Patents
Literature
395 results about "Network management application" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
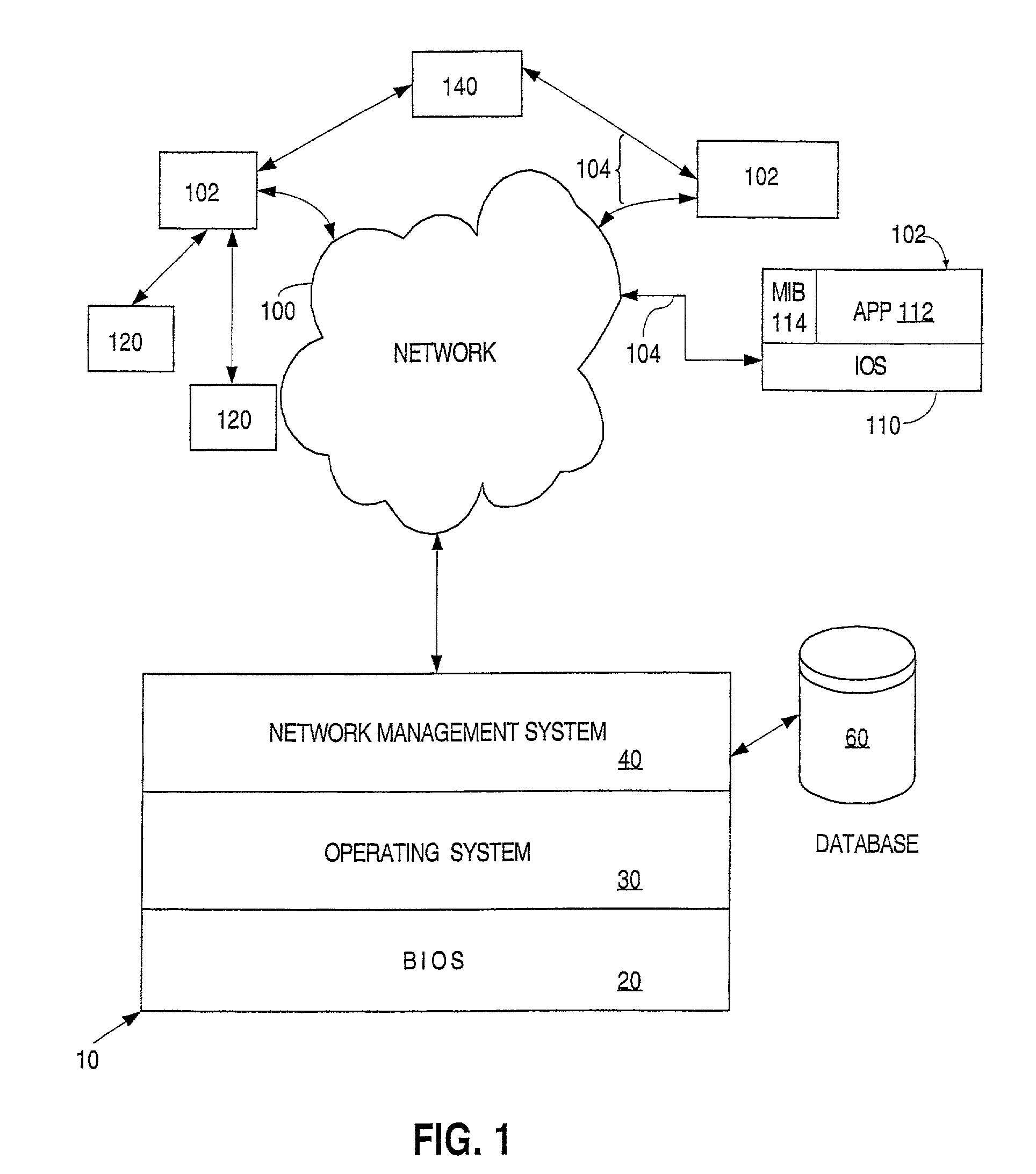
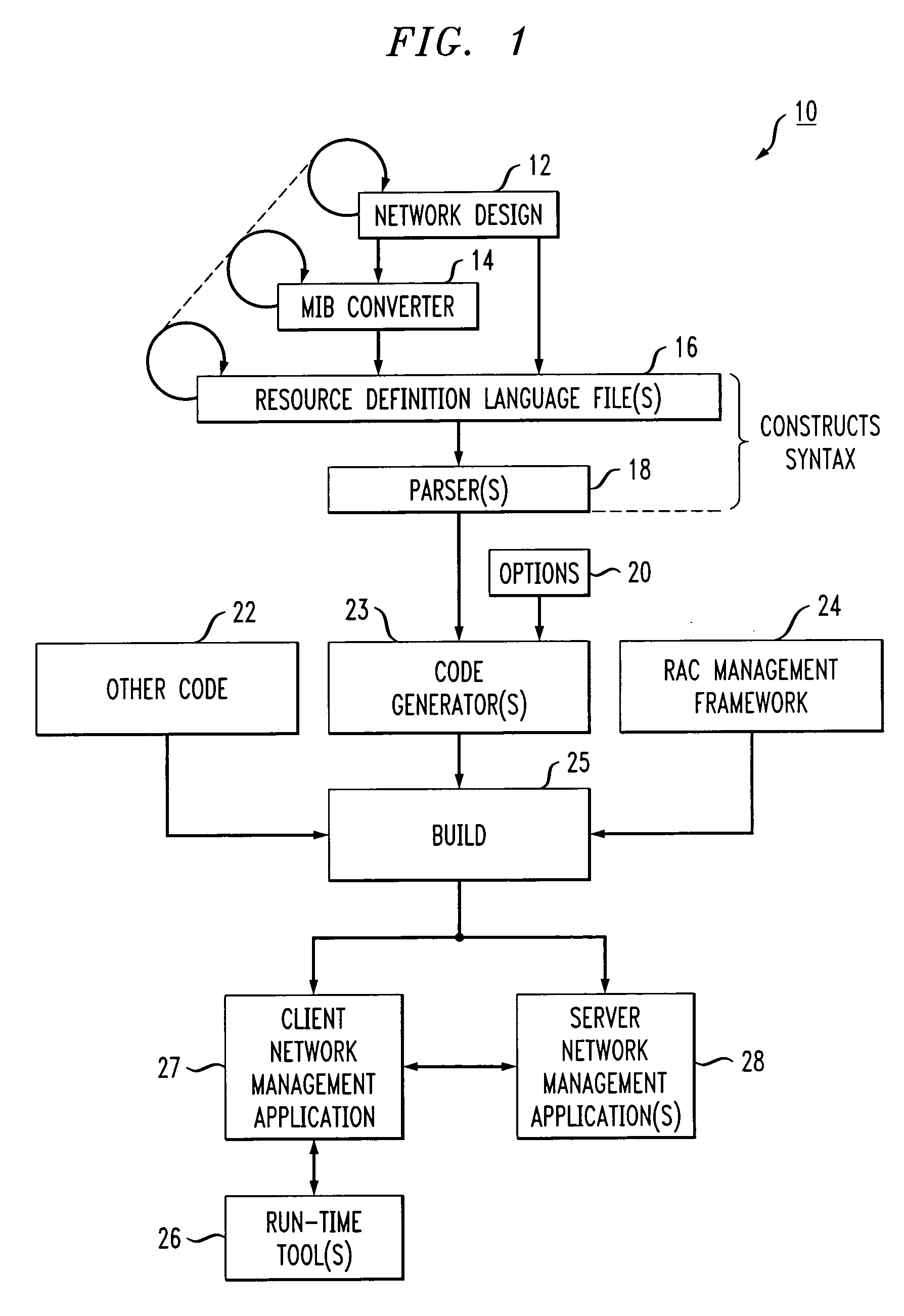
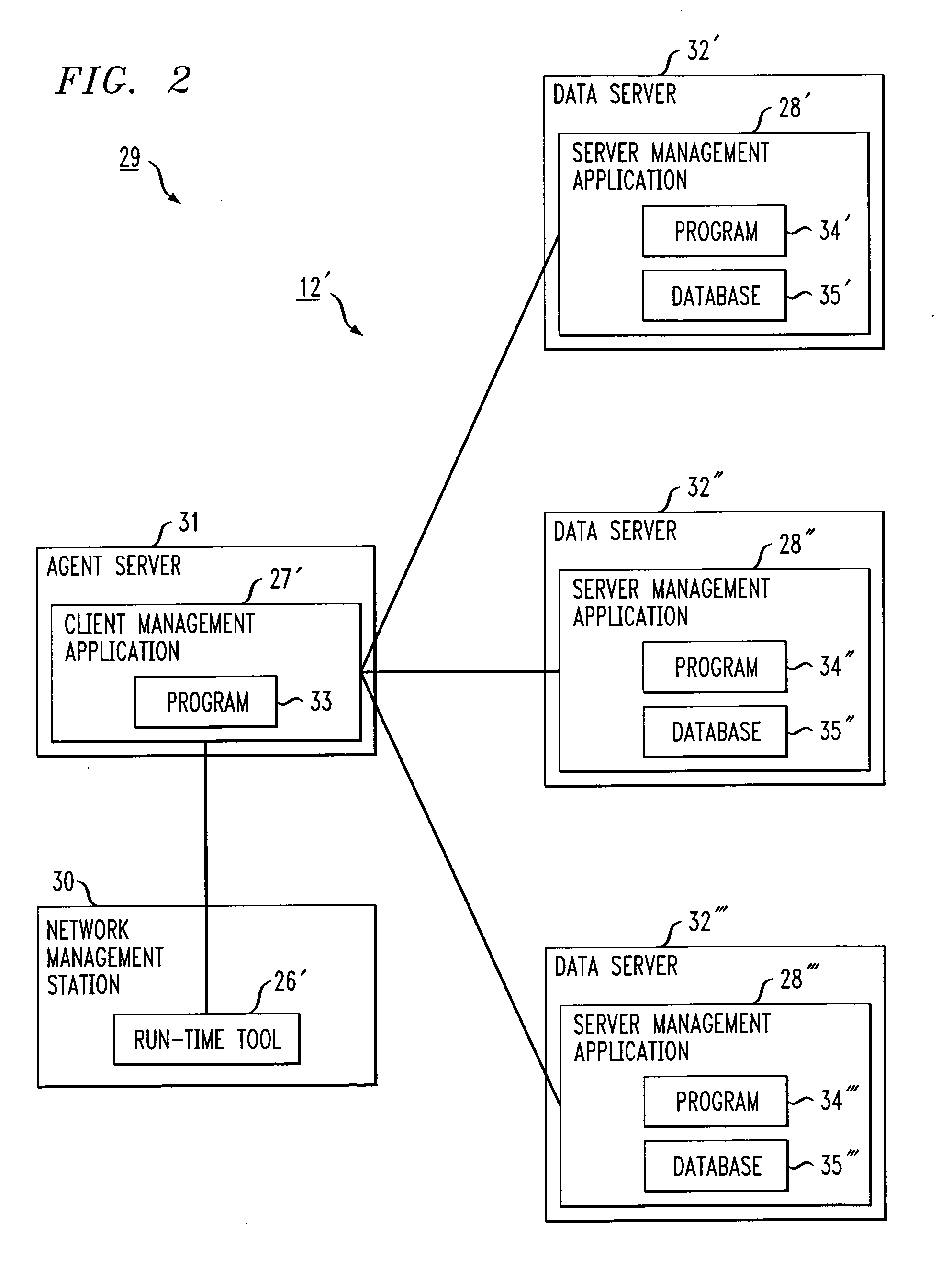
In the network management model, a network management application (NMA) is the software that sits on the network management station (NMS) and retrieves data from management agents (MAs) for the purpose of monitoring and controlling various devices on the network. It is defined by the ISO/OSI network management model and its subset of protocols, namely Simple Network Management Protocol (SNMP) and Common Management Information Protocol (CMIP).we can retrieve the agent data by the help of it.
Method and apparatus for displaying health status of network devices
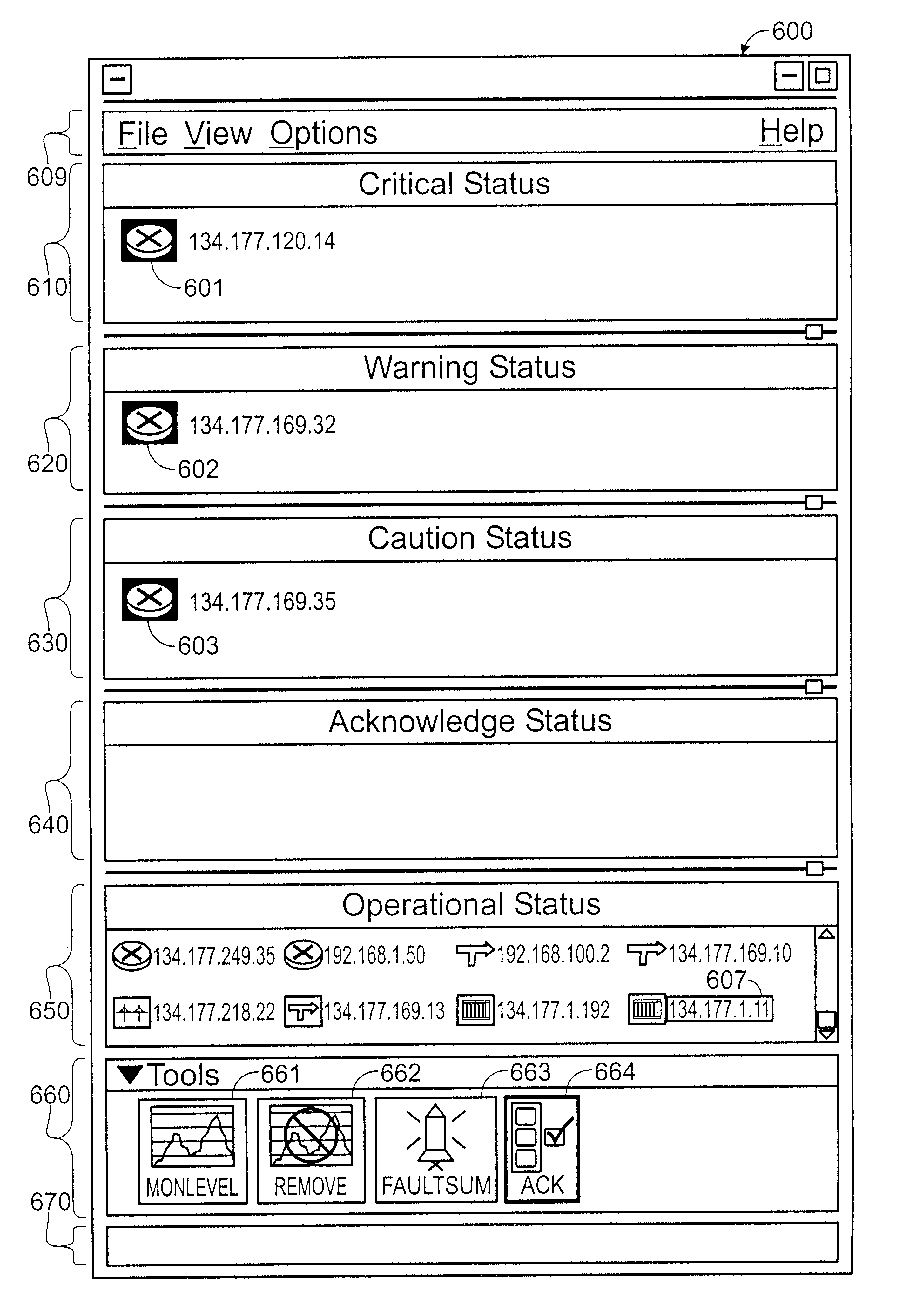
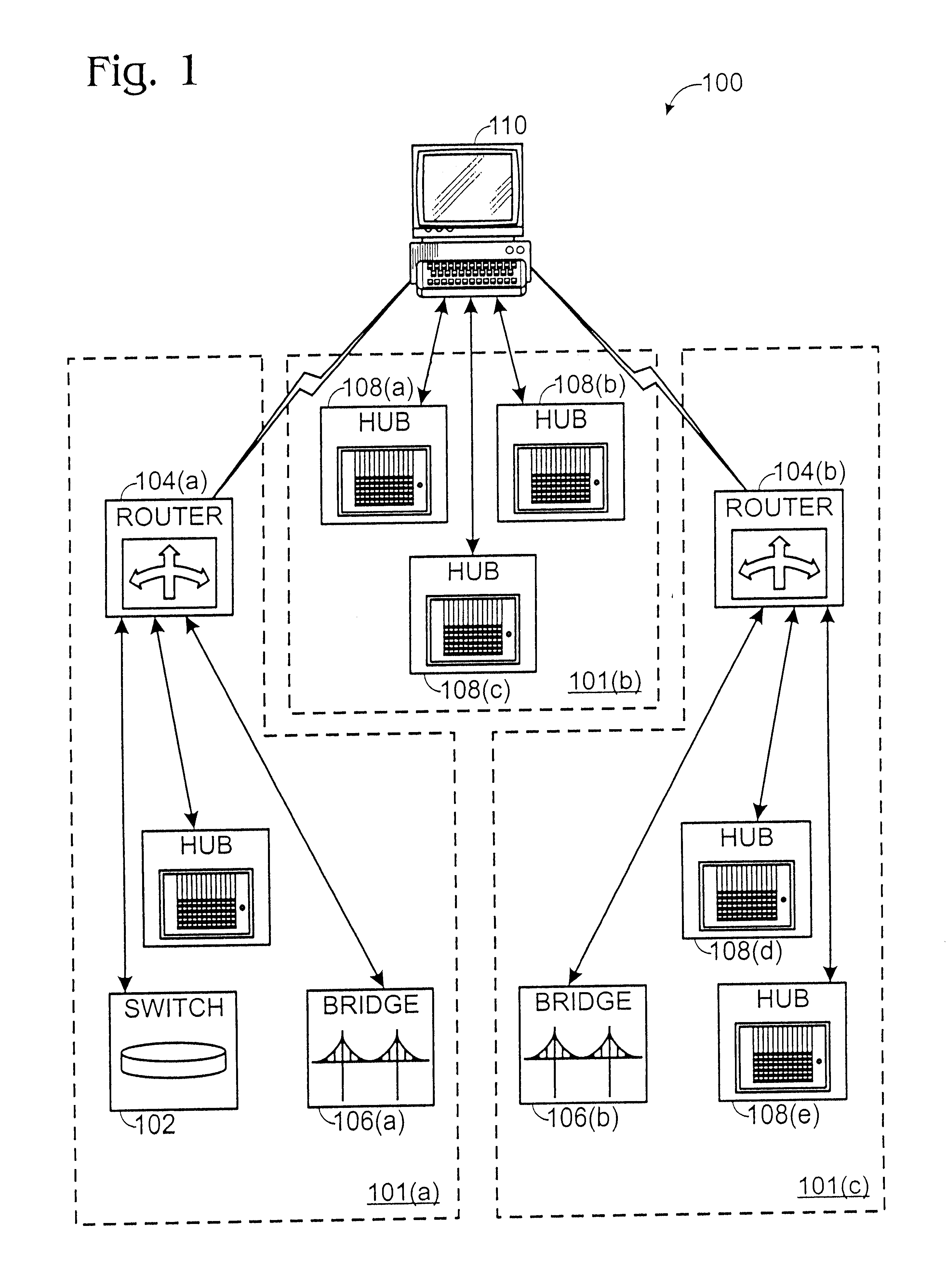
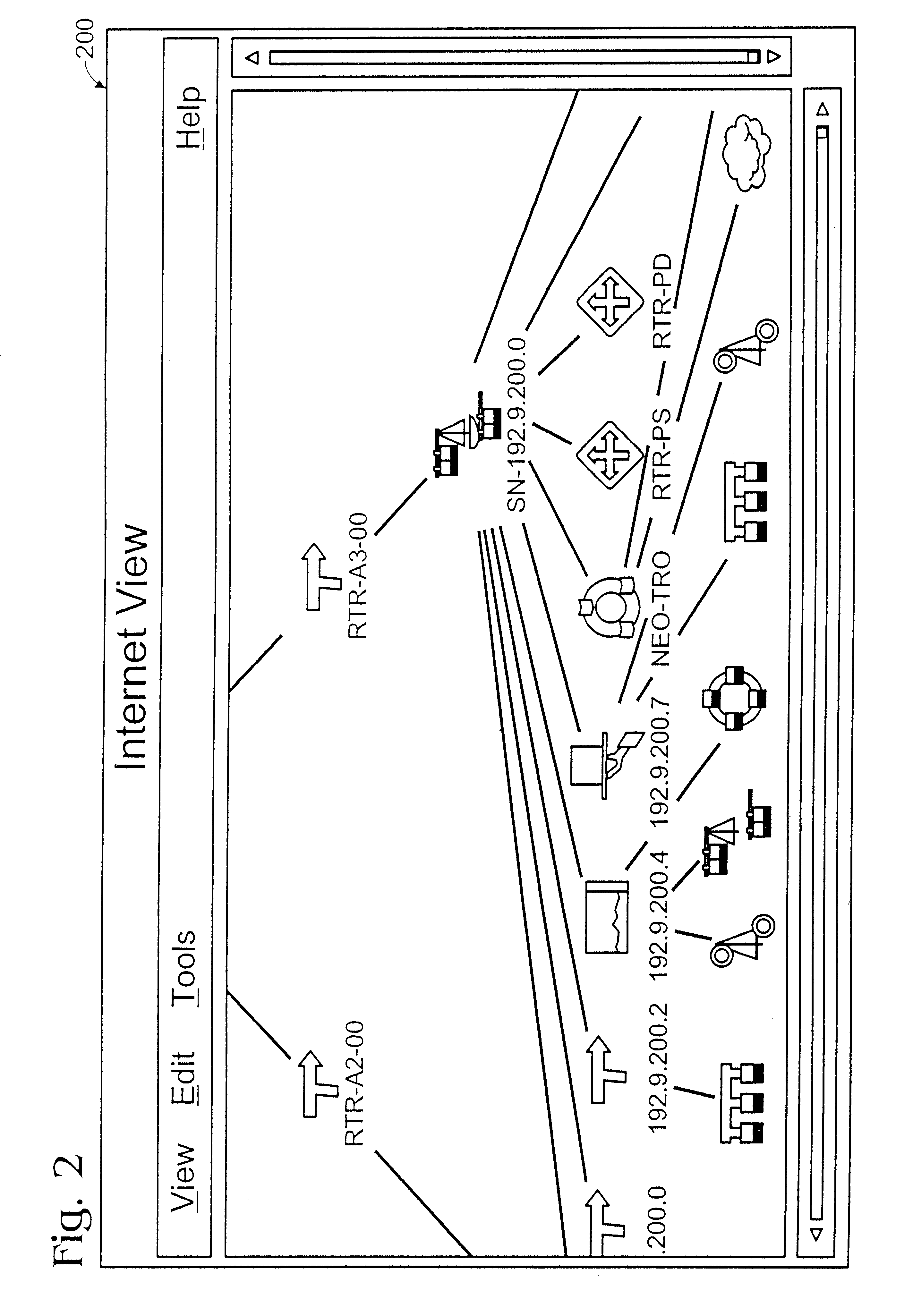
A method and apparatus for concurrently displaying from a single window on a network management station the health status of all network devices and objects of a computer network. The network devices may be categorized according to state or device type, as determined by the network manager. The method and apparatus provides a network manager with the ability to determine the current state of network devices and objects within an enterprise network and invoke further actions such as configuration, performance, fault, and security management tasks. The network manager can drag and drop icons from one network management system application window to another network management system application window to obtain fault information about network devices and objects, thus allowing multiple network management system applications to run concurrently on the same network management station. The network manager is further able to add new network devices and objects by dragging site, folder or device icons from one network management system application window to a second network management system application window for displaying the health status of the new devices. The dragged-in devices are added to the appropriate status panes within the second window according to the method of the present invention.
Owner:NORTEL NETWORKS LTD
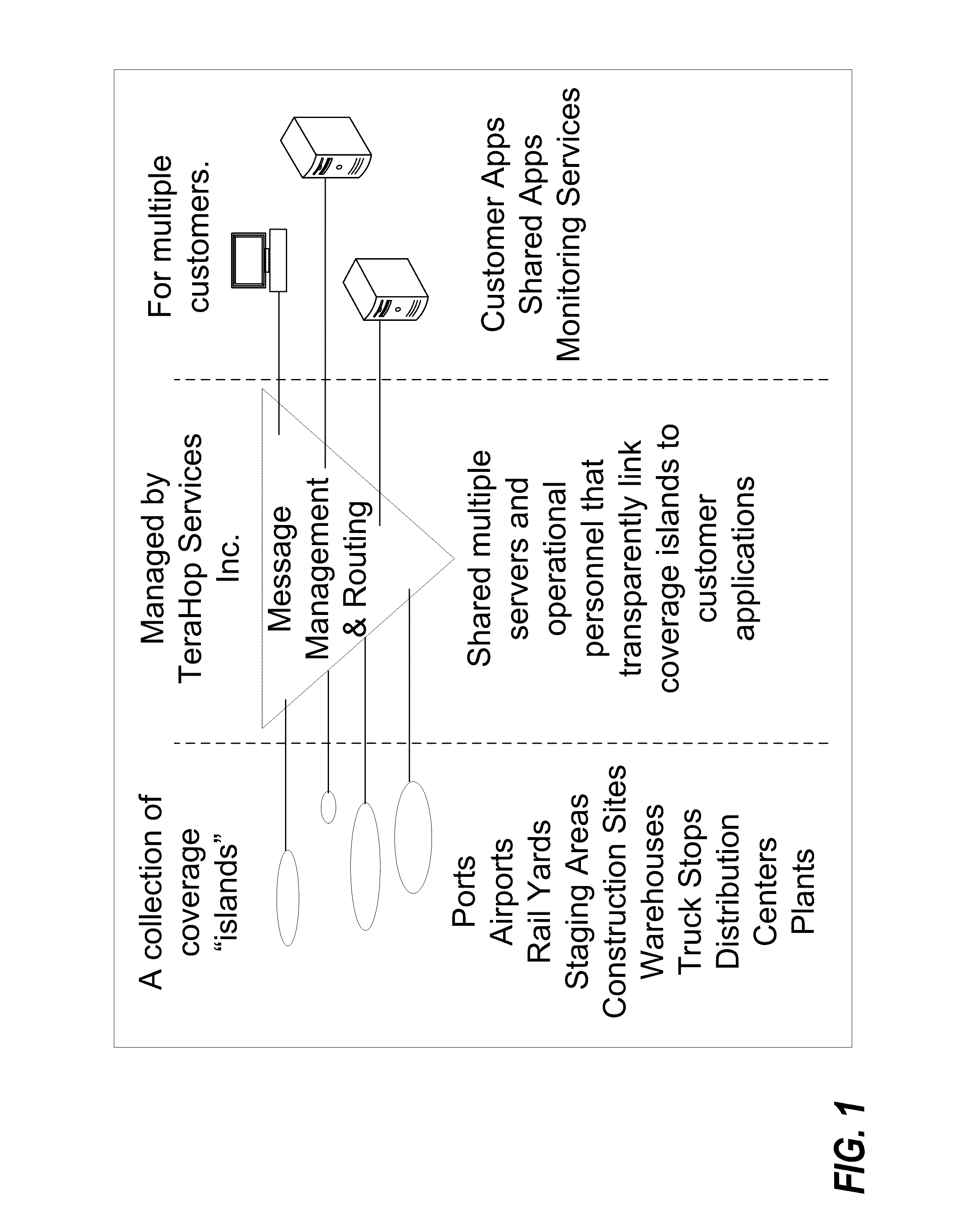
Managing and monitoring emergency services sector resources
InactiveUS20100150122A1Minimize congestionMinimizing RF pollutionService provisioningEmergency connection handlingRadio networksComputer network
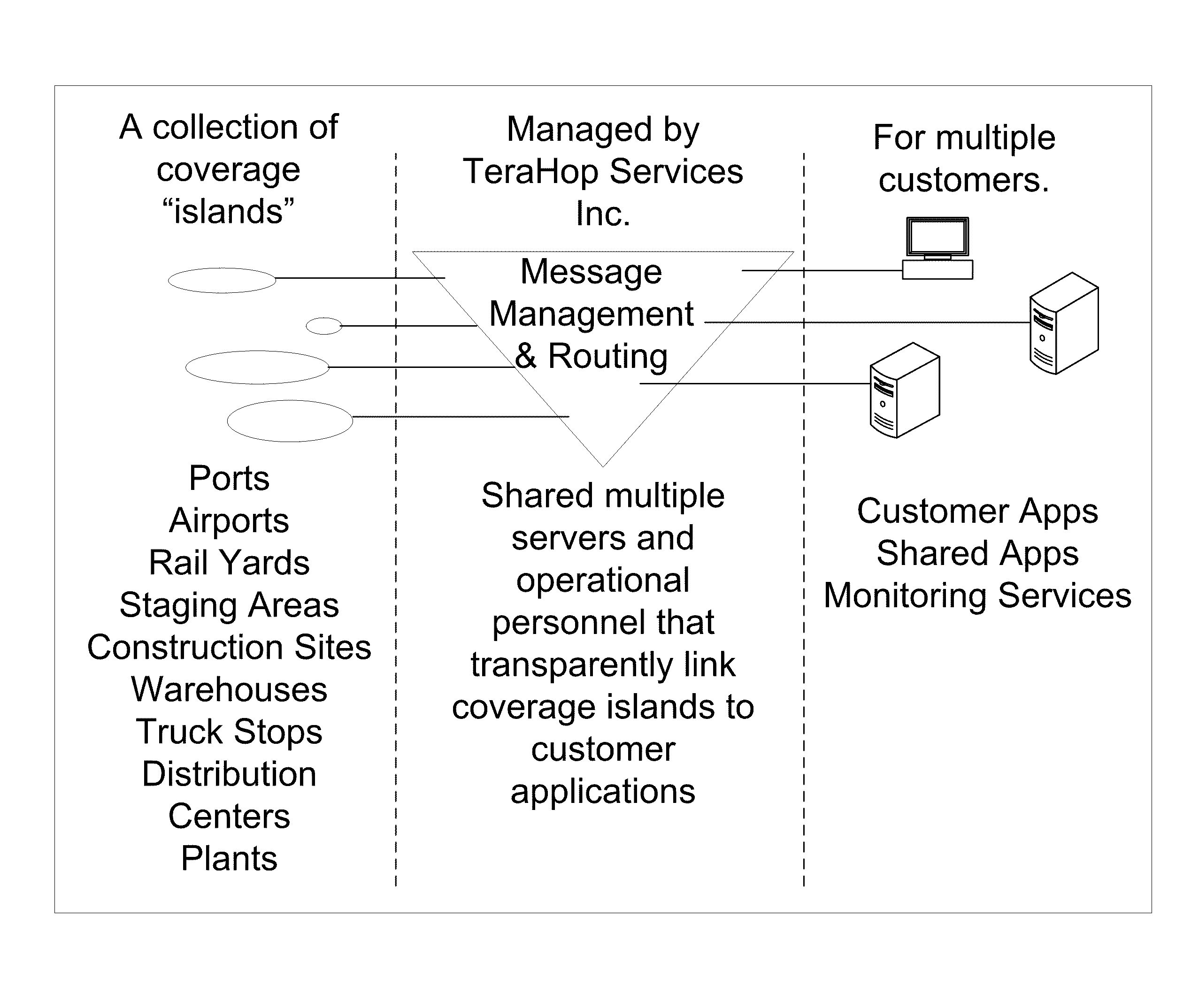
A system includes one or more wireless islands, one or more incident management applications, and one or more message management and routing (MMR) systems. Each MMR systems is configured to act as an intermediary for communication between one of the wireless islands and one or more of the incident management applications. One of the wireless islands includes a radio network. The radio network includes a plurality of remote sensor nodes (RSNs), and a gateway controller. An RSN of the plurality of RSNs is worn by ESS personnel, the gateway controller is mounted to an ESS vehicle, and the RSN is configured to wirelessly communicate with the gateway controller.
