Patents
Literature
52 results about "Captive portal" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A captive portal is a web page accessed with a web browser that is displayed to newly connected users of a Wi-Fi network before they are granted broader access to network resources. Captive portals are commonly used to present a landing or log-in page which may require authentication, payment, acceptance of an end-user license agreement, acceptable use policy, survey completion, or other valid credentials that both the host and user agree to adhere by. Captive portals are used for a broad range of mobile and pedestrian broadband services - including cable and commercially provided Wi-Fi and home hotspots. A captive portal can also be used to provide access to enterprise or residential wired networks, such as apartment houses, hotel rooms, and business centers.
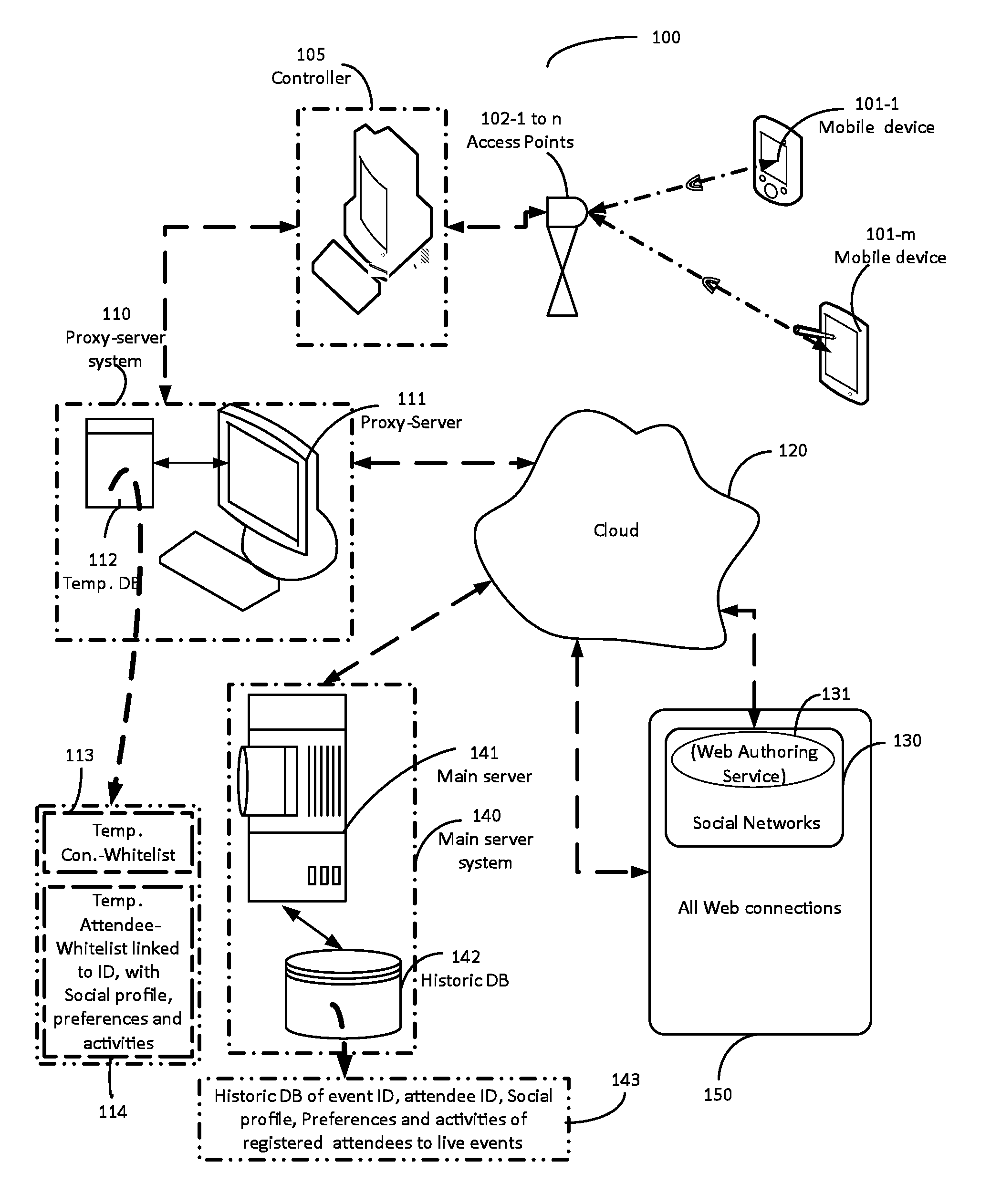
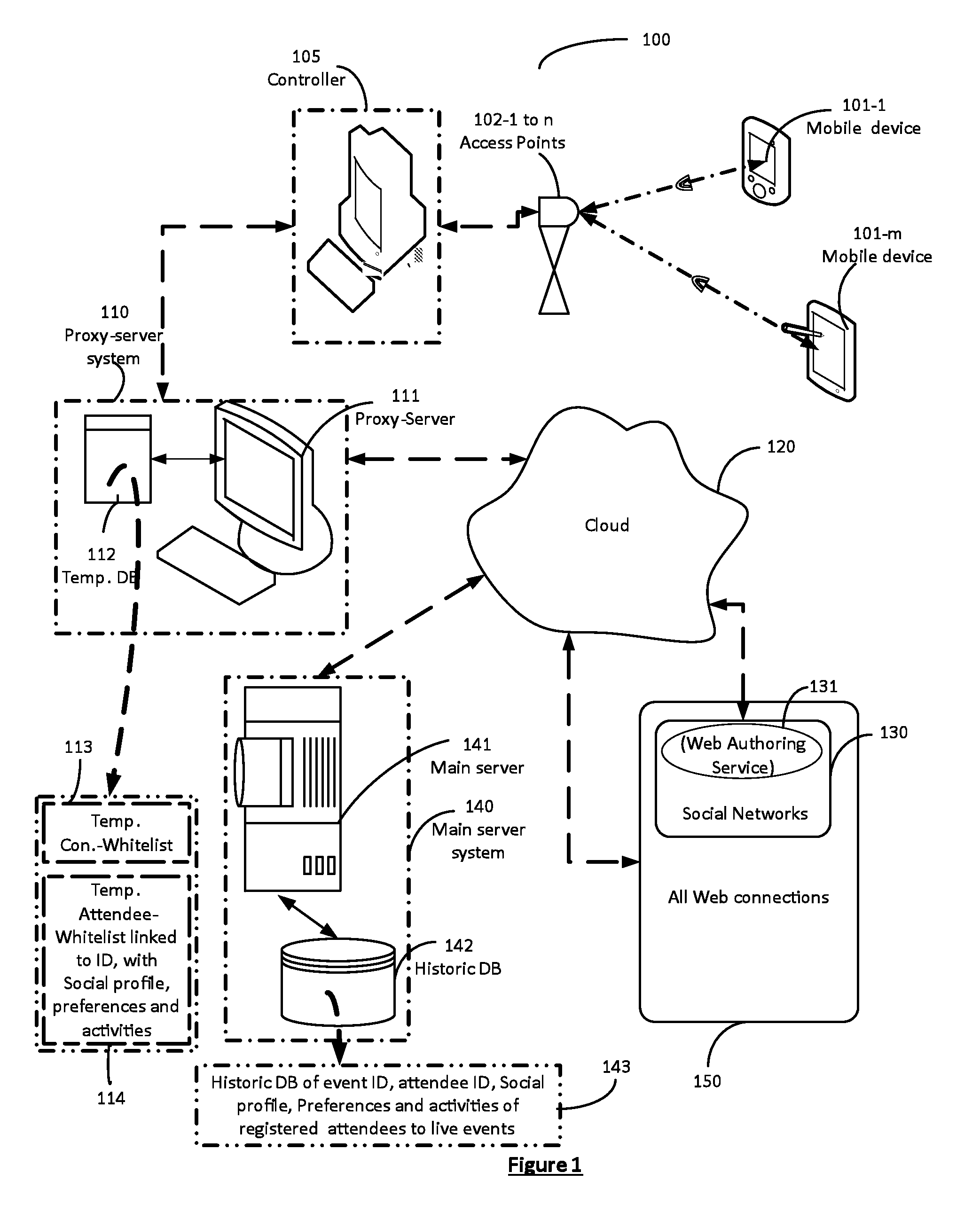
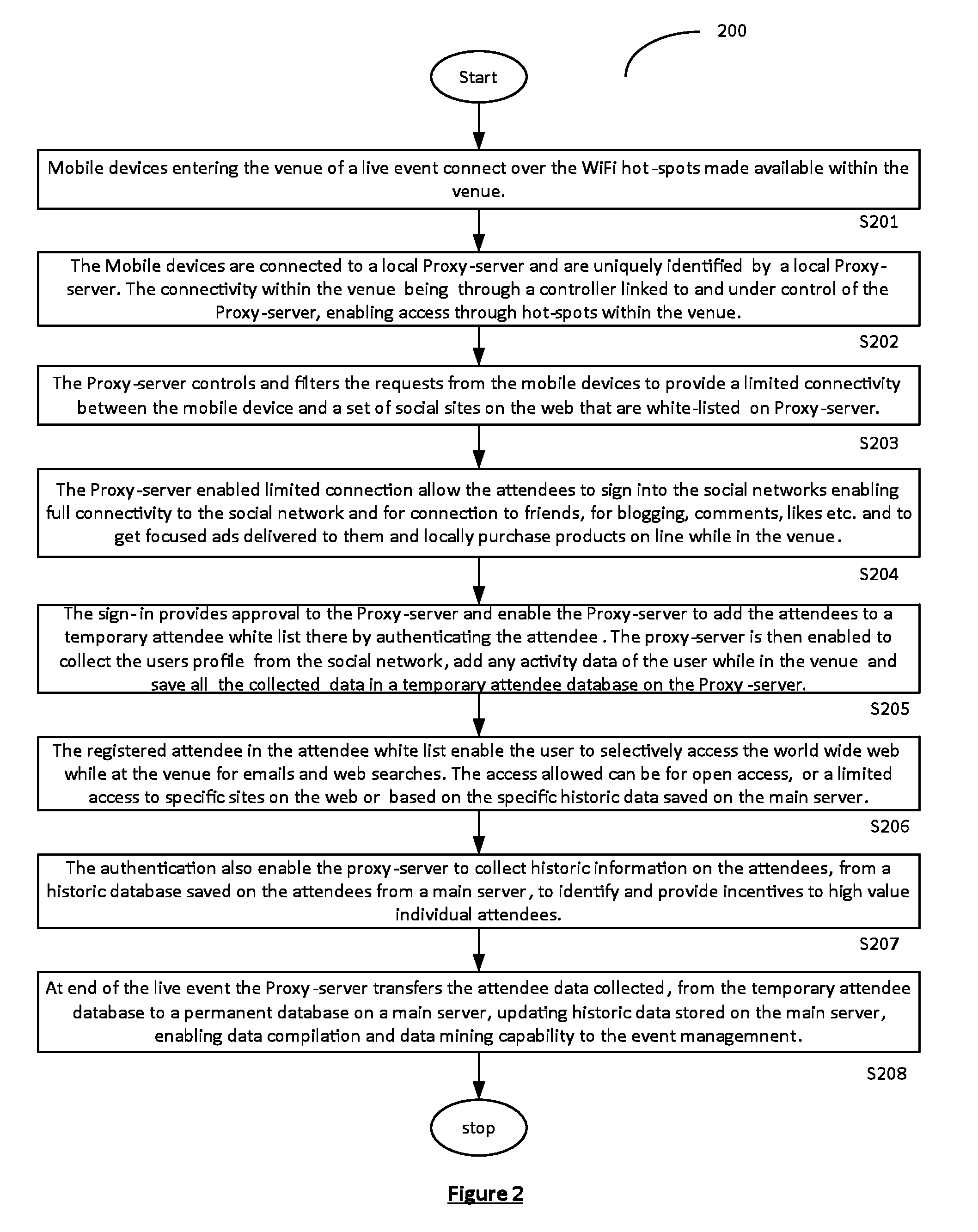
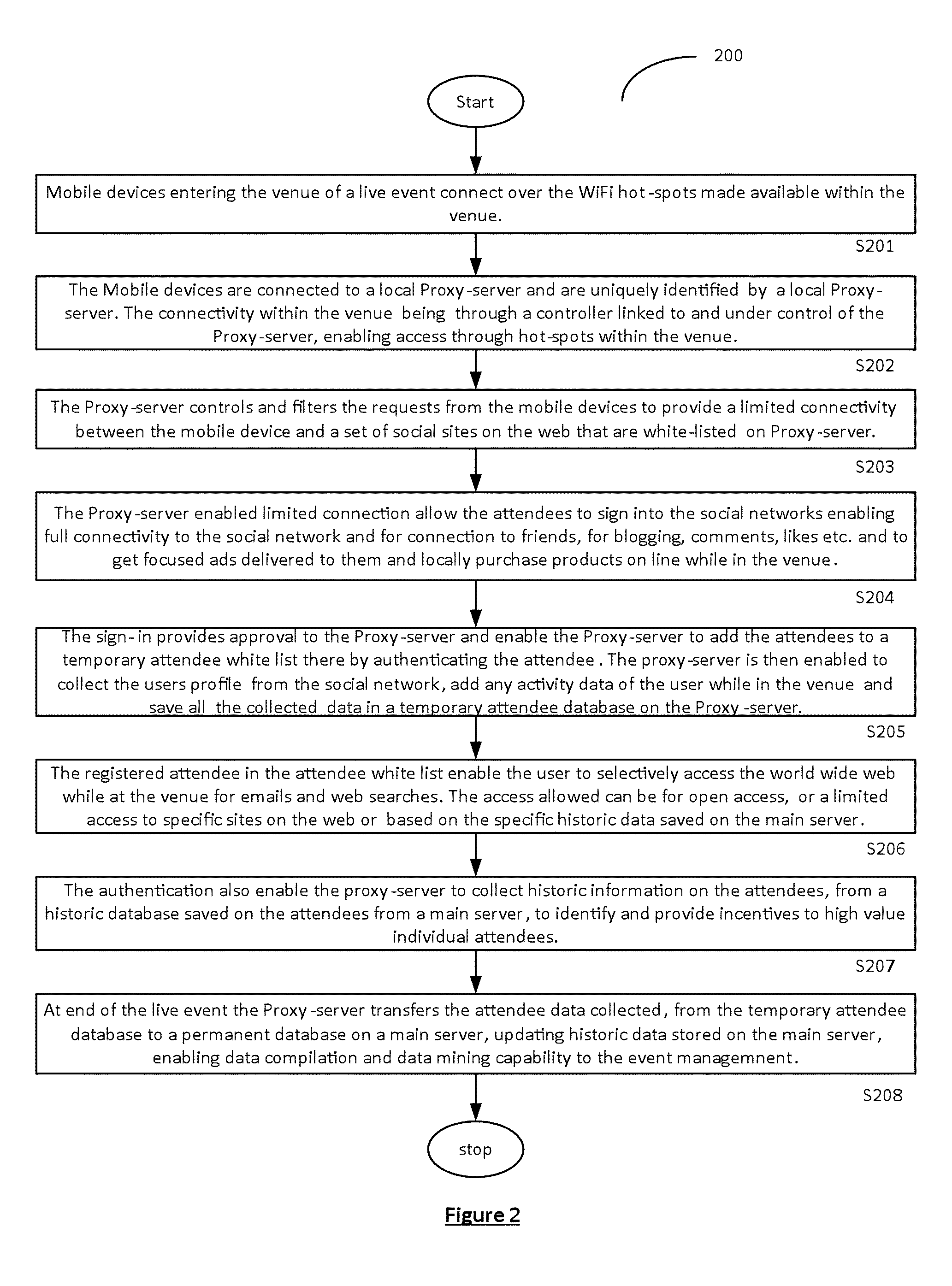
Authenticated registration of participants for web access at live events
ActiveUS20150312760A1Enable connectivityFull connectivityUnauthorised/fraudulent call preventionAdvertisementsTime informationWi-Fi
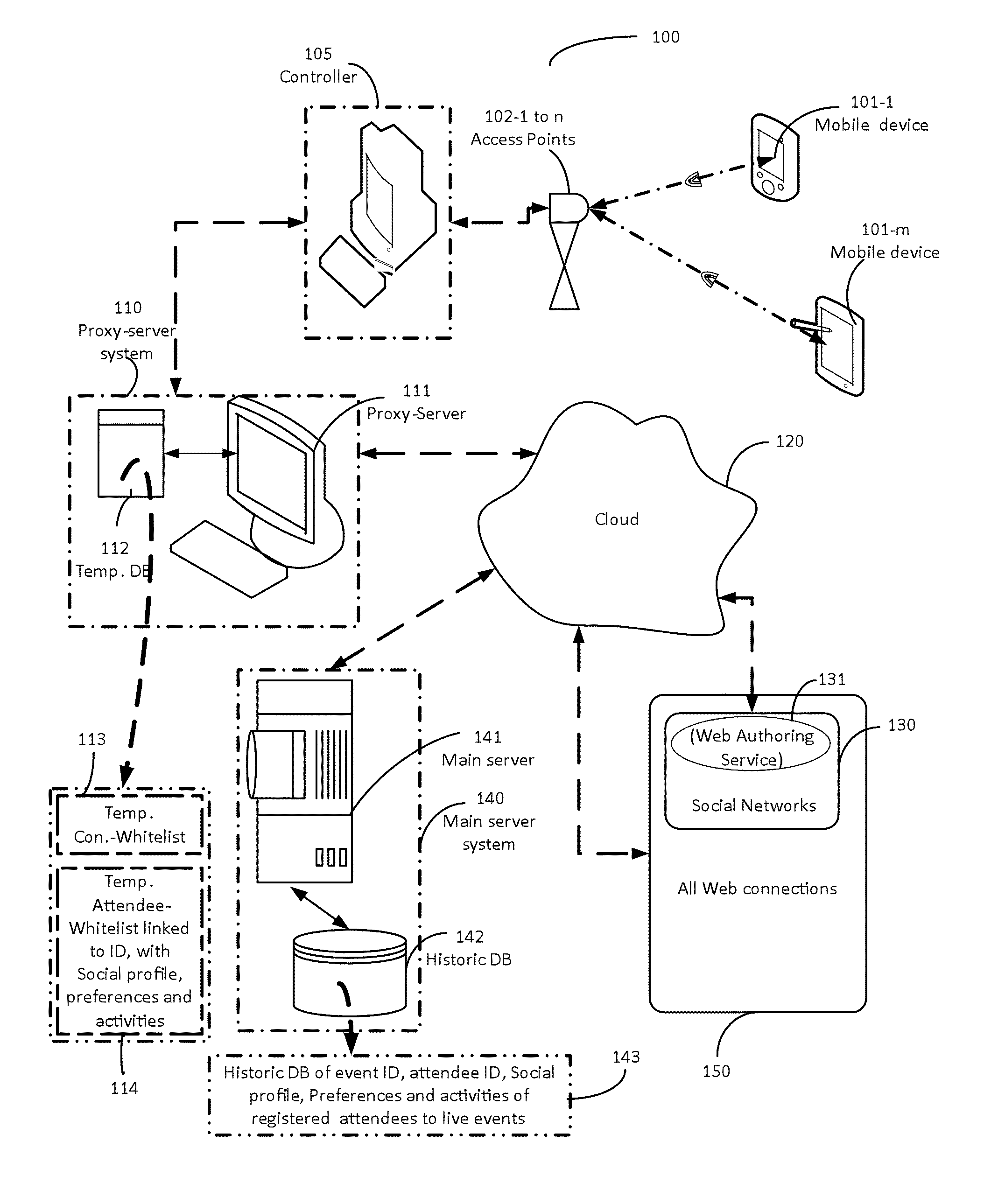
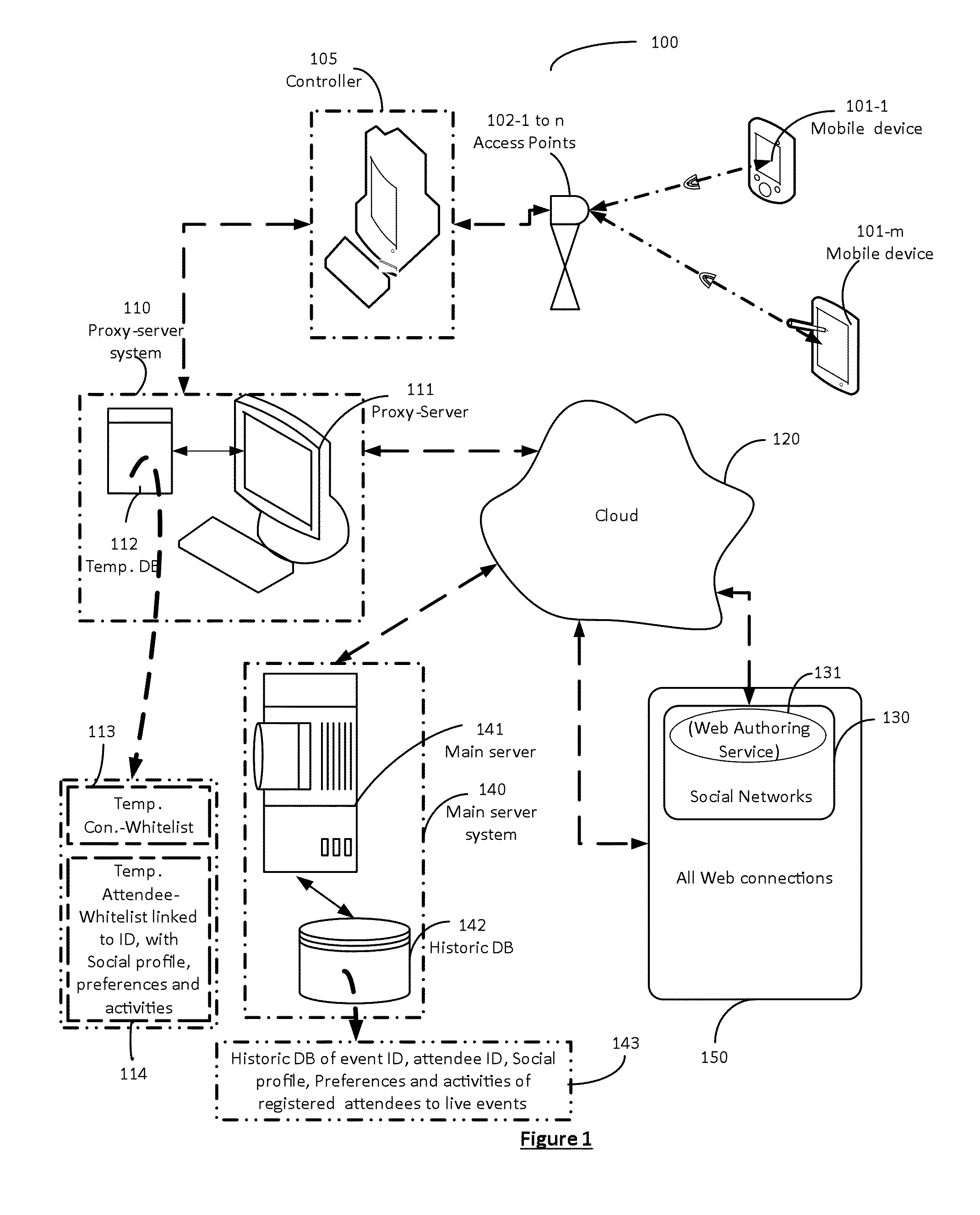
A captive portal technology for registering and authenticating attendees, and for collecting the personal-preferences and social-profile details of individuals participating in a live-event in real-time, is disclosed. Wi-Fi connections within the live-event location are used to register and authenticate the individuals onto a proxy server. Once registered and authenticated, the proxy-server enables a monitoring main server to collect and store the preferences, activities and social profile of the individual in a dedicated database. The authentication provides the individual access to the web for social networking, blogging and other activities at the live-event site. Authorities of live-events are thereby able can identify the individual participants and their habits to provide real time information to improve ticket sales methods, provide incentives, on-site purchase capability and focused advertisements relating to the live-event to improve the live event experience of each individual.
Owner:STAD IO
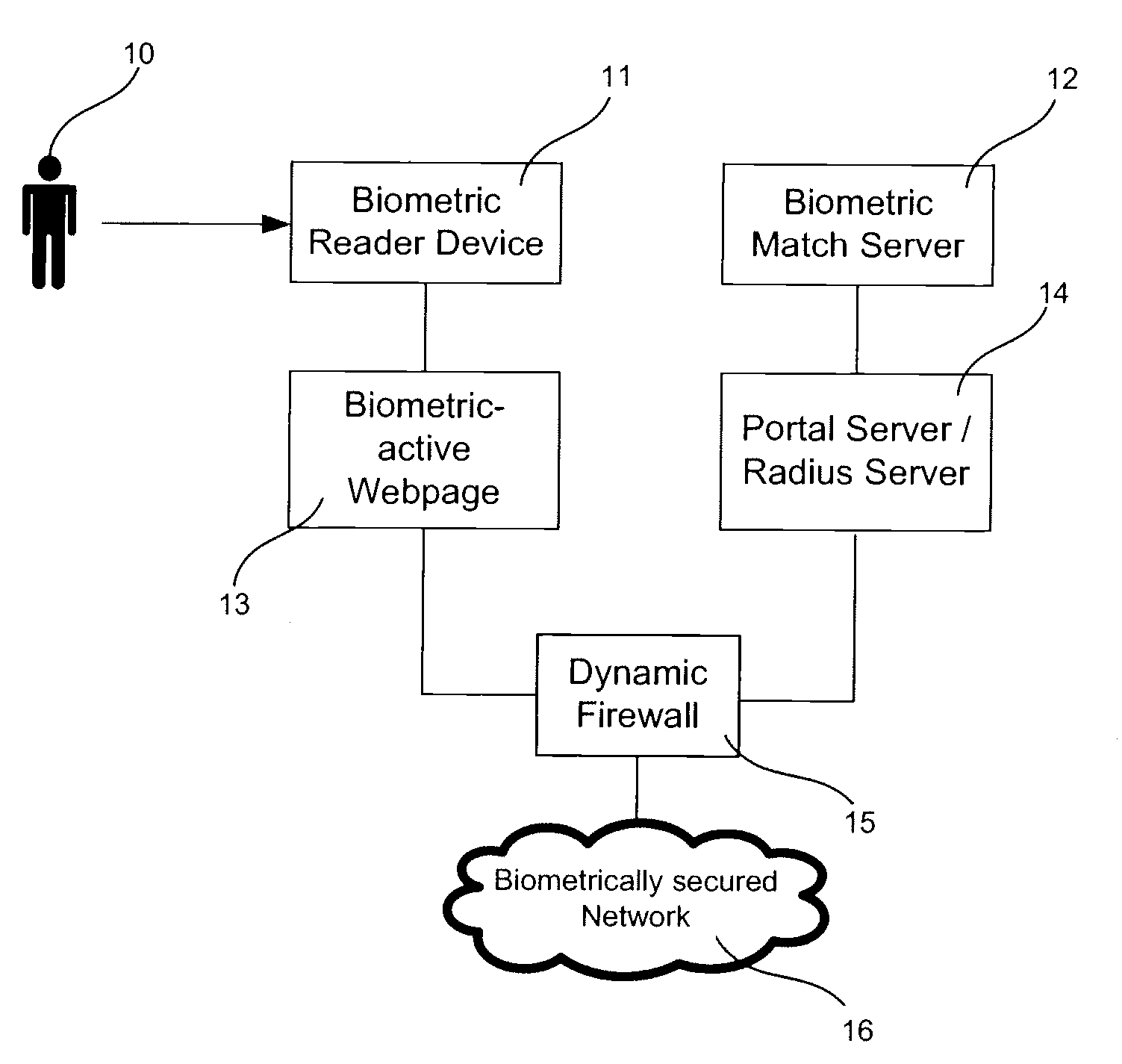
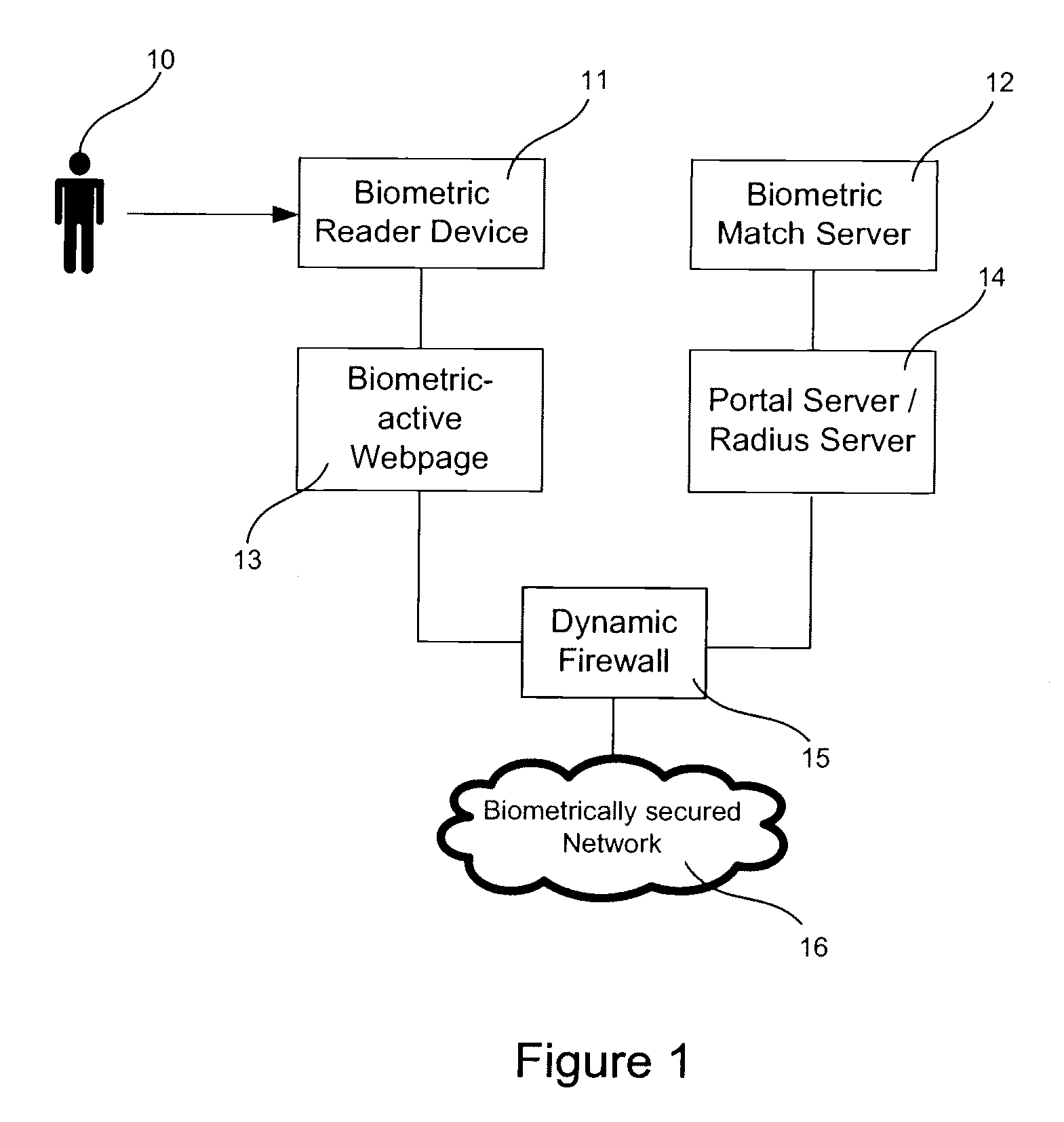
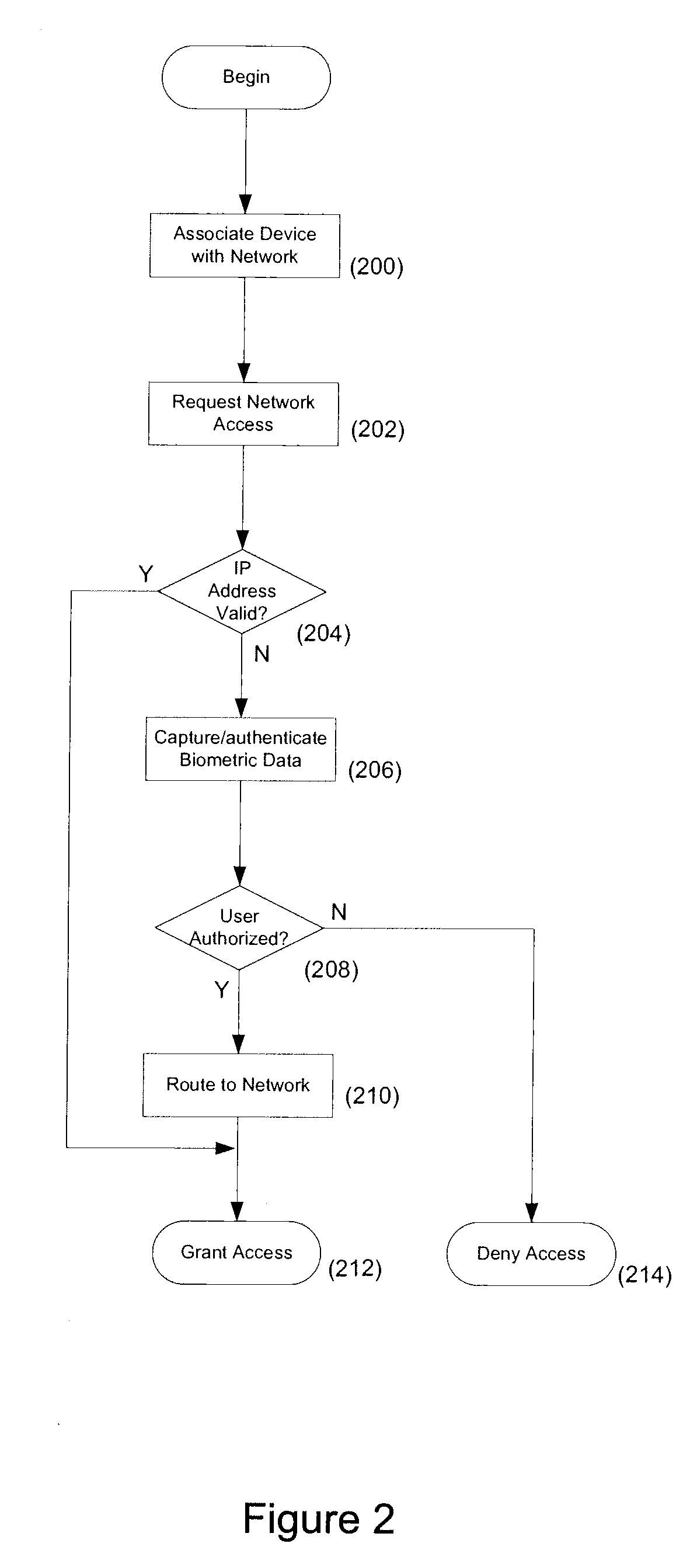
System and method for biometric based network security
InactiveUS20090183247A1More powerDigital data processing detailsUser identity/authority verificationCaptive portalNetwork security policy
Systems and methods of securing access to a network are described. Access to the network is secured using multifactor authentication, biometrics, strong encryption, and a variety of wireless networking standards. Biometrics include fingerprints, facial recognition, retinal scan, voice recognition and biometrics can are used in combination with other authentication factors to create a multi-factor authentication scheme for highly secure network access. Requests that require access to secured network resources may be intercepted and a captive portal page returned to challenge a user. Biometric information returned in response to the portal page is used to authenticate the user and determine access rights to the network.
