Patents
Literature
460results about How to "Small modification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
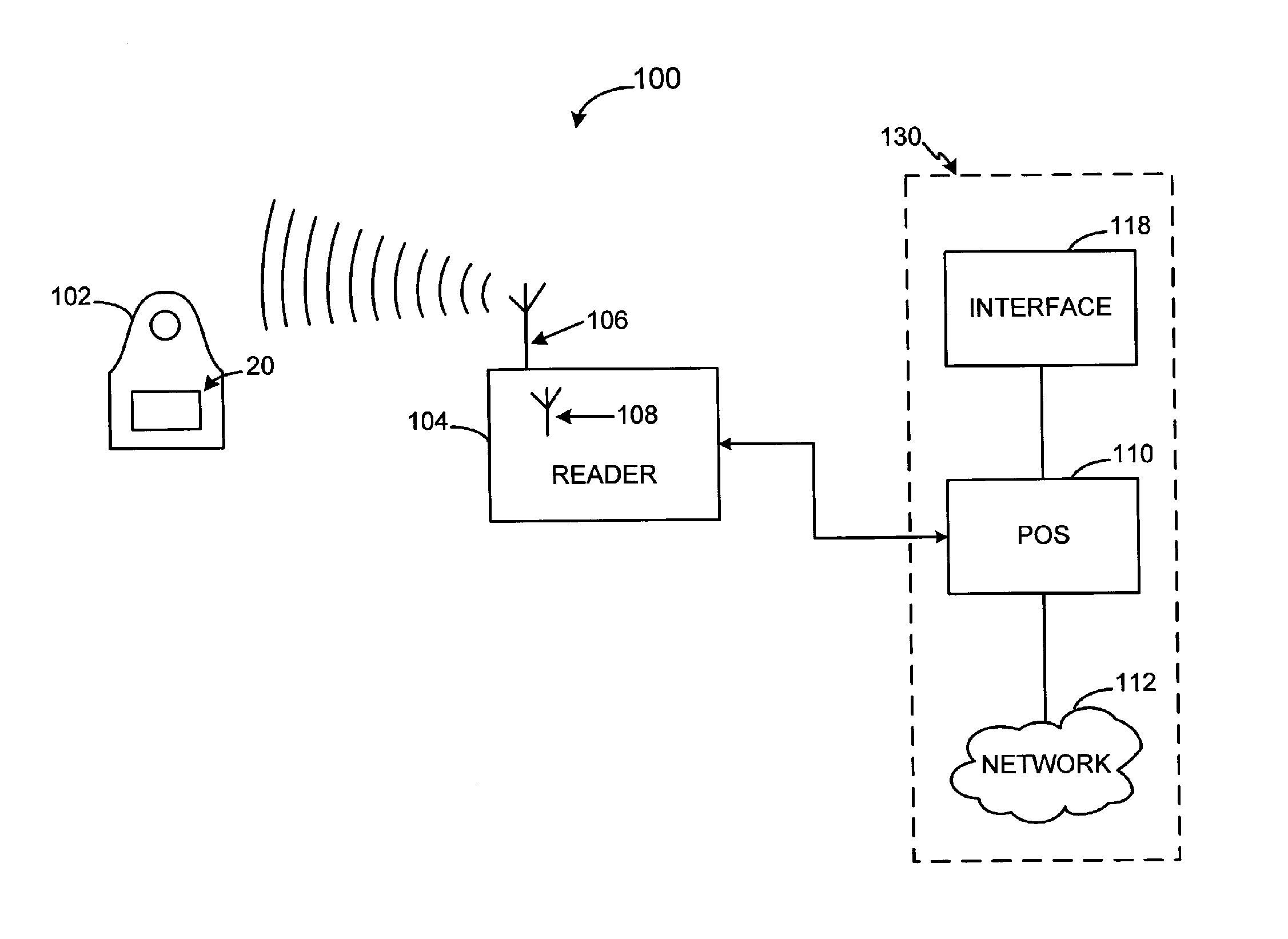
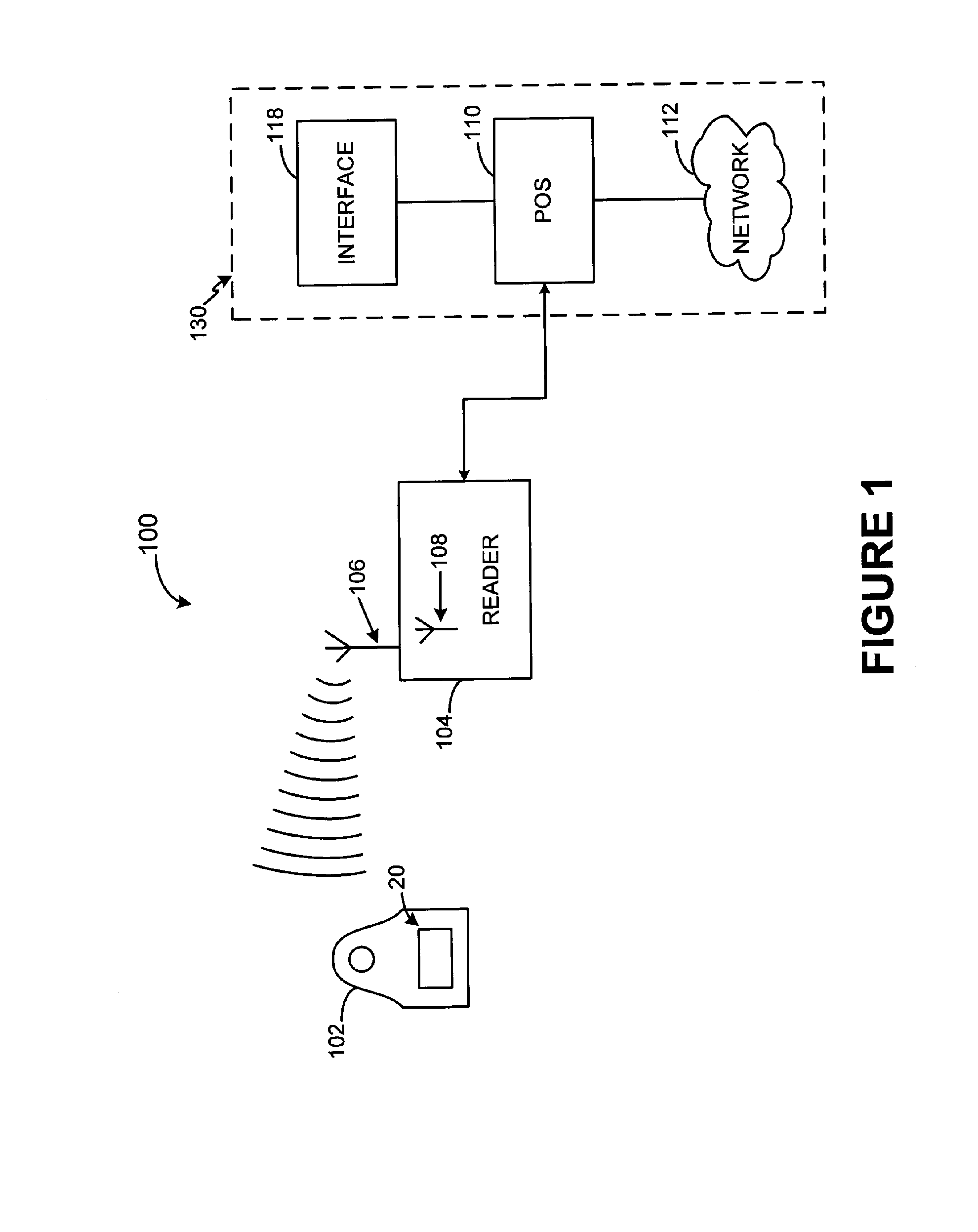
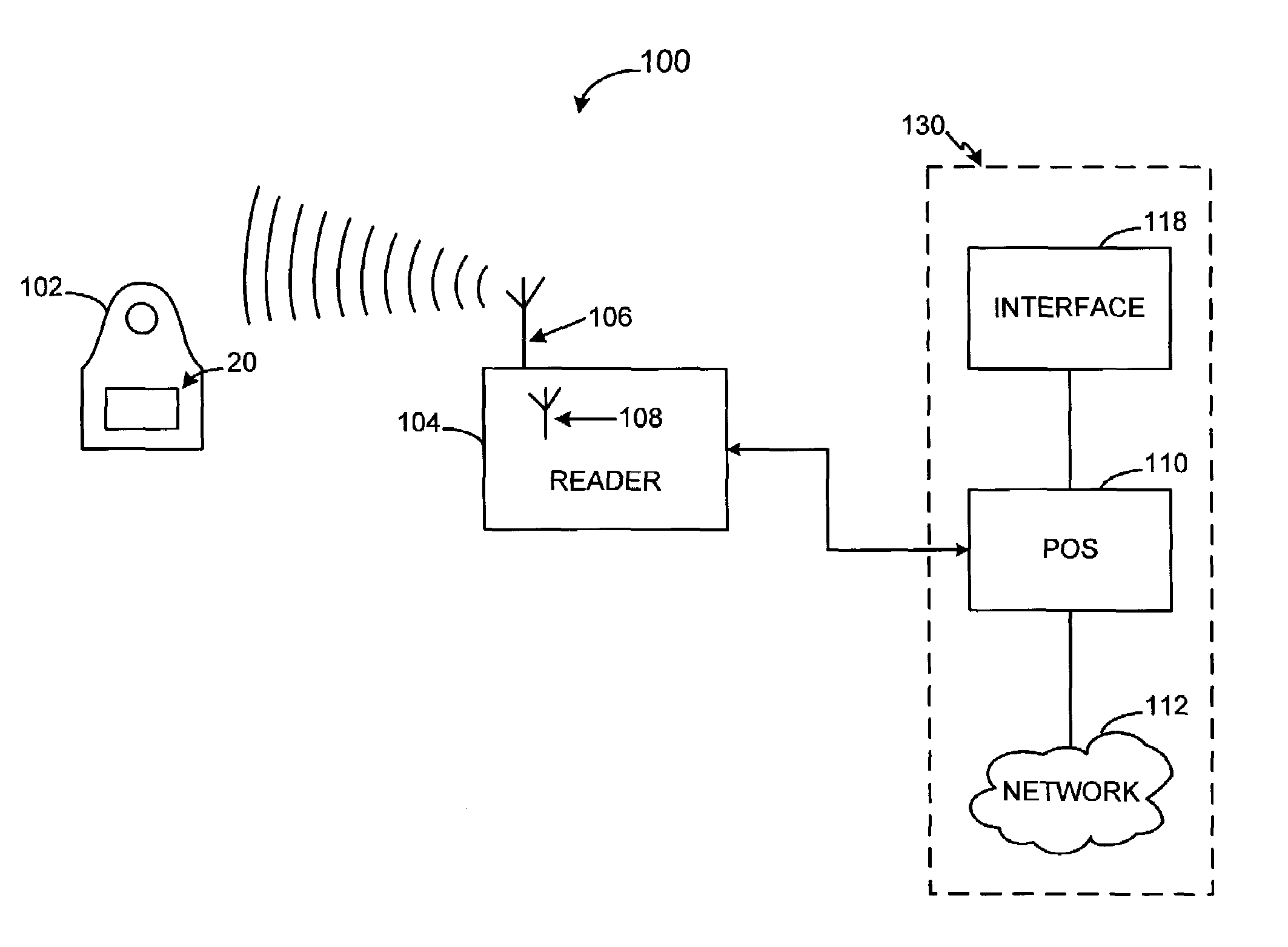
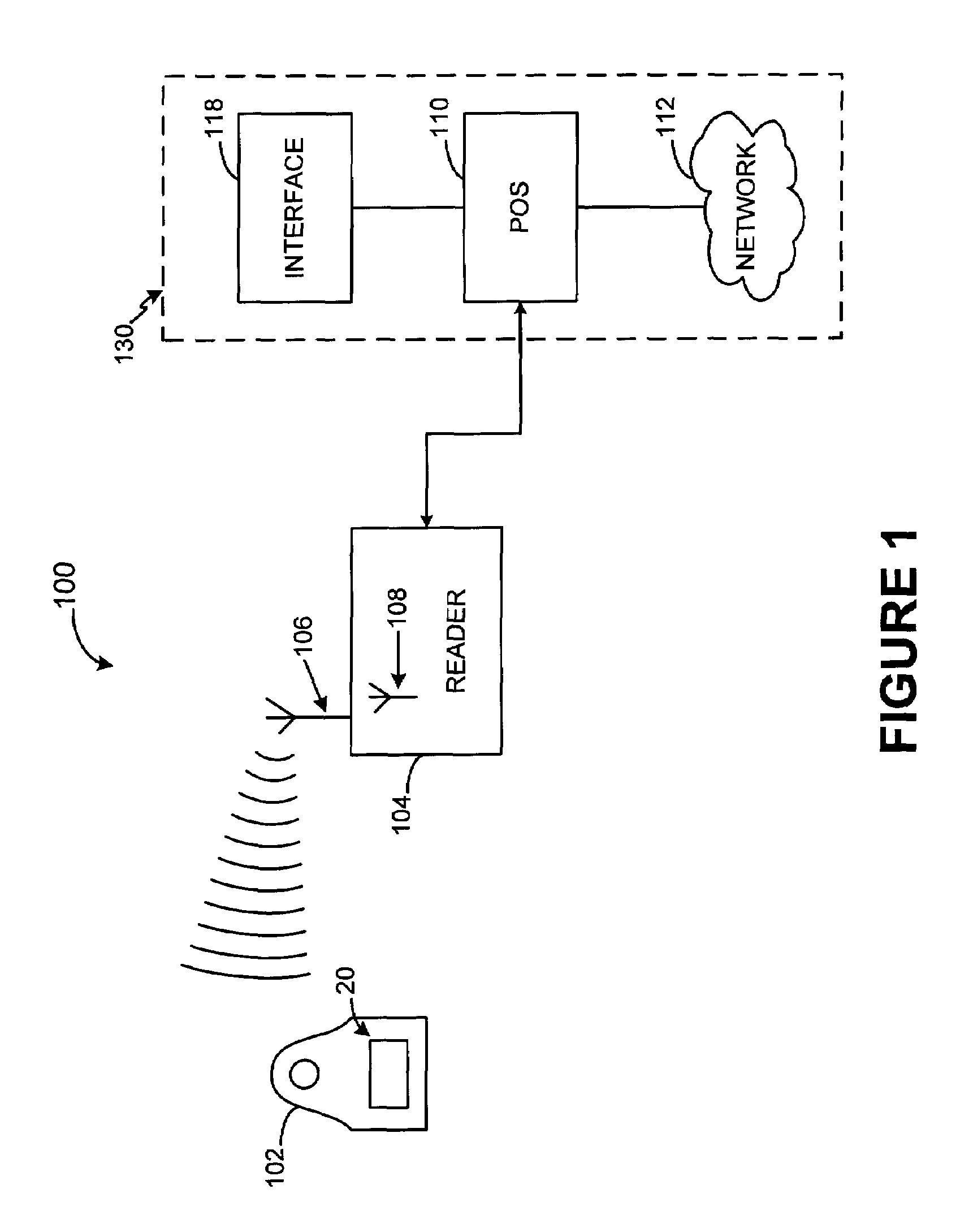
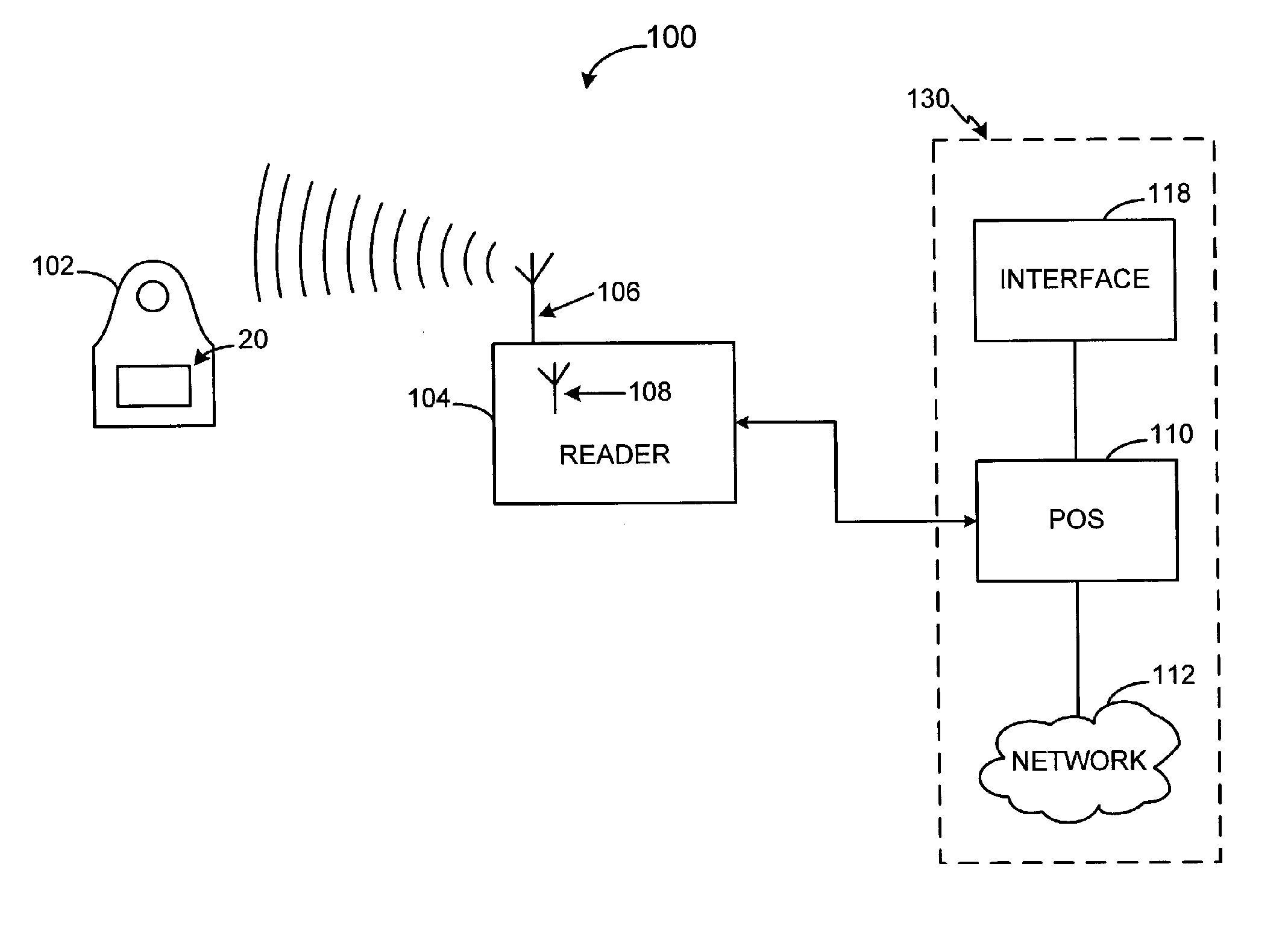
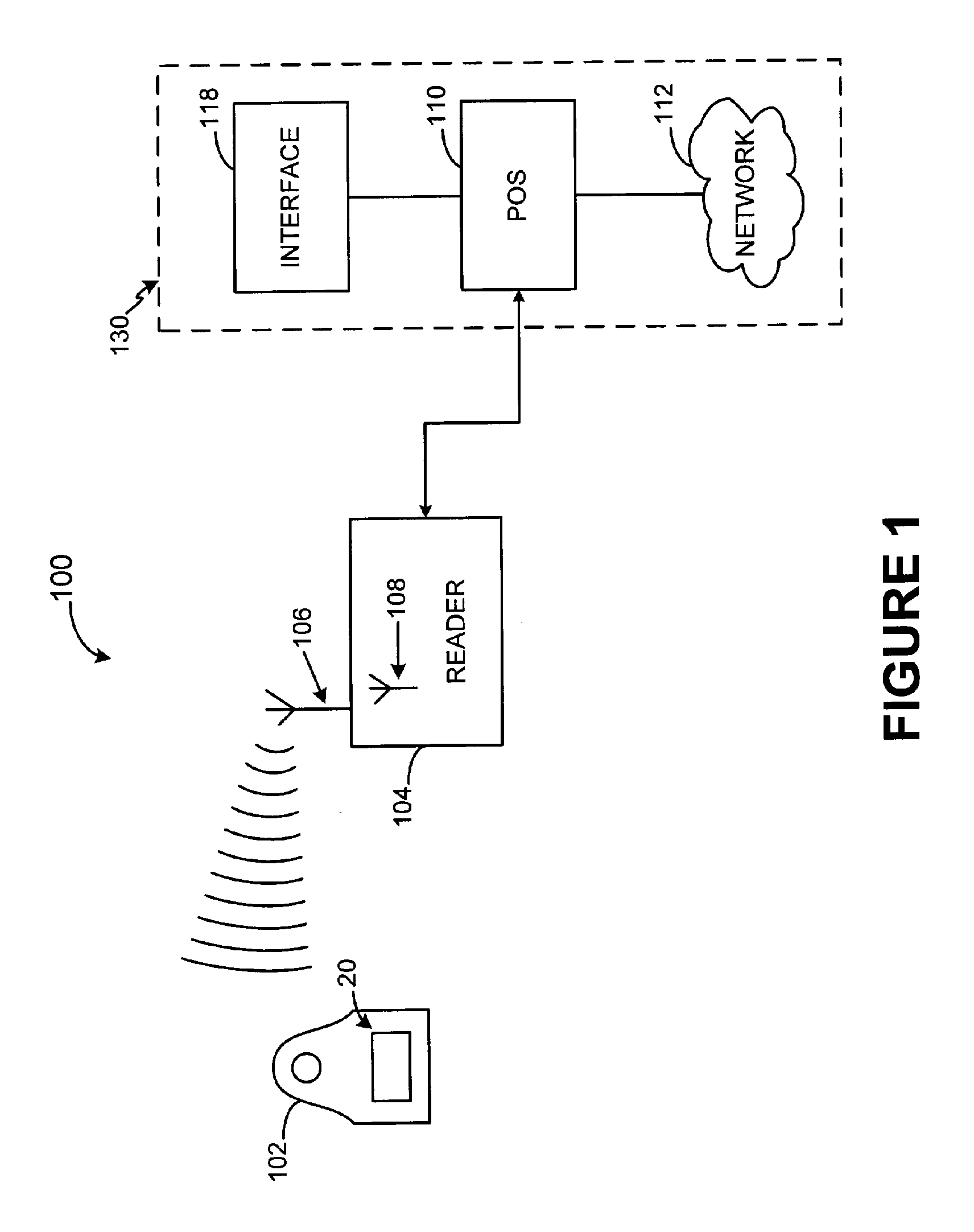
System and method for providing a RF payment solution to a mobile device
InactiveUS20060074698A1Small modificationComputer security arrangementsBuying/selling/leasing transactionsPersonal computerUSB
A process for providing an RF module configured to convert a nontraditional transaction device for traditional transaction completion is disclosed. The RF module is placed in physical and logical communication with a microprocessor of a nontraditional transaction device for providing user account information to the microprocessor and for receiving data from a RFID reader, kiosk or personal computer. The microprocessor is configured to activate operation of the RF module prior to transaction processing. The RF module may also receive secondary identification information, such as, a PIN, voice recognition data or biometric data for secondary end user authentication. The RF module may also transmit user account data for transaction processing using a USB interface of the nontraditional transaction device.
Owner:LIBERTY PEAK VENTURES LLC
RF payment via a mobile device
InactiveUS7493288B2Small modificationComputer security arrangementsBuying/selling/leasing transactionsPaymentBiometric data
A process for providing an RF module configured to convert a nontraditional transaction device for traditional transaction completion is disclosed. The RF module is placed in physical and logical communication with a microprocessor of a nontraditional transaction device for providing user account information to the microprocessor and for receiving data from a RFID reader, kiosk or personal computer. The microprocessor is configured to activate operation of the RF module prior to transaction processing. The RF module may also receive secondary identification information, such as, a PIN, voice recognition data or biometric data for secondary end user authentication. The RF module may also transmit user account data for transaction processing using a USB interface of the nontraditional transaction device.
Owner:LIBERTY PEAK VENTURES LLC
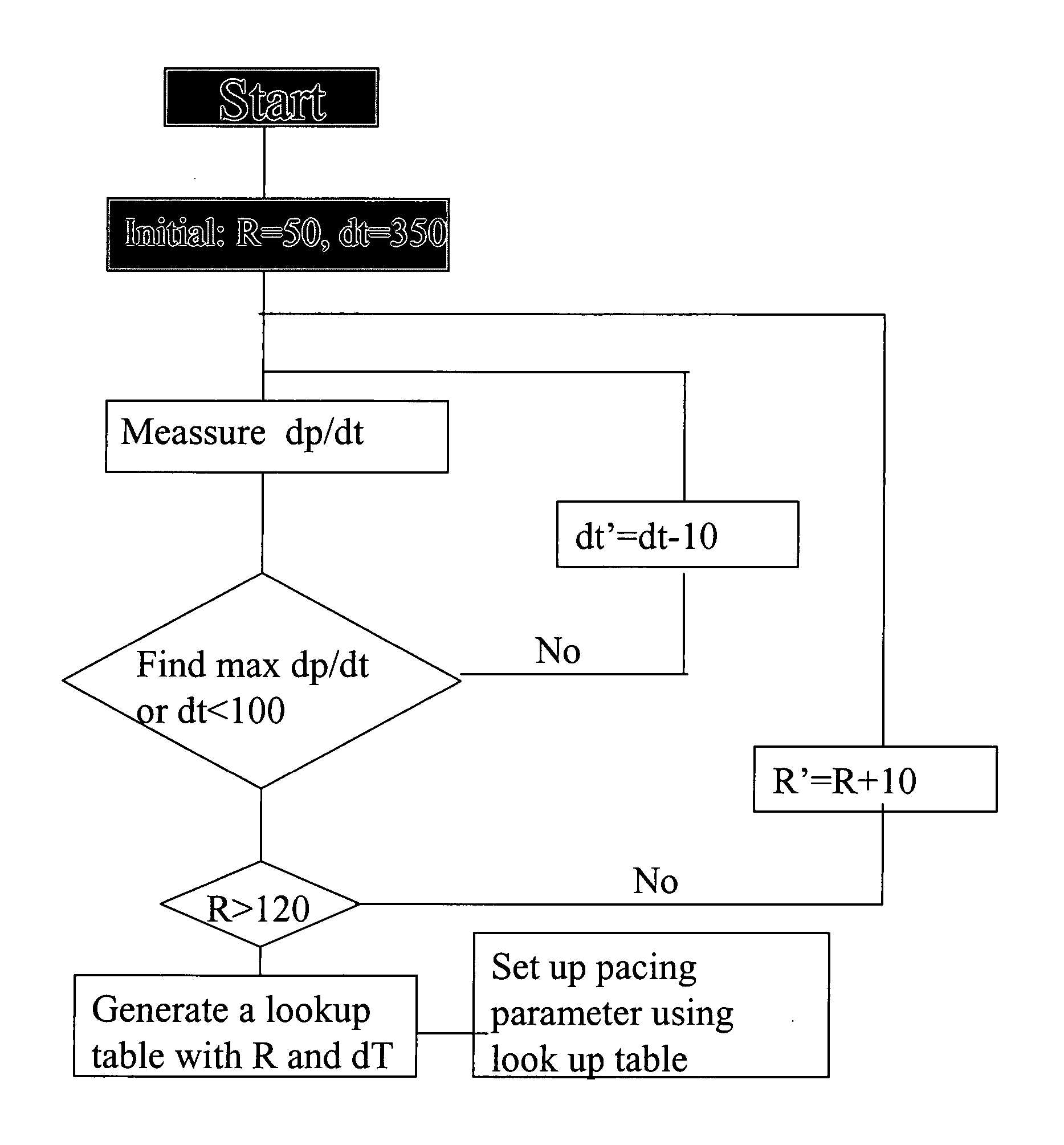
Intracardiac pressure guided pacemaker
InactiveUS20040172081A1Optimize pacing settingFunction increaseHeart stimulatorsCardiac pacemaker electrodePulse rate
The current invention is an intracardiac pressure guided pacemaker. It has a sensor in pacemaker lead to sense intracardiac pressure, which is used to find the best pacing location in the cardiac chamber and to adjust the timing of pacing signal. It will optimize pacing location and pacing timing and, therefore, optimize resychronization of the contraction of myocardium and interaction between different cardiac chambers. This will improve cardiac function at the same working condition without increase in oxygen demand from myocardium. The pacemaker has a computer program, which, based on intracardiac pressure, can adjust pacing parameters of the pacemaker to optimize resynchronization of the myocardium and interaction between different cardiac chambers automatically at different heart rate and in certain time interval specified by care provider. This also can be achieved by using an interrogator manually. The pacemaker can also store profiles of pacing parameter and intracardiac pressure, which can be retrieved for review to help optimize cardiac performance.
