Patents
Literature
148 results about "Problem determination" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Rule-based network management approaches
InactiveUS7668953B1High level of flexibilityHigh level of powerError detection/correctionDigital computer detailsNetwork management applicationNetwork management
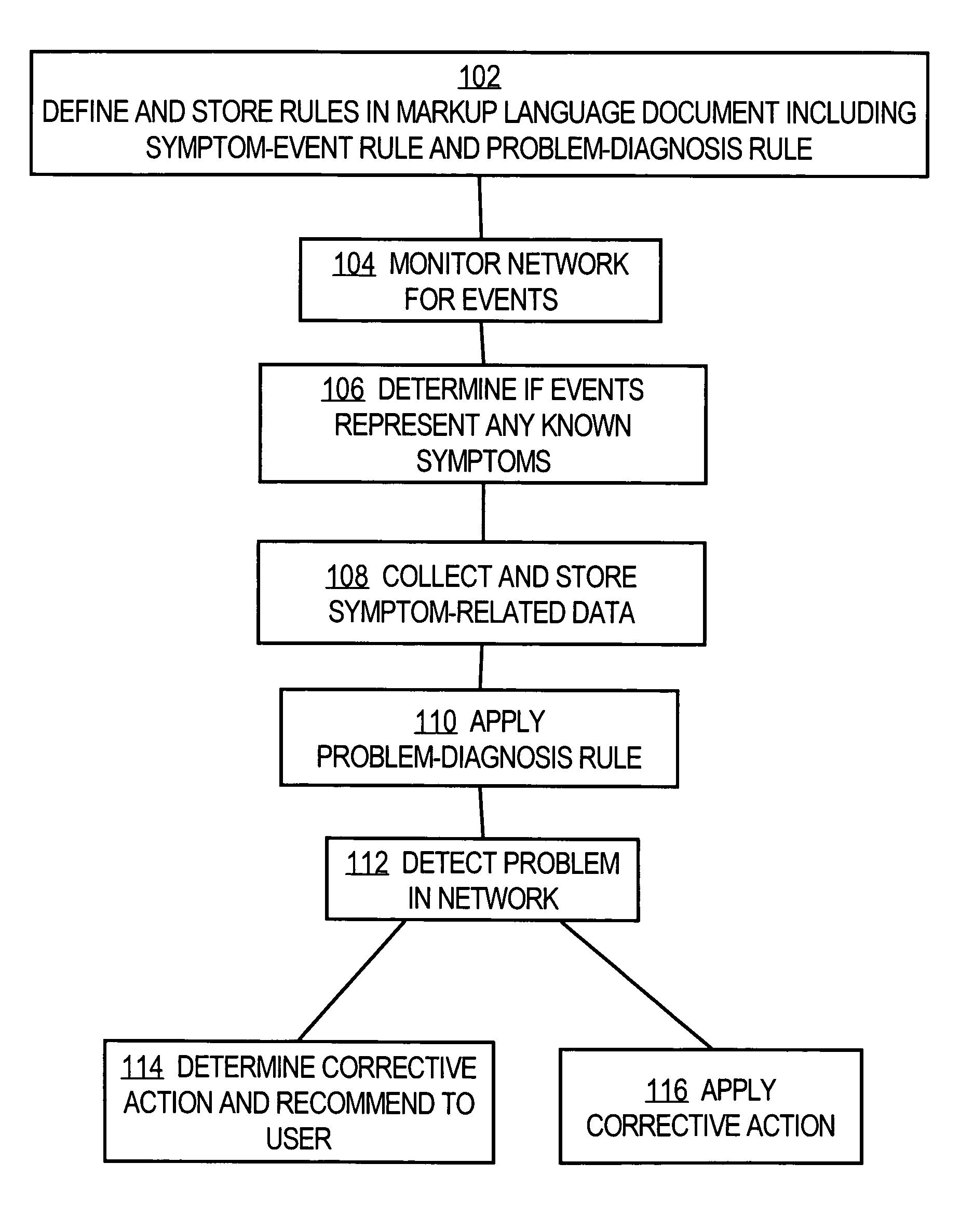
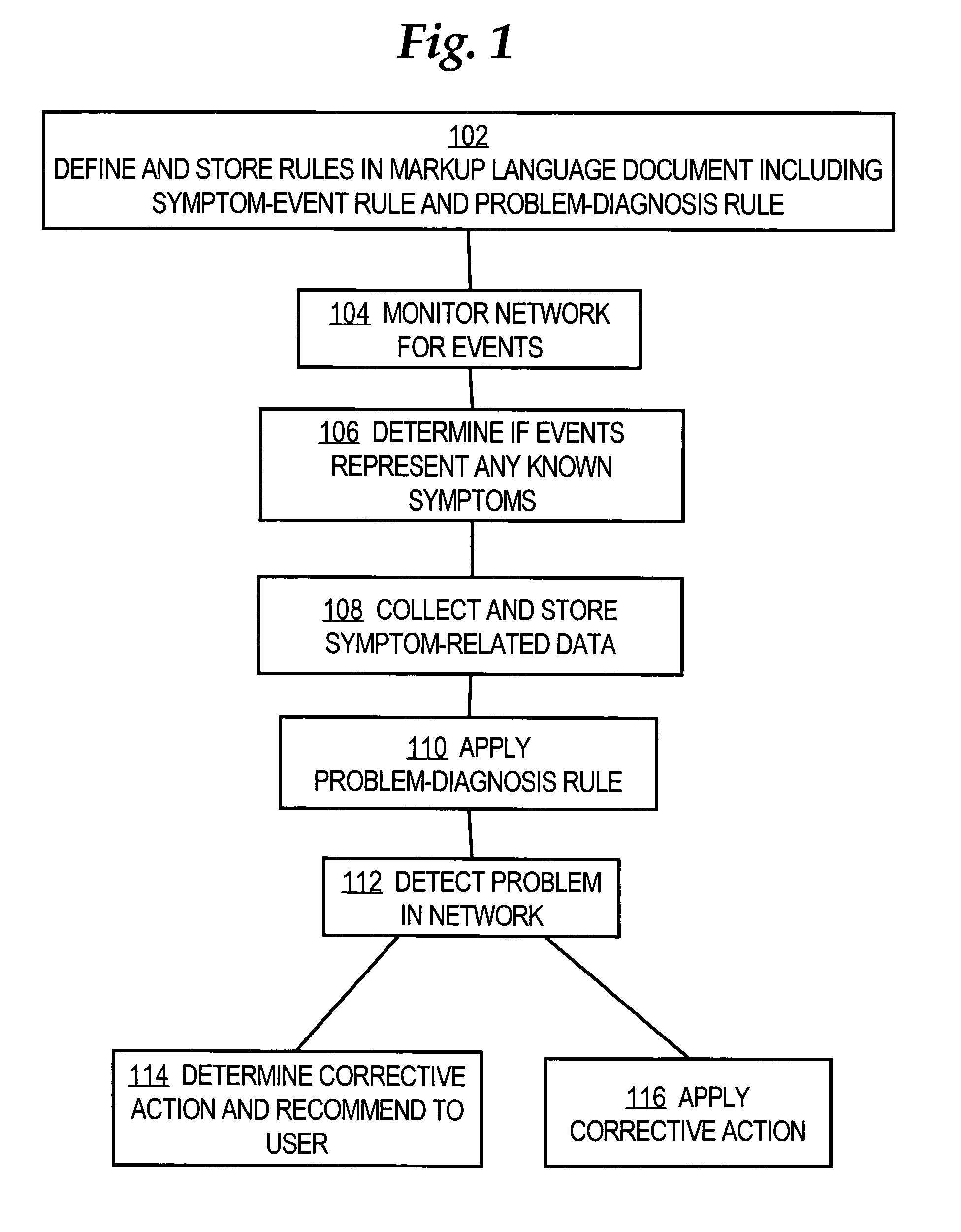
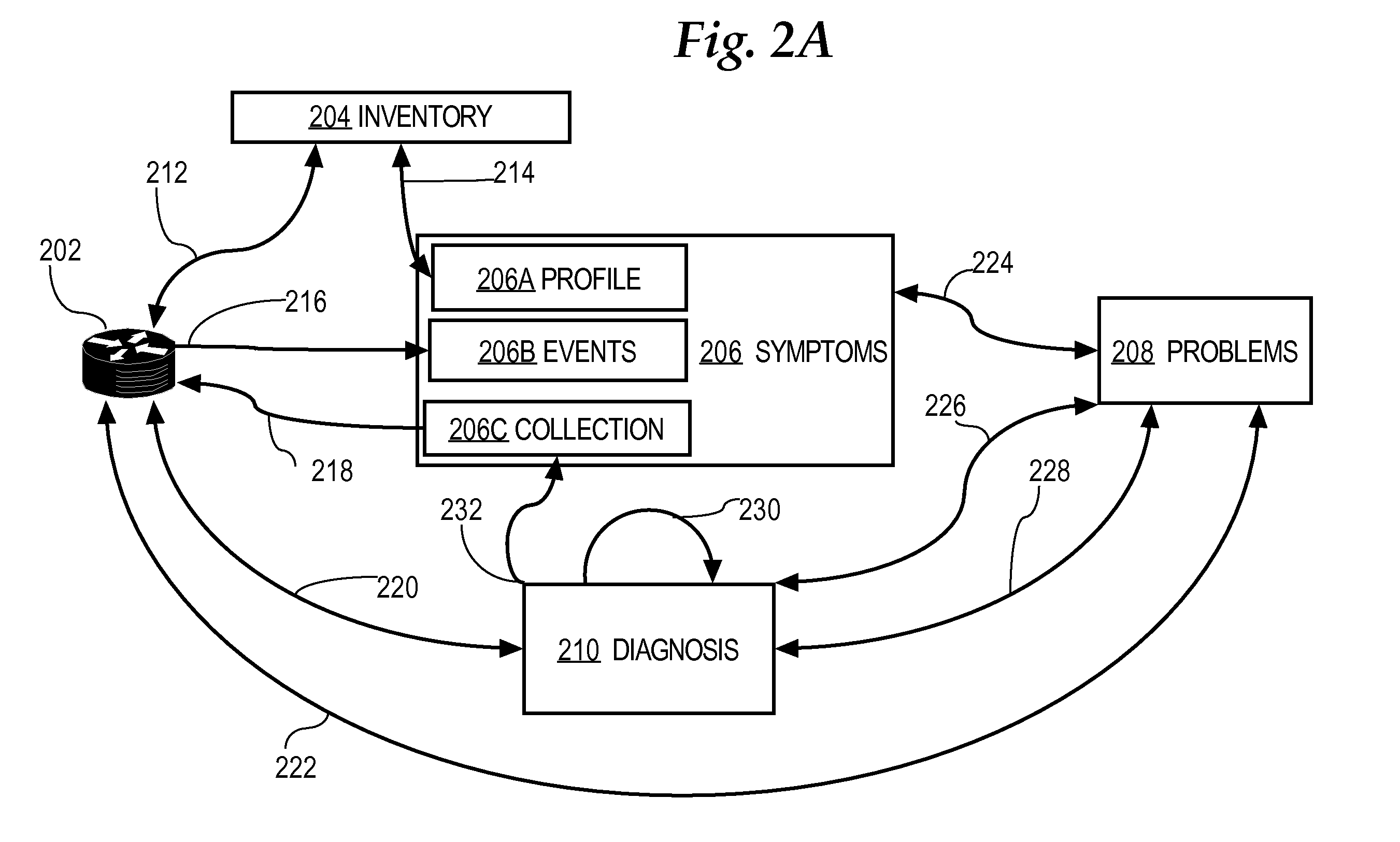
A method is disclosed for detecting symptoms in a network infrastructure, combining one or more symptoms into a problem, then optionally applying detailed diagnosis to the network elements experiencing the problems, ultimately providing detailed problem determination.
Owner:CISCO TECH INC
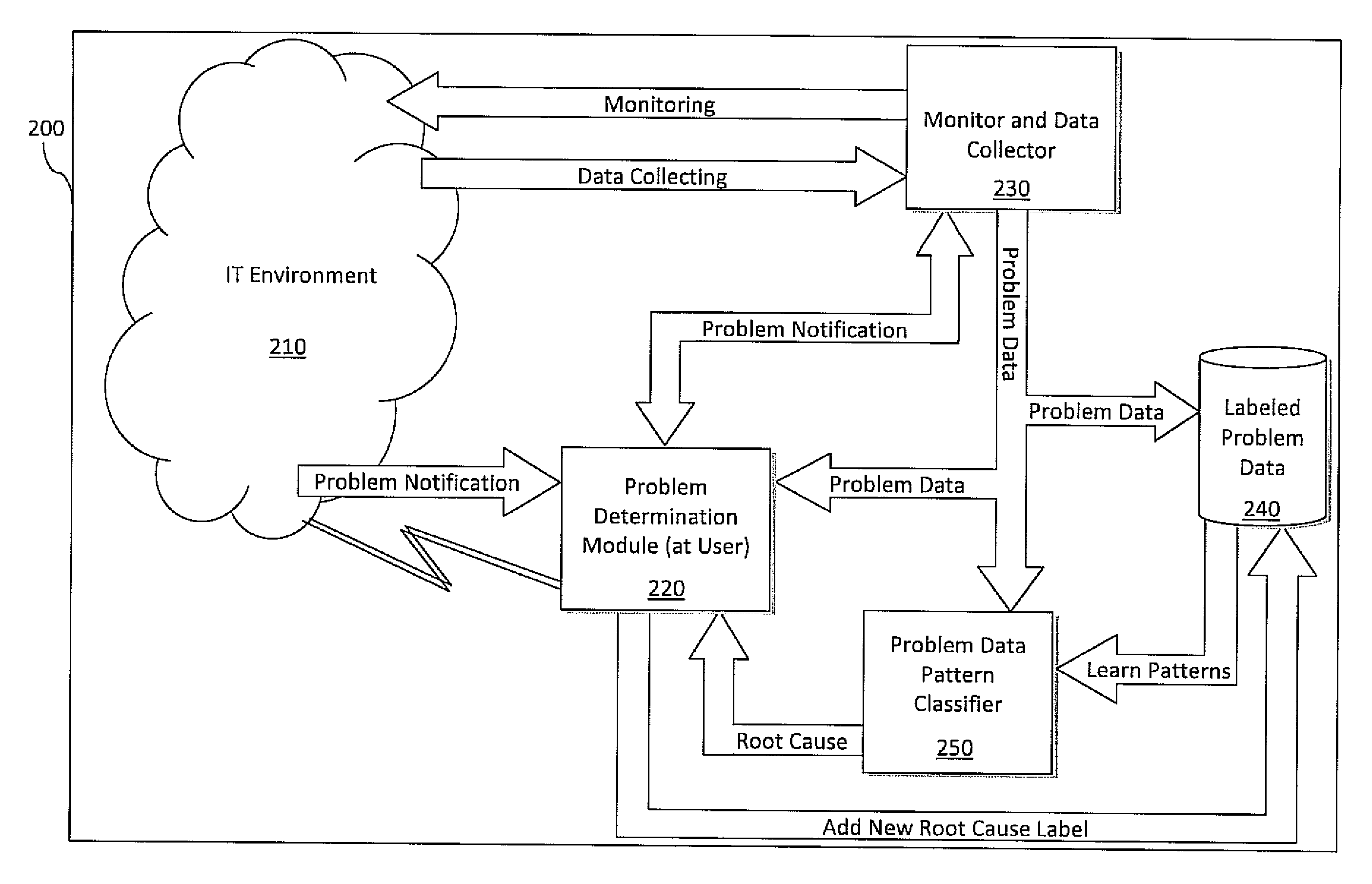
Methods and apparatus for root cause identification and problem determination in distributed systems
InactiveUS7096459B2Logical operation testingHardware monitoringDistributed Computing EnvironmentCondition status
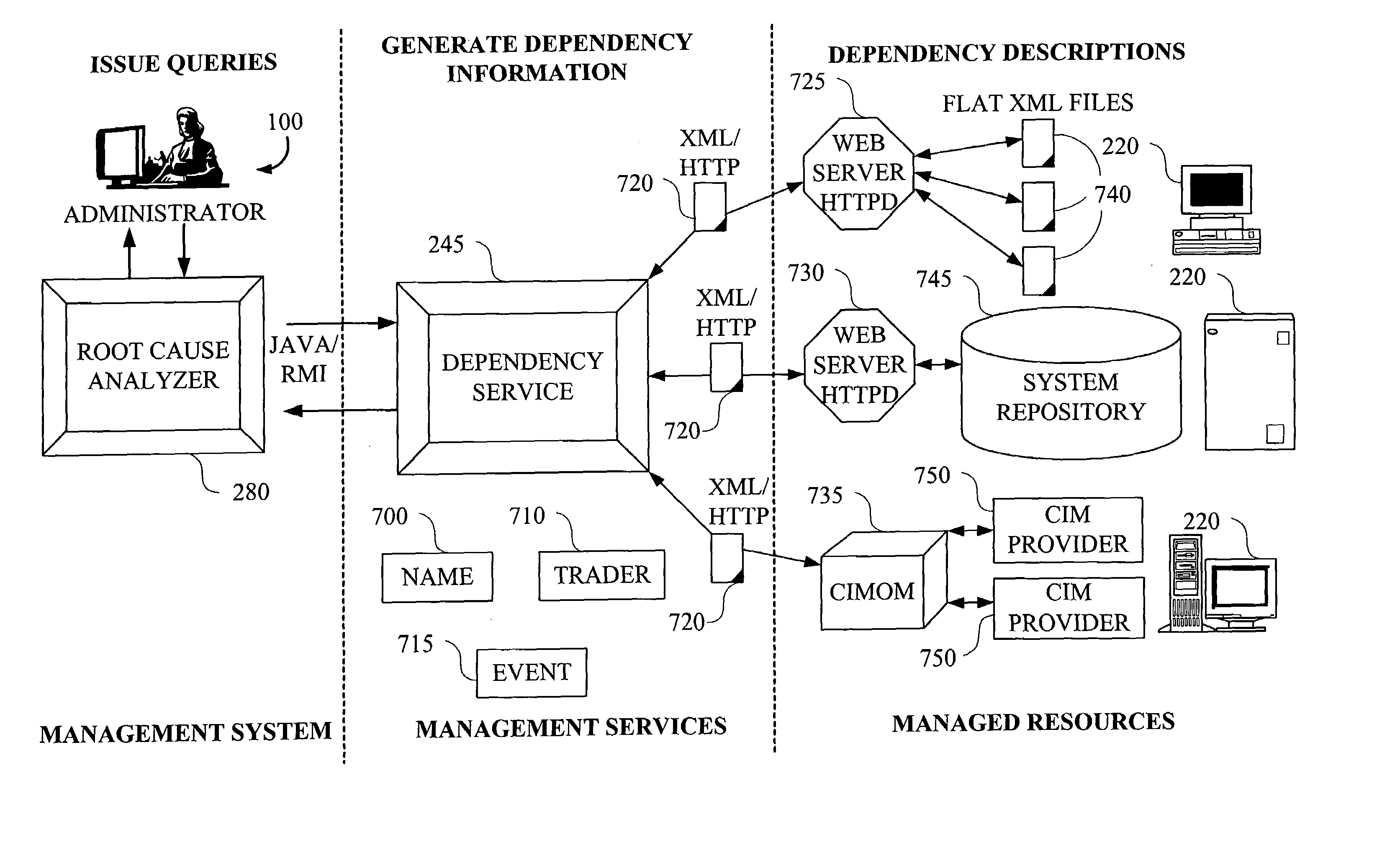
A technique for determining a root cause of a condition (e.g., service outage) of at least one subject component in a computing environment comprises the following steps / operations. First, one or more components in the computing environment upon which the at least one subject component depends (e.g., antecedents) are identified. Identification comprises traversing at least a portion of a model representative of an existence of one or more relationships associated with at least a portion of components of the computing environment and which is capable of accounting for a full lifecycle (e.g., including deployment, installation and runtime) associated with at least one component of the computing environment. Then, one or more procedures are performed in accordance with the one or more identified components to determine a condition status associated with each of the one or more identified components. By way of example, the inventive techniques may be applied to a distributed computing environment. The computing environment may also be an autonomic computing environment.
Owner:IBM CORP
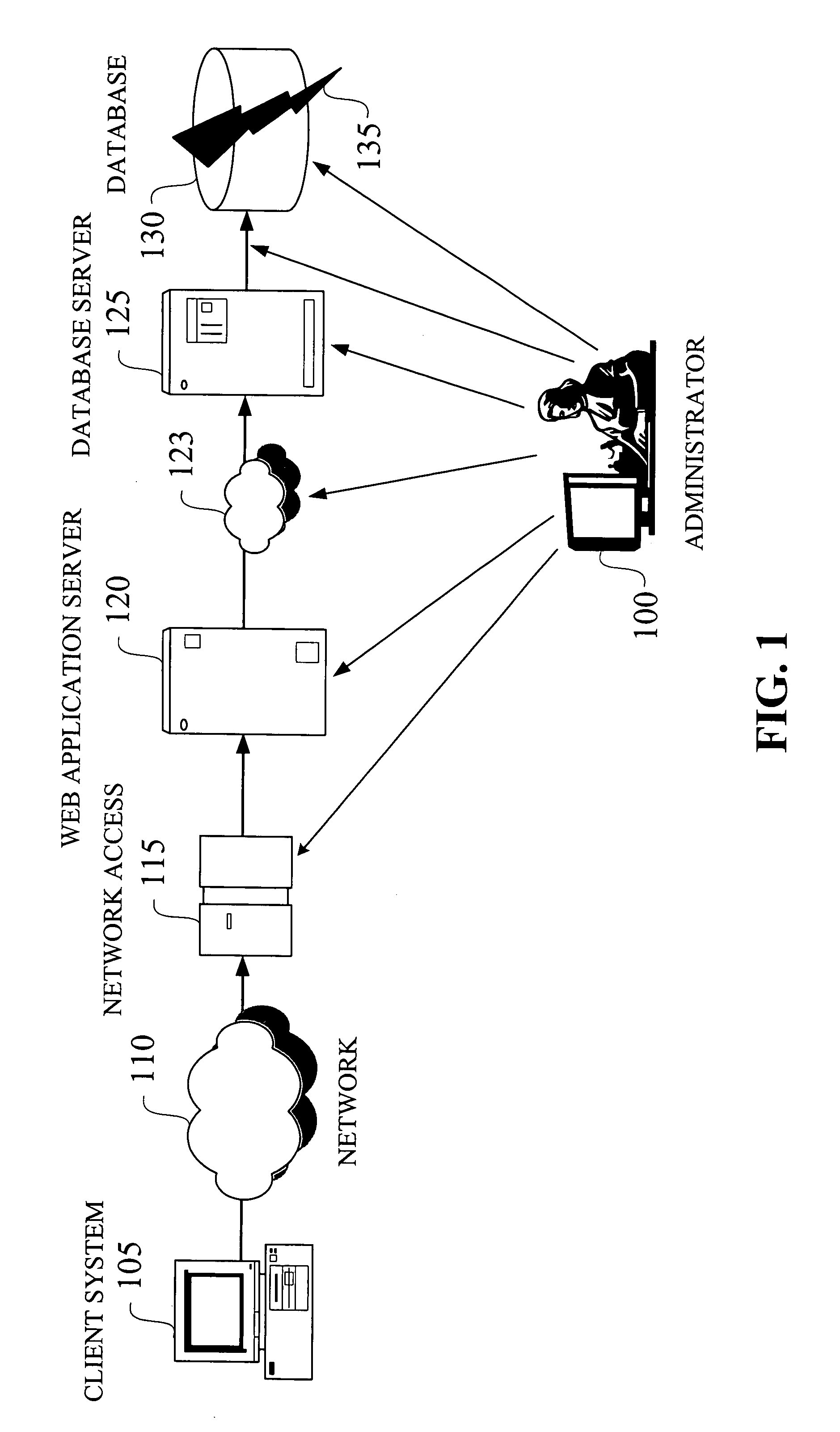
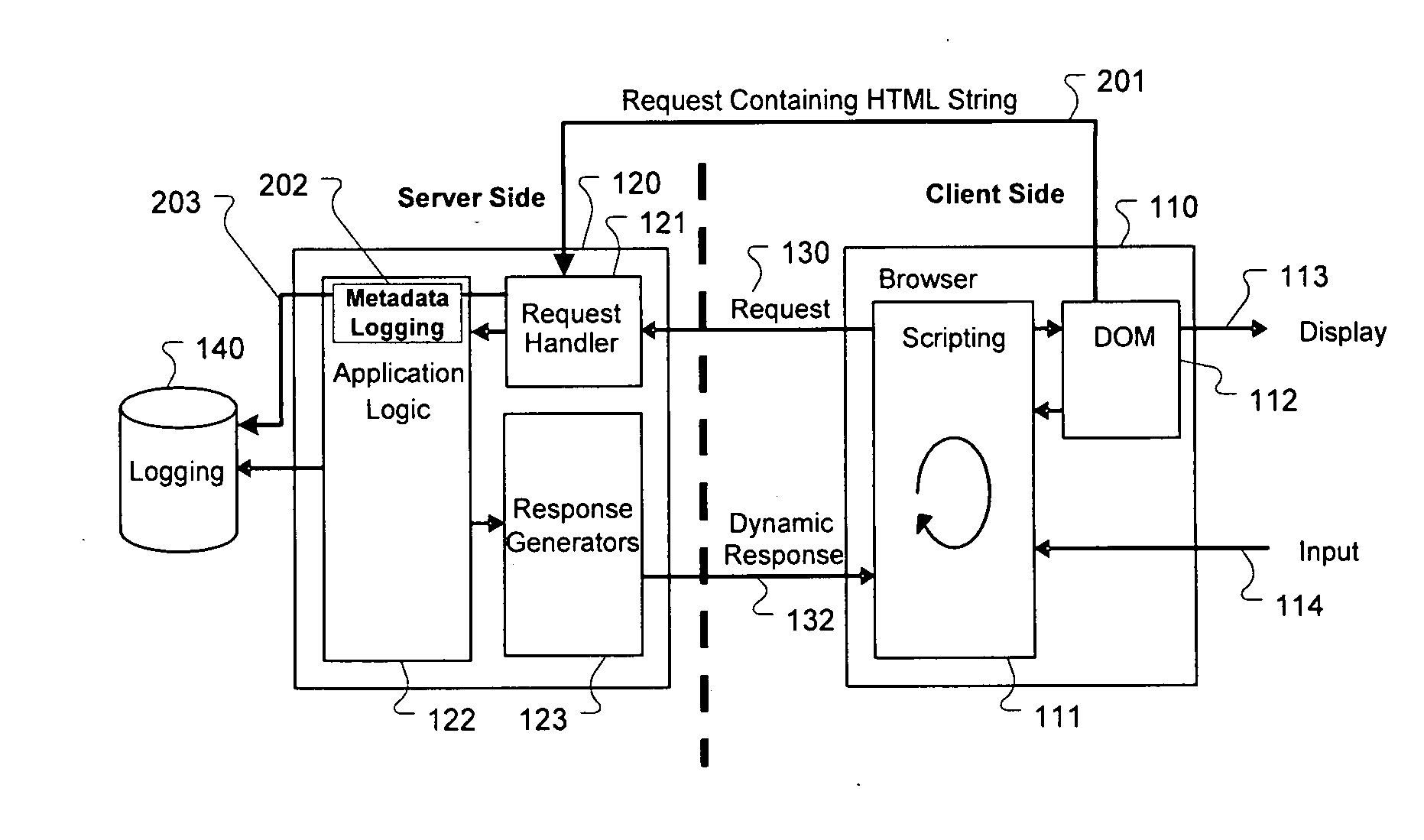
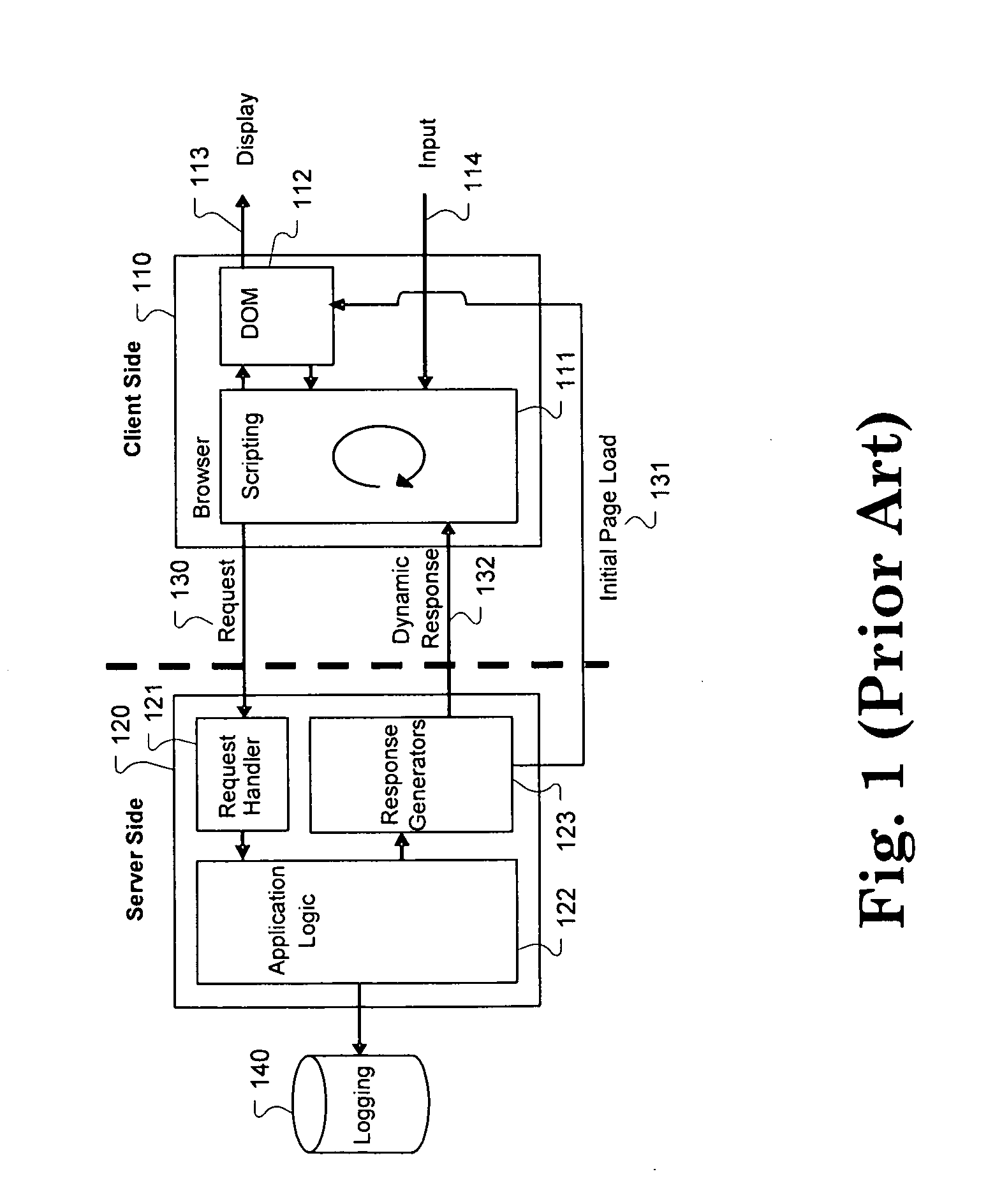
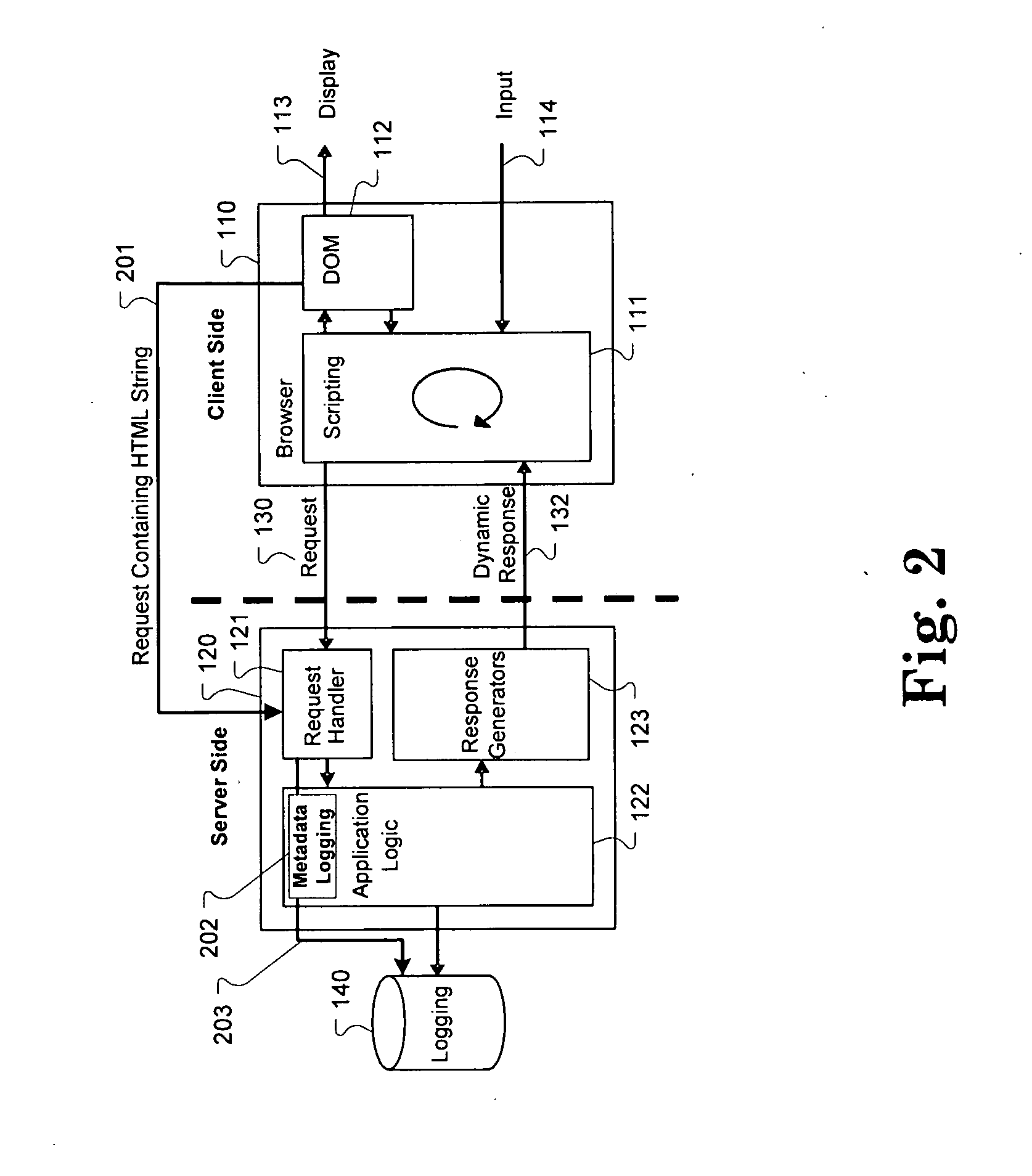
Method for server-side logging of client browser state through markup language
InactiveUS20100174774A1Problem can be identifiedWeb data retrievalNatural language data processingWeb serviceClient-side
One aspect of the present invention includes capturing a client browser state and communicating this captured browser state within markup text for logging at a web server. In one embodiment, the contents of the DOM (Document Object Model) of a webpage accessed by a client are traversed and written as markup text in a string of characters, such as HTML. This markup, in addition to metadata specific to identify the browser display environment, is transmitted from the client to the server as text within a HTTP request. The server may then log the markup text and the metadata for later access. The logged markup text and the metadata can be used to recreate the exact display which occurred within the client browser, and therefore provide details useful for webpage problem determination, testing, and development.