Owner:11I NETWORKS
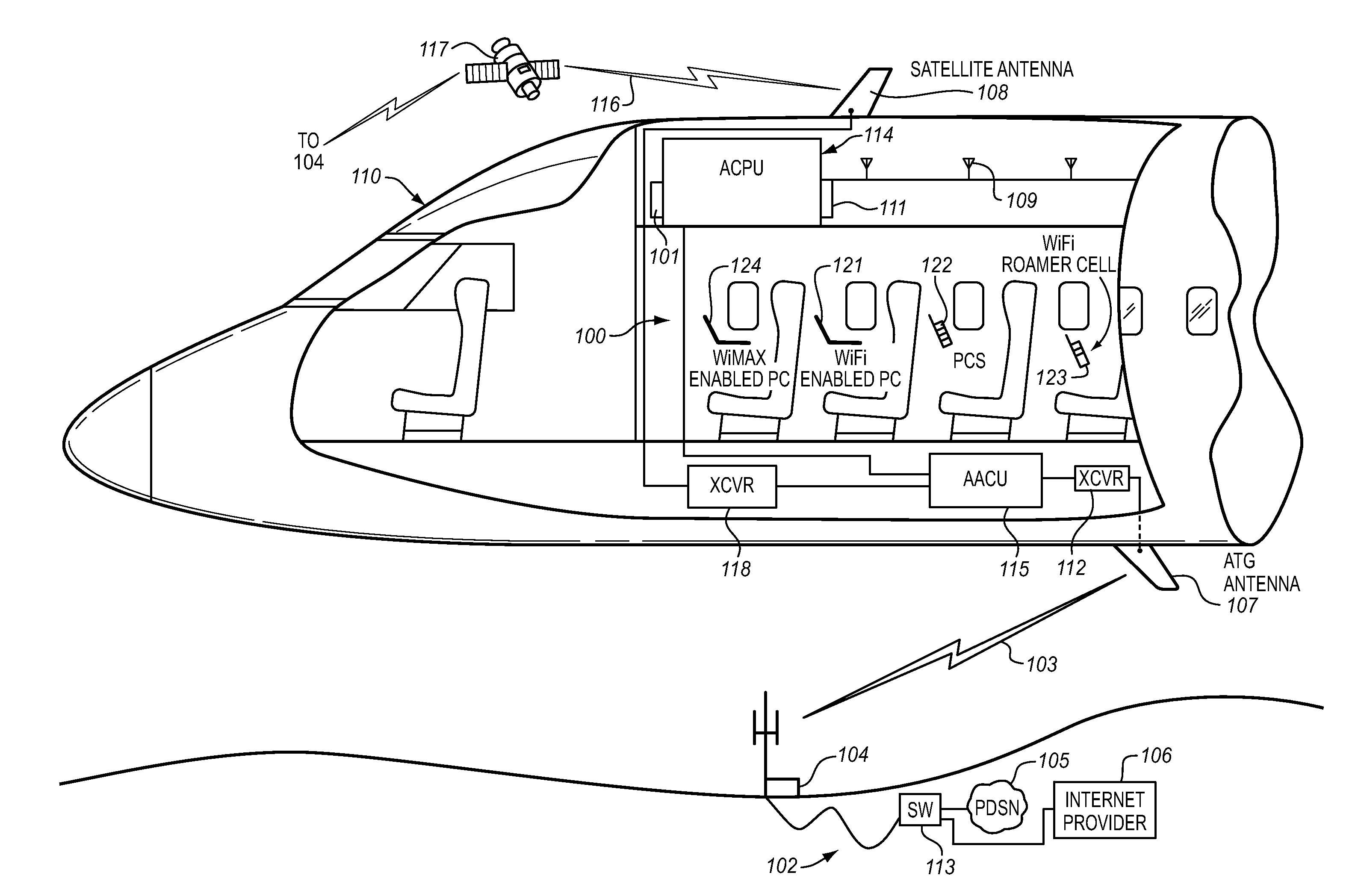
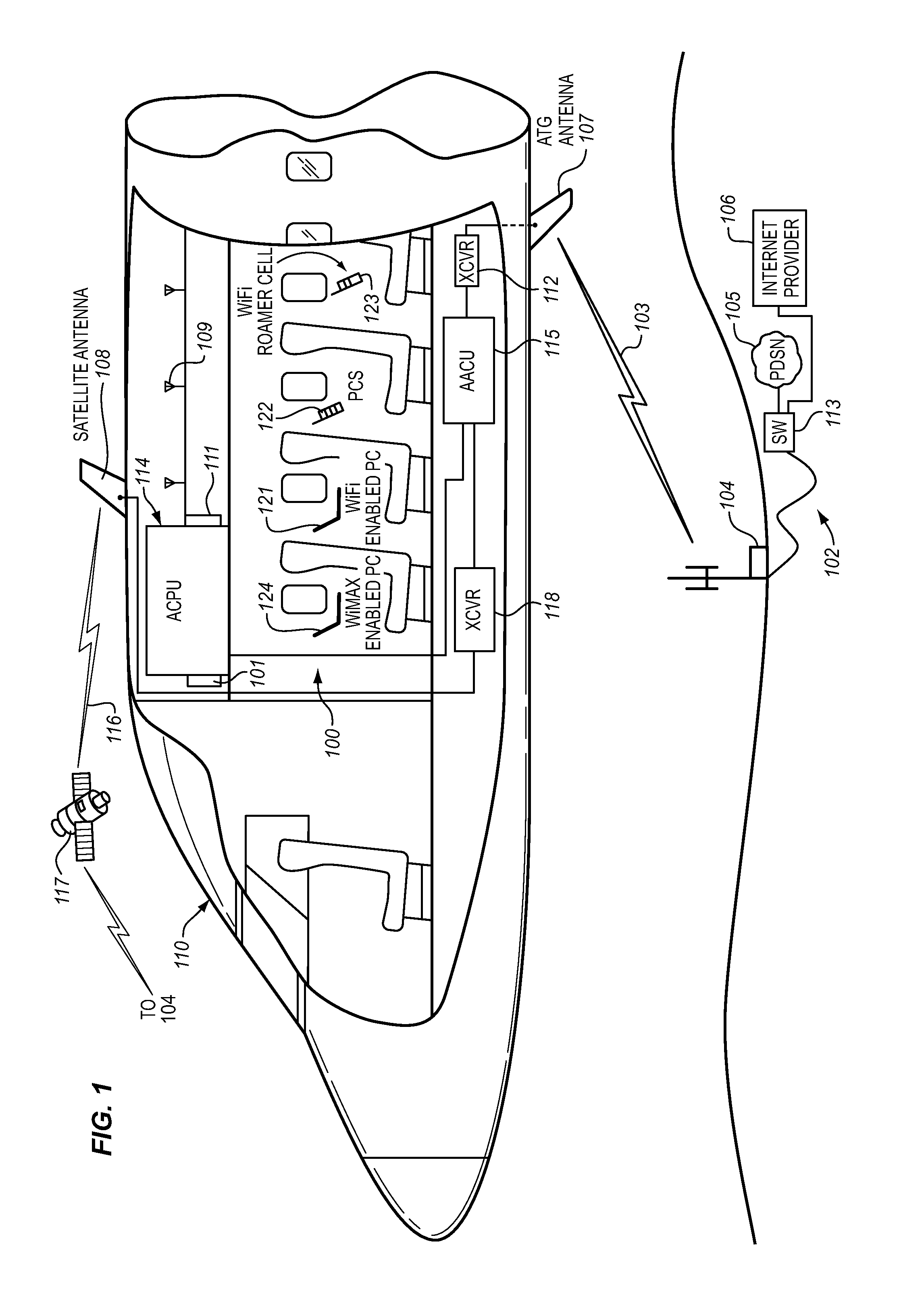
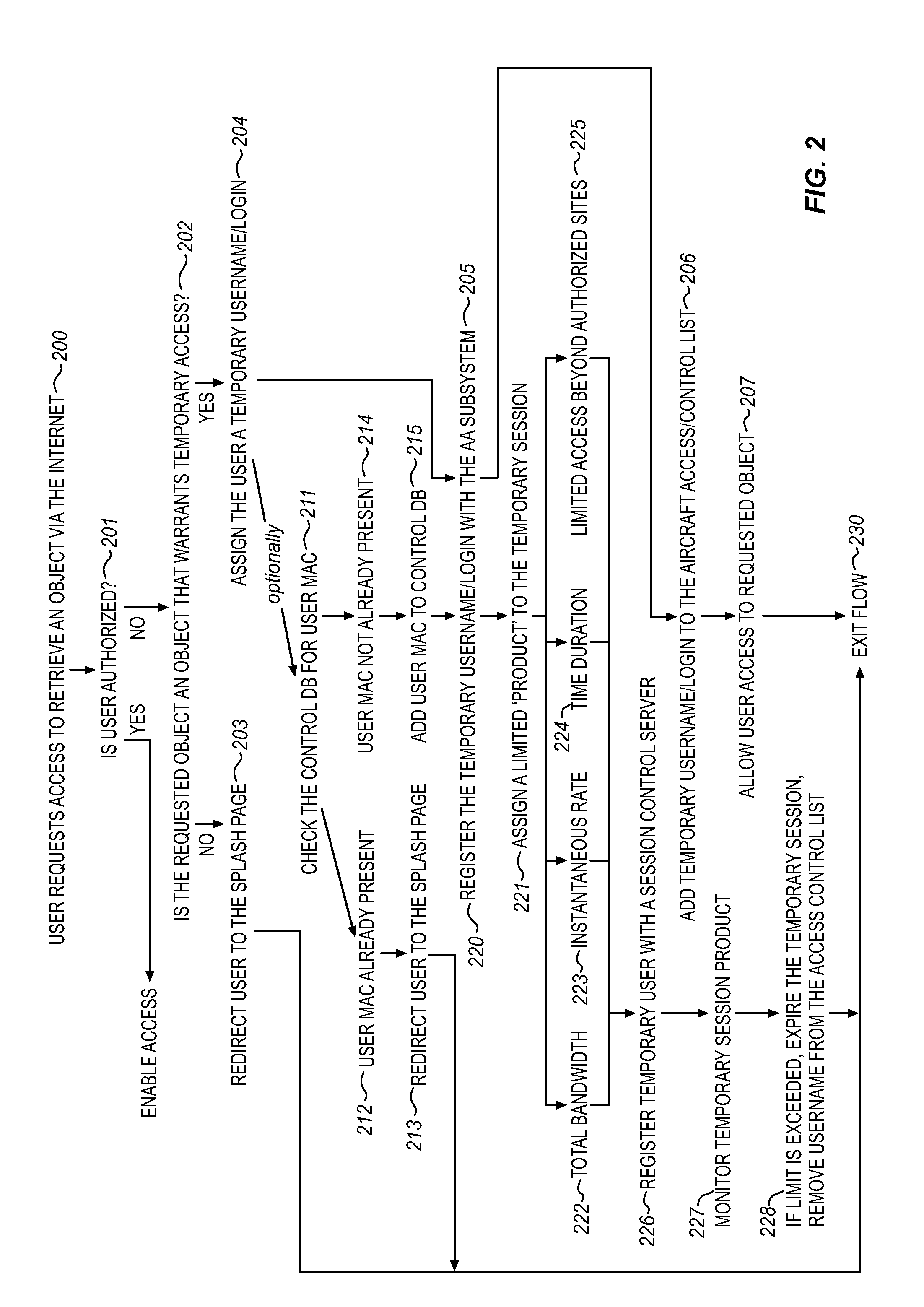
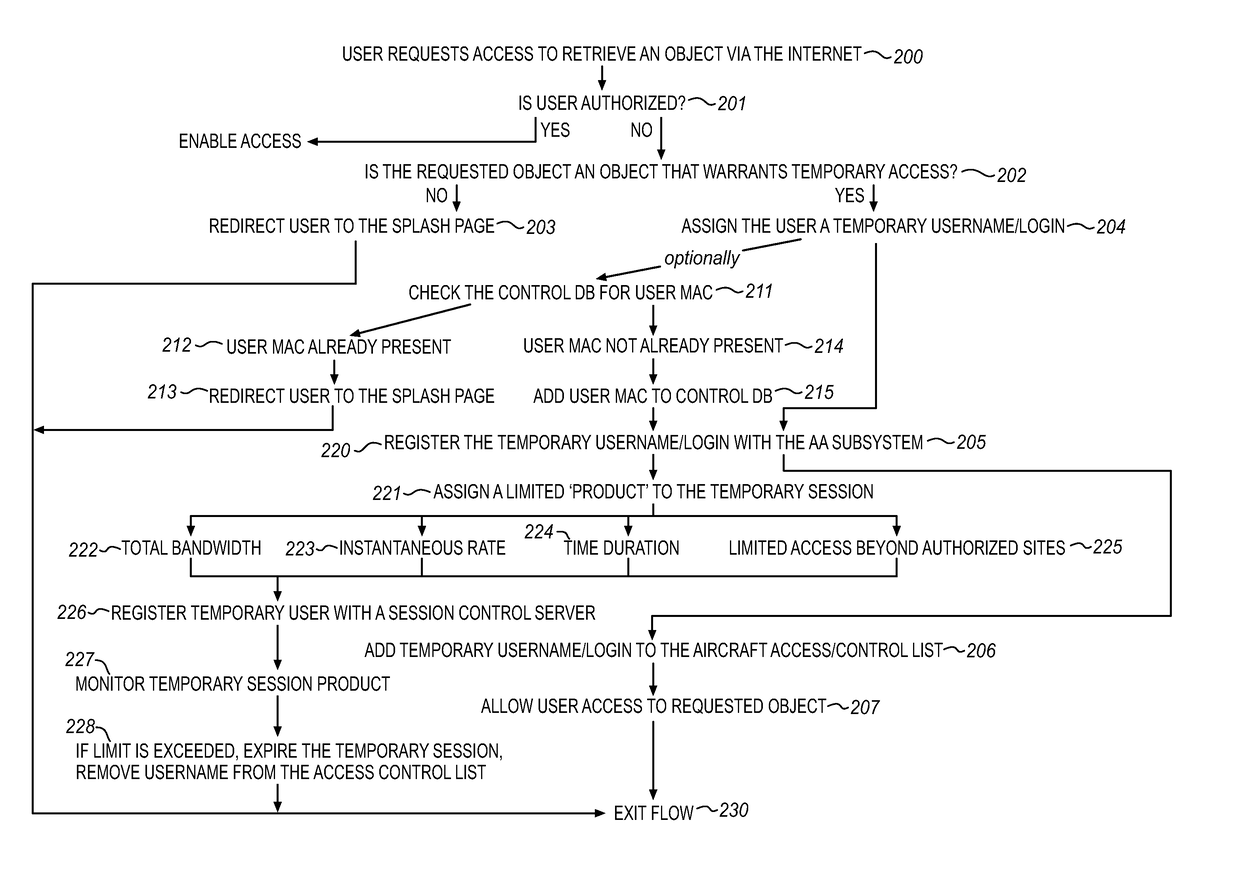
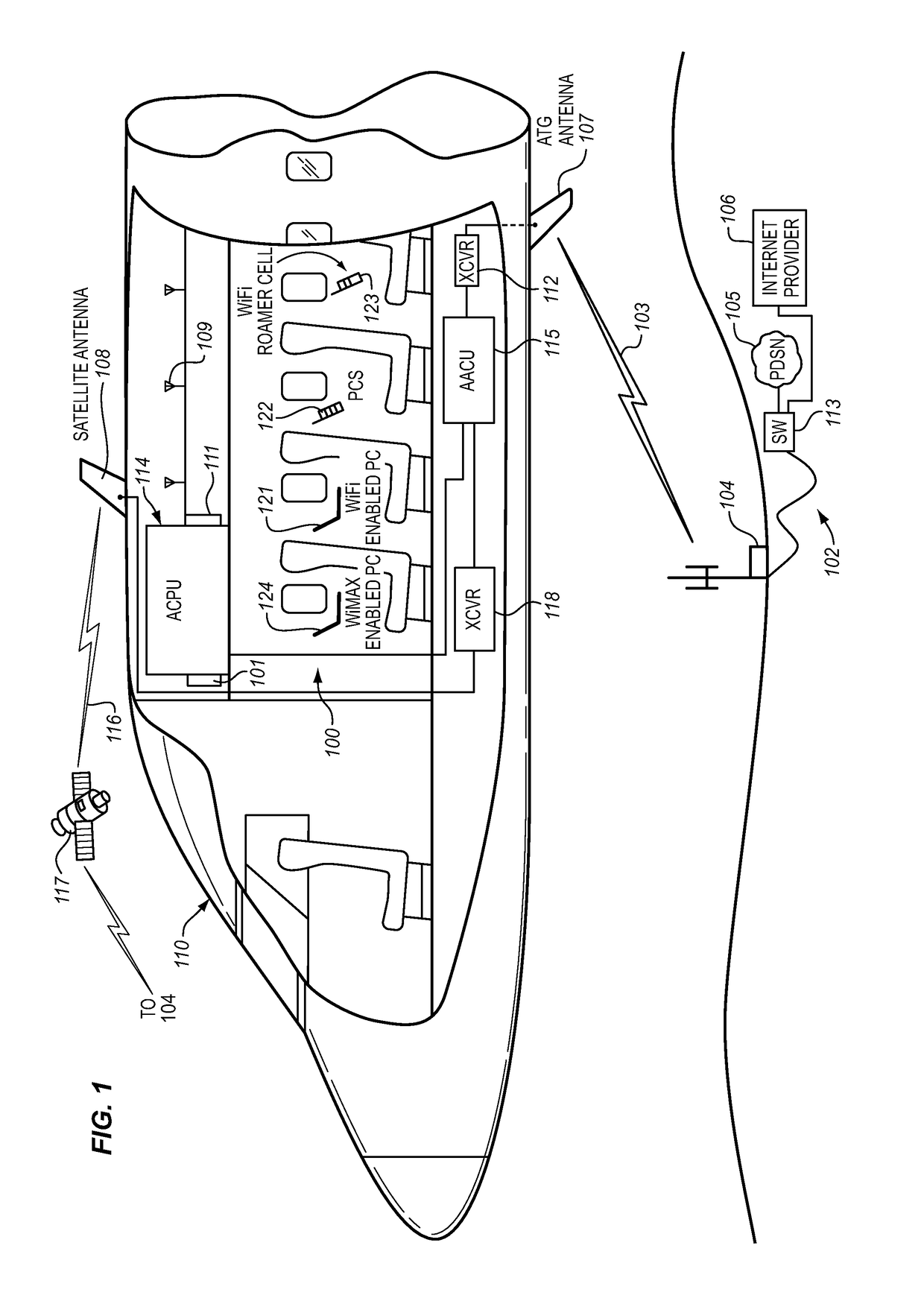
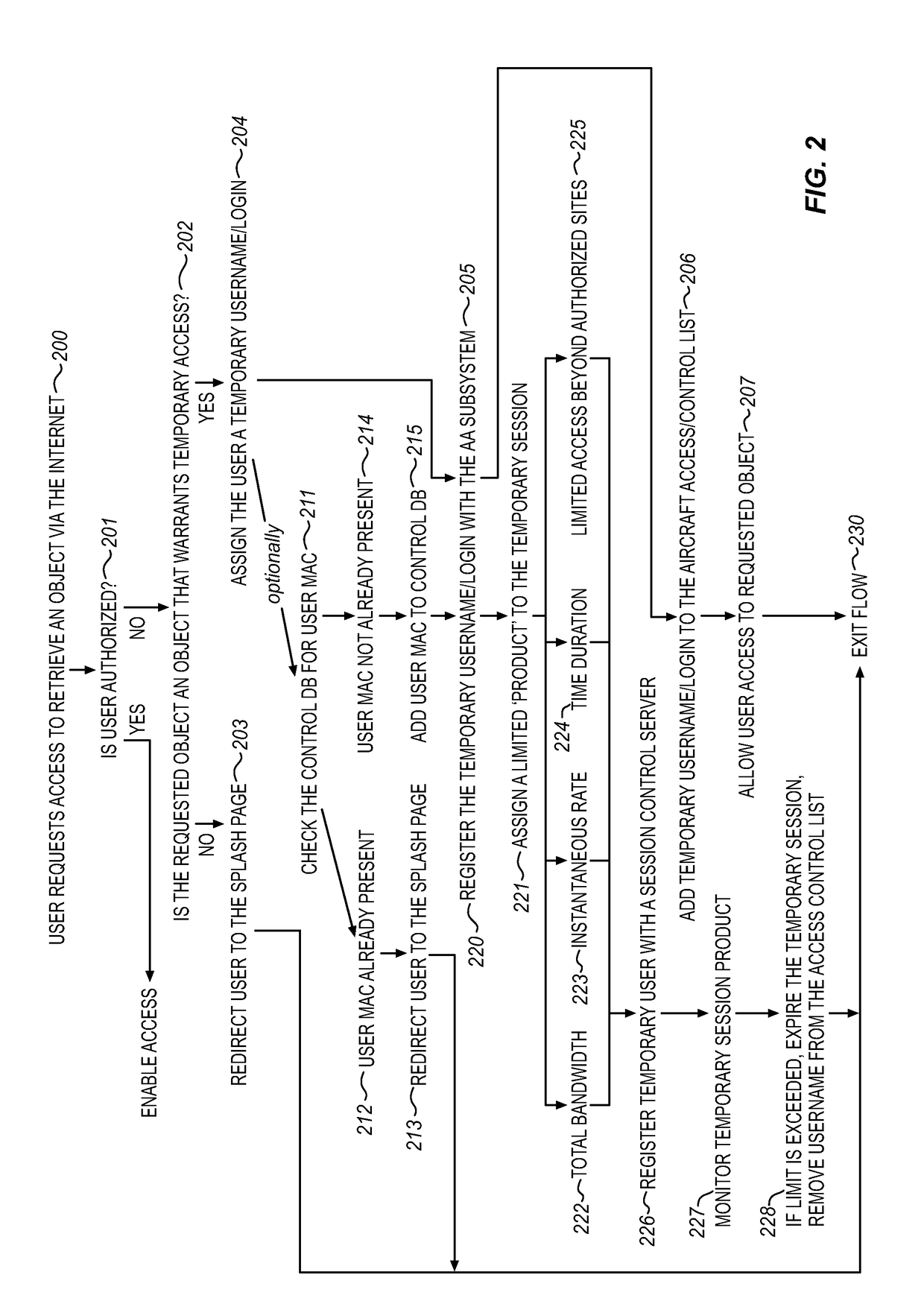
System for providing temporary internet access from a restricted local area network environment
ActiveUS20140053243A1Strict controlOnly be usedDigital data processing detailsConnection managementOn boardCaptive portal
The captive portal environment exists where there is only a single available communication service that is available to the user. An example of a captive portal environment is on board an aircraft in flight, where the passengers have no access to any communication services, other than the aircraft resident wireless Local Area Network. The Restricted LAN Internet Access System functions in the aircraft to grant the user a temporary Internet session so they can download a prerequisite application from the Internet to make use of an application / service resident on the Restricted LAN in the aircraft.
Owner:GOGO BUSINESS AVIATION LLC
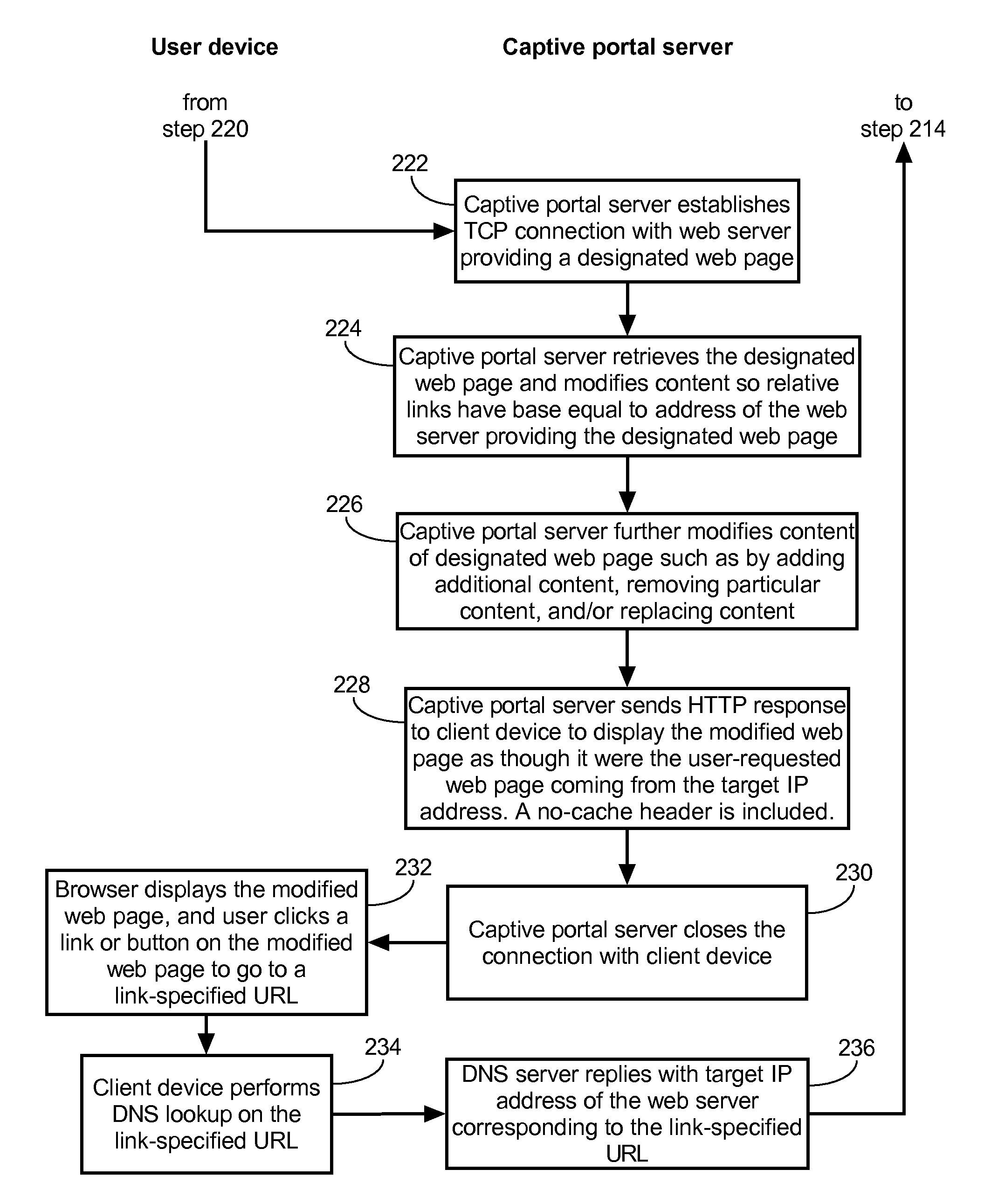
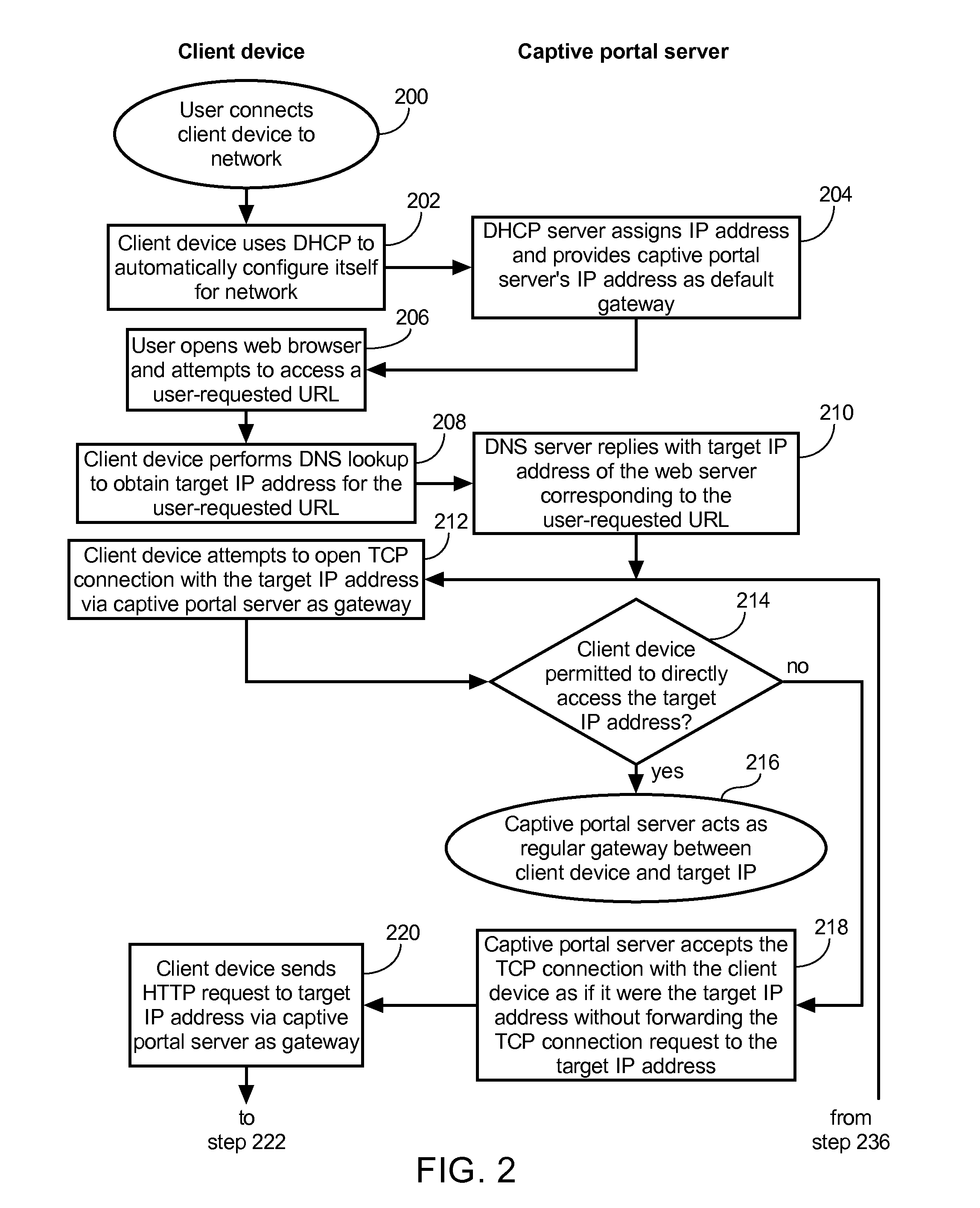
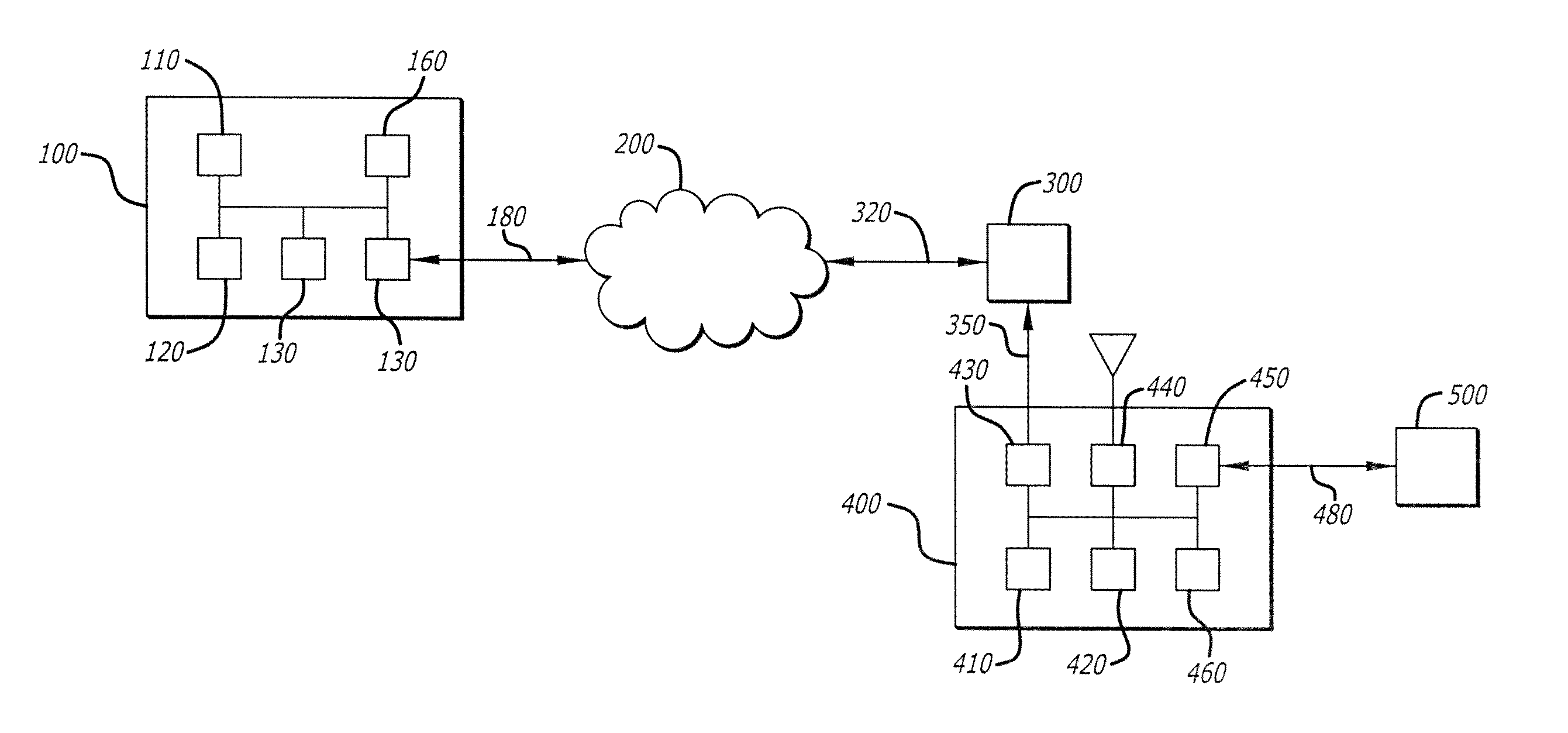
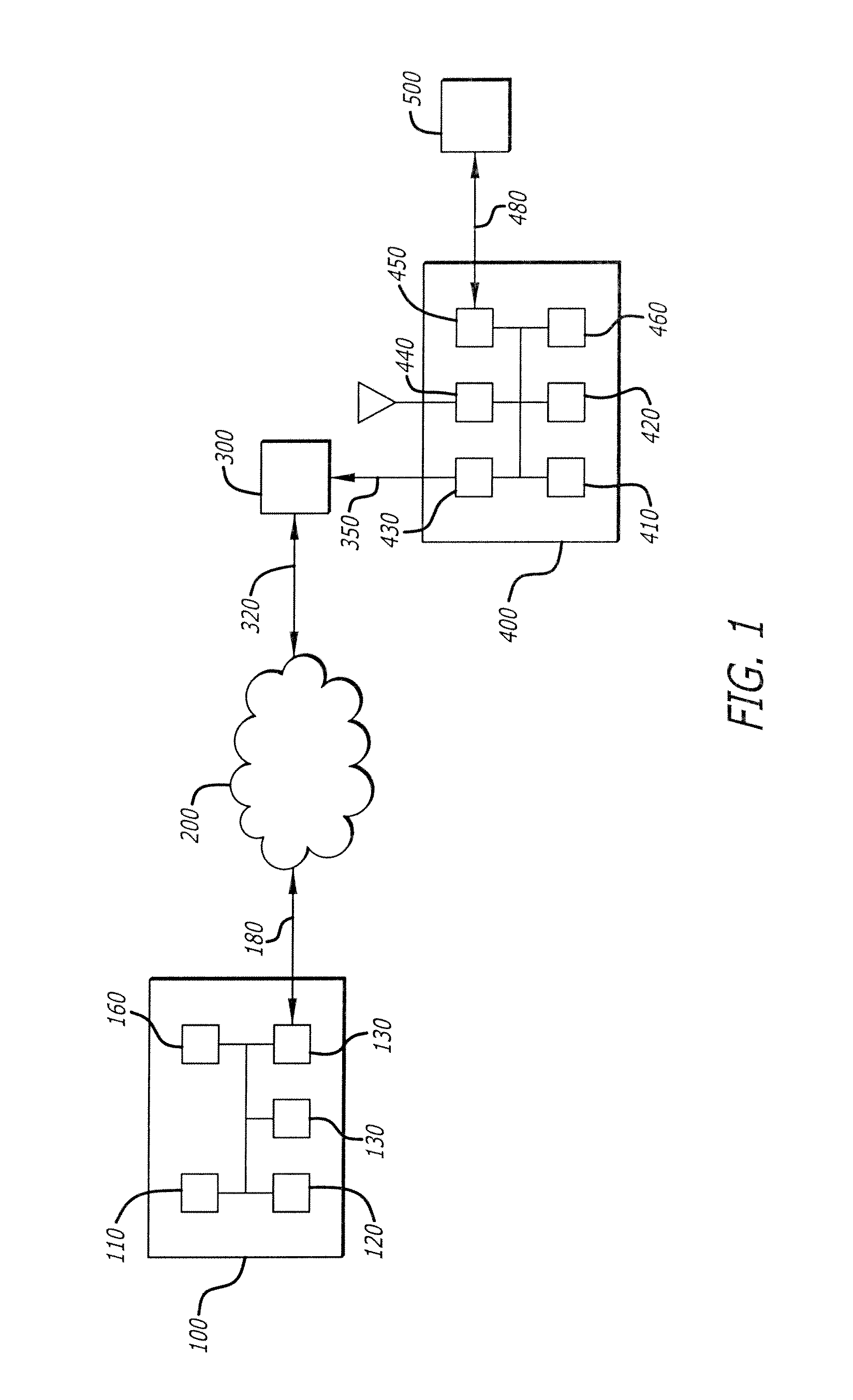
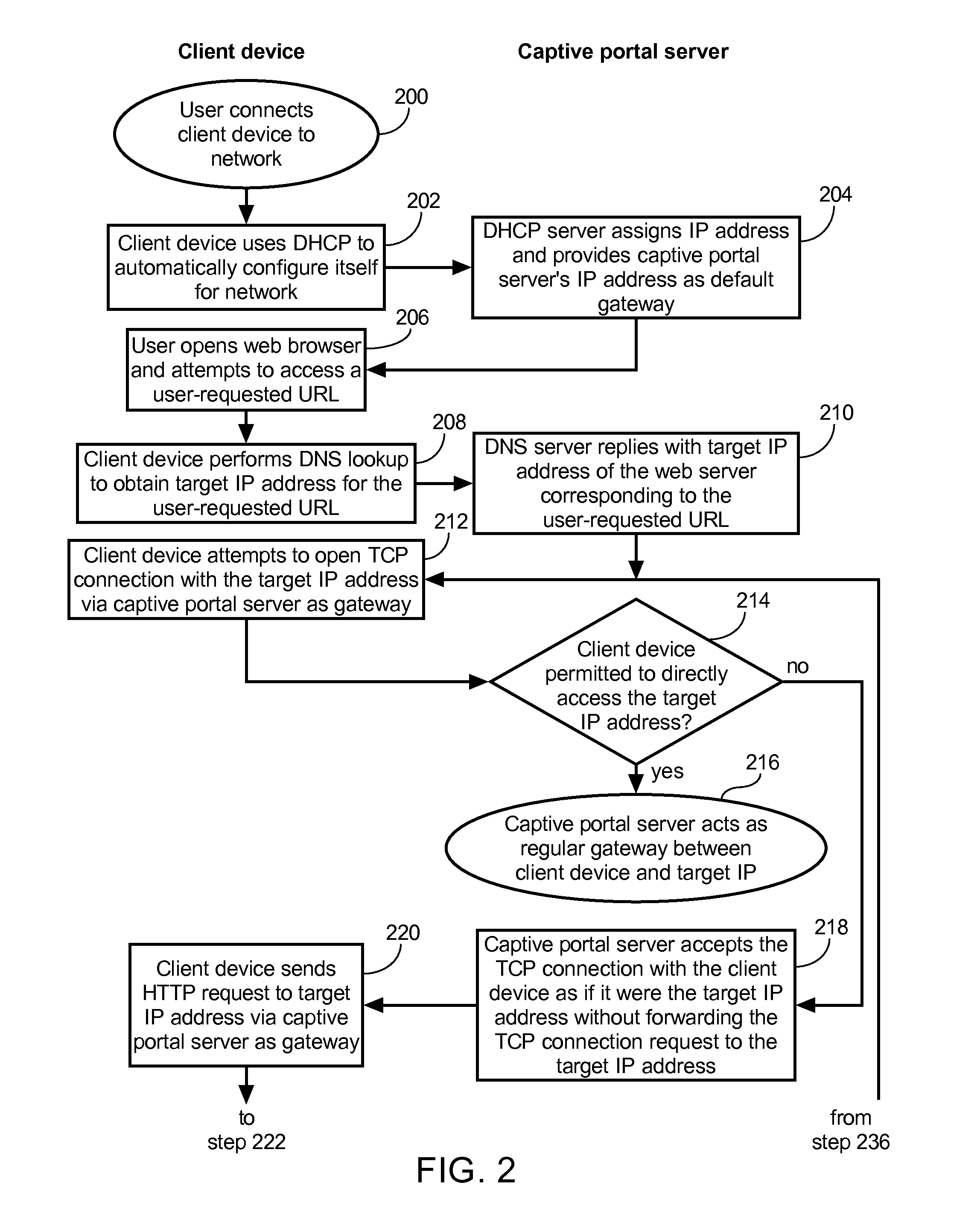
Method of causing a client device to display a designated web page and captive portal server thereof
ActiveUS20120246553A1Digital data information retrievalComputer security arrangementsCaptive portalClient-side
A method of causing a client device to display a designated web page includes receiving from the client device a request for a connection to a first web server, accepting the connection with the client device by pretending to be the first web server, and receiving via the connection a hypertext transfer protocol (HTTP) request. The method further includes retrieving content of the designated web page, modifying the content to form modified content having at least some original content of the designated web page preserved, and replying to the client device via the connection with an HTTP response including the modified content.