Owner:WANG DAI YUAN
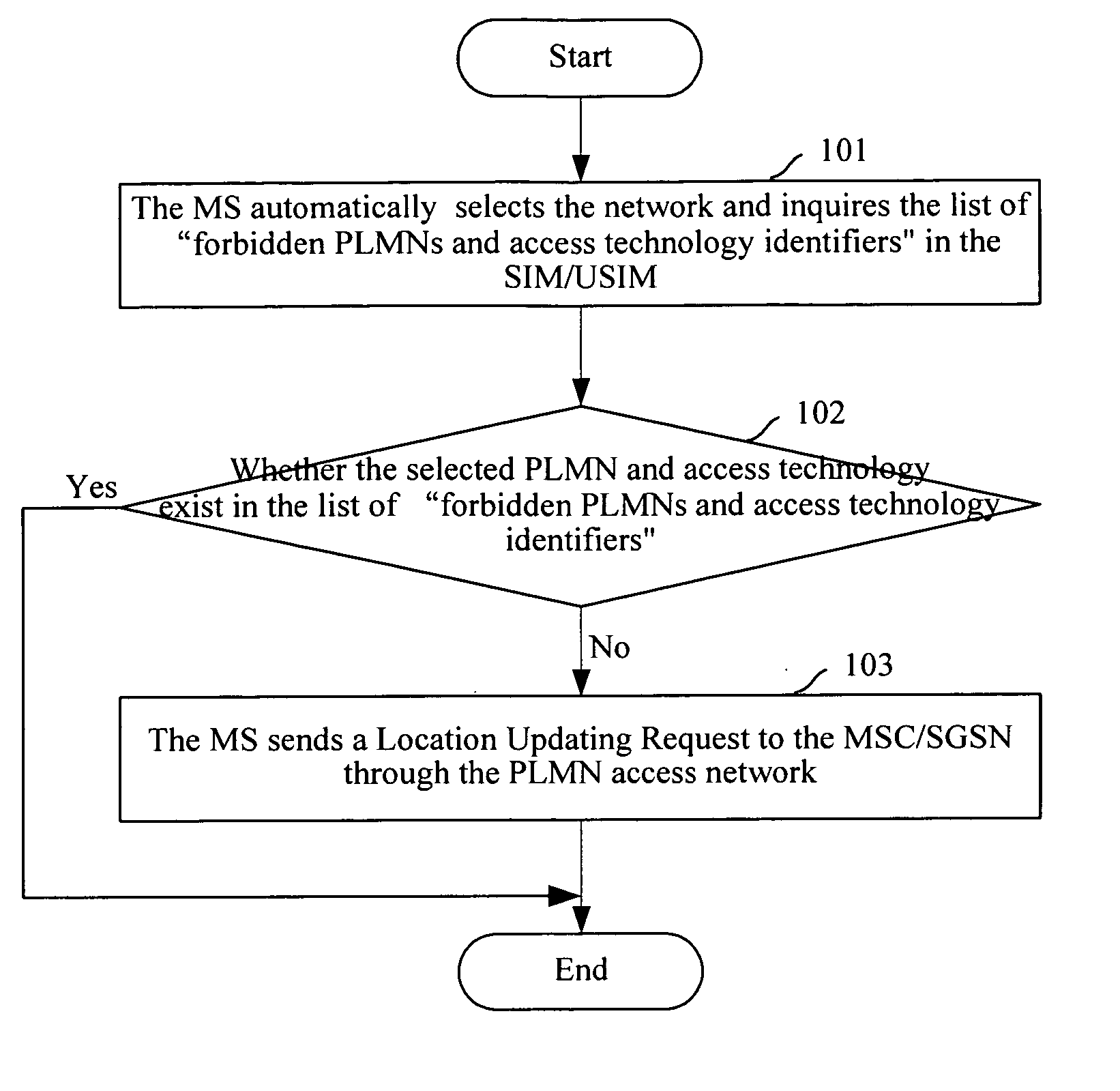
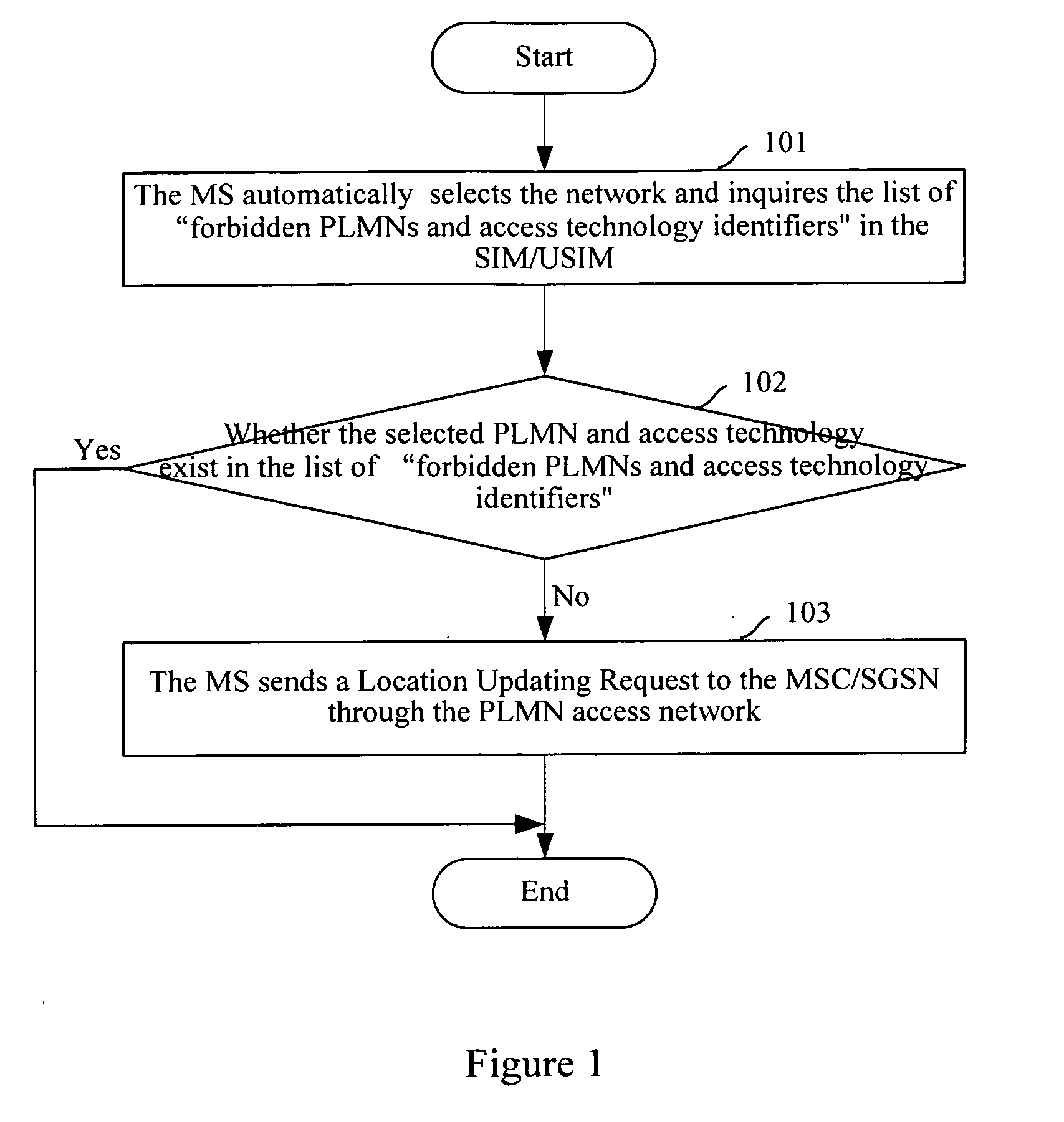
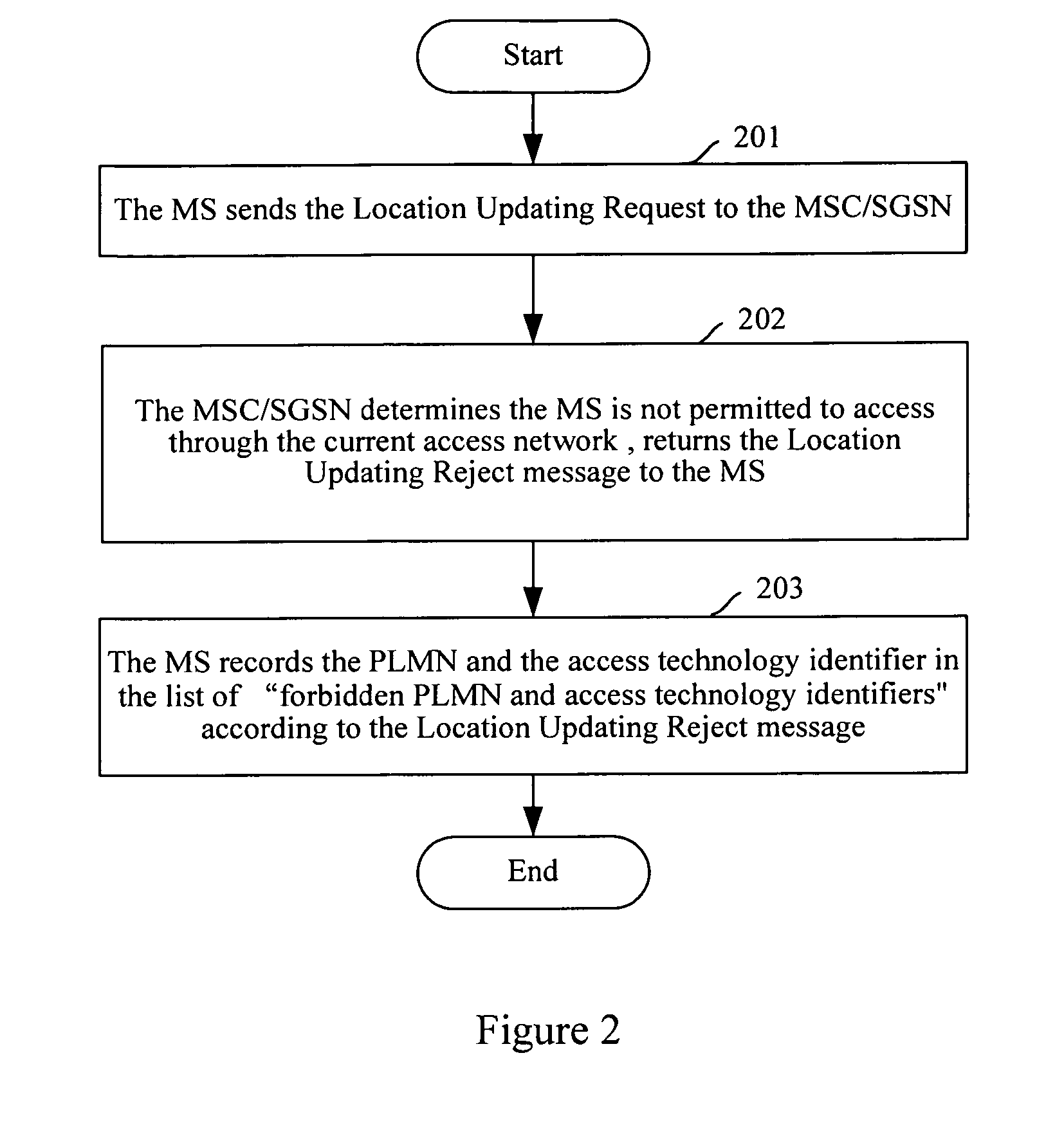
Method for Implementing Access Restriction of Mobile Networks
InactiveUS20070287419A1Easy to implementSatisfies requirementUnauthorised/fraudulent call preventionAssess restrictionAccess networkPublic land mobile network
The present invention discloses a method for implementing access restriction of mobile networks. The method includes the following steps: a Mobile Station (MS) inquiring a list of forbidden Public Land Mobile Networks (PLMNs) and access technology identifiers, which is saved by itself, when selecting a PLMN network; the MS determining whether the selected PLMN network and the access technology exist in the list of forbidden PLMNs and access technology identifiers, if they exist, the MS will not send a Location Updating Request to a Mobile Switching Center / Serving GPRS Support Node (MSC / SGSN); otherwise, the MS will send the Location Updating Request to the MSC / SGSN in order to access to the network. The present invention makes it possible to implement the access restrictions upon different types of access networks using different restriction rules. Furthermore, during the process of implementing the access restriction, the modification to the existing networks and user terminals is very small, the method is easy to implement and can well satisfy demands on the access restriction of operators.
Owner:HUAWEI TECH CO LTD
Automatic bright band detection and compensation
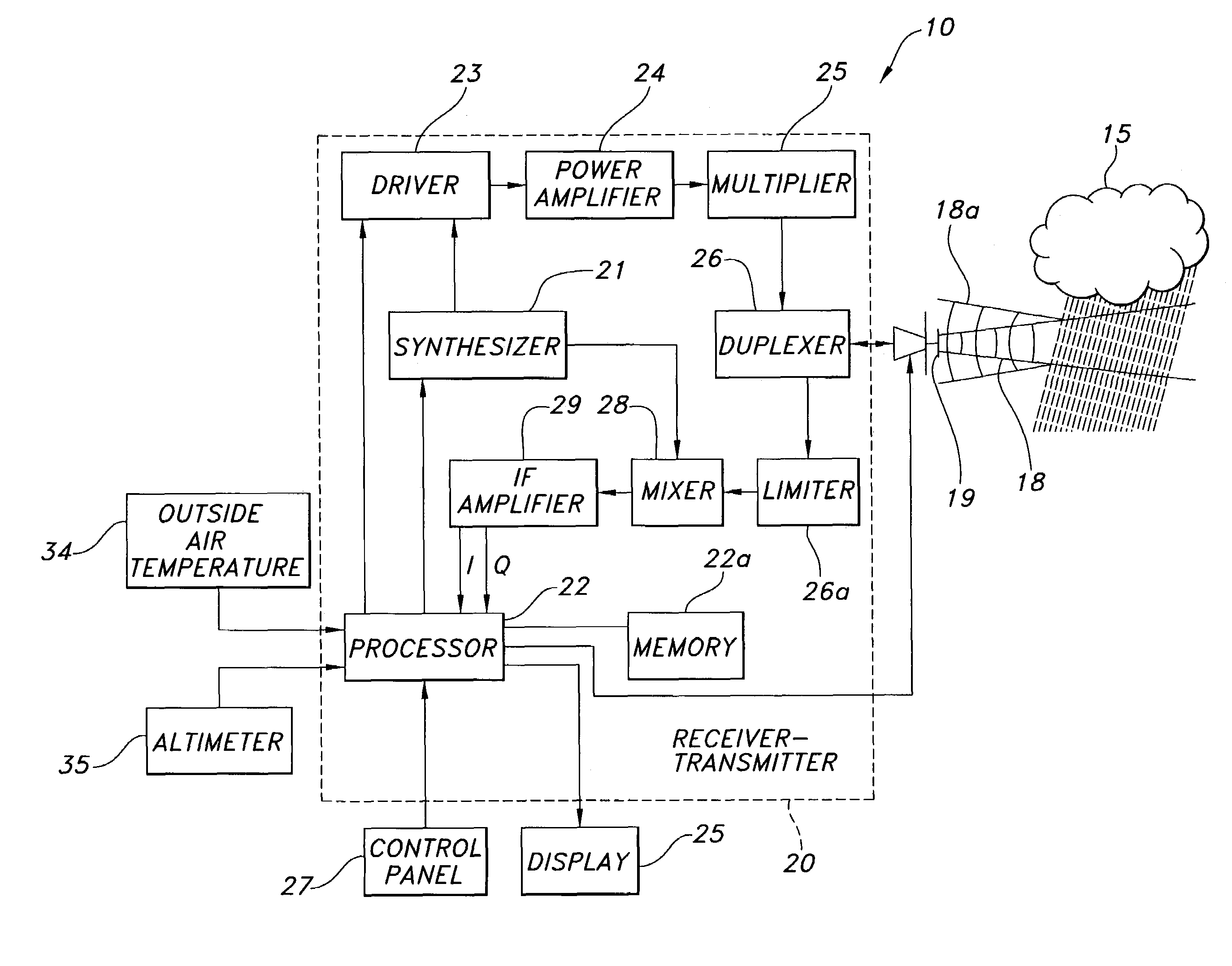
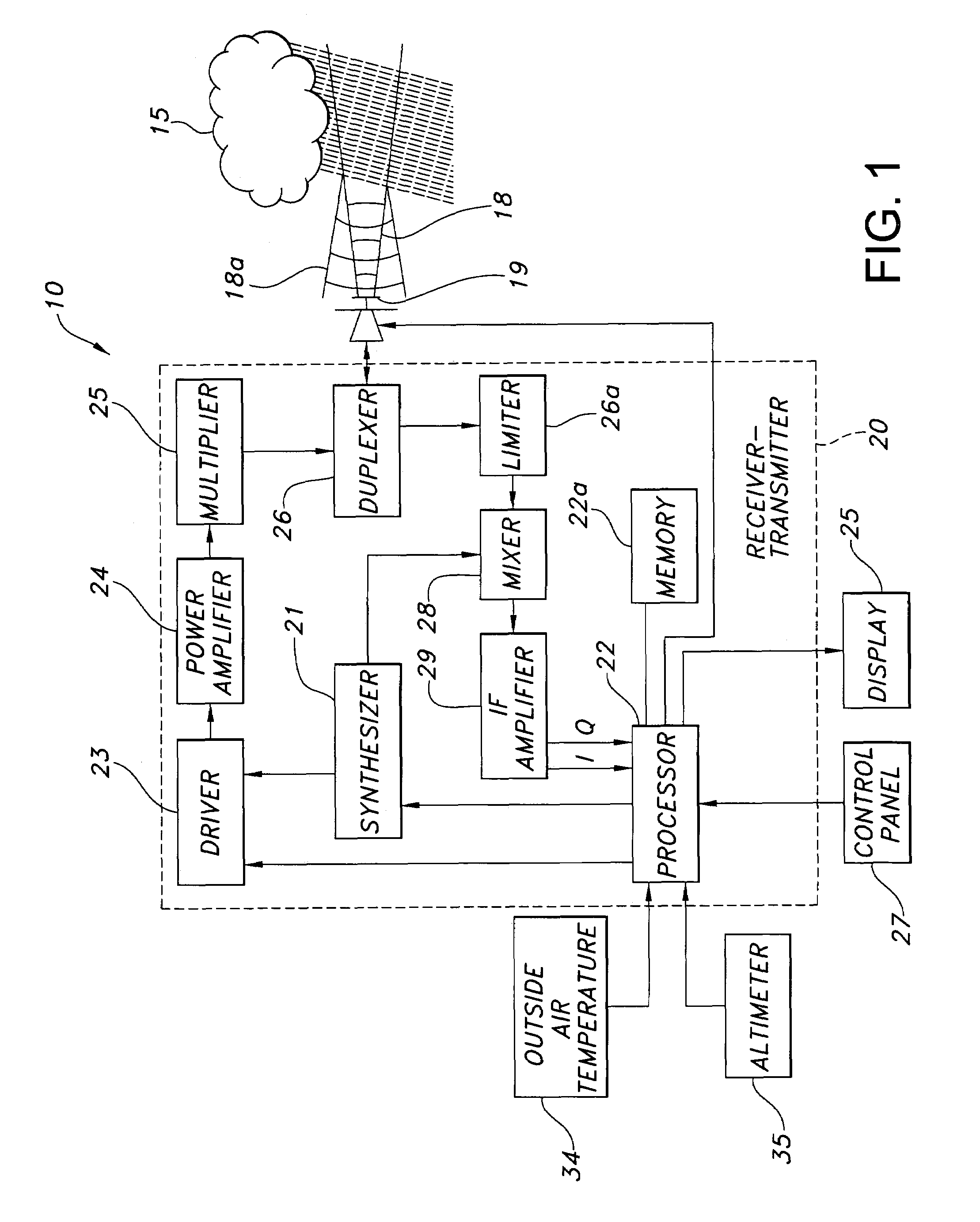
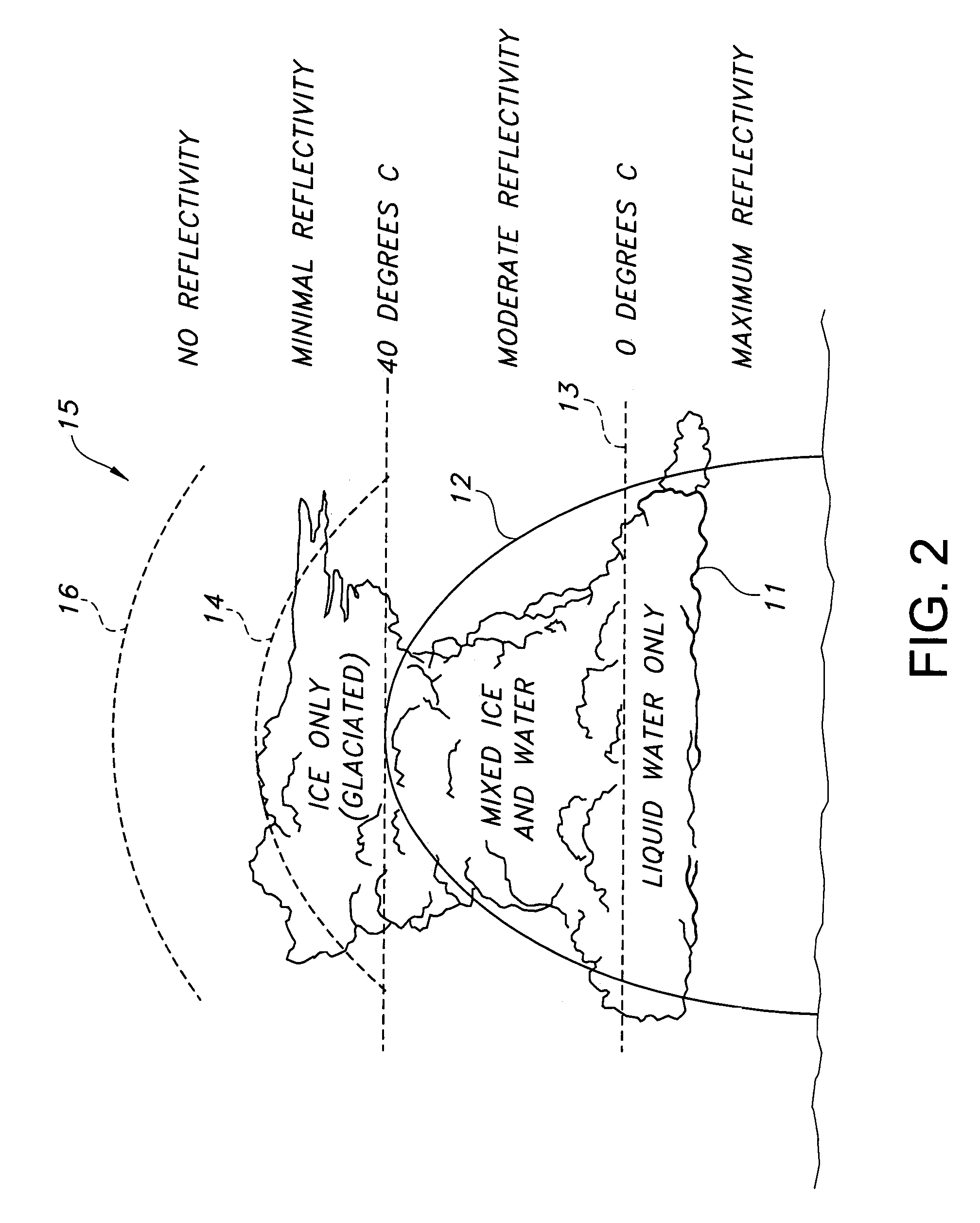
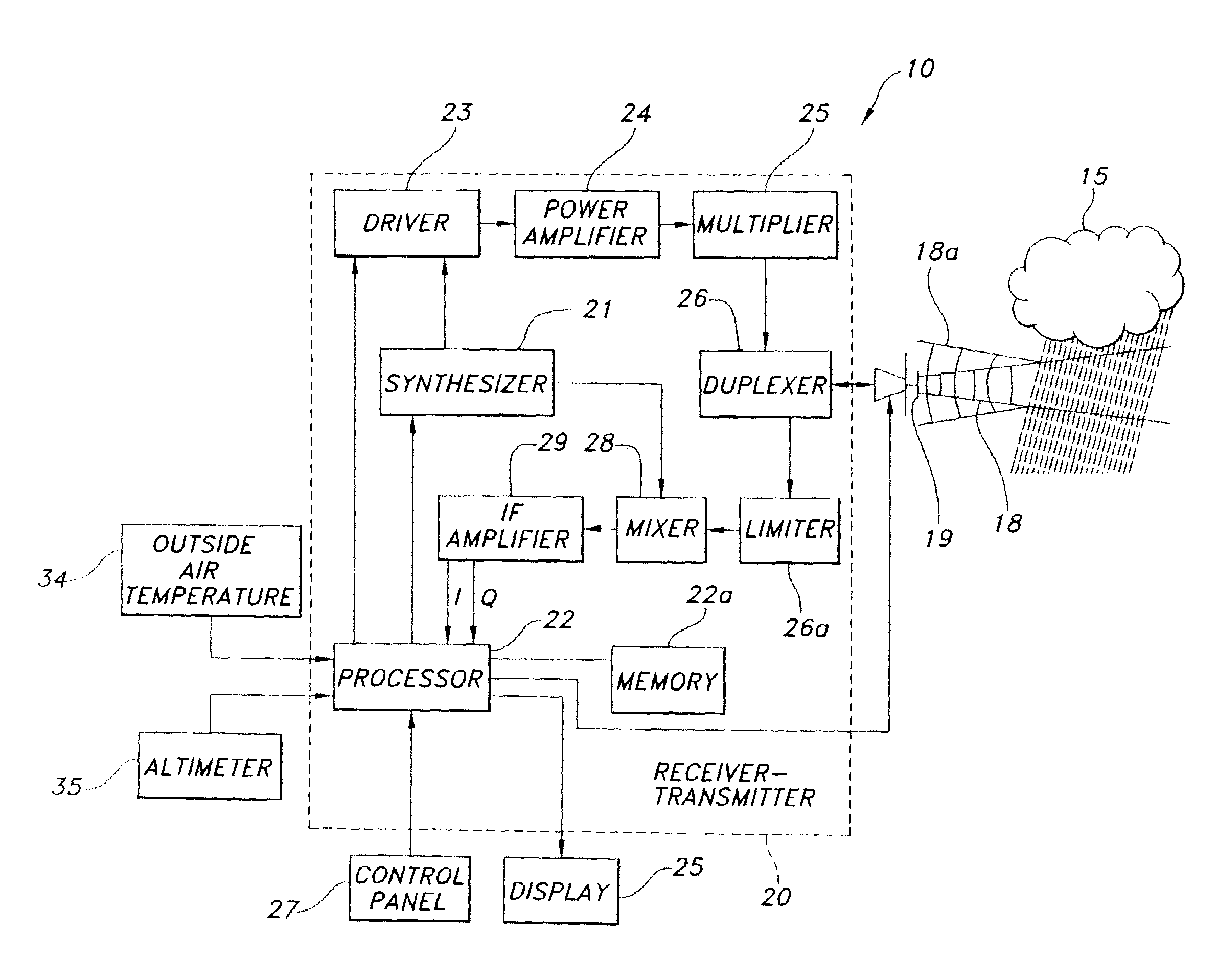
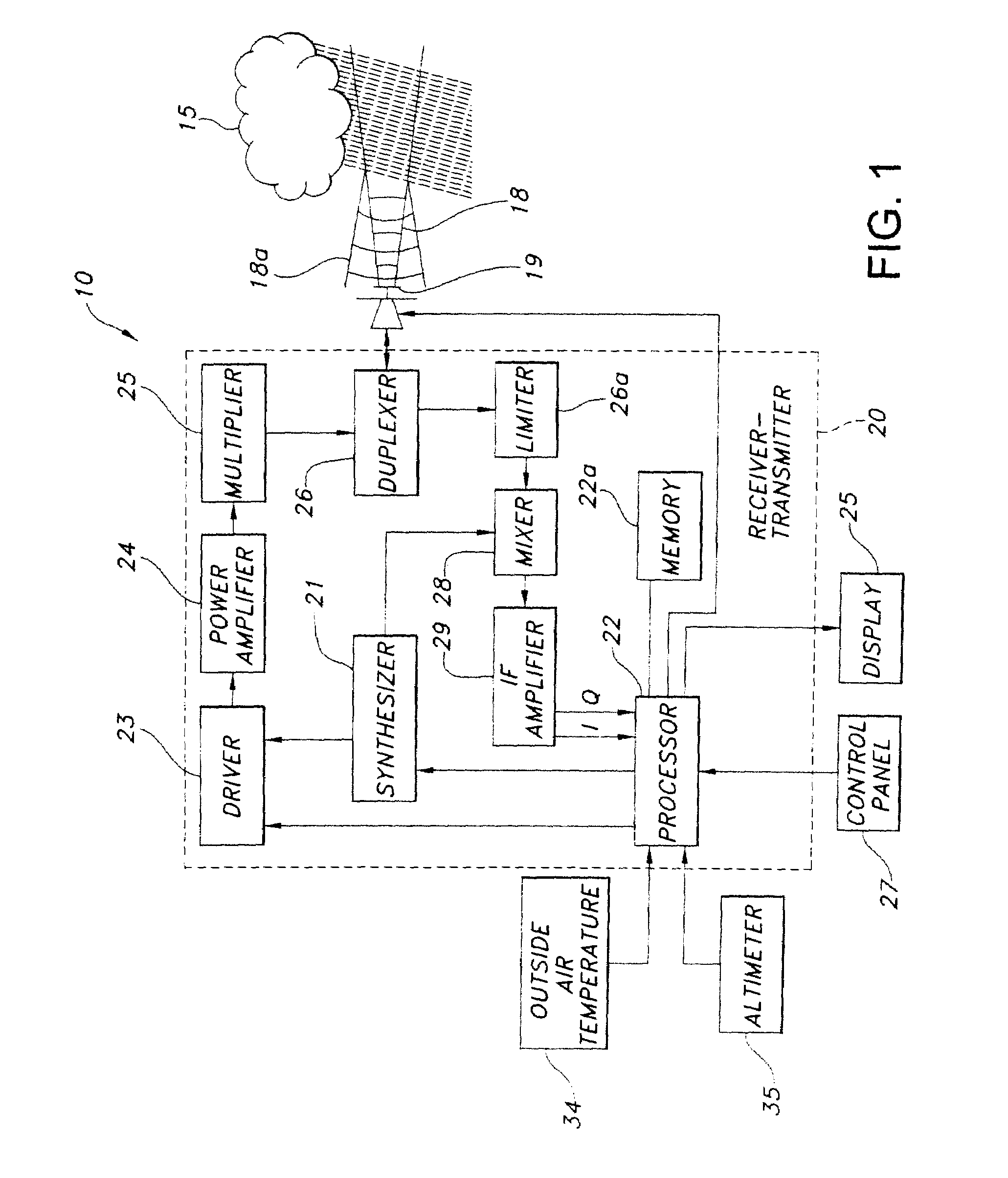
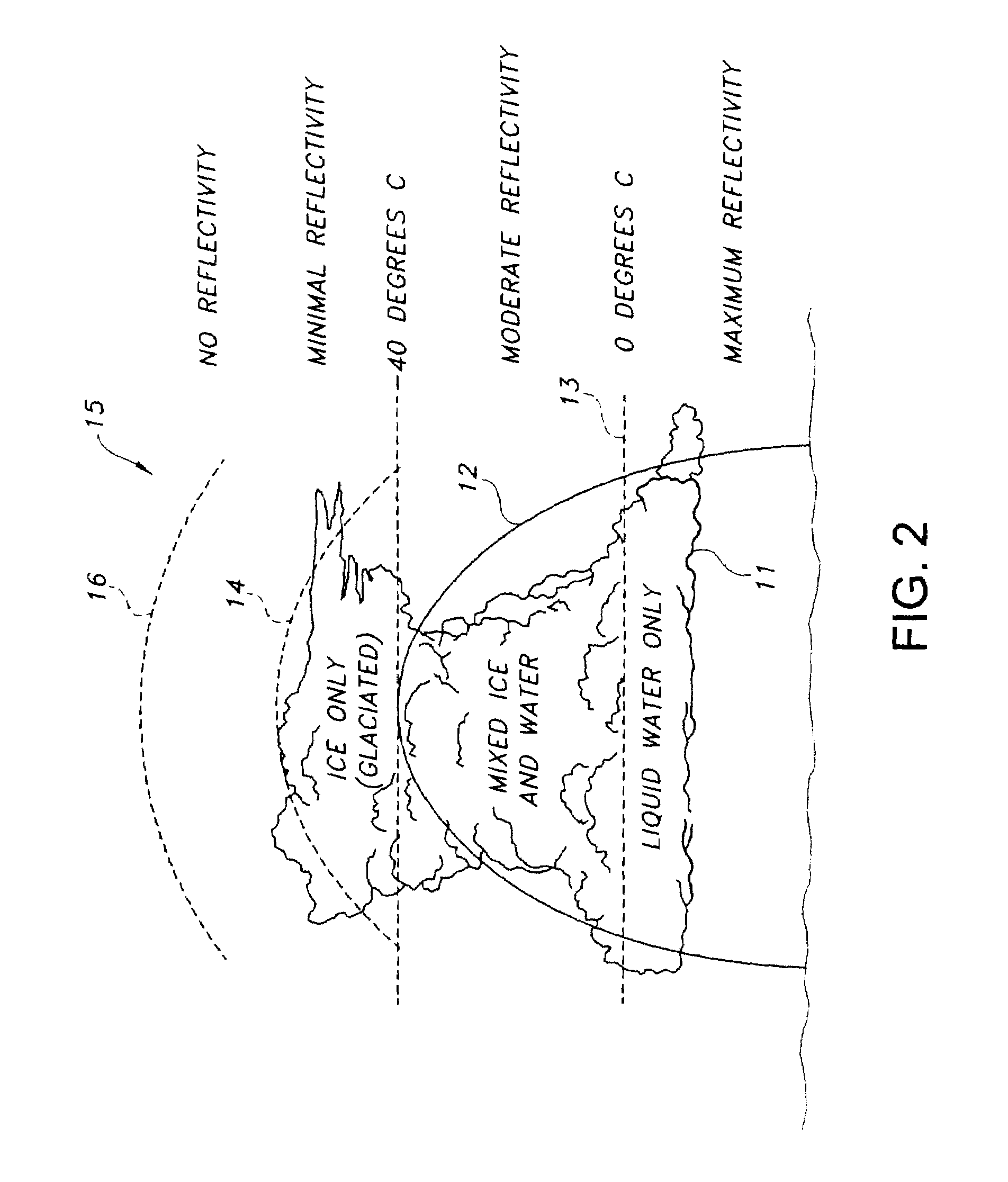
ActiveUS7492304B1Small modificationRadio wave reradiation/reflectionICT adaptationWave bandHigh reflectivity
A weather radar system has bright band detection and compensation. The weather radar system determines that high reflectivity in weather is a bright band and reduces an encoded return level from the bright band to compensate for it on a display. The weather radar system detects the presence of the bright band using an inference system that uses outside air temperature, aircraft altitude, and an assumed lapse rate to estimate the bright band location relative to the aircraft and uses antenna elevation to estimate bright band range to reduce the encoded radar return level on the display. The weather radar system may also detect the presence of the bright band using a detection system that uses radar estimates from normal reflectivity scan operation of the system. The weather radar system may also use an active detection process separate from a normal radar sampling process to detect the bright band.
