Method for performing forced door authentication on user in 802.1X access mode
An access method and access controller technology, applied in user identity/authority verification, digital transmission systems, electrical components, etc., to achieve the effect of effective service bearing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
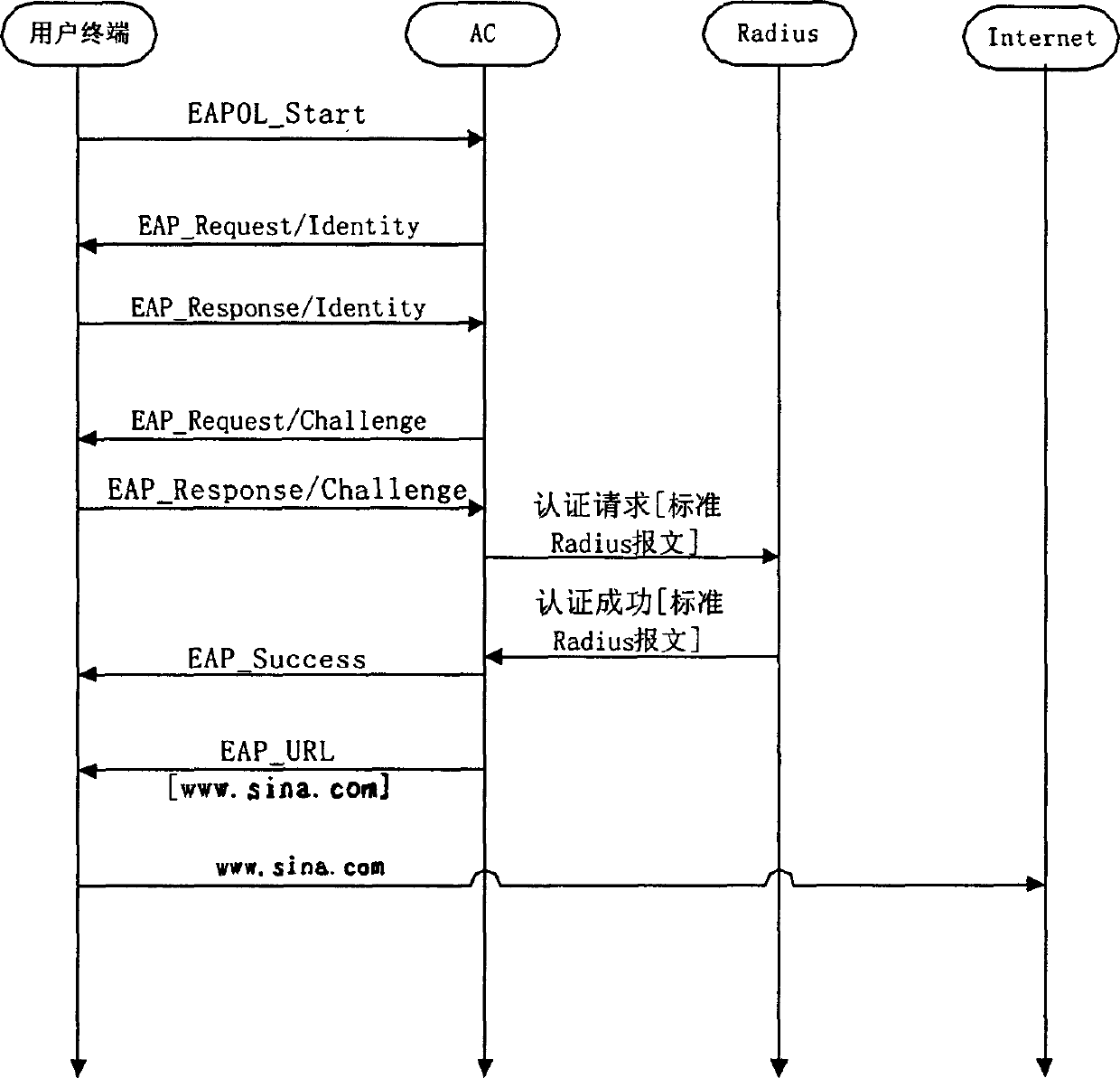
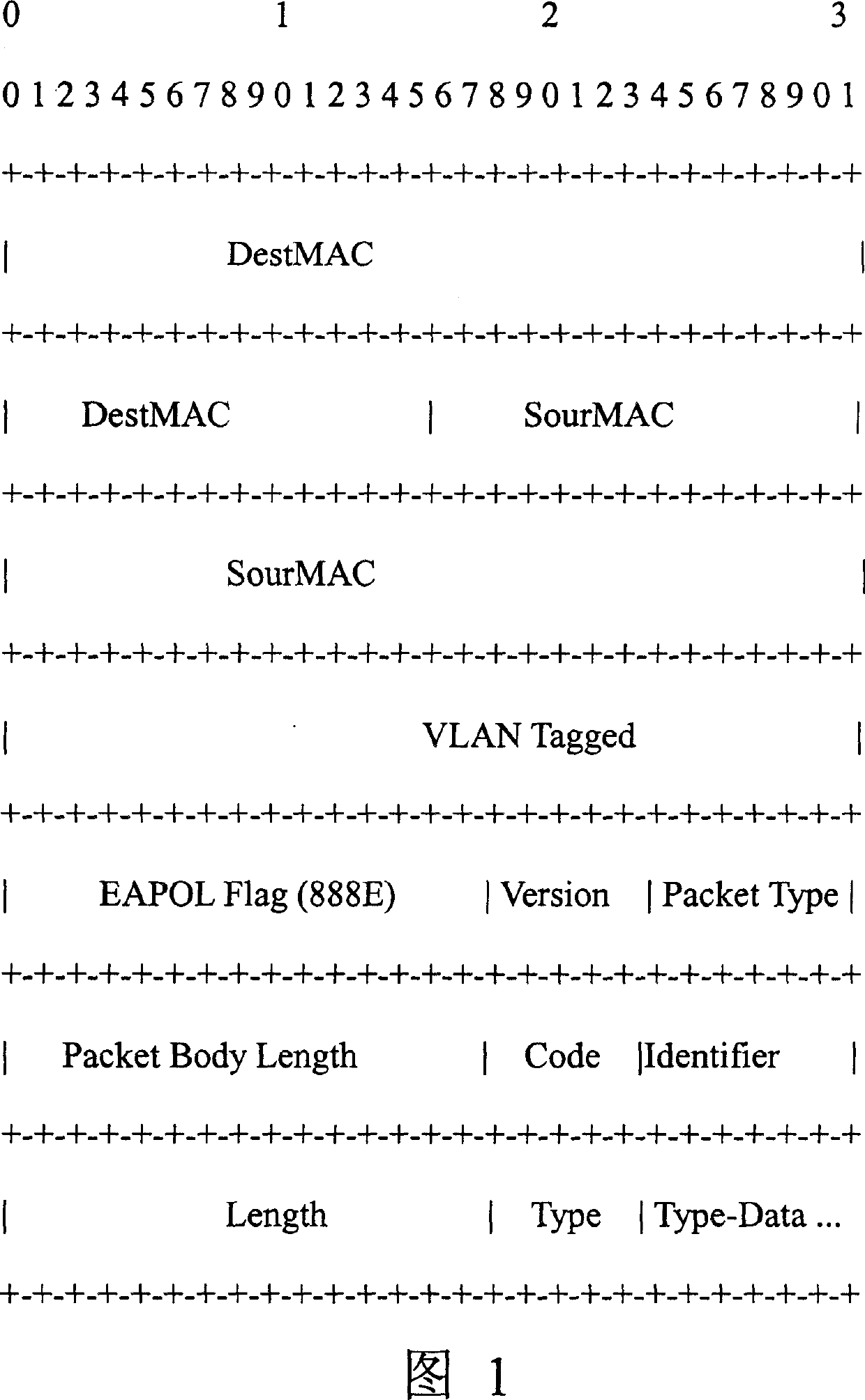
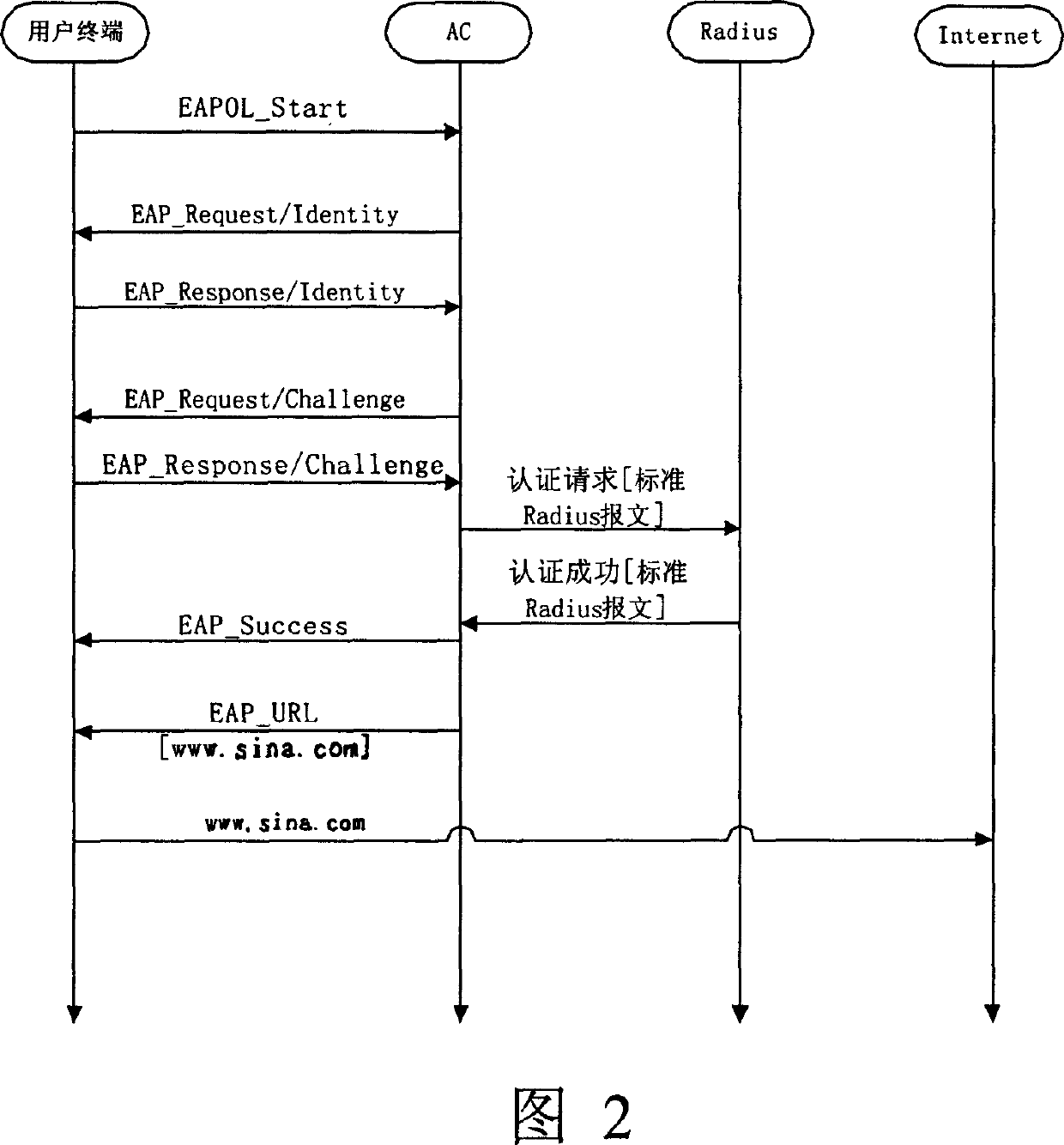
[0013] Figure 1 schematically illustrates the existing EAP protocol. Refer to Figure 1. The fields and their meanings and values are as follows:
[0014] EAPOL Flag: is the flag of the extensible authentication protocol carried by the LAN, and its value is 0x888E
[0015] Version: Version number, its value is 0x01
[0016] Packet Type: packet type, its value and meaning are
[0017] 0 EAP-Package
[0018] 1 EAPOL-Start
[0019] 2 EAPOL-login refused
[0020] 3 EAPOL-Password
[0021] 4 EAPOL-Package-ASF-Warning
[0022] Packet Body Length: This value field is two bytes, indicating the length of the EAPOL packet. The packet body includes DestMAC (sink MAC), SourMAC (source MAC), VLAN Tagged (virtual local area network tag), Version (version), and Packet Type (Packet Type), Packet Body Length (Packet Body Length) and all subsequent data.
[0023] Code: Code, its value and meaning are
[0024] 1 request
[0025] 2 Answer
[0026] 3 success
[0027] 4 failed
[0028] Identifier: Ide...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com