Owner:GUEST TEK INTERACTIVE ENTERTAINMENT
Ethernet confirming access method
InactiveCN1403952ABandwidth controlEnsure normal communicationData switching networksSpecial data processing applicationsOperational systemAccess method
The Ethernet confirming access method is a wideband access method for computer network. The present invention adopts unique double web page server technology, and performs the access control and bandwidth limitation via the user access list operation. The unique forced entrance guard technology can re-orient the unauthorized user request imperatively. The present invention realizes the conformation, authorization, charge and bandwidth limitation of users via web page confirming process without needing any client end software, and this simplifies the user's operation, is independent with the user's operation platform and can operate simple and practically.
Owner:WUHAN POST & TELECOMM RES INST CO LTD
Method and system for detecting captive portals
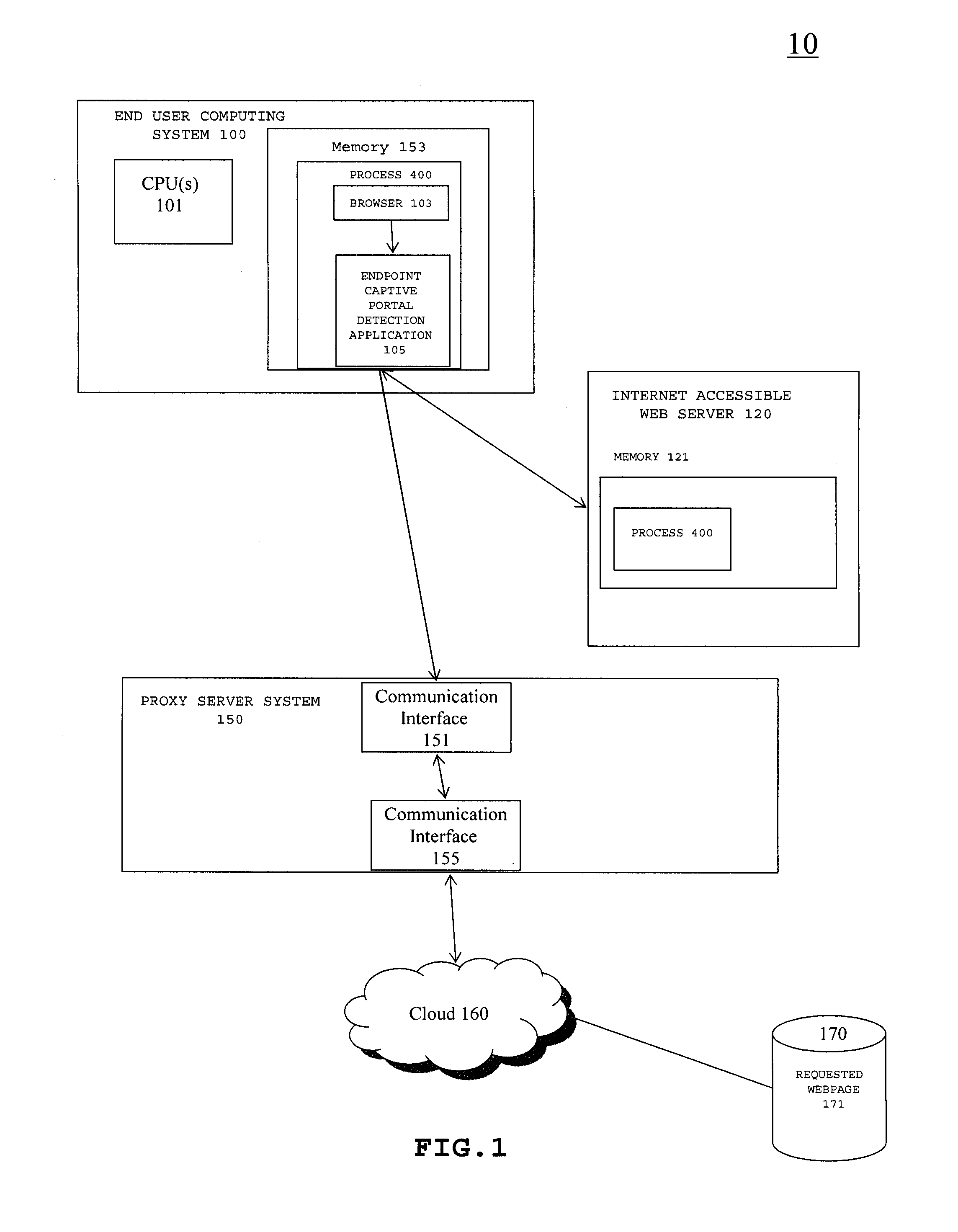
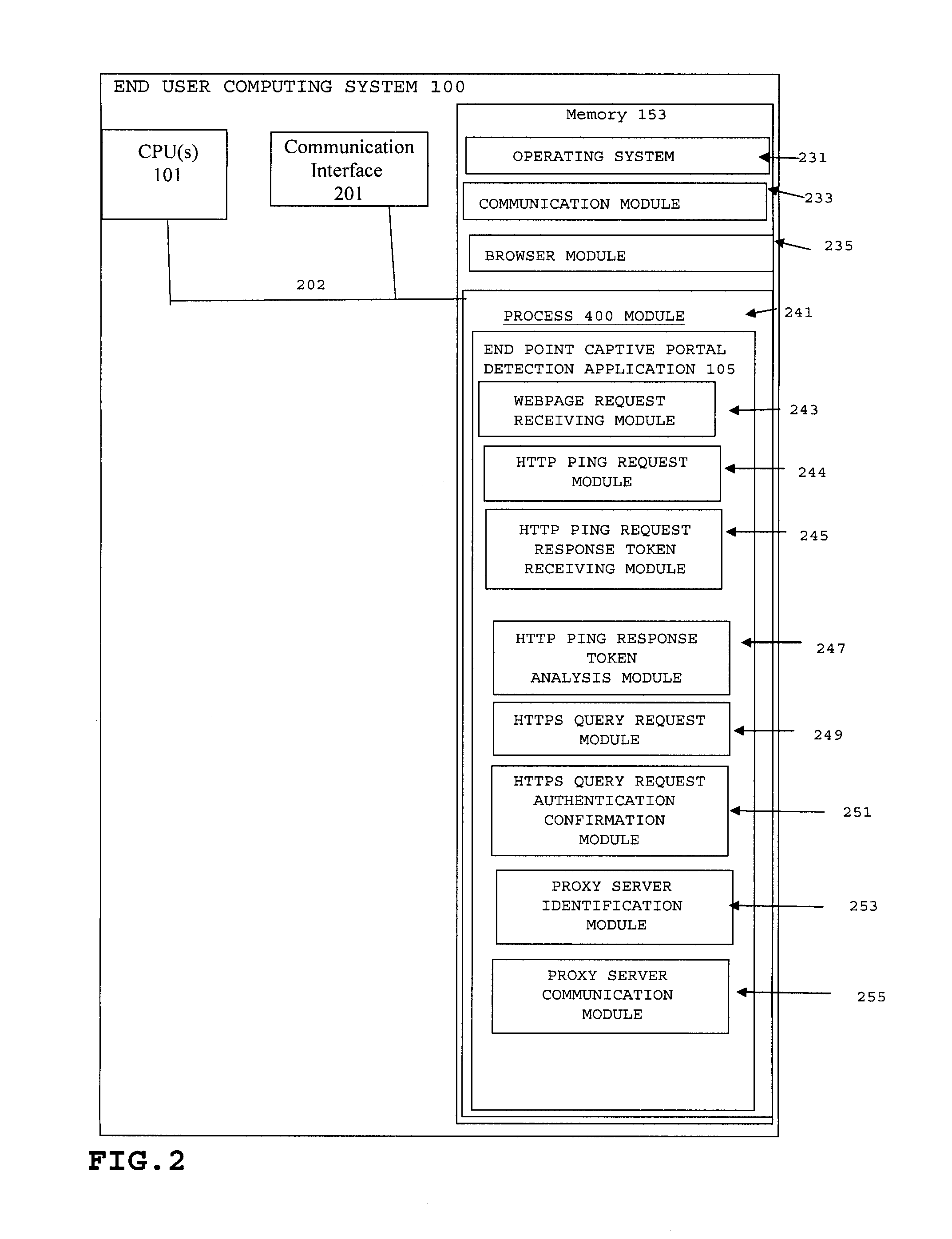
ActiveUS8479263B1Minimal numberFast and efficient and reliable and secureDigital data processing detailsMultiple digital computer combinationsWeb serviceCaptive portal
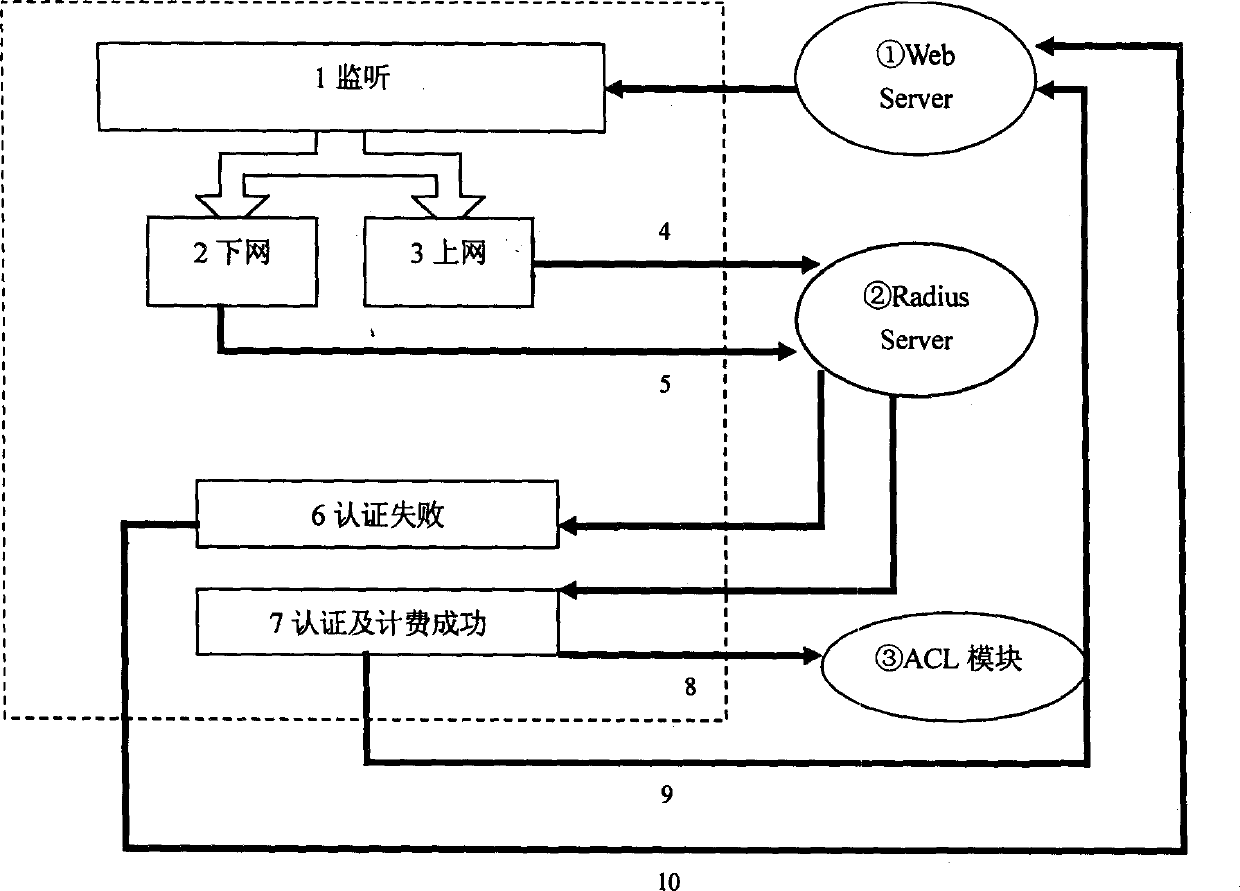
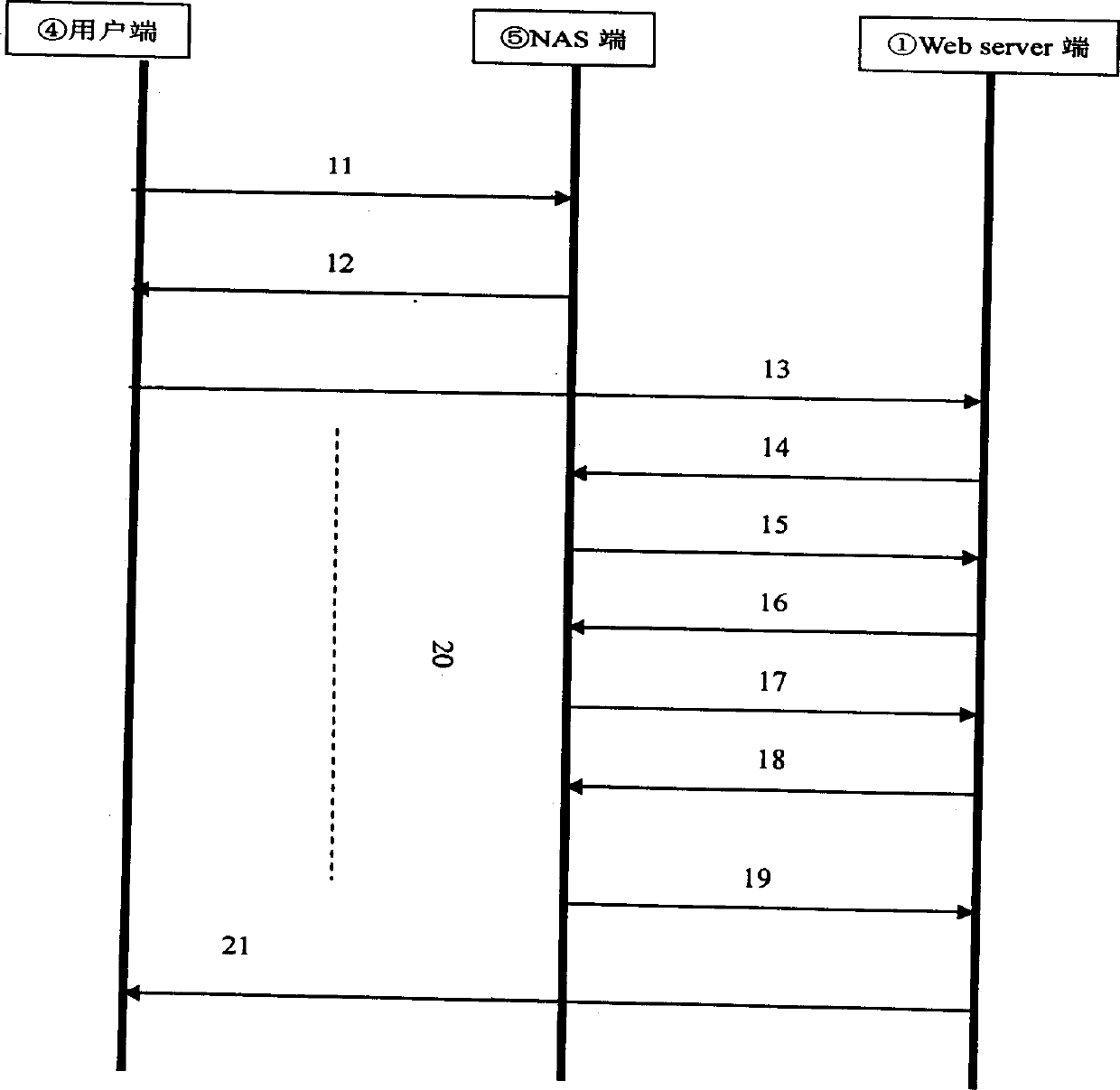
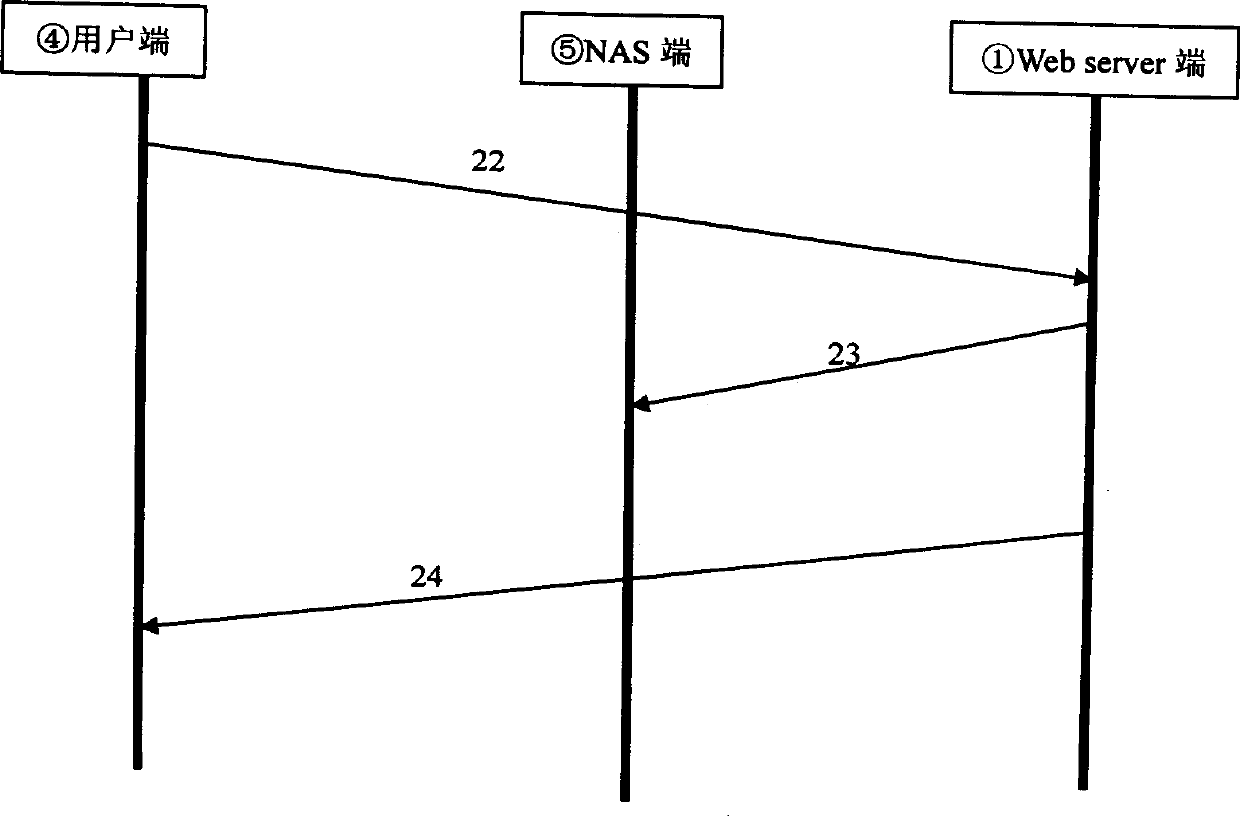
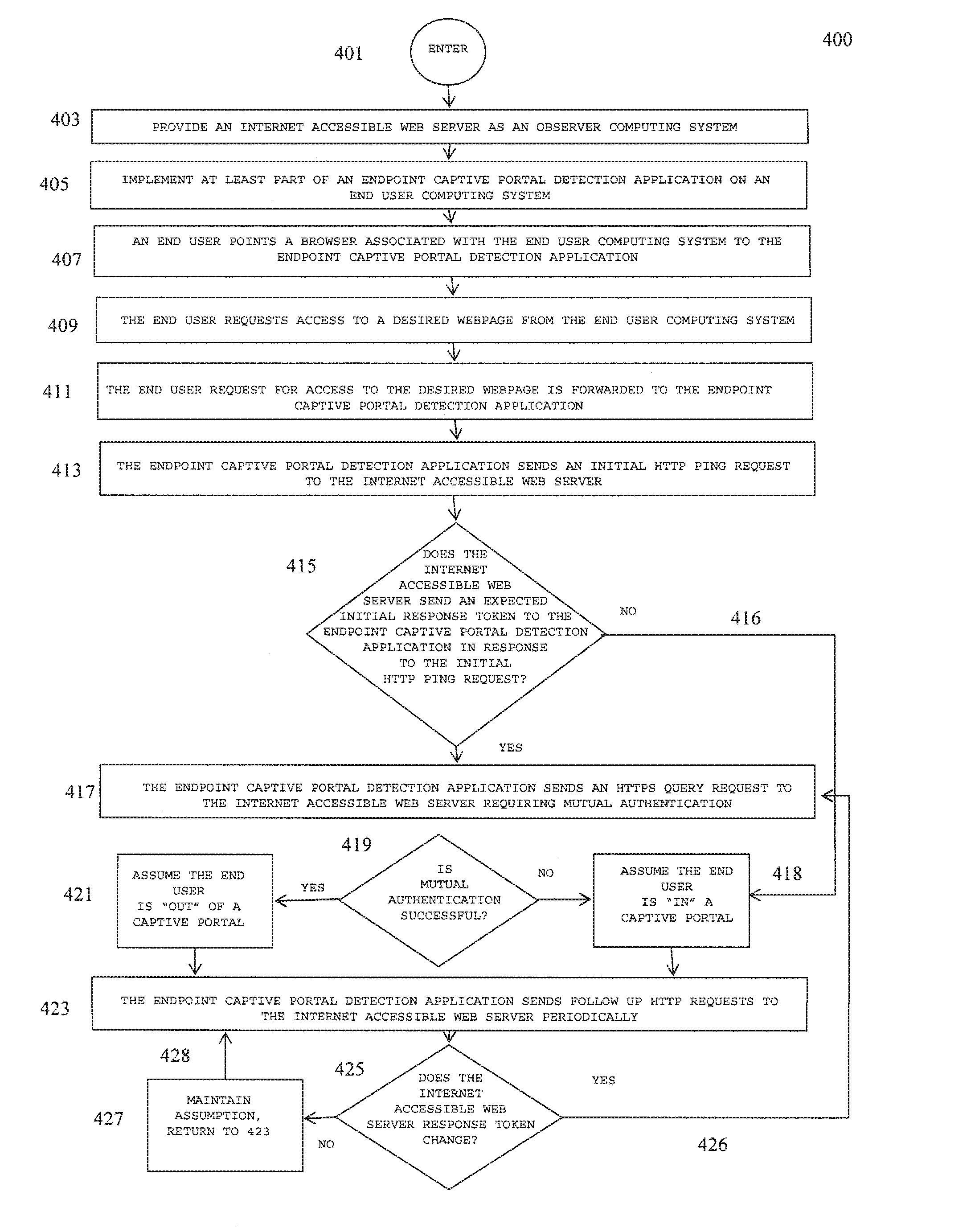
A method and system for detecting captive portals includes a two phase captive portal detection process whereby an initial HTTP ping request is sent from the endpoint captive portal detection application on an end user computing system to an Internet accessible web server. The Internet accessible web server is expected to return an initial response token to the endpoint captive portal detection application in response to the initial HTTP ping request and if the expected initial response token is received, an initial HTTPS query request is then sent together with the returned initial response token that requires server / client mutual authentication. If mutual authentication is accomplished, then it is determined that the user is not in a captive portal. Follow up HTTP ping requests are then periodically generated by the endpoint captive portal detection application and if the responses to the follow up HTTP ping requests do not change, i.e., the token does not change, no new HTTPS query request is sent.
Owner:GEN DIGITAL INC
Scalable captive portal redirect
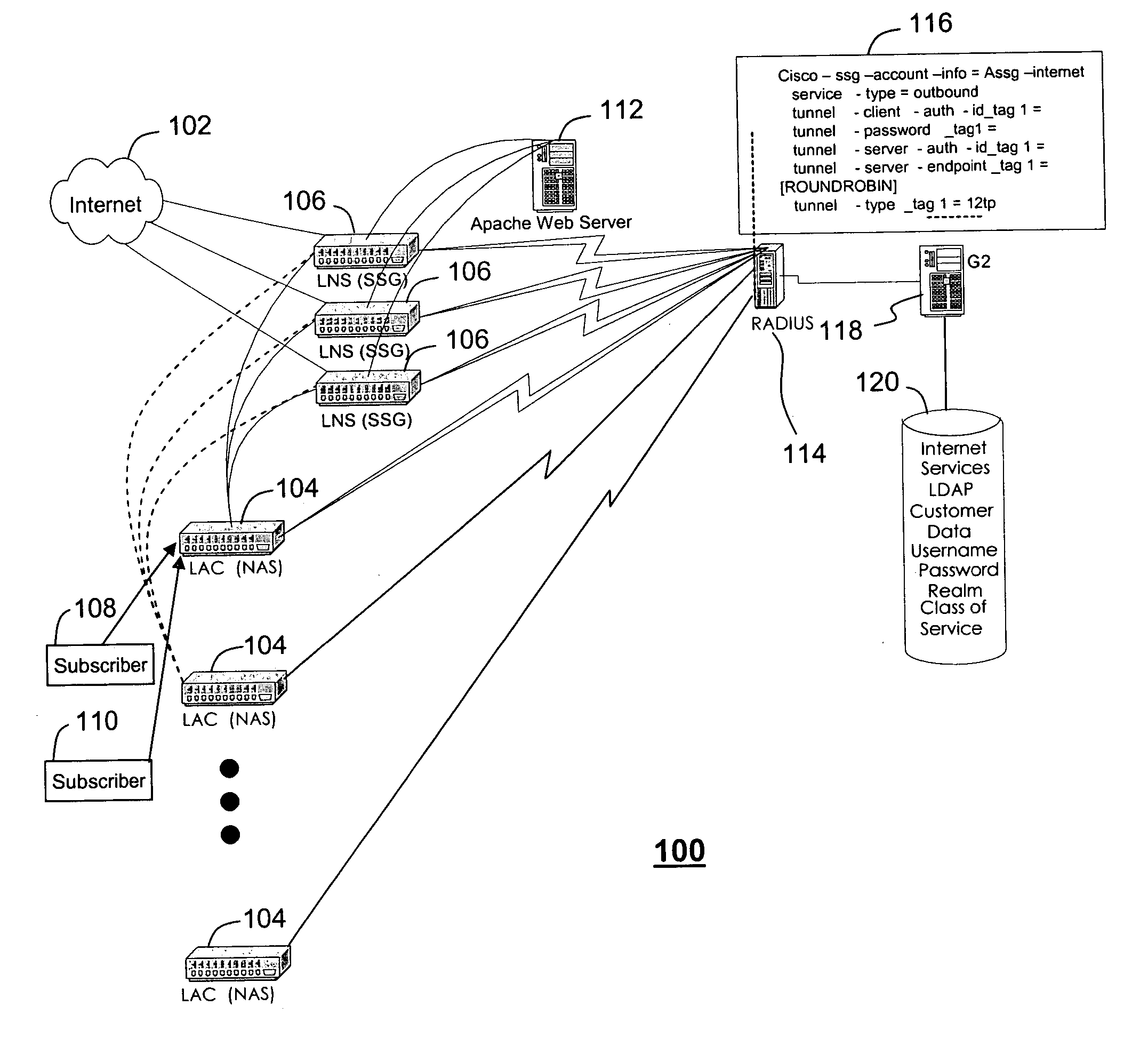
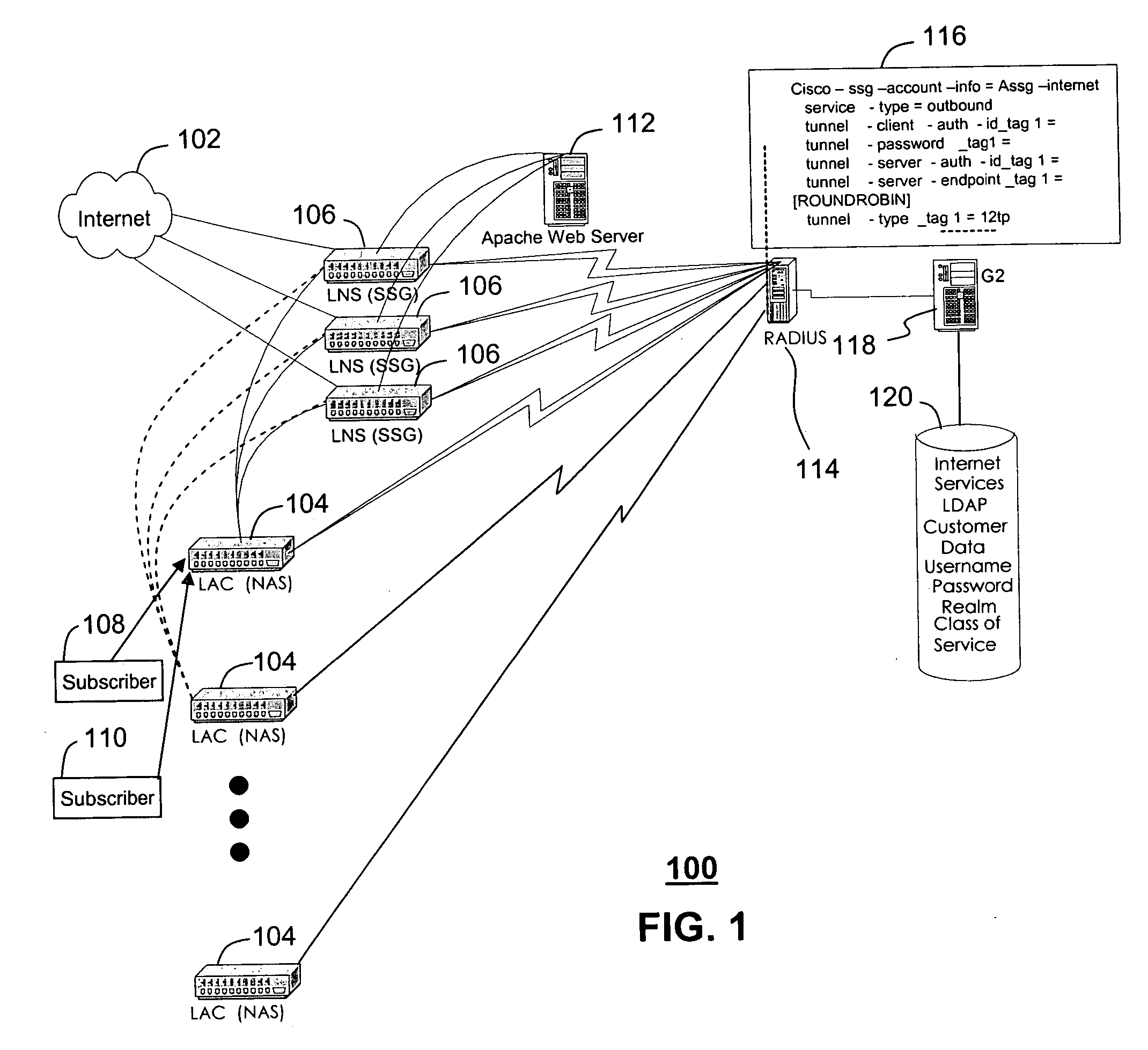
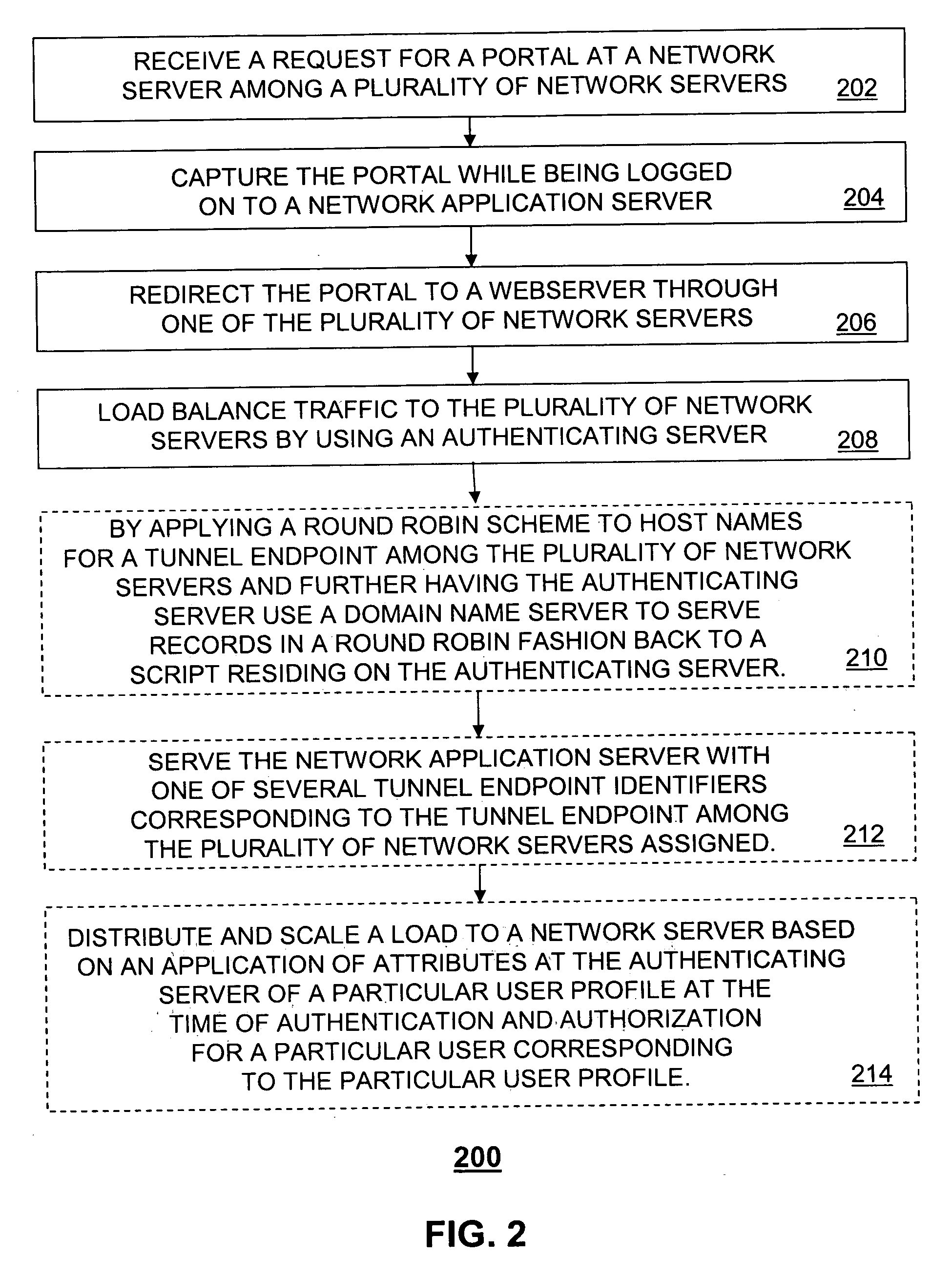
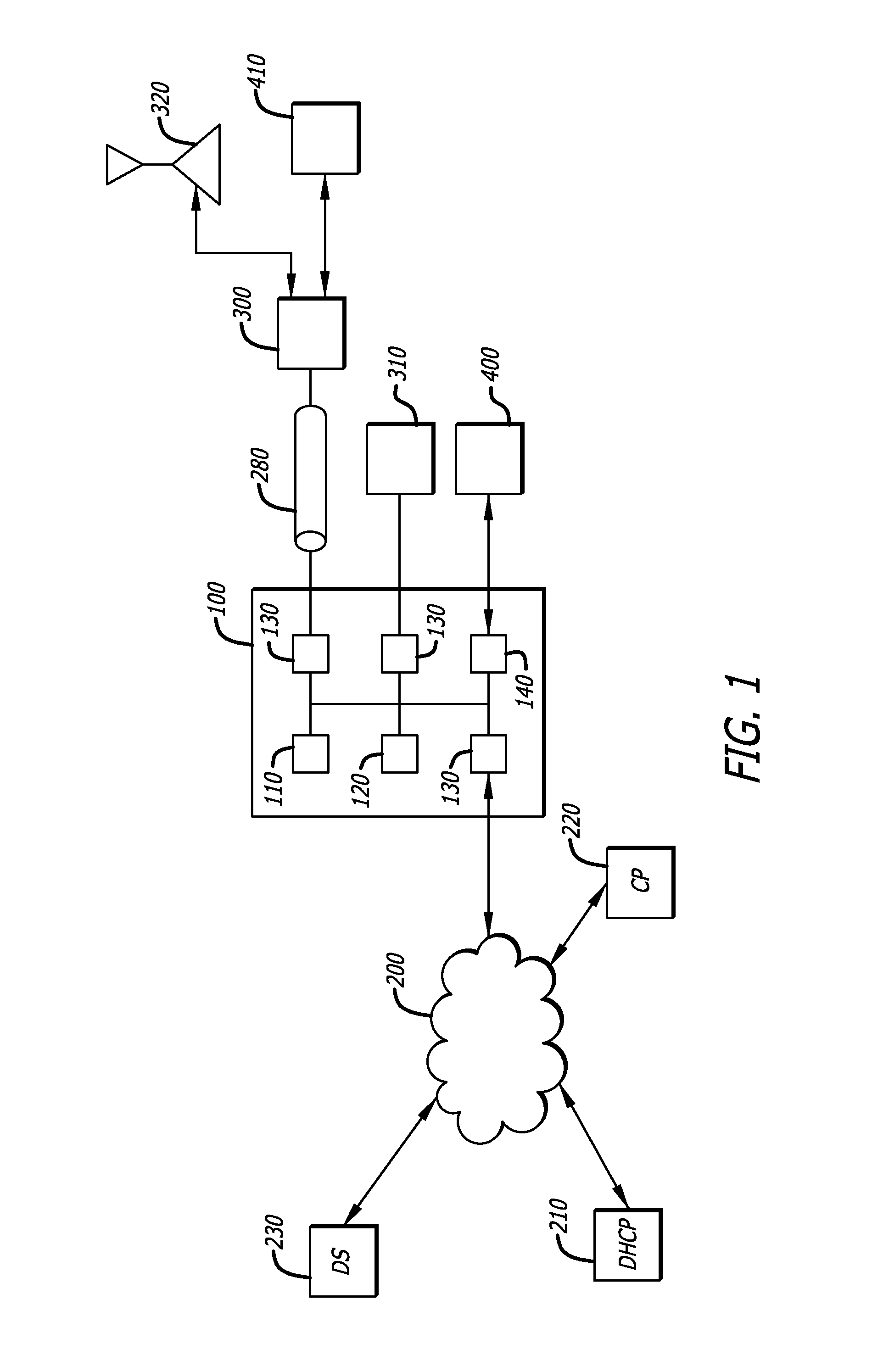
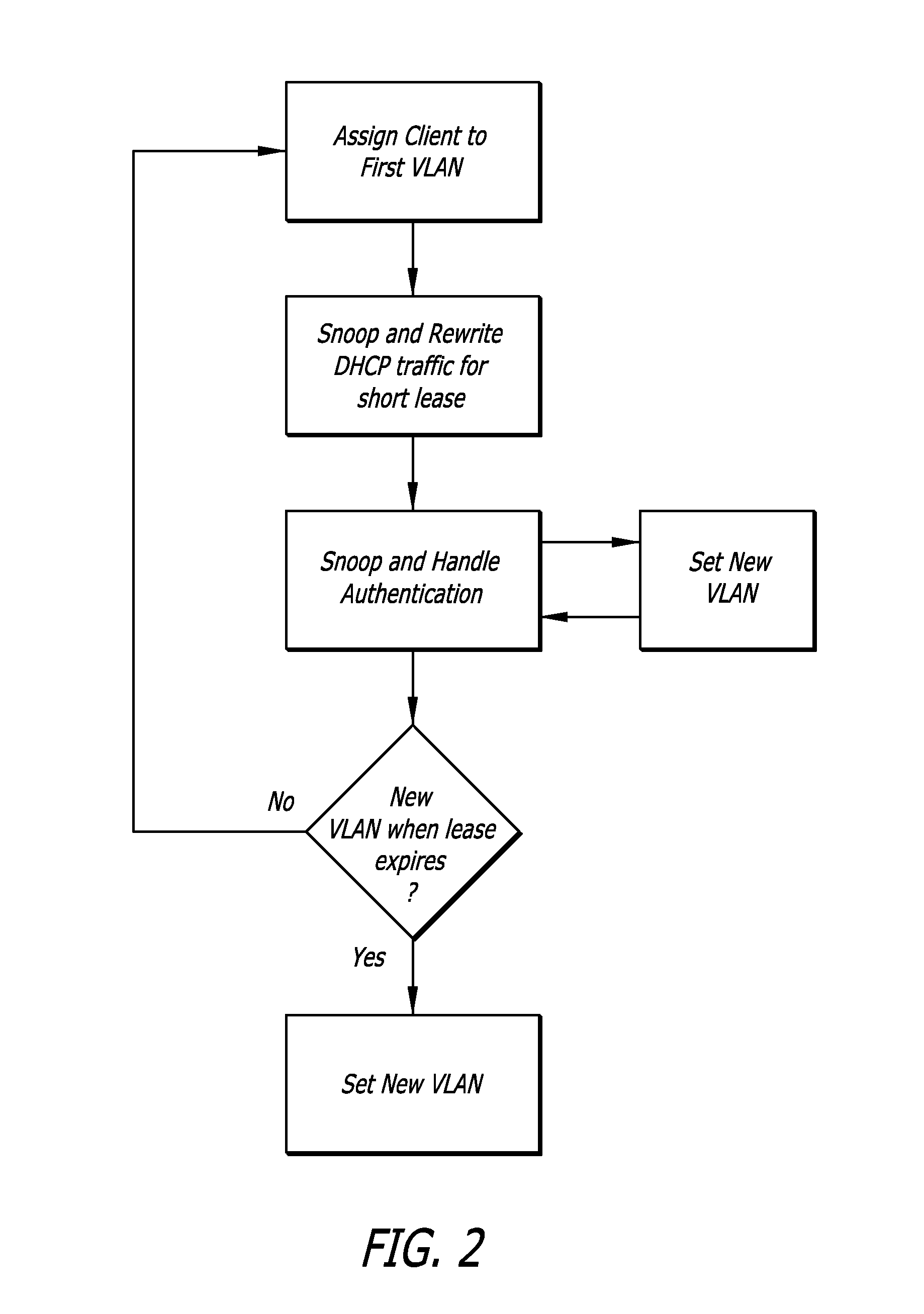
A system (100) and method (200) are disclosed for scalable captive portal and re-direct. A system that incorporates teachings of the present disclosure may include, for example, an authenticating server (114) having a controller (302) that manages operations of network application server (104) and a plurality of network routers (106). The controller can be programmed to receive a request for authenticating or authorizing a user (108, 110) via one of the plurality of network routers, authenticate or authorize the user when received authentication or authorization information matches stored information (120), and instruct the network application server to route traffic via one among the plurality of network routers to a captured portal at a webserver (112). The controller can be further programmed to capture (204) a portal during the authenticating or authorizing step and to load balance (208) traffic to the plurality of network routers. Additional embodiments are disclosed.