Owner:ROCKWELL COLLINS INC
Method of fabricating Schottky diode and related structure
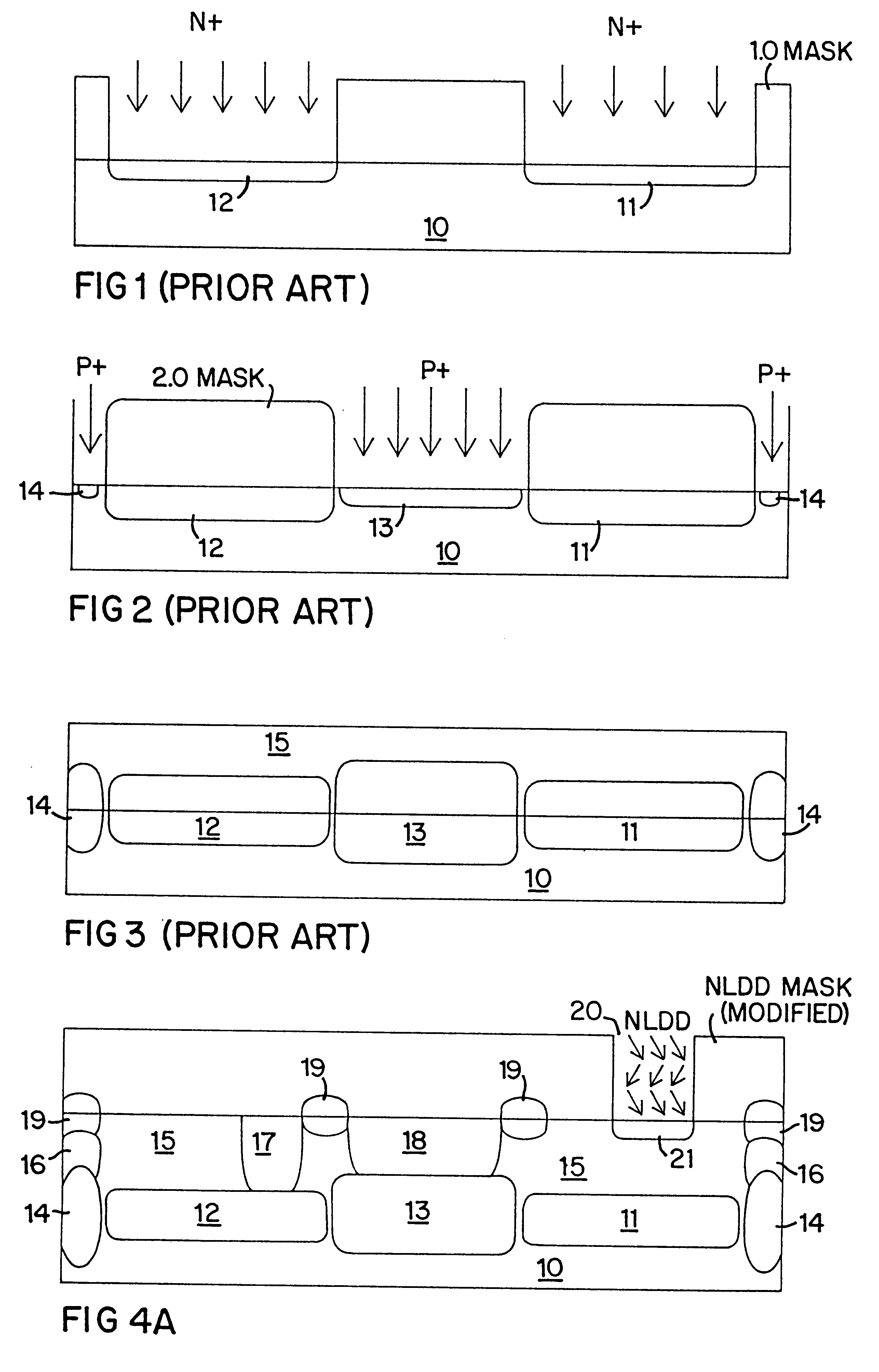
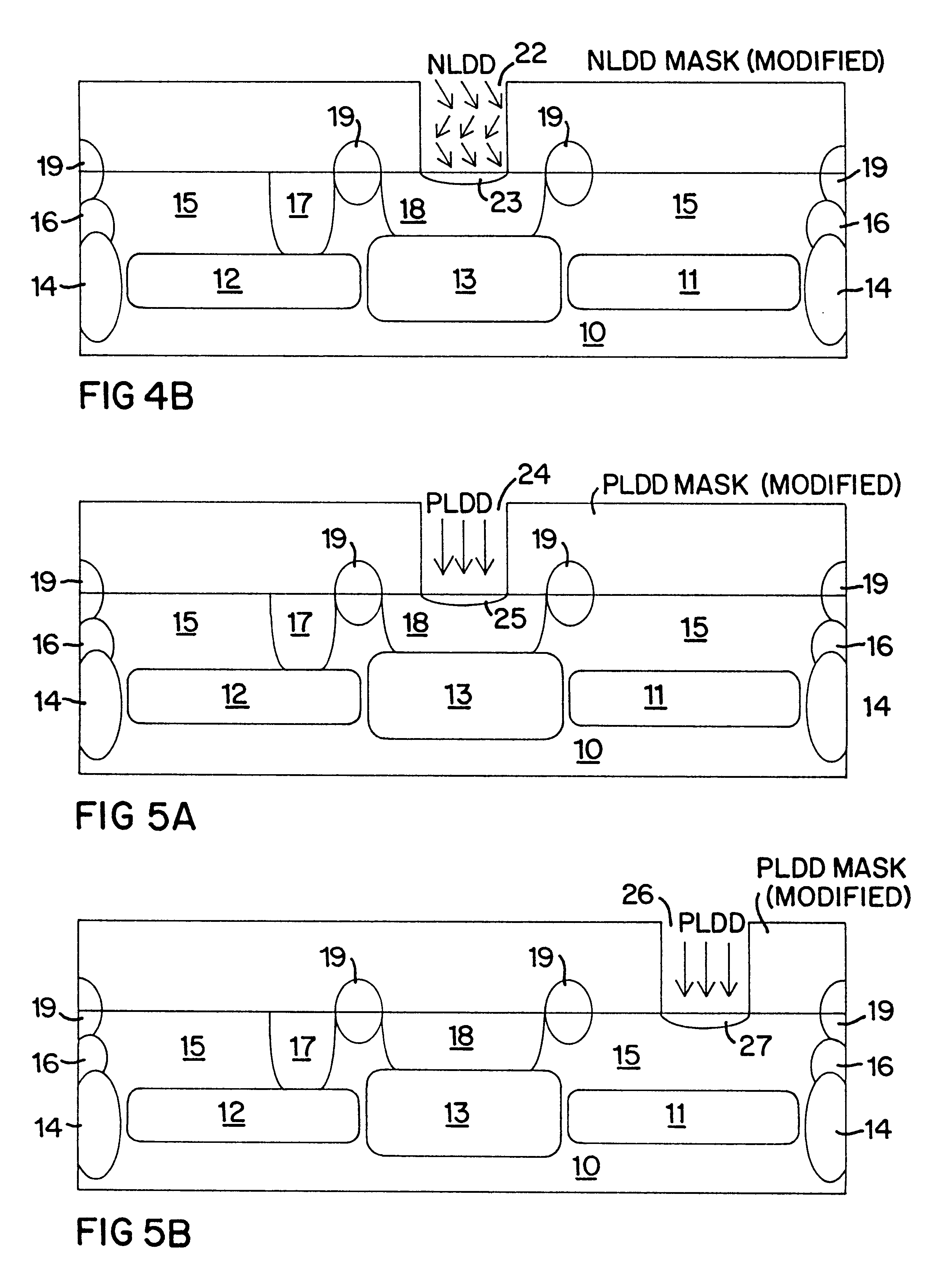
InactiveUS6261932B1Easy to optimizeReduce parasitic capacitanceTransistorSolid-state devicesDopantMetal silicide
A method of forming an improved Schottky diode structure as part of an integrated circuit fabrication process that includes the introduction of a selectable concentration of dopant into the surface of an epitaxial layer so as to form a barrier-modifying surface dopant layer. The epitaxial layer forms the cathode of the Schottky diode and a metal-silicide layer on the surface of the epitaxial layer forms the diode junction. The surface dopant layer positioned between the cathode and the diode junction is designed to raise or lower the barrier height between those two regions either to reduce the threshold turn-on potential of the diode, or to reduce the reverse leakage current of the transistor. The particular dopant conductivity used to form the surface dopant layer is dependent upon the conductivity of the epitaxial layer and the type of metal used to form the metal-silicide junction.
Owner:SEMICON COMPONENTS IND LLC
Automatic bright band detection and compensation
ActiveUS7541971B1Small modificationRadio wave reradiation/reflectionICT adaptationFailure rateRadar systems
A weather radar system has bright band detection and compensation. The weather radar system determines that high reflectivity in weather is a bright band and reduces an encoded return level from the bright band to compensate for it on a display. The weather radar system detects the presence of the bright band using an inference system that uses outside air temperature, aircraft altitude, and an assumed lapse rate to estimate the bright band location relative to the aircraft and uses antenna elevation to estimate bright band range to reduce the encoded radar return level on the display. The weather radar system may also detect the presence of the bright band using a detection system that uses radar estimates from normal reflectivity scan operation of the system. The weather radar system may also use an active detection process separate from a normal radar sampling process to detect the bright band.
Owner:ROCKWELL COLLINS INC
Memory domain based security control with data processing systems
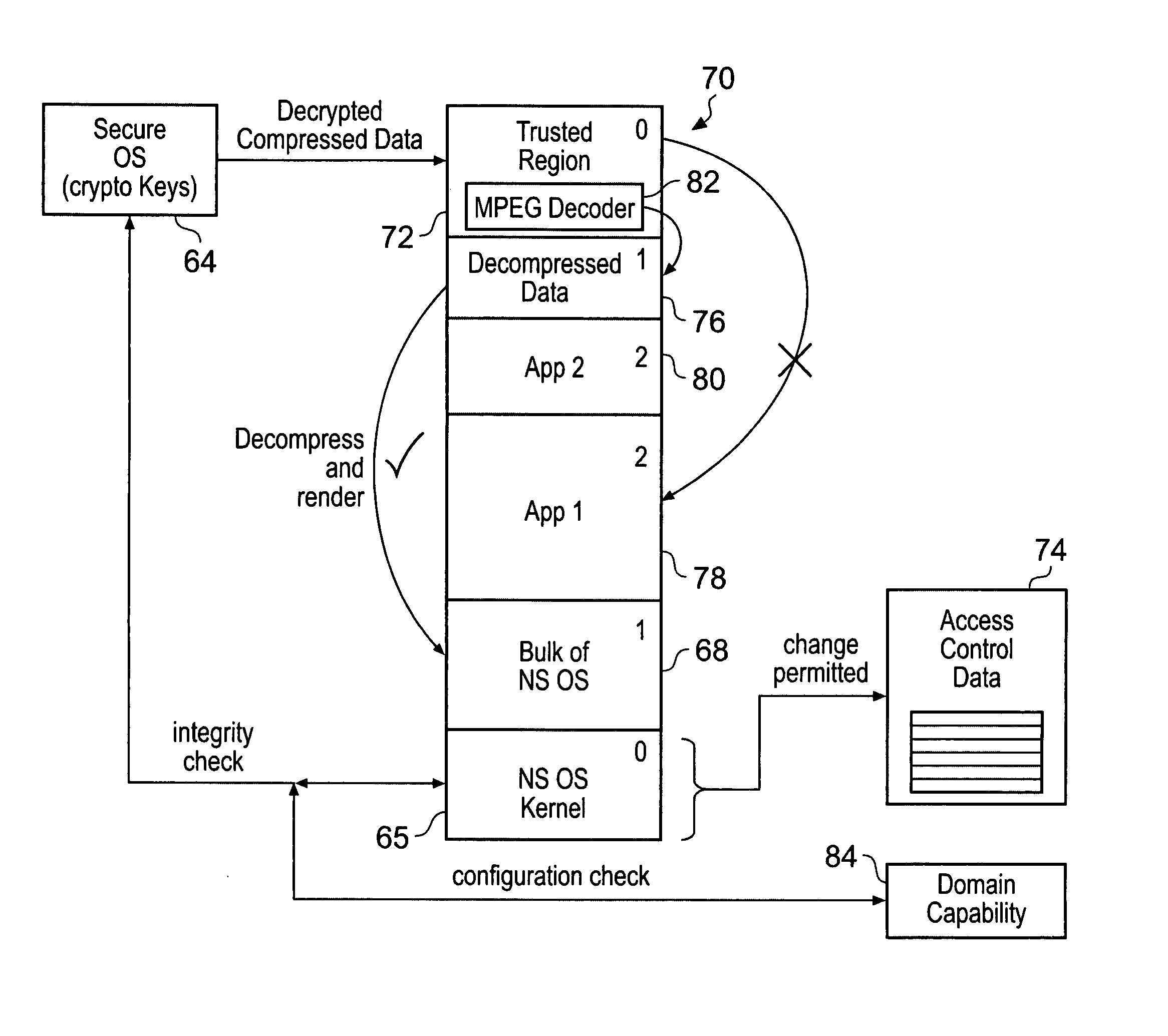
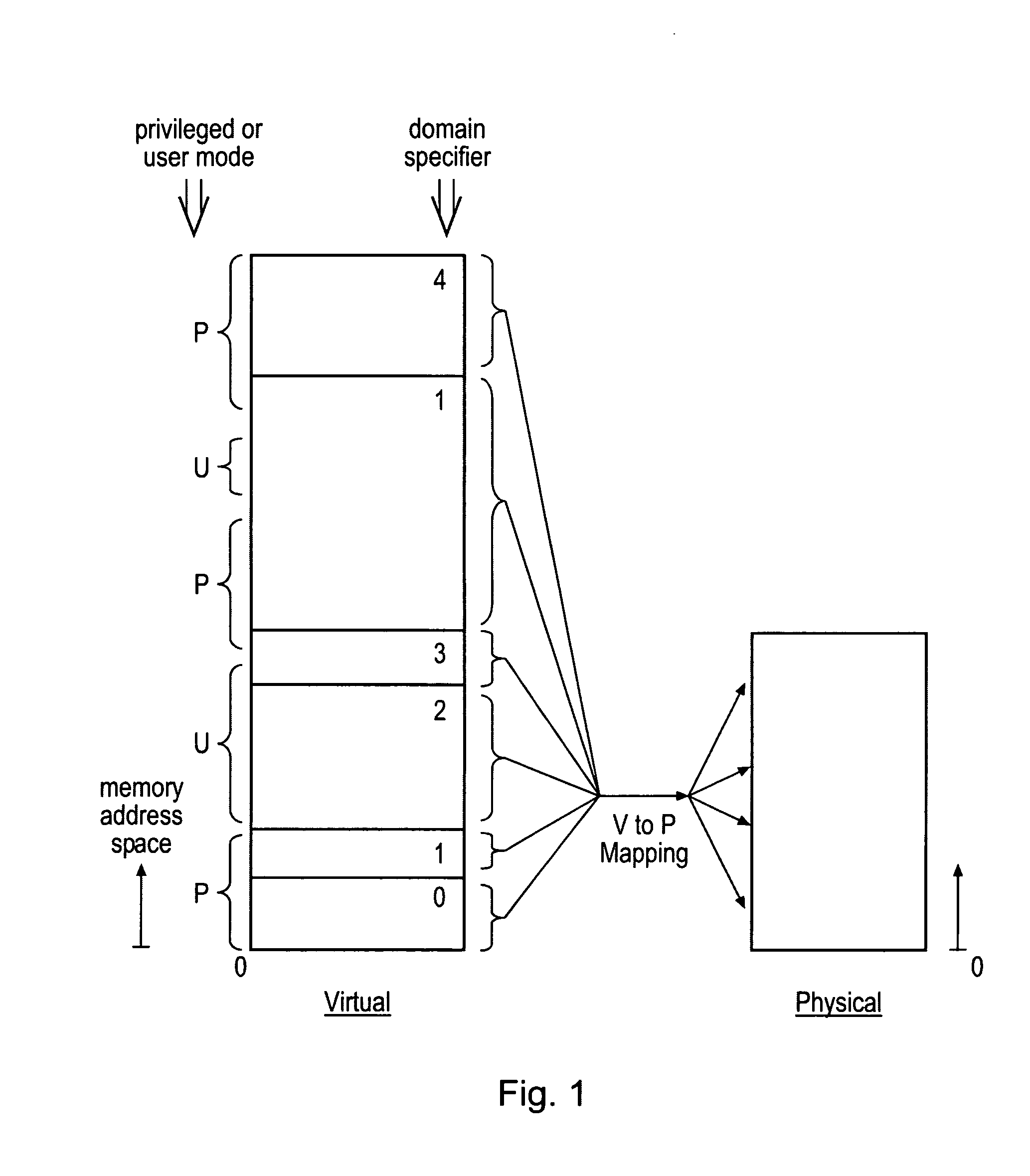
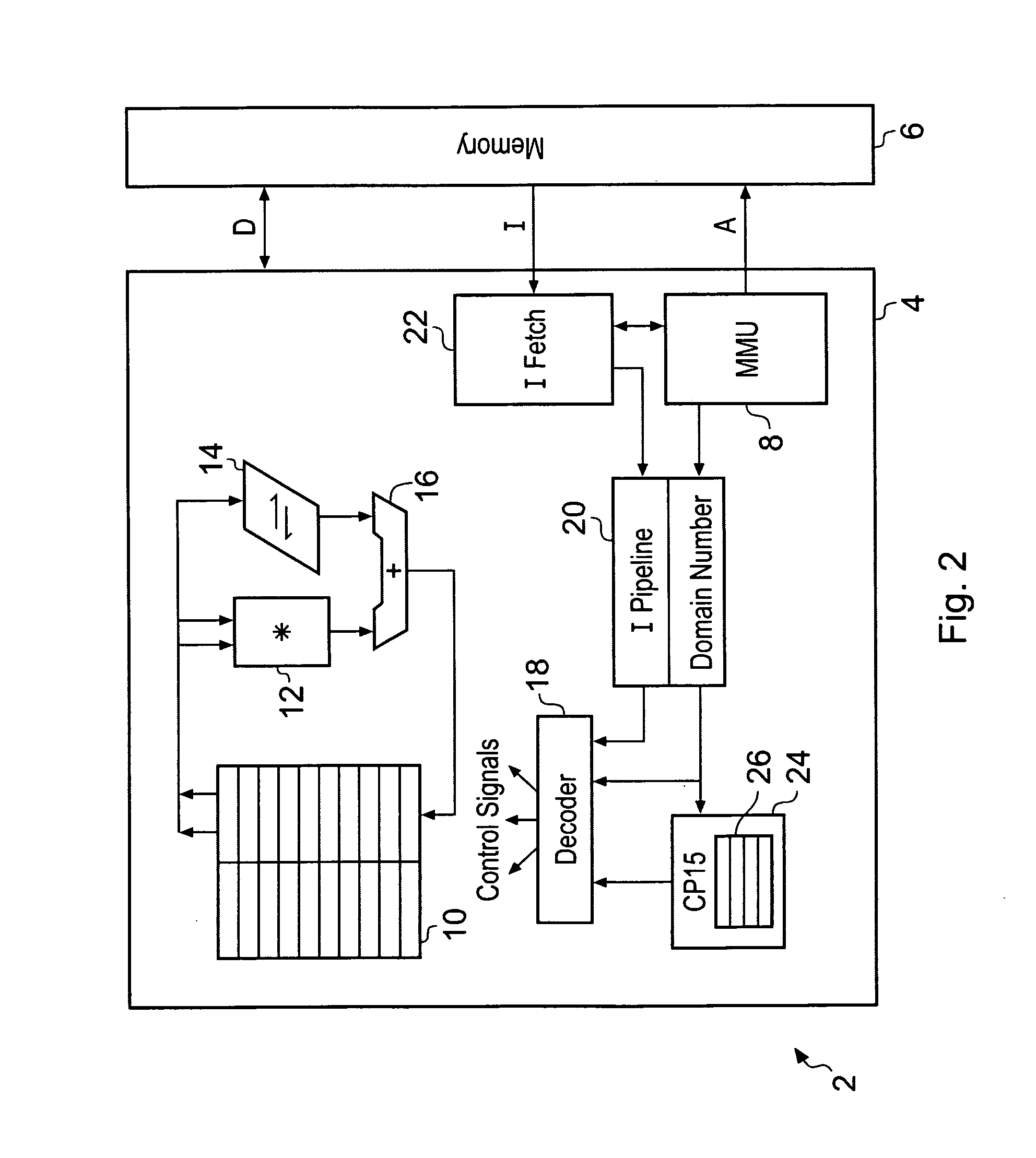
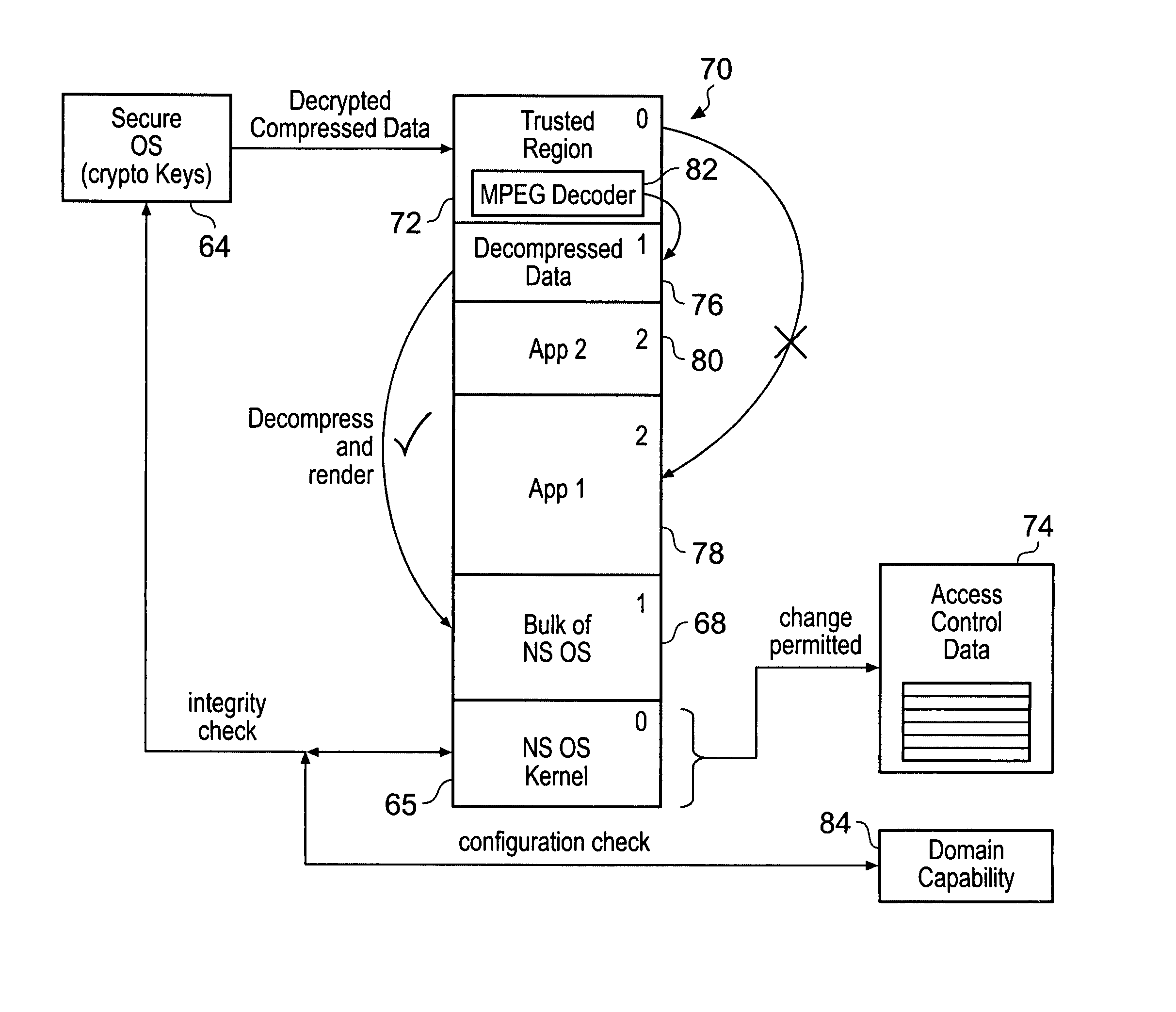
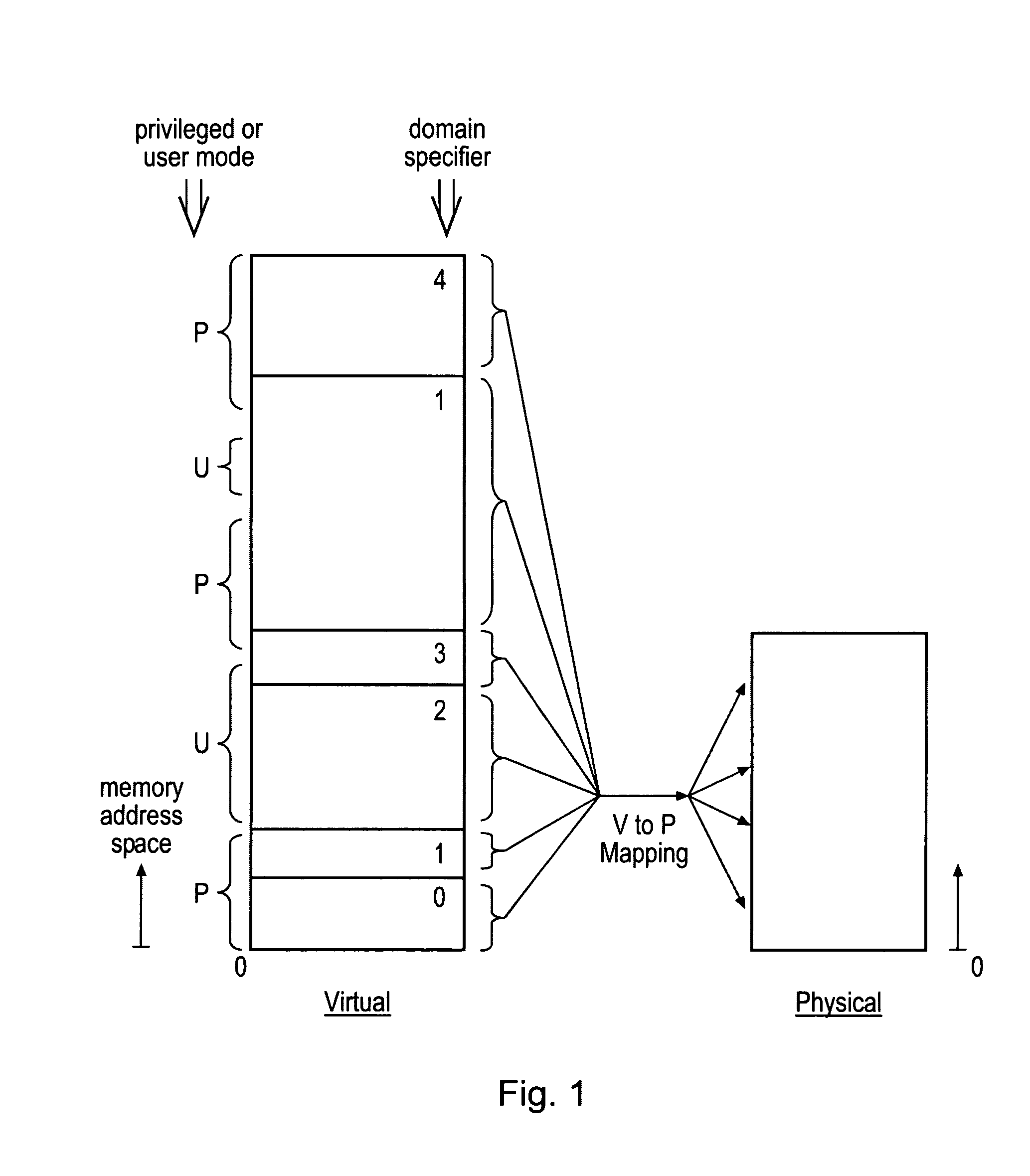
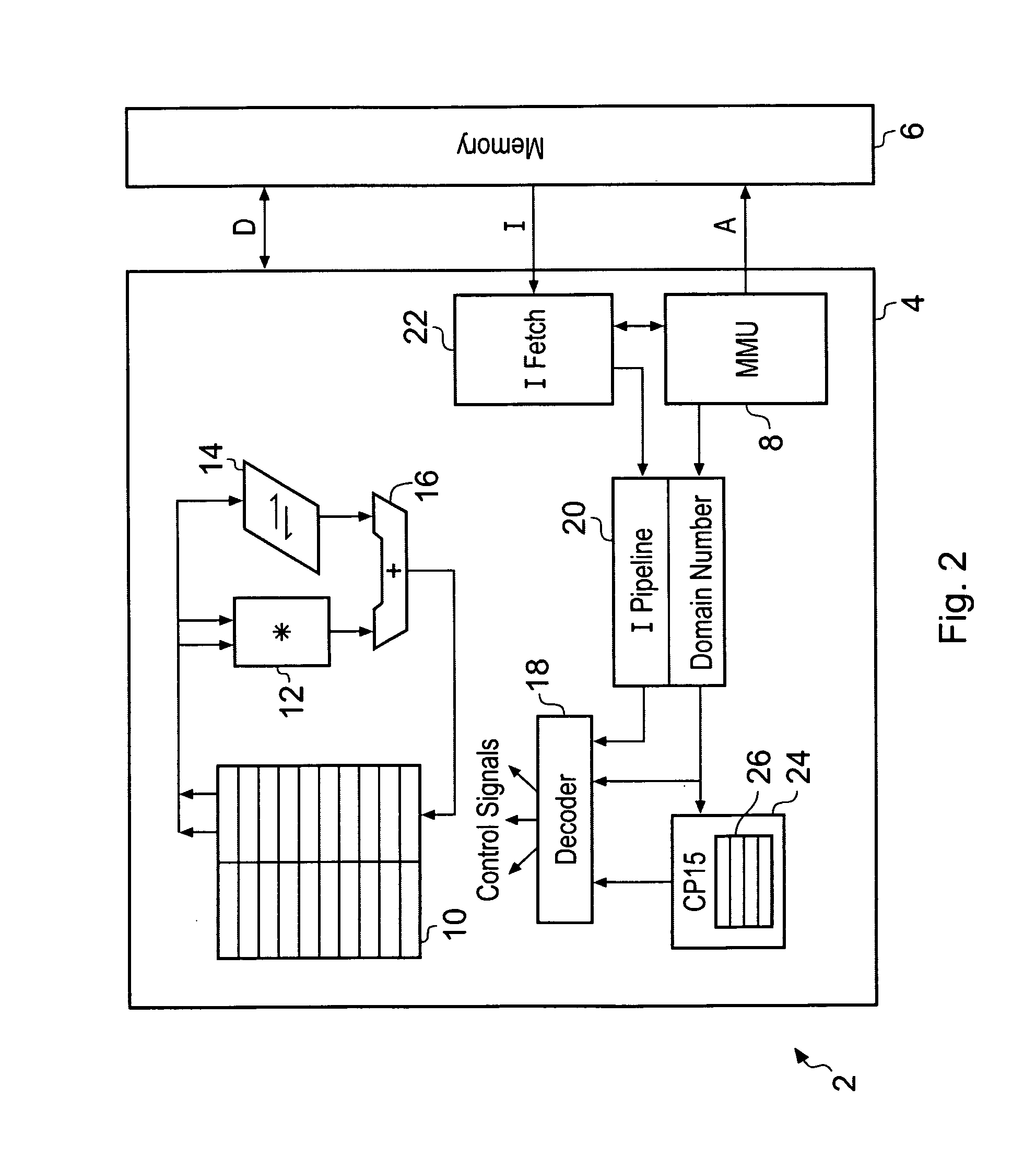
ActiveUS20080250217A1Improve securityLimited abilityDigital computer detailsUnauthorized memory use protectionMemory addressOperational system
Access to memory address space is controlled by memory access control circuitry using access control data. The ability to change the access control data is controlled by domain control circuitry. Whether or not an instruction stored within a particular domain, being a set of memory addresses, is able to modify the access control data is dependent upon the domain concerned. Thus, the ability to change access control data can be restricted to instructions stored within particular defined locations within the memory address space thereby enhancing security. This capability allows systems to be provided in which call forwarding to an operating system can be enforced via call forwarding code and where trusted regions of the memory address space can be established into which a secure operating system may write data with increased confidence that that data will only be accessible by trusted software executing under control of a non-secure operating system.