Owner:GOOGLE LLC
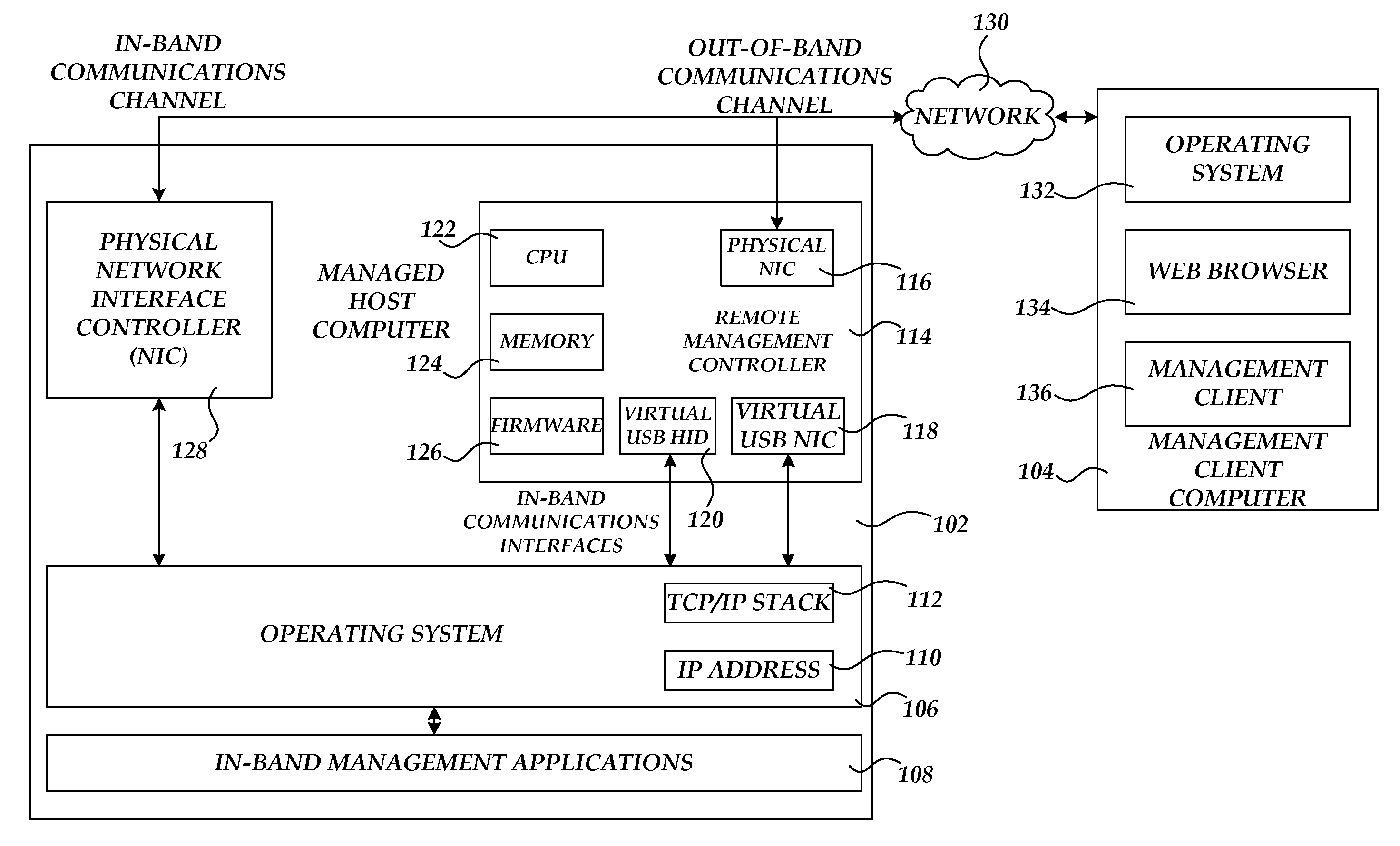
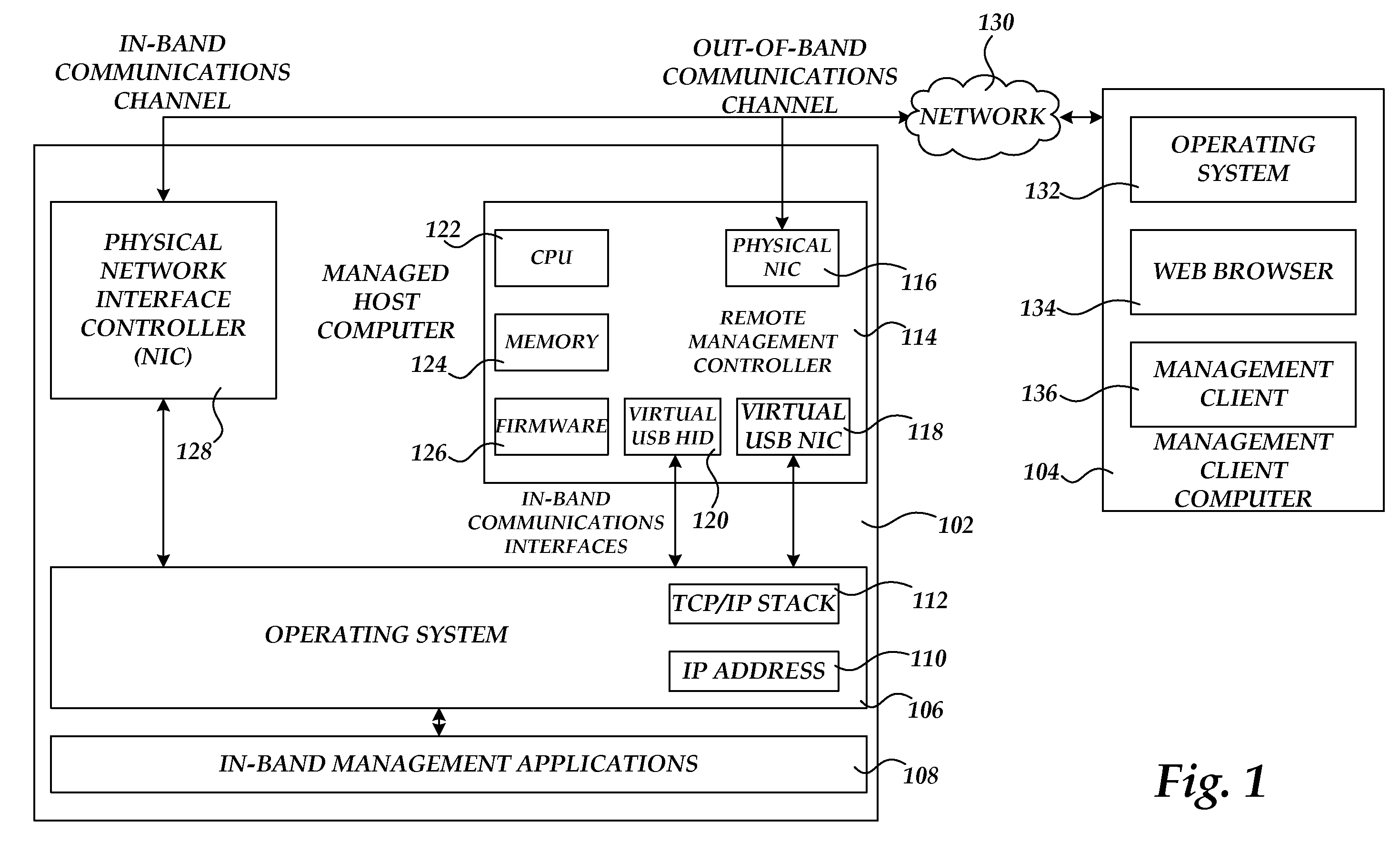
Communicating with an in-band management application through an out-of-band communications channel
ActiveUS20110283006A1Multiple digital computer combinationsData switching networksCommunication interfaceNetwork management application
A remote management controller is provided for use in conjunction with a managed host computer. The remote management controller exposes a virtual network interface controller, such as a driverless virtual USB network interface controller, to the managed host computer. Through the in-band connection provided by the virtual network interface controller, the remote management controller can communicate with in-band management applications executing on the managed host computer. The managed host computer can also access services executing on the remote management controller through the in-band communications interface. The remote management controller can also enable communication between the management client computer and in-band management applications executing on the managed host computer. The managed host computer can also access an out-of-band communications network between the remote management device and a management client computer.
Owner:AMERICAN MEGATRENDS
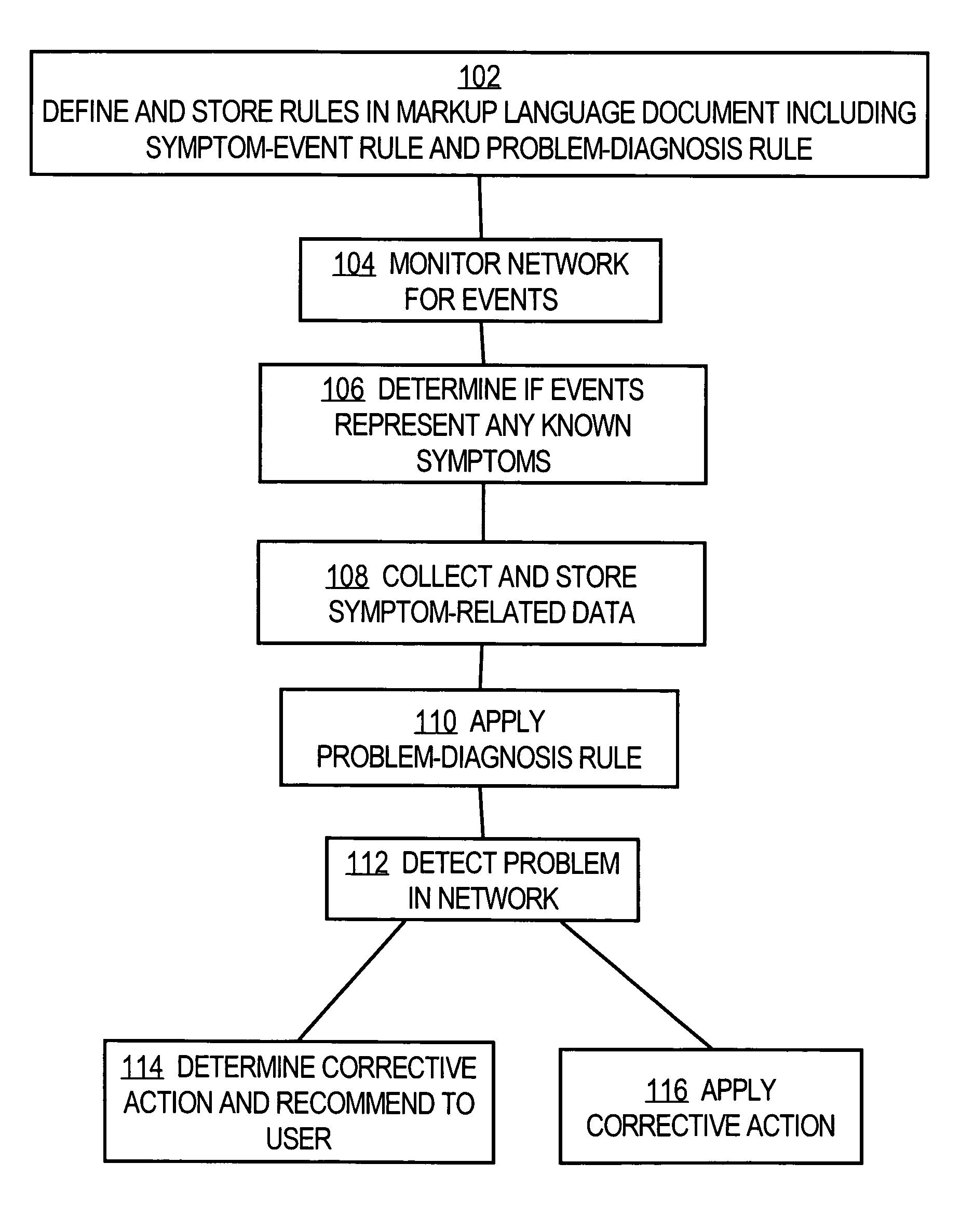
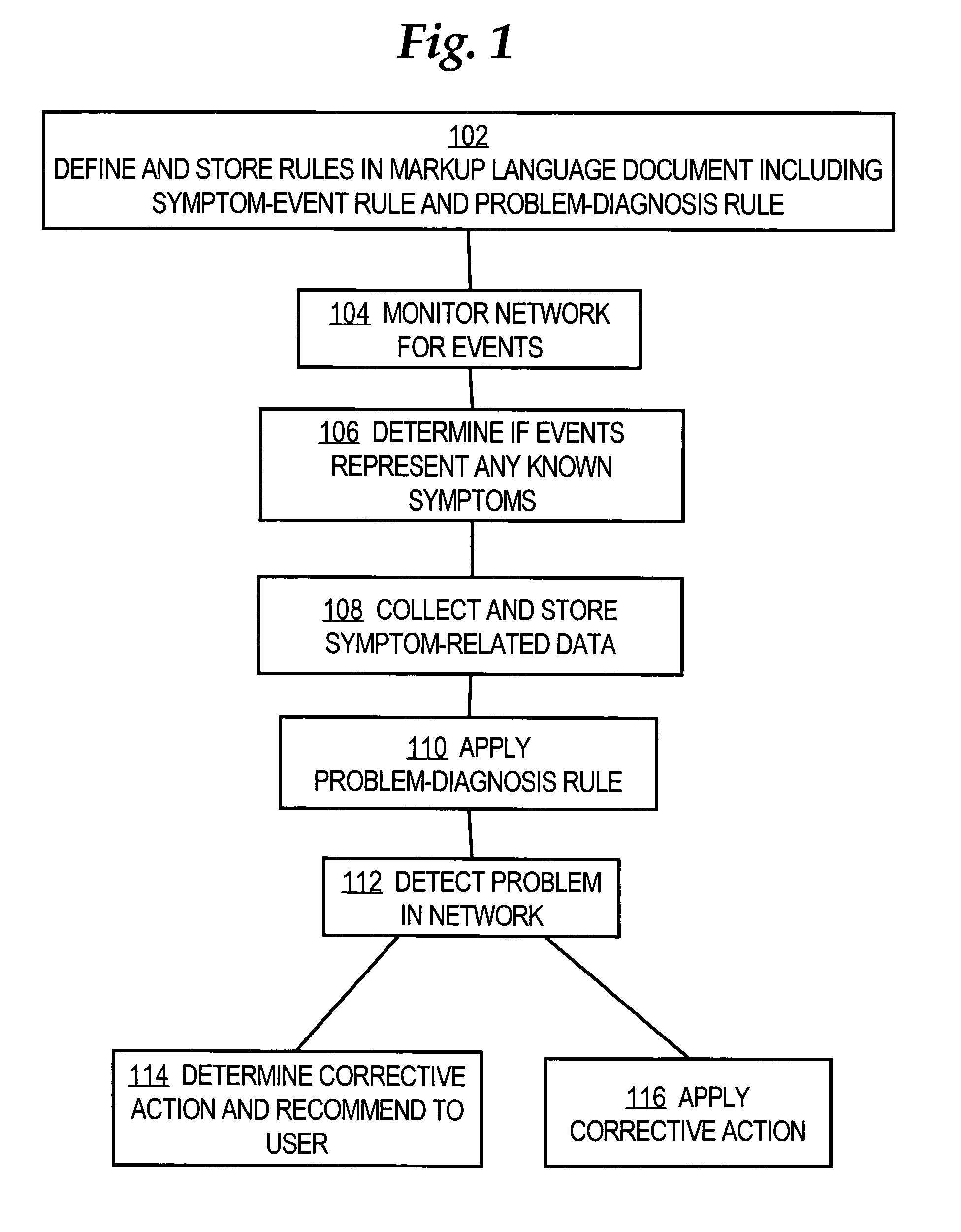
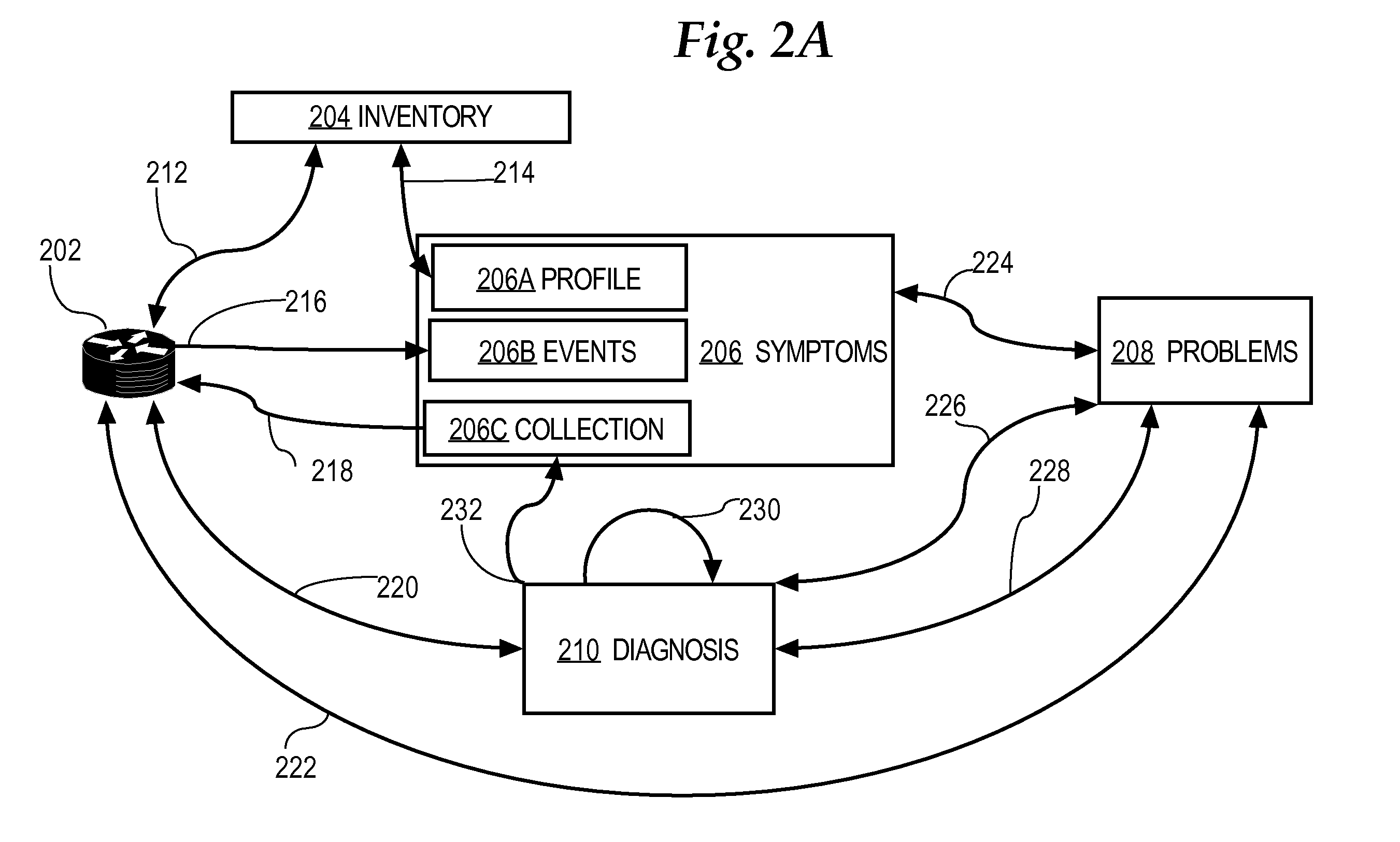
Rule-based network management approaches
InactiveUS7668953B1High level of flexibilityHigh level of powerError detection/correctionDigital computer detailsNetwork management applicationNetwork management
A method is disclosed for detecting symptoms in a network infrastructure, combining one or more symptoms into a problem, then optionally applying detailed diagnosis to the network elements experiencing the problems, ultimately providing detailed problem determination.
Owner:CISCO TECH INC
Automatic configuration of the network devices via connection to specific switch ports
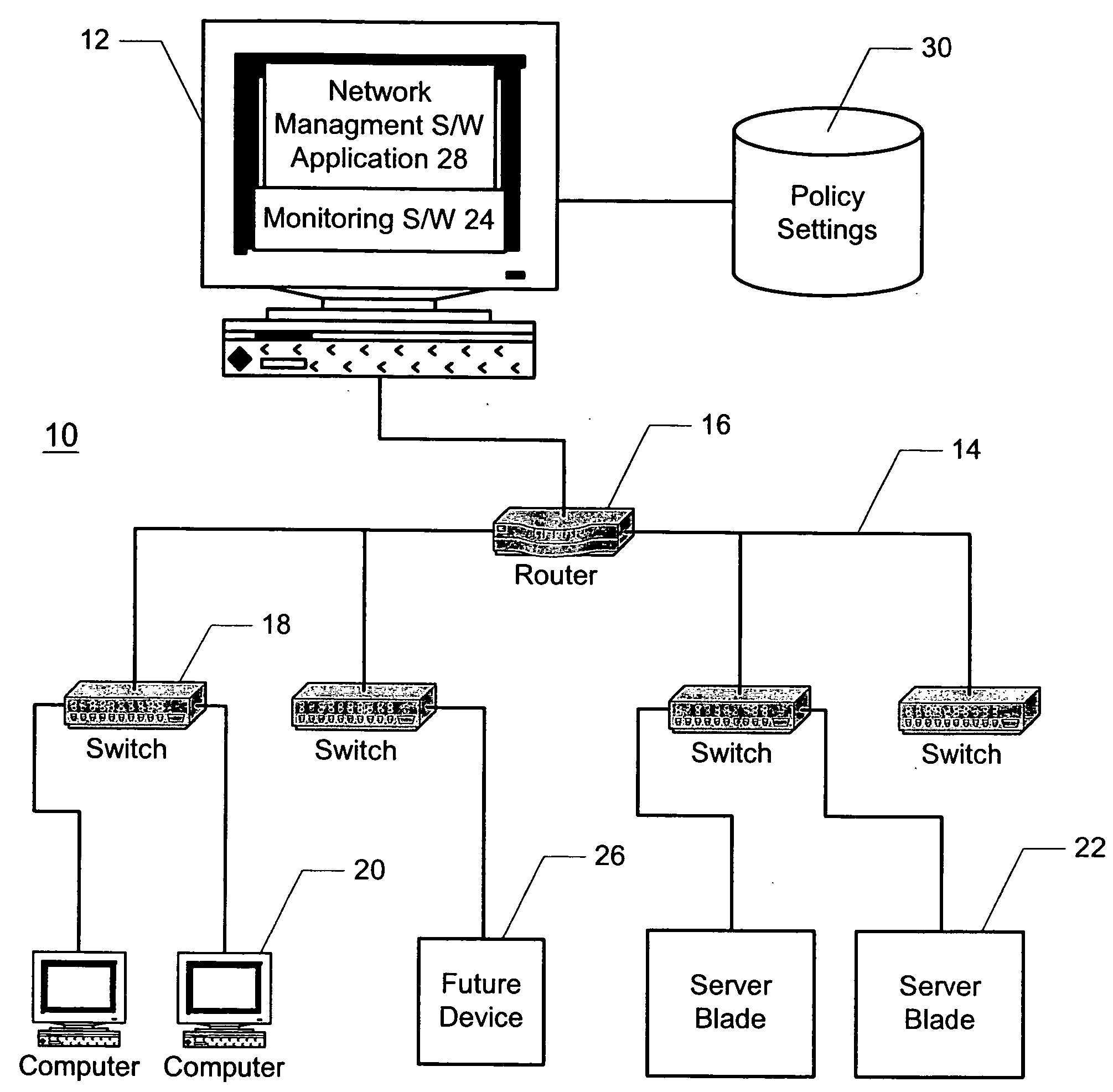
InactiveUS20050114474A1Optimize networkDigital computer detailsLocation information based serviceAuto-configurationNetwork management application
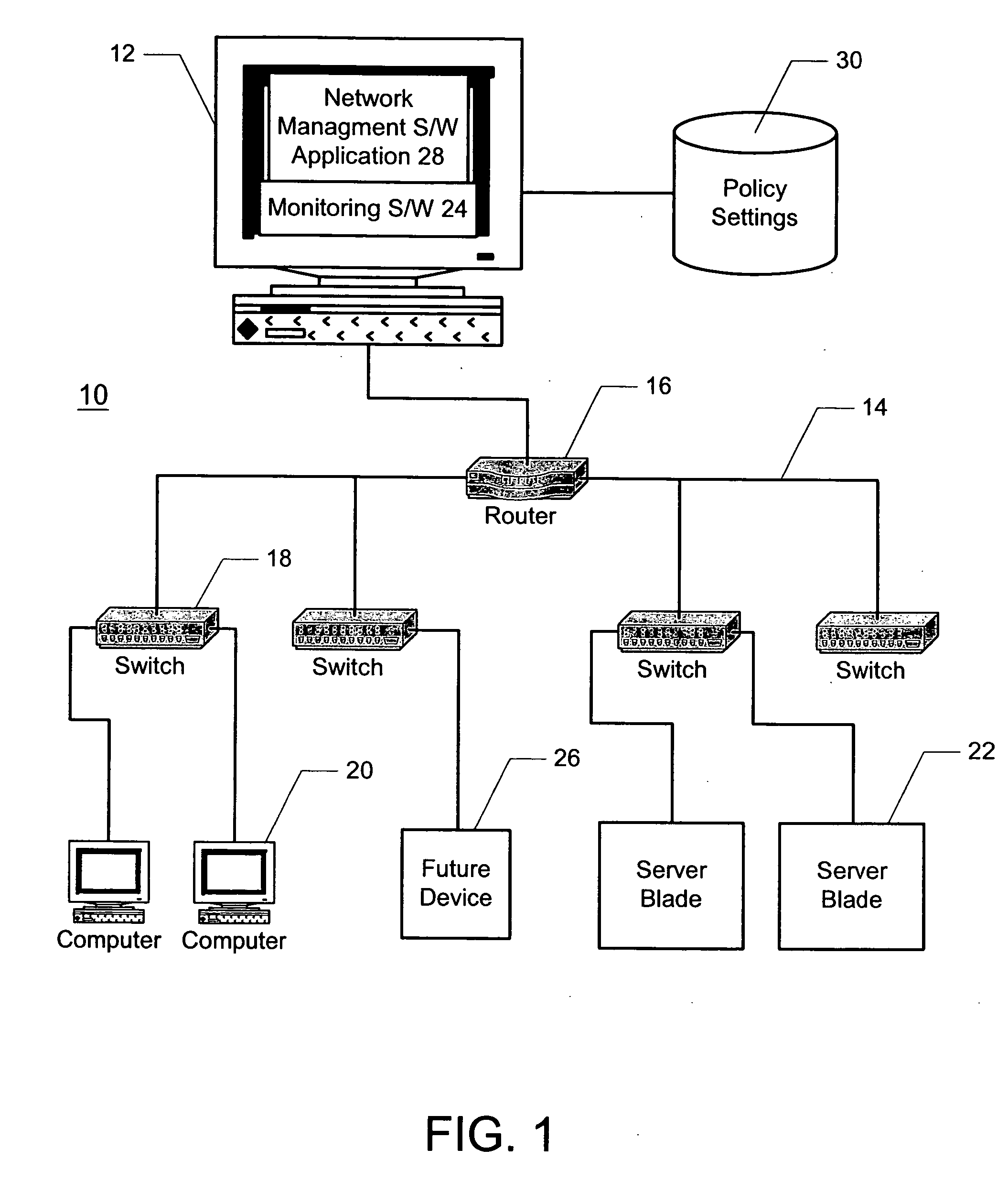
A method and system for automatically configuring devices in a network is disclosed. A network management software application is provided that enables a user to associate policy settings with physical locations in the network. During an operational mode of the network management application, the application automatically detects when a network device is plugged into the network, and determines a location of the device in the network. The device is then automatically configured based on the policy settings associated with the corresponding location.
Owner:IBM CORP
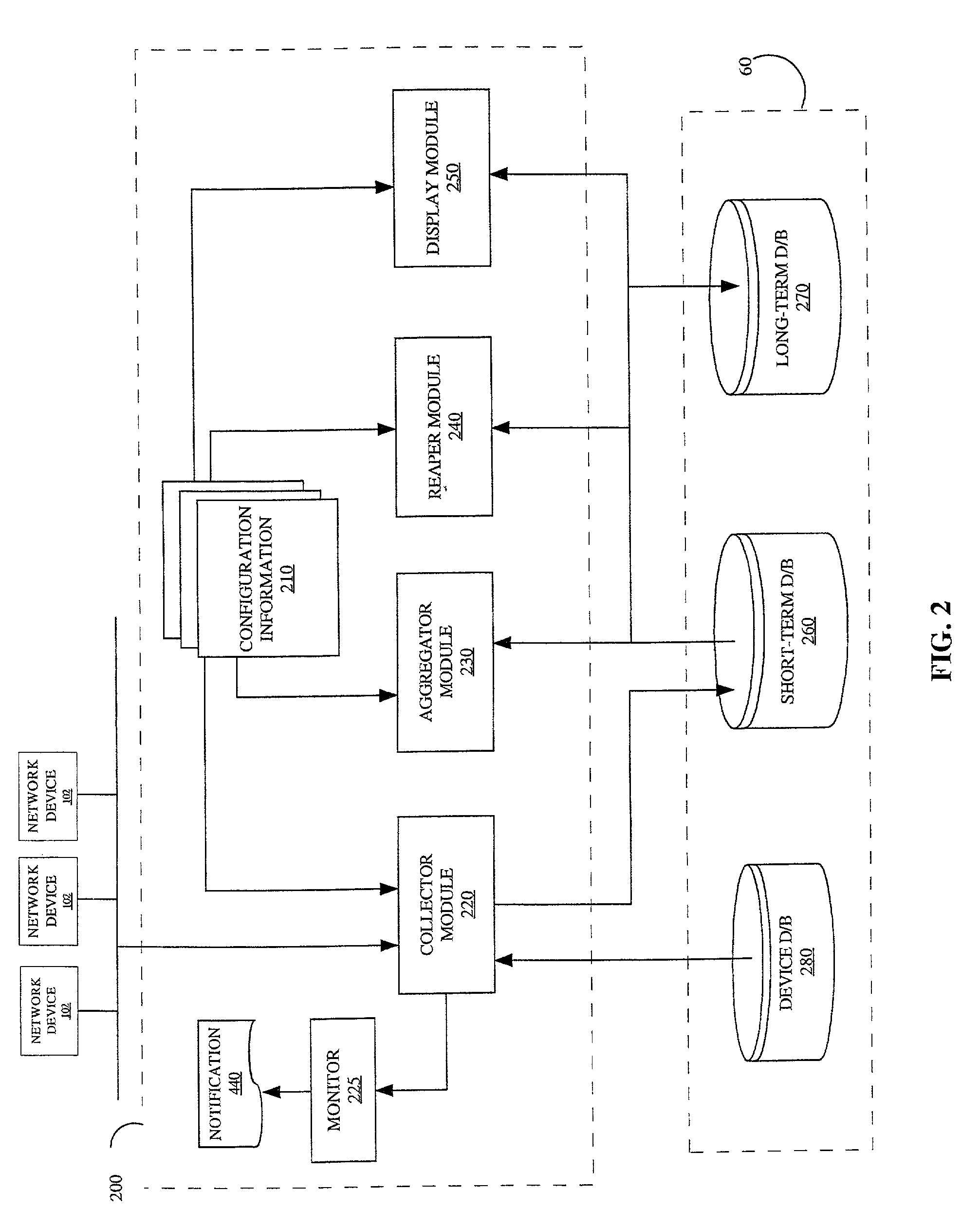
Method and apparatus for collecting, aggregating and monitoring network management information
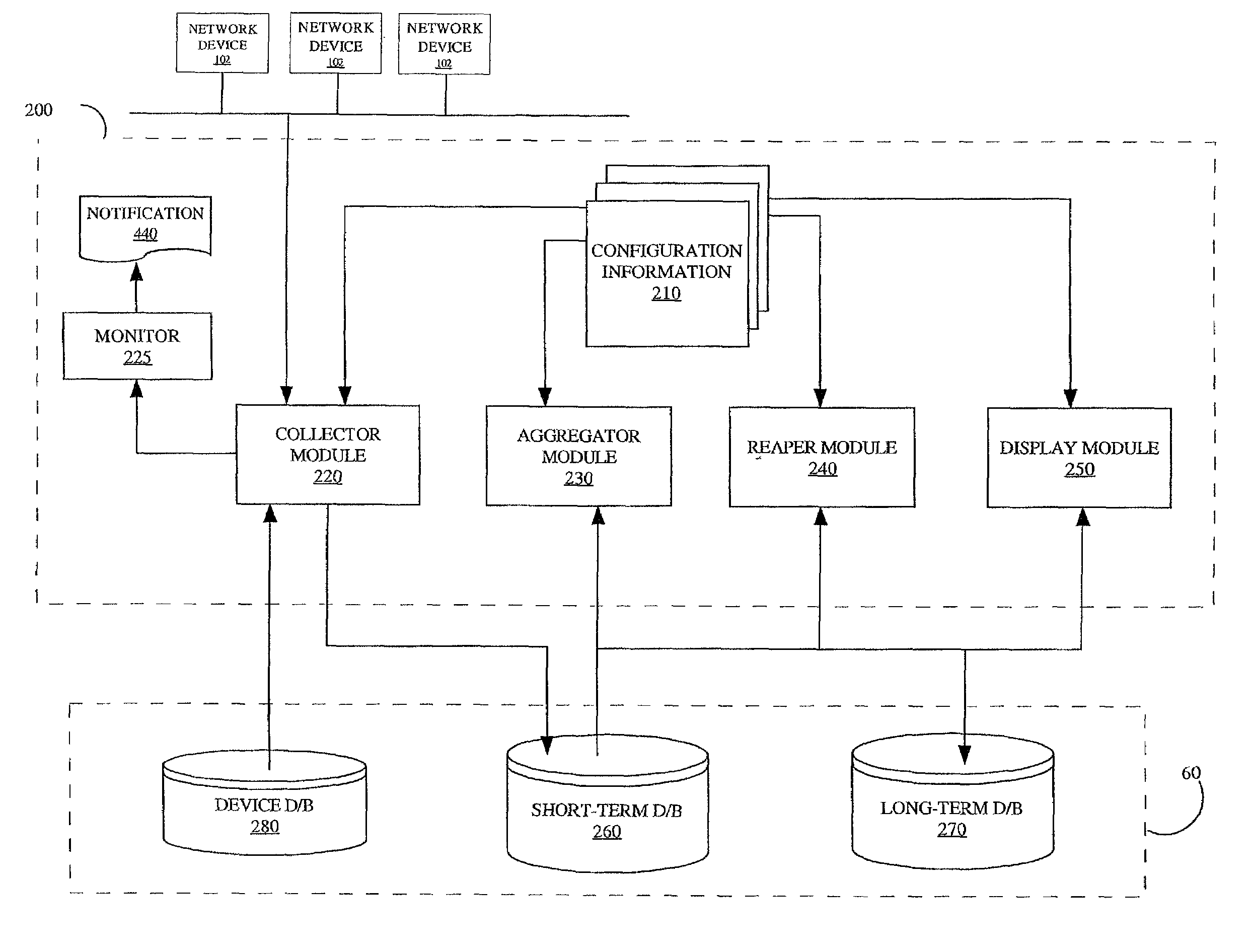
A method is disclosed for collecting, aggregating and monitoring network management information from a plurality of network devices in a network management system. The method utilizes user-definable configuration information that contains an operational specification on what to collect, aggregate and monitor, which can be scheduled at desired times or intervals. The method begins by identifying network devices on the network, then querying and acquiring data in accordance with instructions contained in the operational specification. The method performs transformations and will periodically monitor the data for compliance with specific threshold conditions. Notifications are generated whenever a threshold condition has been met. Data is stored to a database and aggregated to generate trending information. Data stored in the database can be subsequently removed automatically based on aging or other criteria specified by the user. The method renders data to a display for viewing by the user using device-specific GUI attributes.
Owner:CISCO TECH INC
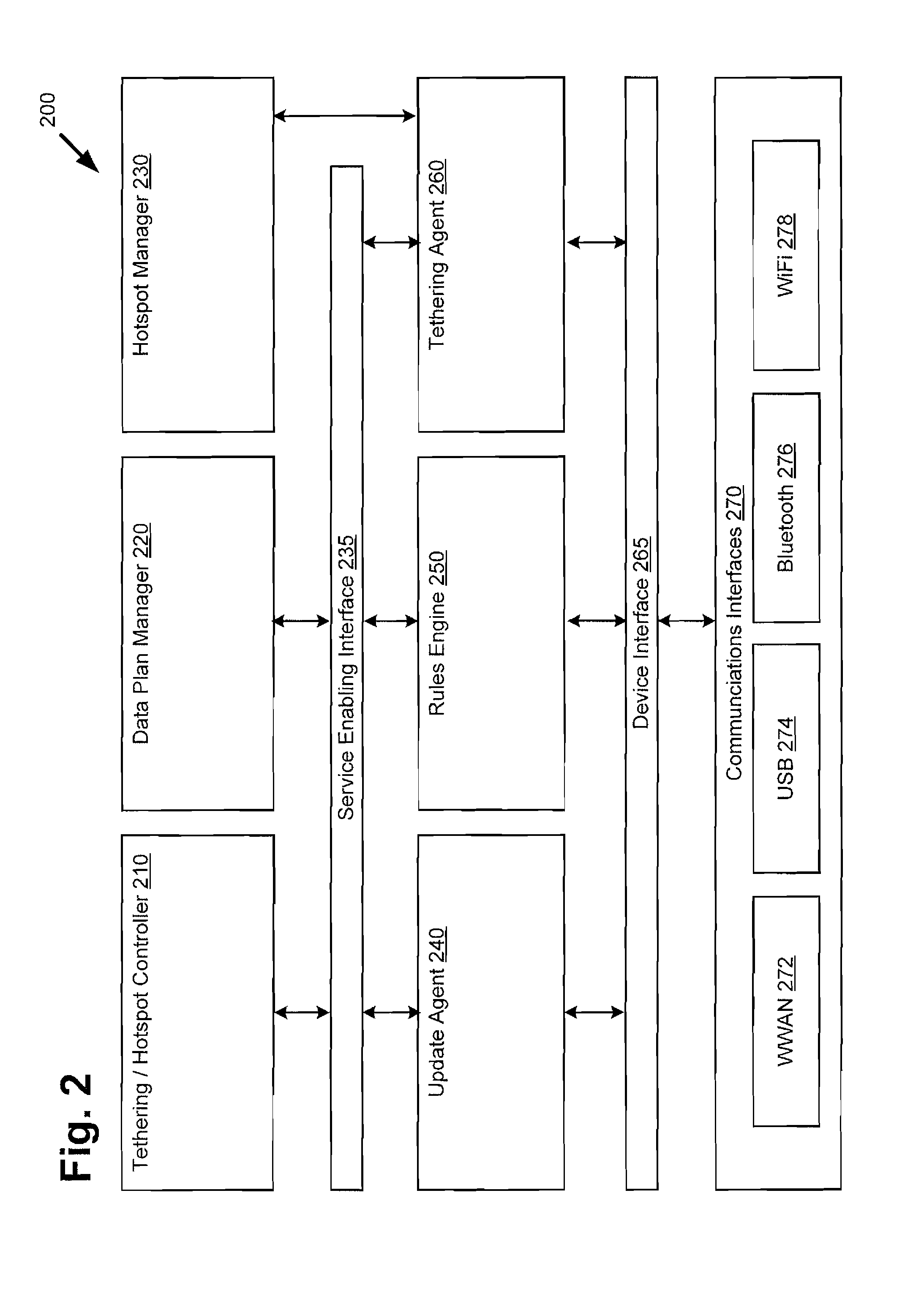
Managing Tethered Data Traffic Over a Hotspot Network
ActiveUS20120240197A1Service provisioningDigital data processing detailsNetwork managementNetwork management application
Presented is a system and method for controlling access to a mobile hotspot on a mobile device utilizing a hotspot management application. The method includes detecting unauthorized data traffic over a tethered link between the mobile device and a tethered device by analyzing a signature of the unauthorized data traffic. Analyzing the signature of the unauthorized data traffic may be carried out utilizing a rules engine, where the rules engine is based on one or more carrier controlled tethering policies and one or more user controlled tethering policies. Detecting unauthorized data traffic may further include detecting an unauthorized tethering application on the mobile device utilizing a database of known unauthorized tethering applications. The method further includes controlling the unauthorized data traffic. The method additionally includes redirecting a user of the mobile device to a captive portal for authorized tethering plan support.