Owner:SBC KNOWLEDGE VENTURES LP
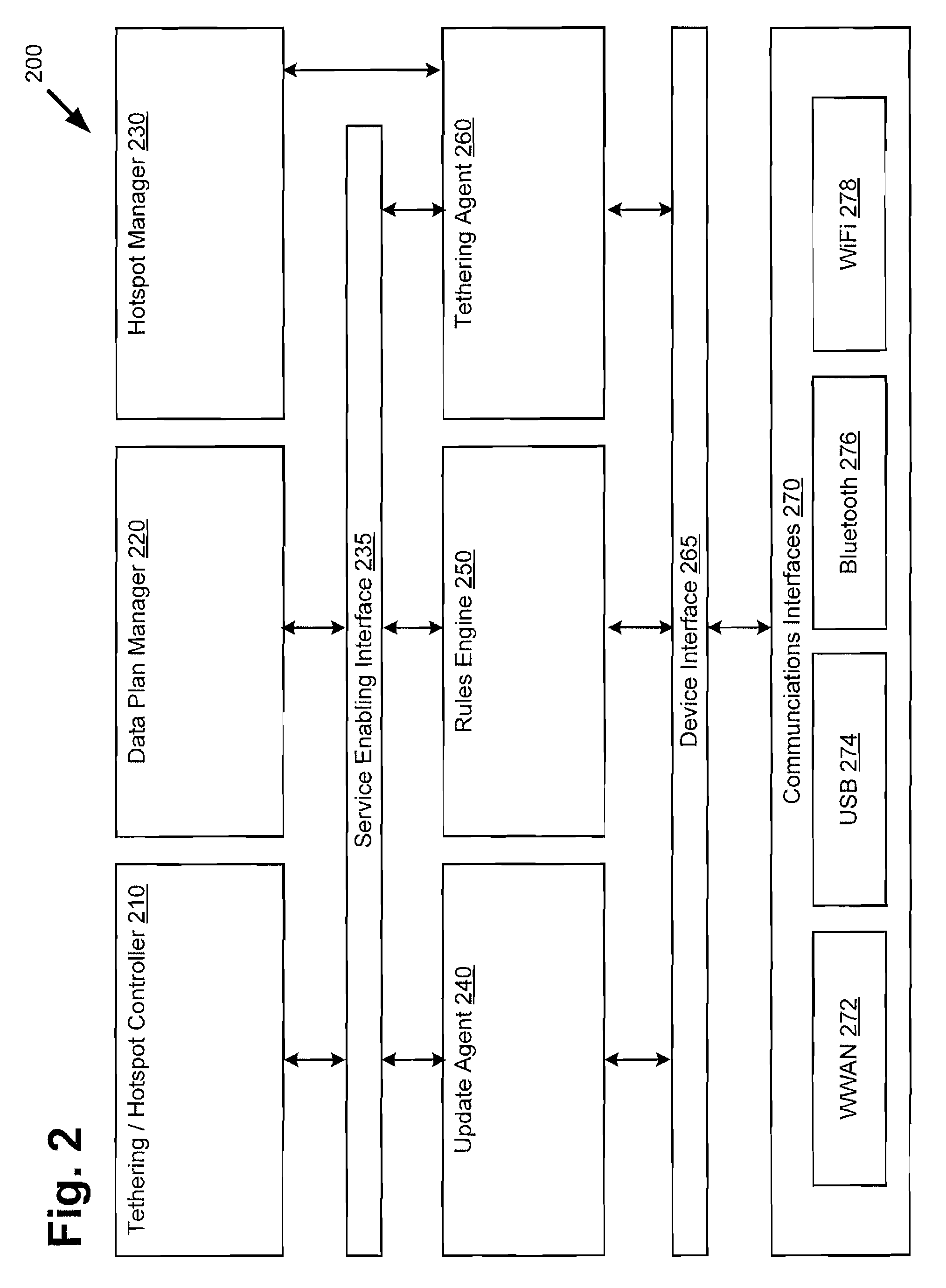
Managing tethered data traffic over a hotspot network
ActiveUS8943554B2Service provisioningDigital data processing detailsCaptive portalNetwork management
Presented is a system and method for controlling access to a mobile hotspot on a mobile device utilizing a hotspot management application. The method includes detecting unauthorized data traffic over a tethered link between the mobile device and a tethered device by analyzing a signature of the unauthorized data traffic. Analyzing the signature of the unauthorized data traffic may be carried out utilizing a rules engine, where the rules engine is based on one or more carrier controlled tethering policies and one or more user controlled tethering policies. Detecting unauthorized data traffic may further include detecting an unauthorized tethering application on the mobile device utilizing a database of known unauthorized tethering applications. The method further includes controlling the unauthorized data traffic. The method additionally includes redirecting a user of the mobile device to a captive portal for authorized tethering plan support.
Owner:SMITH MICRO SOFTWARE INC
Authorizing Remote Access Points
ActiveUS20110252237A1Digital data processing detailsUser identity/authority verificationIp addressPassword
Authorizing remote access points for use in a network: A remote access point contains identity information established during manufacturing; this identity information may be in the nature of a digital certificate which can be used to establish a secure connection between networked entities. After the remote access point is provisioned to communicate securely to a controller using its TCP / IP address provided by a user, the remote access point is put into an un-authorized state by the controller pending further authorization. The user is presented with a secure captive portal page authenticating the end-user. This authorization may be through entering a user name and password, through presenting a certificate, through two-factor methods, or other methods known to the art. User's authentication credentials are verified by the controller. Optionally this verification can be performed using a per-user certificate. After the remote access point has been authorized, the controller marks it verified as a fully functional node, and saves this state. The user performing the authorization is associated with the remote access point, and may be used to monitor the usage and potentially revoke the authorization. The remote access point is provisioned with the current provisioning parameters for the remote access point as configured by the IT administrator for the end user, so that each remote access point can have unique per-user configuration applied.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
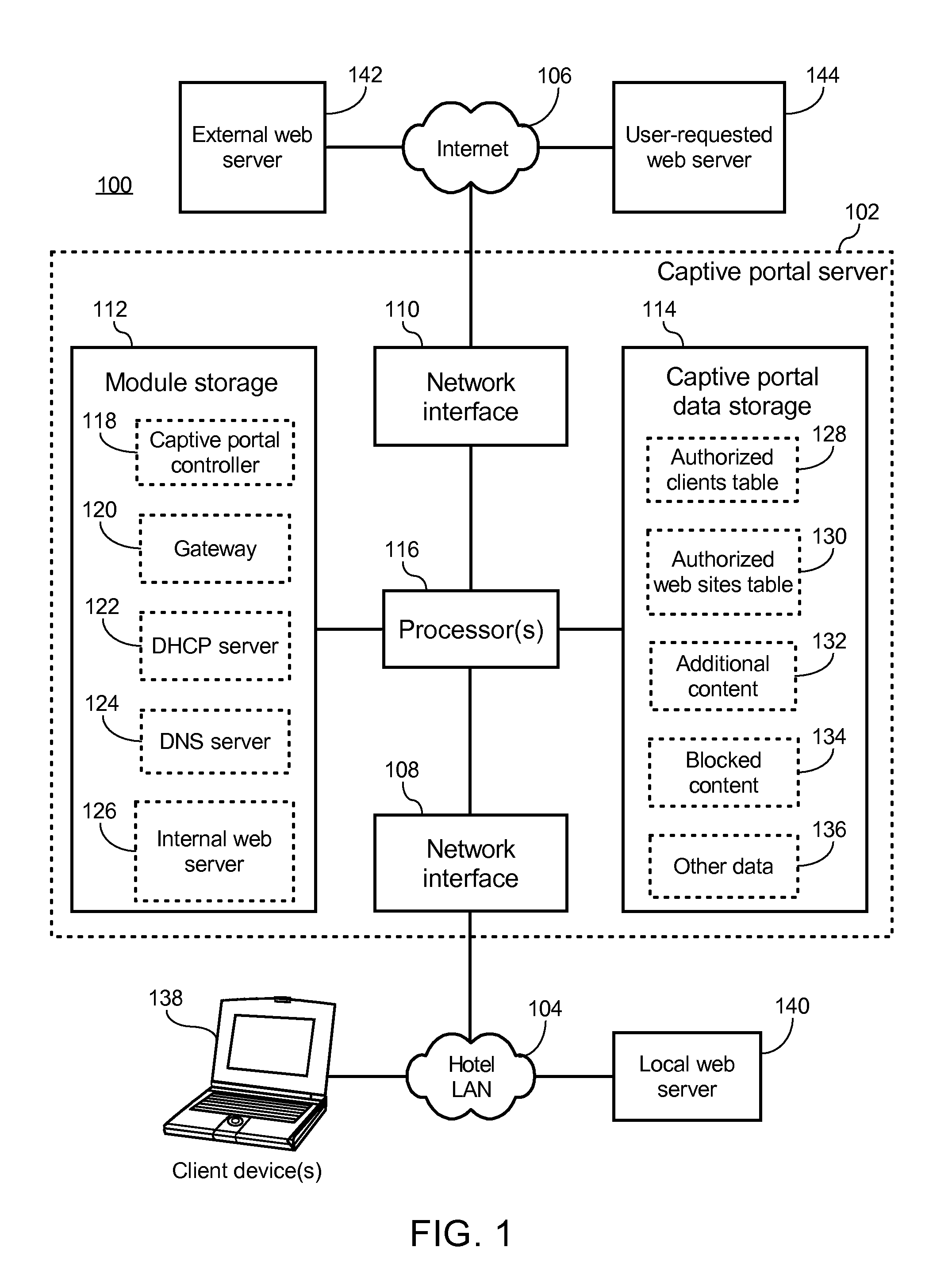
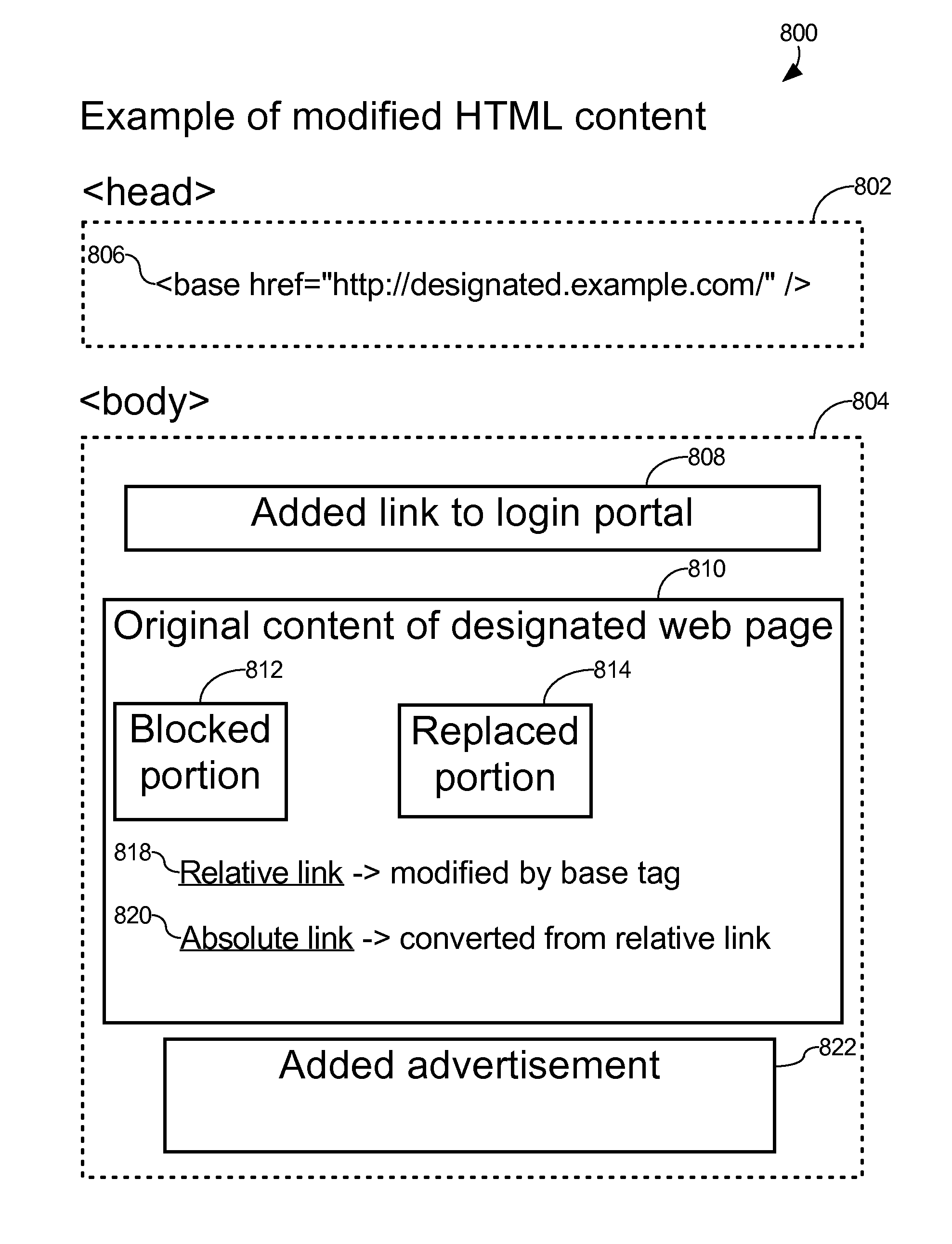
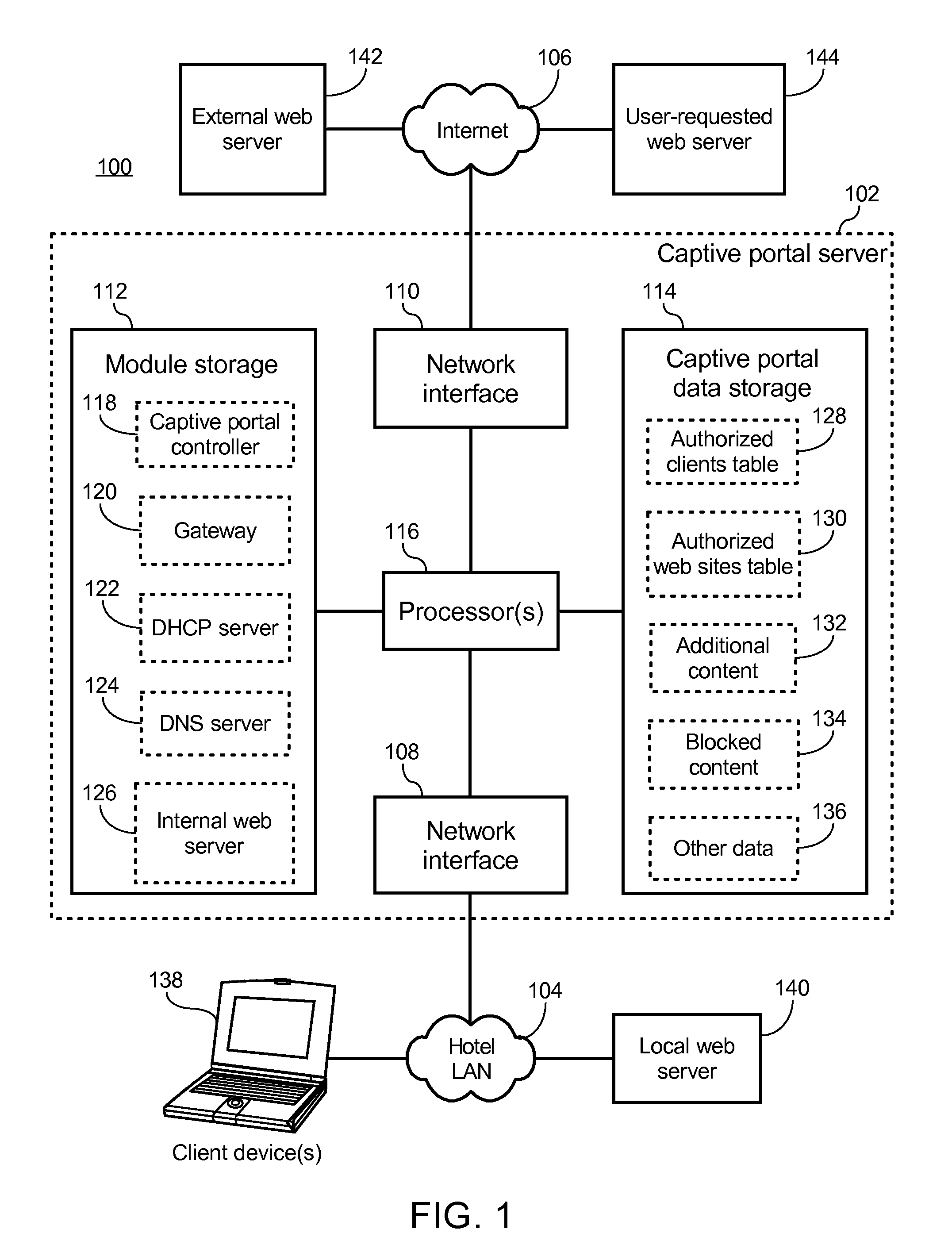
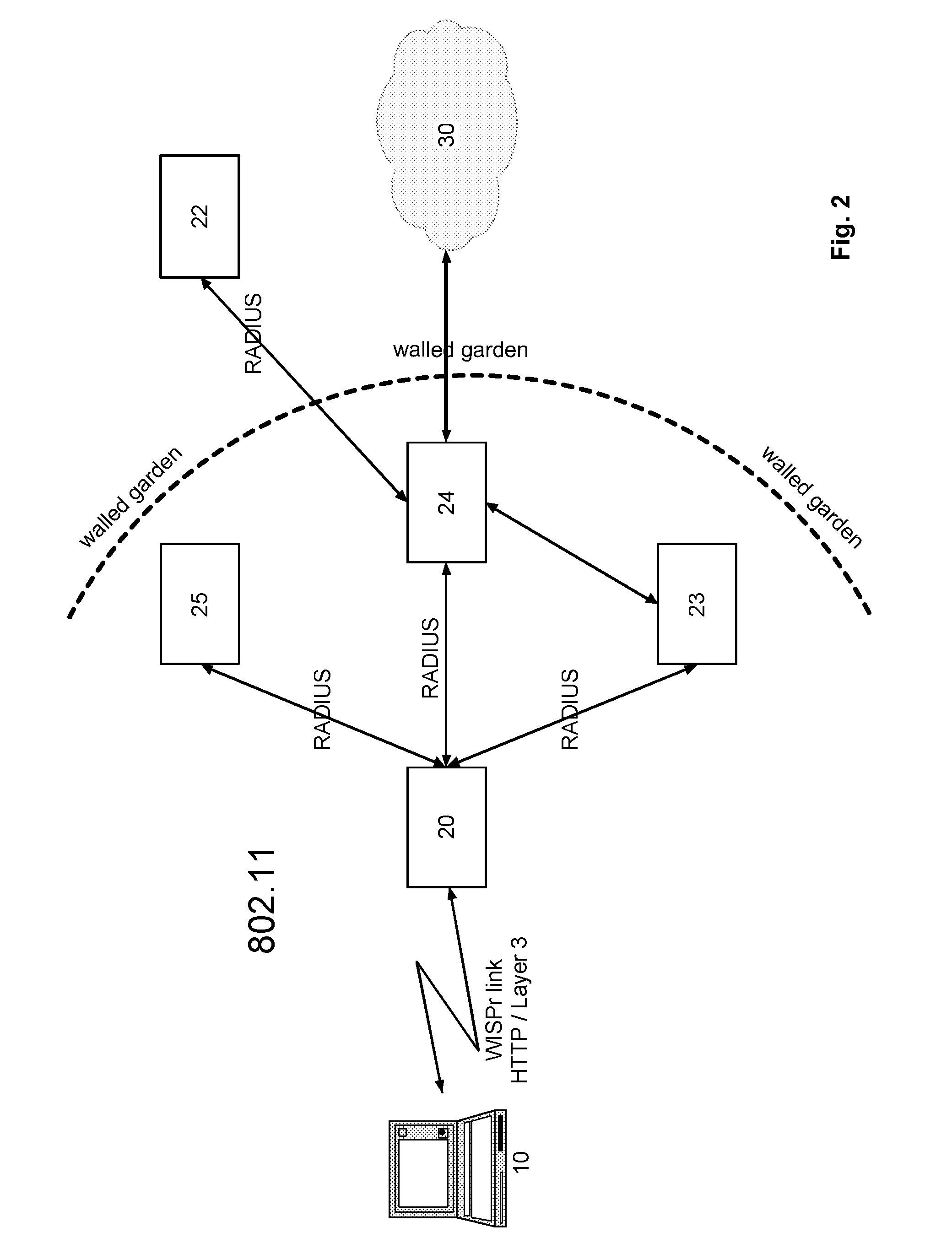
Captive portal that modifies content retrieved from designated web page to specify base domain for relative link and sends to client in response to request from client for unauthorized web page
ActiveUS8650495B2Digital data information retrievalComputer security arrangementsWeb browserWeb service
The described captive portal techniques cause client devices to render and display designated web pages. One designated web page may be different than a requested web page such as when a client is not authorized to access the requested page and is instead caused to display a login portal. The captive portal may modify the designated web page to ensure that relative links lacking base domains now have specified base domains pointing to an authorized web server. The modified content is sent from the captive portal to the client device for display. Client web browser security measures related to redirection messages are thereby bypassed and load on the captive portal is minimal. Another designated web page may be the same as the requested web page such as when the requested page is an authorized page even for non-logged in clients. Authorized pages may be modified to add a login link.
Owner:GUEST TEK INTERACTIVE ENTERTAINMENT
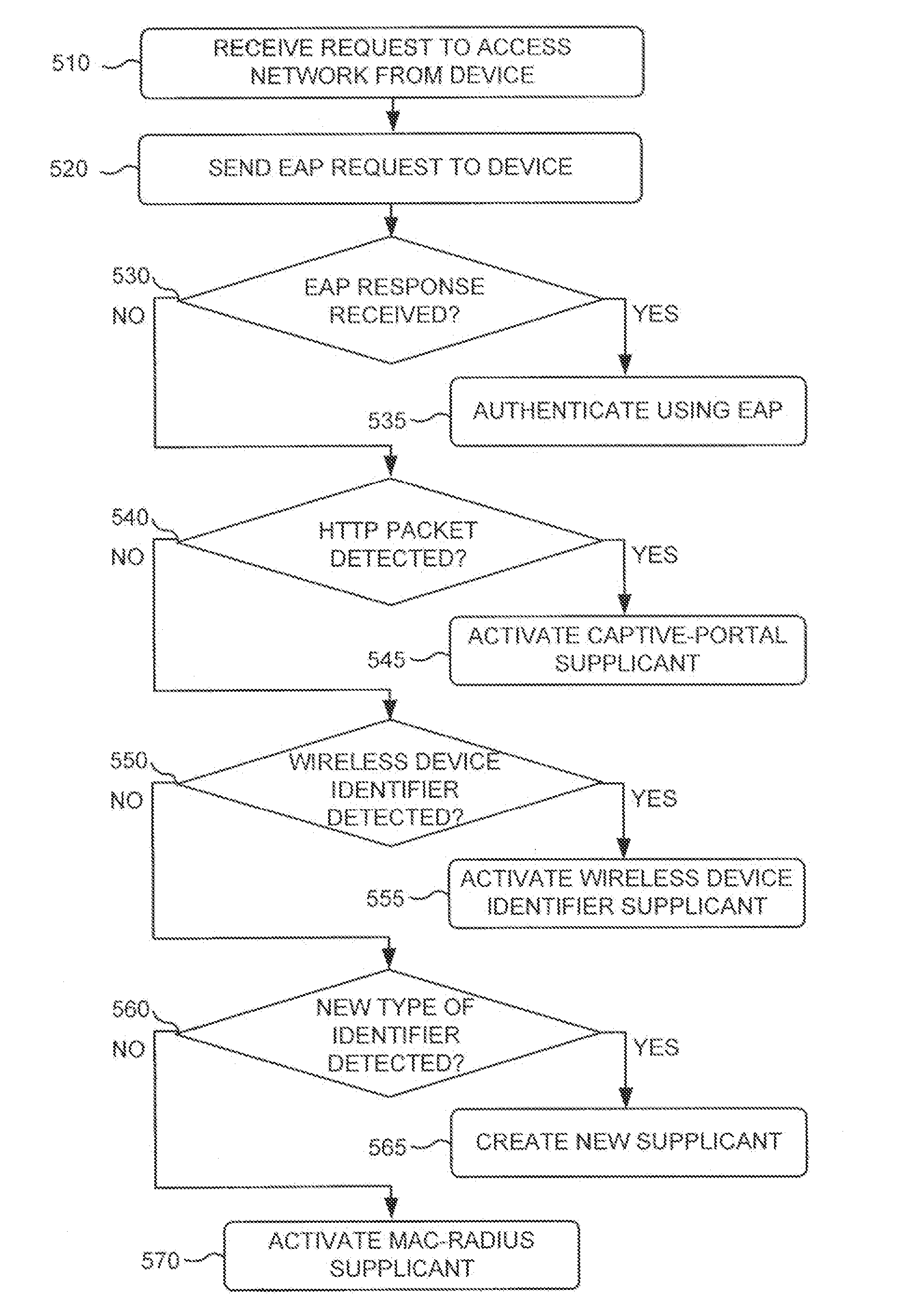
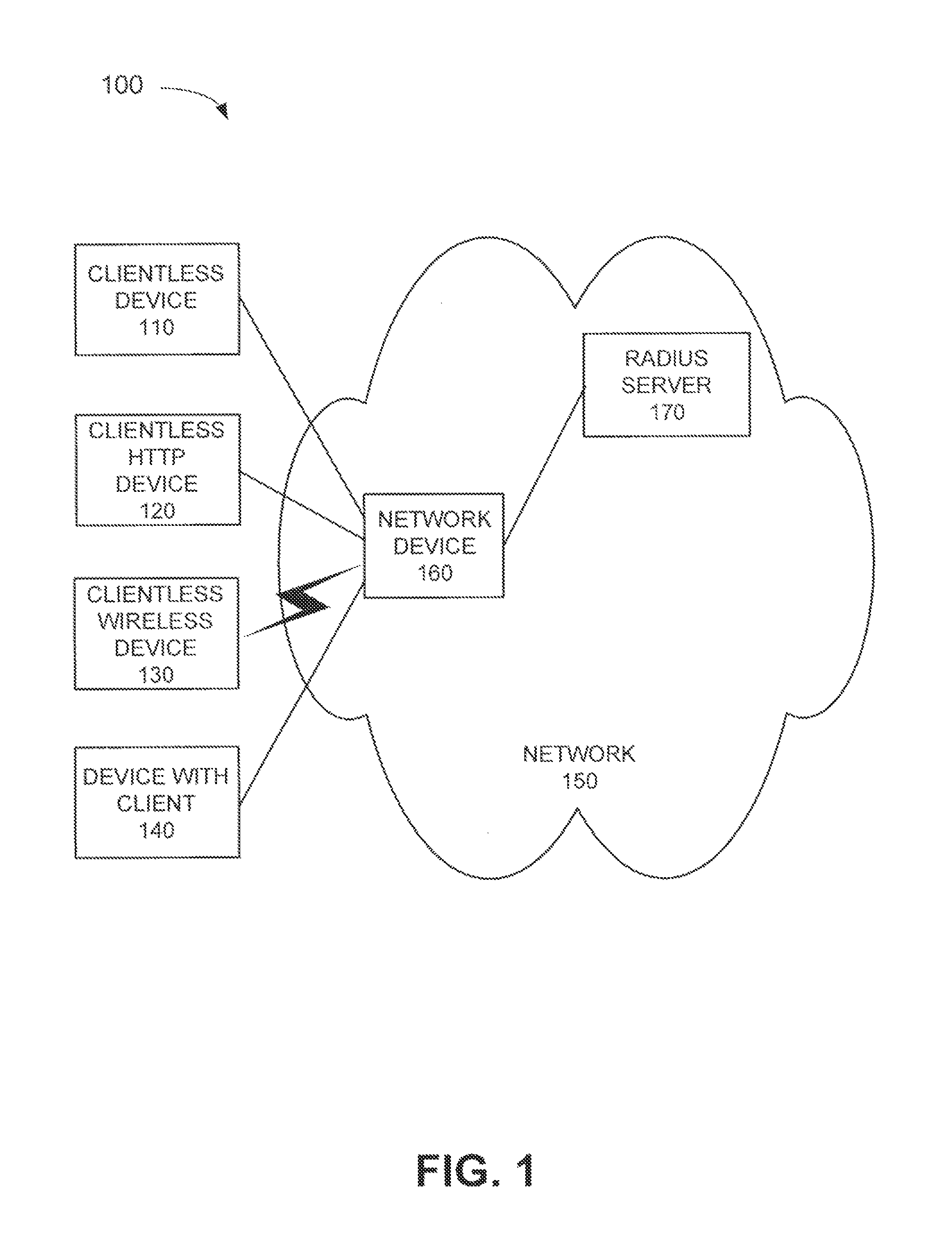
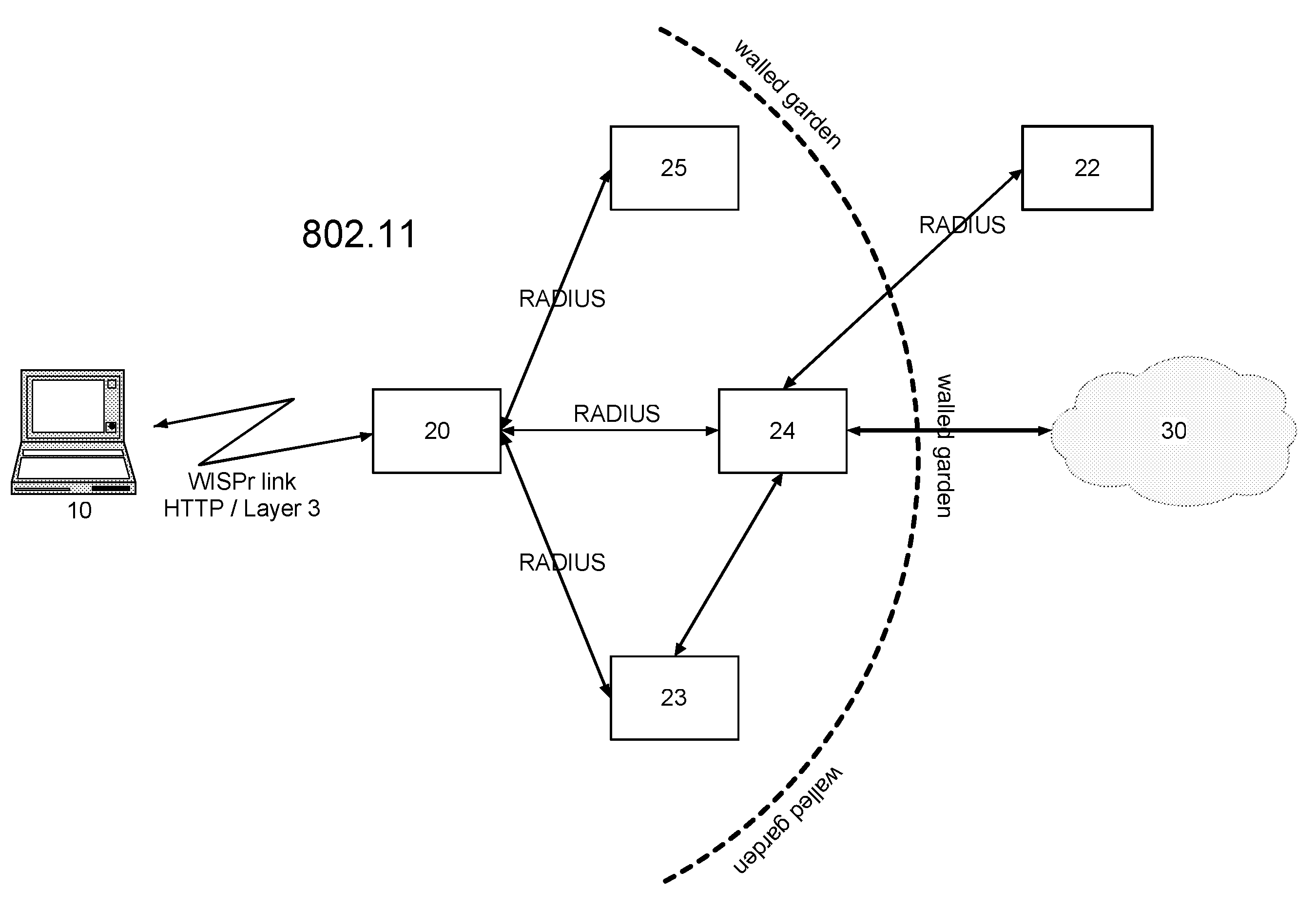
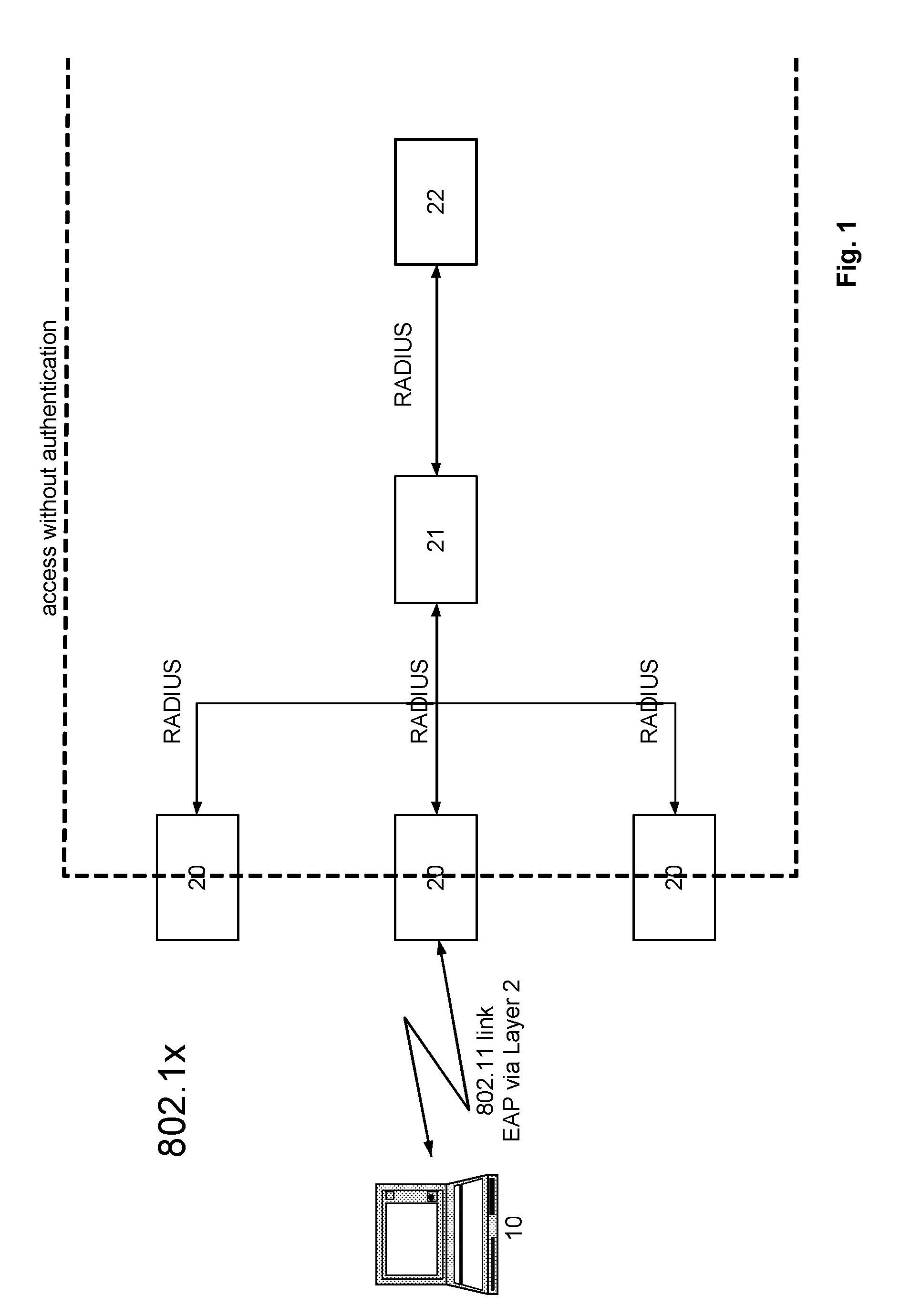
Supplicant framework to handle clientless devices on a dot1x platform
A network device may include a supplicant framework to generate a first 802.1x packet using a MAC address, associated with a first device as a first username and password in the first 802.1x packet; and generate a second 802.1x packet using a second username and password received from a second device via a captive-portal web page. The network device may further include an authenticator state machine to authenticate the first device with a Remote Authentication Dial In User Service (RADIUS) server using a first Extensible Authentication Protocol (EAP) packet that includes the first 802.1x packet; authenticate the second device with the RADIUS server using a second EAP packet that includes the second 802.1x packet; receive a third EAP packet from a third device; and authenticate the third device with the RADIUS server using the third EAP packet.