Owner:ARM LTD
Network and method of realizing local roaming for subscribers
InactiveUS20060089140A1Low costLow resource occupationRadio/inductive link selection arrangementsWireless commuication servicesRoamingMobile Web
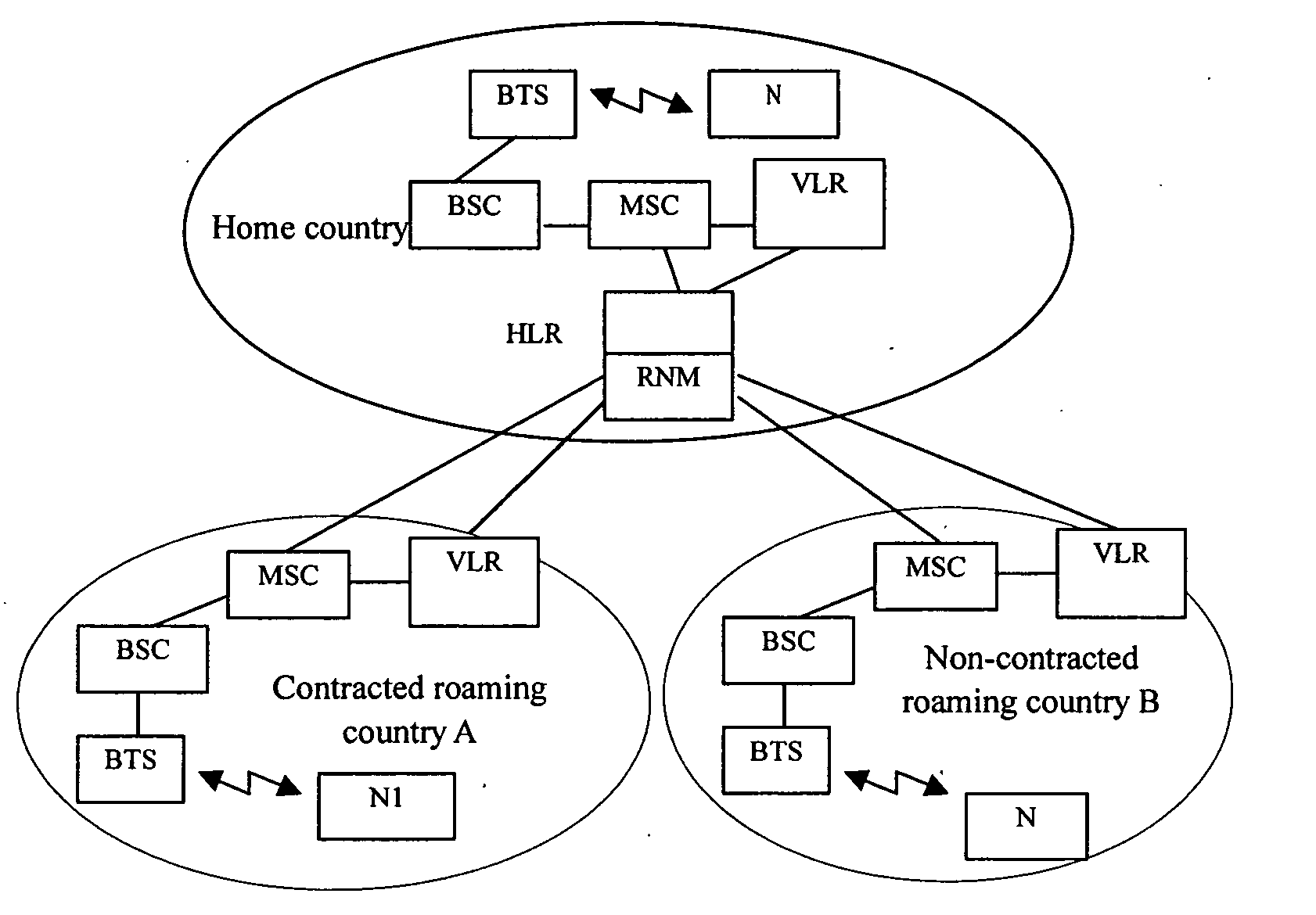
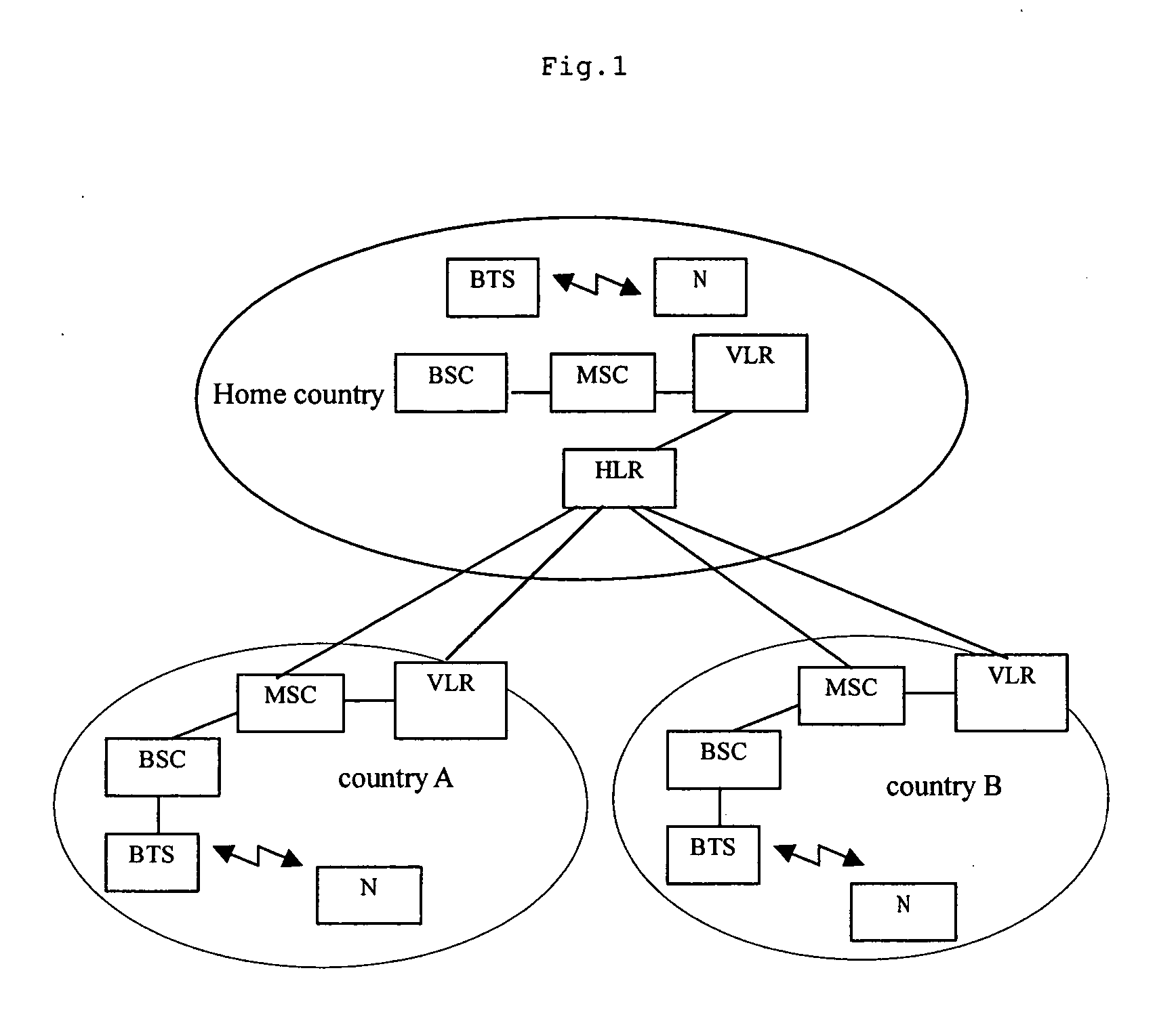
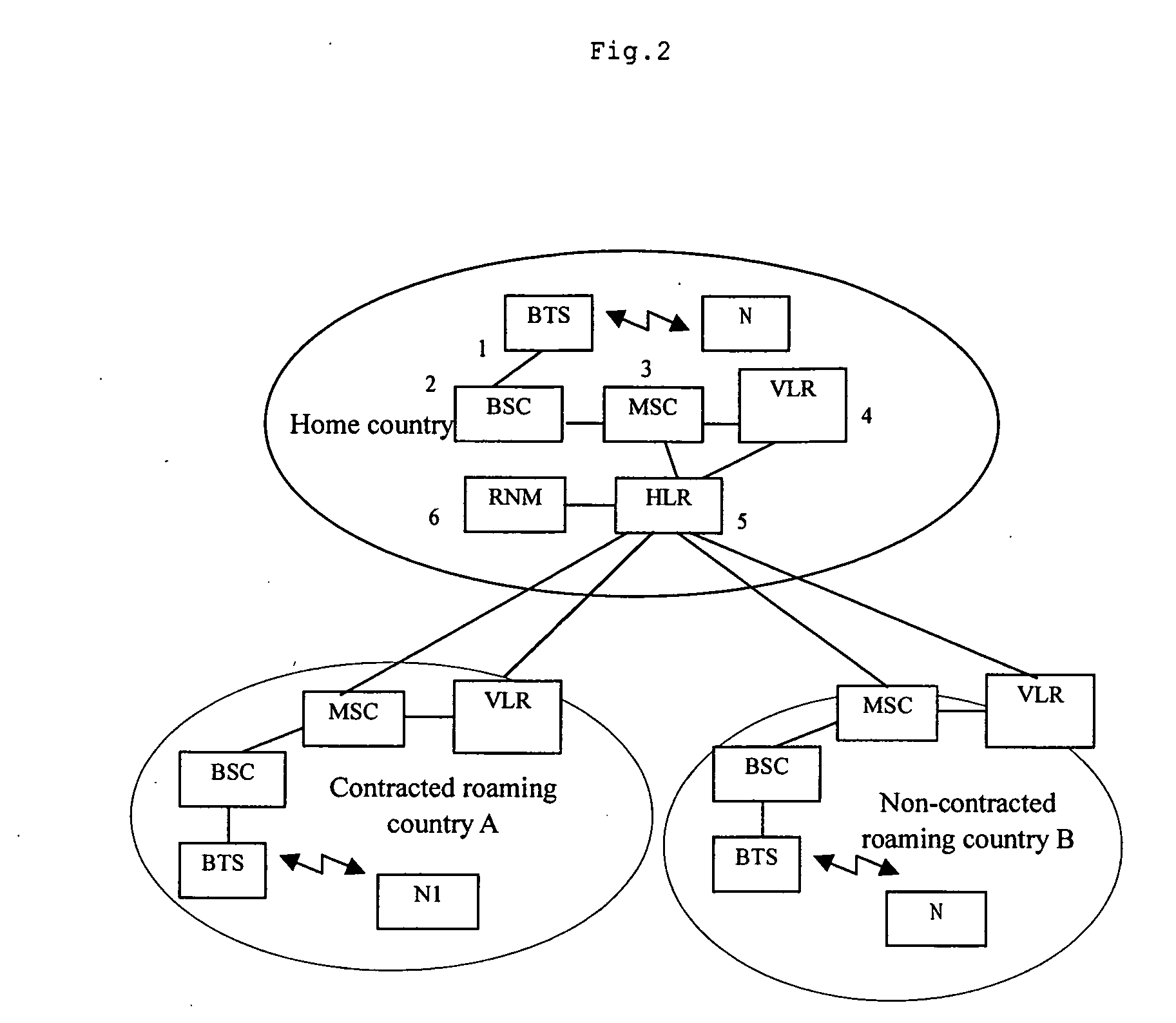
The present invention provides a network and a method for implementing localized roaming of mobile subscribers; said network comprises BTS, BSC, VLR, HLR, and RNM that is connected to HLR; said RNM is used to manage mobile phone numbers in the home region and the contracted roaming region and allocate the numbers in the contracted roaming region to roaming subscribers dynamically to implement localized roaming; said method comprises: configure the numbers in the contracted roaming region, the numbers in the independent PSTN / ISDN, and the code of the SP for the RNM; configure data in the network entities in the contracted roaming region / network and the home network; establish the interface between the RNM and the contracted roaming region / network as well as between the RNM and the home network; the subscribers utilizes above configuration to implement localized roaming. With above method and network, localized roaming of mobile subscribers can be implemented, and the communication costs of subscribers in roaming state can be reduced greatly; furthermore, the solution in the present invention requires little modification to the traditional mobile networks and is featured with low cost and easy implementation.
Owner:HUAWEI TECH CO LTD
User input arrangement and related method of manufacture
InactiveUS20120038593A1Rapid industrial scale manufacturingEasy to replaceTube/lamp screens manufactureLight effect designsTotal internal reflectionUser input
Arrangement (202) for a user input device, such as a touchscreen or a touchpad, comprising a substrate (206), such as an optically substantially transparent flex film or a multilayer film, said substrate comprising support electronics (212) for providing power, control and / or communications connection to further electronic components (210), a number of emitters and detectors (210) arranged to said substrate into contact with the support electronics, for emitting and detecting light, respectively, and a lightguide (208) provided, such as laminated, onto the substrate such that said emitters and detectors are optically coupled to the lightguide material, the properties of the lightguide including the refractive index of the lightguide material being selected and the emitters and detectors being configured so as to enable, when in use, total internal reflection (TIR) -type propagation of light within the lightguide between the emitters and detectors, and recognition of a touch on the basis of a drop in the TIR performance as determined from the detected light. A related method of manufacture is presented.
Owner:TEKNOLOGIAN TUTKIMUSKESKUS VTT
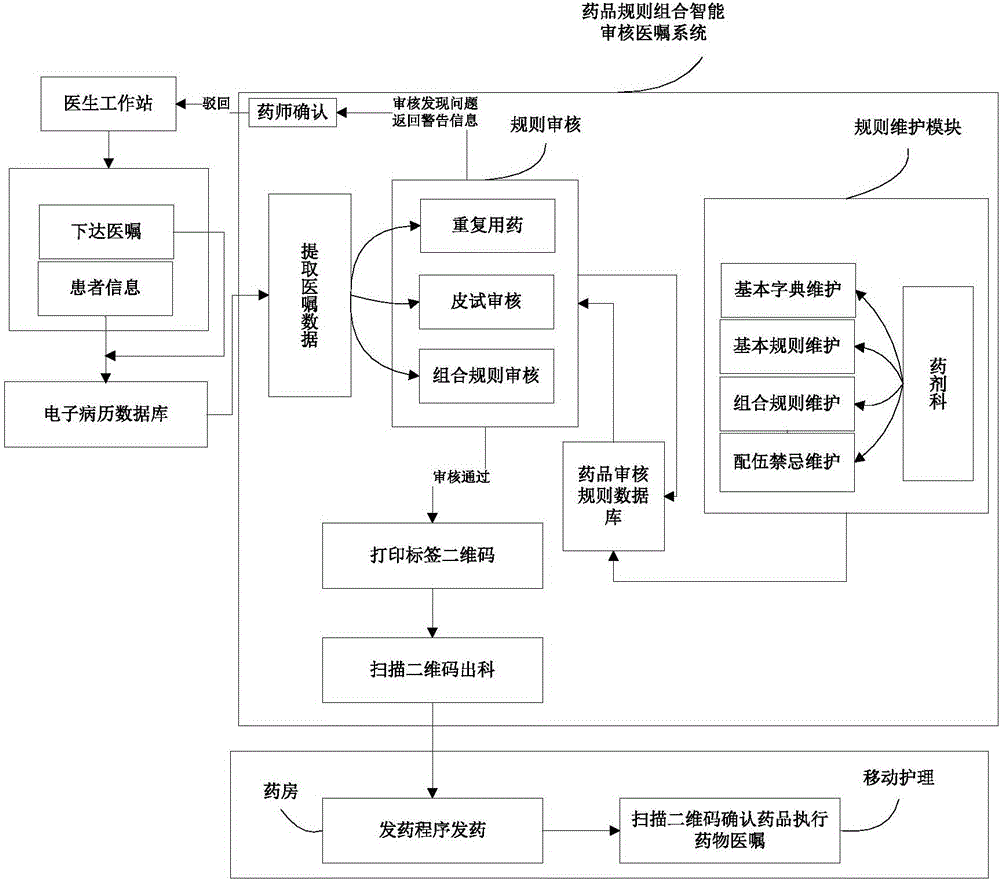
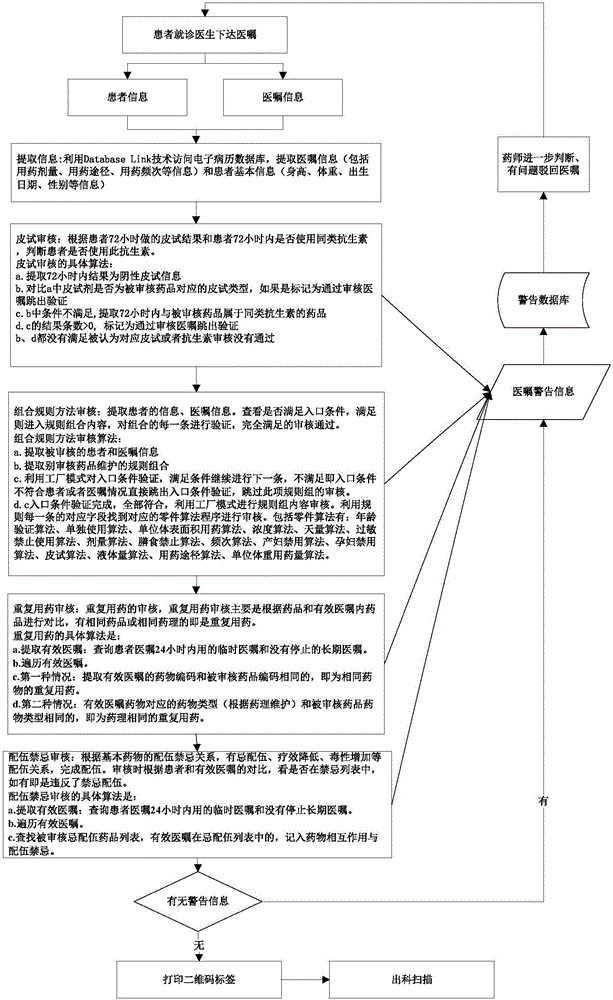
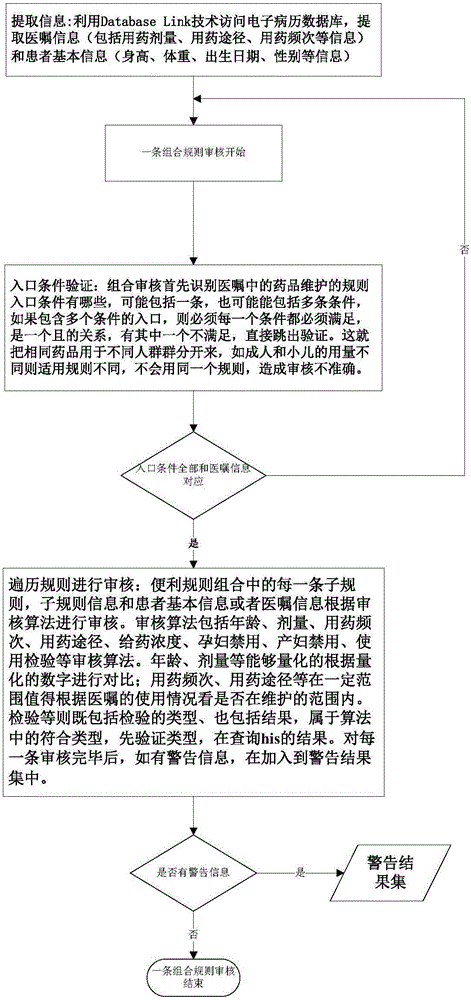
Doctor advice intelligent auditing system and method based on drug rule combination
InactiveCN106503455AResolve accuracyIncrease authenticity of useComputer-assisted medicine prescription/deliverySpecial data processing applicationsMedical recordDrug product
The invention discloses a doctor advice intelligent auditing system and method based on drug rule combination. The system comprises doctor advice basic rule base and rule combination library maintenance module, a doctor advice extraction module, a doctor advice checking module, a label printing (two-dimensional code generation) module and a departmental scanning module. The doctor advice extraction module is used for extracting information of doctor advices from electronic medical records; the doctor advice checking module performs checking in the mode of repeated dosage checking, combination rule joint checking and incompatibility checking to find checking alarm information to send the information to a clinical pharmacist for confirmation, and drugs with problems are turned down to a doctor; the doctor advise basic rule base and rule combination library maintenance module is used for maintaining and updating a combination library; the label printing module is used for labeling checked drugs to generate two-dimensional codes; the departmental scanning module performs departmental scanning on the two-dimensional codes of the drugs when the drugs depart. The doctor advice intelligent auditing system is used for recording the departmental time of the checked drugs and tracking the using process of drugs conveniently.
Owner:SHAN DONG MSUN HEALTH TECH GRP CO LTD
Solar roofing system
ActiveUS20100236542A1Cost effectiveEasy to installPhotovoltaic supportsSolar heating energyFastenerSolar energy
Owner:GARLAND INDS
System and method for remotely initializing a RF transaction
InactiveUS20060074813A1Small modificationAcutation objectsUnauthorised/fraudulent call preventionPersonalizationUSB
The present invention relates to a process for providing a RF module configured to convert a nontraditional transaction device for traditional transaction completion. The RF module is placed in physical and logical communication with a microprocessor of a nontraditional transaction device for receiving a personalization file to enable the RF module to complete RF transactions. In an exemplary embodiment, the microprocessor is configured to receive the personalization file from a mobile device account provider subsequent to an end user establishing communication with the device account provider and notifying the provider that a RF module is to be personalized. The mobile device account provider may receive the personalization file from a RF module account issuer and provide the personalization file to the RF module via the mobile device microprocessor. In another exemplary embodiment, the mobile device may include a USB interface for use in providing the personalization file to the RF module by establishing communications between the USB interface and the mobile device account provider or the RF module account provider as required.
Owner:LIBERTY PEAK VENTURES LLC
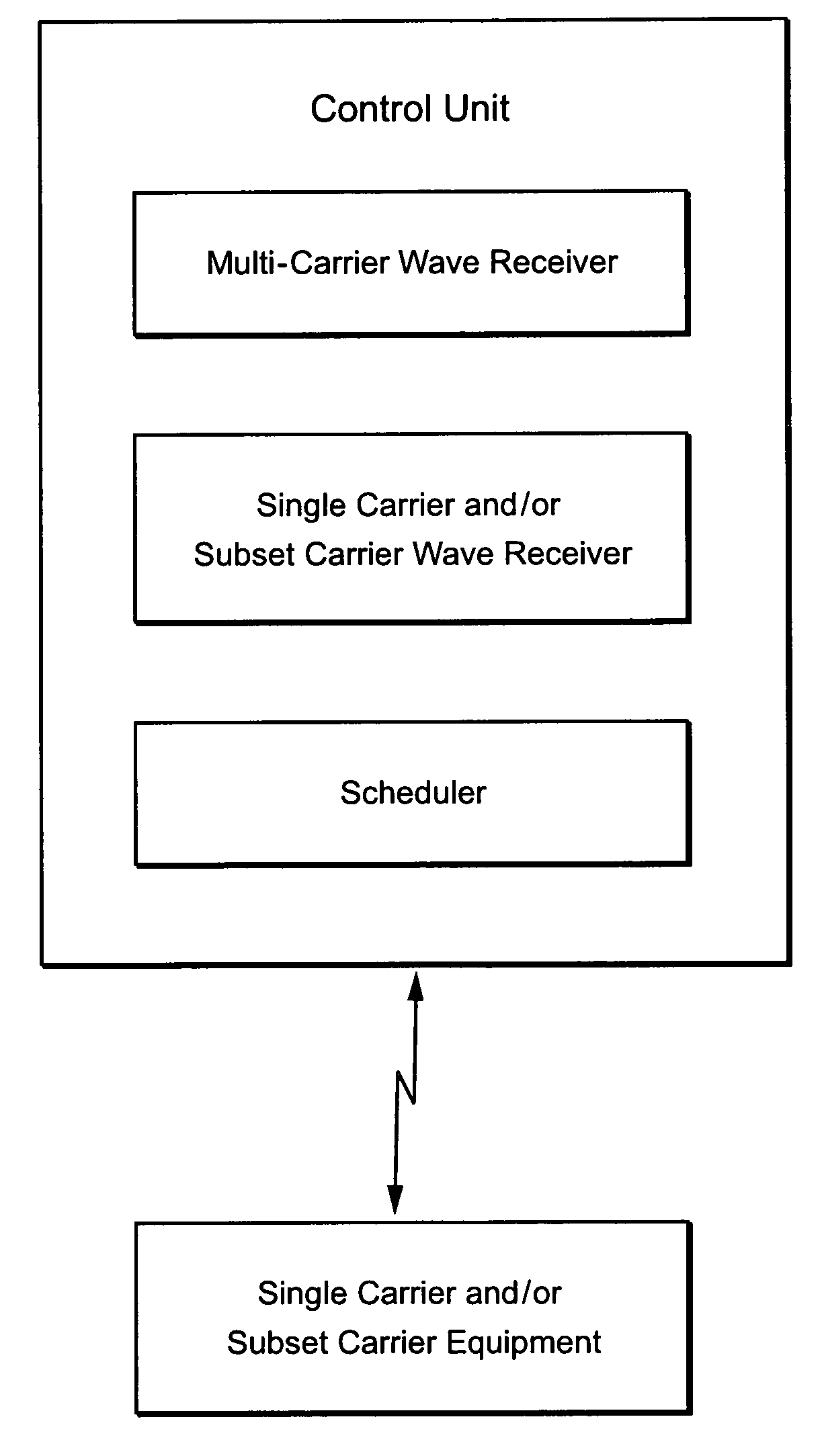
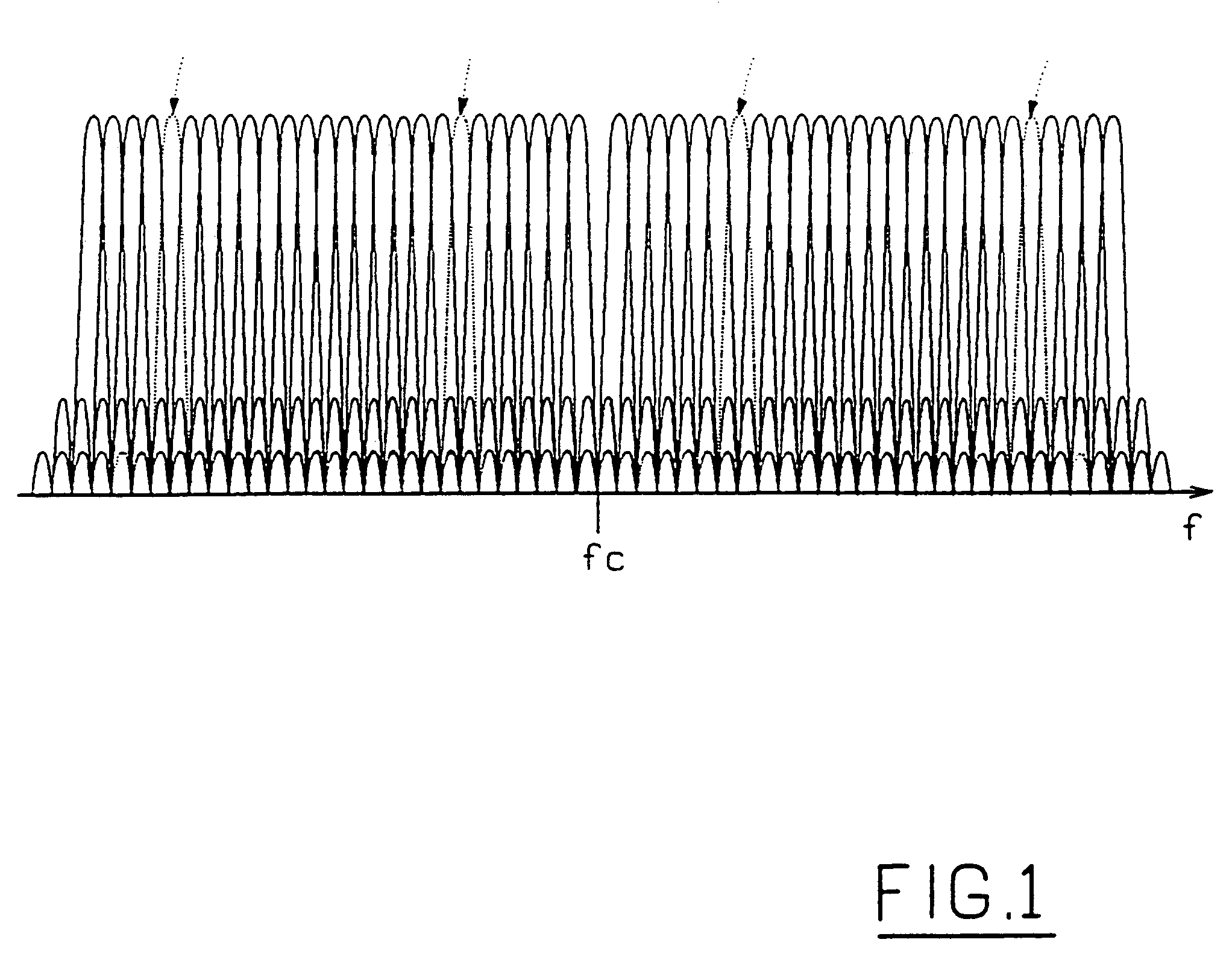
Device for narrow-band communication in a multi-carrier system
ActiveUS7023826B2Limited power supplySmall modificationRadio/inductive link selection arrangementsWireless commuication servicesCarrier signalNarrowband
A central unit for a multi-carrier system receives both multi-carrier and single carrier signals. The single carrier wave is a carrier wave that is part of the multi-carrier system for which the central unit is designed. The central unit schedules transmission from the single-carrier equipment in interaction with the single-carrier equipment.