Owner:SMITH MICRO SOFTWARE INC
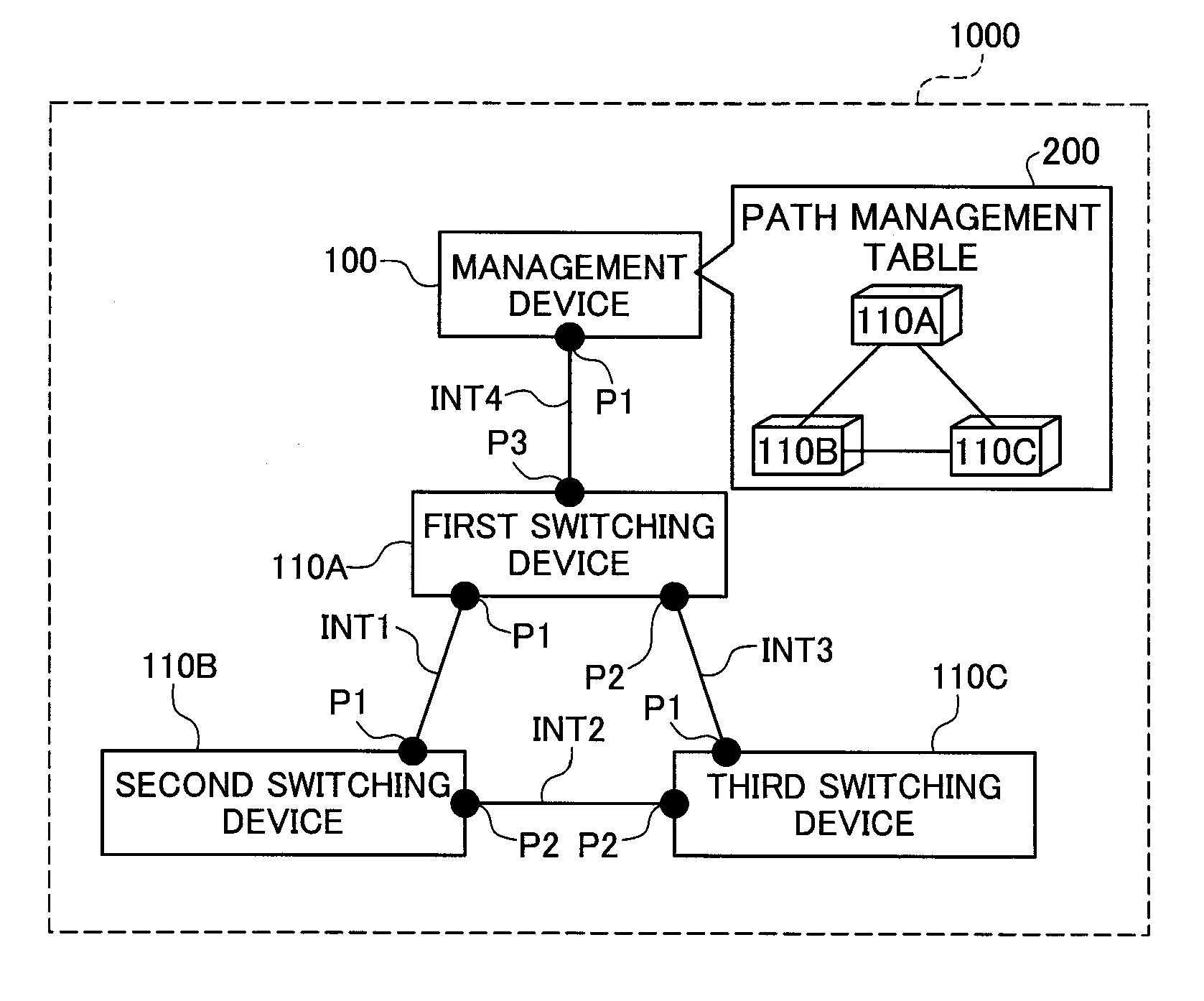
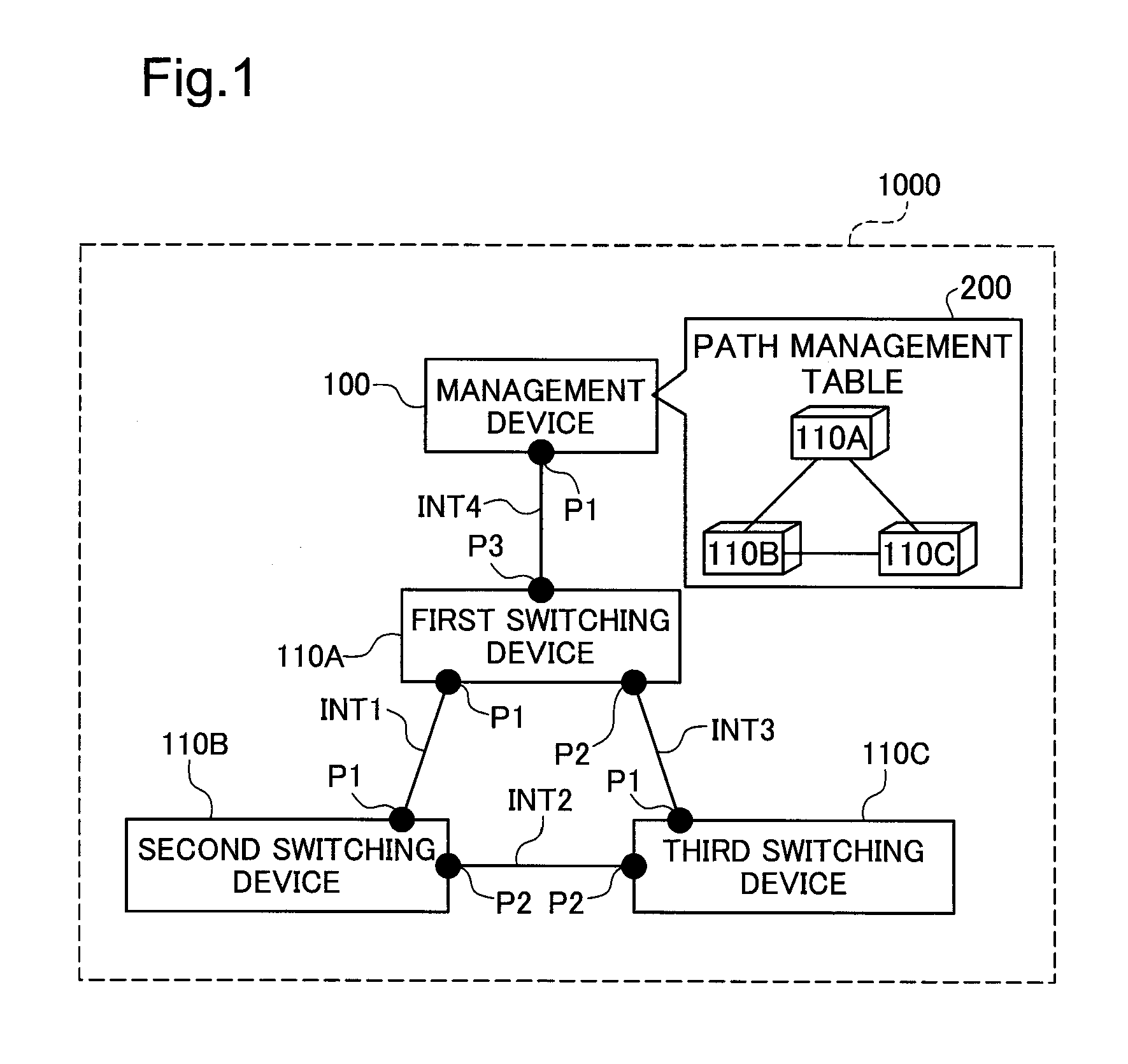
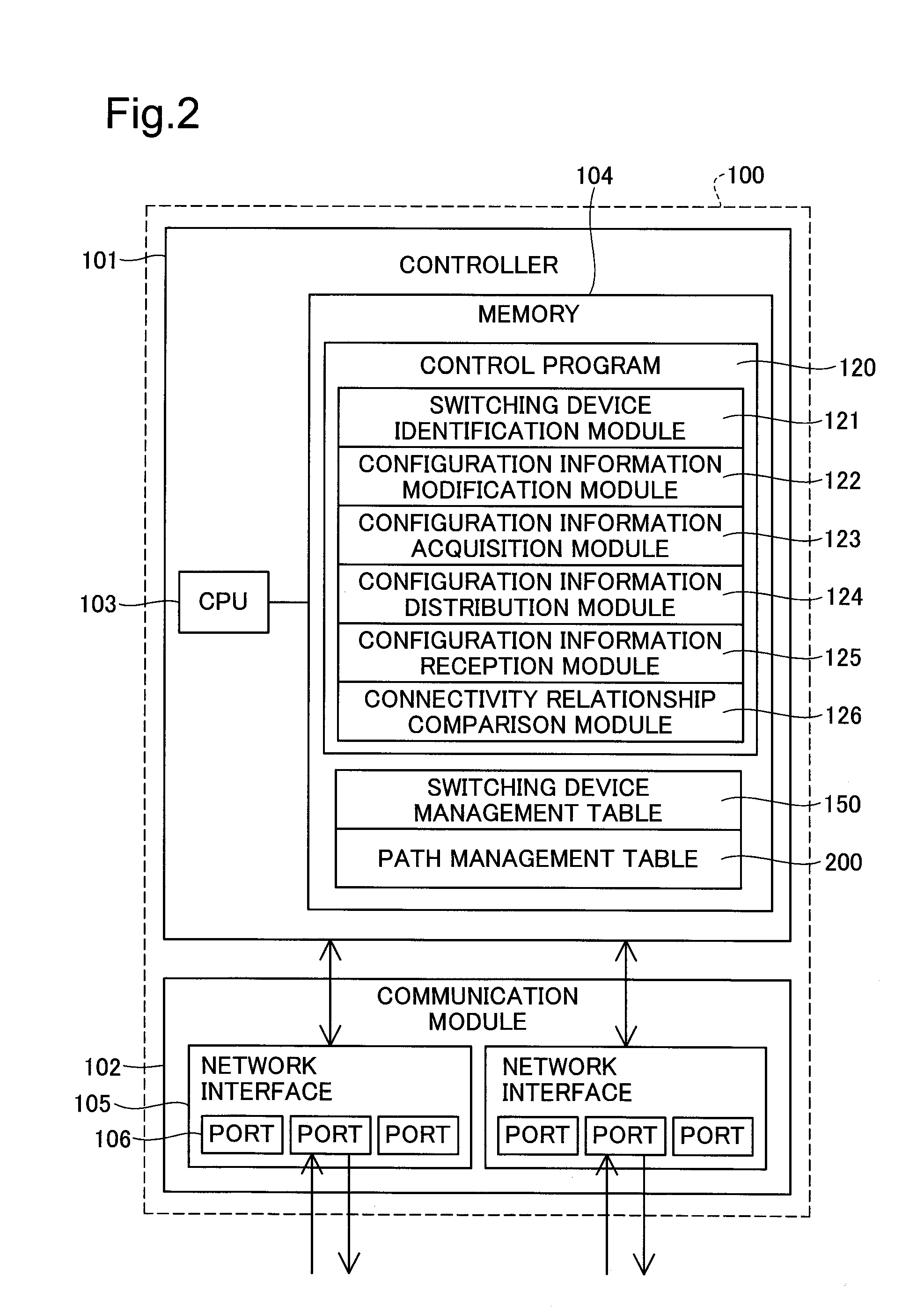
Network management apparatus and switching apparatus
InactiveUS20080186875A1Raise the possibilityData switching by path configurationNetwork management applicationNetwork management
A network management apparatus is for managing a plurality of switching devices that relay data through a data communication network. The network management apparatus includes a configuration information storage, a connectivity relationship detector and a configuration information modifier. The configuration information storage stores first configuration information. The first configuration information is configured in the switching devices and includes information to be determined in accordance with connectivity relationships among the switching devices. The connectivity relationship detector detects changes of connectivity relationships among the switching devices. The configuration information modifier dynamically modifies the first configuration information in accordance with detected changes of connectivity relationships.
Owner:ALAXALA NETWORKS
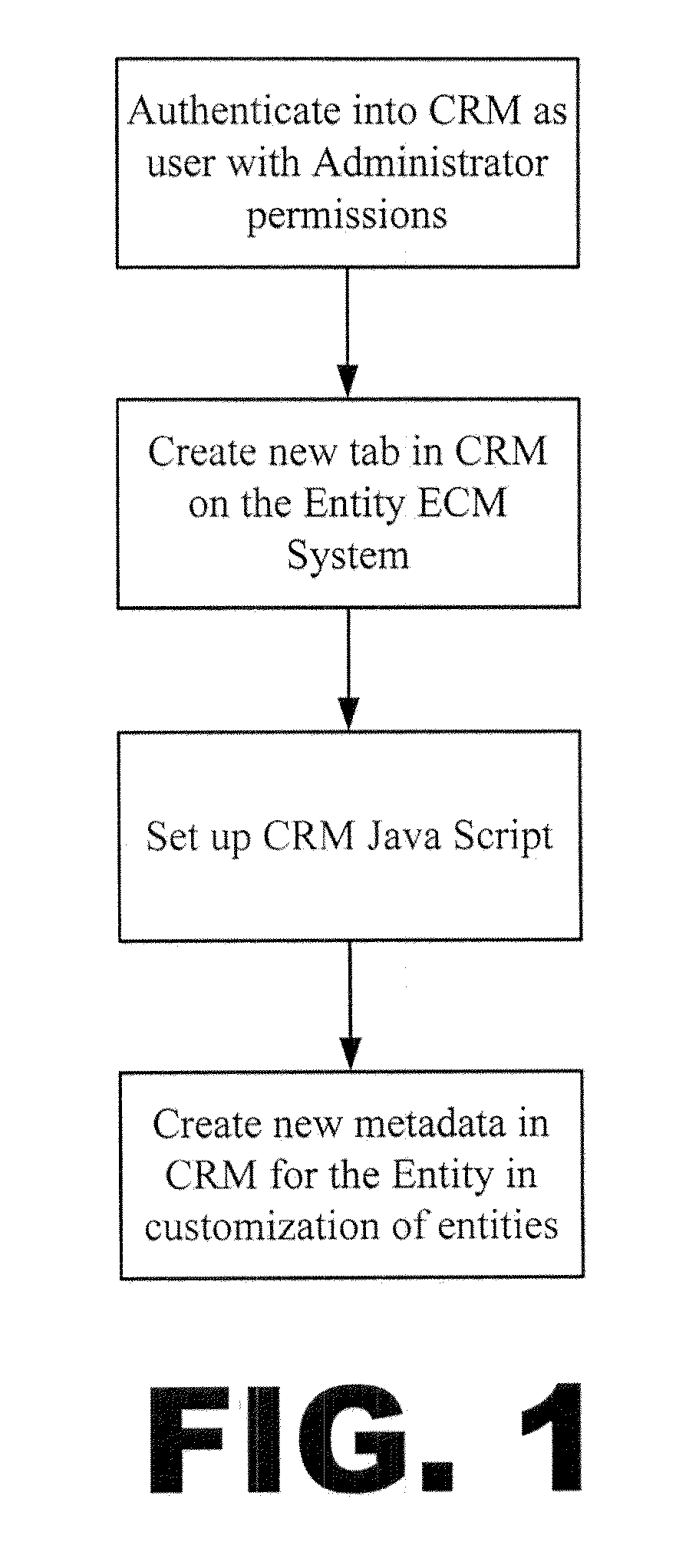
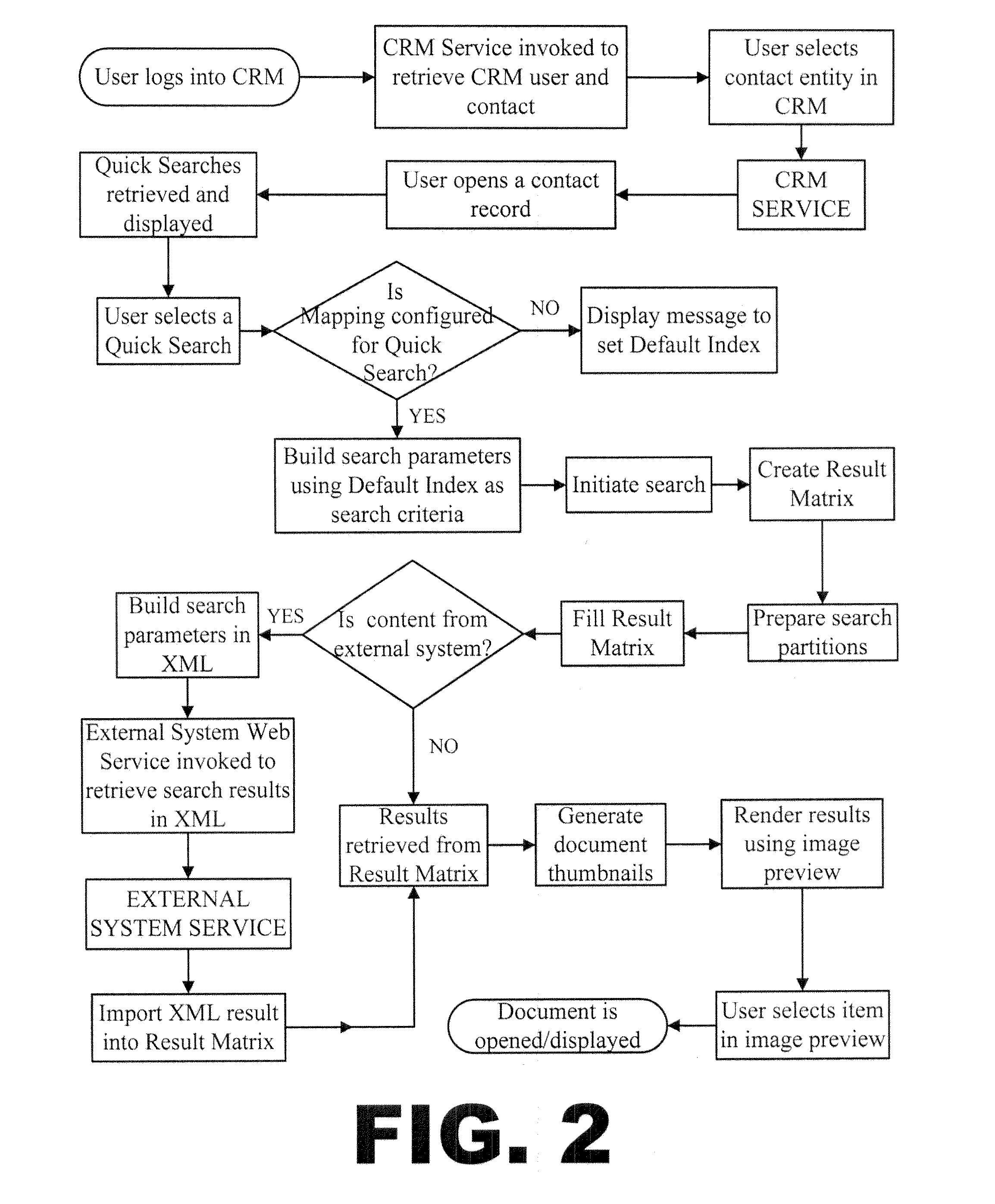
Relationship and Content Management Application
InactiveUS20120072436A1Easy retrievalEliminate needDigital data processing detailsOffice automationNetwork management applicationInternal documentation
A web-based Relationship and Content Management Application combining an organization's CRM and ECM systems by integrating CRM's contacts with an ECM system's key features and functionality. The user of such is able to efficiently store and retrieve a combination of information for a relationship from CRM as well as from ECM, avoiding human error and providing data centralization. Users may store and retrieve content from both internal document repositories within an ECM system as well as external document repositories in the user's system. The major features consist of the ease of use and data consistency, plus the leverages of CRM as the centralization of data.
Owner:WALL STREET NETWORK
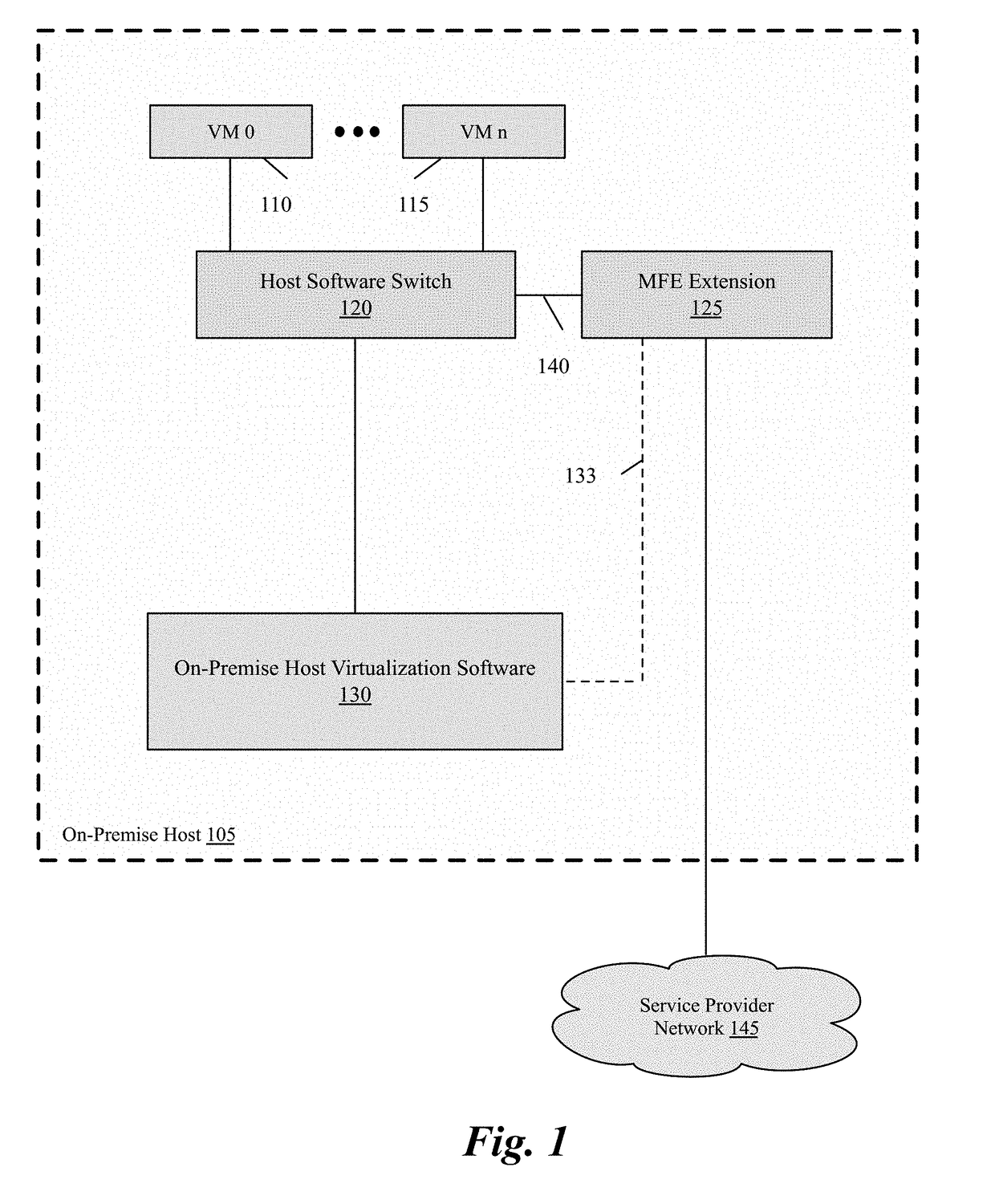
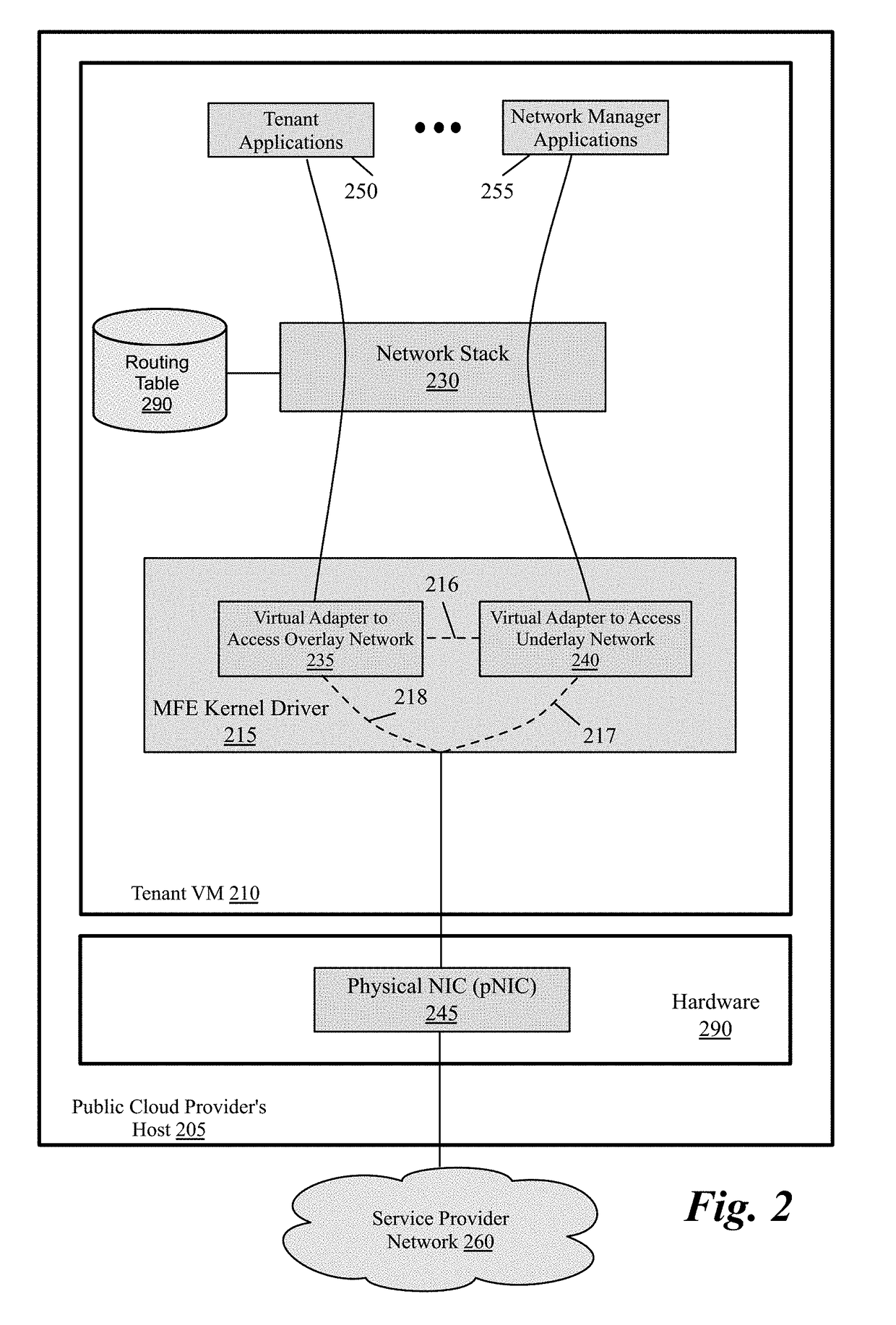
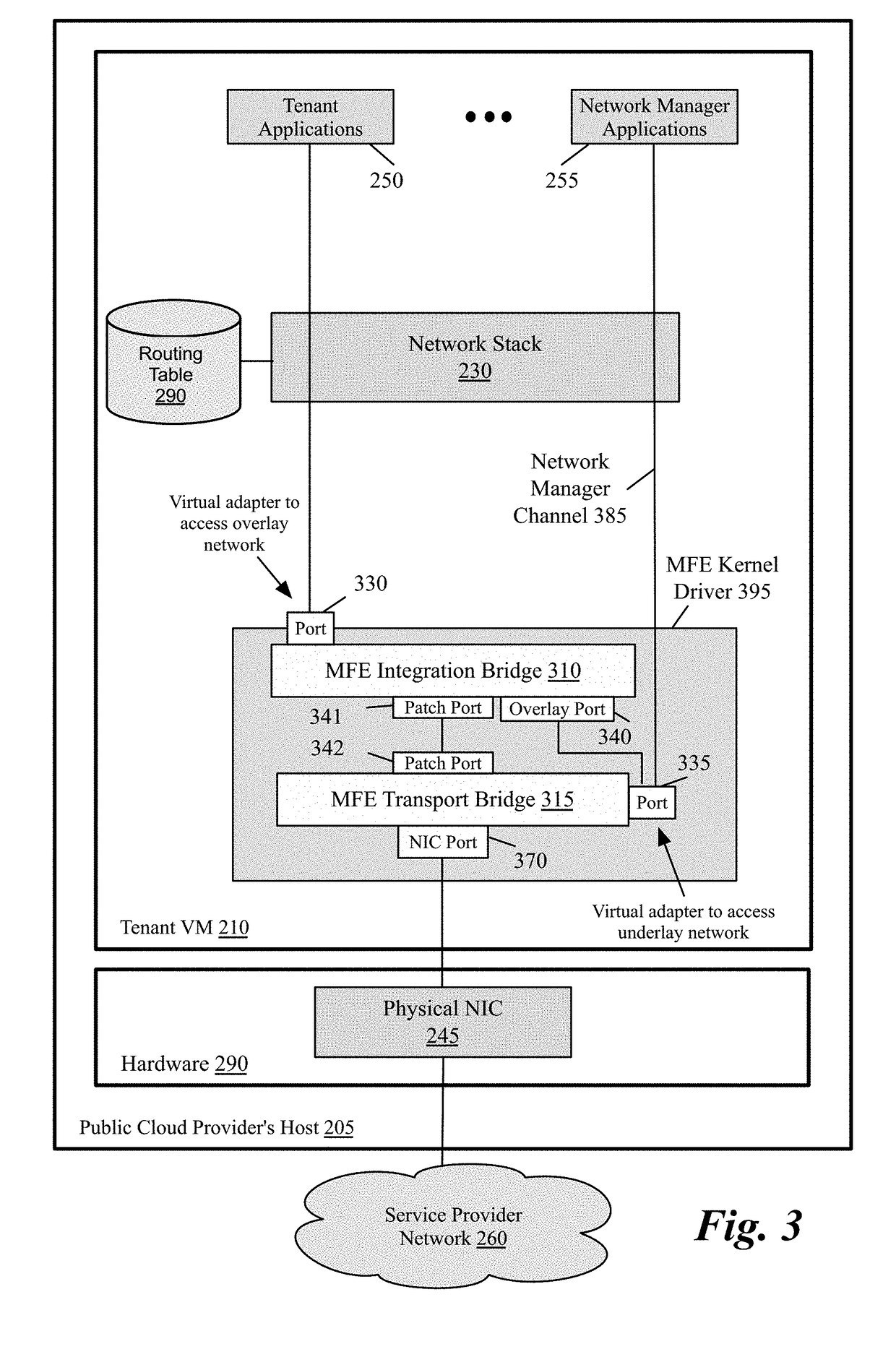
Packet communication between logical networks and public cloud service providers native networks using a single network interface and a single routing table
A data compute node executes (i) a set of tenant applications connected to a third party overlay network, (ii) a set of network manager applications, and (iii) a managed forwarding element that includes a pair of overlay and underlay network virtual adapters. A packet that is received from a network manager application and addressed to an underlay network destination is sent to the underlay network destination address through a physical NIC of the host without network address translation or encapsulation. A packet that is received from a tenant application and addressed to an underlay network destination is subject to SNAT and is sent to the underlay network destination address. A packet that is received from a tenant application and is addressed an overlay destination address is encapsulated with the header of the overlay network and is sent to the overlay network destination address through the underlay virtual adapter.
Owner:NICIRA
Dynamic policy engine for multi-layer network management
ActiveUS9819565B2Multiple digital computer combinationsData switching networksNetwork management applicationNetwork management
Dynamic policy systems and methods for implementing network management of a network include pre-calculating management policies for the network, in an off-line manner, based on past observed network load taking into consideration seasonality of network load, forecasts of the network load, and planned events on the network load; selecting a policy from the pre-calculated management policies, to manage the network in an on-line manner, wherein the selecting is either time-based or performance-based; and performing network management functions in the network utilizing the selected policy.