Owner:IBM CORP
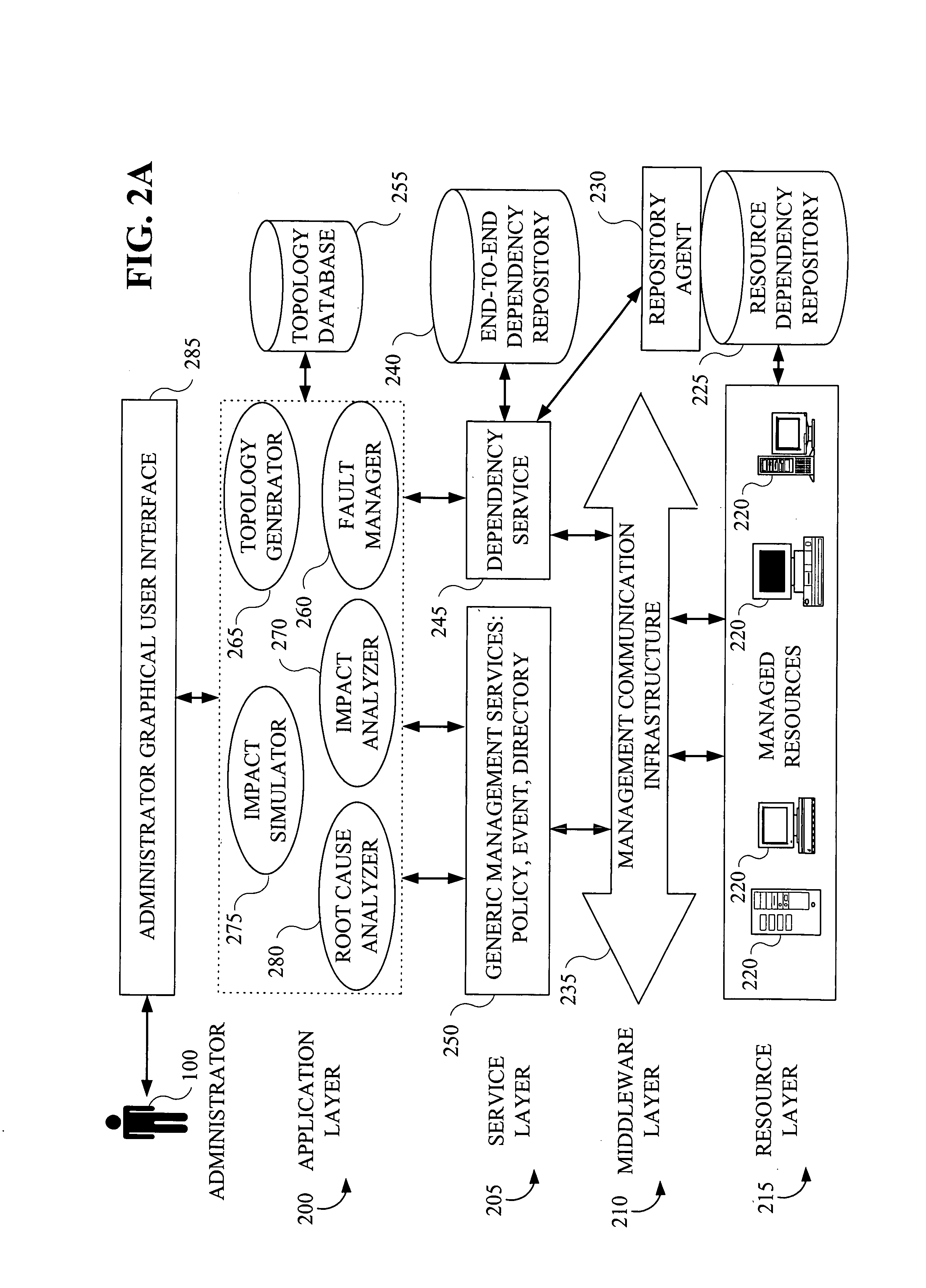
Methods and apparatus for impact analysis and problem determination
ActiveUS7505872B2Digital computer detailsNuclear monitoringDistributed Computing EnvironmentCondition status
A technique for determining an impact of a condition (e.g., service outage) of at least one subject component in a computing environment comprises the following steps / operations. First, one or more components in the computing environment which depend on the at least one subject component (e.g., dependents) are identified. Identification comprises traversing at least a portion of a model representative of an existence of one or more relationships associated with at least a portion of components of the computing environment and which is capable of accounting for a full lifecycle (e.g., including deployment, installation and runtime) associated with at least one component of the computing environment. Then, one or more procedures are performed in accordance with the one or more identified components to determine a condition status associated with each of the one or more identified components. By way of example, the inventive techniques may be applied to a distributed computing environment. The computing environment may also be an autonomic computing environment.
Owner:HUAWEI TECH CO LTD
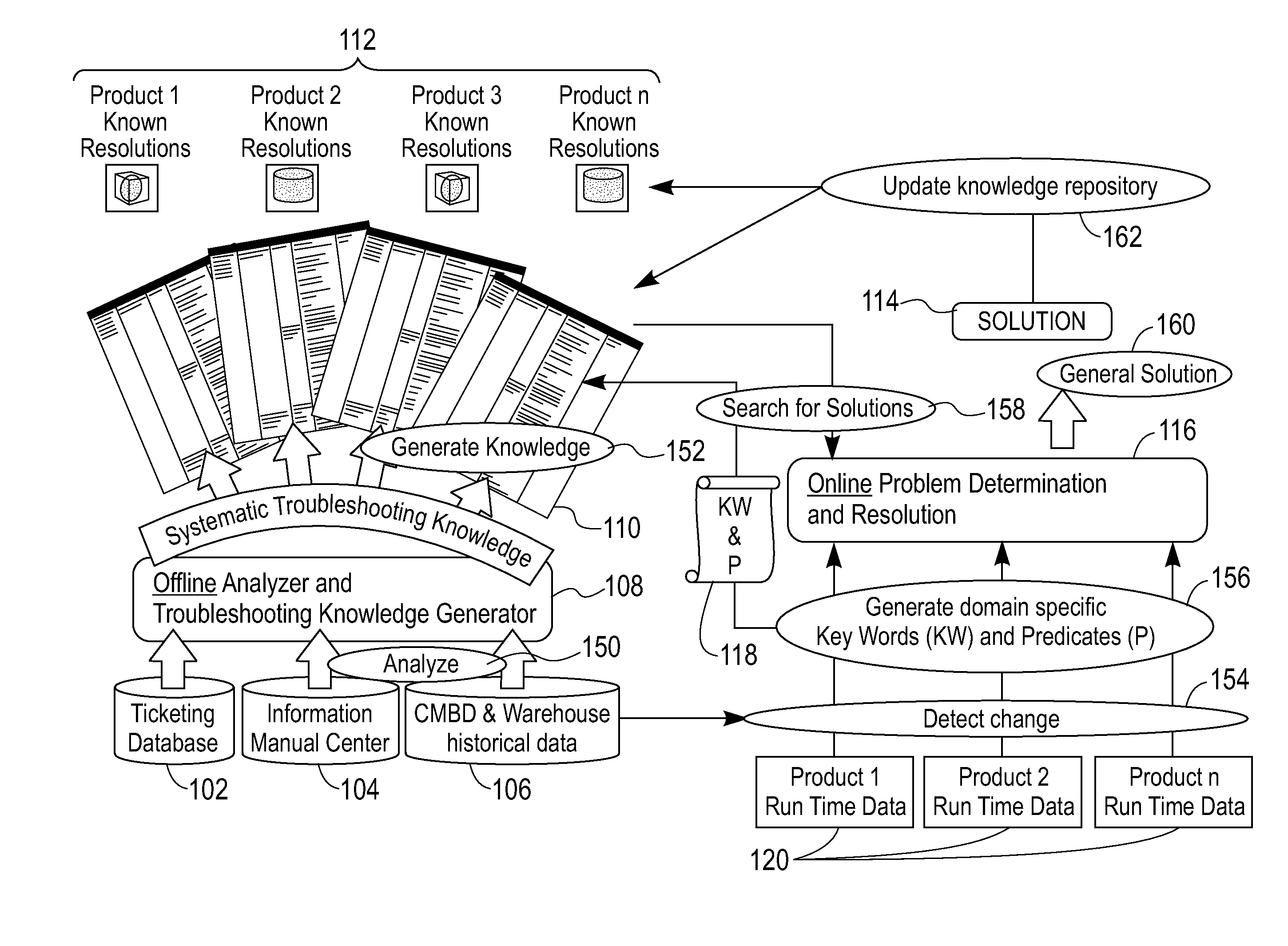
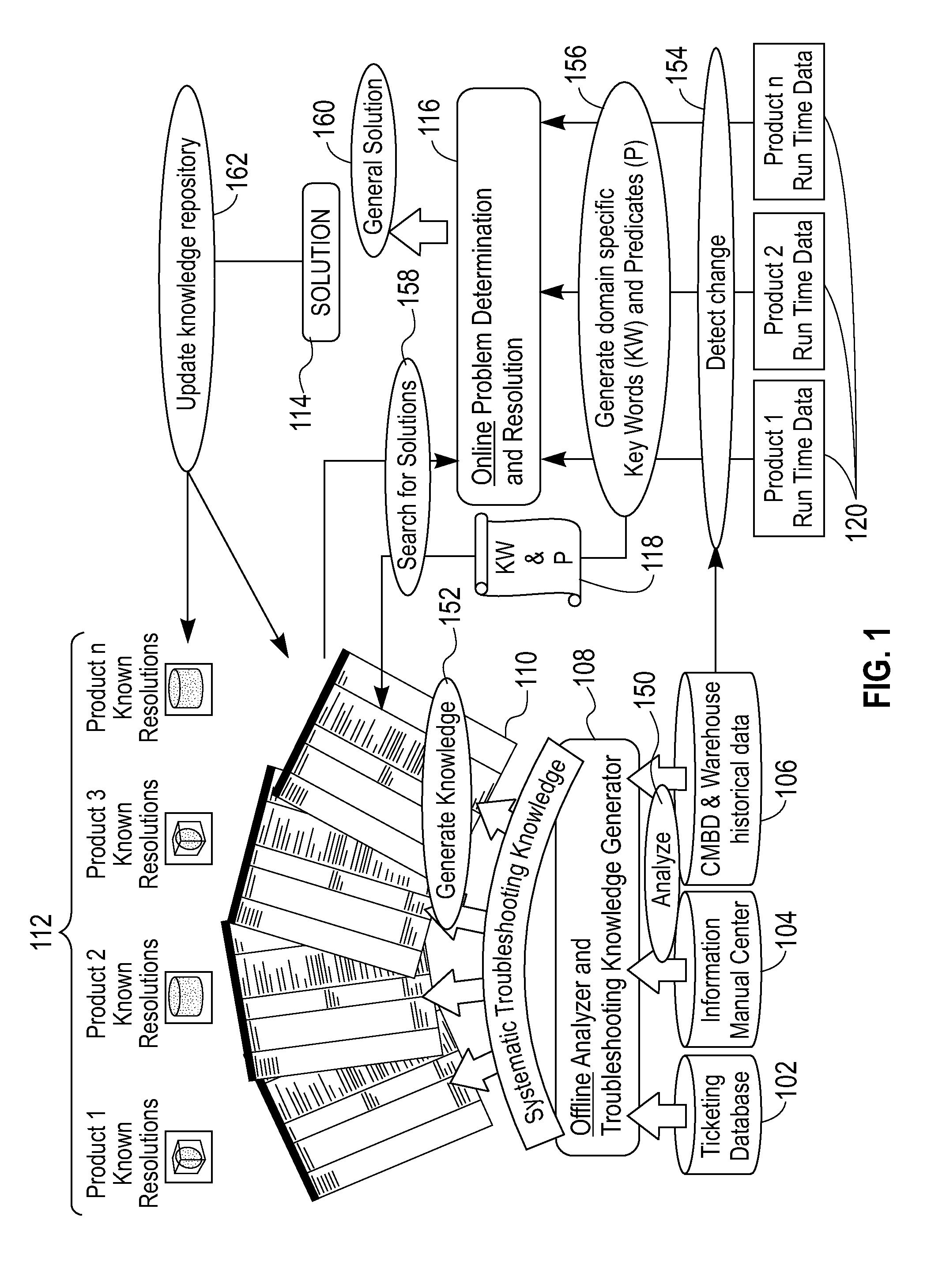
Apparatus And Method For Problem Determination And Resolution
An exemplary method (which can be computer implemented) for problem determination and resolution includes the steps of detecting anomalous changes in an environment for which a problem diagnosis is to be provided, generating domain specific key words and predicates based, at least in part, on the detected anomalous changes, searching in a knowledge resolution repository for solutions related to the generated key words and predicates, and generating a particular solution for the problem, based, at least in part, on the solutions from the knowledge resolution repository
Owner:IBM CORP
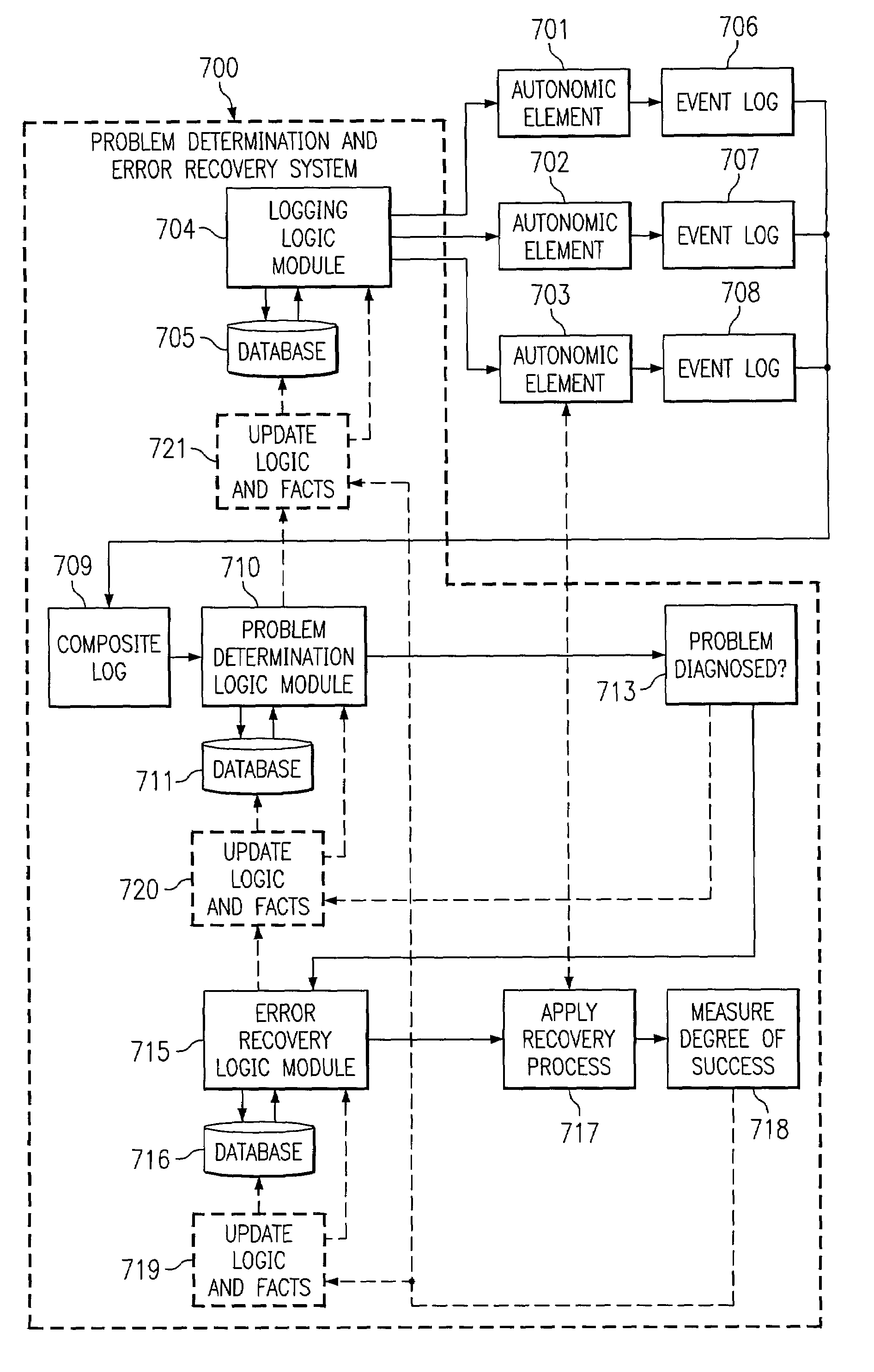
Adaptive problem determination and recovery in a computer system
InactiveUS7194445B2Reliability increasing modificationsError preventionSoftware engineeringSystem configuration
A method, computer program product, and data processing system for recognizing, tracing, diagnosing, and repairing problems in an autonomic computing system is disclosed. Rules and courses of actions to follow in logging data, in diagnosing faults (or threats of faults), and in treating faults (or threats of faults) are formulated using an adaptive inference and action system. The adaptive inference and action system includes techniques for conflict resolution that generate, prioritize, modify, and remove rules based on environment-specific information, accumulated time-sensitive data, actions taken, and the effectiveness of those actions. Thus, the present invention enables a dynamic, autonomic computing system to formulate its own strategy for self-administration, even in the face of changes in the configuration of the system.
Owner:LENOVO PC INT
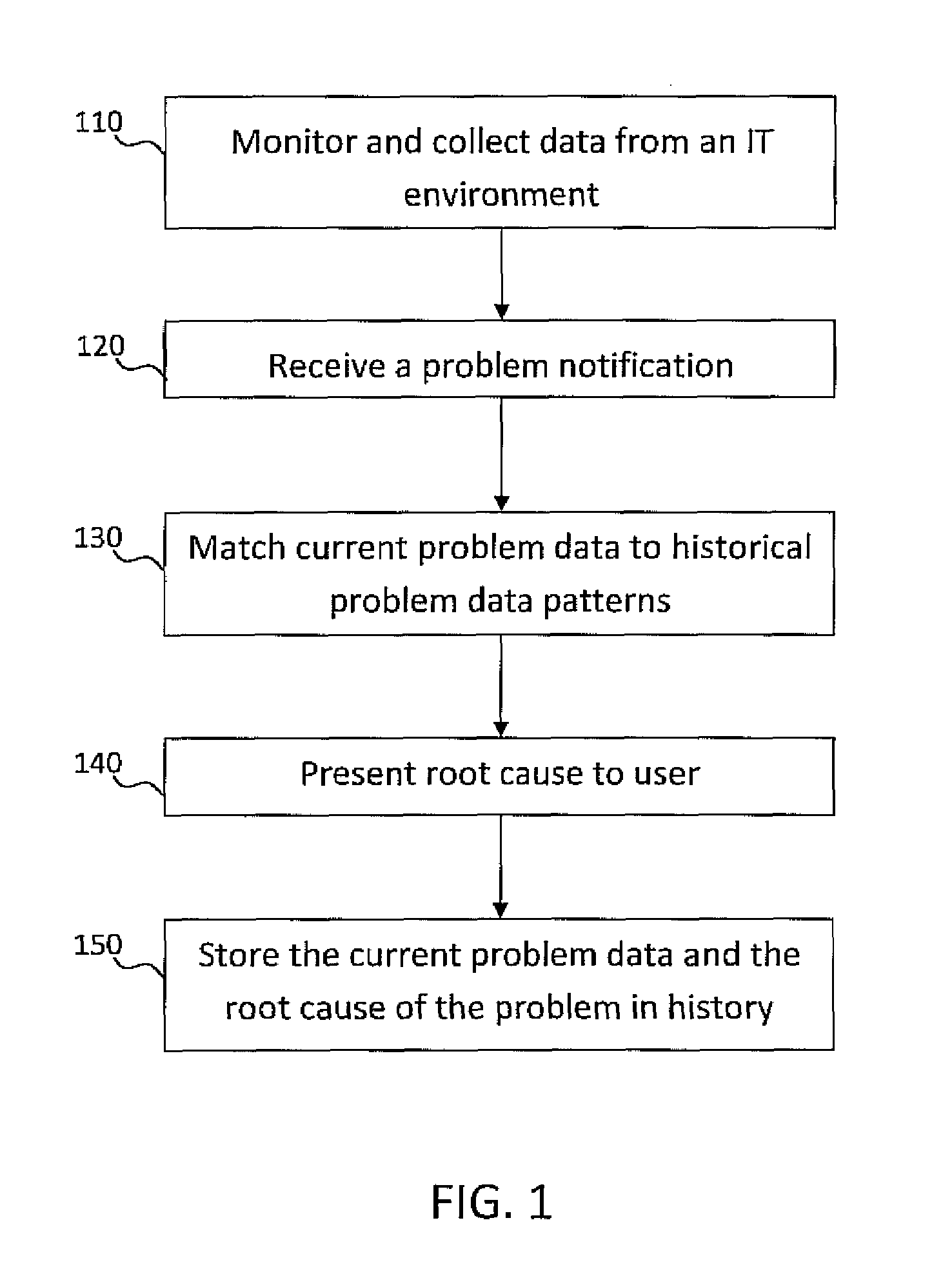
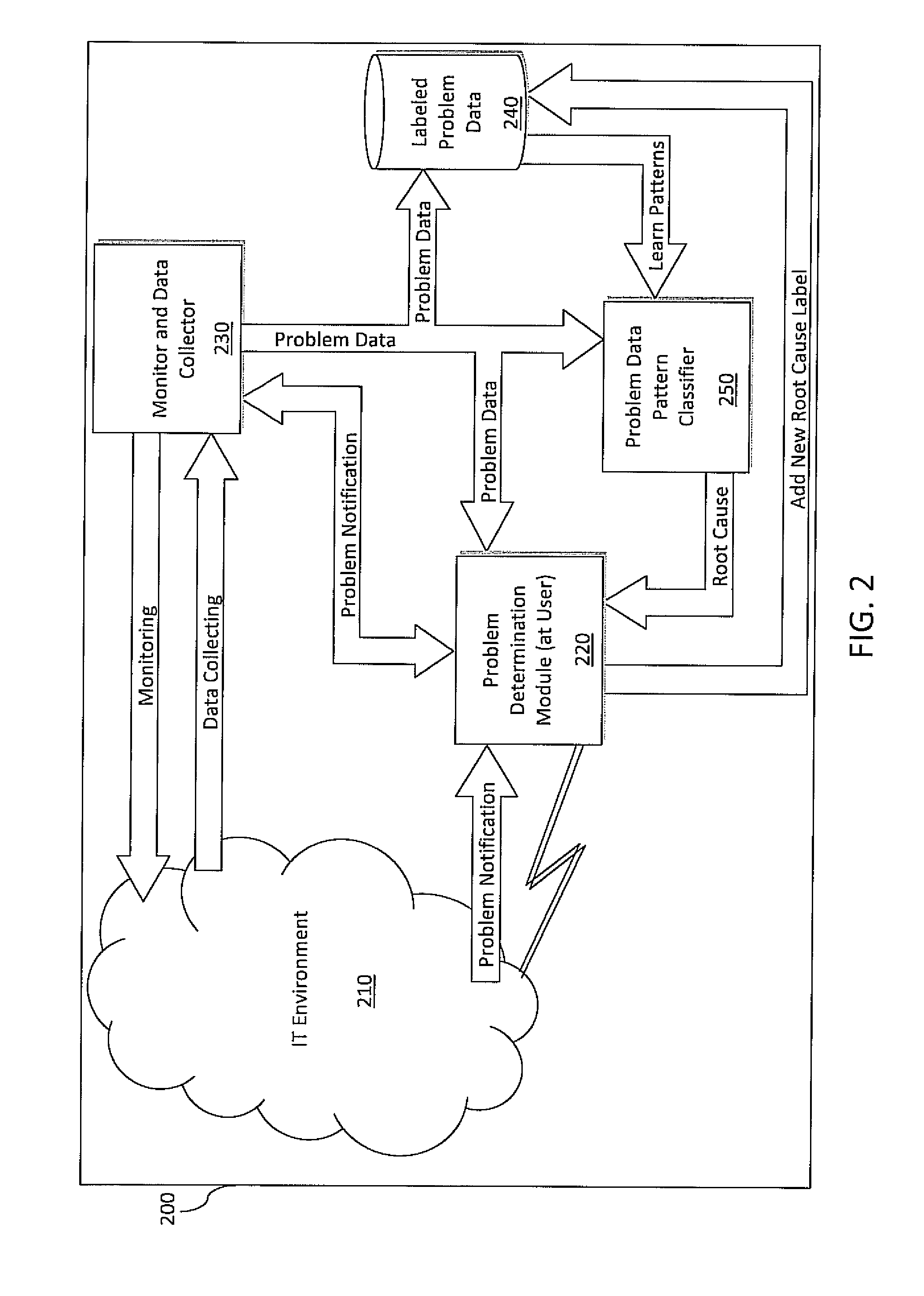
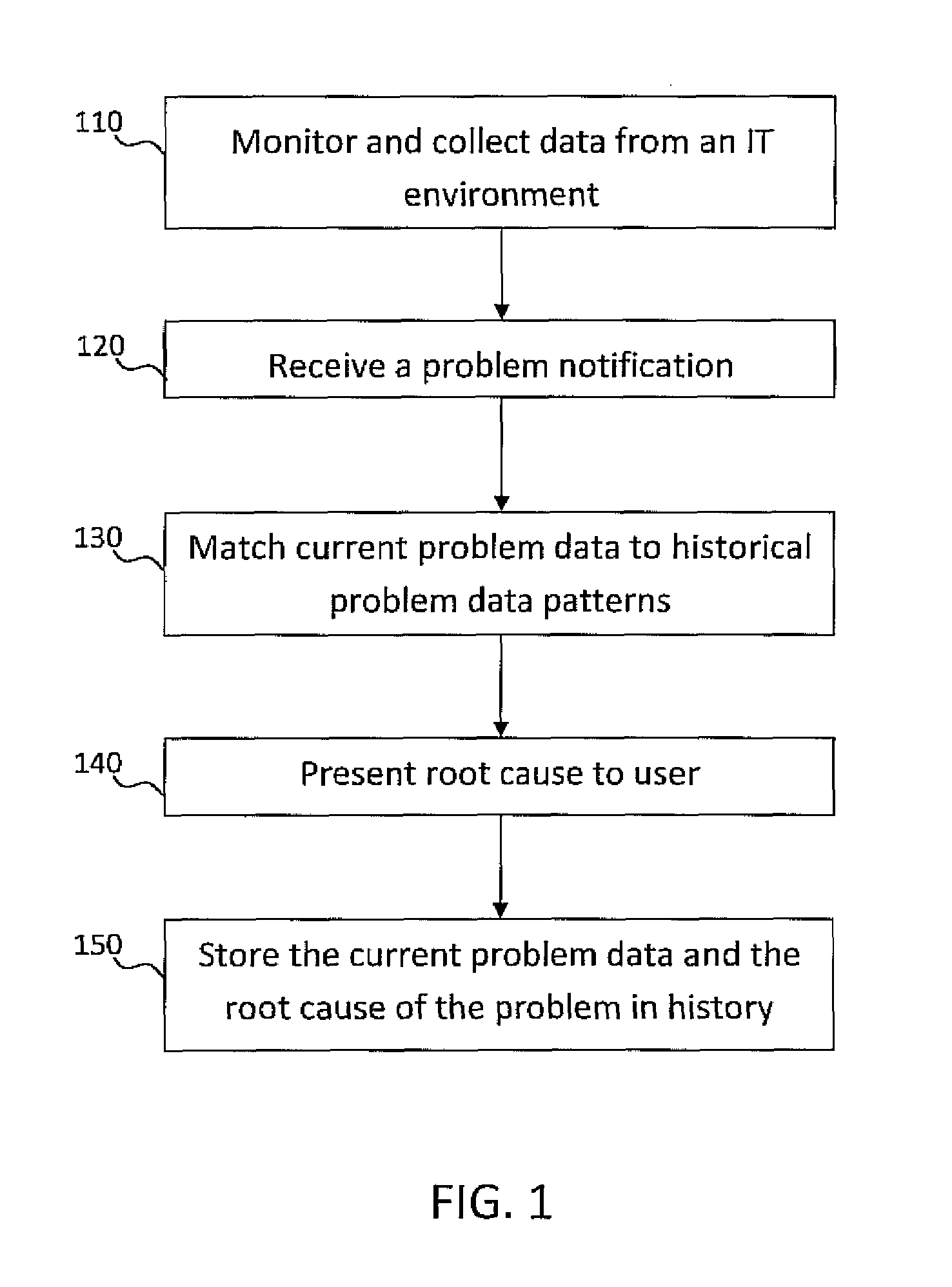
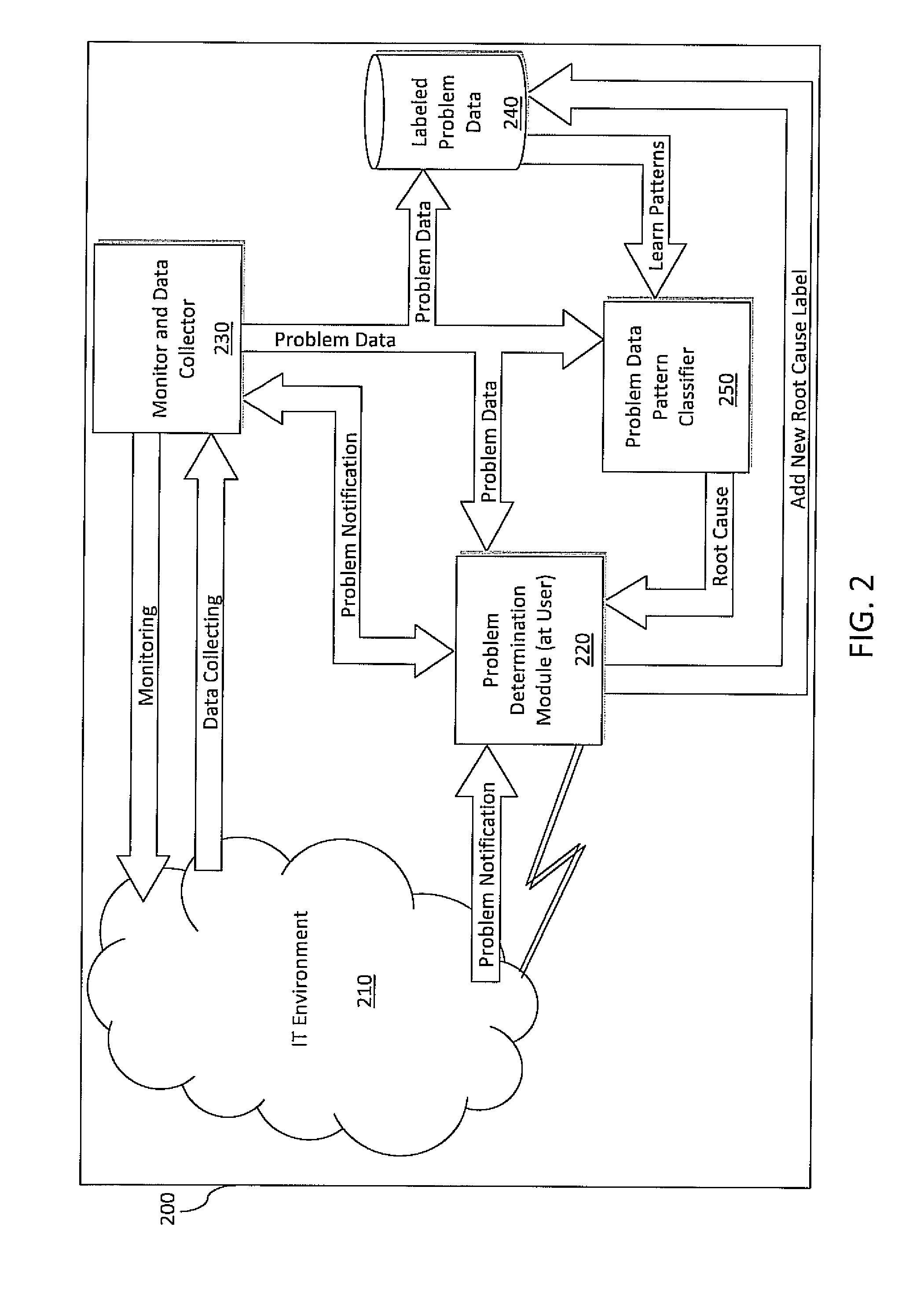
System and method for incident management enhanced with problem classification for technical support services
ActiveUS20100318846A1Reduce system management costsAccurately determineDigital computer detailsNon-redundant fault processingRoot causeOnline learning
A system and method of problem determination and resolution utilizes enhanced problem classification, and effectively categorizes any problem a user experiences by leveraging all available data to recognize the specific problem. Historical problem data is labeled with the cause of that problem and is analyzed to learn problem patterns. The historical problem data is classified into a predefined hierarchical structure of taxonomies by using an incremental online learning algorithm. The hierarchical structure and learned patterns are utilized to recognize problems and generate the root cause of the problem when given a new set of monitoring data and log data.
Owner:MAPLEBEAR INC
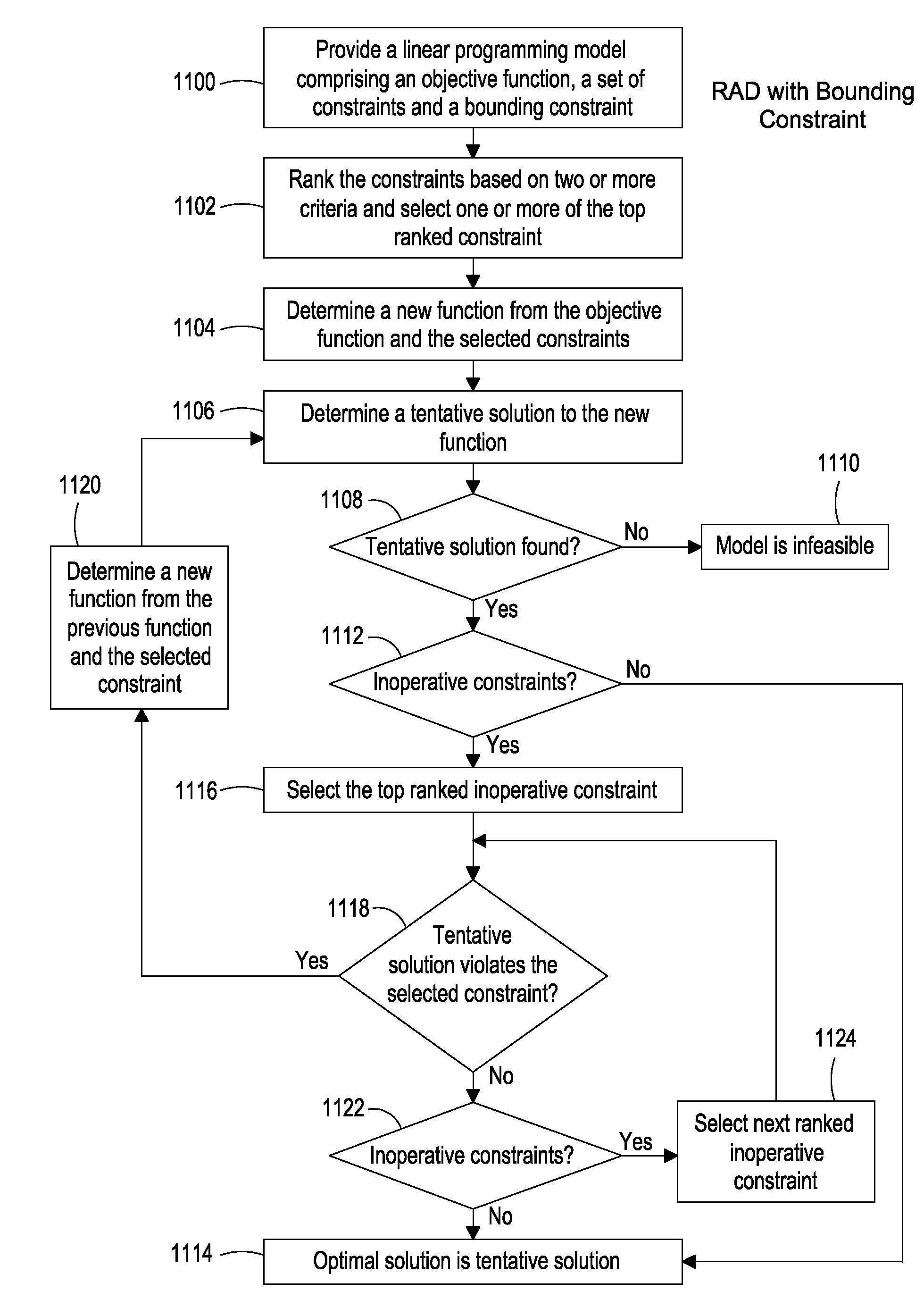
System, Method and Apparatus for Allocating Resources by Constraint Selection
ActiveUS20080134193A1Efficient memory usageGood decisionProgram synchronisationDigital computer detailsObject functionResource allocation
The present invention provides a system, method and apparatus for allocating resources with a linear programming model comprising an objective function and a set of constraints describing feasible allocations of the resources. The method ranks constraints based on a numerical measure derived from criteria selected from at least a first and second group and selects one or more of the top-ranked constraints. A new problem is determined from the model's objective function, the previously selected constraints, and the newly selected constraints, and a tentative resource allocation is determined based on the new problem. Whenever the tentative resource allocation violates a model constraint not in the current problem, one or more of the top-ranked such violated constraints are selected, and the new problem determination and tentative resource allocation steps are repeated. The resources are allocated according to the tentative resource allocation when it does not violate any model constraints.