Owner:JUMIPER NETWORKS INC
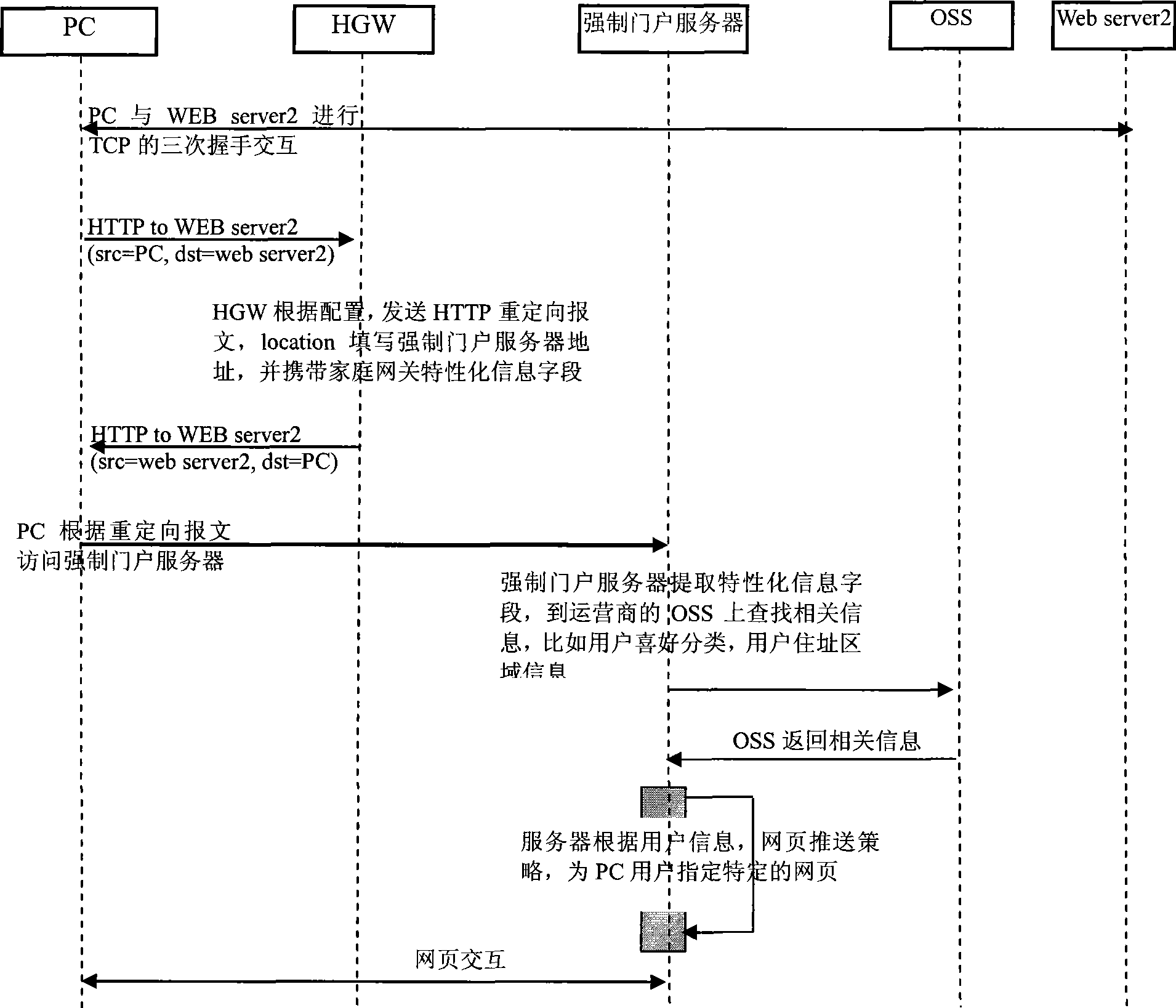
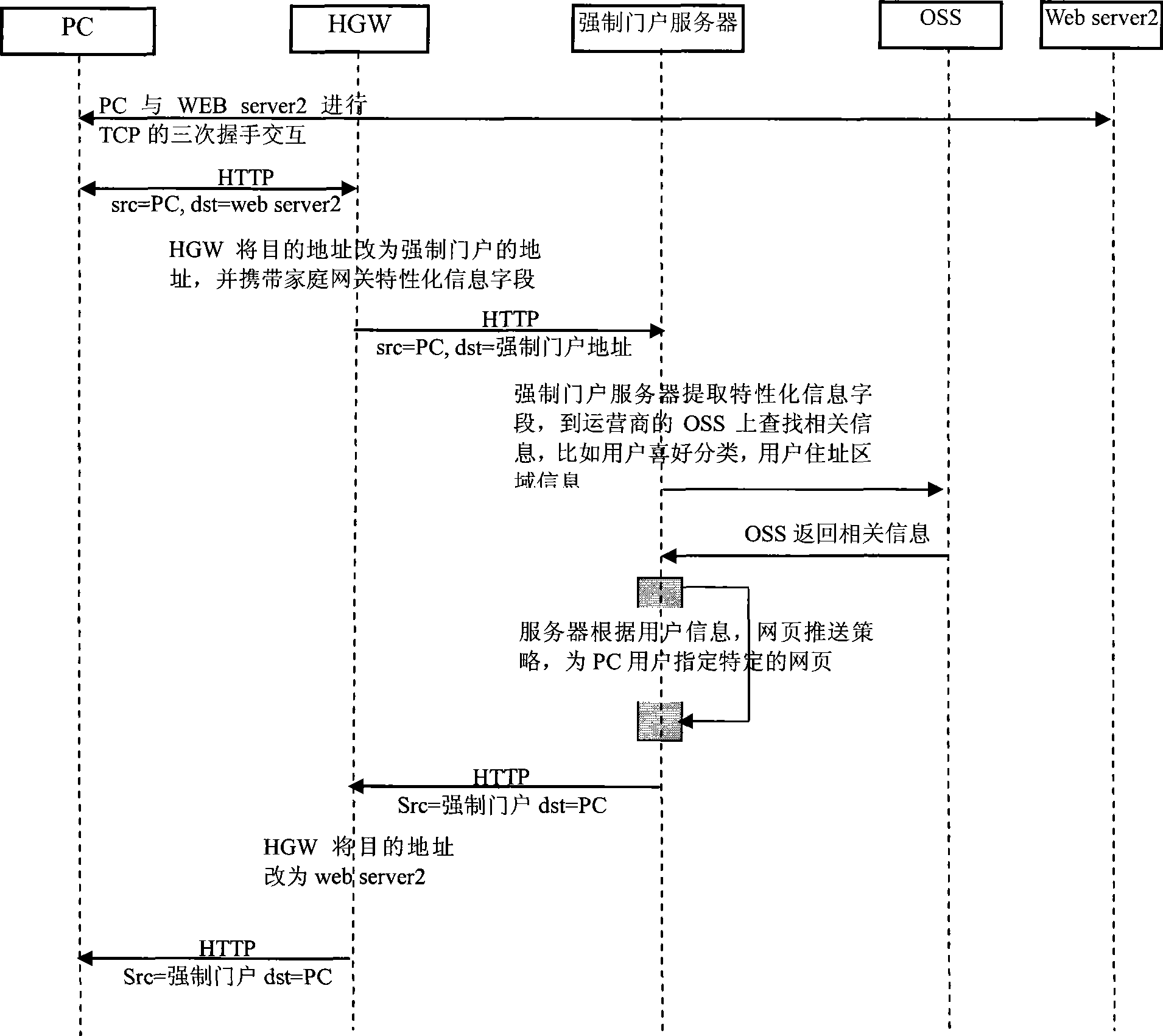
Web page push method, system and apparatus thereof
InactiveCN101510196AReduce loadReduce the complexity of networkingTransmissionSpecial data processing applicationsCaptive portalTerminal equipment
The embodiment of the invention discloses a webpage pushing method, a corresponding system and a relevant device. The method comprises the following steps: a user access terminal detects network access requests initiated by the user; the user access terminal modifies or forms the network access messages; characteristic information fields which are used for identifying the self equipments or user equipments or relevant to users are added in the content of the messages; and the characteristic information fields are used for determining the webpage pushing strategies and controlling the access to be transferred to a captive portal. The technical proposal of the embodiment of the invention at least has the following advantages: the webpage pushing method, the system and the device transfer the control point of the captive portal down to the user terminal device so as to effectively reduce the system load and the complexity of networking.
Owner:HUAWEI TECH CO LTD
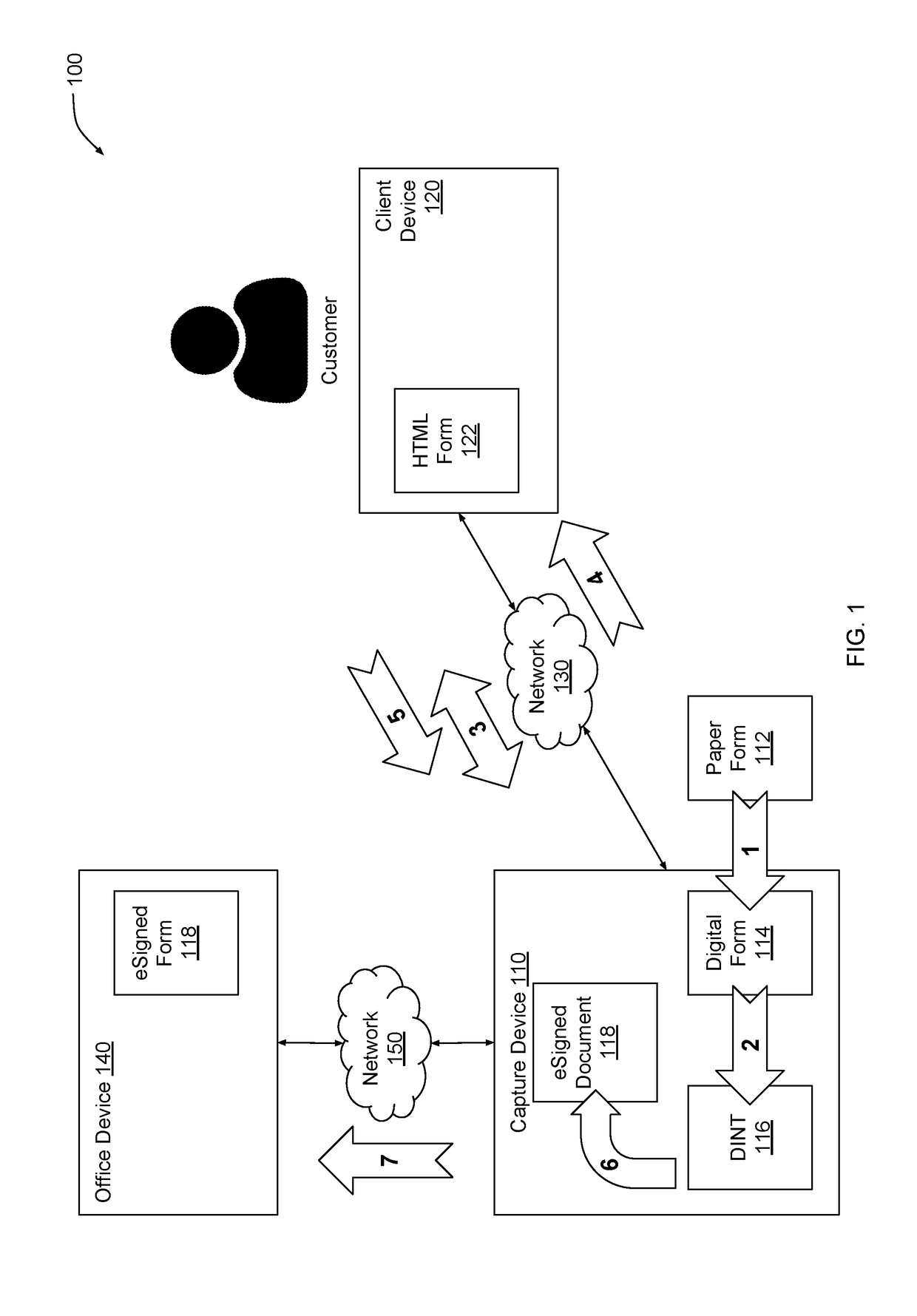
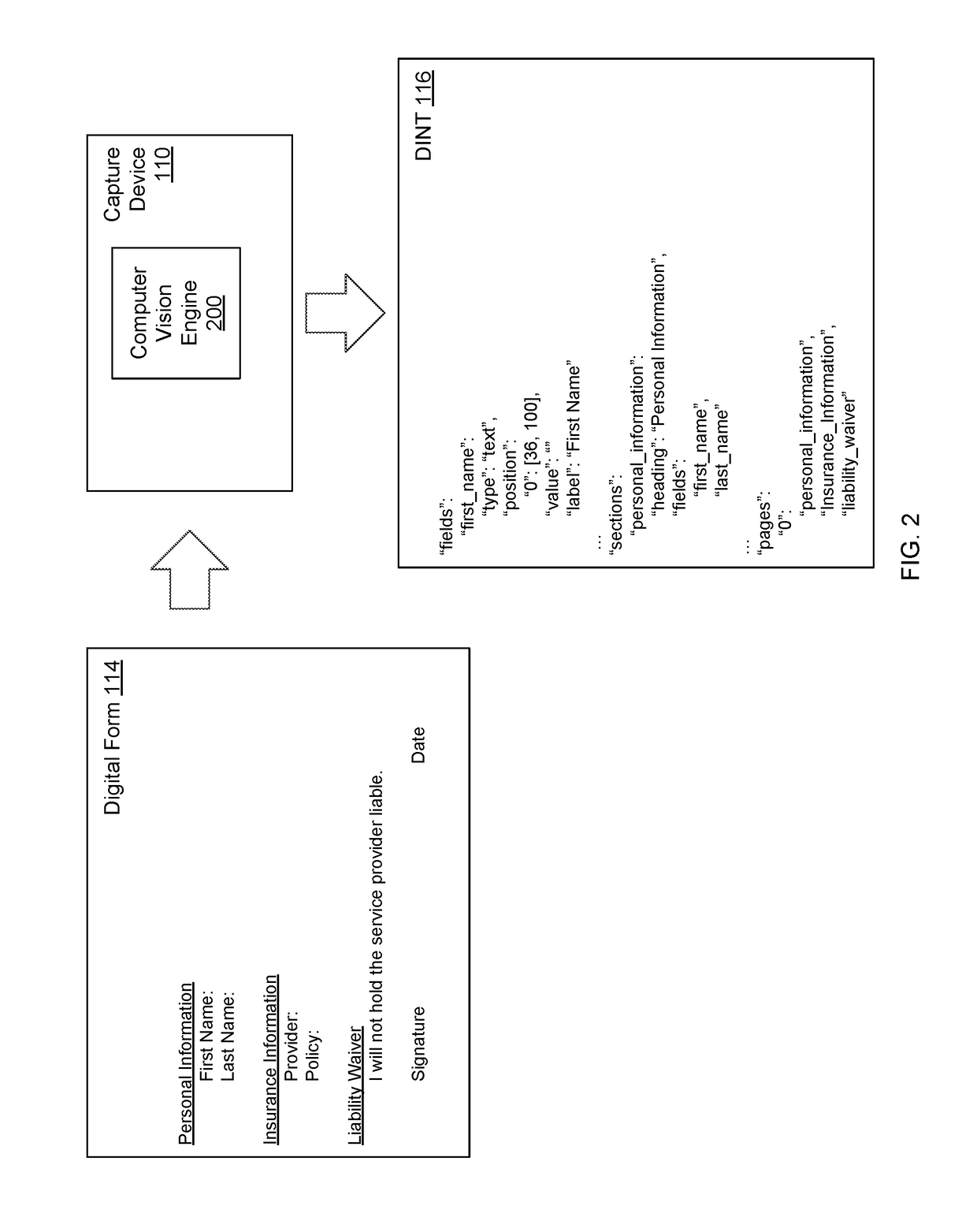
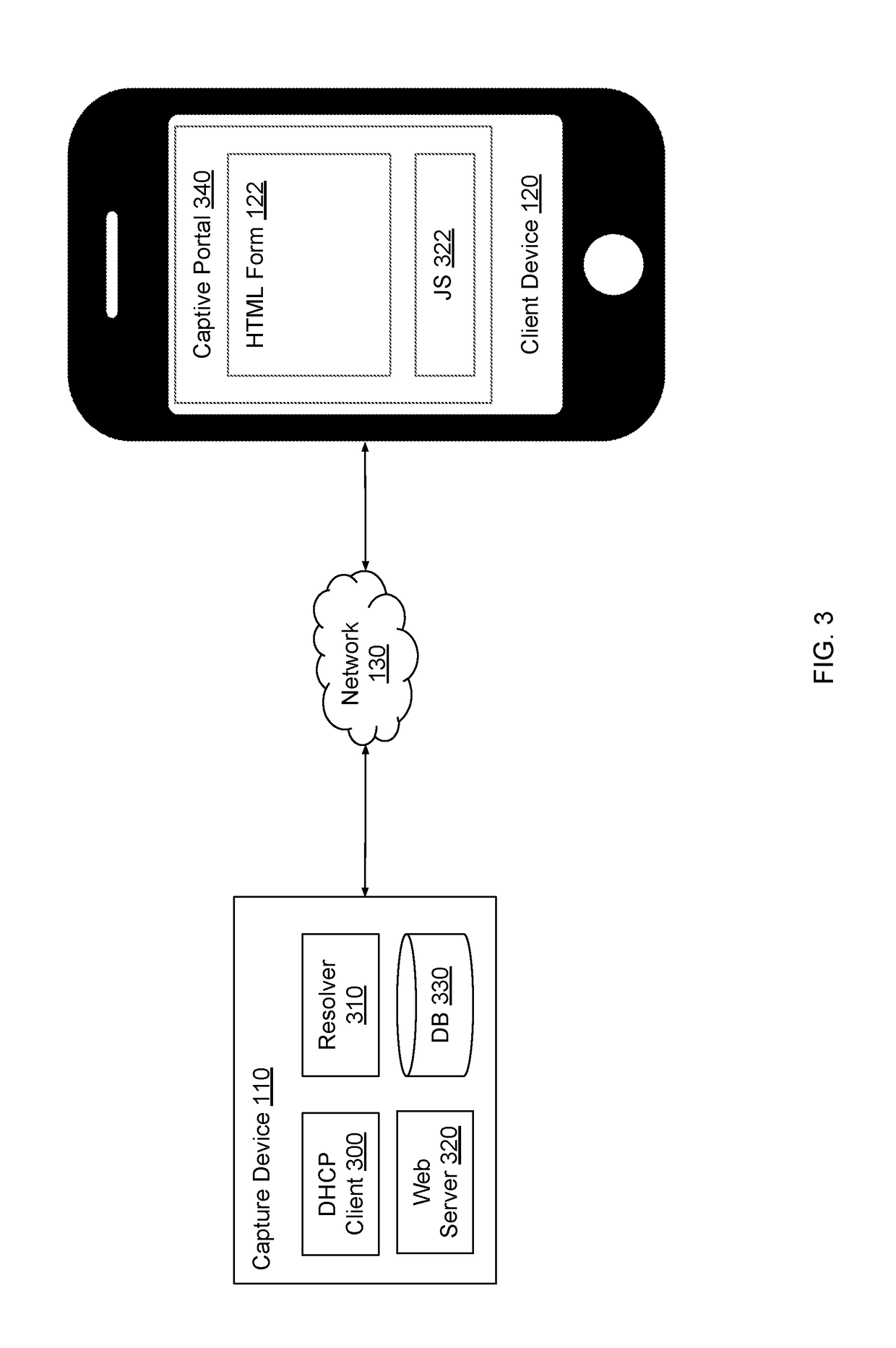
Capturing electronic signatures via captive portal
ActiveUS20190087639A1Simple working processOffice automationInput/output processes for data processingAuto-configurationCaptive portal
A capture device obtains customer data and electronic signatures via a captive portal. The capture device analyzes a digital form provided by a user and automatically configures a digital version of the form for signing. When a client device associated with a customer connects to the capture device, the capture device triggers a captive portal to appear on the client device. The capture device renders the digital form within the captive portal. The customer can then fill out, electronically sign, and submit the form. The capture device generates an audit trail for the electronically signed form based on identifying data captured transparently from the client device. The capture device establishes a secure connection with the client device for enhanced security and to prevent the client device from displaying security warnings.
Owner:CRANE DARIEN
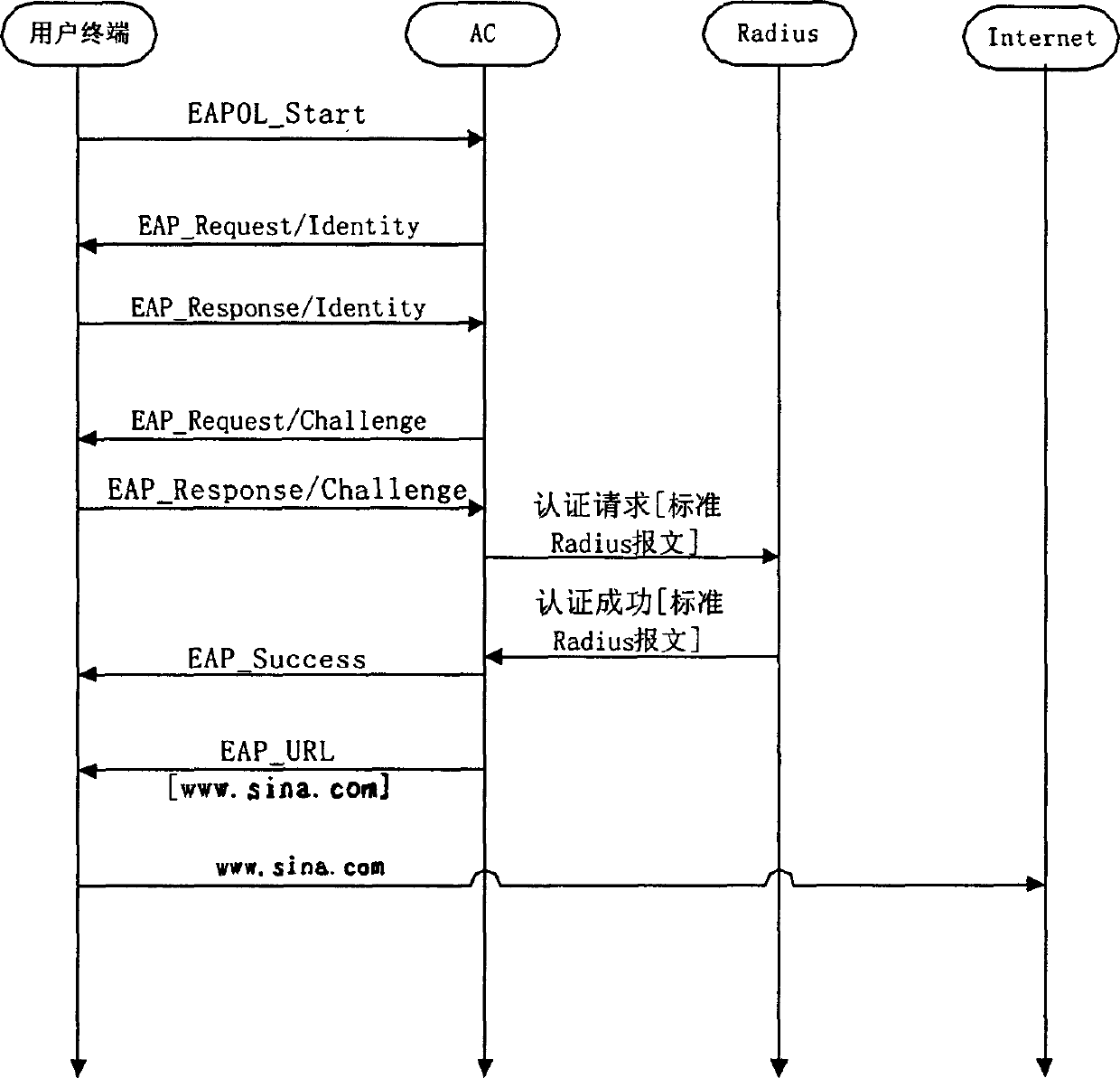
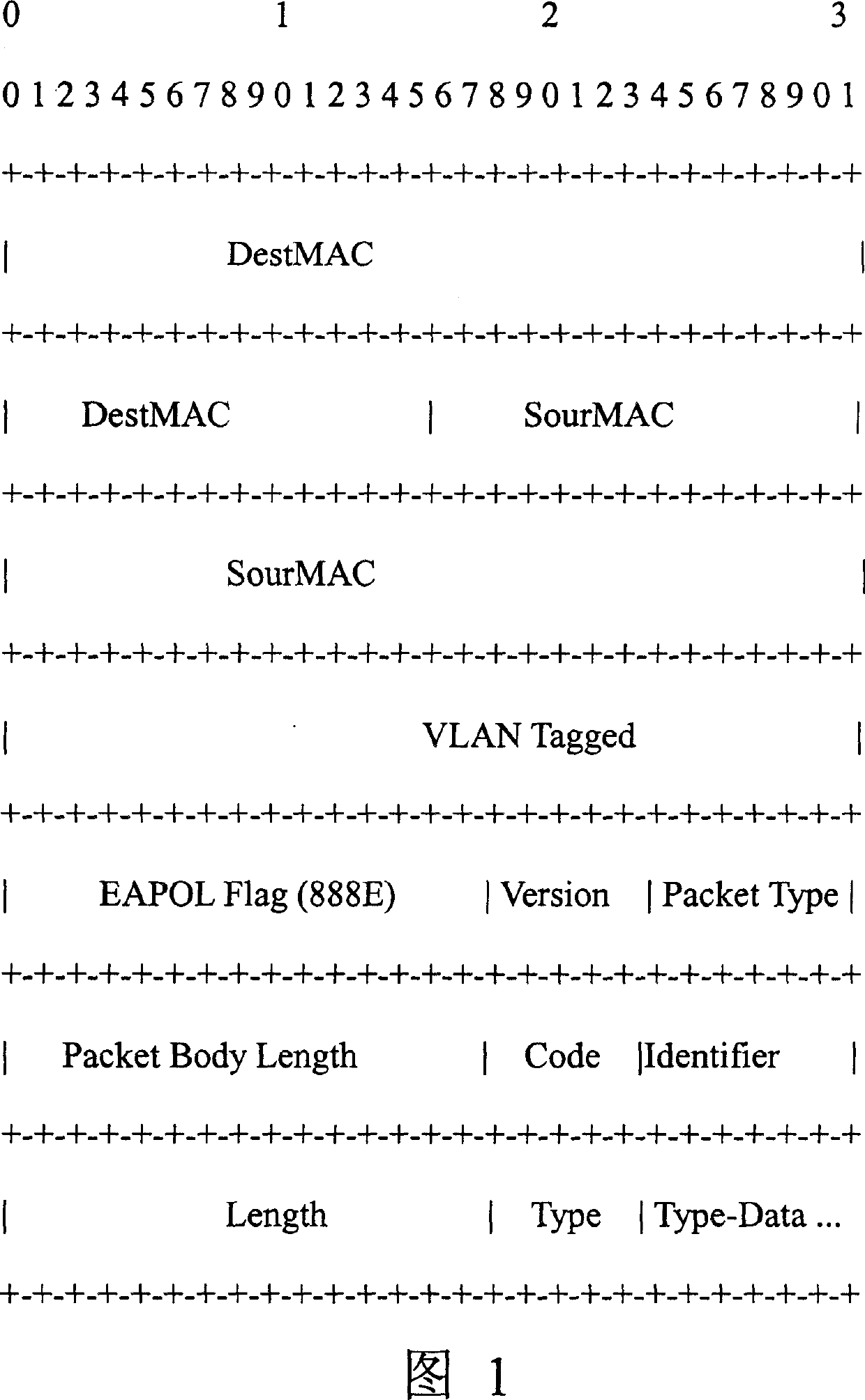
Method for performing forced door authentication on user in 802.1X access mode
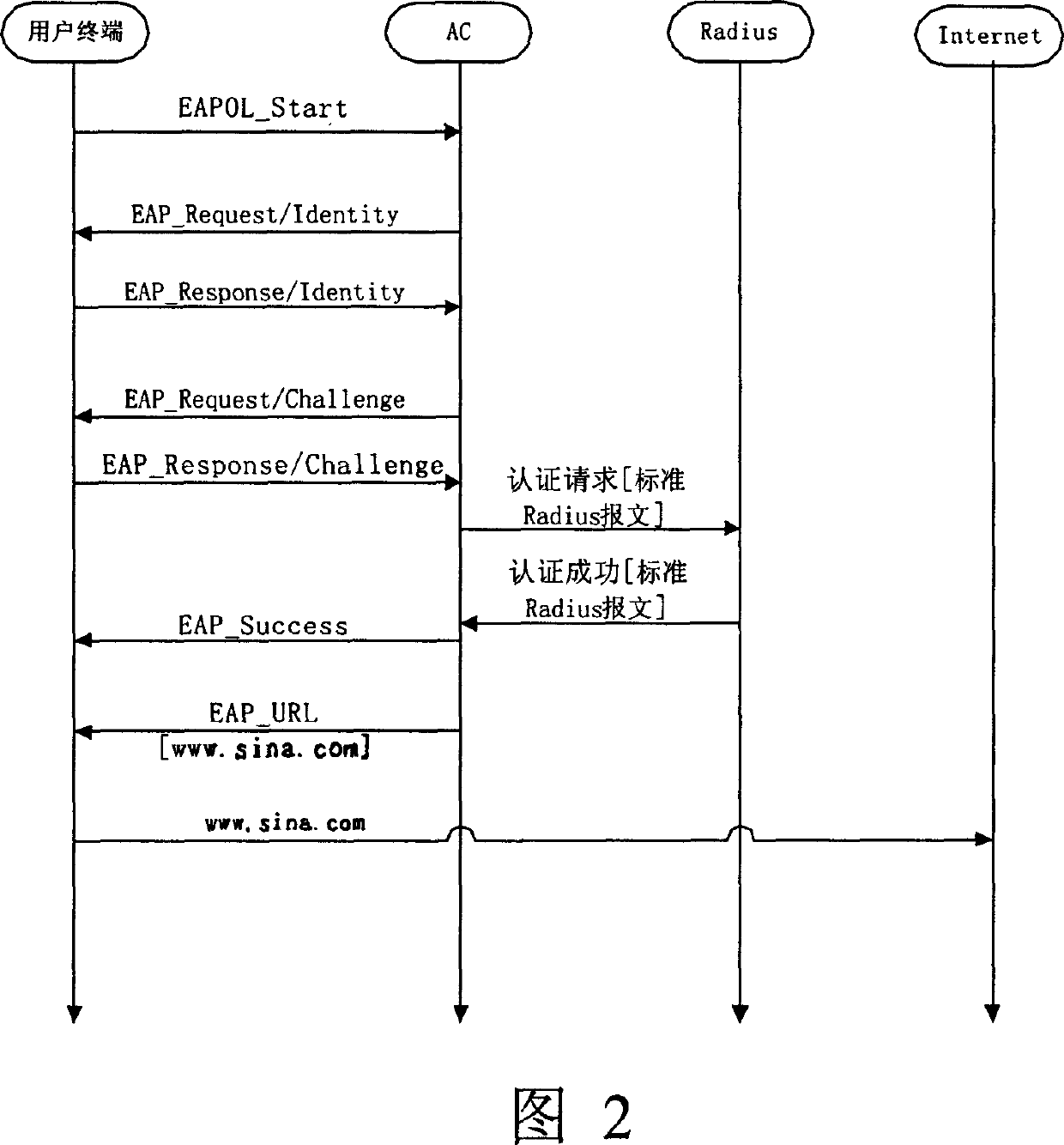
InactiveCN1571332AEffective expansionPayloadUser identity/authority verificationData switching networksMessage typeCaptive portal
The invention provides a method of forcing door attestation on user access in 802.1X accessing mode. The method firstly extends the existing EAP (extendable attestation protocol), thus increasing message types of EAP URL (united resource locator). On this basis, it includes the steps: receiving user connection establishing requirement message by accessing controller, attesting user validity: if the authentication succeeds, notify the user to log on and send EAP-URL message to the user. It provides an effective extension for the existing 802.1X service, thus realizing more effective service supporting.