Owner:CIENA
Method, system, and program product for transaction management in a distributed content management application
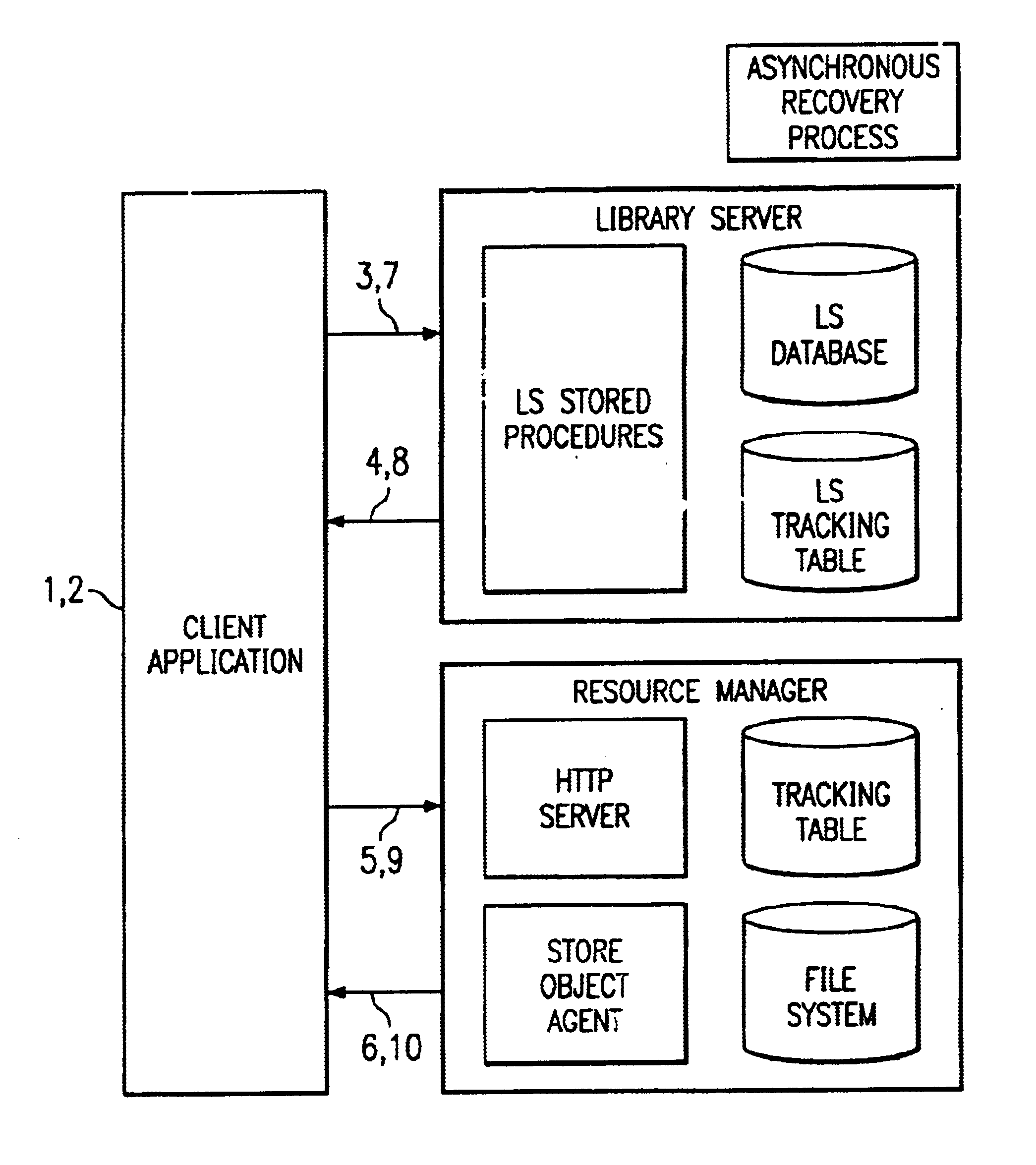
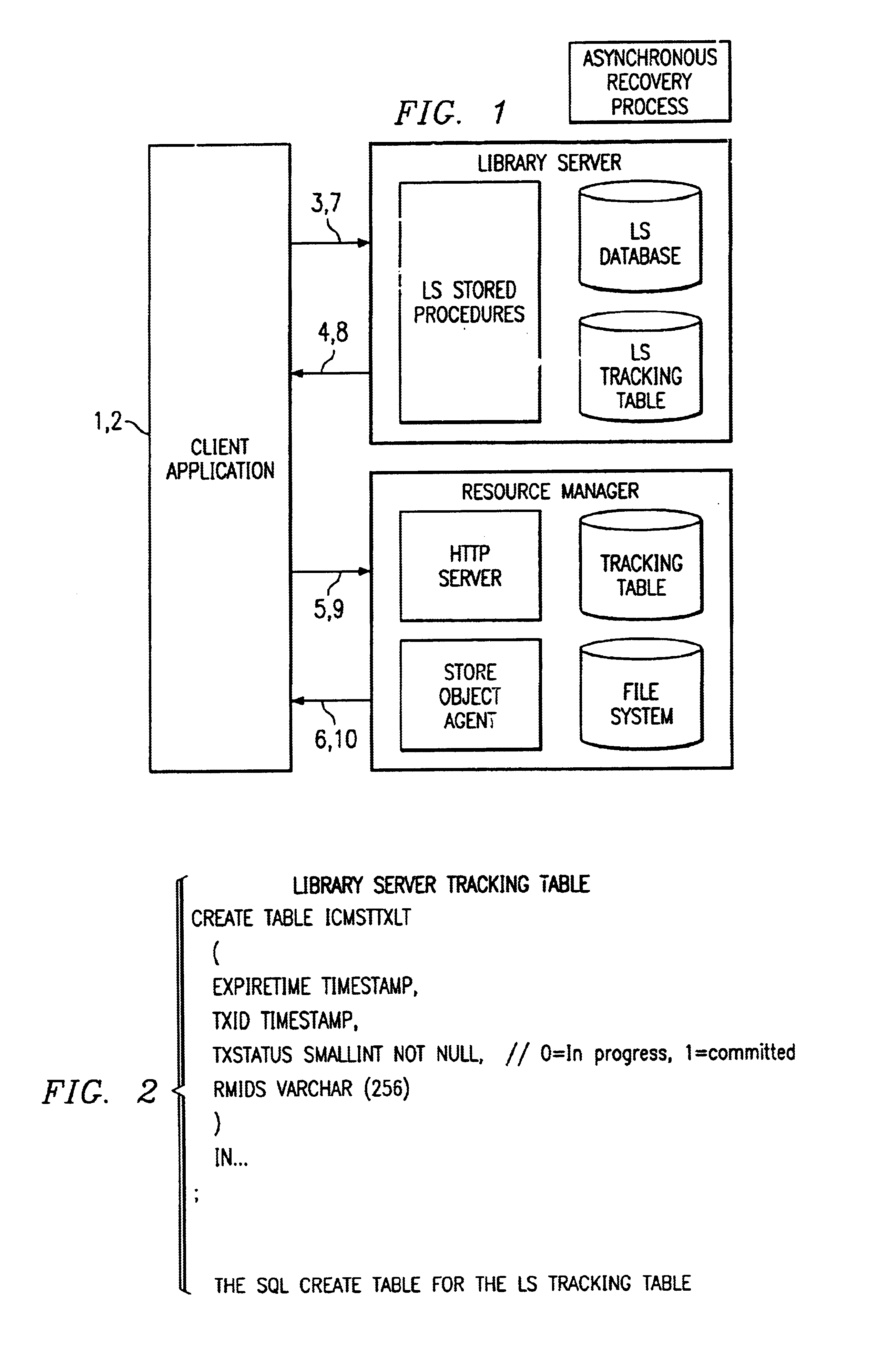
InactiveUS6873995B2Data processing applicationsDigital data information retrievalTransaction managementNetwork management application
Managing a content management system. The content management system is one that is configured and controlled to establish a connection between a client and a library server, generate a transaction identifier and insert, a record for the transaction in a tracking table associated with the library server, pass transaction data from the client to a resource manager, process the transaction at the resource manager and record transaction data in a tracking table associated with the resource manager. The resource manager returns transaction success / failure data to the client, compares activity recorded in the tracking tables, and takes corrective action based upon the activity comparison.
Owner:IBM CORP
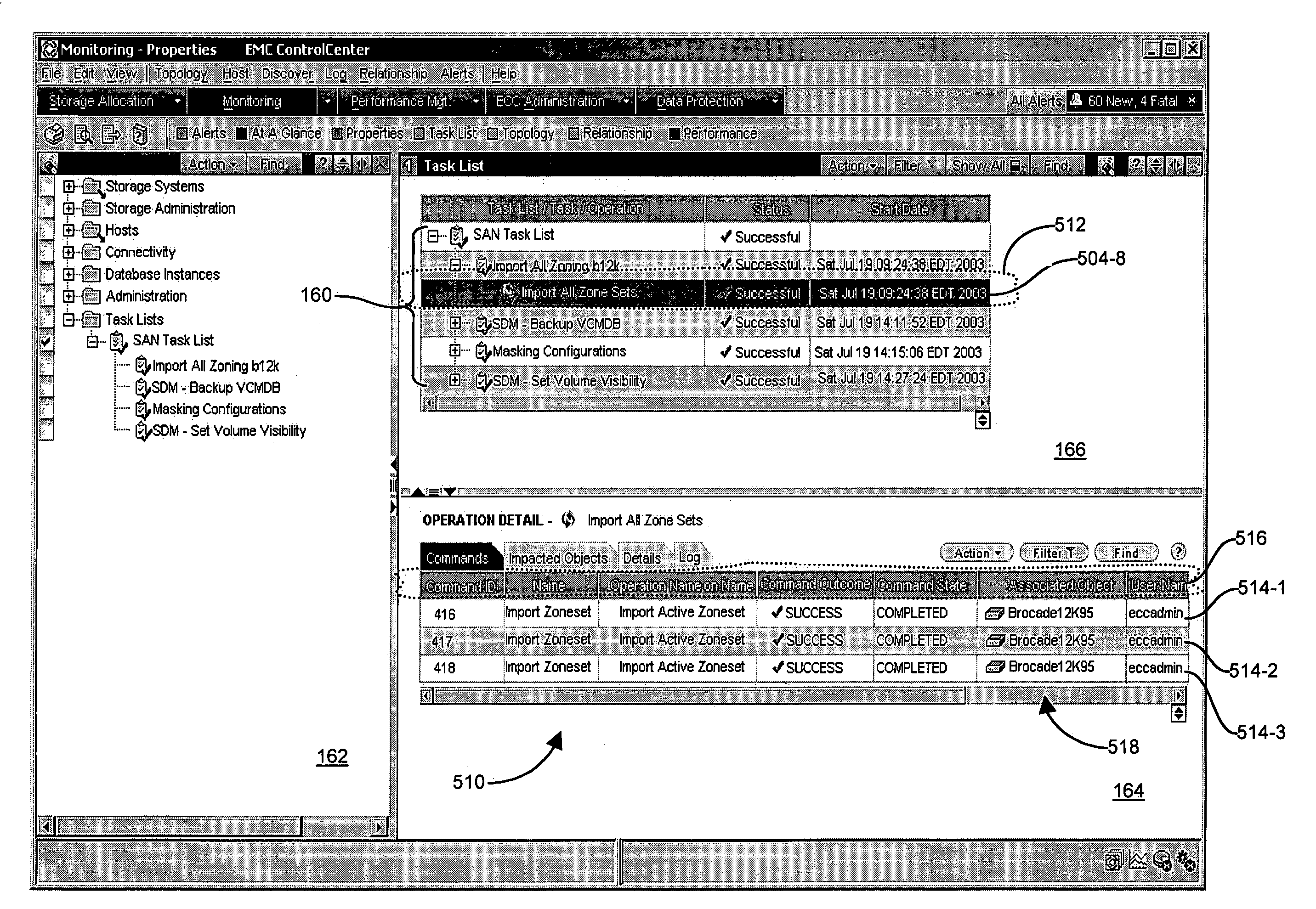
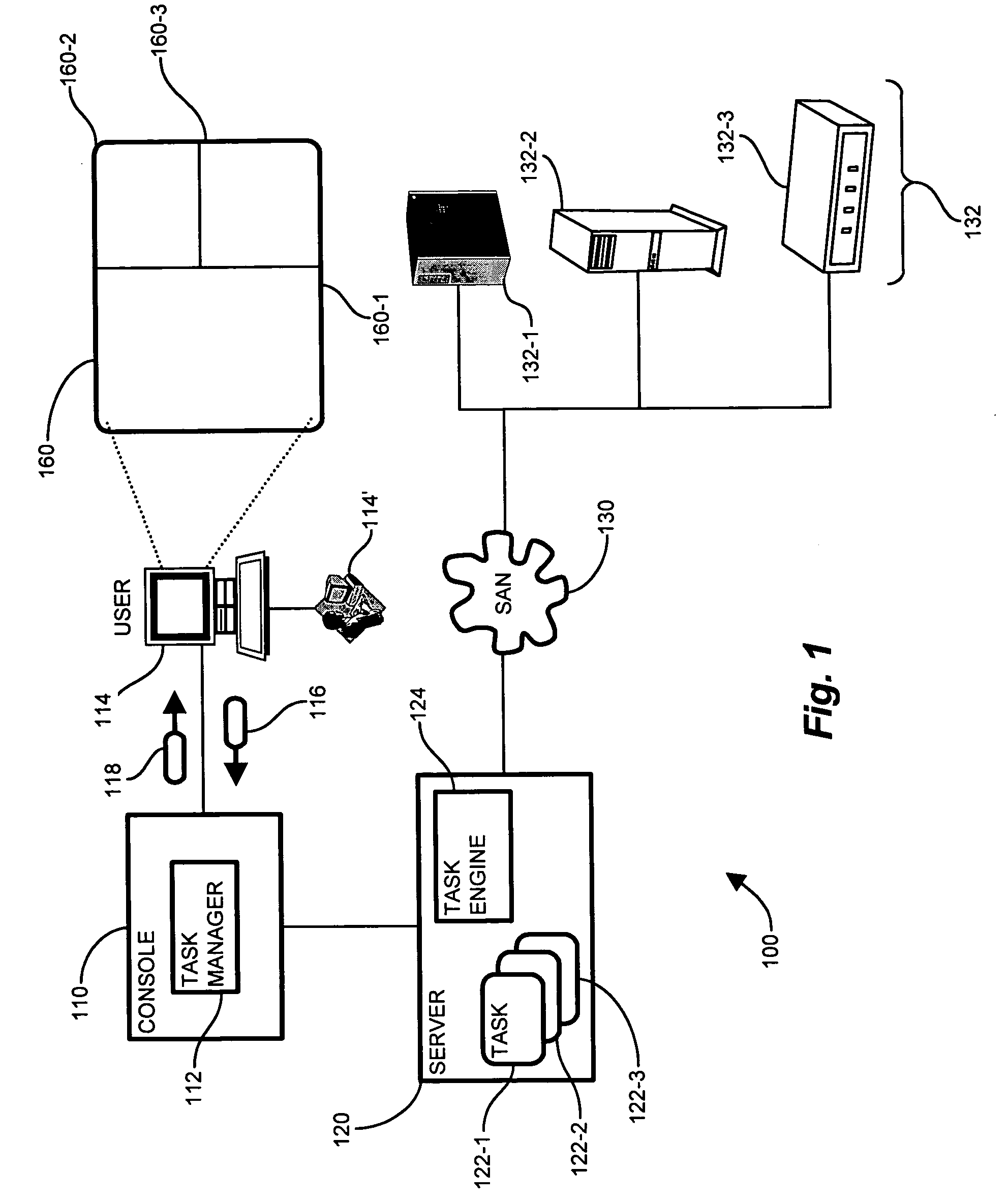
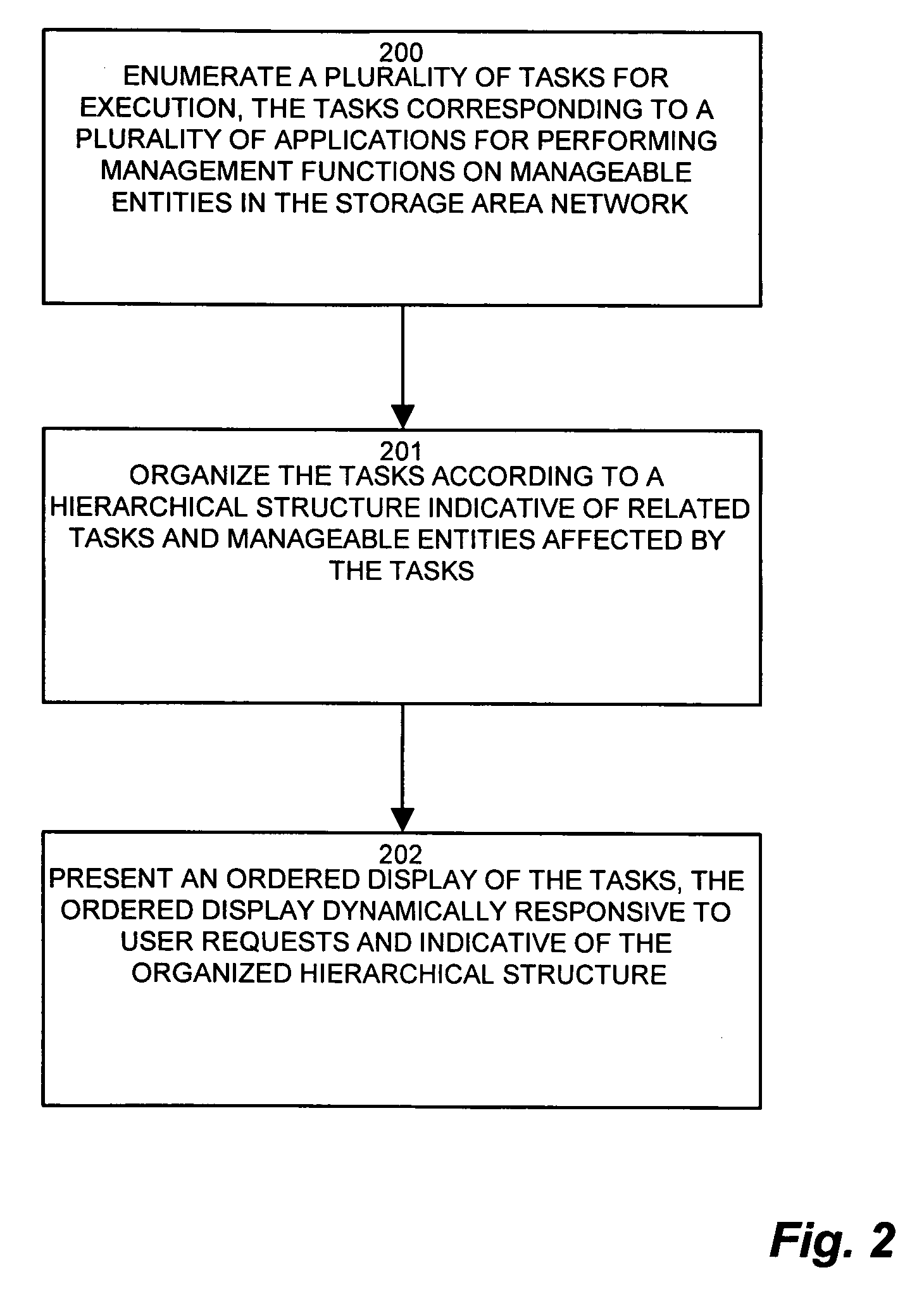
System and methods for a task management user interface
In a large storage area network (SAN), many administrative tasks perform various operations. Managing the tasks can be a formidable activity. A network management application, operable to identify and manipulate the tasks, organizes the tasks in a common graphical user interface (GUI) which allows task management from a single operator console. The task manager provides a GUI having display panes for managing the tasks. The task manager allows selection and invocation of tasks, in which the same task is identifiable by each of the plurality of attributes. The task manager displays the hierarchy of tasks in a task tree, including selectable task icons, in a task tree pane. The task icons are expandable into the corresponding subtasks and operations in a task list pane, and status details about the operations and task status are displayed in a context detail pane. An operator traverses the task tree to drill down into the operation and completion status of tasks in the task tree.
Owner:EMC IP HLDG CO LLC
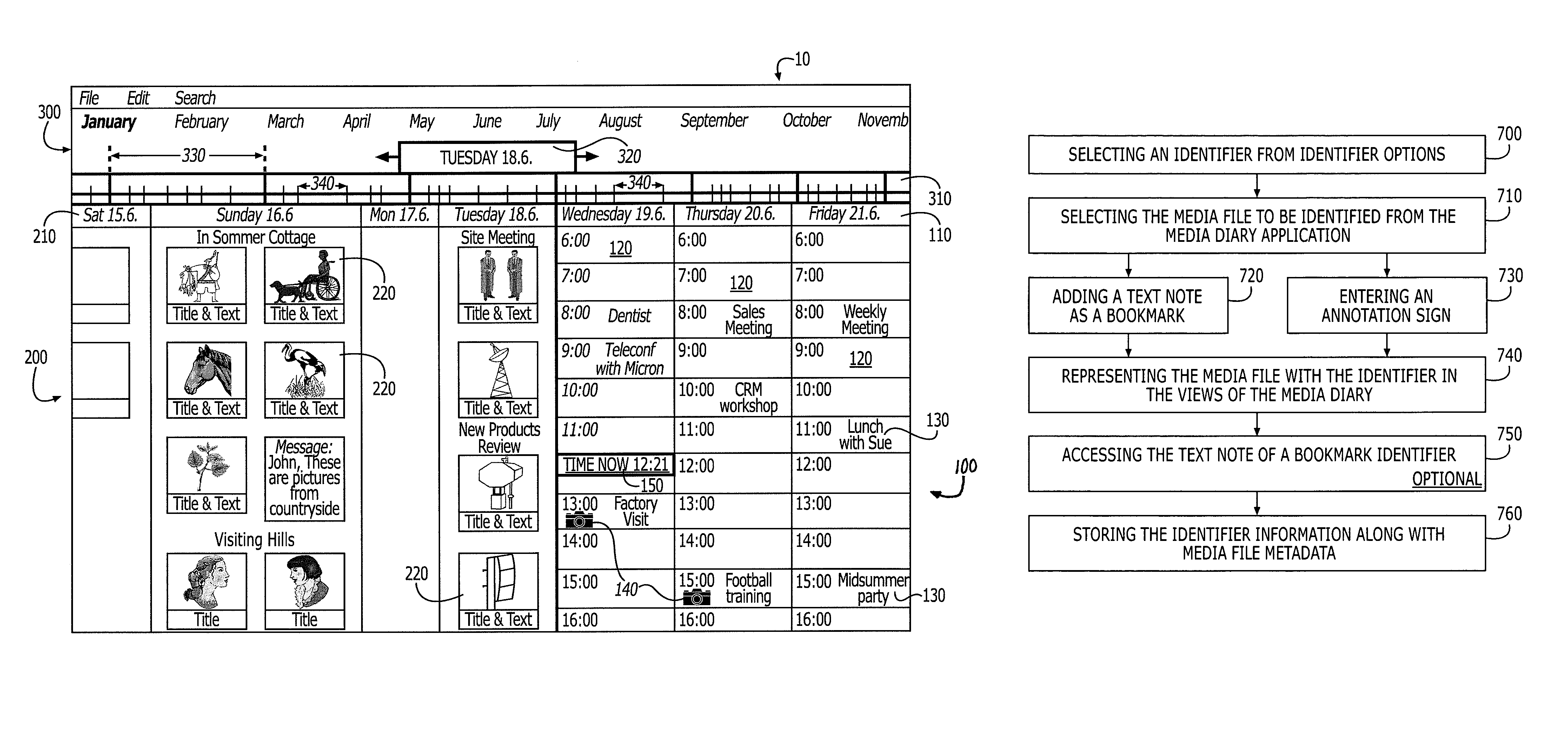
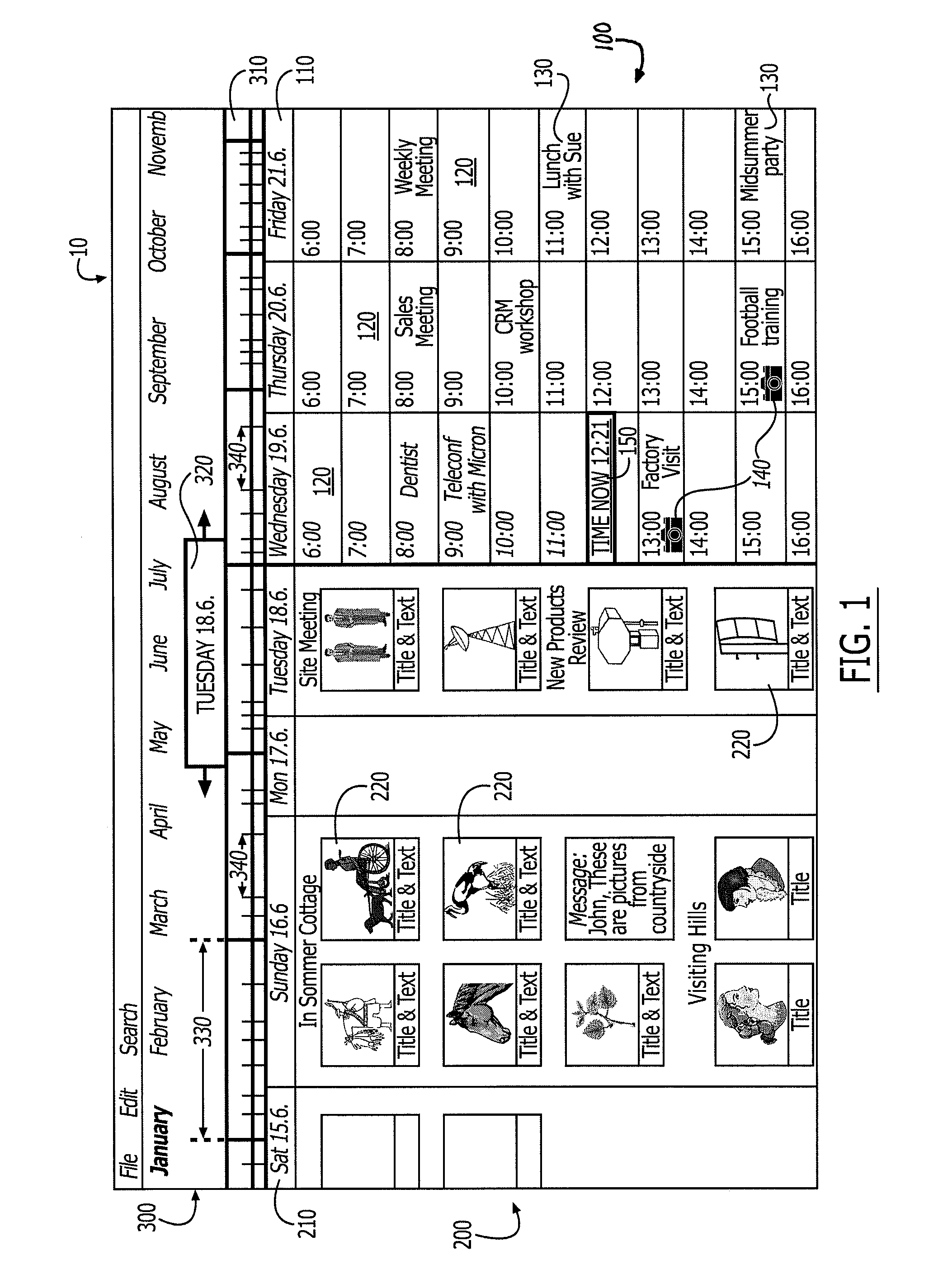
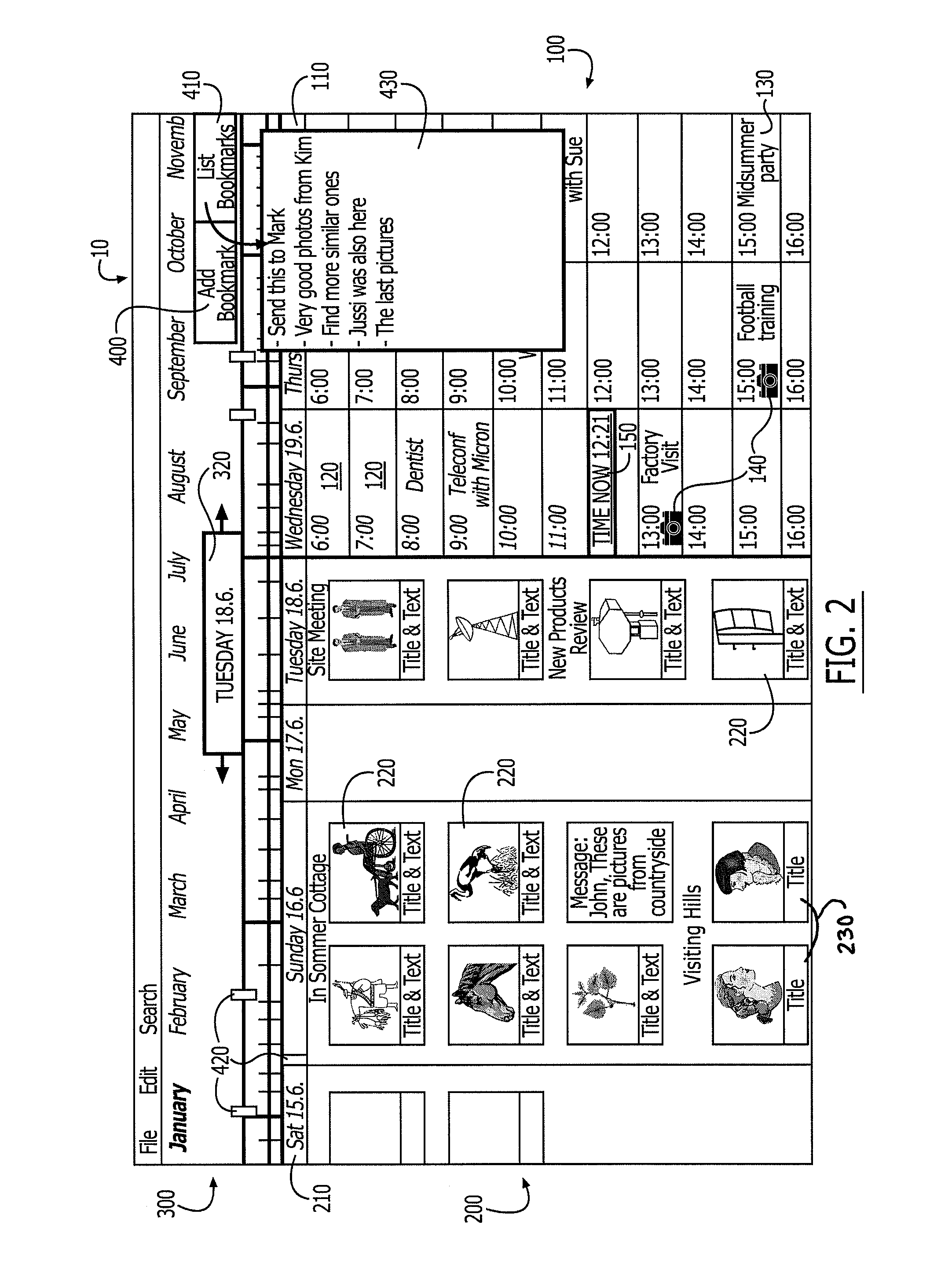
Bookmarking and annotating in a media diary application
InactiveUS8010579B2Increase awarenessEasily and efficiently locatingData processing applicationsDrawing from basic elementsGraphicsBookmarking
A media diary or media management application implemented in a digital device that incorporates a bookmarking and / or annotating mechanism for providing graphical enhancement to media files, calendar events and time periods displayed in the media management application. In addition, the bookmarking and annotation mechanism provides for text notes to be associated with the media files, calendar event or time period and for the text note to be accessible through the bookmark or annotation.