Owner:BOARD OF RGT THE UNIV OF TEXAS SYST
Integrated logging for remote script execution
InactiveUS20080275951A1Multiple digital computer combinationsTransmissionRemote scriptingClient-side
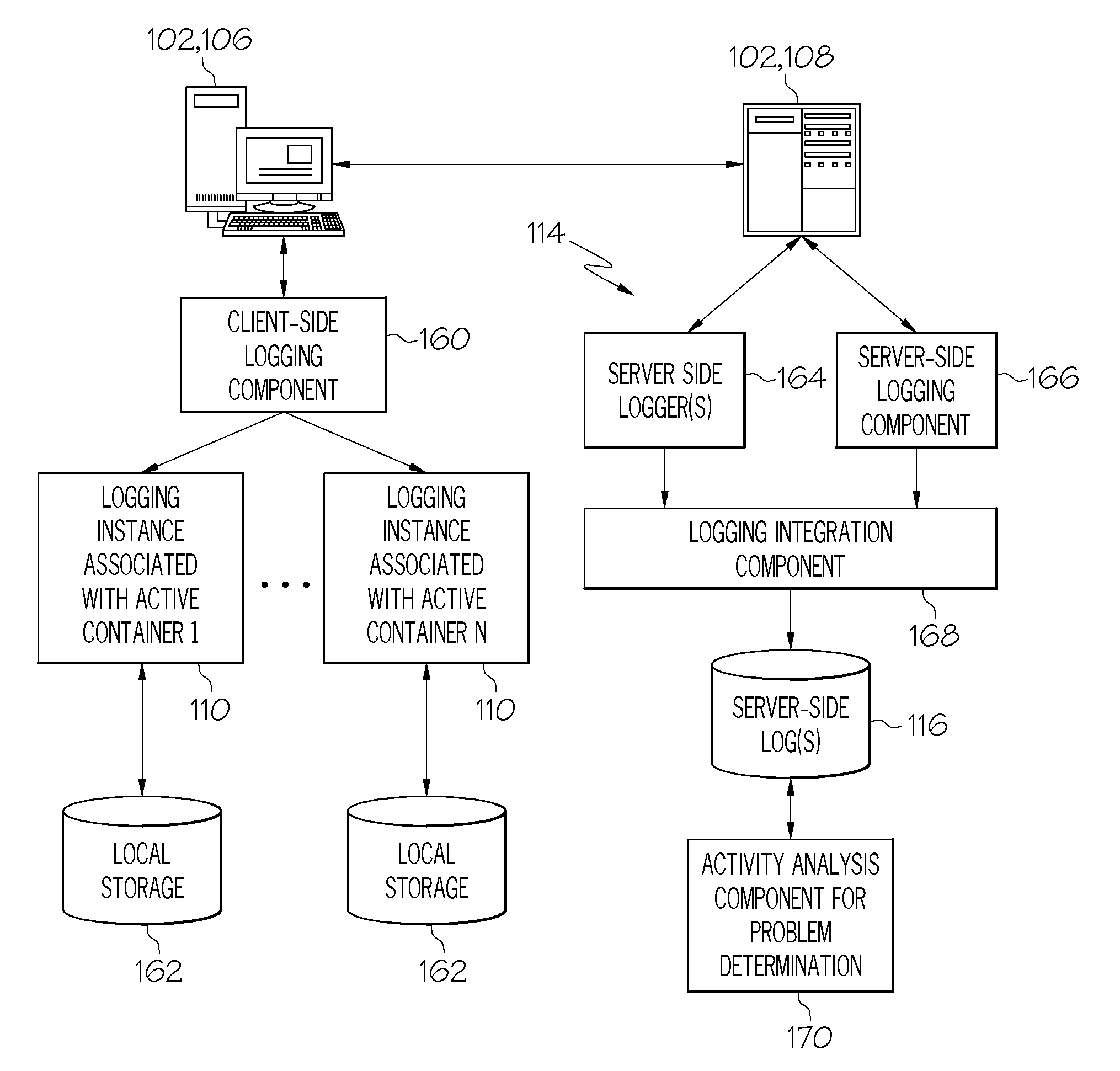
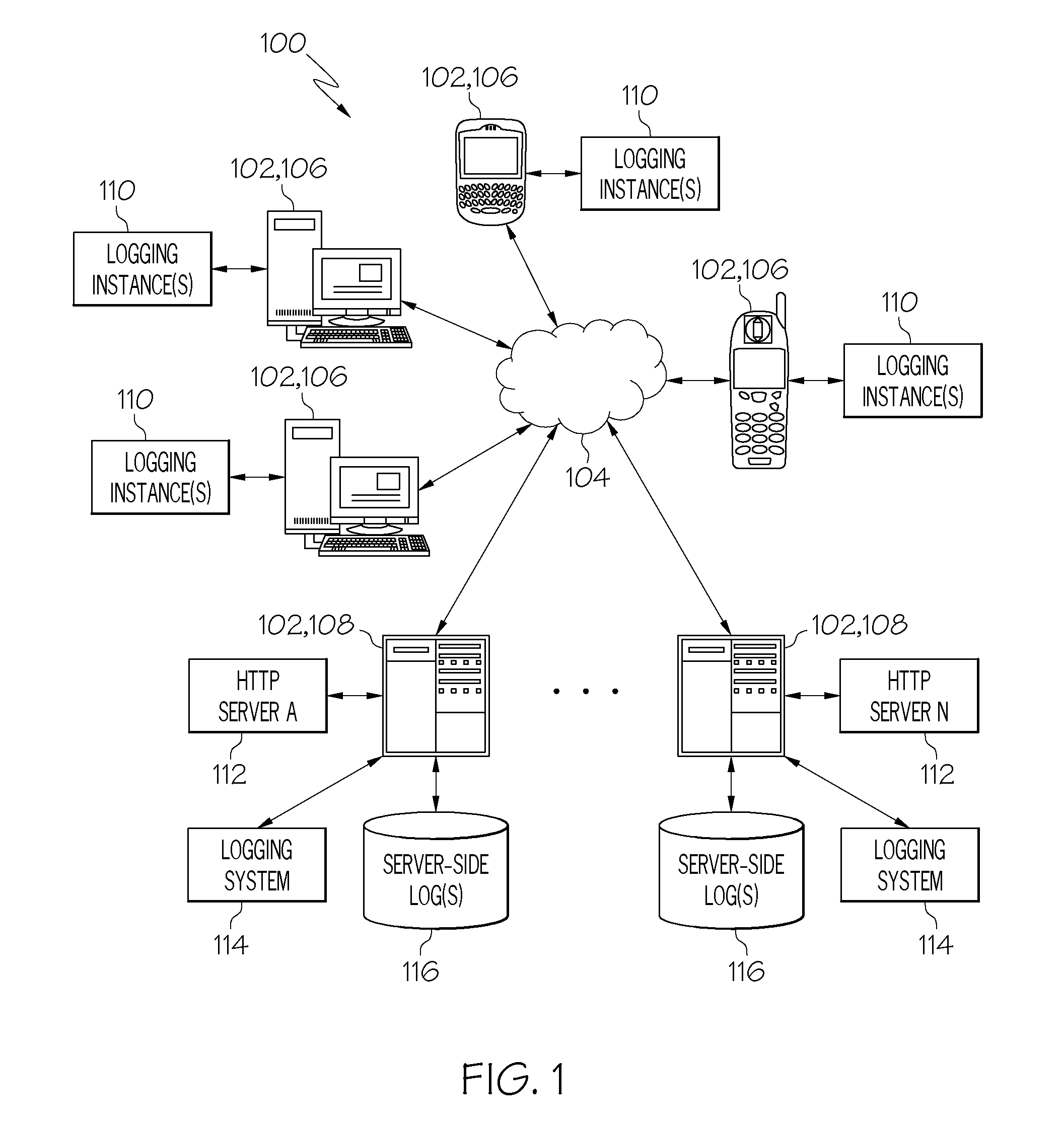
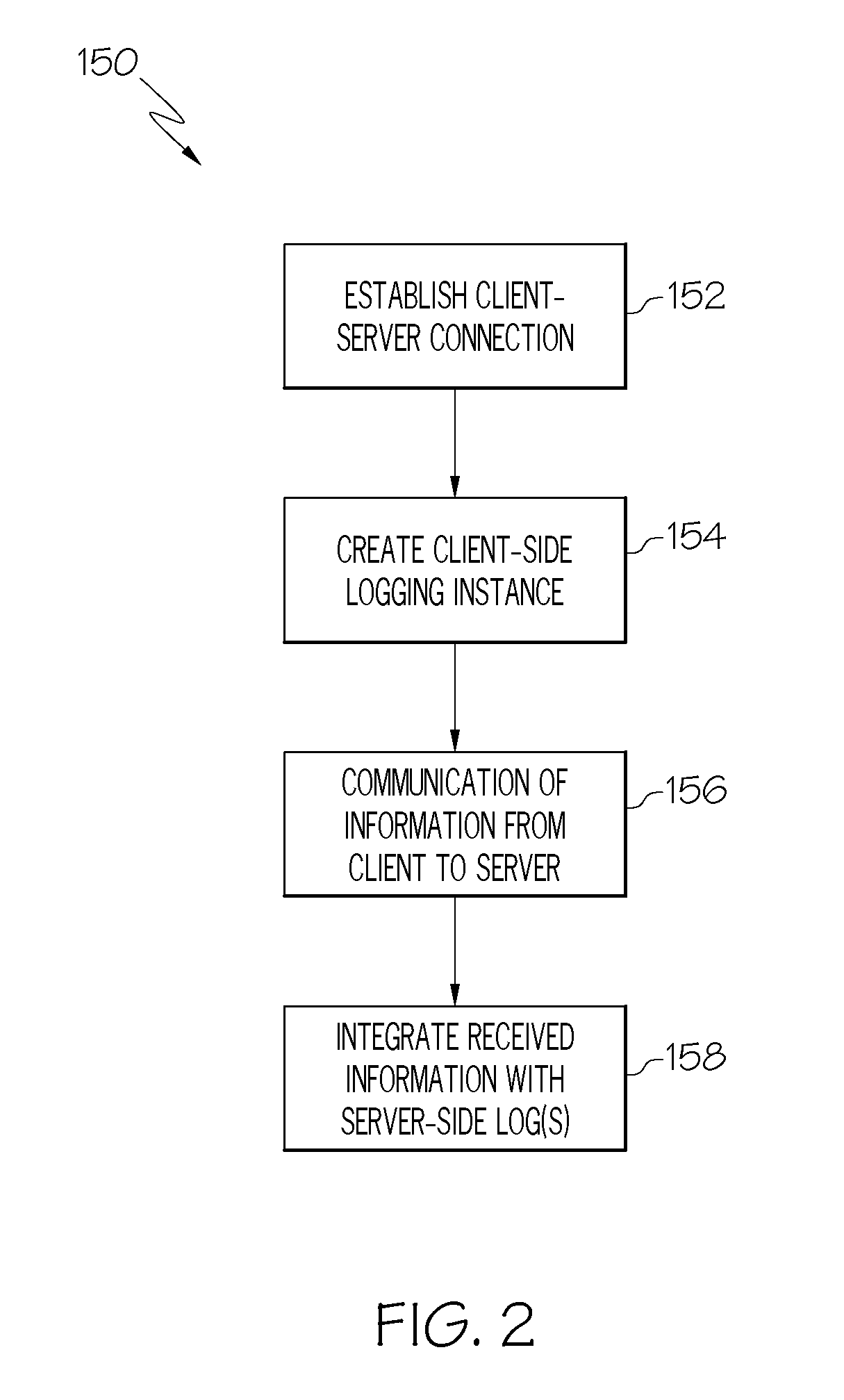
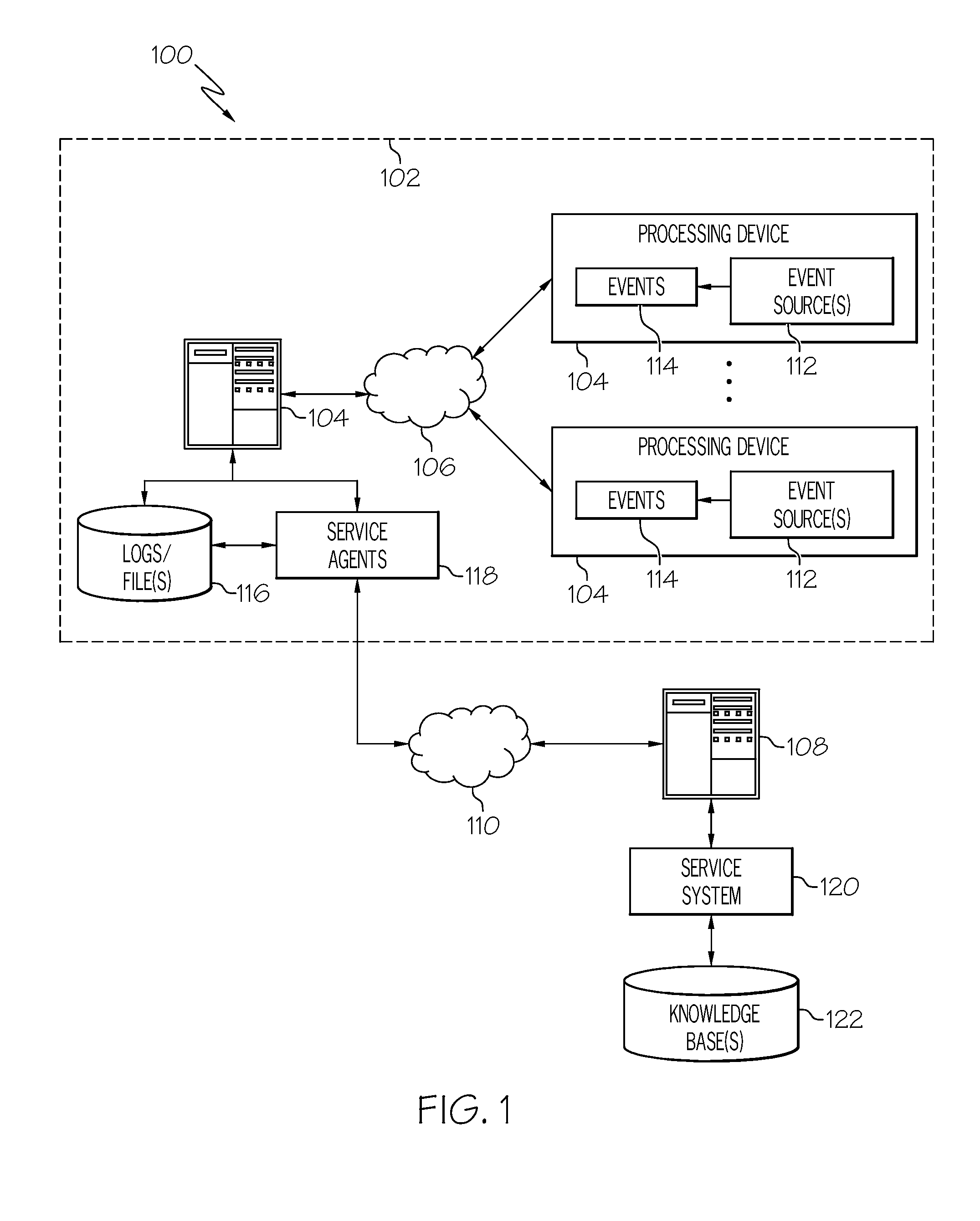
An integrated logging system includes a client-side logging component and a server-side logging component. The client-side logging component possesses the capability of logging client-side activity information, such as may relate to the execution of a script or other suitable client-side code that is controlled and executed independently of a remote server associated with the server-side logging component. The client-side logging component may also communicate logged activity information back to the corresponding server-side logging component. Messages including logged client-side activity information are received from the client-side logging component by the server-side logging component, and the logged activity information is integrated into the server-side log(s) of a server-side logging system. Thus, activity information from an independently controlled and operated processing device, which may be used, for example for problem determination, is integrated from sources that are distributed between systems.
Owner:IBM CORP
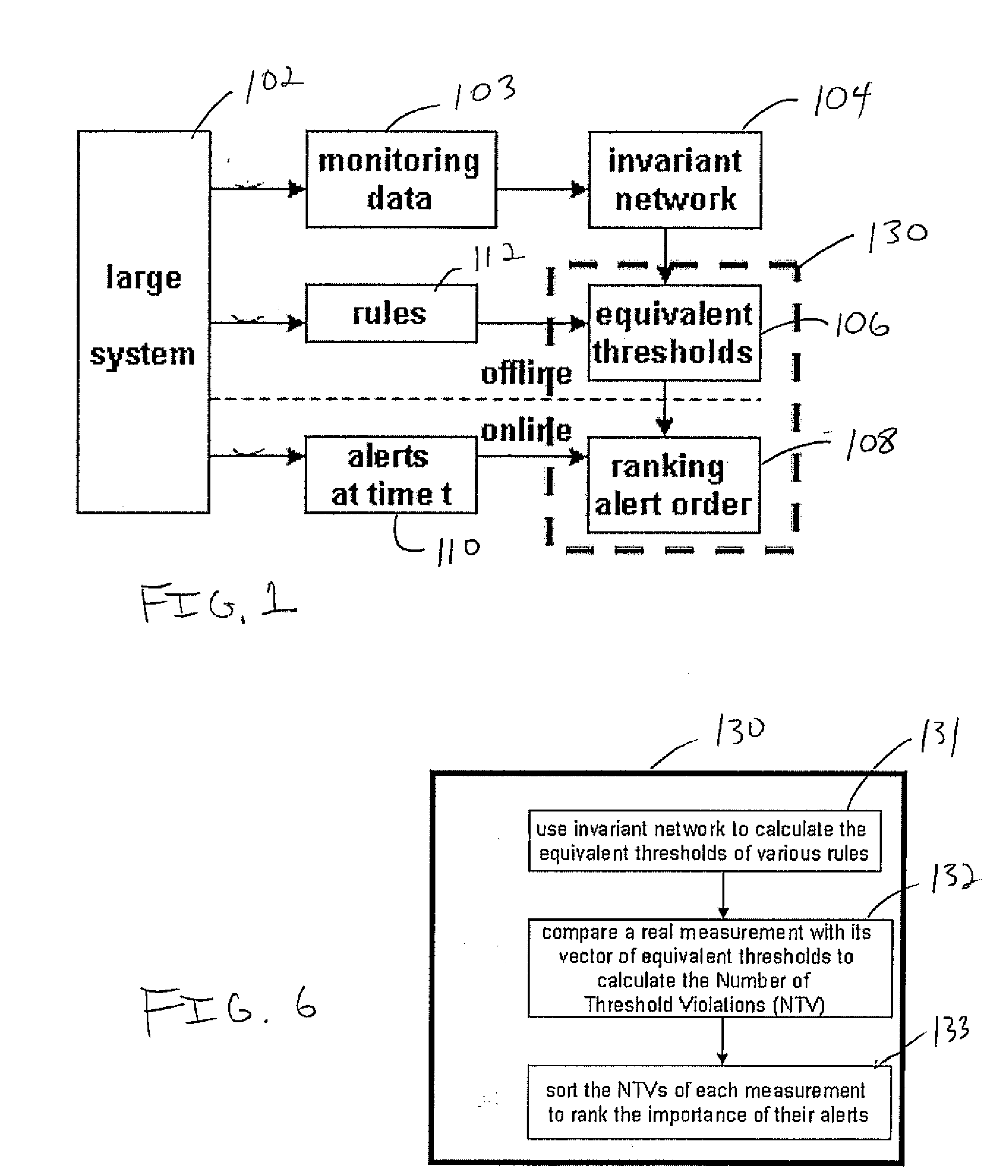
Ranking the importance of alerts for problem determination in large systems
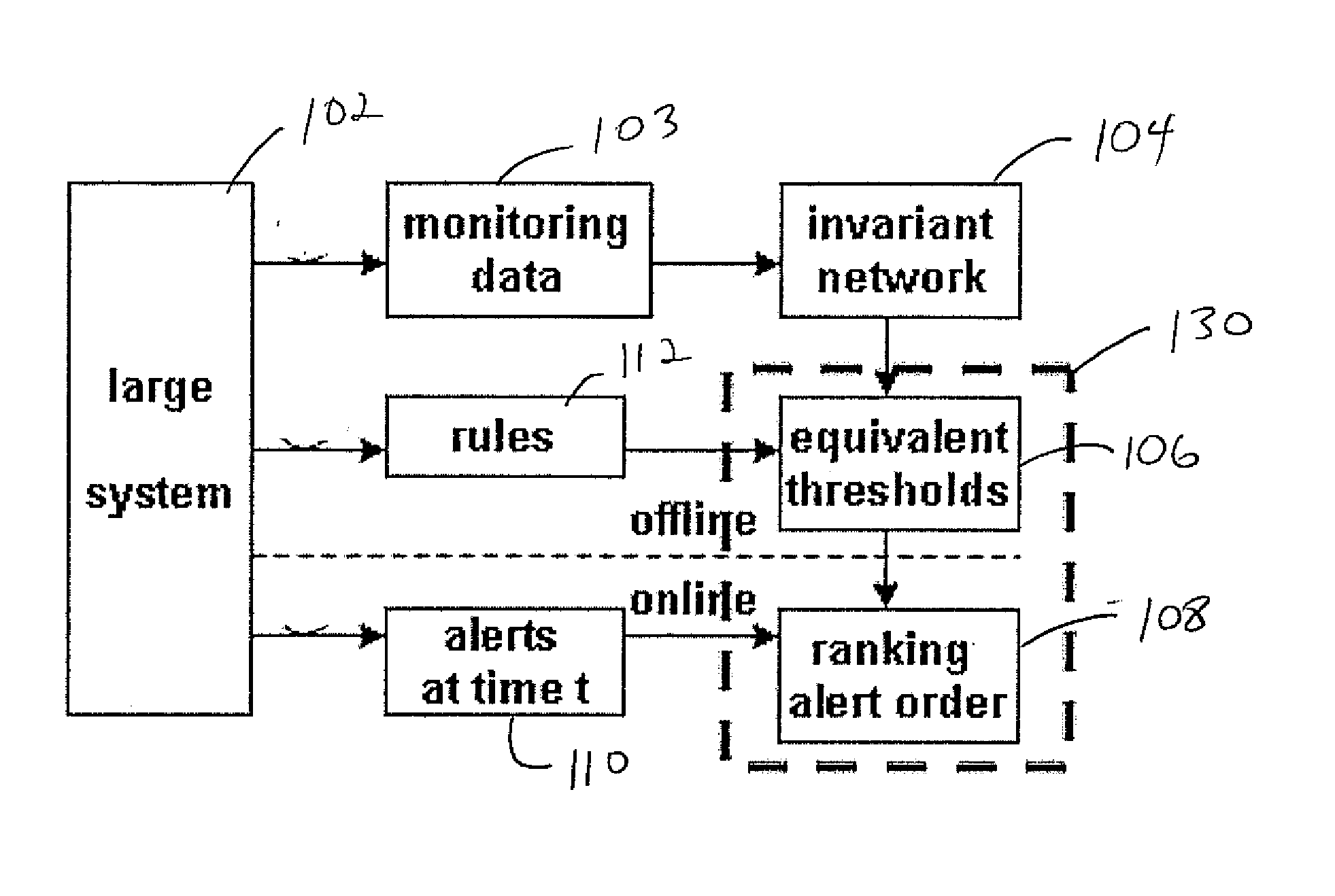
A system and method for prioritizing alerts includes extracting invariants to determine a stable set of models for determining relationships among monitored system data. Equivalent thresholds for a plurality of rules are computed using an invariant network developed by extracting the invariants. For a given time window, a set of alerts are received from a system being monitored. A measurement value of the alerts is compared with a vector of equivalent thresholds, and the set of alerts is ranked.
Owner:NEC CORP
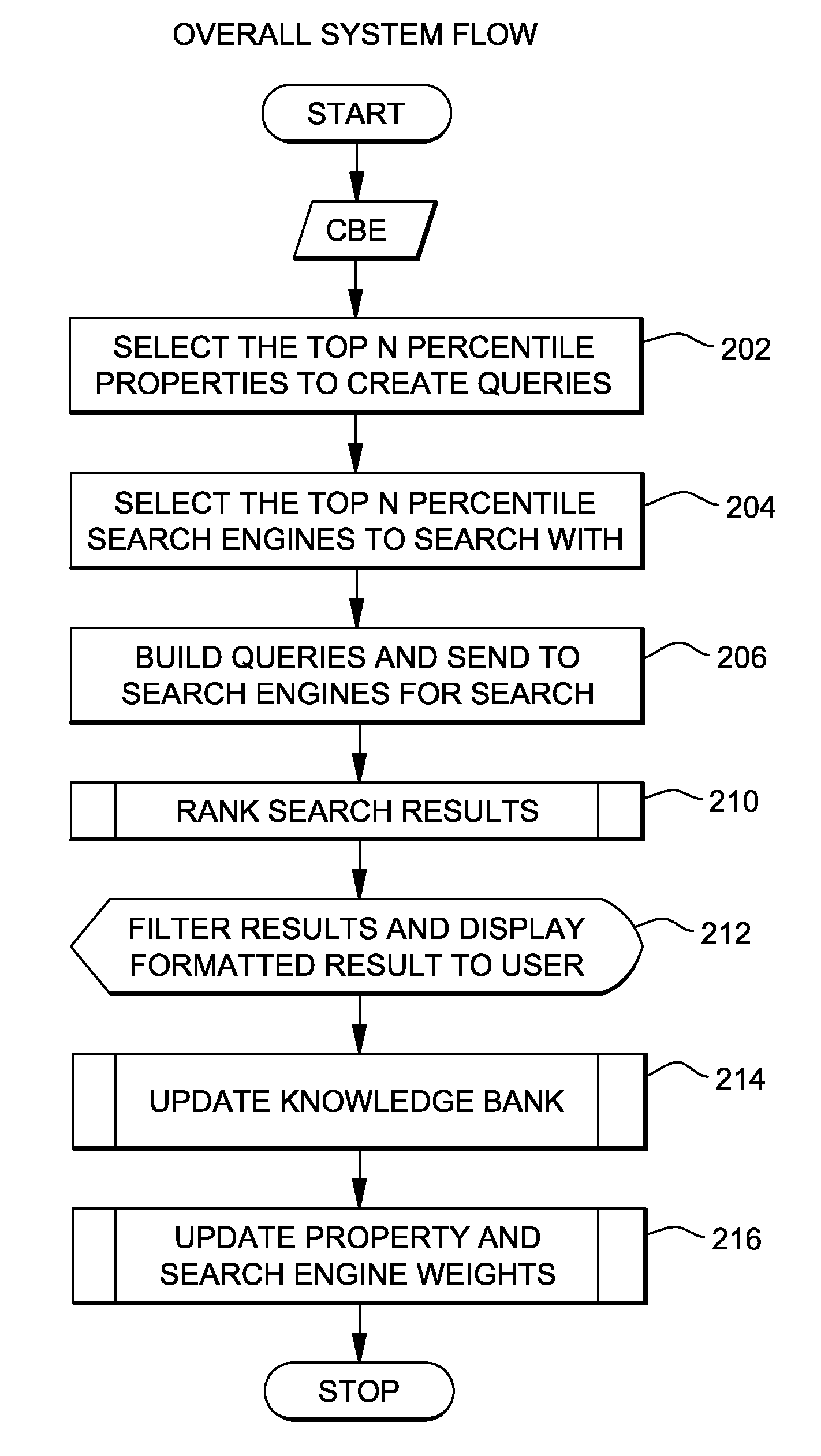
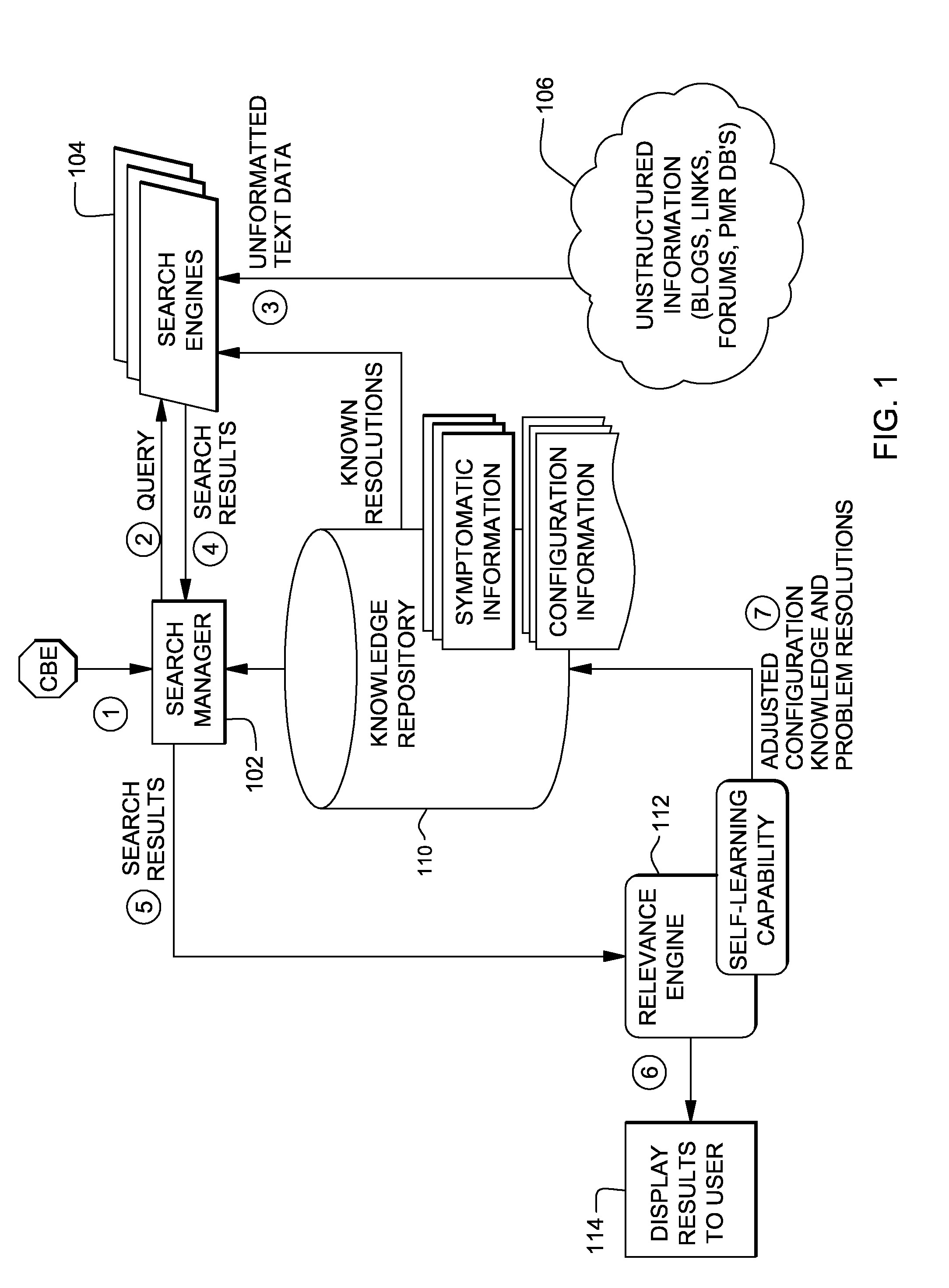
Intelligent event-based data mining of unstructured information
InactiveUS8356047B2Low costProvide informationWeb data indexingDigital data processing detailsRelevant informationSmart data
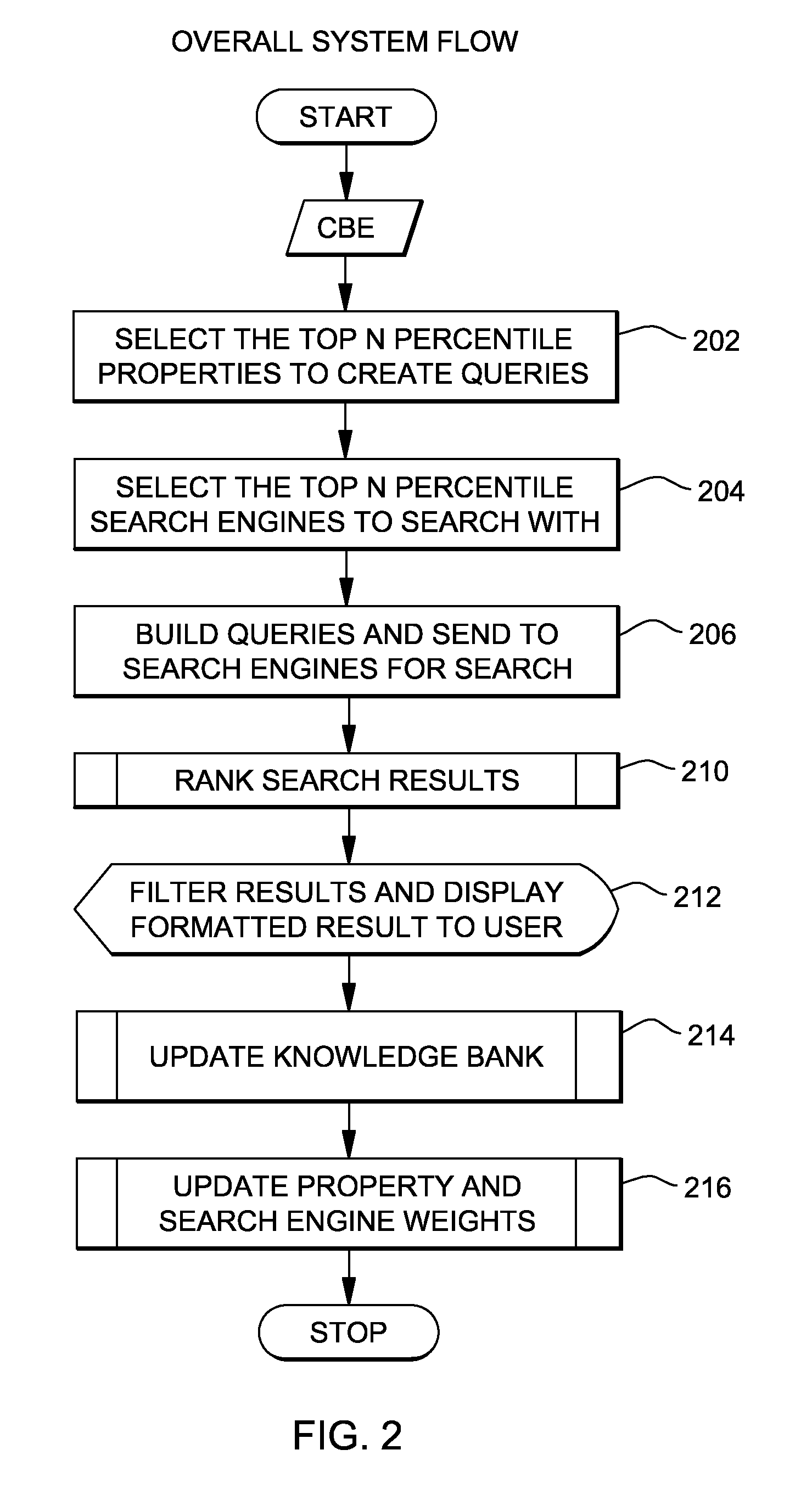
A method, system and computer program product is disclosed for intelligent data mining. The method comprises receiving an event from an application, assigning property weights to properties of the event, and building a query from these properties based on the property weights. The method further comprises assigning search engine weights to a group of search engines, selecting at least some of the search engines based on the search engine weights, and sending the built query to the selected search engines. Results from the selected search engines are stored in a knowledge repository and used to adjust the property weights and the search engine weights. The invention may be used to provide an analysis with information about a problem, and to manage a solutions database which can be used for problem determination. The invention provides a low cost solution for collecting relevant information from online sources.
