Key IP address safety alarm association analysis method based on fuzzy scene
A security alarm and correlation analysis technology, applied in digital transmission systems, electrical components, transmission systems, etc., can solve the problems of insufficient correlation analysis ability of massive security alarm events, and achieve good detection and analysis, good portability, good detection and stability. The effect of analytical skills
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] The present invention will be described in detail below in conjunction with the accompanying drawings.
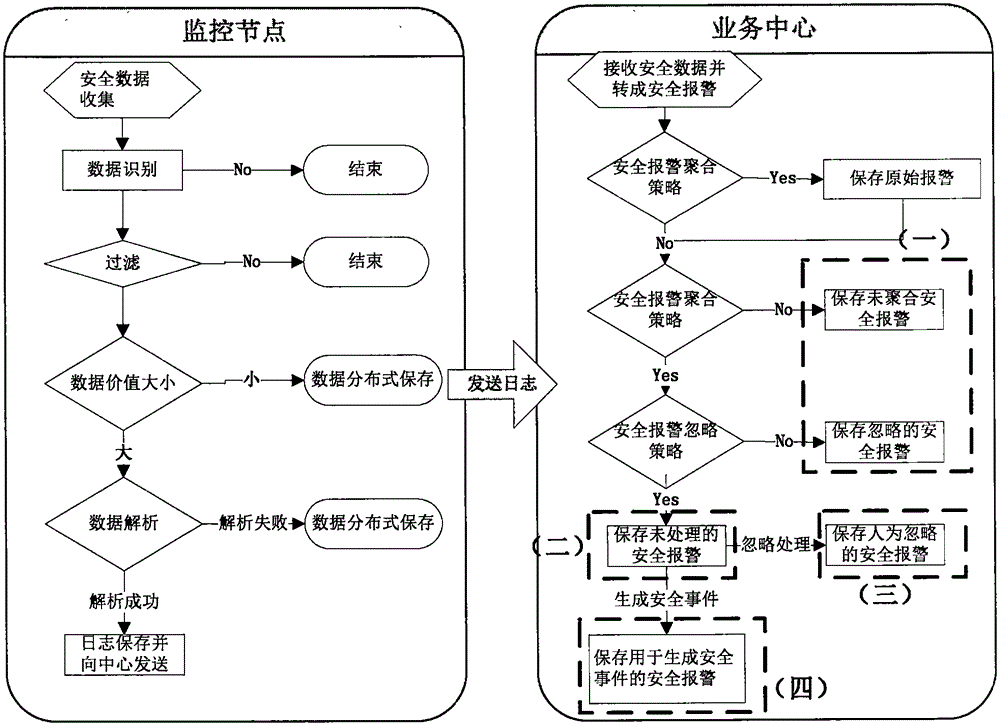
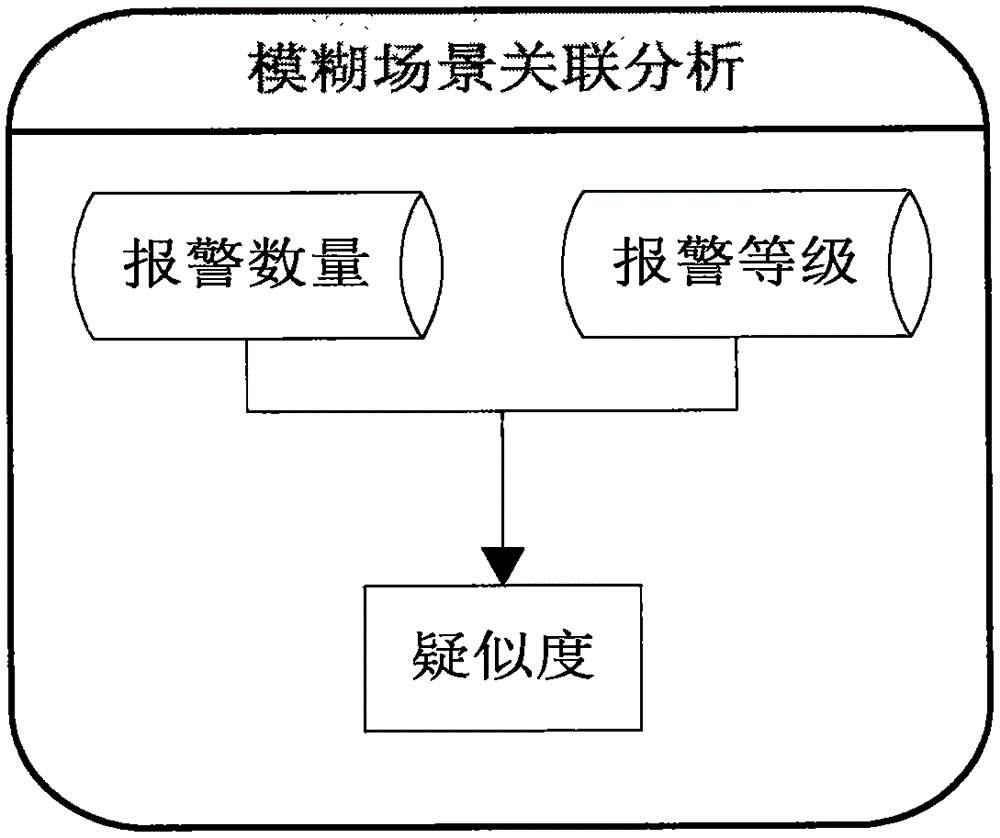
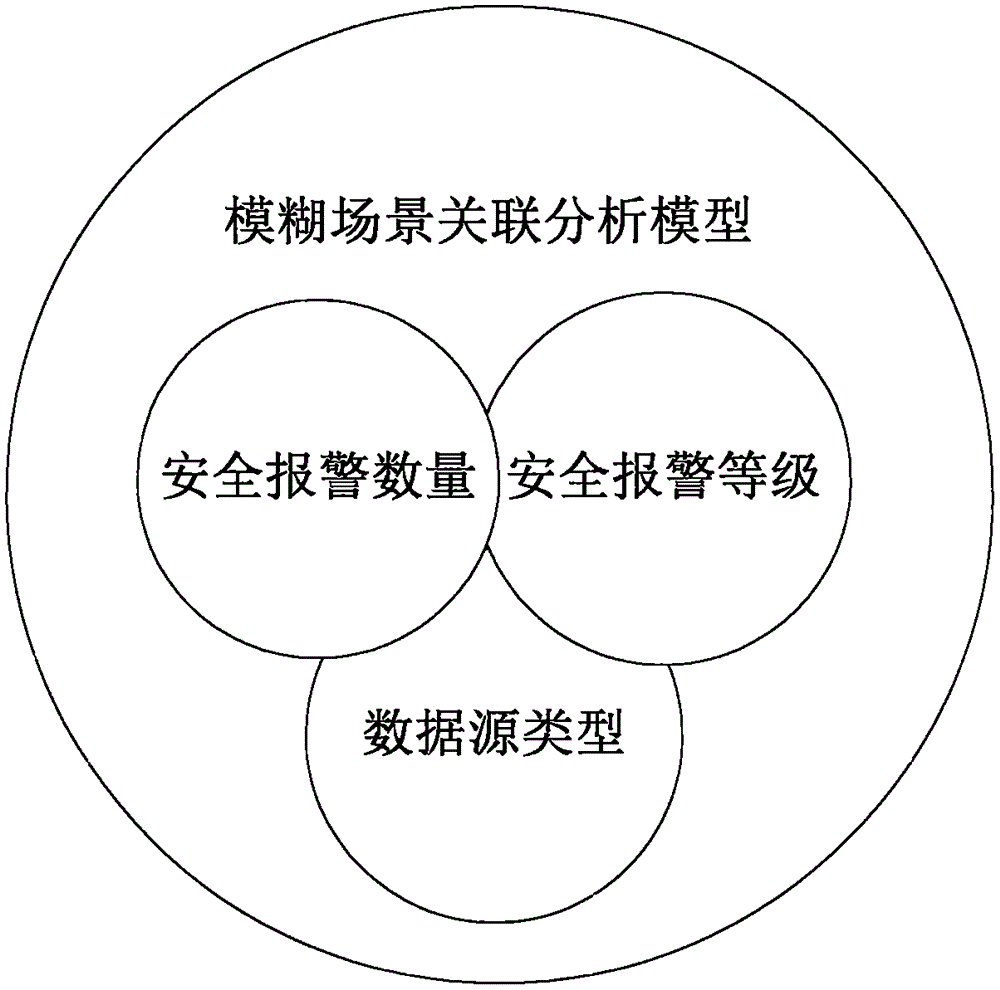
[0042] Such as Figure 1 to Figure 4 As shown, a key IP address security alarm correlation analysis method based on a fuzzy scene, the correlation analysis method includes the following steps: the present invention proposes a correlation analysis method based on a fuzzy scene for a large number of security alarm events, and first uses a statistical method to report to the police Aggregation, then use the policy to ignore and filter the alarm, and finally use the correlation algorithm based on the fuzzy scene to calculate the event suspicion corresponding to the source IP (destination IP), and use the big data analysis method to analyze the alarm log related to the suspected IP Perform statistical queries. According to the size and sorting of the degree of suspicion, managers can have an intuitive understanding of the current network status. Based on the results of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com