Owner:NOKIA CORP
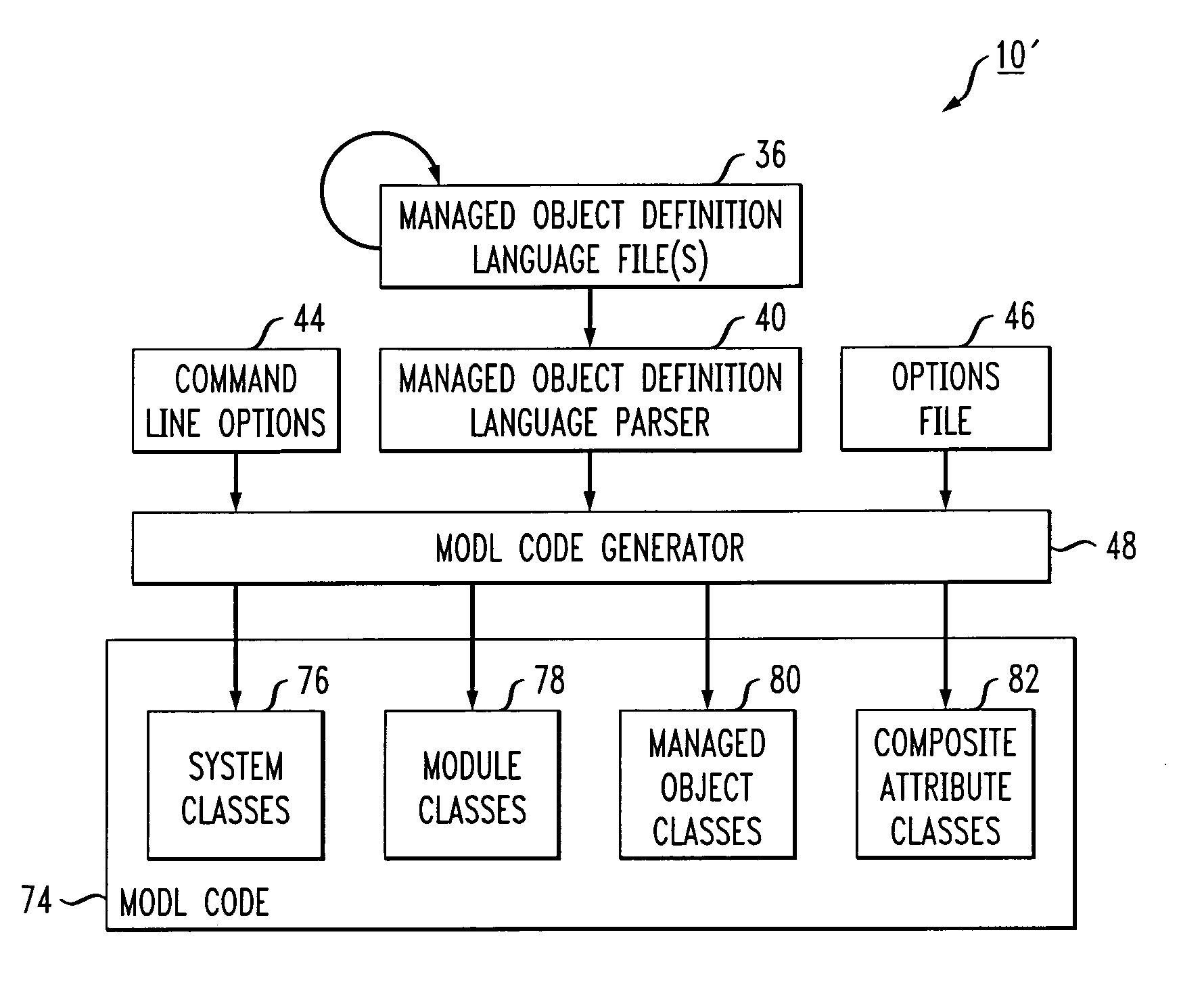
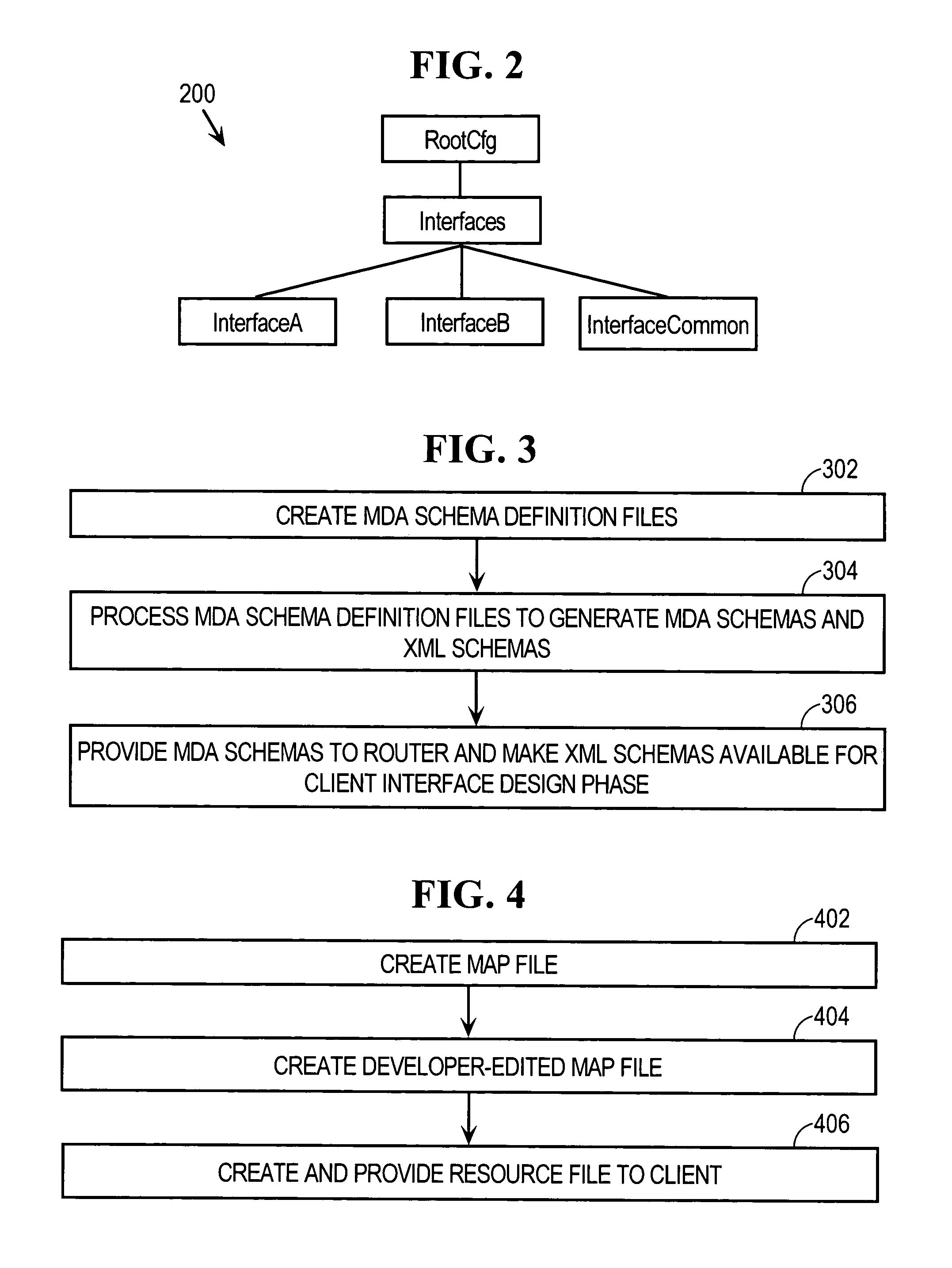
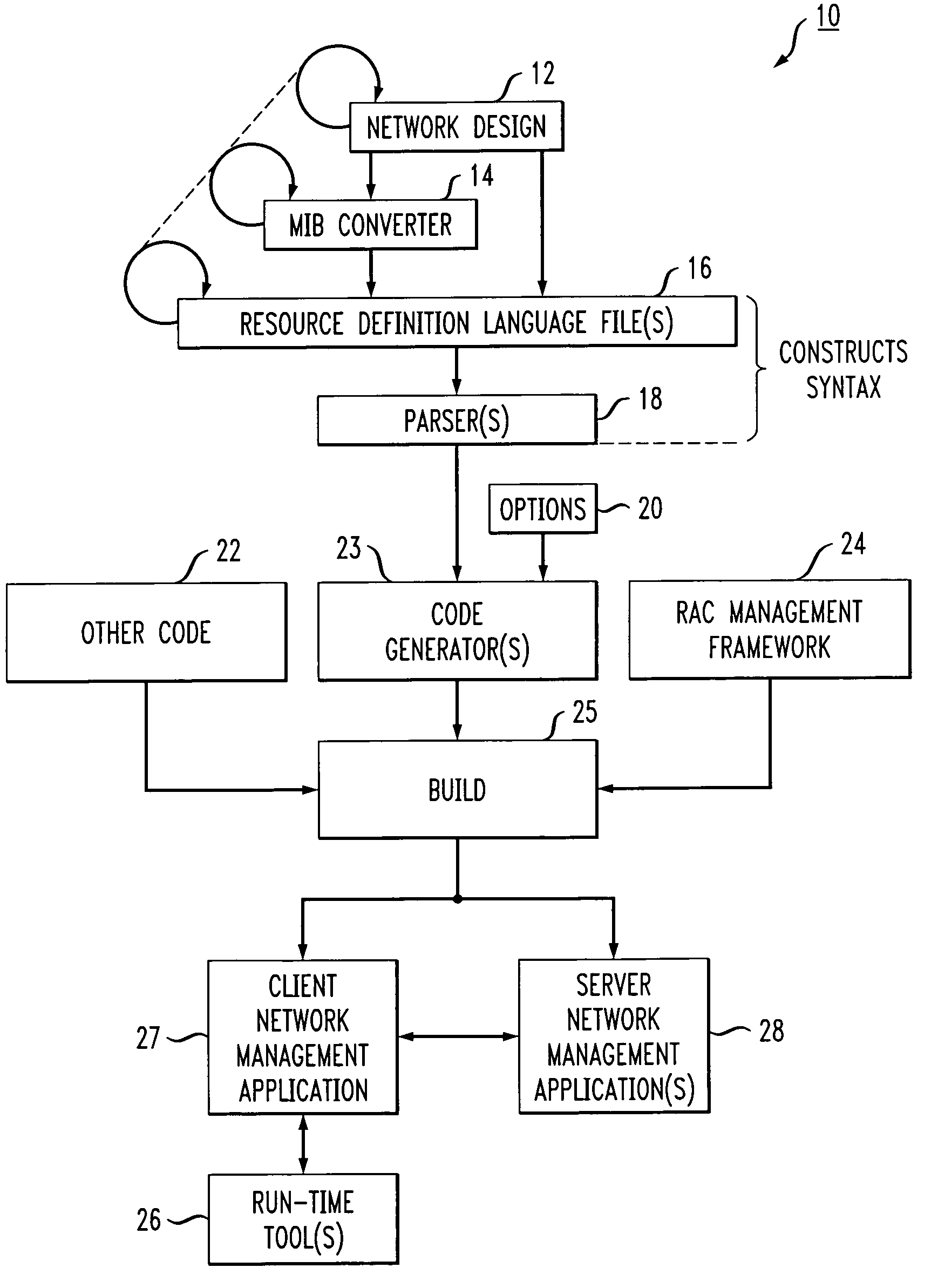
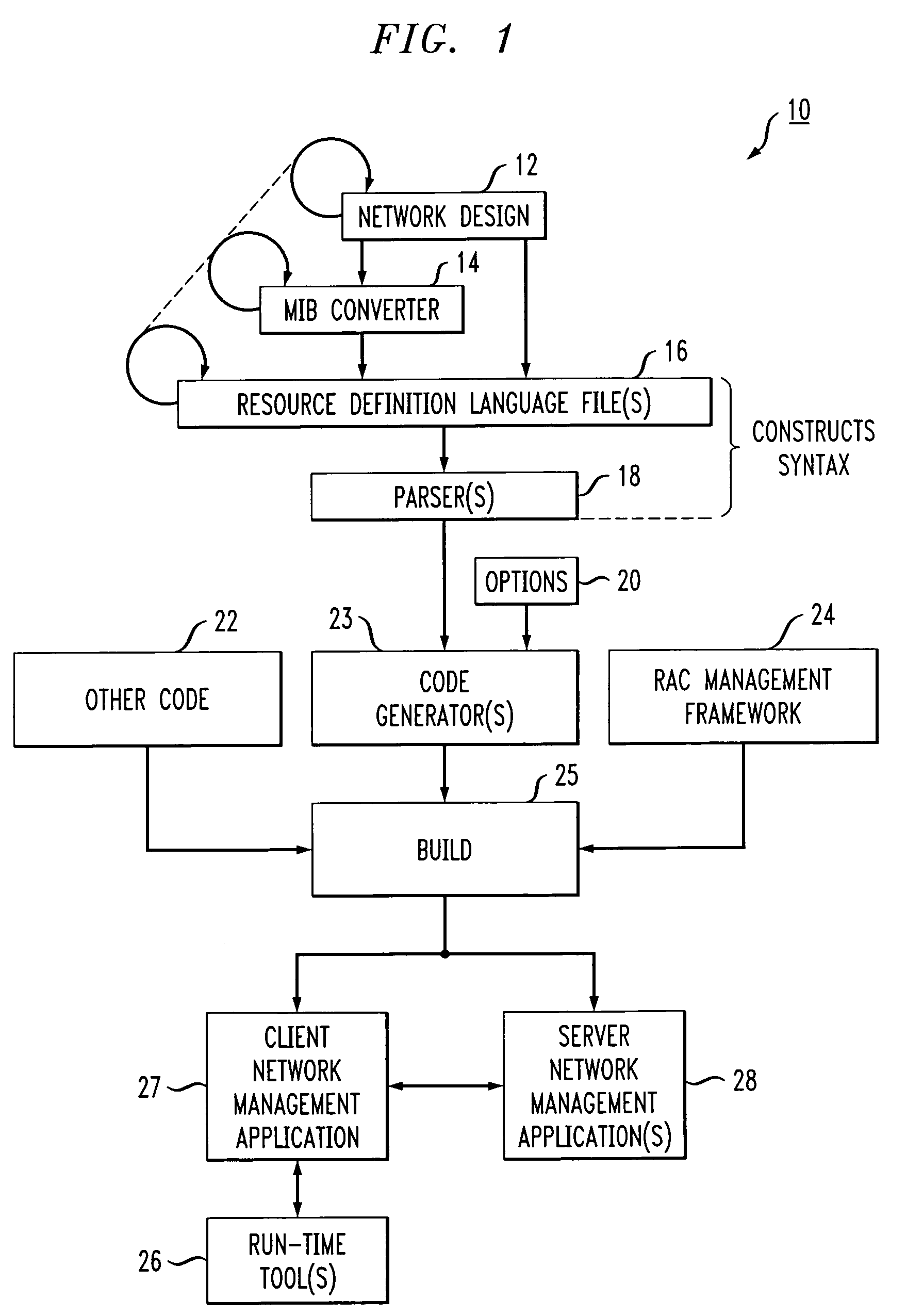
Resource definition language for network management application development
InactiveUS20050278709A1Software designSpecific program execution arrangementsManagement objectSoftware engineering
Methods of defining a distributed system or network to facilitate development of an application program to manage the distributed system or network are provided. In one embodiment, the method includes: a) defining managed objects in a resource definition language and storing the definition in resource definition language files, wherein the definition is based on an existing design and hierarchical structure of the distributed system or network, wherein parent-child relationships between the managed objects are identified in the resource definition language files using the resource definition language to define the managed objects in relation to the hierarchical structure, b) parsing the resource definition language files to ensure conformity with the resource definition language and creating an intermediate representation of the distributed system or network from the conforming resource definition language files, and c) processing the intermediate representation to form programming language classes, database definition files, and script files.
Owner:LUCENT TECH INC
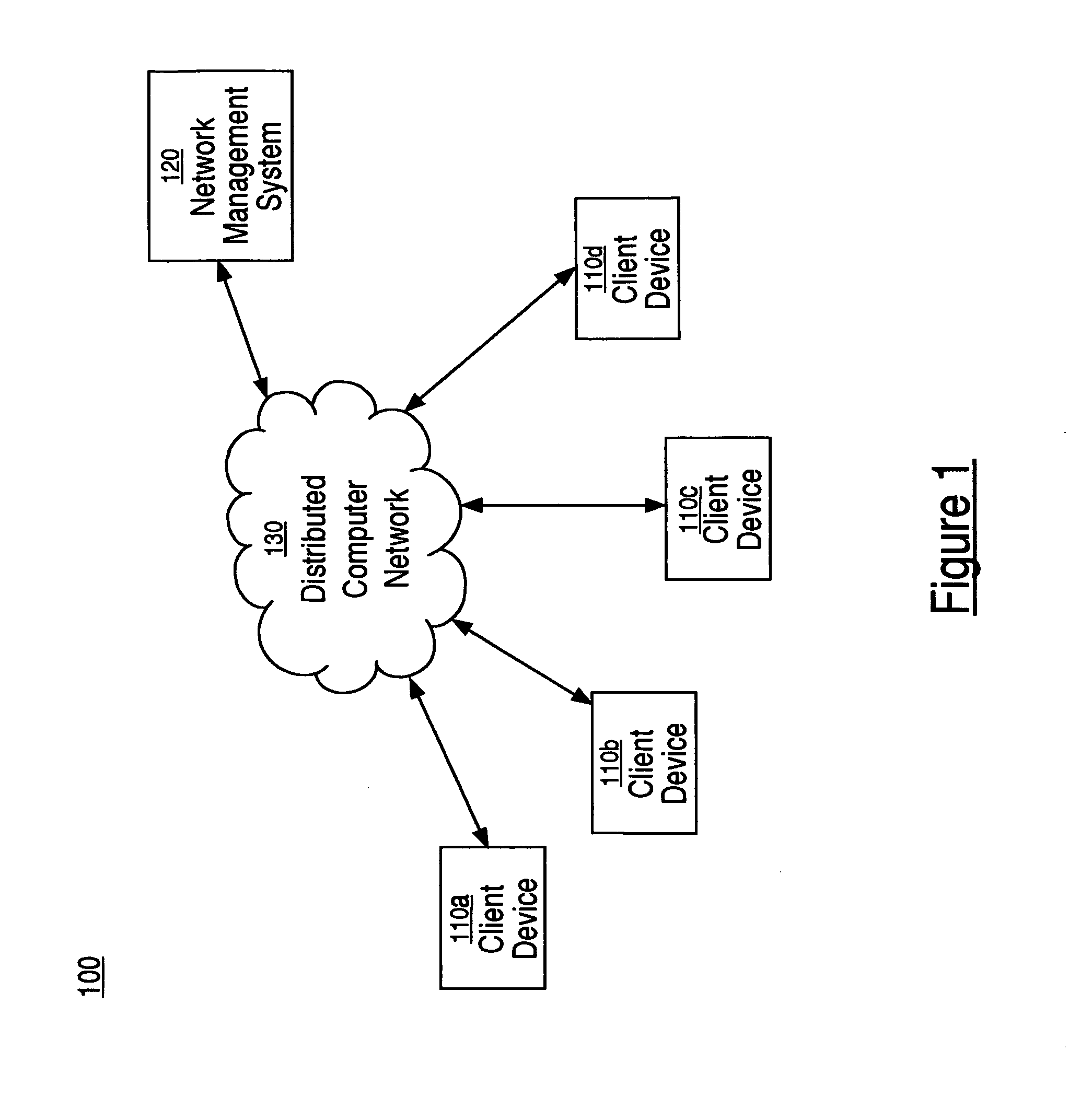
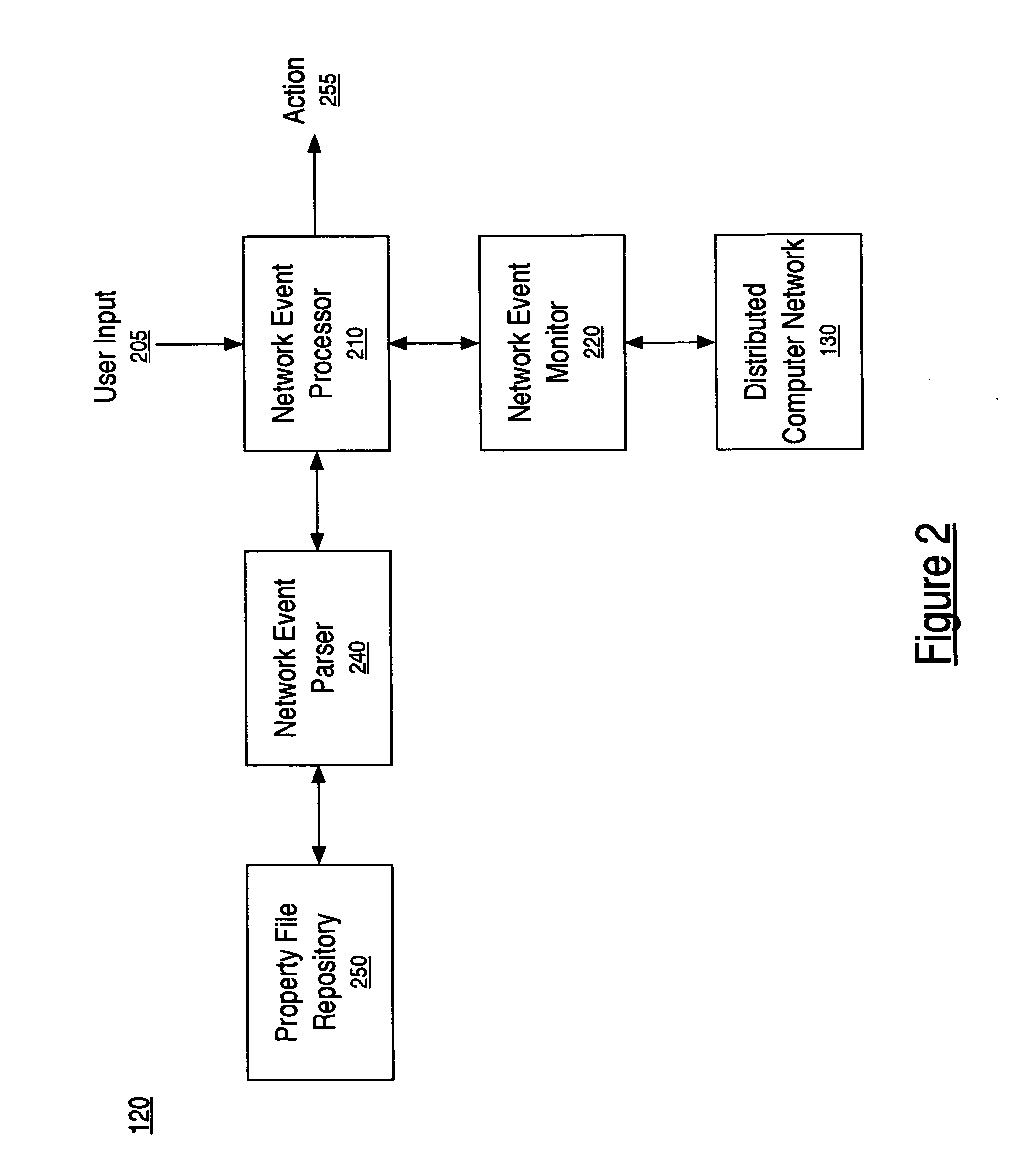
Method and system for event-driven network management
InactiveUS20060248179A1Digital computer detailsTransmissionExternal applicationNetwork management application
A method and system for event-driven network management. A network management application is configured to detect a network event generated by an external application and to execute an action in response to detecting said network event, wherein the network management application is configurable to receive information describing the network event and the action. The network event is monitored for. In response to detecting the network event, the action is executed.
Owner:HEWLETT PACKARD DEV CO LP
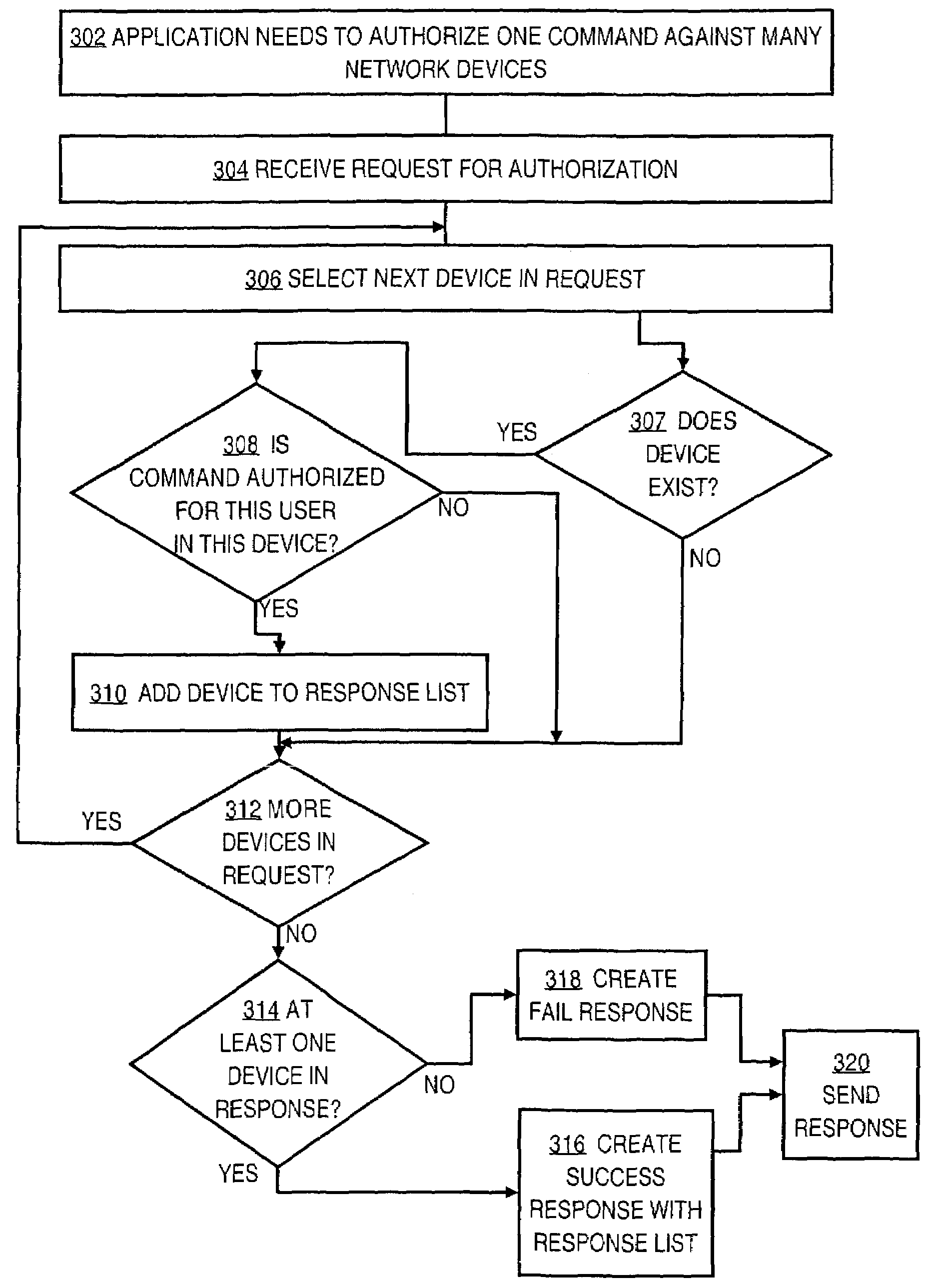
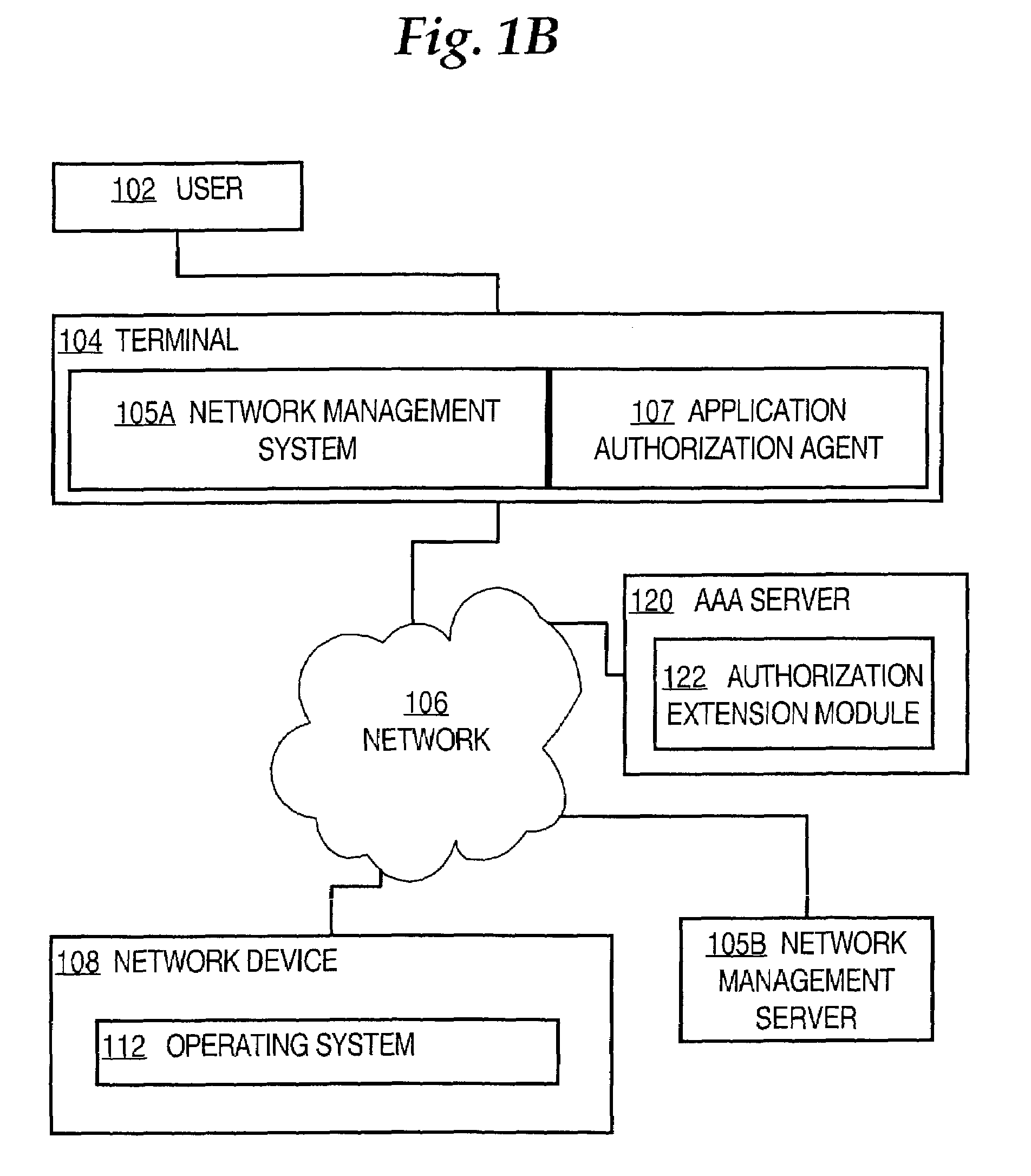
Method and apparatus for authorizing network device operations that are requested by applications
ActiveUS7356601B1Multiple digital computer combinationsTransmissionNetwork management applicationApplication software
A method of authorizing network device operations that are requested by applications is disclosed. A request for authorization from a network management application is received. The request identifies a user who is using the network management application to interact with a network device, the network management application that is seeking to execute one or more application tasks on a network device, the device, and the application tasks. A determination whether the specified user is authorized to execute the application tasks on the device is made. A success message is sent to the application only when the specified user is authorized to execute the application tasks on the device. Other embodiments support authorizing one application task against a plurality of devices or device groups. TACACS+ may be used for communication. A TACACS+ server that can support application authorization, and associated extensions to the TACACS+ protocol, are described.
Owner:CISCO TECH INC
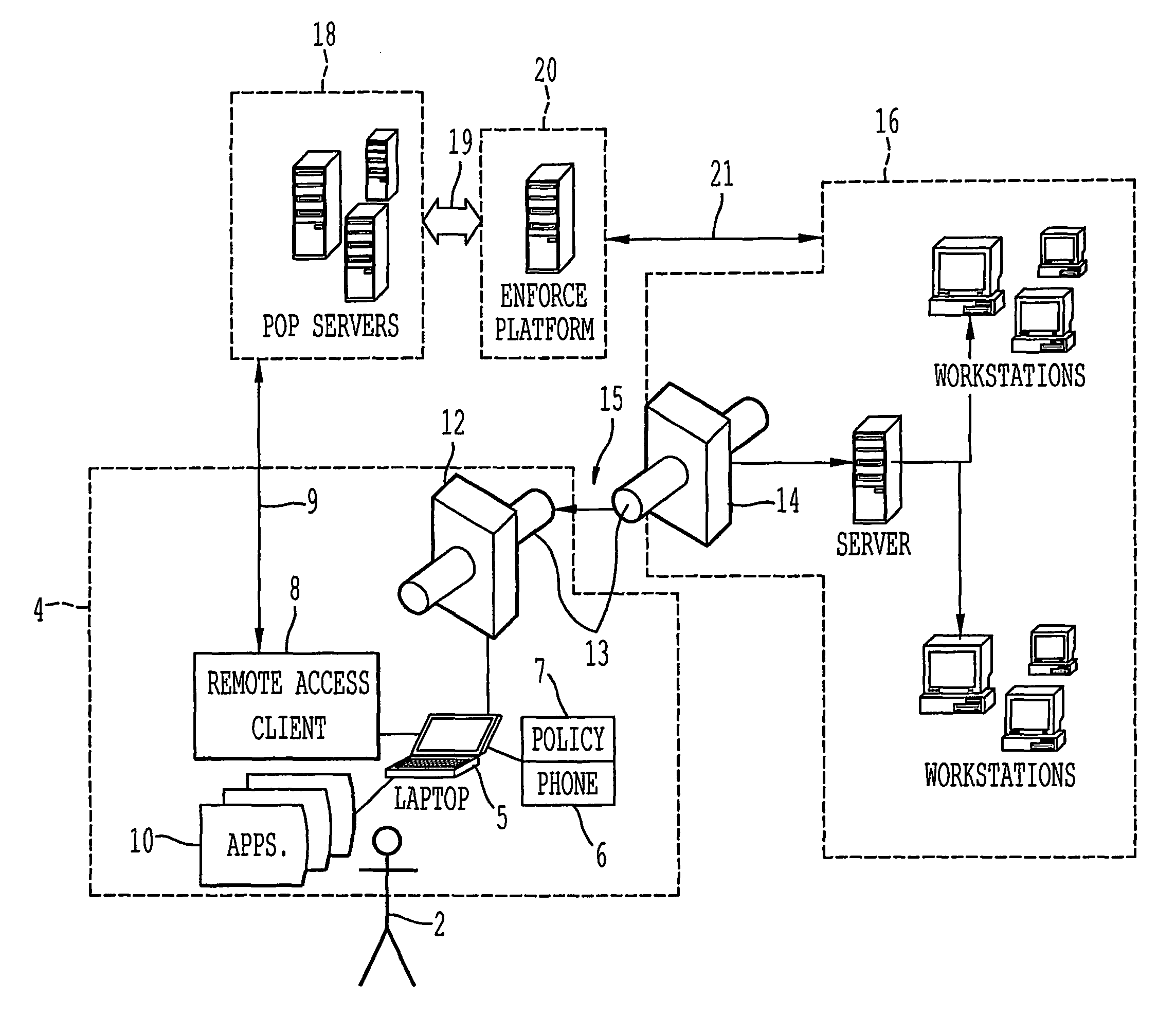
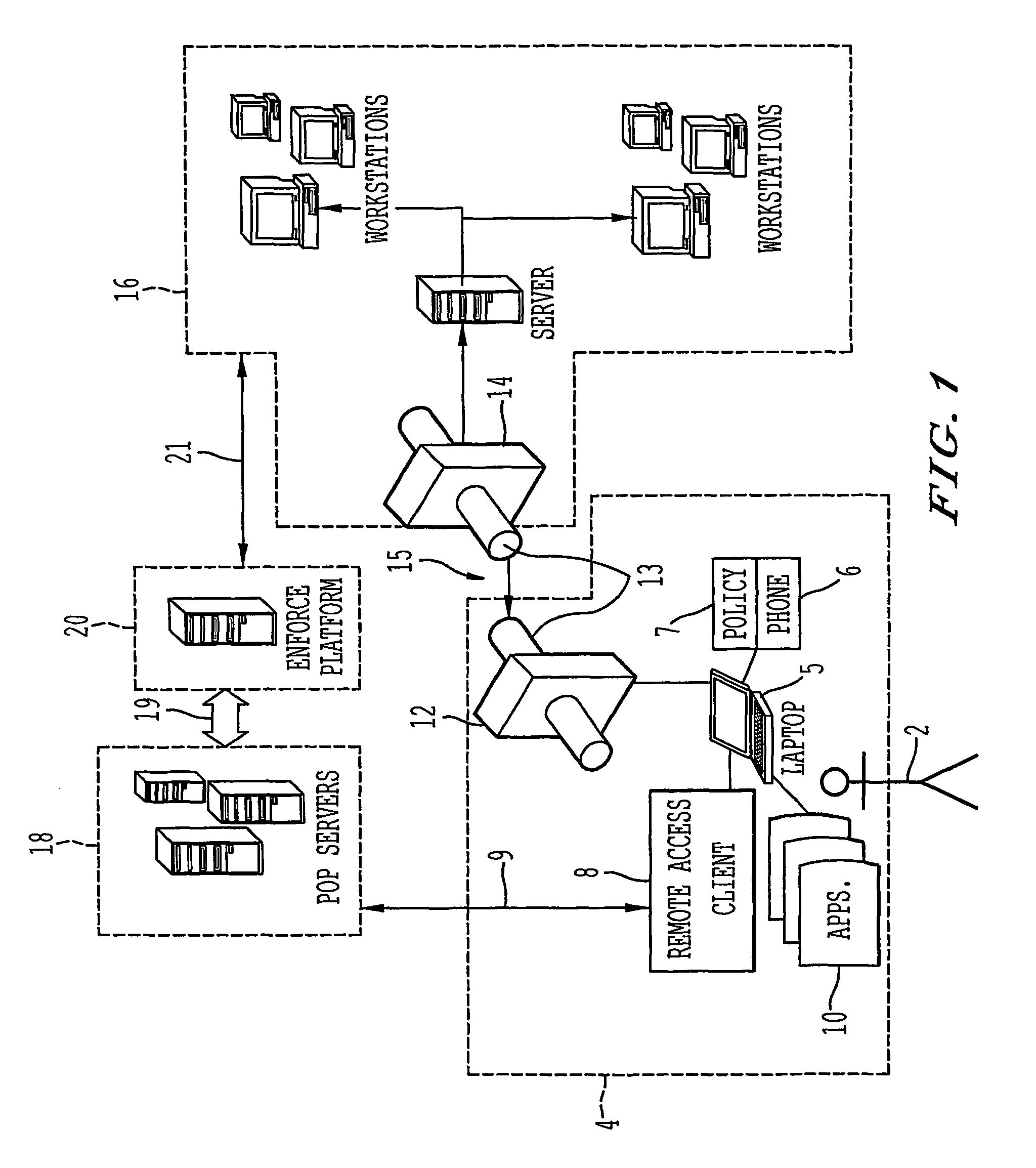
Client-side network access policies and management applications
ActiveUS8200773B2Digital data processing detailsMultiple digital computer combinationsData terminalNetwork management application
A remote access client is provided for enabling communication between a remote data terminal configured to access a public network, and an enterprise network by way of a VPN tunnel through the public network. The remote access client includes at least one application program interface (API) to receive a first verification of the operating state of a predetermined application of the remote data terminal to enable a connection agent for establishing a point of presence on the public network. Upon connection to the point of presence, the API exchanges data between the remote access client and the predetermined application of the remote data terminal. The remote access client receives a second periodic verification of the operating state of the predetermined application via the API for terminating the connection to the point of presence upon the absence of the second verification. The point of presence enables the VPN tunnel for transporting data from the remote data terminal to the enterprise network across the public network.