Owner:TELEFON AB LM ERICSSON (PUBL)
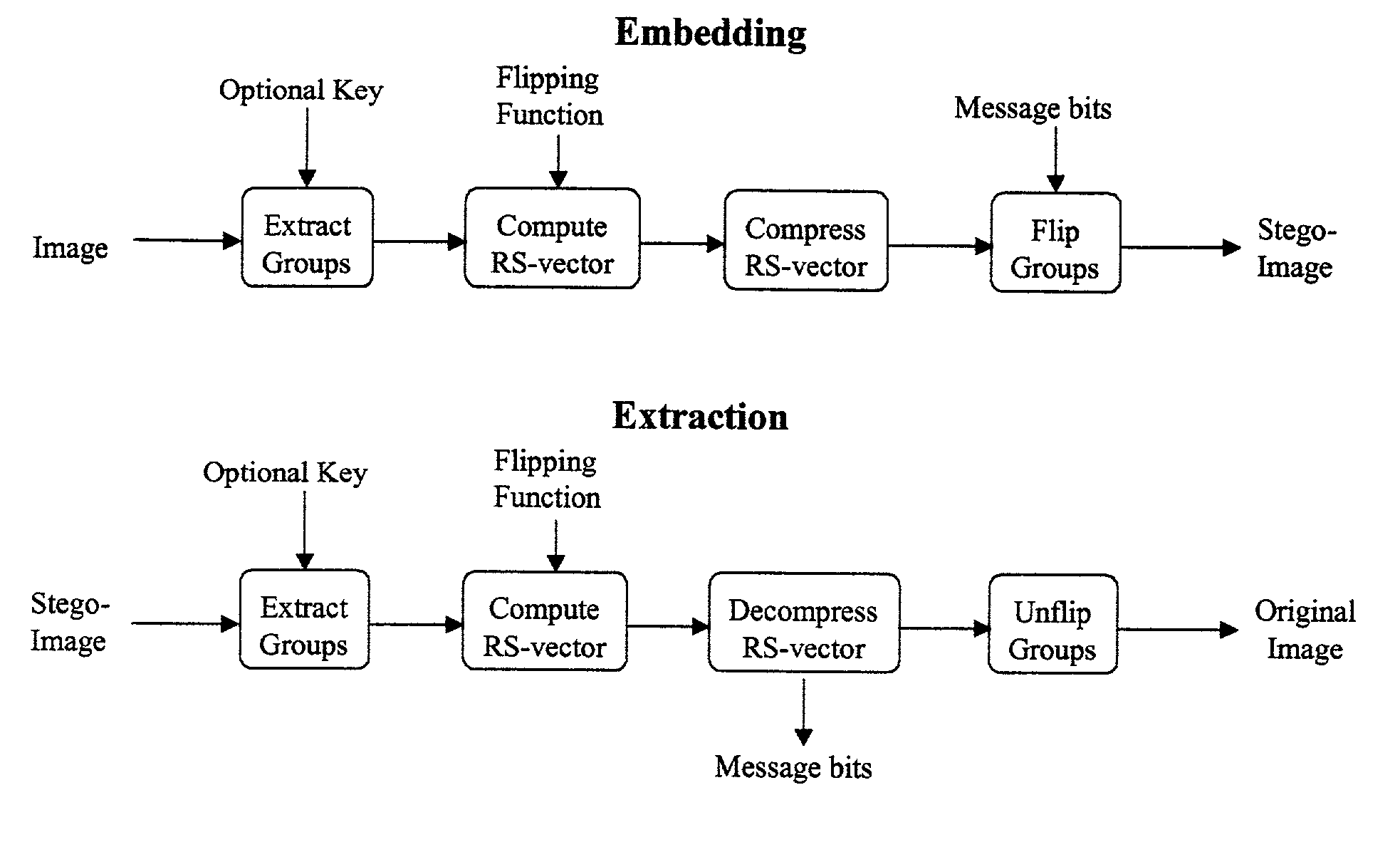
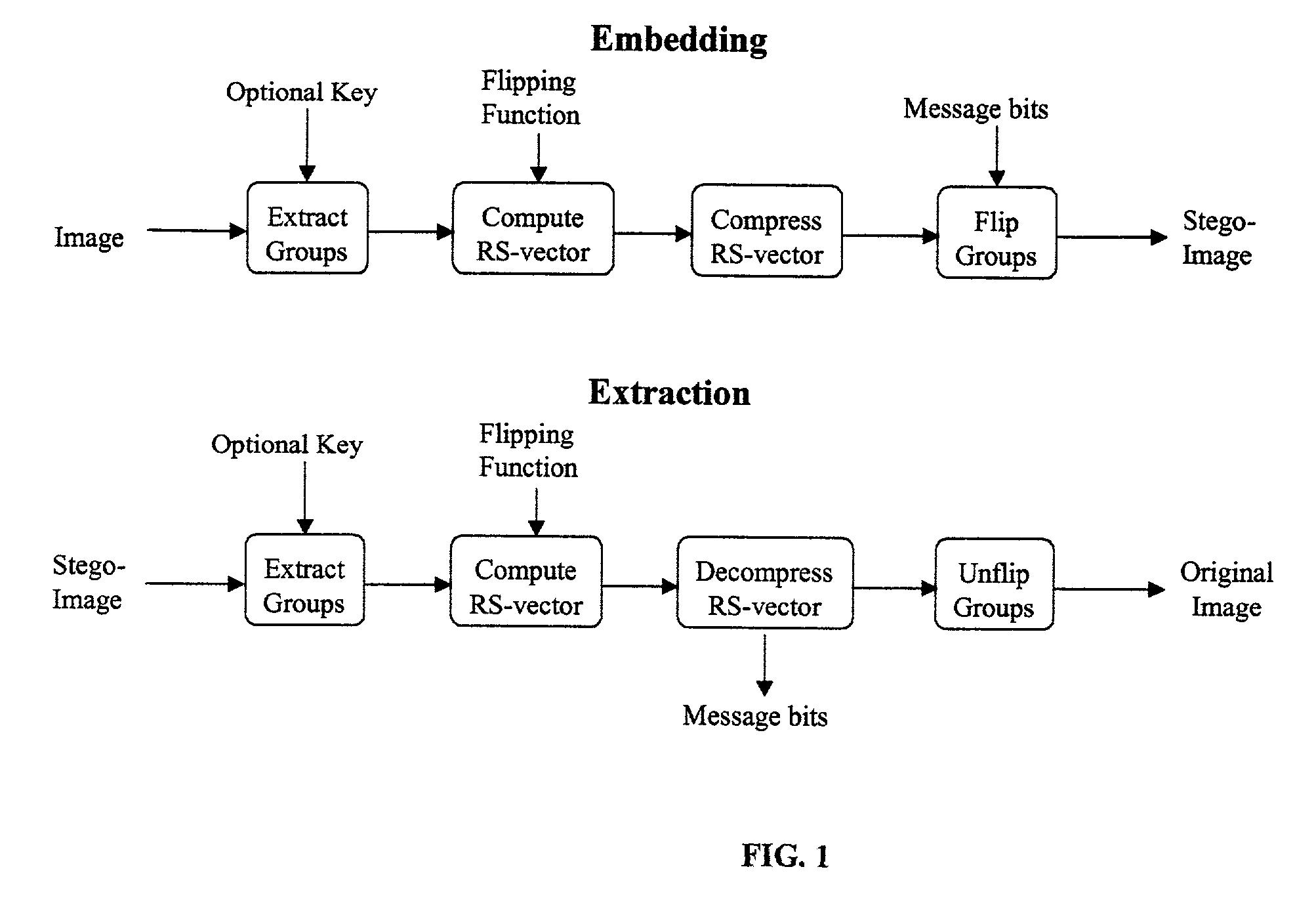
Lossless embedding of data in digital objects
ActiveUS7006656B2Simple and elegant lossless techniqueHeavy loadUser identity/authority verificationCharacter and pattern recognitionSteganalysisHidden data
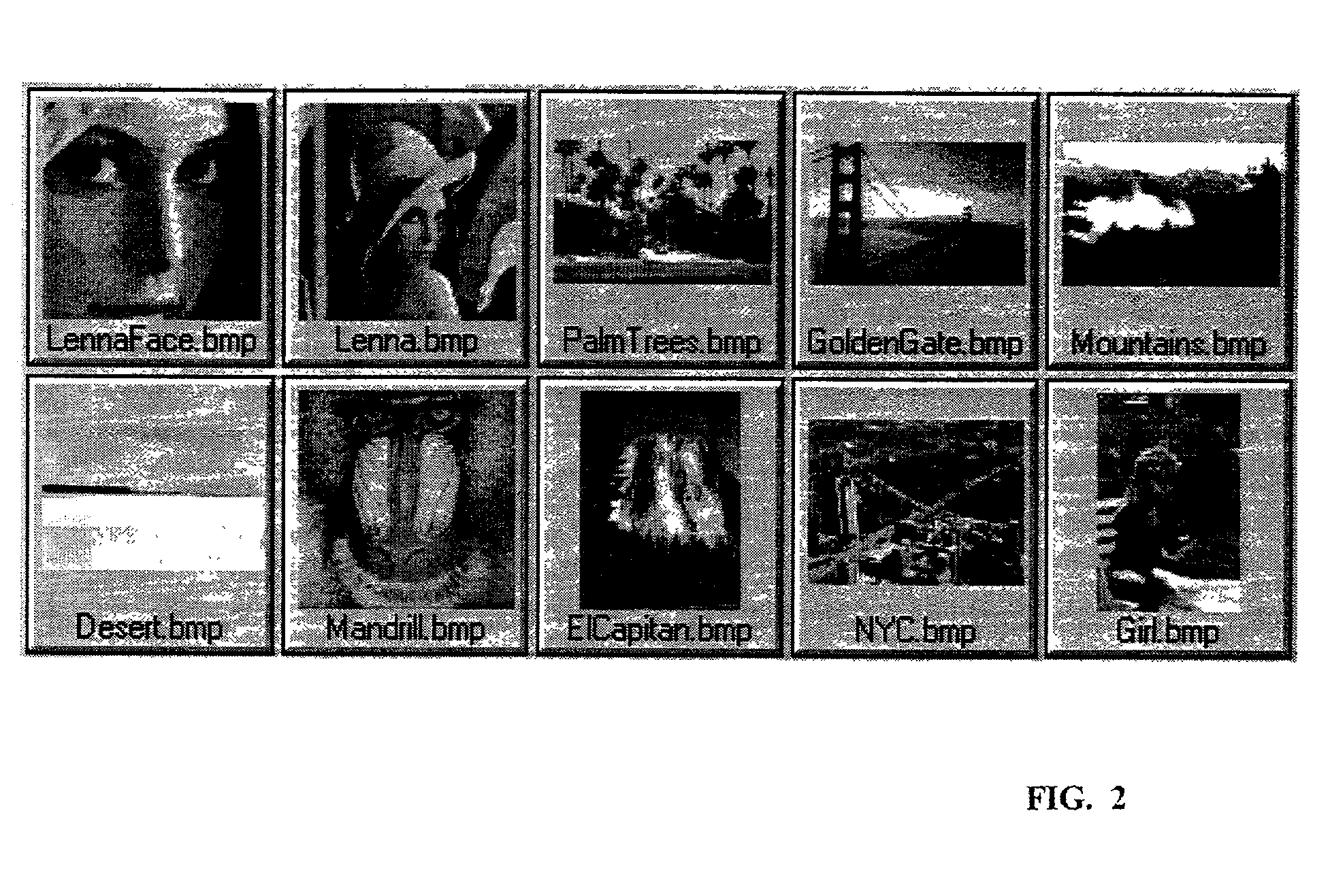
Current methods of embedding hidden data in an image inevitably distort the original image by noise. This distortion cannot generally be removed completely because of quantization, bit-replacement, or truncation at the grayscales 0 and 255. The distortion, though often small, may make the original image unacceptable for medical applications, or for military and law enforcement applications where an image must be inspected under unusual viewing conditions (e.g., after filtering or extreme zoom). The present invention provides high-capacity embedding of data that is lossless (or distortion-free) because, after embedded information is extracted from a cover image, we revert to an exact copy of the original image before the embedding took place. This new technique is a powerful tool for a variety of tasks, including lossless robust watermarking, lossless authentication with fragile watermarks, and steganalysis. The technique is applicable to raw, uncompressed formats (e.g., BMP, PCX, PGM, RAS, etc.), lossy image formats (JPEG, JPEG2000, wavelet), and palette formats (GIF, PNG).
Owner:RES FOUND OF SUNY THE +1
Positive lock piece and electrical connector assembly equipped with same
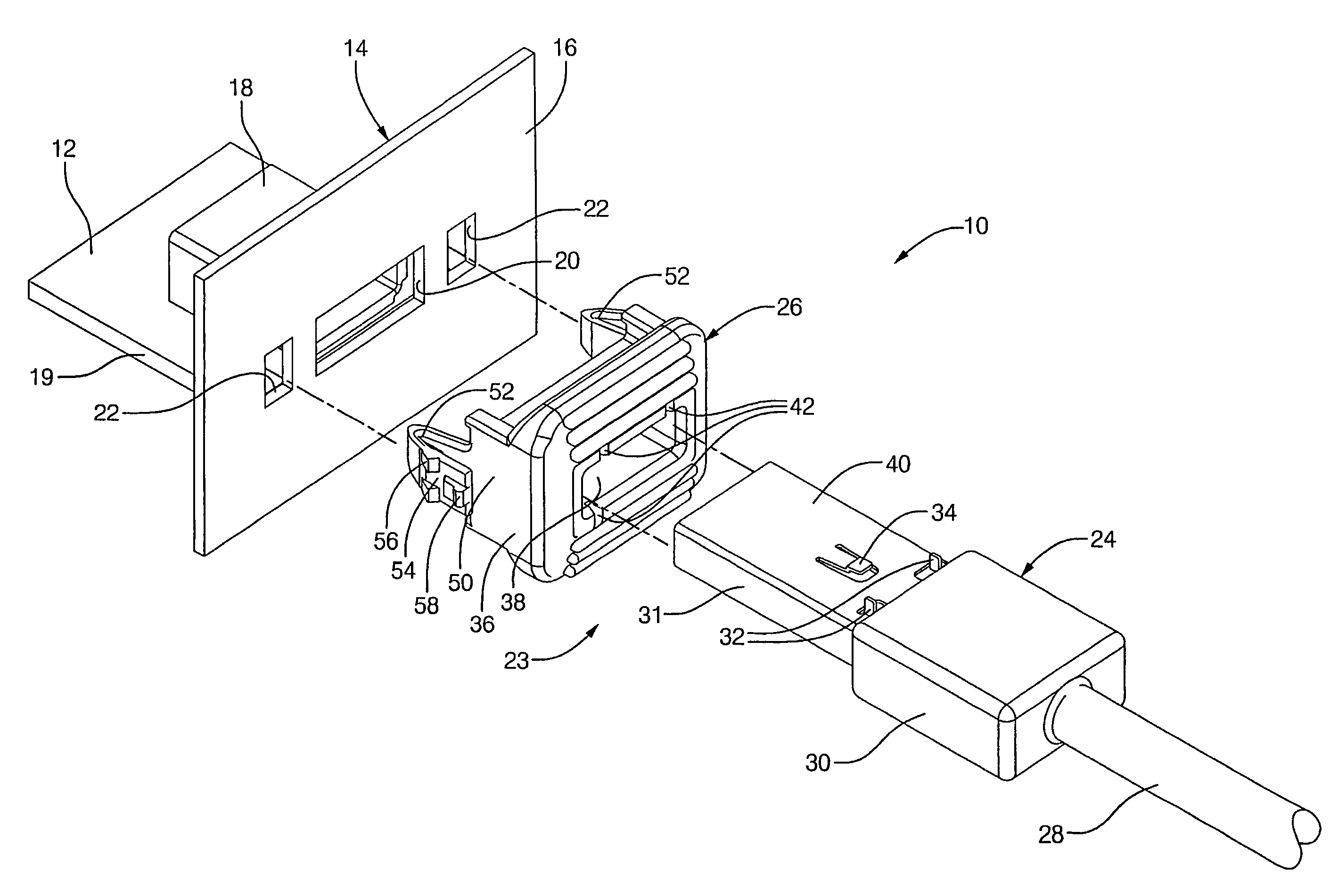
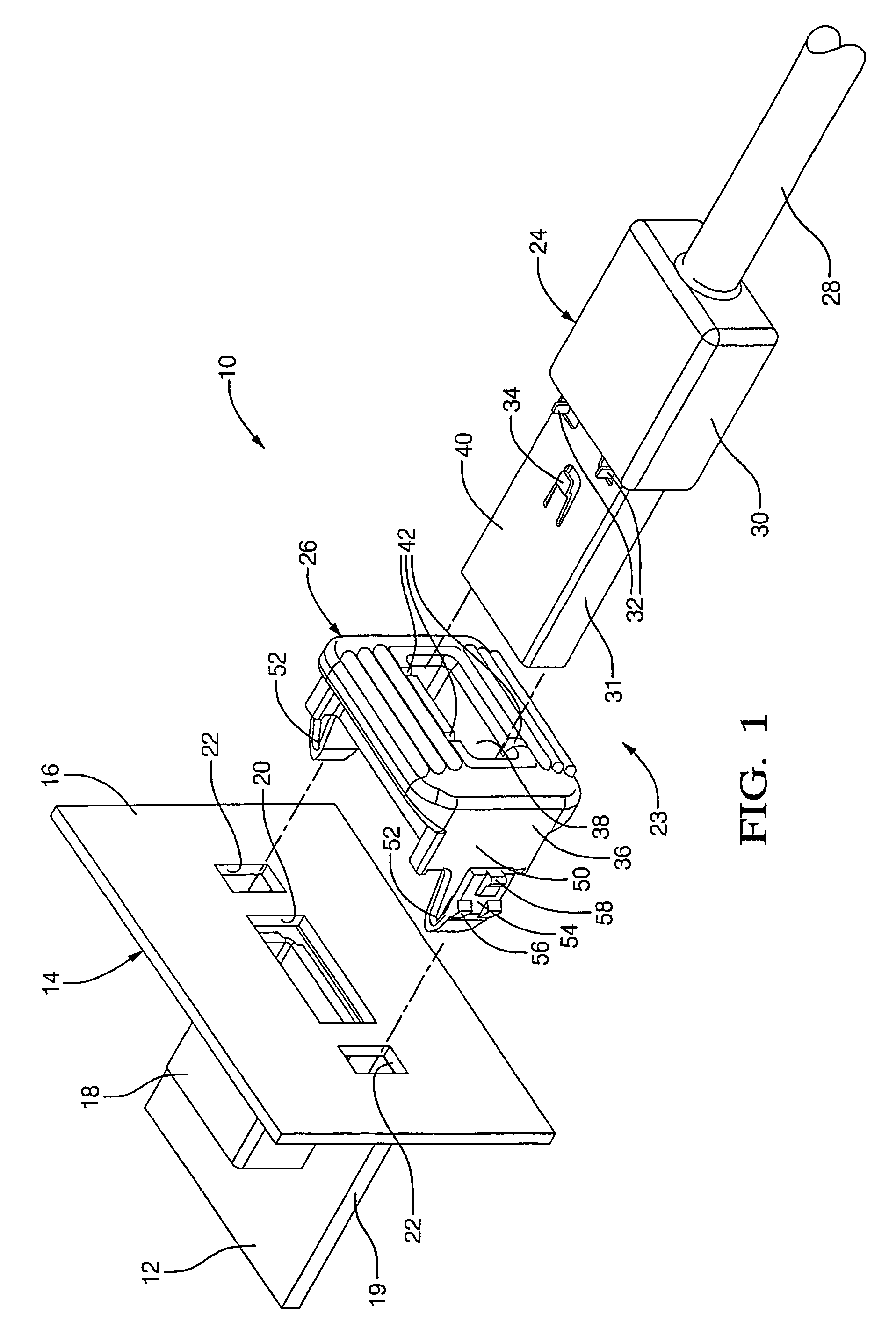
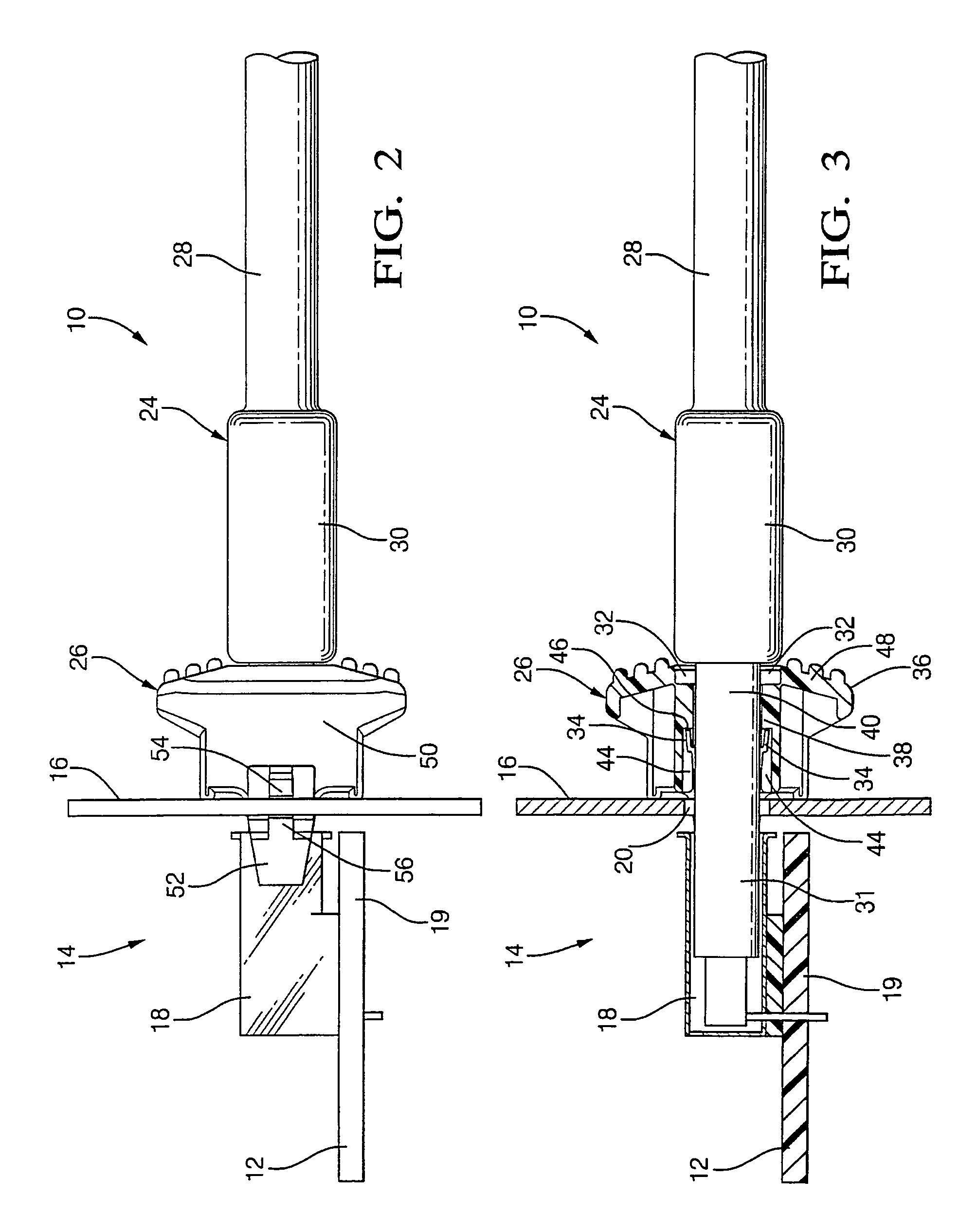
ActiveUS7094099B2Easy and inexpensiveSmall modificationSubstation/switching arrangement detailsCoupling parts mountingElectrical connectorUSB
An electrical connector assembly comprises an electrical USB connector that has a separate lock piece attached to the terminal of the electrical connector. The lock piece has a collar that fits onto the terminal adjacent to the connector body of the electrical connector. The collar has orientation slots that receive tabs of terminal to properly orient the positive lock piece onto the terminal and inner retention shoulders that cooperate with lock fingers of the terminal for locking the positive lock onto the terminal. A flange attached to the collar serves as a finger guard and push surface when the collar is attached to the terminal. The lock piece has lock arms for attaching the collar to a face panel.
Owner:APTIV TECH LTD
Means for replacing common sugars if foods for enhanced nutrition
InactiveUS20080260925A1Great tasteSuperior digestive toleranceFood ingredient functionsFood preparationLow glucoseSide effect
A means for replacing common sugars (particularly sucrose) in a range of foods that maximizes sugar-like taste, texture and other key properties of sugar while minimizing the undesirable traits such as blood sugar response, digestive side effects, high caloric content and aftertastes. Various differing ratios and combinations of high intensity sweetening agents, high molecular weight bulking agent(s), substantially non-digestible sugar(s), and low molecular weight sugar alcohol(s) are used for various applications such as tabletop sugar substitute, frozen deserts, condiments, baked goods, chocolate and confectionaries have different formulations. These sugar replacement approaches are highly relevant to the production of diabetic-friendly foods, diet and / or reduced calorie foods, non-cariogenic (tooth-friendly) foods and other sweet, low-glycemic foods.
Owner:ZINK GALEN PAUL
Method and device for controlling vehicle travel
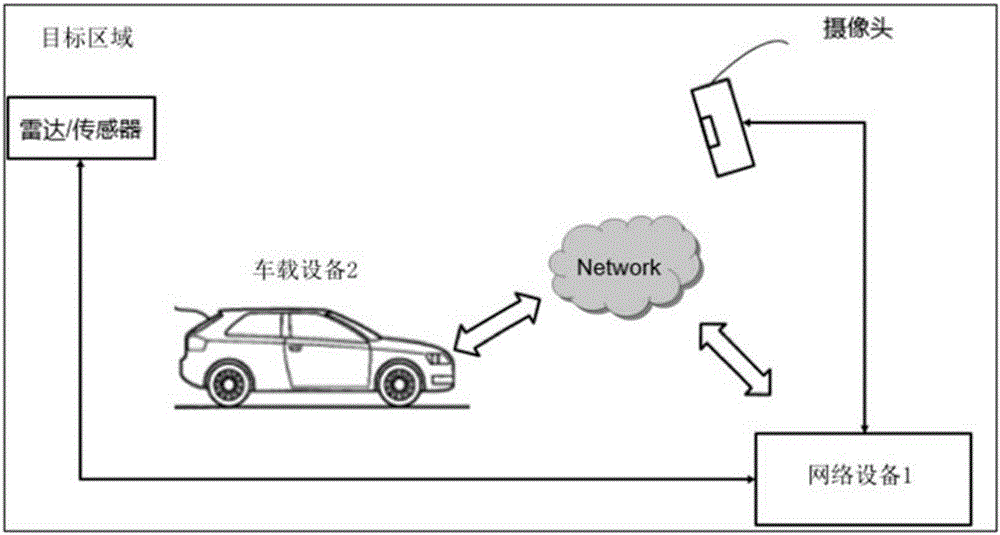
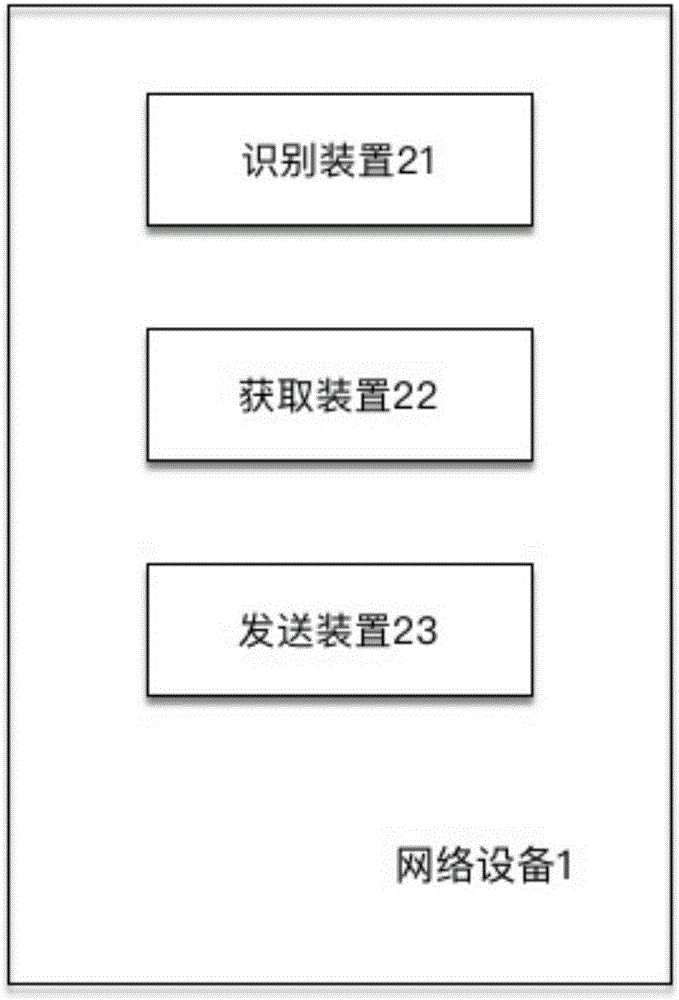
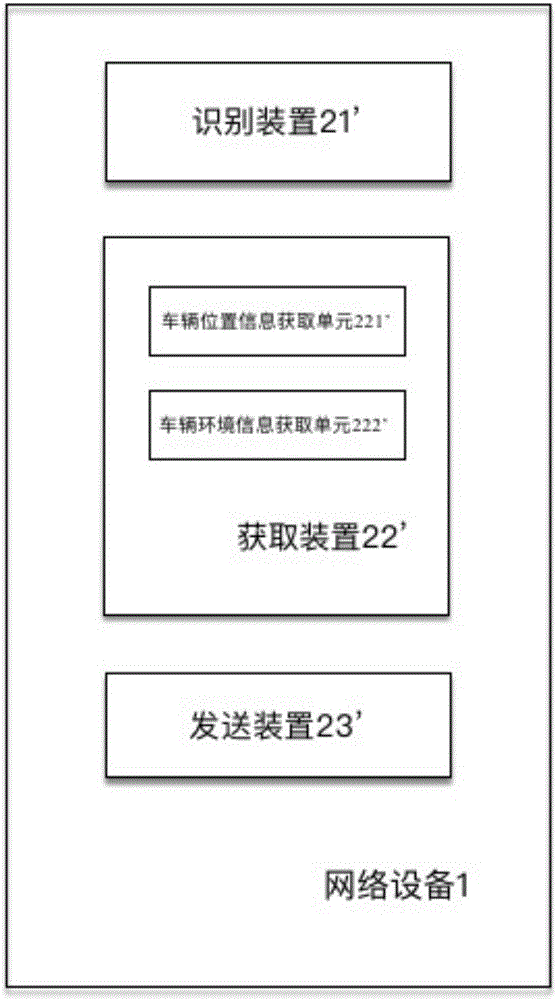
PendingCN107438873ASmall modificationReduce power consumptionRoad vehicles traffic controlEngineeringComputer terminal
An object of the present application is to provide a method and a device for controlling vehicle travel, wherein the method comprises: identifying a traveling vehicle in a target area; acquiring vehicle environment information of the traveling vehicle in the target area; and based on the vehicle environment information, The vehicle-mounted terminal of the traveling vehicle transmits traveling instruction information. Compared with the prior art, the present application does not need to rely on the deployment of a complex and accurate sensing device on a traveling vehicle, even if only a few sensing devices are deployed on the traveling vehicle, or even deployed without deployment The device based on the present application can still achieve accurate control of the running of the vehicle in the target area. Therefore, the present application has less modification to existing vehicles and low power consumption of the vehicle, thus bringing about the overall technical costs reduce.
Owner:UISEE TECH BEIJING LTD
Memory domain based security control with data processing systems
ActiveUS7966466B2Improve securityLimited abilityDigital computer detailsUnauthorized memory use protectionMemory addressOperational system
Access to memory address space is controlled by memory access control circuitry using access control data. The ability to change the access control data is controlled by domain control circuitry. Whether or not an instruction stored within a particular domain, being a set of memory addresses, is able to modify the access control data is dependent upon the domain concerned. Thus, the ability to change access control data can be restricted to instructions stored within particular defined locations within the memory address space thereby enhancing security. This capability allows systems to be provided in which call forwarding to an operating system can be enforced via call forwarding code and where trusted regions of the memory address space can be established into which a secure operating system may write data with increased confidence that that data will only be accessible by trusted software executing under control of a non-secure operating system.