Owner:CHENGDU HUAWEI TECH
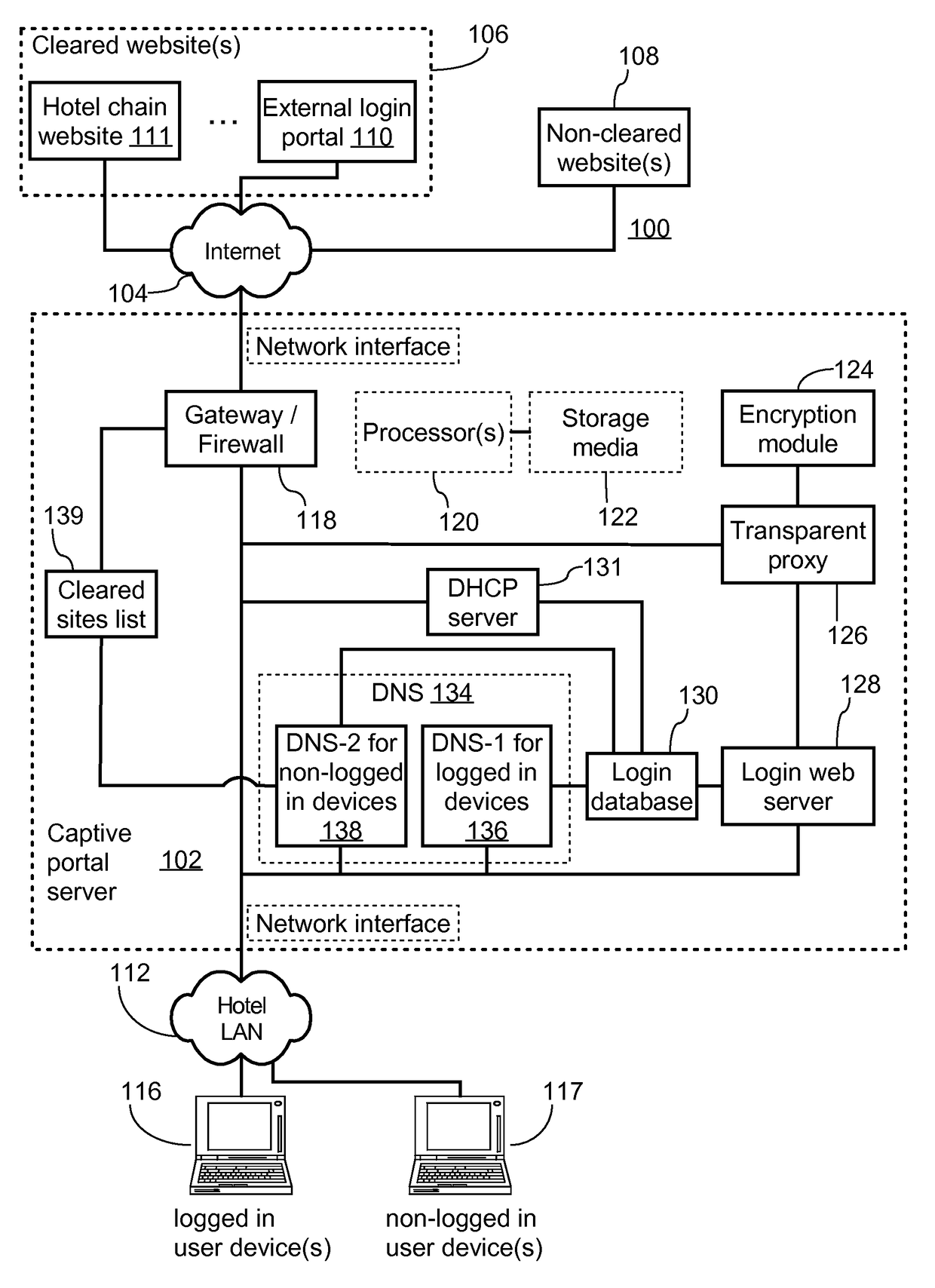
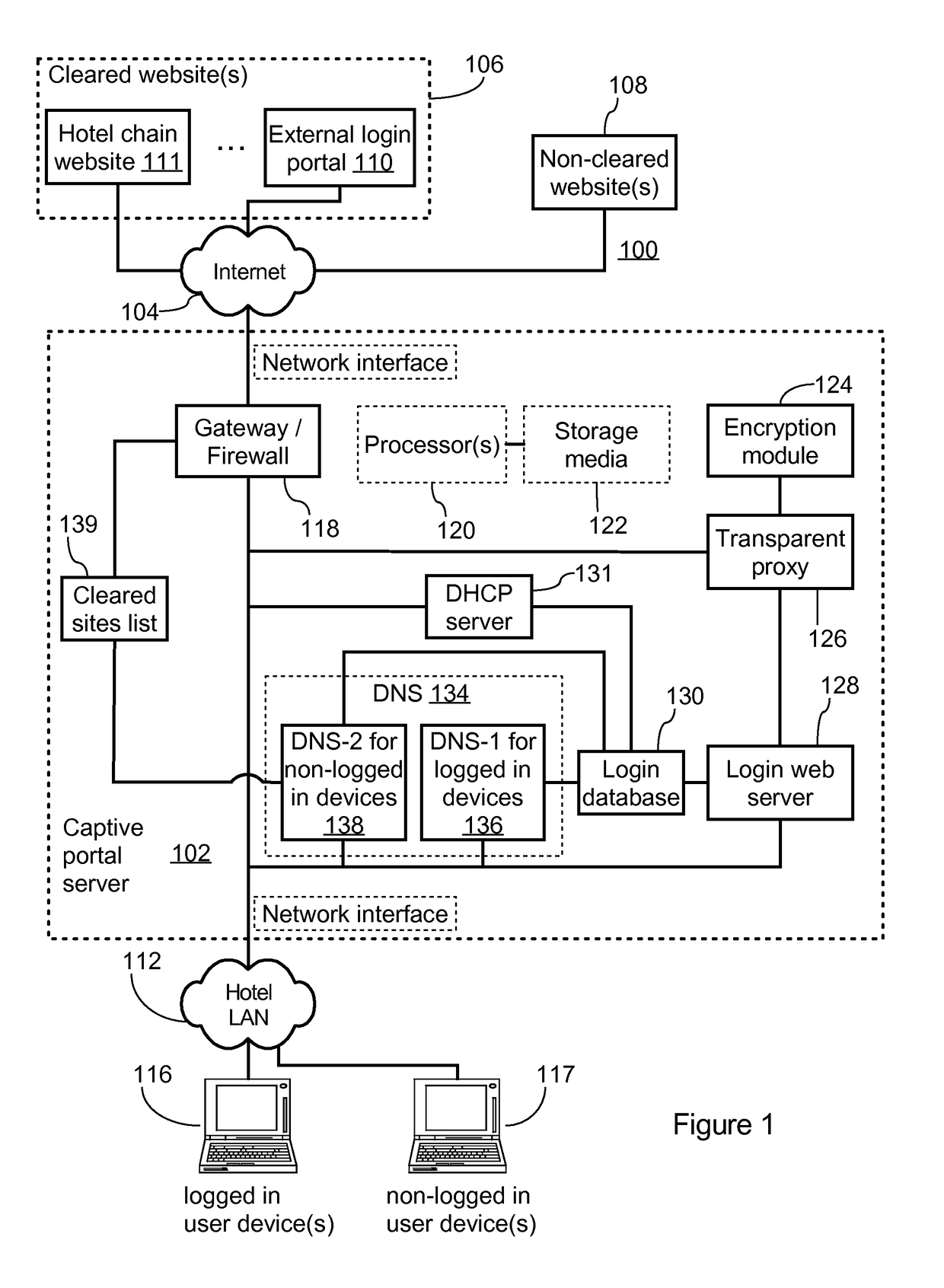
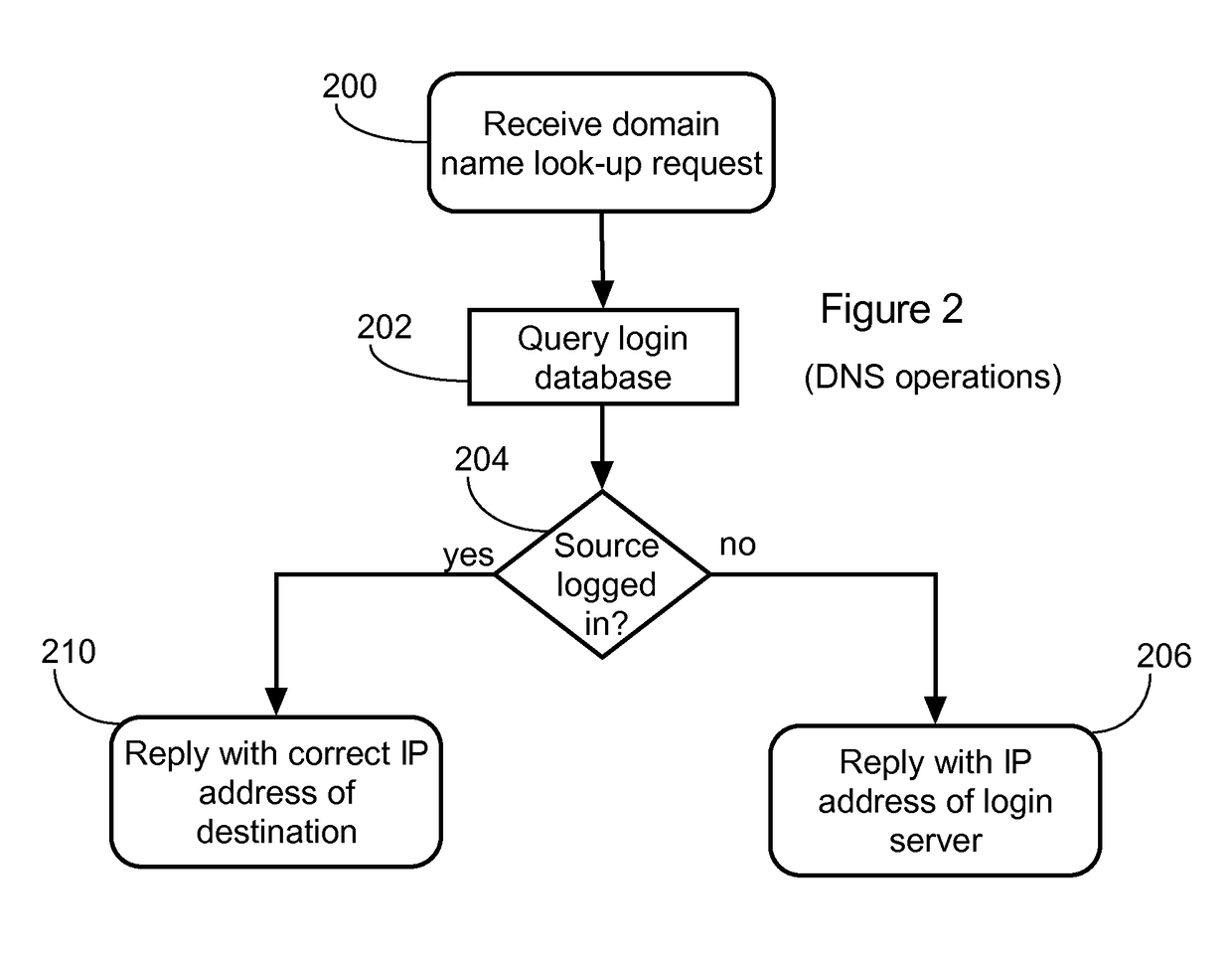
DNS-based captive portal with integrated transparent proxy to protect against user device caching incorrect IP address
A captive portal system includes a login database, a web server, and a name server. The name server receives a DNS request from a user device, queries the login database to determine whether the user device is logged in, and responds to the DNS request with the IP address of the web server as a resolved IP address of the specified domain name when the user device is not logged in. The web server accepts a connection request from the user device to the IP address of the web server, receives an HTTP request specifying a non-local target URL from the user device, queries the login database to determine whether the user device is logged in according to the source address of the user device, and acts as a transparent proxy between the user device and the non-local target URL when the user device is logged in.
Owner:GUEST TEK INTERACTIVE ENTERTAINMENT
Method and system for authenticating a network node in a UAM-based WLAN network
ActiveUS8806587B2Improve mobile performanceDigital data processing detailsUser identity/authority verificationNetwork access serverNetworking protocol
Owner:TOGEWA HLDG
Multimode authentication
ActiveUS8887237B2Digital data processing detailsMultiple digital computer combinationsCaptive portalClient-side
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
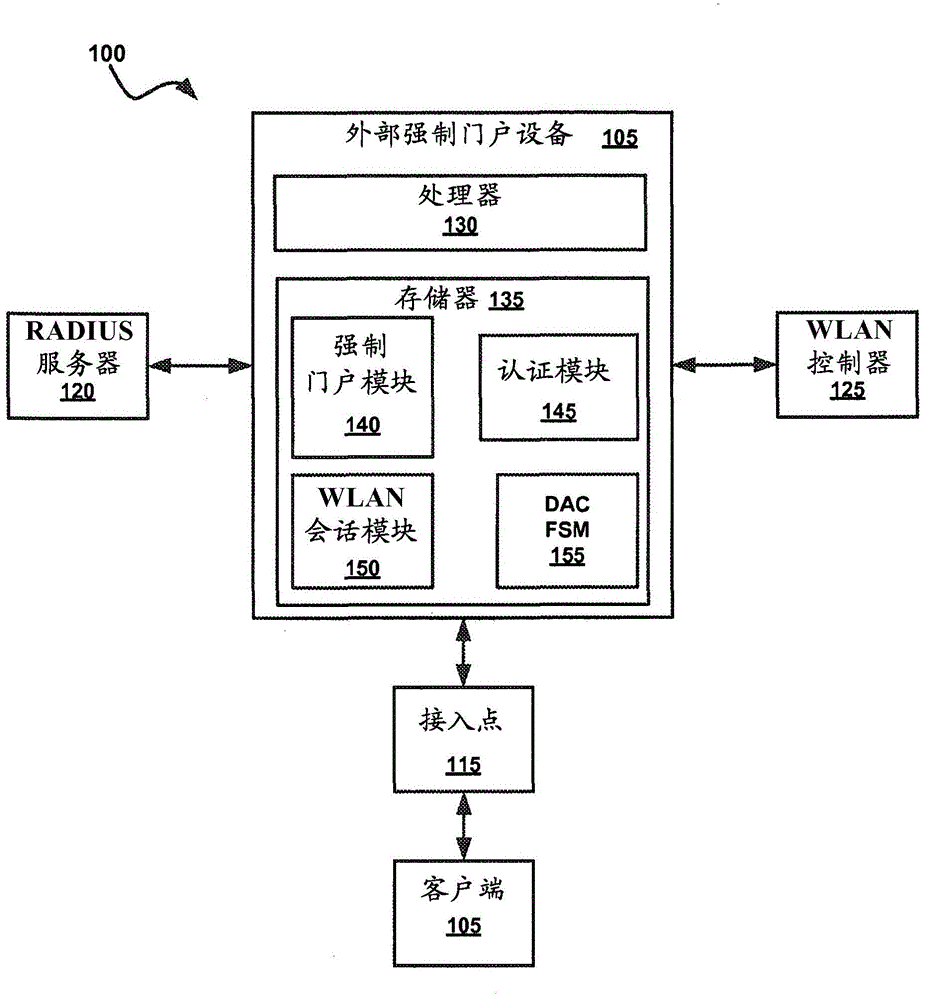
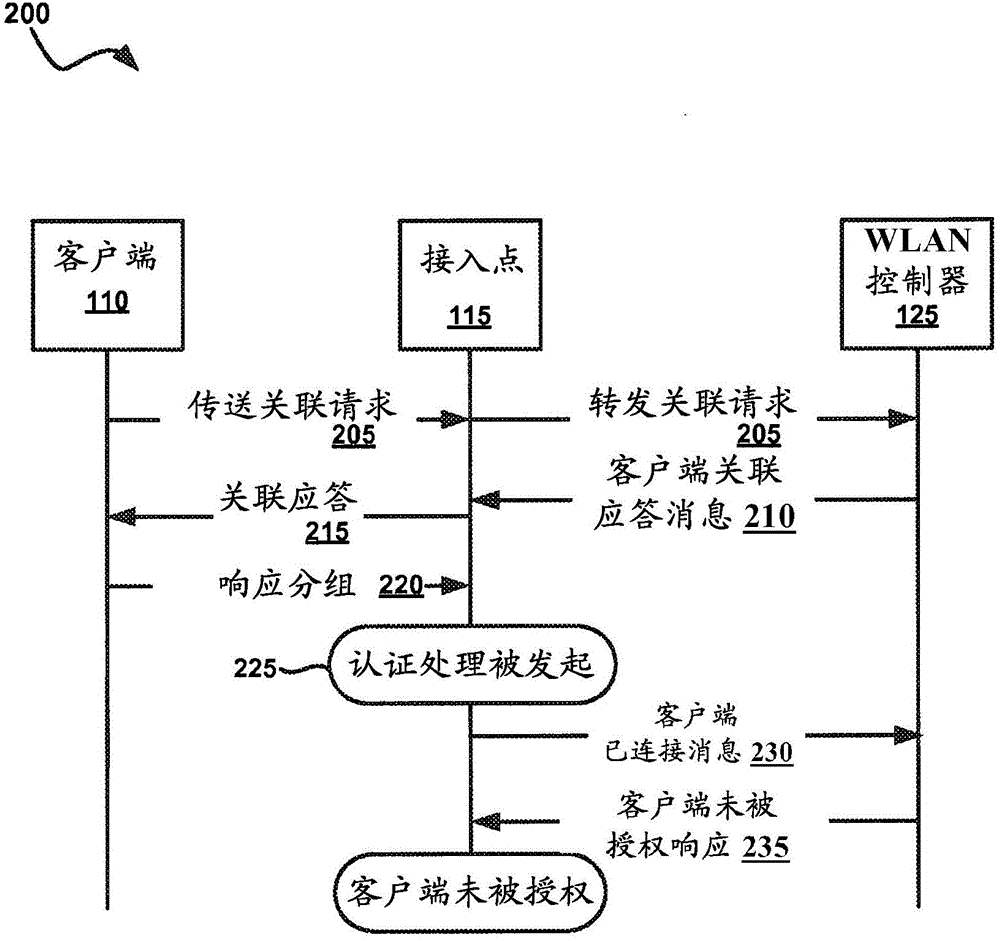
Captive portal systems, methods, and devices
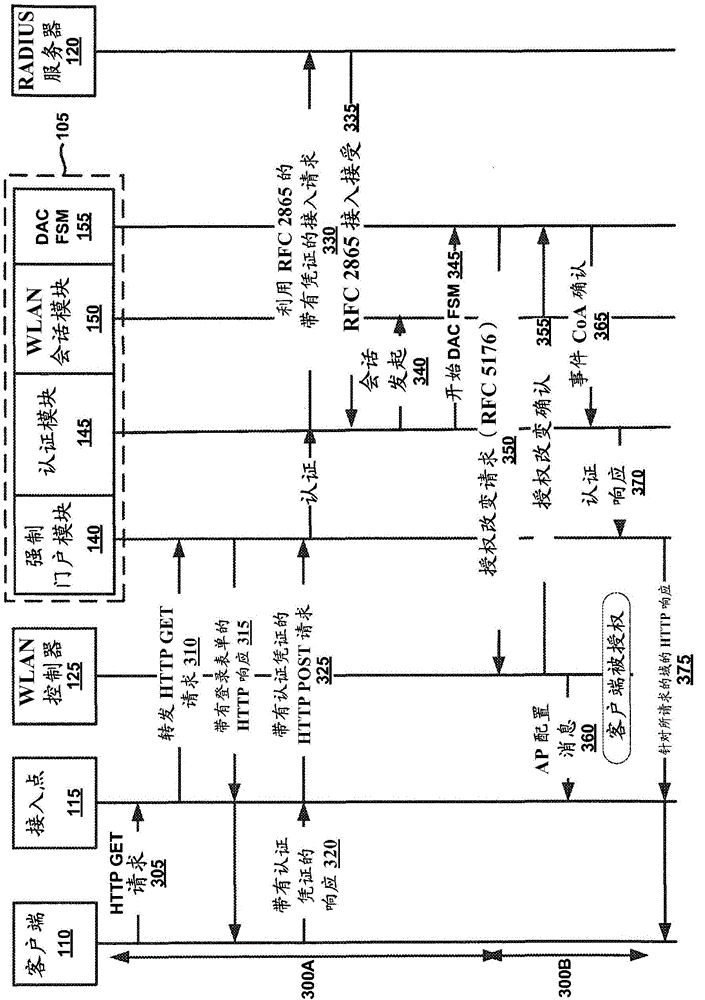
Embodiments of the present technology provide out-of-band captive portal devices, networks, and methods. An example of a method includes executing a redirection of a client request for network access to a captive portal login, initiating an association between the wireless controller and the client, receiving authentication credentials of client from the captive portal login, negotiating a change of authorization with a wireless controller in accordance with RFC 5176 protocol, wherein the controller includes a mapping to a captive portal Internet Protocol (IP) address, and redirecting the client to a URL specified in the client request for network access.
Owner:EXTREME NETWORKS INC
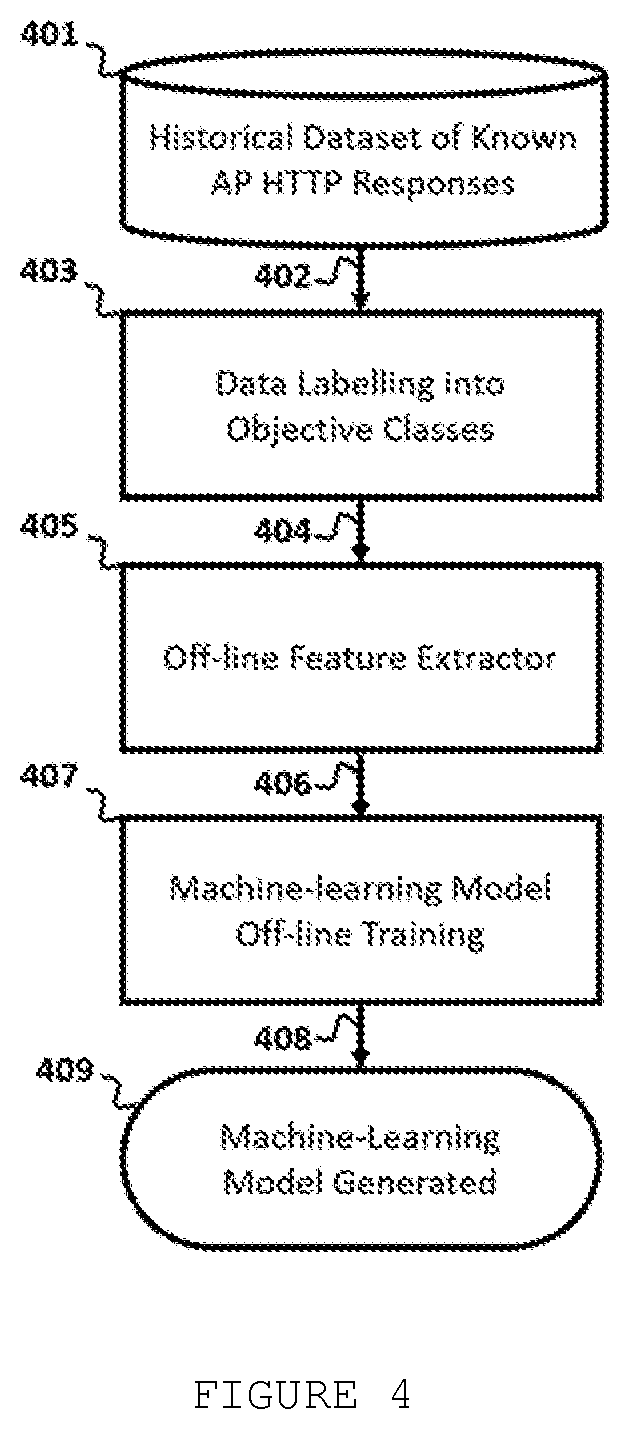
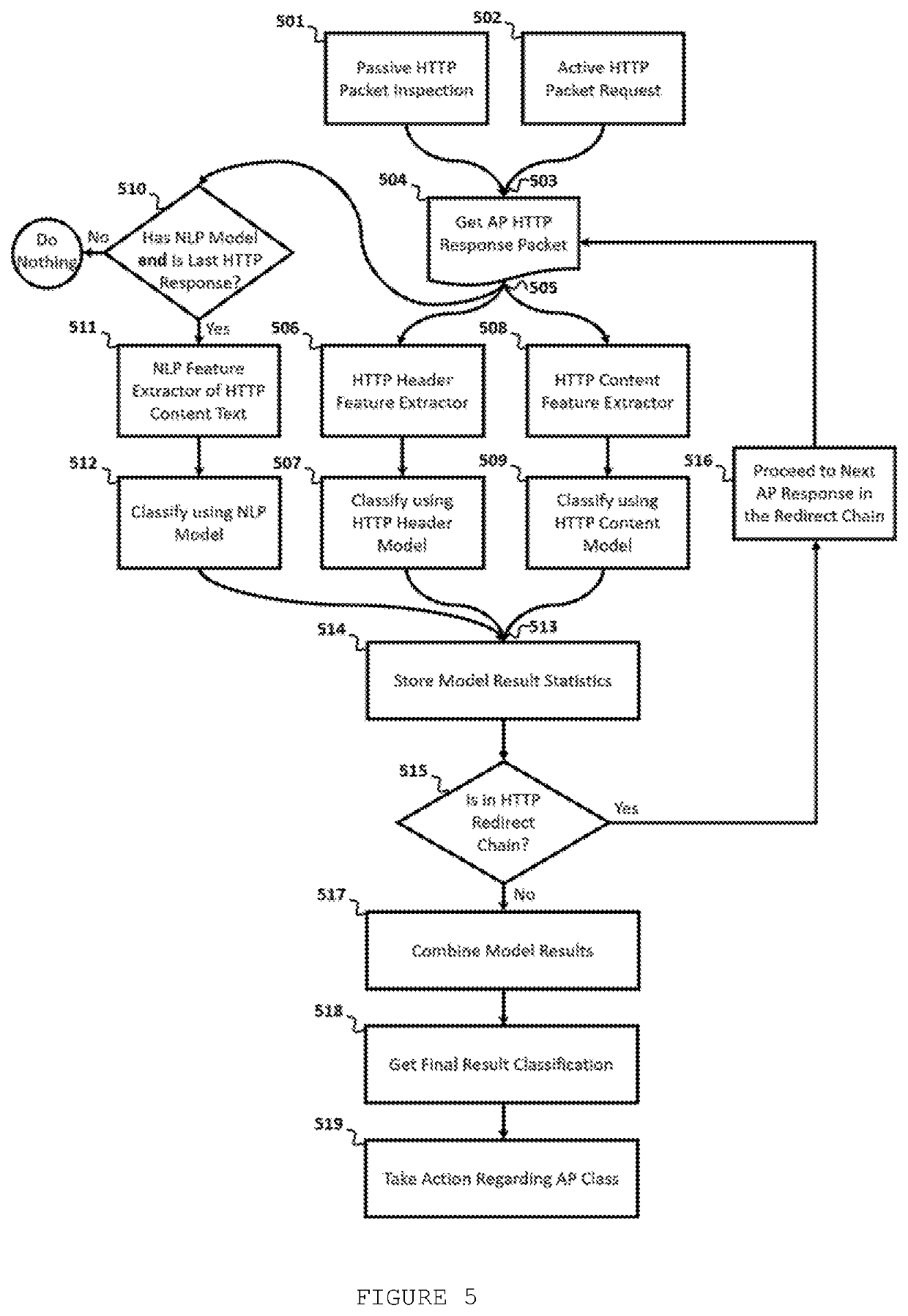
Method for http-based access point fingerprint and classification using machine learning
The present disclosure relates to a technique based on Machine-learning to fingerprint and classify Access Points (AP), using HyperText Transfer Protocol (HTTP) information. Fingerprint and classify Access Points are useful to detect if the AP is benign or malicious, to assess the potential trustworthiness of an AP to the user, to detect AP type, to detect AP infrastructure, to infer an AP web-service software type and version, to detect if AP is software-based or hardware-based, to detect AP running services, to detect AP network configuration, to detect specific malicious tools that are used by attackers to emulate an AP, to detect Fake AP attack, Phishing attacks, Evil Twin Attacks, and any other threats that modify or implement an AP HTTP server or webpage. The proposed technique makes advantage of the captive portal detection packet exchange between a station and an Access Point to passively classify the AP.
Owner:SAMSUNG ELECTRONICSA AMAZONIA
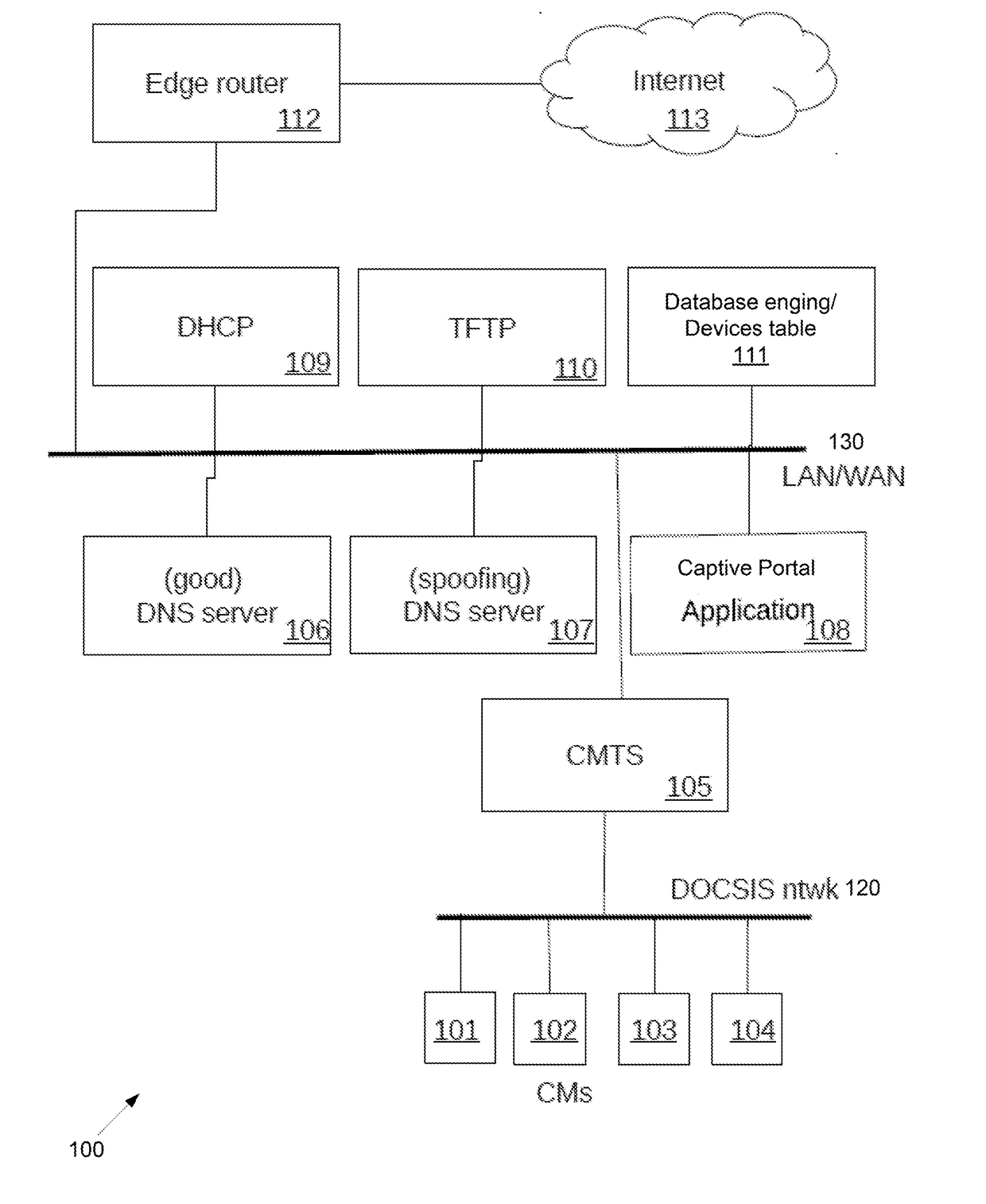
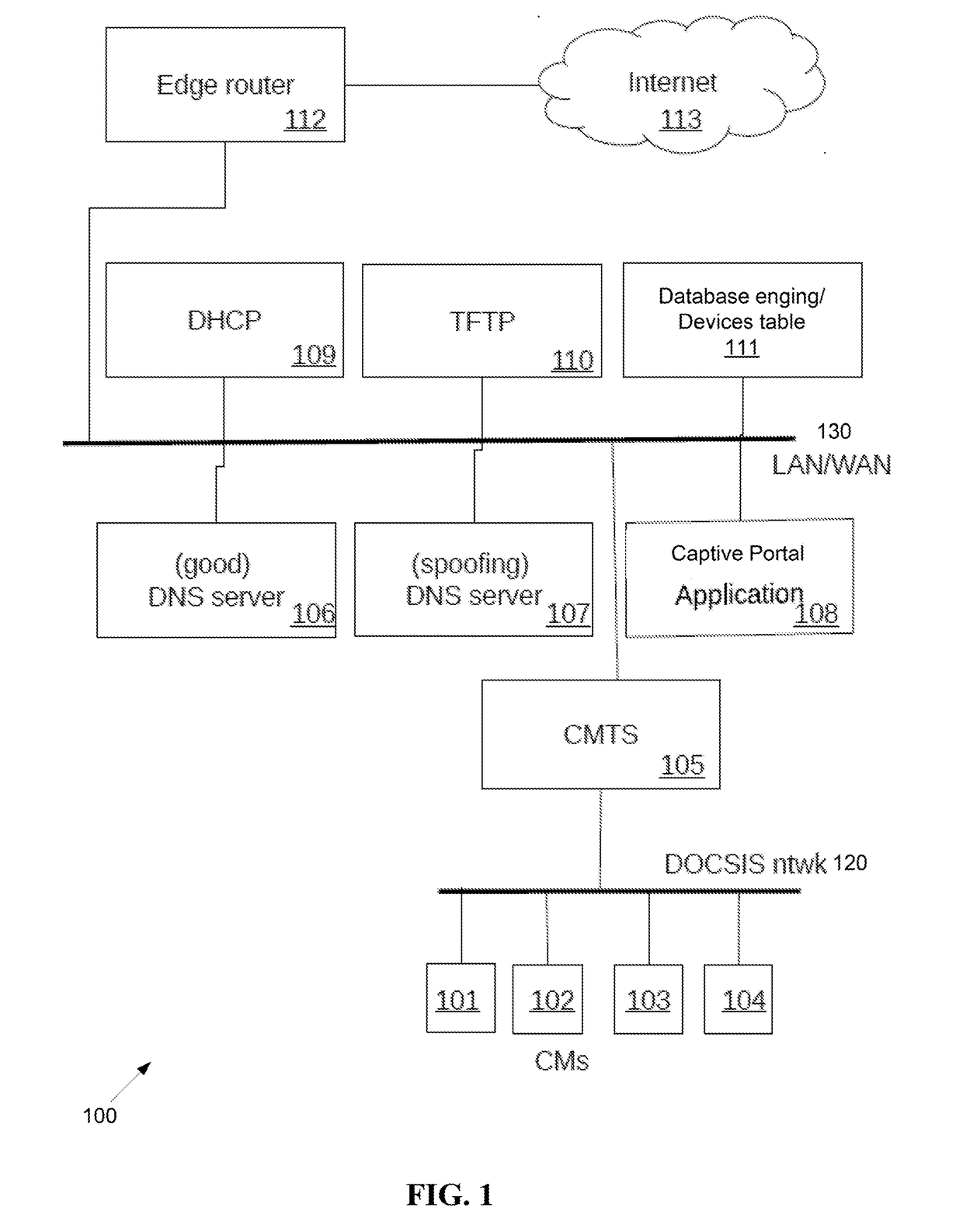
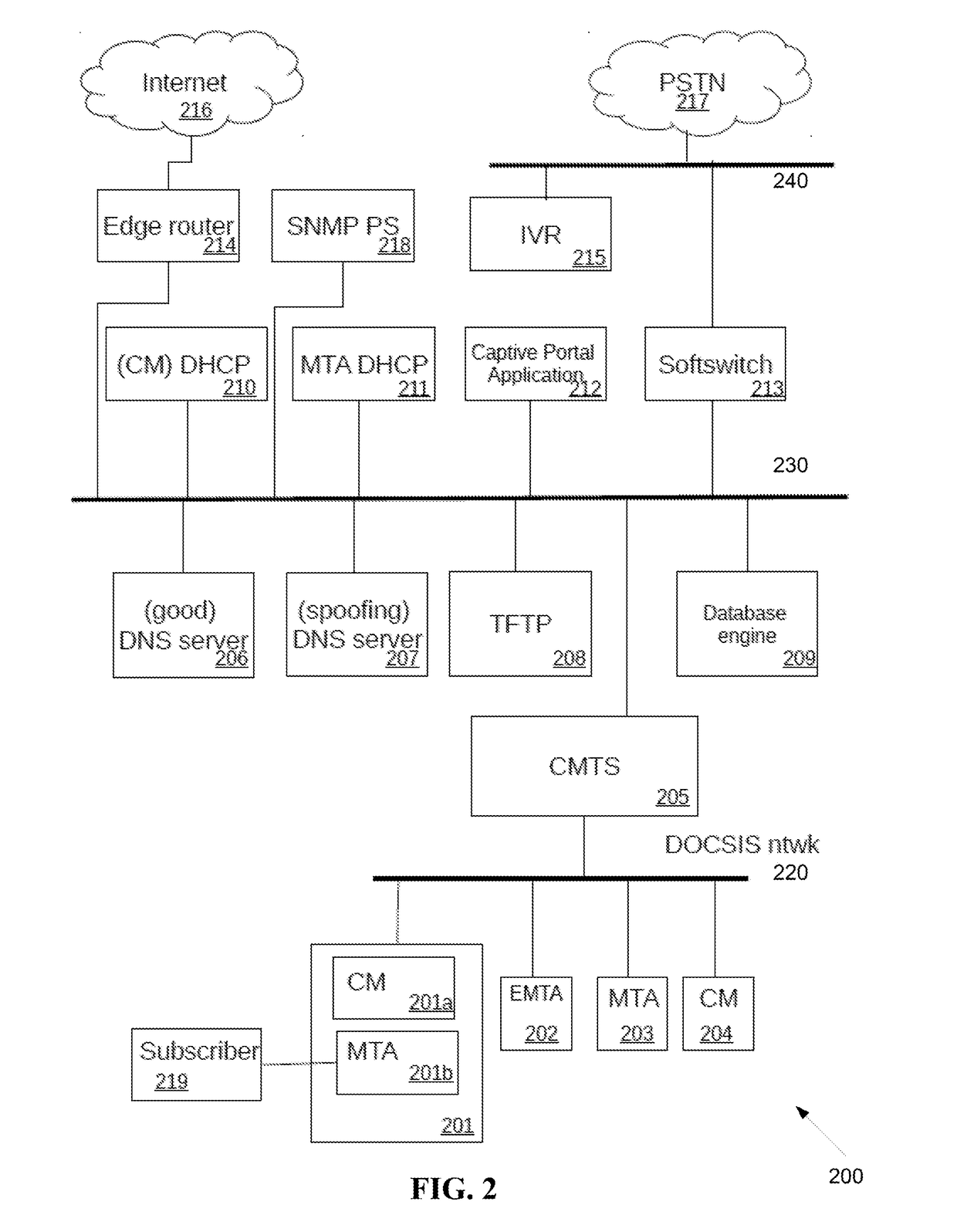
Method and system for self-provisioning of cable modems and multimedia terminal adapters
An unregistered cable modem is in a cable operator network having a computer, a dynamic host configuration protocol (DHCP) server, a spoofing domain name system (DNS) server and a good DNS server, a captive portal application, and a trivial file transfer protocol (TFTP) server. The cable modem is provisioned by the cable modem obtaining a configuration, rebooting, and activating the configuration. The computer obtains a plurality of computer configuration parameters including an IP address of the spoofing DNS. The spoofing DNS server answers an HTTP request from the computer with an IP address associated with the captive portal application. The captive portal obtains an activation code from the computer, verifies the activation code is correct, and forces the cable modem to reboot.