Owner:INT BUSINESS MASCH CORP
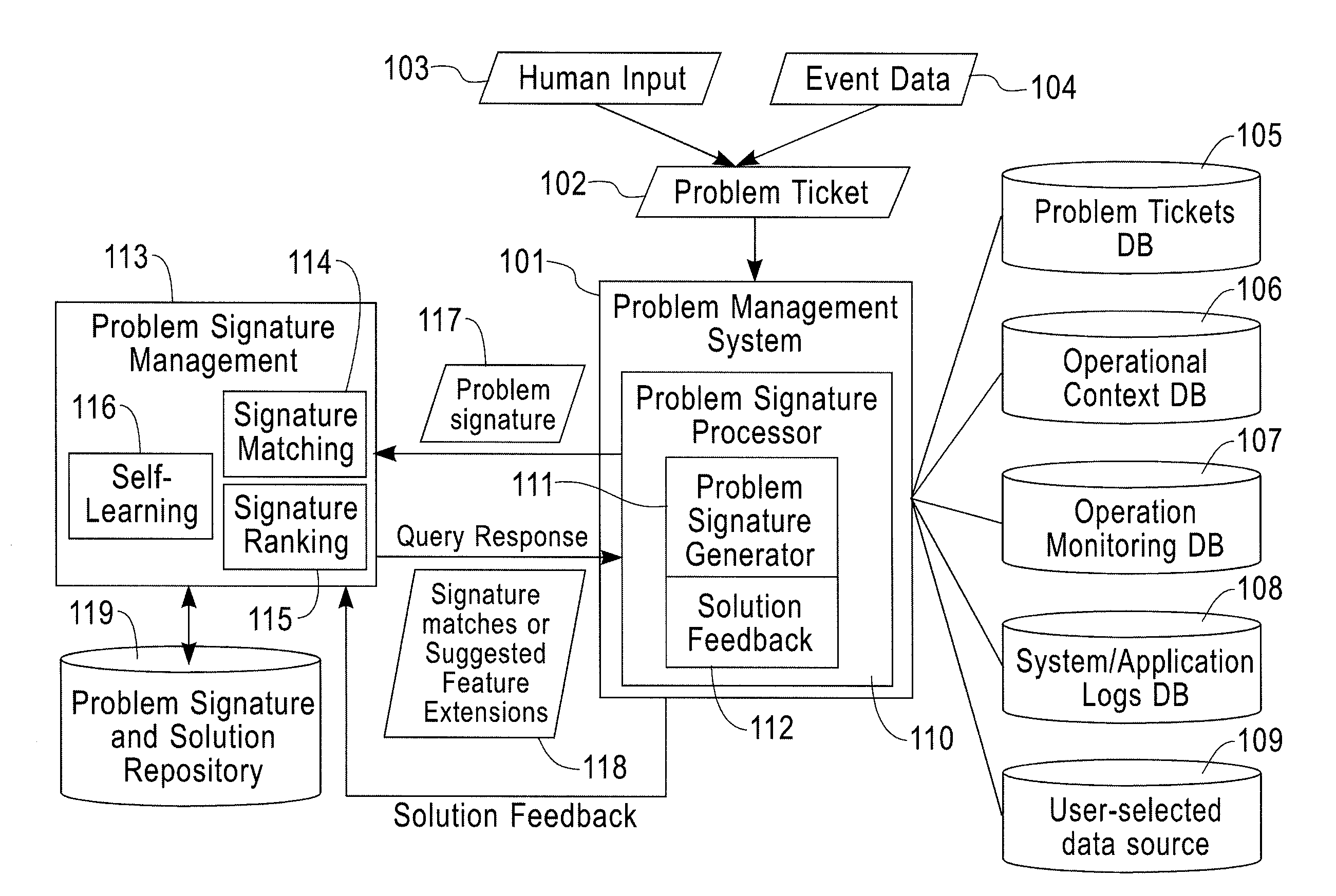
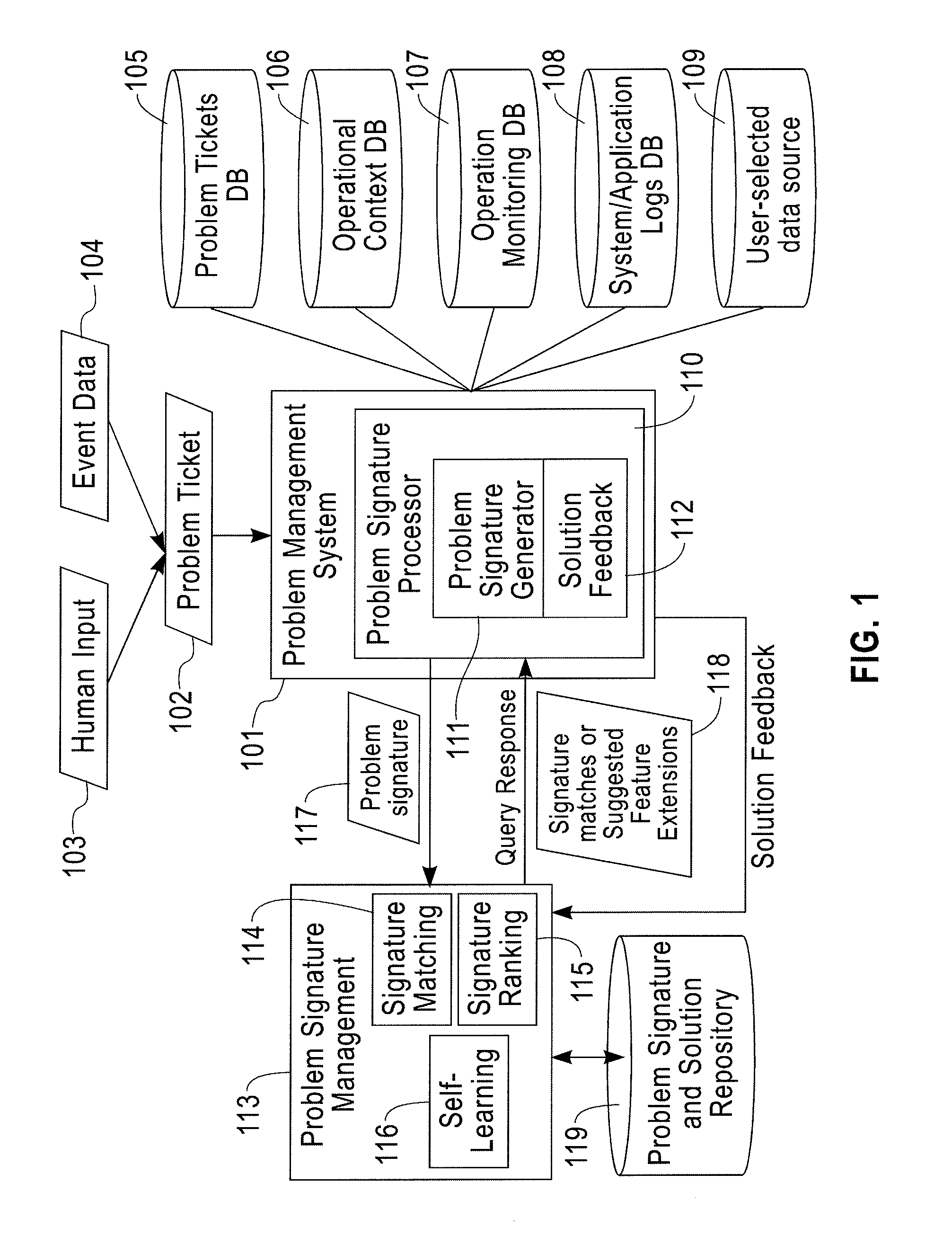
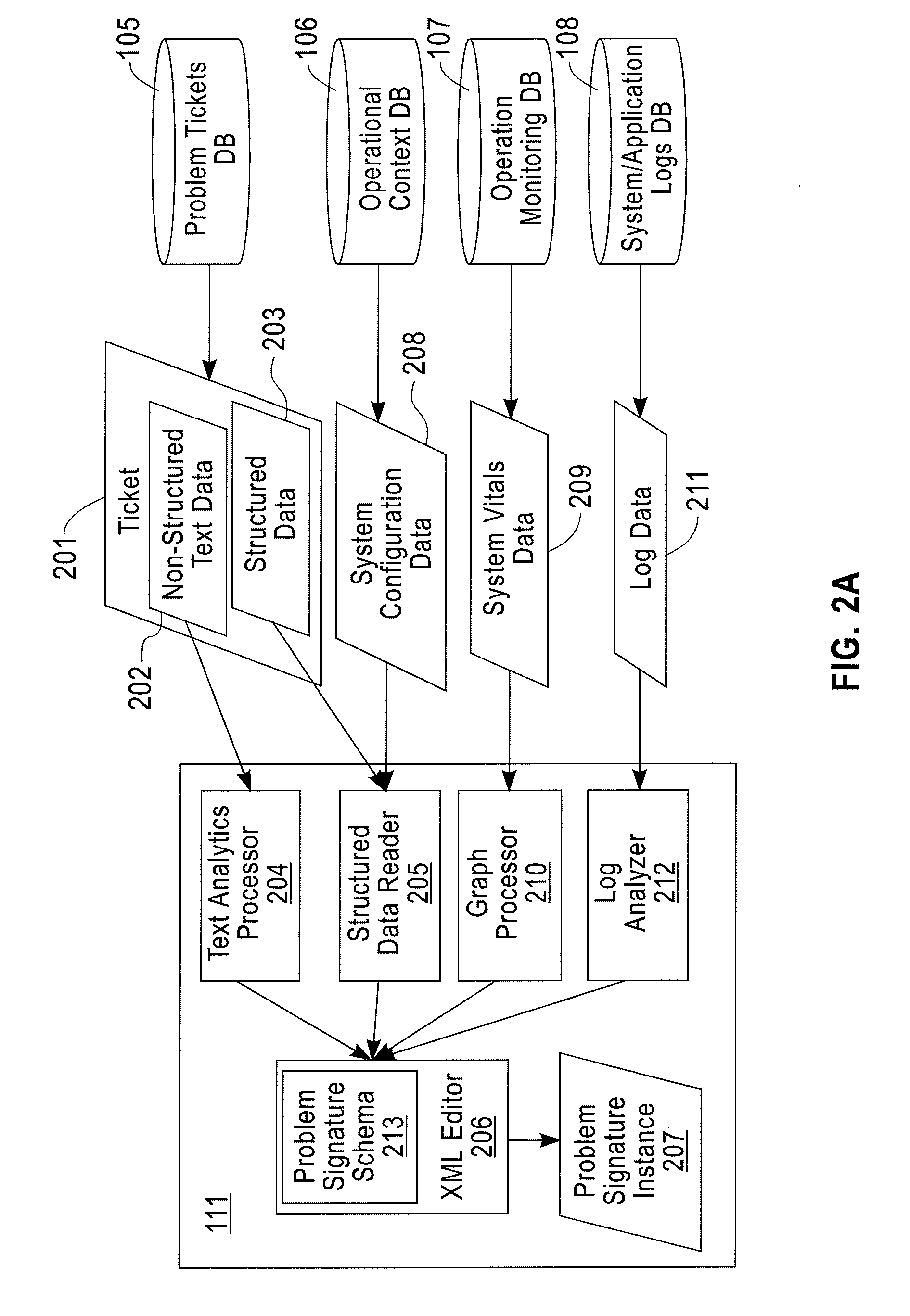
Problem Record Signature Generation, Classification and Search in Problem Determination
A method for problem determination and resolution in an information technology (IT) system includes receiving a problem ticket, searching a database for a plurality of problem features based on data included in the problem ticket, extracting the plurality of problem features from the database, and generating a problem signature corresponding to the problem ticket, wherein the problem signature comprises at least one non-textual feature extracted from the plurality of problem features.
Owner:GLOBALFOUNDRIES US INC
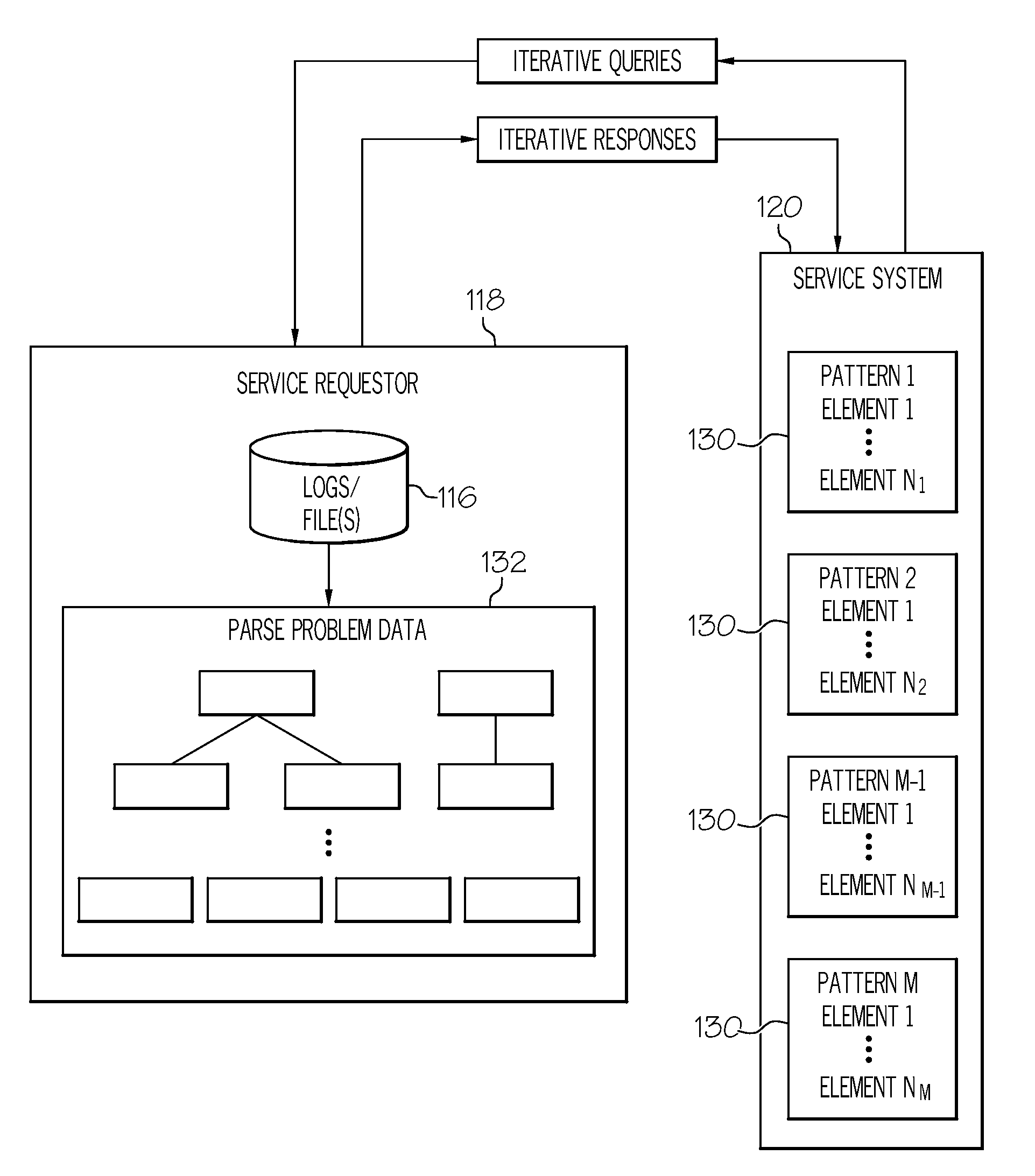
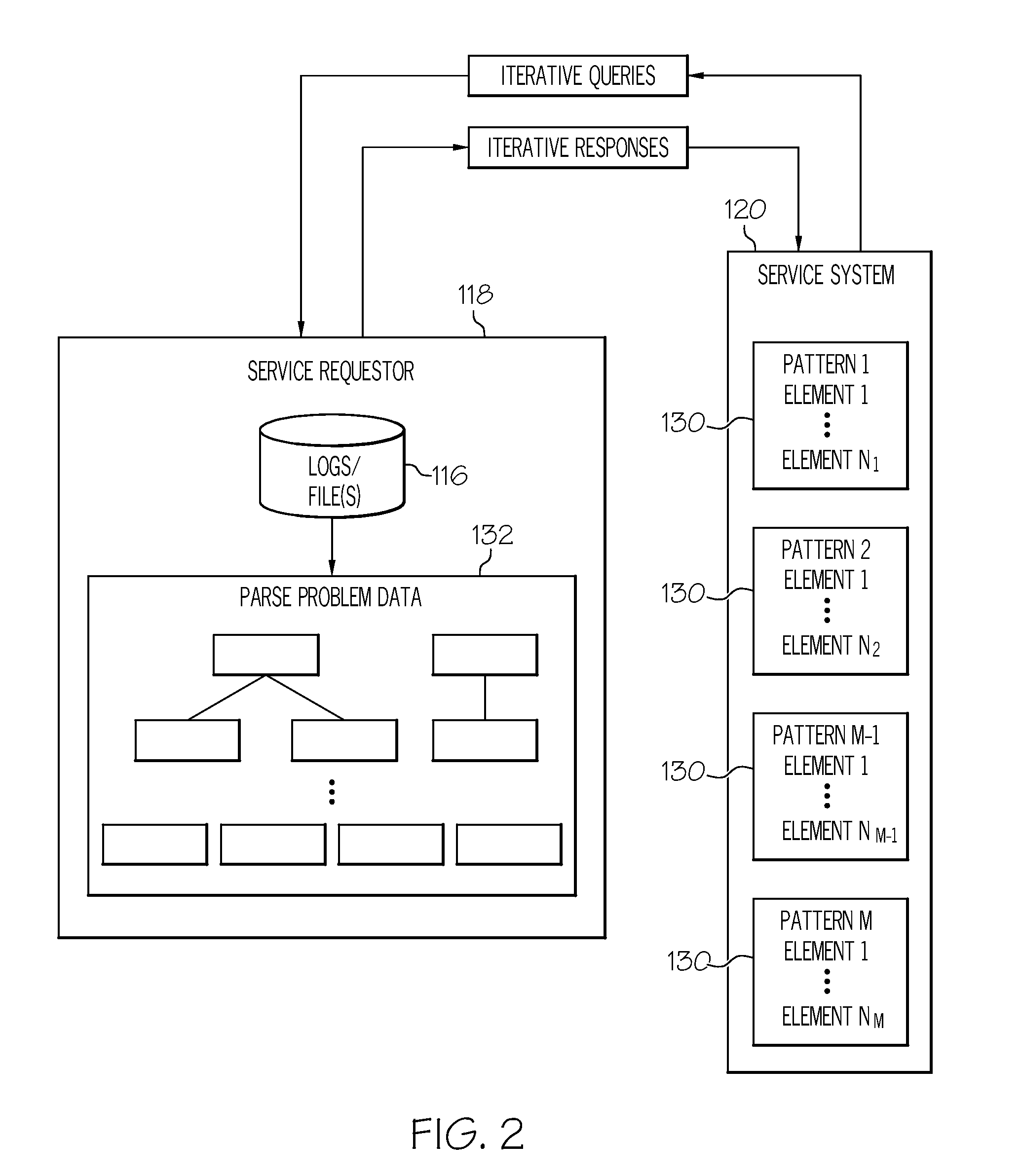
Problem determination service
InactiveUS20080183704A1Digital data processing detailsNuclear monitoringRoot causeProblem resolution
A service system receives a request for problem resolution knowledge from a service requestor. Upon receiving the request, the service system identifies candidate patterns where each candidate pattern has at least one element that characterizes a problem associated with the corresponding pattern. An iterative process is then repeated between the service requestor and the service system until a stopping criterion is met, which attempts to narrow the field of candidate patterns down until one or more possible root causes of the problem experienced by the service requestor are identified. Alternatively, it may be determined that a possible root cause of the problem is not contained in the candidate patterns or that some other action, event, etc., interrupts the iterative process.
Owner:IBM CORP
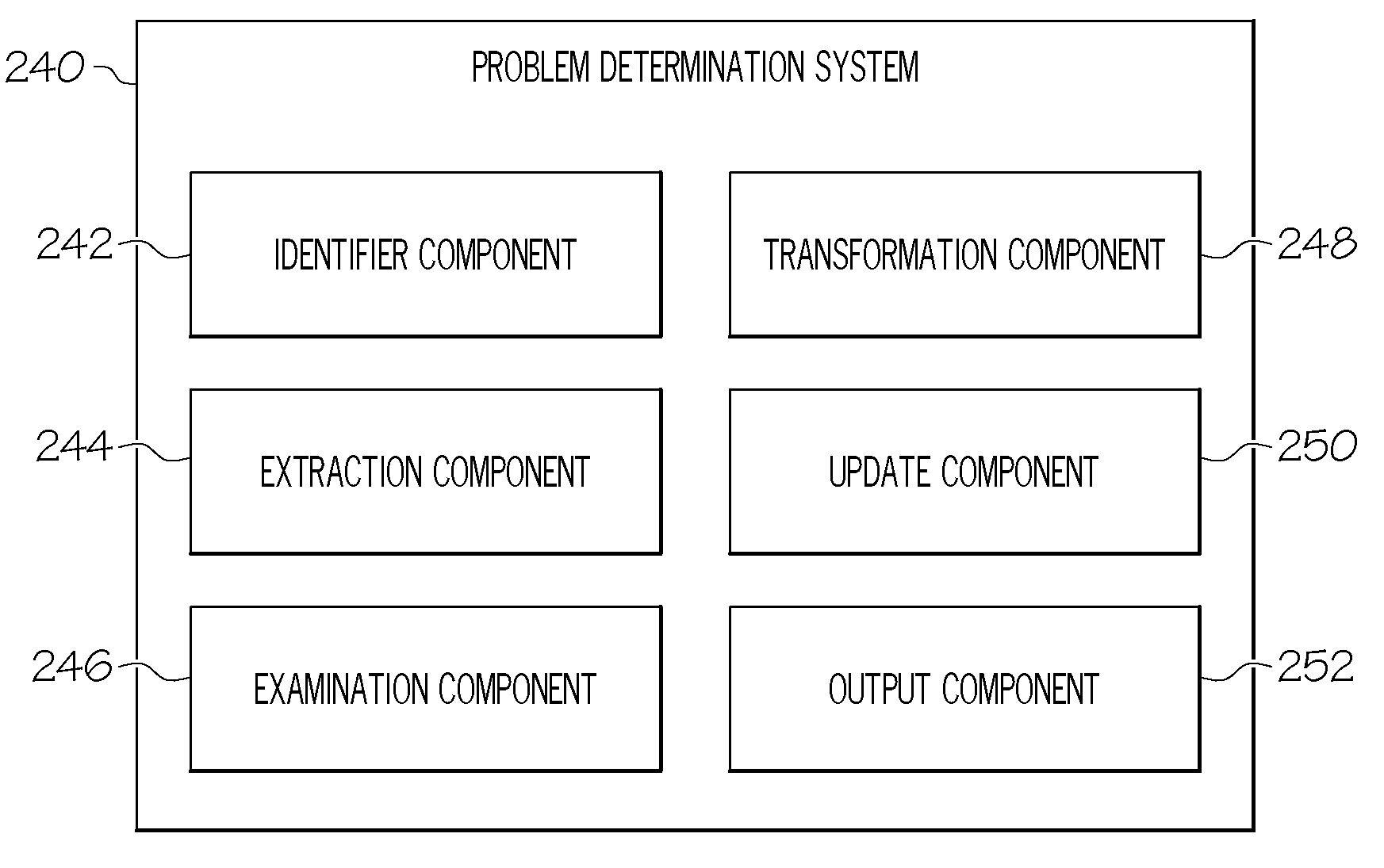
Collecting and representing knowledge
Problem determination knowledge is provided by an extraction tool that extracts tag information recorded in identified problem tracking tools, where the tags relate to problem knowledge. The extracted tag information is examined to produce a catalog of symptom definitions that can be utilized by tools such as problem submission, logging and / or analysis tools.
