Security protection performance evaluation method applicable to core network of wireless power private network
A security protection and wireless private network technology, applied in security devices, wireless communications, electrical components, etc., can solve problems such as leakage of sensitive information, damage to physical protection measures, and tampering of configuration information, so as to improve security protection capabilities and be easy to implement , the effect of preventing security threats
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0051] The present invention will be further described below. The following examples are only used to illustrate the technical solution of the present invention more clearly, but not to limit the protection scope of the present invention.
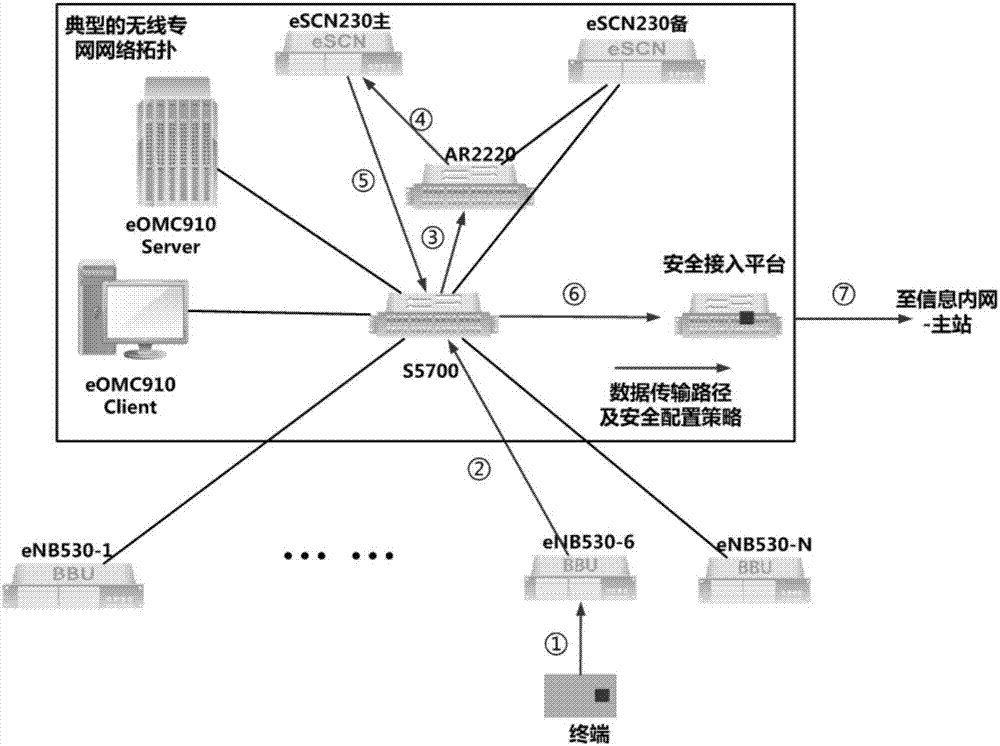
[0052] Before evaluating the security protection performance of the core network of the electric power wireless private network, firstly, according to figure 1 Build a wireless private network test environment, including terminals, several base stations (eNB530-1—eNB530-N in the figure), switches (S5700 is used in this invention), a security encryption gateway (AR2220 is used in this invention), core network (this The invention uses eSCN230), the network management server eOMC910Server, the network management client eOMC910Client, and the secure access platform (the present invention uses NARIUSAP3000-AG), wherein the terminal is connected to the base station, the base station is connected to the switch, the switch is connected to the secur...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com