Owner:ARM LTD
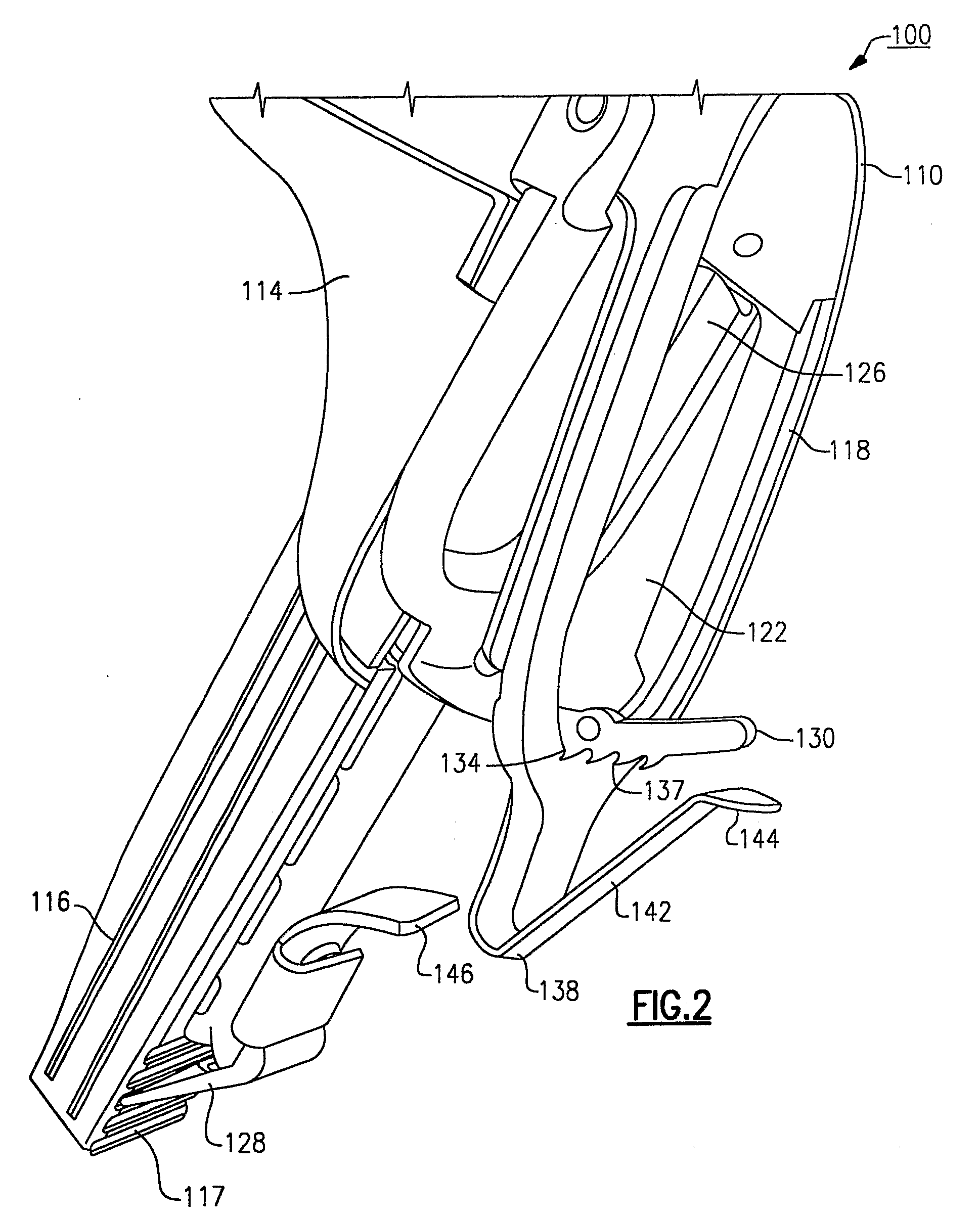
Articulation mechanism for a vaginal speculum
Owner:WELCH ALLYN INC
Method of authentication in IP multimedia subsystem
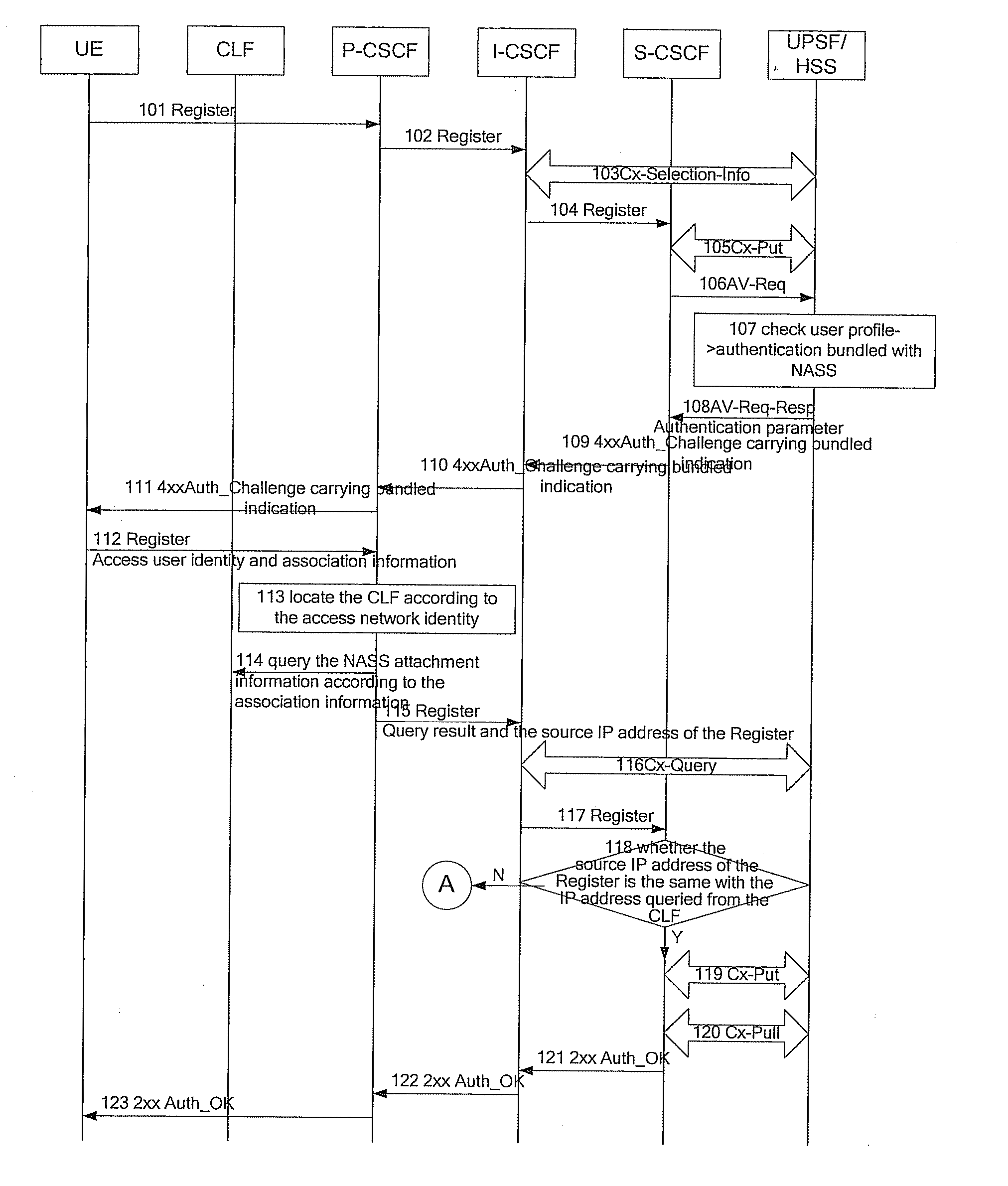
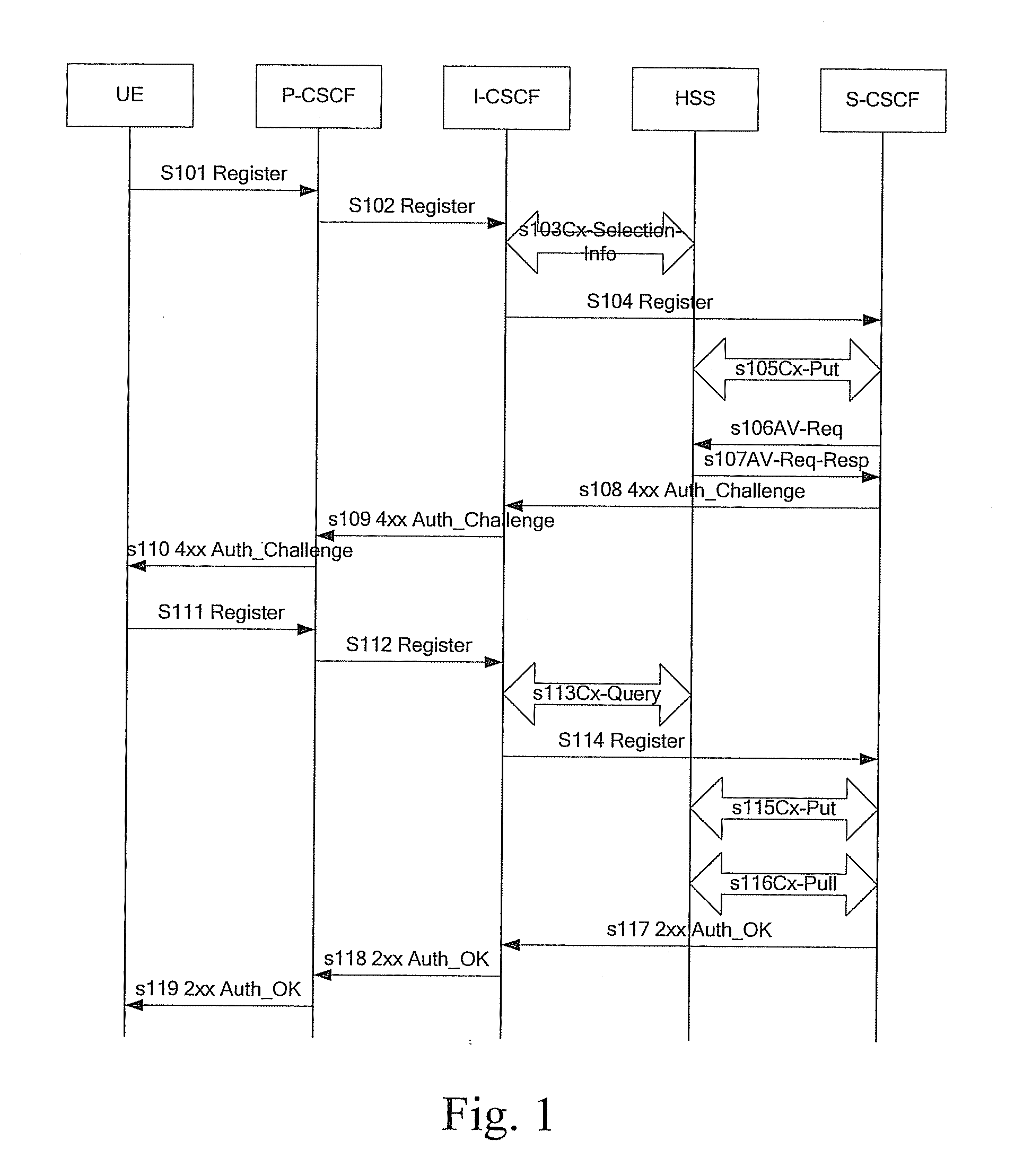
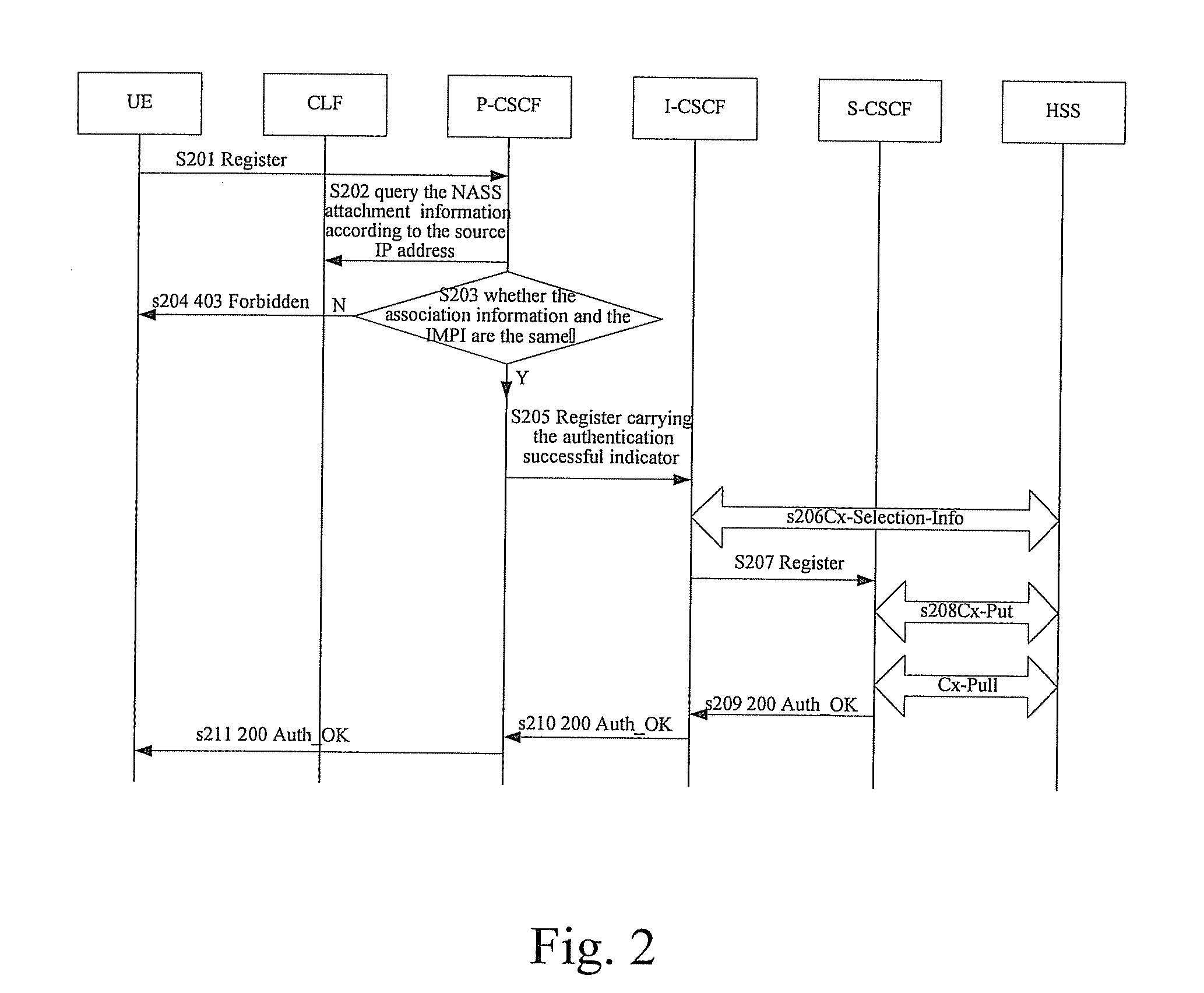
ActiveUS20080020789A1Little modificationSmall modificationUnauthorised/fraudulent call preventionEavesdropping prevention circuitsService layerComputer hardware
A method of authentication in an IMS includes: after receiving a Register message from a UE, locating, by a P-CSCF, a CLF according to information contained in the Register message and a pre-configured relationship; querying, by the P-CSCF, the CLF about NASS attachment information of the UE to obtain a query result, and sending the Register message carrying the query result to an I-CSCF; forwarding, by the I-CSCF, the Register message carrying the query result to a S-CSCF assigned by a UPSF or the HSS; authenticating the UE and sending an authentication result to the UE by the S-CSCF. In embodiments of the present invention, the UPSF or the HSS in the service layer determines the authentication mechanism of the user, and the S-CSCF implements the authentication, which is more reasonable. Embodiments of the present invention also provide combinations of NBA with other authentication mechanisms, thereby guarantees the authentication of the user after the NBA authentication fails.
Owner:HUAWEI TECH CO LTD
Method and device for backing up boot program
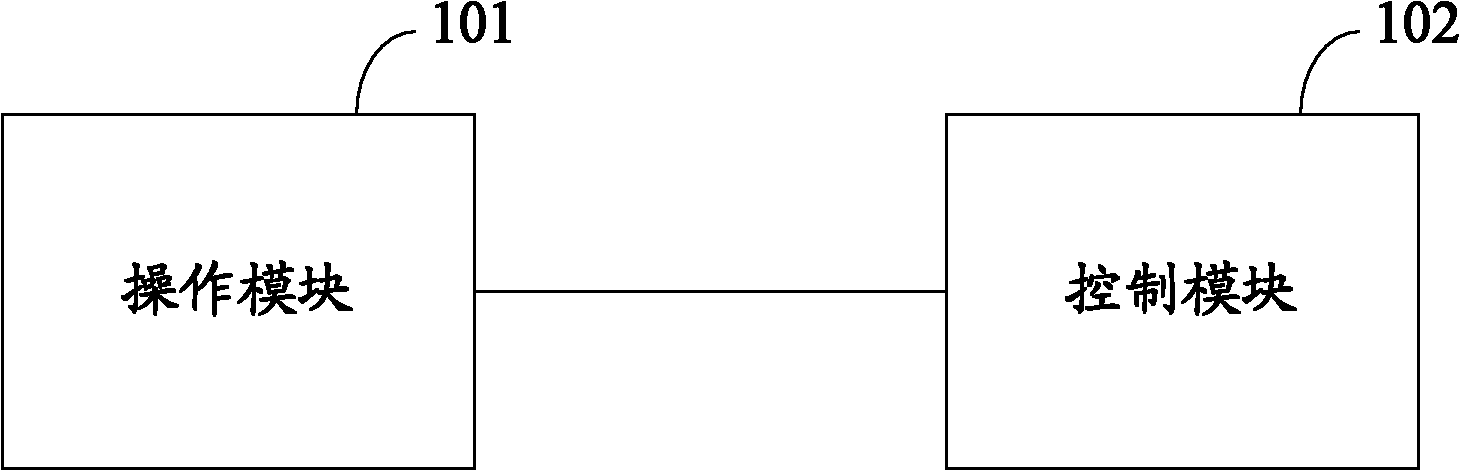
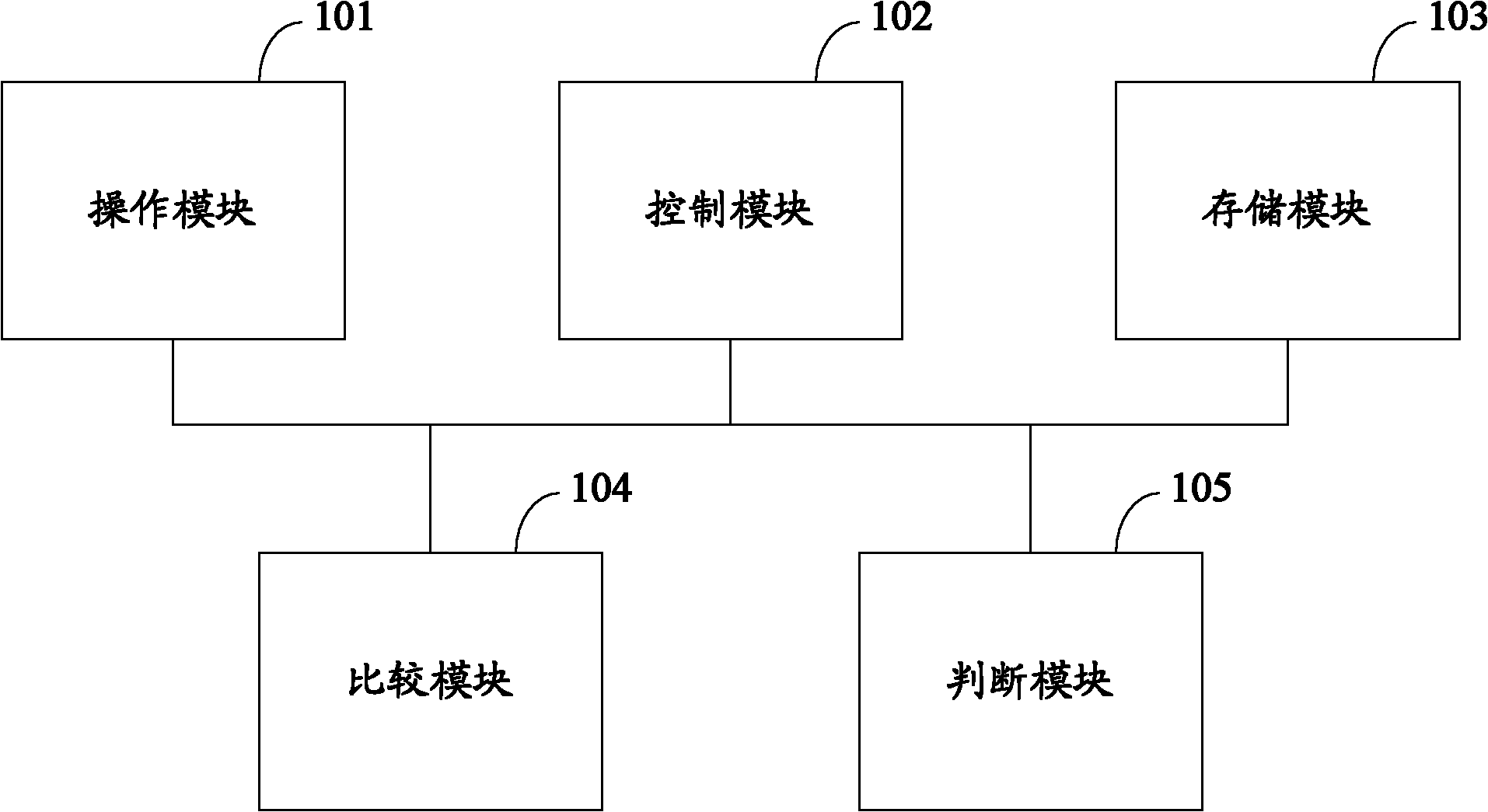
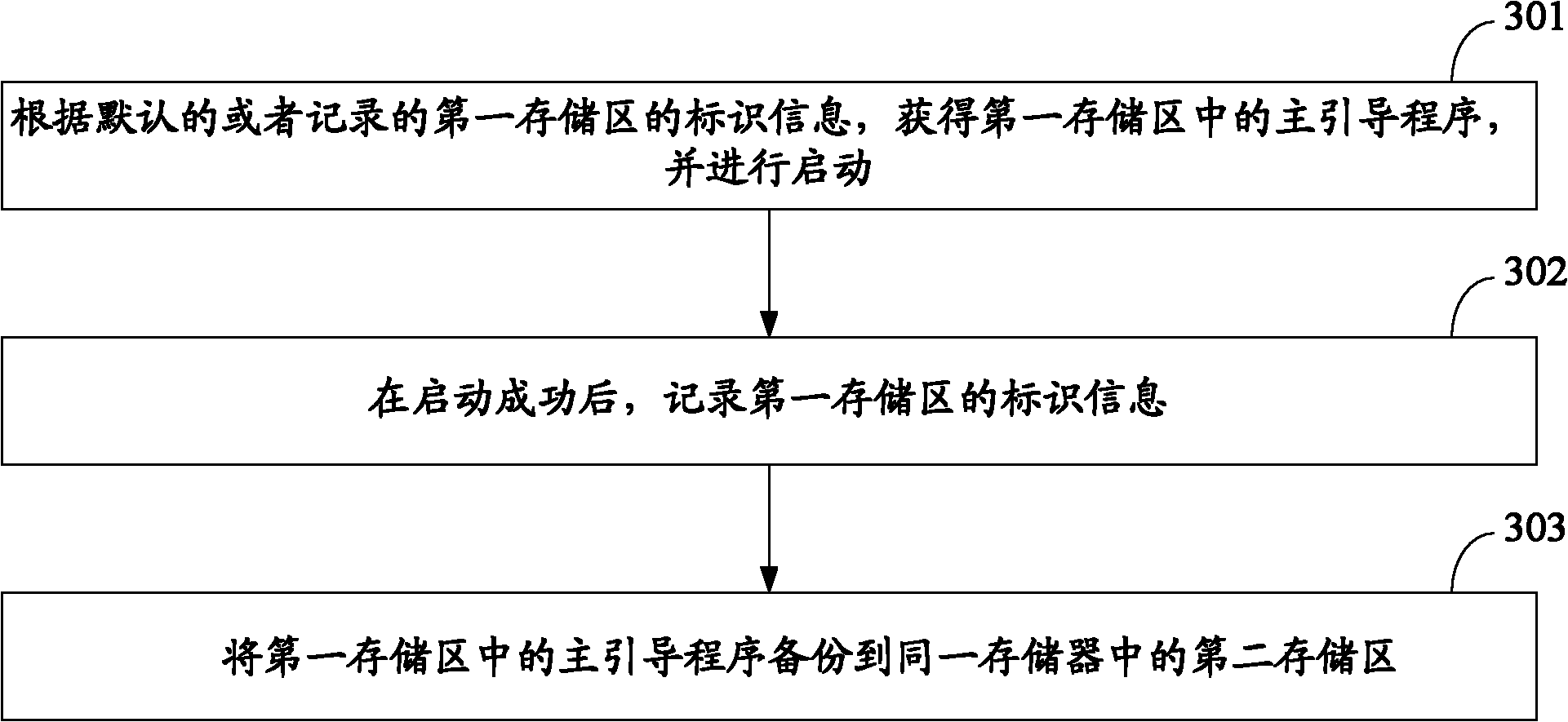
ActiveCN102023908AImplement backupGuaranteed correctnessProgram loading/initiatingRedundant operation error correctionBootingStart up
The invention discloses a method for backing up a boot program, which is used for realizing backup of the boot program and improving the reliability of system startup. The method comprises the following steps: obtaining a main boot program in a first memory area according to the default or recorded identification information in the first memory area, and starting up the main boot program, wherein the first memory area is the current memory area; after the main boot program is successfully started up, recording the identification information in the first memory area; and backing up the main boot program in the first memory area to a second memory area in the same memory. The invention also discloses a method for upgrading a boot program, which is used for realizing upgrading of the boot program. The method comprises the following steps: determining whether the boot program is needed to be upgraded after the main boot program in the first memory area is started up; if so, obtaining upgrading information; and upgrading the boot program backed up to the second memory area according to the obtained upgrading information. The invention also discloses a device for realizing the method.
Owner:ZTE CORP
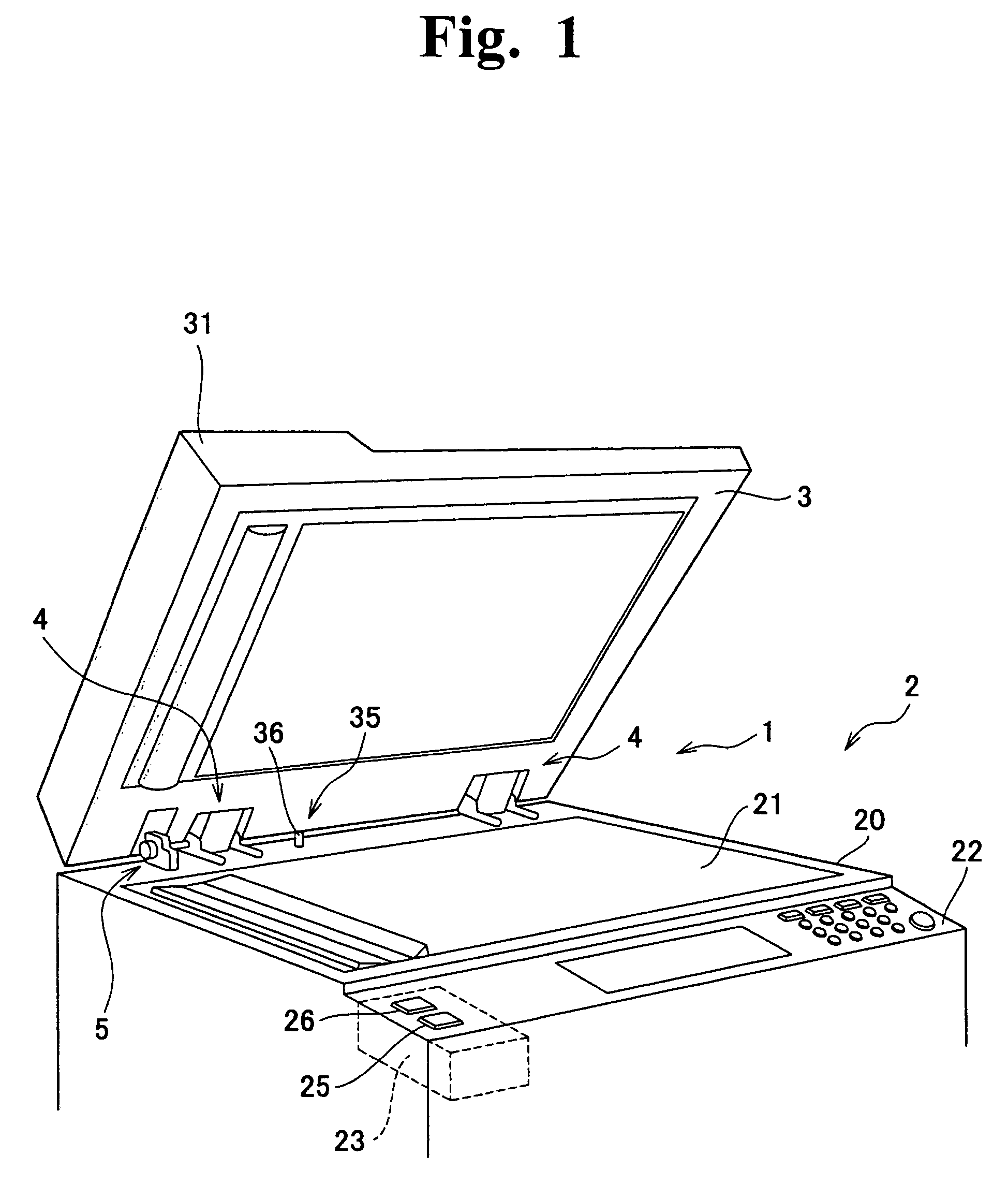
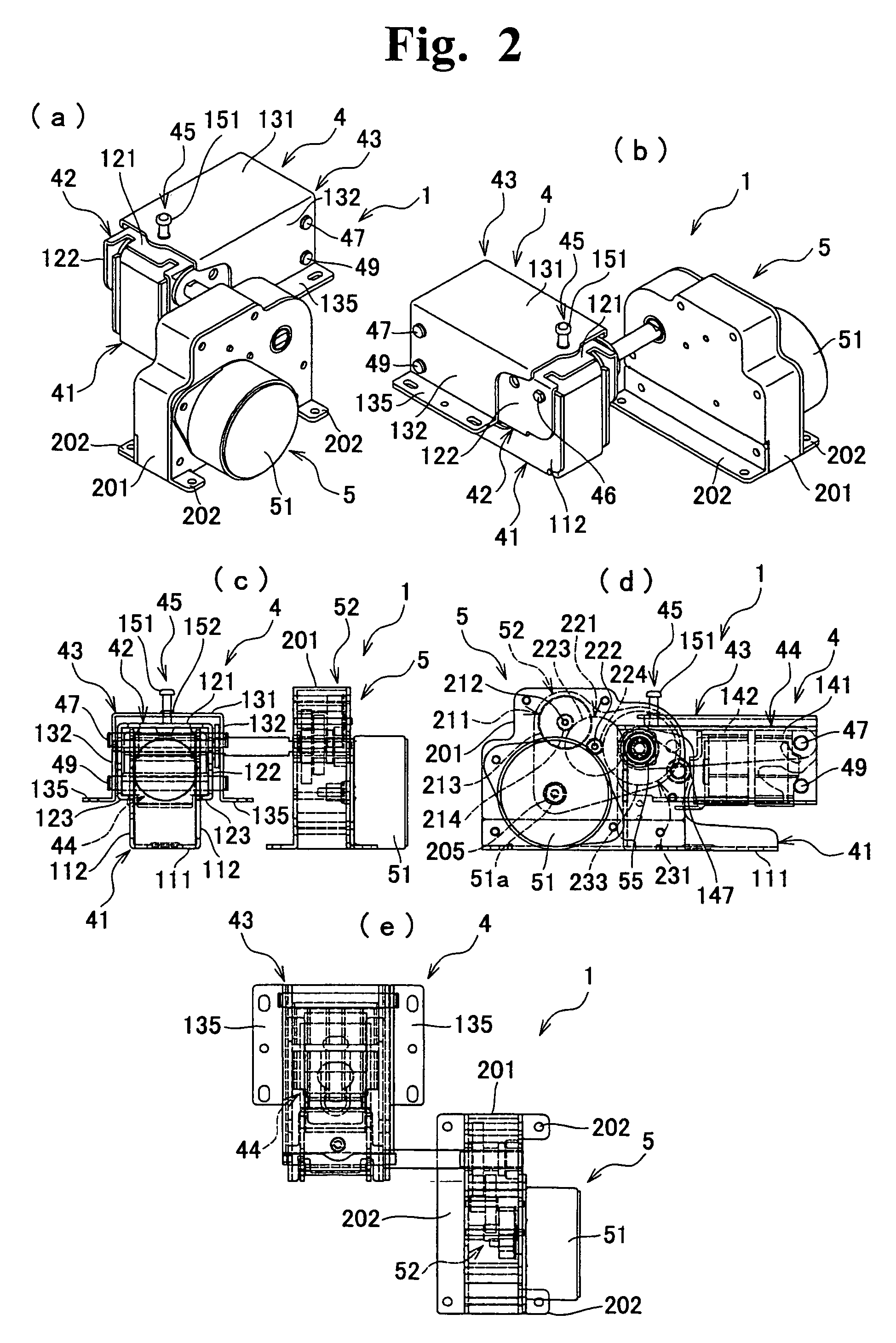
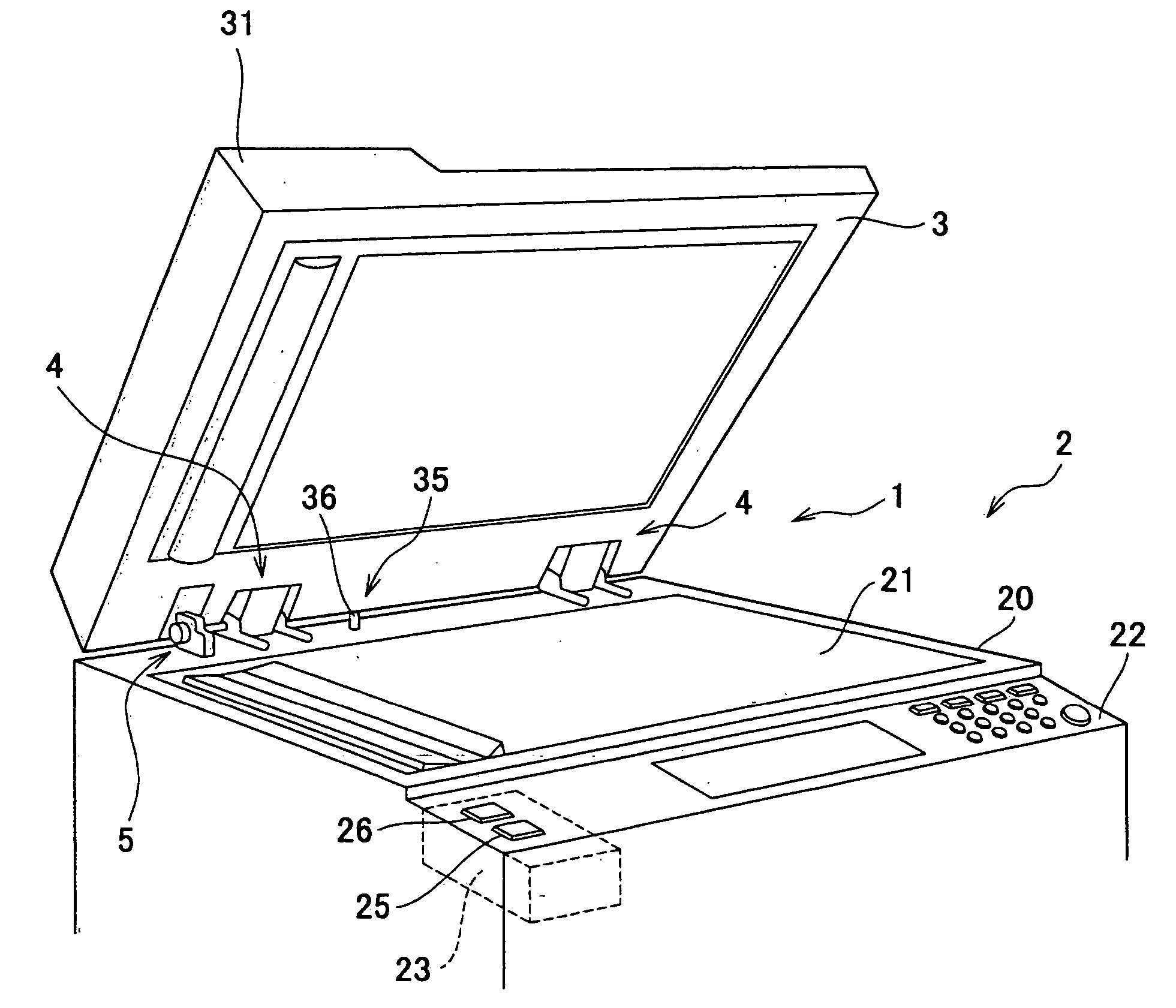
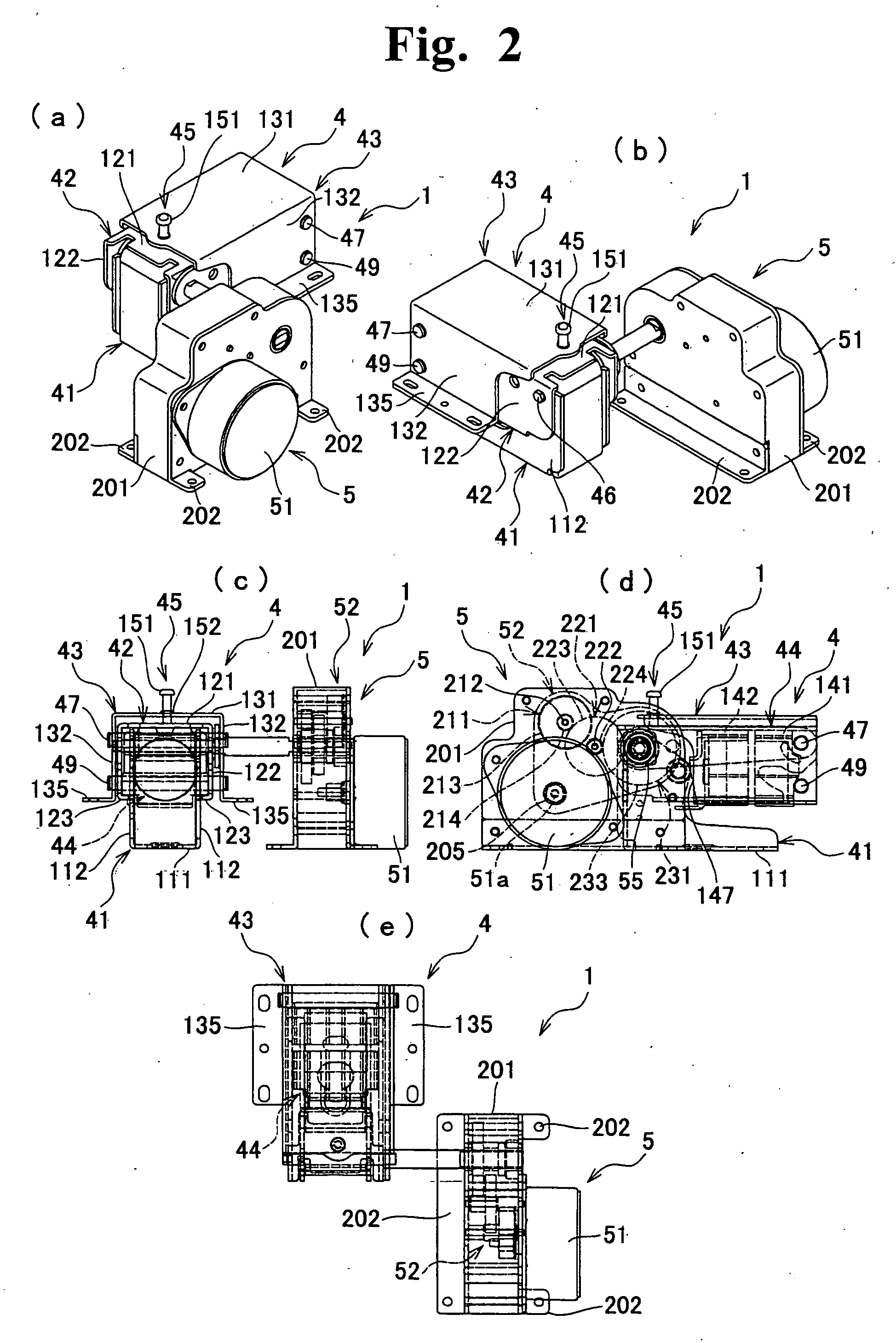
Automatic original cover closer and office equipment including automatic original cover closer
InactiveUS7512376B2Practical to useSmall modificationMan-operated mechanismPower-operated mechanismDrive shaftEngineering
An automatic original cover closer to practically realize an automatic opening and closing function of an original cover, has a hinge part to rotatably support an original cover to the main body of office equipment and a driving part to automatically drive the hinge part. The hinge part includes a mounting member to mount on the main body and a supporting member to support the original cover to be axially supported to this mounting member so as to be rotatable with a rotary shaft via the rotary shaft. The driving part includes a positively and reversely rotatable drive motor and a power transferring mechanism to decelerate and transfer the rotary driving power of this drive motor to a drive shaft. The rotary driving power of the drive motor is transferred to the supporting member via the drive shaft and the rotary shaft, by connecting the rotary shaft to the drive shaft.