Owner:IBM CORP
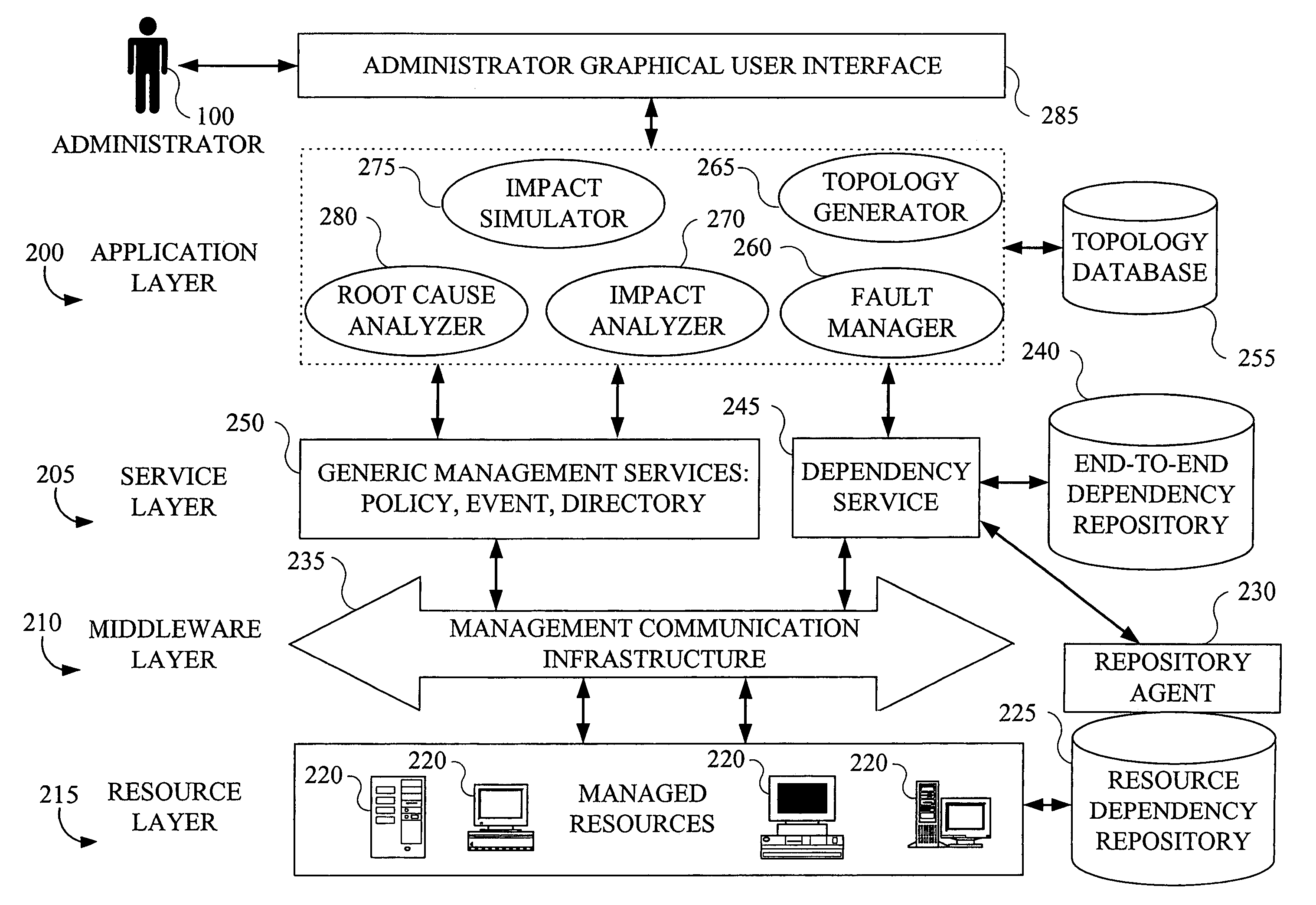
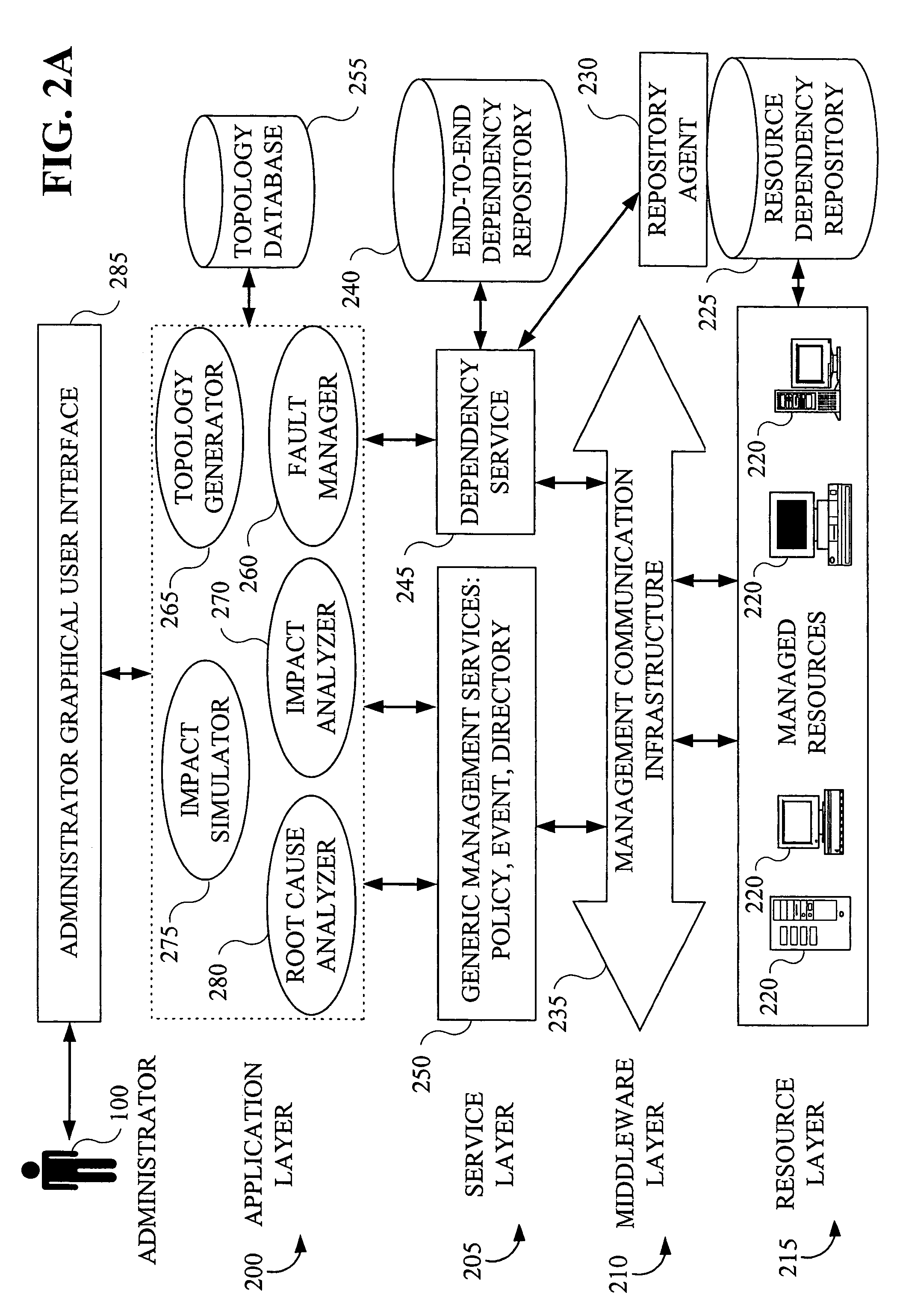
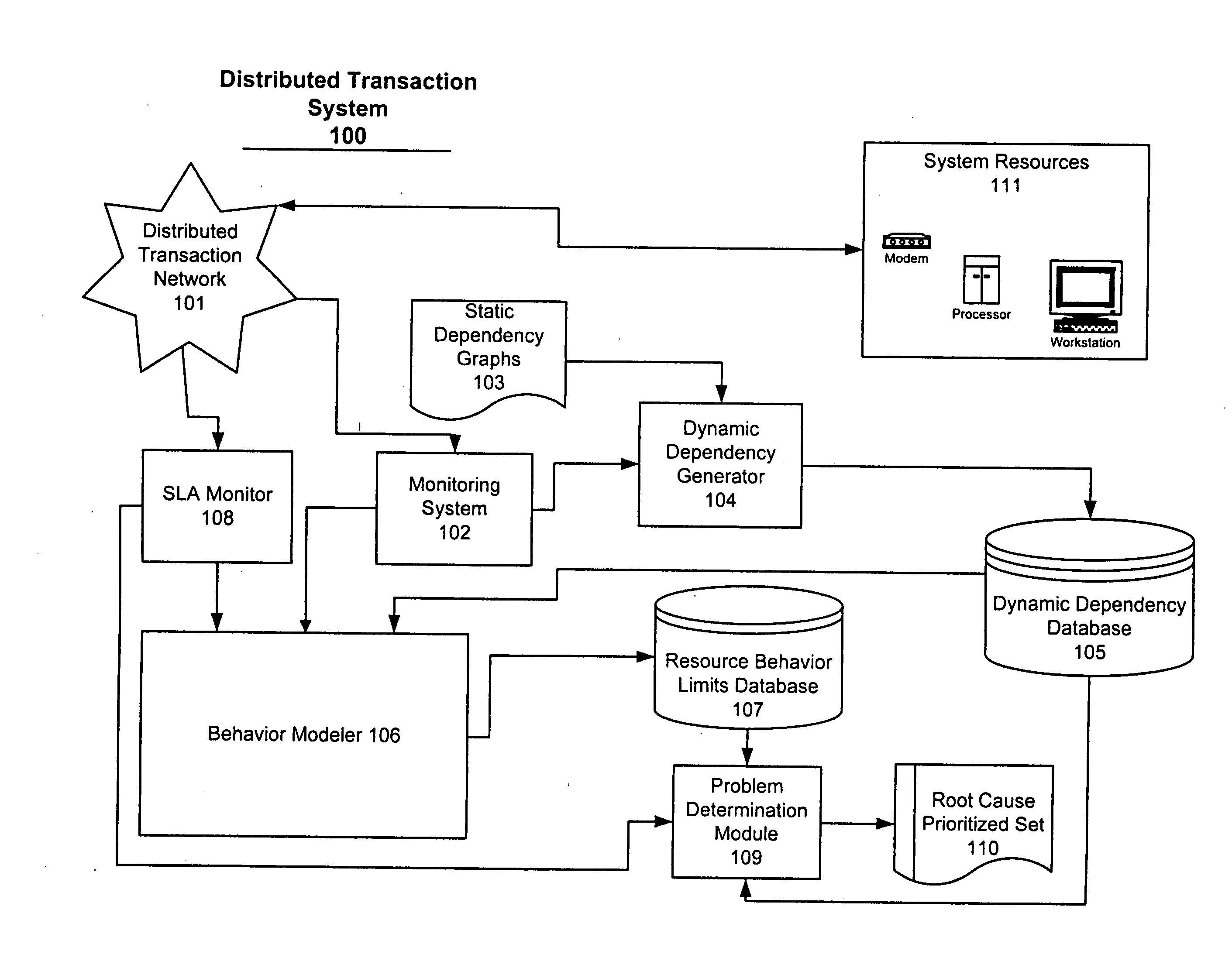
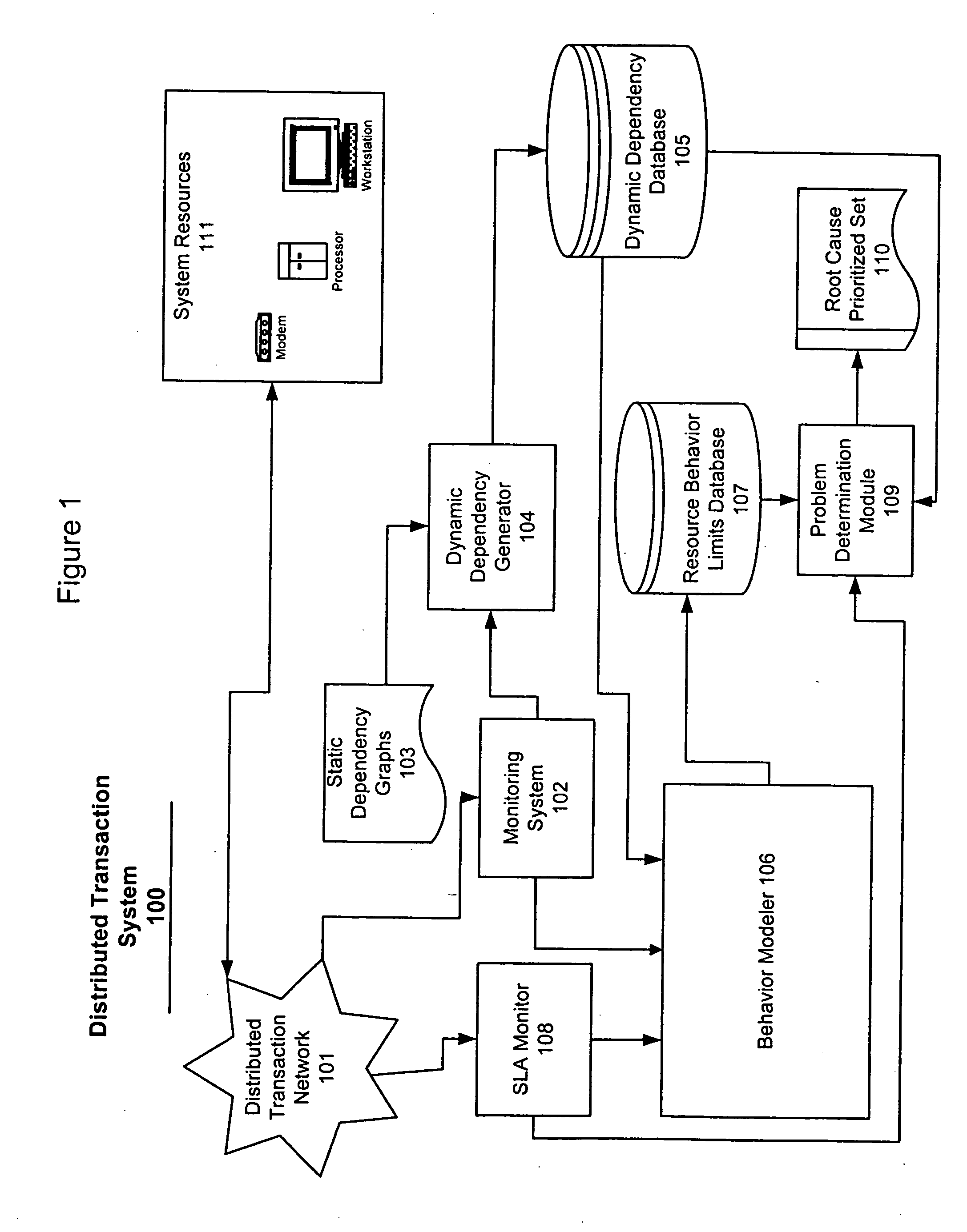
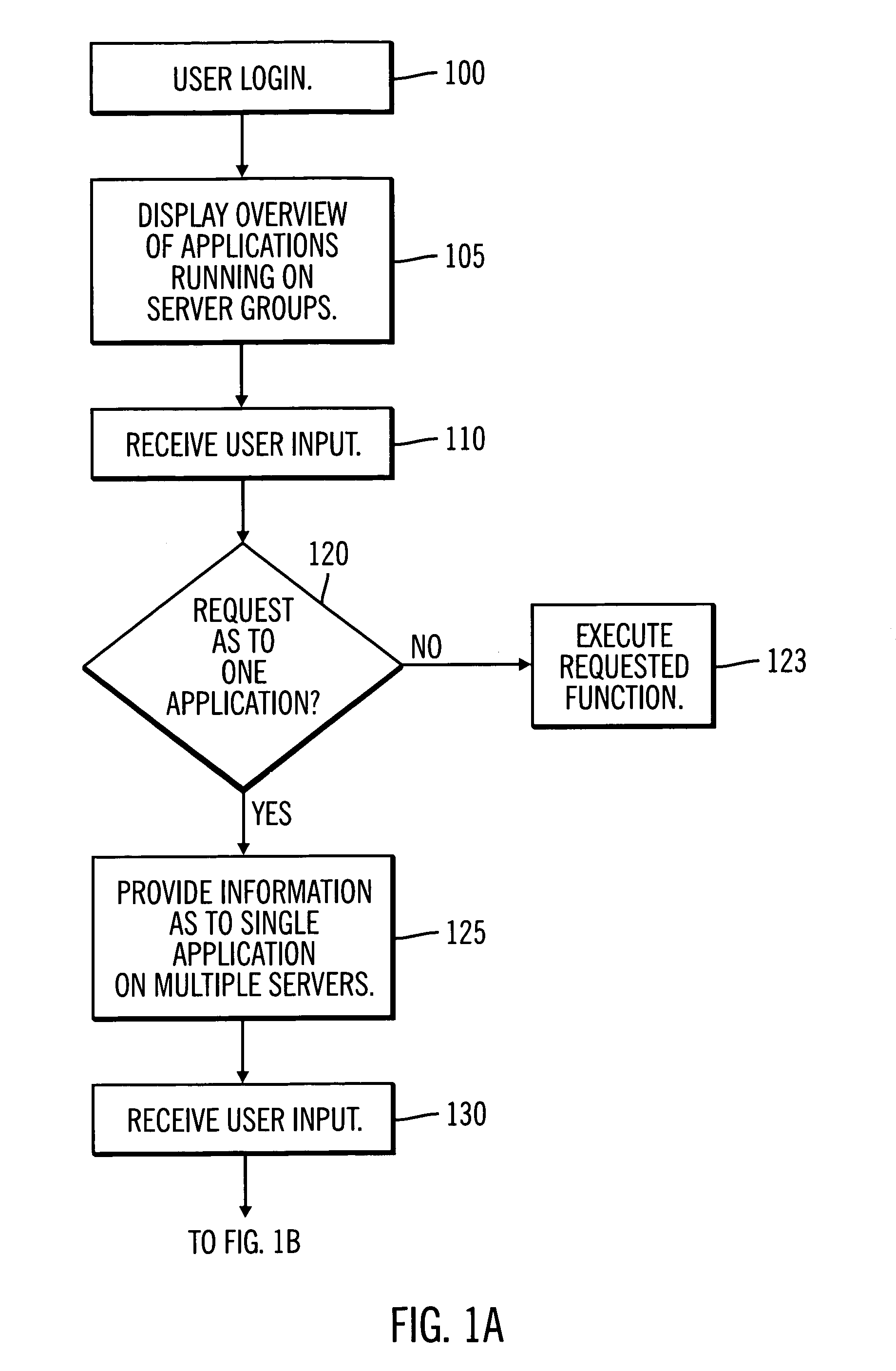
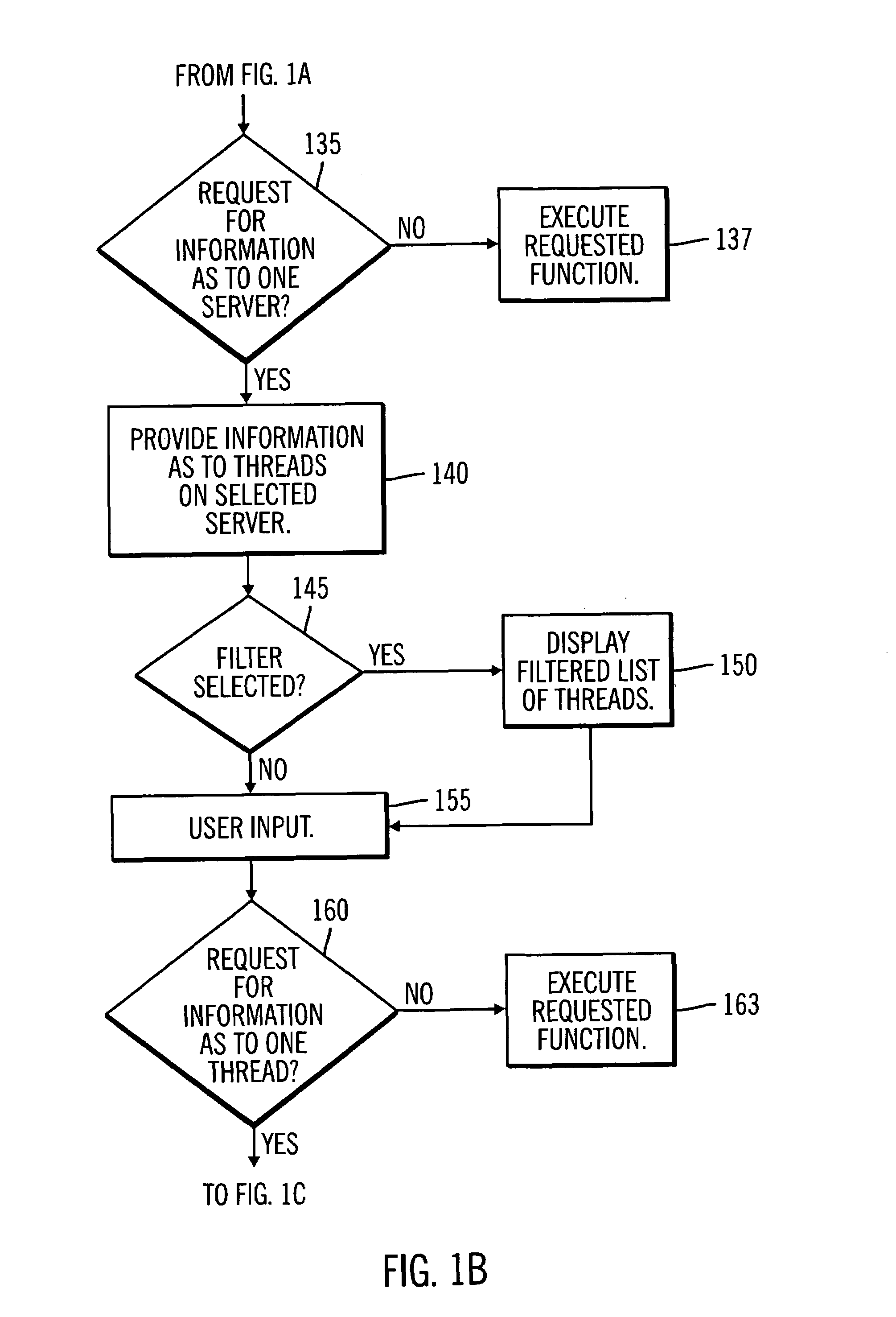
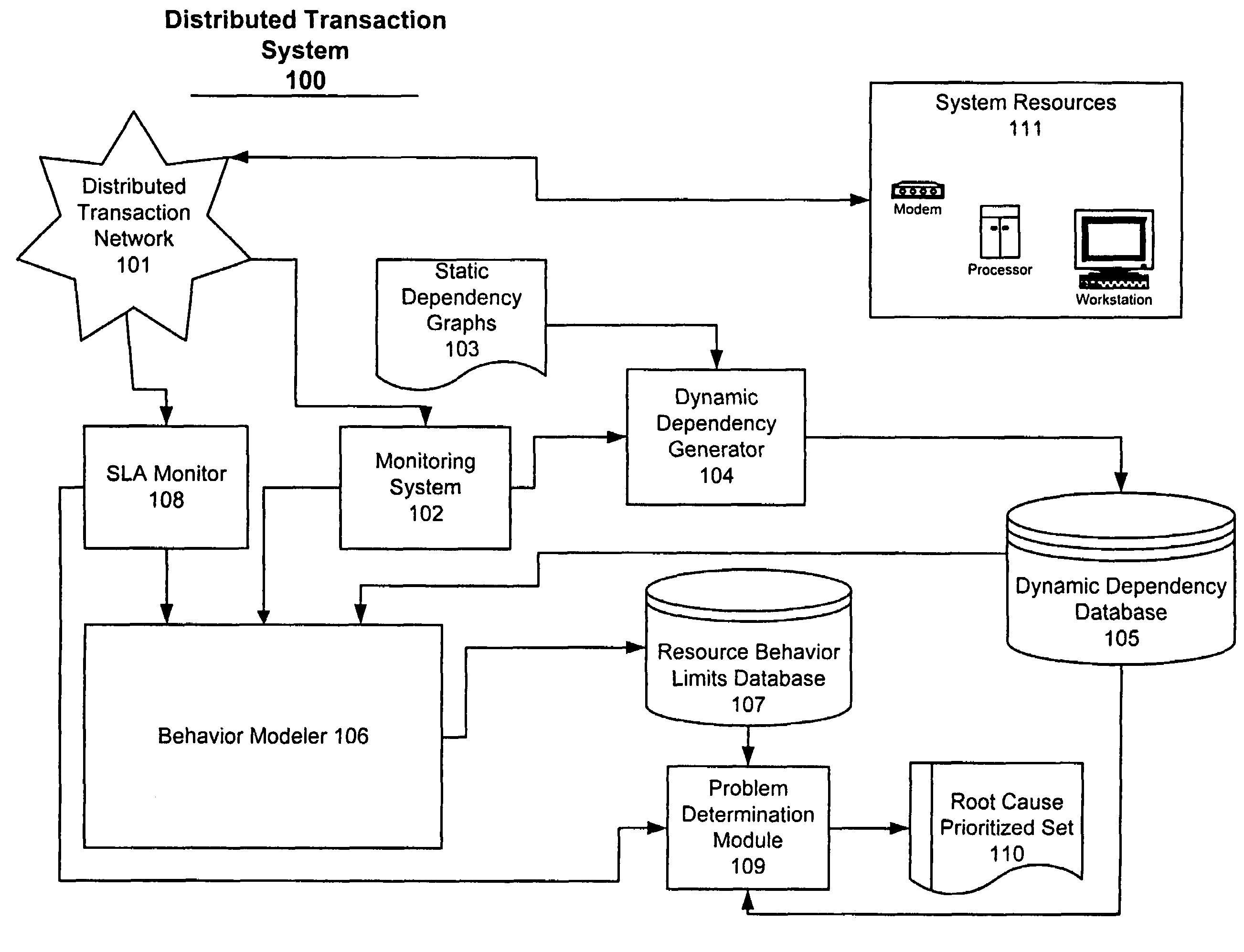
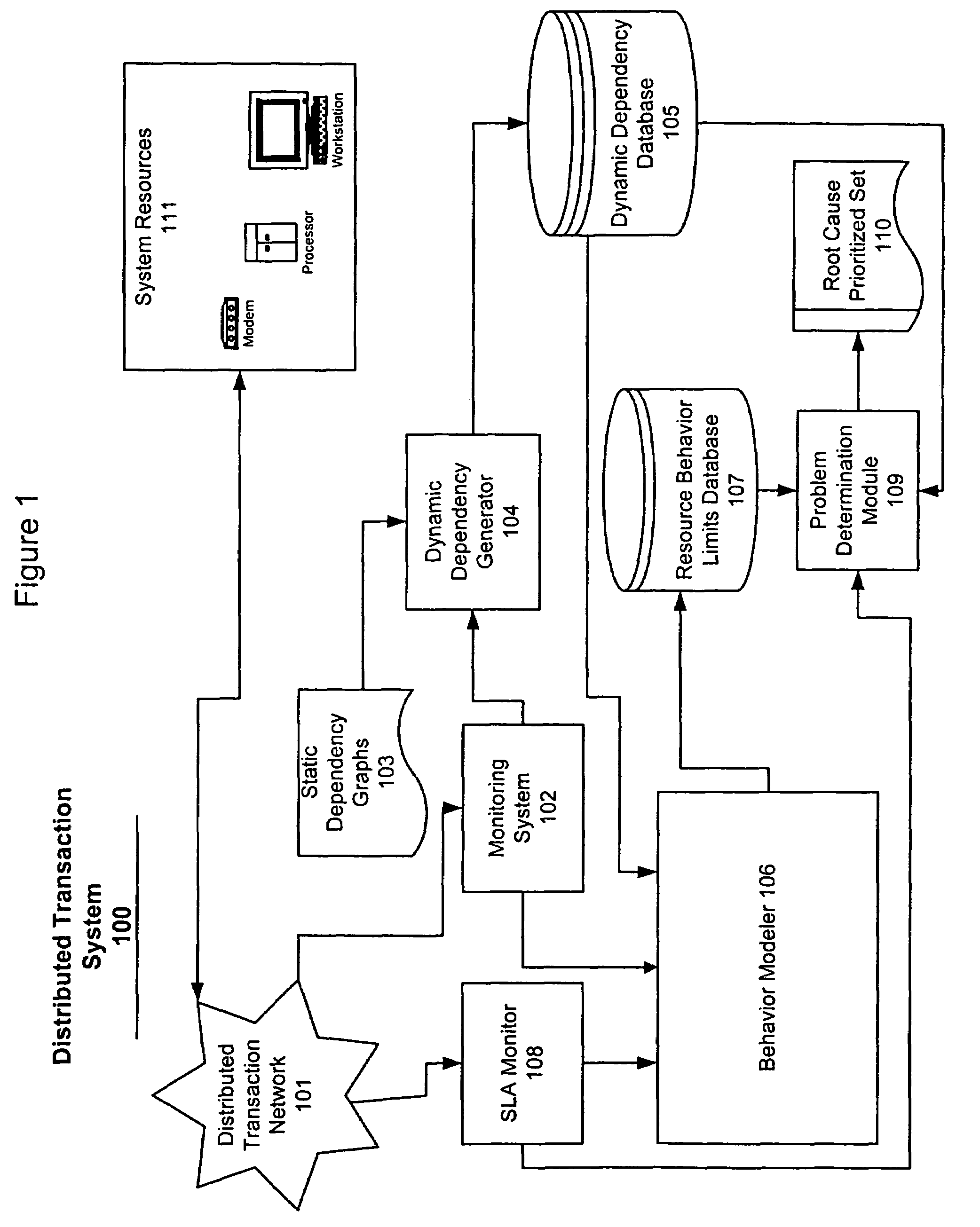
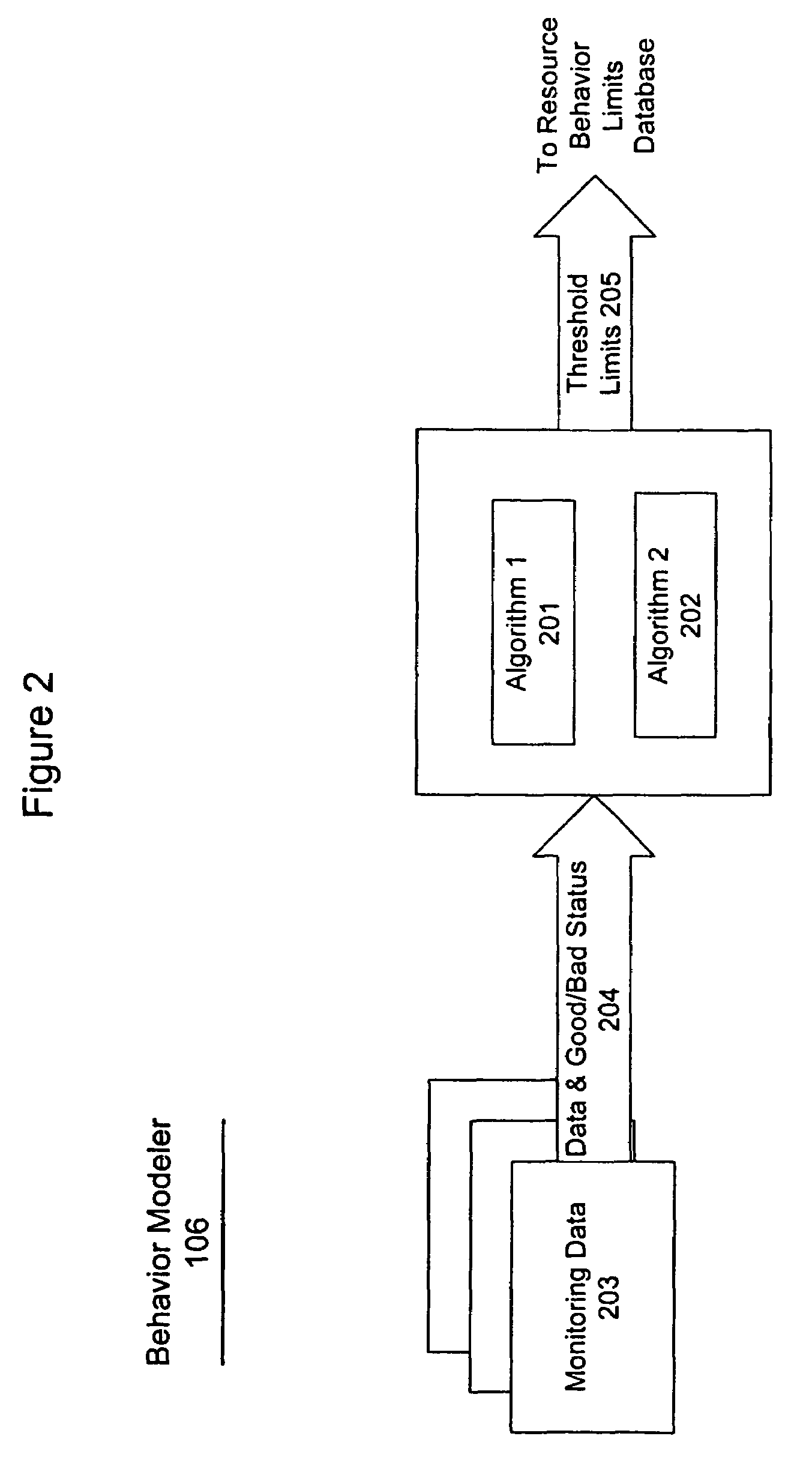
System and method for problem determination using dependency graphs and run-time behavior models
InactiveUS20060101308A1Reduce component countReduce in quantityNon-redundant fault processingMonitoring systemRunning time
A problem determination system and method reduces the time and effort required by system administrators to trouble shot transaction processing difficulties in a large distributed I / T environment by monitoring system component performance and computing operational performance threshold limits based on dependency graphs for the system. Using this data, a prioritized list of suspect components for the I / T system is generated.
Owner:GLOBALFOUNDRIES INC
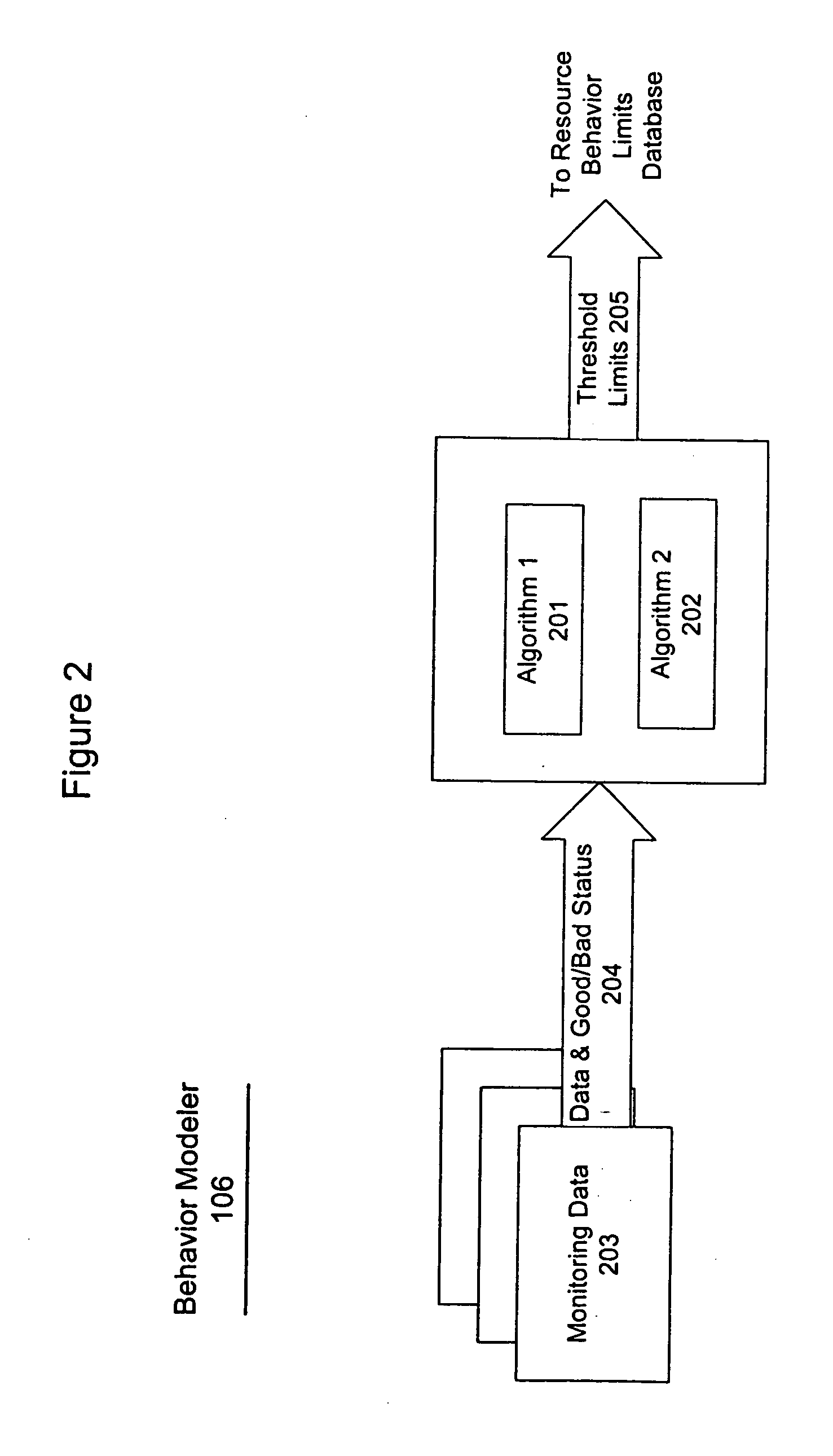
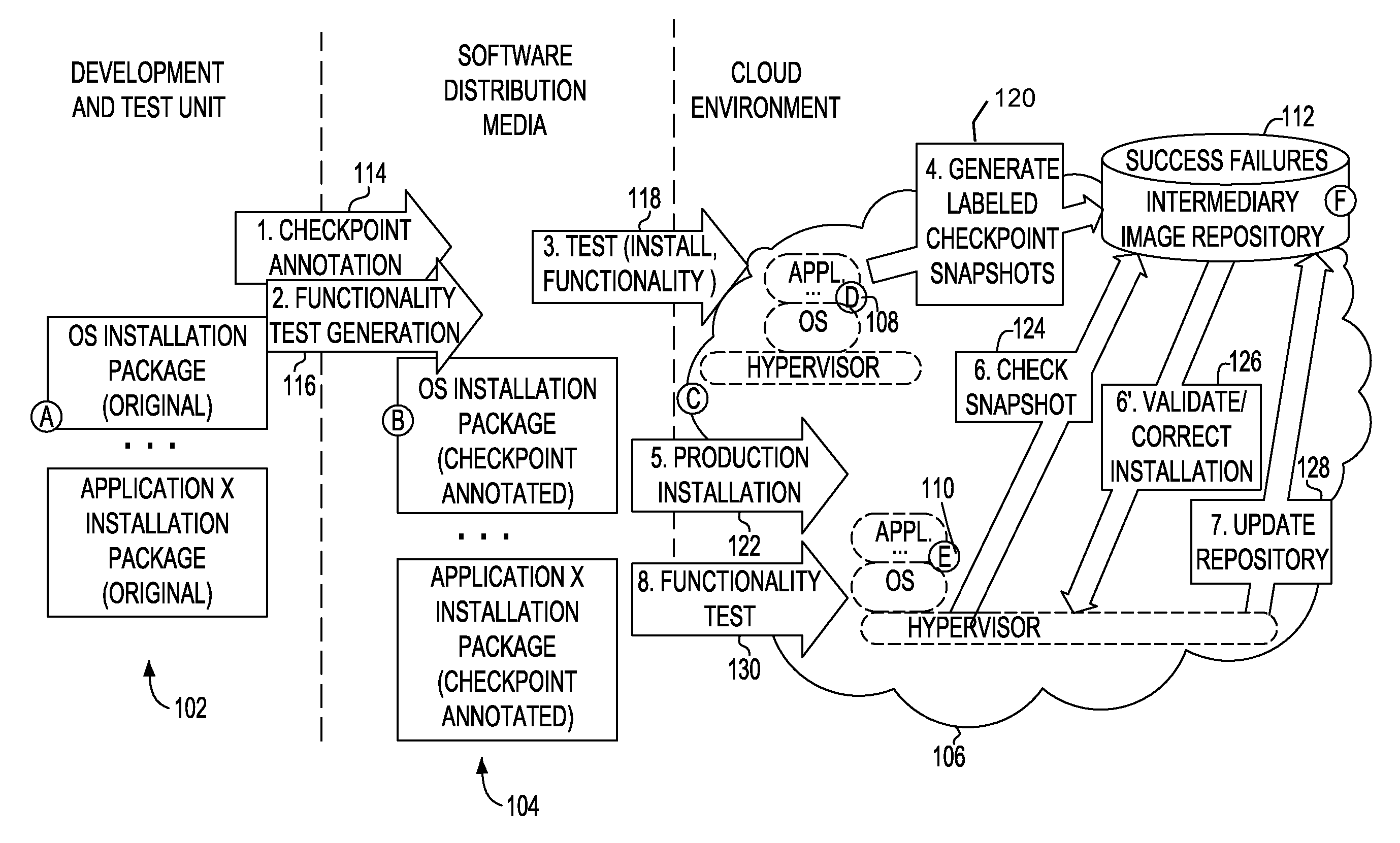
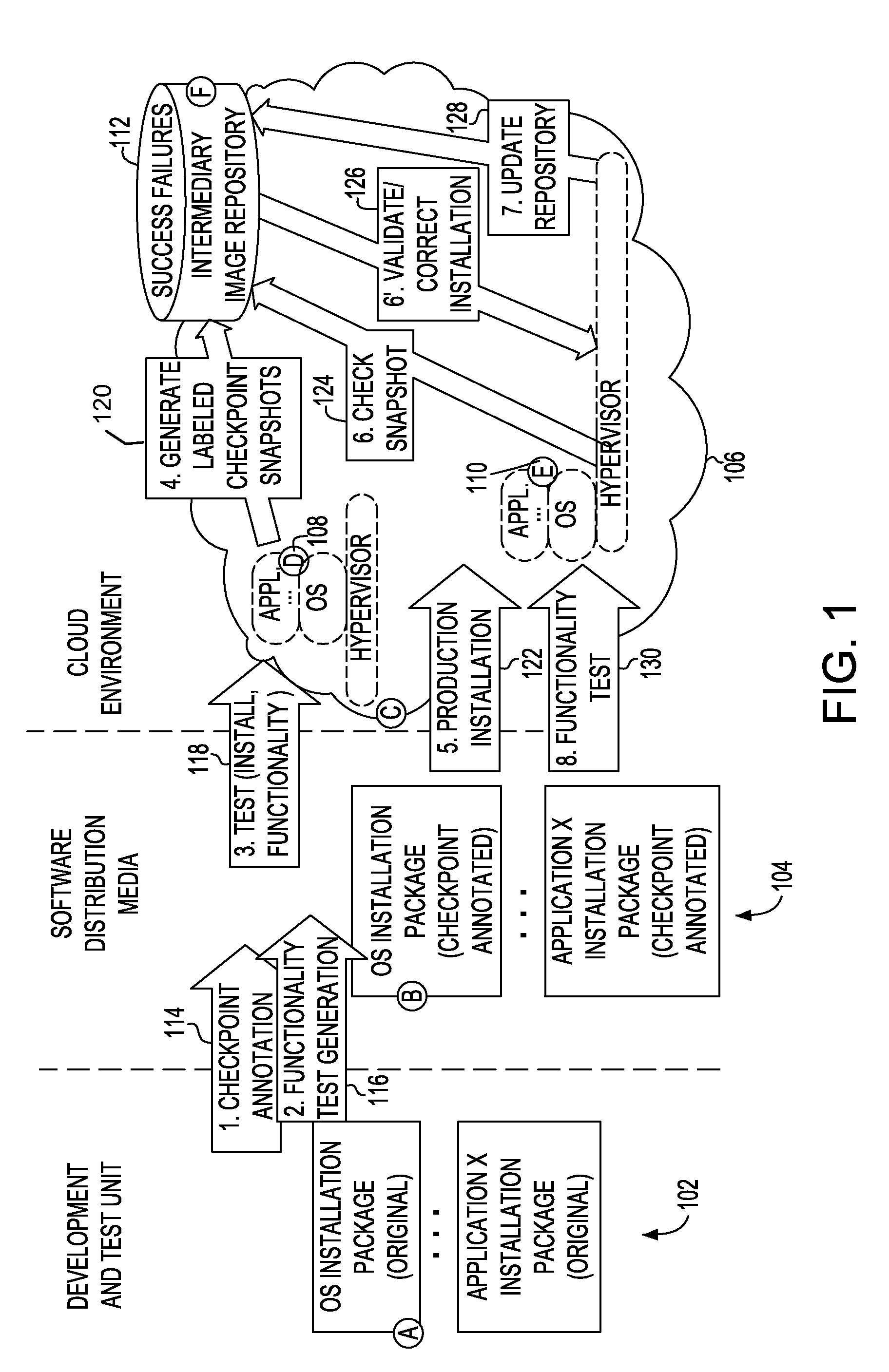
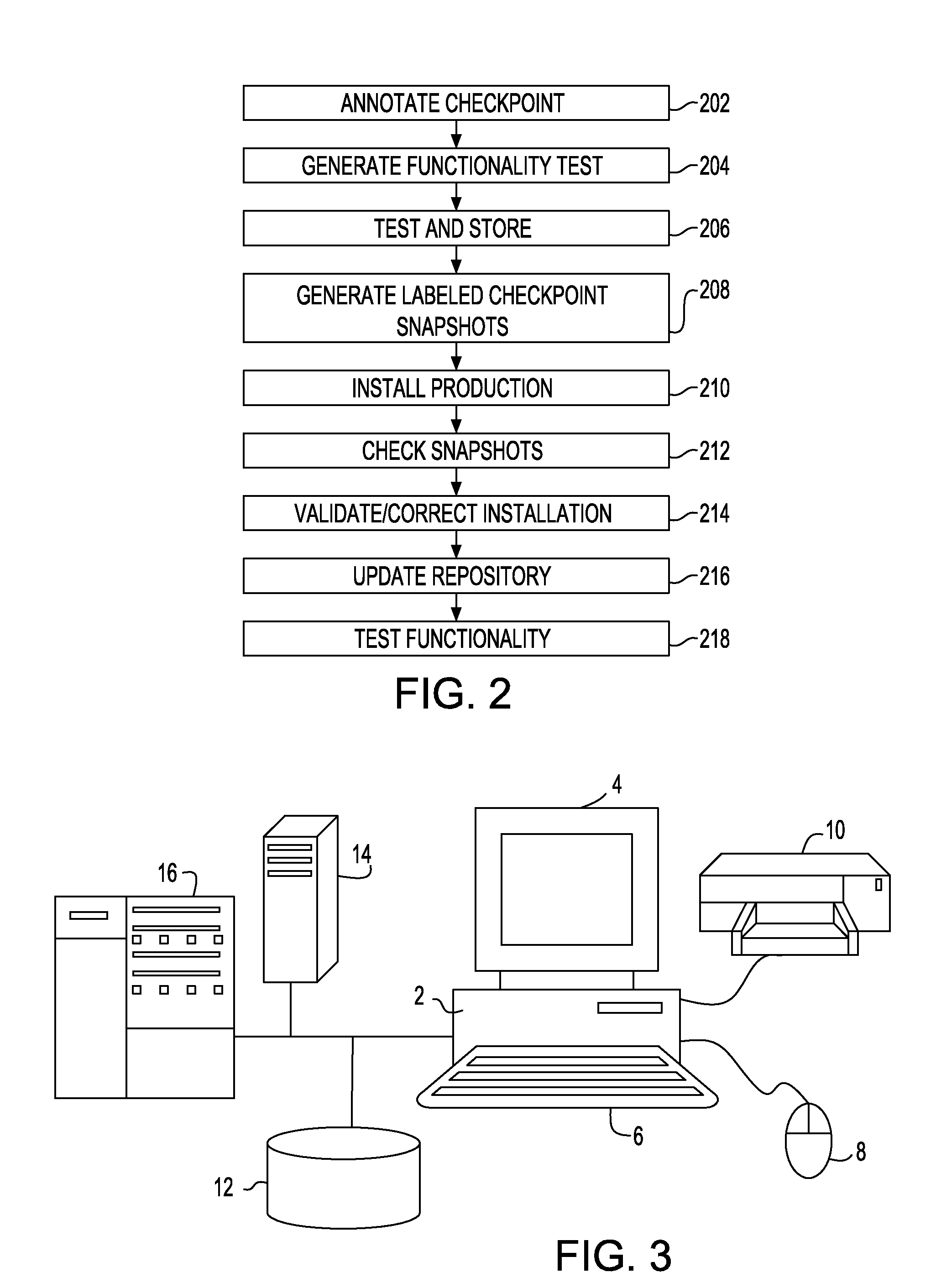
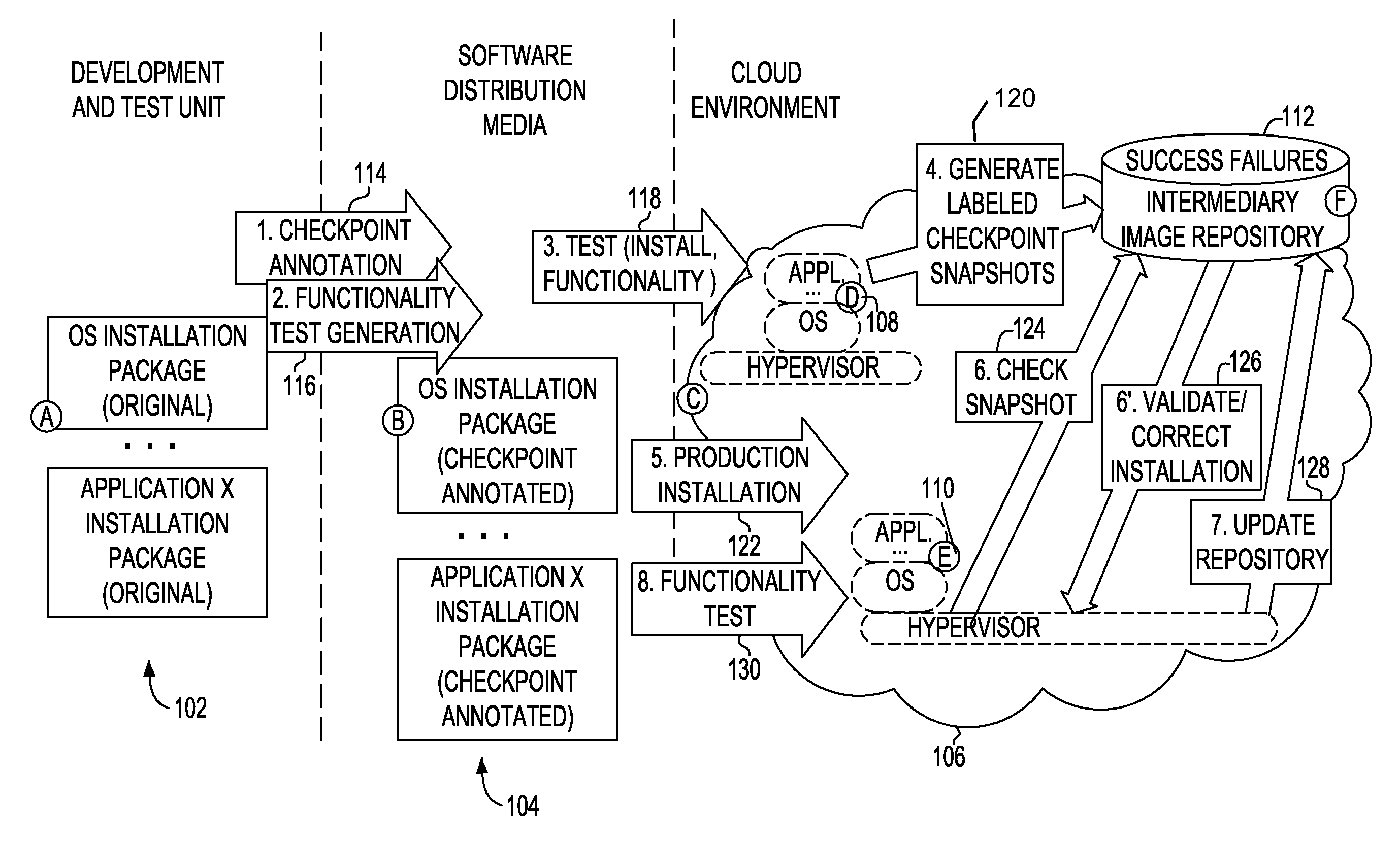
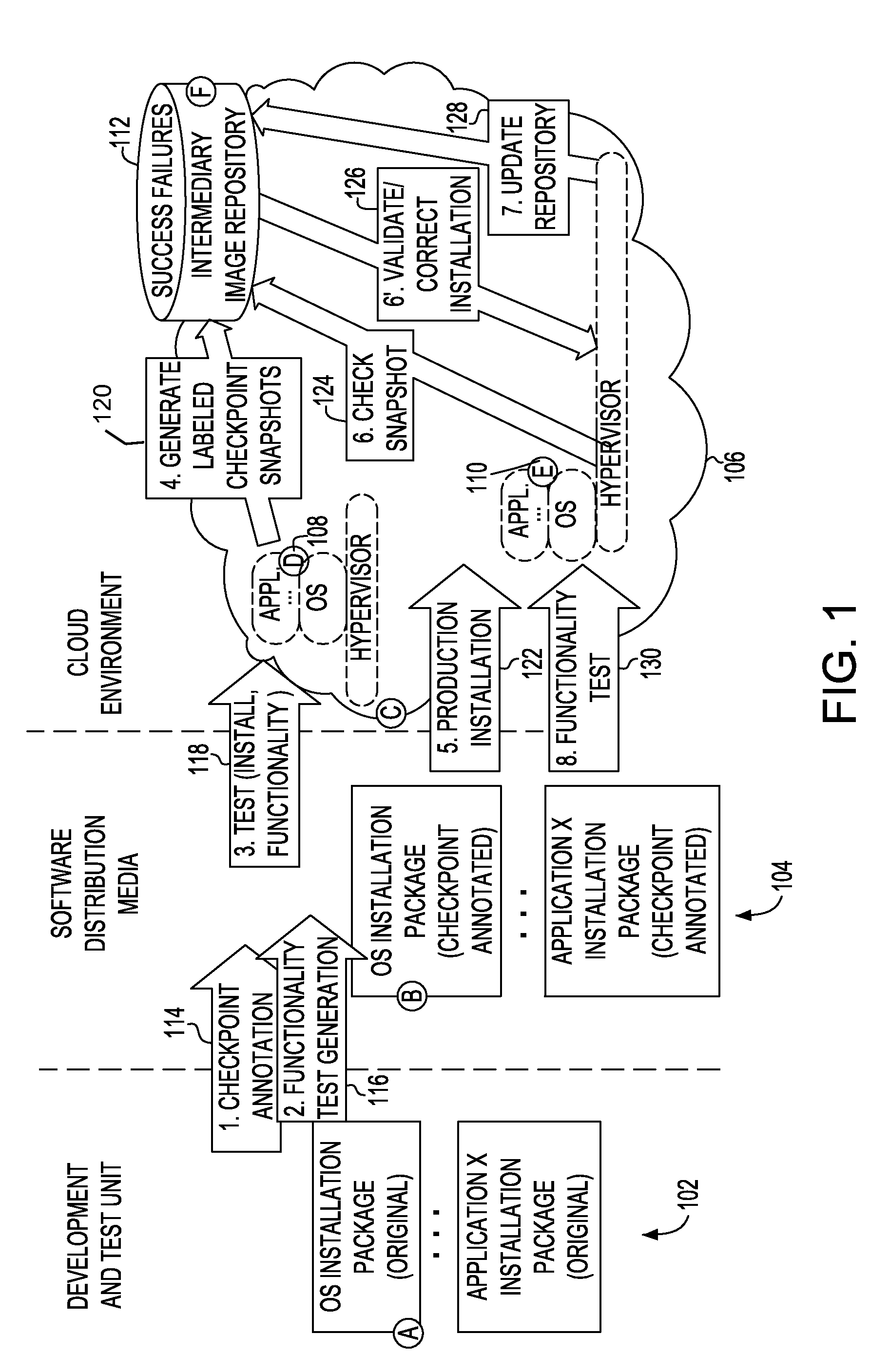
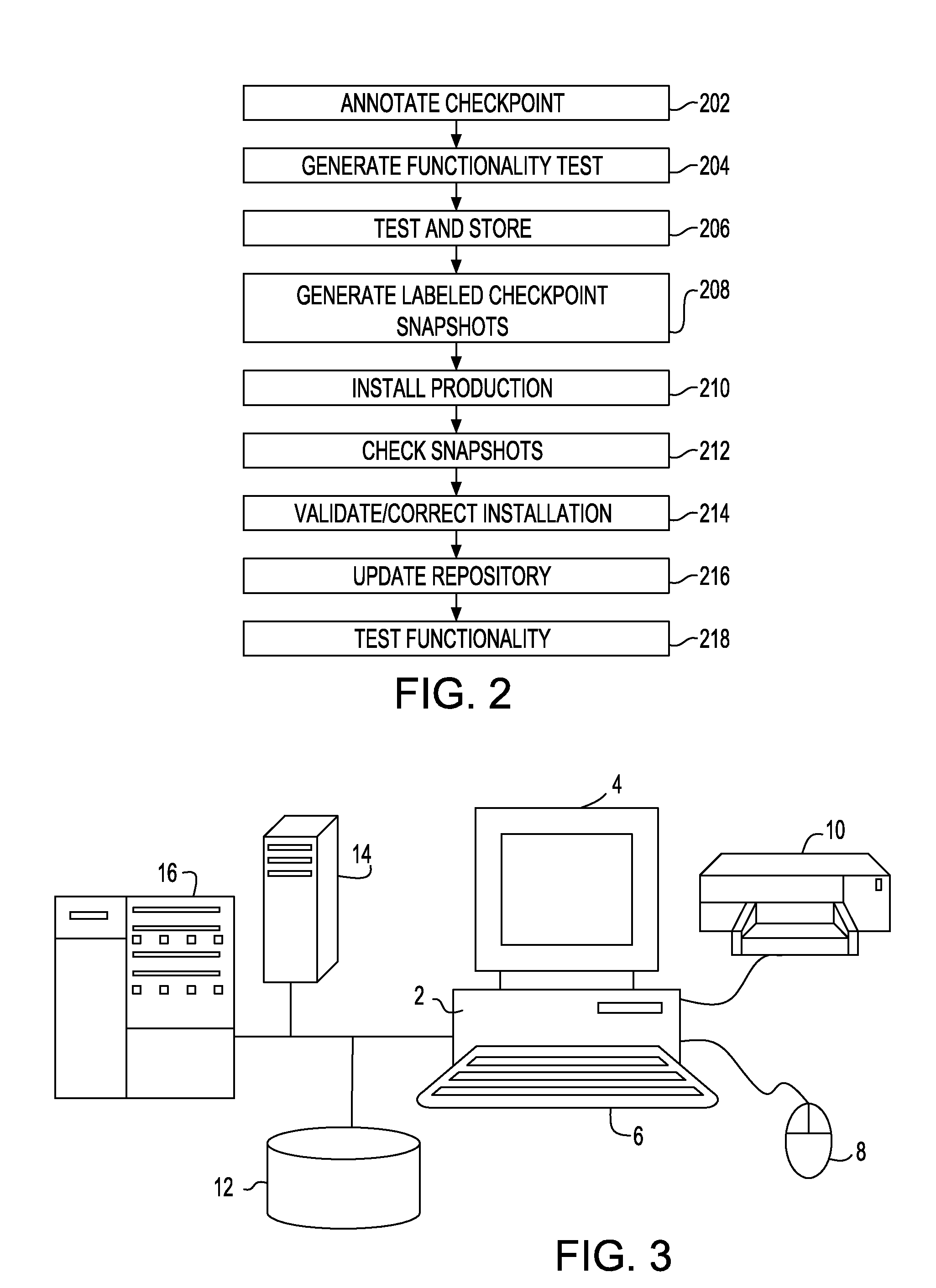
Incremental problem determination and resolution in cloud environments
Installation files are annotated, which annotations may trigger system snapshots to be taken at a plurality of points during the execution of the installation files and / or collected. During a test run, the generated snapshots are examined incrementally to determine whether the installation is success or failure at that point. Checkpoint snapshots are stored, and those indicating failure are recorded with description of the error and / or remediation that suggest how the errors may be resolved or fixed. During a production run, the annotated installation files may be executed and the checkpoint snapshots generated during the production run may be compared with those stored of the test run to incrementally identify and resolve potential problems in the production run.