Owner:INTRAWAY R&D SA
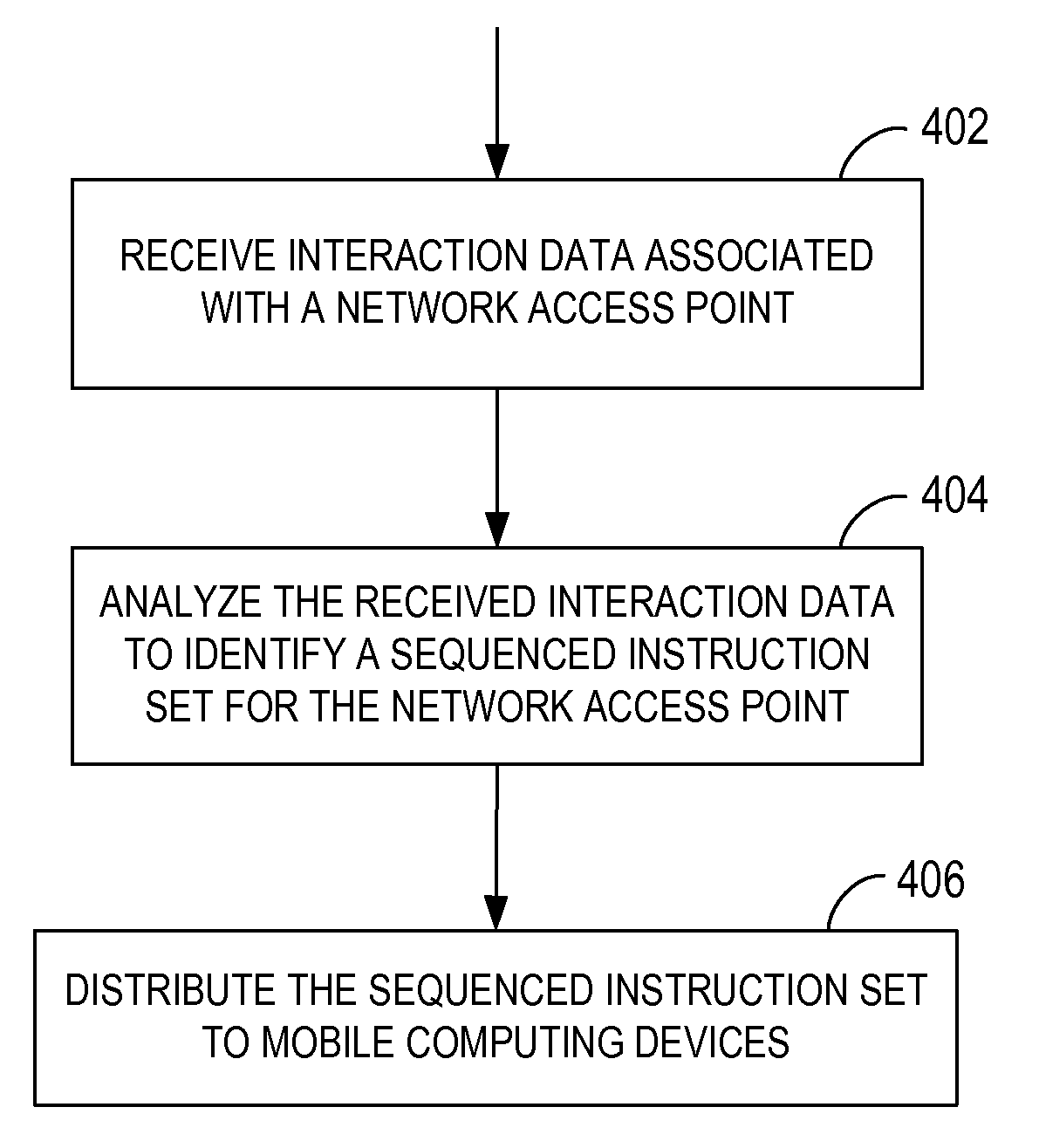
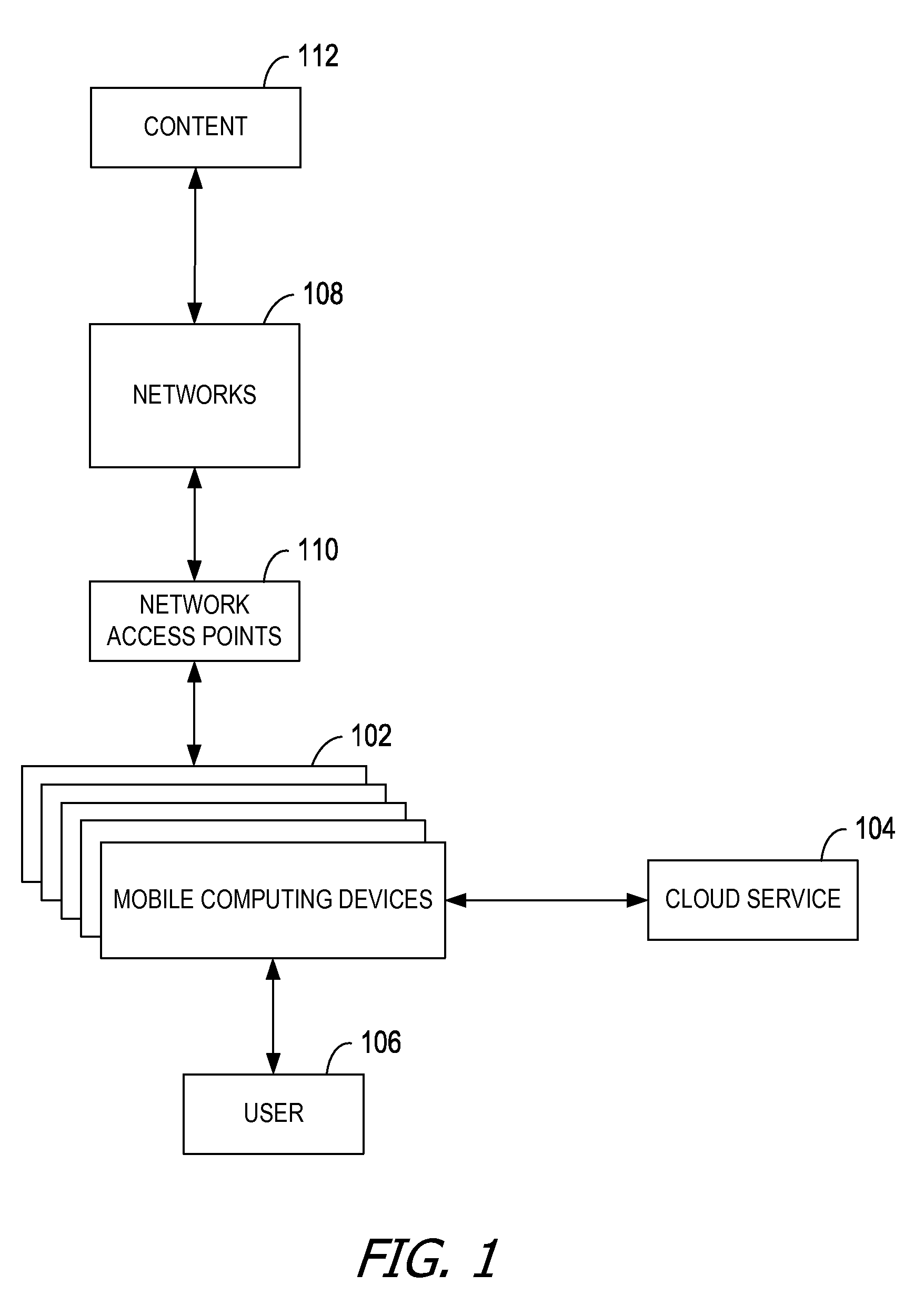
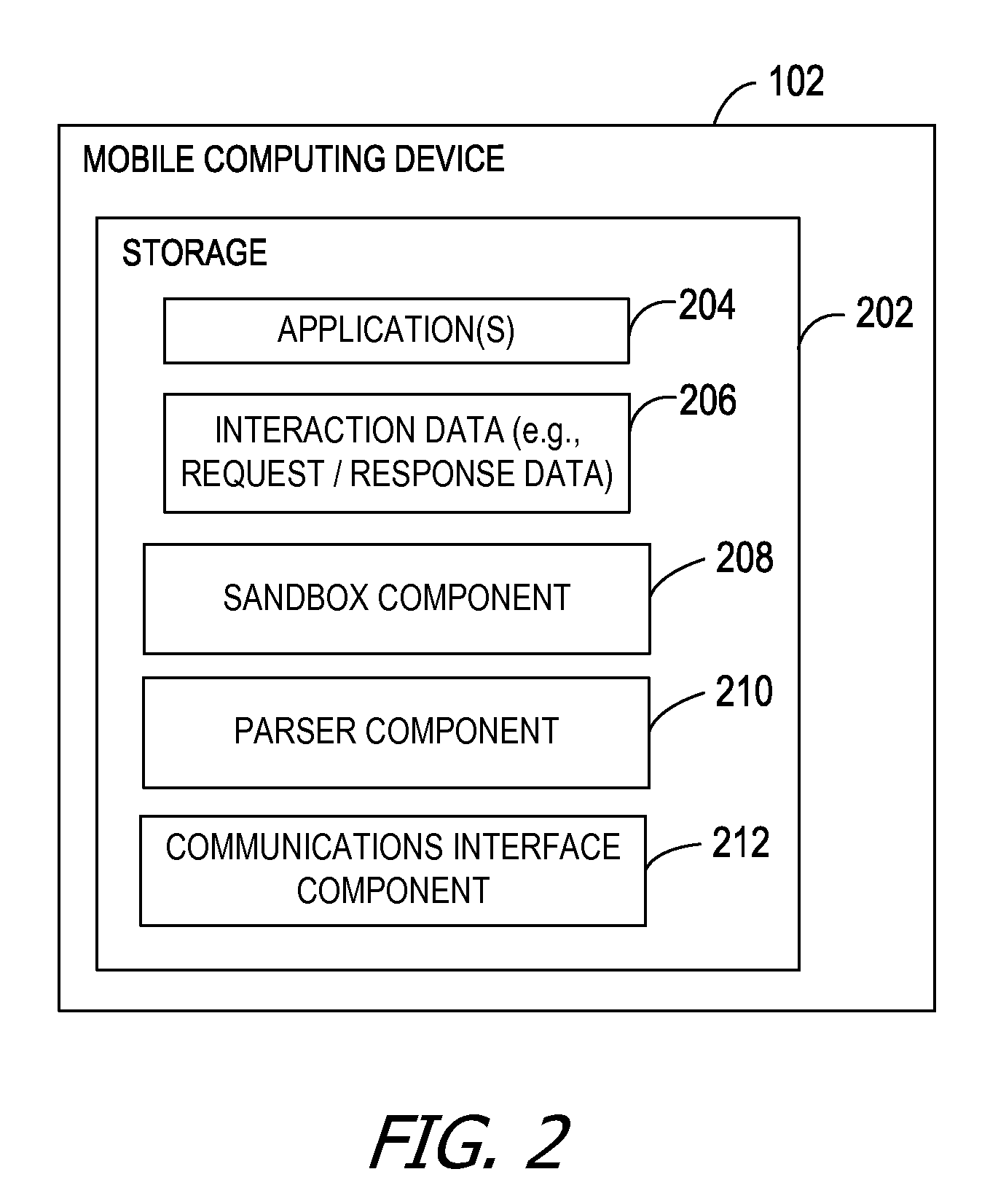
Generating sequenced instructions for connecting through captive portals
Embodiments produce a set of instructions for connecting to a network through a network access point based on data crowdsourced from mobile computing devices. The crowdsourced data describes interactions between the mobile computing devices and the network access point when establishing a connection to the network. A cloud service analyzes the crowdsourced data to identify a set of instructions for association with the network access point. The mobile computing devices replay the set of instructions when subsequently attempting to connect to the network access point.
Owner:MICROSOFT TECH LICENSING LLC
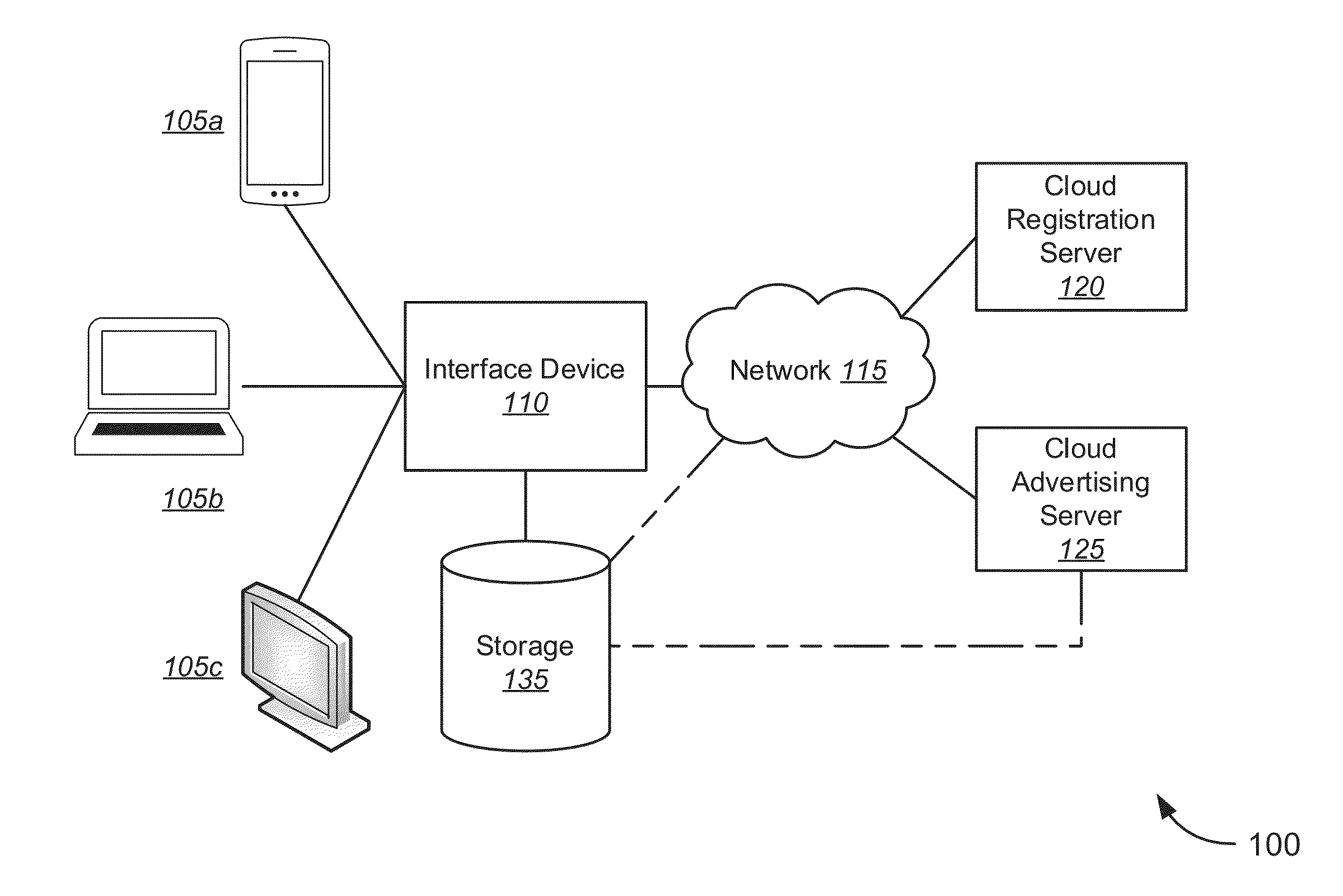
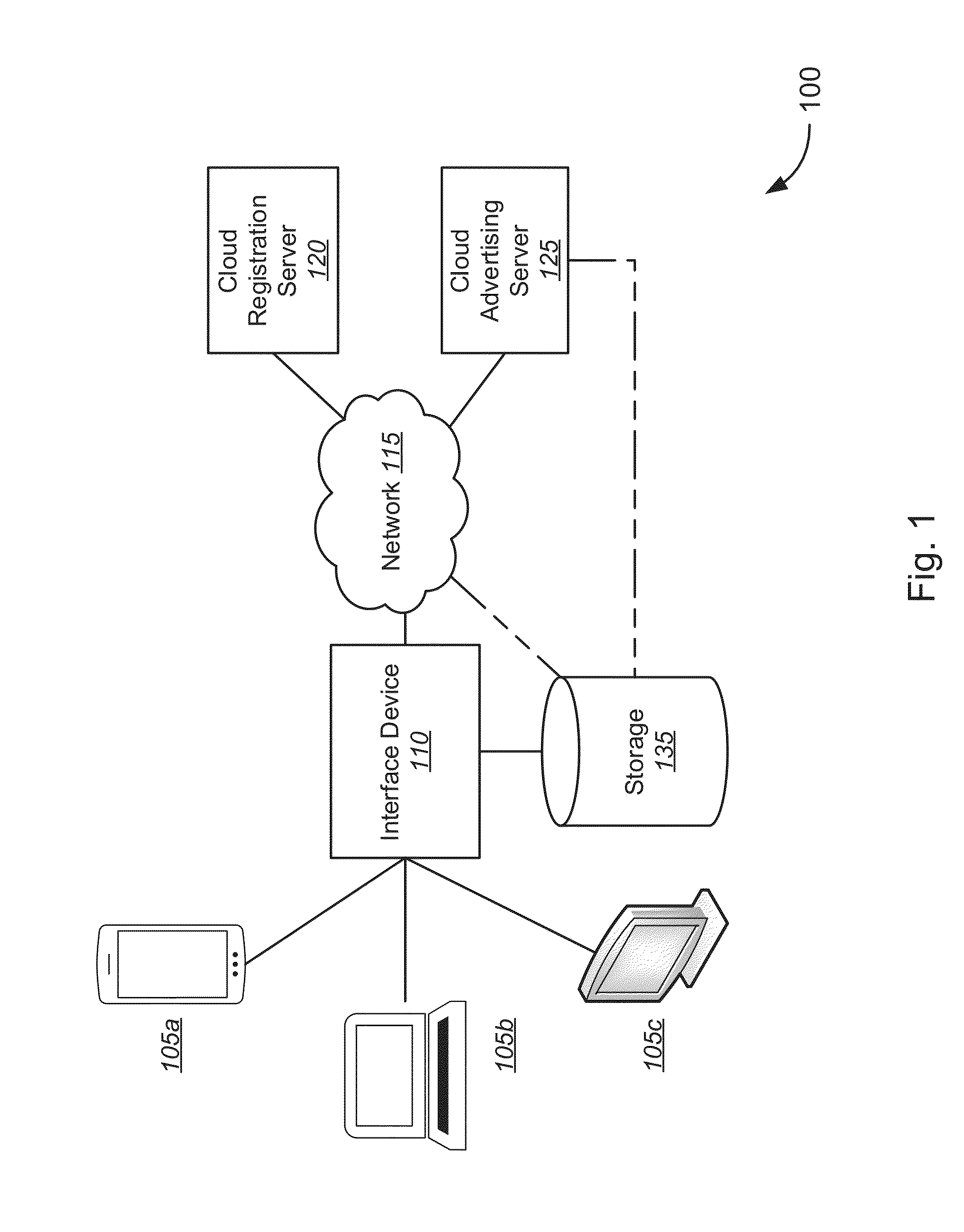
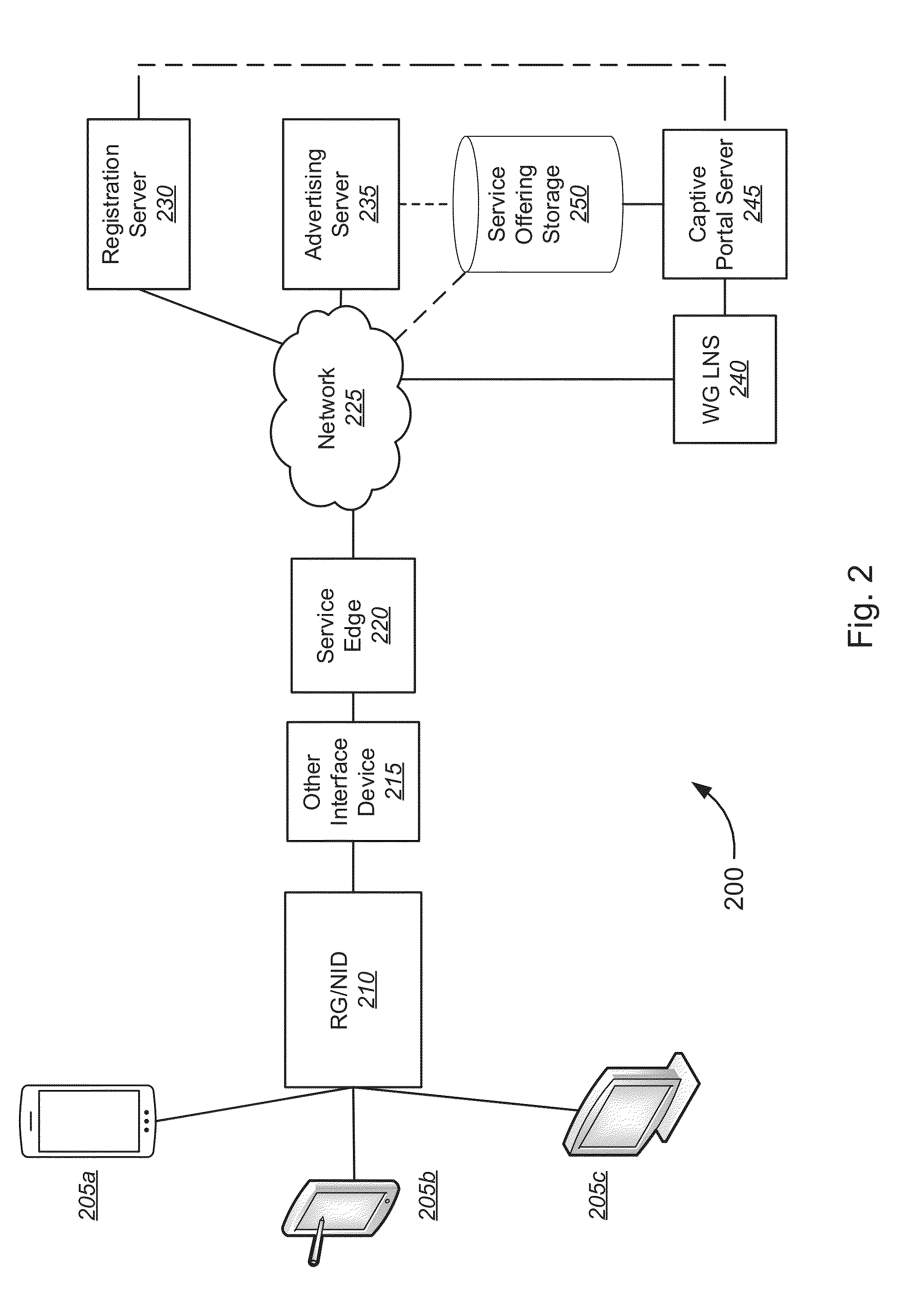
Captive Portal Service Offerings
A captive portal service offering system includes an advertising server hosting at least one captive portal service offering page, a registration server configured to provide user account information associated with a user account, and an interface device associated with the user account. The interface device is configured to retrieve, from the registration server, user account information. Based on the user account information, the interface device determines whether to present the at least one captive portal service offering page to the at least one client device. In response to the determination, the interface device directs at least one client device to the at least one captive portal service offering page. The interface device receives a user selection of the network service offered by the at least one captive portal service offering page and transmits the user selection to the registration server.
Owner:CENTURYLINK INTPROP
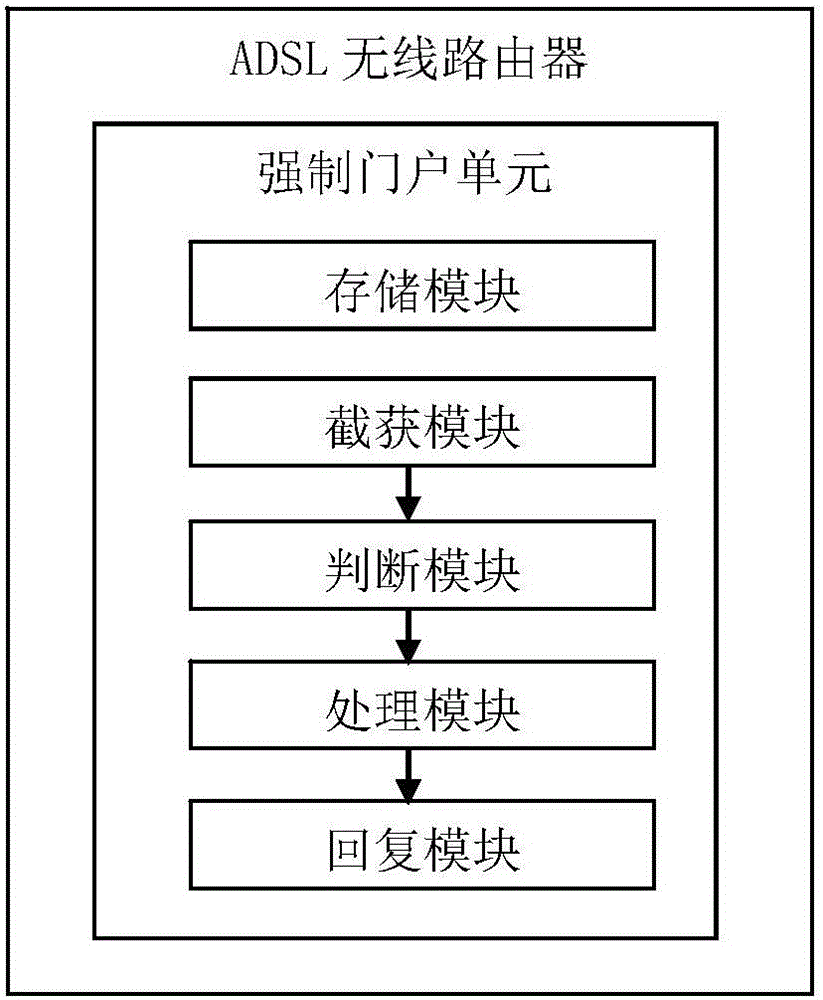
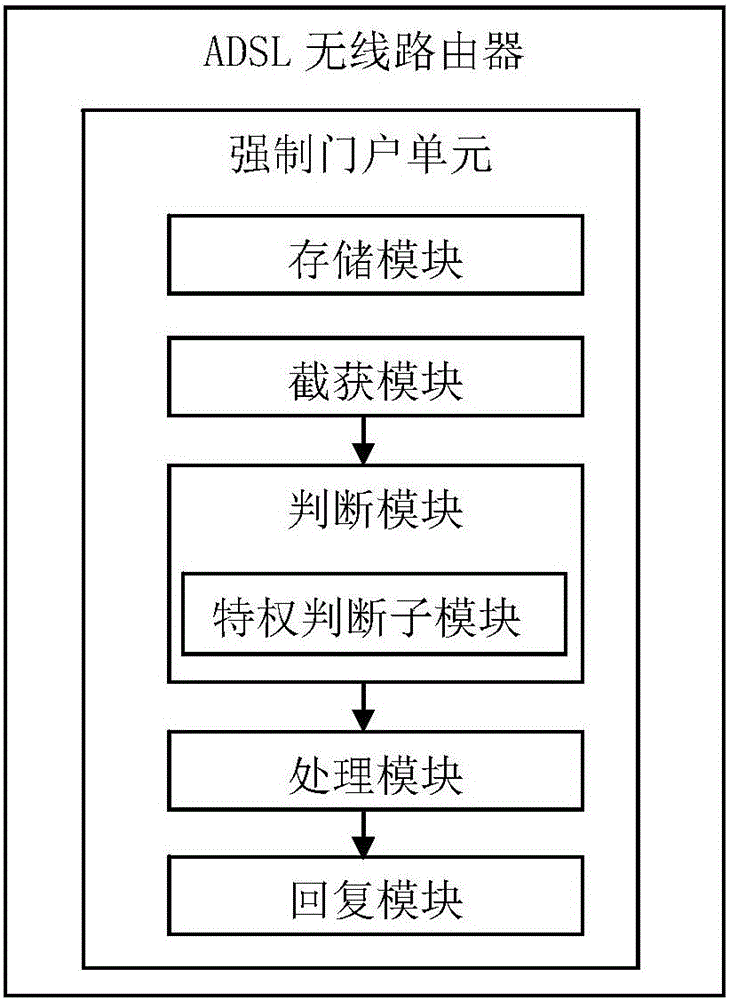
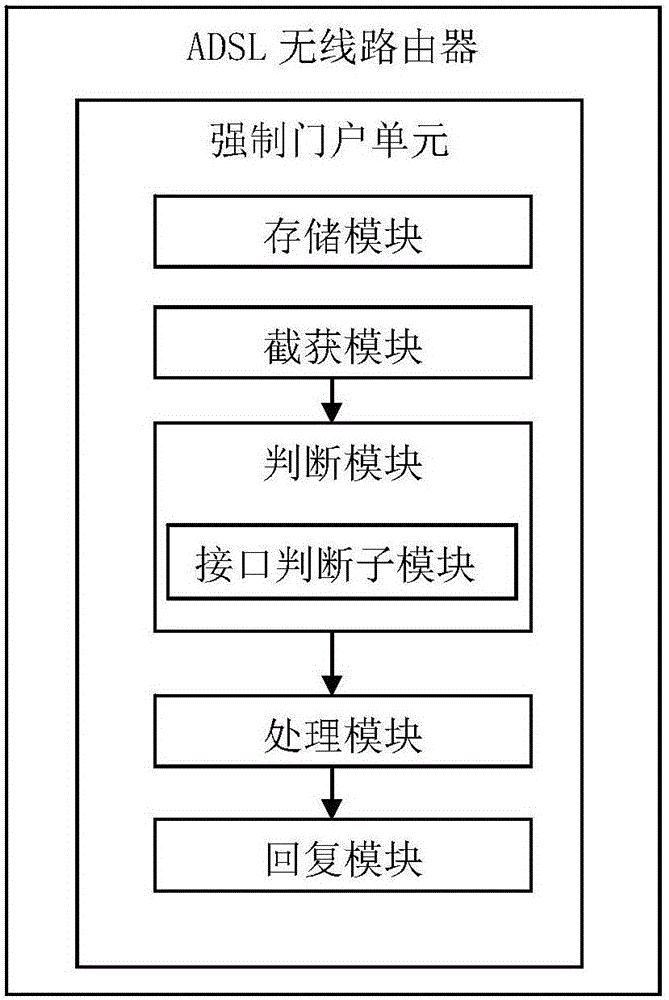
ADSL wireless router, method and system for using the same to realize captive portal under bridge pattern
The invention discloses an ADSL wireless router and a method and a system for using the router to realize a captive portal under a bridge pattern. A captive portal unit is arranged in a Linux kernel of the router. The captive portal unit comprises a storage module for storing network address of the captive portal; an intercepting and capturing module for intercepting and capturing a data message transmitted by a client; a judging module for judging whether the data message is a Get request message in a Http message; a processing module for generating a replying message comprising redirected network address according to the portal network address stored by the storing module; and a replying module for returning the replying message back to the browser of the client, wherein the browser of the client will initiate a new request to require the redirected network address so as to achieve the function of the captive portal.
Owner:湖州帷幄知识产权运营有限公司
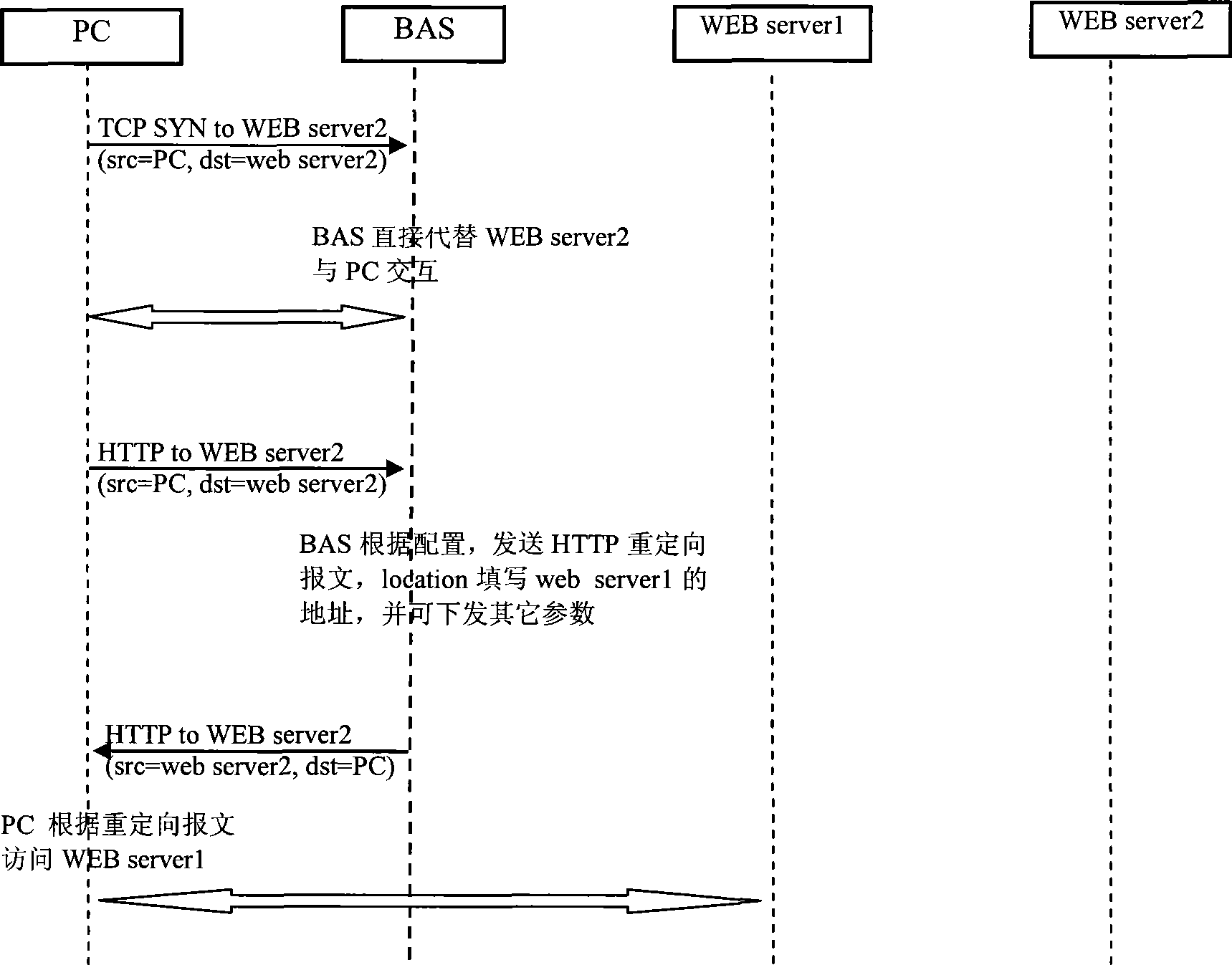
Method for realizing forced gate in WEB identification
PendingCN1598808AData switching networksSpecial data processing applicationsDomain nameWeb authentication
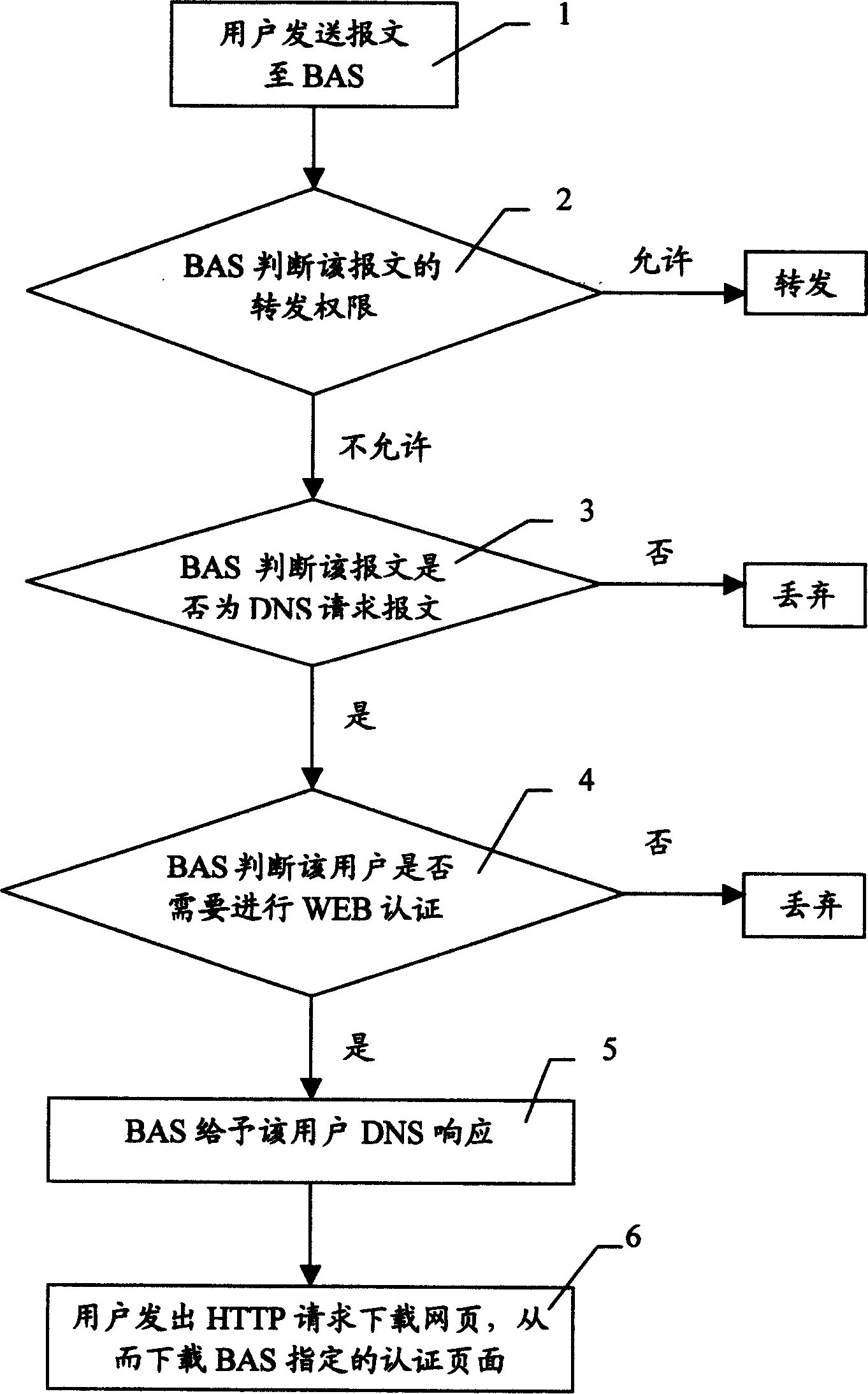
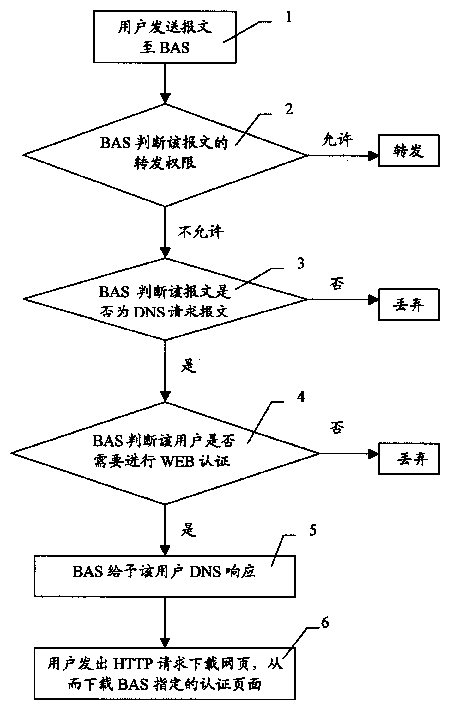
The invention discloses a method of realizing compulsory door in WEB authentication. It applies in concourse equipment under which many users is accessed. Its steps are as follows: user sends message to BAS; BAS judges transmitting rights, if not permitting, BAS judges whether the message is DNS request message, if false, then discarding, or BAS judges whether it needs WEB authentication, if false, then discarding, or BAS gives DNS response to the user; after user gets the DNS response, authentication web pages appointed by BAS is downloaded. Authentication can be done by user inputting any domain name, so it is convenient for both operation company and user.