Owner:KEM HONGKONG
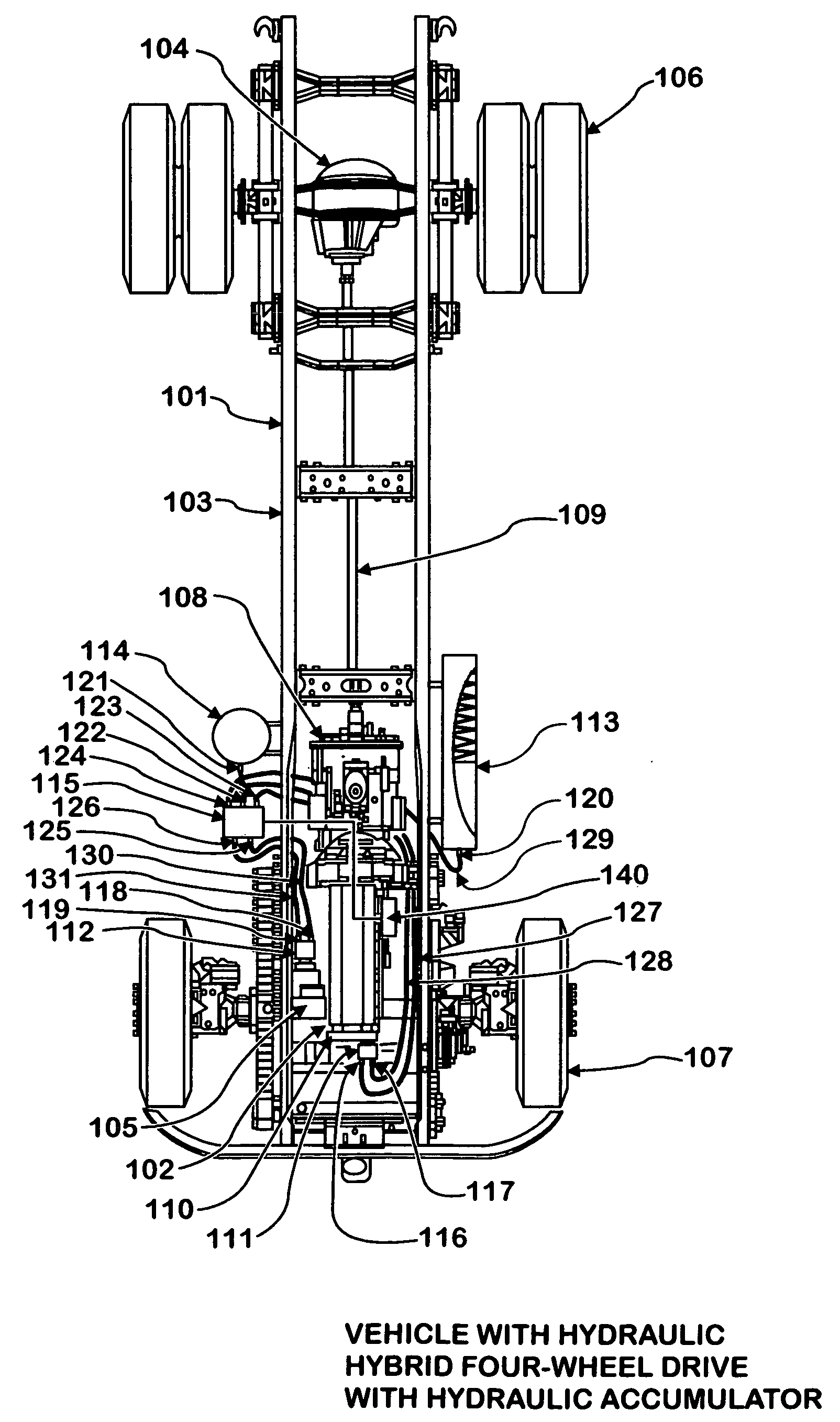
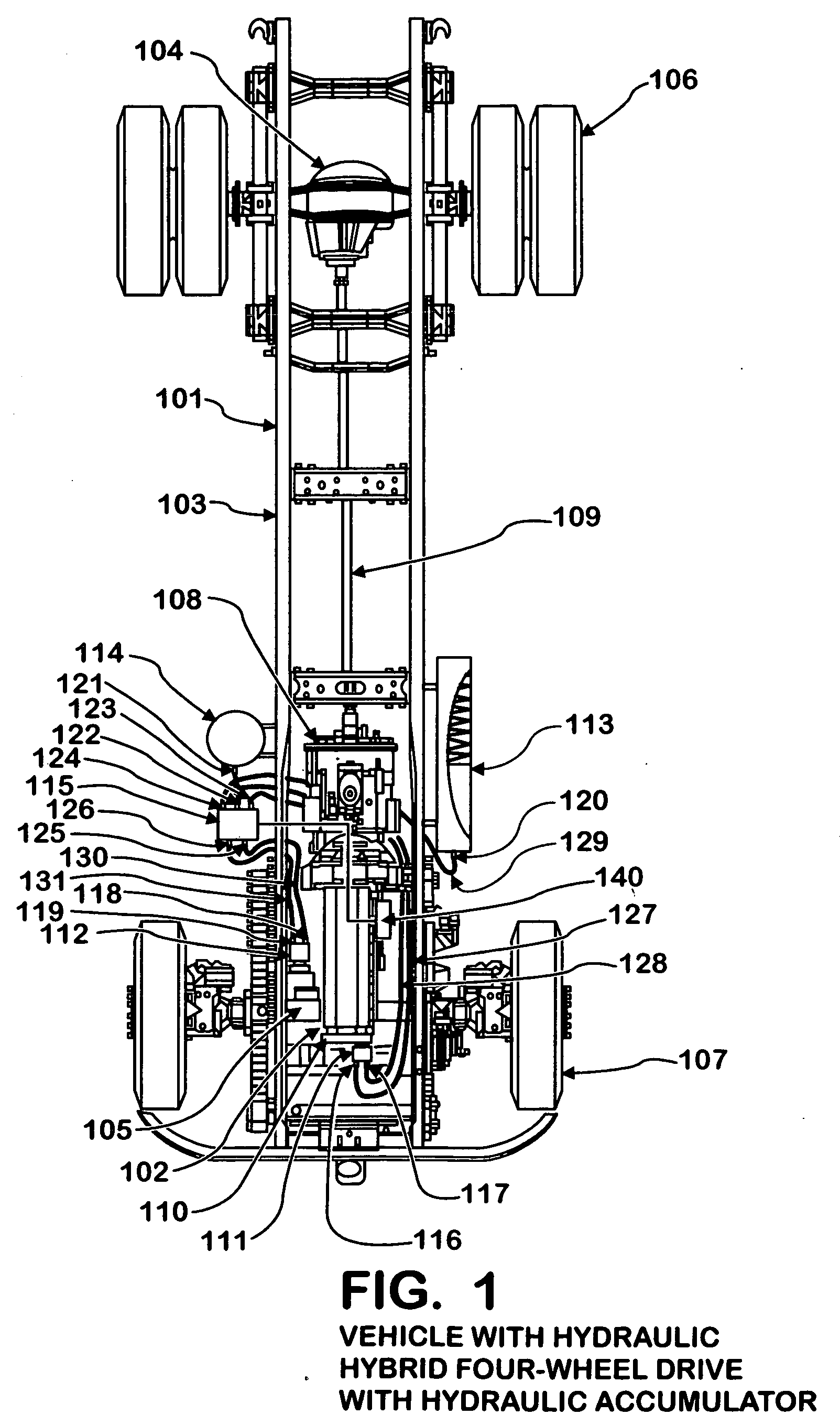
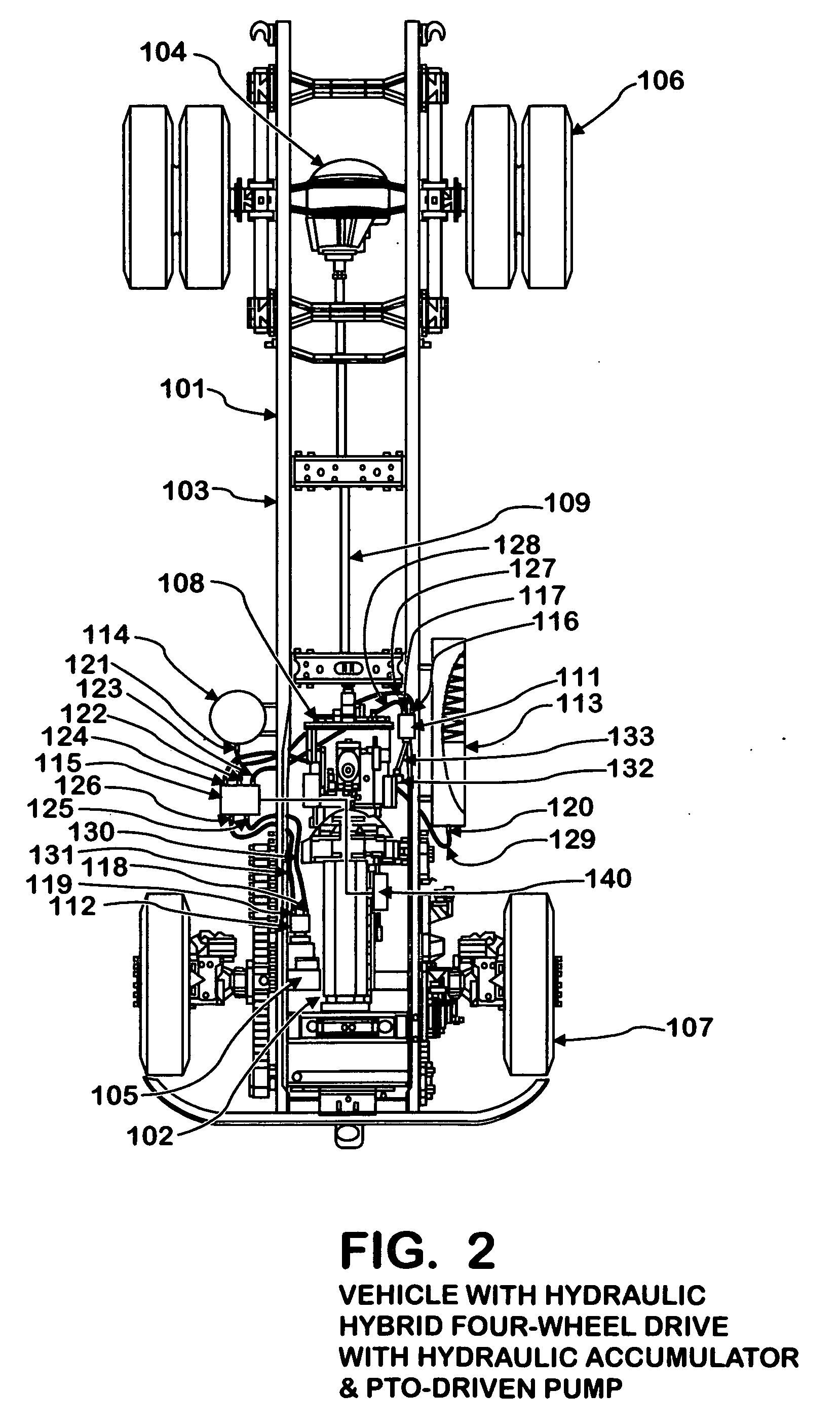
Hydraulic hybrid four wheel drive
InactiveUS20060197375A1Enhance engine brakingImprove fuel efficiencyBraking action transmissionPlural diverse prime-mover propulsion mountingHydraulic motorEngineering
Owner:INT TRUCK INTPROP LLC
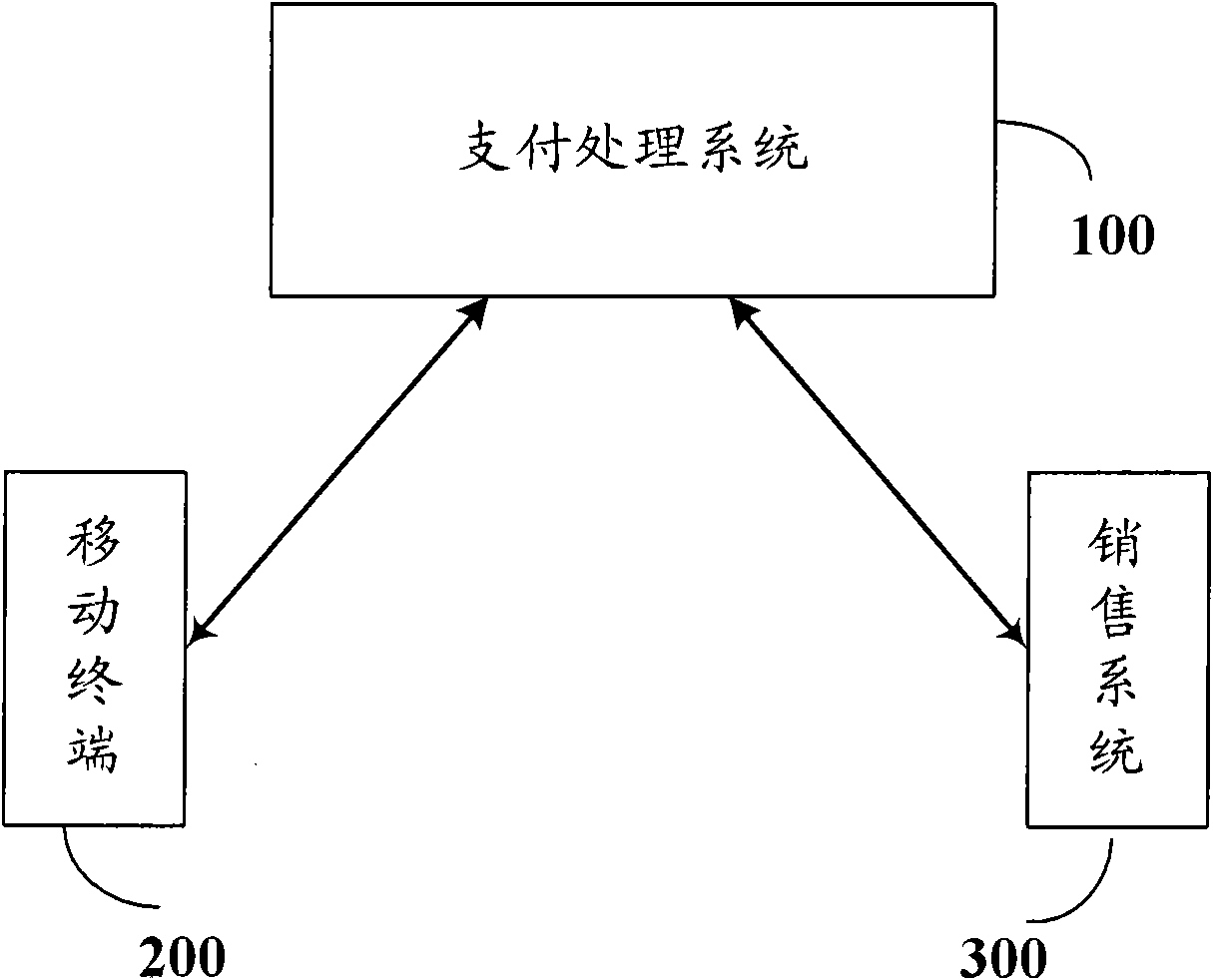
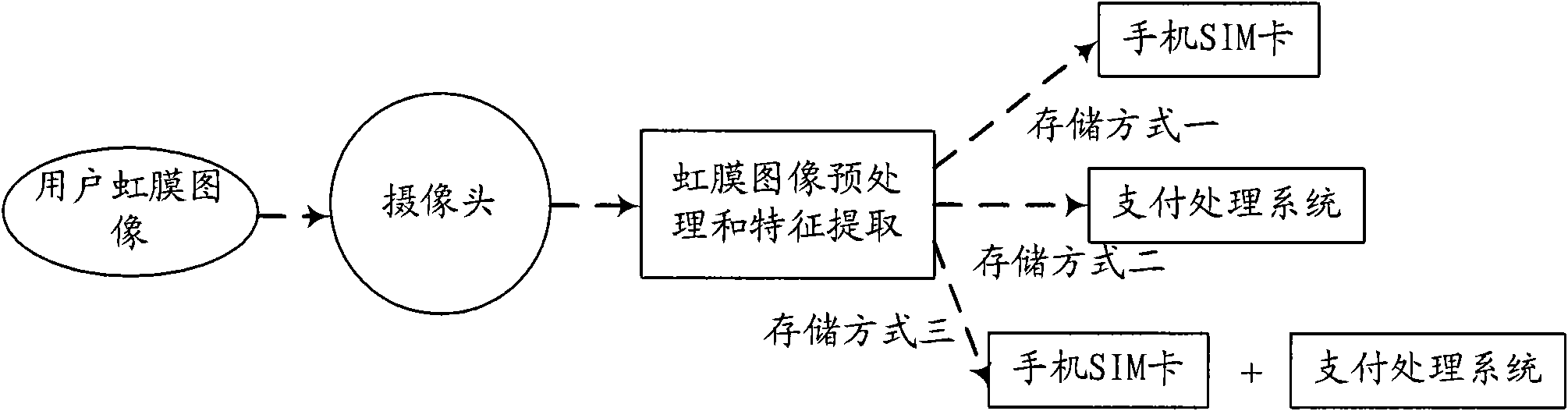
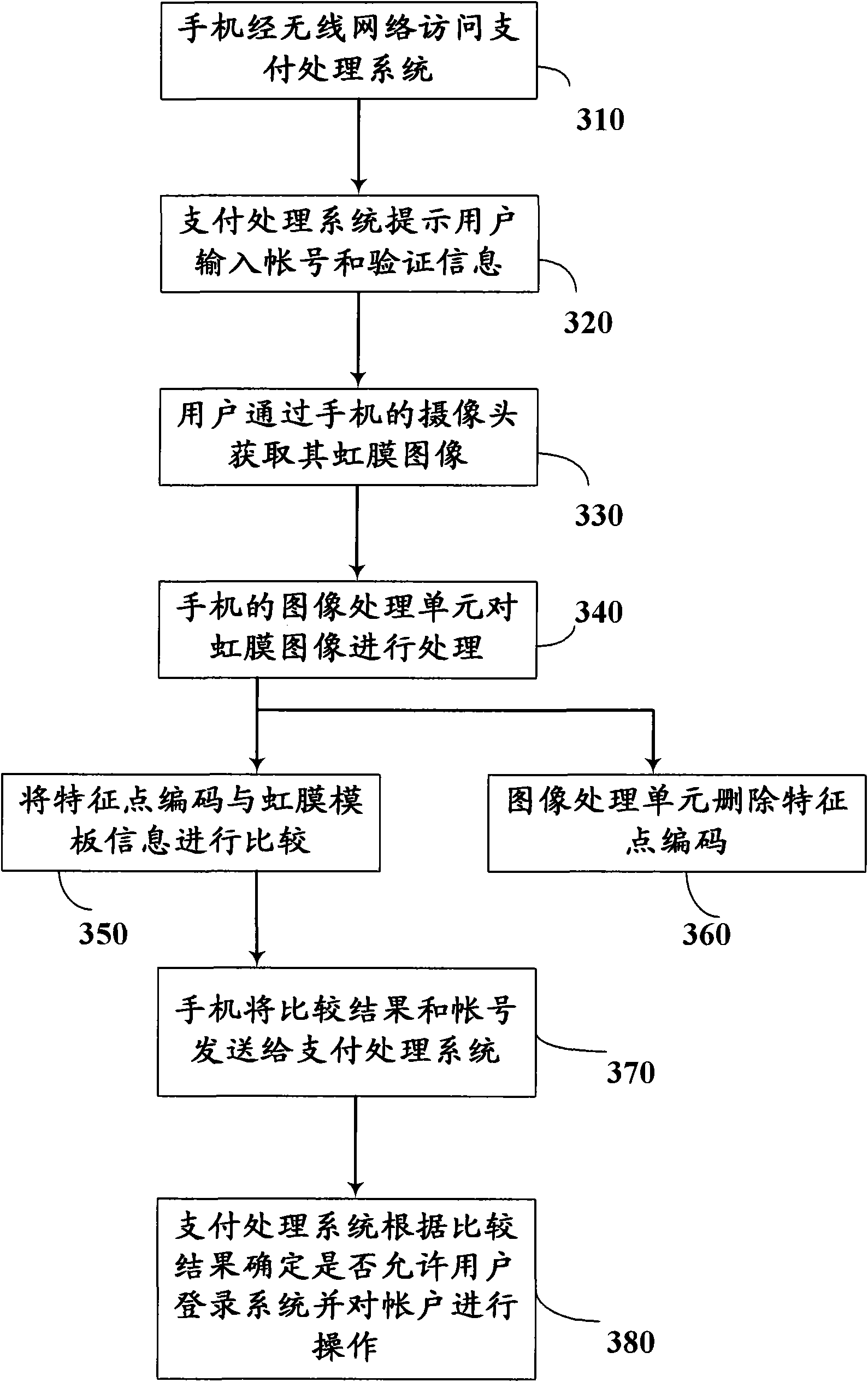
Mobile payment method and equipment for implementing same
InactiveCN102314731AHigh precisionImprove stabilityComplete banking machinesCharacter and pattern recognitionPasswordIris image
The invention relates to an electronic payment technology, in particular to a mobile payment method, and a mobile terminal and a payment processing system for implementing the mobile payment method. According to the invention, the mobile payment method comprises the following steps of: acquiring an iris image of a user by using the mobile terminal which is provided with an image acquisition unit; determining the identity of the user according to the acquired iris image; and with the payment processing system, performing payment processing by using a judgment result. Compared with the conventional mobile payment method, the embodiment of the invention has the advantages that: by using iris information as the authentication information of the identity of the user, the safety of the payment service of a mobile phone is greatly improved; and by using the iris information, the burden on password memorization of the user is eliminated. In the embodiment of the invention, the safety capacity of a smart card technology is fully utilized in the processing of the iris information. Moreover, a camera serves as the standard hardware configuration of the mobile terminal such as the mobile phone, so system hardware can be less modified by using the iris information, stead of password inputting.
Owner:CHINA UNIONPAY
Dice that recognize the values of their own throws and transmit them to computers, with applications to electronic and casino games
InactiveUS20050215312A1ExperienceSmall modificationLottery apparatusVideo gamesElectricityEngineering
Dice are disclosed that detect their state, i.e., their own value once at rest, using for instance gravity, piezoelectricity, or photoelectric cells that are assigned to all faces to recognize the lower face. Said dice preferably transmit said state to a computer. Said computer may be the same that is used for the game that depends on the throw of the dice, or may be used mostly for display as for some casino games. Electricity is used in the die to let it determine its own state and transmit it. Economical protocols of transmission are used such as Bluetooth. Such dice may securely send alerts whenever deviations from a fair distribution of the outcomes is detected and can monitor small modifications of their balance to maintain their fairness. Part or all of the teaching can be realized as MEMS (micro electro-mechanical systems) or NEMS (nano electromechanical systems) modifications of usual dice.
Owner:TRESSER YUVAL ARIE +1
Data access method, module, processor and terminal device for hybrid memory
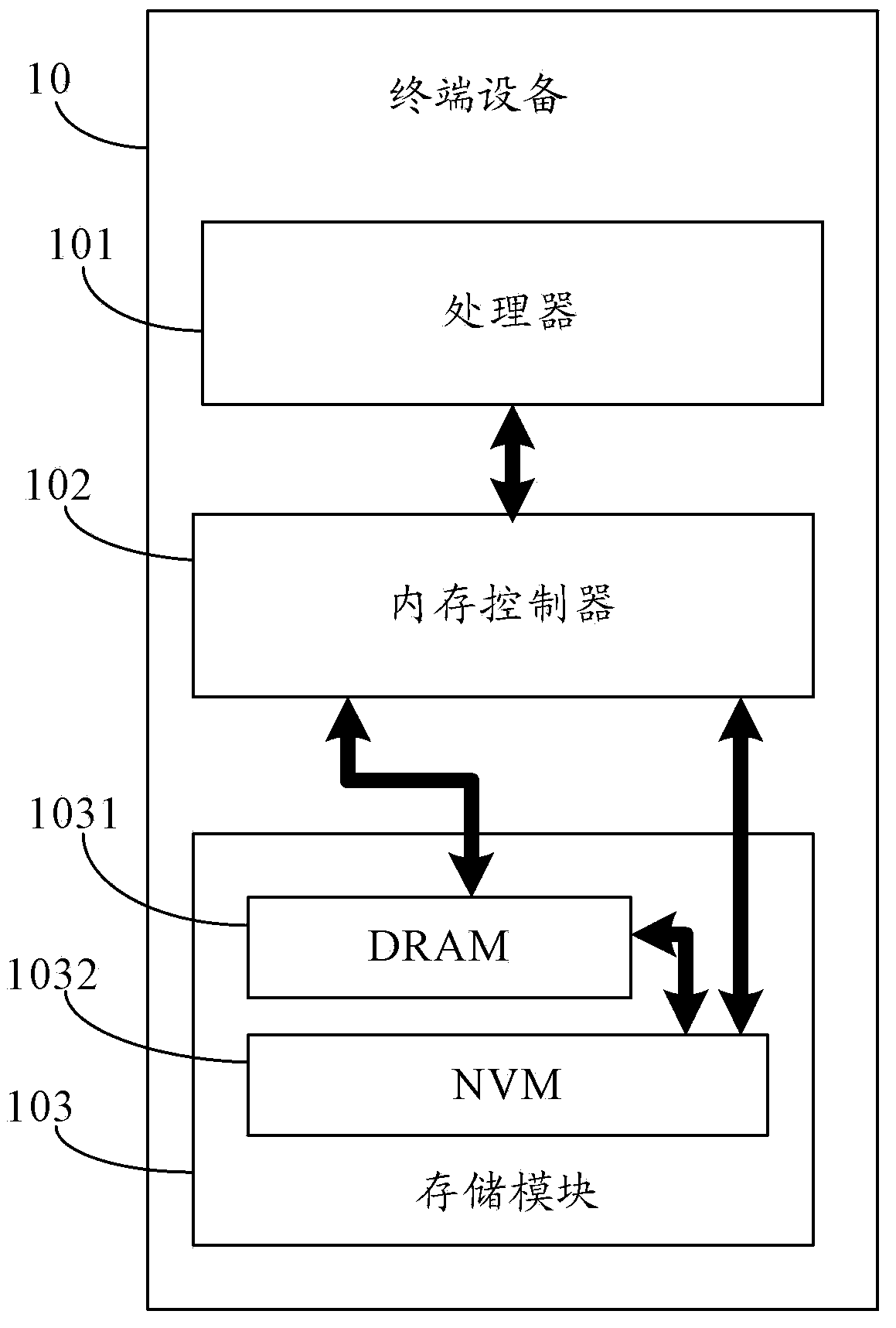
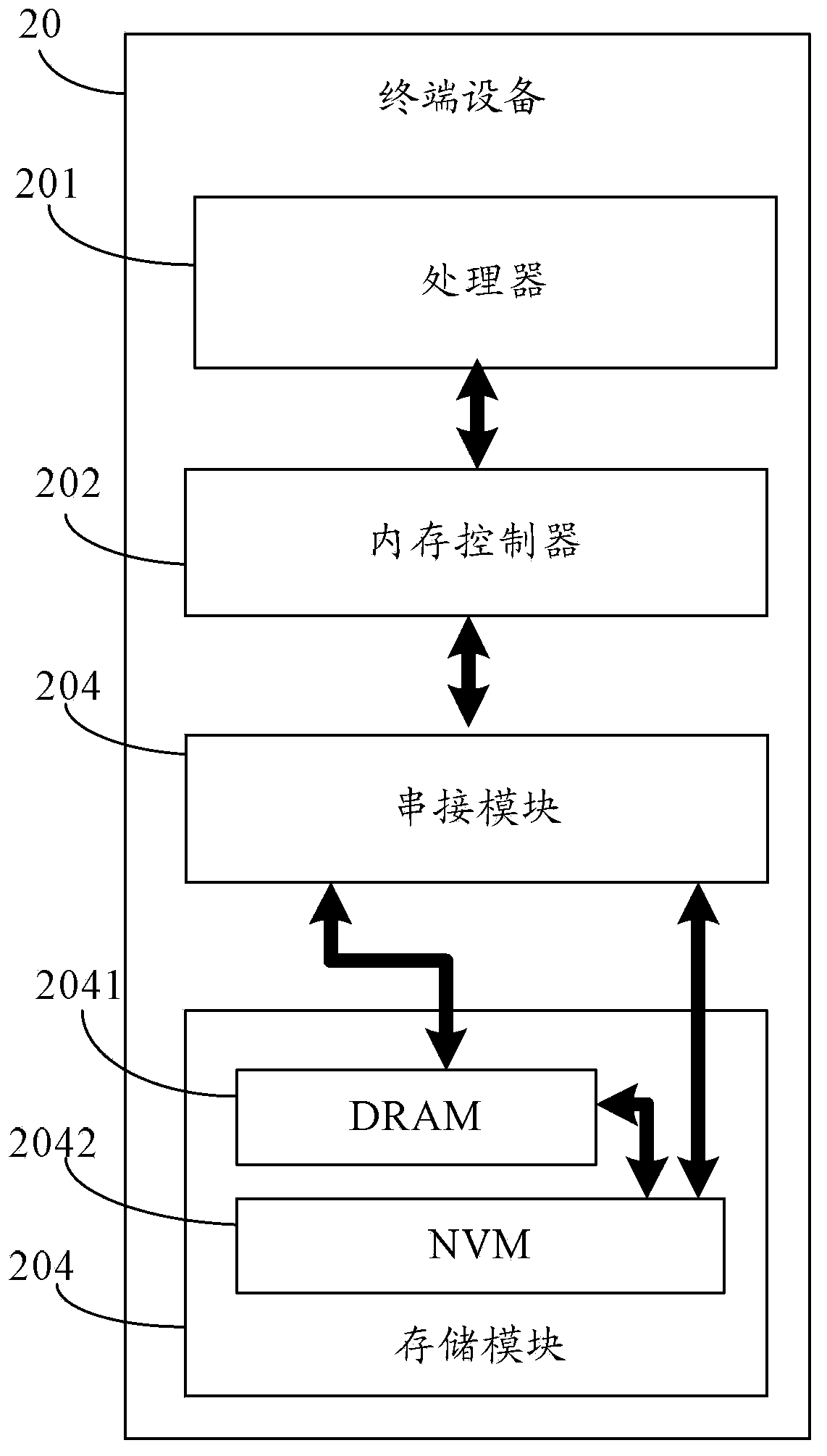
ActiveCN104346293AReduce redesignSmall modificationMemory adressing/allocation/relocationRedundant data error correctionAccess methodData access
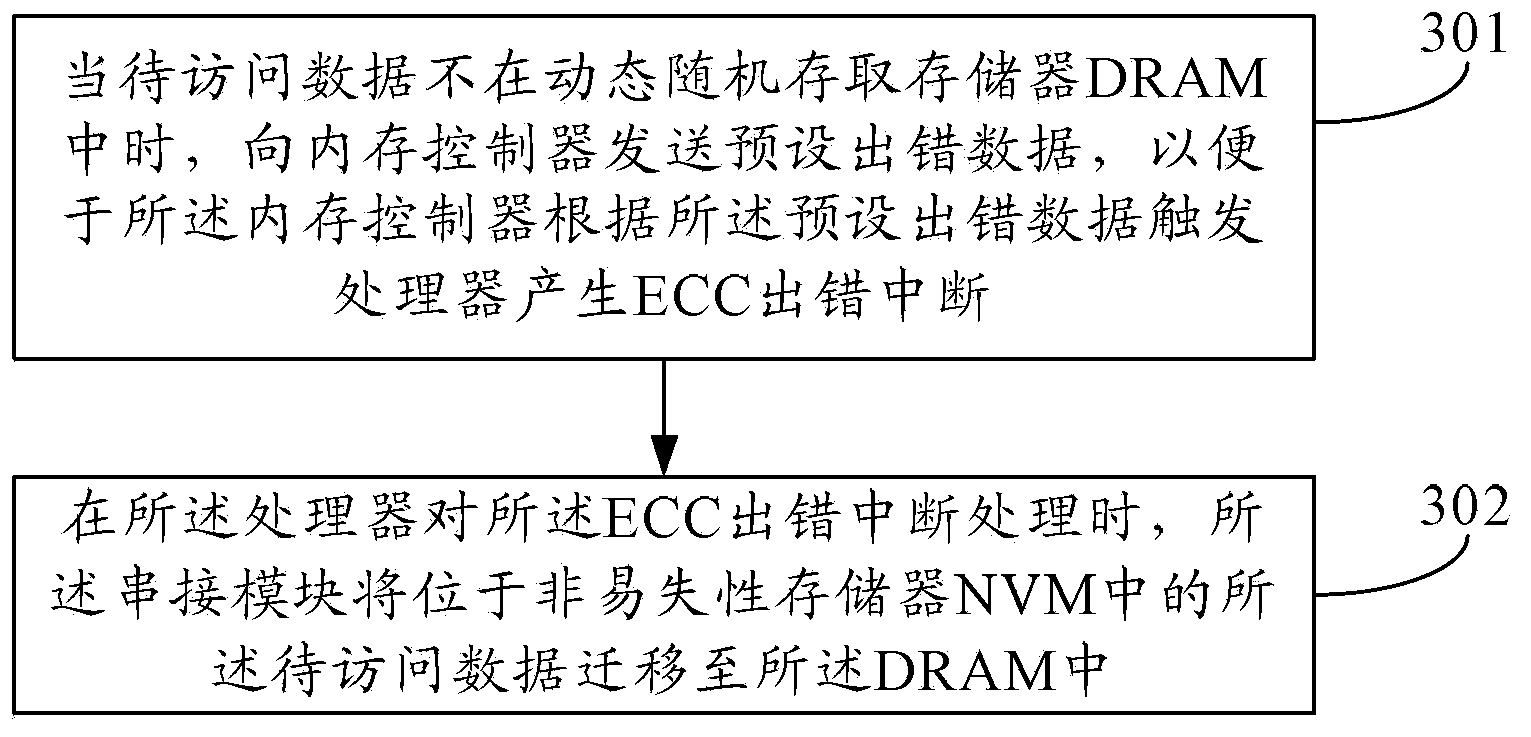
The present invention relates to the field of computers. Provided are a hybrid memory data access method, module, processor and terminal device, capable of simplifying the data access process, the method comprising: when the data to be accessed is not in the dynamic random access memory (DRAM), sending preset error data to a memory controller, so that the memory controller triggers a processor according to the preset error data to generate an error correction code (ECC) error interrupt, the data to be accessed being the data in a data access request; while the processor is handling the ECC error interrupt, a concatenation module transfers the data to be accessed in the non-volatile memory (NVM) to the DRAM. The data hybrid memory access method, module, processor and terminal device are used for hybrid memory data access.
