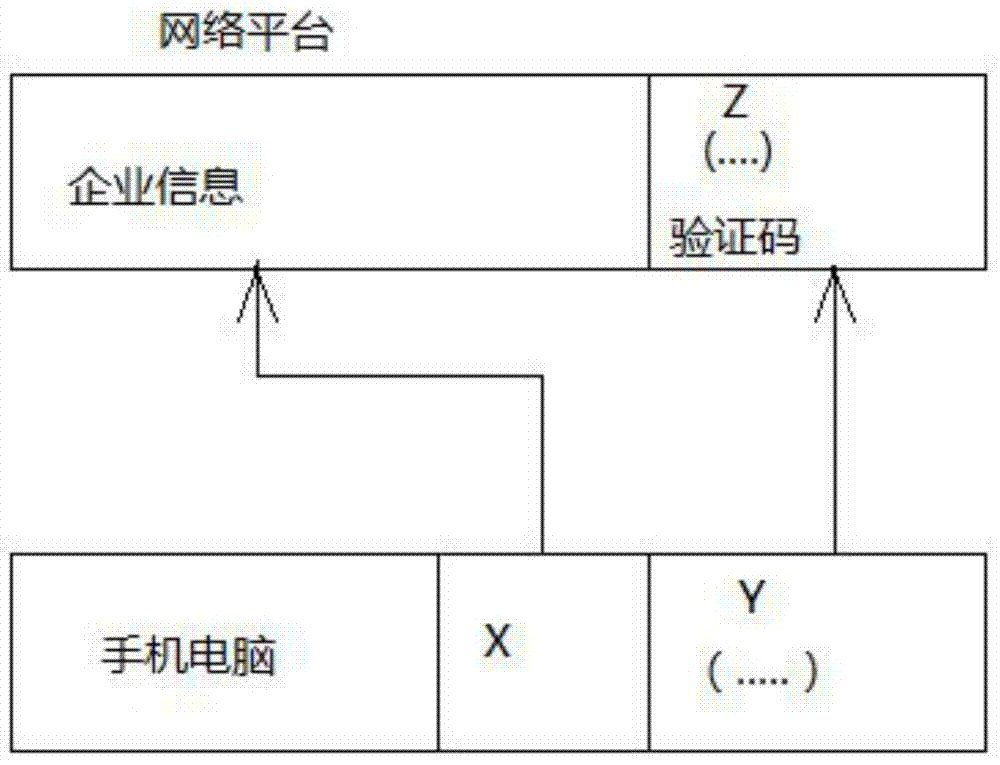
Commodity anti-fake method
The invention discloses a commodity anti-fake method. The method includes the steps that anti-fake codes correlative to the commodity information of commodities are generated, a service terminal including the anti-fake codes and the commodity information of the commodities is built, and the correlative anti-fake code scheme mode is represented by x+y(......)=ze(......), wherein x is the enterprise website, y(......) is the dealer code, and ze is the product verification code. By means of the commodity anti-fake method, the defects existing in the prior art are overcome, due to the fact that two or more passwords are set in the scheme without considering the product, even though the product can be counterfeited, the passwords cannot be copied, and thus counterfeiting cannot be achieved.
Owner:吴永
Automated trading systems
In an electronic trading system, prime brokerage services may be provided by assigning one or more dependent or child deal codes to a deal code. Prime broker trades are conducted via the dependent deal codes but appear to the market as deals with the parent deal code using credit assigned to the parent deal code. The prime bank customer is a dependent deal code of the customer bank which also trades on the system, allowing credit to be allocated by the customer dependent code for prime broker trades. A deal code may have several dependent deal codes which can trade with one another. Dependent deal codes can be used to expand the size of trading floors beyond that which can be supported by a single deal code and to assist in migration between system versions.
Owner:EBS GROUP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com