Owner:GINEGAR LLC
System, method, and service for automatically and dynamically composing document management applications
InactiveUS20060095830A1Efficient processingShorten cycle timeForecastingOffice automationDocumentation procedureDocument analysis
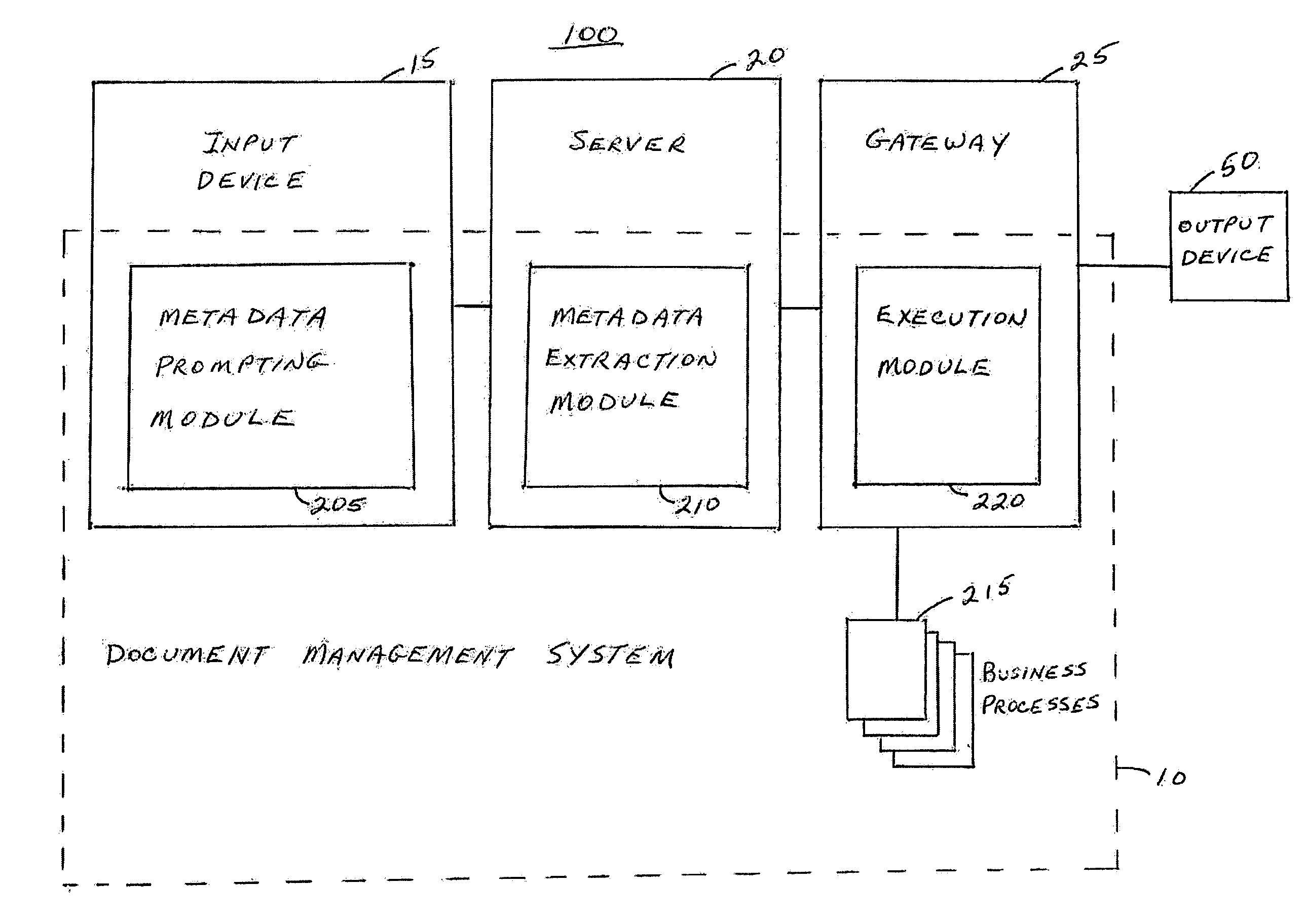
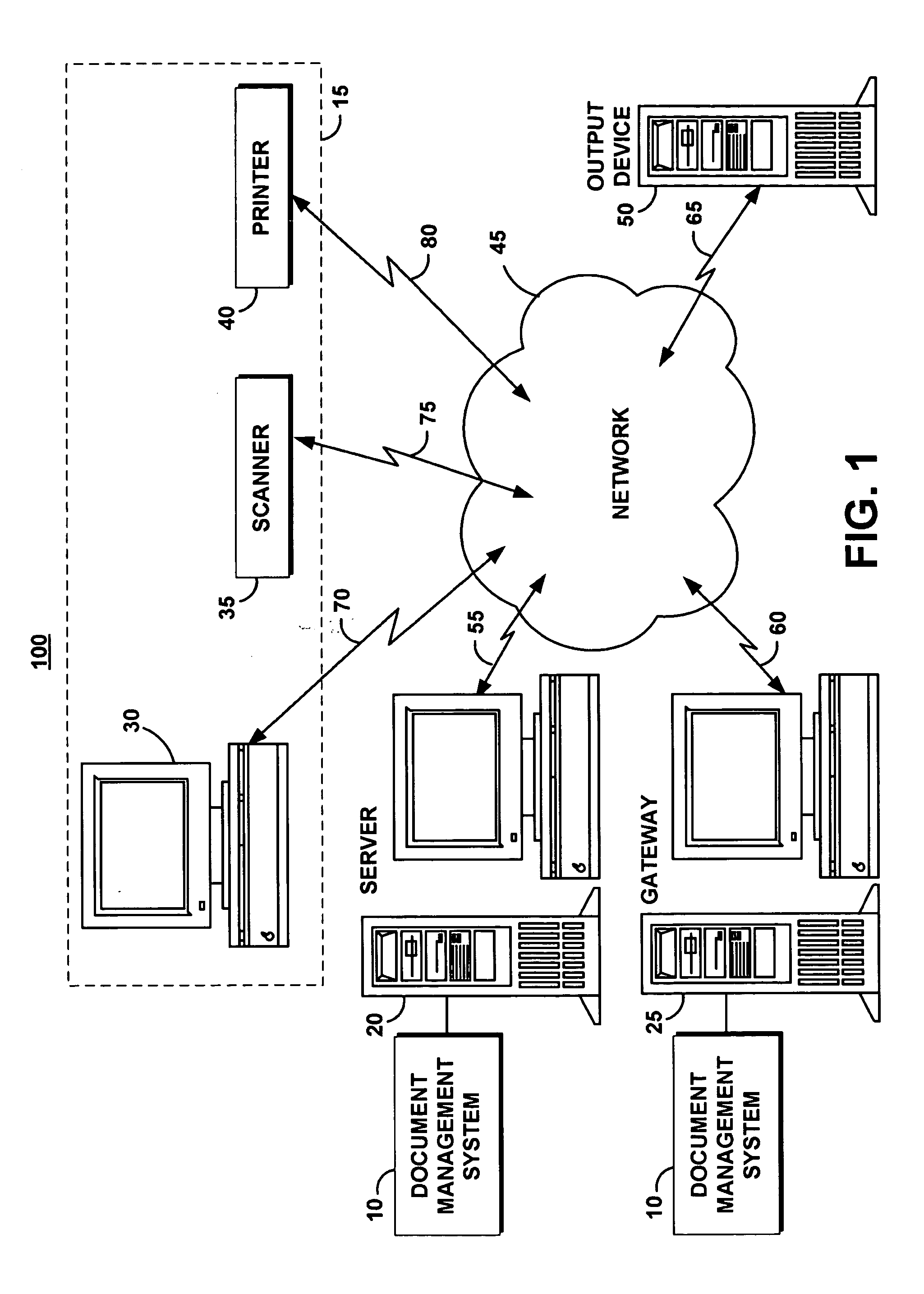
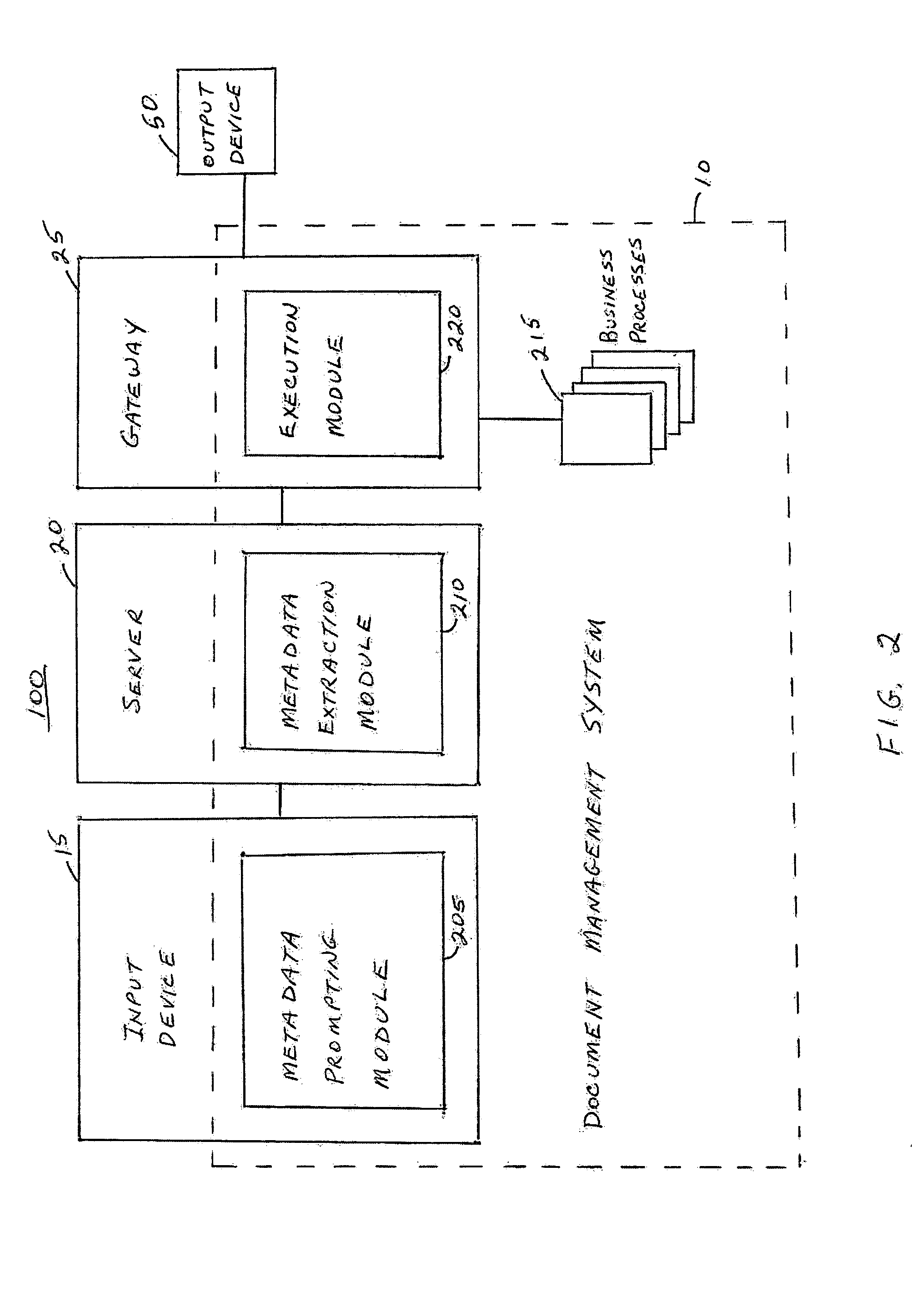
A document management system applies relevant document analysis, metadata extraction, and business process association algorithms and methodology to automatically and dynamically classify documents for routing, processing, and executing customized business logic. The document management system accepts documents from one or more channels, classifies the document and extracts metadata, executes customized application profiles and triggers business logic associated with the process. The document management system comprises a rules engine to detect and classify unstructured forms as well as structured forms, where the locations of attributes and visual layout are not fixed. The document management system provides automatic linkage between disparate systems that manages documents for the complete execution of a business process.
Owner:IBM CORP
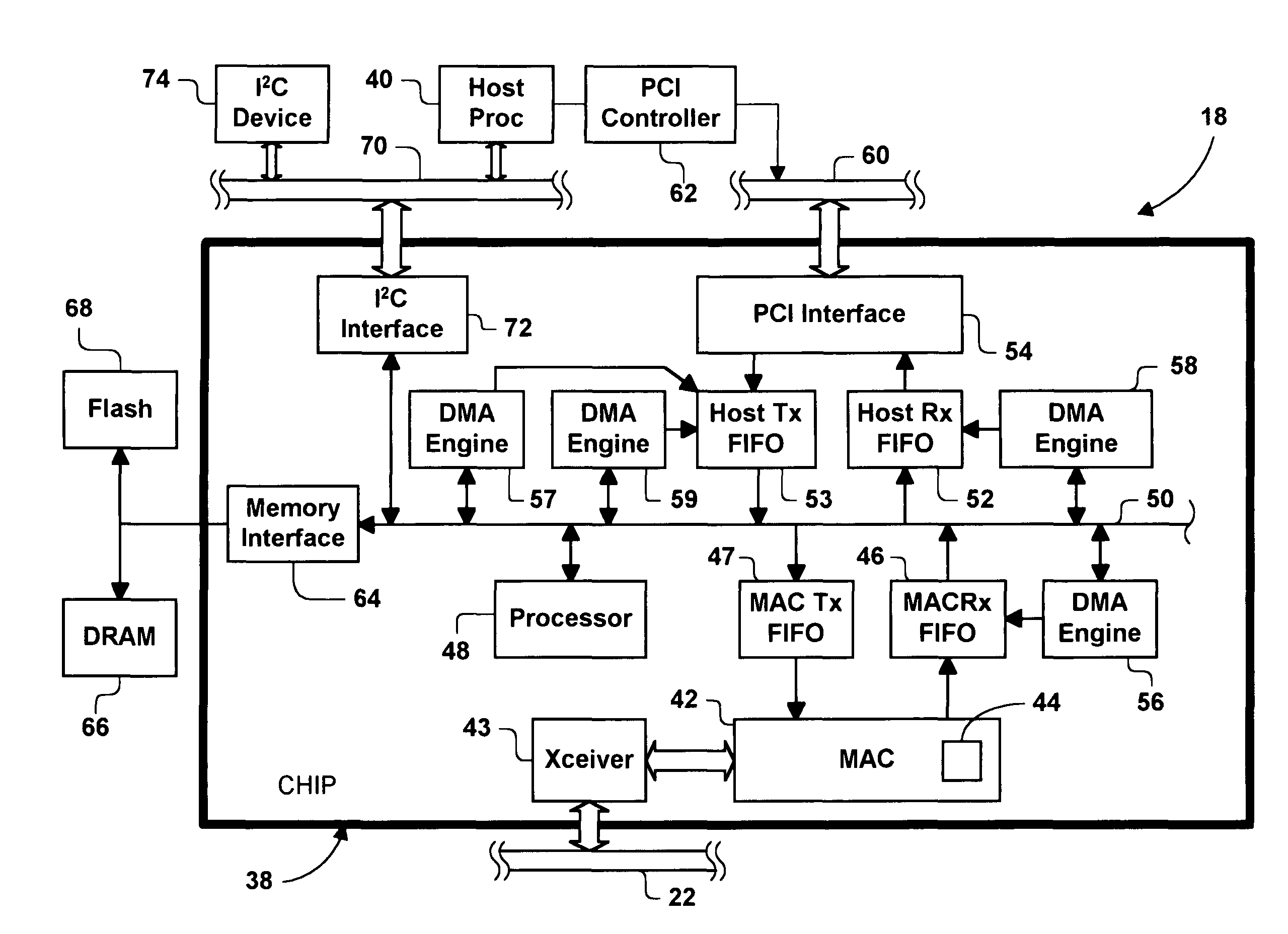
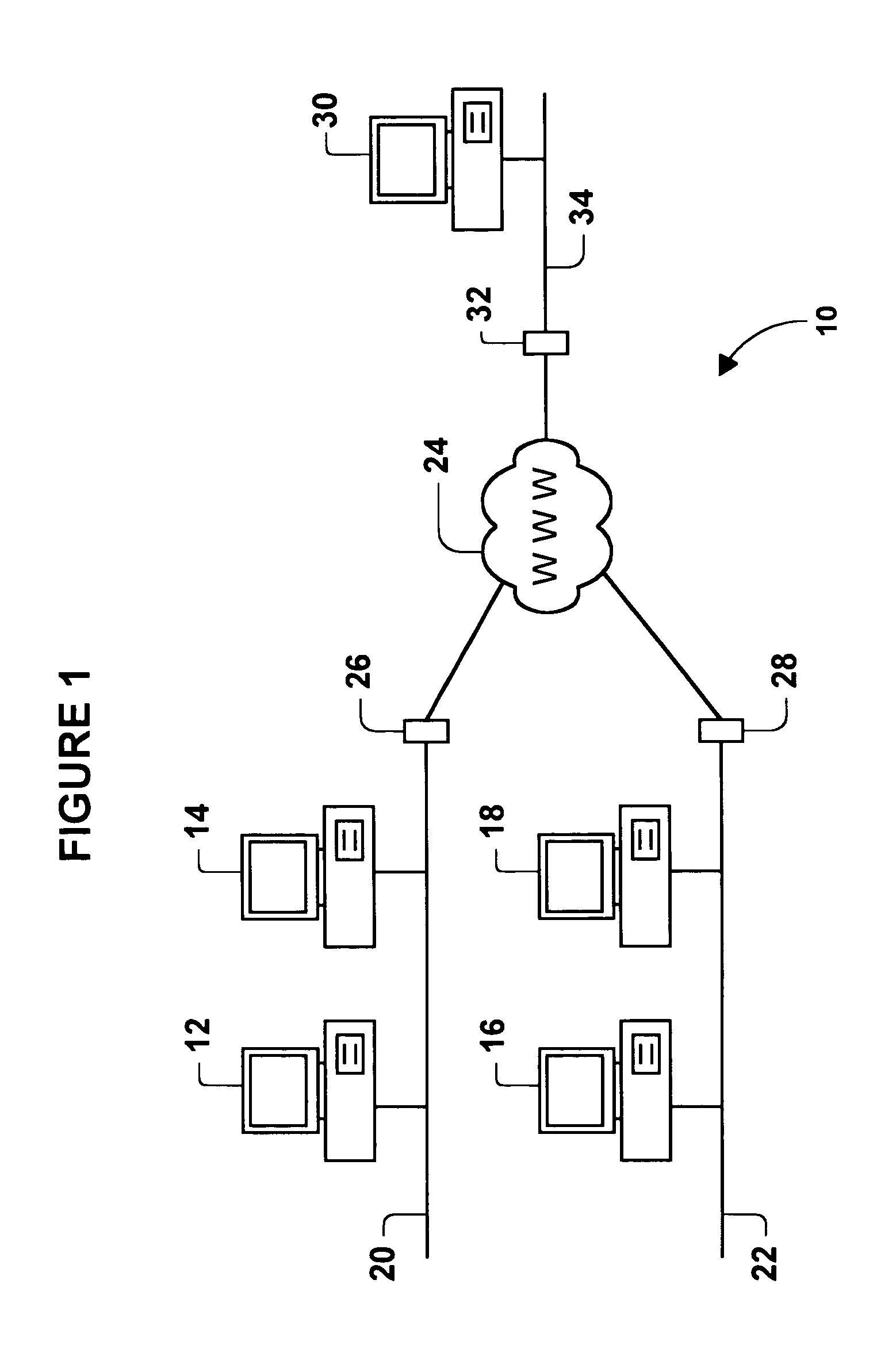
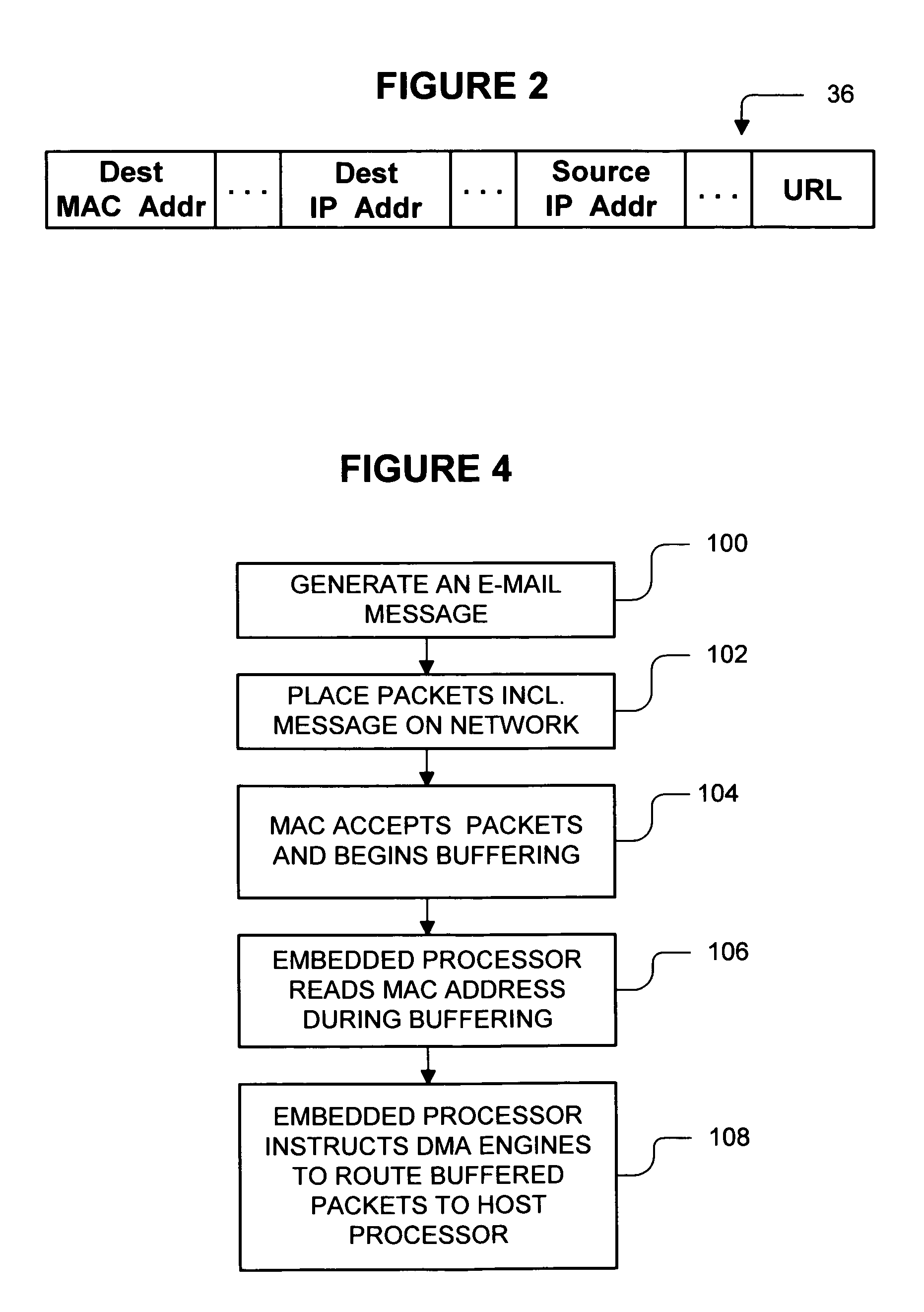
Web server chip for network manageability
A network device includes a web server chip that is connectable to a computer network. The web server chip includes an embedded processor that is programmable to function as a manageability web server, obtain manageability information about the network device and send the manageability to a network manager. The web server chip further includes an interface for communicating with an I2C bus in the network device. The embedded processor is programmable to obtain manageability information about devices connected to the I2C bus. The embedded processor is also programmable to control fan controllers, power supply controllers and other controllers connected to the I2C bus. This, in turn, allows a network manager to command the web server chip to remotely power up and power down the network device. Thus, the web server chip can perform network management functions without burdening the host processor of the network device. If network communications are performed via HTTP, the embedded processor can be programmed to implement an HTTP server, and the network manger can use a web browser and HTML files to run network management software.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
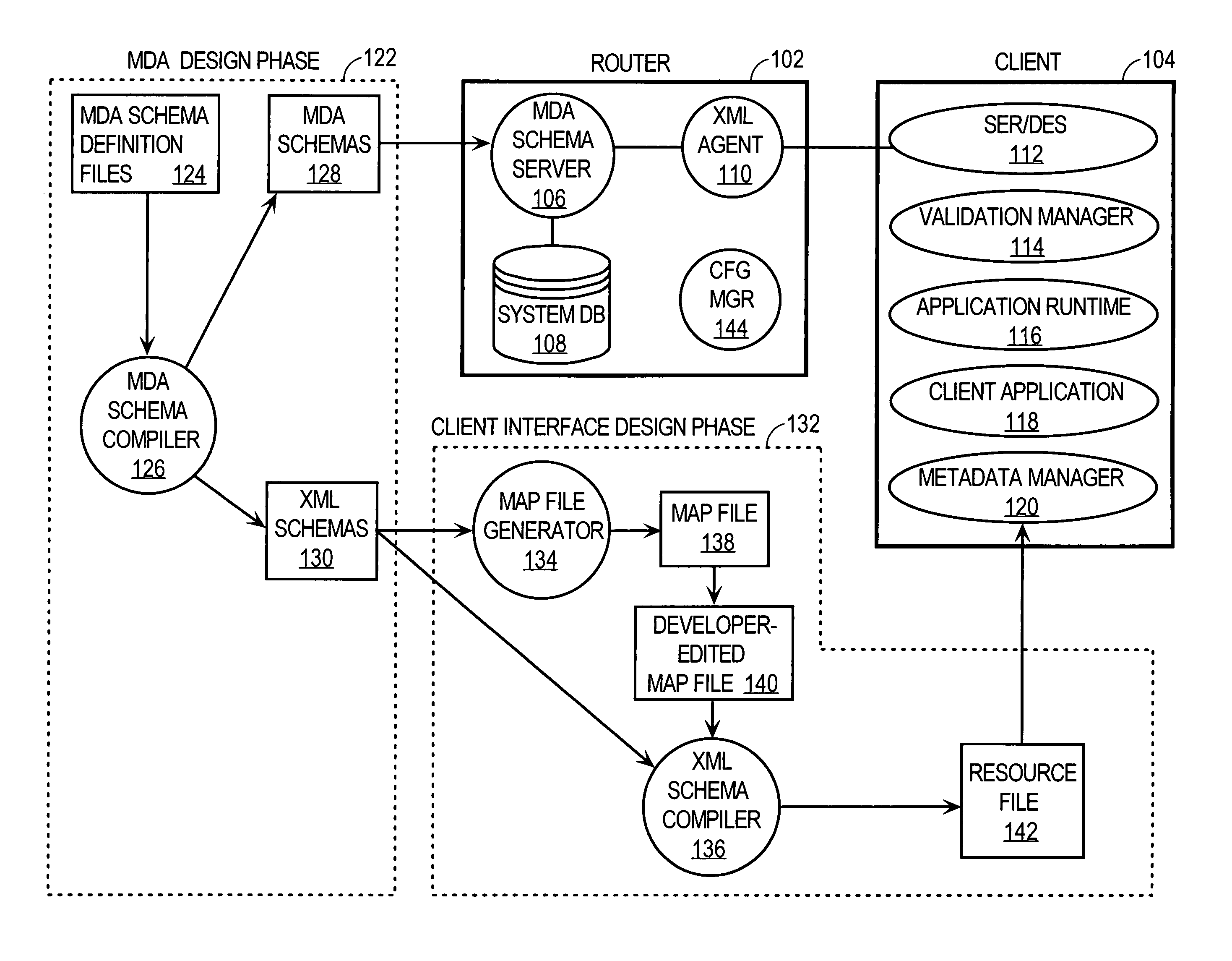
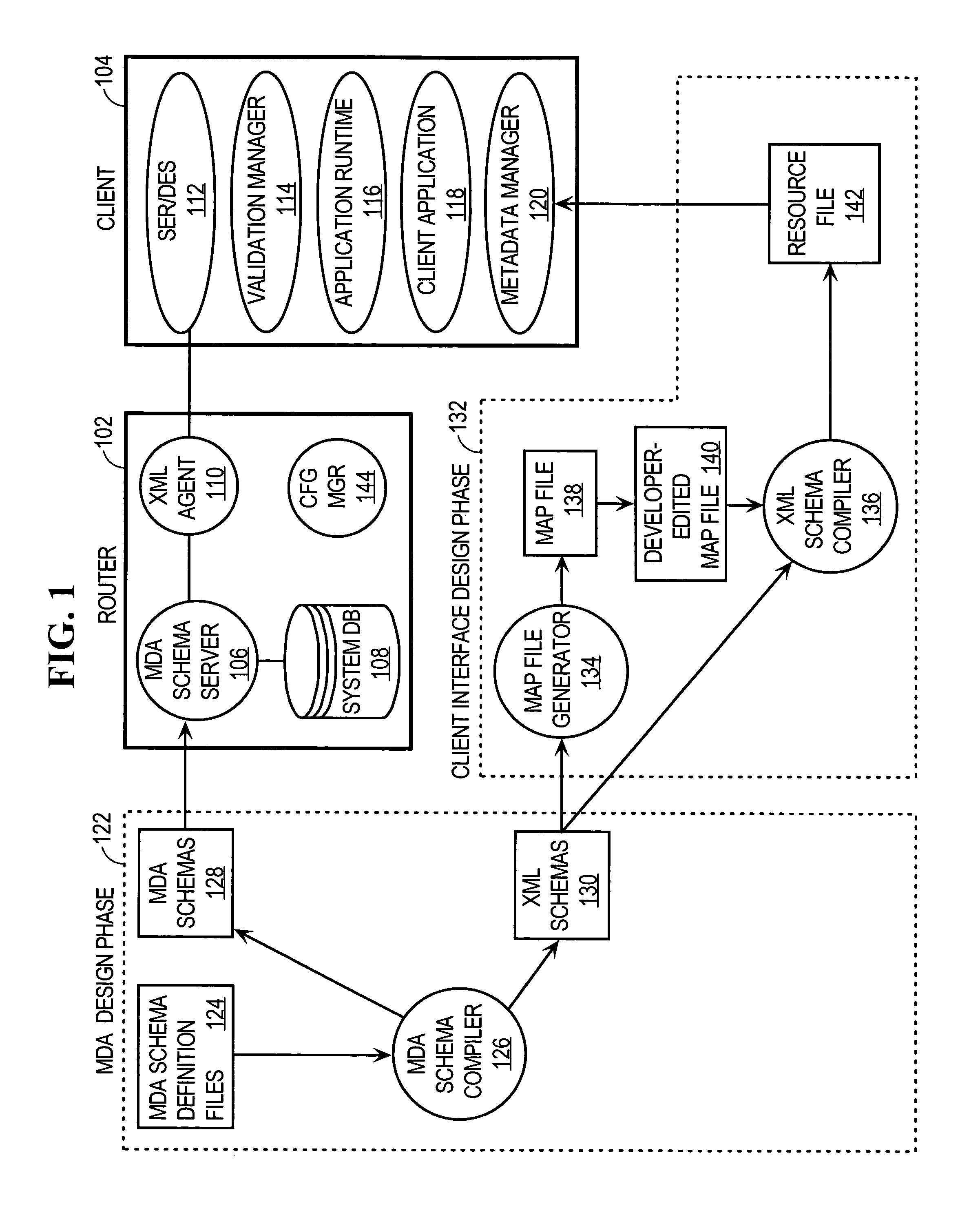
Server-side XML-based development environment for network device management applications
ActiveUS7529825B1Multiple digital computer combinationsTransmissionXML schemaNetwork management application
An end-to-end approach is provided for developing and maintaining network device management applications. The approach includes an XML-based development environment for network device management applications that uses Management Data API (MDA) schemas that define a hierarchical data model for components supported by a network device. The XML-based development environment also uses XML schemas to define a common XML-based interface used by management applications to access management data maintained on the network device. The approach provides programmatic access to network device management data and management data schema with an XML-based data model and interface that is consistent across all network device components. The approach includes mechanisms for automatically generating XML requests that conform to a hierarchical data model from requests that conform to a table-based data model. The approach also includes mechanisms for automatically extracting data from XML replies and conforming to the table-based data model.