Owner:IBM CORP
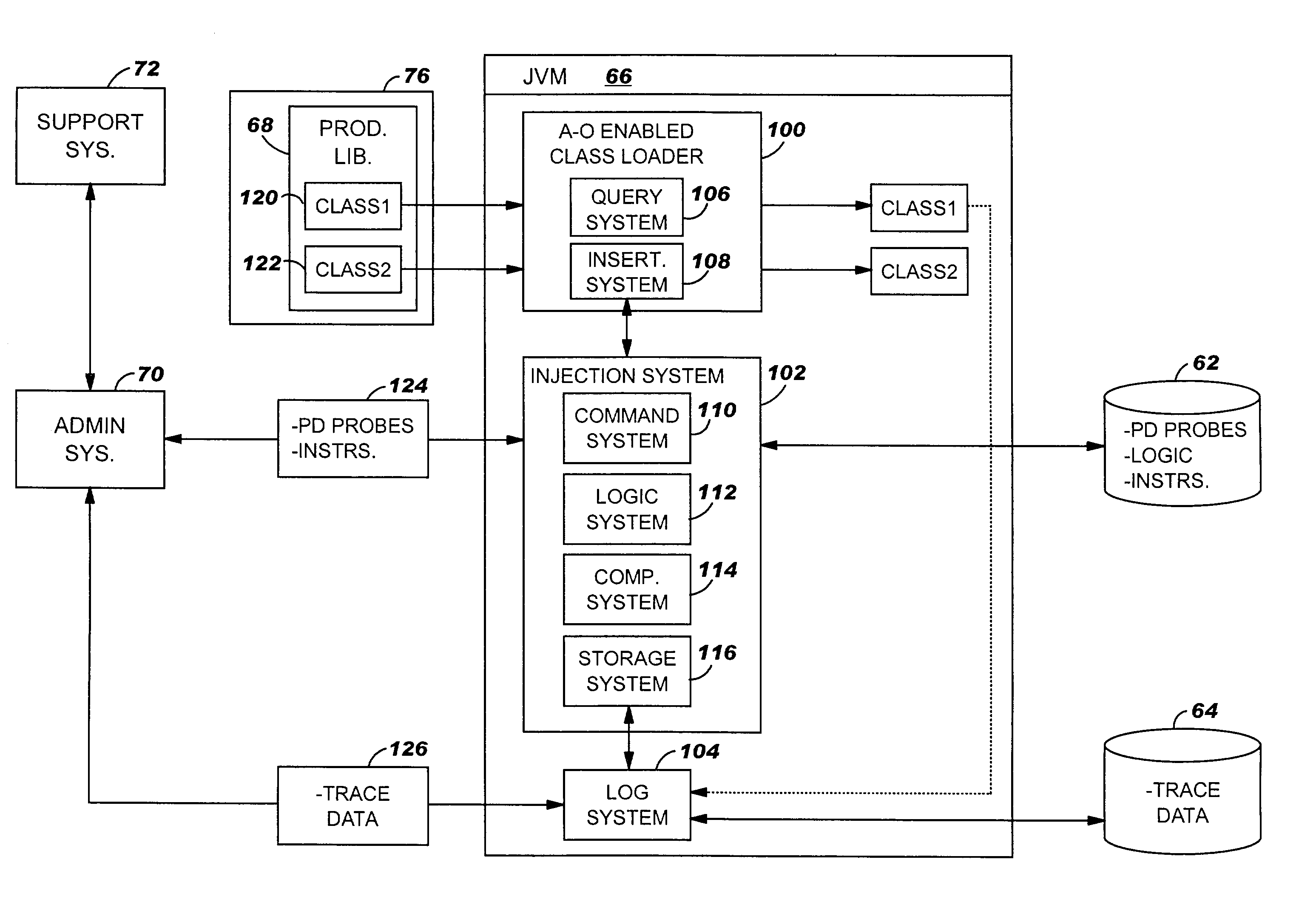
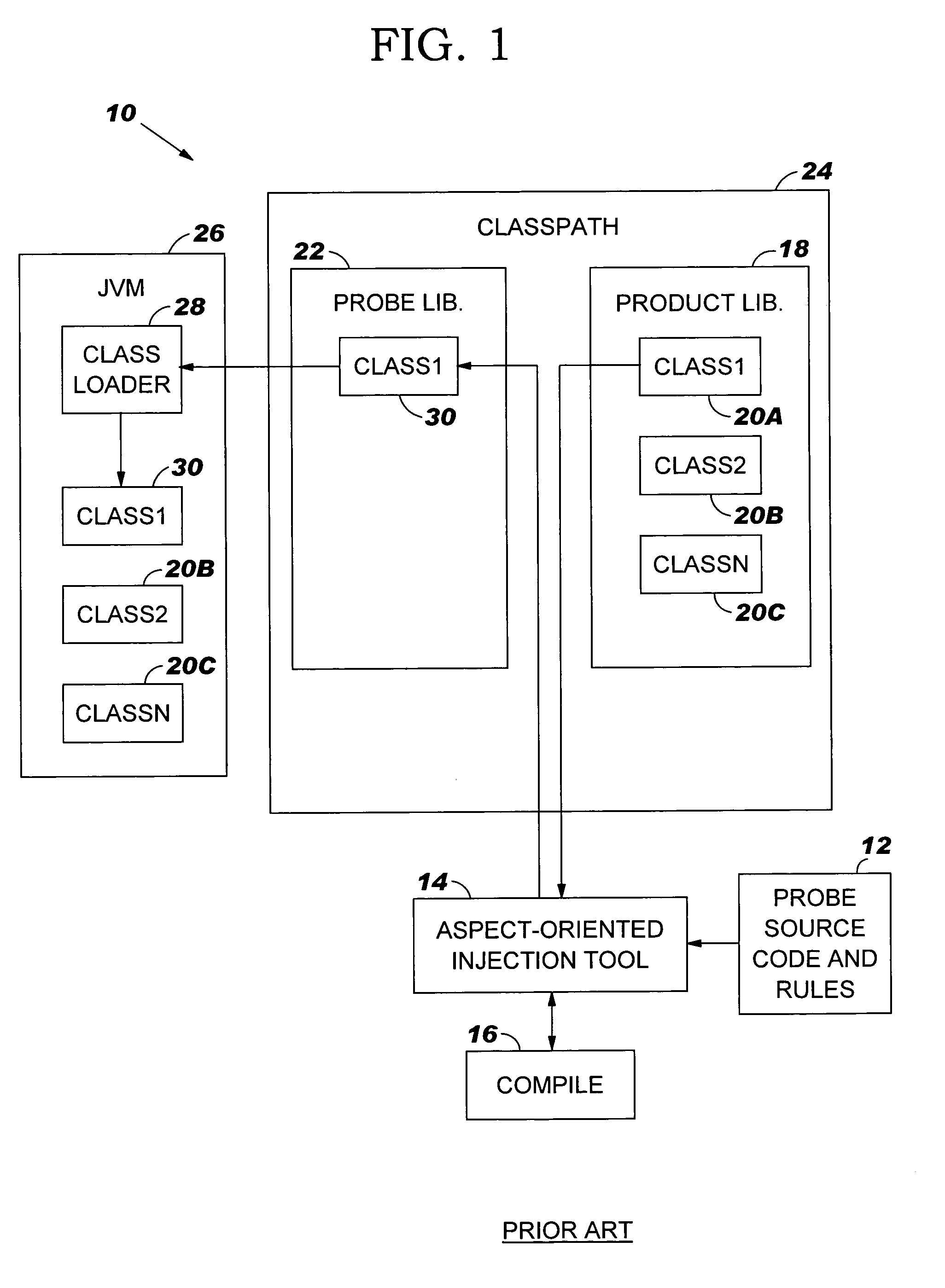
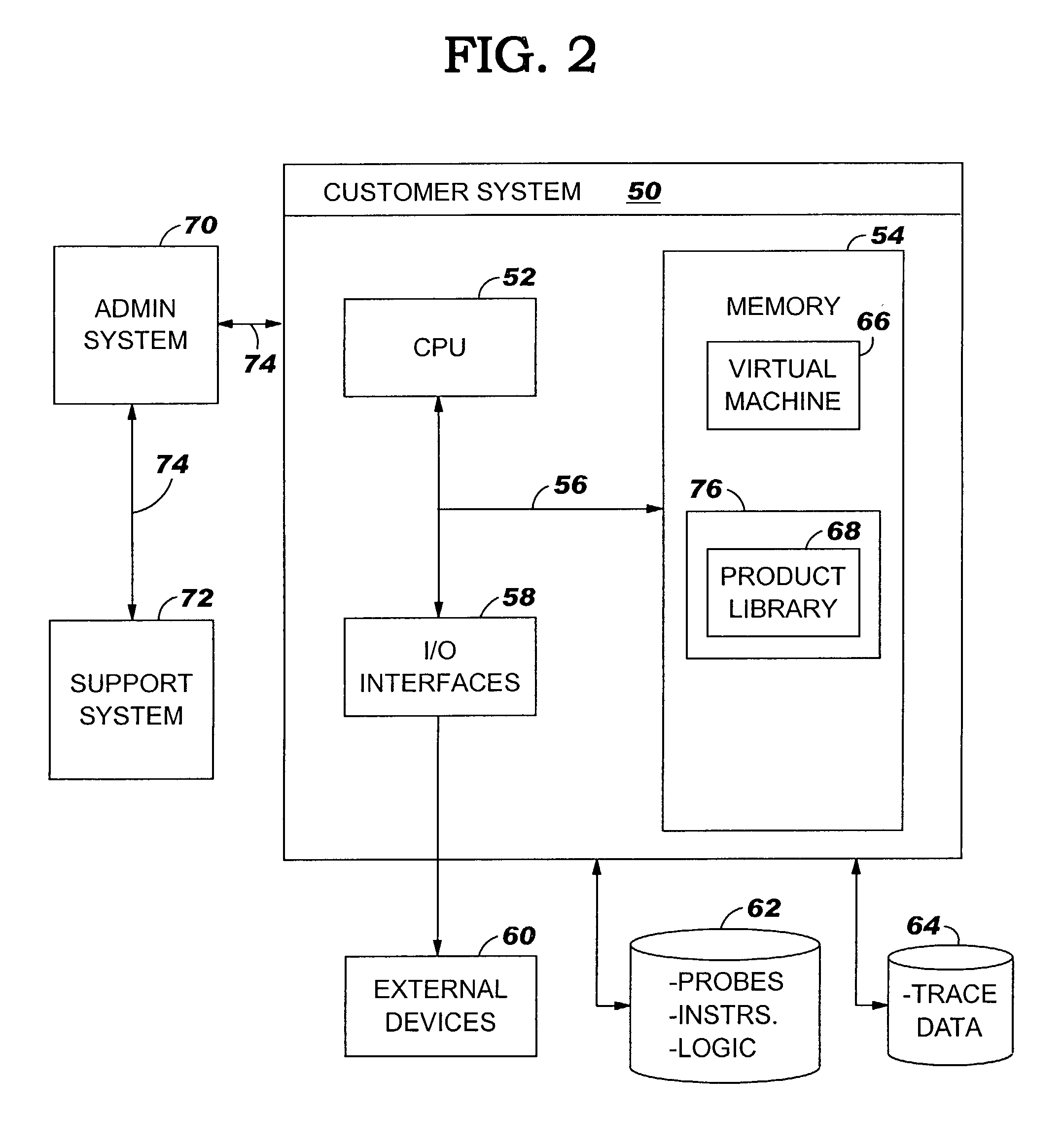
Problem determination method, system and program product
ActiveUS7039644B2Data processing applicationsSoftware testing/debuggingIdentifying problemsComputerized system
A problem determination method, system and program product are provided. Specifically, the present invention identifies problems with software programs by inserting compiled problem determination probes into program classes while the computer system on which the program is loaded is running. Once the probes have been inserted, the classes will be run and trace data will be generated. The trace data can be retrieved and analyzed to identify and address the problem. When the probes are no longer needed, they can be removed while the computer system continues to run.
Owner:IBM CORP
Method for problem determination in distributed enterprise applications
InactiveUS7383332B2Error detection/correctionMultiple digital computer combinationsDistributed enterpriseWorld Wide Web
Owner:INT BUSINESS MASCH CORP
System and method for problem determination using dependency graphs and run-time behavior models
InactiveUS7437611B2Reduce component countReduce in quantityNon-redundant fault processingMonitoring systemRunning time
A problem determination system and method reduces the time and effort required by system administrators to trouble shot transaction processing difficulties in a large distributed I / T environment by monitoring system component performance and computing operational performance threshold limits based on dependency graphs for the system. Using this data, a prioritized list of suspect components for the I / T system is generated.
Owner:GLOBALFOUNDRIES INC
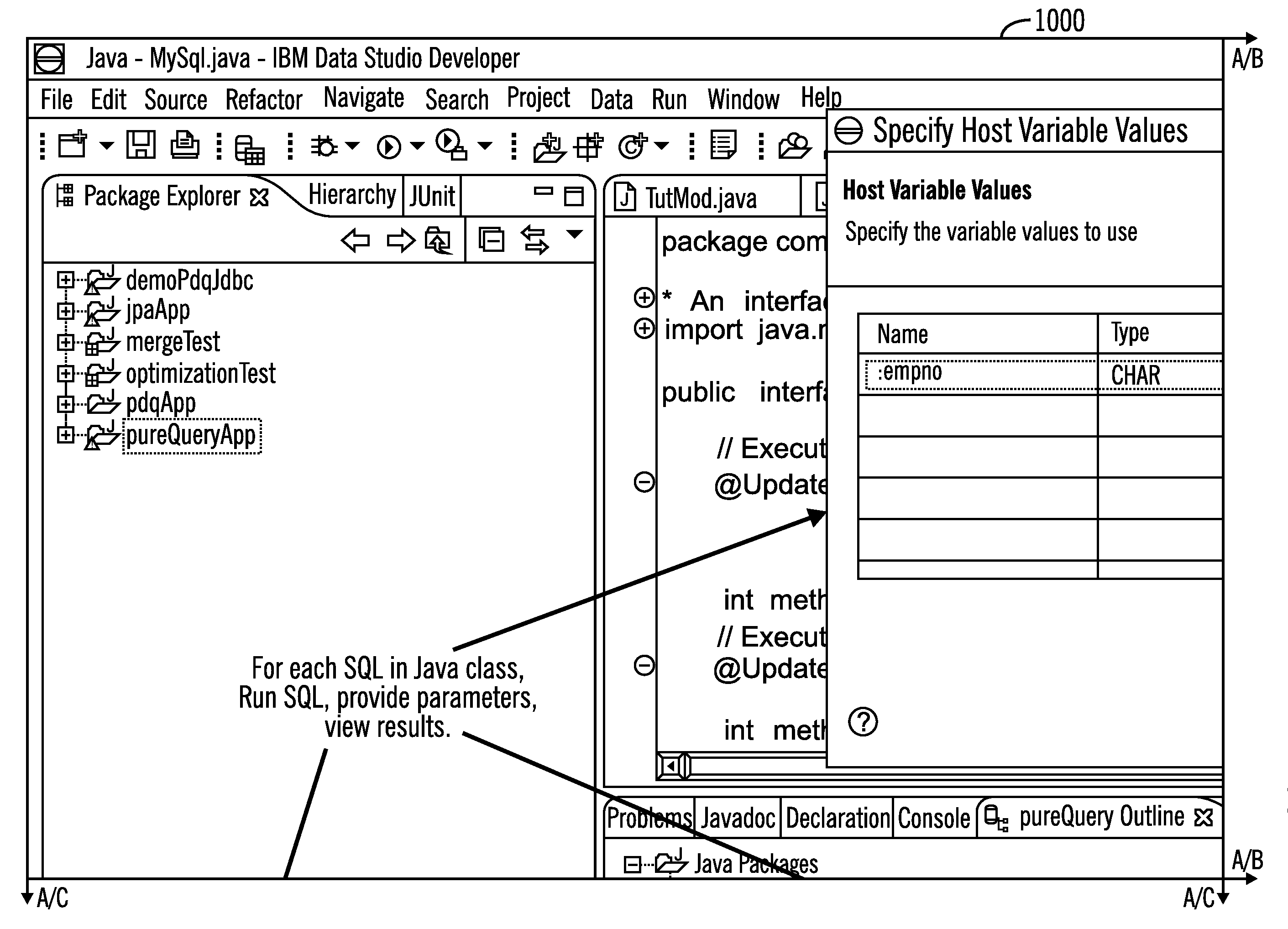
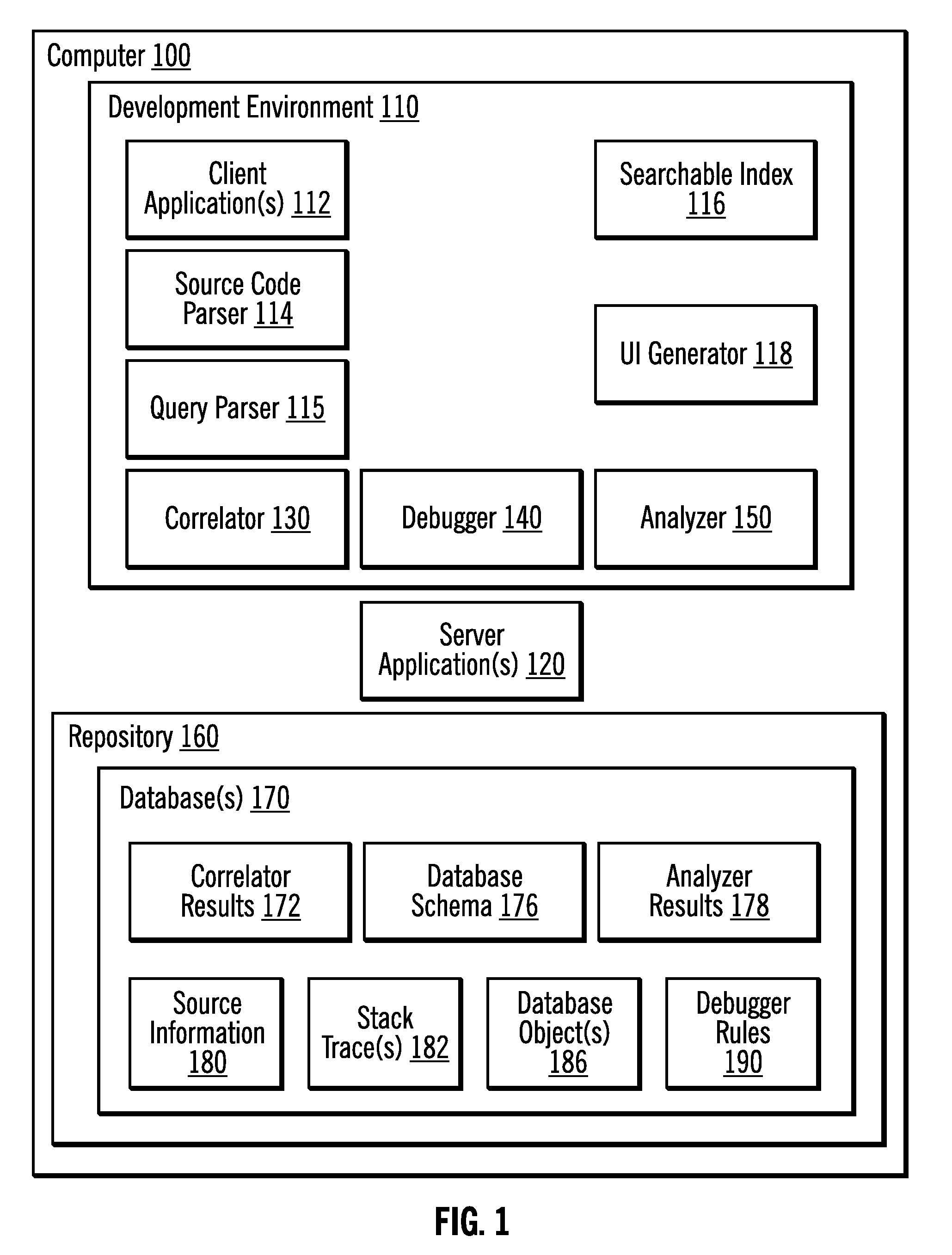
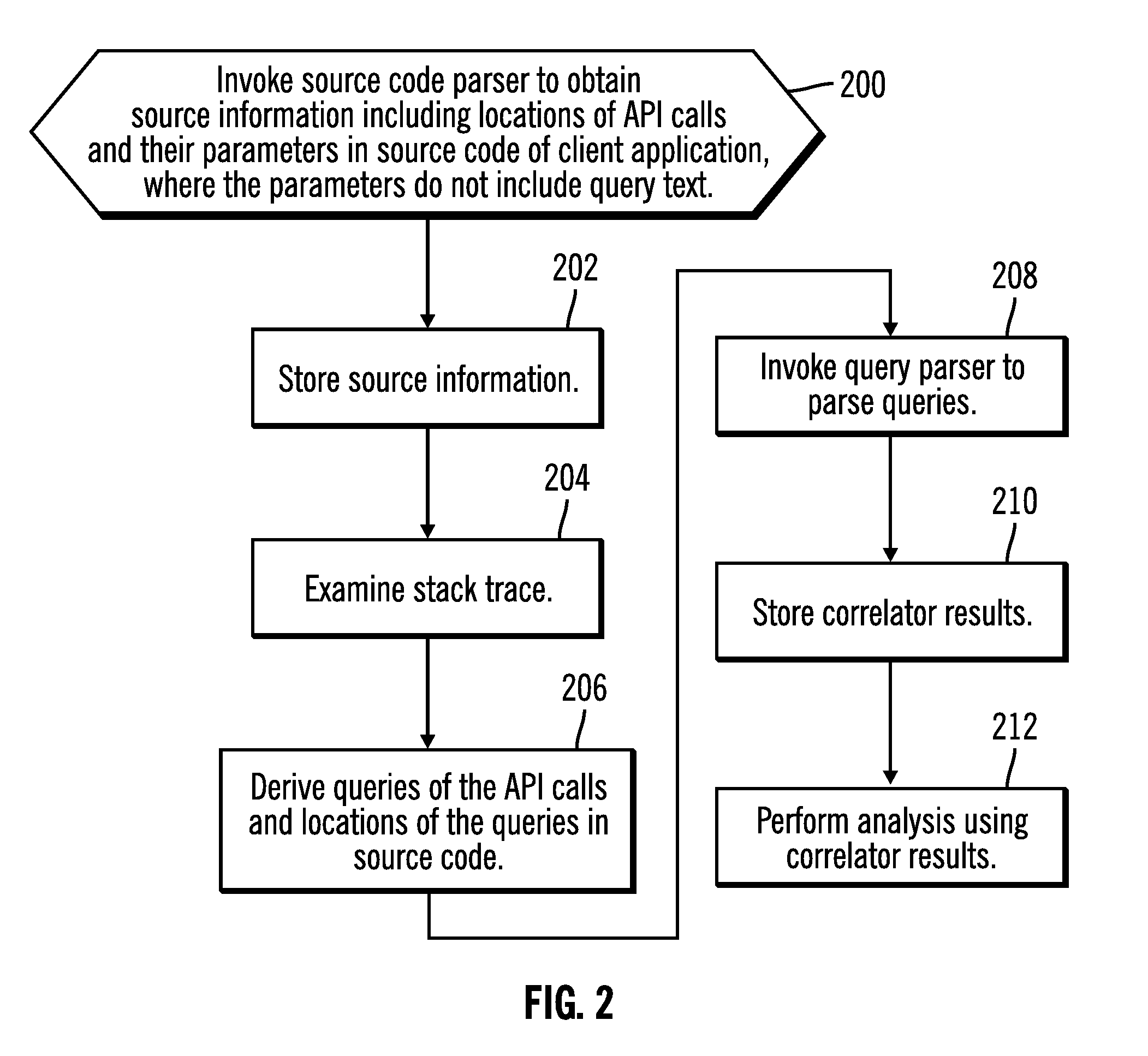
Correlating queries issued by applications with their source lines and analyzing applications for problem determination and where used analysis
InactiveUS20100332473A1Easy to doDigital data processing detailsError detection/correctionApplication programming interfaceClient-side
Provided are techniques for invoking with a processor executing on a computer a source code parser to obtain source information that includes a first location of an Application Programming Interface (API) call and parameters of the API call in source code of a client application, where the parameters the API call do not include query text for a query that is to be used to access a database; examining a stack trace to determine a second location of the API call in the stack trace; and deriving the query of the API call and a third location of the query in the source code by identifying the query in the stack trace at the location of the API call in the stack trace.
Owner:IBM CORP
Incremental problem determination and resolution in cloud environments
Installation files are annotated, which annotations may trigger system snapshots to be taken at a plurality of points during the execution of the installation files and / or collected. During a test run, the generated snapshots are examined incrementally to determine whether the installation is success or failure at that point. Checkpoint snapshots are stored, and those indicating failure are recorded with description of the error and / or remediation that suggest how the errors may be resolved or fixed. During a production run, the annotated installation files may be executed and the checkpoint snapshots generated during the production run may be compared with those stored of the test run to incrementally identify and resolve potential problems in the production run.