Owner:HUAWEI TECH CO LTD +1
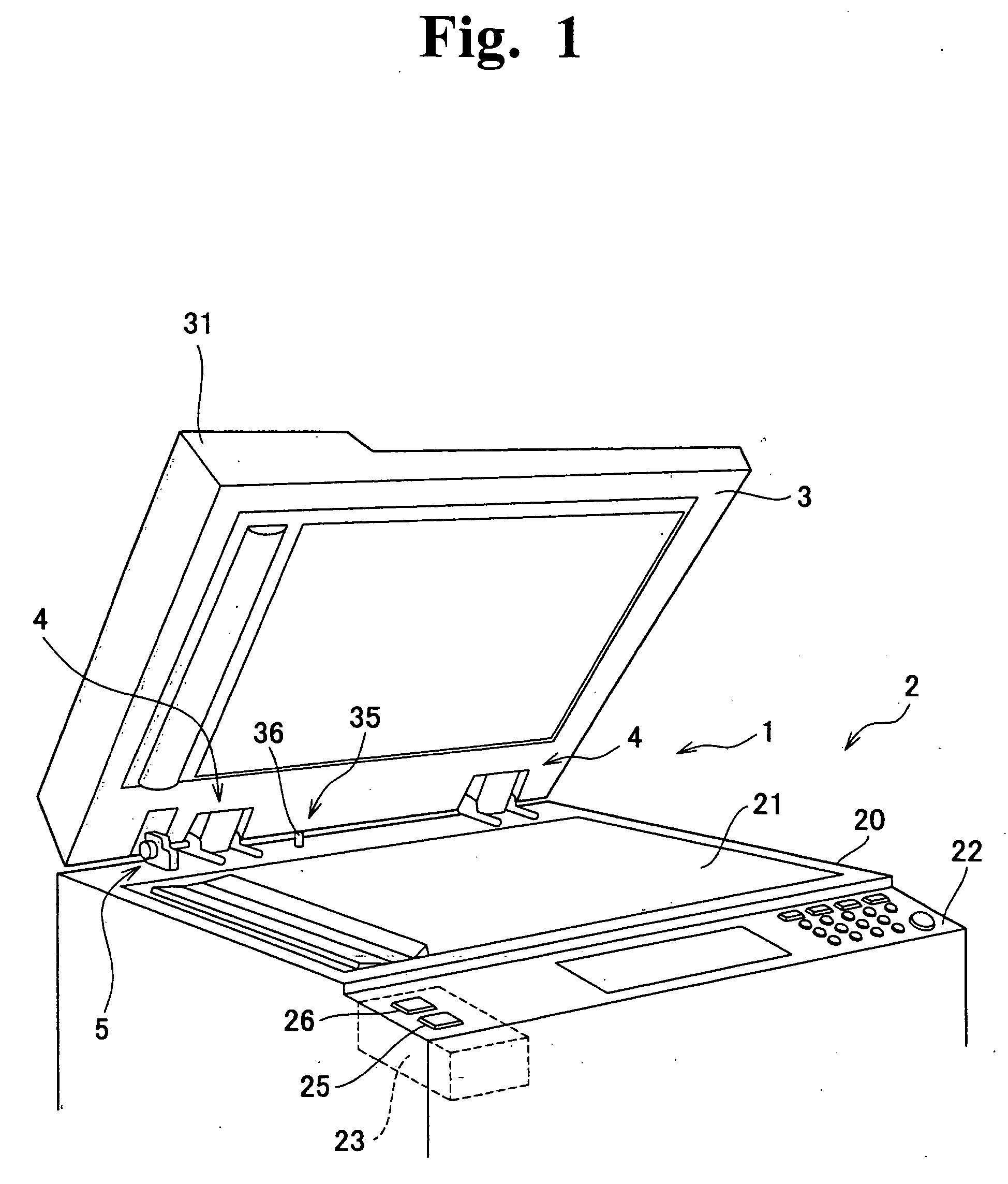
Automatic original cover closer and office equipment including automatic original cover closer
InactiveUS20060180972A1Practical to useSmall modificationElectrographic process apparatusArticle feedersDrive shaftDrive motor
An automatic original cover closer to practically realize an automatic opening and closing function of an original cover, has a hinge part to rotatably support an original cover to the main body of office equipment and a driving part to automatically drive the hinge part. The hinge part includes a mounting member to mount on the main body and a supporting member to support the original cover to be axially supported to this mounting member so as to be rotatable with a rotary shaft via the rotary shaft. The driving part includes a positively and reversely rotatable drive motor and a power transferring mechanism to decelerate and transfer the rotary driving power of this drive motor to a is drive shaft. The rotary driving power of the drive motor is transferred to the supporting member via the drive shaft and the rotary shaft, by connecting the rotary shaft to the drive shaft.
Owner:KEM HONGKONG
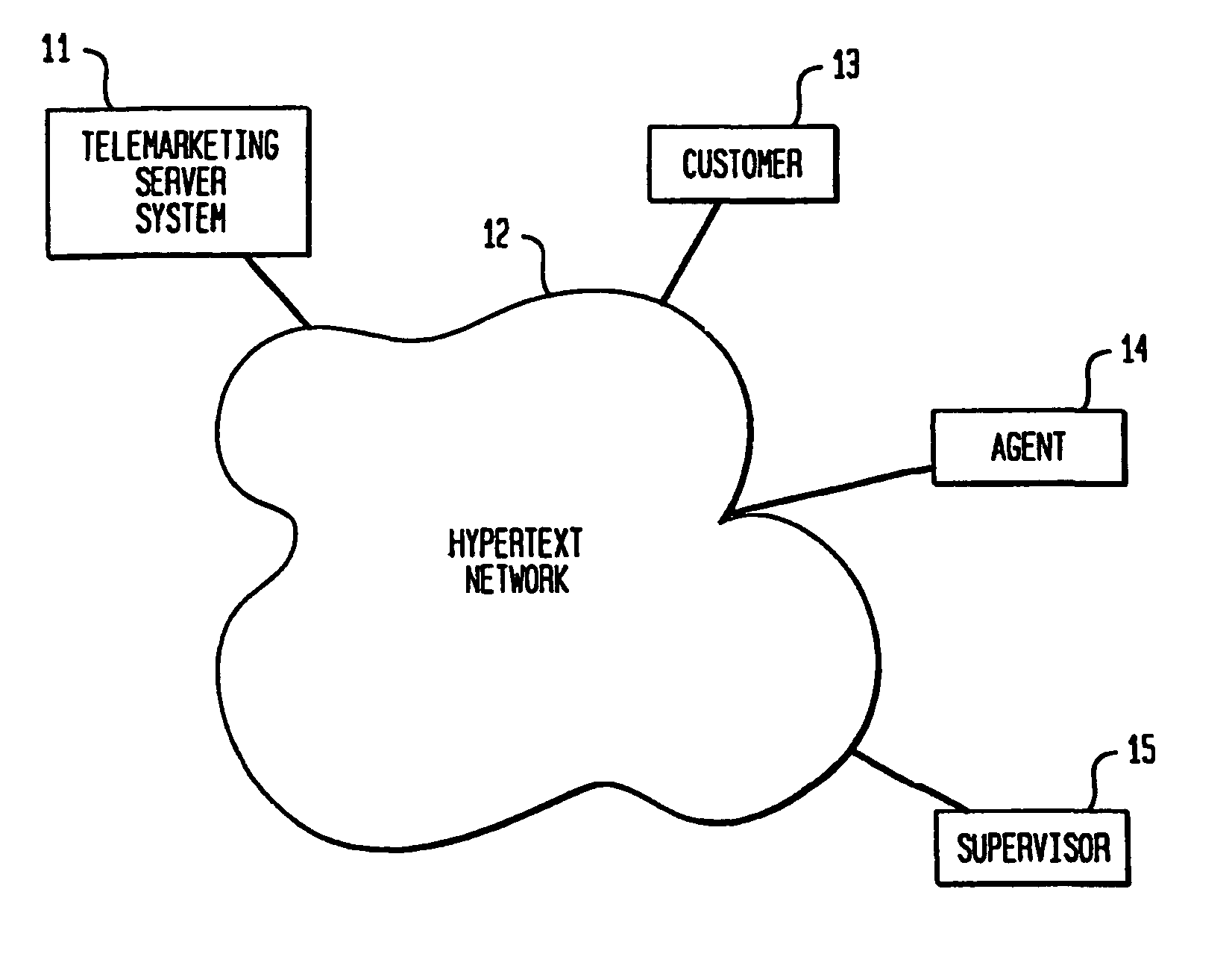
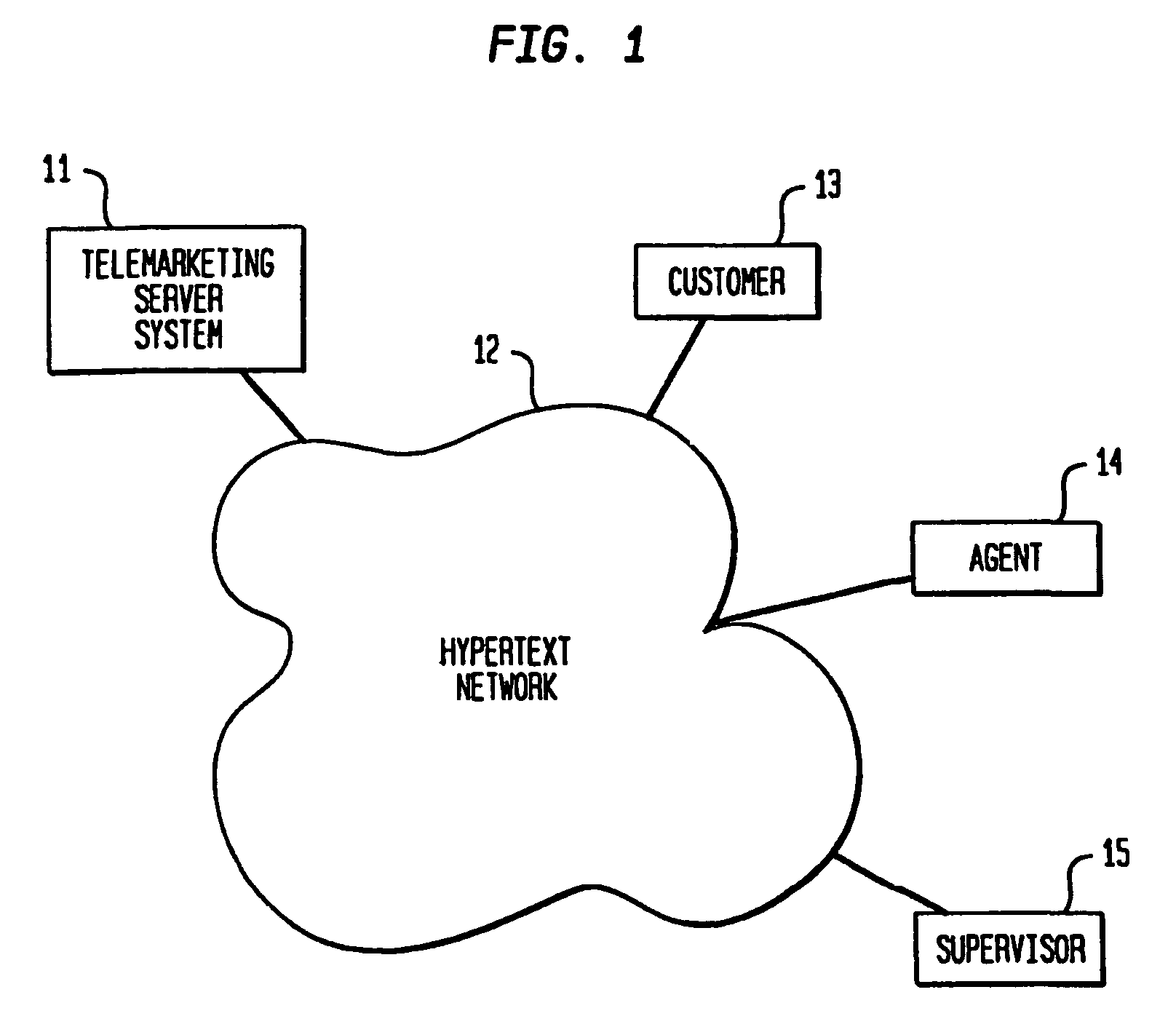
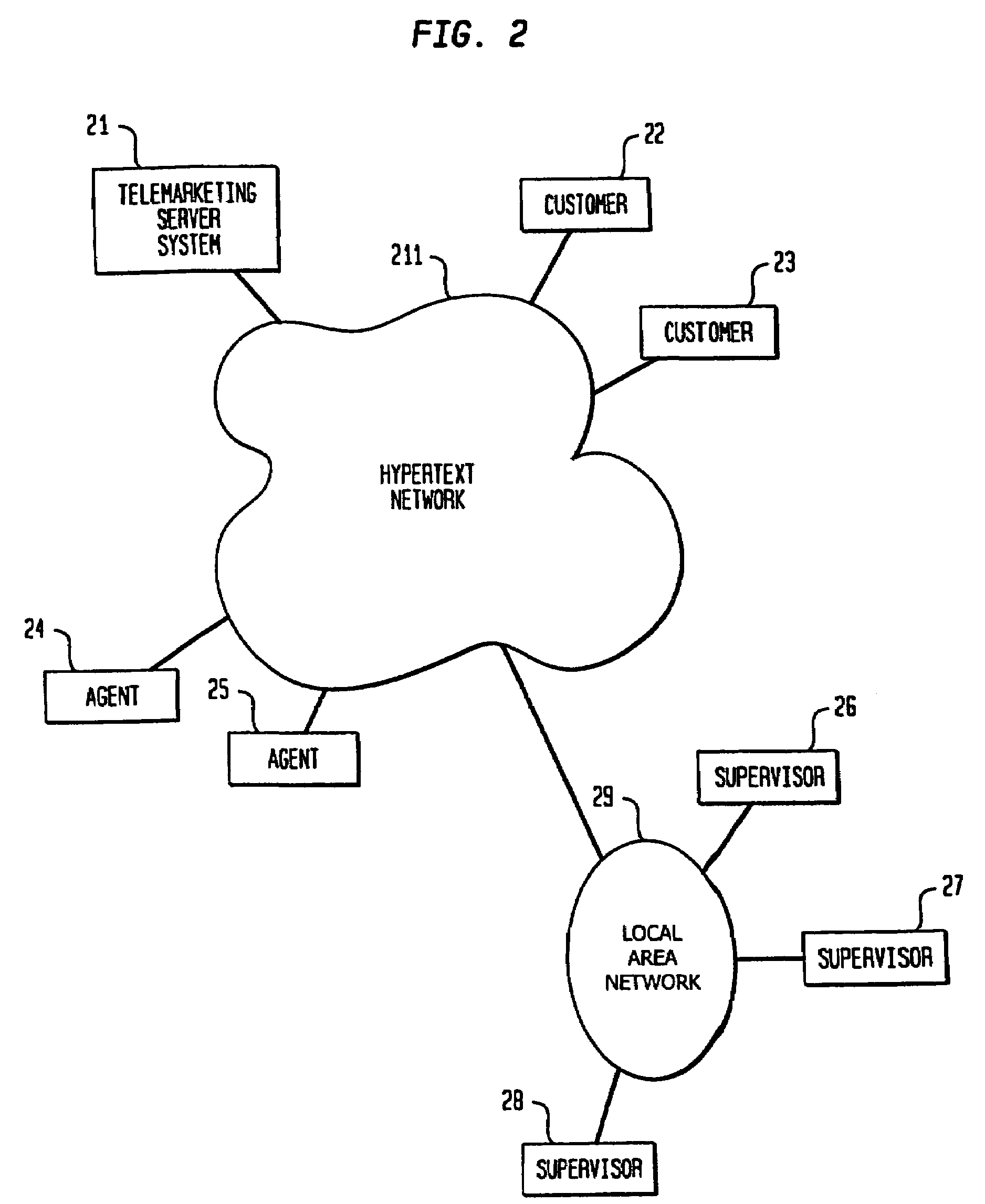
System and method for telemarketing through a hypertext network
InactiveUS7085366B2Reduce complexitySmall modificationSpecial service for subscribersSupervisory/monitoring/testing arrangementsServer systemTelephony
A system and method for providing telemarketing services through a hypertext network that interconnects a telemarketing server system with a customer computer and an agent computer. The telemarketing server accepts a telemarketing request from the customer, and forwards the request to the agent if the agent is available, and to a queue if the agent is not available. When an agent receives a request, communications are either established between the customer and agent at once, or else scheduled for a later time. Telemarketing functions are implemented separately from media transport functions through a hypertext network such that the need for geographic centralization of telemarketing agents is eliminated.
Owner:META PLATFORMS INC
Screen printing process
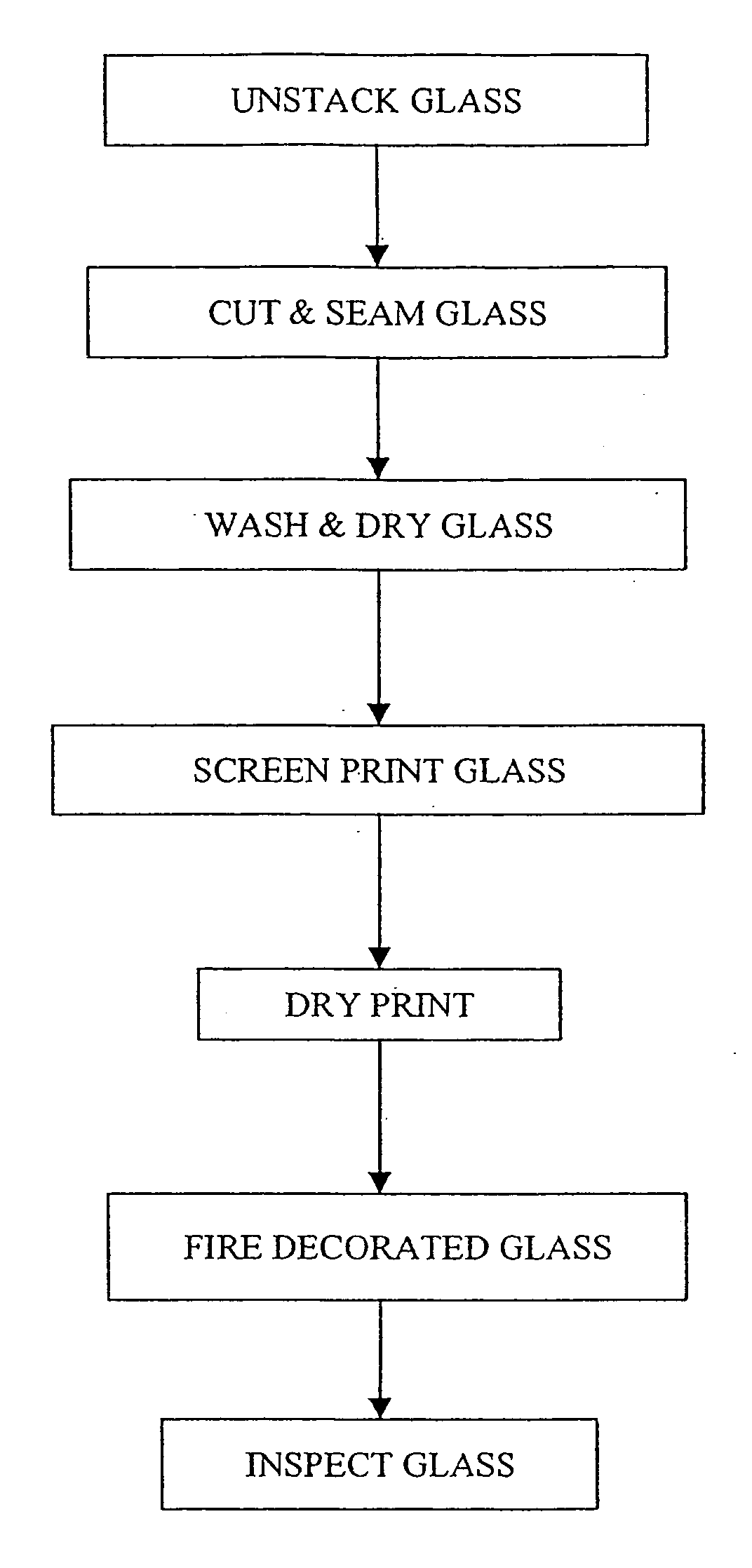
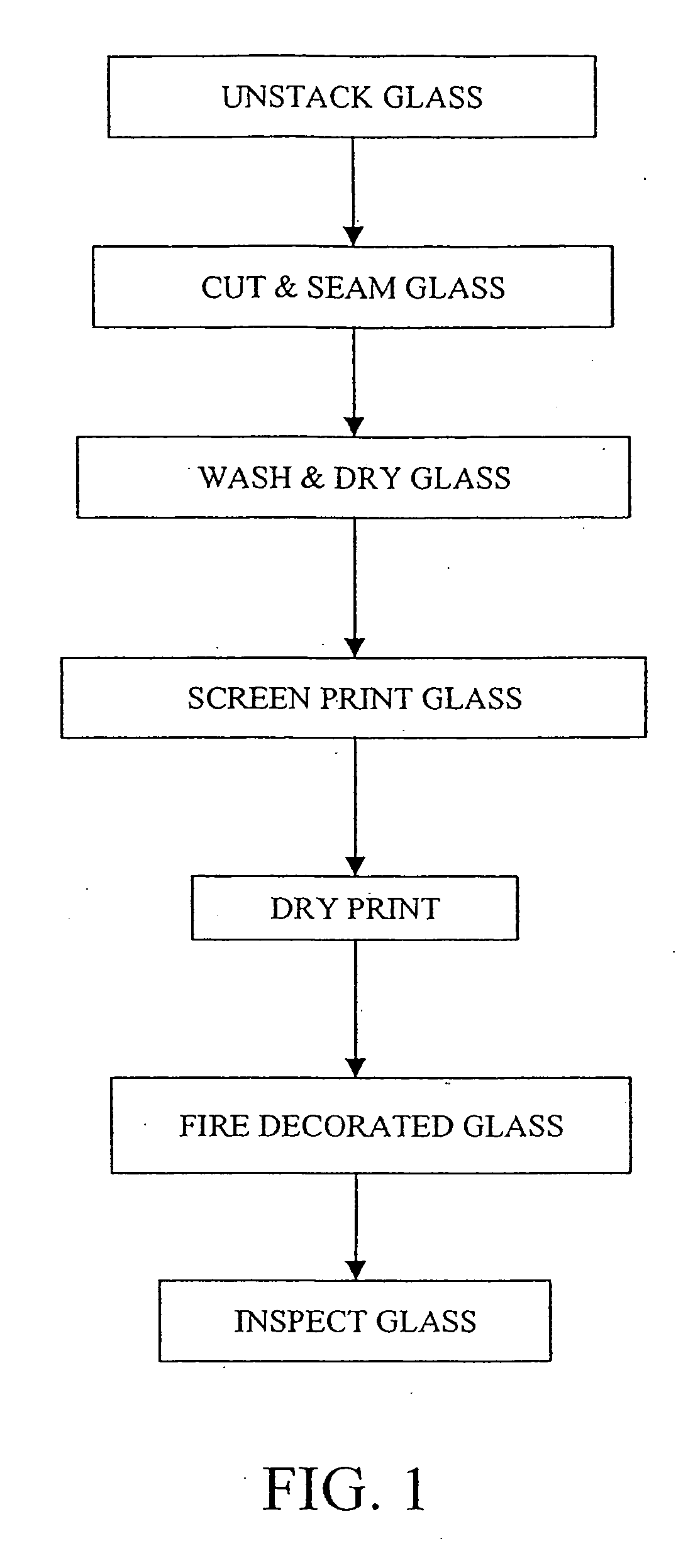
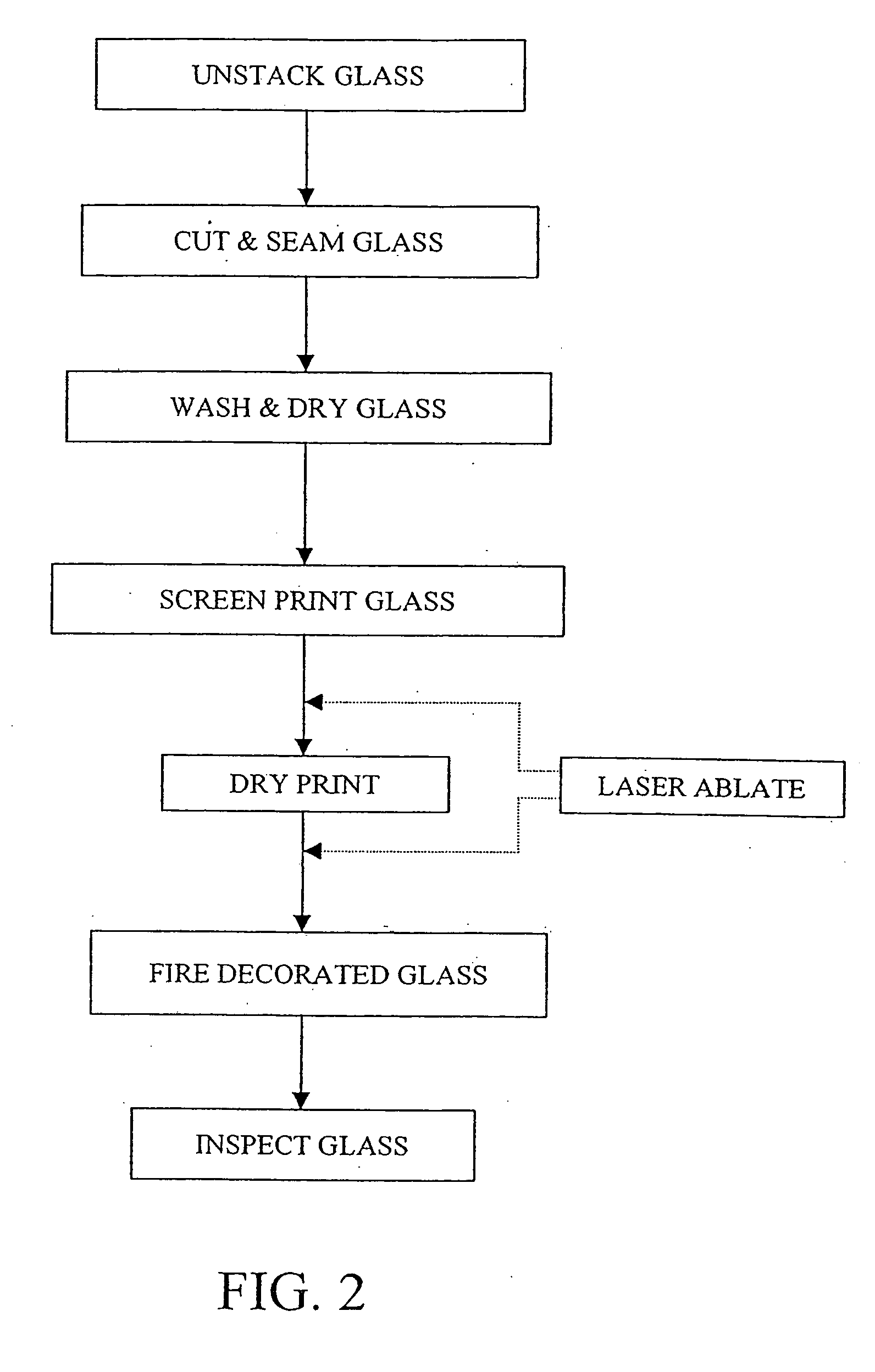
InactiveUS20060112729A1Small modificationDecorative surface effectsPrinted circuit manufactureScreen printingEngineering
A method of screen printing and laser ablating various types of substrates is disclosed. The process may be used to make decorated auto glass with additional indicia such as serial numbers, bar codes, and the like. The substrate with the applied coating may subsequently be shape formed and / or heat strengthened to produce a final product. The invention also provides a screen and a screen printed pattern which include a portion that is subsequently laser ablated to provide specific information such as serialization. In one embodiment, the screen printed and laser ablated glass substrate is fired. In another embodiment, screen printed patterns may be laser ablated with no subsequent heat treatment required.
Owner:FERRO COLOR & GLASS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com