Owner:深圳市格林耐特通信技术有限责任公司
Authenticated registration of participants for web access at live events
A captive portal technology for registering and authenticating attendees, and for collecting the personal-preferences and social-profile details of individuals participating in a live-event in real-time, is disclosed. Wi-Fi connections within the live-event location are used to register and authenticate the individuals onto a proxy server. Once registered and authenticated, the proxy-server enables a monitoring main server to collect and store the preferences, activities and social profile of the individual in a dedicated database. The authentication provides the individual access to the web for social networking, blogging and other activities at the live-event site. Authorities of live-events are thereby able can identify the individual participants and their habits to provide real time information to improve ticket sales methods, provide incentives, on-site purchase capability and focused advertisements relating to the live-event to improve the live event experience of each individual.
Owner:STAD IO
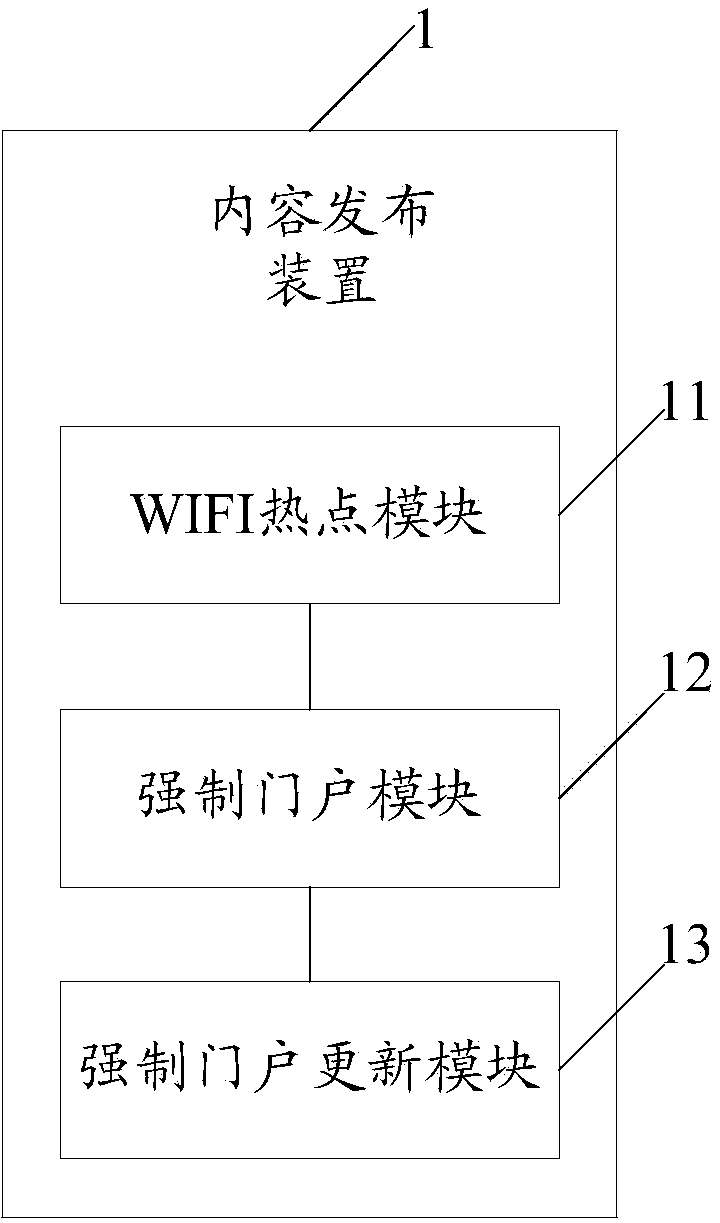
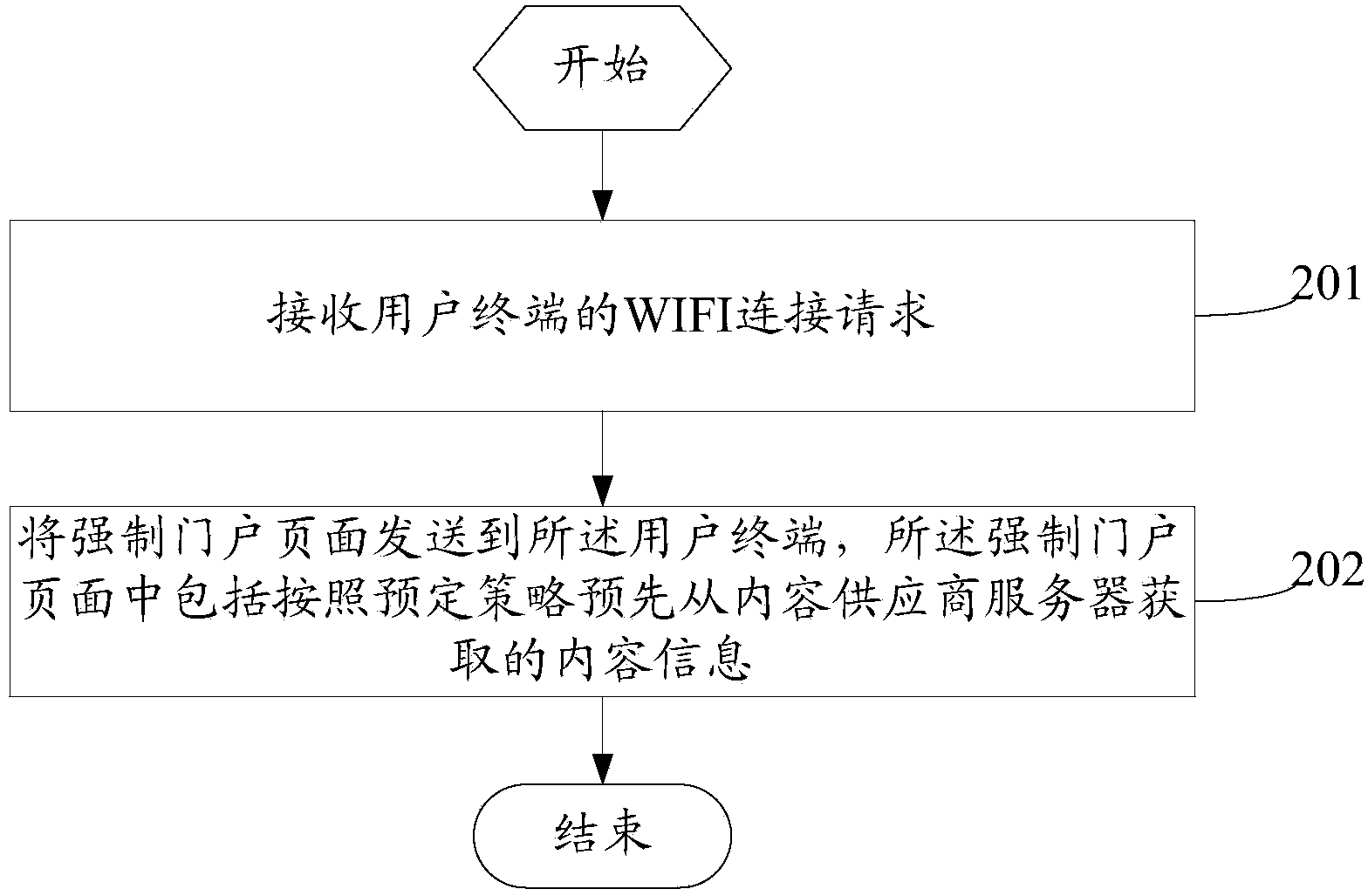
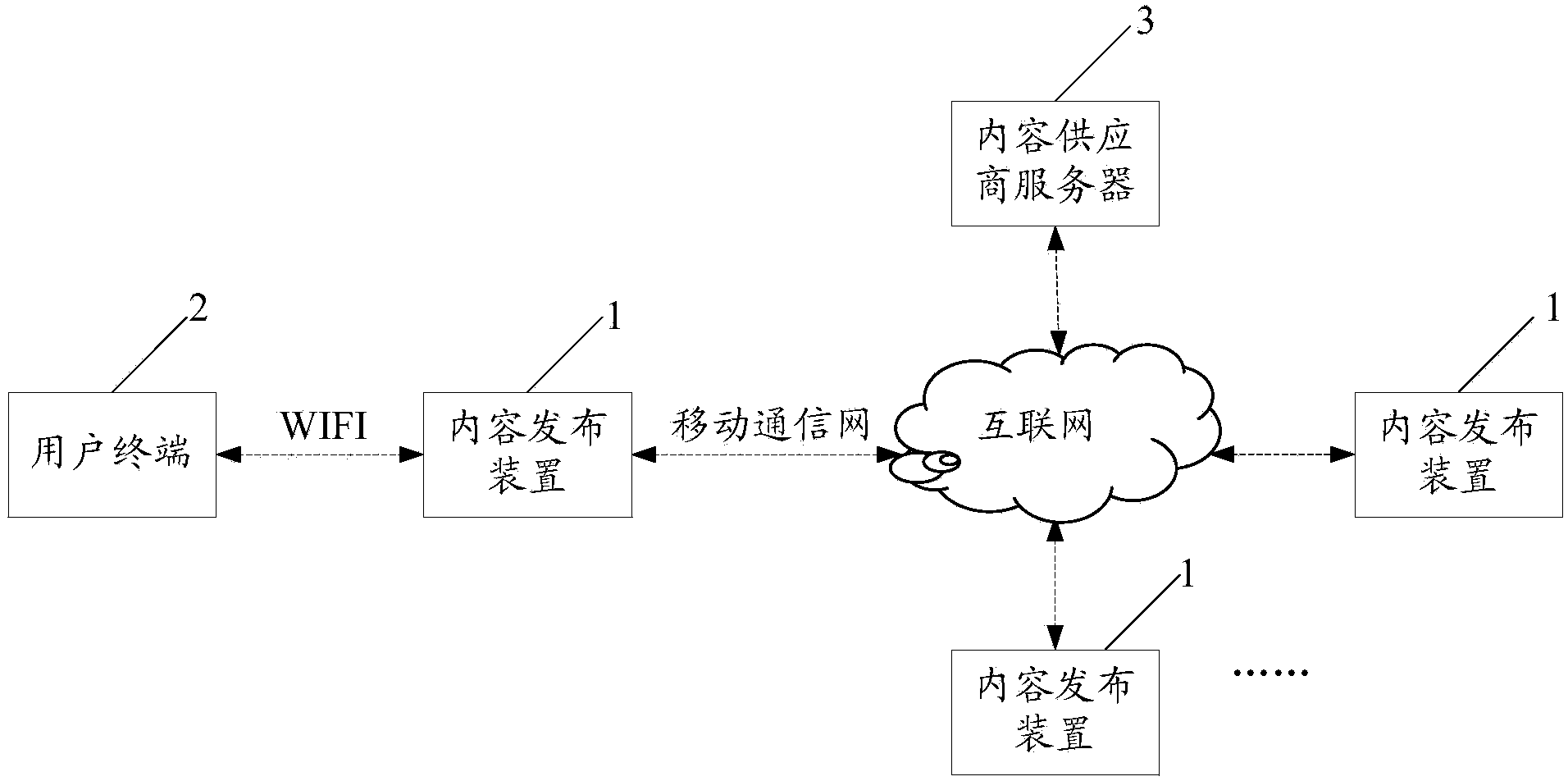
Content issuing device, method and system
InactiveCN103916407ASolve problems limited by network qualitySolve the problem of quality limitationMessaging/mailboxes/announcementsTransmissionCaptive portalComputer terminal
The invention discloses a content issuing device, method and system. When a WIFI hotspot module in the device receives a WIFI access request sent by a user terminal, content information acquired from a content provider server in advance is sent to the user terminal by a compulsory gateway module, the user terminal can directly acquire the content information without having access to the wide area network, and a compulsory gateway updating module acquires content from the content provider server according to a pre-established strategy to update the stored content information. By using the content issuing device to issue the content information, a mode of issuing the content through WIFI hotspots is provided, and the problem that a user is limited by network quality traditionally when having access to the wide area network to acquire content.
Owner:于扬
System for providing temporary internet access from a restricted local area network environment
ActiveUS9825910B2Only be usedStrict controlConnection managementRadio transmissionOn boardCaptive portal
The captive portal environment exists where there is only a single available communication service that is available to the user. An example of a captive portal environment is on board an aircraft in flight, where the passengers have no access to any communication services, other than the aircraft resident wireless Local Area Network. The Restricted LAN Internet Access System functions in the aircraft to grant the user a temporary Internet session so they can download a prerequisite application from the Internet to make use of an application / service resident on the Restricted LAN in the aircraft.
Owner:GOGO BUSINESS AVIATION LLC
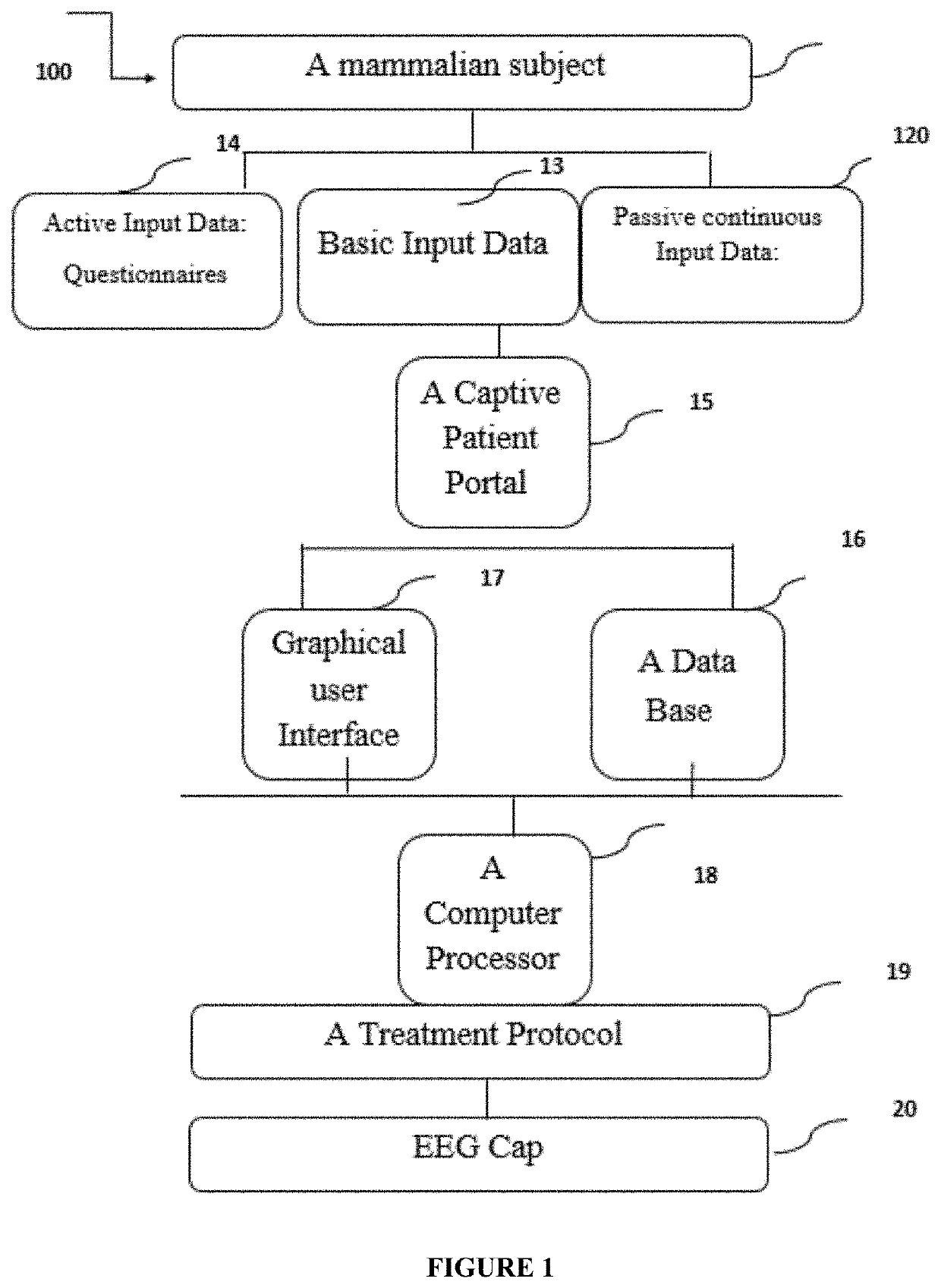
Means and methods for personalized behavioral health assessment system and treatment
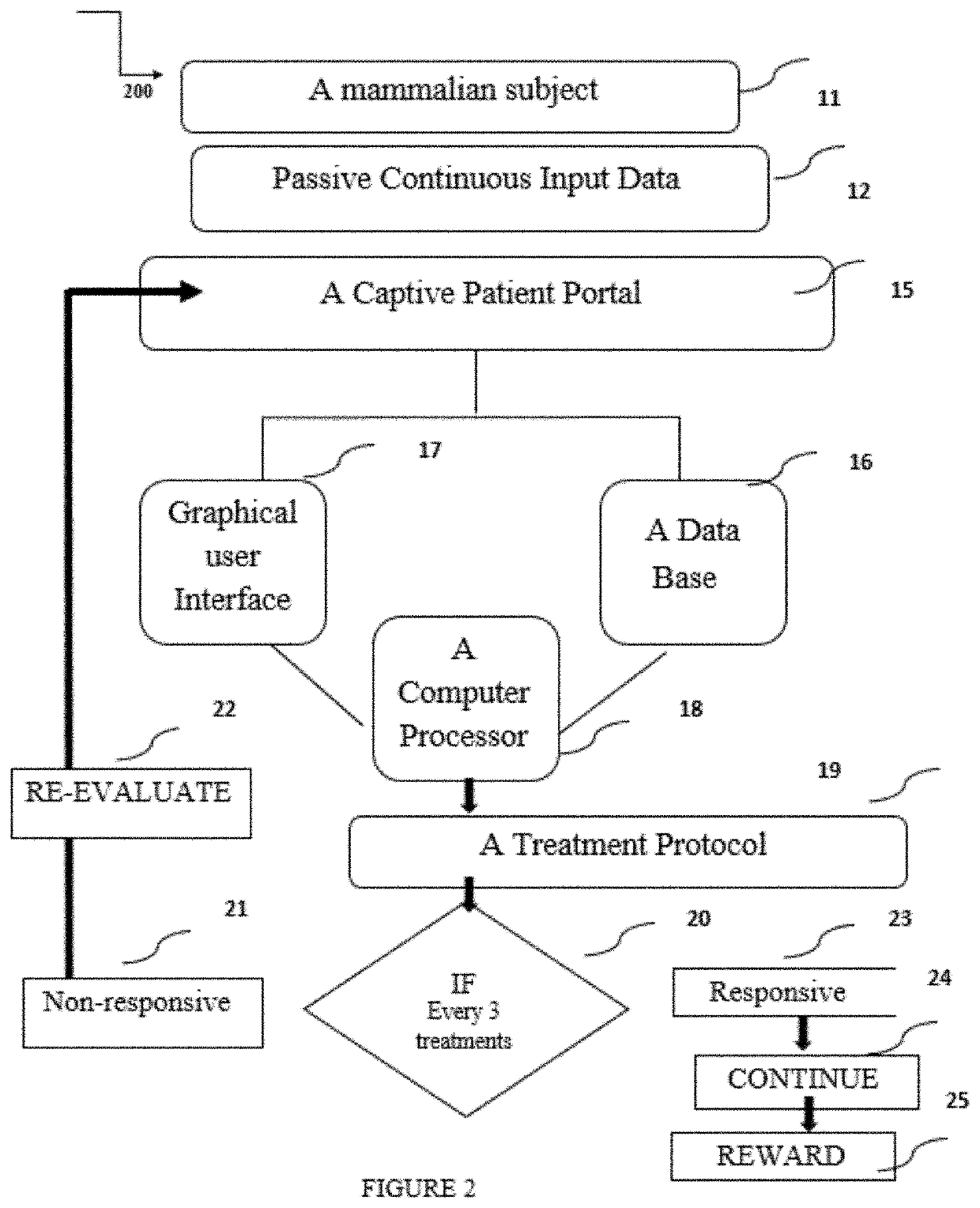
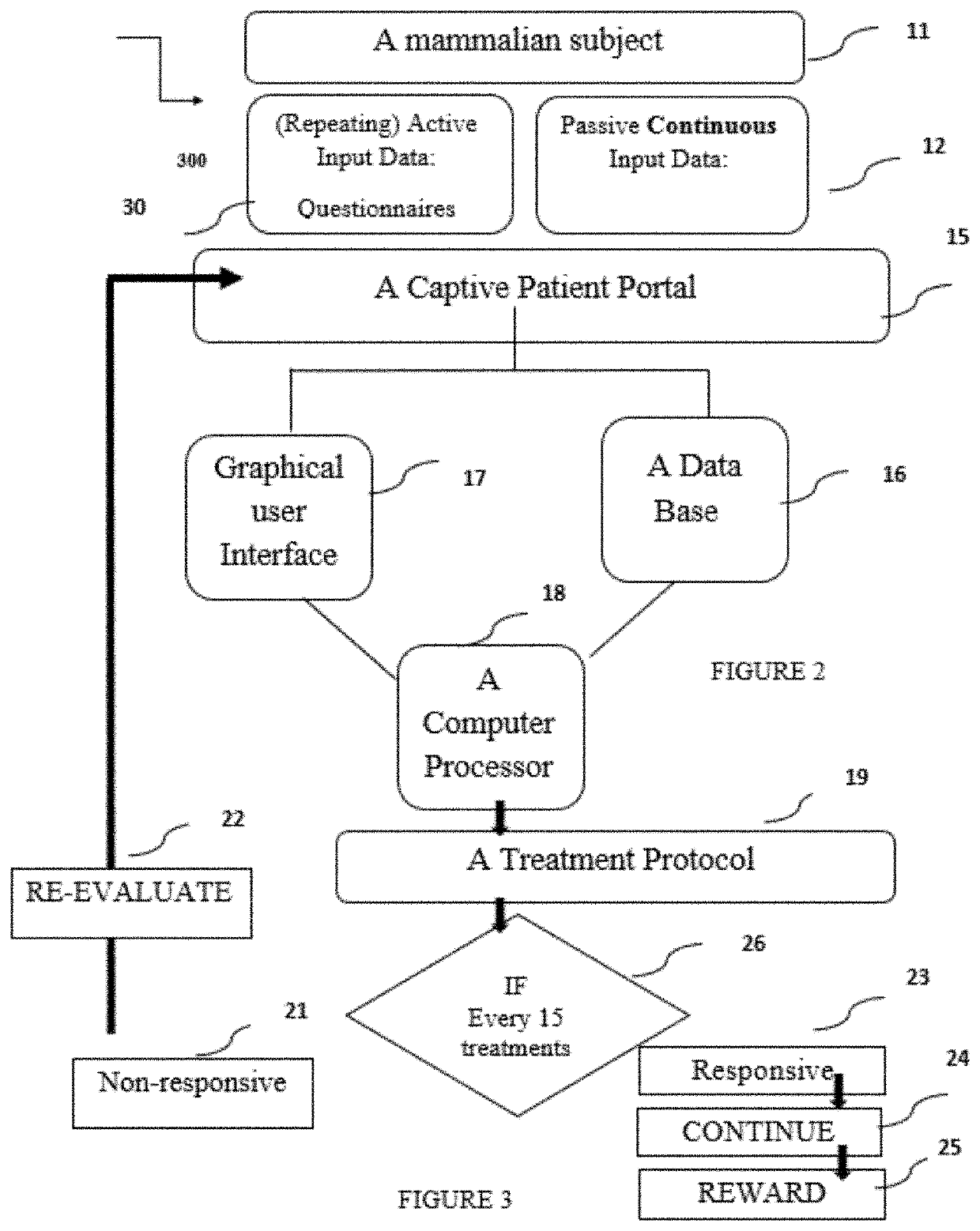
ActiveUS20210251554A1Useful in treatmentPhysical therapies and activitiesElectrotherapyCaptive portalEmergency medicine
The invention presented personalized biofeedback computerized system, an End-to-End eHealth smart platform for analysis, diagnosis and therapy of types of behavioral disorders. The system comprises a Captive Portal (CP) data input for initial input data and for continuous input data, a database comprising data, a Computer Processing Manager (CPM) for processing the patient data and the database, a Graphical User Interface (GUI) for interfacing with a user, and an Electroencephalography (EEG) or hemoencephalography (HEG) cap for stimulating predetermined areas in the brain, wherein the CPM is interconnected to the CPP, the database and the GUI, the CPM provides instructions for cranial electrode mediated stimulation to the areas in the brain according to a predetermined patient data dependent protocol, and the database provides external data. A preferred embodiment of the invention is a multilayered bio-feedbacking system.
Owner:NTW LTD
Authorizing remote access points
ActiveUS8627423B2Digital data processing detailsUser identity/authority verificationIp addressCaptive portal
Authorizing remote access points for use in a network: After the remote access point is provisioned to communicate securely to a controller using its TCP / IP address provided by a user, the remote access point is put into an un-authorized state by the controller pending further authorization. The user is presented with a secure captive portal page authenticating the end-user. User's authentication credentials are verified by the controller. After the remote access point has been authorized, the controller marks it verified as a fully functional node, and saves this state. The remote access point is provisioned with the current provisioning parameters for the remote access point as configured by the IT administrator for the end user, so that each remote access point can have unique per-user configuration applied.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
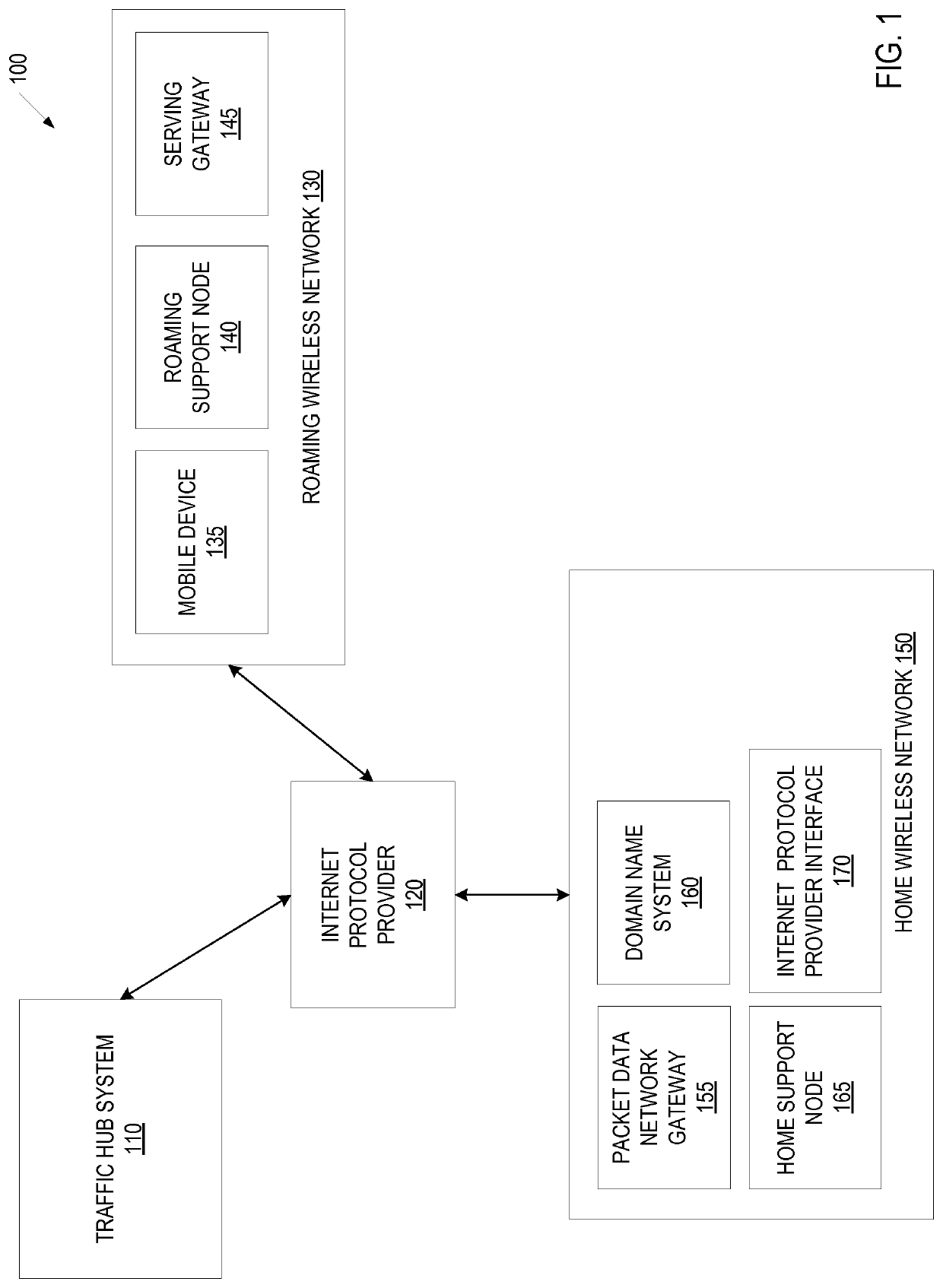
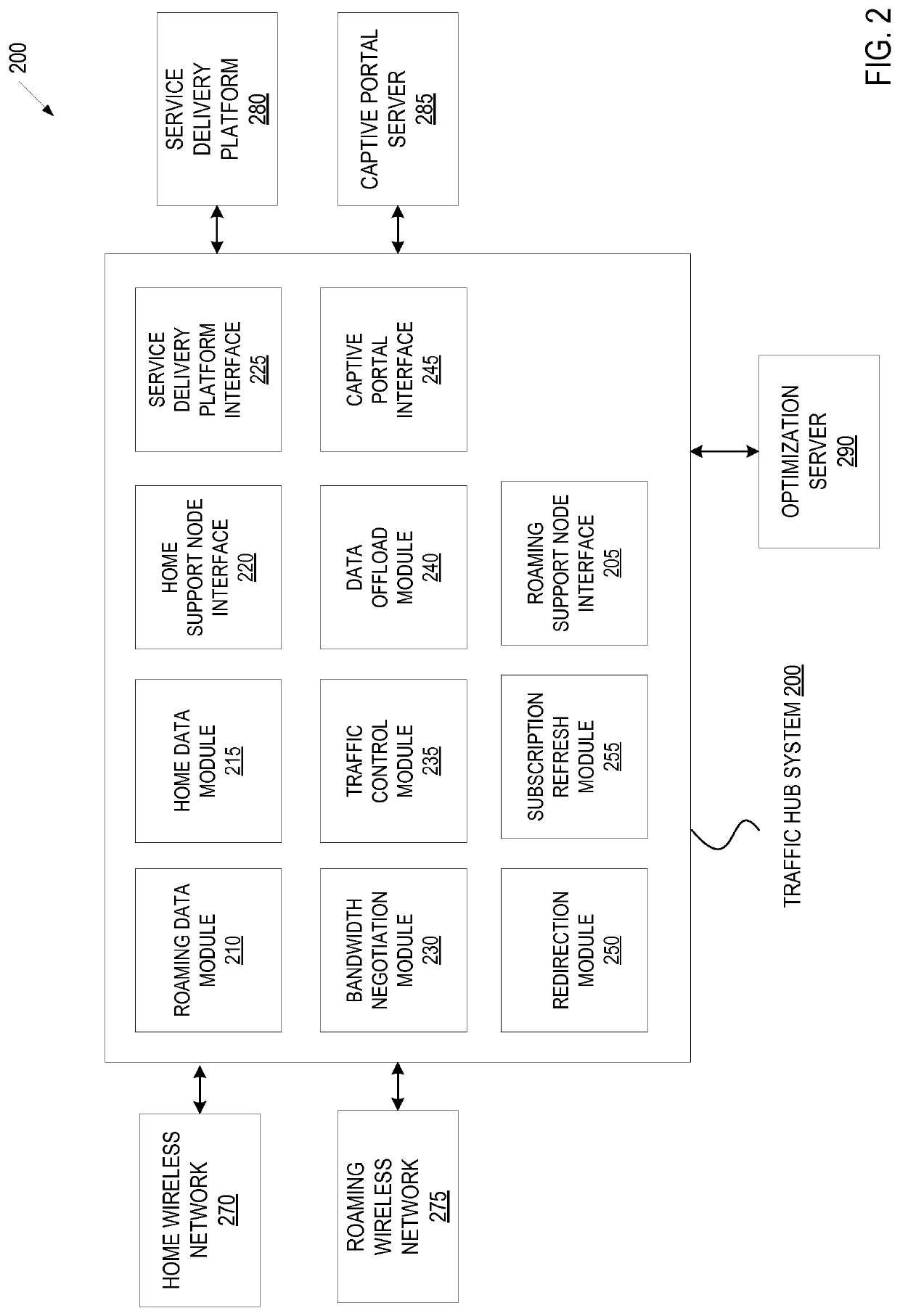
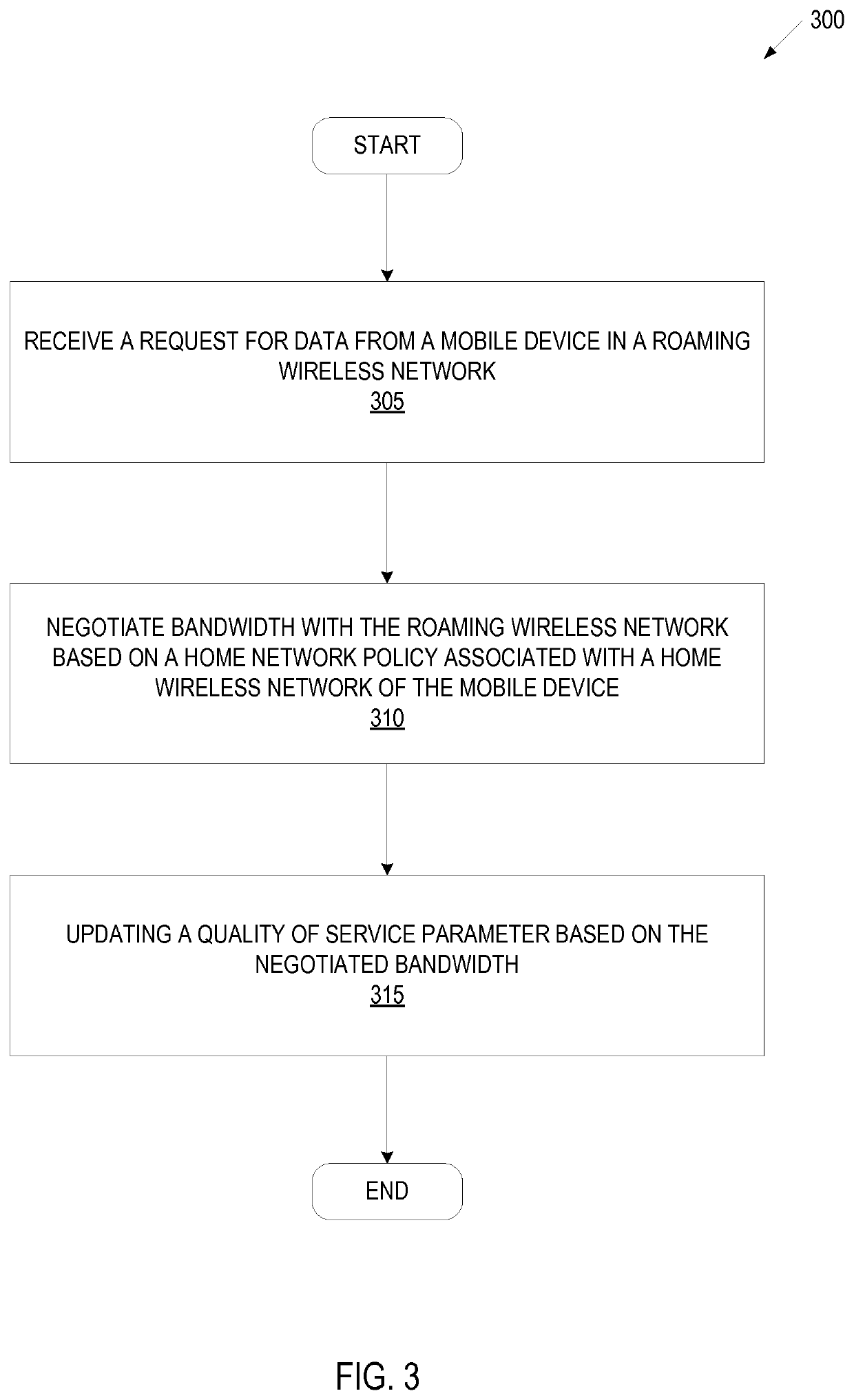
Traffic hub system to provide roaming service in a wireless environment
ActiveUS10506422B1Network traffic/resource managementConnection managementTelecommunicationsCaptive portal
A traffic hub system comprising a roaming data module to send and receive data for a roaming wireless network for a mobile device, the mobile device comprising a service utilizing a high-speed data network, a home data module to send and receive data for a home wireless network for the mobile device, the home wireless network being a different network than the roaming wireless network, the home wireless network comprising a packet data network gateway. The traffic hub system in one embodiment provides a static policy-based HTTP redirection. The traffic hub system in one embodiment, provides a dynamic policy based redirection. The traffic hub system in on embodiment, provides a seamless captive portal access. The traffic hub system in one embodiment provides data-offloading.
Owner:SYNIVERSE TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com