Owner:CISCO TECH INC
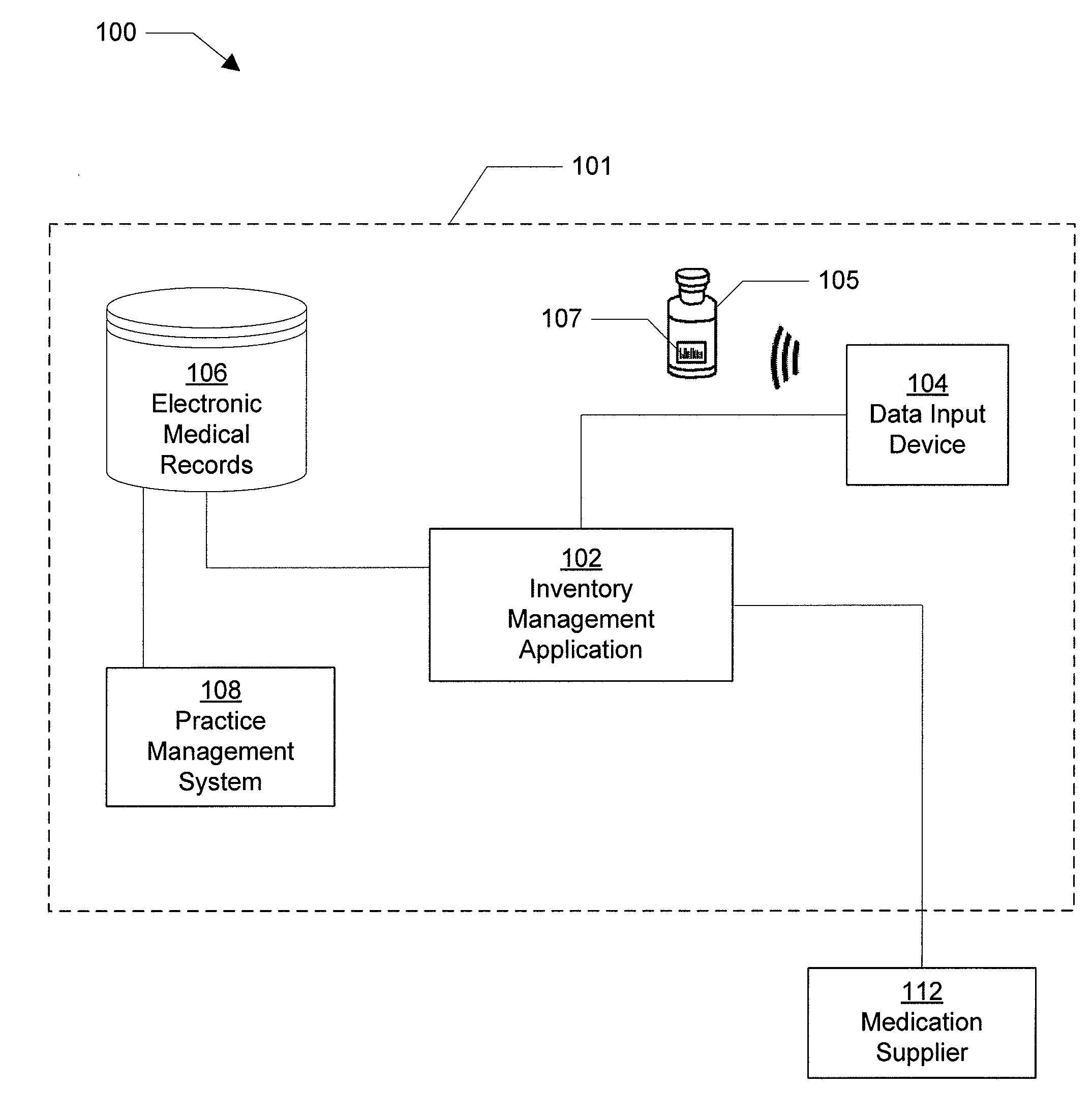
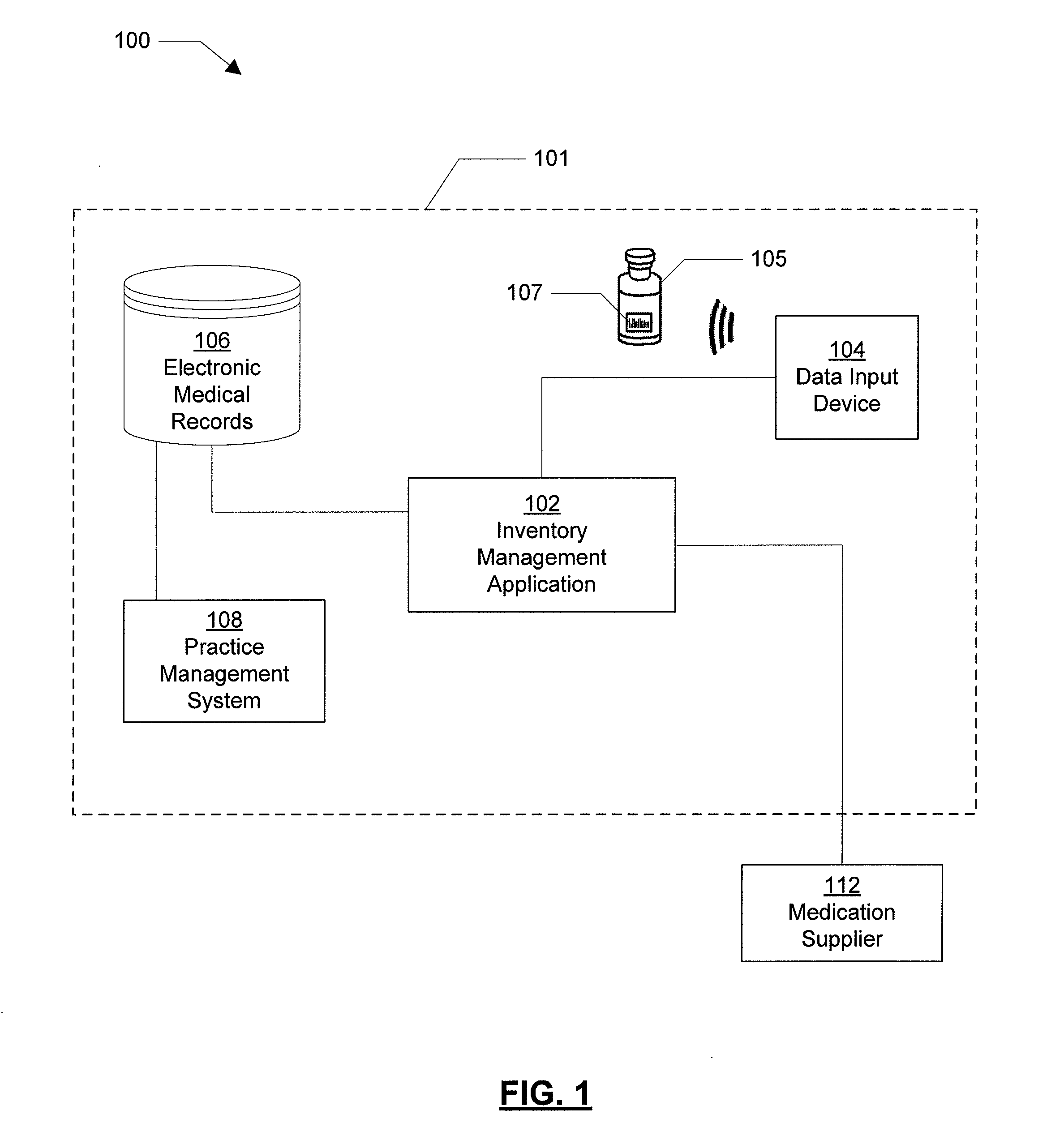
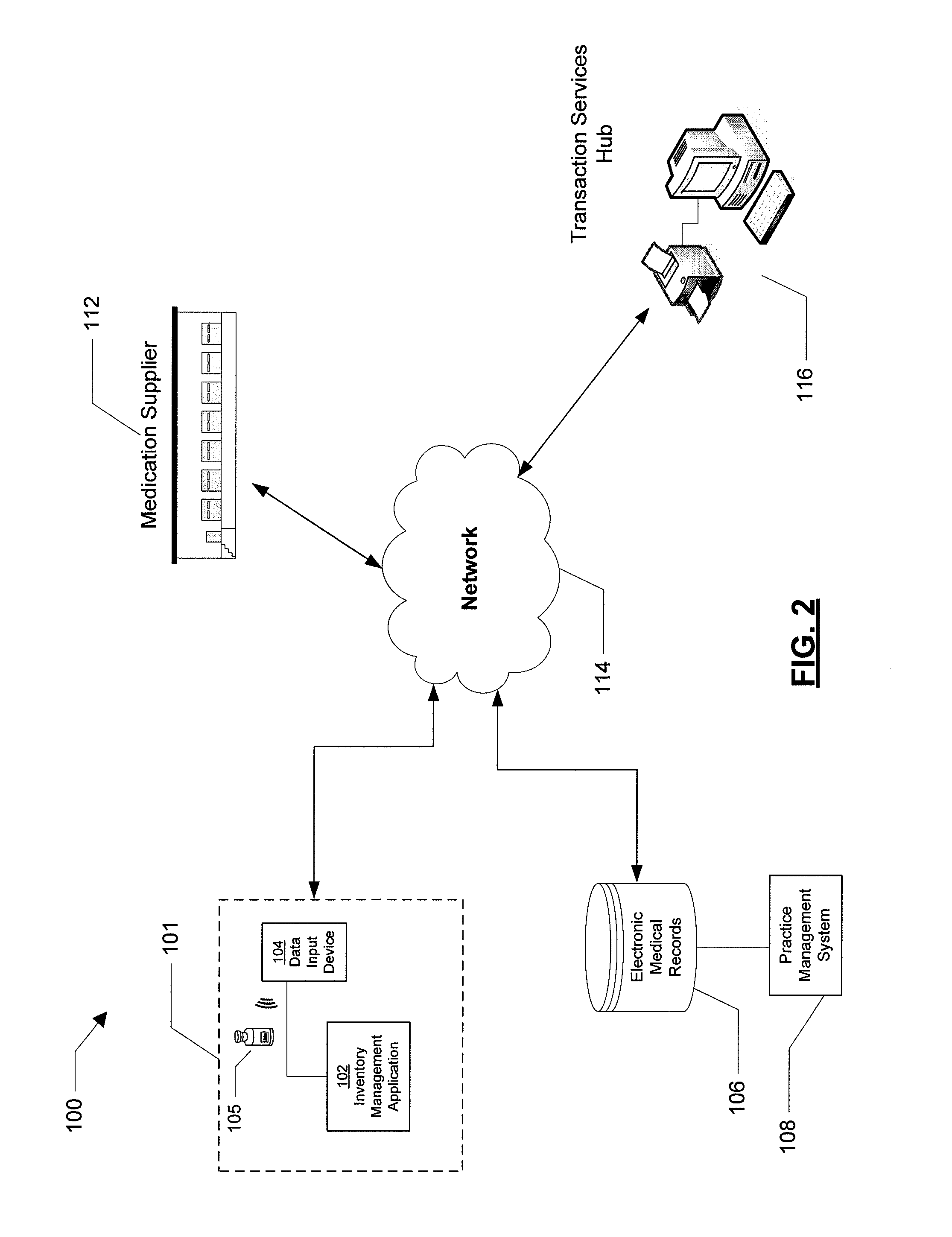
Inventory Management System For A Medical Service Provider
InactiveUS20080270178A1Improved oncology inventory management systemImprove inventory accuracyData processing applicationsHealthcare resources and facilitiesMedical recordApplication software
A system, method, and computer program product are provided for an improved inventory management system. The system supports a medical service provider by interfacing an inventory management application with a database of electronic medical records. In one embodiment, a single graphical user interface interfaces the inventory management application with the database of electronic medical records, thus providing a simplified, transparent solution as compared to the separate, independent, and non-interfaced systems currently available. By interfacing the inventory management application with the database of electronic medical records, inventory accuracy may be increased and processing times may be decreased.
Owner:MCKESSON SPECIALTY DISTRIBUTION
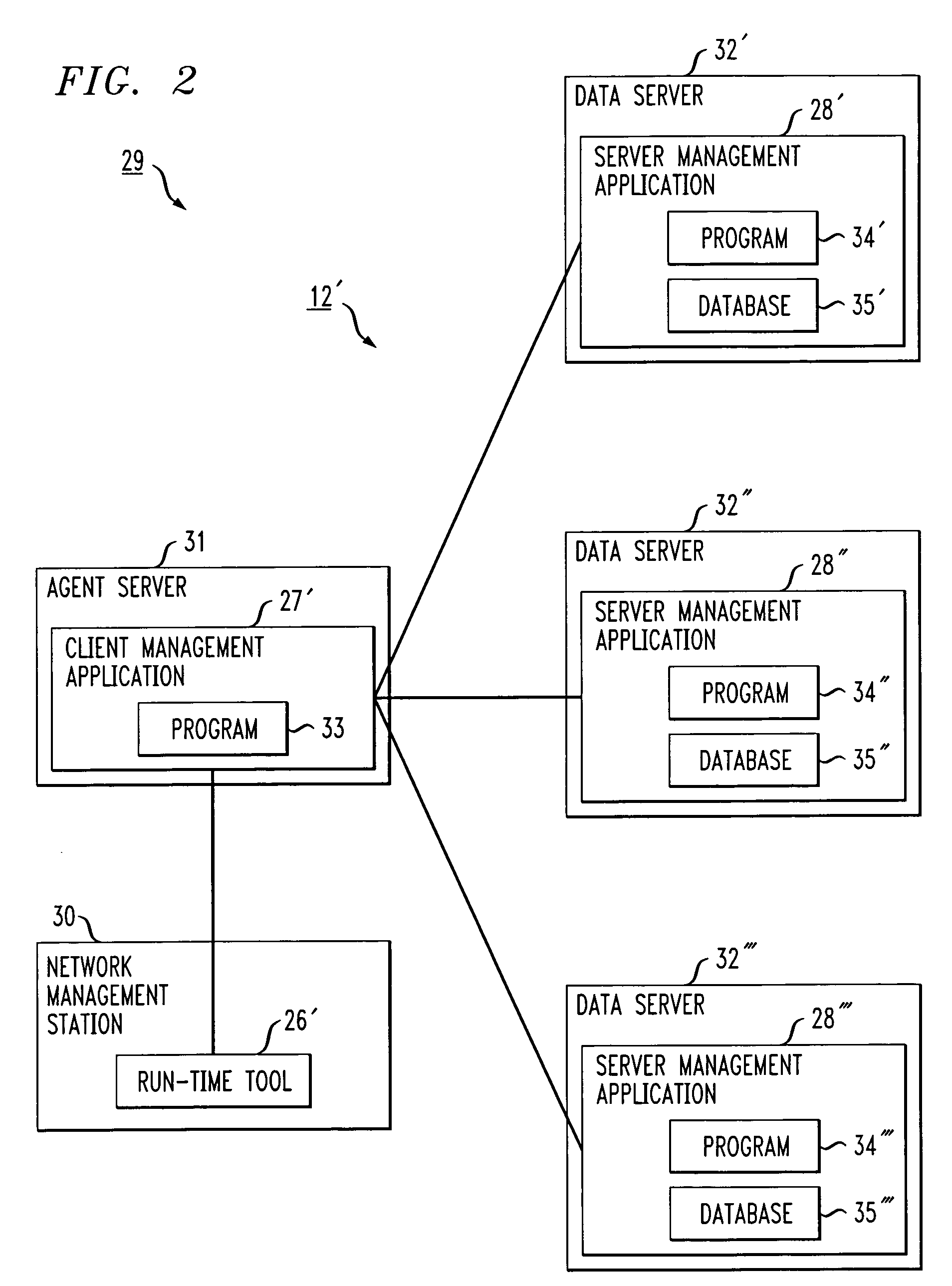
Data management and persistence frameworks for network management application development
InactiveUS20060004856A1Software designSpecial data processing applicationsManagement objectNetwork management application
Methods of developing an application program to manage a distributed system or network are provided. In one embodiment, the method includes: a) defining managed objects in a resource definition language and storing the definition in resource definition language files, b) parsing the resource definition language files to ensure conformity with the resource definition language and creating an intermediate representation of the distributed system, c) processing the intermediate representation to form programming language classes, database definition files, and script files, d) developing a reusable asset center framework to facilitate development of the application program, the reusable asset center including a data management framework that provides creation, deletion, modification, and browsing functions and / or a persistence framework that provides persistent data storage functions in conjunction with the managed objects and the database, and e) building the application program from the programming language classes, database definition files, script files, and the reusable asset framework.
Owner:LUCENT TECH INC
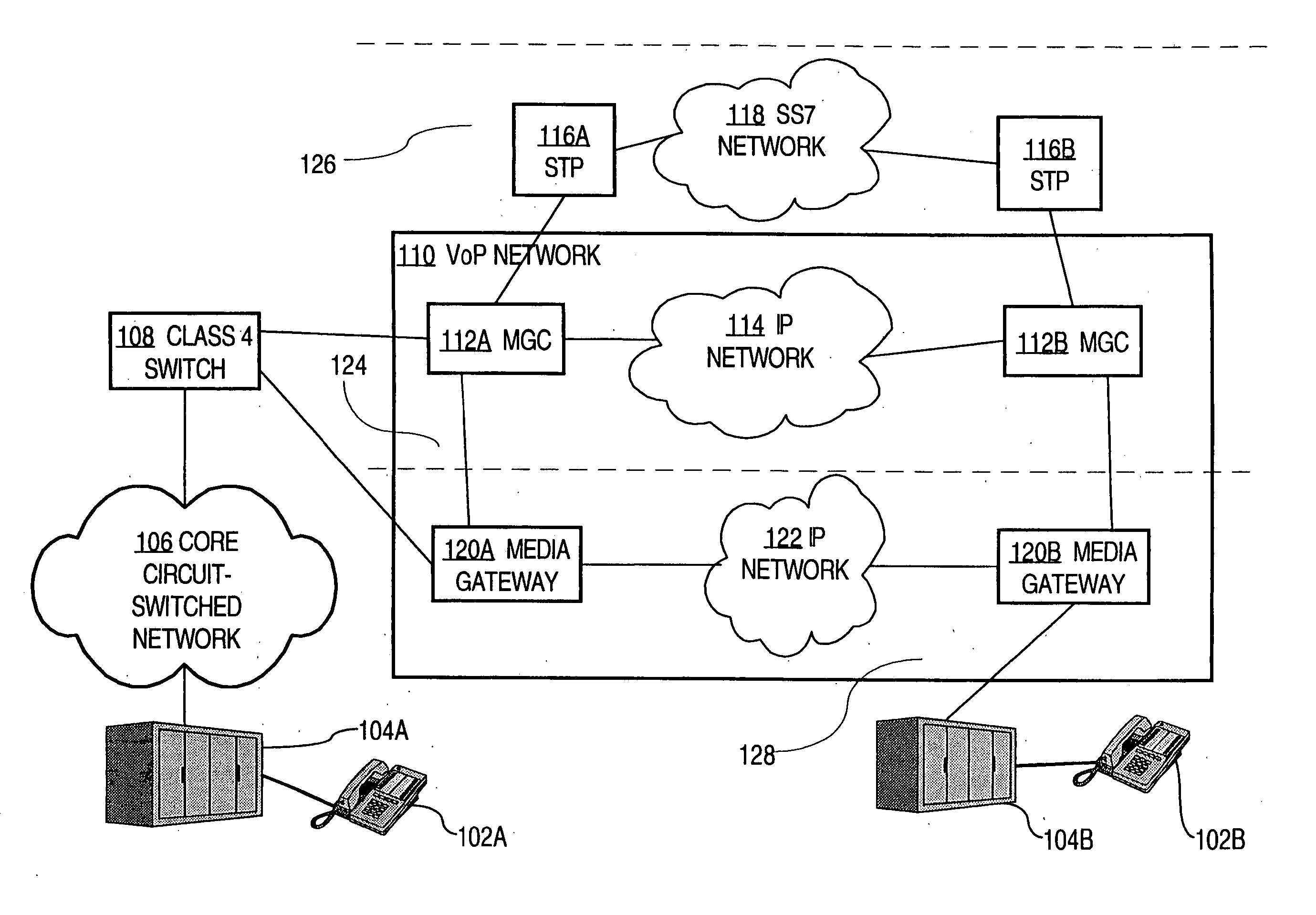
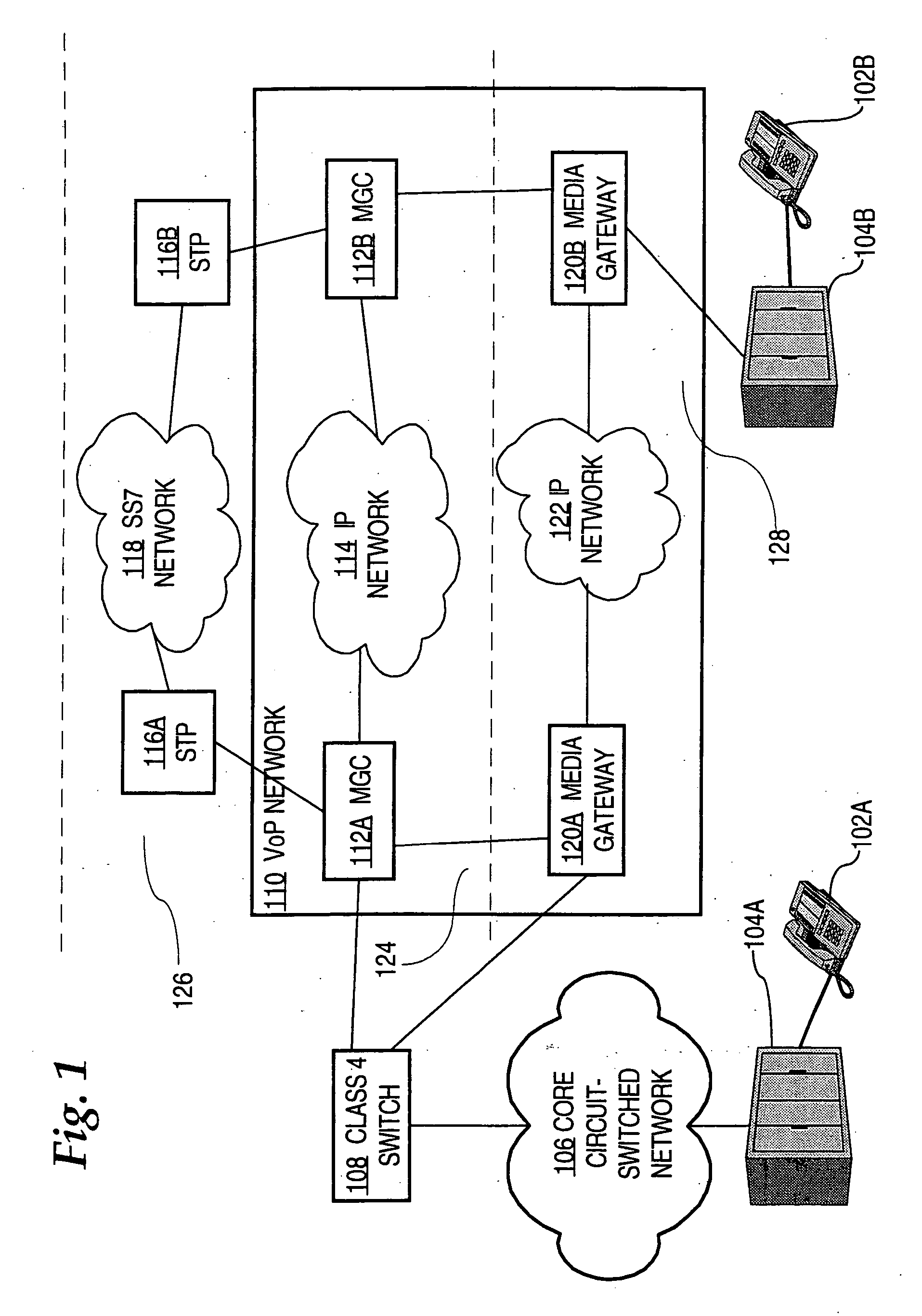
Managing packet voice networks using a virtual switch approach
InactiveUS20070008958A1Reduce in quantityTo offer comfortInterconnection arrangementsSupervisory/monitoring/testing arrangementsUser inputNetwork management application
A method for managing packet voice networks using a virtual switch approach and abstract information model approach is disclosed. A virtual switch object represents a virtual switch having a media gateway controller and one or more associated media gateways. User input specifies a configuration operation on the virtual switch and one or more parameter values. One or more configuration instructions are automatically issued to both the media gateway controller and the media gateway, resulting in configuring both the media gateway controller and the media gateway as specified in the user input. As a result, a user can configure or operate on a virtual switch as an atomic entity, for example, in a network management application, without involvement in complicated details of the actual network devices that provide a particular packet voice service.
Owner:CISCO TECH INC
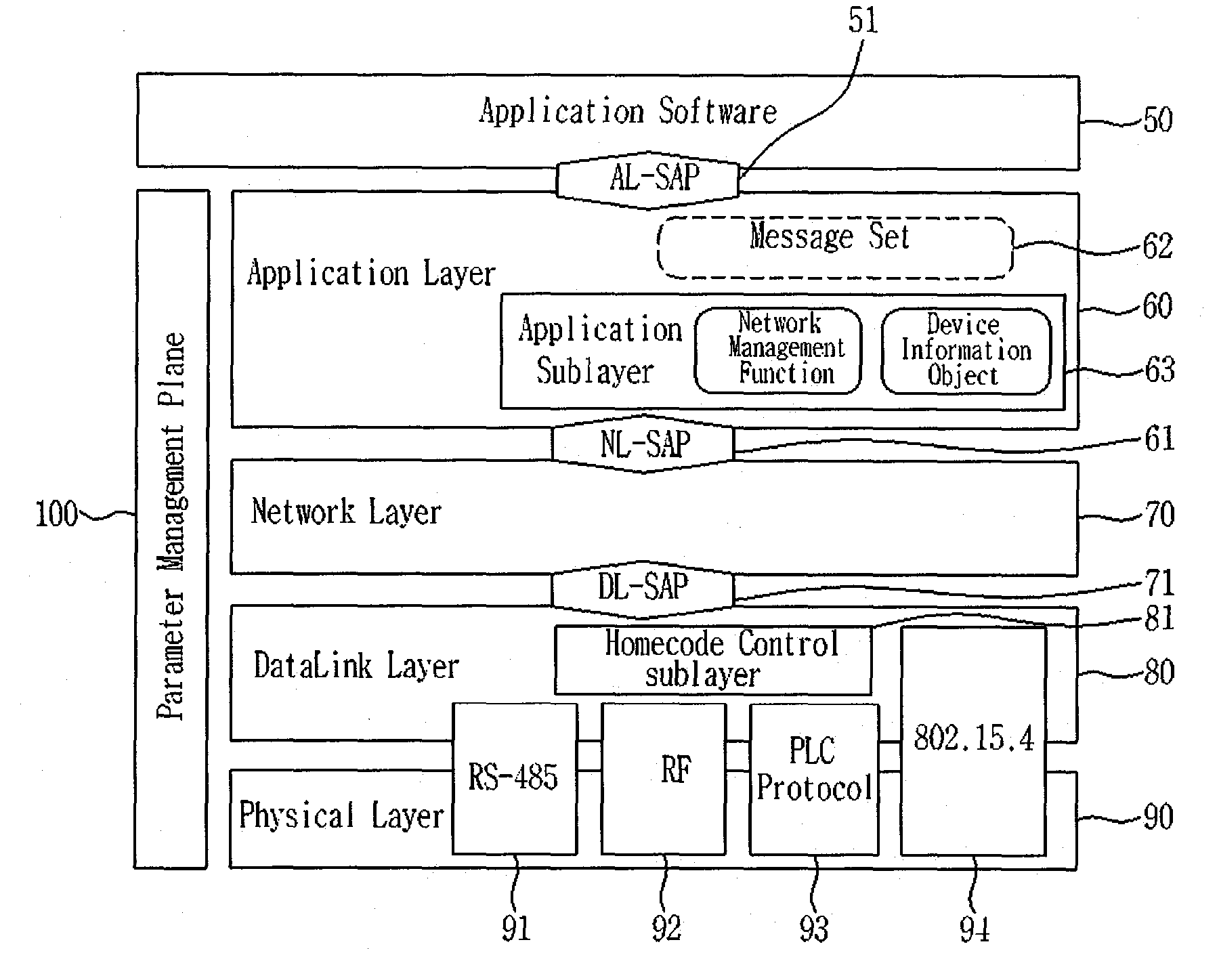
Network device
InactiveUS20100005166A1High performance communication moduleDigital data processing detailsDigital computer detailsMicrocontrollerNetwork connection
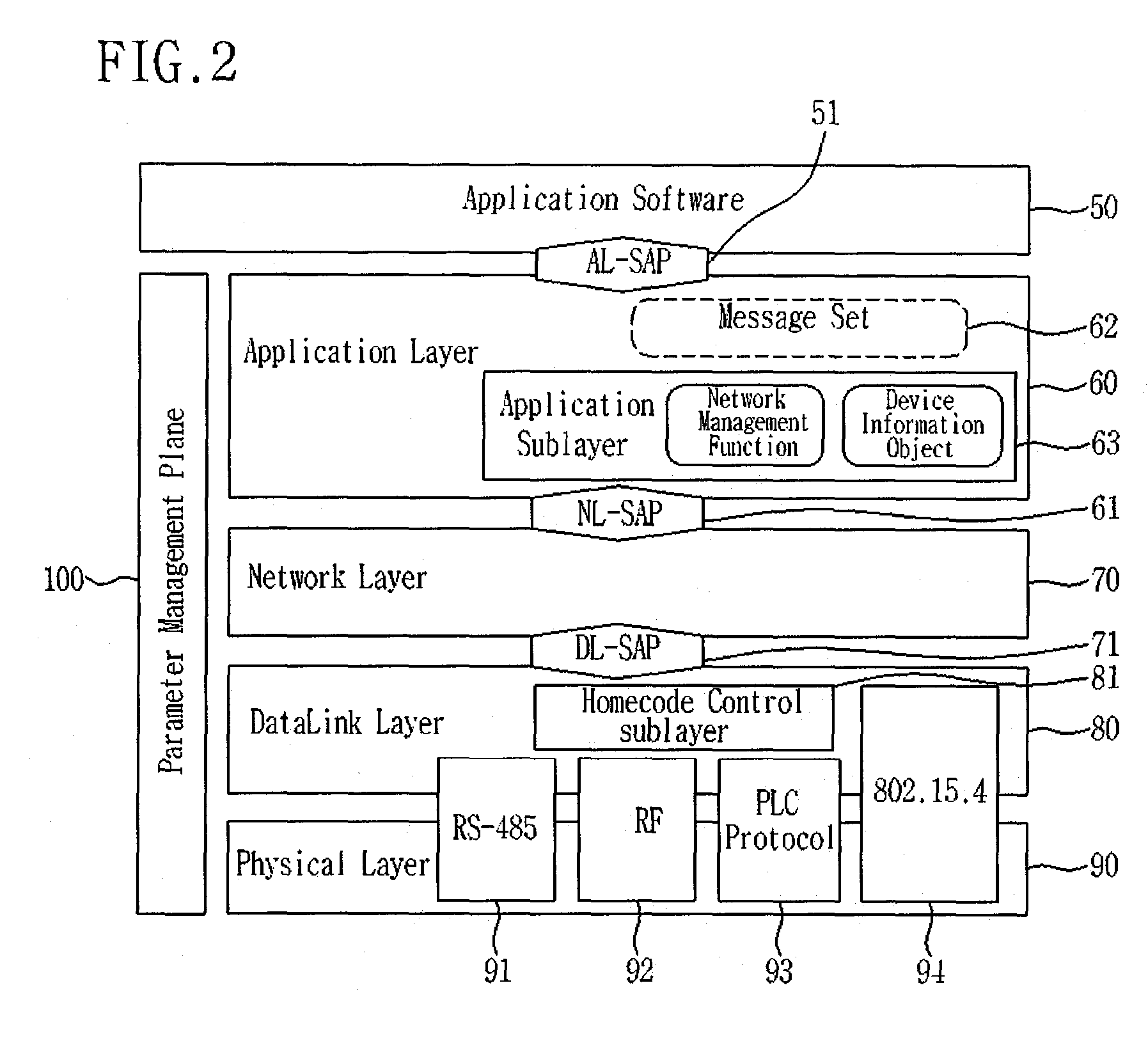
The present invention discloses a network device which can access a home network system and perform network communication based on a predetermined protocol, by using a minimum number of resources of an embedded microcontroller The network device communicates with at least one electric device through a network. The network device adopts a protocol consisting of an application layer for processing a message for controlling or monitoring the electric device, a network layer for performing network connection to the electric device, a data link layer for accessing a shared transmission medium, and a physical layer for providing a physical interface with the electric device. The application layer further includes an application sublayer for performing a network management function or managing device information.
Owner:LG ELECTRONICS INC
Applications as a service
ActiveUS20130204975A1Problem can be addressedMultiple digital computer combinationsData switching networksTransmission protocolNetwork management application
A system and method are provided for managing applications over a network between a server system and client computers. In one example, the method involves receiving user login information from a client computer, then accessing on the server system a user profile associated with the login information. The user profile includes a user environment configuration for a client environment. Transport protocols are selected based on the user profile. The transport protocols are protocols for transporting information between the server system and the client computer. The user environment configuration stored on the server system is then synchronized with a client environment configuration on the client computer.
Owner:GOODRICH JOHN B +1
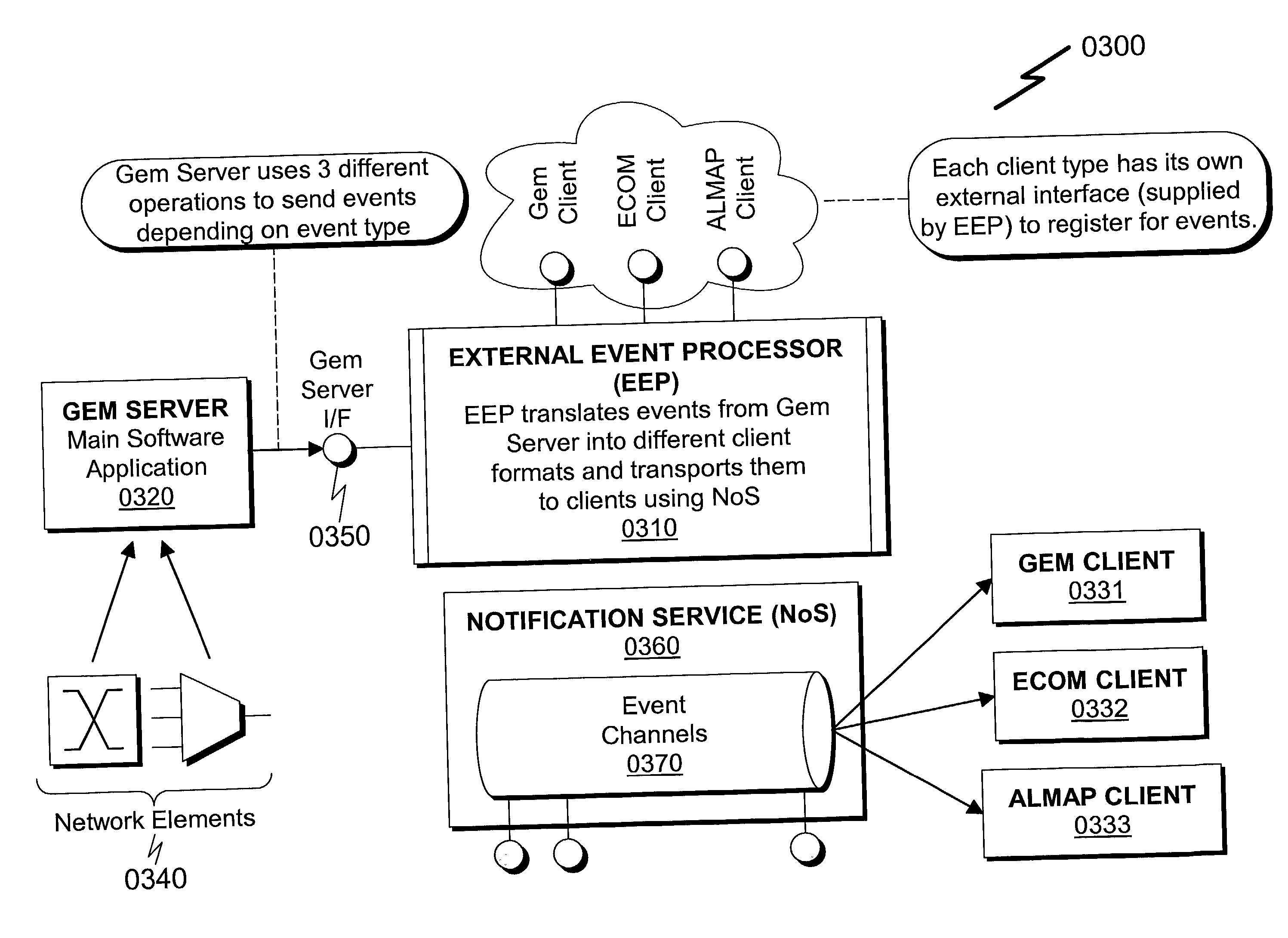
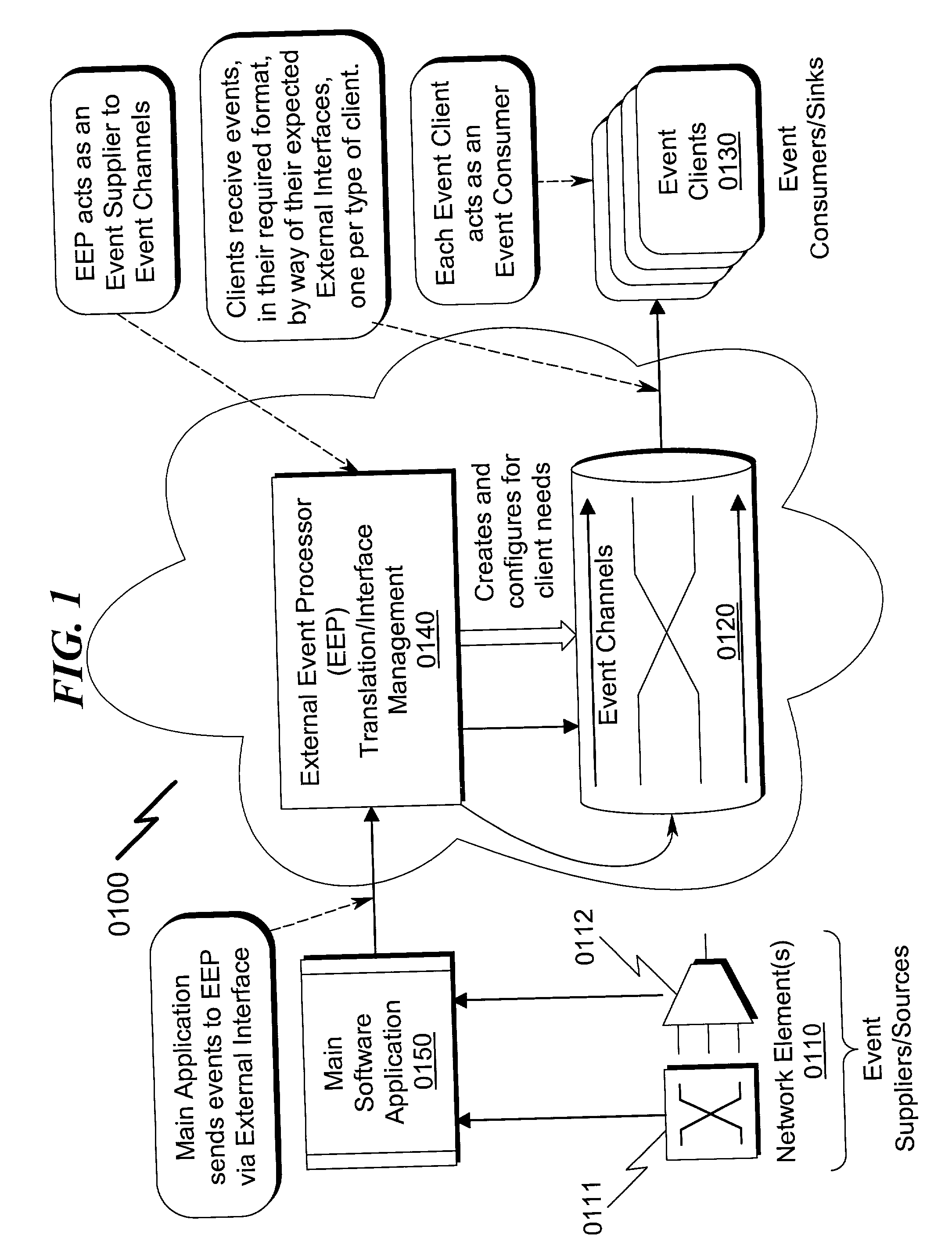
External event processor system and method
InactiveUS20030050983A1Avoid problemsLittle and no lossMultiprogramming arrangementsMultiple digital computer combinationsQuality of serviceComputer hardware
An External Event Processor (EEP) system and method incorporating a separate software component that permits reformatting of received events and transportation of these events to previously registered event consumers is disclosed. The present invention teaches creation of a separate software component to handle event processing and transportation, running within a separate software process. This separate software process has a remote interface utilized by a Network Management application to send events in their most basic form to the External Event Processor (EEP). Subsequently, the EEP performs all other functions that are necessary to convert the supplied even to the proper form and type required by the external event consumers. In addition, the EEP provides the event with Quality of Service (QoS) properties required by external consumers.