Owner:IBM CORP
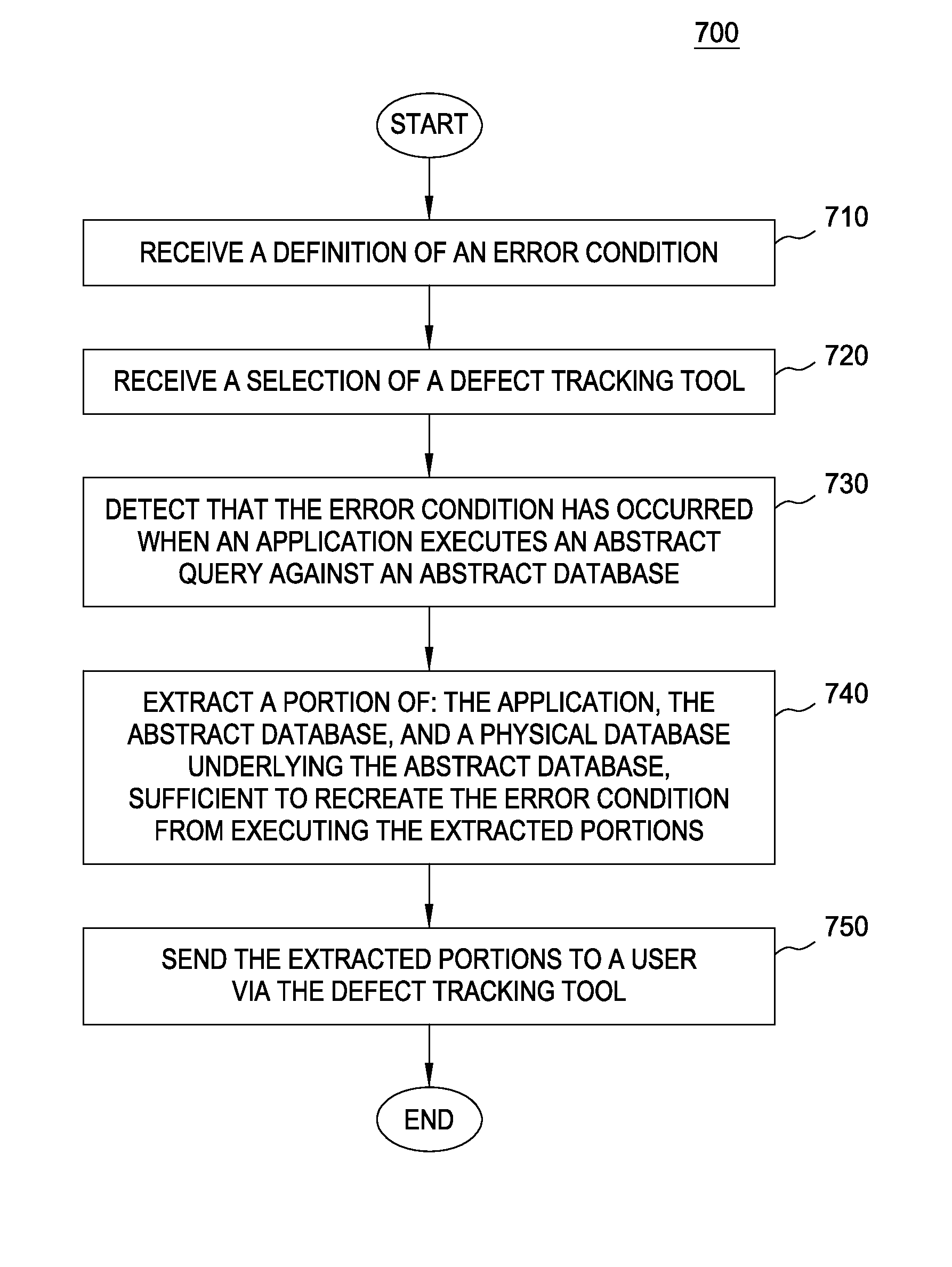
Extracting portions of an abstract database for problem determination
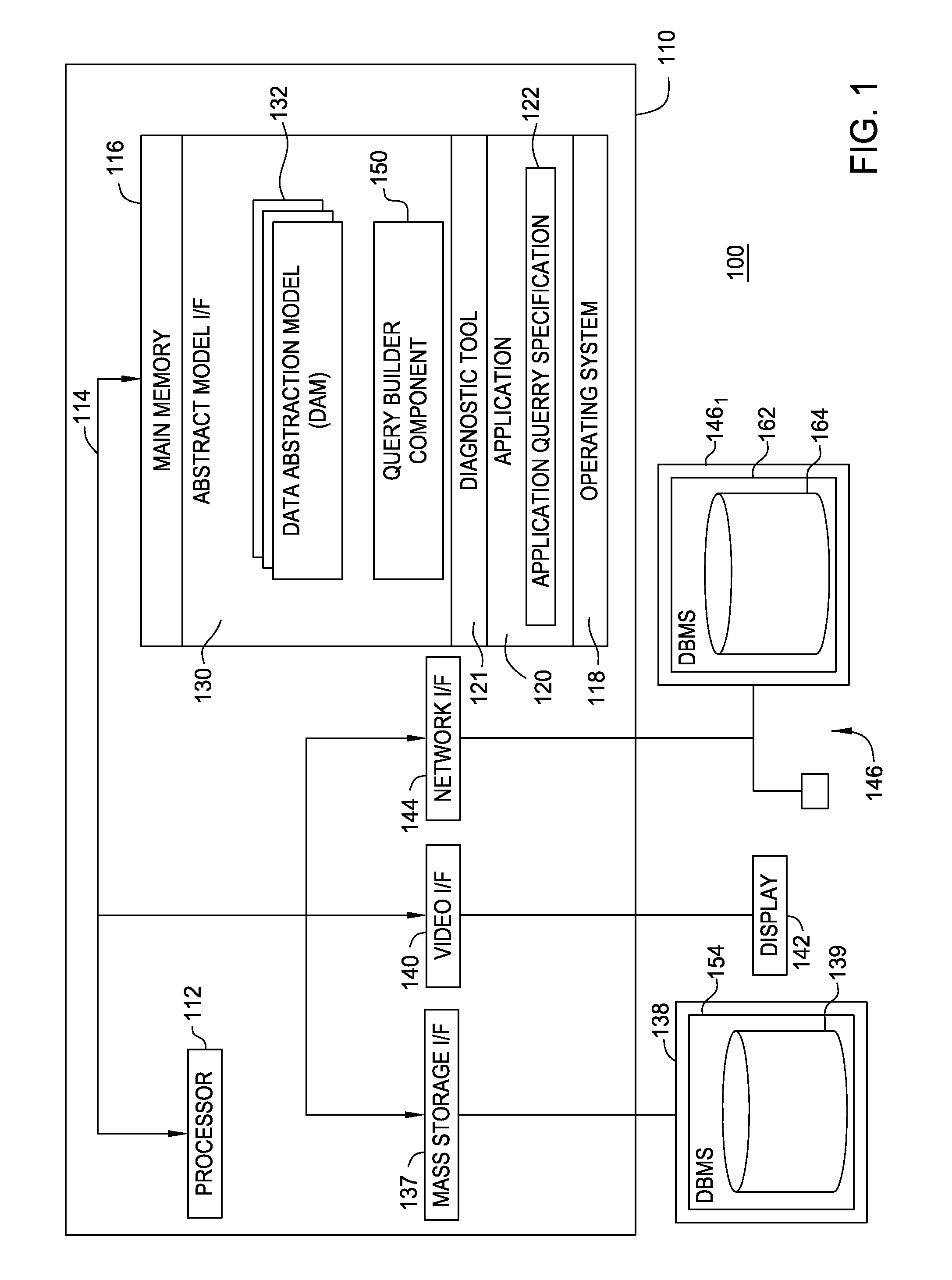
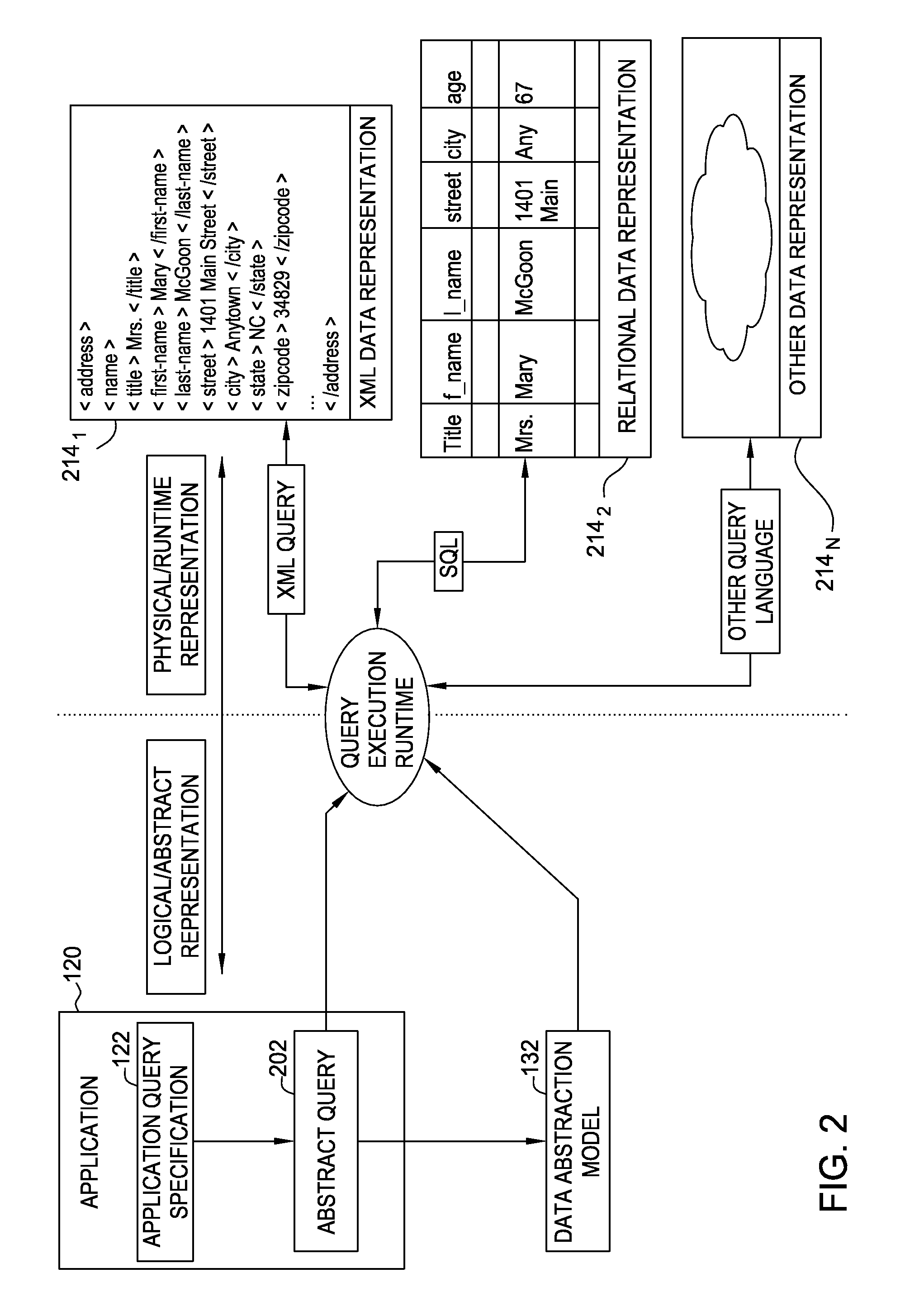
InactiveUS8738607B2Digital data processing detailsRelational databasesData miningProblem determination
Systems, methods and articles of manufacture are disclosed for extracting portions of an abstract database for problem determination. An error may be detected when an application executes an abstract query against the abstract database. A portion of the abstract database may be extracted for problem determination. A defect entry may be created in a defect tracking tool, to store the extracted portion. One or more administrative users may be notified of the defect entry.
Owner:INT BUSINESS MASCH CORP
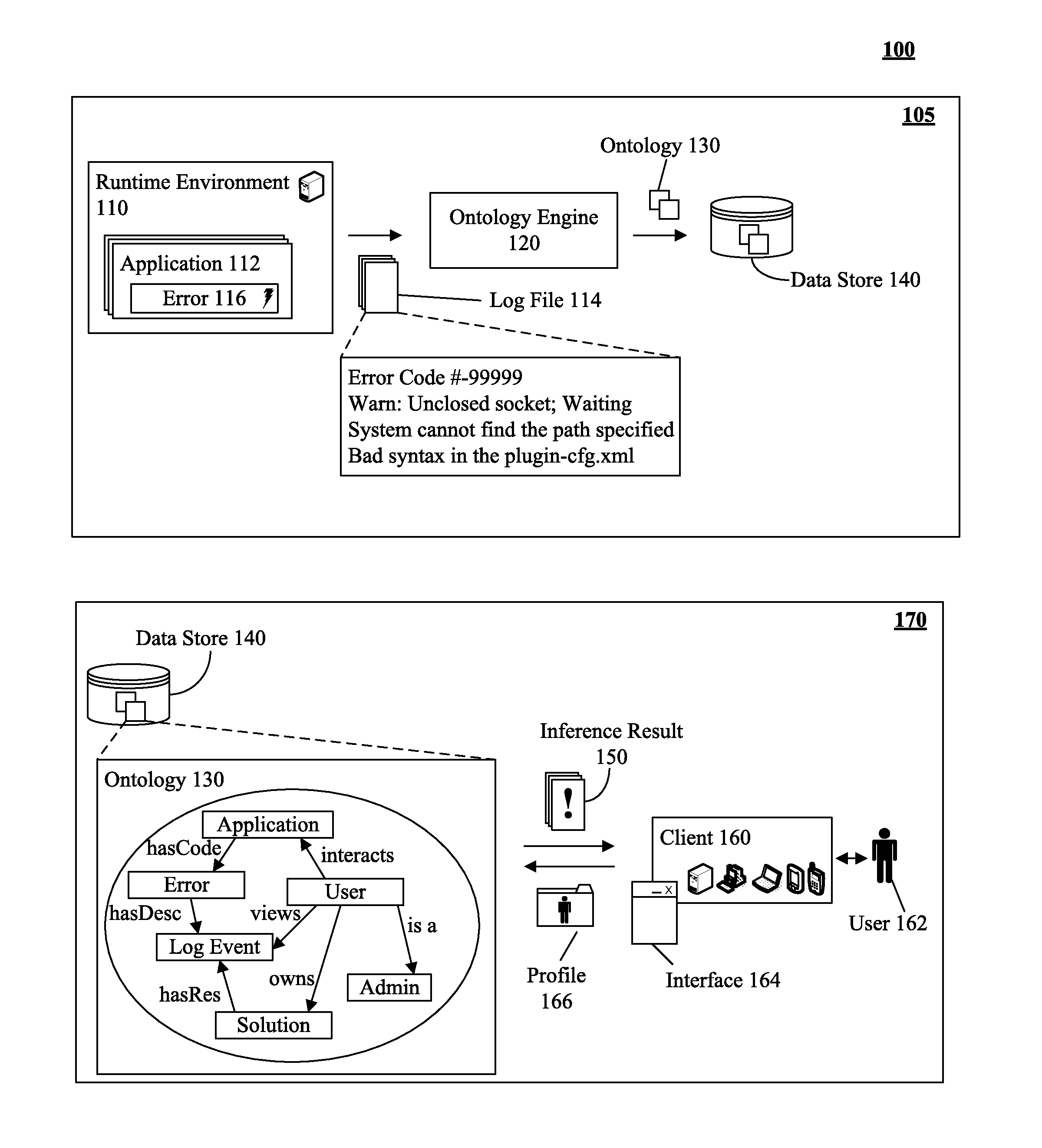
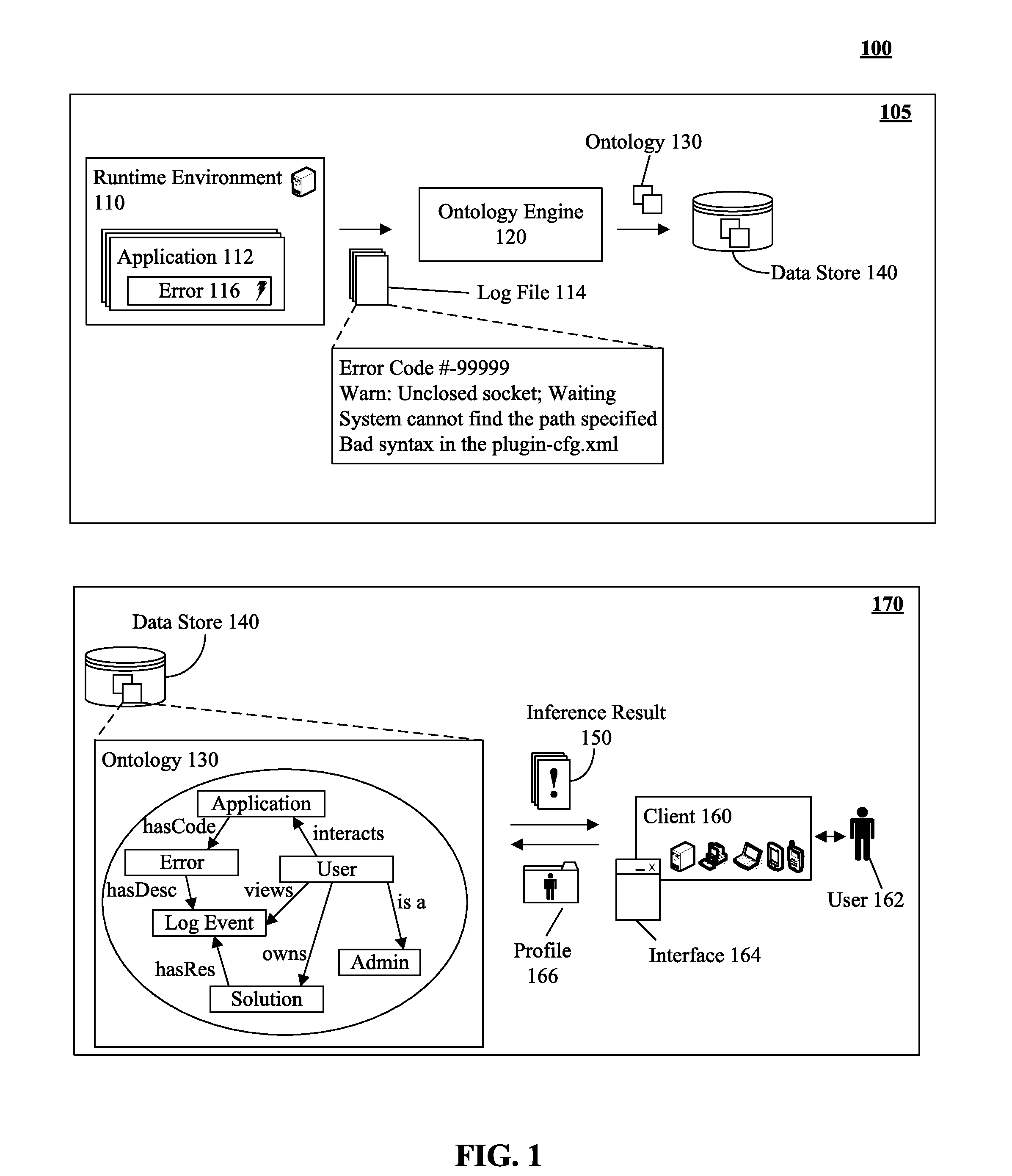
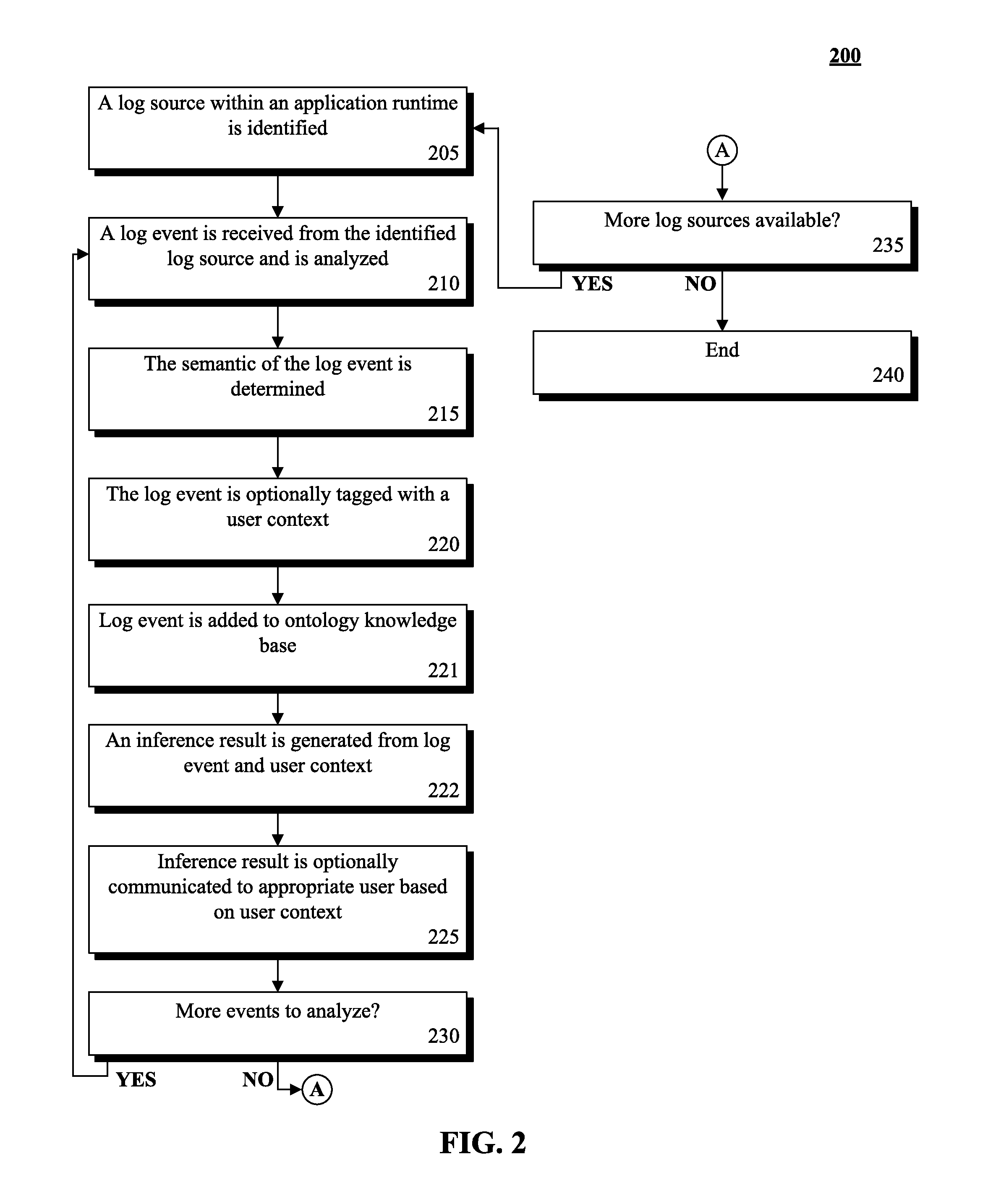
Utilizing log event ontology to deliver user role specific solutions for problem determination
ActiveUS20120036397A1Hardware monitoringSpecial data processing applicationsApplication serverApplication software
A log event can be received from a log source within an application server environment. The log event can be an error message which is associated with a log level. In one embodiment, the application server environment can be a JAVA 2 ENTERPRISE EDITION runtime environment. The log event can be analyzed to determine the ontology of the log event which can comprise of the log event, the user context, and the relationship of the log event to the user context. The log event can be associated with the user context as determined by the relationship of the log event.
Owner:IBM CORP
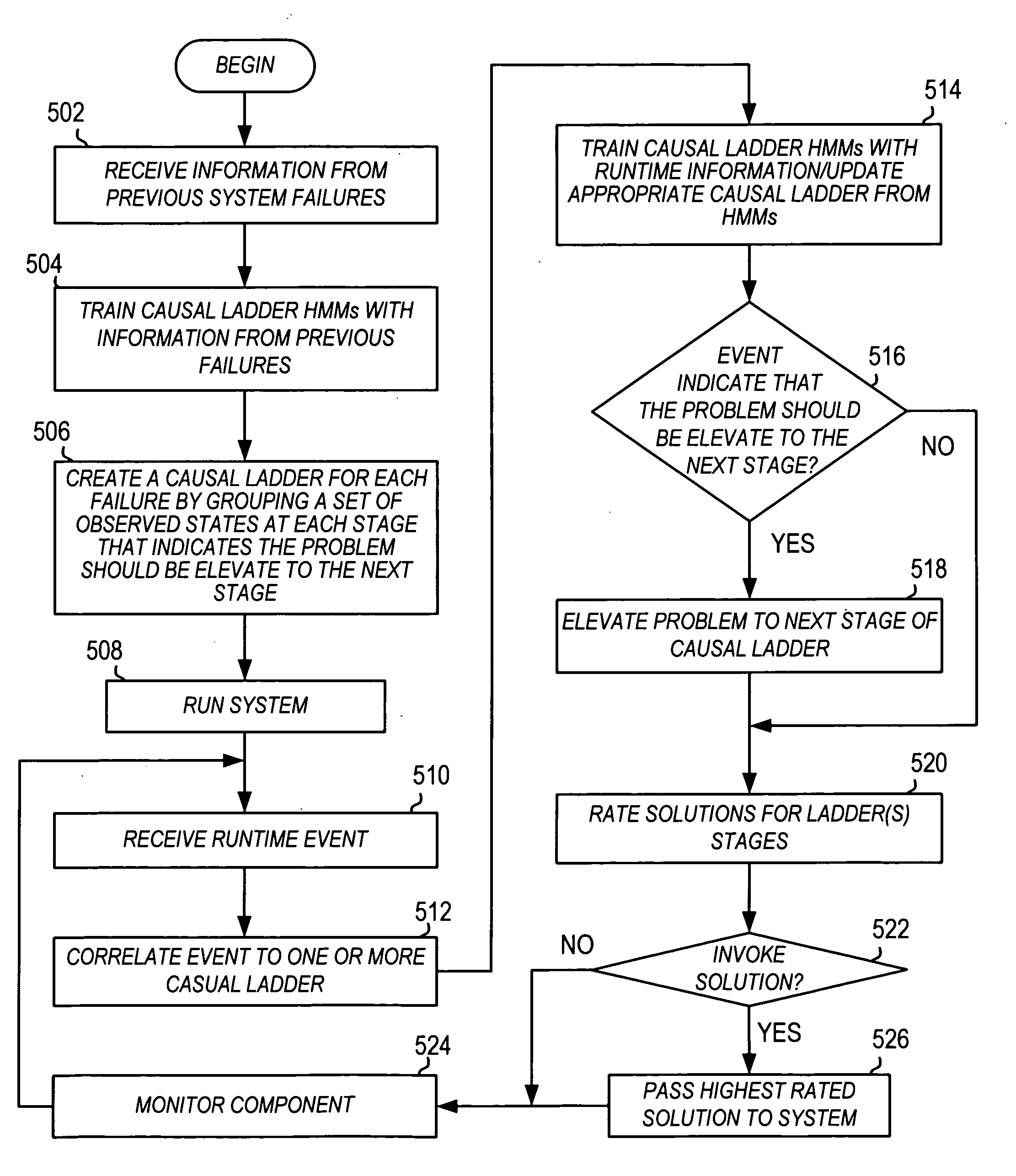
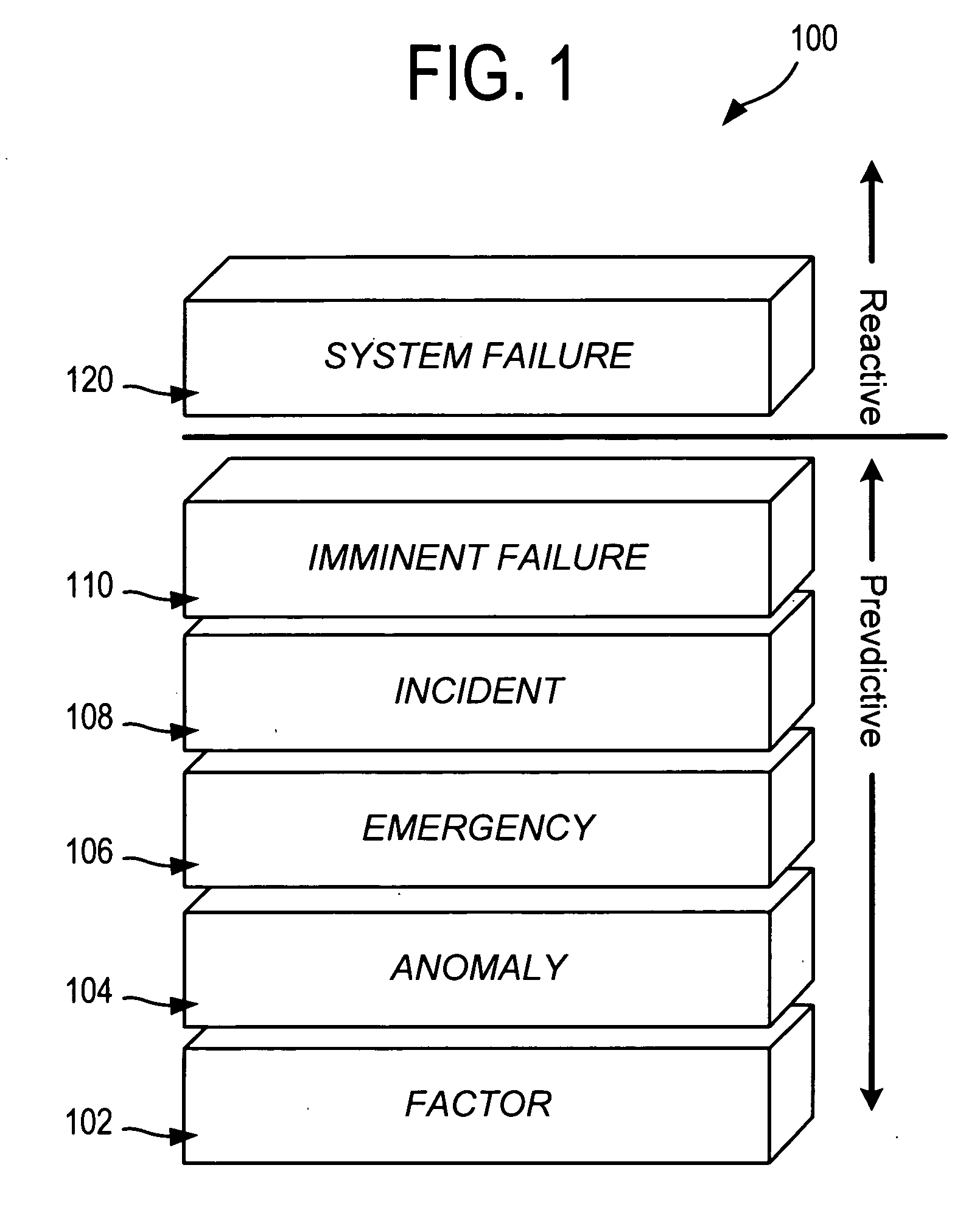
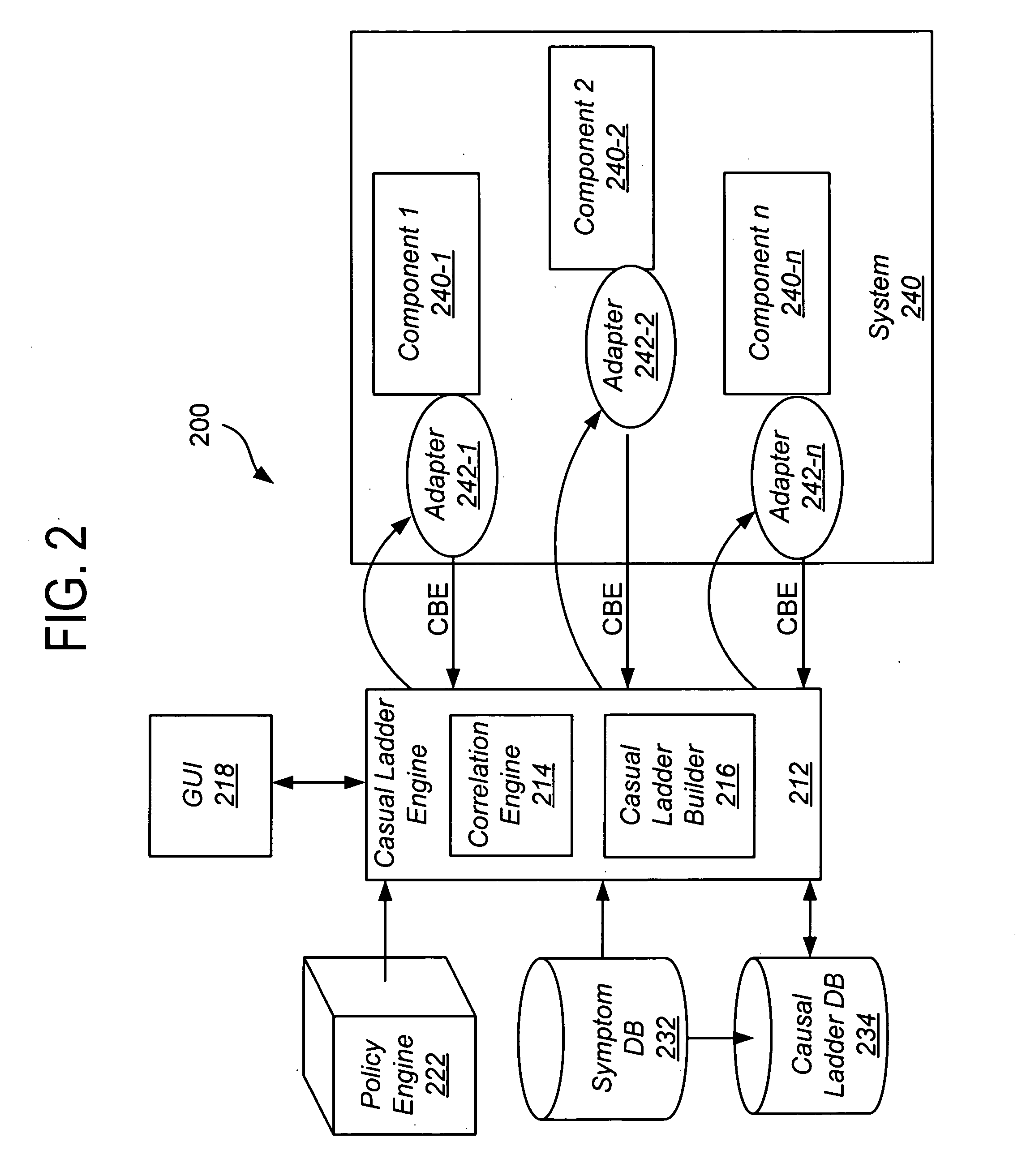
Causal ladder mechanism for proactive problem determination, avoidance and recovery
A plurality of causal ladder is assembled in advance from component system events taken from previous system failures. The ladders classify the various transitions the system goes through from one set of observed states to another in multiple stages representing issues of differing urgency, importance and need for remediation. These stages are used at runtime to determine the criticality of any abnormal system activity and to accurately predict the component failure prior to the system crashing. Each ladder comprises a plurality of elevated stages representing criticality of the problem. At runtime, the causal ladder engine correlates real-time events received from the system to stages of one or more pre-constructed causal ladders and identifies a probable problem (and / or the faulty component) from the corresponding causal ladder. The causal ladder engine also determines the stage of the problem from event occurrences. At each stage, a different potential solution is identified for the problem.
Owner:TREND MICRO INC
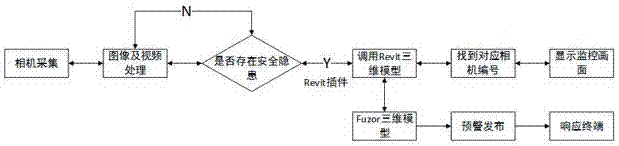
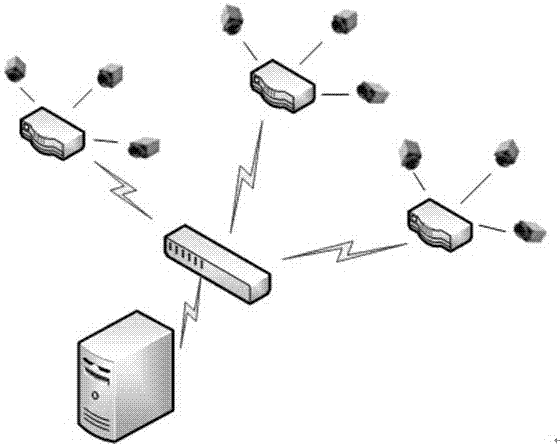
Building working area danger source intelligent identification system
InactiveCN107145851AReduce difficultyLow costImage analysisCharacter and pattern recognitionMonitoring systemLarge range
The present invention discloses a building working area danger source intelligent identification system which is characterized by mainly comprising a large-range working area scene information obtaining system, a foreground target and region of interest (ROI) extraction system under a complicated background, a danger source intelligent identification system and an early warning publishing, responding and interacting system, and is mainly used for the danger source intelligent identification, the working personnel identification, the safety helmet wearing detection and the limit intrusion problem determination in a building working area. The building working area danger source intelligent identification system of the present invention, on one hand, provides the real and effective video data to the management personnel, on the other hand, enables the difficulty and the cost of an omnibearing supervision construction site to be reduced, at the same time, identifies full-automatically and intelligently, is wide in application range, is compatible with a conventional monitoring system at a certain extent, and enables the system operation cost to be saved greatly.