Owner:ALCATEL SOCIETE ANONYME
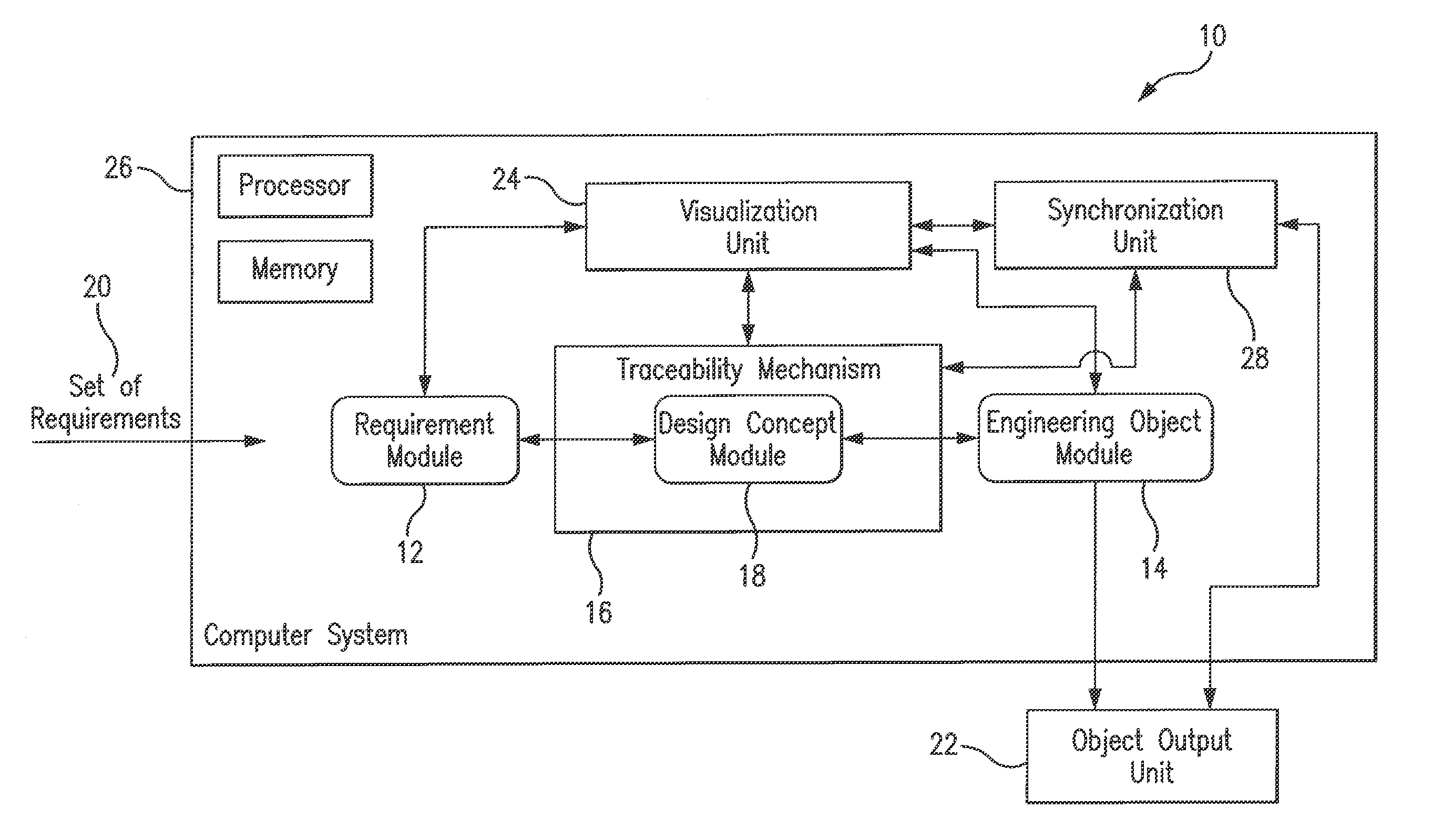
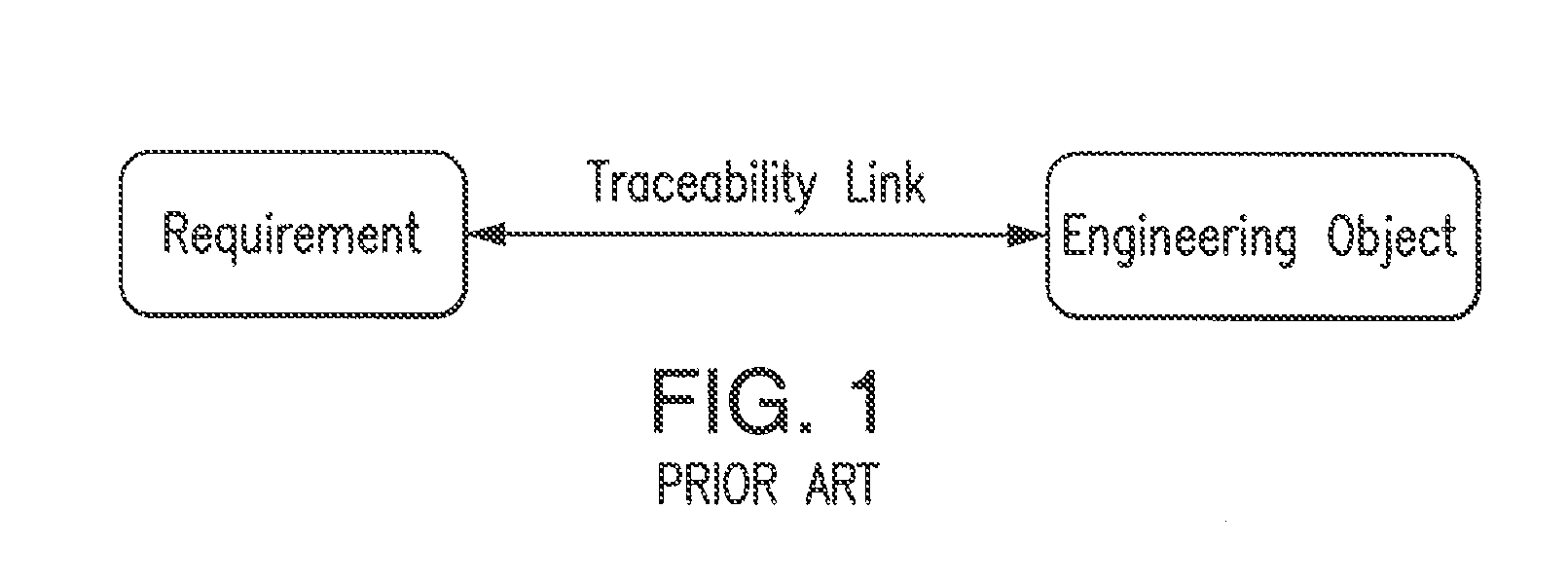
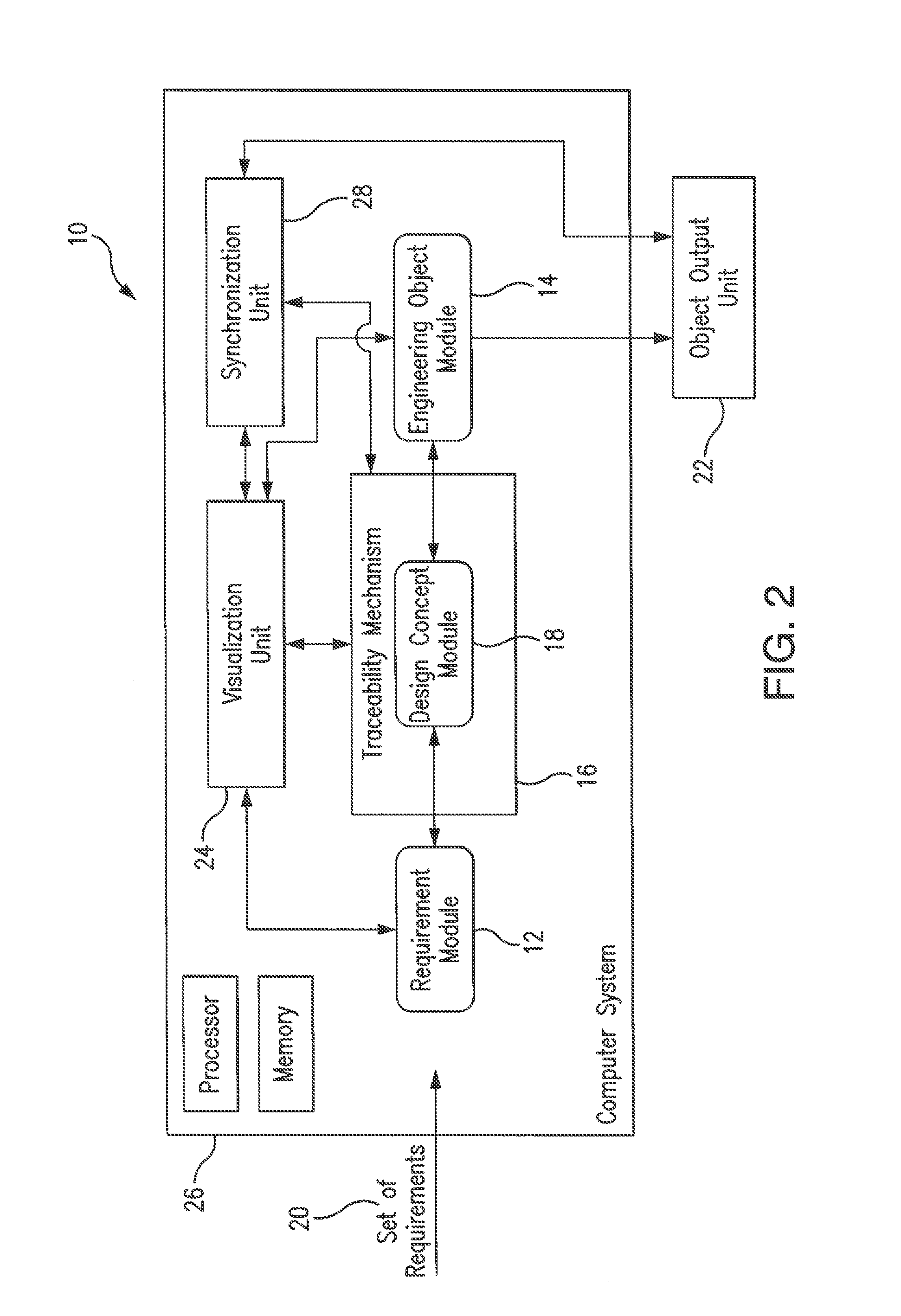
Method and system for ontology-enabled traceability in design and management applications
InactiveUS20120143570A1Enhanced Semantic RepresentationSpecial data processing applicationsNetwork management applicationDesign rule checking
A system and method for ontology-enhanced traceability in design and management applications employ ontology nodes embedded in a processor executable traceability link (network) coupling processor executable requirement modules to processor executable engineering object modules to facilitate in all stages of engineering object development. The engineering object development occurs through multiple models of computation, control, and visualization platform networked together via ontology-enhanced traceability mechanism. Processor executable design rule checking module embedded in the design concept nodes creates a pathway for the development process validation and verification at early stages of the object lifecycle. Linking of ontologies / meta-models is performed for the purposes of supporting ontology-enabled traceability across multiple domains.
Owner:UNIV OF MARYLAND
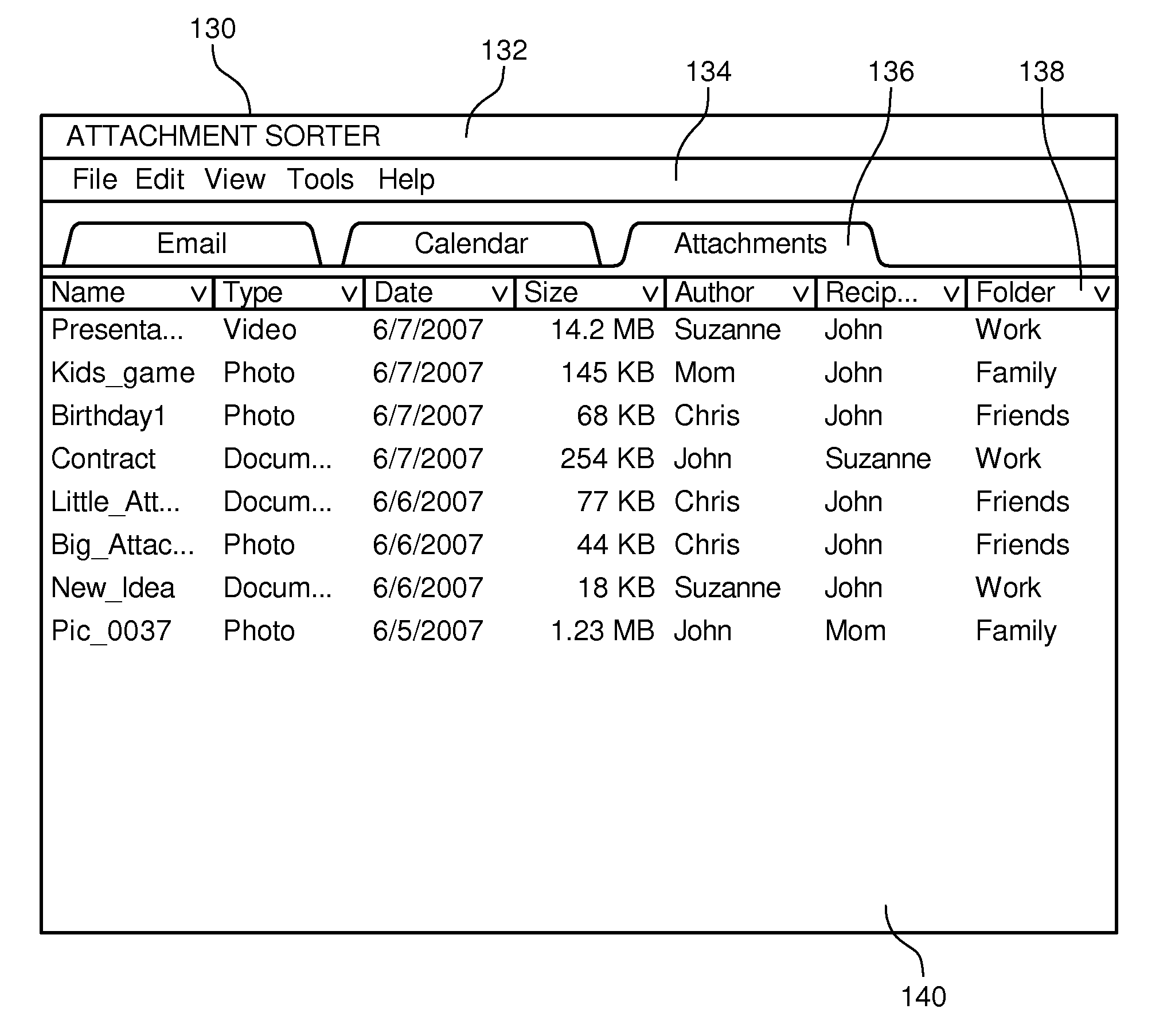
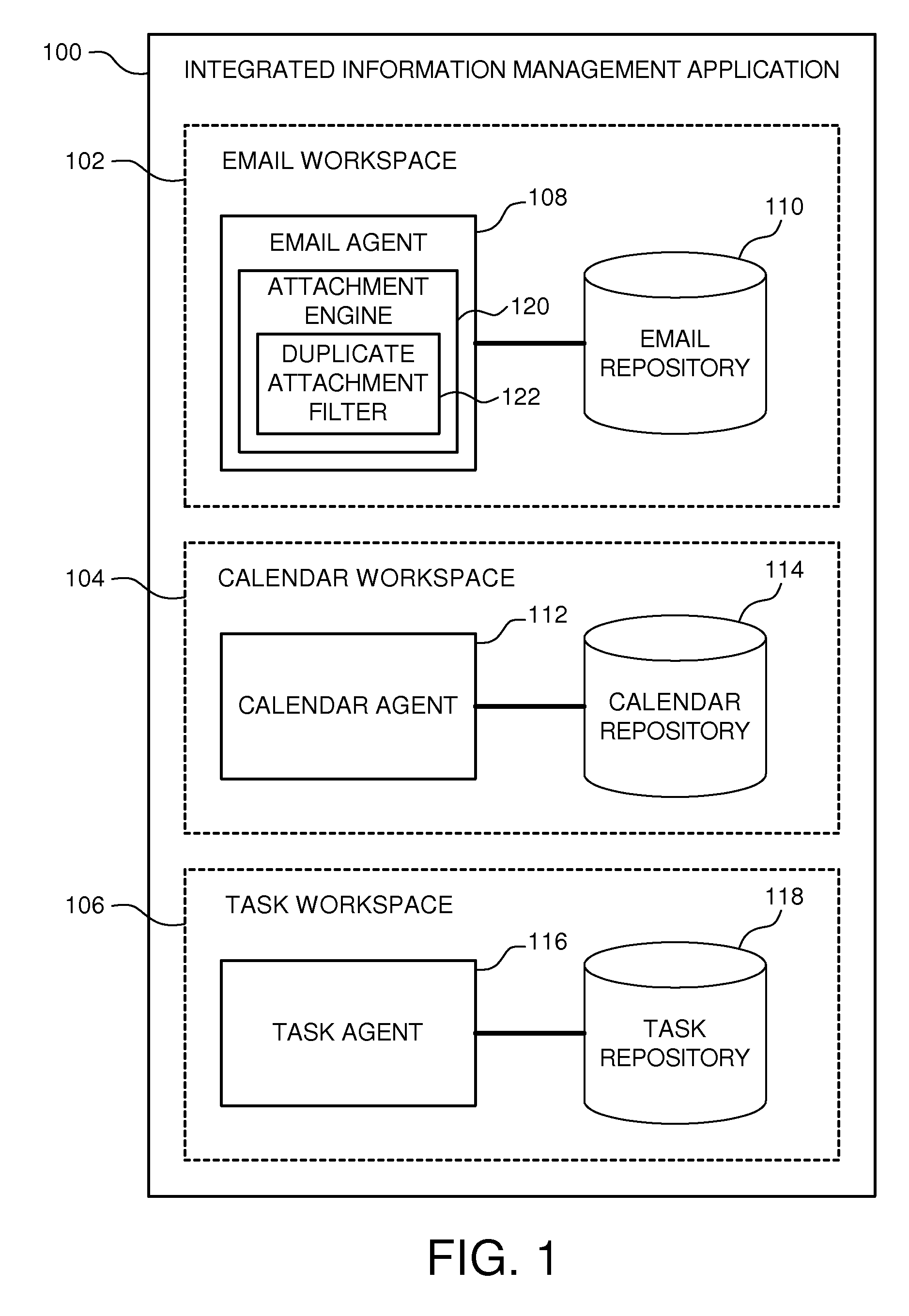
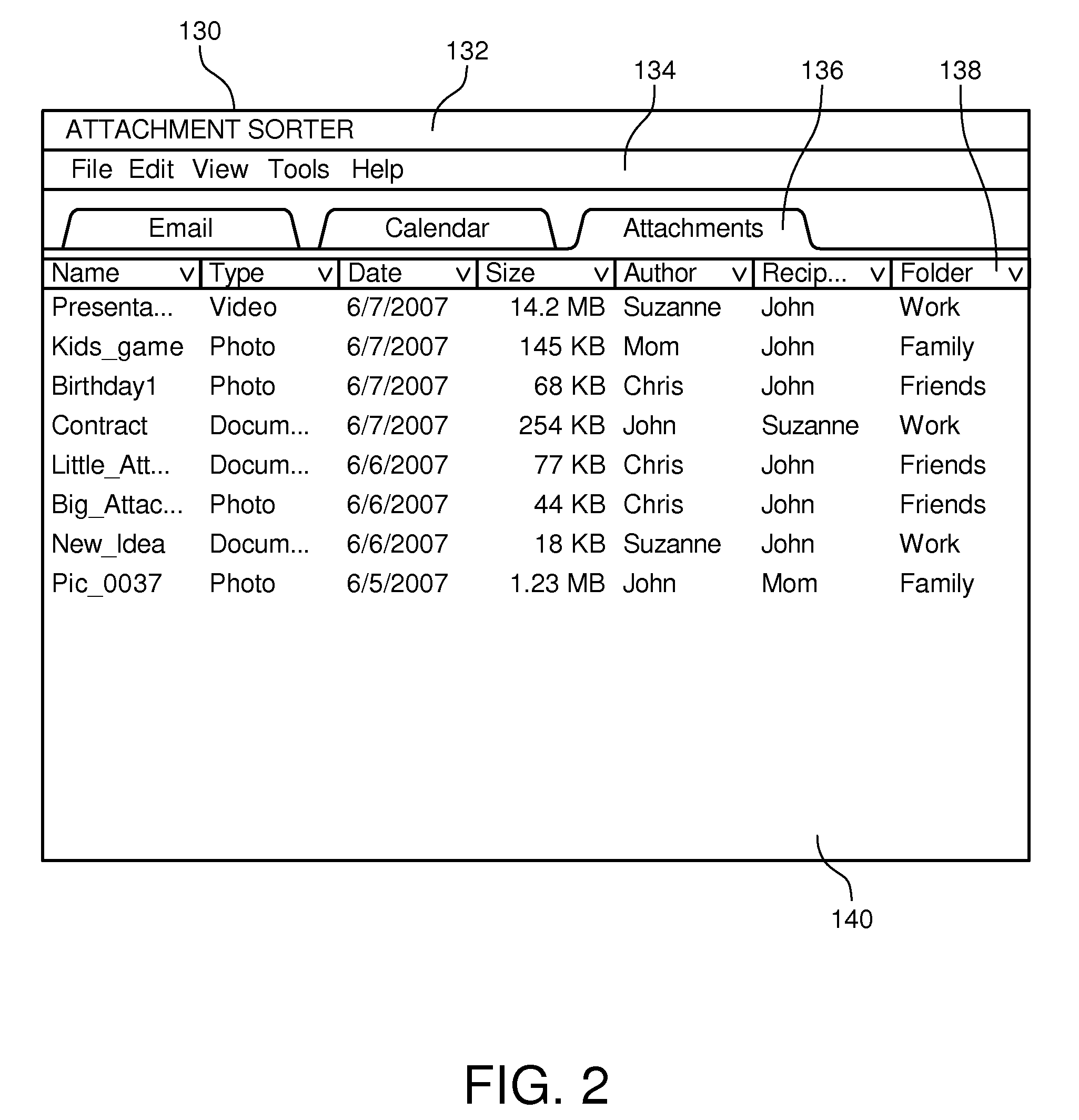
System and method for sorting attachments in an integrated information management application
ActiveUS20090037407A1Improve organizationDigital data processing detailsSpecial data processing applicationsTechnical communicationNetwork management application
A system and method to sort attachments in an integrated information management application. The system includes an email agent, and email repository, and an attachment engine. The email agent facilitates organization of email communications within the integrated information management application. The email repository is coupled to the email agent. The email repository stores a plurality of email files and a plurality of email attachments. The email attachments are associated with at least some of the email files. The attachment engine is coupled to the email agent. The attachment engine generates a list of the email attachments within the email repository for visual communication on a display device.
Owner:CITRIX SYST INT
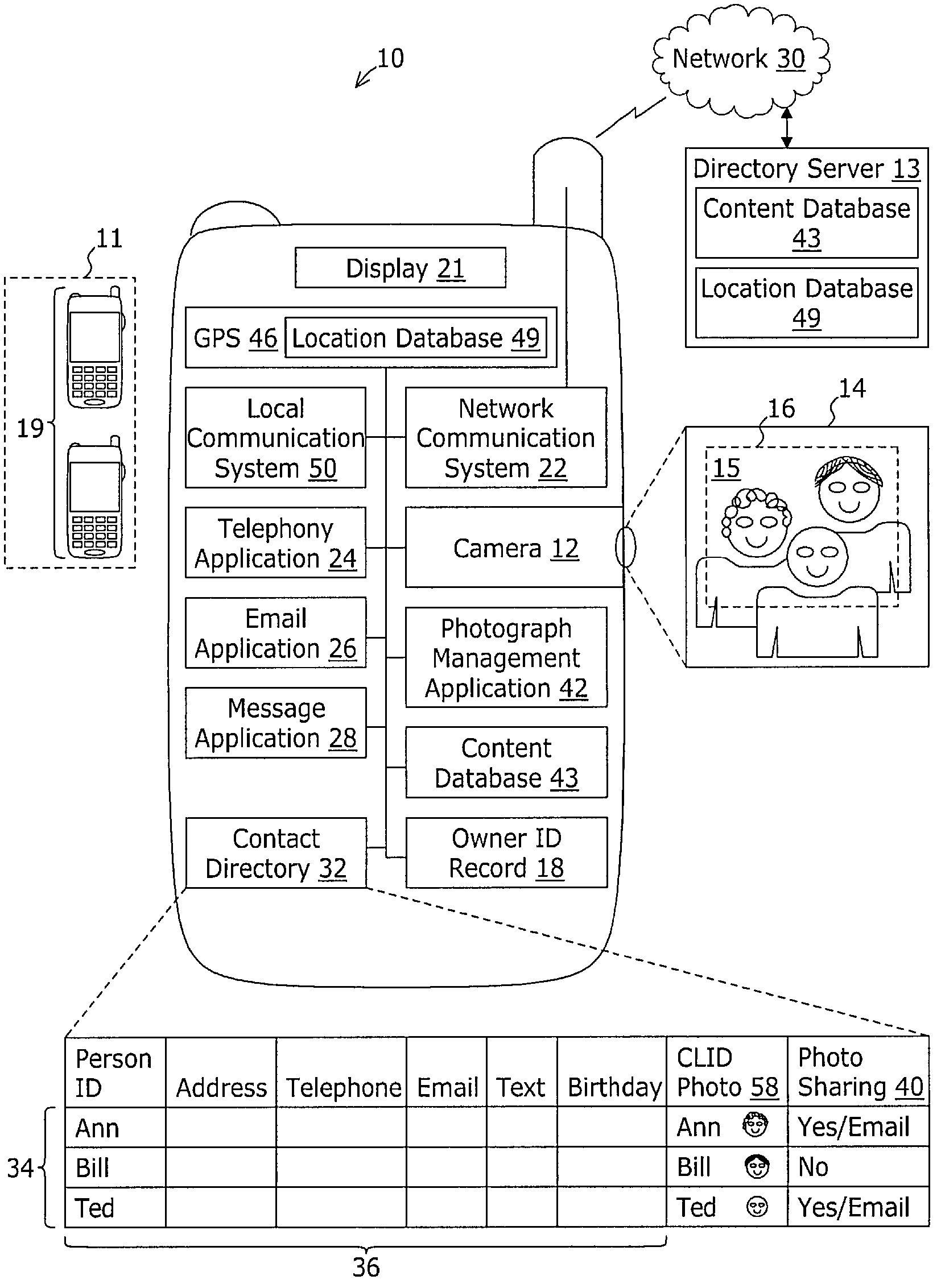
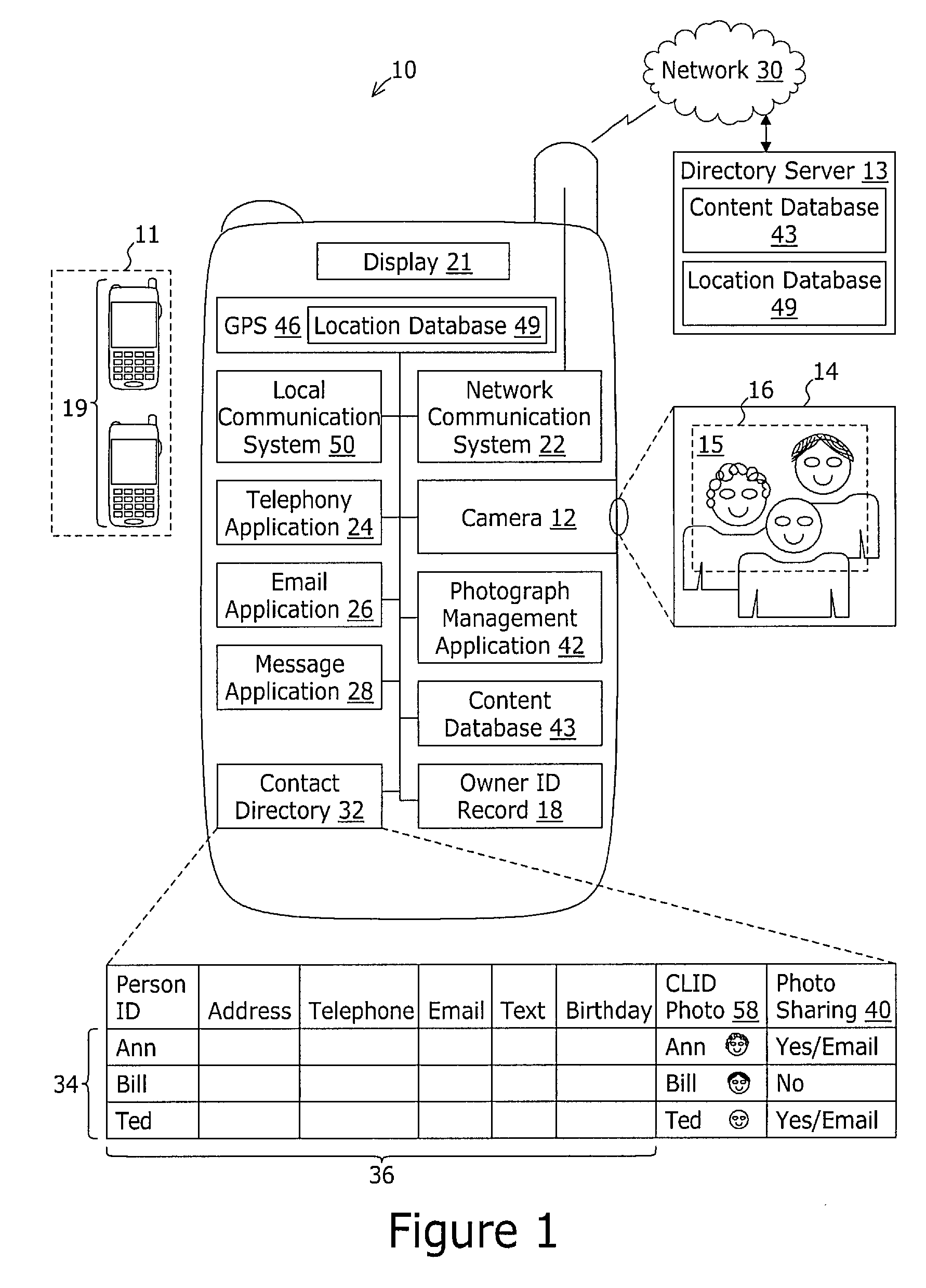
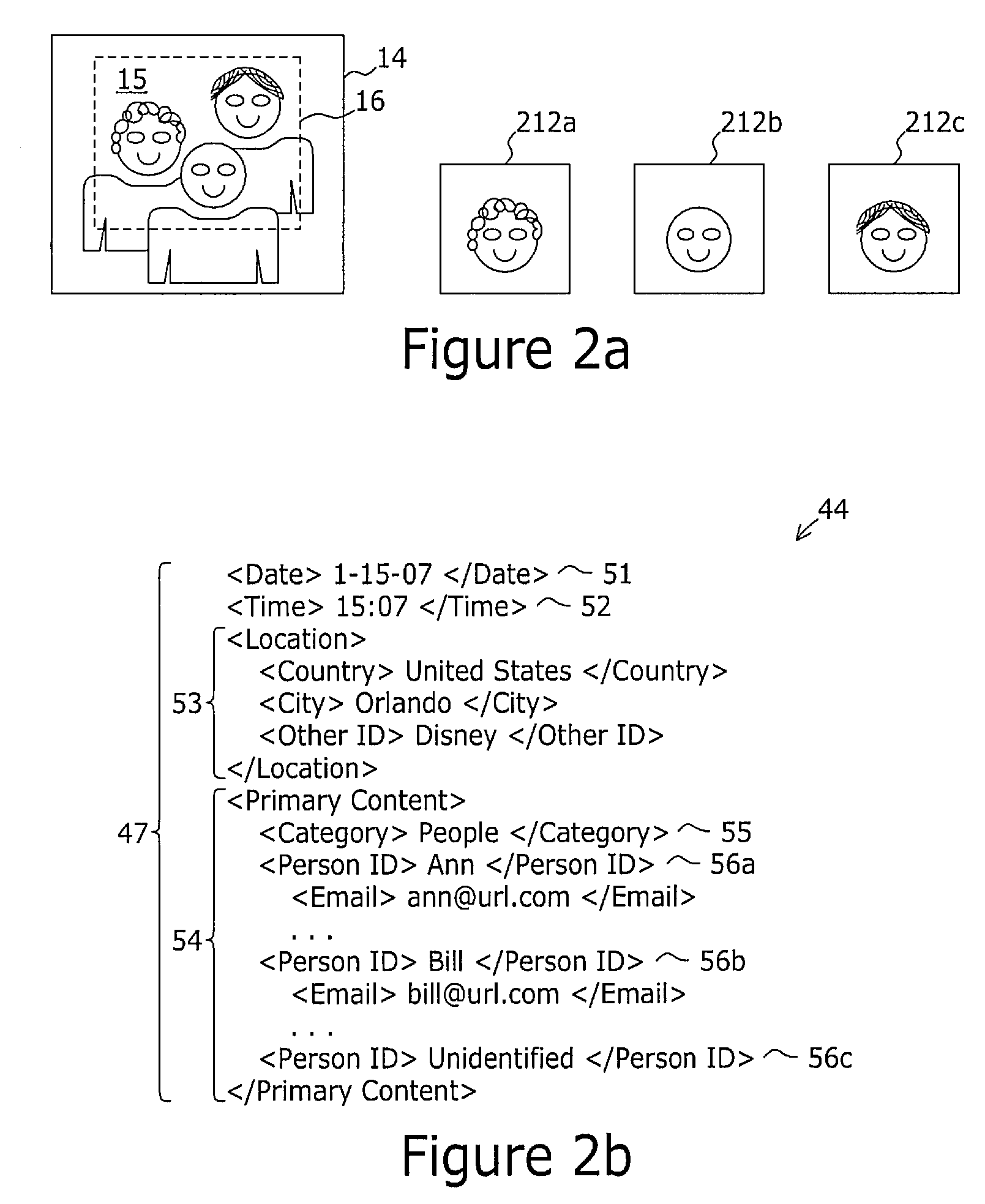
Mobile device with integrated photograph management system
ActiveUS7831141B2PrintersPicture reproducers using cathode ray tubesCommunications systemInternet privacy
A mobile device comprises a network communication system such as a wide area network mobile telephony system, a camera for capturing a digital photograph, and a photograph management application. The photograph management application receives the digital photograph, obtains an information record comprising information related to the digital photograph; and associates at least a portion of the information related to the digital photograph with the digital photograph. The information record may be obtained from local sources such as a contact directory or from a remote directory server.
Owner:SONY MOBILE COMM AB
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com