Owner:SOUTHWEAT UNIV OF SCI & TECH
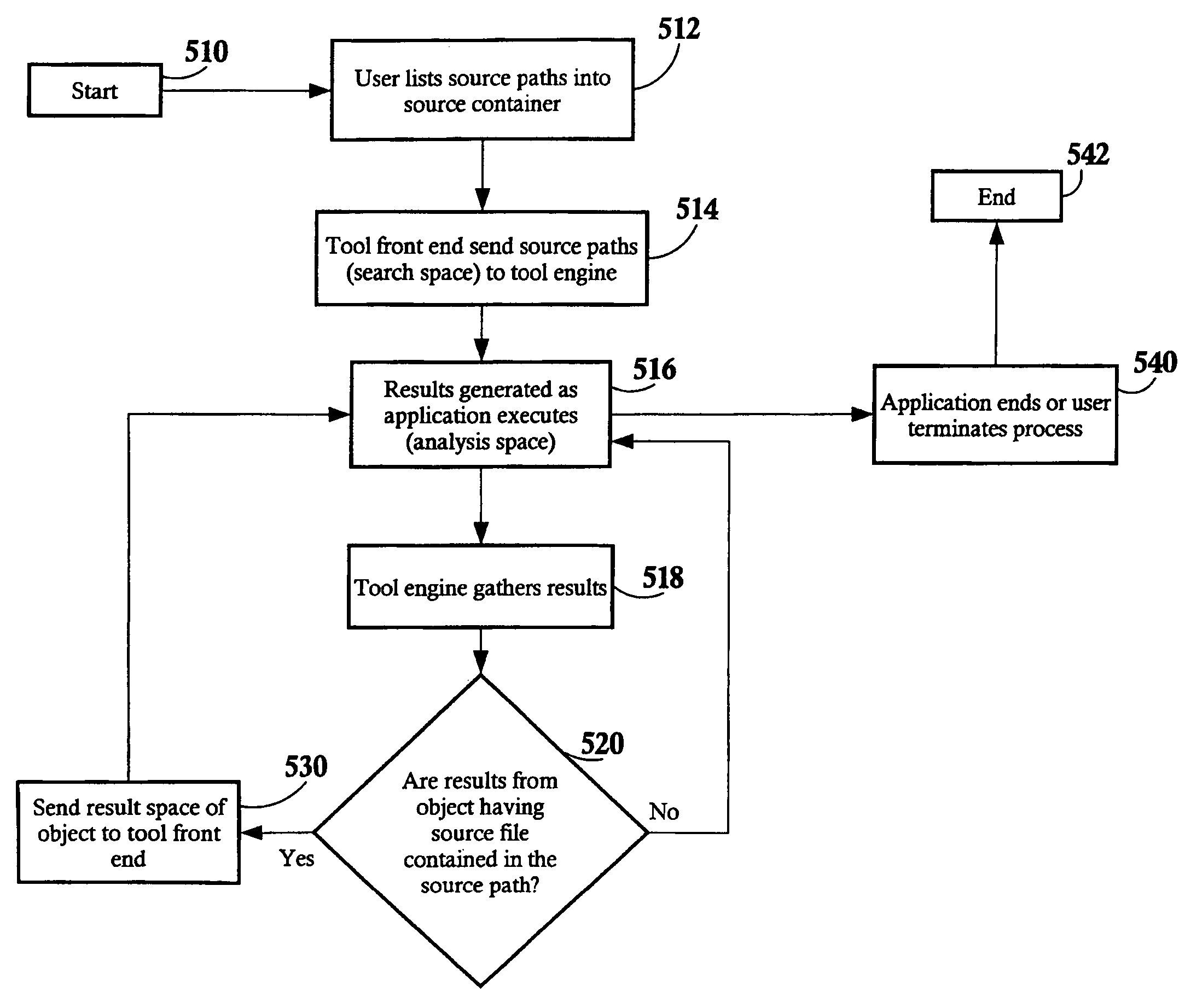
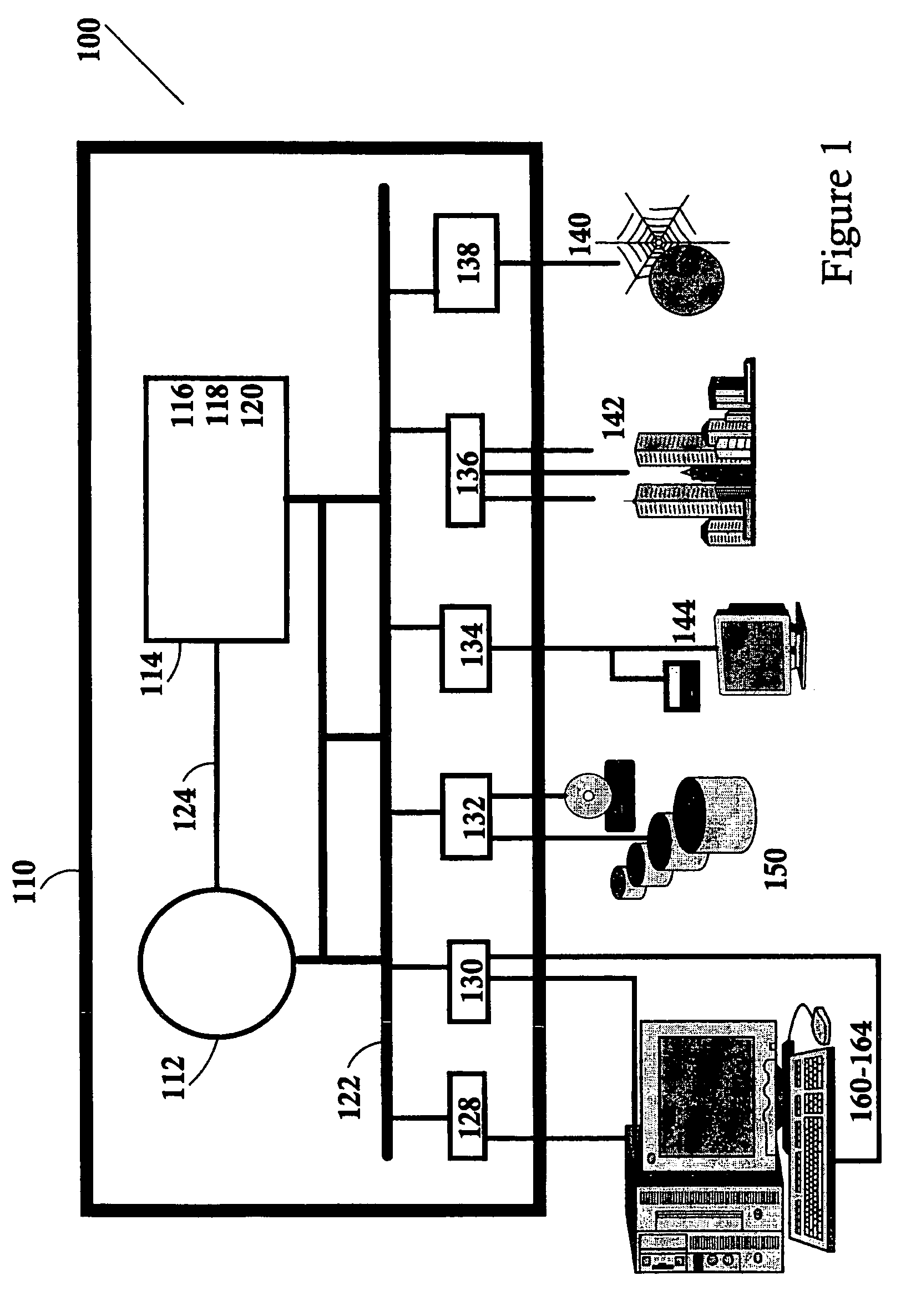
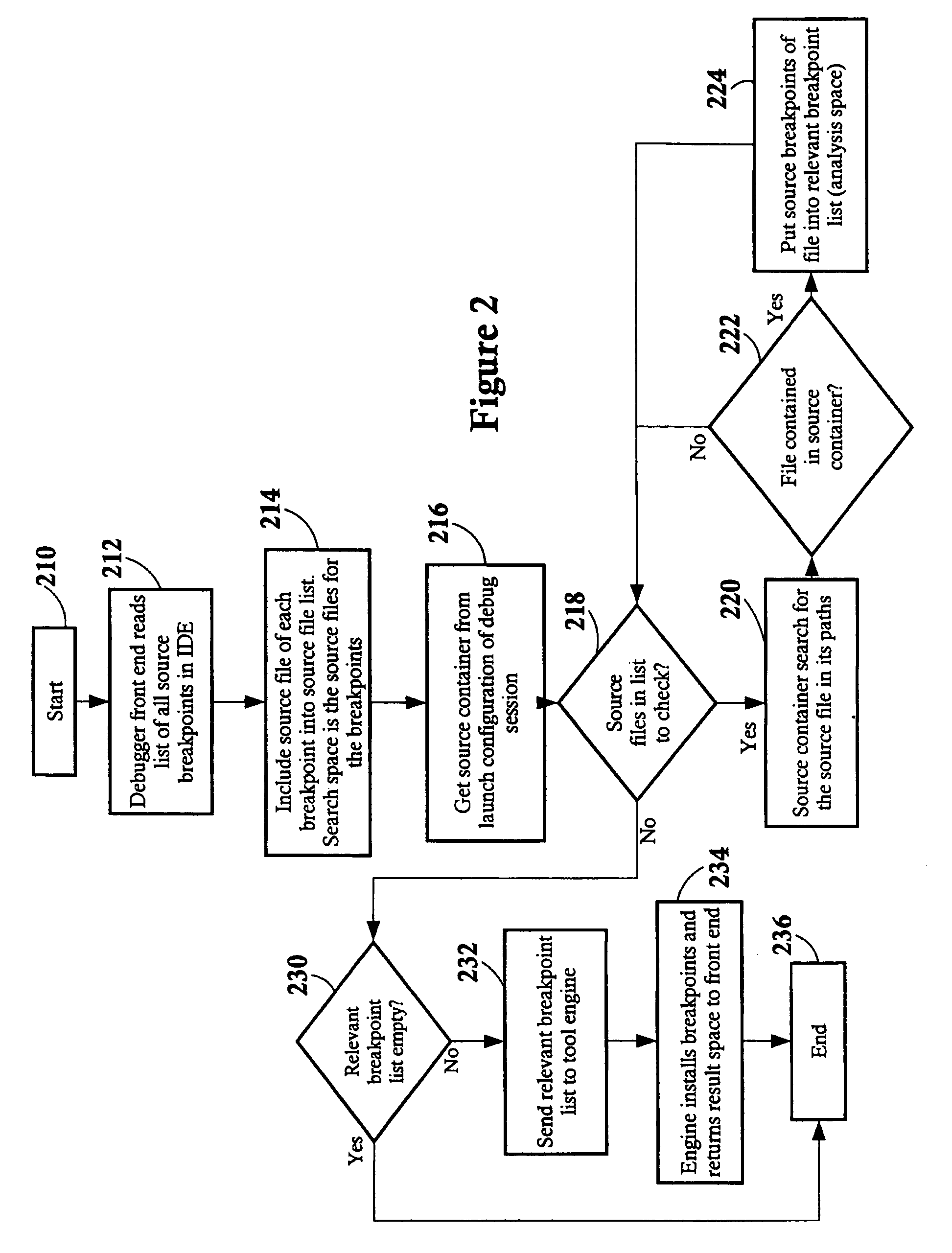
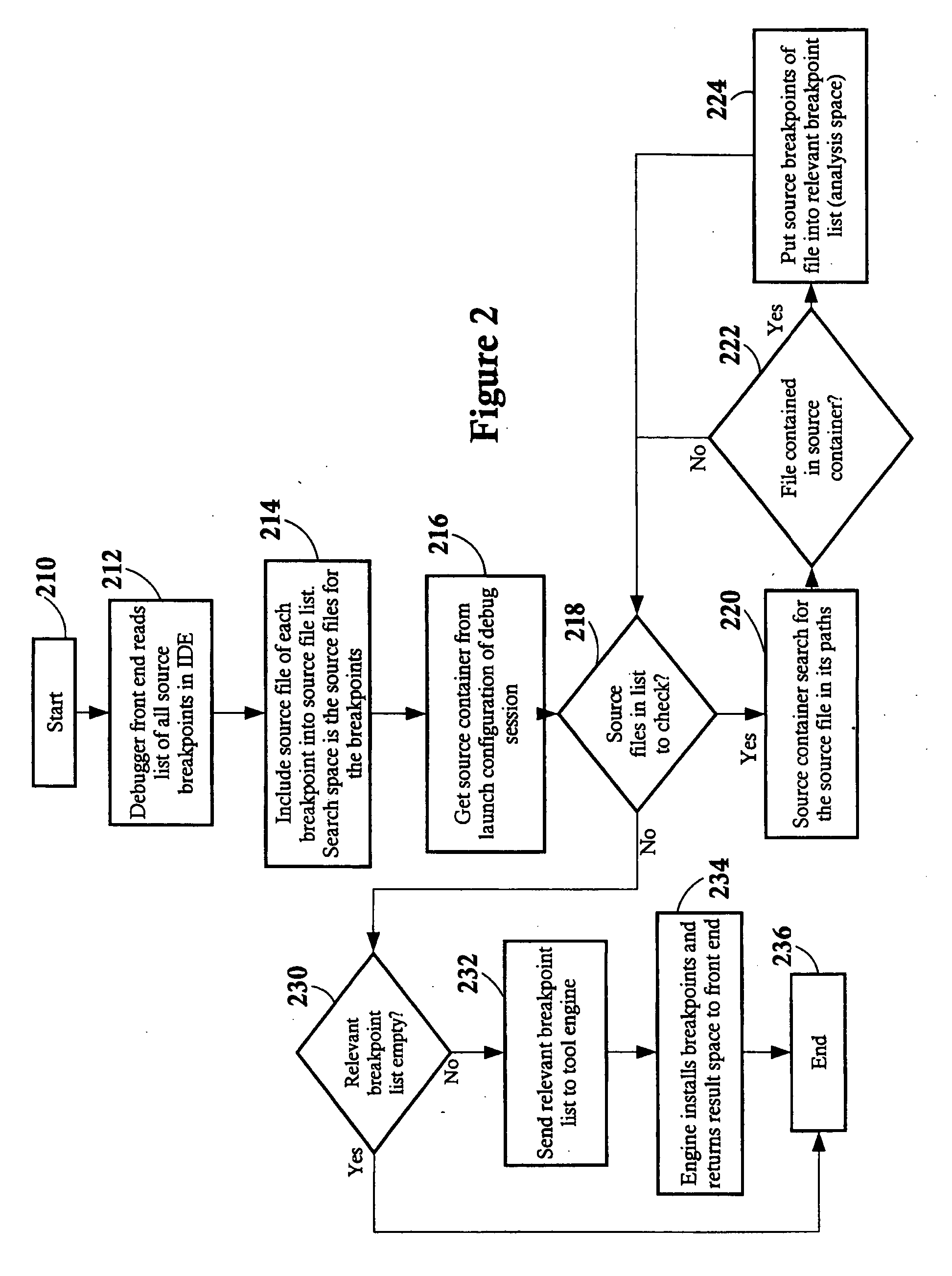
Constraining source code and objects for analysis tools
ActiveUS7917894B2Error detection/correctionSpecific program execution arrangementsAnalysis toolsSoftware development
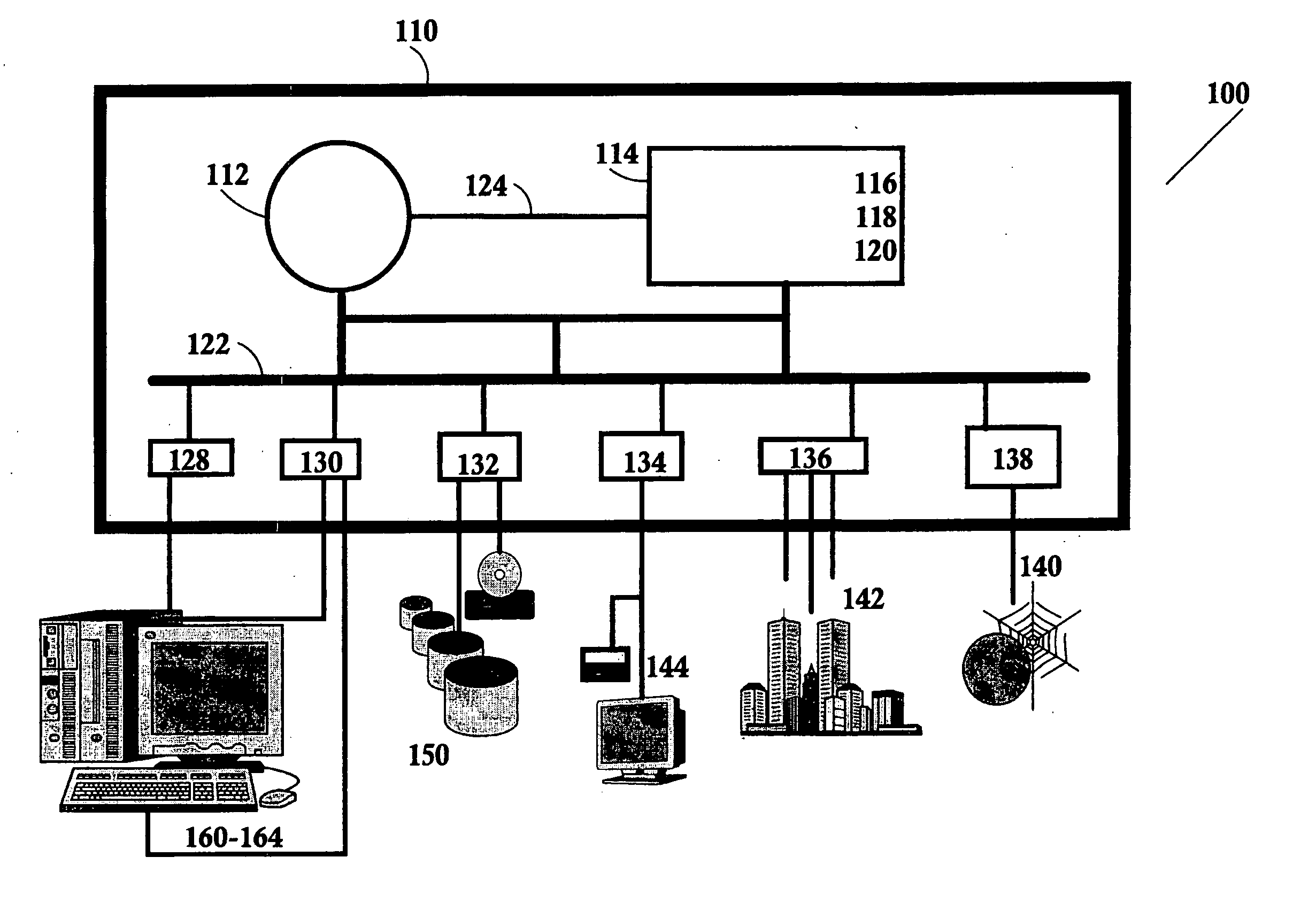
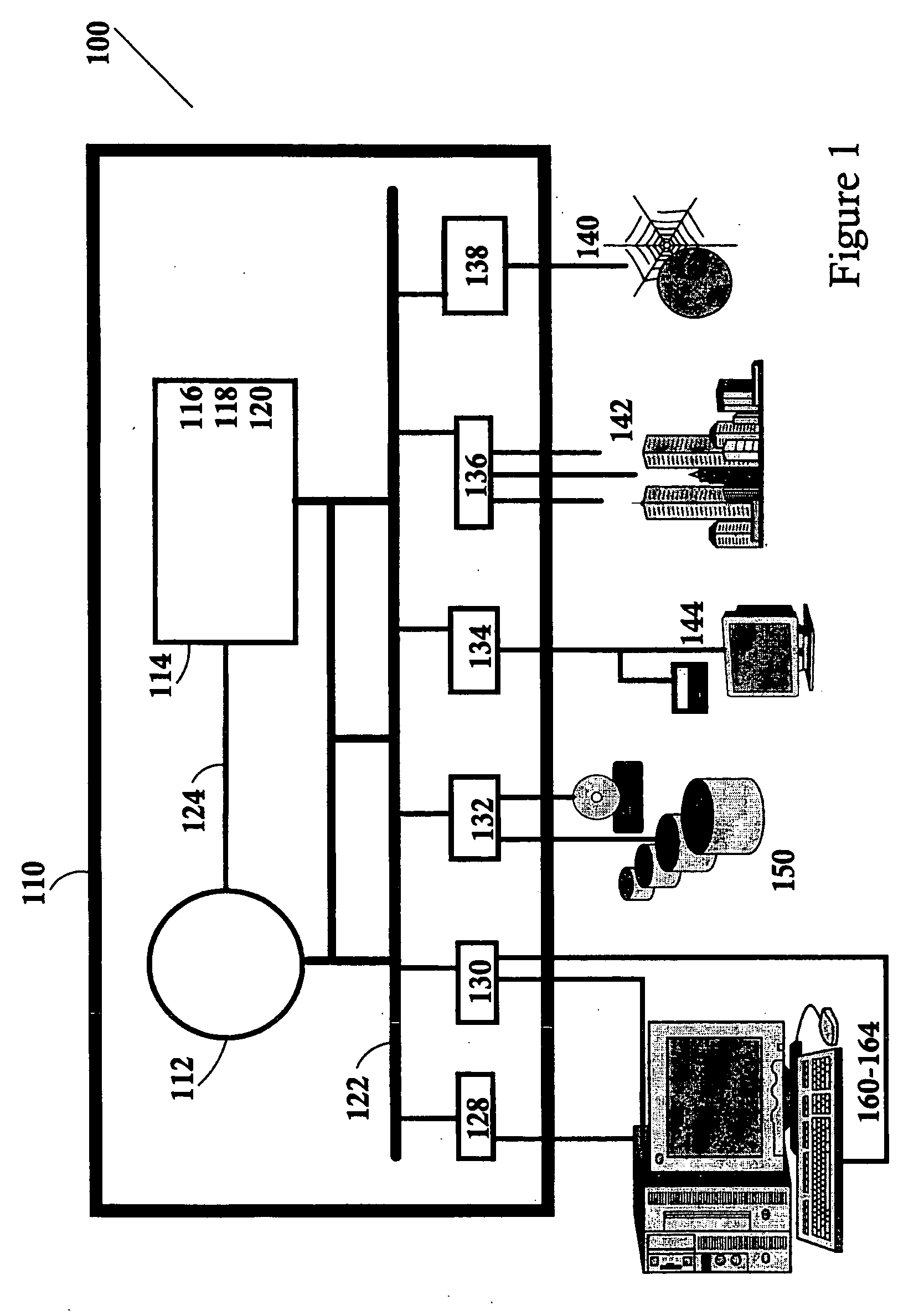
A source container for use in a computer system executing problem determination tools in an integrated environment across a computer network, the source container comprising a list of pathways to a plurality of source files and module objects. A software development may create the source container independently or within the front end of a problem determination tool. The front end of the problem determination tools sends the source container to its engine, and only source files and module objects having a pathway in the source container are analyzed within the engine of the problem determination tool. Furthermore, the results of the analysis of only those source files and module objects having a pathway in the source container are returned to the front end of the problem determination tool for viewing by the software developer. The front ends of the tools of the integrated development environment, the source files, the module objects, the engines of the tools, and different tools may all be located on different servers and / or clients across a computer network.
Owner:IBM CORP
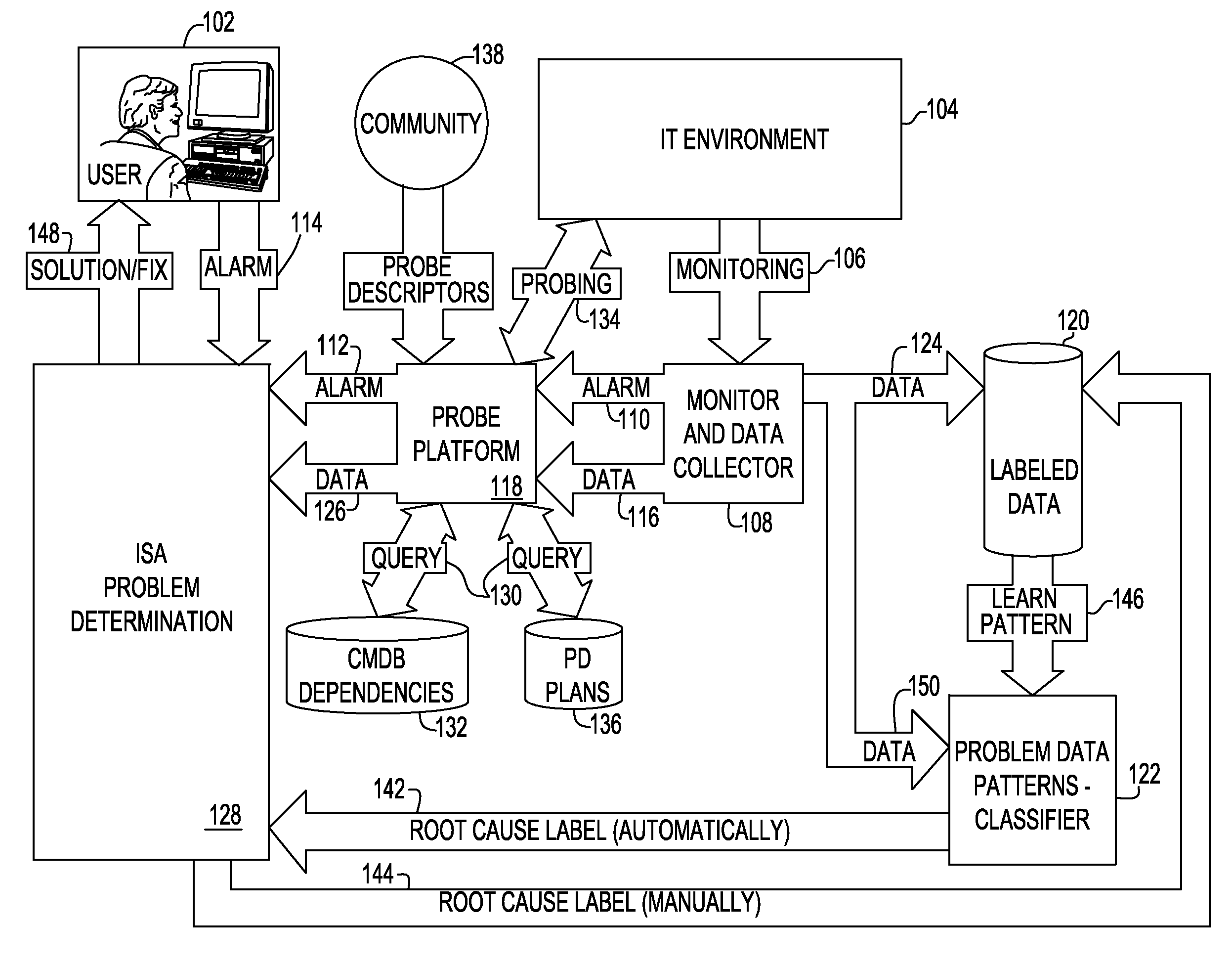
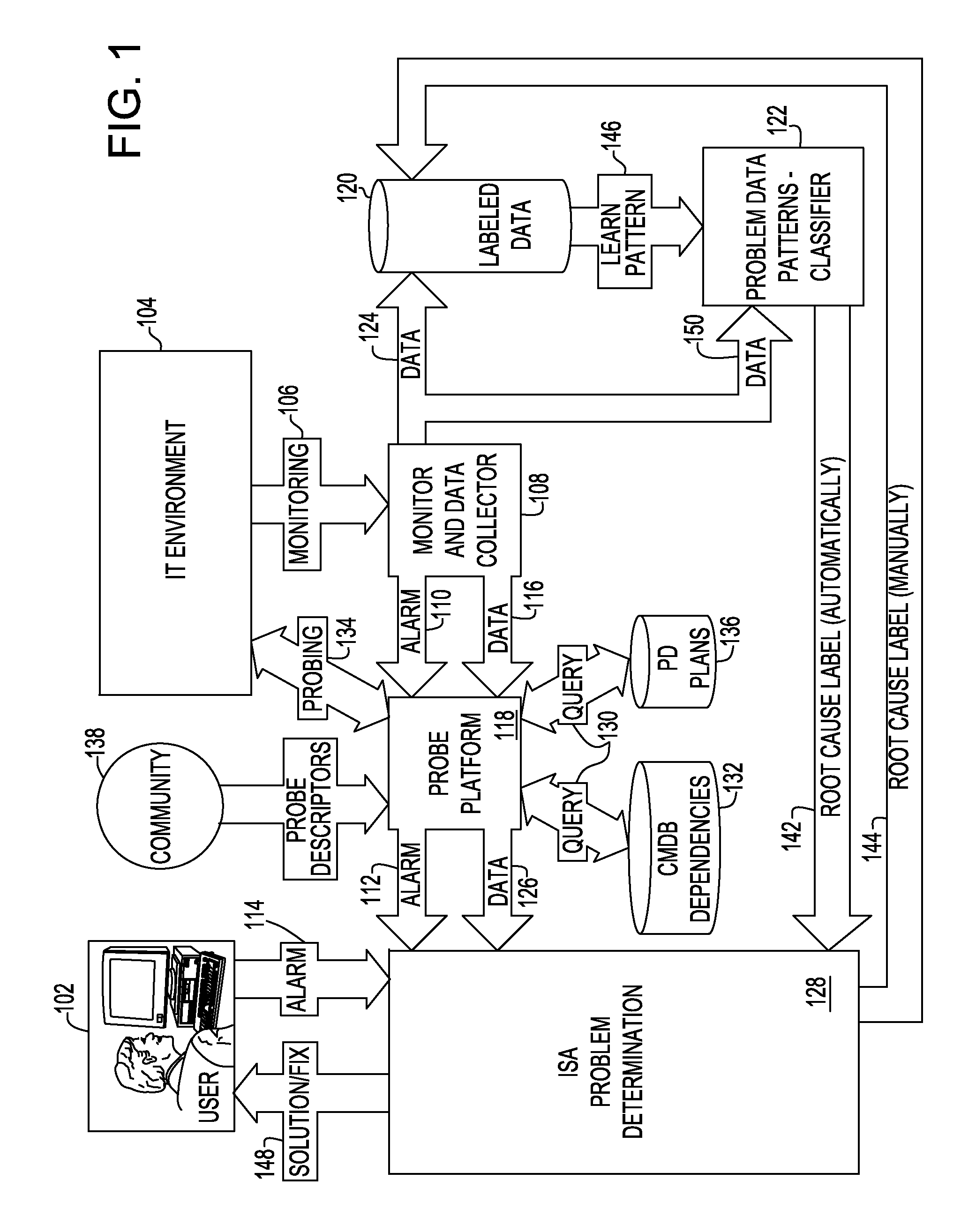
Method and system for problem determination using probe collections and problem classification for the technical support services
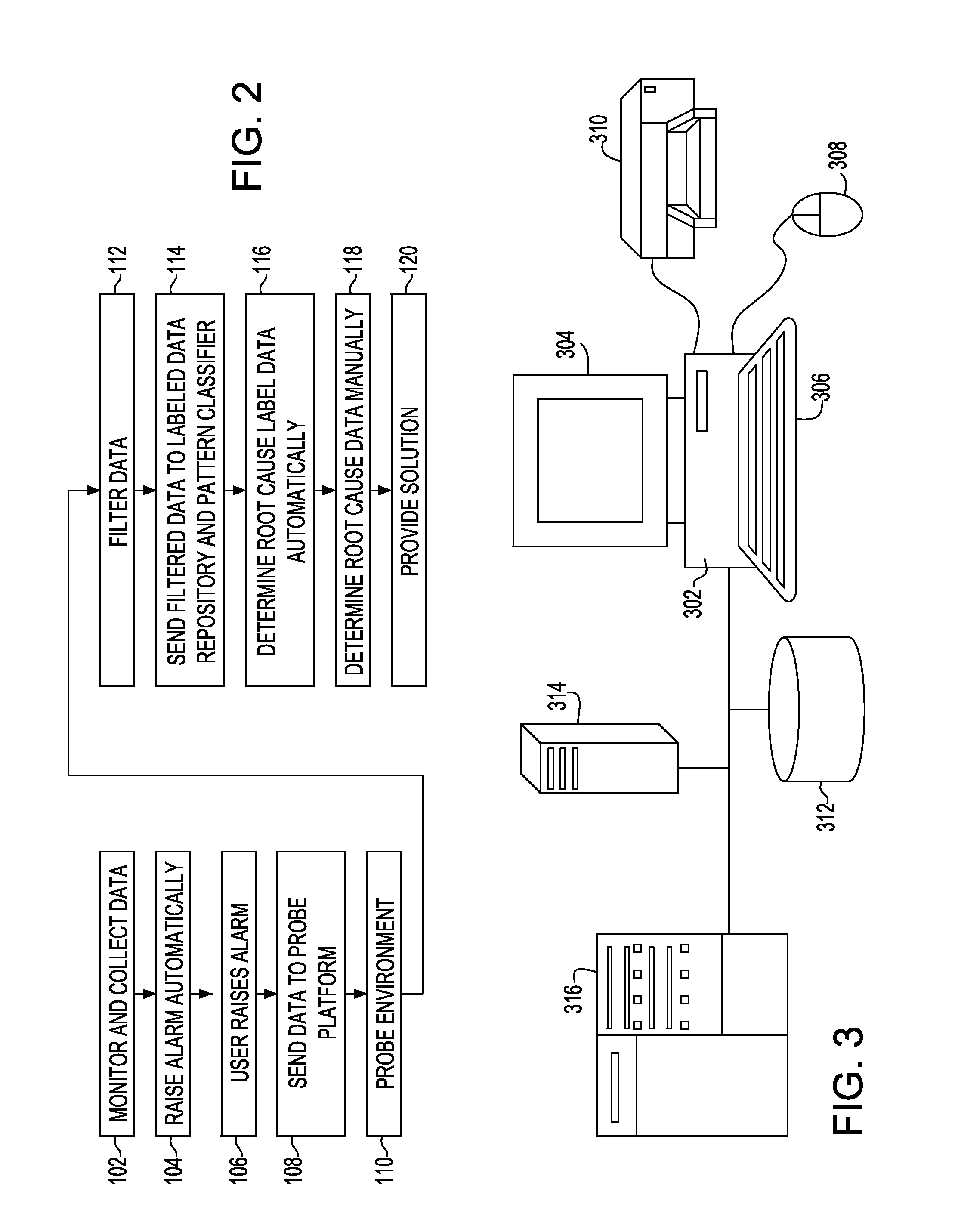
InactiveUS20110060946A1Non-redundant fault processingTransmissionComputerized systemInformation Harvesting
A system and method for problem determination using probe collections and problem classification for the technical support services monitor and collect data associated with a computer system, raise an alarm based on the monitored and collected data, probe the computer system for additional information, filter the monitored and collected data based on the additional information established from probing, and use the filtered data to label a problem associated with the raised alarm.
Owner:GLOBALFOUNDRIES INC
Constraining source code and objects for analysis tools
ActiveUS20060277528A1Error detection/correctionSpecific program execution arrangementsAnalysis toolsSoftware development
A source container for use in a computer system executing problem determination tools in an integrated environment across a computer network, the source container comprising a list of pathways to a plurality of source files and module objects. A software development may create the source container independently or within the front end of a problem determination tool. The front end of the problem determination tools sends the source container to its engine, and only source files and module objects having a pathway in the source container are analyzed within the engine of the problem determination tool. Furthermore, the results of the analysis of only those source files and module objects having a pathway in the source container are returned to the front end of the problem determination tool for viewing by the software developer. The front ends of the tools of the integrated development environment, the source files, the module objects, the engines of the tools, and different tools may all be located on different servers and / or clients across a computer network.
Owner:IBM CORP
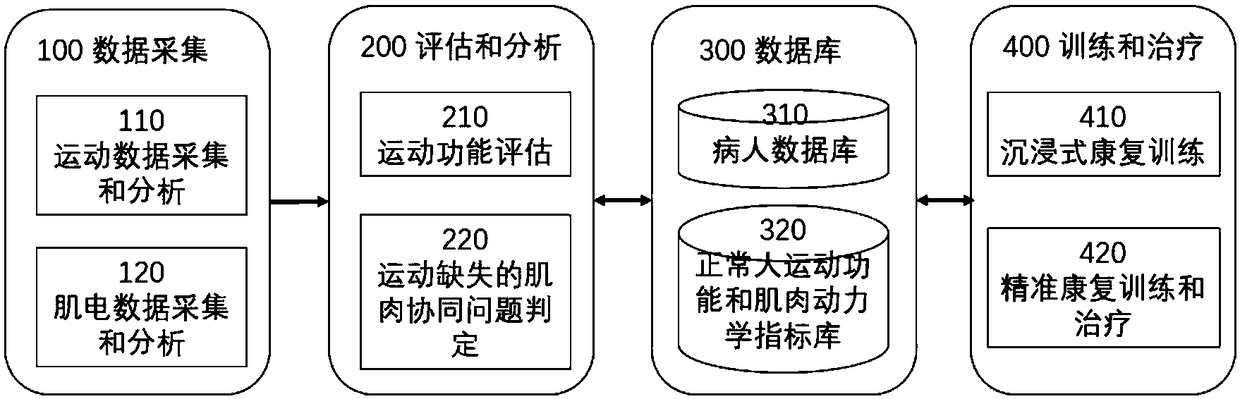
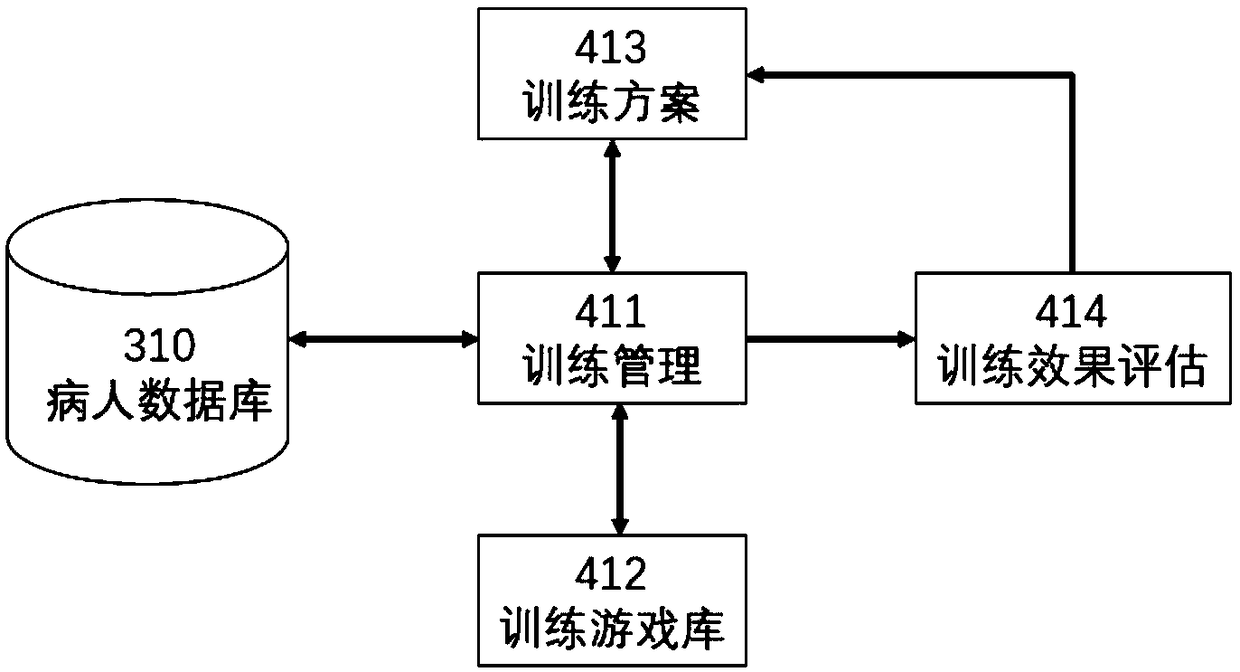
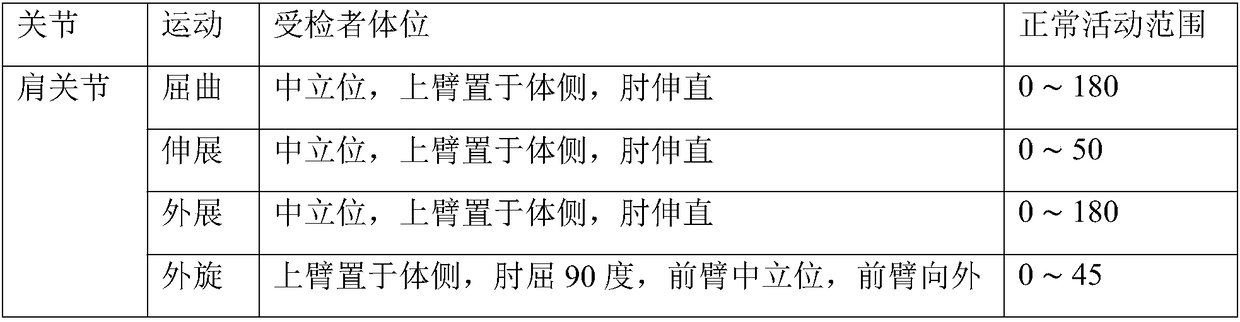
Accurate exercise evaluation and rehabilitation training system
ActiveCN109243572AEasy to acceptGo digitalPhysical therapies and activitiesHealth-index calculationPatient acceptanceMuscle synergy
The invention provides an accurate exercise evaluation and rehabilitation training system comprising an exercise data acquisition and analysis module, an electromyography data acquisition and analysismodule, an exercise function evaluation module, an exercise missing muscle synergy problem determination module, an immersive rehabilitation training module, an accurate rehabilitation training and treatment module, a patient database module and a normal person exercise function and muscle dynamics index library. The exercise function and exercise missing can be accurately and quantitatively evaluated based on the micro-sensor intelligent sensing technology and the information fusion technology, and the problems of the muscle level and the nerve stimulation level of exercise missing can be analyzed and determined so as to specify and perform the rehabilitation training and treatment plan in a targeted way. Meanwhile, the immersive rehabilitation training function is also provided so as tofacilitate patient acceptance and adherence and realize digitalization, accuracy and visualization of exercise rehabilitation.
Owner:中科数字健康科学研究院(南京)有限公司
System and method for incident management enhanced with problem classification for technical support services
ActiveUS8365019B2Faster, more versatile and more effectiveReduce management costsDigital computer detailsNon-redundant fault processingRoot causeOnline learning
Owner:MAPLEBEAR INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com